| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Thursday, 09 November
18:40
We've added 25 new math tools catonmat.net
Team Browserling keeps shipping!
Last week we added 25 new png tools and today we just added 25 new tools to our Online MATH Tools collection.
Here are the new math tools:
- Generate Pascal's Triangle
- Find All Divisors of a Number
- Find Prime Factors of a Number
- Test if a Number is a Prime Number
- Test if a Number is a Fibonacci Number
- Generate Abundant Number Sequence
- Generate Deficient Number Sequence
- Generate Almost Perfect Numbers
- Generate Moser-de Bruijn Sequence
- Generate Even Number Sequence
- Generate Odd Number Sequence
- Generate a Random Matrix
- Generate an Identity Matrix
- Add Matrices
- Subtract Matrices
- Generate Twindragon Curve
- Generate Terdragon Curve
- Generate Quaddragon Curve
- Generate Hexadragon Curve
- Generate Koch Antisnowflake
- Generate Koch Triangle
- Generate Koch Polyflake
- Generate Quadratic Koch Island
- ...
Thursday, 26 October
17:10
We've added another 25 new png tools catonmat.net
Team Browserling keeps shipping!
Last week we added 20 new jpg tools and and today we just added another 25 new tools to our Online PNG Tools collection.
We've done our job and now it's Google's job to index them and rank them well.
Here are the new png tools:
- Change PNG Brightness
- Change PNG Contrast
- Add Sepia Tone to a PNG
- Change PNG Hue
- Invert PNG Colors
- Convert ICO to PNG
- Optimize a PNG
- Create Symmetric PNG
- Generate a Colorful PNG
- Create a PNG from an Emoji
- Add Artifacts to PNG
- Generate 1-by-1 Pixel PNG
- Convert PNG to Two Colors
- Convert PNG to Black and White
- Create a Monochrome PNG
- Add Dithering to a PNG
- Decrease PNG Color Count
- Add a Whirl to a PNG
- Quantize a PNG
- Wrap a PNG in a Polaroid
- Posterize a PNG
- Remove PNG Chroma Key
- Generate a Single-color PNG
- Generate White Noise PNG
- Er...
Monday, 22 May
01:23
rogue and shes working around the clock to stop it saying sexually explicit things Lifeboat News: The Blog
01:22
Sorry, Elon Musk To Suggest Remote Work Isnt Morally Right is a Flawed Attempt to Push Your In-Person Work Agenda. Heres Why Lifeboat News: The Blog

Its as though Musk views in-person work as a kind of hazing ritual he and others did it, so you have to do it too. Well, as my mom frequently said when I proposed doing something dumb because others did it, If all your friends jumped off a bridge, would you?
Picture this: Musk standing on the precipice of the Golden Gate Bridge, urging us all to leap into the frigid waters below simply because he took the plunge. While his bravado might be admired by some, its not a practical or sustainable model for the future of work. Heres a thought: rather than Musks daredevil dive into the deep abyss of forced in-office work, perhaps we should consider a more measured, flexible and hybrid approach to work, one that incorporates both remote and in-person options, as I tell my clients.
Related: Employers: Hybrid Work is Not The Problem Your Guidelines Are. Heres Why and How to Fix Them.
01:22
Superconducting qubits have passed a key quantum test Lifeboat News: The Blog
A Bell test can confirm whether two systems are truly entangled it has now been used to confirm entanglement between qubits in a superconducting circuits.
By Leah Crane
01:00
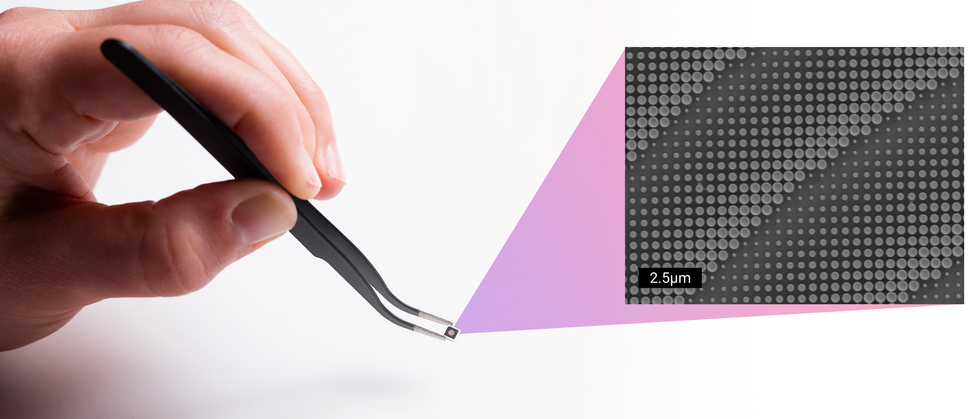
Flat Lenses Made of Nanostructures Transform Tiny Cameras and Projectors IEEE Spectrum

Inside todays computers, phones, and other mobile devices, more and more sensors, processors, and other electronics are fighting for space. Taking up a big part of this valuable real estate are the camerasjust about every gadget needs a camera, or two, three, or more. And the most space-consuming part of the camera is the lens.
The lenses in our mobile devices typically collect and direct incoming light by refraction, using a curve in a transparent material, usually plastic, to bend the rays. So these lenses cant shrink much more than they already have: To make a camera small, the lens must have a short focal length; but the shorter the focal length, the greater the curvature and therefore the thickness at the center. These highly curved lenses also suffer from all sorts of aberrations, so camera-module manufacturers use multiple lenses to compensate, adding to the cameras bulk.
With todays lenses, the size of the camera and image quality are pulling in different directions. The only way to make lenses smaller and better is to replace refractive lenses with a different technology.
That technology exists. Its the metalens, a device developed at Harvard and commercialized at Metalenz, where I am an applications engineer. We create these devices using traditional semiconductor-processing techniques to build nanostructures onto a flat surface. These nanostructures use a phenomenon called metasurface optics to direct and focus light. These lenses can be extremely thina few hundred micrometers thick, about twice the thickness of a human hair. And we can combine the functionality of multiple curved lenses into just one of our devices, further addressing the space crunch and opening up the possibility of new uses for cameras in mobile devices.
Centuries of lens alternatives
Before I tell you how the metalens evolved and how it works, consider a few previous efforts to replace the traditional curved lens.
Conceptually, any device that manipulates light does so by altering its three fundamental properties: phase, polarization, and intensity. The idea that any wave or wave field can be deconstructed down to these properties was proposed by Christiaan Huygens in 1678 and is a guiding principle in all of optics.
 ...
...
00:58
Links 21/05/2023: Unifont 15.0.02 and KDE Plasma 6 Plans Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
00:26
The Moon Society's Lunar Development Conference 2023 will be held July 15-16 in cyberspace. Lifeboat News
The Moon Societys Lunar Development Conference 2023 will be held July 1516 in cyberspace.
Our Niklas Jrvstrt and Madhu Thangavelu will be speaking.00:00
Intel Suggests Dropping Everything But 64-Bit From X86 With Its X86-S Proposal Hackaday

In a move that has a significant part of the internet flashing back to the innocent days of 2001 when Intel launched its Itanium architecture as a replacement for the then 32-bit only x86 architecture before it getting bludgeoned by AMDs competing x86_64 architecture Intel has now released a whitepaper with associated X86-S specification that seeks to probe the communitys thoughts on it essentially removing all pre-x86_64 features out of x86 CPUs.
While today you can essentially still install your copy of MSDOS 6.11 on a brand-new Intel Core i7 system, with some caveats, its undeniable that to most users of PCs the removal of 16 and 32-bit mode would likely go by unnoticed, as well as the suggested removal of rings 1 and 2, as well as range of other low-level (I/O) features. Rather than the boot process going from real-mode 16-bit to protected mode, and from 32- to 64-bit mode, the system would boot straight into the 64-bit mode which Intel figures is what everyone uses anyway.
Where things get a bit hazy is that on this theoretical X86-S you cannot just install and boot your current 64-bit operating systems, as they have no concept of this new boot procedure, or the other low-level features that got dropped. This is whe...
Sunday, 21 May
23:25
Neeva, the would-be Google competitor, is shutting down its search engine Lifeboat News: The Blog
Weve discovered that it is one thing to build a search engine, and an entirely different thing to convince regular users of the need to switch to a better choice.
Neeva, which for a while looked like one of the startups with a real chance to challenge the supremacy of Google Search, announced on Saturday that it is shutting down its search engine. The company says its pivoting to AI and may be acquired by Snowflake, The Information.
Building search engines is hard, Neeva co-founders Sridhar Ramaswamy and Vivek Raghunathan wrote in a blog post announcing the shutdown.
Neeva was ahead of Google on a lot of things in search but still couldnt make users switch.
23:24
Grammarlys New CEO On Why ChatGPT Wont Kill His Business Lifeboat News: The Blog
Theres no kind of a priori right of this technology to upend our world, our lives and displace our own capabilities. I want technology to augment us, not displace us.
But the technology thats enabled Grammarly to expand its core offering could also disrupt it.
Fresh to the CEO role, Rahul Roy-Chowdhury talks about AI legislation, Grammarlys Russia ban and trying to leverage disruptive technologies.
23:24
Who Is Going to Regulate AI? Lifeboat News: The Blog
Summary.
As businesses and governments race to make sense of the impacts of new, powerful AI systems, governments around the world are jostling to take the lead on regulation. Business leaders should be focused on who is likely to win this race, moreso than the questions of how or even when AI will be regulated. Whether Congress, the European Commission, China, or even U.S. states or courts take the lead will determine both the speed and trajectory of AIs transformation of the global economy, potentially protecting some industries or limiting the ability of all companies to use the technology to interact directly with consumers.
Page-utils class= article-utilsvertical hide-for-print data-js-target= page-utils data-id= tag: blogs.harvardbusiness.org, 2007/03/31:999.357112 data-title= Who Is Going to Regulate AI? data-url=/2023/05/who-is-going-to-regulate-ai data-topic= Government policy and regulation data-authors= Blair Levin; Larry Downes data-content-type= Digital Article data-content-image=/resources/images/article_assets/2023/05/May23_28_5389503-383x215.jpg data-summary=
As the world reckons with the impact of powerful new AI systems, governments are jostling to lead the regulatory charge and shape how this technology will grow.
23:24
How do you solve a problem like out-of-control AI? Lifeboat News: The Blog
Plus: The open-source AI boom is built on Big Techs handouts. How long will it last?
Last week Google revealed it is going all in on generative AI. At its annual I/O conference, the company announced it plans to embed AI tools into virtually all of its products, from Google Docs to coding and online search. (Read my story here.)
Googles announcement is a huge deal. Billions of people will now get access to powerful, cutting-edge AI models to help them do all sorts of tasks, from generating text to answering queries to writing and debugging code. As MIT Technology Reviews editor in chief, Mat Honan, writes in his analysis of I/O, it is clear AI is now Googles core product.
23:24
Chatbot Arena helps you find the best open-source chatbot Lifeboat News: The Blog
Until now, there has been no easy way to compare the quality of open-source models. An e-sports-inspired system could help.
The Large Model System Organization (LMSYS), which is behind the open-source model Vicuna, has launched the benchmark platform Chatbot Arena to compare the performance of large language models. Different models compete against each other in anonymous, randomly selected duels. Users then rate the performance of the models by voting for their preferred answer.
23:24
ChatGPTs clever way of balancing 9 eggs with other objects convinced some Microsoft researchers that AI is becoming more like humans Lifeboat News: The Blog
Microsoft researchers asked GPT-4 to stack nine eggs with other objects; its grid solution startled them because it was so clever.
23:23
China is using AI to raise the dead, and give people one last chance to say goodbye Lifeboat News: The Blog
They wanted to speak to their dead grandparents one last time, so they used artificial intelligence to rebuild loved ones theyd lost.
23:19
Dark Web ChatGPT Unleashed: Meet DarkBERT SoylentNews
A language model trained on the fringes of the dark web... for science:
We're still early in the snowball effect unleashed by the release of Large Language Models (LLMs) like ChatGPT into the wild. Paired with the open-sourcing of other GPT (Generative Pre-Trained Transformer) models, the number of applications employing AI is exploding; and as we know, ChatGPT itself can be used to create highly advanced malware.
As time passes, applied LLMs will only increase, each specializing in their own area, trained on carefully curated data for a specific purpose. And one such application just dropped, one that was trained on data from the dark web itself. DarkBERT, as its South Korean creators called it, has arrived follow that link for the release paper, which gives an overall introduction to the dark web itself.
DarkBERT is based on the RoBERTa architecture, an AI approach developed back in 2019. It has seen a renaissance of sorts, with researchers discovering it actually had more performance to give than could be extracted from it in 2019. It seems the model was severely undertrained when released, far below its maximum efficiency.
Originally spotted on The Eponymous Pickle.
Related: People are Already Trying to Get ChatGPT to Write Malware
Read more of this story at SoylentNews.
23:07
Security Affairs newsletter Round 420 by Pierluigi Paganini International edition Security Affairs
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are free for you in your email box.
Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press.
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections where is reported
Securityaffairs or my name Pierluigi Paganini
Please nominate Security Affairs as your favorite blog.
Nominate Pierluigi Paganini and Security Affairs here here: https://docs.google.com/forms/d/e/1FAIpQLSepvnj8b7QzMdLh7vWEDQDqohjBUsHyn3x3xRdYGCetwVy2DA/viewform
22:51
Mr. Thomas Woodruffs Francis Rothbart!: Not Really a Review Random Thoughts
I was idly browsing twitter when I saw the news that Thomas Woodruffs comic book had been nominated for four (!) Eisner awards, and my first thought was man, the public relations dept at Fantagraphics have really done their jobs here presumably by sending copies of the book to all the Eisner judges, but I see now that that wouldnt be that expensive:
The 2023 Eisner Awards judging panel consists of librarian Moni Barrette, educator/collector Peter Jones, retailer Jen King, journalist Sean Kleefeld, scholar/comics creator A. David Lewis, and comics instructor/curator TJ Shevlin.
Because the book is shit. I mean, its really awful. I guess you could make a case for its so transgressive, dude, but its really just shitty and a waste of time. My main reaction when I read it was dude, are you OK?
Which made me read some of the reactions to the announcement and boy, some of Woodruffs previous students at the SVA piped up:
22:42
Arch Linux Completes Its Git Migration Phoronix
Arch Linux on Friday began its Git repository migration and as part of that discontinuing SVN access and some changes to how their package repositories are setup. Arch Linux's Git migration has now been successfully completed...
21:50
Links 21/05/2023: WordPress 6.2.2 and ESPClicker Techrights
![]()
Contents
-
GNU/Linux
-
Applications
-
Linux Links 7 Best Free and Open Source Replacements for ls
ls is a command to list computer files. ls is specified by POSIX and the Single UNIX Specification. When invoked without any arguments, ls lists the files in the current working directory.
The GNU Core Utilities or coreutils is a package of GNU software containing implementations for many of the basic tools, such as cat, ls, and rm, which are used on Unix-like operating systems.
There are many enterprising developers that look to update and enhance many of the commands available in coreutils. ls is no exception.
Heres our r...
-
-
21:45
Gemini Links 21/05/2023: ScummVM and Lagrange 1.16 Techrights
-
Gemini* and Gopher
-
Personal
-
Angel Rocks Hike 2023-05-20 (east of Fairbanks, AK, USA)
Emily and I went on a hike today to Angel Rocks, a trail east of Fairbanks, which goes along the Yukon River and then passes several tors, or rocky outcroppings. I have many pictures to share, so Ill just list them each with a brief description.
-
SpellBinding: DGIZNRL Wordo: ROBES
-
its you and me, phone entertain me
The ego-driven, hyped privilege of the mental/emotional DEMAND that a device I own *entertain* me. And also, why? Entertainment is good and needed in the world, especially that rendering physiological stimulation, feedback of positive consequence, et al., but why the effort/stress of picking up my phone and thinking: ok, lets find some digital amusement
-
-
Technical
-
To remember that ScummVM is great
I had a knowledge of ScummVM existence for a long time but Ive been playing only occasionally in several games for a short while that way. /Pierre Gilhodes/ created this month Gobliiins 5 as the classical 2D original [Gobliiins] style game, so Ive been made to run also the first Gobliiins again. Ive tried the playable Gobliiins 5 demo, and then Ive returned to the original Gobliiins series.
-
Will code you a chatbot for free, Anyone interested?
My chatbots can be tailored to your needs for Personal use (just not NSFW/Sex Bots, Please!). They can run in a terminal or cmd or with GUI and text-to-speech (see the link below in the demos section). My chatbots can, if needed, run on a Linux web server for online usage.
-
Internet/Gemin...
-
-
21:00
Heres How To Build a Tiny Compiler From Scratch Hackaday

Believe it or not, building a tiny compiler from scratch can be as
fun as it is accessible. [James Smith] demonstrates by making a
tiny compiler for an extremely simple programming language, and
showing off a hello world.
Heres what happens with a compiler: human-written code gets compiled into low-level machine code, creating a natively-executable result for a particular processor. [James] compiler created from scratch makes native x64 Linux ELF binary executables with no dependencies, an experience [James] found both educational and enjoyable. The GitHub repository linked below has everything one needs, but [James] also wrote a book, From Source Code to Machine Code, which he offers for sale to anyone who wants to step through the nitty-gritty.
The (very tin...
20:35
CVE-2023-31454: Apache InLong: IDOR make users can bind any cluster Open Source Security
Posted by Charles Zhang on May 21
Severity: importantAffected versions:
- Apache InLong 1.2.0 through 1.6.0
Description:
Incorrect Permission Assignment for Critical Resource Vulnerability in Apache Software Foundation Apache InLong.This
issue affects Apache InLong: from 1.2.0 through 1.6.0.
The attacker can bind any cluster, even if he is not the cluster owner. Users are advised to upgrade to Apache InLong's
1.7.0 or cherry-pick [1] to solve it.[1]...
20:33
CVE-2023-31453: Apache InLong: IDOR make users can delete others' subscription Open Source Security
Posted by Charles Zhang on May 21
Severity: importantAffected versions:
- Apache InLong 1.2.0 through 1.6.0
Description:
Incorrect Permission Assignment for Critical Resource Vulnerability in Apache Software Foundation Apache InLong.This
issue affects Apache InLong: from 1.2.0 through 1.6.0. The attacker can delete others' subscriptions, even if they are
not the owner
of the deleted subscription. Users are advised to upgrade to Apache InLong's 1.7.0 or...
20:30
CVE-2023-31206: Apache InLong: Attackers can change the immutable name and type of nodes Open Source Security
Posted by Charles Zhang on May 21
Severity: importantAffected versions:
- Apache InLong 1.4.0 through 1.6.0
Description:
Exposure of Resource to Wrong Sphere Vulnerability in Apache Software Foundation Apache InLong.This issue affects
Apache InLong: from 1.4.0 through 1.6.0. Attackers can change the immutable name and type of nodes of InLong. Users are
advised to upgrade to Apache InLong's 1.7.0 or cherry-pick [1] to solve it.
[1]...
20:28
CVE-2023-31103: Apache InLong: Attackers can change the immutable name and type of cluster Open Source Security
Posted by Charles Zhang on May 21
Severity: importantAffected versions:
- Apache InLong 1.4.0 through 1.6.0
Description:
Exposure of Resource to Wrong Sphere Vulnerability in Apache Software Foundation Apache InLong.This issue affects
Apache InLong: from 1.4.0 through 1.6.0.
Attackers can change the immutable name and type of cluster of InLong. Users are advised to upgrade to Apache InLong's
1.7.0 or cherry-pick [1] to solve it.
[1] ...
20:26
CVE-2023-31101: Apache InLong: Users who joined later can see the data of deleted users Open Source Security
Posted by Charles Zhang on May 21
Severity: importantAffected versions:
- Apache InLong 1.5.0 through 1.6.0
Description:
Insecure Default Initialization of Resource Vulnerability in Apache Software Foundation Apache InLong.This issue
affects Apache InLong: from 1.5.0 through 1.6.0. Users registered in InLong who joined later can see deleted users'
data. Users are advised to upgrade to Apache InLong's 1.7.0 or cherry-pick [1] to solve it.
[1] ...
20:23
CVE-2023-31098: Apache InLong: Weak Password Implementation in InLong Open Source Security
Posted by Charles Zhang on May 21
Severity: moderateAffected versions:
- Apache InLong 1.1.0 through 1.6.0
Description:
Weak Password Requirements vulnerability in Apache Software Foundation Apache InLong.This issue affects Apache InLong:
from 1.1.0 through 1.6.0.
When users change their password to a simple password (with any character or
symbol), attackers can easily guess the user's password and access the account.
Users are advised to upgrade to Apache...
20:21
CVE-2023-31066: Apache InLong: Insecure direct object references for inlong sources Open Source Security
Posted by Charles Zhang on May 21
Severity: importantAffected versions:
- Apache InLong 1.4.0 through 1.6.0
Description:
Files or Directories Accessible to External Parties vulnerability in Apache Software Foundation Apache InLong.This
issue affects Apache InLong: from 1.4.0 through 1.6.0. Different users in InLong could delete, edit, stop, and start
others' sources! Users are advised to upgrade to Apache InLong's 1.7.0 or cherry-pick [1] to solve it.
[1] ...
20:19
CVE-2023-31065: Apache InLong: Insufficient Session Expiration in InLong Open Source Security
Posted by Charles Zhang on May 21
Severity: moderateAffected versions:
- Apache InLong 1.4.0 through 1.6.0
Description:
Insufficient Session Expiration vulnerability in Apache Software Foundation Apache InLong.This issue affects Apache
InLong: from 1.4.0 through 1.6.0.
An old session can be used by an attacker even after the user has been deleted or the password has been changed.
Users are advised to upgrade to Apache InLong's 1.7.0 or cherry-pick [1],[2] to solve...
20:18
RADV Driver Lands More Vulkan Overhead Reduction Optimizations Phoronix
Timur Kristf of Valve's Linux graphics driver team has landed a new set of patches for Mesa 23.2 that are further optimizing the Radeon Vulkan driver "RADV" for lower overhead in some code paths...
20:16
CVE-2023-31064: Apache InLong: Insecurity direct object references cancelling applications Open Source Security
Posted by Charles Zhang on May 21
Severity: importantAffected versions:
- Apache InLong 1.2.0 through 1.6.0
Description:
Files or Directories Accessible to External Parties vulnerability in Apache Software Foundation Apache InLong.This
issue affects Apache InLong: from 1.2.0 through 1.6.0. the user in InLong could cancel an application that doesn't
belongs to it. Users are advised to upgrade to Apache InLong's 1.7.0 or cherry-pick [1] to solve it.
[1]...
20:14
CVE-2023-31062: Apache InLong: Privilege escalation vulnerability for InLong Open Source Security
Posted by Charles Zhang on May 21
Severity: importantAffected versions:
- Apache InLong 1.2.0 through 1.6.0
Description:
Improper Privilege Management Vulnerabilities in Apache Software Foundation Apache InLong.This issue affects Apache
InLong: from 1.2.0 through 1.6.0. When the attacker has access to a valid (but unprivileged) account, the exploit can
be executed using Burp Suite by sending a login
request and following it with a subsequent HTTP request
using the...
20:12
CVE-2023-31058: Apache InLong: JDBC URL bypassing by adding blanks Open Source Security
Posted by Charles Zhang on May 21
Severity: moderateAffected versions:
- Apache InLong 1.4.0 through 1.6.0
Description:
Deserialization of Untrusted Data Vulnerability in Apache Software Foundation Apache InLong.This issue affects Apache
InLong: from 1.4.0 through 1.6.0. Attackers would bypass the
'autoDeserialize' option filtering by adding blanks. Users are advised to upgrade to Apache InLong's 1.7.0 or
cherry-pick [1] to solve it.
[1]...
20:08
LLVM's libc Gets Much Faster memcpy For RISC-V Phoronix
Being merged into LLVM's libc library recently are an optimized memory copy function "memcpy" implementation for the RISC-V architecture...
19:51
Linux Adding Leakshield Driver Support For Reporting Liquid Cooling System Leaks Phoronix
There is pending patches for adding support for the LEAKSHIELD device to the Aquacomputer Linux device driver. German PC component manufacturer Aquacomputer has been enjoying support for their various products on Linux and the latest seeing support in this open-source driver is the Aquacomputer Leakshield for reporting any water cooling leaks and other performance metrics around your cooling setup...
19:09
[Meme] The Sirius Open Source Revolutionary Tax: Quietly Stealing Money From Peoples Salaries Under the Guise of Pension (That Doesnt Exist) Techrights
Summary: The crimes of Sirius Open Source remain without punishment, albeit we have plans to escalate up to three more levels to ensure justice is done (or to expose a system inherently tolerant of large-scale fraud)
18:58
PyPI Repository Under Attack: User Sign-Ups and Package Uploads Temporarily Halted The Hacker News
The maintainers of Python Package Index (PyPI), the official third-party software repository for the Python programming language, have temporarily disabled the ability for users to sign up and upload new packages until further notice. "The volume of malicious users and malicious projects being created on the index in the past week has outpaced our ability to respond to it in a timely fashion,
18:37
Study Finds 90% of Australian Teachers Can't Afford to Live Where They Teach SoylentNews
Study finds 90% of Australian teachers can't afford to live where they teach:
The teaching profession is already struggling with shortages and a lack of new candidates in a situation widely regarded as a crisis. Now, research warns that teachers are being priced out of housing near their schools, with many areas even too expensive for educators at the top of the pay scale.
The study, published recently in The Australian Educational Researcher analyzed quarterly house sales and rental reports in New South Wales (NSW) and found more than 90% of teaching positions across the statearound 50,000 full-time rolesare located in Local Government Areas (LGAs) where housing is unaffordable on a teacher's salary.
The situation is particularly dire for new teachers. There are 675 schoolsnearly 23,000 full-time teaching positionswhere the median rent for a one-bedroom place is unaffordable on a graduate teacher's salary.
Housing is considered unaffordable if a person spends more than 30% of their income on housing costssometimes called being in housing stress. Those in housing stress may not have enough money remaining to cover the cost of food, clothing, and other essentials.
But affordability isn't just an issue for early career teachers. For experienced educators at the top of the pay scale, 70 schoolsabout 2,000 full-time rolesare in an LGA where a single-bedroom dwelling is also unaffordable.
"The study shows the last time a first-year teacher salary could comfortably afford the rent for a one-bedroom dwelling was around a decade ago," says Professor Scott Eacott, the author of the study and Deputy Director of the Gonski Institute for Education at UNSW Arts, Design & Architecture.
Read more of this story at SoylentNews.
18:25
Action Fraud (British Police) Batch-Processing Cases Without Actually Dealing With Them? schestowitz.com
Video download link |
md5sum 48e9263394120bccc9b1a1adaaa76670
Action Fraud Bots
Creative Commons Attribution-No Derivative Works 4.0
Summary: Sirius Open Source stole money from its own staff and British police isnt doing anything on the matter (despite all the evidence being complete and unambiguous), so one is left with the impression that British businesses can basically get away with serious crimes, even against their own workers
TODAY I opened my E-mail client and I was greeted by a message or presented with a rather familiar message, which at first I thought was sent in error or perhaps wrongly dated because it closely resembled something that I had already received a month ago. As it turns out, Action Fraud operates a bit like a bot; instead of treating crime reports like reports of a crime (fraud) they seem to be treating them a bit like statistics and nothing suggests theyve even looked into the report. They just waited a month before issuing a template response, basically telling something that cannot be true, as the video above explains. The troubling thing is, this signals to anyone in the UK (employers in particular) that pension fraud or embezzlement is OK because law enforcement agencies wont even bother looking into complaints, even when the multiple UK victims and multiple UK perpetrator are all in the UK (no need to cooperate or work with entities outside the country).
I was going to phone Monday (after the Friday call fell on deaf ears*) but sent on the weekend both outside working days and outside working hours was a seemingly automated message. Despite all evidence provided, theres nothing to suggest anyone even looked into it and the message was almost identical to the first, hence akin to an automated reply, timed for 28 days after the report got filed. This is quite likely a very common modus operandi, basically programmed and wired into the system. This sort of gaslighting will shatter faith in the system of justice and accountability nationwide.
Reporting this or referring this to the ombu...
18:17
British Police Refuses to Tackle Fraud That Took Place 100% Inside Britain (Sirius Open Source) Techrights
Video download link |
md5sum 48e9263394120bccc9b1a1adaaa76670
Action Fraud Bots
Creative Commons Attribution-No Derivative Works 4.0
Summary: Sirius Open Source stole money from its own staff and British police isnt doing anything on the matter (despite all the evidence being complete and unambiguous), so one is left with the impression that British businesses can basically get away with serious crimes, even against their own workers
TODAY I opened my E-mail client and I was greeted by a message or presented with a rather familiar message, which at first I thought was sent in error or perhaps wrongly dated because it closely resembled something that I had already received a month ago. As it turns out, Action Fraud operates a bit like a bot; instead of treating crime reports like reports of a crime (fraud) they seem to be treating them a bit like statistics and nothing suggests theyve even looked into the report. They just waited a month before issuing a template response, basically telling something that cannot be true, as the video above explains. The troubling thing is, this signals to anyone in the UK (employers in particular) that pension fraud or embezzlement is OK because law enforcement agencies wont even bother looking into complaints, even when the multiple UK victims and multiple UK perpetrator are all in the UK (no need to cooperate or work with entities outside the country).
This is quite likely a very common modus operandi, basically programmed and wired into the system.I was going to phone Monday (after the Friday call fell on deaf ears*) but sent on the weekend both outside working days and outside working hours was a seemingly automated message. Despite all evidence provided, theres nothing t...
18:00
Week in review: KeePass vulnerability, Apple fixes exploited WebKit 0-days Help Net Security
Heres an overview of some of last weeks most interesting news, articles, interviews and videos: Apple fixes WebKit 0-days under attack (CVE-2023-28204, CVE-2023-32373, CVE-2023-32409) Apple has released security updates for iOS and iPadOS, macOS, tvOS and watchOS, delivering fixes for many vulnerabilities but, most importantly, for CVE-2023-32409, a WebKit 0-day that may have been actively exploited. Google Cloud CISO on why the Google Cybersecurity Certificate matters In this Help Net Security interview, Phil Venables, CISO More
The post Week in review: KeePass vulnerability, Apple fixes exploited WebKit 0-days appeared first on Help Net Security.
18:00
A Look Back at Computer Displays Hackaday

These days, our video cards are actually as powerful as yesterdays supercomputer and our monitors are bigger than the TVs most of us had as kids. But how did we get there? [RetroBytes] covers computer displays starting with the Colossus computer to today.
Back in the days of Colossus, of course, a display was actually a TeleType-like device printing on a roll of paper. The Manchester Baby actually had a crude display which was actually a Williams tube (no relation) that used phosphor persistence to store data. You could physically see memory on the tube or monitor it on a parallel tube an early form of memory-mapped display.
Early commercial computing used cards and often used a typewriter-like device as a console. Timesharing allowed people to use computers directly and drove innovation in user interface technology. Of course, displays didnt start out like the ones we use today. [RetroBytes] shows an old video game that uses vector display technology which was a common way screens worked on early computers. Essentially, the device was an XY oscilloscope driven by the computer.
TeleTypes gave way to glass TeleTypes or terminals. Power supplies and CRTs made these heavy, but they were the users window into the computer. Of course, eventually, the terminal would become the computer.
The video ends at the terminal. Of course, today, not only is the terminal the computer...
17:14
Lifeboat Foundation supports the Space Renaissance International goal of having the UN add the Sustainable Development Goal for "All, on Earth and Beyond", to the UN's 2030 Agenda. Lifeboat News
Lifeboat Foundation supports the Space Renaissance International goal of having the UN add the Sustainable Development Goal for All, on Earth and Beyond, to the UNs 2030 Agenda.
We are joining other organizations including the National Space Society and The Mars Society in this effort. Sign the petition today!17:02
IRC Proceedings: Saturday, May 20, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-200523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-200523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-200523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-200523.gmi
Over HTTP:
|
... |
15:05
When It Comes to Financial Spin-Doctoring, Microsoft is Now Marketers Marketers Marketers Marketers Techrights
Summary: Marketers from Microsoft and former Chief Marketing Officers or HR VPs too are trying to spin Microsofts collapsing business units (and mass layoffs that are under-reported and grossly under-counted in the media); how much of Microsofts remaining financial activity is just financialization and debt-loading (e.g. buying companies to offload debt onto them)?
Microsoft is 80 billion dollars in debt (a lot higher than its cash reserves or bank balance) and the layoffs carry on and on this year (...
15:00
Easy Graphene Production with a Laser Engraver Hackaday

Graphene isnt easy to produce at scale. But making small batches of graphene is doable in a few ways. [Robert Murray-Smith] decided to try producing flash graphene. This requires a big capacitor bank that is moderately expensive, so he decided to explain a different technique he read about using an ordinary laser cutter. Check it out in the video below.
We were a little disappointed that he didnt actually make any graphene this time. He has, however, used other methods in other videos to create some type of graphene. In fact, he has many similar videos going back quite a ways as well as applications with concrete, capacitors, and more. We understand that this method doesnt produce monolayer graphene, but actually creates a graphene foam with interesting properties. [Robert] talks about recent papers that show you can grow graphene on things other than Kapton tape using this method.
If you decide youd like to try this out, wed love to see your results. [James Tour] from Rice University has a video about laser-induced graphene that might help you, too. Weve seen [Zachary Tong]...
13:54
First Full-sized 3D Scan of the Wreck of the Titanic SoylentNews
Deep sea researchers have used two submersibles to make the first full, 3-dimensional scan of the wreck of the sunken passenger ship, The Titanic, including much of the 3-mile long debris field. This is a major step forward in evidence-based analysis of the wreck from over a hundred years ago.
The new scan was "devoid of that," he said, adding, "It is completely based on data and not human interpretation and that is why we are now seeing it in its larger context for the first time ever."
Atlantic Productions said "one major area of deterioration" had already been observed in the officers' quarters. "This included the room of Captain Edward John Smith and discovered that the iconic captain's bathtub has now disappeared from view," it added.
"Now we're getting objective, so we can get really serious with the science of understanding the wreck," Stephenson said.
He added that he was "absolutely convinced," that the photogrammetry model would now be used "not just for Titanic, but for all underwater exploration," because it "ushers in a new phase of exploration and analysis."
Much of the wreck lies in two main pieces, far apart from each other, at a depth of about 4,000 meters. Around 700k images where taken and stitched together to created the model.
Previously:
(2022) Researchers
Discover Wreck of Ship that Tried to Warn the Titanic
(2022) OceanGate
Ramps Up the Research for its Second Deep-sea Expedition to the
Titanic
(2020) An Aurora
that Lit Up the Sky Over the Titanic Might Explain Why It
Sank
(2020) US Court
Grants Permission to Recover Marconi Telegraph from Titanic's
Wreckage [Updated]
(2018) Finding
the Titanic with ROVs and Navy Funding
Read more of this story at SoylentNews.
13:53
Jyothi Devakumar joins our Life Extension Board. Lifeboat News
Jyothi Devakumar joins our Life Extension Board. Jyothi is Group Chief Science Officer and Partner at the Longevity Tech Fund and Chief Science Officer (CSO) at Healthy Longevity Clinic.
12:00
THOR Microwaves Drone Swarms Hackaday

In recent years small drones have gone from being toys and photography tools to a deadly threat on the battlefield. Kamikaze drones have become especially prominent in the news due to their use in the war in Ukraine by both sides. While we havent seen coordinated swarms being actively employed on the modern battlefield, its likely only a matter of time, making drone swarm defense an active field of development in the industry.
The US Air Force Research Laboratory recently conducted tests and a demonstration of an anti-drone weapon that uses pulses of high-power microwave energy to fry the electronics of a swarm of drones. Named the Tactical High-power Operational Responder, or THOR (presumably they picked the acronym first), its housed in a 20ft shipping container with large microwave antenna on top. The form factor is important because a weapon is only useful if it can reach the battlefield, and this can fit in the back of a C130.
THOR likely functions similarly to a shotgun, with a relatively large effective beam. This would have added advantages like frying multiple drones with one pulse and not needing pinpoint tracking and aiming tech required for projectile and...
11:59
Microsoft Layoffs Continue: Workers Given Notice on Friday of Long (Holiday) Weekend, This Time Nuance Techrights
Didnt Microsoft say repeatedly and insist that chatbots are the future? The layoffs pattern does not match the hype pattern.
Summary: Published earlier today was this sole report (its weekend and reporters are away, some on holiday); talk about bad timing to announce layoffs unless the whole point is brushing the news under a rug (there were also loads of Microsoft layoffs last week, but the media barely mentioned this; Microsoft changed the subject to salaries)
Text behind the paywall: (the only publicly available information at this point)
Nuance Communications, the speech-to-text pioneer bought by Microsoft last year, is cutting jobs as it focuses more narrowly on the health care market.
Employees at Burlington-based Nuance received an e-mail on Friday from chief executive Mark Benjamin notifying them of the cutbacks as part of the continued integration with Microsoft, which paid nearly $20 billion for the company.
We continue to see macroeconomic pressures affect our industries, as well as market shifts that are evolving our customers needs, Benjamin wrote in the e-mail, which was obtained by the Globe. It is critically important that we maintain our ability to make key investments in our businesses so that we can deliver on our current plans and are able to capitalize on the future opportunities we have ahead of us. In order to do this, we made the difficult decision this week to eliminate some positions across the company.
Benjamin did not detail the scope of the layoffs at Nuance, which had about 7,000 employees when the Microsoft deal was announced in 2021. The company did not immediately respond to a request for comment on Saturday.
Nuance has a long and winding history in developing image-processing and speech-recognition software and applications. The company started in 1994 as a spinoff from SRI Internationa...
11:41
[Meme] Illegally and Unconstitutionally Starting Unified Patent Court in Violation of Numerous Conventions Techrights
Summary: Team UPC has privately decided that Milan is in London and its time to start a kangaroo court for the EPOs aristocrats, who granted lots of fake patents, which need fake judges to approve them
11:29
London Police Chief Publicly Admits the System is Failing Victims Techrights
In the news (2 days ago): UK Metropolitan Police Chief accuses Crown Prosecution Service of failing victims and cherry-picking cases
In Techrights: Good Morning Britain Host Martin Lewis: Action Fraud is Pointless
Summary: It has now been over 28 days since crimes of Sirius Open Source were reported to the police (Action Fraud in London) and no action has yet been taken, just as we expected all along (they cannot even be contacted)
11:14
Links 20/05/2023: GStreamer 1.22.3, LibreOffice Looks to Attract New Contributors Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
-
GNU/Linux
-
Desktop/Laptop
-
Google ChromeOS
ChromeOS is Googles cloud-connected desktop operating system (OS). This web-app-focused OS powers mostly inexpensive Chromebookslow-cost laptops for people with basic computing needs. Because it runs on affordably priced laptops and is easy to use with tie-ins to Googles online productivity apps, ChromeOS is excellent for students and casual computer users. ChromeOSs Android...
-
-
11:11
Gemini Links 20/05/2023: The Other Wiki and More Techrights
-
Gemini* and Gopher
-
Personal
-
SpellBinding: AYGISTC Wordo: EIDER
-
hey hey mama, have you read the news
I heard Elizabeth Holmes is going to prison for her fraudulent Silicon Valley co (and yea, I will forever mistakenly call her Katie Holmes), so, I figure hey, lets amuse ourselves with some visual irony, and look up the photo where she is with the 30 under 30 crowd with Zuckerberg and other Silicon Valley tech captains of industry.
I search, I scroll, I re-search, scroll more that photo is fxxxing buried. What I DID see (all over the front page of DDG) was the news news news that she is, in fact, being imprisoned and not remaining free until an appeal, or whatever. Not even a Wikipedia entry on her. Not even an insider hot take about what the malicious/malignant culture Silicon Valley portrays and upholds means for tech at-large. She isnt the only bad character in the Bay Area, she just got caught.
-
I NEED HELP OUT OF A VERY BAD SITUATION
A little more than a decade ago, after CAPITALISM handed my ass to me (the 2008 crash, and subsequent fallout), and I was left with pretty much nothing, I agreed to be sent to TX to be with my mother and sister.
-
Blueberries
I love blueberries. I bet you like them too. If you dont, you probably havent been eating very good ones. Lowbush blueberries are the best theyre small, sweet, and packed with flavor!
-
something something yardwork makes beer sweeter
Todays been busy. Got tomato plants, carrot and cucumber seeds, bags of compost. Took the dogs to the vet for their shots and heartworm/tick medication, then got down to business. Weeded the vegetable garden, turned the soil with a garden fork, poured out the compost, worked it in. Found a few potatoes from last year I mustve missed, and...
-
-
09:13
Obstetricians More Emotionally Stable Than Most SoylentNews
Personality is usually summarized in five traits - the so-called "big five": Emotional stability (neuroticism), extroversion, agreeableness, conscientiousness, and openness. Our personality then shapes our decision-making style. In a research study from Lund University, Swedish obstetricians' and gynecologists' personality profiles and clinical experience are linked for the first time to their decision-making styles in acute childbirth situations.
"Obstetricians and gynecologists have a personality profile that differs significantly from the population at large. On average, 85 percent of Sweden's population has significantly lower emotional stability, extroversion, agreeableness, and conscientiousness than the obstetricians in our study. It's hard not to be surprised when the differences are so clear", says Petri Kajonius, associate professor of personality psychology and behavioral measurement at Lund University.
It is our personality that defines what we will enjoy in our professional life, and the consequence is likely a self-selection of people who seek a certain profession. Swedish obstetric-focused physicians' personalities make them comfortable in an environment where a childbirth situation can quickly shift to something acute and potentially escalate into a crisis. Here, traits such as emotional stability and conscientiousness are prominent.
Journal Reference:
Raoust, G., Kajonius, P. & Hansson, S. Personality traits and
decision-making styles among obstetricians and gynecologists
managing childbirth emergencies [open]. Sci Rep
13, 5607 (2023). https://doi.org/10.1038/s41598-023-32658-6
How do you assess your own personal emotional stability. Are you excitable, or calm and methodical, or does it change frequently depending upon the current situation that you find yourself?
Read more of this story at SoylentNews.
09:09
PyPI suspends new user/project registrations LWN.net
The PyPI Python module repository has temporarily suspended acceptance of new users and project names.
New user and new project name registration on PyPI is temporarily suspended. The volume of malicious users and malicious projects being created on the index in the past week has outpaced our ability to respond to it in a timely fashion, especially with multiple PyPI administrators on leave.
09:00
ESPClicker An Elegant Solution for Integrating Dumb Devices into Home Assistant Hackaday

Integrating non-smart devices into your home automation system can be a cumbersome process, involving the wiring of multiple modules. However, [Pricelesstoolkit] has created the ESPClicker a compact, ESP8266-based module that can remotely press buttons and simplify this process.
The ESPClickers core feature is its three relays that can be soldered to the button terminals of any existing dumb device, as [Pricelesstoolkit] demonstrated with his coffee machine in the video after the break. One of the relays can also be configured in the normally closed configuration. A compact twelve pin connector provides a removable wiring interface for the buttons, additional relays, power and even a contactless power detector that can be wrapped around an AC wire.
The module is open source, with all the source files available on Github. It is intended for interfacing to Home Assistant through ESPHome providing a convenient way of programming and updating the module.
...
06:00
Op-Amp Challenge: MOSFETs Make This Discrete Op Amp Tick Hackaday

When it comes to our analog designs, op-amps tend to be just another jellybean part. We tend to spec whatever does the job, and dont give much of a thought as to the internals. And while it doesnt make much sense to roll your own op-amp out of discrete components, that doesnt mean there isnt plenty to be learned from doing just that.
While were more accustomed to seeing [Mitsuru Yamada]s digital projects, hes no stranger to the analog world. In fact, this project is a follow-on to his previous bipolar transistor op-amp, which we featured back in 2021. This design features MOSFETs rather than BJTs, but retains the same basic five-transistor topology as the previous work, with a differential pair input stage, a gain stage, and a buffer stage. Even the construction of the module is similar, using his trademark perfboard and ultra-tidy wiring.
Also new is a flexible evaluation unit for these discrete op-amp modules. This very sturdy-looking circuit provides an easy way t...
04:37
WHO Warns of Unusual Surge in Severe Myocarditis in Babies cryptogon.com
Mmm hmm. Via: Epoch Times: UK authorities are investigating an unusual surge in severe myocarditis which has hit 15 babies in Wales and England and has killed at least one, the World Health Organisation has announced. On Tuesday, the WHO issued an alert that there had been a rise in severe myocarditis in newborns and []
04:26
Intel Shows New Stacked CFET Transistor Design at ITF World SoylentNews
Intel Shows New Stacked CFET Transistor Design At ITF World:
At ITF World 2023, Ann Kelleher, Intel's Technology Development GM, presented an outline of Intel's latest developments in several key areas, and one of the most interesting revelations was that Intel would embrace stacked CFET transistors in the future. This marks the first time that Intel has shown this new type of transistor in its presentations, but Kelleher didn't provide a date or firm timeline for production.
[In the added around the new type of transistor. The first two transistor types at the bottom of the slide are older variants, while the '2024' entry represents Intel's new RibbonFET transistors that we've covered extensively in the past. Intel's first-gen design with the 'Intel 20A' process node features four stacked nanosheets, each surrounded entirely by a gate. Kelleher says this design remains on track to debut in 2024. RibbonFET uses a gate-all-around (GAA) design, which confers both transistor density and performance improvements like faster transistor switching while using the same drive current as multiple fins, but in a smaller area.
Kelleher's slide also shows the next generation of Intel's GAA design the stacked CFET. The Complementary FET (CFET) transistor design has been on imec's roadmaps for some time, but we haven't yet seen it on an Intel slide or heard the company state that it plans to adopt this design. As a reminder, the imec research institute studies future technologies and collaborates with the industry to bring them to fruition.
Naturally, there is some variation between Intel's stylized render and the imec CFET render we've included in the first image of the album above, but Intel's image conveys the point well this design allows the company to stack eight nanosheets, a doubling of the four used with RibbonFET, thus increasing transistor density. We also have images of the three other types of Intel transistors in the album above Planar FET, FinFET, and RibbonFET.
Read more of this story at SoylentNews.
03:47
Popular Pirate Bay Proxy Site Disappears From GitHub TorrentFreak
 As one of the most notorious torrent sites, The Pirate Bay
has been blocked by ISPs around the world.
As one of the most notorious torrent sites, The Pirate Bay
has been blocked by ISPs around the world.
In response to these digital roadblocks, several proxy sites have sprung up to bypass these restrictions. Besides that, there are dedicated sites that help people to find these backdoors.
The Proxy Bay
The Proxy Bay has long been one of the leading information portals. The site didnt offer an official proxy itself but provided an overview of available options. As such, it proved to be quite useful in countries where site blockades are active.
In the UK, for example, where TPB has been blocked for over a decade, the site was particularly popular.
Since the blocking orders often allow rightsholders to add newly appearing proxies, this has turned into a game of whack-a-mole. When proxies are blocked, new domains are launched, which are then picked up by pirates through information portals such as The Proxy Bay.
GitHub Takedown Saga
This routine has been a major source of frustration for rightsholders. It reached the point where some of these linking sites were banned, and when City of London Police got involved in the matter earlier this year, it was clear that things were getting more serious.
Its quite something when the police actively get involved in a copyright matter. In this case, it was particularly salient since The Proxy Bay was hosted at GitHub.
The developer platform swiftly complied with the takedown request, which wasnt unexpected. However, after someone representing the proxy information site sent a counter notice, the domain was restored.
The brief takedown in January hurt the sites traffic but, when it c...
03:16
2021 data breach exposed data of 70 Million Luxottica customers Security Affairs
Luxottica has finally confirmed the 2021 data breach that exposed the personal information of 70 million customers.
Luxottica Group S.p.A. is an Italian eyewear conglomerate and the worlds largest company in the eyewear industry. As a vertically integrated company, Luxottica designs, manufactures, distributes and retails its eyewear brands, including LensCrafters, Sunglass Hut, Apex by Sunglass Hut, Pearle Vision, Target Optical, Eyemed vision care plan, and Glasses.com. Its best known brands are Ray-Ban, Persol, and Oakley. Luxottica also makes sunglasses and prescription frames for designer brands such as Chanel, Prada, Giorgio Armani, Burberry, Versace, Dolce and Gabbana, Miu Miu, and Tory Burch.
On May 12, the cybersecurity expert Andrea Draghetti noticed that a threat actor released data belonging to Luxottica speculating a new databreach.

The threat actor released a 140GB database containing more than 300 million records. The researchers reported that the archive was containing 305.759.991 records (luxottica_nice.csv), with 74.417.098 unique email addresses and 2.590.076 unique domain emails.
03:07
An erasure FEC for SSDV Daniel Estvez
SSDV is an amateur radio protocol that is used to transmit images in packets, in a way that is tolerant to packet loss. It is based on JPEG, but unlike a regular JPEG file, where losing even a small part of the file has catastrophic results, in SSDV different blocks of the image are compressed independently. This means that packet loss affects only the corresponding blocks, and the image can still be decoded and displayed, albeit with some missing blocks.
SSDV was originally designed for transmission from high-altitude balloons (see this reference for more information), but it has also been used for some satellite missions, including Longjiang-2, a Chinese lunar orbiting satellite.
Even though SSDV is tolerant to packet loss, to obtain the full image it is necessary to receive all the packets that form the image. If some packets are lost, then it is necessary to retransmit them. Here I present an erasure FEC scheme that is backwards-compatible with SSDV, in the sense that the first packets transmitted by this scheme are identical to the usual \(k\) packets of standard SSDV, and augments the transmission with FEC packets in such a way that the complete image can be recovered from any set of \(k\) packets (so there is no encoding overhead). The FEC packets work as a fountain code, since it is possible to generate up to \(2^{16}\) packets, which is a limit unlikely to be reached in practice.
Motivation and intended applications
The main motivation for this FEC scheme comes from the Longjiang-2 mission. This satellite, also known as DSLWP-B, carried a small camera and transmitted the images from the camera on demand by telecommand using SSDV. The downlink bitrate was usually 125 bps, so transmitting a single image would take around 20 or 30 minutes. It was not uncommon to miss a few of the SSDV packets. Even if the SNR was quite good when the 25 meter radiotelescope at Dwingeloo was used to receive the downlink, there could be occasional problems such as frequency jumps in the on-board TCXO.
In some cases, the missing pieces of the image corresponded to empty parts of the sky that were known to be completely black. In other cases, the missing parts were interesting, so we attempted to receive the complete image by commanding the spacecraft to transmit the missing packets again, before new images were taken that would overwrite the image in the on-board memory. There were two possible ways of doing this. It was possible to send a telecommand that would start the SSDV transmissio...
02:45
Links 20/05/2023: IPFire 2.27 Core Update 175 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Monopolies
-
GNU/Linux
-
Audiocasts/Shows
-
Bad Voltage 358: Large Langridge Model
Jeremy Garcia, Jono Bacon, and Stuart Langridge present Bad Voltage, in which there is unsceptical intensity, we are all eaten by a T-1000, and we have collected a list of concerns about Large Language Model-based AI, which were going to dive into!
-
Jupiter Broadcasting ...
-
-
02:35
IRC Proceedings: Friday, May 19, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-190523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-190523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-190523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-190523.gmi
Over HTTP:
|
... |
01:38
KDE Begins Laying The Groundwork For HDR Support, Wayland Color Management Phoronix
As covered a few days ago on Phoronix, there's been early progress on HDR display support for the KDE desktop among other highlights this week...
00:13
Cybercrime gang FIN7 returned and was spotted delivering Clop ransomware Security Affairs
Cybercriminal gang FIN7 returned with a new wave of attacks aimed at deploying the Clop ransomware on victims networks.
Researchers at Microsoft Security Intelligence team published a series of tweets to warn of a new wave of attacks aimed at distributing the Clop ransomware and linked it to the financially motivated cybercriminal group Sangria Tempest (ELBRUS, FIN7). The attacks confirm the return of the threat actors after a long period of inactivity. The group was spotted deploying the Clop ransomware in opportunistic attacks in April 2023.
FIN7 is a Russian criminal group (aka Carbanak) that has been active since mid-2015, it focuses on restaurants, gambling, and hospitality industries in the US to harvest financial information that was used in attacks or sold in cybercrime marketplaces.
In recent attacks, Fin7 was observed using the PowerShell script POWERTRASH to load the Lizar post-exploitation tool to get a foothold into the victims networks. Then they use OpenSSH and Impacket to move laterally and deploy the Clop ransomware payload.
The Clop ransomware is just the newest strain the cybercrime gang has used to attacks in the wild.
Clop is the latest ransomware strain that Sangria Tempest has been observed deploying over the years. The group previously deployed REvil and Maze before managing the now-retired DarkSide and BlackMatter ransomware operations. reads one of the tweets published by the experts.
We are in the final!
Please vote for Security Affairs (...
00:00
How Far Can An EULA Go? Hackaday

We read this news with mixed glee and horror: a company called Telly is giving TVs away, for the low price of having to live with an always-on advertisement bar and some pretty stringent terms and conditions. Break the terms, and theyll repossess your TV. If you dont give them the TV, they have your credit card on record and they think the set is worth $1,000.
The hacker in me sees free hardware, so I checked out the terms and conditions, and it doesnt look good. Theyve explicitly ruled out opening up or physically modifying the device, and it has to continually have WiFi for which you pay, naturally. It sounds like it could easily tell if you try to tamper with it. My next thought was, perhaps too cynically, to get one, put it in the closet, and wait for the company to go bankrupt. Because you know that business model isnt going to last.
But its clear that theyve seen through me. The most bizarre clause is that you have to Use the Product as the primary television in Your household. Now, were not lawyers, but it seems like an amazing stretch that they can tell you how int...
Saturday, 20 May
23:37
Reddit Will Allow Users to Upload NSFW Images From Desktop SoylentNews
Reddit will allow users to upload NSFW images from desktop:
Reddit announced Thursday that it will now allow users to upload NSFW images from desktops in adult communities. The feature was already available on the social network's mobile app.
[...] "This now gives us feature parity with our mobile apps, which (as you know) already has this functionality. You must set your community to 18+ if your community's content will primarily be not safe for work (NSFW)," the company said.
Reddit's announcement comes days after Imgur said that the image hosting platform was banning explicit photos from May 15. At that time, the company said that explicit content formed a risk to Imgur's "community and its business". Banning this type of content would "protect the future of the Imgur community."
Many of Reddit's communities rely on Imgur's hosting services. However, the social network allowing native NSFW uploads through desktop might be the most logical solution going forward.
Image hosting is not the only hurdle for NSFW communities. Last month, when Reddit announced that it will start charging for its API, the company also said that it will limit access to mature content available through its API. This would directly impact the experience on third-party Reddit apps. In yesterday's announcement about desktop upload for NSFW images, a Reddit staff members said that the company is discussing how to navigate this situation.
Read more of this story at SoylentNews.
23:23
Generative AI Shakes Global Diplomacy At G7 Summit In Japan Lifeboat News: The Blog
Our technological age is witnessing a breakthrough that has existential implications and risks. The innovative behemoth, ChatGPT, created by OpenAI, is ushering us inexorably into an AI economy where machines can spin human-like text, spark deep conversations and unleash unparalleled potential. However, this bold new frontier has its challenges. Security, privacy, data ownership and ethical considerations are complex issues that we must address, as they are no longer just hypothetical but a reality knocking at our door.
The G7, composed of the worlds seven most advanced economies, has recognized the urgency of addressing the impact of AI.
To understand how countries may approach AI, we need to examine a few critical aspects.
Clear regulations and guidelines for generative AI: To ensure the responsible and safe use of generative AI, its crucial to have a comprehensive regulatory framework that covers privacy, security and ethics. This framework will provide clear guidance for both developers and users of AI technology.
Public engagement: Its important to involve different viewpoints in policy discussions about AI, as these decisions affect society as a whole. To achieve this, public consultations or conversations with the general public about generative AI can be helpful.
23:23
NASA Is Relying On Elon Musk And Jeff Bezos To Get Us Back To The Moon Lifeboat News: The Blog
NASA on Friday announced the second spacecraft it hopes will help return astronauts to the surface of the moon later this decade. Blue Origins Blue Moon lander joins the SpaceX Starship as the two vehicles the space agency aims to use for its Artemis program to once again put boots on lunar regolith.
Over a half-century after NASA used a massive investment of US GDP to fund the Apollo program and build the Saturn V rocket, humanitys next chapter in space is largely in the hands of two of the richest men in the world, SpaceX founder and chief twit Elon Musk and Amazon and Blue Origin head Jeff Bezos.
The shift in the provenance of Apollos mission architecture versus that of Artemis is, at the very least, a symbolic representation of a key shift in American society over the last few generations. Hot off the heels of successful collective action in Europe and elsewhere during World War II, the Americans again came together to catch up to and then surpass the Soviet Union in the space race.
23:23
NASA Should Send $17 Billion Human Mission To Mars In 2033, Say Experts Lifeboat News: The Blog
NASA could take advantage of a rare planetary alignment in 2033 to send the first crewed mission to orbit Mars and, on the way back, Venus. The short tripwhich would be the first interplanetary crew evercould be a pathfinder mission for the first crewed landing on the red planet in 2037.
Its the best time to go to Mars in the next 25 years, said Matt Duggan, mission management and operations manager at Boeing, addressing the 2023 Humans To Mars Summit on Wednesday at the National Academy of Sciences Building in Washington D.C. Thats in terms of the amount of energy and fuel you have to spend to get to Marsits a unique opportunity that comes around once every 15 years.
A mission plan to send crew in existing spacecraft on a 570-day return trip to orbit Mars and Venus will only work every 15 yearsand the next opportunity is 2033.
23:23
Big Tech is already warning us about AI privacy problems Lifeboat News: The Blog
That is, if youre paying attention.
So Apple has restricted the use of OpenAIs ChatGPT and Microsofts Copilot, The Wall Street Journal.
Its not just Apple, but also Samsung and Verizon in the tech world and a whos who of banks (Bank of America, Citi, Deutsche Bank, Goldman, Wells Fargo, and JPMorgan). This is because of the possibility of confidential data escaping; in any event, ChatGPTs privacy policy explicitly says your prompts can be used to train its models unless you opt out. The fear of leaks isnt unfounded: in March, a bug in ChatGPT revealed data from other users.
Apples banned the use of OpenAI as has Samsung, Verizon, and a whos who of banks. Should the rest of us be concerned about how our datas getting used?
23:22
Tesla FSD Overly Aggressive after BIG update Lifeboat News: The Blog

Not perfect, but very impressive.
Sponsored:
Use my special link https://www.privateinternetaccess.com/AIDRIVR
for an 83% discount, 4 months free and 30-day money-back guarantee
on the best VPN Private Internet Access.
Version: 11.4.1 [2023.7.5]
Consider supporting this channel on Patreon: https://patreon.com/AIDRIVR
Filming Equipment:
GoPro Hero 10 Black (Visualizations): https://amzn.to/3kGze2I
GoPro Hero 11 Black (Interior): https://amzn.to/3H7Xsuq.
GoPro Enduro Batteries: https://amzn.to/3wrzhSK
GoPro Dual Battery Charger: https://amzn.to/3XBxnLi.
Fat Gecko Triple Mount (Exterior): https://amzn.to/3R8J0GQ
Fat Gecko Double Suction Mount (Interior): https://amzn.to/3HyW0Tj.
Sony A6400 w/ 18-135mm Lens: https://amzn.to/3RauluT
Sigma 30mm F1.4 Lens: https://amzn.to/3HvOU1C
Insta360 One RS: https://www.insta360.com/sal/one_rs?insrc=INRP7IO
Insta360 X3 (free selfie stick!): https://www.insta360.com/sal/x3?insrc=INRP7IO
Insta360 X2 (free selfie stick!): https://www.insta360.com/sal/one_x2?insrc=INRP7IO
Editing Equipment:
16 MacBook Pro M1: https://amzn.to/3j71X04
Magic Trackpad: https://amzn.to/403P8UV
Roost V3 Laptop Stand: https://amzn.to/3JgqBX4
Phillips Fidelio X2HR: https://amzn.to/3wvuVd7
Dragonfly Cobalt: https://amzn.to/3kHLPCR
Shure SM7B Microphone: https://amzn.to/3wxz9kK
Gator Frameworks Mic Arm: https://amzn.to/3XGGE4E
Elgato Wave XLR Preamp: https://amzn.to/3XEZpW2
I earn from purchases you make via Amazon Associates & Insta360 af...
21:22
Aubrey de Grey: AI, in silico, LEV Foundation, Alpha Fold, Nanobots, OpenAI and Sam Altman Lifeboat News: The Blog

Aubrey: 50% chance to LEV in 1215 years, and a variety of topics from Rey Kurzweil to A.I. to Singularity, and so on.
In this podcast, Aubrey de Grey discusses his work as President and CSO at Lev Foundation and co-founder at Sense Research Foundation in the field of longevity. He explains how the Foundations focus is to combine rejuvenation and damage repair interventions to have greater efficacy in postponing aging and saving lives. De Grey believes that within 12 to 15 years, they have a 50% chance of achieving longevity escape velocity, which is postponing aging and rejuvenating the body faster than time passes. De Grey acknowledges the limitations of traditional approaches like exercise and diet in postponing aging and feels that future breakthroughs will come from high-tech approaches like skin and cell therapies. He discusses the potential of AI and machine learning in drug discovery and the possibility of using it to accelerate scientific experimentation to optimize decisions about which experiments to do next. De Gray cautions that the quality of conclusions from AI depends on the quality and quantity of input data and that the path towards defeating aging would require a symbiotic partnership between humans and AI. Finally, he discusses his excitement about the possibilities of hardware and devices like Apple Watch and Levels in tracking blood sugar levels and their potential to prolong life.
21:00
Hexed Home Assistant Monitors 3D Printers Hackaday

You can babysit your 3D printer 100% of the time, or you can cross your fingers and hope it all works. Some monitor their printers using webcams, but [Simit] has a more stylish method of keeping tabs on six 3D printers.
The idea is to use a 3D printed hex LED display found online. Adding an ESP32 and Home Assistant allows remote control of the display. The printers use Klipper and can report their status using an API called Moonraker. Each hexagon shows the status of one printer. You can tell if the printer is online, paused, printing, or in other states based on the color and amount of LEDs lit. For example, a hex turns totally green when printing is complete.
Once you have a web API and some network-controlled LEDs, it is relatively straightforward to link it together with Home Automation. Of course, you could do it other ways, too, but if you already have Home Automation running for other reasons, why not?
We have seen other ways to do this, of course. If you need an easy monitor, the eyes have it. If you dont use Klipper, OctoPrint can pull a similar stunt.
20:48
Meet 'Jack' from Romania! Mastermind Behind Golden Chickens Malware The Hacker News
The identity of the second threat actor behind the Golden Chickens malware has been uncovered courtesy of a "fatal" operational security blunder, cybersecurity firm eSentire said. The individual in question, who lives in Bucharest, Romania, has been given the codename Jack. He is one of the two criminals operating an account on the Russian-language Exploit.in forum under the name "badbullzvenom
20:30
Intel Publishes "X86-S" Specification For 64-bit Only Architecture Phoronix
Intel quietly released a new whitepaper and specification for their proposal on "X86-S" as a 64-bit only x86 architecture. If their plans workout, in the years ahead we could see a revised 64-bit only x86 architecture...
19:59
US CISA warns of a Samsung vulnerability under active exploitation Security Affairs
US CISA added the vulnerability CVE-2023-21492 flaw affecting Samsung devices to its Known Exploited Vulnerabilities Catalog.
US CISA added the vulnerability CVE-2023-21492 vulnerability (CVSS score: 4.4) affecting Samsung devices to its Known Exploited Vulnerabilities Catalog.
The issue affects Samsung mobile devices running Android 11, 12, and 13, it is described as an insertion of sensitive information into log file vulnerability that allows a privileged, local attacker to conduct an address space layout randomization (ASLR) bypass.
The issue was reported on January 17, 2023, the company addressed the issue by removing kernel pointers in log file.
Kernel pointers are printed in the log file prior to SMR May-2023 Release 1 allows a privileged local attacker to bypass ASLR. reads the advisory published by Samsung. Samsung was notified that an exploit for this issue had existed in the wild
The company did not provide details about the attacks exploiting the flaw, but likely the issue was chained with other vulnerabilities to compromise vulnerable Samsung devices.
CISA also addressed the following issue in the latest turn:
- CVE-2004-1464 Cisco IOS Denial-of-Service Vulnerability. Cisco IOS contains an unspecified vulnerability that may block further telnet, reverse telnet, Remote Shell (RSH), Secure Shell (SSH), and in some cases, Hypertext Transport Protocol (HTTP) access to the Cisco device.
- CVE-2016-6415 Cisco IOS, IOS XR, and IOS XE IKEv1 Information Disclosure Vulnerability. Cisco IOS, IOS XR, and IOS XE contain insufficient condition checks in the part of the code that handles Internet Key an information disclosure vulnerability in the Internet Key memory contents. Successful exploitation could allow the attacker to retrieve memory contents, which can lead to information disclosure.
According to Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities, FCEB agencies have to address the identified vulnerabilities by the due date to protect their networks against attacks exploiting the flaws in the catalog.
E...
19:55
Microsoft Preparing For Their First Vulkan Extension Phoronix
While the Vulkan high performance graphics and compute API is backed by many vendors, Microsoft and Apple are two notable organizations that haven't backed this Khronos Group standard. For Microsoft's part, they obviously prefer their in-house Direct3D. However, Microsoft is making preparations for submitting their first Vulkan extension...
19:43
AMD Has A One-Liner To Help Speed Up Linux System Resume Time Phoronix
AMD engineers have been working out many quirks and oddities in system suspend/resume handling to make it more reliable on their hardware particularly around Ryzen laptops. In addition to suspend/resume reliability improvements and suspend-to-idle (s2idle) enhancements, one of their engineers also discovered an easy one-liner as a small step to speeding up system resume time...
19:28
Virtual ALSA Driver Posted To Help With Linux Testing/Fuzzing Phoronix
Ivan Orlov this past week posted the patches for VALSA, the Virtual ALSA sound driver that aims to help Linux kernel developers in testing and fuzzing of the sound subsystem...
19:22
Wireless power demonstration overcomes a major hurdle Lifeboat News: The Blog
Wireless power would be worth the hype if it were widespread modern life is burdened by a tangle of power cables and an endless hunt for plugs. But despite its potential, wireless power technology is still limited by range.
But Ericsson and PowerLight Technologies have made one dramatic form of wireless power, called optical beaming, work in a proof-of-concept experiment. Their demonstration showed that laser delivery of power to a portable 5G base station could be just around the corner.
The promise of wireless power: Wireless power is straight out of a sci-fi film: electrical power transmitted from place to place through a vacuum or the air. There is no need for wires, poles, outlets, or those pesky USB cubes, which are always lost when you need them most.
19:21
Links 20/05/2023: CodeWeavers Without Jeremy White Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Pseudo-Open Source
- Linux Foundation
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Monopolies
-
GNU/Linux
-
Desktop/Laptop
-
...
-
-
19:15
Gemini Links 20/05/2023: Ascension Day and Closed Registration for flounder.online (Small Web) Techrights
-
Gemini* and Gopher
-
Personal
-
Introducing the Broad Framework
* Pointers on how to get a starter that is more yeast-y (use a stiff starter, maybe 50% hydration) or with more lactic acid bacteria (drown the starter in 500% hydration). Also that the drowning can help with mold problems.
-
Summer Springing Up
For the past two summers in Sacramento, by the time May rolled around it was hot, IE 90+ degrees most days. I moved here May 24Th 2021 and slept on top of the covers every single night until mid September since it would stay hot late into the night. In 2022 it was regularly into the 90s by April and stayed hot late into October, a long, hot Summer. This year we had a pretty brutal Winter, the most rain Ive seen in California in all my life. The rain wasnt actually all that hard, it was the strong winds that came with it that brought down so many trees. However the rain did last for a long time. Normally we would get 2 or 3 days of rain like walls of water when you step outside, and then a couple sprinkles here or there, which almost always wasnt enough water for the year. Now weve gotten more than we possibly can imagine, lakes are filling back up, rivers are higher than ever, everything is so green. The multi-week long light to moderate rain showers was not the California I was used to.
-
Driving in England
I live in the United States, but this weekend the family have traveled to the UK to attend a wedding. I have visited other countries in Europe before, but not England.
We decided to rent a car for the duration of our stay. Ive never driven a right-hand drive vehicle before, much less driven in left-hand traffic. Of course that meant that we, jet-lagged and very tired, had to drive to the inn with everything on the opposite side from that to which Im accustomed.
-
...
-
-
19:02
1xbet Online In India h+ Media
1xbet Online In India
The customers can select either to do the 1xbet apk obtain or the ios download too. Not only this they have the likes of cell browser too, which is less complicated to entry. The website presents a quantity of payment choices for users based out of India, including e-wallets, cryptocurrencies, financial institution transfers and bank playing cards. Curiously, while making UPI transfers, as a substitute of making the cost directly to 1xBet, the registered ID belongs to a private individual and it routinely retains altering.
1xBet analyses the wants of modern society and constantly improves its products. In it, users cant solely bet on cricket and extra sports activities wherever theyre but additionally discover different exciting offers. So, for instance, you can watch matches of your favorite teams reside, play in the on line casino or play unique video games in the 1xGames part. We provide all the data you will want on the qualifying norms associated to the bonus offer.
The firm also ensures that each one transactions are processed quickly and securely. Customers can relaxation assured that their money is secure when utilizing any of the fee strategies available on 1xBet. Withdrawals are also simple to initiate with only a few clicks, allowing customers to access their winnings rapidly and simply. All in all, 1xBet provides a wonderful platform for Indian gamers to enjoy a safe and secure online gambling expertise.
Boxing is a classic type of martial arts that by no means ceases to be well-liked. Betting followers are attracted not solely by the relative ease of guessing the finish result of fights, but additionally by the detailed odds. You can guess on boxing not solely on the winner but in addition on different statistics and leads to specific rounds.
The web site has a Curacao license, confirming its reliability and security. 1xBet is the official partner of Spanish La Liga, Italian Serie A, Nigerian Premier League and Brazilian Serie A. 1xbets customer assist group is always at hand to offer prospective bettors any type of help they search.
This makes the welcome provide both large and versatile, although do keep in mind you only have 30 days from the date of registration to redeem this supply and use the bonus funds. The homepage of the web site reveals all stay games going down with reside odds, and youll select any sport you want to bet on from the listing. There is a menu that permits you to open varied sports activities, reside betting web page, promo code section, on line casino, reside on line casino, 1xGames, TVGames and different sections. The Indian Premier League, or IPL, is amongst the most popular cricket events amongst Indian gamers. 1xBet presents each a desktop web site and a mobile app for betting on the IPL. One of the simplest bookmakers in India is the 1xbet sports app.
Dozens of deposit and withdrawal methods are available on th...
19:02
1xbet Login And Registration, 1xbet Register On h+ Media
1xbet Login And Registration, 1xbet Register On
In India, its not attainable to open an account with 1xbet. But, if youre an avid sports fan, youll love the sites wide selection of choices. With 1xbet, youll find a extensive range of sports activities and casino video games you could bet on. Plus, you can also win real money should you make the right predictions. In addition to its sportsbook, the 1xbet website presents numerous deposit strategies.
As the sport progresses, the betting markets and respective odds update quick on the 1 xbet web site. In this, the chances are up to date each few minutes, and the market stays active to put bets. Playing in a stay on line casino could be very handy as a end result of there you presumably can place extra accurate bets by following every little thing thats happening at the time of a play. In Live Casino, youll be playing only with actual live casino sellers. It is feasible to place bets wherever and whenever you need.
- Bonus amount is the identical as the amount of your deposit .
- You can use the cash to position bets and later withdraw them to your card.
- After you declare the bonus, you need to wager the bonus money in at least 5 accumulator bets with three or further occasions with odds 1.forty or larger.
- The totalizator is a unique betting type provided by us.
- Every Friday and Saturday up to 200 events are supplied, a 3rd of that are streamed reside.
It is accessible by over four hundred,000 users worldwide and there are no legal guidelines towards on-line gambling in India. Indian punters can legally access the platform to wager and play with most withdrawal quantities varying from one banking choice to another. After evaluating the options and features of 1xBet for Indian players, we awarded it the Sportscafe stamp of approval.
At the time of writing, there were almost 300 in-play bets obtainable throughout one stay South Korean womens basketball match alone. In the case of cricket matches, the number may be even larger, with bets out there on individual balls, over or innings. This offers you the chance to actually put your knowledge to the take a look at by predicting the finish result of topical scenarios in addition to the performances of batsmen and bowlers.
Its discussion board for bettors is one other nice supply of help for model new or inexperienced bettors. Not solely are you capable to chat with other prospects there but additionally get some treasured pieces of recommendation from real execs within the sports activities betting world. A secure and reliable casino publishes the origin and its gaming licenses on the homepage. There is a protracted record of playing authorities around the world that regulate online casinos. The hottest homeowners include the United Kingdom and Malta. The UK Gambling Commission, as an example, is responsible for regulating on-line playing providers an...
18:59
1xbet App For Online Betting h+ Media
1xbet App For Online Betting
Just just like the desktop options, gamers can entry all the transaction mediums utilizing 1xBet app. The 1xbet credit or debit card fee method is essentially the most preferred payment option to fund the account. After login, select the Cards option within the Deposit part and fill in the required card details. The primary deposit choice is the e-wallet method for Indian bettors. Below discover the data on how to deposit cash in 1xbet from India and get to know about some new-age deposit strategies from this bookmaker.
1xBet provides an affiliate program where you could earn 200 INR should you refer others to 1xBet and they efficiently be a part of and deposit a minimal of 1,000 INR. You may provide as many suggestions as you like, and you may even share your distinctive link on social media and with like-minded friends. Complete the transaction by getting into the amount you want to deposit into your 1xBet account for the primary time. Signing up at 1xBetbd is completely free, and this course of may be carried out by following the steps talked about within the earlier part. Considering that having an account at this portal is totally free, there is not a trigger for not signing up now. For individuals who might not know, 1xBetbd is the division of 1xBet centered on the nation of Bangladesh.
Multi guess is a mixed bet, the coefficients of which are multiplied. International competitions, including world championships, are also held in kabaddi. Date live pro kabaddi is changing yearly, however all information you can find within the site. 1.Go to your personal account, after which to the Personal information section. The governments draft guidelines for deceptive commercials beneath the Consumer Protection Act prohibit firms from surrogate promoting.
Top cricket matches can have tons of of markets to wager on and there are numerous extra markets obtainable in-play. The website format takes a while to get used to, especially if you have expertise of different major betting sites. But as soon as you know your method round, it becomes slightly easier. The sports activities menu comes within the type of a side-scrolling record that is displayed on the high of the betting menu, so it can always be accessed. In our opinion, this isnt probably the most user-friendly way to navigate a sports activities betting menu.
For example, we prefer to make use of the cell app for betting because it provides a extra user-friendly expertise overall. And we might somewhat use the live chat facility when in need of support. There is a devoted reside streaming web page on 1XBet with reside streams of various sporting events shown 24/7, including top cricket matches from around the globe.
Once you retain track of this stuff, youll dont have any problem wagering your bonus inside the set time. Another argument in favor of this web site is the 1xbet promo code that will permi...
18:57
1xbet Sports Regular Match Males Blue Trousers h+ Media
1xbet Sports Regular Match Males Blue Trousers
The license permits the bookmaker to arrange sports betting occasions in additional than 50 countries around the globe. Users of the 1xBet website should not be afraid of fines or different penalties. Thanks to the presence of a Curacao license, the security of 1xBet India remains at a high degree. 1xBet is a authorized on-line playing website in India, with a Curacao playing license (license quantity 1668/JAZ).
1xbet welcomes grownup resident Indian bettors with a join supply. Provided you meet the qualifying standards, your welcome bonus must be credited to your account proper after you make your first deposit. Just ensure you use it within 30 days of sign-up, in any other case, will in all probability be revoked. Type in the 1XBet promo code in the corresponding subject.
You cant use a 1xbet promo code in case you are already a registered person. As it is clear from the name of the bonus, its intended for model new clients only. This means you can get a welcome bonus, applying the 1xbet promo code SEOALEX only once. When it comes to refiling your betting account with bonus funds, there can be no delays.
To wager on cricket, open the listing of all sports activities in the left corner and choose the category that interests you. Aside from cricket, theres a plethora of sports betting disciplines in which youll attempt your luck. You have a month since receiving a bonus for wagering it. If you dont handle to do this, all of your winnings earned due to bonus cash and every thing that remained on your bonus account will be redeemed. X2 Wednesday is one other nice provide for 1xbet clients.
With this wager , every choice fulfils the minimum odds of 1.40. With such a bet, youll release a part of the bonus. In the top, you must wager the bonus five instances within 30 days. For instance, should you deposit 1,000 INR and obtain a bonus of an extra 1,000 INR, you have to wager a complete of 5,000 INR on sports bets of your selection. If you manage to do that within 30 days with such acca bets, the bonus and all winnings earned with it are yours. In addition to profitable bonuses and a wide range of games, 1xBet offers a broad range of on-line sports activities and esports betting.
The first step in getting the 1xbet promo code bonus for India is to create a model new account. For all new prospects who love betting on sport events. There is a extensive range of sports available to you on this online bookie. As expected, cricket, soccer, or soccer as some know it has the widest outreach. All you have to do is join a new account and it is feasible for you to to claim the welcome bonus and the prevailing players can avail the unique supply for the Indian market. This is great as it allows the new and present players to spend time on this operator greater than they might often do.
In our write-up on the 1xbet promo code, you will disco...
18:57
Wager On Cricket With The Trendy 1xbet Mobile App h+ Media
Wager On Cricket With The Trendy 1xbet Mobile App
Remember to enter your real registered cell quantity. New gamers might have to validate their identification and could additionally be requested to supply identification paperwork for that purpose. Failing to supply them could stop them from claiming the welcome bonus. Players must consent that they want to receive the bonus by going to My Account and enabling the Take half in bonus offers operate. When youre prepared, click on the percentages and your selection will appear in the bet slip. You can add extra markets if you wish to create a multiple or an accumulator to enhance your odds.
Its a one-time supply, and youll never have one other likelihood to receive this kind of bonus. 1xbet offers the widest vary of choices for depositing cash into and withdrawing out of your betting account. 1xbet provides a variety of betting choices in cricket and different sports activities which may be popular amongst Indian bettors. 1xbet offers you the widest potential vary of payment options. As a prospective bettor, the plethora of choices provided will delight you. We list some of these decisions beneath, in our write-up on the 1xbet promo code.
Even although 1xBet is a reasonably well-known model that doesnt want promoting, they keep up the level. Compared to other bookmakers, 1xBets customer support is very fast. And most importantly, it gives full answers to questions. Odds on stay events are variable and alter as an occasion progresses. Odds at 1xbet are among the highest of all online bookies in India.
1xBet has the identical options and features as the desktop identical welcome bonus and some other promotions. If you run into a difficulty, you probably can always contact quickly our buyer help team via live chat, and they will assist you to resolve any problem you may have. The dealer launches the ball across the roulette wheel within the recreation of roulette. If you wager on the sector the place the ball stops, youll be able to win.
There are many variations of this on line casino sport, so it is strongly recommended that you just check all of them out to search out the one which fits your tastes essentially the most. Click on the Login button in the top-right nook. Then, enter the consumer ID, e-mail, or phone quantity, and type in your password.
And every year the curiosity of gamers to guess on pkl is rising. In addition, betting pro kabaddi league is available with favorable odds. As soon as a brand new 1xBet client registers, you should instantly write to the technical assist service and undergo the verification process. As quickly as they want a withdrawal, they start writing to the administration. This might take a while, and even require extra checks.
- The money received as a prize due to a working promo code can be utilized for sports betting w...
18:54
Electric Two-wheelers are Set to Scoot Past EVs in Asia SoylentNews
Electric two-wheelers are set to scoot past EVs in road race:
Video Visit Asia's emerging megacities and you'll quickly notice that scooters and motorbikes vastly outnumber cars. Before long these fleets of two-wheelers will become battery-powered, always-connected, semi-autonomous machines that offer an even more potent alternative to their four-wheeled rivals.
The reasons powered two-wheelers dominate nations such as India, Indonesia and Vietnam with a combined population over 1.75 billion are simple: cars are unaffordable on local wages, few urban homes have space to store them, and warm climates make two-wheelers viable year-round. Plus, many of them sell for less than the equivalent of $1,000 apiece.
The industry has decided many will soon be electric and it looks like drivers will buy them.
"Electrification of micromobility can be adopted at a faster pace than cars, mainly because the motor and batteries are much smaller," Fook Fah Yap, a director at Singapore's Nanyang Technical University's Transport Research Centre told The Register.
Evidence of the shift is not hard to find. Earlier this year Honda announced it will start to sell 10 battery-powered bikes in 2025. Yamaha expects 90 percent of its sales will be electrified by 2050 and Toyota is expected to announce an electric two-wheeler this year.
[...] Twowheelers, by contrast, are all about getting from A to B, quickly and at low cost. Digital technology's role in a two-wheeler is therefore all about information related to navigation.
Read more of this story at SoylentNews.
18:02
Cryptogon Syndication to Twitter Disabled cryptogon.com
For about a decade, Ive been able to automatically post Cryptogon stories to Twitter using a plugin called WP to Twitter. That ended about a hour ago. After trying to troubleshoot, recreating my Twitter apps and API keys, etc. Im getting this error: 403 Forbidden: The request is understood, but has been refused by Twitter. []
18:00
Get That Dream Job, With a Bit of Text Injection Hackaday

Getting a job has always been a tedious and annoying process, as for all the care that has been put into a CV or resume, it can be still headed for the round file at the whim of some corporate apparatchik. At various times there have also been dubious psychometric tests and other horrors to contend with, and now we have the specter of AI before us. We can be tossed aside simply because some AI model has rejected our CV, no human involved. If this has made you angry, perhaps its time to look at [Kai Greshake]s work. Hes fighting back, by injecting a PDF CV with extra text to fool the AI into seeing the perfect candidate, and even fooling AI-based summarizers.
Text injection into a PDF is a technique the same as used by the less salubrious end of the search engine marketing world, of placing text in a web page such that a human cant read it but a machine can. The search engine marketeers put them in tiny white text or offset them far out of the viewport, and it seems the same is possible in a PDF. Hes put the injection in white and a tiny font, and interestingly, overlaid it several times.
Using the ChatGPT instance available in the Bing sidebar hes then able to fool it into an affirmative replay to questions about whether he should be hired. But its not just ChatGPT...
17:22
Apple reportedly limits internal use of AI-powered tools like ChatGPT and GitHub Copilot Lifeboat News: The Blog
As big tech companies are in a fierce race with each other to build generative AI tools, they are being cautious about giving their secrets away. In a move to prevent any of its data from ending up with competitors, Apple has restricted internal use of tools like OpenAIs ChatGPT and Microsoft-owned GitHubs Copilot, a new report says.
According to The Wall Street Journal, Apple is worried about its confidential data ending up with developers who trained the models on user data. Notably, OpenAI launched the official ChatGPT app on iOS Thursday. Separately, Bloomberg reporter Mark Gurman tweeted that the chatbot has been on the list of restricted software at Apple for months.
I believe ChatGPT has been banned/on the list of restricted software at Apple for months. Obviously the release of ChatGPT on iOS today again makes this relevant.
17:22
Apple is on the hunt for generative AI talent Lifeboat News: The Blog
Apple, like a number of companies right now, may be grappling with what role the newest advances in AI are playing, and should play, in its business. But one thing Apple is confident about is the fact that it wants to bring more generative AI talent into its business.
The Cupertino company has posted at least a dozen job ads on its career page seeking experts in generative AI. Specifically, its looking for machine learning specialists passionate about building extraordinary autonomous systems in the field. The job ads (some of which seem to cover the same role, or are calling for multiple applicants) first started appearing April 27, with the most recent of them getting published earlier this week.
The job postings are coming amid some mixed signals from the company around generative AI. During its Q2 earnings call earlier this month, CEO Tim Cook dodged giving specific answers to questions about what the company is doing in the area but also didnt dismiss it. While generative AI was very interesting, he said, Apple would be deliberate and thoughtful in its approach. Then yesterday, the WSJ reported that the company had started restricting use of OpenAIs ChatGPT and other external generative AI tools for some employees over concerns of proprietary data leaking out through the platforms.
17:22
Cruise, Waymo near approval to charge for 24/7 robotaxis in San Francisco Lifeboat News: The Blog
Self-driving vehicle companies Waymo and Cruise are on the cusp of securing final approval to charge fares for fully autonomous robotaxi rides throughout the city of San Francisco at all hours of the day or night.
Amid the citys mounting resistance to the presence of AVs, the California Public Utilities Commission (CPUC) published two draft resolutions late last week that would grant Cruise and Waymo the ability to extend the hours of operation and service areas of their now-limited robotaxi services.
The drafts are dated for a hearing June 29, and theres still room for public comments, which are due May 31. Based on the CPUCs drafted language, many of the protests raised by the city of San Francisco have already been rejected.
17:00
Big Bad Canada Pushes to Protect Profits from Mexico Terra Forming Terra

The Simplest Way to Flush Kidney Stones, Other Stones out of the Body Terra Forming Terra
The Surprising Link Between Water Intake and Stroke Risk Terra Forming Terra
Battle of the Fake Historians Heats Up Terra Forming Terra

16:51
30-Ton Shipment Of Explosive Chemical Disappears Between California And Wyoming cryptogon.com
Fell out the bottom of the rail car? Via: ZeroHedge: A 30-ton shipment of ammonium nitrate, a chemical used as both fertilizer and as a component in explosives, has gone missing during a rail shipment between Wyoming and California last month, resulting in four separate investigations. The railcar was sealed when it left the []
16:49
Notorious Cyber Gang FIN7 Returns With Cl0p Ransomware in New Wave of Attacks The Hacker News
The notorious cybercrime group known as FIN7 has been observed deploying Cl0p (aka Clop) ransomware, marking the threat actor's first ransomware campaign since late 2021. Microsoft, which detected the activity in April 2023, is tracking the financially motivated actor under its new taxonomy Sangria Tempest. "In these recent attacks, Sangria Tempest uses the PowerShell script POWERTRASH to load
16:38
Do You Need a New Iron? cryptogon.com
My wifes taste in dresses, skirts and aprons goes back about 150 years. Rather than attempting to buy clothing like that, she makes it herself using her mothers (borrowed) Bernina sewing machine from 1982 and an iron. The iron shed been using for the last fifteen years blew up. I tried to fix it, but []
15:00
Spy Transceiver Makes Two Tubes Do the Work of Five Hackaday

Here at Hackaday, we love following along with projects as they progress. Thats especially true when a project makes a another, or when the original design gets more elegant. And when you get both improved function and decreased complexity at the same time? Thats the good stuff.
Take the recent improvements to a vacuum tube spy radio as an example. Previously, [Helge (LA6NCA)] built both a two-tube transmitter and a three-tube receiver, either of which would fit in the palm of your hand. A little higher math seems to indicate that combining these two circuits into a transceiver would require five tubes, but thats not how hams like [Helge] roll. His 80-m CW-only transceiver design uses only two tubes and a lot of tricks, which we admit were still wrapping our heads around. On the receive side, one tube serves as a mixer/oscillator, combining the received signal with a slightly offset crystal-controlled signal to provide the needed beat frequency. The second tube serves as the amplifier, bot...
14:15
Warning: Samsung Devices Under Attack! New Security Flaw Exposed The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has warned of active exploitation of a medium-severity flaw affecting Samsung devices. The issue, tracked as CVE-2023-21492 (CVSS score: 4.4), impacts select Samsung devices running Android versions 11, 12, and 13. The South Korean electronics giant described the issue as an information disclosure flaw that could be exploited by a
14:10
Astronomers Solve the 60-Year Mystery of Quasars the Most Powerful Objects in the Universe SoylentNews
First discovered 60 years ago, quasars can shine as brightly as a trillion stars packed into a volume the size of our Solar System. In the decades since they were first observed, it has remained a mystery what could trigger such powerful activity. New work led by scientists at the Universities of Sheffield and Hertfordshire has now revealed that it is a consequence of galaxies crashing together.
The collisions were discovered when researchers, using deep imaging observations from the Isaac Newton Telescope in La Palma, observed the presence of distorted structures in the outer regions of the galaxies that are home to quasars.
Most galaxies have supermassive black holes at their centres. They also contain substantial amounts of gas but most of the time this gas is orbiting at large distances from the galaxy centres, out of reach of the black holes. Collisions between galaxies drive the gas towards the black hole at the galaxy centre; just before the gas is consumed by the black hole, it releases extraordinary amounts of energy in the form of radiation, resulting in the characteristic quasar brilliance.
[...] This is the first time that a sample of quasars of this size has been imaged with this level of sensitivity. By comparing observations of 48 quasars and their host galaxies with images of over 100 non-quasar galaxies, researchers concluded that galaxies hosting quasars are approximately three times as likely to be interacting or colliding with other galaxies.
The study has provided a significant step forward in our understanding of how these powerful objects are triggered and fuelled.
Journal Reference:
C S Pierce et al., Galaxy interactions are the dominant
trigger for local type 2 quasars [open], Monthly Notices of
the Royal Astronomical Society, Volume 522, Issue 2, June
2023, Pages 17361751, https://doi.org/10.1093/mnras/stad455
Read more of this story at SoylentNews.
12:02
OSI Running Microsoft Ads (and Promoting Proprietary GitHub) Under the Guise of Webinar Techrights
The Open Source Initiative, or OSI for short, is basically a Microsoft front group these days
Summary: Microsofters are speaking on behalf of OSI again, jointly with Linux Foundation, essentially promoting Microsofts own initiatives [1, 2, 3, 4] and traps like proprietary GitHub, which abuses the GPL (the OSIs chief actively lobbies for Microsoft on Microsofts payroll in class action litigation over GPL violations)
12:00
Prompt Injection: An AI-Targeted Attack Hackaday

For a brief window of time in the mid-2010s, a fairly common joke was to send voice commands to Alexa or other assistant devices over video. Late-night hosts and others would purposefully attempt to activate voice assistants like these en masse and get them to do ridiculous things. This isnt quite as common of a gag anymore and was relatively harmless unless the voice assistant was set up to do something like automatically place Amazon orders, but now that much more powerful AI tools are coming online were seeing that joke taken to its logical conclusion: prompt-injection attacks.
Prompt injection attacks, as the name suggests, involve maliciously inserting prompts or requests in interactive systems to manipulate or deceive users, potentially leading to unintended actions or disclosure of sensitive information. Its similar to something like an SQL injection attack in that a command is embedded in something that seems like a normal input at the start. Using an AI like GPT comes with an inherent risk of attacks like this when using it to automate tasks, as commands to the AI can be hidden where a user might not ex...
11:30
[Meme] A Racket in Open Source Clothing Techrights
He quietly stole his workers money and bought luxury cars
Summary: The fraud at Sirius Open Source had many victims; most of them are voiceless, however, as they dont blog, but they still got robbed and they want justice.
11:21
Getting Sirius Managers Arrested Before They Dismantle the Company and Vanish schestowitz.com
Summary: The crimes of Sirius Open Source have culminated in two parallel reports; tax fraud was reported as well, as per advice weve received, even though thats not the crime but a side issue for a company that became petty thief (very big thief)
Maybe it shouldnt be so surprising. Ive noticed that almost everyone at Sirius has left already. Very few are left there and they too are looking for a way out (another job). But that wouldnt be the end of this affair because criminals must be held accountable. They know who they are. Theyre managers. Theyre also perpetrators.
Many parties knowingly or unknowingly facilitated the crime. One person recently asked me: Did Standard Life ever send you a statement showing the purported balance of the account or even a statement showing a nil balance?
No is the short answer, but all of us assumed it was just being silent. All of us.
There is a problem associated with legitimisation of the embezzlement, including letters and payslips that fraudulently claimed pension money had been paid. Every single payslip was a lie. Were talking about hundreds of payslips.
The Pensions Regulator deals with different scenarios, so it is inapplicable here.
Another person asked: Do you have legal advice on the topic?
Well, we went to a lawyer as soon as last year. We agreed its not worth suing due to speed and a lack of funds in the company. There would hardly be anything left after 12 months. Litigation is very time-consuming a process. Just 5.5 months after I left the company there are fewer than 5 full-time workers there.
The same person added:
These appear to be the two pertinent questions:
Does the employer owe a debt to you or they owe the money to the pension scheme? This is an important technicality. For example, can they simply discharge their responsibility by giving you a lump sum directly and you can put it in any pension you want.
Defrauding employees and then offering them the money stolen (after getting caught) doesnt change the fact that fraud took place.
It seems possible that the company tried to pay off one victim to keep silent on the matter, but we cannot prove this.
The above...
11:13
Holding Criminals Accountable Part VII Fraud Since 2011 (If Not Earlier) Merits Criminal Prosecution Techrights
Series parts:
- Holding Criminals Accountable Part I Sirius Crimes Reported to British Authorities, Formally Registered With References (Many Victims), Heres What It Means and What Happens Next
- Holding Criminals Accountable Part II Still No Action From Action Fraud
- Holding Criminals Accountable Part III Why Police Action is the Only Option Now
- Holding Criminals Accountable Part IV British Prime Minister Launches Crackdown on Fraud, So Now Prove It
- Holding Criminals Accountable Part V 20 Days Later, UK Action Fraud Shows No Signs of Action
- Holding Criminals Accountable Part VI 26 Days Later and Still Inaction/No Action by the Police That Had Endless Resources for Coronation Ceremony
- YOU ARE HERE Fraud Since 2011 (If Not Earlier) Merits Criminal Prosecution
Summary: The crimes of Sirius Open Source have culminated in two parallel reports; tax fraud was reported as well, as per advice weve received, even though thats not the crime but a side issue for a company that became petty thief (very big thief)
Maybe it shouldnt be so surprising. Ive noticed that almost everyone at Sirius has left already. Ve...
10:17
Edward Snowden in FSF Event: What Happened in 2013 Would Not Have Been Possible Without Free Software Techrights
10:12
10 Years Ago Edward Snowden Did the Right Thing Techrights
This happened 10 years ago:
And he still talks about the dangers:
Summary: Many people have set aside the lessons learned from the NSA leaks, almost as if all these practices just gradually stopped over time (theyve only gotten worse since then)
10:04
Canadian Desktops and Laptops: Windows 61.7%, GNU/Linux 5.5% Techrights
Summary: This months numbers show another shark drop for Windows; GNU/Linux + ChromeOS (based on Gentoo) rose to over 5.5% in Canada, where many schools ditched Windows
09:30
Sirius Open Source Reported to HM Revenue and Customs (HMRC) for Tax Fraud Techrights
Much more to come very soon
Summary: Today, 28 days after crimes of Sirius Open Source had been reported to the police (which barely made any progress, as expected), were proceeding to a report for tax fraud; we have extensive evidence that the payslips of several employees lied for over half a decade, in effect defrauding the British taxpayers, not just embezzling the staff
09:24
Malware Turns Home Routers Into Proxies for Chinese State-Sponsored Hackers SoylentNews
Malware turns home routers into proxies for Chinese state-sponsored hackers
Researchers have uncovered malicious firmware that can turn residential and small office routers into proxies for Chinese state-sponsored hackers. The firmware implant, discovered by Check Point Research, includes a full-featured backdoor that allows attackers to establish communication, issue commands, and perform file transfers with infected devices. The implant was found in TP-Link routers but could be modified to work on other router models.
The malware's main purpose is to relay traffic between infected targets and command-and-control servers, obscuring the origins and destinations of the communication. The control infrastructure was traced back to hackers associated with the Chinese government. By using a chain of infected devices, the attackers can hide the final command and control and make it difficult for defenders to detect and respond to the attack.
This technique of using routers and other IoT devices as proxies is a common tactic among threat actors. The researchers are unsure how the implant is installed on devices but suspect it could be through exploiting vulnerabilities or weak administrative credentials.
While the firmware image discovered so far only affects TP-Link devices, the modular design allows the threat actors to create images for a wider range of hardware. The article concludes with recommendations for users to check for potential infections and apply proactive mitigations such as patching routers and using strong passwords.
Read more of this story at SoylentNews.
09:00
Early Computer Art from the 1950s and 1960s Hackaday

Modern day computer artist, [Amy Goodchild] surveys a history of Early Computer Art from the 1950s and 1960s. With so much attention presently focused on AI-generated artwork, we should remember that computers have been used to created art for many decades.
Our story begins in 1950 when Ben Laposky started using long exposure photography of cathode ray oscilloscopes to record moving signals generated by electronic circuits. In 1953, Gordon Pask developed the electromechanical MusiColor system. MusiColor empowered musicians to control visual elements including lights, patterns, and motorized color wheels using sound from their instruments. The musicians could interact with the system in real-time, audio-visual jam sessions.
In the early 1960s, BEFLIX (derived form Bell Flix) was developed by Ken Knowlton at Bell Labs as a programming language for generating video animations. The Graphic 1 computer featuring a light pen input device was also developed at Bell Labs. Around the sa...
08:59
Links 19/05/2023: AlmaLinux 8.8 and GNU Health in Afghanistan Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Pseudo-Open Source
- Linux Foundation
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Monopolies
-
GNU/Linux
-
Desktop/Laptop
-
07:15
Piracy Bots Channels Are Rampant on Telegram, But For How Long? TorrentFreak
 With over half a billion active users around the globe,
Telegram is one of the most
used messaging services.
With over half a billion active users around the globe,
Telegram is one of the most
used messaging services.
The communication platform helps to connect people from all over the world, with end-to-end encryption providing improved security when compared to some other players in the market.
Telegram can also be an excellent medium to broadcast messages to a wider audience. Through dedicated one-way channels, people can share news, status updates, and emergency alerts, for example.
Telegram on the Anti-Piracy Agenda
Like all technology, these broadcast channels are not only used for legitimate purposes. Pirates use them too, as evidenced by regular mentions in piracy discussions. Not too long ago, the European Commission placed the Telegram app on its Counterfeit and Piracy Watch List.
The app was also mentioned in recommendations to the U.S. Trade Representative (USTR) this year, with the International Intellectual Property Alliance calling for stricter policies on Telegrams part, including the addition of Know Your Business Customer (KYBC) rules.
Telegram should be more accountable in relation to infringements occurring or being facilitated over its service, the recommendation advised.
IIPA recommends that more be done to encourage KYBC disciplines on intermediaries like Telegram and to encourage operators like them to responsibly cooperate.
Courts Get Involved
Piracy concerns and policy musings like these havent been restricted to lobbying and policy efforts. Telegram has also been taken to court on several occasions.
In Portugal, for example, a local court ordered Telegram to block access to more than a dozen piracy-related channels. Similar measures were also taken in Israel and Italy. In India, Telegram a court order required Telegram to disclose the identities of several pirating users.
By now, Telegram is well aware of the piracy challenges but that hasnt put an end to the problem.
While doing research this week, we randomly stumbled upon a Telegram bot that direc...
07:03
Overcoming Kubernetes Monitoring Challenges with Observability Linux.com

Kubernetes adoption is rapidly increasing, surpassing cloud
adoption, as companies recognize its ability to provide agility and
flexibility in deploying critical applications. However, the
additional layers of abstraction in Kubernetes pose challenges to
observability. Understanding whats running in each cluster, node,
or pod is a top monitoring challenge since resources constantly
move. This complexity creates an increased security challenge due
to uncertainty about the running environment.
The post Overcoming Kubernetes Monitoring Challenges with Observability appeared first on Linux.com.
06:59
[$] Fighting the zombie-memcg invasion LWN.net
Memory control groups (or "memcgs") allow an administrator to manage the memory resources given to the processes running on a system. Often, though, memcgs seem to have memory-use problems of their own, and that has made them into a recurring Linux Storage, Filesystem, and Memory-Management Summit topic since at least 2019. The topic returned at the 2023 event with a focus on the handling of shared, anonymous memory. The quirks associated with this memory type, it seems, can subject systems to an unpleasant sort of zombie invasion; a session in the memory-management track led by T.J. Mercier, Yosry Ahmed, and Chris Li discussed possible solutions.
06:40
What Makes Junk Food Junk? SoylentNews
How is "junk food" defined for food policies like taxes? A combination of food category, processing, and nutrients can determine which foods should be subject to health-related policies, according to a new analysis examining three decades of U.S. food policies by researchers at the NYU School of Global Public Health and the Friedman School of Nutrition Science and Policy at Tufts.
[...] "There is a growing recognition that an unhealthy diet stems from overconsumption of what we colloquially refer to as 'junk food,' " said Jennifer Pomeranz, assistant professor of public health policy and management at NYU School of Global Public Health and the first author of the study, published in the journal Milbank Quarterly. "However, public health efforts to address junk food are hindered by a lack of a uniform method to define junk food for policy purposes."
One policy example where a definition for junk food is needed is a junk food tax, which raises the price of such products to reduce consumption and generate revenue for other programs to improve the nutrition and health of communities in need. Previous research by NYU and Tufts shows that taxes on junk food are administratively and legally feasible.
[...] They identified and analyzed 47 laws and bills from 1991 through 2021, including one active junk food tax law implemented by the Navajo Nation, three state snack food sales taxes that were later repealed, and numerous junk food tax bills that have not been enacted. (Their analysis did not include policies that solely focused on beverages such as soda taxes.)
[...] The researchers were surprised that no state tax laws or bills directed the state's public health department to define the foods subject to the tax, a practice regularly used at the federal level and a mechanism that states could use to have experts define the foods to be taxed.
Read more of this story at SoylentNews.
06:24
Luxottica - 77,093,812 breached accounts Have I Been Pwned latest breaches
In March 2021, the world's largest eyewear company Luxoticca suffered a data breach via one of their partners that exposed the personal information of more than 70M people. The data was subsequently sold via a popular hacking forum in late 2022 and included email and physical addresses, names, genders, dates of birth and phone numbers. In a statement from Luxottica, they advised they were aware of the incident and are currently "considering other notification obligations".
06:14
OpenAI Launches ChatGPT App for iOS, Bolstering Accessibility and Safety HackRead | Latest Cybersecurity and Hacking News Site
While the ChatGPT app is currently available exclusively for iOS users, OpenAI assures Android users that they are next in line to experience the benefits of the app.
This is a post from HackRead.com Read the original post: OpenAI Launches ChatGPT App for iOS, Bolstering Accessibility and Safety
06:00
3D Printing Blueprints and Other Wall Art Hackaday

Today if you want to reproduce a big schematic or a mechanical drawing, you just ask it to print or plot from the CAD model. But back in the day, you drew on big sheets at a drafting table. How do you make copies? Sure, there were a few large-format copiers, but they were expensive. A more common method was to use a heliographic copier which, often but not always, resulted in a blueprint that is a blue page with white lines or vice versa. These days, you are more likely to see a blueprint as an artistic wall hanging, and since [Basement Creations] wanted some, he figured out how to make them with a 3D printer.
These prints arent really blueprints. They use the printer as a plotter and deposit white ink on a blue page. In the video below, he shows a number of ways to use a printer to create interesting wall art, even if you want it to be bigger than the print bed. Some of the wall art uses multiple 3D printed parts, and others use the printer as a plotter.
To join the printed pieces, he uses a soldering iron to weld them together. We wondered if it might be worthwhile to make overlapping pieces to glue which would also help with alignment. Plotting is great for making PCBs, of course, and while you could invert the image and print blue on white paper, it wont really look like a blueprint.
Youd think mounting a pen to a printer is easy, and...
05:19
Biden Clears Way for Ukraine to Get F-16 Fighter Jets cryptogon.com
Via: The Messenger: The U.S. will support an international effort to train Ukrainian pilots on F-16 fighter jets, a senior administration official confirmed to The Messenger, a shift in policy that will clear the way for F-16s and other aircraft to be sent to Ukraine. President Joe Biden announced the change to other world leaders []
05:17
Actual Headline: $3 Billion Accounting Error Means the Pentagon Can Send More Weapons to Ukraine cryptogon.com
Via: AP: The Pentagon has overestimated the value of the weapons it has sent to Ukraine by at least $3 billion an accounting error that could be a boon for the war effort because it will allow the Defense Department to send more weapons now without asking Congress for more money. The acknowledgment Thursday []
05:01
Robert F. Kennedy Jr. Names Dennis Kucinich as 2024 Campaign Manager cryptogon.com
Via: The Hill: Robert F. Kennedy Jr. has appointed former Rep. Dennis Kucinich (D-Ohio) as the campaign manager for his 2024 primary challenge to President Biden. Dennis Kucinich has brought invaluable electoral experience to our campaign, Kennedy said in a statement. He knows how the system works from the inside out, and his deep knowledge []
04:52
CIA Contractor, Dr. Garry Nolan, Claims U.S. Government Has, Downed UFOs, Reverse Engineering Programs cryptogon.com
This might be the biggest limited hangout of all time. Nolan states, Whats crashing is not actual living things Mostly, what youre seeing here are either drones or some sort of advanced AI. So, for everyone keeping score, according to Nolan, the U.S. Government is in possession of, Downed UFOs, but dont worry about the []
04:30
Video Friday: Lunar Transport IEEE Spectrum

Video Friday is your weekly selection of awesome robotics
videos, collected by your friends at IEEE Spectrum
robotics. We also post a weekly calendar of upcoming robotics
events for the next few months. Please
send us your events for inclusion.
ICRA 2023: 29 May2 June 2023, LONDON
Energy Drone & Robotics Summit: 1012 June 2023, HOUSTON
RoboCup 2023: 410 July 2023, BORDEAUX, FRANCE
RSS 2023: 1014 July 2023, DAEGU, SOUTH KOREA
IEEE RO-MAN 2023: 2831 August 2023, BUSAN, SOUTH KOREA
IROS 2023: 15 October 2023, DETROIT
CLAWAR 2023: 24 October 2023, FLORIANOPOLIS, BRAZIL
Humanoids 2023: 1214 December 2023, AUSTIN, TEXAS
Enjoy todays videos!
LATTICE is an undergrad project from Caltech thats developing a modular robotic transportation system for the lunar surface that uses autonomous rovers to set up a sort of cable car system to haul things like ice out of deep craters to someplace more useful. The prototype is fully functional, and pretty cool to watch in action.
Were told that the team will be targeting a full system demonstration deploying across a crater on Earth this time next year. As to what those quotes around crater mean, your guess is as good as mine.
[ Caltech ]
Thanks, Lucas!
Happy World Cocktail Day from Flexiv!
...
04:00
IEEE Celebrates Engineering Pioneers and Emerging Technologies IEEE Spectrum

IEEEs Vision, Innovation, and Challenges Summit and Honors Ceremony showcases emerging technologies and celebrates engineering pioneers who laid the groundwork for many of todays electronic devices. I attended this years events, held on 4 and 5 May in Atlanta. Here are highlights of the sessions, which are available on IEEE.tv.
The summit kicked off on 4 May at the Georgia Aquarium with a reception and panel discussion on climate change and sustainability, moderated by Saifur Rahman, IEEE president and CEO. The panel featured Chris Coco, IEEE Fellow Alberto Moreira, and IEEE Member Jairo Garcia. Coco is senior director for aquatic sustainability at the aquarium. Moreira is director of the German Aerospace Center Microwaves and Radar Institute in Oberpfaffenhofen, Bavaria. Garcia is CEO of Urban Climate Nexus in Atlanta. UCN assists U.S. cities in creating and executing climate action and resilience plans.
The panelists focused on how the climate crisis is affecting the ocean and ways technology is helping to track environmental changes.
Coco said one of the biggest challenges facilities such as his are facing is finding enough food for their animals. Because sea levels and temperatures are rising, more than 80 percent of marine life is migrating toward the Earths poles and away from warmer water, he said. With fish and other species moving to new habitats, ocean predators that rely on them for food are following them. This migration is making it more difficult to find food for aquarium fish, Coco said. He added that technology on buoys is monitoring the waters quality, and temperature, and levels.
Moreira, recipient of this years...
03:58
Google's New Registered Domains Include .Zip and .Mov for a More "Exciting" and Insecure Internet SoylentNews
Researchers are debating how the new domains will affect web security and users' habits:
In Google's own words, new generic top-level domains (gTLDs) can help self-expression, creativity and business. The previously approved list of "hundreds" of gTLDs entries now provides some troublesome additions such as "zip" and "mov," which can (and will) be abused to target users with sophisticated phishing attacks.
Google Registry has recently introduced 8 new top-level domains for "dads, grads, and techies," adding .dad, .phd, .prof, .esq, .foo, .nexus, .zip, and .mov to its growing list of some of the "most popular" gTLDs which also include .app and .dev. The .zip and .mov domains, however, have sparked a debate among experts about their potential consequences on internet and web overall security.
The zip and mov gTLDs were available in IANA's DNS records since 2014, but they have now become generally available thanks to Google's involvement. Now, anyone can purchase a ".zip" or ".mov" domain like "techspot.zip," even though the two suffixes have long been used to identify compressed file archives in Zip format and video clip files.
The overlap between two, extremely popular file formats the Zip standard was created by Pkware in 1989, 34 years ago and the recently registered web domains will bring new security threats to the internet ecosystem, some researchers said. Users could be deceived by malicious URLs shared on social networks or by mail, giving cyber-criminals new, "creative" tools to push malware installations, phishing campaigns or other nefarious activities.
Read more of this story at SoylentNews.
03:50
February cyber incident will cost molten metal flow engineering firm Vesuvius 3.5 million Security Affairs
Vesuvius, a leader in molten metal flow engineering and technology, revealed that the February cyber incident will cost it 3.5 million
Vesuvius is a global leader in molten metal flow engineering and technology, it employs more than 10,000 people and is listed on the London Stock Exchange. In February the company disclosed a security breach and revealed that it discovered unauthorized access to its systems. At the time the company did not provide details about the attack.
Immediately upon becoming aware of unauthorised activity on our networks, we have taken the necessary steps to investigate and respond to the incident, including shutting down affected systems. We are working with leading cyber security experts to support our investigations and identify the extent of the issue, including the impact on production and contract fulfilment. reads a statement issued by the company.
In an update provided by Vesuvius, the company explained that the cyber incident will cost it 3.5 million (approximately $4.6 million at the current exchange).
Foundry has delivered particularly well with resilient pricing in the period driving better than expected margin. The Steel division was also ahead of expectations, benefitting from resilient pricing as well as slightly better than anticipated volumes. reads a new statement published by the company. This good performance has been achieved despite the impact of the cyber incident that occurred earlier in the year, which we expect to have a cost impact of c. 3.5m.
Progress in inventory management has been slowed down by the cyber incident but is expected to resume in the coming months. We remain focused and are confident in continuing to make improvements throughout the year.
Please nominate Security Affairs as your favorite blog.
...
03:02
Frans de Jonge tells us about KOReader in this AGPLv3 interview FSF blogs
This is the latest installment of our Licensing and Compliance Lab's series on free software developers who choose GNU licenses for their works.
03:00
VKD3D-Proton 2.9 Released With Performance Improvements Phoronix
Hans-Kristian Arntzen of Valve's Linux team has just released VKD3D-Proton 2.9 as the latest major update to this Direct3D 12 on Vulkan API implementation that is used by Steam Play (Proton) for running modern Windows games on Linux...
02:39
10 Years After Snowden: Some Things Are Better, Some Were Still Fighting For Deeplinks
On May 20, 2013, a young government contractor with an EFF
sticker on his laptop disembarked a plane in Hong Kong carrying
with him evidence confirming, among other things, that the United
States government had been conducting mass surveillance on a global
scale. What came next were weeks of disclosuresand official
declassificationsas Edward Snowden worked with some of the worlds
top news organizations to reveal critical facts about the National
Security Agency vacuuming up peoples online communications,
internet activity, and phone records, both inside and outside the
U.S..
Groups like EFF had been fighting since long before 2013
to reveal and stop the dangerous mass surveillance conducted
within the heart of the secretive national security apparatus. But
after that summer, Snowdens revelations acted like a flood light,
allowing everyone to better see and understand what happens inside
the black box of government surveillance of millions of innocent
people in the US. and around the world. The tremendous amount
of evidence slowed, if not stopped, the disingenuous denials that
the government had made both publicly and privately in response to
our allegations. The actual documentary evidence also helped us to
better pinpoint our demands, our questions, and our legal
tools.
Theres still much work to be done to rein in our overzealous national security state, break political gridlock, and end the extreme secrecy that insulates some of the governments most invasive tactics.
Now, ten years after those pivotal revelations, what has changed? Some things are undoubtedly betterunder the intense scrutiny of public attention, some of the National Security Agencys most egregiously illegal programs and authorities have shuttered or been forced to end. The Intelligence Community has started affirmatively releasing at least some important information, although EFF and others have still had to fight some long Freedom of Information Act (FOIA) battles. Outside of government, companies and organizations have worked to close many of the security holes that the NSA abused, most prominently by encrypting the web.
But its not enoughnot even close. Theres still much work to be done to rein in our overzealous national security state, break political gridlock, and end the extreme secrecy that insulates some of the governments most invasive tactics. One of the most important of those is the upcoming fight to ...
02:30
Accenture invests in SpiderOak to elevate satellite communications security in space Help Net Security
Accenture has made a strategic investment, through Accenture Ventures, in SpiderOak. SpiderOaks OrbitSecure product suite brings zero trust security to zero gravity environments. OrbitSecure leverages a combination of no-knowledge encryption and distributed-ledger technology in order to meet the demands of cybersecurity in space. The product suite includes a fully decentralized key management system that helps enable full availability and continued operations in space, even within disconnected or highly contested networks. This increases resiliency for multi-vendor, More
The post Accenture invests in SpiderOak to elevate satellite communications security in space appeared first on Help Net Security.
02:00
Zerto 10 for Microsoft Azure delivers disaster recovery (DR) and mobility at scale Help Net Security
Zerto has announced the launch of Zerto 10 for Microsoft Azure, delivering enhanced disaster recovery (DR) and mobility for complete infrastructure flexibility. Zerto 10 delivers a new replication architecture for scale-out efficiency and native protection of Azure Virtual Machines (VMs). Zerto 10 provides new support for multi-disk consistency for VMs in Microsoft Azure to protect an organizations data not just to and from Azure but also across Azure regions within the cloud. Zerto coordinates More
The post Zerto 10 for Microsoft Azure delivers disaster recovery (DR) and mobility at scale appeared first on Help Net Security.
01:40
States Should Not Skirt Federal Rules on Fiber Infrastructure Deeplinks
Across the country, states are designing broadband plans to begin spending billions of federal dollars made available by the Infrastructure Investment and Jobs Act (IIJA) and past COVID-19 rescue dollar investment programs. The Biden administration has consistently made clear that states are to build future-proof infrastructure to deliver broadband that will be useful for communities for decades. This is arguably one of the best changes in federal policy for broadband subsidies ever. Past federal subsidy efforts in broadband failed to take long-term needs into account, which is how billions from past investments have gone to waste. But, despite this clear federal guidance, debates continue to rage in state legislatures and implementing bodies as entities unable to deliver future-proof access hope to get a cut of federal subsidy dollars.
Federal Rescue Money and BEAD Grant Rules on Fiber
Both the Treasury Department's Capital Projects Fund and the
National Telecommunications Information Administration's (NTIA)
Broadband Equity Affordability and Deployment grant programs
provide clear guidance to prioritize fiber-based infrastructure.
Under the
Treasury rules that govern rescue dollars, the presumptively
eligible projects for broadband infrastructure must reliably
deliver 100/100 mbps connectivity. While there is an exception for
lower speeds, there is a general expectation that these projects
can scale higher for future needs. Specifically, recipients are
encouraged to prioritize investments in fiber-optic infrastructure
where feasible to emphasize that projects should consider fiber
first.
The NTIA program also
directs states to follow the statutory text of the IIJA.
Under that law, projects must be scalable, able to
facilitate 5G and beyond, able to evolve with community needs, and
build fiber-based infrastructure with limited exceptions for
extremely high-cost areas. Arguably, options such as fixed wireless
and satellite broadband could be considered for extremely high-cost
areaswhich unfortunately are not future-proofed like fiber. But
states relying on federal dollars alone will be forced to deliver
less than states that are matching the federal investment with
their own local dollars.
Wireless Lobby Push on States to Deprioritize Fiber Risks Federal Dollars
Much of the policy-making in telecom subsidies has emphasized technology neutrality, which is code for saying every broadband provider should...
01:30
NTT and Cisco help customers transition to IoT-as-a-Service model Help Net Security
NTT and Cisco have announced a collaboration to develop and deploy joint solutions that empower organizations to improve operational efficiencies and advance sustainability goals. Leveraging NTTs Edge as a Service portfolio and Ciscos IoT capabilities, solutions developed by the two companies will offer real-time data insights, enhanced security, improved decision-making, and reduced operational costs through predictive maintenance, asset tracking, and supply chain management capabilities. The companies will deliver solutions that combine NTTs Managed Services expertise, More
The post NTT and Cisco help customers transition to IoT-as-a-Service model appeared first on Help Net Security.
01:13
What is Bio-Oil, and Why Does Big Tech Think It Can Fight Climate Change? SoylentNews
Some of the biggest names in tech have inked a deal to turn corn stalks and tree trimmings into a barbecue sauce ingredient and then pump the stuff underground to try to fight climate change.
That sounds wild, so let's break it down from the start. Alphabet, Meta, Stripe, Shopify, and McKinsey Sustainability launched a new climate initiative called Frontier about a year ago. The goal is to boost new technologies capable of sucking carbon dioxide out of the atmosphere by convincing other companies to buy into them.
Today, a San Francisco-based climate tech startup called Charm Industrial announced that Frontier's founding members and a smattering of other companies have agreed to pay Charm a total of $53 million to capture and store 112,000 tons of carbon dioxide between 2024 and 2030.
Some of the biggest names in tech have inked a deal to turn corn stalks and tree trimmings into a barbecue sauce ingredient
Charm has an unconventional way of getting that done. First, it collects agricultural and forestry waste i.e., discarded corn stalks or branches leftover from logging. Wherever it finds that stuff, it sends its fleet of flatbed semi trucks hauling reactors that heat up the waste to 500 degrees Celsius without burning it. That turns the waste into bio-oil, a tarry-looking carbon-rich liquid.
The watery part of the bio-oil is essentially the same thing as liquid smoke, an ingredient used to give barbecue sauce and other foods a smokey flavor, according to Charm CEO and co-founder Peter Reinhardt.
Bio-oil also holds the carbon dioxide that the plants or trees its made from absorbed for photosynthesis. Had those corn stalks or tree branches been disposed of by burning or simply left to rot, that CO2 would have escaped again heating the planet along with all the other emissions that come from burning fossil fuels.
Read more of this story at SoylentNews.
01:08
Good Morning Britain Host Martin Lewis: Action Fraud is Pointless Techrights
This was published less than 2 years ago: (check out the video too)
Summary: I may not be the first person to independently reach such conclusions; the pension crime (fraud) of Sirius Open Source was reported to Action Fraud 28 days ago (it has victims other than myself as well) and theres no response; even efforts to phone them up turned up to be useless so far
01:00
New Relic integrates infrastructure and application monitoring for faster troubleshooting Help Net Security
New Relic has unveiled a new, integrated experience for its infrastructure monitoring and application performance monitoring (APM) capabilities that correlates the health and performance of applications and hosts in real-time. Engineers, DevOps, and ITOps can now diagnose application and infrastructure performance issues, and avoid context switching or missing critical insights due to siloed infrastructure monitoring tools. Now organizations can afford to analyze all of their telemetry data without sampling, ensuring they have the necessary data More
The post New Relic integrates infrastructure and application monitoring for faster troubleshooting appeared first on Help Net Security.
00:51
Action Fraud: Anybody Home or Just Bots? schestowitz.com
Video download
link | md5sum
4cd628f27bc3a0865875d46519d80701
Nobody to Speak With Today
Creative Commons Attribution-No Derivative Works 4.0
Summary: 28 days ago I reported fraud committed by Sirius Open Source against many members of its own staff for more than half a decade; An assessment will be made as to whether there are viable lines of enquiry that would enable a law enforcement body, such as the police service, to investigate. The NFIB aim to provide you with an update on your report within 28 days, they said 28 days ago, but no word was received from them. Today I phoned them up for an update and the video above documents the process. The short story is, no human answered the call and I ended up with a silent wait, maybe due to a technical error.
I am sorry to hear you have been a victim of crime, said a message to me 28 days ago. Thank you for taking the time to report to Action Fraud. Your report has been sent to the National Fraud Intelligence Bureau (NFIB) for review.
Did they get back to me? No, Not yet.
Maybe the coronation spectacle kept them very busy.
As the video hopefully makes evident, their answering system isnt working. I didnt even get to speak to a person. I was just muted completely for several minutes (or rather, the other side was perpetually muted, without any indication of any progress whatsoever).
This is especially frustrating as people have been the victims of a crime and theres nobody to even speak to. Manchesters police told me I must contact Action Fraud, not them. After 28 days there has been no action, just inaction, and there seems to be nobody to speak to for updates. Thats a lot worse than I expected when initiating the call.
Maybe its intentional? To keep down the plebs and chavs? Its probably not intentional, but I will try again on Monday to see if I get any luckier, even though these calls arent cheap and quite...
00:50
CodeWeavers Now Controlled By An Employee Ownership Trust Phoronix
CodeWeavers, the company known for its CrossOver software for running Windows games/apps on Linux / macOS / Chrome OS and in turn being the main corporate backer to the Wine project, is now transitioned to being an employee ownership trust. This comes with Jeremy White deciding to leave the company after 27 years...
00:48
Action Fraud: Nobody to Speak to Techrights
Video download
link | md5sum
4cd628f27bc3a0865875d46519d80701
Nobody to Speak With Today
Creative Commons Attribution-No Derivative Works 4.0
Summary: 28 days ago I reported fraud committed by Sirius Open Source against many members of its own staff for more than half a decade; An assessment will be made as to whether there are viable lines of enquiry that would enable a law enforcement body, such as the police service, to investigate. The NFIB aim to provide you with an update on your report within 28 days, they said 28 days ago, but no word was received from them. Today I phoned them up for an update and the video above documents the process. The short story is, no human answered the call and I ended up with a silent wait, maybe due to a technical error.
I am sorry to hear you have been a victim of crime, said a message to me 28 days ago. Thank you for taking the time to report to Action Fraud. Your report has been sent to the National Fraud Intelligence Bureau (NFIB) for review.
I didnt even get to speak to a person.Did they get back to me? No, Not yet.
Maybe the coronation spectacle kept them very busy.
For some background and context, consider reading the follow parts in turn:
00:43
Bernd Schubert led a session at the 2023 Linux Storage, Filesystem, Memory-Management and BPF Summit on the intersection of FUSE and io_uring. He works for DDN Storage, which is using FUSE for two network-storage products; he has found FUSE to be a bottleneck for those filesystems. That could perhaps be improved by using io_uring, which is something he has been working on and wanted to discuss.
00:34
Links 19/05/2023: Newer Laptops With GNU/Linux Preinstalled Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Digital Restrictions (DRM)
- Monopolies
- Gemini* and Gopher
00:30
Strata Identity unifies Maverics ID Orchestration functions across environments Help Net Security
The post Strata Identity unifies Maverics ID Orchestration functions across environments appeared first on Help Net Security.
00:25
NVIDIA R530 vs. AMD Linux 6.3 + Mesa 23.2-dev Gaming Performance Phoronix
Due to the constantly evolving state of the open-source Linux graphics drivers in particular, here is a fresh look at an assortment of AMD Radeon GPUs making use of the Mesa 23.2 development code for the newest RadeonSI and RADV drivers paired with the recently released Linux 6.3 kernel. These open-source Radeon Linux gaming benchmark results are going up against various NVIDIA GeForce RTX 30/40 series graphics cards using the NVIDIA 530.41.09 release as its latest Linux driver.
00:00
Juniper Networks and ServiceNow partner to deliver E2E automation for MSPs and enterprises Help Net Security
Juniper Networks and ServiceNow have formed a partnership to deliver end-to-end automation for managed service providers and enterprises. With this newly formed collaboration leveraging Juniper Mist Cloud and ServiceNow Telecom Service Management and Order Management for Telecom, joint customers can eliminate multi-layer, multivendor solutions, thereby boosting network deployment and operational efficiencies while reducing costs. Juniper Networks joins the ServiceNow Technology Partner Program enabling both companies to expand their global reach while delivering better experiences for More
The post Juniper Networks and ServiceNow partner to deliver E2E automation for MSPs and enterprises appeared first on Help Net Security.
Friday, 19 May
23:30
Check Point CloudGuard secures Microsoft Azure Virtual WAN Help Net Security
Check Point announces its Next-Generation Cloud Firewall natively integrated with Microsoft Azure Virtual WAN to provide customers with improved security. The integration provides advanced threat prevention and multi-layered network security across public, private and hybrid-clouds, enabling businesses to confidently migrate to Azure with maximum operational efficiency. Microsoft Azure Virtual WAN is a network-as-a-service that provides customers with a range of benefits simplifying networking, security and routing functionalities to drive scalability, cost savings and improved performance. More
The post Check Point CloudGuard secures Microsoft Azure Virtual WAN appeared first on Help Net Security.
23:25
Take action now to avoid BianLian ransomware attacks, US Government warns organisations Graham Cluley
A joint alert has been issued by US government agencies, advising organisations of the steps they should take to mitigate the threat posed by BianLian ransomware attacks.
23:00
Zerto Cyber Resilience Vault allows users to monitor for encryption-based anomalies Help Net Security
Zerto launched a new real-time encryption detection mechanism and air-gapped recovery vault for enhanced hybrid cloud protection and security against cyber threats. These new features are part of Zerto 10, which includes advanced detection mechanisms that allow users to monitor for encryption-based anomalies, enabling organizations to pinpoint and mitigate the early stages of a potential ransomware attack. The Cyber Resilience Vault provides the ultimate layer of protection allowing for clean copy recovery from an air-gapped More
The post Zerto Cyber Resilience Vault allows users to monitor for encryption-based anomalies appeared first on Help Net Security.
Thursday, 18 May
20:50
22bet App Cameroon Download 22bet Apk For Android And Ios h+ Media
22bet App Cameroon Download 22bet Apk For Android And Ios
Each week youll be charged the entire amount that you spent on sports betting in the earlier week. The minimal quantity is 1 while the maximum discount is 1,500 per week. Most bonus provides have strict time frames, which may vary from a generous 40-days to a good 7-day turnaround. Make certain you wager all you need to earlier than your time is up, otherwise you will not be capable of take benefit of the provide.
Assistance is offered around-the-clock, so gamers can get info in real-time about the 22bet bonus for esports in addition to the 22bet casino provides. The FAQ page is also an excellent source of knowledge, as a lot of the widespread questions are answered in detail here. Overall, the web site is intuitive and highly responsive, so technical glitches usually are not frequent and players not often want help. One of the top betting apps obtainable in the marketplace is the Dafabet mobile App, which presents a live-streaming option. As with many betting services, 22Bet additionally has an FAQ part, but when making an attempt it out, it did appear to fall quick on a quantity of basic queries, like cost methods. With the variety of options here, it could probably be forgiven barely, however having to contact customer assist simply to seek out out if a certain cost technique was accepted isnt perfect.
These sites have an enormous focus on the Indian market and can ensure you get the correct online betting experience during the IPL. When we are on the topic of betting websites in India, we cannot keep away from the topic of what is the cricket betting sites. Clearly, in our introductory list of finest betting websites weve utilized a rating. Since were looking at cricket betting websites in India first and foremost, these features weigh the best. 1XBet additionally provides very generous welcome bonuses to their new customers and run promotions for the prevailing customers which includes merchandise amongst others. Crickex is available in India and accepts Indian rupees as a type of fee which saves tons of of rupees for Indians in currency exchange. Moreover, if you ever run into problems whereas enjoying betting at this bookmaker web site, you possibly can all the time get skilled help 24/7 via the stay chat characteristic.
This appears to have been an inside drawback with 22bets payment system, which has since been fastened. [newline]22bet has a one hundred pc sign up bonuses, by which they match your first deposit as soon as it has been gambled as soon as. Depending where you reside this deal is sweet to a most of 350. There are additionally esports, horse racing, and darts, among others. Although the Apk app is spectacular, the cellular model of 22bet ticks all the best boxes as well. Typically, whenever you visit load by default.
Users should antici...
00:16
Melbet India
At this web site, it is feasible for you to to get pleasure from a easy registration course of. The on-line gambling platform has advanced quickly in the earlier few years. MelBet is one of the multi-platform websites that will offer you totally different choices.
Unfortunately, because of Google Plays coverage against using any betting apps, Melbet customers will be unable to download the app instantly from there. But the developers of Melbet have found a way out of this case. They developed the Melbet apk specifically in order that users can obtain it and install it on any of their gadgets. Melbet offers presents upon registration, consolation bonuses, tournaments for gamers, and much more. Temporary promotions are located within the part of the same name, everlasting ones are in the More section. Yes, Melbet takes the security and security of its players significantly and implements numerous measures to protect players personal and financial info.
Everyone will be succesful of select for themselves the quickest and most handy way. For example, you need to use your phone number, e-mail handle, or even social media. In any case, Melbet India registration wont take you a lot time.
The odds might be multiplied, growing the potential winnings. But to get the money, all predictions have to be played. If at least considered one of them is incorrect, you lose your wager. When making a deposit, the funds are deposited immediately. Withdrawal takes completely different instances relying on the amount and selected fee system.
You will obtain a confirmation email or SMS with a verification hyperlink or code. Follow the instructions offered to verify your account. You can watch any match you want utilizing reside streaming. And for a extra accurate prediction, you can use real-time statistics. Open the registration form and enter the code word in the Enter promo code field.
As with most bookies obtainable in India, the main focus is on cricket betting, however lovers of other sports activities mustnt worry as a outcome of theyre additionally properly catered for. Click on the withdraw button and as long as youve accomplished all wagering requirements if a bonus was claimed, you should obtain your funds inside the specified times. Choose the tactic of the Melbet withdrawal and enter the amount that you simply wish to withdraw. When this step has been accomplished, a new window will appear which displays your new username and password with the choice of getting these particulars emailed to you. Yes, together with many well-liked currencies, Indian rupees can be found in Melbet.
You get a certain cashback proportion at every of them from 5% to 11%. The money is credited to your account weekly for any bets or deposits. Registration is only available for individuals of authorized gambling age and requires personal information and a sound e-mail handle. As a new...