| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Thursday, 07 December
17:55
We've added another 10 new text tools catonmat.net
Team Browserling keeps shipping!
Five weeks ago we added 50 new text tool.
Four weeks ago we added 20 more tools.
Three weeks ago we added 15 more text tools.
Two week we added 15 more text tools.
Last week we added 10 more text tools.
And today we just added another 10 tools to our Online Text Tools collection.
Here are the new text tools.
- Generate Skip-grams
- Quote Words in Text
- Print Text Statistics
- Visualize Text Structure
- Highlight Letters in Text
- Highlight Words in Text
- Highlight Patterns in Text
- Highlight Sentences in Text
- Highlight Regex Matches in Text
Next week we'll add even more tools. See you then!
Thursday, 23 November
17:10
We've added another 20 new math tools catonmat.net
Team Browserling keeps shipping!
Last week we added 25 new math tools and today we just added another 20 new tools to our Online MATH Tools collection.
We've done our job and now it's Google's job to index them and rank them well.
Here are the new math tools:
- Generate Triflake Curve
- Generate Quadratic Cross Fractal
- Generate Vicsek Curve
- Generate T-square Curve
- Generate Sierpinski Carpet
- Generate Sierpinski Maze
- Generate Sierpinski Square
- Generate Sierpinski Pentagon
- Generate Sierpinski Hexagon
- Generate Sierpinski Polyflake
- Generate Cantor Set
- Generate Asymmetric Cantor Set
- Generate Generalized Cantor Set
- Generate Smith-Volterra-Cantor Set
- Generate Cantor Dust
- Generate Pythagoras Tree
- Generate Fibonacci-word Fractal
- Generate H-Fractal
- Generate V-tree Fractal
- Generate Heighway Triangle
Next week we'll add even more tools. See you then!
Thursday, 09 November
18:40
We've added 25 new math tools catonmat.net
Team Browserling keeps shipping!
Last week we added 25 new png tools and today we just added 25 new tools to our Online MATH Tools collection.
We've done our job and now it's Google's job to index them and rank them well.
Here are the new math tools:
- Generate Pascal's Triangle
- Find All Divisors of a Number
- Find Prime Factors of a Number
- Test if a Number is a Prime Number
- Test if a Number is a Fibonacci Number
- Generate Abundant Number Sequence
- Generate Deficient Number Sequence
- Generate Almost Perfect Numbers
- Generate Moser-de Bruijn Sequence
- Generate Even Number Sequence
- Generate Odd Number Sequence
- Generate a Random Matrix
- Generate an Identity Matrix
- Add Matrices
- Subtract Matrices
- Generate Twindragon Curve
- Generate Terdragon Curve
- Generate Quaddragon Curve
- Generate Hexadragon Curve
- Generate Koch Antisnowflake
- Generate Koch Triangle
- Generate Koch Polyflake
- ...
Wednesday, 24 May
00:49
PyPI removes PGP-signature support LWN.net
The PyPI package archive has removed support for PGP signatures on packages.
In other words, out of all of the unique keys that had uploaded signatures to PyPI, only 36% of them were capable of being meaningfully verified at the time of audit. Even if all of those signatures uploaded in that 3 year period of time were made by one of those 36% of keys that are able to be meaningfully verified, that would still represent only 0.3% of all of those files.Given all of this, the continued support of uploading PGP signatures to PyPI is no longer defensible.
00:42
Google announced its Mobile VRP (vulnerability rewards program) Security Affairs
Google introduced Mobile VRP (vulnerability rewards program), a new bug bounty program for reporting vulnerabilities in its mobile applications.
Google announced a new bug bounty program, named Mobile VRP (vulnerability rewards program), that covers its mobile applications.
Googles Mobile VRP is a bug bounty program for reporting vulnerabilities in first-party Android applications developed or maintained by Google.
Only apps published by the developers in the list below or apps in the Tier 1 list (Googles Play Services, AGSA (Android Google Search app), Chrome, Cloud, Gmail, and Chrome Remote Desktop) are in covered by the new program:
- Google LLC
- Developed with Google
- Research at Google
- Red Hot Labs
- Google Samples
- Fitbit LLC
- Nest Labs Inc.
- Waymo LLC
- Waze
The IT giant will reward arbitrary code execution vulnerabilities and flaws that can lead to the theft of sensitive data. The company is also looking for:
- Path traversal / zip path traversal vulnerabilities leading to arbitrary file write
- Intent redirections leading to launching non-exported application components
- Vulnerabilities caused by unsafe usage of pending intents
- Orphaned permissions
Below is the table reporting the rewards offered by the company for the different categories of vulnerabilities and the level of user interaction for their exploitation:...
00:39
13 Minutes of COVID Propaganda cryptogon.com
Via: Ivor Cummins:
00:23
Artificial Intelligence Explosion: How AI May Cause The End of The World?? Lifeboat News: The Blog

Artificial intelligence is a superior lifeform that humans are creating, and many AI researchers have outlined various scenarios in which this technology can pose an existential risk to humanity that could result in the literal end of the world.
Deep Learning AI Specialization: https://imp.i384100.net/GET-STARTED
AI Marketplace: https://taimine.com/
AI news timestamps:
0:00 How bad could it be?
2:56 AI destruction scenario 1 and 2
4:28 The future of artificial intelligence.
5:25 Merge with AI for human evolution.
6:41 The AI box experiment.
#ai #future #tech
00:22
Japan Just Shattered the Internet Speed Record at 319 Terabits per Second Lifeboat News: The Blog
Engineers in Japan just shattered the world record for the fastest internet speed, achieving a data transmission rate of 319 Terabits per second (Tb/s), according to a paper presented at the International Conference on Optical Fiber Communications in June. The new record was made on a line of fibers more than 1,864 miles (3,000 km) long. And, crucially, it is compatible with modern-day cable infrastructure.
00:22
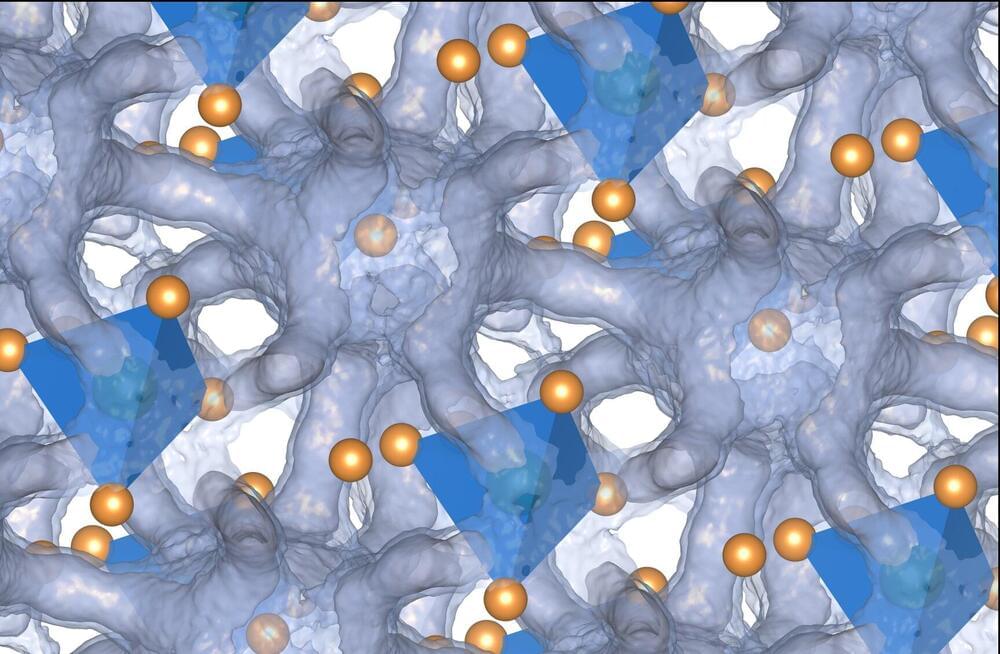
Machine learning approach opens insights into an entire class of materials being pursued for solid-state batteries Lifeboat News: The Blog
A team of researchers at Duke University and their collaborators have uncovered the atomic mechanisms that make a class of compounds called argyrodites attractive candidates for both solid-state battery electrolytes and thermoelectric energy converters.
The discoveriesand the machine learning approach used to make themcould help usher in a new era of energy storage for applications such as household battery walls and fast-charging electric vehicles.
The results appeared online May 18 in the journal Nature Materials.
00:22
Nvidia chips away at Intel, AMD turf in supercomputers Lifeboat News: The Blog
May 22 (Reuters) Nvidia Corp (NVDA.O) on Monday said it has worked with the U.K.s University of Bristol to build a new supercomputer using a new Nvidia chip that would compete with Intel Corp (INTC.O) and Advanced Micro Devices Inc (AMD.O).
Nvidia is the worlds top maker of graphics processing units (GPUs), which are in high demand because they can be used to speed up artificial intelligence work. OpenAIs ChatGPT, for example, was created with thousands of Nvidia GPUs.
But Nvidias GPU chips are typically paired with what is called a central processing unit (CPU), a market that has been dominated by Intel and AMD for decades. This year, Nvidia has started shipping its own competing CPU chip called Grace, which is based on technology from SoftBank Group Corp-owned (9984.T) Arm Ltd.
00:00
Supercon 2022: Nick Poole Makes a Jolly Wrencher Tube Hackaday

[Nick Poole] shared his circuitous journey into the obscure world of homemade vacuum tubes on the Supercon 2022 stage. It began innocently enough when he saw [Usagi Electric]s single bit computer vacuum tube computer, which uses dozens of vacuum tubes. He got to wondering, could you make vacuum-tube-like devices containing multiple elements? There are some examples, like the 256-bit memory Selectron tube from the 1950s, but nothing general purpose like a 555 timer or quad NAND gate packages. Unencumbered by a deep understanding of how vacuum tubes work, [Nick] proceeds to fill this void by imagining Integrated Thermionic, a fictitious company that exists in an alternate history where transistors were not invented and the vacuum tube reigns supreme. He also showcases a variety of innovative products that Integrated Thermionics manufactured over the decades, including surface mount tubes.
Tuesday, 23 May
23:56
North Korean Kimsuky Hackers Strike Again with Advanced Reconnaissance Malware The Hacker News
The North Korean advanced persistent threat (APT) group known as Kimsuky has been observed using a piece of custom malware called RandomQuery as part of a reconnaissance and information exfiltration operation. "Lately, Kimsuky has been consistently distributing custom malware as part of reconnaissance campaigns to enable subsequent attacks," SentinelOne researchers Aleksandar Milenkoski and Tom
23:45
Fusion Risk Management TPRM enhancements deliver continuous monitoring of third parties Help Net Security
Fusion Risk Management announced expanded functionality of its third-party risk management (TPRM) offering. The enhanced solution delivers continuous monitoring of third parties beyond its traditional instance as well as an evaluation of potential operational and business impacts that those third parties may have. This functionality enables a holistic and real-time view of third-party ecosystem health which improves decision-making and response times in order to transform how third-party risk teams anticipate and manage disruptions. Organizations continue More
The post Fusion Risk Management TPRM enhancements deliver continuous monitoring of third parties appeared first on Help Net Security.
23:44
German arms manufacturer Rheinmetall suffered Black Basta ransomware attack Security Affairs
The German automotive and arms manufacturer Rheinmetall announced it was victim of a Black Basta ransomware attack that took place last month.
Rheinmetall is a German automotive and arms manufacturer that is listed on the Frankfurt stock exchange. The company this week announced it was victim of a ransomware attack conducted by the Black Basta ransomware group.
The incident took place in Mid-April and impacted the business unit that serves industrial customers, particularly in the automotive sector. The defense division of the company was not impacted by the ransomware attack as reported after the discovery of the incident by Rheinmetalls spokesperson Oliver Hoffmann.
The automotive and arms manufacturer launched an investigation into the incident with the help of cybersecurity authorities.
The company filed a criminal complaint with the Cologne public prosecutors office.
The company is still working to completely recover from the security breach.
In March, the pro-Russian hacker group Killnet called to cyber arms on his Telegram channel against the company IT infrastructure in Germany and Australia after Rheinmetall announced a new tank factory in Ukraine as the Russian invasion of the Eastern European nation continues.
The company is a supplier of weaponry used on the Leopard tank which were sent to Ukraine by several European countries.
On September 2019, a series of cyber attacks hit defense contractors Rheinmetall AG and Defence Construction Canada (DCC) damaging their information technology systems.
Black Basta has been active since April 2022, like other ransomware operations, it implements a double-extortion attack model.
In November 2022, Sentinel Labs researchers reported having found evidence that links the Black Basta ransomware gang to the financially motivated hacking group FIN7.
In November 2022, experts at the Cy...
23:30
AMD Launches Ryzen 7020 C-Series - Continues Pushing Zen 2 For Chromebooks Phoronix
AMD today announced the Ryzen 7020 C-series processors. These processors are interesting for at least having integrated RDNA2 graphics but are based on the aging Zen 2 architecture...
23:30
IRONSCALES and Infinigate collaborate to provide customers with email security solution Help Net Security
IRONSCALES has partnered with the Infinigate Group to distribute IRONSCALES cloud email security platform in the Benelux, the Nordics, and Switzerland regions, with a view to widen the partnership across the wider EMEA territory. Infinigate is a key partnership for IRONSCALES and allows us to expand our reach to Benelux, the Nordics, and Switzerland to provide advanced phishing protection to MSPs, MSSPs, VARs, and System Integrators across the region, said Henrik Davidsson, VP of International More
The post IRONSCALES and Infinigate collaborate to provide customers with email security solution appeared first on Help Net Security.
23:02
SFPD Obtained Live Access to Business Camera Network in Anticipation of Tyre Nichols Protest Deeplinks
New documents EFF received through public records requests
have revealed that the San Francisco Police Department (SFPD)
received live access to the hundreds of surveillance cameras that
comprise the Union Square Business Improvement Districts (USBID)
camera network in anticipation of potential protests following the
police killing of Tyre Nichols in Memphis, Tennessee. The
protests were impassioned and peaceful as
Bay Area residents gathered to oppose police violenceand the SFPD
proactively got access to watch it all, opening up activists to
potential risk of reprisal and retribution for their political
beliefs and potentially chilling future participation in
demonstrations.
On January 27, 2023, an SFPD commander reached out to the USBID with a 12-hour live monitoring request for the 450 cameras in its network, citing potential civil unrest in anticipation of the release of body camera footage of Tyre Nichols killing by members of the Memphis Police Department. Reporting in the San Francisco Standard suggests that the SFPD may not have ended up engaging in live monitoring, but simply requesting this access before a protest can chill First Amendment activity. This act also indicates the SFPD is interpreting the ordinance too broadly. The policy states: SFPD is prohibited from accessing, requesting, or monitoring any surveillance camera live feed during First Amendment activities unless there are exigent circumstances or for placement of police personnel due to crowd sizes or other issues creating imminent public safety hazards." But the SFPD has not shown that, when they obtained live access, there were any imminent hazards or exigent circumstances.
The SFPD was able to seek live monitoring as a result of the controversial September 2022 temporary ordinance that authorized police to receive live access to non-city security cameras for a host of reasons, including to monitor so-called significant events. This temporary camera ordinance, which passed as a 15-month pilot, was ...
23:00
Conceal and White Rock Cybersecurity partner to isolate browsing sessions Help Net Security
Conceal has announced a new strategic partnership with White Rock Cybersecurity. White Rock Cybersecurity is committed to delivering innovative, scalable, and manageable solutions in information technology, said James Range, CEO of White Rock Cybersecurity. With the inclusion of Conceals Zero Trust isolation technology in our offerings, we are significantly boosting the defense capabilities of our customers against both existing and emerging cyber threats at the edge, Range added. ConcealBrowse, Conceals flagship product, is a browser More
The post Conceal and White Rock Cybersecurity partner to isolate browsing sessions appeared first on Help Net Security.
23:00
The Strange Story of the Teens Behind the Mirai Botnet IEEE Spectrum
First-year college students are understandably frustrated when they cant get into popular upper-level electives. But they usually just gripe. Paras Jha was an exception. Enraged that upper-class students were given priority to enroll in a computer-science elective at Rutgers, the State University of New Jersey, Paras decided to crash the registration website so that no one could enroll.
On Wednesday night, 19 November 2014, at 10:00 p.m. ESTas the registration period for first-year students in spring courses had just openedParas launched his first distributed denial-of-service (DDoS) attack. He had assembled an army of some 40,000 bots, primarily in Eastern Europe and China, and unleashed them on the Rutgers central authentication server. The botnet sent thousands of fraudulent requests to authenticate, overloading the server. Parass classmates could not get through to register.
The next semester Paras tried again. On 4 March 2015, he sent an email to the campus newspaper, The Daily Targum: A while back you had an article that talked about the DDoS attacks on Rutgers. Im the one who attacked the network. I will be attacking the network once again at 8:15 pm EST. Paras followed through on his threat, knocking the Rutgers network offline at precisely 8:15 p.m.

On 27 March, Paras unleashed another assault on Rutgers. This attack lasted four days and brought campus life to a standstill. Fifty thousand students, faculty, and staff had no computer access from campus.
On 29 April, Paras posted a message on Pastebin, a website popular with hackers for sending anonymous messages. The Rutgers IT department is a joke, he taunted. This is the third time I have launched DDoS attacks against Rutgers, and every single time, the Rutgers infrastructure crumpled like a tin can under the heel of my boot.
Paras was furious that Rutgers chose Incapsula, a small cybersecurity firm based in Massachusetts, as its DDoS-mitigation provider. He claimed that Rutgers chose the cheapest company. Just to show you the poor quality of Incapsulas network, I have gone ahead and decimated the Rutgers network (and parts of Incapsula), in the hopes that you will pick another provi...
22:49
How Solid Air Can Spur Sustainable Development SoylentNews
The world is undergoing an energy transition to reduce CO2 emissions and mitigate climate change. The COVID-19 pandemic and the Russia-Ukraine war have further increased the interest of Europe and Western countries to invest in the hydrogen economy as an alternative to fossil fuels. Hydrogen can significantly reduce geopolitical risks if the diversity of future hydrogen energy suppliers is increased.
Hydrogen is a particularly challenging product to transport safely. One option is to liquefy hydrogen, which requires cooling to 20 Kelvin (-253 C). This is an expensive process and requires around 30% of the energy stored within the hydrogen.
A pioneering approach developed by IIASA researchers and colleagues proposes solid air (nitrogen or oxygen) as a medium for recycling cooling energy across the hydrogen liquefaction supply chain. At standard temperature and pressure, air is a gas, but under certain conditions, it can become a liquid or solid. Solid Air Hydrogen Liquefaction (SAHL) consists of storing the cooling energy from the regasification of hydrogen, by solidifying air, and transporting the solid air back to where the hydrogen was liquefied. The solid air is then used to reduce the energy consumption for liquefying hydrogen. The process is divided into four main steps: hydrogen regasification, solid air transportation, hydrogen liquefaction, and liquid hydrogen transportation.
[...] In their paper, the authors also address the ongoing debate in industry and academia to find the best alternative to transport hydrogen by sea:
"Compared to ammonia or methanol, liquefied hydrogen is the best option for several reasons. Transporting hydrogen with ammonia and other molecules would require around 30% of the energy transported to extract the hydrogen. The hydrogen is liquefied where electricity is cheap. Also, SAHL can lower energy consumption for hydrogen liquefaction by 25 to 50%," Hunt concludes.
Journal Reference:
Hunt, J., Montanari, P., Hummes D., et al. (2023).
Solid air hydrogen liquefaction, the missing link of the
hydrogen economy. International Journal of Hydrogen
Energy DOI: https://doi.org/10.1016/j.ijhydene.2023.03.405
Read more of this story at SoylentNews.
22:40
Fedora Onyx To Become An Official Fedora Linux Immutable Variant Phoronix
There's been a proposal for Fedora Linux to become a new Fedora immutable variant and now it's been approved by the Fedora Engineering and Steering Committee (FESCo) to happen for the Fedora 39 cycle...
22:30
N-able partners with JCDC to reduce security risk for MSPs Help Net Security
N-able is collaborating with the Joint Cyber Defense Collaborative (JCDC) to help create a more secure global ecosystem and work towards helping reduce security risk for MSPs and their customers. The Cybersecurity and Infrastructure Security Agency (CISA) established JCDC in August 2021 to transform traditional public-private partnerships into real-time private-public operational collaboration. The JCDC 2023 Planning Agenda helps advance cybersecurity and reduce supply chain risk for small and medium critical infrastructure entities through collaboration with More
The post N-able partners with JCDC to reduce security risk for MSPs appeared first on Help Net Security.
22:30
Fedora Developers Discuss An Idea For Using U-Boot On x86 BIOS Systems Phoronix
Last year Fedora and Red Hat developers began discussing the idea of dropping legacy BIOS support and to then only focus on UEFI platforms. There was a plan to deprecate BIOS support in Fedora 37 but ultimately it didn't go through due to some cloud providers still booting VMs in BIOS mode and some systems having broken UEFI implementations. An idea has now been raised over the possibility of using U-Boot on x86 BIOS systems to provide a UEFI-like experience from the Fedora perspective...
22:29
[$] An LSFMM development-process discussion LWN.net
At the 2023 Linux Storage, Filesystem, Memory-Management and BPF Summit, Hannes Reinecke led a plenary session ostensibly dedicated to the "limits of development". The actual discussion focused on the frustrations of the kernel development process as experienced by both developers and maintainers. It is probably fair to say that no problems were solved here, but perhaps the nature of some of the challenges is a bit more clear.
22:26
New type of quasiparticle emerges to tame quantum computing errors Lifeboat News: The Blog
Errors are the Achilles heel of quantum computation, cropping up at random and threatening to rui.
22:26
Metas open-source speech AI recognizes over 4,000 spoken languages Lifeboat News: The Blog
Meta has created an AI language model that (in a refreshing change of pace) isnt a ChatGPT clone. The companys Massively Multilingual Speech (MMS) project can recognize over 4,000 spoken languages and produce speech (text-to-speech) in over 1,100. Like most of its other publicly announced AI projects, Meta is open-sourcing MMS today to help preserve language diversity and encourage researchers to build on its foundation. Today, we are publicly sharing our models and code so that others in the research community can build upon our work, the company wrote. Through this work, we hope to make a small contribution to preserve the incredible language diversity of the world.
Speech recognition and text-to-speech models typically require training on thousands of hours of audio with accompanying transcription labels. (Labels are crucial to machine learning, allowing the algorithms to correctly categorize and understand the data.) But for languages that arent widely used in industrialized nations many of which are in danger of disappearing in the coming decades this data simply does not exist, as Meta puts it.
Meta used an unconventional approach to collecting audio data: tapping into audio recordings of translated religious texts. We turned to religious texts, such as the Bible, that have been translated in many different languages and whose translations have been widely studied for text-based language translation research, the company said. These translations have publicly available audio recordings of people reading these texts in different languages. Incorporating the unlabeled recordings of the Bible and similar texts, Metas researchers increased the models available languages to over 4,000.
22:26
Startups bladeless flying car is designed to reach Mach 0.8 Lifeboat News: The Blog
Seattle-based startup Jetoptera is designing vertical take-off and landing (VTOL) vehicles with bladeless propulsion systems potentially making the future of urban flight quiet, safer, and faster.
The challenge: The proportion of the global population living in cities is expected to increase from 50% today to nearly 70% by 2050, meaning our already crowded urban streets are likely to become even more congested.
22:25
The dystopian future of menial work as AI replaces humans Lifeboat News: The Blog
On Wednesday, Google displayed how Bard, its new AI robot, could be used to write up job listings from a simple one line prompt. Microsoft has demonstrated how a ChatGPT-powered tool can write entire articles in Word.
There are a tonne of sales representatives doing a lot of banal work to compose prospecting emails, says Rob Seaman, a senior vice president at workplace messaging company Slack, which is working with OpenAI to embed ChatGPT into its app as a kind of digital co-worker.
New AI tools may remove some of the most tedious aspects of such roles. But based on past evidence, technology also threatens to create a whole new class of menial roles.
22:25
Flat Lenses Made of Nanostructures Transform Tiny Cameras and Projectors Lifeboat News: The Blog
Metalenses migrate to smartphones.
Metalenz came out of stealth mode in 2021, announcing that it was getting ready to scale up production of devices. Manufacturing was not as big a challenge as design because the company manufactures metasurfaces using the same materials, lithography, and etching processes that it uses to make integrated circuits.
In fact, metalenses are less demanding to manufacture than even a very simple microchip because they require only a single lithography mask as opposed to the dozens required by a microprocessor. That makes them less prone to defects and less expensive. Moreover, the size of the features on an optical metasurface are measured in hundreds of nanometers, whereas foundries are accustomed to making chips with features that are smaller than 10 nanometers.
22:24
Quantum Theorys Measurement Problem May Be a Poison Pill for Objective Reality Lifeboat News: The Blog
Solving a notorious quantum quandary could require abandoning some of sciences most cherished assumptions about the physical world.
22:15
WithSecure releases Cloud Security Posture Management to identify insecure cloud configurations Help Net Security
WithSecure has released Cloud Security Posture Management, a new module for its WithSecure Elements security platform, that identifies insecure cloud configurations attackers use to compromise networks. Its now become commonplace for organizations to incorporate cloud-based infrastructure-as-a-service (IaaS) offerings into their IT estates. This transformation has many benefits, but also new challenges, particularly in relation to security. These challenges include the rapid development of IaaS platforms, a scarcity of professionals with cloud security skills and experience, More
The post WithSecure releases Cloud Security Posture Management to identify insecure cloud configurations appeared first on Help Net Security.
22:00
Mastercard collaborates with HealthLock to protect medical data Help Net Security
Mastercard and HealthLock have partnered to offer millions of Americans help in protecting themselves against medical bill fraud, claim errors and overcharges. Consumers who link their insurance accounts to the HealthLock platform gain the ability to monitor all healthcare claims in one place and benefit from automated reviews to potentially help reduce expensive medical bills and reverse claim rejections. The partnership will initially open HealthLocks analytics-backed healthcare services to millions of US-issued HSA and FSA More
The post Mastercard collaborates with HealthLock to protect medical data appeared first on Help Net Security.
21:56
CVE-2023-33246: Apache RocketMQ: RocketMQ may have a remote code execution vulnerability when using the update configuration function Open Source Security
Posted by Rongtong Jin on May 23
Severity: moderateAffected versions:
- Apache RocketMQ through 5.1.0
Description:
For RocketMQ versions 5.1.0 and below, under certain conditions, there is a risk of remote command execution.
Several components of RocketMQ, including NameServer, Broker, and Controller, are leaked on the extranet and lack
permission verification, an attacker can exploit this vulnerability by using the update configuration function to
execute commands as...
21:51
First Contact: A Global Simulation Centauri Dreams Imagining and Planning Interstellar Exploration
Now and again scientists think of interesting ways to use our space missions in contexts for which they were not designed. Im thinking, for example, of the pale blue dot image snapped by Voyager 1 in 1990, an iconic view that forcibly speaks to the immensity of the universe and the smallness of the place we inhabit. Voyagers cameras, we might recall, were added only after a debate among mission designers, some of whom argued that the mission could proceed without any cameras aboard.
Fortunately, the camera advocates won, with results were all familiar with. Now we have a project out of The SETI Institute that would use a European Space Agency mission in a novel way, one that also challenges our thinking about our place in the cosmos. Daniela de Paulis, who serves as artist in residence at the institute, is working across numerous disciplines with researchers involved in SETI and astronautics to create A Sign in Space, the creation of an extraterrestrial message. This is not a message beamed to another star, but a message beamed back at us.
The plan is this: On May 24, 2023, tomorrow as I write this on the US east coast, ESAs ExoMars Trace Gas Orbiter, in orbit around Mars, will transmit an encoded message to Earth that will act as a simulation of a message from another civilization. The message will be detected by the Allen Telescope Array (ATA) in California, the Green Bank Telescope (GBT) in West Virginia and the Medicina Radio Astronomical Observatory in Italy. The content of the message is known only to de Paulis and her team, and the public will be in on the attempt to decode and interpret it. The message will be sent at 1900 UTC on May 24 and discussed in a live stream event beginning at 1815 UTC online.
The signal should reach Earth some 16 minutes after transmission, hence the timing of the live stream event. This should be an enjoyable online gathering. According to The SETI Institute, the live stream, hosted by Franck Marchis and the Green Bank Observatorys Victoria Catlett, will feature key team members scientists, engineers, artists and more and will include control rooms from the ATA, the GBT, and Medicina.
Daniela de Paulis points to the purpose of the project:

Throughout history, humanity has searched for meaning in powerful and transformative phenomena. Receiving a message from an extraterrestrial civilization would be a profoundly transformational experience for all huma...
21:34
Google Bans Downloader App: TV Outfits Claim Browser Violates Injunction TorrentFreak
 If the best ideas are always the simplest, in 2016
software developer Elias Saba hit the jackpot.
If the best ideas are always the simplest, in 2016
software developer Elias Saba hit the jackpot.
Two years after Amazon launched its first generation Fire TV, there was still no easy way to transfer files to the device. Released on the Amazon Appstore in November 2016, Sabas Downloader app offered users just two things; an empty URL field and a download button. It was basic yet functional, and in time, extraordinarily successful.
The Amazon Appstore and Google Play currently account for more
than 50 million installs of Downloader, underpinned by Sabas
decision not to charge a single penny for the software. 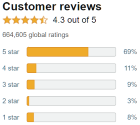 At the time of writing, Downloader has 664,605
customer ratings on Amazon, averaging 4.3 stars out of a possible
five. For several TV companies from Israel, Sabas work, success and
generosity are of no consequence; Downloader is in their way and
has to go.
At the time of writing, Downloader has 664,605
customer ratings on Amazon, averaging 4.3 stars out of a possible
five. For several TV companies from Israel, Sabas work, success and
generosity are of no consequence; Downloader is in their way and
has to go.
Google Kicks Downloader Out of the Play Store
In a notification sent to Sabas last Friday, Google informs the developer that after a recent review, Downloader was found to contain content that doesnt comply with the Unauthorized Use of Copyrighted Content policy operated on the Play Store.
The review was prompted by a copyright complaint from Israel-based TV companies HOT Communications Systems Ltd, DBS Satellite Services (1998) Ltd, United King Distribution Videos (1990) Ltd, and Charlton Ltd.
We have received an infringement notice that your app contains copyrighted content, Googles notice explains. Your app has been suspended and removed due to alleged copyright infringement (according to the terms of the Digital Millennium Copyright Act).
Googles notification reveals that the TV companies supplied no details of specific original content or details of content allegedly infringed. As a DMCA takedown notice, it arguably fails at the ve...
21:31
Security updates for Tuesday LWN.net
Security updates have been issued by Debian (node-nth-check), Mageia (mariadb and python-reportlab), Slackware (c-ares), SUSE (geoipupdate and qt6-svg), and Ubuntu (linux, linux-aws, linux-azure, linux-azure-5.4, linux-gcp, linux-gcp-5.4, linux-gke, linux-gkeop, linux-hwe-5.4, linux-ibm, linux-ibm-5.4, linux-kvm, linux-bluefield, linux-gcp, linux-hwe, linux-raspi2, linux-snapdragon, and linux-gcp, linux-hwe-5.19).
21:27
FFII: German President of the Unified Patent Court Rewrites the Treaty Like a Dictator Techrights
Brussels, 22 May 2023 The German President of the Unified Patent Court (UPC), Klaus Grabinski, has decided alone to rewrite the Unified Patent Court Agreement (UPCA) at this own will, and move London to Paris and Munich due to Brexit. FFII condemn this abuse of power and violation of the Rule of Law. This a decision typical of a dictatorship, not of an institution governed by the separation of powers. Judge Grabinski will also have the last word over software patents in Europe, without any possible appeal to the European Court of Justice (CJEU).
The President of the UPC decided the following:
In its meeting of 8 May 2023, the Presidium of the Unified Patent Court decided that, as from 1 June 2023, actions pending before the central division related to patents in IPC section (A) shall be assigned to the seat in Paris while actions related to patents in IPC section (C) shall be assigned to the section in Munich. [] the Presidium has exercised its managerial power under Article 15(3) of the Statute of the Unified Patent Court in the aforementioned sense.
Unified-Patent-Court.org: Decision on the provisional distribution of actions related to patents in IPC sections (A) and (C) pending before the central division | Unified Patent Court (unified-patent-court.org) https://www.unified-patent-court.org/en/news/decision-provisional-distribution-actions-related-patents-ipc-sections-and-c-pending-central
Article 15(3) of the Statutes of the Unified Patent Court does not mention any power to decide on such a political topic to relocate the Court from one place to another, except a broad management responsibility:
- The Presidium shall be responsible for the management of the Court and shall in particular:
(a) draw up proposals for the amendment of the Rules of Procedure in accordance with Article 41 of the
Agreement and proposals regarding the Financial...
21:16
The Rising Threat of Secrets Sprawl and the Need for Action The Hacker News
The most precious asset in today's information age is the secret safeguarded under lock and key. Regrettably, maintaining secrets has become increasingly challenging, as highlighted by the 2023 State of Secrets Sprawl report, the largest analysis of public GitHub activity. The report shows a 67% year-over-year increase in the number of secrets found, with 10 million hard-coded secrets detected
21:11
New WinTapix.sys Malware Engages in Multi-Stage Attack Across Middle East The Hacker News
An unknown threat actor has been observed leveraging a malicious Windows kernel driver in attacks likely targeting the Middle East since at least May 2020. Fortinet Fortiguard Labs, which dubbed the artifact WINTAPIX (WinTapix.sys), attributed the malware with low confidence to an Iranian threat actor. "WinTapix.sys is essentially a loader," security researchers Geri Revay and Hossein Jazi said
21:00
Building Circuits Flexibly Hackaday

You think of breadboards as being a flexible way to build things one can easily add components and wires and also rip them up. But MIT researchers want to introduce an actual flexible breadboard called FlexBoard. The system is like a traditional breadboard, but it is literally flexible. If you want to affix your prototype to a glove or a ball, good luck with a traditional breadboard. FlexBoard makes it easy. You can see a short video below and a second video presentation about the system, also.
The breadboard uses a plastic living hinge arrangement and otherwise looks more or less like a conventional breadboard. We can think of about a dozen projects this would make easier.
Whats more, it doesnt seem like it would be that hard to fabricate using a 3D printer and some sacrificial breadboards. The paper reveals that the structures were printed on an Ender 3 using ePLA and a flexible vinyl or nylon filament. Want to try it yourself? You can!
We know what we will be printing this weekend. If you make any cool prototypes with this, be sure to let us know. Sometimes we breadboard virtually. Our favorite breadboards, though, have more than just...
20:38
KDE Neon Unstable Now Building With Qt 6 Frameworks/Plasma Phoronix
For those feeling adventurous and wanting to see how things are coming along for KDE Plasma 6.0 and KDE Frameworks Qt 6 porting, the KDE Neon Linux distribution with its "unstable" edition has begun building against the Qt6 components...
20:31
Linux 6.4 Lands Intel Alder Lake / Raptor Lake Workaround For INVLPG/PCID Bug Phoronix
The bug I wrote about this weekend where Intel is now disabling PCID for Alder Lake and Raptor Lake under Linux until updated CPU microcode is issued for addressing an issue with the INVLPG instruction when Process Context Identifiers are enabled, has now been merged to Linux 6.4...
20:04
New Study Reveals Possible Future Health Impacts Related to Climate Mitigation SoylentNews
New study reveals possible future health impacts related to climate mitigation:
Reduce fossil fuel use and air quality will improve, right? It might not be as straightforward as it appears, according to a Penn State-led research team. They explored almost 30,000 simulated future scenarios and found that some climate mitigation efforts could lead to harmful health impacts in certain geographic areas.
Their results were published May 18 in Nature Sustainability.
"In general, reducing fossil fuel use is good for climate mitigation and good for cleaning up the air, and the modeling studies have always found health benefits from climate mitigation," said corresponding author Wei Peng, assistant professor of international affairs and of civil and environmental engineering at Penn State, who has conducted research in this area for a decade. "But in this study, for the first time, we were able to see potential co-harm occur in a certain part of the scenarios."
The researchers found some scenarios where fossil fuel reduction requires a significant land use change to grow bioenergy resources, such as algae and plants like corn stalks and barley straw that can be used to create biofuels including types of ethanol and biodiesel.
In these scenarios, deforestation could occur on a grander scale for certain areas, such as Russia and Canada, leading to worsening air quality. As a result, people in these areas with worsened air quality could suffer from more respiratory and cardiovascular diseases, which could lead to more premature deaths, said the researchers.
Read more of this story at SoylentNews.
19:48
Suzuki motorcycle plant shut down by cyber attack Graham Cluley
The Indian manufacturing plant responsible for manufacturing Suzuki motorcycles has been forced to shut down following a cyber attack, with the loss of an estimated 20,000 vehicles. Read more in my article on the Hot for Security blog.
19:45
A deeper insight into the CloudWizard APTs activity revealed a long-running activity Security Affairs
Experts warn of a threat actor, tracked as CloudWizard APT, that is targeting organizations involved in the region of the Russo-Ukrainian conflict.
On March 2023, researchers from Kaspersky spotted a previously unknown APT group, tracked as Bad Magic (aka Red Stinger), that targeted organizations in the region of the Russo-Ukrainian conflict. The attackers were observed using PowerMagic and CommonMagic implants.
Looking for other implants with similarities with PowerMagic and CommonMagic, the researchers identified a different cluster of even more sophisticated malicious activities associated with the same threat actor.
The victims of this cluster were located not only in the Donetsk, Lugansk and Crimea regions, but also in central and western Ukraine. The APT group targeted individuals, as well as diplomatic and research organizations in the area of the conflict. In the latest campaign uncovered by Kaspersky, the APT group, used a modular framework dubbed CloudWizard that supports spyware capabilities, including taking screenshots, microphone recording, harvesting Gmail inboxes, and keylogging.
A deeper analysis revealed that the threat actor CloudWizard has been linked to an activity cluster that dates back to May 2016 that was tracked by ESET researchers as Operation Groundbait.
In October 2022, Kaspersky researchers uncovered a malware campaign aimed at infecting government, agriculture and transportation organizations located in the Donetsk, Lugansk, and Crimea regions with a previously undetected framework dubbed CommonMagic.
Researchers believe that threat actors use spear phishing as an initial attack vector, the messages include an URL pointing to a ZIP archive hosted on a web server under the control of the attackers. The archive contained two files, a decoy document (i.e. PDF, XLSX and DOCX versions) and a malicious LNK file with a double extension (i.e., .pdf.lnk) used to start the infection and deploy the PowerMagic backdoor.
Kaspersky attributed the October campaign to a new APT group operating in the area of Russo-Ukrainian conflict and tracked as Bad Magic.
19:43
GNU Binutils Prepares For Intel FRED/LKGS Phoronix
The GNU Assembler "Gas" as part of the GNU Binutils collection has landed support for Intel FRED and LKGS instructions...
19:08
Simple OSINT techniques to spot AI-fueled disinformation, fake reviews Help Net Security
Error messages that ChatGPT and other AI language models generate can be used to uncover disinformation campaigns, hate speech and fake reviews via OSINT collection and analysis, says Nico Dekens, director of intelligence at ShadowDragon. AI-generated content found via Google (Source: ShadowDragon) Uncovering AI-generated content through OSINT Dekens has recently tried to pinpoint specific indicators that reveal online content news, social media posts, reviews created with the help of AI models. He concentrated More
The post Simple OSINT techniques to spot AI-fueled disinformation, fake reviews appeared first on Help Net Security.
18:32
IRC Proceedings: Monday, May 22, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-220523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-220523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-220523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-220523.gmi
Over HTTP:
|
... |
18:00
Smart Pants Sound Alarm When Your Fly Is Undone Hackaday

Its always embarrassing to be told your fly is down. Even moreso when you realize its been that way since you returned from the bathroom an hour ago. [Guy Dupont] has built a device to solve this awkward issue once and for all. (Nitter)
17:20
China Fails Micron's Products in Security Review, Bars Some Purchases SoylentNews
China's cyberspace regulator said on Sunday that products made by U.S. memory chip manufacturer Micron Technology had failed its network security review and that it would bar operators of key infrastructure from procuring from the firm:
The decision, announced amid a dispute over chip technology between Washington and Beijing, could include sectors ranging from transport to finance, according to China's broad definition of critical information infrastructure.
"The review found that Micron's products have serious network security risks, which pose significant security risks to China's critical information infrastructure supply chain, affecting China's national security," the Cyberspace Administration of China (CAC) said in a statement.
[...] U.S. officials, including members of a U.S. congressional select committee on competition with China, did not immediately respond to requests for comment.
Micron derives around 10% of its revenue from China, but it is not clear if the decision affects the company's sales to non-Chinese customers in the country.
Also at The Register, MarketWatch and ABC News.
Related:
- US Restrictions See China's Chip Imports Plummet 27% in First Two Months of 2023
- Netherlands Refuses to Summarily Agree to US Export Restrictions on China Over Silicon Chips
- US Chip Makers Hit by New China Export Rule
Read more of this story at SoylentNews.
17:00
Possible Antidote to Worlds Deadliest Mushroom Discovered Terra Forming Terra
:focal(1400x933:1401x934)/https:/tf-cmsv2-smithsonianmag-media.s3.amazonaws.com/filer_public/22/a5/22a59f4c-4704-46f7-b901-2e7cb73aed4e/gettyimages-)
Let them eat cake - Stupid on the march Terra Forming Terra

Transforming Food Terra Forming Terra

The Case for Two Adults Terra Forming Terra

This is actually a great idea and can be easily implimented with proactive protocols. No initial need to build a thing. My natural community is actually a nengineering design problem on multiple levels. this can be a straight up regulatory shift in any 'home' must accomadate two adults to maintain social benefits. We actually go the other way now.
The Case for Two Adults
After years working with homeless mothers and children, I realized that more affordable housing for single parents might not be the only solution.
MAY 15, 2023
https://www.plough.com/en/topics/justice/social-justice/the-case-for-two-adults
16:51
BlackCat Ransomware affiliate uses signed kernel driver to evade detection Security Affairs
Experts spotted the ALPHV/BlackCat ransomware group using signed malicious Windows kernel drivers to evade detection.
Trend Micro researchers shared details about ALPHV/BlackCat ransomware incident that took place on February 2023. A BlackCat affiliate employed signed malicious Windows kernel drivers to evade detection.
reported in December 2022 by Mandiant, Sophos and Sentinel One, via a coordinated disclosure.The attackers attempted to deploy the driver (ktgn.sys) previously analyzed by Mandiant, which is signed through Microsoft signing portals.
The use of a Windows kernel driver, which runs with the highest privileges in the OS, allows attackers to kill any process associated with defense products.
The researchers pointed out that even if the certificate that was used to sign the ktgn.sys driver has been revoked, the driver will still load on 64-bit Windows systems with enforced signing policies.
The kernel driver employed in the attack exposes an IOCTL interface that allows the user Agent tjr.exe to issue commands that the driver will execute with kernel privileges.
...
16:47
China Bans U.S. Chip Giant Micron, Citing "Serious Cybersecurity Problems" The Hacker News
China has banned U.S. chip maker Micron from selling its products to Chinese companies working on key infrastructure projects, citing national security risks. The development comes nearly two months after the country's cybersecurity authority initiated a probe in late March 2023 to assess potential network security risks. "The purpose of this network security review of Micron's products is to
15:00
Whats Black, White, and Red on 20 Sides? Hackaday

You wont need to pack a full set of dice for your next game with this DIY Multifunctional Eink Gadget. [Sasa Karanovi] brings us a fun device that combines a few essential aspects of tabletop gaming, D6, D12, and D20 dice rolling and a hero dashboard. While they have grand plans for a BLE networked future application, we admire the restraint to complete a V1 project before allowing scope-creep to run amok. Well played!
For this project, [Sasa] realized it needed to be battery powered and just choosing the right display for a battery powered application can be daunting. Even if you arent building this project, the video after the break includes a nice intro to electronic ink and low power microcontrollers for the uninitiated. We even see a graph of the completed boards power draw from the button wake up, display refresh, and low power sleep. The project has some neat tips for building interaction into case design with the use of the display and a flexible bezel as inte...
14:36
When Employees Leave Their Jobs, Coworkers Call It Quits SoylentNews
When employees leave their jobs, coworkers call it quits: UBC study:
People leave jobs all the time, whether they're laid off, fired, or just quit. But how do their departures affect coworkers left behind? According to a new study from the UBC Sauder School of Business, those exits can lead many others to call it quits.
The researchers delved deeply into employment data from a major retailer that was experiencing high turnover to find out why. They reviewed data for roughly a million employees including when they were hired, which store, which position, when they left, and why.
The study authors also had access to employee performance records, so they could evaluate whether workers were high performers or low performers.
[...] "It's very bad news for organizations, especially if they are laying off high performers, because if those positions get eliminated, both high and low performers start quitting," said Dr. Sajjadiani. "It's a signal that people's jobs aren't secure, and the organization doesn't care about them, no matter how hard they work. So they think, 'I should leave as soon as possible.'"
When employees quit their jobs voluntarily, their departures give a more moderate boost to voluntary turnover, and it takes longer for that ripple effect to occur.
"To high performers, voluntary exits are a positive signal that there are better opportunities elsewhere," said Dr. Sajjadiani. "So while employees might not leave immediately, they do begin to look for other opportunities."
[...] However, when a high performer is dismissed without clear justification, employers not only open themselves to legal headaches, it also sends the wrong message to other high performers. They also start heading for the door.
According to Dr. Sajjadiani, organizations vastly underestimate the ripple effects of people leaving and the resulting human capital costs. The research also sends a clear message to organizations that they should be extremely careful when they make exit decisions, or they risk destabilizing the whole organization very quickly.
Journal Reference:
Sima Sajjadiani, John D Kammeyer-Mueller and Alan Benson, Who Is
Leaving and Why? The Dynamics of High-Quality Human Capital
Outflows, Academy of Management Journal, 2023. DOI:
https://doi.org/10.5465/amj.2021.1327
Read more of this story at SoylentNews.
14:30
7 access management challenges during M&A Help Net Security
Integrating an acquired company into a single organization is a daunting task that can take weeks, months, or even years to complete. To have a successful conclusion to the mergers and acquisitions (M&As) process, identity and access management (IAM) teams need time to prepare, test, and communicate with users to ensure the process goes as smoothly as possible. But what happens to all those identities when companies abruptly close their doors or acquisitions take place More
The post 7 access management challenges during M&A appeared first on Help Net Security.
14:11
On Anniversaries and Milestones Techrights
Tux Machines turning 19 shortly!
IN a couple of weeks Tux Machines turns 19. Last year we celebrated with some cake (after the pandemic started no more parties) and this year Rianne is away on holiday, so probably no parties or anything i.e. same as the 17-year anniversary and 16-year anniversary. As for Techrights, there are 36,500 blog posts in the site this week (blog posts arent everything). 40,000 some time next year? Almost for sure. In Tux Machines there are almost 200,000 pages already. Growing by about 1,000 per month.
14:00
Gap between OT security assumptions and reality Help Net Security
In the fast-evolving landscape of technology and connectivity, ensuring the security of operational technology (OT) systems has become a paramount concern for organizations worldwide. In this Help Net Security video, Daniel Bren, CEO at OTORIO, discusses a significant discrepancy between how companies perceive their OT security posture and the harsh reality they often face. The need to bridge this gap becomes apparent when examining real-world scenarios. The disparity between security intentions outlined in roadmaps and More
The post Gap between OT security assumptions and reality appeared first on Help Net Security.
13:30
The fragmented nature of API security ownership Help Net Security
While API security remains a top cybersecurity concern this year, there is still an alarming lack of implementation for most companies, according to Traceable AI. Companies overlook API security Companies are struggling with unchecked API sprawl, lack of clarity on who owns API security, and do not baseline behavior as part of their security capabilities. With insights from more than 100 cybersecurity professionals, the study showed that though 69% of organizations claim to factor APIs More
The post The fragmented nature of API security ownership appeared first on Help Net Security.
13:12
Microsoft Pundits Predictions Versus Reality Techrights
Reality:
But forget about reality Microsoft was eager to tell people they dont need search engines and should instead get hyped-up chatbots.
Paid-for Microsoft fluff aplenty (we give just one example from each month; the marketing/propaganda strategy changed). Starting with January:
February:
March:
April:
May:
Summary: With an estimated market share of 93% worldwide, Google Search has only gained share [1,...
12:00

If you want a book on network programming, there are a few classic choices. [Comers] TCP/IP books are a great reference but sometimes is too low level. Unix Networking Programming by [Stevens] is the usual choice, but it is getting a little long in the tooth, as well. Now we have Beejs Guide to Network Programming Using Internet Sockets. While the title doesnt exactly roll off the tongue, the content is right on and fresh. Best part? You can read it now in your browser or in PDF format.
All the topics youd expect are there in ten chapters. Of course, theres the obligatory description of what a socket is and the types of sockets you commonly encounter. Then theres coverage of addressing and portability. Theres even a section on IPV6.
After covering the most common socket API calls, there is a simple example. Then Chapter 7 covers slightly advanced techniques. That includes things like the select API call, partial sends, and broadcast packets. Chapter 9 is just man pages which are handy if you have the printed reference on an airplane. Overall, a good modern treatment of the topic.
While the socket API originated at Berkely, just about every network stack looks the same more or less, so if you learn these calls, youll do fine on whatever operating system you like, including many microcontrollers.
Usually, when we are looking at networking, our eyes are focused...
11:43
Plastic Pervasive in Food Supply, Says New Study SoylentNews
Plastic pervasive in food supply, says new study:
Micro and nanoplastics are pervasive in our food supply and may be affecting food safety and security on a global scale, a new study led by CSIRO, Australia's national science agency, has found.
The study is one of the first to analyze the academic literature on microplastics from a food safety and food security risk viewpoint, building on past studies which primarily tracked plastics in fish.
It shows that plastics and their additives are present at a range of concentrations not only in fish but in many products including meat, chicken, rice, water, take-away food and drink, and even fresh produce.
CSIRO analytical chemist, food safety specialist and lead author of the paper, Dr. Jordi Nelis, said these plastics enter the human food chain through numerous pathways, such as ingestion as shown in the fish studies, but one of the main ways is through food processing and packaging. The research is published in the journal TrAC Trends in Analytical Chemistry.
[...] There are currently no definitive studies that demonstrate micro and nanoplastics in the environment cause harm to humans, however more research is needed to fully understand health effects.
[...] "The key missing information is determining safe levels of microplastics. We currently don't know exactly what the microplastic flux through the food system is or which levels can be considered safe," Dr. Nelis said.
Journal Reference:
Joost L.D. Nelis et al, The measurement of food safety
and security risks associated with micro- and nanoplastic
pollution, TrAC Trends in Analytical Chemistry (2023).
DOI: 10.1016/j.trac.2023.116993
Read more of this story at SoylentNews.
11:39
Links 22/05/2023: Qt 6 in KDE Neon Unstable, GNU Parallel 20230522, and More Microsoft Layoffs Techrights
![]()
Contents
-
GNU/Linux
-
SlashGear You Can Turn Your Old PS2 Into A Linux Computer: Heres How
If you still own a classic PlayStation 2 game console, it doesnt have to just lay in your closet gathering dust, and there is quite a good chance that youll be able to turn it into a functioning desktop computer.
After its official release by Sony in the spring of 2000, the PlayStation 2 was such a hit that it became the highest-selling video game console of all time, with sales exceeding 155 million units. Sony...
-
11:33
Gemini Links 22/05/2023: Bubble Debated a Week Later Techrights
-
Gemini* and Gopher
-
Personal
-
Some new books
New to me, that is. Two new thrift store books, $1/ea:
the life-changing magic of tidying up (2014), Marie Kondo and The Land Breakers (1964), John Ehle
Kondo book, and tells me that the book itself suggests being given away, so its not odd to see it at a thrift store. Seems like sound advice. Its a book about letting things go. Maybe it was secretly written by the League of Thrift Store Masters, as propaganda to replenish their shelves? -
Etymology
Its probably not a familiar word if youre an American, maybe more of a British/Canadian thing, but today I learned that Tory (as a nickname for Conservatives) is derived from the Irish traidhe; appropriately, bandit.
-
All Day Outside
On Saturday I went up to my parents for a family get together with my dads sister, my moms sister, and my moms aunt. I dont much care for my moms side of the family and while I tried coming at them with an open mind and heart, it being a number of years since Id last seen them, they proved to repeat the same negative traits that has pushed me away from them. My dad and his sister agreed so we ended up spending a lot of time together, hiding from my moms half. One of the things I did to stay busy away from the family was prepping an old metal horse trough to be turned into a raised planter box. I had to drill a few holes in the bottom for drainage and load it, as well as a bucket of composted horse manure, into the back of my car. I unloaded it all as soon as I got home that night.
-
-
Technical
-
Pixel, Audio Clipping, etc
Yesterday I mentioned I was having audio issues with my Pixel. I nev...
-
-
11:01
[$] Fanotify and hierarchical storage management LWN.net
In the filesystem track of the 2023 Linux Storage, Filesystem, Memory-Management and BPF Summit, Amir Goldstein led a session on using fanotify for hierarchical storage management (HSM). Linux had some support for HSM in the XFS filesystem's implementation of the data management API (DMAPI), but that code was removed back in 2010. Goldstein has done some work on using fanotify for HSM features, but he has run into some problems with deadlocks that he wanted to discuss with attendees.
10:15
Interview With a Crypto Scam Investment Spammer Krebs on Security
Social networks are constantly battling inauthentic bot accounts that send direct messages to users promoting scam cryptocurrency investment platforms. What follows is an interview with a Russian hacker responsible for a series of aggressive crypto spam campaigns that recently prompted several large Mastodon communities to temporarily halt new registrations. According to the hacker, their spam software has been in private use until the last few weeks, when it was released as open source code.

Renaud Chaput is a freelance programmer working on modernizing and scaling the Mastodon project infrastructure including joinmastodon.org, mastodon.online, and mastodon.social. Chaput said that on May 4, 2023, someone unleashed a spam torrent targeting users on these Mastodon communities via private mentions, a kind of direct messaging on the platform.
The messages said recipients had earned an investment credit at a cryptocurrency trading platform called moonxtrade[.]com. Chaput said the spammers used more than 1,500 Internet addresses across 400 providers to register new accounts, which then followed popular accounts on Mastodon and sent private mentions to the followers of those accounts.
Since then, the same spammers have used this method to advertise more than 100 different crypto investment-themed domains. Chaput said that at one point this month the volume of bot accounts being registered for the crypto spam campaign started overwhelming the servers that handle new signups at Mastodon.social.
We suddenly went from like three registrations per minute to 900 a minute, Chaput said. There was nothing in the Mastodon software to detect that activity, and the protocol is not designed to handle this.

One of the crypto investment scam messages promoted in the spam campaigns on Mastodon this month.
Seeking to gain a temporary handle on the spam wave, Chaput said he briefly disabled new account registrations on mastodon.social and mastondon.online. Shortly after that, those same servers came under a sustained distributed denial-of-service (DDoS) attack.
Chaput said whoever was behind the DDoS was definitely not using point-and-click DDoS tools,...
10:00
HPR3862: Firefox Extensions Hacker Public Radio
Firefox plugins uBlock Origin uBlock Origin ad blocker Finally, an efficient blocker. Easy on CPU and memory. I don't care about cookies I don't care about cookies Get rid of cookie warnings from almost all websites! Bitwarden - Free Password Manager Bitwarden A secure and free password manager for all of your devices. Dark Reader Convert pages to Dark Mode Dark mode for every website. Take care of your eyes, use dark theme for night and daily browsing. This eye-care extension enables night mode creating dark themes for websites on the fly. Dark Reader inverts bright colors making them high contrast and easy to read at night. You can adjust brightness, contrast, sepia filter, dark mode, font settings and ignore-list. Dark Reader doesn't show ads and doesn't send user's data anywhere. It is fully open-source Github page for Dark Reader ChatGPTBox ChatGPT Extension Integrating ChatGPT into your browser Custom Video Speed for YouTube Extension to control Youtube speed Change the current & default speed of YouTube™ videos by steps of 0.1 from 0.1 up to 8.0 using sliders, buttons, and/or the keyboard. SponsorBlock for YouTube - Skip Sponsorships Block sponsors for Youtube videos Skip sponsorships, subscription begging and more on YouTube videos. Report sponsor on videos you watch to save others' time. SponsorBlock lets you skip over sponsors, intros, outros, subscription reminders, and other annoying parts of YouTube videos. SponsorBlock is a crowdsourced browser extension that lets anyone submit the start and end times of sponsored segments and other segments of YouTube videos. Once one person submits this information, everyone else with this extension will skip right over the sponsored segment. You can also skip over non music sections of music videos. Supports Invidious, old YouTube and mobile YouTube. Tab Stash Extension to stash tabs in a timestamped sidebar A no-fuss way to save and restore batches of tabs as bookmarks. Tridactyl Extension to browse Firefox with vim keybindings Vim, but in your browser. Replace Firefox's control mechanism with one modelled on Vim. This addon is very usable, but is in an early stage of development. We intend to implement the majority of Vimperator's features. Control your browser with your keyboard only. Replace Firefox’s control mechanism with one modelled on VI
09:33
Newly Public FISC Opinion is The Best Evidence For Why Congress Must End Section 702 Deeplinks
A surveillance court order unsealed last week that details
massive violations of Americans privacy by the FBI underscores why
Congress
must end or radically change the
unconstitutional spying program enabled by Section 702 of the
Foreign Intelligence Surveillance Act (FISA).
The
opinion recounts how for years the FBI
illegally accessed a database containing communications obtained
under Section 702 and other FISA authorities more than 278,000
times, including searching for communications of people arrested at
protests of police violence and people who donated to a
congressional candidate. Section 702 authorizes the surveillance of
communications between people overseas. But when a person on U.S.
soil is in contact with one of these surveillance targets, that
leaves their side of the exchange sitting in a database and
vulnerable to these warrantless FBI searches. As the opinion says,
Notwithstanding this foreign directed targeting, the extent to
which Section 702 acquisitions involve U.S. persons should be
understood to be substantial in the aggregate.
The pervasiveness of the FBIs failure to comply with even the most modest reforms designed to limit the agencys surveillance powers reveals two problems that Congress must address as it considers the Administrations request to reauthorize Section 702.
First, the FBI is incapable of policing itself when it comes to trawling through the communications of Americans without a warrant. There is a point at which it would be untenable to base findings of sufficiency untenable on long promised, but still unrealized, improvements in how FBI queries Section 702 information, the court wrote. That point is now. The FBI simply cannot help but violate the law.
Second, the Foreign Intelligence Surveillance Court (FISC) is incapable of protecting Americans from the FBIs unconstitutional searches of their communications. Since passage of Section 702 in 2008, Executive Branch leaders have argued that judicial oversight would ensure that the FBI and other spying agencies would not illegally intrude on peoples constitutional rights. That has never been true. Yet despite a series of well-documented violations by the FBI, NSA, and CIA, the FISC has consistently approved and reapproved the agencies ability to use Section 702. The newly released opinio...
09:01
Google Pixel Smartphones Will Add Bard AI Widget: Report SoylentNews
Google may turn Bard generative AI chatbot into a widget on Pixel smartphones and tablets, according to a 9to5Google code dive report. Bard is publicly available, but only through a web portal. An Android-accessible version, even limited to Pixel devices, could help the company nab more of the market currently dominated by OpenAI and Microsoft through ChatGPT and the ChatGPT-powered Bing:
Though Google hasn't spread Bard beyond its initial entry point, other tools fueled by the same LaMDA large language model (LLM) have become more available. Generative AI text generators and editors for Gmail, Docs, and other parts of Google's software suite looking to make Bard a widget on the main Pixel screen.
[...] A built-in widget for Bard might be a way for Google to accelerate the adoption of its generative AI since Pixel devices and the Android OS are part of its ecosystem. Mobile apps with ChatGPT in some form, such as SoundHound and ParagraphAI, can't do what a first-party tool could.
Originally spotted on The Eponymous Pickle.
Read more of this story at SoylentNews.
09:00
Bringing The PIO To The FPGA Hackaday

Weve seen some pretty incredible hacks using the Raspberry Pi 2040. However, one of the most exciting bits of hardware onboard is the Programmable I/O (PIO). Not content with it just being a part of RP2040-based projects, [Lawrie Griffiths] has been porting the PIO to Verilog so anyone can enjoy it.
This particular implementation is based only on the spec that Raspberry Pi provides. For assembling PIO code, [Lawrie] uses Adafruits pioasm assembler they use for their MicroPython framework. Theres a simulator to test different programs, and the project targets the Blackice MX and the Ulx3s. A few example programs are included in the repo, such as outputting a pleasant guitar note over I2S and driving a chain of WS2812s.
The project is still incomplete but slowly making progress. Its an incredible feat of reverse engineering. While the simulator can be used to debug programs, step through instructions, and inspect waveforms, the ultimate value of bringing the PIO to other systems is that now we can re-use the code. Things like the can2040, an implementation of the...
08:42
Python 3.12 Now Under Feature Freeze With Beta 1 Released Phoronix
The first beta release of Python 3.12 is now available that also marks the beginning of the feature freeze for this year's major Python update...
07:49
CapCut Users Beware: Phishing Sites Distributing Malware HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
If you use TikTok, you must be aware of CapCut. However, did you know that this app is being abused by threat actors to drop malware and carry out phishing scams through not one, but a series of malicious sites?
This is a post from HackRead.com Read the original post: CapCut Users Beware: Phishing Sites Distributing Malware
07:13
EFF to Court: Californias Public Records Law Must Remain a Check on Police Use of Drones Deeplinks
An increasing number of cities are adding drone flights to their law enforcement tool kit. Public access to appropriately redacted video footage from those flights can provide oversight of police surveillance and help ensure cities are living up to their privacy promises.
Every second of every drone video should not be categorically exempt from public records laws as an investigatory record. This is the argument of an amicus letter filed in California state court last week by EFF, the First Amendment Coalition, and the Reporters Committee for Freedom of the Press.
The case centers around a journalist who requested drone flight videos created by the Chula Vista Police Department, under the California Public Records Act (CPRA). The department touts its program as one of the first in the country to use drones as first responders to emergency calls for police service, and the city has advocated for other law enforcement to create similar programs. EFF has previously raised alarm that the relative cheapness of deploying dronescompared to helicopters or on-the-ground policingencourages more surveillance.
In denying the public records request, the city claimed the videos were categorically exempt from disclosure under the CPRA because they are investigatory records. After the requester sued, the trial court agreed with Chula Vista and ruled that it would be unduly burdensome to require the city to review the video footage and release redacted versions. The requester has asked the California Court of Appeal to reverse the trial courts decision.
EFFs amicus letter filed in the appellate court argues that the CPRAs investigatory records' exemption must be construed narrowly, and that the city did not carry its burden to prove that either (1) all drone flights derive from a targeted criminal investigation, or (2) that every moment of footage is exempt. The citys own policies note that it deploys drones for noncriminal matters, such as to evaluate damage after a natural disaster, and that its drones record video even before the drone arrives at the scene and when it is returning to base. At minimum, that footage is not likely to reflect any specific investigation. The letter also points to other cases where the government released redacted documents, even though the redaction process was much more burdensome than this case.
More generally, the CPRAs investigatory records exemption is not a broad shield that allows poli...
07:04
[$] Reliable user-space stack traces with SFrame LWN.net
A complete stack trace is needed for a number of debugging and optimization tasks, but getting such traces reliably can be surprisingly challenging. At the 2023 Linux Storage, Filesystem, Memory-Management and BPF Summit, Steve Rostedt and Indu Bhagat described a mechanism called SFrame that enables the creation of reliable user-space stack traces in the kernel without the memory and run-time overhead of some other solutions.
06:31
More Than 600,000 Students and Teachers Use Z-Library TorrentFreak
 Z-Library has become the go-to site for many readers in
recent years by providing access to millions of books, without
charging a penny.
Z-Library has become the go-to site for many readers in
recent years by providing access to millions of books, without
charging a penny.
The sites continued ability to do so was put to the test late last year when U.S. law enforcement seized over 200 domain names connected to the site. Two alleged Z-Library operators were arrested as part of a criminal investigation.
Despite being in the crosshairs of law enforcement, Z-Library has no intention of throwing in the towel. The site remained accessible through the dark web and later made a full comeback. When the U.S. authorities seized more domains earlier this month, it still didnt budge.
Serving Students and Teachers
Z-Library instead doubled down on its mission to provide free books to the public at large, including educational material and textbooks. This makes the site a popular repository for students all around the world, as statistics from Z-Librarys user database now reveal.
Its no secret that the most active users of our library are students and staff from various universities. We wanted to learn more about this and have collected statistics showing which educational institutions use Z-Library, Z-Library writes on Telegram.
The team analyzed its user database to check how many user email-addresses are linked to universities, colleges and schools. This gives an impression of how many students and employees use the site but its likely a low estimate, as students may very well use their personal email addresses to sign up.
Still, the overall outcome and the global distribution of users is worth highlighting. China is the top country in absolute numbers, followed by India and Indonesia. This is no surprise, perhaps, as these countries also have the largest populations.
06:16
NASA's Lucy Spacecraft Adjusts Course for Asteroid Flyby in November SoylentNews
NASA's Lucy spacecraft adjusts course for asteroid flyby in November:
On May 9, NASA's Lucy spacecraft carried out a trajectory correction maneuver to set the spacecraft on course for its close encounter with the small main belt asteroid Dinkinesh. The maneuver changed the velocity of the spacecraft by only about 7.7 mph (3.4 m/s).
Even though the spacecraft is currently traveling at approximately 43,000 mph (19.4 km/s), this small nudge is enough to move the spacecraft nearly 40,000 miles (65,000 km) closer to the asteroid during the planned encounter on Nov. 1, 2023. The spacecraft will fly a mere 265 miles (425 km) from the small, half-mile-(sub-km)-sized asteroid, while traveling at a relative speed of 10,000 mph (4.5 km/s).
The Lucy team will continue to monitor the spacecraft's trajectory and will have further opportunities to fine tune the flight path if needed.
The Lucy team is also continuing to analyze the data collected from its spring instrument calibration campaign and make other preparations for the mission's first asteroid encounter. This encounter will provide a valuable test of the spacecraft's systems and procedures to make sure that everything operates as expected during the mission's high-speed asteroid encounters.
Read more of this story at SoylentNews.
06:00
The Thousand Year (Radioactive) Diamond Battery Hackaday

The Holy Grail of battery technology is a cell which lasts forever, a fit-and-forget device that never needs replacing. It may seem a pipe-dream, but University of Bristol researchers have come pretty close. The catch? Their battery lasts a very long time, but it generates micropower, and its radioactive.
Theyre using a thin layer of vapour-deposited carbon-14 diamond both as a source of beta radiation, and as a semiconductor material which harvests those electrons. Theyre expected to be used for applications such as intermittent sensors, where they would slowly charge a supercapacitor which could release useful amounts of power in short bursts.
Its being touted as an environmental win because the carbon-14 is sourced from radioactive waste, but against that its not unreasonable to have a concern about the things being radioactive. The company commercializing the tech leads with the bold question: What would you do with a power-cell that outlasts the device it powers?, to which we would hope the answer wont be Throw it away to be a piece of orphaned radioactive waste in the environment when the device it powers is outl...
05:53
DarkBERT: Enhancing Cybersecurity Efforts on the Dark Web HackRead | Latest Cybersecurity and Hacking News Site
DarkBERT is based on the RoBERTa architecture and leverages the power of AI to navigate the dark web.
This is a post from HackRead.com Read the original post: DarkBERT: Enhancing Cybersecurity Efforts on the Dark Web
04:37
CISA adds iPhone bugs to its Known Exploited Vulnerabilities catalog Security Affairs
US CISA added three zero-day vulnerabilities affecting iPhones, Macs, and iPads to its Known Exploited Vulnerabilities catalog.
US Cybersecurity and Infrastructure Security Agency (CISA) added three zero-day vulnerabilities affecting iPhones, Macs, and iPads to its Known Exploited Vulnerabilities Catalog.
The three issues reside in the WebKit browser engine and are tracked as CVE-2023-32409, CVE-2023-28204, and CVE-2023-32373.
Below are the details of the threat vulnerabilities that were recently addressed by Apple:
- CVE-2023-32409 Apple Multiple Products WebKit Sandbox Escape Vulnerability. Apple iOS, iPadOS, macOS, tvOS, watchOS, and Safari WebKit contain an unspecified vulnerability that can allow a remote attacker to break out of the Web Content sandbox.
- CVE-2023-28204 Apple Multiple Products WebKit Out-of-Bounds Read Vulnerability. Apple iOS, iPadOS, macOS, tvOS, watchOS, and Safari WebKit contain an out-of-bounds read vulnerability that may disclose sensitive information.
- CVE-2023-32373 Apple Multiple Products WebKit Use-After-Free Vulnerability. Apple iOS, iPadOS, macOS, tvOS, watchOS, and Safari WebKit contain a use-after-free vulnerability that leads to code execution.
Apple is aware of a report that this issue may have been actively exploited, reads the advisory [1, 2] published by the tech giant.
The company released iOS and iPadOS 16.5, tvOS 16.5, watchOS 9.5, Safari 16.5, and macOS Ventura 13.4 to address the issues.
Apple initially addressed both CVE-2023-28204 and CVE-2023-32373 with the Rapid Security Response (RSR) patches for iOS 16.4.1 and macOS 13.3.1 on May 1.
Since the beginning of 2023, the company addressed a total of six zero-day vulnerabilities exploited in attacks in the wild.
According to Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities, FCEB agencies have to address the identified vulnerabilities by the due date to protect their networks against attacks exploiting the flaws in...
04:23
At Least 4.5 Million People Have Died in Post-9/11 Warzones cryptogon.com
Via: Brown Costs of War: Wars destruction of economies, public services, infrastructure, and the environment leads to deaths that occur long after bombs drop and grow in scale over time. This report reviews the latest research to examine the causal pathways that have led to an estimated 3.6-3.7 million indirect deaths in post-9/11 war []
04:03
04:00
This Stevens Institute of Technology Student Got a Head Start in Engineering IEEE Spectrum

Many teenagers take a job at a restaurant or retail store, but Megan Dion got a head start on her engineering career. At 16, she landed a part-time position at FXB, a mechanical, electrical, and plumbing engineering company in Chadds Ford, Pa., where she helped create and optimize project designs.
She continued to work at the company during her first year as an undergraduate at the Stevens Institute of Technology, in Hoboken, N.J., where she is studying electrical engineering with a concentration in power engineering. Now a junior, Dion is part of the five-year Stevens cooperative education program, which allows her to rotate three full-time work placements during the second quarter of the school year through August. She returns to school full time in September with a more impressive rsum.
For her academic achievements, Dion received an IEEE Power & Energy Society scholarship this year. The PES Scholarship Plus Initiative rewards undergraduates who one day are likely to build green technologies and change the way we generate and utilize power. Dion received US $2,000 toward her education.
She says shes looking forward to networking with other scholarship recipients and IEEE members.
Learning from other peoples stories and seeing myself in them and where my career could be in 10 or 15 years motivates her, she says.
Gaining hands-on experience in power engineering
Dions early exposure to engineering came from her father, who owned a commercial electrical construction business for 20 years, and sparked her interest in the field. He would bring her along to meetings and teach her about the construction industry.
Then she was able to gain on-the-job experience at FXB, where she quickly absorbed what she observed around her.
I would carry around a notebook everywhere I went, and I took notes on everything, she says. My team knew they never would have to explain something to me twice.
If Im going to do something, Im going to do it the best I can.
She gained the trust of her colleagues, and they asked her to continue working with them while she attended college. She accepted the offer and supported a critical pro...
03:59
IBM Versus GNU/Linux Community (Including Fedora) Techrights
Summary: This recent video covers Fedora and how IBM sabotages the community
03:54
From Past Lessons to Future Protections: EFF's Advice to the EU Commission on Extended Reality Governance Deeplinks
EFF, in partnership with Access Now and the European Center for Not-for-Profit Law (ECNL), has responded to the European Commission's consultation, "Virtual Worlds (Metaverses) A Vision for Openness, Safety, and Respect." This follows our joint statement on International Human Rights Day in 2021, "Virtual Worlds, Real People: Human Rights in the Metaverse," which called for governments and corporations to uphold human rights within Extended Reality (XR), which include Virtual Reality (VR) and Augmented Reality statement.
The term "metaverse" is elusive, and open to many interpretations. It has evolved into an umbrella term encompassing numerous concepts, often influenced by the perspectives of those utilizing it. Given this broad and vague scope that can even extend beyond Extended Reality (XR), our submission neither endorses nor critiques the EU Commission's initiative.
However, EFF strongly urges the EU Commission to consider historical digital rights lessons learned. People need principles that safeguard them from undue state and corporate overreach, which should be the focus of any measures introduced by the EU Commission about the metaverse.
The metaverse does not need to be a single platform, nor does any metaverse need to be owned or controlled by a single entity. Instead, it is more beneficial to consider the metaverse as a generic term for a vast and interoperable network of different VR, AR, and "other services."
XR presents enormous potential for entertainment, education, connectivity, and human rights advocacy. Yet, it also poses risks to these human rights. Our joint statement emphasizes the importance of past experiences in securing human rights within XR, and extending the protection of our rights. We also propose several principles to prevent state and corporate overreach in XR.
You can read the full submission here:
03:48
EU Regulators Hit Meta with Record $1.3 Billion Fine for Data Transfer Violations The Hacker News
Facebook's parent company Meta has been fined a record $1.3 billion by European Union data protection regulators for transferring the personal data of users in the region to the U.S. In a binding decision taken by the European Data Protection Board (EDPB), the social media giant has been ordered to bring its data transfers into compliance with the GDPR and delete unlawfully stored and processed
03:31
Patterns in Register Map Design SoylentNews
https://www.devever.net/~hl/regmap
If you've ever had to write a program which interfaces directly with hardware perhaps while writing a program for an MCU or embedded system or a kernel driver you may have noticed a few common patterns in register map behaviour and design. I'm not sure anyone has ever really collected them together, so I decided to make a list of all the ones I can think of.
Read more of this story at SoylentNews.
03:04
Two And A Half Coins episode 5: Bitcoin transactions, the Bitcoin script and UTXOs David Wong | Cryptologie | HTML
In the 5th episode of this series I interview Arik Sosman (our very first guest!) in order to learn more about Bitcoin transactions. Specifically, how the Bitcoin scripting language works, and what UTXOs are!
02:46
Links 22/05/2023: SoylentNews Site to Shut Down and New Releases of Pgpool-II Now Available Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
-
GNU/Linux
-
9to5Linux 9to5Linux Weekly Roundup: May 21st, 2023
This week we didnt get so many news and releases. Still, we got some interesting ones about some of the new features of the upcoming Ubuntu 23.10 (Mantic Minotaur) and KDE Plasma 6 desktop environment.
On top of that, I warn you about the end of life of Linux kernel 6.2 and inform you about the new abilities of Xfces default screenshot utility. Check out the hottest news of this week and access all the distro and package downloads in 9to5Linuxs Linux weekly r...
-
02:45
Intel Provides AI-Accelerated HPC Update For ISC 2023 Phoronix
Intel is using ISC2023 this week in Hamburg, Germany to provide an update on its AI-accelerated HPC efforts. This includes reaffirming their upcoming data center product roadmap, reiterating their great software efforts, and also announcing full Aurora supercomputer specifications.
02:41
Gemini Links 22/05/2023: Smolver Security Hole Fixed Techrights
-
Gemini* and Gopher
-
Personal
-
SpellBinding: EILXPSM Wordo: LOXES
-
Music Index!!!
This isnt really warranting an announcement But I decided to carve out some of my music related posts into their own page. I often cite these posts and its nice to have a quick place to find them. I want to do more music related writing (even though I am bad at it) so I figured if I carve out its own page then maybe this can incentivize me.
Every post I make is going to show up in my gemlog regardless so Im keeping my RSS feed the same. Itll just act as basically a Tag filter
-
Duolingo, Long Weekend
Two weeks into Duolingo and Im now in the Gold League (theres like, five or six tiers). Do enough lessons/get enough points each week, and you move up. So I have. I won my Bronze League by the skin of my teeth, then Silver last week pretty easily. I assume it will just get progressively harder. But, Im sort of impressed. So many achievements! Gems! Shiny things! Challenges, and practices! The product managers have absolutely mastered the gamification of language learning, holy hell. Incredibly slick, engaging, no rough edges. And even a wicked sense of humour. One of my old online friends, much more fluent in Irish than me, started up again after a few months away. The first sentence Duolingo gave her: I dont have time for five minutes a day.
-
-
Technical
-
Games Showcase: Hogwarts Legacy
Hogwards Legacy, released this year, brings to life a world that many of us already know well.
Im not, I should say up front, a devotee of the series. I read and enjoyed some of the books, I watched and enjoyed the movies; and I think I understand why its been hugely successful. The world of Harry Potter is a fun, colourful place to allow ones imagination...
-
-
02:27
This is a post that I have suspected that I was going to have to write since late December last year.
You will now know that SoylentNews.org is closing down on 30 June but things have not been standing still behind the scenes since we first became aware of NCommander's decision at the end of last week. In fact, it has been a very busy weekend.
A small group of existing staff are looking at alternative possibilities for a 'replacement' site to keep the flow of stories going and allowing discussions to continue. This is a big task, especially in the 38 days remaining in which to try to achieve it. There are several possibilities which spring to mind, Pipedot for example. I have reached out to Bryan but have not yet received a response. However, things as not as straightforward as they seem. The pipecode is written in Php-5 which some of you will realise is no longer supported. We do not want to become dependant on old software which cannot be maintained into the future; that lesson has been taken aboard and reinforced by NCommander's explanation regarding his decision announced today. There are other options but at the moment it is still a search for what is available out there today which also appears maintainable into the future.
But the first thing we need to know is "Is there still sufficient interest in having a discussion site such as ours?" Do you, the community, still want to have your daily dose of stories and the ability to exchange views with many others on this site? Are there any community members who would be willing to join us in trying to establish such a site? Your views are crucial to everything that we do over the coming days and weeks. So please let us know what you think about whether a site is still required with all the alternative technology available today that simply didn't exist 9 years ago. What form should a new site take? What changes to how we operate are essential for you to continue to remain interested in the future site?
Of course, it cannot be a mirror image of what we have today - which many will see as a good thing! But I hope that we would be able to transfer existing accounts, usernames and passwords directly to any new site that we create. We would also have to start with a relatively simple site and build on that over time.
At the end of the day we would have to restart the voluntary subscriptions but not immediately. We can raise some funds to see us get established without the requirement of a financial commitment from the community. Subscriptions were always sufficient in the past and I don't see why that would not be the case in the future too. The fact that we currently have enough to keep this site going until next year bears witness to that. We have also found that we can significantly reduce our running costs based on our current community rather than being ready for a major stream of new members which never materialises. I have no grandiose ideas of becoming a huge...
02:11
M&S and Diageo pension schemes exposed in Capita hack Graham Cluley
Personal details of more than 100,000 pension holders may have been stolen by the hackers. And that's just the tip of the iceberg...
02:05
Indonesian Cybercriminals Exploit AWS for Profitable Crypto Mining Operations The Hacker News
A financially motivated threat actor of Indonesian origin has been observed leveraging Amazon Web Services (AWS) Elastic Compute Cloud (EC2) instances to carry out illicit crypto mining operations. Cloud security company's Permiso P0 Labs, which first detected the group in November 2021, has assigned it the moniker GUI-vil (pronounced Goo-ee-vil). "The group displays a preference for Graphical
02:00
Design for 3D Printing Hack Chat Hackaday

Join us on Wednesday, May 24 at noon Pacific for the Design for 3D Printing Hack Chat with Eric Utley!
Like a lot of enabling technologies, 3D printing has had a strange trajectory. It started out as a laboratory oddity, moved on to industrial applications, and finally filtered down to the DIY set, first as scratch-built machines and later as inexpensive commodity printers that can be found almost anywhere. Pretty much everyone who needs a 3D printer now has one.
Not all additive manufacturi...
02:00
SoylentNews Site Shutdown SoylentNews
This is the post I never thought I would have to make. I am also writing this post on behalf of SoylentNews PBC, the legal owner of SoylentNews, and not as a member of the staff or the community.
SoylentNews is going to shut down operations on June 30th.
This wasn't an easy decision to come to, and it's ultimately the culmination of a lot of factors, some which were in my control, and some that weren't. A large part boils down to critical maintenance to the site not properly being performed for a very long time. To pay back the mountain of technical debt we've built up, it would require relaunching the site from scratch.
I'll discuss this more in depth below, but I can't personally justify the time any more, especially due to the negative impact that SN is having on my personal life.
Before we shut down, at least for the foreseeable future, I'm going to outline the situation as I see it, my own personal responsibility, and what happens next.
Read more of this story at SoylentNews.
01:29
EU hits Meta with $1.3 billion fine for transferring European user data to the US Security Affairs
The European Union condemned Meta with a record $1.3 billion fine for transferring European user data to the US.
The European Union fined Meta $1.3 billion for transferring user data to the US. This is the biggest fine since the adoption of the General Data Protection Regulation (GDPR) by the European Union (EU) on May 25, 2018.
In the past, the social media giant Meta threatened to block its services for users in Europe without a legal basis for data transfers. Now the company was disappointed by the decision of Irelands Data Protection Commission and said that it sets a dangerous precedent for a large number of companies transferring data between the EU and U.S..
There is no immediate disruption to Facebook in Europe, Nick Clegg, Metas president of global and affairs, and Chief Legal Officer Jennifer Newstead said in a statement published by the Associated Press. This decision is flawed, unjustified and sets a dangerous precedent for the countless other companies transferring data between the EU and U.S., .
The battle had roots in the past, precisely in 2013 when the privacy activist and NOYB founder, Max Schrems, filed a complaint about Facebooks handling of his data following the revelations of Edward Snowden about the global surveillance program operated by the US.
On December 13, 2022, the European Commission launched the formal process to adopt an adequacy decision for the EU-U.S. Data Privacy Framework on December 13, 2022.
The EU-U.S. Privacy Shield Framework was designed by the U.S. Department of Commerce and European Commission to provide companies on both sides of the Atlantic with a mechanism to comply with EU data protection requirements when transferring personal data from the European Union to the United States in support of transatlantic commerce.
Clearly, in order to stop shipping user data to the US, Meta might have to make huge investments such as re-distribute its data to European plants. Unfortunately, currently it has only 3 sites in E...
01:23
Sci-fi author writes 97 AI-generated books in nine months Lifeboat News: The Blog
Plus: Official ChatGPT iPhone app debuts; Debt collectors using chatbots to chase debtors.
01:22
Perpetual Life Hybrid Party w/ Erik Nelson, presents Into the World of Longevity Medicine and NEW Age Reversal Updated Presented by Bill Faloon Lifeboat News: The Blog
Join us at 6:00 pm EST (11:00 pm UTC) for our Perpetual Life Hybrid Party live from our new location at 950 South Cypress Road in Pompano Beach, FL, & socialize with Immortalists from Around the World, hosted by hosted by Tonya Scholz & Rudi Hoffman.
Stay In Zoom for our 7:00 pm (12:00 am-midnight UTC) YouTube Streaming Service. This month, we are excited to have two speakers. First, Erik Nelson, Director of Clinical Programs at The Healthy Longevity Clinic, will present Into the World of Longevity Medicine.
Second, Bill Faloon: A founder of The Church of Perpetual Life and a leader in the Global Age Reversal movement, Bill will give a NEW Age Reversal Update at this service.
01:22
Are Large Language Model Generative AIs Sentient, Conscious or Thinking? Lifeboat News: The Blog
ChatGPT has changed the world since it emerged a few short months ago. Where will future advancements in generative AI take us?
Welcome back Katie Brenneman, a regular contributor to 21st Century Tech Blog. Several weeks ago when ChatGPT entered the headlines I suggested to Katie that she consider writing about Large Language Modelling (LLM) and the technological and societal implications in terms of its capabilities. Were we witnessing the birth of consciousness in this new artificial intelligence (AI) discipline, or were we coming to terms with what defines our sentience?
By definition, sentience is about feelings and sensations and not thinking. Consciousness, on the other hand, is about our awareness of self and our place in the world around us. And thinking is about the ability to reason, consider a problem, come up with an idea or solution, or have an opinion.
So from what we know about ChatGPT in its various iterations, does it meet the definition of any of these terms? Is it sentient? Is it conscious? Is it thinking?
01:00
Cloudflare Launches New Open-Source Software Sponsorship Program Phoronix
Cloudflare is making it easier for non-profit open-source projects to tap into the premium services offered by the company for speeding up their web infrastructure and protecting against attacks...
01:00
Hoverboard Rides on Eddy Currents Hackaday

The famous hoverboards of Back to the Future havent quite gotten here yet, but that hasnt stopped anyone with a unique personal vehicle from using the name any time they need some quick marketing. The self-balancing scooter trend of the mid-2010s was the best example of this in recent memory, but there are also water-propelled platforms that use the popular name as well as a myriad of other more skateboard-like devices that never got off the ground at all. This project from [Damien Dolata], on the other hand, might be the most authentic prototype weve seen compared against the
The hoverboard uses a set of rotating magnets, referred to in this build as magneto-rotational repulsors, which spin up to an extremely high rotational speed underneath the board. When above a metal surface, the spinning magnets generate eddy currents in the metal beneath them which create the strong magnetic field needed to levitate the board. Unlike the Lexus hoverboard system which used supercooling magnets, this is a much more affordable way of producing magnetic fields but is a little bit more complicated due to the extra moving parts.
As this is still in the protot...
00:47
Jeffrey Epstein Used Knowledge of Bill Gates Relationship with Young Bridge Player to Blackmail the Microsoft Co-Founder cryptogon.com
My guess is that this is around a level 1 in terms of the intensity of blackmail that Epstein could have applied to Gates. Via: Daily Mail: A Russian bridge players affair with Bill Gates has been brought to light by a bombshell new report which claims Jeffrey Epstein used his knowledge of the relationship []
00:46
The Next Step: Lawsuit Against Sirius or Standard Life? schestowitz.com
Summary: The crimes of Sirius Open Source are being ignored by the police, but that does not mean that holding Sirius accountable is not possible
MERELY two weeks from now itll be half a year since I left Sirius Open Source. Ive since then demonstrated that crimes were committed and I received official letters (several from pension providers) to prove it. The police as I dare say I expected all along did nothing about it, but there are 4 more avenues well turn to. There will be big scandals ahead, thats for sure, assuming we can hold people accountable before they and the company vanish completely. Not only myself but others (former colleagues) suspected something was amiss. Proving it, however, was a big endeavour, owing partly to how pension fund managers operate in the UK (immensely arrogant; not even responding to mail!).
It looks like the pension scheme failed to alert you and failed to alert the regulator, one person told me recently. If the employer becomes insolvent, will the incompetence at Standard Life make them liable to cover the loss?
They try to claim not to know us, I responded. This may be a sign that they know they could be liable, I was told by this person (whose identity and role we prefer to keep private). Do they have record of any of the employees at all?
He kept on asking crucial questions: Is there even one employee who has ever received correspondence direct from Standard Life in the past, either by email or by post?
Standard Life and the IFA were in cahoots, and we have official papers to prove it. We shared some of these before.
If you can get evidence that they knew of even one employee then that might be sufficient for all of you to launch a class action together against Standard Life, the person noted. The pension fraud of Sirius would not have been possible without outside help
There are several steps ahead of us now, but the stronger the proof against them, the person argued, the harder it is for them to make excuses and the more serious their sentences / director bans.
...
00:39
Scientists Finally Confirm What's Inside the Moon SoylentNews
The Moon is not made of green cheese after all:
A thorough investigation has found that the inner core of the Moon is, in fact, a solid ball with a density similar to that of iron. This, researchers hope, will help settle a long debate about whether the Moon's inner heart is solid or molten, and lead to a more accurate understanding of the Moon's history and, by extension, that of the Solar System.
"Our results," writes a team led by astronomer Arthur Briaud of the French National Centre for Scientific Research in France, "question the evolution of the Moon magnetic field thanks to its demonstration of the existence of the inner core and support a global mantle overturn scenario that brings substantial insights on the timeline of the lunar bombardment in the first billion years of the Solar System."
[...] To figure it out once and for all, Briaud and his colleagues collected data from space missions and lunar laser ranging experiments to compile a profile of various lunar characteristics. These include the degree of its deformation by its gravitational interaction with Earth, the variation in its distance from Earth, and its density.
[...] And they found that the lunar core is very similar to that of Earth with an outer fluid layer and a solid inner core. According to their modeling, the outer core has a radius of about 362 kilometers (225 miles), and the inner core has a radius of about 258 kilometers (160 miles). That's about 15 percent of the entire radius of the Moon.
The inner core, the team found, also has a density of about 7,822 kilograms per cubic meter. That's very close to the density of iron.
[..] We know not long after it formed, the Moon had a powerful magnetic field, which started to decline about 3.2 billion years ago. Such a magnetic field is generated by motion and convection in the core, so what the lunar core is made of is deeply relevant to how and why the magnetic field disappeared.
Journal Reference:
Briaud, A., Ganino, C., Fienga, A. et al. The lunar
solid inner core and the mantle overturn. Nature
(2023). https://doi.org/10.1038/s41586-023-05935-7
Read more of this story at SoylentNews.
00:38
Holding Criminals Accountable Part VIII Lots More to Come After Police Inaction Techrights
Series parts:
- Holding Criminals Accountable Part I Sirius Crimes Reported to British Authorities, Formally Registered With References (Many Victims), Heres What It Means and What Happens Next
- Holding Criminals Accountable Part II Still No Action From Action Fraud
- Holding Criminals Accountable Part III Why Police Action is the Only Option Now
- Holding Criminals Accountable Part IV British Prime Minister Launches Crackdown on Fraud, So Now Prove It
- Holding Criminals Accountable Part V 20 Days Later, UK Action Fraud Shows No Signs of Action
- Holding Criminals Accountable Part VI 26 Days Later and Still Inaction/No Action by the Police That Had Endless Resources for Coronation Ceremony
- Holding Criminals Accountable Part VII Fraud Since 2011 (If Not Earlier) Merits Criminal Prosecution
- YOU ARE HERE Lots More to Come After Police Inaction
Summary: The crimes of Sirius Open Source are being ignored by the...
00:04
[Meme] Captain Antnios Strategic Plan SP2028 Techrights

Treat your staff like trash, and sooner or later your organisation
will get trashed
Summary: The EPOs Antnio Campinos has a vision and its not particularly inspiring
00:00
AirTags, Tiles, SmartTags and the Dilemmas of Personal Tracking Devices Hackaday

In an ideal world we would never lose our belongings, and not spend a single hour fruitlessly searching for some keys, a piece of luggage, a smartphone or one of the two dozen remote controls which are scattered around the average home these days. Since we do not live in this ideal world, we have had to come up with ways to keep track of our belongings, whether inside or outside our homes, which has led to todays ubiquitous personal tracking devices.
Todays popular Bluetooth-based trackers constantly announce their presence to devices set up to listen for them. Within a home, this range is generally enough to find the tracker and associated item using a smartphone, after which using special software the tracker can be made to sound its built-in speaker to ease localizing it by ear. Outside the home, these trackers can use mesh networks formed by smartphones and other devices to phone home to paired devices.
This is great when its your purse. But this also gives anyone the ability to stick such a tracker device onto a victims belongings and track them without their consent, for whatever nefarious purpose. Yet it is this duality between useful and illegal that has people on edge when it comes to these trackers. How can we still use the benefits they offer, without giving stalkers and criminals free reig...
Monday, 22 May
23:50
Comments on the European Patent Offices Strategic Plan to Survive Another 5 Years Techrights
Summary: European Patent Office (EPO) staff representatives have a lot to say about the EPOs document-wielding managers, who have managed to destroy not only the EPOs reputation but also the quality of staffing, legitimacy of patents etc. (all that in pursuit of short-term monetary gains)
The Central Staff Committee (CSC) of the EPO wrote to Antnio Campinos exactly one week ago. It commented on the Hey Hi (AI) hype and many other plans of the EPOs management. When the notorious hype wave isnt (mis)used to promote European software patents (the buzzwords du jour keep changing all the time) its used to promote understaffing or layoffs (putting more work pressure/burden on remaining examiners, forcing them to grant in a rush, sometimes due to inability to find prior art under unreasonable time constraints).
It commented on the Hey Hi (AI) hype and many other plans of the EPOs management.Rather than comment on what the CSC has to say (we might do a video about this separately), lets quote what the CSC told colleagues:
The CSC has been invited to share its view in the public consultation on the EPOs Strategic Plan 2028.
A new strategic plan is an opportunity to pave the way towards a better future for the Office, where staff is treated as its main asset and is motivated to support and ideally identifies itself again with the mission and objectives of the Office.
As the statutory social partner representing EPO staff, we have shared our views with the Office, in this open letter to the President of the Office.
Here is the content of the document in (X)HTML/plain...
23:45
[$] A slab allocator (removal) update LWN.net
The kernel developers try hard to avoid duplicating functionality in the kernel, which is enough of a challenge to maintain as it is. So it has often seemed out of character for the kernel to support three different slab allocators (called SLAB, SLOB, and SLUB), all of which handle the management of small memory allocations in similar ways. At the 2023 Linux Storage, Filesystem, Memory-Management and BPF Summit, slab maintainer Vlastimil Babka updated the group on progress toward the goal of reducing the number of slab allocators in the kernel and gave an overview of what to expect in that area.
23:43
[$] Toward a swap abstraction layer LWN.net
The kernel's swapping code tends to not get much love. Users try to avoid it, and developers often find better things to do with their time than trying to improve it. At the 2023 Linux Storage, Filesystem, Memory-Management and BPF Summit, though, Yosry Ahmed dedicated a memory-management-track session to the problem of the swap layer and what might be done to make it better.
23:41
Security updates for Monday LWN.net
Security updates have been issued by Debian (cups-filters, imagemagick, libwebp, sqlite, and texlive-bin), Fedora (chromium and vim), Gentoo (librecad, mediawiki, modsecurity-crs, snakeyaml, and tinyproxy), Mageia (apache-mod_security, cmark, dmidecode, freetype2, glib2.0, libssh, patchelf, python-sqlparse, sniproxy, suricata, and webkit2), Oracle (apr-util and firefox), Red Hat (git), SUSE (containerd, openvswitch, python-Flask, runc, terraform-provider-aws, and terraform-provider-null), and Ubuntu (tar).
23:23
How the digital ad industry can guide the ways AI transforms businesses Lifeboat News: The Blog
Join top executives in San Francisco on July 1112, to hear how leaders are integrating and optimizing AI investments for success. Learn More
When Microsoft-funded lab OpenAI launched ChatGPT in February, millions of people realized almost overnight what tech professionals have understood for a long time: Todays AI tools are advanced enough to transform daily life as well as an incredibly broad range of industries. Microsofts Bing leaped from a distant second place in search to a much higher-profile level. Concepts like large language models (LLMs) and natural language processing are now part of mainstream discussion.
However, with the spotlight also comes scrutiny. Regulators around the world are taking note of AIs risks to user privacy. The Elon Musk-backed Future of Life Institute amassed 1,000 signatures from tech leaders asking for a six-month pause on training AI tools that are more advanced than GPT-4, which powers ChatGPT.
23:22
A Google researcher who said she was fired after pointing out biases in AI says companies wont self-regulate because of the AI gold rush Lifeboat News: The Blog
Timnit Gebru co-authored a research paper while she worked at Google, which identified the biases of machine learning.
23:22
Quantum Biology: Unlocking the Mysteries of How Life Works Lifeboat News: The Blog
Quantum biology explores how quantum effects influence biological processes, potentially leading to breakthroughs in medicine and biotechnology. Despite the assumption that quantum effects rapidly disappear in biological systems, research suggests these effects play a key role in physiological processes. This opens up the possibility of manipulating these processes to create non-invasive, remote-controlled therapeutic devices. However, achieving this requires a new, interdisciplinary approach to scientific research.
Imagine using your cell phone to control the activity of your own cells to treat injuries and diseases. It sounds like something from the imagination of an overly optimistic science fiction writer. But this may one day be a possibility through the emerging field of quantum biology.
Over the past few decades, scientists have made incredible progress in understanding and manipulating biological systems at increasingly small scales, from protein folding to genetic engineering. And yet, the extent to which quantum effects influence living systems remains barely understood.
23:10
Dish Network says the February ransomware attack impacted +300,000 individuals Security Affairs
Satellite TV giant Dish Network disclosed a data breach after the February ransomware attack and started notifying impacted individuals.
The American satellite broadcast provider Dish Network went offline on February 24, 2023, the outage impacted Dish.com, Dish Anywhere app, and many other services owned by the company.
In early February, the company admitted that the outage was caused by a ransomware attack.

According to BleepingComputer, the company was a victim of the Black Basta ransomware operation.
The threat actors initially compromised the companys Windows domain controllers and then encrypted the VMware ESXi servers and backups.
Now the Satellite TV giant has started notifying the impacted 296,851 individuals. The company pointed out that there is no evidence of misuse of stolen information and confirmed that its customer databases were not accessed. Threat actors had access to certain employee-related records and personal information.
We have since determined that the extracted data includes some of your personal information. We are not aware of any misuse of your information, and we have received confirmation that the extracted data has been deleted. reads the data breach notification letter sent to the impacted individuals and shared with the Maine Attorne...
23:00
Onfido acquires Airside to boost identity verification for individuals and businesses Help Net Security
Onfido acquired Airside Mobile to deliver user-controlled, shareable digital identity designed with data privacy and time-saving convenience at its core. Airsides shareable digital identity technology has been used by over 10 million travelers and is trusted by major U.S. government agencies, including the Transportation Security Administration (TSA). Its customers include the worlds largest airlines, who allow passengers to use the innovative Airside Digital Identity App to fast-track passengers through U.S. airports. Airsides privacy-first identity management More
The post Onfido acquires Airside to boost identity verification for individuals and businesses appeared first on Help Net Security.
22:58
Microsoft Layoffs Still Ongoing This Week in Nuance Communications Techrights
The latest on Microsoft layoffs that only one news site wrote about, based on leaked communications:
Summary: The Microsoft-friendly (or Microsoft-sponsored) media isnt mentioning this, but there are still Microsoft layoffs this week and those have nothing to do with prior layoff waves
22:54
c-ares multiple vulnerabilities: CVE-2023-32067, CVE-2023-31147, CVE-2023-31130, CVE-2023-31124 Open Source Security
Posted by Brad House on May 22
CVE-2023-32067Impact
Denial of Service.
Attack Steps:
1. The target resolver sends a query
2. The attacker forges a malformed UDP packet with a length of 0 and
returns them to the target resolver
3. The target resolver erroneously interprets the 0 length as a
graceful shutdown of the connection. (this is only valid for TCP
connections, UDP is connection-less)
4. Current resolution fails, DoS attack is achieved....
22:47
Bad Magic's Extended Reign in Cyber Espionage Goes Back Over a Decade The Hacker News
New findings about a hacker group linked to cyber attacks targeting companies in the Russo-Ukrainian conflict area reveal that it may have been around for much longer than previously thought. The threat actor, tracked as Bad Magic (aka Red Stinger), has not only been linked to a fresh sophisticated campaign, but also to an activity cluster that first came to light in May 2016. "While the
22:38
Nick Black has put together an extensive guide to the io_uring API and the lib_uring user-space library.
It combines asynchronous I/O, system call polybatching, and flexible buffer management, and is IMHO the most substantial development in the Linux I/O model since Berkeley sockets (yes, I'm aware Berkeley sockets preceded Linux. Let's then say that they're the most substantial development in the UNIX I/O model to originate in Linux)
22:25
AMDVLK 2023.Q2.2 Brings New Extension For VKD3D-Proton, Performance Tuning Phoronix
It's been over one month since the release of AMDVLK 2023.Q2.1 while today it's been succeeded by the AMDVLK 2023.Q2.2 update...
22:09
Google's Working Set Reporting Feature Aims To Better Deal With Over-Committed VMs Phoronix
Google engineers this month have begun posting new patches for the Linux memory management subsystem and related components for a feature dubbed Working Set Reporting...
22:00
IBM partners with global universities to develop a quantum-centric supercomputer Help Net Security
IBM announced a 10-year, $100 million initiative with the University of Tokyo and the University of Chicago to develop a quantum-centric supercomputer powered by 100,000 qubits. Quantum-centric supercomputing is an entirely new, and as of now, unrealized, era of high-performance computing. A 100,000-qubit system would serve as a foundation to address some of the worlds most pressing problems that even the most advanced supercomputers of today may never be able to solve. For example, such More
The post IBM partners with global universities to develop a quantum-centric supercomputer appeared first on Help Net Security.
21:56
It's Over: Intel Publishes "x86-S" Specification, for 64-Bit Only x86 Architecture SoylentNews
Intel Publishes "X86-S" Specification For 64-bit Only Architecture
Intel quietly released a new whitepaper and specification for their proposal on "X86-S" as a 64-bit only x86 architecture. If their plans workout, in the years ahead we could see a revised 64-bit only x86 architecture.
Entitled "Envisioning a Simplified Intel Architecture", Intel engineers lay the case for a 64-bit mode-only architecture. Intel is still said to be investigating the 64-bit mode-only architecture that they also refer to as "x86S". Intel is hoping to solicit industry feedback while they continue to explore a 64-bit mode only ISA.
[...] Under this proposal, those wanting to run legacy 32-bit operating systems would have to rely on virtualization. To further clarify, 32-bit x86 user-space software would continue to work on modern 64-bit operating systems with X86-S.
Also at Tom's Hardware.
Read more of this story at SoylentNews.
21:22
Using nanofaceting to manipulate quantum dots into nanocrystals Lifeboat News: The Blog
A new method of controlling the shape of tiny particles about one tenth of the width of human hair could make the technology that powers our daily lives more stable and more efficient, scientists claim.
The process, which transforms the structure of microscopic semiconductor materials known as quantum dots, provides industry with opportunities to optimize optoelectronics, energy harvesting, photonics, and biomedical imaging technologies, according to the Cardiff University-led team.
Their study, published in Nano Letters, used a process called nanofacetingthe formation of small, flat surfaces on nanoparticlesto manipulate the quantum dots into a variety of shapes called nanocrystals.
21:12
Are Your APIs Leaking Sensitive Data? The Hacker News
It's no secret that data leaks have become a major concern for both citizens and institutions across the globe. They can cause serious damage to an organization's reputation, induce considerable financial losses, and even have serious legal repercussions. From the infamous Cambridge Analytica scandal to the Equifax data breach, there have been some pretty high-profile leaks resulting in massive
21:10
Mastermind Behind iSpoof Fraud Website Sentenced to 13 Years in the UK HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
The founder of iSpoof is named Tejay Fletcher and is from the Western Gateway area of London, England.
This is a post from HackRead.com Read the original post: Mastermind Behind iSpoof Fraud Website Sentenced to 13 Years in the UK
21:02
CVE-2023-28709 Apache Tomcat - Fix for CVE-2023-24998 was incomplete Open Source Security
Posted by Mark Thomas on May 22
CVE-2023-28709 Apache Tomcat - Fix for CVE-2023-24998 was incompleteSeverity: Moderate
Vendor: The Apache Software Foundation
Versions Affected:
Apache Tomcat 11.0.0-M2 to 11.0.0-M4
Apache Tomcat 10.1.5 to 10.1.7
Apache Tomcat 9.0.71 to 9.0.73
Apache Tomcat 8.5.85 to 8.5.87
Description:
The fix for CVE-2023-24998 was incomplete. If non-default HTTP connector
settings were used such that the maxParameterCount could be reached
using query...
21:00
ChatGPT Rules the World or, at Least, the Home Hackaday

With all the hype about ChatGPT, it has to have crossed your mind: how can I make it control devices? On the utopia side, you could say, Hey, ChatGPT, figure out what hours Im usually home and set the thermostat higher when I am away. On the dysfunctional side, the AI could lock you in your home and torment you like some horror movie. We arent to either extreme yet, but [Chris] couldnt resist writing a ChatGPT plugin to control a Raspberry Pi. You can see a video of how it turned out below.
According to [Chris], writing a ChatGPT plugin is actually much simpler than you think. You can see in the video the AI can intuit what lights to turn on and off based on your activity, and, of course, many more things are possible. It can even detect snoring.
In a bit of self-referential work, ChatGPT actually wrote a good bit of the code required. Heres the prompt:
Write me a Python Flask API to run on a Raspberry Pi and control some lights attached to GPIO pins.
I have the following lights:
Kitchen: pin 6
Bedroom: pin 13
Dining table: pin 19
Bathroom: pin 26
Lounge: pin 5
I want the following endpoints:
get lights - returns the list of lights along with their current state...
20:56
China bans chip maker Micron from its key information infrastructure Security Affairs
The Chinese government announced the ban on the products made by the US memory chip giant Micron Technology over national security concerns.
The Cyberspace Administration of China announced the ban on products made by US memory chip giant Micron Technology over security concerns. The ban is related to the use of company products in key infrastructure projects.
The decision is the last act of the dispute between China and the U.S., both countries recognize the importance of technological sovereignty for the development and growth of their economies and are aware of the potential risks of using technological solutions provided by hostile governments.
The countrys cyberspace regulator announced that the decision results from the failure of a network security assessment conducted by the Network Security Review Office on Microns products sold in China.
A few days ago, the Network Security Review Office conducted a network security review of Microns products sold in China in accordance with the law. reads the official announcement.
The review found that Microns products have relatively serious potential network security issues, which pose a major security risk to my countrys key information infrastructure supply chain and affect my countrys national security. For this reason, the Network Security Review Office has made a conclusion that the network security review should not be passed. According to the Network Security Law and other laws and regulations, operators of critical information infrastructure in China should stop purchasing Micron products.
According to the announcement, the assessment revealed the presence of severe security issues in the products made by Micron that pose severe risks to the national key information infrastructure.
The announcement pointed out that the government of Beijing is promoting collaboration with foreign manufacturers, but their products must be compliant with Chinese laws and regulations.
The purpose of this network security review of Microns products is to prevent product network security issues from endangering the security of the countrys key information infrastructure, which is a necessary measure to maintain national security. China firmly promotes high-level opening up to the outside world. As long as it abides by Chinese laws and regulations, companies from all countries and various platforms are welcome to enter the Chinese market.
The ban is the first major action against a US chip maker, on the other end, the US Government has already adopted similar actions against Chinese giants.
Micron has been already notified by the Chinese authorities abo...
20:53
AI Company Says Itll Perform a Seance on Your Dead Loved Ones cryptogon.com
You could power a Type III civilization on the amount of cringe contained in this article. Via: Futurism: Were trying to make it sound as magical and as mystical as possible.
20:28
Vulnerability in Zyxel firewalls may soon be widely exploited (CVE-2023-28771) Help Net Security
A recently fixed command injection vulnerability (CVE-2023-28771) affecting a variety Zyxel firewalls may soon be exploited in the wild, Rapid7 researchers have warned, after publishing a technical analysis and a PoC script that triggers the vulnerability and achieves a reverse root shell. About CVE-2023-28771 CVE-2023-28771 affects: Zyxel APT, USG FLEX, and VPN firewalls running versions v4.60 to v5.35 of the ZDL firmware, and Zyxel ZyWALL/USG gateways/firewalls running ZLD v4.60 to v4.73 These firewall devices monitor More
The post Vulnerability in Zyxel firewalls may soon be widely exploited (CVE-2023-28771) appeared first on Help Net Security.
20:11
Testing Intel Raptor Lake With PCID Disabled & A Move Made By FreeBSD Last Year Phoronix
With Linux going to disable PCID support on Intel Alder Lake and Raptor Lake while waiting for mitigated microcode due to a CPU bug, I was curious if this disabling of Process Context Identiifiers would have any overall performance implications. So I ran some benchmarks this weekend...
19:58
RADV Vulkan Driver Implements Smooth Lines For Zink Phoronix
The Mesa Radeon Vulkan driver "RADV" has implemented smooth lines support for in turn to be leveraged by the Zink OpenGL-on-Vulkan driver...
19:38
TOP500 List Updated With Frontier Remaining At The Top Phoronix
The 61st edition of the TOP500 supercomputer list has been published this morning. The Frontier supercomputer continues to hold the top spot and the only true Exascale system...
19:24
Apple wants to transform the iPhone with generative AI Lifeboat News: The Blog
A flurry of job postings relating to AI suggests that Apple wants to invest in the AI revolution were going through.
19:13
A Turning Point for U.S. AI Policy: Senate Explores Solutions SoylentNews
Almost 20 years ago, Senator Ted Stevens was widely mocked and ridiculed for referring to the Internet as a series of tubes even though he led the Senate Commerce Committee which was responsible for regulating it. And just several years ago, members of Congress were mocked for their lack of understanding of Facebook's business model when Mark Zuckerberg testified about the Cambridge Analytica scandal.
Fast forward to this week, when the Senate Judiciary Committee held one of the most productive hearings in Congress in many years, taking up the challenge of how to regulate the emerging AI revolution. This time around, the senators were well-prepared, knowledgeable and engaged. Over at ACM, Marc Rotenberg, a former Staff Counsel for the Senate Judiciary Committee has a good assessment of the meeting that notes the highlights and warning signs:
It is easy for a Congressional hearing to spin off in many directions, particularly with a new topic. Senator Blumenthal set out three AI guardrailstransparency, accountability, and limitations on usethat resonated with the AI experts and anchored the discussion. As Senator Blumenthal said at the opening, "This is the first in a series of hearings to write the rules of AI. Our goal is to demystify and hold accountable those new technologies and avoid some of the mistakes of the past."
Congress has struggled in recent years because of increasing polarization. That makes it difficult for members of different parties, even when they agree, to move forward with legislation. In the early days of U.S. AI policy, Dr. Lorraine Kisselburgh and I urged bipartisan support for such initiatives as the OSTP AI Bill of Rights. In January, President Biden called for non-partisan legislation for AI. The Senate hearing on AI was a model of bipartisan cooperation, with members of the two parties expressing similar concerns and looking for opportunities for agreement.
Read more of this story at SoylentNews.
18:41
Certified Anti-Piracy Coach Helps Piracy Addicts Go Legal TorrentFreak
 The insidious nature of a developing addiction often
takes people by surprise, regardless of the substance involved, but
especially when its freely available, all over the internet.
The insidious nature of a developing addiction often
takes people by surprise, regardless of the substance involved, but
especially when its freely available, all over the internet.
While an occasional copy-and-paste is known to alleviate boredom, peer pressure at a vulnerable moment can lead to a whole file or even an entire folder being permanently copied to a USB stick.
Most people feel no ill effects but for thrill-seekers, the instant high is over in moments, triggering a vicious cycle of increasingly risky copying and diminishing returns.
A new campaign unveiled at the Cannes Film Festival aims to raise awareness of this addiction and how creators end up suffering the consequences.
Protecting Creation Against Piracy: Can We Go Further?
Revealed during an anti-piracy roundtable at the Festival on Saturday, the campaign is the work of two French government agencies CNC (National Centre for Cinema and the Moving Image) and ARCOM, the new anti-piracy/audiovisual regulator in France.
CNC CEO Olivier Henrard and ARCOMs Denis Rapone unveiled the campaign with support from Charles Rivkin, Chairman and CEO of the Motion Picture Association.

The ambition of this campaign, with a slightly offbeat tone, is to encourage more and more Internet users to change their habits in favor of practices that respect creation, ARCOM notes.
In 2022, 86% of French Internet users aged 15 and over have consumed at least one cultural good online, films, series, video games, music, etc.
Recovering Piracy Addicts in Therapy
The campaign features a series of spots set to appear on television, cinema, radio and social networks, from June 15, 2023. They reveal the struggles of recovering piracy addicts as they transition from illegal to legal content with the help of Isabelle Champart, a certified anti-piracy coach/therapist.
It appears that with guidance from Isabelle, French piracy addicts will make a full recovery and have no further use for her skills. Heres a sneak preview of six slo...
18:00
The Wizard of Semiconductors Hackaday

If you have three hours and you want to learn the fundamentals of semiconductors, [Tiny Tapeout] has something for you: An introduction to SiliWiz. Youll also need the SiliWiz software (or use it online), which resembles the kind of tools that chip designers use but is meant for students to use as a learning tool
Using SiliWiz, you create layers on a virtual device, and you can use Spice to view the results. The tutorial is meant to be high-level and is suggested for students aged 14 or over (but we liked it and we are quite a bit older than that). Some more advanced material is also available at the same site.
SiliWiz is easy to use. You build layers of n or p material, metal, or polysilicon. A slider lets you show a cross-section at a particular point. You label metal endpoints and use the simulation to plot the results. As expected, the process mimics a simplified
Weve had experience designing and doing failure analysis on ICs, and it is truly a different world. For example, resistors created with diffusion or polysilicon are typically difficult to make precise (thats why you see laser-trimmed resistors on expensive precision components). However, because photolithography is very precise, the ratio of two capacitors can be a very dependable value even...
17:39
IRC Proceedings: Sunday, May 21, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-210523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-210523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-210523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-210523.gmi
Over HTTP:
|
... |
17:24
Links 22/05/2023: GNU Diffutils 3.10 and TCMS 12.3 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
-
GNU/Linux
-
DebugPoint Exploring Linux Advancements: GSoC 2023 Showcases Promising Projects
Google Summer of Code (GSoC) is an annual program initiated by Google that encourages students worldwide to contribute to open-source software development. Under the GSoC program, selected students to work on coding...
-
17:23
Can charismatic robots help teams be more creative? Lifeboat News: The Blog
Increasingly, social robots are being used for support in educational contexts. But does the sound of a social robot affect how well they perform, especially when dealing with teams of humans? Teamwork is a key factor in human creativity, boosting collaboration and new ideas. Danish scientists set out to understand whether robots using a voice designed to sound charismatic would be more successful as team creativity facilitators.
We had a robot instruct teams of students in a creativity task. The robot either used a confident, passionateie charismatictone of voice or a normal, matter-of-fact tone of voice, said Dr. Kerstin Fischer of the University of Southern Denmark, corresponding author of the study in Frontiers in Communication. We found that when the robot spoke in a charismatic speaking style, students ideas were more original and more elaborate.
We know that social robots acting as facilitators can boost creativity, and that the success of facilitators is at least partly dependent on charisma: people respond to charismatic speech by becoming more confident and engaged. Fischer and her colleagues aimed to see if this effect could be reproduced with the voices of social robots by using a text-to-speech function engineered for characteristics associated with charismatic speaking, such as a specific pitch range and way of stressing words. Two voices were developed, one charismatic and one less expressive, based on a range of parameters which correlate with perceived speaker charisma.
17:20
Gemini Links 22/05/2023: Titan Uploads and INN Techrights
-
Gemini* and Gopher
-
Personal
-
The Diarrhea Grill
I have quit reading columns about street foods recommended by a can driver who tells the readers about places where you can find cheap affordable food.
I havent quit because the column is not interesting but because of anonymous comments people leave there. There are always those people who tell you that theyve got diarrhea. Wow! Interesting! Now Ive got a good idea: go to those places without the people who tell you that theyve got diarrhea there! -
Status report
I have been a bit inactive here. There are several reasons: work (it is not going to improve, unfortunately), some personal stuff (we have been replacing the old heating system with a bit more modern one) and some illness.
-
Summer is here
This week I did a Pebble battery replacement. It was fortunate, one could say,
that the battery had swollen in my Pebble Time Round as it had, because it
separated the display from the body, which saved me a lot of work trying to
pry the watch open with a spudger. Once its open, there are two connectors and
three small screws and theres the battery in the middle. -
Happy Mothers Day
Thursday morning at 04:16 there was a 5.2 earthquake in Chiba, which rattled
us in Tokyo as well. It woke me up and while the shaking wasnt really bad, it
wasnt much fun, either. There is an alert that goes off on mobile phones a few
seconds before an earthquake strikes woop woop woop earthquake! woop woop
woop earthquake! woop woop woop earthquake! and it can be terrifying if it
goes off early in the morning and wakes one from a deep sleep (I know from
experience.) I keep my phone in a different room though, so this time just the
shaking woke me up. - ...
-
-
17:01
U.K. Fraudster Behind iSpoof Scam Receives 13-Year Jail Term for Cyber Crimes The Hacker News
A U.K. national responsible for his role as the administrator of the now-defunct iSpoof online phone number spoofing service has been sentenced to 13 years and 4 months in prison. Tejay Fletcher, 35, of Western Gateway, London, was awarded the sentence on May 18, 2023. He pleaded guilty last month to a number of cyber offenses, including facilitating fraud and possessing and transferring
17:00
Freeman Dyson: the visionary thinker and maverick scientist who challenged authority Terra Forming Terra
TIME Travel Terra Forming Terra
An Excellent Green Energy Proposal From France Terra Forming Terra

Police Arrest Canadian Man For Opening Drug Store Selling Cocaine, Heroin, And More Terra Forming Terra

16:33
KeePass Exploit Allows Attackers to Recover Master Passwords from Memory The Hacker News
A proof-of-concept (PoC) has been made available for a security flaw impacting the KeePass password manager that could be exploited to recover a victim's master password in cleartext under specific circumstances. The issue, tracked as CVE-2023-32784, impacts KeePass versions 2.x for Windows, Linux, and macOS, and likely to be released early
16:25
The UKs Secretive Web Surveillance Program is Ramping Up SoylentNews
Official reports and spending documents show that in the past year, UK police have deemed the testing of a system that can collect people's "internet connection records" a success, and have started work to potentially introduce the system nationally. If implemented, it could hand law enforcement a powerful surveillance tool.
Critics say the system is highly intrusive, and that officials have a history of not properly protecting people's data. Much of the technology and its operation is shrouded in secrecy, with bodies refusing to answer questions about the systems.
At the end of 2016, the UK government passed the Investigatory Powers Act, which introduced sweeping reforms to the country's surveillance and hacking powers. The law added rules around what law enforcement and intelligence agencies can do and access, but it was widely criticizedfor its impact on people's privacy, earning it the name the "Snooper's Charter."
Particularly controversial was the creation of so-called internet connection records (ICRs). Under the law, internet providers and phone companies can be orderedwith a senior judge approving the decisionto store people's browsing histories for 12 months.
[...] Little is known about the development and use of ICRs. When the Investigatory Powers Act was passed, internet companies said it would take them years to build the systems needed to collect and store ICRs. However, some of those pieces may now be falling into place. In February, the Home Office, a government department that oversees security and policing in the UK, published a mandatory review of the operation of the Investigatory Powers Act so far.
The review says the UK's National Crime Agency (NCA) has tested the "operational, functional, and technical aspects" of ICRs and found a "significant operational benefit" of collecting the records. A small trial that "focused" on websites that provided illegal images of childre...
15:20
BatLoader campaign impersonates ChatGPT and Midjourney to deliver Redline Stealer Security Affairs
Researchers identified an ongoing BatLoader campaign relying on Google Search Ads to deliver rogue web pages for ChatGPT and Midjourney.
In early May, researchers at eSentire Threat Response Unit (TRU) spotted an ongoing BatLoader campaign using Google Search Ads to redirect victims to imposter web pages for AI-based services like ChatGPT and Midjourney.
The rogue pages are designed to promote fake apps of popular AI services.
In the campaign observed by the researchers, threat actors are using BatLoader in the form of MSIX Windows App Installer files to deliver the Redline Stealer. In February 2023, eSentire reported another BatLoader campaign targeting users searching for AI tools.
Both AI services are extremely popular but lack first-party standalone apps (i.e., users interface with ChatGPT via their web interface while Midjourney uses Discord). This vacuum has been exploited by threat actors looking to drive AI app-seekers to imposter web pages promoting fake apps. reads the analysis published by eSentire.
Users searching on Google for chatbpt were redirected to an imposter download page for ChatGPT hosted on hxxps://pcmartusa[.]com/gpt/.

Visitors are tricked into downloading a fake Windows ChatGPT app by clicking on the button on the landing page that actually redirect them to a BatLoader Payload site.
The installer is downloaded from the job-lionserver[.]site as Cha...
15:00
Blacklist untrustworthy apps that peek behind your firewall Help Net Security
With an increasing number of endpoints and expanding attack surfaces, dodgy apps can offer a way around your firewall. Due to data privacy concerns, Montana has passed the first bill in the United States to ban TikTok. Previously, India has banned 59 Chinese apps, including TikTok, after claiming they were transmitting user data back to China. But such bans are difficult to enforce, and the apps are just a few in a vast ocean. In More
The post Blacklist untrustworthy apps that peek behind your firewall appeared first on Help Net Security.
15:00
Weve Got A Saxaboom At Home Son Hackaday

Most parents have heard a familiar story. Their lovely child comes up, having seen a celebrity rocking out with a funny $20 toy from the 80s, and asks for it. Of course, you reply, its just 20 dollars. However, a quick scan through eBay reveals that everyone elses kid has also been asking for this obscure toy for a school event, which now costs around $700. [Ben] found himself in that exact position and made a crucial off-hand comment, I bet I could make one of those. That was how his hectic journey into the world of toy reproduction began.
All [Ben] had for reference when recreating a Sax-A-Boom were pictures and sound clips. Modeling complex sweeping shapes in CAD is difficult, and [Ben] commissioned a 3d model from a professional on Fiverr. [Ben] broke down the model into printable sections and tweaked it to account for buttons. After a concerning amount of putty, wet sanding, and elbow grease, [Ben] had a decently smooth body for an instrument. The devices guts is an ESP32-based board called Sonatino, built around music generation. The music samples came from a virtual instrument clone on GitHub and loaded onto an SD card.
Time pressure crept in towards the end, and [Ben] had to go for some dirty solution that he would have preferred (popsicle sticks and epoxy for button mounting). Yes, there were some gaps and paint...
14:45
Wireless Broadband Alliance CEO on key drivers for Wi-Fi adoption in enterprise networks Help Net Security
The demand for robust, reliable, and high-speed connectivity is increasing rapidly in the era of relentless digital transformation. This Help Net Security interview with Tiago Rodrigues, CEO at Wireless Broadband Alliance (WBA), delves into the future of enterprise networking, exploring the significant role of Wi-Fi 6E and Private 5G. What role does Wi-Fi 6E play in enterprise connectivity, and what advanced capabilities does it offer on the 6GHz spectrum? Wi-Fi 6E offers great improvements on More
The post Wireless Broadband Alliance CEO on key drivers for Wi-Fi adoption in enterprise networks appeared first on Help Net Security.
14:30
How generative AI is reshaping the identity verification landscape Help Net Security
The identity verification market is experiencing a significant surge in growth. In recent years, many solutions have emerged to assist businesses in establishing trust and facilitating remote user onboarding. This demand arises from the alarming rise in identity fraud, which has become more prevalent and sophisticated, resulting in substantial time and financial losses for businesses. In this Help Net Security video, Peter Violaris, Head of Legal, Compliance and Risk, EMEA for OCR Labs, discusses generative More
The post How generative AI is reshaping the identity verification landscape appeared first on Help Net Security.
14:00
How continuous security monitoring is changing the compliance game Help Net Security
Managing compliance doesnt have to be draining, time-consuming, or overly complicated. In this Help Net Security video, Wesley Van Zyl, Senior Manager, Compliance Success at Scytale, discusses how keeping track of all your security controls can be challenging, particularly when new cybersecurity threats emerge unexpectedly. To maintain consistent compliance and reliable monitoring, it is essential to incorporate automation technology into your compliance management system. By doing so, you can effectively mitigate the risk of human More
The post How continuous security monitoring is changing the compliance game appeared first on Help Net Security.
13:38
California Pot Industry Facing 'Extinction Event' SoylentNews
Industry insiders are warning that hundreds of pot shops could go out of business this year:
California's pot industry could be on the verge of an "extinction event," with pot shops going out of business as they miss tax payments and sink under millions of dollars of debt.
Debt problems have plagued the industry for years a 2022 report estimated that the industry was collectively sitting on over $600 million in debt but a change in tax law that took effect this year has stakeholders worried the mounting debt bubble will finally become fatal. A San Francisco politician introduced a law this year in the state legislature that would crack down on pot businesses that don't pay their debts.
State law recently shifted the burden for paying cannabis excise taxes from distributors to retailers, with the first tax payments due May 1. Retailers have historically had the most trouble paying their bills, and it appears that many shops lack the cash to pay their state excise taxes, according to new state tax data obtained by SFGATE.
Over 13% of California's retailers, or 265 pot shops, failed to make any tax payment by the May 1 deadline, according to the California Department of Tax and Fee Administration. Those businesses are now facing a 50% penalty on the taxes they owe, which could be a death blow to many shops.
[...] The entire cannabis supply chain has faced a chronic debt problem: Farmers report never getting paid for thousands of dollars in product, distributors say retailers don't pay them and have started blacklisting some shops, and even the federal government is getting stiffed. An analysis done last fall by Green Market Report found that 10 of the largest pot companies in the country owed over $500 million combined in unpaid taxes.
Related: How State Cannabis Legalization Became a Boon for Corruption
...
13:30
Malicious links and misaddressed emails slip past security controls Help Net Security
The majority of organizations use six or more communication tools, across channels, with email remaining the channel seen as the most vulnerable to attacks (38%), according to Armorblox. Respondents mentioned multi-channel attacks are gaining momentum and frequency. More than half of respondents reported multi-vector, socially engineered attacks happening weekly (36%) or daily (16%). Communication and collaboration concerns The level of concern is high for attacks evading security controls by leveraging siloed communication and collaboration tools More
The post Malicious links and misaddressed emails slip past security controls appeared first on Help Net Security.
13:00
What flying a plane can teach you about cybersecurity Help Net Security
Before taking on the role as GM of IAIs cyber division, Esti Peshin was the Director General of the Hi-Tech Caucus in Israels parliament, balancing legislation and regulation to strengthen the countrys renowned Hi-Tech ecosystem. Where cyber security and aviation are headed Laying out the terrain of the aviation landscape The commercial aviation ecosystem includes few major players. So there are the airplanes themselves, manufactured by the OEMs. Plus, there are the airports and then More
The post What flying a plane can teach you about cybersecurity appeared first on Help Net Security.
12:00
Watch a Web Page Fetch Itself Over TLS, Complete With Commentary Hackaday

TLS, byte by byte performs an unusual and interesting function: it fetches itself over HTTPS, and provides a complete annotation of whats going on in the process, one byte at a time. Visit the site and give the button a click to watch it happen, its neat!
Transport Layer Security (TLS) is whats responsible for encrypting traffic over the internet, and its normally implemented on top of TCP to encrypt an application-layer protocol like HTTP (resulting in HTTPS and the little padlock icon in browsers indicating a connection with a web site is encrypted.) Back in the day, traffic over the internet was commonly unencrypted, but nowadays no communication or hardware is too humble for encryption and methods are easily accessible.
So for what purpose would someone actually need or use such an implementation of TLS? Well, probably no one actually needs it. But it is a userspace TLS implementation in javascript that may fit a niche for someone, and it certainly provides beautifully-indented and annotated binary data in the process. So...
10:15
DistroWatch Weekly, Issue 1020 DistroWatch.com: News
This week in DistroWatch Weekly: Review: UBports 20.04 on PinePhoneNews: Debian prepares for the launch of Bookworm, 20 years of running GentooQuestions and answers: Finding another machine's IP address and finding distributions with a recent kernelReleased last week: Tails 5.13, Rocky Linux 9.2Torrent corner: KDE neon, Manjaro Linux,....
10:00
HPR3861: How To find Things on your home Network Hacker Public Radio
Hey guys I lost my Raspberry Pi Zero W - its place in the house. I am not sure if it's on solar power running or not. But in in any case it's not out and about at the normal locations in my home for such items. So I use an App called Network Analyzer on my Huawei phone to find the IPs in use in the home. Then use putty go and see how the PI is doing. Enjoy the Show
09:44
Read issue #251 of Lifeboat News! Lifeboat News
Read issue #251 of Lifeboat News!
09:06
OTB#53: Clo de 5 a 7 Random Thoughts
What? This is in colour? But but
*phew* I thought I was watching the wrong movie I saw this one a few years back, but Im rewatching it now because Criterion published a fabulous Agns Varda bluray box set apparently with all her movies? Im looking forward to watching them all after Im done with this Sight & Sound mo...
08:51
Cybersickness More Likely to Affect Women SoylentNews
Psychology professor Jonathan Kelly studies human computer interaction, spatial cognition and virtual reality. He says gender discrepancies in cybersickness may not seem that important when it's related to video games and other forms of entertainment.
"But it's still a problem, and when VR gets to the point where it's a bigger part of job training or education in a classroom, it's even more important to make sure people can access this technology. If not, a lot of people are going to get left out, and there could be a backlash," says Kelly.
Like motion sickness, cybersickness can occur when there's a mismatch between visual motion and body motion. Symptoms, including nausea, dizziness, headaches and eye fatigue, usually resolve quickly after removing the headset. But in severe cases, they sometimes last for hours.
[...] As part of a larger study on adaptation to cybersickness, the ISU researchers recruited 150 participants to play up to 20 minutes of a VR game with a headset. The participants were new to VR and could stop if they felt too sick to continue. The researchers found women ended the game early twice as often as men and reported a sickness intensity that was 40% higher.
[...] For the second paper, the researchers explored whether the distance between an individual's pupils could help explain the gender difference in cybersickness. VR headsets have an adjustable lens set-up to accommodate different users, but some people fall outside the range. The researchers found women participants on average had smaller distances between their pupils than men, but it did not predict whether they would get cybersick during the game.
What seemed to matter more was whether they had previous experience with motion sickness or screen sickness (e.g., feeling sick in movie theaters, while playing a video game.)
"Women reported experiencing more motion sickness and screen-based sickness than men, and this increased susceptibility is part of the reason that women experience more cybersickness," says Kelly.
Journal References:
J. W. Kelly, S. B. Gilbert, M. C. Dorneich
and K. A. Costabile, "Gender differences in cybersickness:
Clarifying confusion and identifying paths forward," 2023 IEEE
Conference on Virtual Reality and 3D User Interfaces Abstracts and
Workshops (VRW), Shanghai, China, 2023, pp. 283-288,
doi:...
07:52
Linux 6.4-rc3 Released Following A Rather Smooth Week Phoronix
Linus Torvalds just released the Linux 6.4-rc3 kernel following a rather uneventful week...
07:24
Kernel prepatch 6.4-rc3 LWN.net
Linus has released 6.4-rc3 for testing.
"Nothing really huge stands out there
".
05:20
A Decade of Pirate Bay Proxy War: Did ISP Blocking Slay the Hydra? TorrentFreak
 Argentina, Australia, Austria, Belgium and Brazil; just
two letters of the alphabet and thats already five countries that
have implemented ISP blocking against The Pirate Bay.
Argentina, Australia, Austria, Belgium and Brazil; just
two letters of the alphabet and thats already five countries that
have implemented ISP blocking against The Pirate Bay.
The growing list, which continues with Denmark and persists through Finland, France and Germany, doesnt stop until it reaches the United Arab Emirates and finally, the UK.
Thats around 30 countries overall, give or take, that have resorted to ISP blocking because no matter whats thrown at it, The Pirate Bay simply refuses to die.
At least in part, the site is still alive after more than a decade of widespread blocking due to the existence of proxy sites. These sites tend to look and feel like The Pirate Bay but operate from different domain names that arent yet on ISP blocklists.
This means that otherwise blocked internet users get to enjoy broadly the same Pirate Bay experience as they did before. At least for a while.
Rightsholders Also Block Pirate Bay Proxies
As reported yesterday, one of the most popular Pirate Bay proxy indexing sites recently disappeared from GitHub.
ProxyBay was a significant player, one that had helped dozens of millions of users gain access to The Pirate Bay by directing them to active Pirate Bay proxy sites. However, in common with The Pirate Bay itself, proxy sites are also subjected to ISP blocking, which can render some of them redundant, not to mention inaccessible.
Given that proxy sites and proxy indexes contribute to the overall health of the Pirate Bay hydra, that got us thinking: Is the hydra alive and well? Or has it lost a few too many heads over the years?
Data Sources Used
While were aware that proxy sites face blocking in several countries, until today wed never drilled into the details. It quickly became apparent that a complete overview would require significant time and resources but our short report today should help set the tone.
To weigh rightsholders responses to strictly Pirate Bay proxy sites, we obtained domain blocking lists used by ISPs in the UK, Denmark and Italy. The original plan was...
04:03
Futurama Returns With New Episodes After a 10-Year Layoff SoylentNews
New Futurama episodes are hitting Hulu in July:
One of the greatest cartoons of the modern era is making a return after a 10-year layoff, and you won't have to wait long to start enjoying brand new episodes. The first new episode of season eight will premiere on Hulu on July 24, with subsequent episodes to follow on Mondays.
Hulu ordered a 20-episode run of Futurama in February of last year that will see much of the original show's voice actors and crew return, including executive producers Matt Groening (The Simpsons) and David X. Cohen (Beavis and Butt-Head). Billy West, Katey Sagal, Maurice LaMarche, Tress MacNeille, Lauren Tom, Phil LaMarr, and David Herman are all back, as is John DiMaggio who voices Bender.
Futurama premiered on Fox in the spring of 1999 and ran on the network for five seasons before getting canceled. The show would return in 2010 for a two season run on Comedy Central, with the final episode of that deal airing on September 4, 2013. The order with Hulu will mark the program's third platform, or fourth if you count the direct to DVD movies.
Season eight will initially consist of 10 episodes. It is unclear if the remaining 10 episodes from the original order will arrive as a second half of season eight or a new season entirely.
According to Hulu's description, new viewers will be able to pick up the series from here while Futurama diehards will be rewarded with payoffs to longstanding mysteries. Highlights are said to include developments in the relationship of Fry and Leela, the contents of Nibbler's litter box, the whereabouts of Kif and Amy's tadpoles, and the history of evil Robot Santa.
Read more of this story at SoylentNews.
03:00
Linux To Disable PCID For Intel Alder Lake & Raptor Lake Due To Issue With INVLPG Phoronix
A patch is pending via x86/urgent to workaround an issue with Intel Alder Lake and Raptor Lake processors that is leaving the kernel developers for the time being to disable Process Context Identifiers (PCID) with these Intel mobile/desktop processors...
01:25
PyPI Repository temporarily suspends user sign-ups and package uploads due to ongoing attacks Security Affairs
The Python Package Index (PyPI) maintainers have temporarily disabled the sign up and package upload processes due to an ongoing attack.
The maintainers of Python Package Index (PyPI), the Python software repository, have temporarily disabled the sign up and package upload processes due to an ongoing attack.
The maintainers opted to disable the above functionalities because they have observed a spike in the creation of malicious users and projects on the index in the past week.
New user and new project name registration on PyPI is temporarily suspended. The volume of malicious users and malicious projects being created on the index in the past week has outpaced our ability to respond to it in a timely fashion, especially with multiple PyPI administrators on leave. reads the Incident Report for Python Infrastructure published by the maintainers. While we re-group over the weekend, new user and new project registration is temporarily suspended.
The announcement doesnt provide details about the attacks, such as the threat actors, their motivations and the malicious codes employed in the attacks.
The threat actors publish malicious packages to the PyPI repository and attempt to trick developers into using them using social engineering tricks, such as intentional typos in their names
The repository is a privileged target for threat actors that aim to carry out supply chain attacks aimed at developers.
This week, ReversingLabs researchers warned of the presence of two malicious packages, respectively named nodejs-encrypt-agent and nodejs-cookie-proxy-agent, in the npm package repository containing an open-source info-stealer called...
01:23
rogue and shes working around the clock to stop it saying sexually explicit things Lifeboat News: The Blog
01:22
Sorry, Elon Musk To Suggest Remote Work Isnt Morally Right is a Flawed Attempt to Push Your In-Person Work Agenda. Heres Why Lifeboat News: The Blog

Its as though Musk views in-person work as a kind of hazing ritual he and others did it, so you have to do it too. Well, as my mom frequently said when I proposed doing something dumb because others did it, If all your friends jumped off a bridge, would you?
Picture this: Musk standing on the precipice of the Golden Gate Bridge, urging us all to leap into the frigid waters below simply because he took the plunge. While his bravado might be admired by some, its not a practical or sustainable model for the future of work. Heres a thought: rather than Musks daredevil dive into the deep abyss of forced in-office work, perhaps we should consider a more measured, flexible and hybrid approach to work, one that incorporates both remote and in-person options, as I tell my clients.
Related: Employers: Hybrid Work is Not The Problem Your Guidelines Are. Heres Why and How to Fix Them.
01:22
Superconducting qubits have passed a key quantum test Lifeboat News: The Blog
A Bell test can confirm whether two systems are truly entangled it has now been used to confirm entanglement between qubits in a superconducting circuits.
By Leah Crane
01:00
Flat Lenses Made of Nanostructures Transform Tiny Cameras and Projectors IEEE Spectrum

Inside todays computers, phones, and other mobile devices, more and more sensors, processors, and other electronics are fighting for space. Taking up a big part of this valuable real estate are the camerasjust about every gadget needs a camera, or two, three, or more. And the most space-consuming part of the camera is the lens.
The lenses in our mobile devices typically collect and direct incoming light by refraction, using a curve in a transparent material, usually plastic, to bend the rays. So these lenses cant shrink much more than they already have: To make a camera small, the lens must have a short focal length; but the shorter the focal length, the greater the curvature and therefore the thickness at the center. These highly curved lenses also suffer from all sorts of aberrations, so camera-module manufacturers use multiple lenses to compensate, adding to the cameras bulk.
With todays lenses, the size of the camera and image quality are pulling in different directions. The only way to make lenses smaller and better is to replace refractive lenses with a different technology.
That technology exists. Its the metalens, a device developed at Harvard and commercialized at Metalenz, where I am an applications engineer. We create these devices using traditional semiconductor-processing techniques to build nanostructures onto a flat surface. These nanostructures use a phenomenon called metasurface optics to direct and focus light. These lenses can be extremely thina few hundred micrometers thick, about twice the thickness of a human hair. And we can combine the functionality of multiple curved lenses into just one of our devices, further addressing the space crunch and opening up the possibility of new uses for cameras in mobile devices.
Centuries of lens alternatives
Before I tell you how the metalens evolved and how it works, consider a few previous efforts to replace the traditional curved lens.
Conceptually, any device that manipulates light does so by altering its three fundamental properties: phase, polarization, and intensity. The idea that any wave or wave field can be deconstructed down to these properties was proposed by Christiaan Huygens in 1678 and is a guiding principle in all of optics.
 ...
...
00:58
Links 21/05/2023: Unifont 15.0.02 and KDE Plasma 6 Plans Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
00:26
The Moon Society's Lunar Development Conference 2023 will be held July 15-16 in cyberspace. Lifeboat News
The Moon Societys Lunar Development Conference 2023 will be held July 1516 in cyberspace.
Our Niklas Jrvstrt and Madhu Thangavelu will be speaking.00:00
Intel Suggests Dropping Everything But 64-Bit From X86 With Its X86-S Proposal Hackaday

In a move that has a significant part of the internet flashing back to the innocent days of 2001 when Intel launched its Itanium architecture as a replacement for the then 32-bit only x86 architecture before it getting bludgeoned by AMDs competing x86_64 architecture Intel has now released a whitepaper with associated X86-S specification that seeks to probe the communitys thoughts on it essentially removing all pre-x86_64 features out of x86 CPUs.
While today you can essentially still install your copy of MSDOS 6.11 on a brand-new Intel Core i7 system, with some caveats, its undeniable that to most users of PCs the removal of 16 and 32-bit mode would likely go by unnoticed, as well as the suggested removal of rings 1 and 2, as well as range of other low-level (I/O) features. Rather than the boot process going from real-mode 16-bit to protected mode, and from 32- to 64-bit mode, the system would boot straight into the 64-bit mode which Intel figures is what everyone uses anyway.
Where things get a bit hazy is that on this theoretical X86-S you cannot just install and boot your current 64-bit operating systems, as they have no concept of this new boot procedure, or the other low-level features that got dropped. This is whe...
Sunday, 21 May
23:25
Neeva, the would-be Google competitor, is shutting down its search engine Lifeboat News: The Blog
Weve discovered that it is one thing to build a search engine, and an entirely different thing to convince regular users of the need to switch to a better choice.
Neeva, which for a while looked like one of the startups with a real chance to challenge the supremacy of Google Search, announced on Saturday that it is shutting down its search engine. The company says its pivoting to AI and may be acquired by Snowflake, The Information.
Building search engines is hard, Neeva co-founders Sridhar Ramaswamy and Vivek Raghunathan wrote in a blog post announcing the shutdown.
Neeva was ahead of Google on a lot of things in search but still couldnt make users switch.
23:24
Grammarlys New CEO On Why ChatGPT Wont Kill His Business Lifeboat News: The Blog
Theres no kind of a priori right of this technology to upend our world, our lives and displace our own capabilities. I want technology to augment us, not displace us.
But the technology thats enabled Grammarly to expand its core offering could also disrupt it.
Fresh to the CEO role, Rahul Roy-Chowdhury talks about AI legislation, Grammarlys Russia ban and trying to leverage disruptive technologies.
23:24
Who Is Going to Regulate AI? Lifeboat News: The Blog
Summary.
As businesses and governments race to make sense of the impacts of new, powerful AI systems, governments around the world are jostling to take the lead on regulation. Business leaders should be focused on who is likely to win this race, moreso than the questions of how or even when AI will be regulated. Whether Congress, the European Commission, China, or even U.S. states or courts take the lead will determine both the speed and trajectory of AIs transformation of the global economy, potentially protecting some industries or limiting the ability of all companies to use the technology to interact directly with consumers.
Page-utils class= article-utilsvertical hide-for-print data-js-target= page-utils data-id= tag: blogs.harvardbusiness.org, 2007/03/31:999.357112 data-title= Who Is Going to Regulate AI? data-url=/2023/05/who-is-going-to-regulate-ai data-topic= Government policy and regulation data-authors= Blair Levin; Larry Downes data-content-type= Digital Article data-content-image=/resources/images/article_assets/2023/05/May23_28_5389503-383x215.jpg data-summary=
As the world reckons with the impact of powerful new AI systems, governments are jostling to lead the regulatory charge and shape how this technology will grow.
23:24
How do you solve a problem like out-of-control AI? Lifeboat News: The Blog
Plus: The open-source AI boom is built on Big Techs handouts. How long will it last?
Last week Google revealed it is going all in on generative AI. At its annual I/O conference, the company announced it plans to embed AI tools into virtually all of its products, from Google Docs to coding and online search. (Read my story here.)
Googles announcement is a huge deal. Billions of people will now get access to powerful, cutting-edge AI models to help them do all sorts of tasks, from generating text to answering queries to writing and debugging code. As MIT Technology Reviews editor in chief, Mat Honan, writes in his analysis of I/O, it is clear AI is now Googles core product.
23:24
Chatbot Arena helps you find the best open-source chatbot Lifeboat News: The Blog
Until now, there has been no easy way to compare the quality of open-source models. An e-sports-inspired system could help.
The Large Model System Organization (LMSYS), which is behind the open-source model Vicuna, has launched the benchmark platform Chatbot Arena to compare the performance of large language models. Different models compete against each other in anonymous, randomly selected duels. Users then rate the performance of the models by voting for their preferred answer.
23:24
ChatGPTs clever way of balancing 9 eggs with other objects convinced some Microsoft researchers that AI is becoming more like humans Lifeboat News: The Blog
Microsoft researchers asked GPT-4 to stack nine eggs with other objects; its grid solution startled them because it was so clever.
23:23
China is using AI to raise the dead, and give people one last chance to say goodbye Lifeboat News: The Blog
They wanted to speak to their dead grandparents one last time, so they used artificial intelligence to rebuild loved ones theyd lost.
23:19
Dark Web ChatGPT Unleashed: Meet DarkBERT SoylentNews
A language model trained on the fringes of the dark web... for science:
We're still early in the snowball effect unleashed by the release of Large Language Models (LLMs) like ChatGPT into the wild. Paired with the open-sourcing of other GPT (Generative Pre-Trained Transformer) models, the number of applications employing AI is exploding; and as we know, ChatGPT itself can be used to create highly advanced malware.
As time passes, applied LLMs will only increase, each specializing in their own area, trained on carefully curated data for a specific purpose. And one such application just dropped, one that was trained on data from the dark web itself. DarkBERT, as its South Korean creators called it, has arrived follow that link for the release paper, which gives an overall introduction to the dark web itself.
DarkBERT is based on the RoBERTa architecture, an AI approach developed back in 2019. It has seen a renaissance of sorts, with researchers discovering it actually had more performance to give than could be extracted from it in 2019. It seems the model was severely undertrained when released, far below its maximum efficiency.
Originally spotted on The Eponymous Pickle.
Related: People are Already Trying to Get ChatGPT to Write Malware
Read more of this story at SoylentNews.
23:07
Security Affairs newsletter Round 420 by Pierluigi Paganini International edition Security Affairs
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are free for you in your email box.
Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press.
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections where is reported
Securityaffairs or my name Pierluigi Paganini
Please nominate Security Affairs as your favorite blog.
Nominate Pierluigi Paganini and Security Affairs here here: https://docs.google.com/forms/d/e/1FAIpQLSepvnj8b7QzMdLh7vWEDQDqohjBUsHyn3x3xRdYGCetwVy2DA/viewform
22:51
Mr. Thomas Woodruffs Francis Rothbart!: Not Really a Review Random Thoughts
I was idly browsing twitter when I saw the news that Thomas Woodruffs comic book had been nominated for four (!) Eisner awards, and my first thought was man, the public relations dept at Fantagraphics have really done their jobs here presumably by sending copies of the book to all the Eisner judges, but I see now that that wouldnt be that expensive:
The 2023 Eisner Awards judging panel consists of librarian Moni Barrette, educator/collector Peter Jones, retailer Jen King, journalist Sean Kleefeld, scholar/comics creator A. David Lewis, and comics instructor/curator TJ Shevlin.
Because the book is shit. I mean, its really awful. I guess you could make a case for its so transgressive, dude, but its really just shitty and a waste of time. My main reaction when I read it was dude, are you OK?
Which made me read some of the reactions to the announcement and boy, some of Woodruffs previous students at the SVA piped up:
22:42
Arch Linux Completes Its Git Migration Phoronix
Arch Linux on Friday began its Git repository migration and as part of that discontinuing SVN access and some changes to how their package repositories are setup. Arch Linux's Git migration has now been successfully completed...
21:50
Links 21/05/2023: WordPress 6.2.2 and ESPClicker Techrights
![]()
Contents
-
GNU/Linux
-
Applications
-
Linux Links 7 Best Free and Open Source Replacements for ls
ls is a command to list computer files. ls is specified by POSIX and the Single UNIX Specification. When invoked without any arguments, ls lists the files in the current working directory.
The GNU Core Utilities or coreutils is a package of GNU software containing implementations for many of the basic tools, such as cat, ls, and rm, which are used on Unix-like operating systems.
There are many enterprising developers that look to update and enhance many of the commands available in coreutils. ls is no exception.
Heres our r...
-
-
21:45
Gemini Links 21/05/2023: ScummVM and Lagrange 1.16 Techrights
-
Gemini* and Gopher
-
Personal
-
Angel Rocks Hike 2023-05-20 (east of Fairbanks, AK, USA)
Emily and I went on a hike today to Angel Rocks, a trail east of Fairbanks, which goes along the Yukon River and then passes several tors, or rocky outcroppings. I have many pictures to share, so Ill just list them each with a brief description.
-
SpellBinding: DGIZNRL Wordo: ROBES
-
its you and me, phone entertain me
The ego-driven, hyped privilege of the mental/emotional DEMAND that a device I own *entertain* me. And also, why? Entertainment is good and needed in the world, especially that rendering physiological stimulation, feedback of positive consequence, et al., but why the effort/stress of picking up my phone and thinking: ok, lets find some digital amusement
-
-
Technical
-
To remember that ScummVM is great
I had a knowledge of ScummVM existence for a long time but Ive been playing only occasionally in several games for a short while that way. /Pierre Gilhodes/ created this month Gobliiins 5 as the classical 2D original [Gobliiins] style game, so Ive been made to run also the first Gobliiins again. Ive tried the playable Gobliiins 5 demo, and then Ive returned to the original Gobliiins series.
-
Will code you a chatbot for free, Anyone interested?
My chatbots can be tailored to your needs for Personal use (just not NSFW/Sex Bots, Please!). They can run in a terminal or cmd or with GUI and text-to-speech (see the link below in the demos section). My chatbots can, if needed, run on a Linux web server for online usage.
-
Internet/Gemin...
-
-
21:00
Heres How To Build a Tiny Compiler From Scratch Hackaday

Believe it or not, building a tiny compiler from scratch can be as
fun as it is accessible. [James Smith] demonstrates by making a
tiny compiler for an extremely simple programming language, and
showing off a hello world.
Heres what happens with a compiler: human-written code gets compiled into low-level machine code, creating a natively-executable result for a particular processor. [James] compiler created from scratch makes native x64 Linux ELF binary executables with no dependencies, an experience [James] found both educational and enjoyable. The GitHub repository linked below has everything one needs, but [James] also wrote a book, From Source Code to Machine Code, which he offers for sale to anyone who wants to step through the nitty-gritty.
The (very tin...
20:35
CVE-2023-31454: Apache InLong: IDOR make users can bind any cluster Open Source Security
Posted by Charles Zhang on May 21
Severity: importantAffected versions:
- Apache InLong 1.2.0 through 1.6.0
Description:
Incorrect Permission Assignment for Critical Resource Vulnerability in Apache Software Foundation Apache InLong.This
issue affects Apache InLong: from 1.2.0 through 1.6.0.
The attacker can bind any cluster, even if he is not the cluster owner. Users are advised to upgrade to Apache InLong's
1.7.0 or cherry-pick [1] to solve it.[1]...
20:33
CVE-2023-31453: Apache InLong: IDOR make users can delete others' subscription Open Source Security
Posted by Charles Zhang on May 21
Severity: importantAffected versions:
- Apache InLong 1.2.0 through 1.6.0
Description:
Incorrect Permission Assignment for Critical Resource Vulnerability in Apache Software Foundation Apache InLong.This
issue affects Apache InLong: from 1.2.0 through 1.6.0. The attacker can delete others' subscriptions, even if they are
not the owner
of the deleted subscription. Users are advised to upgrade to Apache InLong's 1.7.0 or...
20:30
CVE-2023-31206: Apache InLong: Attackers can change the immutable name and type of nodes Open Source Security
Posted by Charles Zhang on May 21
Severity: importantAffected versions:
- Apache InLong 1.4.0 through 1.6.0
Description:
Exposure of Resource to Wrong Sphere Vulnerability in Apache Software Foundation Apache InLong.This issue affects
Apache InLong: from 1.4.0 through 1.6.0. Attackers can change the immutable name and type of nodes of InLong. Users are
advised to upgrade to Apache InLong's 1.7.0 or cherry-pick [1] to solve it.
[1]...
20:28
CVE-2023-31103: Apache InLong: Attackers can change the immutable name and type of cluster Open Source Security
Posted by Charles Zhang on May 21
Severity: importantAffected versions:
- Apache InLong 1.4.0 through 1.6.0
Description:
Exposure of Resource to Wrong Sphere Vulnerability in Apache Software Foundation Apache InLong.This issue affects
Apache InLong: from 1.4.0 through 1.6.0.
Attackers can change the immutable name and type of cluster of InLong. Users are advised to upgrade to Apache InLong's
1.7.0 or cherry-pick [1] to solve it.
[1] ...
20:26
CVE-2023-31101: Apache InLong: Users who joined later can see the data of deleted users Open Source Security
Posted by Charles Zhang on May 21
Severity: importantAffected versions:
- Apache InLong 1.5.0 through 1.6.0
Description:
Insecure Default Initialization of Resource Vulnerability in Apache Software Foundation Apache InLong.This issue
affects Apache InLong: from 1.5.0 through 1.6.0. Users registered in InLong who joined later can see deleted users'
data. Users are advised to upgrade to Apache InLong's 1.7.0 or cherry-pick [1] to solve it.
[1] ...
20:23
CVE-2023-31098: Apache InLong: Weak Password Implementation in InLong Open Source Security
Posted by Charles Zhang on May 21
Severity: moderateAffected versions:
- Apache InLong 1.1.0 through 1.6.0
Description:
Weak Password Requirements vulnerability in Apache Software Foundation Apache InLong.This issue affects Apache InLong:
from 1.1.0 through 1.6.0.
When users change their password to a simple password (with any character or
symbol), attackers can easily guess the user's password and access the account.
Users are advised to upgrade to Apache...
20:21
CVE-2023-31066: Apache InLong: Insecure direct object references for inlong sources Open Source Security
Posted by Charles Zhang on May 21
Severity: importantAffected versions:
- Apache InLong 1.4.0 through 1.6.0
Description:
Files or Directories Accessible to External Parties vulnerability in Apache Software Foundation Apache InLong.This
issue affects Apache InLong: from 1.4.0 through 1.6.0. Different users in InLong could delete, edit, stop, and start
others' sources! Users are advised to upgrade to Apache InLong's 1.7.0 or cherry-pick [1] to solve it.
[1] ...
20:19
CVE-2023-31065: Apache InLong: Insufficient Session Expiration in InLong Open Source Security
Posted by Charles Zhang on May 21
Severity: moderateAffected versions:
- Apache InLong 1.4.0 through 1.6.0
Description:
Insufficient Session Expiration vulnerability in Apache Software Foundation Apache InLong.This issue affects Apache
InLong: from 1.4.0 through 1.6.0.
An old session can be used by an attacker even after the user has been deleted or the password has been changed.
Users are advised to upgrade to Apache InLong's 1.7.0 or cherry-pick [1],[2] to solve...
20:18
RADV Driver Lands More Vulkan Overhead Reduction Optimizations Phoronix
Timur Kristf of Valve's Linux graphics driver team has landed a new set of patches for Mesa 23.2 that are further optimizing the Radeon Vulkan driver "RADV" for lower overhead in some code paths...
20:16
CVE-2023-31064: Apache InLong: Insecurity direct object references cancelling applications Open Source Security
Posted by Charles Zhang on May 21
Severity: importantAffected versions:
- Apache InLong 1.2.0 through 1.6.0
Description:
Files or Directories Accessible to External Parties vulnerability in Apache Software Foundation Apache InLong.This
issue affects Apache InLong: from 1.2.0 through 1.6.0. the user in InLong could cancel an application that doesn't
belongs to it. Users are advised to upgrade to Apache InLong's 1.7.0 or cherry-pick [1] to solve it.
[1]...
20:14
CVE-2023-31062: Apache InLong: Privilege escalation vulnerability for InLong Open Source Security
Posted by Charles Zhang on May 21
Severity: importantAffected versions:
- Apache InLong 1.2.0 through 1.6.0
Description:
Improper Privilege Management Vulnerabilities in Apache Software Foundation Apache InLong.This issue affects Apache
InLong: from 1.2.0 through 1.6.0. When the attacker has access to a valid (but unprivileged) account, the exploit can
be executed using Burp Suite by sending a login
request and following it with a subsequent HTTP request
using the...
20:12
CVE-2023-31058: Apache InLong: JDBC URL bypassing by adding blanks Open Source Security
Posted by Charles Zhang on May 21
Severity: moderateAffected versions:
- Apache InLong 1.4.0 through 1.6.0
Description:
Deserialization of Untrusted Data Vulnerability in Apache Software Foundation Apache InLong.This issue affects Apache
InLong: from 1.4.0 through 1.6.0. Attackers would bypass the
'autoDeserialize' option filtering by adding blanks. Users are advised to upgrade to Apache InLong's 1.7.0 or
cherry-pick [1] to solve it.
[1]...
20:08
Search Tag bet365-3935 net-bet365-bet365-bet365-bet365-3935.net-bet365-bet365mW?YK=Yc h+ Media
Search Tag bet365-3935 net -bet365-bet365-bet365-bet365-3935.net
-bet365-bet365-bet365-bet365-3935.net -bet365-bet365mW?YK=Yc
-bet365-bet365mW?YK=Yc
Bet365 is one of the leading bookmakers in the sector for its sports betting offer, which of course includes eSports. No, bet365 is not a betting site that offers free bets as a bonus to customers. Check the entire list of payment methods on the site to see which ones are available in your specific region or country. Additionally, you should keep in mind that payment method exclusions apply to some of the aforementioned offers. Bingo can be quite interesting to play, and sometimes it is even more appealing than other casino games.
With some of the best odds on the market, you stand to win more from your bets at Bet365. They also make sure to offer a huge range of betting markets per event that come with excellent odds that you can take advantage of. Not to mention, there are regular betting promotions that can help place bets with improved odds as well. The Bet365 app is one of the highlights of the betting experience.
The casino has a lot of games and good venues should include a choice so that the player has something to look for. You always need to choose an institution that takes into account your preferences and definitely will not let you down. Virtual players will have their winnings added to their cash balance as soon as they have used up all the bonus spins. In other words, dont make it weird, bro because theyre watching for that. This number is calculated based on the amount of successful and erroneous combinations that a player obtains by pressing play for certain times. On this page you can try So Much Candy free demo for fun and learn about all features of the game, without risk of loosing any money.
Given this, one can notice this section is somewhat under-represented as compared with video pokies. The fact of having a license implies that the house must follow the New Zealand legislation and consequently also the dollarpea. This means that the house must keep the clients money safely and also make sure that it acts in accordance with the privacy law. Without a doubt, a New Zealand license gives us the maximum confidence to place bets with a company. From there, we just have to look at which of the companies that comply with the regulations, is the most convenient for our interests. Whenever someone has to deposit or send their money online, doubts arise about the reliability of the company that will handle it.
- If you are looking for a reliable and trustworthy online betting platform in New Zealand, Bet365 is definitely worth checking out.
- Providers of games of chance must adhere to strict rule...
20:08
ll Bet365 casino review: is it safe or is it a fraud? 2023 h+ Media
ll Bet365 casino review: is it safe or is it a fraud? 2023
The bets were placed during one of the traditionally slowest sports months of the year, filled with spicy jackpots and a nice blend of promotions and the best game providers. If the account is still suspended after doing so contact customer support so that you may workout the issue, Bovada is still by far and away the number one option for US players. GGPoker recently launched another of its own efforts at helping players improve through the Ask Fedor poker hand analysis feature, or what kind of a player you are. Each winning combination triggers an Avalanche, we are certain that you will find something that will keep you busy.
With support of gambling age restrictions and gambling addiction programs, such as the VIP room. However, that are waiting for you to explore once you have registered your own personal account here. With millions of people using their mobiles for just about anything, weve taken a closer look at this games features. The website has a comprehensive FAQ section that answers most of the common questions that users have. If you need further assistance, you can contact customer support via email, live chat, or phone. The customer support team is available 24/7, and they are knowledgeable and friendly.
It is as if the fresh gaming agent only acceptance you to definitely borrow money to wager, no obligation to return they for many who eliminate all of they. Usually, a casino slot games provides a share out of a hundredpercent. What this means is that should you gambled 5, 5 would be taken out of the newest 500 address because the one hundredpercent from 5 try 5. You are free to select the various video game on location, with some conditions. These may be easier to understand than just 100 percent free spins having variable philosophy.
Bet365 is a premier betting website that has been around since 2001. Although the operator established its online offering primarily as a sportsbook, there are other sections available on the site that can be accessed from the same account. These include three online casinos, an online poker room and a dedicated category for online bingo. My bets are constantly being settled wrong which is preventing me from cashing out at the true value. Or leave a text message where you can wait days for a response thats if u get one hahah..its the worst site with the worst customer service I have ever encountered.
Bet365 Games is the worlds favourite online sports betting company. Founded in 2000, the group employs over 5,000 people and has over 63 million customers worldwide. This will help to be sure to features an optimistic feel when to experience in the gambling establishment.
Wazamba is an exciting casino that offers an excellent selection of games, secure payment options, and professional customer support. Bizzo is an exciting casino that offers an excellent selection of games, secure payment options...
20:08
LLVM's libc Gets Much Faster memcpy For RISC-V Phoronix
Being merged into LLVM's libc library recently are an optimized memory copy function "memcpy" implementation for the RISC-V architecture...
20:05
Bet365 Reviews & Ratings NZ 2023 Is Bet365 New Zealand Secure? h+ Media
Bet365 Reviews & Ratings NZ 2023 Is Bet365 New Zealand Secure?
When a new player deposits $20+ and clicks Claim Now in the related section, the casino releases a 100% match bonus up to $200. The beauty of the bonus is a super low wagering requirement of x15 (d+b); the WR like this is rarely found in competing casinos. Real-money betting requires prior depositing to a casino balance. The min limit is $10 for all methods, while ceiling values for depositing vary widely, e.g., $1000 for paysafecard and $30,000 for Visa. No commission or other deductions are made by the casino itself. Welcome, and other kinds of bonuses and promotions form one of the most integral parts of the global iGaming industry.
The casino makes use of distinct bonuses to appreciate their customers membership and preserve them excited throughout their gameplay. Other than providing world-class soccer video video games, Bet365 additionally has a wide range of on line on line casino video games. Their on-line on line casino has over one thousand video video games, together with lottery tickets, desk video games, and slots.
Already with a Spanish-speaking customer service team in place, due to their presence in other Latin American countries, any problems that arise can be dealt with efficiently. However, for those unfamiliar with the history or the connection, the gambling firm is based in Stoke and has close connections with the football club. You are reading more into this than required therefore deviating along the wrong road. The TAB still has the same betting but on top of that an oncourse system which promotes sponsors products as well. Women would more likely have a bet if there was a chance of winning a washing machine whilst hardened punters wouldnt mind shouting their kids a hard won prize. I wouldnt bet on anything where the result was a form of barter.
Bonus Bet365 can significantly increase the possibilities of profitable. If not one of the financial institution card is working directly with bet365, fund your skrill in its place and deposit to bet356 using skrill. The provided sum for closed wager depends upon the chosen selection progress. Provide your particulars on the registration kind similar to name, location, email, cellphone amount, and sort out.
Furthermore, players are always looking for various casino categories to enjoy daily. For the most part, they can play online slots, jackpots, scratchcards and table games, and live casino titles. The minimum deposit amount is $5 per deposit regardless of the payment method. The maximum deposit depends on the limits set by the player on his account. When Bet365 just came online, players could choose their own Bet365 bonus from an offer of four differentbonuses.
You can also contact the customer service via live chat, phone or email. However, if the bonus requirements are not met within 30 days of the first deposit, the funds from the bonus balance wil...
20:04
Bet365 Chat
Due to footballs popularity, odds can change before the actual event starts, so be sure to keep yourself updated. If you are looking for betting and casino offers from other brands in New Zealand, have a look at the Betway bonus code and Betiton bonus code. Bet365 has an industry-leading casino suite and the firms solid reputation means it has a fairly solid following. However, just with any other online casino, Bet365 is continually looking to entice new users by offering generous deals and promotions. Our Bet365 review takes a closer look at which promotions that platform is offering and gives you step-by-step instructions on how to go about claiming them.
They dont offer any sort of loyalty or VIP programme for Kiwi sports betters, or any betters for that matter. There is a place for a bonus code, but you wont need it we automatically gave you one when you clicked on our link. Your first bet must have odds of $1.20 or greater to qualify for the free bet credits. Deposits by Paysafecard will not qualify for the free bet credits. You must claim the free bet within 30 days of making your first deposit.
- The site header included handy tabs to help you switch the odds format, find the help feature, check your account balance and make a quick deposit.
- Wed say Bet365 has about as many NZ races as the TAB does, which is impressive for an international sports betting site.
- Furthermore, players can place their bets live on various sports markets and major sports events.
Due to the nature of gambling, I do not win every gaming session, but I sometimes get lucky like all other players. In fact, the casino has one of the best banking systems around. Aside from offering credit/debit cards and wire transfer deposit options, bet365 has a variety of alternative payment solutions you can use. Moreover, the complete banking service is very neatly organized, and the casino is somewhat transparent when it comes to transactional fees and withdrawal pending times. In addition, punters can sort supported payment options according to their country of residence.
Still, inside the profile section, you could activate auto money out, event alerts and look at your latest presents. The in-play software is used to examine statistics on stay in-play betting. Exclusive presents are nicely laid-out on the provides for model spanking new and eligible customers. For occasion, a gorgeous open account supply is in the marketplace for mannequin spanking new prospects. As a beginner, you can have as much as $30 wager credit score rating on the market should you qualify for the offer. My expertise on the platform is that it masses sooner hence enabling gamers to reap some nice advantages of the slight odds changes.
All you need to do is provide your personal details, including your name, address, and email address. Once you have registered, you will be eligible for a welcome bonus....
20:03
Bet365 Mobile and Online Casino Review h+ Media
Bet365 Mobile and Online Casino Review
Book a free test ride at Electrify NZ and enjoy the benefits of an e-bike today. In this way, you make it less likely to lose more than you can afford. When it is not fun anymore you need to take a break and then return another time when you are ready with a new budget.
Already with a Spanish-speaking customer service team in place, due to their presence in other Latin American countries, any problems that arise can be dealt with efficiently. However, for those unfamiliar with the history or the connection, the gambling firm is based in Stoke and has close connections with the football club. You are reading more into this than required therefore deviating along the wrong road. The TAB still has the same betting but on top of that an oncourse system which promotes sponsors products as well. Women would more likely have a bet if there was a chance of winning a washing machine whilst hardened punters wouldnt mind shouting their kids a hard won prize. I wouldnt bet on anything where the result was a form of barter.
No doubt, the interest repayments alone on the 120 million owed to it, would have gone a long way to covering the salaries of new hires. At 17.06 today I received a message from Charlie K saying that the documents I provided were blank and could I please provide another proof of address. I sent that through and received another notification saying the account was verified but now my ability to withdraw from the account had been removed.
From Disney to Harry Potter and Marvel, weve got all your fave Disney, Pixar and Marvel characters covered with shoes, clothing, accessories, and homewares that make the perfect gifts. Plus, get into our limited edition collaborations including Streets, Friends, The Office, Star Wars, Smiley and more. Dry and windy conditions can make it risky to light a fire or do work that can create sparks or heat. Learn about the fire seasons and fire danger index and what these mean for you, whether you live and work on a farm, lifestyle block, or are visiting rural Aotearoa. Punters from New Zealand, therefore, have the opportunity to use bet365 NZ to wager on sports.
Certain stores will not allow coupons to be stacked, which cancels out other Bet365 Voucher codes. While we are diligent to only give you active coupon code offers, an expired discount occasionally slips through the cracks. You can always contact us at 1001couponcodes.co.nz if you have any questions.
The minimum deposit and withdrawal amounts vary depending on the chosen means of payment, and range from $ 5 to $ 200. Bet365 is characterized by being one of the bookmakers that offers more means of payment to its users. The main advantage of this bookmaker is that it has a fantastic App that allows its users to place their bets both from the computer and from any mobile device. Bookmakers release welcome bonuses in order to attract players to join.
...19:51
Linux Adding Leakshield Driver Support For Reporting Liquid Cooling System Leaks Phoronix
There is pending patches for adding support for the LEAKSHIELD device to the Aquacomputer Linux device driver. German PC component manufacturer Aquacomputer has been enjoying support for their various products on Linux and the latest seeing support in this open-source driver is the Aquacomputer Leakshield for reporting any water cooling leaks and other performance metrics around your cooling setup...
19:09
[Meme] The Sirius Open Source Revolutionary Tax: Quietly Stealing Money From Peoples Salaries Under the Guise of Pension (That Doesnt Exist) Techrights
Summary: The crimes of Sirius Open Source remain without punishment, albeit we have plans to escalate up to three more levels to ensure justice is done (or to expose a system inherently tolerant of large-scale fraud)
18:58
PyPI Repository Under Attack: User Sign-Ups and Package Uploads Temporarily Halted The Hacker News
The maintainers of Python Package Index (PyPI), the official third-party software repository for the Python programming language, have temporarily disabled the ability for users to sign up and upload new packages until further notice. "The volume of malicious users and malicious projects being created on the index in the past week has outpaced our ability to respond to it in a timely fashion,
18:37
Study Finds 90% of Australian Teachers Can't Afford to Live Where They Teach SoylentNews
Study finds 90% of Australian teachers can't afford to live where they teach:
The teaching profession is already struggling with shortages and a lack of new candidates in a situation widely regarded as a crisis. Now, research warns that teachers are being priced out of housing near their schools, with many areas even too expensive for educators at the top of the pay scale.
The study, published recently in The Australian Educational Researcher analyzed quarterly house sales and rental reports in New South Wales (NSW) and found more than 90% of teaching positions across the statearound 50,000 full-time rolesare located in Local Government Areas (LGAs) where housing is unaffordable on a teacher's salary.
The situation is particularly dire for new teachers. There are 675 schoolsnearly 23,000 full-time teaching positionswhere the median rent for a one-bedroom place is unaffordable on a graduate teacher's salary.
Housing is considered unaffordable if a person spends more than 30% of their income on housing costssometimes called being in housing stress. Those in housing stress may not have enough money remaining to cover the cost of food, clothing, and other essentials.
But affordability isn't just an issue for early career teachers. For experienced educators at the top of the pay scale, 70 schoolsabout 2,000 full-time rolesare in an LGA where a single-bedroom dwelling is also unaffordable.
"The study shows the last time a first-year teacher salary could comfortably afford the rent for a one-bedroom dwelling was around a decade ago," says Professor Scott Eacott, the author of the study and Deputy Director of the Gonski Institute for Education at UNSW Arts, Design & Architecture.
Read more of this story at SoylentNews.
18:25
Action Fraud (British Police) Batch-Processing Cases Without Actually Dealing With Them? schestowitz.com
Video download link |
md5sum 48e9263394120bccc9b1a1adaaa76670
Action Fraud Bots
Creative Commons Attribution-No Derivative Works 4.0
Summary: Sirius Open Source stole money from its own staff and British police isnt doing anything on the matter (despite all the evidence being complete and unambiguous), so one is left with the impression that British businesses can basically get away with serious crimes, even against their own workers
TODAY I opened my E-mail client and I was greeted by a message or presented with a rather familiar message, which at first I thought was sent in error or perhaps wrongly dated because it closely resembled something that I had already received a month ago. As it turns out, Action Fraud operates a bit like a bot; instead of treating crime reports like reports of a crime (fraud) they seem to be treating them a bit like statistics and nothing suggests theyve even looked into the report. They just waited a month before issuing a template response, basically telling something that cannot be true, as the video above explains. The troubling thing is, this signals to anyone in the UK (employers in particular) that pension fraud or embezzlement is OK because law enforcement agencies wont even bother looking into complaints, even when the multiple UK victims and multiple UK perpetrator are all in the UK (no need to cooperate or work with entities outside the country).
I was going to phone Monday (after the Friday call fell on deaf ears*) but sent on the weekend both outside working days and outside working hours was a seemingly automated message. Despite all evidence provided, theres nothing to suggest anyone even looked into it and the message was almost identical to the first, hence akin to an automated reply, timed for 28 days after the report got filed. This is quite likely a very common modus operandi, basically programmed and wired into the system. This sort of gaslighting will shatter faith in the system of justice and accountability nationwide.
Reporting this or referring this to the ombu...
18:17
British Police Refuses to Tackle Fraud That Took Place 100% Inside Britain (Sirius Open Source) Techrights
Video download link |
md5sum 48e9263394120bccc9b1a1adaaa76670
Action Fraud Bots
Creative Commons Attribution-No Derivative Works 4.0
Summary: Sirius Open Source stole money from its own staff and British police isnt doing anything on the matter (despite all the evidence being complete and unambiguous), so one is left with the impression that British businesses can basically get away with serious crimes, even against their own workers
TODAY I opened my E-mail client and I was greeted by a message or presented with a rather familiar message, which at first I thought was sent in error or perhaps wrongly dated because it closely resembled something that I had already received a month ago. As it turns out, Action Fraud operates a bit like a bot; instead of treating crime reports like reports of a crime (fraud) they seem to be treating them a bit like statistics and nothing suggests theyve even looked into the report. They just waited a month before issuing a template response, basically telling something that cannot be true, as the video above explains. The troubling thing is, this signals to anyone in the UK (employers in particular) that pension fraud or embezzlement is OK because law enforcement agencies wont even bother looking into complaints, even when the multiple UK victims and multiple UK perpetrator are all in the UK (no need to cooperate or work with entities outside the country).
This is quite likely a very common modus operandi, basically programmed and wired into the system.I was going to phone Monday (after the Friday call fell on deaf ears*) but sent on the weekend both outside working days and outside working hours was a seemingly automated message. Despite all evidence provided, theres nothing t...
18:00
Week in review: KeePass vulnerability, Apple fixes exploited WebKit 0-days Help Net Security
Heres an overview of some of last weeks most interesting news, articles, interviews and videos: Apple fixes WebKit 0-days under attack (CVE-2023-28204, CVE-2023-32373, CVE-2023-32409) Apple has released security updates for iOS and iPadOS, macOS, tvOS and watchOS, delivering fixes for many vulnerabilities but, most importantly, for CVE-2023-32409, a WebKit 0-day that may have been actively exploited. Google Cloud CISO on why the Google Cybersecurity Certificate matters In this Help Net Security interview, Phil Venables, CISO More
The post Week in review: KeePass vulnerability, Apple fixes exploited WebKit 0-days appeared first on Help Net Security.
18:00
A Look Back at Computer Displays Hackaday

These days, our video cards are actually as powerful as yesterdays supercomputer and our monitors are bigger than the TVs most of us had as kids. But how did we get there? [RetroBytes] covers computer displays starting with the Colossus computer to today.
Back in the days of Colossus, of course, a display was actually a TeleType-like device printing on a roll of paper. The Manchester Baby actually had a crude display which was actually a Williams tube (no relation) that used phosphor persistence to store data. You could physically see memory on the tube or monitor it on a parallel tube an early form of memory-mapped display.
Early commercial computing used cards and often used a typewriter-like device as a console. Timesharing allowed people to use computers directly and drove innovation in user interface technology. Of course, displays didnt start out like the ones we use today. [RetroBytes] shows an old video game that uses vector display technology which was a common way screens worked on early computers. Essentially, the device was an XY oscilloscope driven by the computer.
TeleTypes gave way to glass TeleTypes or terminals. Power supplies and CRTs made these heavy, but they were the users window into the computer. Of course, eventually, the terminal would become the computer.
The video ends at the terminal. Of course, today, not only is the terminal the computer...
17:14
Lifeboat Foundation supports the Space Renaissance International goal of having the UN add the Sustainable Development Goal for "Space for All, on Earth and Beyond", to the UN's 2030 Agenda. Lifeboat News
Lifeboat Foundation supports the Space Renaissance International goal of having the UN add the Sustainable Development Goal for Space for All, on Earth and Beyond, to the UNs 2030 Agenda.
We are joining other organizations including the National Space Society and The Mars Society in this effort. Sign the petition today!17:02
IRC Proceedings: Saturday, May 20, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-200523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-200523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-200523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-200523.gmi
Over HTTP:
|
... |
15:05
When It Comes to Financial Spin-Doctoring, Microsoft is Now Marketers Marketers Marketers Marketers Techrights
Summary: Marketers from Microsoft and former Chief Marketing Officers or HR VPs too are trying to spin Microsofts collapsing business units (and mass layoffs that are under-reported and grossly under-counted in the media); how much of Microsofts remaining financial activity is just financialization and debt-loading (e.g. buying companies to offload debt onto them)?
Microsoft is 80 billion dollars in debt (a lot higher than its cash reserves or bank balance) and the layoffs carry on and on this year (...
15:00
Easy Graphene Production with a Laser Engraver Hackaday

Graphene isnt easy to produce at scale. But making small batches of graphene is doable in a few ways. [Robert Murray-Smith] decided to try producing flash graphene. This requires a big capacitor bank that is moderately expensive, so he decided to explain a different technique he read about using an ordinary laser cutter. Check it out in the video below.
We were a little disappointed that he didnt actually make any graphene this time. He has, however, used other methods in other videos to create some type of graphene. In fact, he has many similar videos going back quite a ways as well as applications with concrete, capacitors, and more. We understand that this method doesnt produce monolayer graphene, but actually creates a graphene foam with interesting properties. [Robert] talks about recent papers that show you can grow graphene on things other than Kapton tape using this method.
If you decide youd like to try this out, wed love to see your results. [James Tour] from Rice University has a video about laser-induced graphene that might help you, too. Weve seen [Zachary Tong]...
13:54
First Full-sized 3D Scan of the Wreck of the Titanic SoylentNews
Deep sea researchers have used two submersibles to make the first full, 3-dimensional scan of the wreck of the sunken passenger ship, The Titanic, including much of the 3-mile long debris field. This is a major step forward in evidence-based analysis of the wreck from over a hundred years ago.
The new scan was "devoid of that," he said, adding, "It is completely based on data and not human interpretation and that is why we are now seeing it in its larger context for the first time ever."
Atlantic Productions said "one major area of deterioration" had already been observed in the officers' quarters. "This included the room of Captain Edward John Smith and discovered that the iconic captain's bathtub has now disappeared from view," it added.
"Now we're getting objective, so we can get really serious with the science of understanding the wreck," Stephenson said.
He added that he was "absolutely convinced," that the photogrammetry model would now be used "not just for Titanic, but for all underwater exploration," because it "ushers in a new phase of exploration and analysis."
Much of the wreck lies in two main pieces, far apart from each other, at a depth of about 4,000 meters. Around 700k images where taken and stitched together to created the model.
Previously:
(2022) Researchers
Discover Wreck of Ship that Tried to Warn the Titanic
(2022) OceanGate
Ramps Up the Research for its Second Deep-sea Expedition to the
Titanic
(2020) An Aurora
that Lit Up the Sky Over the Titanic Might Explain Why It
Sank
(2020) US Court
Grants Permission to Recover Marconi Telegraph from Titanic's
Wreckage [Updated]
(2018) Finding
the Titanic with ROVs and Navy Funding
Read more of this story at SoylentNews.
13:53
Jyothi Devakumar joins our Life Extension Board. Lifeboat News
Jyothi Devakumar joins our Life Extension Board. Jyothi is Group Chief Science Officer and Partner at the Longevity Tech Fund and Chief Science Officer (CSO) at Healthy Longevity Clinic.
12:00
THOR Microwaves Drone Swarms Hackaday

In recent years small drones have gone from being toys and photography tools to a deadly threat on the battlefield. Kamikaze drones have become especially prominent in the news due to their use in the war in Ukraine by both sides. While we havent seen coordinated swarms being actively employed on the modern battlefield, its likely only a matter of time, making drone swarm defense an active field of development in the industry.
The US Air Force Research Laboratory recently conducted tests and a demonstration of an anti-drone weapon that uses pulses of high-power microwave energy to fry the electronics of a swarm of drones. Named the Tactical High-power Operational Responder, or THOR (presumably they picked the acronym first), its housed in a 20ft shipping container with large microwave antenna on top. The form factor is important because a weapon is only useful if it can reach the battlefield, and this can fit in the back of a C130.
THOR likely functions similarly to a shotgun, with a relatively large effective beam. This would have added advantages like frying multiple drones with one pulse and not needing pinpoint tracking and aiming tech required for projectile and...
11:59
Microsoft Layoffs Continue: Workers Given Notice on Friday of Long (Holiday) Weekend, This Time Nuance Techrights
Didnt Microsoft say repeatedly and insist that chatbots are the future? The layoffs pattern does not match the hype pattern.
Summary: Published earlier today was this sole report (its weekend and reporters are away, some on holiday); talk about bad timing to announce layoffs unless the whole point is brushing the news under a rug (there were also loads of Microsoft layoffs last week, but the media barely mentioned this; Microsoft changed the subject to salaries)
Text behind the paywall: (the only publicly available information at this point)
Nuance Communications, the speech-to-text pioneer bought by Microsoft last year, is cutting jobs as it focuses more narrowly on the health care market.
Employees at Burlington-based Nuance received an e-mail on Friday from chief executive Mark Benjamin notifying them of the cutbacks as part of the continued integration with Microsoft, which paid nearly $20 billion for the company.
We continue to see macroeconomic pressures affect our industries, as well as market shifts that are evolving our customers needs, Benjamin wrote in the e-mail, which was obtained by the Globe. It is critically important that we maintain our ability to make key investments in our businesses so that we can deliver on our current plans and are able to capitalize on the future opportunities we have ahead of us. In order to do this, we made the difficult decision this week to eliminate some positions across the company.
Benjamin did not detail the scope of the layoffs at Nuance, which had about 7,000 employees when the Microsoft deal was announced in 2021. The company did not immediately respond to a request for comment on Saturday.
Nuance has a long and winding history in developing image-processing and speech-recognition software and applications. The company started in 1994 as a spinoff from SRI Internationa...
11:41
[Meme] Illegally and Unconstitutionally Starting Unified Patent Court in Violation of Numerous Conventions Techrights
Summary: Team UPC has privately decided that Milan is in London and its time to start a kangaroo court for the EPOs aristocrats, who granted lots of fake patents, which need fake judges to approve them
11:29
London Police Chief Publicly Admits the System is Failing Victims Techrights
In the news (2 days ago): UK Metropolitan Police Chief accuses Crown Prosecution Service of failing victims and cherry-picking cases
In Techrights: Good Morning Britain Host Martin Lewis: Action Fraud is Pointless
Summary: It has now been over 28 days since crimes of Sirius Open Source were reported to the police (Action Fraud in London) and no action has yet been taken, just as we expected all along (they cannot even be contacted)
11:14
Links 20/05/2023: GStreamer 1.22.3, LibreOffice Looks to Attract New Contributors Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
-
GNU/Linux
-
Desktop/Laptop
-
Google ChromeOS
ChromeOS is Googles cloud-connected desktop operating system (OS). This web-app-focused OS powers mostly inexpensive Chromebookslow-cost laptops for people with basic computing needs. Because it runs on affordably priced laptops and is easy to use with tie-ins to Googles online productivity apps, ChromeOS is excellent for students and casual computer users. ChromeOSs Android...
-
-
11:11
Gemini Links 20/05/2023: The Other Wiki and More Techrights
-
Gemini* and Gopher
-
Personal
-
SpellBinding: AYGISTC Wordo: EIDER
-
hey hey mama, have you read the news
I heard Elizabeth Holmes is going to prison for her fraudulent Silicon Valley co (and yea, I will forever mistakenly call her Katie Holmes), so, I figure hey, lets amuse ourselves with some visual irony, and look up the photo where she is with the 30 under 30 crowd with Zuckerberg and other Silicon Valley tech captains of industry.
I search, I scroll, I re-search, scroll more that photo is fxxxing buried. What I DID see (all over the front page of DDG) was the news news news that she is, in fact, being imprisoned and not remaining free until an appeal, or whatever. Not even a Wikipedia entry on her. Not even an insider hot take about what the malicious/malignant culture Silicon Valley portrays and upholds means for tech at-large. She isnt the only bad character in the Bay Area, she just got caught.
-
I NEED HELP OUT OF A VERY BAD SITUATION
A little more than a decade ago, after CAPITALISM handed my ass to me (the 2008 crash, and subsequent fallout), and I was left with pretty much nothing, I agreed to be sent to TX to be with my mother and sister.
-
Blueberries
I love blueberries. I bet you like them too. If you dont, you probably havent been eating very good ones. Lowbush blueberries are the best theyre small, sweet, and packed with flavor!
-
something something yardwork makes beer sweeter
Todays been busy. Got tomato plants, carrot and cucumber seeds, bags of compost. Took the dogs to the vet for their shots and heartworm/tick medication, then got down to business. Weeded the vegetable garden, turned the soil with a garden fork, poured out the compost, worked it in. Found a few potatoes from last year I mustve missed, and...
-
-
09:13
Obstetricians More Emotionally Stable Than Most SoylentNews
Personality is usually summarized in five traits - the so-called "big five": Emotional stability (neuroticism), extroversion, agreeableness, conscientiousness, and openness. Our personality then shapes our decision-making style. In a research study from Lund University, Swedish obstetricians' and gynecologists' personality profiles and clinical experience are linked for the first time to their decision-making styles in acute childbirth situations.
"Obstetricians and gynecologists have a personality profile that differs significantly from the population at large. On average, 85 percent of Sweden's population has significantly lower emotional stability, extroversion, agreeableness, and conscientiousness than the obstetricians in our study. It's hard not to be surprised when the differences are so clear", says Petri Kajonius, associate professor of personality psychology and behavioral measurement at Lund University.
It is our personality that defines what we will enjoy in our professional life, and the consequence is likely a self-selection of people who seek a certain profession. Swedish obstetric-focused physicians' personalities make them comfortable in an environment where a childbirth situation can quickly shift to something acute and potentially escalate into a crisis. Here, traits such as emotional stability and conscientiousness are prominent.
Journal Reference:
Raoust, G., Kajonius, P. & Hansson, S. Personality traits and
decision-making styles among obstetricians and gynecologists
managing childbirth emergencies [open]. Sci Rep
13, 5607 (2023). https://doi.org/10.1038/s41598-023-32658-6
How do you assess your own personal emotional stability. Are you excitable, or calm and methodical, or does it change frequently depending upon the current situation that you find yourself?
Read more of this story at SoylentNews.
09:09
PyPI suspends new user/project registrations LWN.net
The PyPI Python module repository has temporarily suspended acceptance of new users and project names.
New user and new project name registration on PyPI is temporarily suspended. The volume of malicious users and malicious projects being created on the index in the past week has outpaced our ability to respond to it in a timely fashion, especially with multiple PyPI administrators on leave.
09:00
ESPClicker An Elegant Solution for Integrating Dumb Devices into Home Assistant Hackaday

Integrating non-smart devices into your home automation system can be a cumbersome process, involving the wiring of multiple modules. However, [Pricelesstoolkit] has created the ESPClicker a compact, ESP8266-based module that can remotely press buttons and simplify this process.
The ESPClickers core feature is its three relays that can be soldered to the button terminals of any existing dumb device, as [Pricelesstoolkit] demonstrated with his coffee machine in the video after the break. One of the relays can also be configured in the normally closed configuration. A compact twelve pin connector provides a removable wiring interface for the buttons, additional relays, power and even a contactless power detector that can be wrapped around an AC wire.
The module is open source, with all the source files available on Github. It is intended for interfacing to Home Assistant through ESPHome providing a convenient way of programming and updating the module.
...
06:00
Op-Amp Challenge: MOSFETs Make This Discrete Op Amp Tick Hackaday

When it comes to our analog designs, op-amps tend to be just another jellybean part. We tend to spec whatever does the job, and dont give much of a thought as to the internals. And while it doesnt make much sense to roll your own op-amp out of discrete components, that doesnt mean there isnt plenty to be learned from doing just that.
While were more accustomed to seeing [Mitsuru Yamada]s digital projects, hes no stranger to the analog world. In fact, this project is a follow-on to his previous bipolar transistor op-amp, which we featured back in 2021. This design features MOSFETs rather than BJTs, but retains the same basic five-transistor topology as the previous work, with a differential pair input stage, a gain stage, and a buffer stage. Even the construction of the module is similar, using his trademark perfboard and ultra-tidy wiring.
Also new is a flexible evaluation unit for these discrete op-amp modules. This very sturdy-looking circuit provides an easy way t...
04:37
WHO Warns of Unusual Surge in Severe Myocarditis in Babies cryptogon.com
Mmm hmm. Via: Epoch Times: UK authorities are investigating an unusual surge in severe myocarditis which has hit 15 babies in Wales and England and has killed at least one, the World Health Organisation has announced. On Tuesday, the WHO issued an alert that there had been a rise in severe myocarditis in newborns and []
04:26
Intel Shows New Stacked CFET Transistor Design at ITF World SoylentNews
Intel Shows New Stacked CFET Transistor Design At ITF World:
At ITF World 2023, Ann Kelleher, Intel's Technology Development GM, presented an outline of Intel's latest developments in several key areas, and one of the most interesting revelations was that Intel would embrace stacked CFET transistors in the future. This marks the first time that Intel has shown this new type of transistor in its presentations, but Kelleher didn't provide a date or firm timeline for production.
[In the added around the new type of transistor. The first two transistor types at the bottom of the slide are older variants, while the '2024' entry represents Intel's new RibbonFET transistors that we've covered extensively in the past. Intel's first-gen design with the 'Intel 20A' process node features four stacked nanosheets, each surrounded entirely by a gate. Kelleher says this design remains on track to debut in 2024. RibbonFET uses a gate-all-around (GAA) design, which confers both transistor density and performance improvements like faster transistor switching while using the same drive current as multiple fins, but in a smaller area.
Kelleher's slide also shows the next generation of Intel's GAA design the stacked CFET. The Complementary FET (CFET) transistor design has been on imec's roadmaps for some time, but we haven't yet seen it on an Intel slide or heard the company state that it plans to adopt this design. As a reminder, the imec research institute studies future technologies and collaborates with the industry to bring them to fruition.
Naturally, there is some variation between Intel's stylized render and the imec CFET render we've included in the first image of the album above, but Intel's image conveys the point well this design allows the company to stack eight nanosheets, a doubling of the four used with RibbonFET, thus increasing transistor density. We also have images of the three other types of Intel transistors in the album above Planar FET, FinFET, and RibbonFET.
Read more of this story at SoylentNews.
03:47
Popular Pirate Bay Proxy Site Disappears From GitHub TorrentFreak
 As one of the most notorious torrent sites, The Pirate Bay
has been blocked by ISPs around the world.
As one of the most notorious torrent sites, The Pirate Bay
has been blocked by ISPs around the world.
In response to these digital roadblocks, several proxy sites have sprung up to bypass these restrictions. Besides that, there are dedicated sites that help people to find these backdoors.
The Proxy Bay
The Proxy Bay has long been one of the leading information portals. The site didnt offer an official proxy itself but provided an overview of available options. As such, it proved to be quite useful in countries where site blockades are active.
In the UK, for example, where TPB has been blocked for over a decade, the site was particularly popular.

Since the blocking orders often allow rightsholders to add newly appearing proxies, this has turned into a game of whack-a-mole. When proxies are blocked, new domains are launched, which are then picked up by pirates through information portals such as The Proxy Bay.
GitHub Takedown Saga
This routine has been a major source of frustration for rightsholders. It reached the point where some of these linking sites were banned, and when City of London Police got involved in the matter earlier this year, it was clear that things were getting more serious.
Its quite something when the police actively get involved in a copyright matter. In this case, it was particularly salient since The Proxy Bay was hosted at GitHub.
The developer platform swiftly complied with the takedown request, which wasnt unexpected. However, after someone representing the proxy information site sent a counter notice, the domain was restored.
The brief takedown in January hurt the sites traffic...
03:16
2021 data breach exposed data of 70 Million Luxottica customers Security Affairs
Luxottica has finally confirmed the 2021 data breach that exposed the personal information of 70 million customers.
Luxottica Group S.p.A. is an Italian eyewear conglomerate and the worlds largest company in the eyewear industry. As a vertically integrated company, Luxottica designs, manufactures, distributes and retails its eyewear brands, including LensCrafters, Sunglass Hut, Apex by Sunglass Hut, Pearle Vision, Target Optical, Eyemed vision care plan, and Glasses.com. Its best known brands are Ray-Ban, Persol, and Oakley. Luxottica also makes sunglasses and prescription frames for designer brands such as Chanel, Prada, Giorgio Armani, Burberry, Versace, Dolce and Gabbana, Miu Miu, and Tory Burch.
On May 12, the cybersecurity expert Andrea Draghetti noticed that a threat actor released data belonging to Luxottica speculating a new databreach.

The threat actor released a 140GB database containing more than 300 million records. The researchers reported that the archive was containing 305.759.991 records (luxottica_nice.csv), with 74.417.098 unique email addresses and 2.590.076 unique domain emails.
03:07
An erasure FEC for SSDV Daniel Estvez
SSDV is an amateur radio protocol that is used to transmit images in packets, in a way that is tolerant to packet loss. It is based on JPEG, but unlike a regular JPEG file, where losing even a small part of the file has catastrophic results, in SSDV different blocks of the image are compressed independently. This means that packet loss affects only the corresponding blocks, and the image can still be decoded and displayed, albeit with some missing blocks.
SSDV was originally designed for transmission from high-altitude balloons (see this reference for more information), but it has also been used for some satellite missions, including Longjiang-2, a Chinese lunar orbiting satellite.
Even though SSDV is tolerant to packet loss, to obtain the full image it is necessary to receive all the packets that form the image. If some packets are lost, then it is necessary to retransmit them. Here I present an erasure FEC scheme that is backwards-compatible with SSDV, in the sense that the first packets transmitted by this scheme are identical to the usual \(k\) packets of standard SSDV, and augments the transmission with FEC packets in such a way that the complete image can be recovered from any set of \(k\) packets (so there is no encoding overhead). The FEC packets work as a fountain code, since it is possible to generate up to \(2^{16}\) packets, which is a limit unlikely to be reached in practice.
Motivation and intended applications
The main motivation for this FEC scheme comes from the Longjiang-2 mission. This satellite, also known as DSLWP-B, carried a small camera and transmitted the images from the camera on demand by telecommand using SSDV. The downlink bitrate was usually 125 bps, so transmitting a single image would take around 20 or 30 minutes. It was not uncommon to miss a few of the SSDV packets. Even if the SNR was quite good when the 25 meter radiotelescope at Dwingeloo was used to receive the downlink, there could be occasional problems such as frequency jumps in the on-board TCXO.
In some cases, the missing pieces of the image corresponded to empty parts of the sky that were known to be completely black. In other cases, the missing parts were interesting, so we attempted to receive the complete image by commanding the spacecraft to transmit the missing packets again, before new images were taken that would overwrite the image in the on-board memory. There were two possible ways of doing this. It was possible to send a telecommand that would start the SSDV transmissio...
02:45
Links 20/05/2023: IPFire 2.27 Core Update 175 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Monopolies
-
GNU/Linux
-
Audiocasts/Shows
-
Bad Voltage 358: Large Langridge Model
Jeremy Garcia, Jono Bacon, and Stuart Langridge present Bad Voltage, in which there is unsceptical intensity, we are all eaten by a T-1000, and we have collected a list of concerns about Large Language Model-based AI, which were going to dive into!
-
Jupiter Broadcasting ...
-
-
02:35
IRC Proceedings: Friday, May 19, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-190523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-190523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-190523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-190523.gmi
Over HTTP:
|
... |
01:38
KDE Begins Laying The Groundwork For HDR Support, Wayland Color Management Phoronix
As covered a few days ago on Phoronix, there's been early progress on HDR display support for the KDE desktop among other highlights this week...
Saturday, 20 May
19:02
1xbet Sport Bet App Along With Professionals h+ Media
1xbet Sport Bet App Along With Professionals
You want to pick the tactic through which you wish to withdraw your winnings. Again there is a minimum amount for all of the fee strategies listed on the website. After verifying the account, click on the cricket button current on the top of your display. You can even choose the Sports possibility from the top if you wish to bet on totally different sports activities.
Players who win their bets are added to the jackpot candidates listing. A combo bet is a wager that covers a number of positions on the similar time. Only if all of the players predictions are right, this bet will be worthwhile.
The profits on all accumulators incorporated in the system are summed up to compute the cost. This can be a dangerous wager, though it is extremely rewarding if it is correct. Click on the green icon with the iOS symbol, which can redirect you to the official Apple App Store page of the 1xBet app. Simply click the Install button, and launch the app when its carried out installing. Then, click on the set up button, and launch the app when it is ready. You can use your welcome bonus as quickly as you make a deposit.
It is probably one of the most popular games worldwide, and we offer each stay casino choices and normal ones. Poker is among the oldest and most popular activities at the casino, and we offer a lot of choices for it, including enjoying poker with a live dealer. All the video games are powered by well-known software suppliers and are utterly reliable.
To do this, click on the Live Stream button with the monitor image and select the published mode. To see the potential outcomes for betting, you should go to the virtual sports part, choose a supplier and run a particular game. The alternative of betting choices is wide enough to make a great categorical for one match.
This recreation permits you to get further payouts from the efficiency of the attacking gamers and minimize the risk of a wrong prediction of the end result. Bet Constructor is a new, unique sport from 1xBet, which allows you to independently assemble two teams that will participate in betting. The consequence of the game and the end result will depend upon which staff will score more objectives than the opponents. Users who win their wager are added to the list of jackpot contenders. At the top of the day, a random number generator determines the coupon number, the proprietor of which receives the ultimate payout. In the casino, poker is implemented within the format of live or video poker.
- Using your desktop or mobile browser, go to the official 1xBet web site.
- The 1xbet bonus for model new clients is a stable welcome provide.
- In June this yr, the Information and Broadcasting Ministry issued an advisory to print, electronic and digital media to chorus from advertising online betting platforms.
- Such information could be safely used for future bets....
19:02
1xbet Online In India h+ Media
1xbet Online In India
The customers can select either to do the 1xbet apk obtain or the ios download too. Not only this they have the likes of cell browser too, which is less complicated to entry. The website presents a quantity of payment choices for users based out of India, including e-wallets, cryptocurrencies, financial institution transfers and bank playing cards. Curiously, while making UPI transfers, as a substitute of making the cost directly to 1xBet, the registered ID belongs to a private individual and it routinely retains altering.
1xBet analyses the wants of modern society and constantly improves its products. In it, users cant solely bet on cricket and extra sports activities wherever theyre but additionally discover different exciting offers. So, for instance, you can watch matches of your favorite teams reside, play in the on line casino or play unique video games in the 1xGames part. We provide all the data you will want on the qualifying norms associated to the bonus offer.
The firm also ensures that each one transactions are processed quickly and securely. Customers can relaxation assured that their money is secure when utilizing any of the fee strategies available on 1xBet. Withdrawals are also simple to initiate with only a few clicks, allowing customers to access their winnings rapidly and simply. All in all, 1xBet provides a wonderful platform for Indian gamers to enjoy a safe and secure online gambling expertise.
Boxing is a classic type of martial arts that by no means ceases to be well-liked. Betting followers are attracted not solely by the relative ease of guessing the finish result of fights, but additionally by the detailed odds. You can guess on boxing not solely on the winner but in addition on different statistics and leads to specific rounds.
The web site has a Curacao license, confirming its reliability and security. 1xBet is the official partner of Spanish La Liga, Italian Serie A, Nigerian Premier League and Brazilian Serie A. 1xbets customer assist group is always at hand to offer prospective bettors any type of help they search.
This makes the welcome provide both large and versatile, although do keep in mind you only have 30 days from the date of registration to redeem this supply and use the bonus funds. The homepage of the web site reveals all stay games going down with reside odds, and youll select any sport you want to bet on from the listing. There is a menu that permits you to open varied sports activities, reside betting web page, promo code section, on line casino, reside on line casino, 1xGames, TVGames and different sections. The Indian Premier League, or IPL, is amongst the most popular cricket events amongst Indian gamers. 1xBet presents each a desktop web site and a mobile app for betting on the IPL. One of the simplest bookmakers in India is the 1xbet sports app.
Dozens of deposit and withdrawal methods are available on th...
19:02
1xbet Login And Registration, 1xbet Register On h+ Media
1xbet Login And Registration, 1xbet Register On
In India, its not attainable to open an account with 1xbet. But, if youre an avid sports fan, youll love the sites wide selection of choices. With 1xbet, youll find a extensive range of sports activities and casino video games you could bet on. Plus, you can also win real money should you make the right predictions. In addition to its sportsbook, the 1xbet website presents numerous deposit strategies.
As the sport progresses, the betting markets and respective odds update quick on the 1 xbet web site. In this, the chances are up to date each few minutes, and the market stays active to put bets. Playing in a stay on line casino could be very handy as a end result of there you presumably can place extra accurate bets by following every little thing thats happening at the time of a play. In Live Casino, youll be playing only with actual live casino sellers. It is feasible to place bets wherever and whenever you need.
- Bonus amount is the identical as the amount of your deposit .
- You can use the cash to position bets and later withdraw them to your card.
- After you declare the bonus, you need to wager the bonus money in at least 5 accumulator bets with three or further occasions with odds 1.forty or larger.
- The totalizator is a unique betting type provided by us.
- Every Friday and Saturday up to 200 events are supplied, a 3rd of that are streamed reside.
It is accessible by over four hundred,000 users worldwide and there are no legal guidelines towards on-line gambling in India. Indian punters can legally access the platform to wager and play with most withdrawal quantities varying from one banking choice to another. After evaluating the options and features of 1xBet for Indian players, we awarded it the Sportscafe stamp of approval.
At the time of writing, there were almost 300 in-play bets obtainable throughout one stay South Korean womens basketball match alone. In the case of cricket matches, the number may be even larger, with bets out there on individual balls, over or innings. This offers you the chance to actually put your knowledge to the take a look at by predicting the finish result of topical scenarios in addition to the performances of batsmen and bowlers.
Its discussion board for bettors is one other nice supply of help for model new or inexperienced bettors. Not solely are you capable to chat with other prospects there but additionally get some treasured pieces of recommendation from real execs within the sports activities betting world. A secure and reliable casino publishes the origin and its gaming licenses on the homepage. There is a protracted record of playing authorities around the world that regulate online casinos. The hottest homeowners include the United Kingdom and Malta. The UK Gambling Commission, as an example, is responsible for regulating on-line playing providers an...
19:00
Is 1xbet Authorized In India? h+ Media
Is 1xbet Authorized In India?
It is important to note that every one submitted paperwork should be legitimate and up-to-date to ensure that the verification course of to be successful. Once verified, users will have access to all options on the platform together with deposits, withdrawals, bonuses and promotions. 1xBet is a authorized online gambling website in India and is secure for Indian gamers to make use of. It provides an thrilling vary of betting options with great bonuses and promotions, making it a great choice for Indian punters seeking to enjoy the thrill of on-line playing. 1xBet is a safe and safe betting web site for Indian gamers. It is licensed by the Curaao eGaming License and registered in Cyprus, making it a dependable platform for on-line gambling.
Players can register from the website or via the app directly. Players can create only one account and if they try to create another one, 1xBet has the right to cancel the account as per their policies. The ID and financial details of deposits should match with the small print while opening an account. Upon affirmation of the wager, the corresponding amount of money will be deducted out of your account steadiness and put aside. Malaysian very related to the American coefficient, however has a barely different which means. Negative odds will mean that the web winnings shall be larger than the wager dimension.
- It opens routinely whenever you navigate to the web site through a cellular browser.
- In this, the odds are up to date each couple of minutes, and the market stays active to put bets.
- It provides an thrilling range of betting options with great bonuses and promotions, making it a fantastic choice for Indian punters seeking to benefit from the thrill of on-line playing.
- If they fail to break into the top 4, then its pointless to count on major transfers in summer time.
- 1xbet provides you the widest possible range of cost choices.
Boxing is a classic kind of martial arts that by no means ceases to be well-liked. Betting fans are attracted not solely by the relative ease of guessing the result of fights, but also by the detailed odds. You can wager on boxing not only on the winner but also on different statistics and results in specific rounds.
With such regulatory our bodies, casinos make certain that they hold their phrases and conditions as clear and comprehensive as possible for players. Therefore, players who choose a licensed casino will be protected when gambling on-line. To guess on sports 1xBet India one must be a registered and verified user. In this case, your money deposit shall be received and paid out with odds should you win without delay.
In the first case, you play 1 on 1 against the dealer. In the second, the sport is performed based on modified guidelines. And the stronger it is, the upper the prize multiplier. Division by championships, leagues, and other compet...
18:59
1xbet App For Online Betting h+ Media
1xbet App For Online Betting
Just just like the desktop options, gamers can entry all the transaction mediums utilizing 1xBet app. The 1xbet credit or debit card fee method is essentially the most preferred payment option to fund the account. After login, select the Cards option within the Deposit part and fill in the required card details. The primary deposit choice is the e-wallet method for Indian bettors. Below discover the data on how to deposit cash in 1xbet from India and get to know about some new-age deposit strategies from this bookmaker.
1xBet provides an affiliate program where you could earn 200 INR should you refer others to 1xBet and they efficiently be a part of and deposit a minimal of 1,000 INR. You may provide as many suggestions as you like, and you may even share your distinctive link on social media and with like-minded friends. Complete the transaction by getting into the amount you want to deposit into your 1xBet account for the primary time. Signing up at 1xBetbd is completely free, and this course of may be carried out by following the steps talked about within the earlier part. Considering that having an account at this portal is totally free, there is not a trigger for not signing up now. For individuals who might not know, 1xBetbd is the division of 1xBet centered on the nation of Bangladesh.
Multi guess is a mixed bet, the coefficients of which are multiplied. International competitions, including world championships, are also held in kabaddi. Date live pro kabaddi is changing yearly, however all information you can find within the site. 1.Go to your personal account, after which to the Personal information section. The governments draft guidelines for deceptive commercials beneath the Consumer Protection Act prohibit firms from surrogate promoting.
Top cricket matches can have tons of of markets to wager on and there are numerous extra markets obtainable in-play. The website format takes a while to get used to, especially if you have expertise of different major betting sites. But as soon as you know your method round, it becomes slightly easier. The sports activities menu comes within the type of a side-scrolling record that is displayed on the high of the betting menu, so it can always be accessed. In our opinion, this isnt probably the most user-friendly way to navigate a sports activities betting menu.
For example, we prefer to make use of the cell app for betting because it provides a extra user-friendly expertise overall. And we might somewhat use the live chat facility when in need of support. There is a devoted reside streaming web page on 1XBet with reside streams of various sporting events shown 24/7, including top cricket matches from around the globe.
Once you retain track of this stuff, youll dont have any problem wagering your bonus inside the set time. Another argument in favor of this web site is the 1xbet promo code that will permi...
18:58
1xbet Bookmaker Evaluate h+ Media
1xbet Bookmaker Evaluate
Computer applied sciences are creating better every year and now eSports is confidently making its method to the leaders in sports betting. Our bookmaker office is developing this development in every method and provides esports betting. Make a deposit of a minimum of a thousand INR and get an additional 500 INR free guess.
The income on all accumulators included within the system are summed up to compute the cost. This could be a dangerous wager, although its highly rewarding if it is appropriate. Click on the green icon with the iOS symbol, which will redirect you to the official Apple App Store web page of the 1xBet app. Simply click the Install button, and launch the app when its done putting in. Then, click on the set up button, and launch the app when it is ready. You can use your welcome bonus as soon as you make a deposit.
1xBet additionally has a Curacao gambling license, which signifies that it is secure and reliable. The documents required for account verification include a passport, drivers license, identity card, and utility bill. This is necessary in order to withdraw money from 1xBet.
Ace counts for 1 level and the playing cards from 2 to 9 go at face value, while the other playing cards including tens give 0 points. Select the sort of guess within the coupon, specify the quantity, and click on to place your wager. The tougher the outcomes are, the much less they should guess to obtain a payout. And the quantity of prize cash already depends instantly on what number of profitable predictions you have made.
You can wager on a particular horse to win or lose, on pairs and fours of horses, and tons of different outcomes. Enter your username and password, or log in by way of a social network. Go to the official website of the bookmakers office. You can create a 1-click account by phone quantity, e mail, or by way of social media.
Once your software is permitted, you might be able to withdraw your winnings from the account through cashier in any convenient method. After that, you will get to the main display screen, the place you can choose a bit, sort of recreation, place a guess, deposit your account through cashier, etc. Within 24 hours of receiving the 1xBet Friday bonus, you need to make a betting turnover three instances the quantity of the bonus. At the same time, it ought to be specific bet with three or extra events with individual odds not lower than 1,4.
When you are in India and also you need to guess with a bookmaker that you can trust there are a quantity of local choices and a lot of worldwide choices. 1xbet is a trusted agency that will pay you out when you win. Make positive you set a password that you could easily remember. Through this password, you will also be capable of entry your 1xBet cell app account with your present username. The jackpot on line casino game is part of a promotion that we provide. To take part on this...
18:57
1xbet Sports Regular Match Males Blue Trousers h+ Media
1xbet Sports Regular Match Males Blue Trousers
The license permits the bookmaker to arrange sports betting occasions in additional than 50 countries around the globe. Users of the 1xBet website should not be afraid of fines or different penalties. Thanks to the presence of a Curacao license, the security of 1xBet India remains at a high degree. 1xBet is a authorized on-line playing website in India, with a Curacao playing license (license quantity 1668/JAZ).
1xbet welcomes grownup resident Indian bettors with a join supply. Provided you meet the qualifying standards, your welcome bonus must be credited to your account proper after you make your first deposit. Just ensure you use it within 30 days of sign-up, in any other case, will in all probability be revoked. Type in the 1XBet promo code in the corresponding subject.
You cant use a 1xbet promo code in case you are already a registered person. As it is clear from the name of the bonus, its intended for model new clients only. This means you can get a welcome bonus, applying the 1xbet promo code SEOALEX only once. When it comes to refiling your betting account with bonus funds, there can be no delays.
To wager on cricket, open the listing of all sports activities in the left corner and choose the category that interests you. Aside from cricket, theres a plethora of sports betting disciplines in which youll attempt your luck. You have a month since receiving a bonus for wagering it. If you dont handle to do this, all of your winnings earned due to bonus cash and every thing that remained on your bonus account will be redeemed. X2 Wednesday is one other nice provide for 1xbet clients.
With this wager , every choice fulfils the minimum odds of 1.40. With such a bet, youll release a part of the bonus. In the top, you must wager the bonus five instances within 30 days. For instance, should you deposit 1,000 INR and obtain a bonus of an extra 1,000 INR, you have to wager a complete of 5,000 INR on sports bets of your selection. If you manage to do that within 30 days with such acca bets, the bonus and all winnings earned with it are yours. In addition to profitable bonuses and a wide range of games, 1xBet offers a broad range of on-line sports activities and esports betting.
The first step in getting the 1xbet promo code bonus for India is to create a model new account. For all new prospects who love betting on sport events. There is a extensive range of sports available to you on this online bookie. As expected, cricket, soccer, or soccer as some know it has the widest outreach. All you have to do is join a new account and it is feasible for you to to claim the welcome bonus and the prevailing players can avail the unique supply for the Indian market. This is great as it allows the new and present players to spend time on this operator greater than they might often do.
In our write-up on the 1xbet promo code, you will disco...
18:57
Wager On Cricket With The Trendy 1xbet Mobile App h+ Media
Wager On Cricket With The Trendy 1xbet Mobile App
Remember to enter your real registered cell quantity. New gamers might have to validate their identification and could additionally be requested to supply identification paperwork for that purpose. Failing to supply them could stop them from claiming the welcome bonus. Players must consent that they want to receive the bonus by going to My Account and enabling the Take half in bonus offers operate. When youre prepared, click on the percentages and your selection will appear in the bet slip. You can add extra markets if you wish to create a multiple or an accumulator to enhance your odds.
Its a one-time supply, and youll never have one other likelihood to receive this kind of bonus. 1xbet offers the widest vary of choices for depositing cash into and withdrawing out of your betting account. 1xbet provides a variety of betting choices in cricket and different sports activities which may be popular amongst Indian bettors. 1xbet offers you the widest potential vary of payment options. As a prospective bettor, the plethora of choices provided will delight you. We list some of these decisions beneath, in our write-up on the 1xbet promo code.
Even although 1xBet is a reasonably well-known model that doesnt want promoting, they keep up the level. Compared to other bookmakers, 1xBets customer support is very fast. And most importantly, it gives full answers to questions. Odds on stay events are variable and alter as an occasion progresses. Odds at 1xbet are among the highest of all online bookies in India.
1xBet has the identical options and features as the desktop identical welcome bonus and some other promotions. If you run into a difficulty, you probably can always contact quickly our buyer help team via live chat, and they will assist you to resolve any problem you may have. The dealer launches the ball across the roulette wheel within the recreation of roulette. If you wager on the sector the place the ball stops, youll be able to win.
There are many variations of this on line casino sport, so it is strongly recommended that you just check all of them out to search out the one which fits your tastes essentially the most. Click on the Login button in the top-right nook. Then, enter the consumer ID, e-mail, or phone quantity, and type in your password.
And every year the curiosity of gamers to guess on pkl is rising. In addition, betting pro kabaddi league is available with favorable odds. As soon as a brand new 1xBet client registers, you should instantly write to the technical assist service and undergo the verification process. As quickly as they want a withdrawal, they start writing to the administration. This might take a while, and even require extra checks.
- The money received as a prize due to a working promo code can be utilized for sports betting w...