| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Wednesday, 21 June
02:09
100,000 Hacked ChatGPT Accounts Discovered on Dark Web HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
Most of the hacked ChatGPT accounts originated from India, Pakistan, and Brazil.
This is a post from HackRead.com Read the original post: 100,000 Hacked ChatGPT Accounts Discovered on Dark Web
02:05
Semiconductor Lasers Hit Steel-Slicing Levels IEEE Spectrum
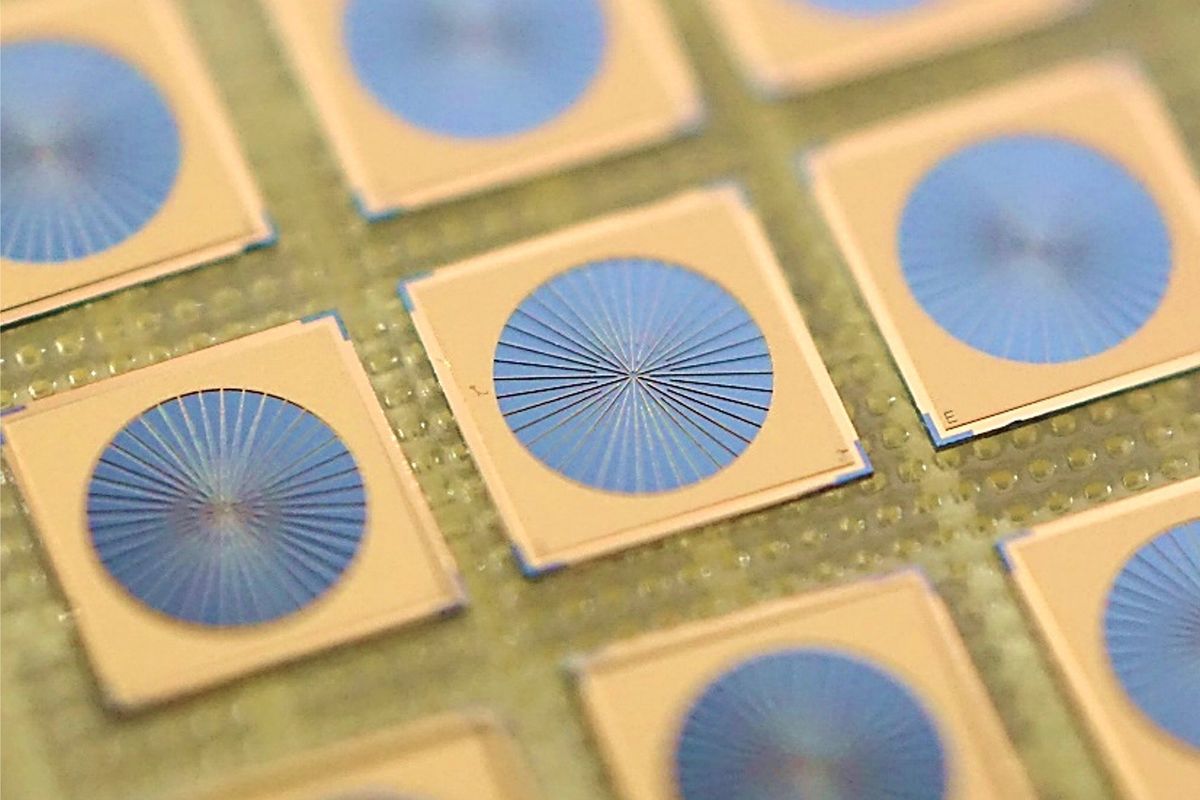
Semiconductor lasers, unlike bulky gas lasers and fiber lasers,
are tiny, energy efficient, and highly controllable. The one thing
they cant do is deliver their competitors steel-slicing
brightness.
In results reported last week in Nature, a group of researchers at Kyoto University, led by IEEE Fellow Susumu Noda, has taken a big step in overcoming the limitations of semiconductor laser brightness by changing the structure of photonic-crystal surface-emitting lasers (PCSELs). A photonic crystal is composed of a semiconductor sheet punched through with regular, nanometer-scale air-filled holes. Photonic crystal lasers are attractive candidates for high-brightness lasers, but until now engineers havent been able to scale them up to deliver beams bright enough for practical metal cutting and processing.
(Brightness is a figure of merit that encompasses a lasers output power and beam quality and encapsulates how well a beam of light can be focused or how little it diverges. The threshold for metal work is about 1 gigawatt per square centimeter per steradian.)
Slicing Stainless Steel With a PCSEL youtu.be
Nodas group, which has been working on PCSELs for more than two decades, was able to develop a laser with a diameter of 3 millimeters, a 10-fold areal jump up from previous 1-millimeter-diameter PCSEL devices. The new laser has a power output of 50 watts, a similar increase from the 5 to 10 W power output of the 1 mm PCSELs. The new lasers brightness, about 1 GW/cm2/str, is now high enough for applications currently dominated by bulky gas l...
02:00
Next DLP Scoped Investigations separates employee identity from their behavioral data Help Net Security
Next DLP announced a new Scoped Investigations capability in the Reveal platform that protects privacy by time bounding and restricting access to employee activity to only investigators with an approved and legitimate need to access it. A complementary pseudonymization feature redacts personally identifiable information (PII) so that security professionals can investigate potential incidents without seeing employee details. This prevents bias and protects employee privacy while permitting security professionals to get their jobs done. Organizations now More
The post Next DLP Scoped Investigations separates employee identity from their behavioral data appeared first on Help Net Security.
01:46
EV Chargers for All! IEEE Spectrum

When IEEE Spectrums Editor in Chief Harry Goldstein needed to replace his 2008 Honda Fit in October 2020, he thought seriously about buying an electric vehicle. Two obstacles stood in his way. One was affordability. Even without a son soon to be entering college, the premium prices of EVs were a turn-off.
The other challenge was where to charge the EV. Harrys 200-unit condominium building in Minneapolis, Minnesota does not have any EV chargers in its 5-story indoor parking garage. There were two Level 2 charging stations about six-blocks away in a grocery store parking lot, but that was not a convenient or reliable option.
Harry decided to forego buying an EV but remains open to purchasing one if both the affordability and charging issues are better addressed.
I asked about installing charging stations in our garage and was invited to bring the issue up before the HOA (homeowners association) board, where all good ideas go to die, he said. They rejected my request to allow cyclists to hose off their bikes in the alley behind the building, which cost nothing. Considering the costs associated with installation and maintenance and anticipating the resistance Im likely to encounter, I decided to put my charger crusade on hold.
Harry is not alone in his EV hesitationit is widely shared by other condo owners and, even more importantly in terms of sheer numbers, renters. Consumer surveys from J.D. Power, for instance, indicate that while 27% of potential car shoppers are very likely to consider an EV as their next purchase, only 17% of renters indicate the same level of interest.
The transition to EVs in the U.S. will hit a deep pothole unless the more than one-third of the 124 million households that rent can be convinced to purchase an EV.
And if they make an EV purchase, they often regret it. For instance, the Minneapolis Star-Tribune...
01:30
Punched Cards Are In The Cloud, With This Arduino Hackaday

Grizzled veterans of the computing industry will relate stories of submitting projects on stacks of punched cards, something those of us who stored their 8-bit works on audio cassettes could only imagine. But for those who fancy experimenting with the format its still possible to make a basic card reader using LEDs and light sensors, as [Nino Ivanov] has done using an Arduino Uno as the brains. And these arent just for show, each of his cards holds a LISP program that runs in a cloud service.
The Uno does the job of reading, passing its data over its USB serial port to a tablet. On the tablet the serial data is piped to a cloud API to a LISP interpreter. It seems a needlessly complex way to run a factorial program and its certainly a little over the top, but on the other hand we love it as a glorious combination of the old and the new. With only 23 characters per card its quite an impressive feat to even fit a program on the format, perhaps writing code to fit on minimalist punched cards like this could become a programming challenge in its own right for a generation accustomed to mega-and gigabytes.
If you fancy a go yourself, this isnt the first punched card reader weve shown you...
01:30
CYE Hyver enhancements empower organizations with real-time risk analysis module Help Net Security
CYE announced a new capability in its Hyver platform that calculates dynamic risk in real-time. Hyver sets a new standard for the industry that will allow CISOs to take mitigation plans to the next level by optimizing real-time data to make both short-term and long-term decisions. Ultimately, Hyver helps CISOs make faster, more informed decisions, while they deal with budget concerns and strategic or tactical organizational decisions regarding security investments. Many companies today build their More
The post CYE Hyver enhancements empower organizations with real-time risk analysis module appeared first on Help Net Security.
01:00
Cymulate Exposure Analytics provides users with an attackers view of their cyber resilience Help Net Security
Cymulate released a new solution for organizations to run an informed continuous threat exposure management (CTEM) program. The CTEM program, which was coined by Gartner is designed to diagnose the severity of exposures, create an action plan for remediation and facilitate a common language for discussions between business and technical teams. Disparate data sources, point-in-time collection, and lack of business context create challenges for cybersecurity teams to ingest and contextualize exposure data and translate it More
The post Cymulate Exposure Analytics provides users with an attackers view of their cyber resilience appeared first on Help Net Security.
00:57
Bob Kahn on the Birth of Inter-networking IEEE Spectrum

IEEE Spectrum recently published a profile of Vint Cerf, who together with Bob Kahn developed what later became known as TCP/IP, the suite of protocols that power the Internet. That article didnt detail the events leading up to their influential technical collaboration, though. So IEEE Spectrum talked with Kahn to learn this part of the story and his conception of open-architecture networking.
Maybe we could start at the beginning of your professional career after you got your Ph.D. You started at BBN [Bolt, Beranek, and Newman], right?
Bob Kahn: I got my Ph.D. from Princeton in 1964 and took a job as an assistant professor at MIT in the electrical engineering department. I was there for a few years. In late 1966, I took a leave of absence (which I thought would be only for a year or two) to get some practical experience. I went to BBN. I started working on networking and ended up not going back to academia.
1966 was at the start of the conception of the ARPANET [the Advanced Research Projects Agency Network], was it not?
Kahn: Close. When I started working on computer networking, I had heard of ARPA, but I had never worked with them. I didnt know what they did. And I didnt even know that they were interested in networking at the time. As far as I was concerned, computer networking was just an idea that I thought was really interesting, especially the communication-network aspects. But there had been other people who had been interested in computer networking well before that.
There was a series of reports that Paul Baran wrote at the Rand Corporation on distributed communications. He was proposing that there be some kind of a network based on the use of discrete addressed message blocks, as he called themthe term packet hadnt been introduced yet.
At around the same time, Len (Leonard) Kleinrock was doing theoretical work on que...
00:31
Virgin Galactic to start regular commercial flights to space in August Lifeboat News: The Blog
After that, those who have been waiting more than a decade for their ride aboard Virgin Galactics rocket-powered space plane are expected to get their chance. The company said the first of those flights will begin in early August, with monthly flights following that.
This next exciting chapter for Virgin Galactic has been driven by innovation, determination and a commitment to delivering an unparalleled and truly transformative customer experience, CEO Michael Colglazier said in a statement.
Virgin Galactic has been working for years to send paying passengers on short space trips and in 2021 finally won the federal governments approval. The company completed its final test fight in May.
00:30
NASA Will Make SpaceX Starship into Space Stations Lifeboat News: The Blog
NASA will partner with SpaceX to make Starship space stations. This is part of NASA partnering with seven U.S. companies to make advanced space capabilities. SpaceX is collaborating with NASA on an integrated low Earth orbit architecture to provide a growing portfolio of technology with near-term Dragon evolution and concurrent Starship development. This architecture includes Starship as a transportation and in-space low-Earth orbit destination element supported by Super Heavy, Dragon, and Starlink, and constituent capabilities including crew and cargo transportation, communications, and operational and ground support.
Making Giant Space Stations Using SpaceX Starships
Each Starship has more than the volume of the International Space Station. They are also similar in size to the external fuel tank of the old Space Shuttle. There were many space station proposals based upon the external fuel tank of the Space Station. It will be easier to build with SpaceX Starships. The steel construction the SpaceX Starship makes them easy to weld, cut and modify. The SpaceX Starships will start being able to support astronauts.
00:30
Orange Business, Orange Cyberdefense and Palo Alto Networks improve security for enterprises Help Net Security
Orange Business, Orange Cyberdefense and Palo Alto Networks have joined forces to deliver a managed Secure Access Service Edge (SASE) solution that meets enterprise customers most demanding networking and security requirements with high performance, simplicity, and Zero Trust Network Access 2.0. The shift to working from anywhere, software-defined networking, and the rapid adoption of cloud connectivity is enabling global enterprises to drive new levels of productivity and efficiency. However, as they redesign their distributed network More
The post Orange Business, Orange Cyberdefense and Palo Alto Networks improve security for enterprises appeared first on Help Net Security.
00:29
Lofi Generator Lifeboat News: The Blog
 This week my guest Anne Scherer, a professor of
marketing at the University of Zurich who specializes in the
psychological and societal impacts that result from the increased
automation and digitization of the consumer-company
relationship.
This week my guest Anne Scherer, a professor of
marketing at the University of Zurich who specializes in the
psychological and societal impacts that result from the increased
automation and digitization of the consumer-company
relationship.
In this episode we focus on the details Anne covers in, You and AI, a book she co-authored with Cindry Candrian to bring an accessible understanding of the ways in which AI is shaping our lives. This takes on a tour of topics such as our symbiotic relationship with AI, manipulation, regulation, the proposed 6 month pause on AI development, the business advantages of better data policies around AI, the difference between artificial intelligence and human intelligence, and more.
Find out more about Anne and her book at annescherer.me.
Host: Steven Parton LinkedIn / Twitter
Music by: Amine el Filali.
Subscribe: http://bit.ly/1Wq6gwm.
00:28
Photos: Infosecurity Europe 2023 Help Net Security
Infosecurity Europe is taking place at ExCeL London from 20-22 June 2023 and Help Net Security is on site. Heres a closer look at the conference featuring: Island, Crowdstrike, Panorays, ManageEngine, Mazebolt, Cobalt, Intruder, TikTok, and CensorNet.
The post Photos: Infosecurity Europe 2023 appeared first on Help Net Security.
00:08
Zyxel addressed critical flaw CVE-2023-27992 in NAS Devices Security Affairs
Zyxel released security updates to address a critical vulnerability affecting its network-attached storage (NAS) devices.
Zyxel released security updates to address a critical security flaw, tracked as CVE-2023-27992 (CVSS score: 9.8), affecting its network-attached storage (NAS) devices.
The vulnerability is a pre-authentication command injection issue that impacts the Zyxel NAS326 firmware versions prior to V5.21(AAZF.14)C0, NAS540 firmware versions prior to V5.21(AATB.11)C0, and NAS542 firmware versions prior to V5.21(ABAG.11)C0. A remote, unauthenticated attacker can exploit the vulnerability to execute some operating system (OS) commands by sending a specially crafted HTTP request.
Zyxel has released patches addressing a pre-authentication command injection vulnerability in some NAS versions. reads the advisory published by Zyxel. The pre-authentication command injection vulnerability in some Zyxel NAS devices could allow an unauthenticated attacker to execute some operating system (OS) commands remotely by sending a crafted HTTP request,
The vulnerability was reported by Andrej Zaujec, NCSC-FI, and Maxim Suslov.
In early June, Zyxel published guidance for protecting firewall and VPN devices from the ongoing attacks and exploiting CVE-2023-28771, CVE-2023-33009, and CVE-2023-33010 vulnerabilities.
Threat actors are actively attempting to exploit the command injection vulnerability CVE-2023-28771 impacting Zyxel firewalls. Their objective is to leverage this vulnerability to deploy and install malware on the affected systems. US CISA added...
00:00
Abundant Phosphorus in Enceladus Ocean Increases Habitability: But is Enceladus Inhabited? Centauri Dreams Imagining and Planning Interstellar Exploration
Finding the right conditions for life off the Earth justifiably drives many a researchers work, but nailing down just what might make the environment beneath an icy moons surface benign isnt easy. The recent wave of speculation about Enceladus revolves around the discovery of phosphorus, a key ingredient for the kind of life we are familiar with. But Alex Tolley speculates in the essay below that we really dont have a handle on what this discovery means. Theres a long way between habitable and inhabited, and many data points remain to be analyzed, most of which we have yet to collect. Can we gain the knowledge we need from a future Enceladus plume mission?
by Alex Tolley
There has been abundant speculation about the possibility of life in the subsurface oceans of icy moons. Europas oceans with possible hydrothermal vents mimicking Earths abyssal oceans and the probable site of the origin of life, caught our attention now that Mars has no extant surface life. Arthur C Clarke had long suggested Europa as an inhabited moon in his novel 2010: Odyssey Two. (1982). While Europas hot vents are still speculative based on interpretations of the surface features of its icy crust, Saturns moon, Enceladus, showed visible aqueous plumes at the southern pole. These plumes ejected material that contributes to the E-Ring around Saturn as shown below.

While most searches for evidence for life focus on organic material, it has been noted that of the necessary elements for terrestrial life, Carbon, Hydrogen, Oxygen, Nitrogen, Sulfur, and Phosphorus (CHONSP), phosphorus is the least abundant cosmically. Phosphorus is a key component in terrestrial life, from energy management (ATP-ADP cycle) and information molecules DNA, and RNA, with their phosphorylated sugar backbones.
If phosphorus is absent, terrestrial biology cannot exist. Phosphorus is often the limiting factor for biomass on Earth, In freshwater environments phosphorus is the limiting nutrient [1]. Typically, algae require about 10x as much nitrogen as phosphorus. If the amount of available nitrogen is increased, th...
00:00
Cottonization: Making Hemp and Flax Fibers Into The Better Cotton Hackaday

These days its hard to imagine that fabrics were ever made out of anything other than cotton or synthetic fibers, yet it wasnt too long ago that hemp and flax-based fabrics linen were the rule rather than the exception. Cotton production has for centuries had the major disadvantages of requiring a lot of water and pesticides, and harvesting the cotton was very labor-intensive, making cotton rather expensive. In order to make separating the cotton fibers from the seed easier, improved versions of the cotton gin (cotton engine) were developed, with the 19th centurys industrial revolution enabling a fully automated version.
What makes cotton attractive is the ease of processing these fibers, which are part of the seed pod. These fibers are 25 mm 60 mm long, 12 m 45 m fine fibers that can be pulled off the seeds and spun into yarn or whatever else is needed for the final product, much like wool. Hemp and flax fibers, in contrast, are extracted from the plant stem in the form of bast fibers. Rather being pure cellulose, these fibers are mostly a mixture of cellulose, lignin, hemicellulose and pectin, which provide the plant with rigid...
00:00
ExaGrid Version 6.3 guards customers against external threats Help Net Security
ExaGrid released software Version 6.3, which started shipping in June 2023. With each software update in Version 6, ExaGrid has been adding additional layers of security to its Tiered Backup Storage, which already guards against external threats by utilizing a non-network-facing repository tier (tiered air gap) with delayed deletes and immutable data objects where backup data is stored for longer-term retention that cannot be accessed by threat actors and cannot be modified by malicious attacks. More
The post ExaGrid Version 6.3 guards customers against external threats appeared first on Help Net Security.
Tuesday, 20 June
23:30
Black Kite releases two modeling solutions for ransomware and business interruption scenarios Help Net Security
Black Kite released automated cyber risk quantification (CRQ) modeling for ransomware and business interruption scenarios. The new capabilities, which automates FAIR methodology, extends Black Kites data breach CRQ model to now provide visibility into all third-party risk scenarios, adds environmental, social, and corporate governance (ESG) factors and makes it possible to continuously monitor supply chain risk. Cyber risk quantification provides deeper and more useful insights than a mere security score or rating. Yet, getting it More
The post Black Kite releases two modeling solutions for ransomware and business interruption scenarios appeared first on Help Net Security.
23:22
Linux 6.5 Slated To Add Provisioning Primitives For Thinly Provisioned Storage Phoronix
Another feature scheduled to be sent in for the upcoming Linux 6.5 kernel merge window is introducing support for provisioning primitives for thinly provisioned storage with the Device Mapper (DM) code...
23:08
The Rust Leadership Council LWN.net
The Rust project has announced the formation of the Rust Leadership Council, which will take the place of the existing Core Team and Leadership Chat groups.
The Council will assume responsibility for top-level governance concerns while most of the responsibilities of the Rust Project (such as maintenance of the compiler and core tooling, evolution of the language and standard libraries, administration of infrastructure, etc.) remain with the nine top level teams.
The details on how this body is supposed to work can be found in RFC 3392.
23:00
Edgescan EASM allows organizations to secure their critical assets and applications Help Net Security
Edgescan released its new External Attack Surface Management solution, offering visibility and continuous monitoring to help secure organizations of all sizes. Todays enterprises require a cloud-savvy security solution that effectively inventories, monitors, manages and protects their corporate assets across their digital footprint. Traditional ad hock approaches and laborious, manual processes, combined with legacy tools make the process complex, expensive, and false positive prone due to human error. An essential way to gain complete visibility and More
The post Edgescan EASM allows organizations to secure their critical assets and applications appeared first on Help Net Security.
22:59
Today's AI is Artificial Artificial Artificial Intelligence SoylentNews
AI is going to eat itself: Experiment shows people training bots are using bots
Workers hired via crowdsource services like Amazon Mechanical Turk are using large language models to complete their tasks which could have negative knock-on effects on AI models in the future.
Data is critical to AI. Developers need clean, high-quality datasets to build machine learning systems that are accurate and reliable. Compiling valuable, top-notch data, however, can be tedious. Companies often turn to third party platforms such as Amazon Mechanical Turk to instruct pools of cheap workers to perform repetitive tasks such as labeling objects, describing situations, transcribing passages, and annotating text.
Their output can be cleaned up and fed into a model to train it to reproduce that work on a much larger, automated scale.
AI models are thus built on the backs of human labor: people toiling away, providing mountains of training examples for AI systems that corporations can use to make billions of dollars.
But an experiment conducted by researchers at the cole polytechnique fdrale de Lausanne (EPFL) in Switzerland has concluded that these crowdsourced workers are using AI systems such as OpenAI's chatbot ChatGPT to perform odd jobs online.
Training a model on its own output is not recommended. We could see AI models being trained on data generated not by people, but by other AI models perhaps even the same models. That could lead to disastrous output quality, more bias, and other unwanted effects.
Read more of this story at SoylentNews.
22:56
Security updates for Tuesday LWN.net
Security updates have been issued by Debian (libxpm and php7.3), Fedora (chromium), Mageia (kernel, kernel-linus, and sysstat), Red Hat (c-ares), SUSE (libwebp), and Ubuntu (cups-filters, libjettison-java, and libsvgpp-dev).
22:31
PX11: The Land Unknown Random Thoughts
The Land Unknown by Gary Panter (170x261mm)
This book was published (in France, but in English) in 2011, and Ive somehow never seen a copy before. I happened onto this one in the 50 Watts Books store, but I see that its still available from the publisher here, and for just 15. So its (still, 12 years later) generally available, and Im rather puzzled that I didnt happen onto a copy back when I was doing the Punk Comix blog series.
So lets take a look at the book.
Its about 120 pages long, and is on matte stock, and is mostly printed in colour....
22:25
Creating Lithography-Free Photonic Reprogrammable Circuits Lifeboat News: The Blog
The field of photonics has seen significant advances during the past decades, to the point where it is now an integral part of high-speed, international communications. For general processing photonics is currently less common, but is the subject of significant research. Unlike most photonic circuits which are formed using patterns etched into semiconductor mask using lithography, purely light-based circuits are a tantalizing possibility. This is the focus of a recent paper (press release, ResearchGate) in Nature Photonics by [Tianwei Wu] and colleagues at the University of Pennsylvania.
What is somewhat puzzling is that despite the lofty claims of this being the first time that such an FPGA-like device has been created for photonics, this is far from the case, as evidenced by e.g. a 2017 paper by [Kaichen Dong] and colleagues (full article PDF) in Advanced Materials. Here the researchers used a slab of vanadium dioxide (VO2) with a laser to heat sections to above 68 C where the material transitions from an insulating to a metallic phase and remains that way until the temperature is lowered again. The m-sized features that can be created in this manner allow for a wide range of photonic devices to be created.
What does appear to be different with the photonic system presented by [Wu] et al. is that it uses a more traditional 2D approach, with a slab of InGaAsP on which the laser pattern is projected. Whether it is more versatile than other approaches remains to be seen, with the use of fully photonic processors in our computers still a long while off, never mind photonics-accelerated machine learning applications.
22:24
See the bolt of lightning on Jupiter that caused an eerie green glow Lifeboat News: The Blog
Spacecraft Juno has been orbiting Jupiter for years sending back images. NASA shares the images online. Take a look at what one person discover on an image.
22:24
Metallic bond between two beryllium atoms made for the first time Lifeboat News: The Blog
A quartet of chemists at the University of Oxford has, for the first time, found a way to get two beryllium atoms to bond with one another. In their paper published in the journal Science, Josef Boronski, Agamemnon Crumpton, Lewis Wales and Simon Aldridge, describe their process and how they managed to do it in a safe wayand at room temperature. Jason Dutton with La Trobe University, has published a Perspective piece in the same journal issue, outlining the work done by the team in England.
Beryllium is a strong but lightweight, alkaline earth metal. It is also brittle.
Beryllium only ever occurs naturally when mixed with other elements, forming minerals. It is often found in gemstones such as emeralds. And it is used in a variety of applications, from telecommunications equipment to computers and cell phones. It is also mixed with other metals to create alloys used in applications such as gyroscopes and electrical contacts.
22:24
BepiColombo spacecraft makes its third Mercury flyby today Lifeboat News: The Blog
The European Space Agency (ESA) launched the BepiColombo mission in 2018, and it is set to enter orbit around Mercury in 2025. In the meantime, it will be making several flybys of the planet, including a close approach today. Thats because the spacecrafts route takes it on a series of increasingly close flybys that use the planets gravity to adjust its course each time.
In total, between its launch in 2020 and its arrival in Mercury orbit in 2025, the spacecraft will make one flyby of Earth, two of Venus, and six of Mercury. The Earth and Venus flybys are already complete, and today BepiColombo is making its third Mercury flyby, coming within 150 miles of the planets surface.
The maneuver will help to slow the spacecraft down so that it can eventually enter orbit. As BepiColombo starts feeling Mercurys gravitational pull, it will be traveling at 3.6 kilometers per second [2.2 miles per second] with respect to the planet. Thats just over half the speed it approached with during the previous two Mercury flybys, explained ESA flight dynamics expert Frank Budnik in a statement. And this is exactly what the point of such events is. Our spacecraft began with far too much energy because it launched from Earth and, like our planet, is orbiting the sun. To be captured by Mercury, we need to slow down, and were using the gravity of Earth, Venus and Mercury to do just that.
22:24
Amazon.com: Exponential Organizations 2.0: The New Playbook for 10x Growth and Impact eBook : Ismail, Salim, Diamandis, Peter H., Malone, Michael S., Kurzweil, Ray : Kindle Store Lifeboat News: The Blog
Exponential Organizations 2.0: The New Playbook for 10x Growth and Impact Kindle edition by Ismail, Salim, Diamandis, Peter H., Malone, Michael S., Kurzweil, Ray. Download it once and read it on your Kindle device, PC, phones or tablets. Use features like bookmarks, note taking and highlighting while reading Exponential Organizations 2.0: The New Playbook for 10x Growth and Impact.
22:23
Machine learning helps researchers identify hit songs with 97% accuracy Lifeboat News: The Blog
Every day, tens of thousands of songs are released. This constant stream of options makes it difficult for streaming services and radio stations to choose which songs to add to playlists. To find the ones that will resonate with a large audience, these services have used human listeners and artificial intelligence. This approach, however, lingering at a 50% accuracy rate, does not reliably predict if songs will become hits.
Now, researchers in the US have used a comprehensive machine learning technique applied to brain responses and were able to predict hit songs with 97% accuracy.
By applying machine learning to neurophysiologic data, we could almost perfectly identify hit songs, said Paul Zak, a professor at Claremont Graduate University and senior author of the study published in Frontiers in Artificial Intelligence. That the neural activity of 33 people can predict if millions of others listened to new songs is quite amazing. Nothing close to this accuracy has ever been shown before.
22:22
CERN plans to collaborate with projects for future gravitational-wave observatories Lifeboat News: The Blog
Gravitational waves, like the discovery of the Higgs boson in 2012, have made their mark on a decade of extraordinary discoveries in physics. Unlike gravity, which is created when massive objects leave their mark in the fabric of spacetime, gravitational waves are very weak ripples in spacetime that are caused by gravity-accelerated masses.
So far, researchers have been able to detect the gravitational waves produced by the melting together of very heavy objects, such as black holes or neutron stars. When this happens, these echoes from the past reverberate through the whole universe and finally reach Earth, allowing us to piece together what happened millions of light-years ago.
Current gravitational-wave observatories can only detect a few gravitational waves as they cover just a narrow spectrum of the whole range of wavelengths that are emitted. Future gravitational-wave observatories, such as the Einstein Telescope, a CERN-recognized experiment, need to be larger in order to search for a larger bandwidth of gravitational waves that could tell us more about the universe.
22:22
The Reddit Files: Hackers Demand $4.5M Ransom and API Access Waiver HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
The hackers from the infamous BlackCat ransomware gang (also known as ALPHV) have claimed to have stolen 80GB of data from Reddit.
This is a post from HackRead.com Read the original post: The Reddit Files: Hackers Demand $4.5M Ransom and API Access Waiver
22:12
Zyxel Releases Urgent Security Updates for Critical Vulnerability in NAS Devices The Hacker News
Zyxel has rolled out security updates to address a critical security flaw in its network-attached storage (NAS) devices that could result in the execution of arbitrary commands on affected systems. Tracked as CVE-2023-27992 (CVSS score: 9.8), the issue has been described as a pre-authentication command injection vulnerability. "The pre-authentication command injection vulnerability in some Zyxel
22:03
Linux 6.5 Adding Qualcomm Adreno 690 Open-Source GPU Support Phoronix
The upcoming Linux 6.5 kernel is poised to add support for Qualcomm's Adreno 690 GPU to the open-source MSM kernel graphics/display driver. The A690 is notably used by the Snapdragon 8cx Gen 3 (SC8280XP) platform that in turn is what's found inside the Lenovo ThinkPad X13s laptop and other hardware...
21:58
Code of Conduct: Still Falsely Advertised by Online Bullies and Serial Defamers Who Rely on Corporate Enforcers for Gate-keeping Techrights
Summary: Online bullying in social control media and even in IRC (our network has been trolled a lot lately) is a serious issue; to make matters worse, the CoC system has been weaponised by trolls to silence and intimidate critics of unethical corporations (habitually employing those trolls on 6-digit if not 7-figure salaries)
MORE than 3 years ago we cautioned that the Linux Foundation's Linux Kernel Code of Conduct (CoC) Committee had become "Officially Corporate". Its all about one thing: censorship. Who for? Check the members of the Code of Conduct (CoC) Committee. Theyre the cops, not to mention the judge, the witness, and the jury (the phrase is often judge, jury, executioner; but theyre also the cops/vigilante on the scene). Theyd also process the appeals if any are registered. This is lynching, not a system of justice, and salaries peripheral to the role govern who is punished and what for. Those committees arent full-time jobs. Theyre for corporate lynch mobs to crucify communities.
What the Linux Foundation does with CoCs is still relevant, albeit buried under Easter holidays (because its embarrassing; people file complaints for insulting companies)If the so-called Linux Foundation wants not to be seen as a "Microsoft proxy" anymore, then the answer is simple: just quit being a Microsoft proxy like the Open Source Initiative (OSI) still is. It should be noted that the OSI never quit being a Microsoft proxy. More time passes and the OSI falls deeper and deeper into Microsofts hands, just like the Linux Foundation. Friend brings a friend, mole brings another mole. Shooting the messenger tactics wont help when the message is factual and clearly demonstrable, based on hard evidence; for instance, beware trolls saying/insinuating/alleging that someone is sexist and pro-rape (or choosing moles who are female so that critics...
21:57
SaaS in the Real World: How Global Food Chains Can Secure Their Digital Dish The Hacker News
The Quick Serve Restaurant (QSR) industry is built on consistency and shared resources. National chains like McDonald's and regional ones like Cracker Barrel grow faster by reusing the same business model, decor, and menu, with little change from one location to the next. QSR technology stacks mirror the consistency of the front end of each store. Despite each franchise being independently
21:55
Experts Uncover Year-Long Cyber Attack on IT Firm Utilizing Custom Malware RDStealer The Hacker News
A highly targeted cyber attack against an East Asian IT company involved the deployment of a custom malware written in Golang called RDStealer. "The operation was active for more than a year with the end goal of compromising credentials and data exfiltration," Bitdefender security researcher Victor Vrabie said in a technical report shared with The Hacker News. Evidence gathered by the Romanian
21:20
Silobreaker unveils new geopolitical threat intelligence capabilities With RANE Help Net Security
Silobreaker announced that it will be showcasing its enhanced geopolitical threat intelligence capabilities with RANE (Risk Assistance Network + Exchange) at Infosecurity Europe 2023. The tie-up will see Silobreaker integrate global risk intelligence company RANEs Enterprise Geopolitical Intelligence into its own threat intelligence platform, providing cyber threat intelligence (CTI) teams with real-time information about world events that could heighten the risk of cyberattacks. With the addition of RANEs geopolitical threat intelligence, analysis and forecasting capabilities, More
The post Silobreaker unveils new geopolitical threat intelligence capabilities With RANE appeared first on Help Net Security.
21:17
Supply Chain Attack: Abandoned S3 Buckets Used for Malicious Payloads HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
Threat actors have been taking over abandoned S3 buckets to launch malicious binaries, steal login credentials and more.
This is a post from HackRead.com Read the original post: Supply Chain Attack: Abandoned S3 Buckets Used for Malicious Payloads
21:15
Netskope Intelligent SSE helps enterprises securely manage employee use of generative AI apps Help Net Security
Netskope has released a comprehensive data protection solution to help enterprises securely manage employee use of ChatGPT and other generative AI applications, such as Google Bard and Jasper. As part of its Intelligent Security Service Edge (SSE) platform, Netskope enables safe usage of generative AI thanks to patented data protection techniques. Following incidents in 2023 of sensitive data exposure from generative AI, many enterprises are now prioritising if and how to safely enable the use More
The post Netskope Intelligent SSE helps enterprises securely manage employee use of generative AI apps appeared first on Help Net Security.
21:06
Read "Pharmacological and non-pharmacological countermeasures to Space Motion Sickness: a systematic review" coauthored by our Barry L. Bentley along with researchers at NASA and ISRO. Lifeboat News
Read "Pharmacological and non-pharmacological countermeasures to Space Motion Sickness: a systematic review" coauthored by our Barry L. Bentley along with researchers at NASA and ISRO.
21:00
Cosmic Ray Navigation Hackaday

GPS is a handy modern gadget until you go inside, underground, or underwater. Japanese researchers want to build a GPS-like system with a twist. It uses cosmic ray muons, which can easily penetrate buildings to create high-precision navigation systems. You can read about it in their recent paper. The technology goes by MUWNS or wireless muometric navigation system quite a mouthful.
With GPS, satellites with well-known positions beam a signal that allows location determination. However, those signals are relatively weak radio waves. In this new technique, the reference points are also placed in well-understood positions, but instead of sending a signal, they detect cosmic rays and relay information about what it detects to receivers.
The receivers also pick up cosmic rays, and by determining the differences in detection, very precise navigation is possible. Like GPS, you need a well-synchronized clock and a way for the reference receivers to communicate with the receiver.
Muons penetrate deeper than other particles because of their greater mass. Cosmic rays form secondary muons in the atmosphere. About 10,000 muons reach every square meter of our planet at any minute. In reality, the cosmic ray impacts atoms in the atmosphere and creates pions which decay rapidly into muons. The muon lifetime is short, but time dilation means that a short life traveling at 99% of the speed of light seems much longer on Earth and this allows them to reach deep un...
20:58
Citizen Lab on Jamal Khashoggi widow suing spyware firm NSO Group: CBC Radio- As It Happens with Nil Kksal, Chris Howden News The Citizen Lab
In an interview with As It Happens with Nil Kksal, Chris Howden on CBC Radio, Citizen Lab Director Ron Deibert discussed Jamal Khashoggis widow Hanan Elatars lawsuit against Israeli spyware company NSO. Hanan Elatr Khashoggi claimed in a civil lawsuit lodged with the Northern District of Virginia that NSO intentionally targeted her devices and caused her immense harm, both through the tragic loss of her husband and through her own loss of safety, privacy, and autonomy.
Ron explains how Citizen Lab learned that Hanans device had spyware installed on it: Someone typed in a website that was used to install Pegasus when her phone was not in her possession when Hanan was interrogated at the Dubai airport and the phone communicated several times with a server that is part of the NSO infrastructure, he said. When trusted devices become an enemy, Ron notes that it has a psychological and emotional toll on victims and some of the victims carry a huge amount of emotional guilt, illuminating the psychological cost of spyware.
Speaking about how the US executive order has altered cybersecurity and what needs to be done more, he says, Executive order is a big deal and prohibits US federal agencies from purchasing spyware that presents a national security risk or is involved in human rights abuses. Countries like Canada and others should follow suit.
20:49
Tackling Data Sovereignty with DDR Security Affairs
Data-centric distributed resilience (DDR) offers a compelling approach to addressing data sovereignty in cybersecurity.
As much of our modern life relies upon the cloud, the question of data protection is front of mind for many organizations. Those who fail to take a proactive approach to secure their data often learn the hard way how vulnerable and valuable that data can be.
Data sovereignty plays a crucial role in a robust security strategy. Organizations must hope for the best yet plan for the worst, keeping their data, end users, and company safe from intruders as cybersecurity threats are on the rise.
Understanding Data Sovereignty
Data sovereignty has emerged as a critical concern for businesses worldwide in todays interconnected digital landscape. When data is sovereign, an organization retains control and ownership over that data. Data sovereignty also encompasses the rights and regulations governing data storage, processing, and transfer and often intersects with privacy, security, and legal considerations.
Various data sovereignty challenges arise for many businesses, such as cross-border data transfers, compliance with differing data protection laws, and protecting sensitive information from unauthorized access. These challenges are intensified in industries that handle large volumes of sensitive data under stringent regulations, such as financial services, healthcare, and government sectors.
Understanding the nuances of data sovereignty is crucial for organizations to effectively address cybersecurity concerns, protect sensitive information, and ensure compliance with relevant regulations. By recognizing the significance of data sovereignty, businesses can take measures to enhance data security and control, mitigating these risks.
About DDR (Data-centric Distributed Resilience)
Data-centric distributed resilience (DDR) offers a compelling approach to addressing data sovereignty in cybersecurity. At its core, DDR emphasizes the protection and control of data itself, regardless of its physical location or the infrastructure supporting it.
Unlike traditional approaches that focus solely on securing the perimeter, DDR places data at the center of the security strategy. It employs encryption, tokenization, and data masking to ensure that sensitive information remains protected throughout its lifecycle, both in transit and...
20:42
XFS Large Extent Counts Feature No Longer Considered Experimental Phoronix
As another feature on the way for the upcoming Linux 6.5 kernel cycle is the large extent counts feature of the XFS file-system no longer being treated as "experimental" but is now considered safe to deploy...
20:14
Linux 6.5 Preps For IBM POWER's "DEXCR" Phoronix
Patches being queued ahead of the upcoming Linux 6.5 kernel merge window prepare initial support for DEXCR that is found in recent Power ISA specifications...
20:00
Libreboot To Provide New Firmware ROMs With CPU Microcode Removed Phoronix
CPU microcode updates are commonly done in the name of security fixes and resolving functionality issues.. In recent years, CPU microcode updates have been a much more common -- and important -- occurrence. While all modern CPUs rely on microcode it's just a minority" of users are unhappy with CPU microcode being included in Libreboot ROMs. Thus moving forward there will be alternative builds of Libreboot for different motherboards with the CPU microcode stripped out in the name of software freedom...
19:24
[Meme] Media Going Down the Drain Techrights
Front page story a few moments ago:
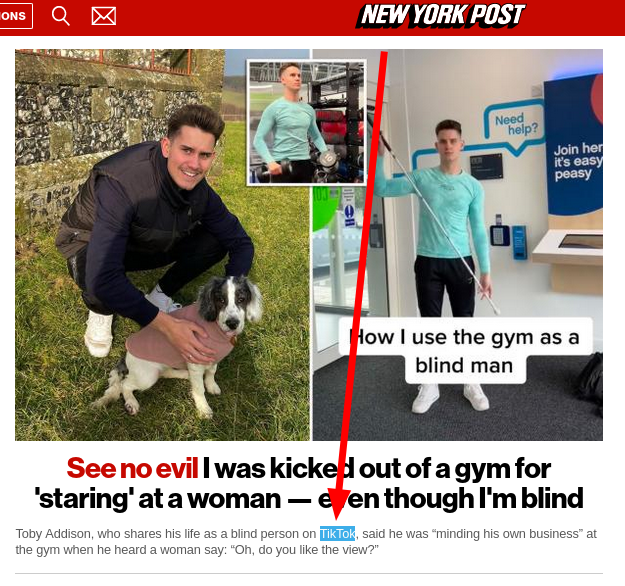
Summary: Rupert Murdochs media empire keeps promoting TikTok trash [1, 2] every single day this year (New York Post does about 2 stories based on TikTok per day sometimes a lot more and the above is a new example); we need to get people focused on information, not gossip and tabloid trash; society is paralysed when people reject journalism, stuck in outage cycles that are manufactured by the rich (averting class issues while billionaires pander to woke/non-woke, i.e. culture wars and mutually-harmful infighting)
18:56
Linux Foundation Increases Number of Microsoft Employees in the Board of Directors to THREE, the Only Geek in the Board Has Left (or Got Removed) Techrights
This shown-below page like their Web site in general also stopped being a Web page; its a JavaScript app now, instead (they dont care about accessibility or disabled people, but they say DEI a lot):
Summary: The Linux Foundation is gradually becoming a shadow of Microsoft, just like the Open Source Initiative, where most of the money comes from Microsoft and the official blog promotes Microsoft, its proprietary software, and Microsofts side in a class action lawsuit over GPL violations (with 9 billion dollars in damages at stake). So it all started with one Board member after the Microsoft loves Linux PR charade (money passed to Jim Zemlin, who gives talks at Microsoft and is married to Microsoft*); then it became two (more money paid for the second seat; the Linux Foundation openly advertises that Board seats are up for sale with upper bound of 2) and now its three through the loophole (subsidiary to evade membership limits being exceeded, just like at the OSI and Redmonk). Its like a completely covert takeover in slow motion and the AT-LARGE DIRECTOR is also a Microsoft employee (all 3 are female, so talking about this hostile act of entryism will get baited as being sexist**); Mr. Mason is no longer there, so no geeks or Linux developers left in the Board (its just suits and corporate actors). As a reminder, Microsoft is also in the Technical Advisory Board of the Linux Foundation and its current Bo...
18:52
IRC Proceedings: Monday, June 19, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-190623.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-190623.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-190623.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-190623.gmi
Over HTTP:
|
... |
18:39
ASUS Releases Patches to Fix Critical Security Bugs Impacting Multiple Router Models The Hacker News
Taiwanese company ASUS on Monday released firmware updates to address, among other issues, nine security bugs impacting a wide range of router models. Of the nine security flaws, two are rated Critical and six are rated High in severity. One vulnerability is currently awaiting analysis. The list of impacted products are GT6, GT-AXE16000, GT-AX11000 PRO, GT-AXE11000, GT-AX6000, GT-AX11000,
18:14
MSI Launches Power Supply With Yellow Connectors to Prevent 16-Pin Connector Meltdowns SoylentNews
MSI's latest PSU series aims to mitigate user error with one minor change:
MSI has launched its MAG GL power supplies, showcased at Computex 2023. These new power supplies are PCIe 5.0 compatible and are compliant with the ATX 3.0 standard. In addition to meeting new spec guidelines, they have the bonus of featuring yellow pin connectors on both ends of the cable. The idea behind the subtle change is to make it easier for users to see whether or not the cable is completely inserted, preventing a few common hardware failures, such as the 16-pin connector meltdowns on the GeForce RTX 4090, one of the best graphics cards.
According to MSI, users frequently reported problems with burnt power supply connectors when using them with newer high-end GPUs. Upon investigation, the team realized one of the most common causes of this issue was improperly connected cables. With the new yellow pin connectors, users can easily see whether or not the cable has been fully inserted when assembling their PC.
The new MAG GL series PSUs are designed to handle Nvidia GeForce RTX 40-series graphics cards. They are also compatible with Intel's Power Supply Design Guide (PSDG) ATX 3.0 standard. This support only waivers when the power supply isn't correctly installed, which is always necessary, especially given the latest hardware demands.
Previously: Another 16-pin RTX 4090 Power Adapter Has Melted, but From the PSU Side This Time
Read more of this story at SoylentNews.
18:12
Over 100,000 Stolen ChatGPT Account Credentials Sold on Dark Web Marketplaces The Hacker News
Over 101,100 compromised OpenAI ChatGPT account credentials have found their way on illicit dark web marketplaces between June 2022 and May 2023, with India alone accounting for 12,632 stolen credentials. The credentials were discovered within information stealer logs made available for sale on the cybercrime underground, Group-IB said in a report shared with The Hacker News. "The number of
18:00
Creating Lithography-Free Photonic Reprogrammable Circuits Hackaday

The field of photonics has seen significant advances during the past decades, to the point where it is now an integral part of high-speed, international communications. For general processing photonics is currently less common, but is the subject of significant research. Unlike most photonic circuits which are formed using patterns etched into semiconductor mask using lithography, purely light-based circuits are a tantalizing possibility. This is the focus of a recent paper (press release, ResearchGate) in Nature Photonics by [Tianwei Wu] and colleagues at the University of Pennsylvania.
What is somewhat puzzling is that despite the lofty claims of this being the first time that such an FPGA-like device has been created for photonics, this is far from the case, as evidenced by e.g. a...
17:27
The Collapse of Reddit Helps Gemini Grow and the Message About Gemini Protocol Spread Techrights
Summary: People who used the Internet before are still on the Internet but not necessarily on the Web; weve seen growth in the number of Gemini users (this month has been the best so far) and if more people reject apps not the same as HTTP/S perhaps we can move technology in a healthier direction
FOR those who dont pay much attention to Internet gossip, Reddit is in trouble and its CEO is spamming people (via E-mail) together with NPR, trying hard to control the narrative/story about whats happening. Yesterday he was linked to Musk, which is a total disaster. In addition, this past week there were stories such as these:
-
Reddit Blackouts Impact Music Communities Online CEO Not Backing Down
-
Reddit Blackuut: What, Why and How It is Impacting Users
-
Reddit: users boycott to force platform to scrap plans to charge for access, company wont budge
-
The Reddit Protest Is a Battle for the Soul of the Human Internet
Yesterday in IRC Alexei said, Both Steve Huffman and Elon Musk must be reaffirmed by Volodymyr Saldo when he was in Nova Kakhovka standing next to a flooded theatre and saying on camera that people are walking, driving and working just fine. Saldo was filmed on June 6th of course.
Are some more Reddit clones on their way? Based on Gemini protocol alone?From what we can gather, Reddit will never be the same again. Many users, not only moderators (slaves/volunteer staff) left permanently. Some of them ended up in Gemini. They say so themselves. There are some hello world posts.
Is the collapse of Reddit helping Gemini grow so much faster this month?...
17:00
IBM Achieves Breakthrough In Quantum Computing Terra Forming Terra

Why Everything You Know About World War II Is Wrong. Ron Unz Terra Forming Terra

The huge take home for me is that Rooseveldt needed a full on war, or at least fully believed he did. He lacked an alternative in his imagination that allowed massive money printing to re start the USA economy. this is not just turning a blind eye to the japanese. We have all underestimated his planned intent nor acknowledge his actions and choices so informed.
By Ron Unz and Mike Whitney
Global Research, June 14, 2023
The Unz Review
The digitalisation of social interactions has enormous consequences for society Terra Forming Terra

Space Travel Can Change Astronauts Brains for Years Terra Forming Terra
:focal(2650x1741:2651x1742)/https:/tf-cmsv2-smithsonianmag-media.s3.amazonaws.com/filer_public/9a/9d/9a9d4f31-c088-4205-876b-88667e5e34b1/gettyimage)
16:56
ASUS addressed critical flaws in some router models Security Affairs
ASUS addressed critical vulnerabilities in multiple router models, urging customers to immediately install firmware updates.
ASUS is warning customers to update some router models to the latest firmware to address critical vulnerabilities.
The impacted models are GT6, GT-AXE16000, GT-AX11000 PRO, GT-AX6000, GT-AX11000, GS-AX5400, GS-AX3000, XT9, XT8, XT8 V2, RT-AX86U PRO, RT-AX86U, RT-AX86S, RT-AX82U, RT-AX58U, RT-AX3000, TUF-AX6000, and TUF-AX5400.
The firmware released by the company addressed nine vulnerabilities, including CVE-2023-28702, CVE-2023-28703, CVE-2023-31195, CVE-2022-46871, CVE-2022-38105, CVE-2022-35401, CVE-2018-1160, CVE-2022-38393, and CVE-2022-26376.
The most severe vulnerabilities are two critical issues, below are their descriptions:
- CVE-2022-26376 is a memory corruption vulnerability that resides in the httpd unescape functionality of Asuswrt prior to 3.0.0.4.386_48706 and Asuswrt-Merlin New Gen prior to 386.7. An attacker can trigger the issue by sending a specially-crafted HTTP request to impacted routers leading to memory corruption.
- CVE-2018-1160 is an out-of-bounds write issue that resides in dsi_opensess.c. The issue impacts Netatalk before 3.1.12 and stems from the lack of bounds checking on attacker-controlled data. A remote, unauthenticated attacker can trigger the issue to execute arbitrary code on vulnerable devices.
We strongly encourage you to periodically audit both your equipment and your security procedures, as this will ensure that you will be better protected. reads the advisory published by ASUS. Update your router to the latest firmware. We strongly recommend that you do so as soon as new firmware is released.
Please note, if you choose not to install this new firmware version, we strongly recommend disabling services accessible from the WAN side to avoid potential unwanted intrusions. These services include remote access from WAN, port forwarding, DDNS, VPN server, DMZ, port trigger. ASUS added.
In case customers cannot immediately install the updates, Asus recommends disabling services accessible from the WAN side to avoid potential unwanted intrusions. These services include remote access from WAN, port forwarding, DDNS, VPN server, DMZ, port trigger.
The vendor also recommends creating distinct, strong passwords for the wireless network and router administration pages.
Follow me on Twitter:...
16:48
Pirate Movie Supplier Quits After Russian Pirates Cammed its Pirate Releases TorrentFreak
 Straight answers in response to straight questions is far
from the default position in Hollywood where piracy is concerned.
The topic is always controversial, and most of the interesting
questions have answers that have the potential to make it even more
so.
Straight answers in response to straight questions is far
from the default position in Hollywood where piracy is concerned.
The topic is always controversial, and most of the interesting
questions have answers that have the potential to make it even more
so.
Whether the details will ever see the light of day is unclear, but the discussions that led to Hollywood ending theatrical releases in Russia in response to the invasion of Ukraine mustve been fascinating.
Corporations are rarely considered worthy recipients of sympathy votes, but tearing down a patiently-built market that had overcome many piracy challenges over the previous decade wont have been easy, even if it was necessary.
Cant Buy It Legally? Someone Will Sell It Illegally
The developing legal content market in Russia has always faced stiff competition from pirates. Improvement in content availability gave consumers choice beyond the piracy default, but with no new Hollywood content available to buy, there was never any doubt that pirates would attempt to pick up the slack.
That some Russian cinemas were able to screen major Hollywood movies in perfect quality still came as a surprise. By December 2022, alongside the screenings of Avatar: The Way of Water, people spoke of major movies being supplied complete with Russian dubbing by sources in Kazakhstan.
While welcomed by Russian movie fans, these releases faced inevitable and immediate competition from pirates. A high-quality telesync copy of Avatar 2, presumably recorded from an unlicensed screening in Russia, was among other titles that exploited the growing theatrical pirate market in Russia, or at least for as long as it lasted.
WesternRus: Russias Hollywood Movie Supplier
After being referenced in the media regularly but rarely by name, last week an announcement made by Kazakhstan-based company WesternRus leaked from its private Telegram channel and into the hands of journalists. Cinema industry publication ProfiCinema identified WesternRus as the main supplier of Western movies to Russian theaters.
ProfiCinema said that WesternRus had been supplying new Hollywood releases that had already undergone localization. Transactions took place on WesternRus Telegram channel, where the company would hand out keys to theatrical distribu...
16:42
shutdown/reboot now require membership of group _shutdown OpenBSD Journal
Theo de Raadt (deraadt@) committed
changes which result in the shutdown(8) and
reboot(8)
commands (in -current) requiring membership of the the (new) group
"_shutdown". The commit message explains the
rationale:
15:59
Links 20/06/2023: DeVault Promising a Reform, Libreboot Promising No-microcode ROMs Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
-
GNU/Linux
-
Audiocasts/Shows
-
Jupiter Broadcasting Ham Sandwich | LINUX Unplugged 515
Is Ham Radio a natural hobby for Linux users? An old friend joins us to explain where the two overlap. Special Guest: Noah Chelliah.
- ...
-
-
15:51
Search and Rescue Operation Underway for Submarine Visiting the Titanic Wreck SoylentNews
A search and rescue mission was underway Monday for a submarine that went missing in the North Atlantic on an expedition to explore the wreckage of the Titanic. Lt. Jordan Hart of the U.S. Coast Guard in Boston first confirmed to CBS News that personnel were "currently undergoing a search and rescue operation" when asked about the rescue efforts off the coast of Newfoundland.
At a news conference Monday afternoon, Rear Admiral John Mauger confirmed that five people were on board. A Coast Guard official identified them as an operator and four mission specialists a term the company uses for its passengers.
The vessel submerged on a dive Sunday morning, and the crew of the Polar Prince the ship that ferried the submersible and expedition members to the dive site "lost contact with them approximately 1 hour and 45 minutes into the vessel's dive," the Coast Guard said in a tweet.
Read more of this story at SoylentNews.
15:45
The World Wide Web Blender Techrights
Video download link |
md5sum 0c28463215e56abd1ffb5ea388e4ae20
Straining RSS Feeds
Creative Commons Attribution-No Derivative Works 4.0
Summary: Were still developing better tools for finding and clustering/grouping news from the World Wide Web, seeing that the Web rapidly deteriorates and theres no way to ameliorate this other than swallowing thousands of RSS feeds, then straining them for the actual signal (meaningful and important news, not hearsay/gossip)
THE VIDEO above discusses the deterioration of the media, especially in the signal-to-noise ratio sense. We wrote about it yesterday (also here) because the alarming rate of decline (in signal) means that harvesting the important news or curating what actually matters will be getting harder. Even news about GNU/Linux became rather scarce. The video covers some new and old rants about what Phoronix became. In days of slow news theres even promotion of Microsoft junk, GitHub stuff, and various hardware products which are proprietary and patented, albeit spun as community.
The Web is rapidly becoming a junkyard and graveyard. Sites turn into mostly junk or go offline.Some time next week we hope to do more proper coverage of ways to scan the news, via RSS feeds, with additional annotation that aids discovery, classification and so on. Without a lot of editing and human intervention its possible that over 80% of whats new on the Web can be deemed junk. The Web is rap...
15:05
Rogue Android Apps Target Pakistani Individuals in Sophisticated Espionage Campaign The Hacker News
Individuals in the Pakistan region have been targeted using two rogue Android apps available on the Google Play Store as part of a new targeted campaign. Cybersecurity firm Cyfirma attributed the campaign with moderate confidence to a threat actor known as DoNot Team, which is also tracked as APT-C-35 and Viceroy Tiger. The espionage activity involves duping Android smartphone owners into
15:00
Whats In a Slip Ring? Hackaday

We know that when [Big Clive] puts up another video, the chances are were in for another fascinating look into a piece of tech on his bench. The latest is a slip ring assembly, and he gives it a teardown to reveal its secrets.
For most of us, the only place we encounter a slip ring is in some electric motors or alternators when it provides a connection via a conductive ring and a graphite brush from a fixed component to a rotating one. But they also appear as components in their own right wherever a rotating assembly needs an electrical contact, and its one of these that [Clive] has on his bench. Its a compact unit with an impressive six conductors, and its manufacturer boldly claims that its good for mains voltages. Were going with the verdict in the video below the break. Thats wishful thinking, given the size of the unit.
Inside is a rotor with six brass rings and a couple of decent little bearings, while the other half of the unit is a set of gold-plated spring contacts. There is extensive use of potting, and the verdict is that this is a surprisingly good quality component for the eBay price. We look forward to our community finding inventive uses for them. Having a ready-made unit sure beats making your own.
...
13:28
Is the US Trying to Kill Crypto-Currency? SoylentNews
Is the US trying to kill crypto?:
[...] The sector was already under pressure, after prices of virtual currencies collapsed last year. Further damage came from the meltdown of several high-profile firms, including FTX, run by the so-called "Crypto King" Sam Bankman-Fried, whom prosecutors have accused of conducting "one of the biggest financial frauds" in US history.
Jolted by the turmoil, US regulators stepped up their policing of the sector, which authorities say has been on notice since at least 2017 that their activity runs afoul of US financial rules intended to protect investors.
The campaign has yielded a steady drumbeat of charges against crypto firms and executives, alleging violations ranging from failing to register properly with authorities and provide adequate disclosure of their activity to, in some cases, more damaging claims such as mishandling of consumer funds and fraud.
[...] Gary Gensler, the chairman of the Securities and Exchange Commission, defended the moves this month, comparing the state of affairs in the industry to the 1920s, before the US put in place many of the rules in question: "Hucksters. Fraudsters. Scam artists. Ponzi schemes. The public left in line at the bankruptcy court."
[...] Critics accuse the SEC under Mr Gensler of hostile "regulation by enforcement" aimed at boosting his own political profile.
[...] Whether the SEC's moves could actually kill the industry - in which by at least one estimate one in every six Americans has invested - is another question.
Read more of this story at SoylentNews.
12:00
Using Trash To Keep Plastic Trash Out Of Oceans By Kabooming Them Hackaday

For a few years now, [Richard] of Tropical Ocean Cleanup fame has been working hard to clean the Philippines of the plastic trash that litters everything, and washes down the canals and rivers into the ocean. Using nothing but what is essentially trash old car tires, rope and empty soda bottles he creates kabooms that prevent this trash floating in the canals from polluting the beaches, kill wildlife and gather in the oceans. In a recent video he covers how he creates these systems, and the basics of how they are installed.
We previously covered [Richard]s efforts, and although these kabooms have received a few tweaks along the way, the basic principle has remained the same. The empty bottles provides the buoyancy, while the tires are excellent structural elements that can take a beating from the weather and debris. Some of the kabooms are lashed together with rope, while for other types holes are drilled into the tires using a hole saw, all of which help to create a self-supporting trash capture system that can be installed easily with a group of volunteers.
Fetching the thus captured trash is still a bit of a struggle, requiring a fair bit of manual labor, nets and boats from local fishermen when they have some spar...
11:41
Gemini Links 19/06/2023: Tale Of Two Unknowns and Perfect Home Lab Techrights
-
Gemini* and Gopher
-
Personal/Opinions
-
Three variations on a feedback theme
It shouldnt need pointing out that positive feedback can be a terribly bad thing. Lets consider some very different cases.
[..]
Mais oui, it still _would be_ a problem even if the users had the full ownership of this technology. The scenario that comes to my mind is that people already use their headphones to mask out an undesirable, harsh sonic environment. In response to this shielding, I suppose, sound signals and announcements have to be made louder to reach even those listening to music in their headset. Anyway, I can think of no equally plausible explanation for the absurdly loud announcements of the next stop at the regional train, occasionally also on busses. Yes, the populations hearing is also gradually deteriorating by frequent exposure to loud sound levels, so the signals that must penetrate the noise have to be made louder again.
The Acoustic Ecology movement (R. Murray Schafer and others) would ordain increased awareness of our sounding surroundings instead of trying to block them out. Which is not to say that a noisy city dominated by the diffuse persistent motor hum and rubber decks against roads, mixed to a blur of vehicles at all distances, is an ideal or particularly fascinating soundscape. Schafer would prefer a quiter backdrop in which delicate sounds are given a chance to be heard, a rural, pre-industrial soundscape.
-
A few photos from a river walk last week
From the trails along the Tanana River
-
Garden Photos
A few photos from last week, from the garden in front of our apartment.
-
More river trail photos
I believe this flower is the same as the Northern Bluebell mentioned in this Wikipedia article
-
...
-
-
11:16
Young People Who Understand That Richard Stallman (RMS) Was Right, Even Long Before They Were Born Techrights
Video download link |
md5sum c9743d29a192263f9ad7155e1f8bf443
The RMS Effect in Gemini
Creative Commons Attribution-No Derivative Works 4.0
Summary: Dr. Richard Stallman (RMS) still travels the world and gives talks; he still manages to convince people, even very young people, that Software Freedom is very important for very many reasons
THE video above discusses the new article (in Gemini) We need more of Richard Stallman, not less (we included it in Daily Links half a day ago). Its pleasant to see someone relatively young supporting the message of Richard Stallman. Many young people are easily misled by campaigns of defamation and distraction.
We previously managed to convince Brodie Robertson, a young Australian with over 50,000 YouTube subscribers, that Stallman ISNT OUT OF TOUCH With Technology! (he had previously criticised him harshly).
People just need to listen to the message of Stallman, going back to 1984 (literally, the year). Well-funded monopolistic corporations cannot easily attack the message; so they demonise the messenger.
10:50
[Meme] Independent EPO/EU Courts for Patents Techrights
If the dictator on the right finds that his for-profit court is not legal, then he changes the text to make it "legal", in turn blessing the abuse of the dictator on the left (its all about money anyway, justice isnt the goal)

3 judges resigned before it even started
Summary: With
corrupt dictators as chief judges, the kangaroos of EPO
dictators (even doing photo ops to boast about
it* with Antnio Campinos), one wonders why European
Union (EU) officials including Commissioners who are connected
closely to Benot Battistelli have the audacity
to blast the Polish regime on a basis such as rule of law or law
and order; even the so-called media colludes in these criminal acts
now **, as the criminals basically pay
it to do so
_____
* They see no need to even pretend that
their court is legal and constitutional because the lobbyists and
officials are in their back pockets. Some act as their
attack dogs (and then
start issuing threats to people who show those photo ops as if
we're in Stalinist Russia; highlighting corruption is illegal
now? Im a foreign agent who discredits the military̶...
10:17
The EPOs NO-Career System Will be Scrutinised by a Tribunal, the ILOAT, 3 Weeks From Now Techrights
Video
download link | md5sum
6e6b6b17f5c1bef3c93e2527bbb20998
The GCC Report of EPO Staff Reps
Creative Commons Attribution-No Derivative Works 4.0
Summary: The Central Staff Committee at the EPO protests proposals from Antnio Campinos and his cronies; it asserts that the [management of the] Office does not want to question the New Career System [a NO-Career System now, as the ILOAT will deliver in public the judgments of its 136th session on Friday 7 July 2023, including three important cases relating to the EPOs New Career System. As a reminder, sometimes it takes ILOAT nearly a decade to strike down illegal regulations (more than 3 years not 3 weeks after the culprit, Benot Battistelli, had already left the Office)
THERE will be some interesting news in a few weeks because the EPO, which grants European software patents (illegally) and then passes such patents for a kangaroo court to judge (an illegal court where...
09:00
Bringing Back the Minitel Hackaday

If you didnt live in France in the 80s or 90s, its likely you missed out on one of the most successful computer networks in existence prior to the modern Internet. Known as Minitel, it was an online service available over existing phone lines that offered a connected computer terminal for users to do most things we associate with the modern world, such as booking travel, viewing news, looking up phone numbers, and plenty of other useful activities. While a lot of the original system was never archived, there are still some efforts to restore some of its original functionality like this MiniMit.
The build requires either an original or a recreation of a Minitel terminal in all its 80s glory, but pairs an ESP32 to support modern network connectivity. The ESP32 interfaces with the Minitels DIN socket and provides it with a translation layer between WiFi and the networking type that it would have originally expected to see from the telephone lines. Two of the original developers of Minitel are working on restoring some of the services that would have been available originally as well, which means that the entire system is being redeveloped and not just the original hardware.
Weve mentioned that this system was first implemented in the 80s, but the surprising thing is that even well after broadband Internet would...
09:00
VPN for Privacy: Shielding Your Online Activities from Prying Eyes HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
Protect your online privacy with trustworthy VPNs. Shield your sensitive data from prying eyes and browse the internet
This is a post from HackRead.com Read the original post: VPN for Privacy: Shielding Your Online Activities from Prying Eyes
08:56
Linux 6.5 Adding Support For NCT6799D Sensors Found In Various Newer Motherboards Phoronix
If your newer desktop motherboard has a NCT6799D Super I/O controller or one of the variants like NCT6799D-S, the Linux 6.5 kernel is set to introduce support for this ASIC in order to expose hardware sensor support under Linux...
08:43
IBM Says It's Made a Big Breakthrough in Quantum Computing SoylentNews
IBM Says It's Made a Big Breakthrough in Quantum Computing:
[...] Scientists at IBM say they've developed a method to manage the unreliability inherent in quantum processors, possibly providing a long-awaited breakthrough toward making quantum computers as practical as conventional ones or even moreso.
The advancement, detailed in a study published in the journal Nature, comes nearly four years after Google eagerly declared "quantum supremacy" when its scientists claimed they demonstrated that their quantum computer could outperform a classical one.
Though still a milestone, those claims of "quantum supremacy" didn't exactly pan out. Google's experiment was criticized as having no real world merit, and it wasn't long until other experiments demonstrated classical supercomputers could still outpace Google's.
IBM's researchers, though, sound confident that this time the gains are for real.
"We're entering this phase of quantum computing that I call utility," Jay Gambetta, an IBM Fellow and vice president of IBM Quantum Research, told The New York Times. "The era of utility."
[...] These spooky principles allow for a far smaller number of qubits to rival the processing power of regular bits, which can only be a binary one or zero. Sounds great, but at the quantum level, particles eerily exist at uncertain states, arising in a pesky randomness known as quantum noise.
Managing this noise is key to getting practical results from a quantum computer. A slight change in temperature, for example, could cause a qubit to change state or lose superposition.
Read more of this story at SoylentNews.
07:59
Anti-Piracy Group Signals Opportunities to Tackle Online Piracy Apps TorrentFreak
 Over the past decade, mobile applications have become
the standard platform for most people to consume content
online.
Over the past decade, mobile applications have become
the standard platform for most people to consume content
online.
Whether its for shopping, news, or entertainment, there is an app available for any type of content.
This shift in consumption patterns is not limited to legal content; movie and TV piracy has gone mobile as well. In some cases, these pirate streaming apps can be found in official app stores, reaching an audience of millions of users.
The App Piracy Problem
Copyright holders are not happy with these unauthorized apps, which are big business. In a recent publication by the Audiovisual Anti-Piracy Alliance (AAPA), NOS Head of Content Protection Pedro Bravo provides a detailed overview of the problem.
App piracy includes legitimate apps that are copied but we reserve our reporting to those that are advertised as a gateway to pirated content or live streams. While these apps lure users with free stuff, they dont necessarily offer pirated content.
The ultimate goal of the developers is the same though. They want to convert users into a revenue stream, one way or another. Some apps may monetize user data, for example, but for the vast majority advertising is the income stream of choice.
Stealing Ad Dollars
That can be quite a lucrative business model and poses yet another problem for legitimate content creators. In addition to stealing content, these pirate apps steal their potential advertising revenue too.
Ad words campaigns are the most lucrative for Pirates. Yes, not only are rights holders losing money from the lack of legitimate App downloads, but Pirates steal what should be their ad revenue as well, Bravo notes.
In the past, some pirate sites and services have embraced the Robin Hood image, in the sense that they distribute content from wealthy corporations to the public at large. However, the AAPA piece notes that it is nave to think that pirates are well-intended folk heroes.
[Pirates] are not charities, handing out access to content to ease the economic pressures. Quite the opposite. Pirates are in it for the money. They are often large, international organizations spread across different jurisdictions, with IT infrastructure and sizeable resources....
07:45
07:39
Alpine Linux fatal error: ncurses.h: No such file or directory fix nixCraft
When I try to compile a program on
Alpine Linux, it fails with the following error:
app.c:1:10: fatal error: ncurses.h: No such file or directory
1 | #include <ncurses.h>
| ^~~~~~~~~~~
compilation terminated.
Love this? sudo share_on: Twitter - Facebook - LinkedIn - Whatsapp - Reddit
The post Alpine Linux fatal error: ncurses.h: No such file or directory fix appeared first on nixCraft.
07:30
9 Astounding Facts That Prove the Moon is Artificial Why Is It There? Terra Forming Terra

06:31
Unlocking the Secrets of Smooth Domain Transfers: A Step-by-Step Guide HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
Are you looking to switch your web address to another registrar? According to ICANN, youre free to do
This is a post from HackRead.com Read the original post: Unlocking the Secrets of Smooth Domain Transfers: A Step-by-Step Guide
05:38
Experts found components of a complex toolkit employed in macOS attacks Security Affairs
Researchers uncovered a set of malicious files with backdoor capabilities that they believe is part of a toolkit targeting Apple macOS systems.
Bitdefender researchers discovered a set of malicious files with backdoor capabilities that are suspected to be part of a sophisticated toolkit designed to target Apple macOS systems.
The investigation is still ongoing, the experts pointed out that the samples are still largely undetected.
The researchers analyzed a total of four samples that were uploaded to VirusTotal, with the earliest sample that was uploaded by an anonymous actor to the platform on April 18, 2023. The remaining ones have been uploaded by the victim.
Two of the three samples uploaded by a victim are generic Python backdoors that target Windows, Linux, and macOS systems.
The first file identified by the experts is shared.dat, once executed it generates a unique device identifier UID and uses a routine to check the OS running on the target machine.
The files connect to the C2 server to receive additional commands to execute.
The malware can be instructed to extract systems information, run specific commands
This includes gathering system information, running encoded as base64 commands, downloading and executing routines, and killing itself.
The DownExec routine works differently, based on the victims operating system.
For MacOS devices, the function writes a file to /Users/Shared/AppleAccount.tgz. The content that is written to the archive is also encoded as base64 when received from server. It unpacks the archive to the /Users/Shared folder, then opens the /Users/Shared/TempUser/AppleAccountAssistant.app application. reads the...
05:16
F2FS Preparing To Land Async Buffered Write Support Phoronix
The Flash-Friendly File-System (F2FS) is preparing to land async buffered write support into the Linux kernel as another performance win for this flash-optimized file-system...
04:56
Data Breach at New BreachForums: 4,000 members data leaked HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
BreachForums is a recently resurfaced alternative to the popular hacker and cybercrime forum, Breach Forums, which is now defunct.
This is a post from HackRead.com Read the original post: Data Breach at New BreachForums: 4,000 members data leaked
03:59
The Legend of "x86 CPUs Decode Instructions Into RISC Form Internally" SoylentNews
https://fanael.github.io/is-x86-risc-internally.html
There is a widespread idea that modern high-performance x86 processors work by decoding the "complex" x86 instructions into "simple" RISC-like instructions that the rest of the pipeline then operates on. But how close is this idea to how the processors actually work internally?
To answer this question, let's analyze how different x86 processors, ranging from the first "modern" Intel microarchitecture, P6, to their current designs, handle the following simple loop (the code is 32-bit just to allow us to discuss very old x86 processors):
x86 assembly
.loop:
add [edx], eax
add edx, 4
sub eax, 1
jnz .loop
Read more of this story at SoylentNews.
02:31
A Wearable Robotic Assistant Thats All Over You IEEE Spectrum

This is a guest post. The views expressed here are solely those of the author and do not represent positions of IEEE Spectrum or the IEEE.
Researchers at the Small Artifacts Lab (SMART LAB) at the University of Maryland have been working on a small wearable robot called Calico. Weighing just 18 grams, the robot attaches to a special track sewn on top of your clothing and is ready for work by traversing your garments, which allows it to do all kinds of things, including acting as a stethoscope to listen to your heart and lungs and coaching you through a fitness class.
University of Maryland
One of the biggest challenges for Calico is localization: GPS, of course, isnt precise enough to help you determine where the robot is on your clothing. The researchers solved this problem by embedding neodymium magnets into the clothing track at even intervals, which can be used as markers. With onboard sensors, Calico can detect these magnets, and use them to estimate where the robot is currently located and allowing it to effectively plan a path across your body. Its a very effective system, as the robot never missed a single marker throughout the development cycle.
The Calico robot can carry a 20-gram payload. Depending on the direction of travel, the robot can achieve speeds between 115 millimeters per second and 227 mm/s. Thanks to the low-power design, the little rovers 100 milliampere-hour battery will last more than 8 hours in an idle state or 30 minutes with continuous movement. Wireless charging could further extend the operating time of the robot.
When describing their research, the SMART LAB members came up with many applications for their wearable. A microphone and a stethoscope add-on enable the robot to sense vital signs, for example. The robot could travel to a predefined location to listen to your organs, or a doctor could teleoperate it in real time. And because the system already has an accelerometer, it could be used...
01:40
DeVault: Reforming the free software message LWN.net
Drew DeVault has announced the launch of a new web site that is intended to be a better introduction to the free-software community.
Some of my criticisms focused on the message: fsf.org and gnu.org together suffer from no small degree of incomprehensibility and inaccessibility which makes it difficult for new participants to learn about the movement and apply it in practice to their own projects.This is something which is relatively easily fixed!
01:35
The Latest 2023 Tech Layoff Numbers in Three Charts IEEE Spectrum

Last November, with tech layoff announcements seemingly coming faster and faster every day, IEEE Spectrum asked Intellizence, an AI startup that provides market intelligence services for corporate clients, to dig through the news to assemble actual data. Though not perfectly comprehensive, this data gave us a decent snapshot on what was going on, but we couldnt tell whether that wave represented a bad news peak or just the beginning of a tsunami. (Intellizence gathered this data from WARN filings, news reports, and press releases, using AI-based tools to extract key details.)
We went back to Intellizence this month for an update. Looking at these latest numbers, its clear that in last November, the wave of bad news for tech professionals was just getting started. After a dip in layoff announcements in December (Happy holidays, yall!), the number of tech company employees facing pink slips in January was nearly double the November spike. Since then, the pace of layoffs has leveled off some, but the numbers are still high.
Heres what the data show to date. January was a brutal month, with tech companies announcing that more than 100,000 positions were being cut. Since then, more than 70,000-plus tech company employees have been given notice.
Since last August, when the tech downturn became apparent, more than a quarter of a million U.S. tech jobs have disappeared, according to Intellizences analysis. The crunch hit professionals at companies big and small, but the most dramatic news came from Alphabet, Amazon, and Meta, which together accounted for more than 75,000 layoffs.
01:29
Red Hat Aiming To Address IBRS Mitigation Still Being Too Costly On Performance Phoronix
Red Hat engineers are working to deal with Indirect Branch Restricted Speculation (IBRS) being too costly for mitigating Spectre V2 and Retbleed on older Intel Xeon Scalable processors. A new patch has been floated to disable IBRS when idle and is working out well at least for Red Hat Enterprise Linux 9 while isn't clear yet if it will be accepted into the upstream kernel...
01:21
[$] PostgreSQL reconsiders its process-based model LWN.net
In the fast-moving open-source world, programs can come and go quickly; a tool that has many users today can easily be eclipsed by something better next week. Even in this environment, though, some programs endure for a long time. As an example, consider the PostgreSQL database system, which traces its history back to 1986. Making fundamental changes to a large code base with that much history is never an easy task. As fundamental changes go, moving PostgreSQL away from its process-oriented model is not a small one, but it is one that the project is considering seriously.
01:21
New Mystic Stealer Malware Targets 40 Web Browsers and 70 Browser Extensions The Hacker News
A new information-stealing malware called Mystic Stealer has been found to steal data from about 40 different web browsers and over 70 web browser extensions. First advertised on April 25, 2023, for $150 per month, the malware also targets cryptocurrency wallets, Steam, and Telegram, and employs extensive mechanisms to resist analysis. "The code is heavily obfuscated making use of polymorphic
00:56
Aviator Predictor V1 Ninety Four Apk Mod 2023 Free Obtain Iphone h+ Media
Aviator Predictor V1 Ninety Four Apk Mod 2023 Free Obtain Iphone
The Aviator game got here with a groundbreaking chat function for players. This feature allows gamers to share pleasant interactions in the course of the sport. Only 10 players can reap the benefits of this offer at a time.
Nevertheless, gamers can use sure methods and game tricks to increase the possibilities of profitable. Check out our useful tips for enjoying Aviator in the Best 1Win Aviator Tricks part of this web page. In this recreation, you should put together yourself to seize the controls of the aircraft and cash out earlier than it takes off with your bet. Aviator on-line game can even allow you to uncover your casino abilities to awaken your competitive facet and take your online casino expertise to the next level.
Spribe Aviator is simple to study and could be performed by anyone, regardless of their experience with online on line casino video games. The cutting-edge technology in Aviator recreation offers a seamless and interesting expertise for anyone to take pleasure in. Play Aviator actual money recreation at an internet on line casino that uses cutting-edge know-how provides an excellent person experience and is safe. Aviator Spribe gaming, an online on line casino India actual cash, is a one-of-a-kind on line casino game that seeks to reward you.
Players can connect with us over mail at with a 3 hour turn round time. For membership players, direct phone support is also available. It is suggested not to use running shoes for on a daily basis actions as it can damage the shoe faster than it was meant to last. Running sneakers have unique midsoles that provide consolation and stretch after a run. Prolonged utilization would imply the midsole would lose its properties to absorb the shock from the bottom.
Select the betting websites with Aviator sport, for example 1win. Find Spribe Aviator game via the search bar or within the list of well-liked video games. To win at Aviator game, first of all you want to make your gaming strategy and stick with it.
It is generated with the help of the players who participate within the spherical. The maximum single guess at Aviator betting recreation is $100 USD. However, this does not indicate that you can solely place one wager. The sport additionally lets you place two bets on the same time.
The steady betting environment and constant bonuses upload some other layer of attraction to the platform. This positions Aviator not merely as an iGaming application, but as an entire, immersive, and secure gaming journey. Players can place bets on each spherical and potentially win huge payouts at Aviator betting recreation. However, it is important to remember to guess inside ones means and to make sensible, calculated decisions to avoid unnecessary dangers. In addition to that, Aviator video games features entice players. It allows you to make the most effect...
00:48
Aviator Sport Apk Obtain 2023 h+ Media
Aviator Sport Apk Obtain 2023
Enjoyable bonuses, special promo codes, massive winnings and a new gaming expertise await you. Spribe Aviator is an exciting on-line casino sport that provides gamers with an interesting and immersive expertise. Its simple controls, configurable planes, and several sport modes make it a prime choose for fans of online casino games. Yes, online casinos are real and provide the same video games youll discover at a land-based on line casino. It is essential to examine for the right licensing and laws of any on-line casino youre considering enjoying with to ensure that it is authorized and protected.
To claim your first prize, use promo code AVIATORWORLD, a singular combination of letters and numbers that will pave the method in which for money rewards. It is necessary to grasp that you can play Aviator at 1win India on line casino for a payment or free of charge. The demo model will introduce the participant to the full performance of the sport, let you master the rules and permit to test strategies which are easy to search out on the web. But its disadvantage is the inaccessibility of earnings. Since the player makes bets on the casinos expense, he will not be Aviator is the right software, offering you with the chance to comprehend its guidelines with out operating out of cash.
If we talk in regards to the fairness of the game, then Aviator makes use of provably honest technology, which lets you exclude the interference of third parties in the recreation course of. This technique requires plenty of investment, however it works reliably and infrequently pays off. The complete point is to bet a big amount without delay and withdraw virtually instantly. Due to the fact that the amount of cash in the guess is large, you will casino regler kort receive a good win even when the coefficient is sort of small. Aviator, like different Spribe video games, is predicated on HTML5 expertise. This implies that the game will work perfectly both on PC and on tablets and smartphones so you probably can obtain Aviator in your system and benefit from the game.
Over the years, the bookmaker has won the belief of millions of gamers. Parimatch has a huge status not only in India but all over the world. Unlike different bookmakers, Parimatch offers its clients security, a large number of bonus programs, and much more! You do not want to fret in regards to the legality of the bookmaker, as it owns all the required licenses. Here youll find many alternative sports corresponding to football, cricket, basketball, volleyball, tennis, esports, unconventional betting, and more.
As for a newcomer its highly really helpful to keep along with your limit. As for all gamers as quickly as your winning goal is full you are beneficial to money out to have the abil...
00:48
Buy Trainers On-line For Males Starts Rs 2,009 h+ Media
Buy Trainers On-line For Males Starts Rs 2,009
In the Aviator mini-game, winnings are calculated by the multiplier you cashed out multiplied by your bets. Before the beginning of each round, the RNG generates a multiplier during which the airplane will fly away. The Random Number Generator is totally honest, youll be able to examine it.
To earn cash in the game Aviator you should register and make your first deposit into your account. You can make deposits in INR or another obtainable currency. You can even withdraw your winnings through a handy fee system. Each of them has a certain theme, impression, and rules, however there is a demand for all of them among customers. Recently, the Aviator game has turn out to be particularly in style in the on line casino.
You are provided to obtain Aviator reside Signal chatbots, Aviator signal telegram predictors, as properly as varied different apps and software aimed at hacking this well-liked recreation. YouTube channels and teams in all kinds of social networks are calling to hitch their communities, promising mountains of gold and large every day winnings. It is essential to notice that each on-line on line casino could have totally different guidelines, phrases and conditions, fees, and processing occasions for withdrawals.
- But specialists dont count on the central bank to begin out cutting interest rates any time soon.
- This item is non-returnable due to hygiene/health and private care/wellness/consumable nature of the product.
- Here is a few necessary info that you should know earlier than kicking off this extremely popular sport.
- The key level to win big prizes is to money out your winnings earlier than your airplane takes off.
- The sport is totally primarily based on random numbers, so gamers cannot predict the Aviator and everyone can win.
Aviator is gaining recognition in India and is obtainable by a wide variety of bookmakers. Some of the most popular international and Indian bookmakers providing Aviator are 1xBet, Betway, 10cric, and Goawin. Some of the following bookmakers, e.g. 1xBet, additionally let you play Aviator free of charge in a demo model. However, keep in thoughts that these demo variations typically suggest that winning at Aviator is easy, whereas the actual money model tends to be a bit tougher. The following record of bookmakers with Aviator consists of internationals in addition to Indian betting websites.
Multipliers x1.20 or less are also considered unprofitable. They happen extra typically than x1, as much as about ten occasions per 100 rounds. In the higher proper nook, there is a panel with fundamental settings. It is really helpful to show off the sound and music in order that they do not distract you and dont intervene with focusing on profitable. Lastly, contemplate the level of buyer assist, together with the provision of stay chat and the responsiveness of the help...
00:27
Links 19/06/2023: Cinnamon 5.8 and Alpine Has New ISOs Techrights
00:25
Quantum Frustration Leads to Fundamental Physics Discovery: A New Phase of Matter Lifeboat News: The Blog
A team of physicists, including University of Massachusetts assistant professor Tigran Sedrakyan, recently announced in the journal Nature that they have discovered a new phase of matter. Called the chiral bose-liquid state, the discovery opens a new path in the age-old effort to understand the nature of the physical world.
Under everyday conditions, matter can be a solid, liquid, or gas. But once you venture beyond the everydayinto temperatures approaching absolute zero.
Absolute zero is the theoretical lowest temperature on the thermodynamic temperature scale. At this temperature, all atoms of an object are at rest and the object does not emit or absorb energy. The internationally agreed-upon value for this temperature is 273.15 C (459.67 F; 0.00 K).
00:24
Starlink is One Among Many LEO Constellations Affected by Satellite Signal Jamming Lifeboat News: The Blog
After Russian hackers destroyed Viasat satellite ground receivers spanning Europe, SpaceX provided coverage via Starlink, its Lower Earth Orbit satellite constellation, and soon began noticing cyberattacks and software interferences. Now, a year later, the U.S. Department of Defense announced Russia is still attempting to complicate connections within the satellite constellation and others like it.
Documents were leaked by U.S. National Guard airman Ryan Teixeira, as reported by The Washington Post back in April of 2023. Ukraine has also stated it is experiencing similar security issues.
Russias quest to sabotage Ukrainian forces internet access by targeting the Starlink satellite operations that billionaire Elon Musk has provided to Kyiv since the wars earliest days appear to be more advanced than previously known, according to a classified U.S. intelligence report.
00:24
Scientists Use Stem Cells to Create Model Human Embryos Lifeboat News: The Blog
Id like to emphasize that these are neither embryos, nor are we trying to make embryos actually, Dr. Jitesh Neupane, of the University of Cambridges Gurdon Institute, said.
00:23
Elon Musk reveals theres a Twitter app coming to Smart TVs thatll solve a major problem Lifeboat News: The Blog
According to a recent tweet from Twitter owner Elon Musk who recently confirmed the app, Twitter is preparing to launch its own video app for Smart TVs.
00:23
Critical cancer drug shortage forces doctors, patients to make tough choices Lifeboat News: The Blog
Hospitals and cancer centers are running out of two major injectable cancer drugs: carboplatin and cisplatin. Dr. Eleonora Teplinsky, head of breast medical oncology for the Valley Health System in New Jersey, joins Ali Rogin to discuss the causes and effects of the shortages, and the dilemmas that providers and their patients now face.
00:22
SpaceX launches Indonesian telecommunications satellite Lifeboat News: The Blog
SpaceXs Falcon 9 carrying the PSN Satria satellite successfully launched and deployed at 6:21 PM ET (22:21 UTC).
The launch had a 178-minute window, and upper-level winds delayed the first launch attempt at the opening of the window, but SpaceX had plenty of time to work with and launched just a bit later into the launch window.
The PSN Satria Indonesian Telecommunications was first contracted to be built in 2020 by Thales Alenia Spaceby the Indonesian government and delivered to the launch site in Cape Canaveral, Florida, in May 2023.
00:22
New Research Shows HIV Can Lie Dormant in the Brain Lifeboat News: The Blog
Scientists from the HIV Cure Center at the UNC School of Medicine, University of California San Diego, Emory University, and University of Pennsylvania have been searching for where exactly these latent cells are hiding in the body. New research published in the Journal of Clinical Investigations confirms that microglial cells which are specialized immune cells with a decade-long lifespan in the brain can serve as a stable viral reservoir for latent HIV.
Yuyang Tang, PhD, and Guochun Jiang, PhD, in the UNC School of Medicine extracted living brain tissue to conclude that specialized immune cells in the brain can harbor latent but replication-competent HIV.
As a part of its life cycle, the human immunodeficiency virus-1 (HIV) inserts a copy of its DNA into human immune cells. Some of these newly infected immune cells can then transition into a dormant, latent state for a long period of time, which is referred to as HIV latency.
Although current therapies, such current antiretroviral therapy (ART), can successfully block the virus from replicating further, it cannot eradicate latent HIV. If treatment is ever discontinued, the virus can rebound from latency and reignite the progression of HIV infection to AIDS.
00:20
Gemini Links 19/06/2023: We Need More of Richard Stallman, Not Less Techrights
-
Gemini* and Gopher
-
Personal/Opinions
-
SpellBinding: ACYGINF Wordo: SKIPS
-
Re: ~christyotwistys Five Questions for June 2023
I guess it depends a bit on what you consider an object? And whether I should limit it to things I have a realistic possibility of ever buying. Is a house an object? If so, Id like a Victorian in a walkable neighborhood, please. If a house isnt, but a car is, Id like a Hyundai Ioniq or Kia EV6. Im under no misapprehension that electric cars are a real solution to climate change; we need to aim at eliminating cars almost entirely, in favor of universal quality public transit. While Im waiting on that dream, I hate my current car. It gets much worse in-town gas mileage than I expected it to, and has been unexpectedly expensive to maintain. I dont have any foreseeable chance of buying either of those things, since electric cars are still priced as luxury items here in the US.
-
Good Music You Havent Heard Of
Music is my life is a cliche, so Ill refrain from saying it. Suffice it to say that my life has revolved significantly around music for a very long time.
Starting from high school I was one of those kids who had headphones on at every possible second. While not quite so anti-social anymore, I have worked as a developer for more than 10 years at this point, and have spent every work day of all of those listening to music while coding. And thats to say nothing of the hundreds of thousands of miles driven, workouts worked, and dinners cooked while blasting tunes.
-
Medevel 23 Free and Open-source Documentation Generators For Developers
What is a Documentation Generator?
A documentation generator is a tool that automates the process of creating documentation for software projects, APIs, or other technical products.
-
- ...
-
00:20
SVT-AV1 1.6 Squeezes Out Even More Performance For CPU-Based AV1 Encoding Phoronix
00:00
Security updates for Monday LWN.net
Security updates have been issued by Debian (golang-go.crypto, maradns, requests, sofia-sip, and xmltooling), Fedora (chromium, iaito, iniparser, libX11, matrix-synapse, radare2, and thunderbird), Red Hat (c-ares, jenkins and jenkins-2-plugins, and texlive), SUSE (bluez, chromium, go1.19, go1.20, jetty-minimal, kernel, kubernetes1.18, kubernetes1.23, kubernetes1.24, libX11, open-vm-tools, openvswitch3, opera, syncthing, and xen), and Ubuntu (libcap2, libpod, linux, linux-aws, linux-aws-5.15, linux-azure, linux-azure-5.15, linux-azure-fde-5.15, linux-gcp, linux-gcp-5.15, linux-gke, linux-gke-5.15, linux-gkeop, linux-hwe-5.15, linux-ibm, linux-kvm, linux-lowlatency, linux-lowlatency-hwe-5.15, linux-oracle, linux-oracle-5.15, linux-raspi, linux, linux-aws, linux-azure, linux-gcp, linux-hwe-5.19, linux-kvm, linux-lowlatency, linux-oracle, linux-raspi, linux, linux-aws, linux-lowlatency, linux-raspi, linux-oem-5.17, linux-oem-6.1, pypdf2, and qemu).
00:00
Review: InfiRay P2 Pro Thermal Camera Hackaday

It probably wont surprise you to learn that Hackaday is constantly hounded by companies that want us to review their latest and greatest gadget. After all, getting us to post about their product is cheaper, easier, and arguably more effective than trying to come up with their own ad campaign. But if youve been with us for awhile, youll also know that in-house reviews arent something we actually do very often.
00:00
iStorage launches datAshur PRO+C with Type-C USB interface Help Net Security
iStorage added a new encrypted flash drive to its highly successful datAshur range. The new datAshur PRO+C, with the Type-C interface, is the flash drive pending the new FIPS 140-3 Level 3 validation scheme. This offers robust guarantees as to its data security credentials. iStorages new datAshur PRO+C is a user-friendly USB 3.2 (Gen 1) Type-C flash drive that combines speed, ease of use and the highest-level security measures. It employs PIN protection and hardware More
The post iStorage launches datAshur PRO+C with Type-C USB interface appeared first on Help Net Security.
Monday, 19 June
23:56
EU member states are urged to restrict without delay 5G equipment from risky suppliers Security Affairs
The European Commission urges member states to limit without delay equipment from Chinese suppliers from their 5G networks, specifically Huawei and ZTE.
The European Commission told member states to impose restrictions on high-risk suppliers for 5G networks without delay, with a specific focus on the dependency on high-risk suppliers, specifically Chinese firms Huawei and ZTE.
According to a second report on Member States progress in implementing the EU Toolbox on 5G Cybersecurity, member states are recommended to ensure that the restrictions cover critical and highly sensitive assets identified in the EU Coordinated risk assessment, including the Radio Access Network.
The report was prepared by Member States authorities (NIS Cooperation Group), with the support of the Commission and the EU Agency for Cybersecurity (ENISA).
Ten Member States have used these powers to impose obligations on MNOs to restrict or exclude suppliers considered as high-risk from their 5G networks. reads the report published by the EU. Several Member States have taken measures to restrict the use of, or exclude, high-risk suppliers or components. In three Member States, decisions on high-risk suppliers or equipment are taken based on applications from MNOs to deploy 5G equipment. One Member State has taken a public decision to exclude Huawei and ZTE from its 5G network.
The report provides an overview of the implementation of the EU Toolboxs strategic and technical measures. The strategic measures aimed at mitigating risks associated with long-term dependency on specific suppliers. The technical measures focus on bolstering the security of 5G networks and equipment, analyzing the problems from different perspectives, including technologies, processes, human involvement, and physical elements.
The call to restrict the suppliers is subordinate to the assessments made by member states national authorities.
The report highlights the risks to collective security associated with delays in limiting the provision of network equipment from high-risk suppliers.
Out of the twenty-four Member States that possess or are in the process of developing legislative powers, seventeen have already implemented or are planning to adopt an ex-ante approach. This approach allows the states to restrict the deployment of 5G equipment from risky providers. Additionally, nineteen Member States have already confirmed their ability to enforce the removal of exis...
23:35
We are Restricting Freedom for the Common Good: Irish Green Party Calls For Limiting Free Speech cryptogon.com
Via: Jonathan Turley: The Irish Green Party followed many on the left around the world, including our own Democratic Party, this week and came out for censorship and speech controls. Indeed, the party went full Orwellian as its chairwoman Pauline OReilly called for restricting freedom to protect it. Limiting free speech has become an []
23:24
Buying the News and Gutting the News: How Information Online is Increasingly Controlled by the Few, for the Few Techrights
Summary: Information on the World Wide Web, including censorship hubs known as social control media, is getting hard to find; in the midst of tweets and TikTok anecdotes we very rarely see any truly fascinating breaking stories and investigative journalism; to make matters worse, many sites lie intentionally
THE media in the UK is perhaps least trusted among people of the same country. By some measures, the UK is in last place in Europe, as measured among the domestic population. Its not a new problem and the subject was being raised a lot back in the dawn of the Brexit referendum, in which many voters relied on lies. The problem is so severe that I refuse to access any mainstream news site in the UK. Many others who live here feel the same way. Thats a lot worse/lower than in east European countries and this new survey says, as per the Press Gazette [1]: Trust in news in the UK was at 33%, joint 12th lowest among 46 markets.
The problem is so severe that I refuse to access any mainstream news site in the UK.The Press Gazette also says [2] UK science publisher Texere acquired by Broadcast Med (everything is up for sale; the biggest papers in the UK are also being sold and our former Prime Minister, Boris Johnson, will write for a notorious tabloid which spreads lie).
The United States has a similar problem, but the media culture there is different from Europes and some clueless politicians try to pass new laws that would further kill the press, not just the Net. Public Knowledge wrote about this twice a few days ago [3-4].
This past weekend I spent endless time working on tools to better curate the news, seeing that about 90% of the news in my RSS feeds are worthless junk and perhaps 5% are actually important.Social control media wont replace the media. We wrote about Reddit, YouTube, Twitter and Facebook in recent days and they all struggle. See the new article [5] entitled Website Owners Say Traffic Is Plummeting After a Facebook Algorithm Change (Facebook sees decline in active users and will thus try to retain whats left of them inside the walled garden).
This past weekend I spent endless time working on tools to better curate the news, seeing that about 90% of the news items in my RSS feeds are worthless junk and perhaps 5% are actually i...
23:24
Why Good Weather Isn't a Good Thing for Stock Markets SoylentNews
A study suggests sunny weather can influence how investors perform and affect stock market prices:
Sunshine levels have a significant impact on the bidding behaviour of stock market investors, according to new research.
The study examined the relationship between sunny weather and how market participants perform, as well as the subsequent seasoned equity offerings (SEOs). These discounts for shares act as an effective tool for companies to raise finance and are essential for a functioning modern economy.
[...] The data revealed investors made higher bids in sunny periods, which led to lower discounts for shares in the primary market. In fact, just a one standard deviation increase in sunshine intensity caused bid discounts to decline by 2.4 percent, while a one standard deviation increase in sunshine duration caused bid discounts to drop by 3.33 percent.
Professor Jia Liu, CISF Centre Director and Professor of Accounting and Finance at the University of Portsmouth, said: "With sunny weather, often come good spirits which in many circumstances is a positive, but that's not the case with financial decision-making. When the sunshine intensifies, bidders become overly optimistic and less risk-averse, which can lead to higher bid prices for seasoned equities."
Existing research has shown meteorological conditions, especially exposure to sunshine, affects a person's emotional state and sentiment. These weather-driven moods have been proved to influence a buyer's car choice, art prices at auction, and the tendency to take risks in a lottery.
[...] Professor Liu added: "We want to make investors aware that during periods of sunny weather, they become more optimistic about their investments. This will make them more inclined to take risks that aren't justified by asset values. Therefore, they should factor this consideration in when bidding for shares or they might suffer losses.
"Maintaining the stability of markets could depend upon our understanding of this phenomenon, since the onset of climate change might have an increasingly destabilizing impact on the judgment of investors and market-makers, with unpredictable consequences for global trading."
Journal Reference:
Qian Sun, Xiaoke Cheng, Shenghao Gao, Tao Chen, Jia Liu,
Sunshine-induced mood and SEO pricing: Evidence from detailed
investor bids in SEO auctions, Journal of Corporate
Finance, 80, 2023, https://doi.org/10.1016/j.jcorpfin.2023.102411
...
23:20
Britain: Teacher Scolded Pupil for Rejecting Classmates Claim That She Identified as a Cat cryptogon.com
Via: Daily Mail: A woke teacher has come under fire after telling a pupil she should go to a different school for rejecting a classmates claim that she identified as a cat. The pupil said she was made to stay after class by the teacher, who can be heard in a secret recording calling her []
23:17
IRC Proceedings: Sunday, June 18, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-180623.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-180623.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-180623.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-180623.gmi
Over HTTP:
|
... |
23:00
IBM expands collaboration with Adobe to help users navigate the complex generative AI landscape Help Net Security
IBM announced plans to expand its longstanding partnership with Adobe to help brands successfully accelerate their content supply chains through the implementation of next-generation AI including Adobe Sensei GenAI services and Adobe Firefly (currently in beta), Adobes family of creative generative AI models. Drawing on decades of AI experience, IBM Consulting is launching a new portfolio of Adobe consulting services to help clients navigate the complex generative AI landscape, bringing together innovation, technology and design More
The post IBM expands collaboration with Adobe to help users navigate the complex generative AI landscape appeared first on Help Net Security.
22:38
After Promoting Azure Every Day This Past Week Red Hat Exposes a Severe Weakness Techrights
Promoted by Red Hats official site this past Friday: (every day prior to this the Red Hat official Web site promoted Azure, as we noted in Daily Links)
Address change at Red Hat:
Summary: Looking closely at what Red Hat promotes under the guise of diversity, it turns out IBM lacks the office space to host a meeting; IBM has 288,300 employees worldwide compared to 221,000 at Microsoft (probably a lot less after this years mass layoffs), but together with Microsoft, the foremost opponent of GNU/Linux, Red Hat under IBM actively undermines the community and criticising this event would seem racist and sexist (IBM is against racists, even if its founder admired and saluted Hitler himself)
22:37
Researchers Discover New Sophisticated Toolkit Targeting Apple macOS Systems The Hacker News
Cybersecurity researchers have uncovered a set of malicious artifacts that they say is part of a sophisticated toolkit targeting Apple macOS systems. "As of now, these samples are still largely undetected and very little information is available about any of them," Bitdefender researchers Andrei Lapusneanu and Bogdan Botezatu said in a preliminary report published on Friday. The Romanian firm's
22:23
Homo sapiens is #9. Who were the eight other human species? Lifeboat News: The Blog
There were at least eight other human species, some of whom existed for far longer than we have. Who were they?
22:23
3D-printed superalloy could make power plants more efficient Lifeboat News: The Blog
A new high-performance metal alloy, called a superalloy, could help boost the efficiency of the turbines used in power plants and the aerospace and automotive industries.
Created using a 3D printer, the superalloy is composed of a blend of six elements that altogether form a material thats both lighter and stronger than the standard materials used in conventional turbine machinery. The strong superalloy could help industries cut both costs and carbon emissions if the approach can be successfully scaled up.
The challenge: In the world of materials science, the search for new metal alloys has been heating up in recent years. For over a century, weve depended on relatively simple alloys like steel, composed of 98% iron, to form the backbone of our manufacturing and construction industries. But todays challenges demand more: alloys that can withstand higher temperatures and remain strong under stress, yet still be lightweight.
22:22
Researchers develop new device that transforms vibrations into electricity for self-powered sensors Lifeboat News: The Blog
An international research group has engineered a new energy-generating device by combining piezoelectric composites with carbon fiber-reinforced polymer (CFRP), a commonly used material that is both light and strong. The new device transforms vibrations from the surrounding environment into electricity, providing an efficient and reliable means for self-powered sensors.
Details of the groups research were published in the journal Nano Energy on June 13, 2023.
Energy harvesting involves converting energy from the environment into usable electrical energy and is something crucial for ensuring a sustainable future.
22:03
Most Prolific World Cup Pirates Also Most Likely to Use a Paid Service TorrentFreak
 The World Cup only takes place every four years so when
the opportunity to see the worlds best players arrived again last
year, an estimated 1.5 billion eventually tuned in to see the elite
square off in the final.
The World Cup only takes place every four years so when
the opportunity to see the worlds best players arrived again last
year, an estimated 1.5 billion eventually tuned in to see the elite
square off in the final.
Millions cheered on the French national team as the defending champions pursued glory against Argentina. After the French lost in a dramatic penalty shoot-out, for some it became a tournament to forget. For French telecoms regulator Arcom, the end of the competition signaled the start of research to determine how citizens consumed World Cup 2022 and how France benefited from it financially.
World Cup 2022 Audiovisual Broadcasting Review
Published this week, Arcoms study reveals that more than six out of 10 French people watched or listened to at least one live match during the World Cup, a figure that rose to 73% in respect of all content, including replays, match analysis, and behind-the-scenes reporting.
Of those who watched live matches, 90% did so from home, with television the medium of choice for 96% of respondents. Around one in five football fans watched at least one match on a smartphone, with 14% and 7% viewing on computers and tablets, respectively.
Most Fans Watched Matches for Free
Football is traditionally seen as a sport of the people, with national teams serving their countries and citizens rather than their usual corporate paymasters. For these and similar reasons, some countries have laws or regulations in place that prevent the whole of the World Cup from being locked away behind TV subscription packages.
In France, all matches played by the national team must be broadcast on a widely accessible system, at no charge to the public. The same applies to the opening match, semi-finals, and the final, regardless of which teams are playing.
Free TV broadcaster TF1 won the rights to air these games in 2022 and, as a result, 87% of those who watched live World Cup matches did so on TF1, legally and for free.
Paywalls Guarantee Piracy
Of the 64 matches played in the tournament, 36 matches were broadcast exclusively by beIN Sports. Since users of beIN must have a subscription, piracy of World Cup matches was...
21:56
A third MOVEit vulnerability fixed, Cl0p lists victim organizations (CVE-2023-35708) Help Net Security
Progress Software has asked customers to update their MOVEit Transfer installations again, to fix a third SQL injection vulnerability (CVE-2023-35708) discovered in the web application in less that a month. Previously, the Cl0p cyber extortion gang exploited CVE-2023-34362 to grab enterprise data, and Huntress researchers discovered CVE-2023-35036 after partnering with Progress to perform a code review of the web app. About CVE-2023-35708 CVE-2023-35708 is a vulnerability that could lead to escalated privileges and unauthorized access. More
The post A third MOVEit vulnerability fixed, Cl0p lists victim organizations (CVE-2023-35708) appeared first on Help Net Security.
21:55
Revised Intel Shadow Stack Support May Be Ready For Linux 6.5 Phoronix
Intel engineers had sent in Shadow Stack support for Linux 6.4 as this feature part of Control-flow Enforcement Technology (CET) but it hit a last-minute snag during the merge window with issues raised by Linus Torvalds. Now it looks like the cleaned-up Shadow Stack code will be re-submitted for the upcoming Linux 6.5 cycle...
21:51
Introducing AI-guided Remediation for IaC Security / KICS The Hacker News
While the use of Infrastructure as Code (IaC) has gained significant popularity as organizations embrace cloud computing and DevOps practices, the speed and flexibility that IaC provides can also introduce the potential for misconfigurations and security vulnerabilities. IaC allows organizations to define and manage their infrastructure using machine-readable configuration files, which are
21:40
Microsoft Discloses DDoS Attack Impact with Limited Details HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
Microsoft has acknowledged that the crippling service outages in early June 2023 were caused by a DDoS attack apparently carried out by "Anonymous Sudan."
This is a post from HackRead.com Read the original post: Microsoft Discloses DDoS Attack Impact with Limited Details
21:01
Microsoft confirms DDoS attacks against M365, Azure Portal Help Net Security
The Microsoft 365 and Azure Portal outages users expirienced this month were caused by Layer 7 DDoS attacks, Microsoft has confirmed on Friday. The DDoS attacks against Microsoft 365 and Azure Portal Throughout the first half June 2023 Microsoft confirmed, at various times, ongoing issues with its cloud-based services Microsoft 365 (including Outlook on the web and OneDrive) and Azure Portal but did not say at the time that they were caused by More
The post Microsoft confirms DDoS attacks against M365, Azure Portal appeared first on Help Net Security.
21:00
Using Sonar To Measure Traffic Speeds Hackaday

One of the most common ways of measuring the speed of a vehicle is by using radar, which typically involves generating radio waves, directing them at a moving vehicle, and measuring the various ways that they return to the device. This is a tried-and-true method, but can be expensive and technically complex. [GeeDub] wanted an easier way of measuring vehicles passing by his home, so he switched to using sonar instead to measure speeds based on the sounds the cars generate themselves.
The method he is using is similar to passive sonar in submarines, which can locate objects underwater based on the sounds they produce. After a false start attempting to measure Doppler shift, he switched to time correlation using two microphones, essentially using stereo audio input to detect subtle differences in arrival times of various sounds to detect the positions of passing vehicles. Doing this fast enough and extrapolating the data gathered, speed information can be calculated. For the data gathering and calculation, [GeeDub] is using a Raspberry Pi to help keep costs down, and some further configuration of the microphones and their power supplies were also needed to ensure quality audio was gathered.
With the system in place in a window, it detected around 9,000 vehicles over a three-day period. The software generates a n...
20:30
GCC Lands AVX-512 Fully-Masked Vectorization Phoronix
Stemming from looking at the generated x264 video encode binary and some performance inefficiencies, SUSE engineers have worked out AVX-512 fully masked vectorization support for the GCC 14 development code...
20:12
Linux 6.5 Upgrading The Rust Toolchain, New Modules Added Phoronix
While the Linux 6.5 merge window isn't opening for another week, Rust for Linux lead developer Miguel Ojeda has already submitted the pull request of the new Rust kernel code destined for this next kernel cycle...
19:57
Open-Source Vulkan Driver Continues To Be Worked On For Old Radeon HD 6000 Series GPUs Phoronix
The "Terakan" Vulkan driver continues to be developed as an open-source Vulkan API implementation catering to the aging Radeon HD 6000 series graphics processors...
19:33
State-Backed Hackers Employ Advanced Methods to Target Middle Eastern and African Governments The Hacker News
Governmental entities in the Middle East and Africa have been at the receiving end of sustained cyber-espionage attacks that leverage never-before-seen and rare credential theft and Exchange email exfiltration techniques. "The main goal of the attacks was to obtain highly confidential and sensitive information, specifically related to politicians, military activities, and ministries of foreign
18:40
iPhone Maker Foxconn to Switch to Cars as US-China Ties Sour SoylentNews
iPhone maker Foxconn to switch to cars as US-China ties sour:
iPhone maker Foxconn is betting big on electric cars and redrawing some of its supply chains as it navigates a new era of icy Washington-Beijing relations.
In an exclusive interview, chairman and boss Young Liu told the BBC what the future may hold for the Taiwanese firm.
[...] "Look at this - this is a big iPhone, so we're very familiar with this," he said, pointing to a panel that controlled the car he had taken us for a drive in. Built for families and priced for an aspiring global middle class, the shiny white SUV is one of several models manufactured by Foxconn.
"The reason why we think this is a great opportunity for us is that with the traditional gas engine, you have engines which are mostly mechanical. But with EVs, it's batteries and motors," he explains. That is a familiar language for a technology company like Foxconn, he added.
Read more of this story at SoylentNews.
18:37
Microsoft Blames Massive DDoS Attack for Azure, Outlook, and OneDrive Disruptions The Hacker News
Microsoft on Friday attributed a string of service outages aimed at Azure, Outlook, and OneDrive earlier this month to an uncategorized cluster it tracks under the name Storm-1359. "These attacks likely rely on access to multiple virtual private servers (VPS) in conjunction with rented cloud infrastructure, open proxies, and DDoS tools," the tech giant said in a post on Friday. Storm-#### (
18:00
Teardown Of An Aircraft Video Symbol Generator Hackaday

[Adrian Smith] recently scored an avionics module taken from a British Aerospace 146 airliner and ripped it open for our viewing pleasure. This particular aircraft was designed in the early 1980s when the electronics used to feed the various displays in the cockpit were very different from modern designs. This particular box is called a symbol generator and is used to generate the various real-time video feeds that are sent to the cockpit display units. Various instruments, for example, the weather radar, feed into it, and it then reformats the video if needed, mixing in any required additional display.
17:48
Diicot cybercrime gang expands its attack capabilities Security Affairs
Researchers found evidence that Diicot threat actors are expanding their capabilities with new payloads and the Cayosin Botnet.
Cado researchers recently detected an interesting attack pattern linked to an emerging cybercrime group tracked as Diicot (formerly, Mexals) and described in analyses published by Akamai and Bitdefender.
The experts discovered several payloads, some of which were not publicly known, that are being used as part of a new ongoing campaign.
Evidence collected by Cado suggests the deployment of a botnet having DDoS capabilities.
The use of the name Diicot, which is also the name of a Romanian organized crime and anti-terrorism policing unit, and the presence of Romanian-language strings and log statements in the payloads suggests that the group could be based in Romania.
The Diicot cybercrime group has traditionally been associated with cryptojacking campaigns, but Cado Labs observed the group deploying the off-the-shelf Mirai-based bot known as Cayosin. The Cayosin bot employed in the attacks observed by Cado targeted routers running the Linux-based embedded devices operating system OpenWrt.
The group has distinctive TTPs such as the heavy use of the (using a header modified with the bytes 0x59545399) to prevent unpacking via the standard command (upx -d c).
Diicot heavily used Discord for C2, the platform supports HTTP POST requests to a webhook URL, allowing exfiltrated data and campaign statistics to be viewed within a given channel. Cado identified four distinct channels used in this campaign.
Diicot campaigns generally involve a long execution chain, with individual payloads and their outputs forming interdependent relationships. shc executables are typically used as loaders and prepare the system for mining via Diicots custom fork of XMRig, along with registering persistence. reads the report published by Cado. Executables written in Golang tend to be dedicated to scanning, brute-forcing and propagation, and a fork of the zmap i...
17:17
The Pre-play Attack in Real Life Light Blue Touchpaper
Recently I was contacted by a Falklands veteran who was a victim of what appears to have been a classic pre-play attack; his story is told here.
Almost ten years ago, after we wrote a paper on the pre-play attack, we were contacted by a Scottish sailor whod bought a drink in a bar in Las Ramblas in Barcelona for 33, and found the following morning that hed been charged 33,000 instead. The bar had submitted ten transactions an hour apart for 3,300 each, and when we got the transaction logs it turned out that these transactions had been submitted through three different banks. Whats more, although the transactions came from the same terminal ID, they had different terminal characteristics. When the sailors lawyer pointed this out to Lloyds Bank, they grudgingly accepted that it had been technical fraud and refunded the money.
In the years since then, Ive used this as a teaching example both in tutorial talks and in university lectures. A payment card user has no trustworthy user interface, so the PIN entry device can present any transaction, or series of transactions, for authentication, and the customer is none the wiser. The mere fact that a customers card authenticated a transaction does not imply that the customer mandated that payment.
Payment by phone should eventually fix this, but meantime the frauds continue. Theyre particularly common in nightlife establishments, both here and overseas. In the first big British case, the Spearmint Rhino in Bournemouth had special conditions attached to its license for some time after a series of frauds; a second case affected a similar establishment in Soho; there have be...
17:00
'Silent' killer in cholesterol more firmly linked to heart disease? Terra Forming Terra

otherwise, i would like to have far better answers than any of this which assumes the association is significant when it may well not be. Far too often meta stats throw up indications that are simply that and certainly no proof of causation..
Over-the-counter antihistamine repairs nerve damage caused by MS Terra Forming Terra
Meat's damaged DNA damages your own to raise cancer risk, says study Terra Forming Terra

15:00
The Remoteduino Nano is a Tiny IR Remote Thats Truly Universal Hackaday

Universal remotes are extremely convenient if they work correctly. But setting them up can be quite a hassle: often, you need to browse through long lists of TV models, key in the codes on the remote with just a blinking LED as confirmation, and then pray that the manufacturer included the correct codes for all your equipment. IR isnt a very complicated technology, however, so its perfectly possible to roll your own universal remote, as [sjm4306] shows in his latest project, the Remoteduino Nano. Its a fully programmable IR remote that gives you maximum flexibility when emulating the codes for those obscure A/V systems scattered around your home.
The remote runs on an ATmega328p in a tiny QFN package, which drives a standard 5 mm IR LED through a transistor. Eight buttons are available to the user, which can be freely mapped to any desired code. A five-pin header is included to program the ATmega through its serial port. However, this was mainly done to help debug a user who only needs to program the device once would typica...
14:30
Goodbyes are difficult, IT offboarding processes make them harder Help Net Security
When employees, contractors and service providers leave an organization, they take with them knowledge, capabilities, and professional achievements. They should leave behind any proprietary or confidential data belonging to the organization, but Osterman Research found that 69% of organizations polled have suffered a loss of data or knowledge upon the departure of an employee. This alarming finding points to a severe gap in one of the most sensitive, challenging and potentially dangerous stages of the More
The post Goodbyes are difficult, IT offboarding processes make them harder appeared first on Help Net Security.
14:04
Misconceptions Put Women Off STEM Subjects SoylentNews
Young women seem to be less drawn to degrees in science or technology. A sociological study has revealed that outdated gender stereotypes play a major role:
Why do so few female school leavers with good grades in mathematics choose to study a technical subject despite the high salaries and good employment prospects in the STEM sector? This question has long preoccupied the social sciences, especially as studies show that girls and boys do equally well in mathematics at school.
It is possible that socially embedded gender stereotypes play a role, such as: men think logically and in abstract terms, women are more creative; men should be the breadwinners, women take care of the family; men are competitive, women are more risk-averse. A study by Benita Combet from the Department of Sociology at the University of Zurich has now shown that some of these ingrained beliefs do indeed influence people's subject choices.
[...] "Especially with regard to factors such as logical thinking style and technical skills, strong gender stereotypes still exist, which obviously significantly influence the decisions of female high school students," says Combet. "We should therefore continue to work on challenging and questioning these fixed beliefs." With regard to analytical thinking, for example, it has by no means been scientifically proven that there are differences between men and women. Moreover, the ability to think analytically is a basic requirement for almost every subject area.
Combet also believes schoolchildren should be given better and more detailed information about future subject choices: "Many of their current perceptions are not accurate." For example, many believe that to be good at engineering, all you need is an affinity for technology. In fact, says Combet, "interpersonal and creative skills are also important in engineering, for example working in a team to develop new products."
Journal Reference:
require systemizing skills causes gendered field of study choice,
European Sociological Review, 2023; https://doi.org/10.1093/esr/jcad021
Read more of this story at SoylentNews.
14:00
How to simplify the process of compliance with U.S. Executive Order 14028 Help Net Security
In this Help Net Security video, Nick Mistry, SVP and CISO at Lineaje, offers tips to simplify the process of compliance with U.S. Executive Order 14028. A key part of U.S. Executive Order 14028 is for organizations that work with federal agencies to publish accurate Software Bill of Materials (SBOMs). But with hundreds of pages in the document, it can be challenging for even the most security-driven companies to distinguish precisely what is required to More
The post How to simplify the process of compliance with U.S. Executive Order 14028 appeared first on Help Net Security.
13:30
Exploring the role of AI in cybersecurity Help Net Security
In this Help Net Security round-up, we present parts of previously recorded videos from experts in the field that discuss about how AI technologies will impact the cybersecurity industry in the next few years. AI is a powerful tool in cybersecurity, adapting to emerging threats by analyzing data and improving detection. However, ethical considerations, privacy, and adversarial attacks must be addressed to maintain trust. AI will continue to play a vital role in safeguarding digital More
The post Exploring the role of AI in cybersecurity appeared first on Help Net Security.
13:00
Three cybersecurity actions that make a difference Help Net Security
Organizations that closely align their cybersecurity programs to business objectives are 18% more likely to achieve target revenue growth and market share and improve customer satisfaction, as well as 26% more likely to lower the cost of cybersecurity breaches/incidents, on average, according to Accenture. Driving successful outcomes The report identifies a group of companies that are leading the way in their cybersecurity efforts. These companies which Accenture calls cyber transformers and account for 30% More
The post Three cybersecurity actions that make a difference appeared first on Help Net Security.
12:30
Untangling the web of supply chain security with Tony Turner Help Net Security
Decades ago, Tony Turner, CEO of Opswright and author of Software Transparency: Supply Chain Security in an Era of a Software-Driven Society, faced an SQL Slammer worm. Having been one of the 75,000 infected users, he called upon his skills and risk management experience, to ensure his team will be ready for when the next attack comes. During his 25-year career in supply chain security and product security, he became an expert in engineering, security, More
The post Untangling the web of supply chain security with Tony Turner appeared first on Help Net Security.
12:00
Too Much Git? Try Gitless Hackaday

Git has been a powerful tool for software development and popularity since then. Originally built by none other than Linus Torvalds for handling Linux kernel development, its branched out for use with all kinds of other projects. That being said, it is not the easiest thing to learn how to use, with tons of options, abstract ideas, and non-linear workflows to keep track of. So if youre new to the system or dont need all of its vast swath of features, you might want to try out an alternative like Gitless.
Thanks to the fact that the original Git is open source, its free to modify and use as any user sees fit, and there are plenty of options available. This one aims to simplify many of the features found in the original Git, implementing a tracking system which somewhat automates commits. It also includes a simplified branching system, making it easier to switch between branches and keep better track of all thats happening in a project. The command line interface is simplified as well, and the entire system is backwards-compatible with Git which means that if you find yourself needing some of the more ad...
11:41
Links 18/06/2023: Slow News Weekend Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Monopolies
-
GNU/Linux
-
Kernel Space
...
-
11:36
Gemini Links 18/06/2023: Division, remainder, mod Techrights
![]()
Contents
-
Gemini* and Gopher
-
Personal/Opinions
-
SpellBinding: BKLYRUO Wordo: CURDY
-
Coffee
I drink too much coffee. Any time I pass coffee machine I get a double cup. Maybe 5 or 6 doubles through the day until evening.
I will try to take a break from coffee for 2 weeks starting today.
-
Alan Kays Dynabook
I recently stumbled about a PDF file detailing the Dynabook, a sort of personal mobile computer envisioned by Alan Kay in the seventies and oh boy, what he envisioned was lightyears away from todays locked town and appliance-ified smartphones.
-
Face Blindness
I dont remember when I learned about face blindnessbut I was glad I did, as I learned its not just me.
Face blindness is a condition in which the ability to recognize familiar facesto identify people by their faceis impaired.
According to Wikipedia the prevalence in the general population is 2.5%, so its not particularly rare.
-
Soylent Tea is People
I follow the youtuber The Spiffing Brit, because he is a fellow gamer and tea drinker with a good sense of humour and lots of fun game exploits.
He also likes OpenTTD and recently held an event where community members could participate in a match like no other.
The game had (its just been removed) a system for buying shares from other companies. This was rarely activated in multiplayer games because of how broken most players found it. In this case another community member had modded that system and much more of the code to allow for an experience never before possible in OpenTTD.
-
...
-
-
10:37
10:17
DistroWatch Weekly, Issue 1024 DistroWatch.com: News
This week in DistroWatch Weekly: Review: Debian 12News: Debian's releases updated Hurd port, Ubuntu 22.10 nears end of life, FreeBSD turns 30Tips and tricks: A safer way to use ddReleased last week: Voyager Live 12, risiOS 38, SparkyLinux 7.0, SysLinuxOS 12Torrent corner: IPFire, KDE neon, SparkyLinuxUpcoming releases: FreeBSD....
10:00
HPR3881: Xplane_VatSim_2022 Hacker Public Radio
https://github.com/freeload101/SCRIPTS/tree/master/VatSim_OLD Xplane11 This repo is dedicated to xplane plugin automation! VATSIM DOCS https://rmccurdy.com/.scripts/downloaded/VATSIM/TRAINING_CBT_ZAE_ZTL_BIBLE_S1_S2_20210402.zip Scenery Zhenhao Yang: https://forums.x-plane.org/index.php?/files/file/39173-atlanta-vfr/ https://simheaven.com/simdownloads/x-america/ https://forums.x-plane.org/index.php?/files/file/36327-us-orthophotos/ or https://verticalsims.com/vorthos/ logic: check for admin check for xplane binary have config file and folder for plugins/resources to be imported prompt install of stuff if found in the folders for Ortho4XP or alpilotx backup files to be modified automate Ortho4XP automate alpilotx automate common plugin installs (traffic / lighting / models/planes etc) Models: ZIBO 737-800 https://drive.google.com/file/d/1v-mBJ92EpV5sDPbH4s-T4EYmL2WQsZJf/view?usp=sharing Ultimate 737-700 Ultimate 737-900 Flight Factor B777-200LR Default B747-400 ??? Utilities: LiveTraffic Todo Plugins?: https://forums.x-plane.org/index.php?/files/file/50472-single-pilot-assistant-for-zibo-mod-737-800/&tab=reviews&sort=newest#review-81477 Autogate FlyWithLua ? Zibo 737-800x Headshake Vivid Sky Airport Environment HD Terrain Radar Avitab VFR Photo Scenery Aerosoft MegaAirports XTraffic XPFlightplanner XSquawkBox x-vision.pro FlyWithLua betterpushback betterpushbackc ?!? (not working for my build ) http://www.xsquawkbox.net/xpsdk/mediawiki/DataRefEditor PlaneCommand SomCoders Terrain Radar https://www.reddit.com/r/flightsim/comments/7tbcsh/shoutoutreview_forkboy2s_orthophotos/ ? https://forums.x-plane.org/index.php?/files/file/43314-webfmc/ Things to learn stab trim inop GPU/CPU tune https://www.x-plane.com/manuals/desktop/#settingtherenderingoptionsforbestperformance Help/FAQ: reset FMC by setting a new origin save views CTRL+NUMBERPAD recall NUMBERPAD Scenery ini
09:42
Soap2day Shuts Down Permanently Free Legal and Paid Alternatives HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
The online streaming website Soap2day has announced its permanent shutdown, ceasing its entire operation without providing a specific
This is a post from HackRead.com Read the original post: Soap2day Shuts Down Permanently Free Legal and Paid Alternatives
09:28
Kernel prepatch 6.4-rc7 LWN.net
The 6.4-rc7
kernel prepatch is out for testing. "Nothing particular stands
out in the rc this week, unless you count the mptcp selftest
changes that are about making the tests work on stable kernels
too.
"
09:18
New Linux and 24 Year Old Portable Hardware: No Problem SoylentNews
Contemporary linux runs well on decades-old portable hardware : https://raymii.org/s/blog/My_24_year_old_HP_Jornada_can_do_things_your_modern_iPhone_still_cant_do.html
They bother to cite NCommander, even:
NCommander has an excellent video on the 680e and the use of the device at the Dutch Railways (NS).
[hubie] An interesting short article for those who haven't repurposed a mobile device with a new operating system. The author notes:
Boy do I miss the good old days, where devices were programmable by their owners instead of just e-waste consumption slabs.
How many devices do you have lying in a drawer somewhere that are just fine hardware wise, but lack the software updates or development capabilities to be useful today?
[hubie] How often do you extend the life or repurpose retired mobile devices and how have you done it? Through advice and encouragement I got from the SN community, a few years ago I resurrected an old Samsung tablet by installing LineageOS and I use it all the time to play games I get off of F-Droid.
Read more of this story at SoylentNews.
09:17
Microsoft: June Outlook and cloud platform outages were caused by DDoS Security Affairs
Microsoft confirmed that the recent outages to the Azure, Outlook, and OneDrive services were caused by cyber attacks.
In early June, Microsoft suffered severe outages for some of its services, including Outlook email, OneDrive file-sharing apps, and the cloud computing infrastructure Azure.
A collective known as Anonymous Sudan (aka Storm-1359) claimed responsibility for the DDoS attacks that hit the companys services.
Threat actors relied on access to multiple virtual private servers (VPS) in conjunction with rented cloud infrastructure, open proxies, and DDoS tools.
Initially, the IT giant did not provide details about the outage, but now it has confirmed it was targeted by DDoS attacks in a report titled Microsoft Response to Layer 7 Distributed Denial of Service (DDoS) Attacks.
Beginning in early June 2023, Microsoft identified surges in traffic against some services that temporarily impacted availability. Microsoft promptly opened an investigation and subsequently began tracking ongoing DDoS activity by the threat actor that Microsoft tracks as Storm-1359. reads the report published by the company.
The attackers launched a series of powerful Layer 7 Distributed Denial of Service (DDoS) attacks.
The company pointed out that they have seen no evidence that customer data has been accessed or compromised. Microsoft enhanced layer 7 protections, including tuning Azure Web Application Firewall (WAF), to mitigate such types of attacks.
The company observed Anonymous Sudan launching several layer 7 DDoS attack traffic types, including HTTP(S) flood attacks, cache bypass, and Slowloris.
The report published by Microsoft also includes Layer 7 DDoS protection tips
Collective Anonymous Sudan has been active since January 2023, it claims to target any country that is against Sudan. However, some security researchers believe that Anonymous Sudan is a sub-group of the Pro-Russian threat group Killnet.
SpiderLabs cannot confirm that the group is based in Sudan, nor if any of its members are from that nation, but based on the evidence available, it seems quite likely that Anonymous Sudan is a Killnet project, possibly including some Eastern European members. states SpiderLabs.
Follow me on Twitter: @securityaffa...
09:00
Hackaday Links: June 18, 2023 Hackaday

Will it or wont it? Thats the question much on the minds of astronomers, astrophysicists, and the astro-adjacent this week as Betelgeuse continued its pattern of mysterious behavior that might portend a supernova sometime soon. Youll recall that the red giant star in the constellation Orion went through a great dimming event back in 2019, where its brightness dipped to 60% of its normal intensity. That was taken as a sign that perhaps the star was getting ready to explode or rather, that the light from whatever happened to the star 548 years ago finally reached us and was much anticipated by skywatchers, yours truly included. As it turned out, the dimming was likely caused by Betelgeuse belching forth an immense plume of dust, temporarily obscuring our view of its light. Disappointing.
Those who gave up on the hope of seeing a supernova might have done so too fast, though, because now, the star seems to be swinging the other way and brightening. It briefly became the brightest star in Orion, nearly outshining nearby Sirius, the brightest star in the sky. So what does all this on-again, off-again business mean? According to Dr. Becky, a new study not yet peer-reviewed, so proceed with caution s...
07:41
Linux 6.4-rc7 Released With The Quiet Cycle Continuing Phoronix
Linus Torvalds took time out of his Father's Day to release Linux 6.4-rc7 as the newest weekly test candidate for this kernel that's likely to be officially released next weekend...
06:25
Netflix and Amazon DMCA Notices Target Legal Streaming Options TorrentFreak
 Copyright holders send out millions of takedown notices a
day, hoping to remove pirated content or make it harder to
find.
Copyright holders send out millions of takedown notices a
day, hoping to remove pirated content or make it harder to
find.
The efficacy of the DMCA takedown process is open for debate, but it certainly doesnt help when companies flag legal websites as copyright-infringing.
It is particularly ironic when these mistakenly targeted sites are supposed to help the public find their way to the right streaming service. This is exactly what happened recently.
Netflix and Amazon Target Reelgood
Anti-piracy company Marketly, which handles DMCA takedown requests for many reputable rightsholders, repeatedly targeted URLs from the streaming search engine Reelgood. This Webby-award-winning service has nothing to do with piracy. Instead, it helps people to find sources to stream movies and series online legally.
Apparently, this rather important nuance wasnt picked up by the takedown software. As a result, several Reelgood pages have been removed from Googles search results.
One of the notices in question was sent in on behalf of Netflix. It lists a few hundred URLs that allegedly point to pirated copies of titles such as DAHMER, Cable Girls, Cursed, and Bridgerton.
In most cases the links indeed point to problematic sites but Reelgood is also thrown into the mix. Not just that; Google has also removed this page from its search results.
Another DMCA notice, sent by the same takedown outfit, aims to protect Amazon content. This includes URLs that point to pirated copies of Clarksons Farm, Britannia, and Bosch: Legacy. Again, Reelgood was erroneously included and removed from Google search.
Looking a...
06:00
Marvin Minskys 2500 Logo Computer Hackaday

[Prof. Marvin Minsky] is a very well-known figure in the field of computing, having co-founded the MIT AI lab, published extensively on AI and computational intelligence, and, lets not forget, inventing the confocal microscope and, of course, the useless machine. But did you know he also was a co-developer of the first Logo turtle, and developed a computer intended to run Logo applications in an educational environment? After dredging some PDP-10 tapes owned by the MIT Media Lab, the original schematics for his machine, the Turtle Terminal TT2500 (a reference to the target price of $2500, in 1970...
05:35
Reddit Files: BlackCat/ALPHV ransomware gang claims to have stolen 80GB of data from Reddit Security Affairs
The BlackCat/ALPHV ransomware gang claims to have stolen 80GB of data from the Reddit in February cyberattack.
In February, the social news aggregation platform Reddit suffered a security breach, attackers gained unauthorized access to internal documents, code, and some business systems.
The company announced it was hit by a sophisticated and highly-targeted attack that took place on February 5, 2023. A highly-targeted phishing attack hit the employees of the company. The company pointed out that Reddit user passwords and accounts were not compromised.
The spear-phishing messages redirected users to a website mimicking the companys intranet gateway, the landing page was designed to trick victims into providing credentials and second-factor tokens.
On late (PST) February 5, 2023, we became aware of a sophisticated phishing campaign that targeted Reddit employees. As in most phishing campaigns, the attacker sent out plausible-sounding prompts pointing employees to a website that cloned the behavior of our intranet gateway, in an attempt to steal credentials and second-factor tokens. reads a notice published by the company.
Once obtained a single employees credentials, threat actors gained access to some internal docs, code, as well as some internal dashboards and business systems. The primary production systems of the company were not compromised.
Exposure included limited contact information for (currently hundreds of) company contacts and employees (current and former), as well as limited advertiser information. continues the notice. Based on several days of initial investigation by security, engineering, and data science (and friends!), we have no evidence to suggest that any of your non-public data has been accessed, or that Reddits information has been published or distributed online.
The company states that the phished employee self-reported and launched an internal investigation to determine the extend of the incident. The Security team responded quickly to the incident by locking out the intruders.
Now the BlackCat/ALPHV ransomware gang claimed responsibility for the February cyberattack on the company. The cybercrime gang claims to have stolen 80GB of data (zipped) from Reddit. The group attempted to contact Reddit twice, on April 13 and June 16, without success.
05:15
Temporary Phone Number: An Essential Tool for Privacy Protection HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
In an era where our lives are increasingly interconnected with the digital world, safeguarding our privacy has become
This is a post from HackRead.com Read the original post: Temporary Phone Number: An Essential Tool for Privacy Protection
04:58
IBM Responds to Techrights Report (Citing Inside Sources): No, We Did Not Kill OpenSource.com, We Cannot Explain What We Did Techrights
Almost 2 weeks ago:
6 days ago:
Summary: Playing fast and loose with the word community (which was attacked systematically after the Red Hat takeover) IBM decided to issue an intriguing and vague statement the day after Techrights had blasted it for what it had done to OpenSource.com [1, 2, 3] and OpenOffice.org/LibreOffice (the Techrights article reached a vast audience); based on the timing, there was almost certainly a correlation; almost a fortnight has passed and IBM has said absolutely nothing since the above blurb
04:39
Dr. Peter Hotez Refuses To Debate RFK Jr. Despite $1.5 Million Charity Pot cryptogon.com
Via: ZeroHedge: With Dr. Fauci having exited stage left, the MSMs has anointed a new vax-peddling talking head Dr. Peter Hotez. Last week, podcast giant Joe Rogan had Hotez on his show, where he proceeded to badmouth anti-vax presidential candidate Robert Kennedy Jr. before telling Rogan that hed be uncomfortable debating him.
04:35
Megaupload Duo Plead Guilty in NZ to Avoid US Extradition SoylentNews
Kim Dotcom still fighting decade-long battle to avoid being shipped to US over copyright abuse:
The decade-long legal brawl over cloud storage locker Megaupload has moved a little closer to resolution after two of the outfit's execs pled guilty to a variety of charges.
Megaupload, fronted by colorful entrepreneur Kim Dotcom, offered users the chance to upload files and store them in a cloud. Files could then be made available to other members. The outfit's heyday was the mid-2000s a time when plenty of content was available using BitTorrent and before content streaming services offered easy and affordable access to content online.
[...] Big Content of course deluged Megaupload with copyright-related lawsuits, which have been rumbling along for over a decade as Dotcom and his associates argued they should not be held responsible for users' uploads.
US authorities and Big Content have pointed to Megaupload's payments to uploaders of stolen content as evidence the outfit intended to profit from copyright abuse. They attempted to extradite Dotcom and his associates from New Zealand to face American courts.
Yesterday, two of those associates Mathias Ortmann and Bram van der Kolk, both programmers for Megaupload pled guilty in New Zealand's High Court.
Read more of this story at SoylentNews.
04:26
AMD is Not a Community and Michael Larabel Is Not Objective Techrights
Published yesterday:
AMD tweets (Elon Scam Musk-controlled quips) as sources:
Brought to by recipient of AMD 'gifts' aplenty:
Summary: Objectivity in Linux-centric media continues to wane. Follow the trail of money/gifts.
04:01
There is No Such Thing as Cryptocurrency and Please Stop Referring to It as Cryptocurrency Techrights
Summary: A lot of reckless media, including the journal of record New York Times, helps a bunch of spammers and scammers hijack and distort words in order to promote theft
THE scam that is cryptocurrency has cost my friend his life savings. Hes in his 60s, a university professor. For nearly a year he was too shy to tell his friends what had happened. It was embarrassing. He fell for it. He should have asked friends. Earlier today a friend told me that crypto is cryptography, whereas cryptocurrency is a scam + waste of electricity (a sentiment with which I agree).
Say what you will about the international/global banking system (yes, it is corrupt), but the alternative to it isnt some charlatans or frauds, boosted online by bros in social control media. Get rich fast schemes have long relied on misinformation, more so or especially relying on much-deserved distrust (alluding to traditional banks and governments). Having an alternative to something does not mean the alternative is better or safer. My above-mentioned friend was scammed by cryptocurrency charlatans through Microsofts LinkeIn, which is social control media where corruption flourishes. No wonder, its controlled by a company where scams are business as usual (Microsoft).
Binance should be shredded to pieces and these pieces then be scattered into the deepest ocean.Earlier today we saw that the Securities and Exchange Commission (SEC) agreed to let Binance be [1]. Were not happy about this. Binance should be shredded to pieces and these pieces then be scattered into the deepest ocean. Banks in the US are collapsing and certainly more American banks will collapse by the end of the year. Binance might also collapse, just like FTX and the scam of Jim Zemlins wife [1, 2,...
03:23
Daniel Ellsberg Taught Us That Making Powerful People Angry and Anxious is Good For Society at Large Techrights
Summary: A parting word to Mr. Ellsberg, who helped stop needless militarism and saved many lives by doing so
THE news that Daniel Ellsberg is dead was mentioned here several times yesterday, not only in Daily Links but in articles.
Daniel Ellsberg did not die so suddenly or unexpectedly. He anticipated this because of a medical diagnosis dating months back. He even had the chance to say goodbyes and give last interviews.
Mr. Ellsberg is celebrated among haters of US militarism [1], stressing that Ellsbergs renown for openly challenging the mentalities of militarism began on June 23, 1971, when he appeared on CBS Evening News ten days after news broke about the Pentagon Papers that hed provided to journalists. [2]
He is also celebrated among haters of Russian and Chinese militarism, hypocrites like New York Times who promoted an invasion of Iraq based on lies [3].
The German national broadcaster paid tributes [4] and weve given many more references in Daily Links, including especially touching pieces [5]. Mr. Ellsberg was very much liked among sites that we like and follow closely.
Speaking truth to power, even at great personal risk, is typically worth it. Ive received more threats than I can count from the EPO, even as recently as months ago. Benot Battistelli and Antnio Campinos are basically criminals. They surround themselves by other criminals (enablers). Telling the truth about them isnt easy because you receive threats and you must even explain to the spouse why envelopes appear around or right at the doorstep, issuing terrifying statements.
You only live once. Everyone lives once. No person ever lived more than once. Do the most of your time on this planet. Try to make the planet better. Mr. Ellsberg made the world better. Rest in peace and thank you.
Related/contextual items from the news:
-
Dan Ellsbergs Parting Plea: Dont Wait
Sam Adams Associates for Integrity honored the...
03:14
Direct Construction of Aperiodic Tilings with the Hat Monotile, by Ulrich Reitebuch.
libmceliece is a Classic McEliece microlibrary, by Daniel J. Bernstein and Tung Chou.
Rash is a shell language, library, and REPL for Racket.
Tech debt metaphor maximalism, by Avery Pennarun.
REFAL () was created in Russia, then USSR, in the second half of the 1960s. It is a functional programming language in which computation is driven by pattern matching on textual and symbolic information. Manual. Refal Plus. Refal 5.
The Joy Of Duplexes, by Coda Hale. In this post, well talk about permutations, sponge functions, and duplexeswhat they are, how theyre built, what makes them secure, and how theyre used.
An archive of the GNU arch-verse, provided by Patrick Georgi in remembrance of Tom Lord.
I booted Linux 292,612 times and follow up, by Richard WM Jones.
Update: U+237C &angzarr, in search of the origins of a glyph.
02:59
Techrights Statement on Paths Ahead in the Era of News Drought and Widely-Waning Web Techrights
Summary: Were striving to get into a habit of publishing about a dozen blog posts per day; in order to do this we change our strategy with immediate effect
YESTERDAY we wrote about the need to pause and rethink how we do articles and how we curate Daily Links. Weve since then experimented with a new approach and published about half a dozen articles with many recent references in each.
This site is turning 17 in a few months. It did change (it evolved) a lot over the years. Daily Links turned 15 this past February and IRC turned 15 about a month ago.
It is with that in mind that we:
- Pause our old approach of gathering news links (too low a signal-to-noise ratio in them).
- prioritise writing new articles, even if that means fewer batches of Daily Links
- Prepare videos where video presentation is more suitable and desirable than textual form
Were in the privileged position of enjoying greater personal freedom than ever before (when this site started in 2006 I was still a Ph.D candidate working on my thesis, later I worked part time and then full time). Wed like to make best use of time to promote Software Freedom and to advance justice, with greater focus on science and technology matters rather than pure politics.
Social control media is in disarray at the moment (several large platforms are collapsing, not exactly for the same reasons). We hope that many of the escapees will end up self-hosting and, better yet, adopting Gemini.
In recent years weve been producing over 3,000 blog posts (with analogous GemLog posts) per year and we should be able to do over 4,000 a year if we adopt the correct strategy. Priorities need to change somewhat. We have some exciting (to me us least) plans for the next 5-10 years; theyre not limited to the World Wide Web, so the fate of the Web does not matter so much to us (were resistant to the Webs demise; all our articles are in IPFS, GemText, plain text and more). We have hitherto identified where a lot of time was being (mostly) wasted and we will work to correct those older habits and hopefully exceed a dozen blog posts per day once the dust settles.
The Web is getting smaller (yes, weve provided evidence over the years that it is shrinking over time), search engines rapidly deteriorate in terms of quality (the reasons for this merit a discussion some other day, in isolation), and newsrooms collapse at an alarming rate, with editors forced to resign from widely-known news sites almost every week. These trends seem irr...
01:00
Qubit Quest Takes a Topological Turn IEEE Spectrum

The math that explains why a donut is really the same shape as coffee mug but not a waste bin could be the key to making quantum computers practicable. Two teams of researchers have used topology, a centuries-old field of mathematics, and a new kind of quasiparticle to come up with an error-correction technique for quantum computers that could leave others developed to date in the bin.
Error-correction systems are essential to quantum computers, because the unprotected quantum bit (qubit) is such a perpetually delicate thingoften a single particle or quantum state that is forever at the mercy of thermal or random noise in the system. And because qubits are typically quantum mechanically interconnected with one anotherto use the jargon, qubits are typically entangledknocking just one or two out of commission can affect the whole system.
The hunt for the best quantum error-correction systems today takes many forms. Quantum error-scrubbing prototypes, techniques, and inventions regularly emerge from labs, startups, and aspiring quantum-computing behemoths around the world. But a new development harnesses a long-elusive quasiparticle whose behaviors might be bent to suit the most pressing needs of the perpetually finicky qubit. Two companiesGoogles Quantum AI unit and the Broomfield, Colo.based startup Quantinuumnow vie for discovery rights to a quantum entity...
Sunday, 18 June
19:58
22bet Nigeria Evaluation Login To Get 50,000 Ngn Bonus h+ Media
22bet Nigeria Evaluation Login To Get 50,000 Ngn Bonus
While 22Bet doesnt have an official cellphone quantity for support, you can still get prompt customer assist using the stay chat performance thats built into the platform. Congratulations, you have passed 22Bet registration, and now you can even make predictions in your favorite sports and play unbelievable video games. The subsequent time you need to visit the positioning, you simply must log into your account with your 22Bet login and password. 22Bet NG login is processed as fast as possible to save tons of you time. You can start the 22Bet on line casino Login process instantly on the web site or cell app.
22Bet is an all-rounded betting platform and loads of choices additionally mean more enjoyable and leisure. They respond to questions promptly with options for stay chat, e-mail, cellphone assist, including social media. Customer support is essential, and its a factor you must pay attention to.
Accumulators assist bettors to get some a half of their cash and to keep away from total loss on predicted game outcomes. There is an option to learn the ropes of how an accumulator works before dabbling into it. To qualify for this welcome bonus, you need to register on the site, get verified, and make a deposit following the minimum deposit which is 400NGN. Your bonus could be credited into your account automatically once your stability has been replenished. Note that the bonus itself should be wagered 50x before you presumably can claim all of your rewards, but simple peasy it is.
These embody basketball, tennis, volleyball, ice hockey, desk tennis, handball, American soccer, and extra. With every sport, you might be certain to seek out huge betting options. Better but, the chances on nearly all of markets are competitive, and this ensures that you just get value in your successful bets.
The critiques and feedback of users left on the positioning are on their very own duty and arent related to our groups work in any means. All content material revealed on Betting Africa is acknowledged as region-specific and applicable to Nigeria only. This possibility allows you to choose totally different outcomes from multiple video games. For instance, you can predict events from multiple sports like baseball, basketball, etc.
You can even select the full registration method, which requires you to enter your e mail and full names. Once you might have your Nigerian cellphone number, you presumably can easily sign up by way of the cellphone registration technique. The very first thing to do if you want to bet on 22Bet is to enroll on the site. Now check that the forex is ready at Nigerian naira, and enter a promo code when you have one. Enter your affirmation code within the area supplied on the 22Bet registration type and click Confirm. 22Bet registration by cellphone quantity is the quickest approach to open a 22Bet account in Nigeria...
Friday, 16 June
18:51
May England Take A Look At Coach Brendon Mccullum Be Banned For Ties With Gambling Firm 22bet? Ecb Investigation On h+ Media
May England Take A Look At Coach Brendon Mccullum Be Banned For Ties With Gambling Firm 22bet? Ecb Investigation On
There are nonetheless some good names on the roster and their experience ought to show useful on this match towards Gloucestershire. Middlesex are usually good when batting within the later overs and have reliable names scattered by way of the order, so they need to get this victory. Lets briefly check out the distinguished options and functionalities of the 22Bet app within the following part.
22Bet holds a gaming license with Curacao (license number 8048/JA) and uses SSL encryption to protect its clients and their information. 22Bet India is an online sportsbook, established in 2017. Players can enjoy its great on-line betting offers with sporting markets from all over the world, high odds, plus quick payouts. This on-line venue is legal, it is registered with Curacao Gambling Authority.
A Multibet with a Lobby is a combination wager that mixes both a Lobby wager and a system wager with several selections. A bet slip will have to have three or more decisions so as to be considered a Multibet. 22Bet options 9 completely different guess varieties that you ought to use to maximise your winnings from a selection of sports occasions. You can discover some of the hottest ones down below, along with brief descriptions of each one. Keep in thoughts that the bonus is only legitimate for accumulator wagers on no much less than three sporting occasions. Withdrawals from the client account arent possible until the wagering criteria have been satisfied and the bonus has been wagered seven instances.
Here, the display on which you might be enjoying will be divided into 3 or four sections. The possibilities of you successful might be increased by using this function supplied by 22bet. This is a critical 22bet evaluation that touches all of the sectors. This sports betting site is a fantastic on-line venue; I highly suggest it if youd like not simply to wager however to win. I at all times select 22Bet in terms of my sports betting.
Tap on withdrawal. Select the Withdrawal option from the tab of your system after initiating a login with your account. The spotlight of 22bet withdrawal India is the variety of transaction methods out there in it. Along with the most popular game in India, Cricket, many other sports activities are available in 22bet.
At StarPick, we suggest 22Bet as an excellent betting site that India gamblers can use. As a model new customer at 22Bet, you stand an opportunity to say the operators welcome bonus in your first deposit. There are two completely different kinds of welcome bonuses provided; one for sports betting and the other for the web on line casino section.
The bonus will be locked into your Bonus Wallet after successful software. Launch the 22bet app from the menu on your mobile device in a single click on. If youve forgotten your...
18:51
22bet Evaluate India 2023 h+ Media
22bet Evaluate India 2023
On the page of the chosen match, you may be given a wide choice of markets for your bets. 22bet requires a registered account to make monetary transactions and play for real cash. Creating an account is feasible each via the official web site and the Android and iOS applications. On this page, you will find detailed instructions for profitable registration. At 22Bet in the sportsbook, you might place nets utilizing a selection of wager varieties on virtually three,000 events which are provided every day across a variety of sports activities.
Specialists will consider your request on a first-come-first-served foundation. Once the verification process is full, you will be notified through email. Upload photographs of the paperwork confirming your identification and address to the e-mail of 22bet assist service. Make certain that the info indicated on the documents coincide with the information you entered in your private profile. The vendor spins the roulette wheel whereas the ball is being spun throughout it. If you wager on the world the place the ball falls, you might win.
And, fortunately, for Indian customers, it emphasizes cricket, with an entire sportsbook dedicated to it, in addition to other broadly performed sports in India, like basketball and desk tennis. See what you might guess on by trying at the events talked about below. Only single bets and accumulators are offered on this promotion (TOTO bets, system and chain bets, and bets with odds greater than 3.00 dont qualify for the bonus). The betting markets are classes of potential bets on specific occasions.
A handy chat button can always be discovered within the backside right-hand nook of the website. Clicking this button will connect you on to 22Bet customer assist. The stay chat feature is often essentially the most environment friendly channel for such buyer help. However, the amount of time it takes from requesting your funds to them arriving in your chosen account varies depending on the withdrawal methodology. We discovered the deposit course of for making a payment at 22Bet friendly and accessible.
So , in easier text, youre going to get a broad variety when ever deciding on a meet to speculate on. They absolutely have strongest casino video games just like black jack and associated other card video video games that you could play everytime you want. You might need to have some abilities to discover a way to get these recreation titles.
The other kinds of extra bonuses which youll find a way to instantly declare embrace advance payment extra, match-up additional, free spins and a lot of extra. 22Bet utility is licensed by the Curacao gaming which is among the many trusted gaming proper and the playing app employs dependable and protected information well being and security and price gateways. Certainly, 22Bet app is legal in India since it can primarily based exterior surfaces of Indi...
18:51
22bet Evaluation India 2023 h+ Media
22bet Evaluation India 2023
On the web page of the chosen match, you might be given a large alternative of markets for your bets. 22bet requires a registered account to make monetary transactions and play for real money. Creating an account is feasible both through the official web site and the Android and iOS functions. On this page, you can see detailed directions for successful registration. At 22Bet in the sportsbook, you might place nets using a quantity of bet kinds on almost 3,000 occasions that are supplied every day throughout a wide range of sports.
- Once you complete your first-time deposit, go to My promotion page, search for 200% Evolution Welcome Bonus Limited Claims Daily and click on Apply.
- News and opinion web site that brings you reviews and narrative from a perspective often ignored or suppressed by the mainstream media of India.
- Whatever question you have, you presumably can fill in 22Bets kind on the web site and youll get a reply inside 24 hours.
- Bonuses are one of many main attractions of a sports betting website, 22bet.
- Make a minimal deposit or greater than that to get the bonus.
- You shall be presented with the available deposit options, and you can select the one which best suits your choice.
Leicestershire staff batted first and succeeded in scoring 166 runs for the lack of 7 wickets in their stipulated quota of 20 overs. Birmingham Bears succeeded in chasing down this complete simply with 5 wickets to spare and with 15 balls remaining. It was a below-par goal set by Leicestershire on a wonderful batting wicket. Worcestershire goes into this game with a couple of wins under their belt. This is certain to have their players in a more confident state of mind.
The apparent starting point for this 22 guess review is with the selection of matches which are made obtainable. As you would count on, the corporate covers the most important games of all, and theres a strong give attention to India. International fixtures and matches from the IPL will appeal to lots of curiosity, and theyll often be moved to the top of the page. One thing we especially liked about this bookie is the banking department.
The reside customer help chat can take some time to join to an agent. Indian gamers can use Hindi as the site language, which improves accessibility. Not solely world giants, desi entrepreneurs are also trying to get a chunk of the pie. They are attracting smartphone customers with specifically designed apps. The reaction in India where 400 million users exchange extra messages on WhatsApp than wherever in the world has pressured the messaging app to unleash an promoting blitz. Contact MethodResponse TimeEmailUp to 24 hoursPhoneN/ALive ChatInstant 5 minutesAs youll have the ability to see, theres no phone assist obtainable at 22bet, which is a shame.
McCu...
18:51
Ecb Trying Into Take A Look At Coach Brendon Mccullums Relationship With 22bet India h+ Media
Ecb Trying Into Take A Look At Coach Brendon Mccullums Relationship With 22bet India
7cric reserve the right to amend, cancel and reclaim or refuse any promotion at its personal discretions. Once you complete your first-time deposit, go to My promotion web page, look for 250% Spribe Aviator Welcome Bonus Limited Claims Daily and click on Apply. Once you complete your first-time deposit, go to My promotion page, look for 250% Sports Welcome Bonus Limited Claims Daily and click Apply. The Bonus is locked in the Bonus wallet till the Rollover requirement is fulfilled.
Once once more, this is a 100 percent match on your opening deposit but this time it could possibly climb as a lot as a most determine of 10,000 INR. Youll have to know the way to use the 22bet welcome bonus so lets begin by signing up for a new account. You can definitely benefit from offers and promotions at 22Bet India, and these are available for the lifetime of your account. Well start this section of the 22Bet cricket review by taking a glance at what deals are on the desk for existing clients.
At StarPick, we recommend 22Bet as a good betting web site that India gamblers can use. As a new customer at 22Bet, you stand a chance to assert the operators welcome bonus in your first deposit. There are two totally different kinds of welcome bonuses offered; one for sports activities betting and the opposite for the web on line casino section.
There is a restricted amount of live betting featured for the customers. However, theres a lack of promotions and other bonuses on the net site. It is necessary for the authority to do promotions and supply bonuses every so often to keep the person interested within the web site. It has more than 50 different sorts of sports and more than a thousand types of betting available in India. If you are the sort of one that likes to place bets on different kinds of sports then this app might be useful for you.
- Once you select a selected race on the betting website, you will see the racecard as well as details about the horses.
- You can by no means go wrong with an interactive stay supplier game.
- Having reliable buyer assist to enhance your experience is essential.
- The welcome bonus is a 100% match of the deposit amount, which could reach as high as 25,000 INR.
- Once you full your first-time deposit, go to My promotion page, look for 250% Sports Welcome Bonus Limited Claims Daily and click on Apply.
If you are looking for an online casino that caters particularly to Indian players, look no further than 7Cric. This web site is presently probably the greatest choices for real money casino video games, with over 2000 totally different video games obtainable. 7Cric also offers gamers with a secure and safe setting by which to gamble, wit...
18:51
Middlesex Vs Gloucestershire 22nd Match h+ Media
Middlesex Vs Gloucestershire 22nd Match
It states that every side must keep away from intentional damage or obtain a warning of harm and factors deduction. The different aspect shall be credited 5 runs as compensation for every subsequent incident that would have been avoided. You can anticipate them to get greater than 6 runs in the first over. Worcestershire openers to get more than 6 runs in the first over of their innings. You can wager on him to score greater than 24 runs on this encounter. Michael Bracewell to score in extra of 24 runs in the match.
Now, Choletti is in talks to affix Tata Digitals funds enterprise. A South Korean ladys optimistic evaluation on Zomato helped enhance the score of a poorly rated restaurant in Jaipur, India, exhibiting the impact of on-line evaluations on small businesses. No info contained on the SevenJackpots.com website is intended for unlawful functions. This material is for general information solely and is not intended as legal advice and no responsibility of care is owed to any reader. The readers of this materials are requested to interact their very own authorized counsel in order to make any legal or enterprise selections and to acquire authorized recommendation particular to them.
Access to playing products could also be restricted in certain states. Please be positive that your use of the products complies with the applicable legal guidelines in your area. [newline]Not obtainable for residents of the State of Andhra Pradesh, Meghalaya, Nagaland, Sikkim, Tamil Nadu, and Telangana. The 22Bet app download also is obtainable in quite so much of languages. Some of those languages embody German, Greek, Finnish, Spanish, Russian, Polish, Turkish, and more.
Apart from Charlesworths fifty six runs and Dents 55 runs, there wasnt a lot to be enthusiastic about in either of Gloucestershires first two video games. Considering that that they had a good batting effort in 2022, we hoped rather more from Jack Taylor and James Bracey, but both have combined for 24 runs across two matches very poor. Bet 2 play, Bet 2 win, he has captioned one of his videos.
The website was created by a group of betting veterans who joined forces to offer a service from a customers perspective. As for payout, every withdrawal request is manually checked by 22Bet employees. Although opinions differ right here, youve a reasonable processing time of two business days. The platform is the holder of a betting legal license issued by the federal government of Curacao, Curaao eGaming License. It is thus a proven and secure portal that can provide its providers legally.
The number of correct bets of your TOTO guess slip will resolve the quantity you win from the TOTO prize pool. Selected 22Games contribute 200% to the wagering requirement. Wagering requirement needs to be met inside seven days after deposit. Completing an account verification is customary in any...


























![Empowering change through DEI: Red Hats women in technology event highlights role models and success stories: On Jun. 7, Red Hat hosted its annual Women in Technology event [...] From the venue in the Microsoft Canada head office on the 43rd floor of 81 Bay Street](../../techrights.org/wp-content/uploads/2023/06/mirosoft-redhat.png)












