| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Thursday, 26 October
17:10
We've added another 25 new png tools catonmat.net
Team Browserling keeps shipping!
Last week we added 20 new jpg tools and and today we just added another 25 new tools to our Online PNG Tools collection.
We've done our job and now it's Google's job to index them and rank them well.
Here are the new png tools:
- Change PNG Brightness
- Change PNG Contrast
- Add Sepia Tone to a PNG
- Change PNG Hue
- Invert PNG Colors
- Convert ICO to PNG
- Optimize a PNG
- Create Symmetric PNG
- Generate a Colorful PNG
- Create a PNG from an Emoji
- Add Artifacts to PNG
- Generate 1-by-1 Pixel PNG
- Convert PNG to Two Colors
- Convert PNG to Black and White
- Create a Monochrome PNG
- Add Dithering to a PNG
- Decrease PNG Color Count
- Add a Whirl to a PNG
- Quantize a PNG
- Wrap a PNG in a Polaroid
- Posterize a PNG
- Remove PNG Chroma Key
- Generate a Single-color PNG
- Generate White Noise PNG
- Er...
Thursday, 12 October
17:05
We've added another 20 new jpg tools catonmat.net
Team Browserling keeps shipping!
Last week we added 20 new number tools and and today we just added another 20 new tools to our Online JPG Tools collection.
We've done our job and now it's Google's job to index them and rank them well.
Here are the new jpg tools:
- Add a JPG Border
- Remove a JPG Border
- Create a Noisy JPG
- Remove JPG Background
- Add JPG Artifacts
- Remove JPG Artifacts
- Extract RGB Color Channels from a JPG
- Extract CMYK Color Channels from a JPG
- Extract HSL Color Channels from a JPG
- Find Dominant JPG Colors
- Reduce JPG Colors
- Create a Dithered JPG
- Create a Binary Two-color JPG
- Upsize a JPG
- Downsize a JPG
- Optimize a JPG
- Watermark a JPG
- Highlight a JPG Region
- Change JPG Orientation
- Generate a JPG by a Color Name
- Create a JPG For Social Media
- Annotate a JPG
Next week we'll add even more tools. See you then!
Thursday, 28 September
16:30
We've added 20 new number tools catonmat.net
Team Browserling keeps shipping!
Last week we added 20 new binary tools and and today we just added 20 new tools to our Online Number Tools collection.
We've done our job and now it's Google's job to index them and rank them well.
Here are the new number tools.
- Generate Fibonacci-like Series
- Calculate Linear Recurrence Series
- Find the Greatest Common Divisor
- Find the Least Common Multiple
- Generate a Sequence of Squares
- Generate a Sequence of Cubes
- Generate Powers of Two
- Generate Powers of Ten
- Shuffle Digits in a Number
- Add Fractions
- Find the Inverse of a Matrix
- Find the Maximum Number
- Find the Minimum Number
- Convert Numbers to Words
- Convert Words to Numbers
- Convert a Number to Negadecimal Base
- Change a Number's Base
- Create Neat Unicode Fractions
- Create a Palindrome from a Number
- Check if a Number is a Palindrome
Next week we'll add even more tools. See you then!
Sunday, 21 May
00:13
Cybercrime gang FIN7 returned and was spotted delivering Clop ransomware Security Affairs
Cybercriminal gang FIN7 returned with a new wave of attacks aimed at deploying the Clop ransomware on victims networks.
Researchers at Microsoft Security Intelligence team published a series of tweets to warn of a new wave of attacks aimed at distributing the Clop ransomware and linked it to the financially motivated cybercriminal group Sangria Tempest (ELBRUS, FIN7). The attacks confirm the return of the threat actors after a long period of inactivity. The group was spotted deploying the Clop ransomware in opportunistic attacks in April 2023.
FIN7 is a Russian criminal group (aka Carbanak) that has been active since mid-2015, it focuses on restaurants, gambling, and hospitality industries in the US to harvest financial information that was used in attacks or sold in cybercrime marketplaces.
In recent attacks, Fin7 was observed using the PowerShell script POWERTRASH to load the Lizar post-exploitation tool to get a foothold into the victims networks. Then they use OpenSSH and Impacket to move laterally and deploy the Clop ransomware payload.
The Clop ransomware is just the newest strain the cybercrime gang has used to attacks in the wild.
Clop is the latest ransomware strain that Sangria Tempest has been observed deploying over the years. The group previously deployed REvil and Maze before managing the now-retired DarkSide and BlackMatter ransomware operations. reads one of the tweets published by the experts.
We are in the final!
Please vote for Security Affairs (...
00:00
How Far Can An EULA Go? Hackaday

We read this news with mixed glee and horror: a company called Telly is giving TVs away, for the low price of having to live with an always-on advertisement bar and some pretty stringent terms and conditions. Break the terms, and theyll repossess your TV. If you dont give them the TV, they have your credit card on record and they think the set is worth $1,000.
The hacker in me sees free hardware, so I checked out the terms and conditions, and it doesnt look good. Theyve explicitly ruled out opening up or physically modifying the device, and it has to continually have WiFi for which you pay, naturally. It sounds like it could easily tell if you try to tamper with it. My next thought was, perhaps too cynically, to get one, put it in the closet, and wait for the company to go bankrupt. Because you know that business model isnt going to last.
But its clear that theyve seen through me. The most bizarre clause is that you have to Use the Product as the primary television in Your household. Now, were not lawyers, but it seems like an amazing stretch that they can tell you how int...
Saturday, 20 May
23:37
Reddit Will Allow Users to Upload NSFW Images From Desktop SoylentNews
Reddit will allow users to upload NSFW images from desktop:
Reddit announced Thursday that it will now allow users to upload NSFW images from desktops in adult communities. The feature was already available on the social network's mobile app.
[...] "This now gives us feature parity with our mobile apps, which (as you know) already has this functionality. You must set your community to 18+ if your community's content will primarily be not safe for work (NSFW)," the company said.
Reddit's announcement comes days after Imgur said that the image hosting platform was banning explicit photos from May 15. At that time, the company said that explicit content formed a risk to Imgur's "community and its business". Banning this type of content would "protect the future of the Imgur community."
Many of Reddit's communities rely on Imgur's hosting services. However, the social network allowing native NSFW uploads through desktop might be the most logical solution going forward.
Image hosting is not the only hurdle for NSFW communities. Last month, when Reddit announced that it will start charging for its API, the company also said that it will limit access to mature content available through its API. This would directly impact the experience on third-party Reddit apps. In yesterday's announcement about desktop upload for NSFW images, a Reddit staff members said that the company is discussing how to navigate this situation.
Read more of this story at SoylentNews.
23:23
Generative AI Shakes Global Diplomacy At G7 Summit In Japan Lifeboat News: The Blog
Our technological age is witnessing a breakthrough that has existential implications and risks. The innovative behemoth, ChatGPT, created by OpenAI, is ushering us inexorably into an AI economy where machines can spin human-like text, spark deep conversations and unleash unparalleled potential. However, this bold new frontier has its challenges. Security, privacy, data ownership and ethical considerations are complex issues that we must address, as they are no longer just hypothetical but a reality knocking at our door.
The G7, composed of the worlds seven most advanced economies, has recognized the urgency of addressing the impact of AI.
To understand how countries may approach AI, we need to examine a few critical aspects.
Clear regulations and guidelines for generative AI: To ensure the responsible and safe use of generative AI, its crucial to have a comprehensive regulatory framework that covers privacy, security and ethics. This framework will provide clear guidance for both developers and users of AI technology.
Public engagement: Its important to involve different viewpoints in policy discussions about AI, as these decisions affect society as a whole. To achieve this, public consultations or conversations with the general public about generative AI can be helpful.
23:23
NASA Is Relying On Elon Musk And Jeff Bezos To Get Us Back To The Moon Lifeboat News: The Blog
NASA on Friday announced the second spacecraft it hopes will help return astronauts to the surface of the moon later this decade. Blue Origins Blue Moon lander joins the SpaceX Starship as the two vehicles the space agency aims to use for its Artemis program to once again put boots on lunar regolith.
Over a half-century after NASA used a massive investment of US GDP to fund the Apollo program and build the Saturn V rocket, humanitys next chapter in space is largely in the hands of two of the richest men in the world, SpaceX founder and chief twit Elon Musk and Amazon and Blue Origin head Jeff Bezos.
The shift in the provenance of Apollos mission architecture versus that of Artemis is, at the very least, a symbolic representation of a key shift in American society over the last few generations. Hot off the heels of successful collective action in Europe and elsewhere during World War II, the Americans again came together to catch up to and then surpass the Soviet Union in the space race.
23:23
NASA Should Send $17 Billion Human Mission To Mars In 2033, Say Experts Lifeboat News: The Blog
NASA could take advantage of a rare planetary alignment in 2033 to send the first crewed mission to orbit Mars and, on the way back, Venus. The short tripwhich would be the first interplanetary crew evercould be a pathfinder mission for the first crewed landing on the red planet in 2037.
Its the best time to go to Mars in the next 25 years, said Matt Duggan, mission management and operations manager at Boeing, addressing the 2023 Humans To Mars Summit on Wednesday at the National Academy of Sciences Building in Washington D.C. Thats in terms of the amount of energy and fuel you have to spend to get to Marsits a unique opportunity that comes around once every 15 years.
A mission plan to send crew in existing spacecraft on a 570-day return trip to orbit Mars and Venus will only work every 15 yearsand the next opportunity is 2033.
23:23
Big Tech is already warning us about AI privacy problems Lifeboat News: The Blog
That is, if youre paying attention.
So Apple has restricted the use of OpenAIs ChatGPT and Microsofts Copilot, The Wall Street Journal.
Its not just Apple, but also Samsung and Verizon in the tech world and a whos who of banks (Bank of America, Citi, Deutsche Bank, Goldman, Wells Fargo, and JPMorgan). This is because of the possibility of confidential data escaping; in any event, ChatGPTs privacy policy explicitly says your prompts can be used to train its models unless you opt out. The fear of leaks isnt unfounded: in March, a bug in ChatGPT revealed data from other users.
Apples banned the use of OpenAI as has Samsung, Verizon, and a whos who of banks. Should the rest of us be concerned about how our datas getting used?
23:22
Tesla FSD Overly Aggressive after BIG update Lifeboat News: The Blog

Not perfect, but very impressive.
Sponsored:
Use my special link https://www.privateinternetaccess.com/AIDRIVR
for an 83% discount, 4 months free and 30-day money-back guarantee
on the best VPN Private Internet Access.
Version: 11.4.1 [2023.7.5]
Consider supporting this channel on Patreon: https://patreon.com/AIDRIVR
Filming Equipment:
GoPro Hero 10 Black (Visualizations): https://amzn.to/3kGze2I
GoPro Hero 11 Black (Interior): https://amzn.to/3H7Xsuq.
GoPro Enduro Batteries: https://amzn.to/3wrzhSK
GoPro Dual Battery Charger: https://amzn.to/3XBxnLi.
Fat Gecko Triple Mount (Exterior): https://amzn.to/3R8J0GQ
Fat Gecko Double Suction Mount (Interior): https://amzn.to/3HyW0Tj.
Sony A6400 w/ 18-135mm Lens: https://amzn.to/3RauluT
Sigma 30mm F1.4 Lens: https://amzn.to/3HvOU1C
Insta360 One RS: https://www.insta360.com/sal/one_rs?insrc=INRP7IO
Insta360 X3 (free selfie stick!): https://www.insta360.com/sal/x3?insrc=INRP7IO
Insta360 X2 (free selfie stick!): https://www.insta360.com/sal/one_x2?insrc=INRP7IO
Editing Equipment:
16 MacBook Pro M1: https://amzn.to/3j71X04
Magic Trackpad: https://amzn.to/403P8UV
Roost V3 Laptop Stand: https://amzn.to/3JgqBX4
Phillips Fidelio X2HR: https://amzn.to/3wvuVd7
Dragonfly Cobalt: https://amzn.to/3kHLPCR
Shure SM7B Microphone: https://amzn.to/3wxz9kK
Gator Frameworks Mic Arm: https://amzn.to/3XGGE4E
Elgato Wave XLR Preamp: https://amzn.to/3XEZpW2
I earn from purchases you make via Amazon Associates & Insta360 af...
21:22
Aubrey de Grey: AI, in silico, LEV Foundation, Alpha Fold, Nanobots, OpenAI and Sam Altman Lifeboat News: The Blog

Aubrey: 50% chance to LEV in 1215 years, and a variety of topics from Rey Kurzweil to A.I. to Singularity, and so on.
In this podcast, Aubrey de Grey discusses his work as President and CSO at Lev Foundation and co-founder at Sense Research Foundation in the field of longevity. He explains how the Foundations focus is to combine rejuvenation and damage repair interventions to have greater efficacy in postponing aging and saving lives. De Grey believes that within 12 to 15 years, they have a 50% chance of achieving longevity escape velocity, which is postponing aging and rejuvenating the body faster than time passes. De Grey acknowledges the limitations of traditional approaches like exercise and diet in postponing aging and feels that future breakthroughs will come from high-tech approaches like skin and cell therapies. He discusses the potential of AI and machine learning in drug discovery and the possibility of using it to accelerate scientific experimentation to optimize decisions about which experiments to do next. De Gray cautions that the quality of conclusions from AI depends on the quality and quantity of input data and that the path towards defeating aging would require a symbiotic partnership between humans and AI. Finally, he discusses his excitement about the possibilities of hardware and devices like Apple Watch and Levels in tracking blood sugar levels and their potential to prolong life.
21:00
Hexed Home Assistant Monitors 3D Printers Hackaday

You can babysit your 3D printer 100% of the time, or you can cross your fingers and hope it all works. Some monitor their printers using webcams, but [Simit] has a more stylish method of keeping tabs on six 3D printers.
The idea is to use a 3D printed hex LED display found online. Adding an ESP32 and Home Assistant allows remote control of the display. The printers use Klipper and can report their status using an API called Moonraker. Each hexagon shows the status of one printer. You can tell if the printer is online, paused, printing, or in other states based on the color and amount of LEDs lit. For example, a hex turns totally green when printing is complete.
Once you have a web API and some network-controlled LEDs, it is relatively straightforward to link it together with Home Automation. Of course, you could do it other ways, too, but if you already have Home Automation running for other reasons, why not?
We have seen other ways to do this, of course. If you need an easy monitor, the eyes have it. If you dont use Klipper, OctoPrint can pull a similar stunt.
20:48
Meet 'Jack' from Romania! Mastermind Behind Golden Chickens Malware The Hacker News
The identity of the second threat actor behind the Golden Chickens malware has been uncovered courtesy of a fatal operational security blunder, cybersecurity firm eSentire said. The individual in question, who lives in Bucharest, Romania, has been given the codename Jack. He is one of the two criminals operating an account on the Russian-language Exploit.in forum under the name "badbullzvenom,"
20:30
Intel Publishes "X86-S" Specification For 64-bit Only Architecture Phoronix
Intel quietly released a new whitepaper and specification for their proposal on "X86-S" as a 64-bit only x86 architecture. If their plans workout, in the years ahead we could see a revised 64-bit only x86 architecture...
19:59
US CISA warns of a Samsung vulnerability under active exploitation Security Affairs
US CISA added the vulnerability CVE-2023-21492 flaw affecting Samsung devices to its Known Exploited Vulnerabilities Catalog.
US CISA added the vulnerability CVE-2023-21492 vulnerability (CVSS score: 4.4) affecting Samsung devices to its Known Exploited Vulnerabilities Catalog.
The issue affects Samsung mobile devices running Android 11, 12, and 13, it is described as an insertion of sensitive information into log file vulnerability that allows a privileged, local attacker to conduct an address space layout randomization (ASLR) bypass.
The issue was reported on January 17, 2023, the company addressed the issue by removing kernel pointers in log file.
Kernel pointers are printed in the log file prior to SMR May-2023 Release 1 allows a privileged local attacker to bypass ASLR. reads the advisory published by Samsung. Samsung was notified that an exploit for this issue had existed in the wild
The company did not provide details about the attacks exploiting the flaw, but likely the issue was chained with other vulnerabilities to compromise vulnerable Samsung devices.
CISA also addressed the following issue in the latest turn:
- CVE-2004-1464 Cisco IOS Denial-of-Service Vulnerability. Cisco IOS contains an unspecified vulnerability that may block further telnet, reverse telnet, Remote Shell (RSH), Secure Shell (SSH), and in some cases, Hypertext Transport Protocol (HTTP) access to the Cisco device.
- CVE-2016-6415 Cisco IOS, IOS XR, and IOS XE IKEv1 Information Disclosure Vulnerability. Cisco IOS, IOS XR, and IOS XE contain insufficient condition checks in the part of the code that handles Internet Key an information disclosure vulnerability in the Internet Key memory contents. Successful exploitation could allow the attacker to retrieve memory contents, which can lead to information disclosure.
According to Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities, FCEB agencies have to address the identified vulnerabilities by the due date to protect their networks against attacks exploiting the flaws in the catalog.
E...
19:55
Microsoft Preparing For Their First Vulkan Extension Phoronix
While the Vulkan high performance graphics and compute API is backed by many vendors, Microsoft and Apple are two notable organizations that haven't backed this Khronos Group standard. For Microsoft's part, they obviously prefer their in-house Direct3D. However, Microsoft is making preparations for submitting their first Vulkan extension...
19:43
AMD Has A One-Liner To Help Speed Up Linux System Resume Time Phoronix
AMD engineers have been working out many quirks and oddities in system suspend/resume handling to make it more reliable on their hardware particularly around Ryzen laptops. In addition to suspend/resume reliability improvements and suspend-to-idle (s2idle) enhancements, one of their engineers also discovered an easy one-liner as a small step to speeding up system resume time...
19:28
Virtual ALSA Driver Posted To Help With Linux Testing/Fuzzing Phoronix
Ivan Orlov this past week posted the patches for VALSA, the Virtual ALSA sound driver that aims to help Linux kernel developers in testing and fuzzing of the sound subsystem...
19:22
Wireless power demonstration overcomes a major hurdle Lifeboat News: The Blog
Wireless power would be worth the hype if it were widespread modern life is burdened by a tangle of power cables and an endless hunt for plugs. But despite its potential, wireless power technology is still limited by range.
But Ericsson and PowerLight Technologies have made one dramatic form of wireless power, called optical beaming, work in a proof-of-concept experiment. Their demonstration showed that laser delivery of power to a portable 5G base station could be just around the corner.
The promise of wireless power: Wireless power is straight out of a sci-fi film: electrical power transmitted from place to place through a vacuum or the air. There is no need for wires, poles, outlets, or those pesky USB cubes, which are always lost when you need them most.
19:21
Links 20/05/2023: CodeWeavers Without Jeremy White Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Pseudo-Open Source
- Linux Foundation
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Monopolies
-
GNU/Linux
-
Desktop/Laptop
-
...
-
-
19:15
Gemini Links 20/05/2023: Ascension Day and Closed Registration for flounder.online (Small Web) Techrights
-
Gemini* and Gopher
-
Personal
-
Introducing the Broad Framework
* Pointers on how to get a starter that is more yeast-y (use a stiff starter, maybe 50% hydration) or with more lactic acid bacteria (drown the starter in 500% hydration). Also that the drowning can help with mold problems.
-
Summer Springing Up
For the past two summers in Sacramento, by the time May rolled around it was hot, IE 90+ degrees most days. I moved here May 24Th 2021 and slept on top of the covers every single night until mid September since it would stay hot late into the night. In 2022 it was regularly into the 90s by April and stayed hot late into October, a long, hot Summer. This year we had a pretty brutal Winter, the most rain Ive seen in California in all my life. The rain wasnt actually all that hard, it was the strong winds that came with it that brought down so many trees. However the rain did last for a long time. Normally we would get 2 or 3 days of rain like walls of water when you step outside, and then a couple sprinkles here or there, which almost always wasnt enough water for the year. Now weve gotten more than we possibly can imagine, lakes are filling back up, rivers are higher than ever, everything is so green. The multi-week long light to moderate rain showers was not the California I was used to.
-
Driving in England
I live in the United States, but this weekend the family have traveled to the UK to attend a wedding. I have visited other countries in Europe before, but not England.
We decided to rent a car for the duration of our stay. Ive never driven a right-hand drive vehicle before, much less driven in left-hand traffic. Of course that meant that we, jet-lagged and very tired, had to drive to the inn with everything on the opposite side from that to which Im accustomed.
-
...
-
-
18:54
Electric Two-wheelers are Set to Scoot Past EVs in Asia SoylentNews
Electric two-wheelers are set to scoot past EVs in road race:
Video Visit Asia's emerging megacities and you'll quickly notice that scooters and motorbikes vastly outnumber cars. Before long these fleets of two-wheelers will become battery-powered, always-connected, semi-autonomous machines that offer an even more potent alternative to their four-wheeled rivals.
The reasons powered two-wheelers dominate nations such as India, Indonesia and Vietnam with a combined population over 1.75 billion are simple: cars are unaffordable on local wages, few urban homes have space to store them, and warm climates make two-wheelers viable year-round. Plus, many of them sell for less than the equivalent of $1,000 apiece.
The industry has decided many will soon be electric and it looks like drivers will buy them.
"Electrification of micromobility can be adopted at a faster pace than cars, mainly because the motor and batteries are much smaller," Fook Fah Yap, a director at Singapore's Nanyang Technical University's Transport Research Centre told The Register.
Evidence of the shift is not hard to find. Earlier this year Honda announced it will start to sell 10 battery-powered bikes in 2025. Yamaha expects 90 percent of its sales will be electrified by 2050 and Toyota is expected to announce an electric two-wheeler this year.
[...] Twowheelers, by contrast, are all about getting from A to B, quickly and at low cost. Digital technology's role in a two-wheeler is therefore all about information related to navigation.
Read more of this story at SoylentNews.
18:02
Cryptogon Syndication to Twitter Disabled cryptogon.com
For about a decade, Ive been able to automatically post Cryptogon stories to Twitter using a plugin called WP to Twitter. That ended about a hour ago. After trying to troubleshoot, recreating my Twitter apps and API keys, etc. Im getting this error: 403 Forbidden: The request is understood, but has been refused by Twitter. []
18:00
Get That Dream Job, With a Bit of Text Injection Hackaday

Getting a job has always been a tedious and annoying process, as for all the care that has been put into a CV or resume, it can be still headed for the round file at the whim of some corporate apparatchik. At various times there have also been dubious psychometric tests and other horrors to contend with, and now we have the specter of AI before us. We can be tossed aside simply because some AI model has rejected our CV, no human involved. If this has made you angry, perhaps its time to look at [Kai Greshake]s work. Hes fighting back, by injecting a PDF CV with extra text to fool the AI into seeing the perfect candidate, and even fooling AI-based summarizers.
Text injection into a PDF is a technique the same as used by the less salubrious end of the search engine marketing world, of placing text in a web page such that a human cant read it but a machine can. The search engine marketeers put them in tiny white text or offset them far out of the viewport, and it seems the same is possible in a PDF. Hes put the injection in white and a tiny font, and interestingly, overlaid it several times.
Using the ChatGPT instance available in the Bing sidebar hes then able to fool it into an affirmative replay to questions about whether he should be hired. But its not just ChatGPT...
17:22
Apple reportedly limits internal use of AI-powered tools like ChatGPT and GitHub Copilot Lifeboat News: The Blog
As big tech companies are in a fierce race with each other to build generative AI tools, they are being cautious about giving their secrets away. In a move to prevent any of its data from ending up with competitors, Apple has restricted internal use of tools like OpenAIs ChatGPT and Microsoft-owned GitHubs Copilot, a new report says.
According to The Wall Street Journal, Apple is worried about its confidential data ending up with developers who trained the models on user data. Notably, OpenAI launched the official ChatGPT app on iOS Thursday. Separately, Bloomberg reporter Mark Gurman tweeted that the chatbot has been on the list of restricted software at Apple for months.
I believe ChatGPT has been banned/on the list of restricted software at Apple for months. Obviously the release of ChatGPT on iOS today again makes this relevant.
17:22
Apple is on the hunt for generative AI talent Lifeboat News: The Blog
Apple, like a number of companies right now, may be grappling with what role the newest advances in AI are playing, and should play, in its business. But one thing Apple is confident about is the fact that it wants to bring more generative AI talent into its business.
The Cupertino company has posted at least a dozen job ads on its career page seeking experts in generative AI. Specifically, its looking for machine learning specialists passionate about building extraordinary autonomous systems in the field. The job ads (some of which seem to cover the same role, or are calling for multiple applicants) first started appearing April 27, with the most recent of them getting published earlier this week.
The job postings are coming amid some mixed signals from the company around generative AI. During its Q2 earnings call earlier this month, CEO Tim Cook dodged giving specific answers to questions about what the company is doing in the area but also didnt dismiss it. While generative AI was very interesting, he said, Apple would be deliberate and thoughtful in its approach. Then yesterday, the WSJ reported that the company had started restricting use of OpenAIs ChatGPT and other external generative AI tools for some employees over concerns of proprietary data leaking out through the platforms.
17:22
Cruise, Waymo near approval to charge for 24/7 robotaxis in San Francisco Lifeboat News: The Blog
Self-driving vehicle companies Waymo and Cruise are on the cusp of securing final approval to charge fares for fully autonomous robotaxi rides throughout the city of San Francisco at all hours of the day or night.
Amid the citys mounting resistance to the presence of AVs, the California Public Utilities Commission (CPUC) published two draft resolutions late last week that would grant Cruise and Waymo the ability to extend the hours of operation and service areas of their now-limited robotaxi services.
The drafts are dated for a hearing June 29, and theres still room for public comments, which are due May 31. Based on the CPUCs drafted language, many of the protests raised by the city of San Francisco have already been rejected.
17:00
Big Bad Canada Pushes to Protect Profits from Mexico Terra Forming Terra

The Simplest Way to Flush Kidney Stones, Other Stones out of the Body Terra Forming Terra
The Surprising Link Between Water Intake and Stroke Risk Terra Forming Terra
Battle of the Fake Historians Heats Up Terra Forming Terra

16:51
30-Ton Shipment Of Explosive Chemical Disappears Between California And Wyoming cryptogon.com
Fell out the bottom of the rail car? Via: ZeroHedge: A 30-ton shipment of ammonium nitrate, a chemical used as both fertilizer and as a component in explosives, has gone missing during a rail shipment between Wyoming and California last month, resulting in four separate investigations. The railcar was sealed when it left the []
16:49
Notorious Cyber Gang FIN7 Returns With Cl0p Ransomware in New Wave of Attacks The Hacker News
The notorious cybercrime group known as FIN7 has been observed deploying Cl0p (aka Clop) ransomware, marking the threat actor's first ransomware campaign since late 2021. Microsoft, which detected the activity in April 2023, is tracking the financially motivated actor under its new taxonomy Sangria Tempest. "In these recent attacks, Sangria Tempest uses the PowerShell script POWERTRASH to load
16:38
Do You Need a New Iron? cryptogon.com
My wifes taste in dresses, skirts and aprons goes back about 150 years. Rather than attempting to buy clothing like that, she makes it herself using her mothers (borrowed) Bernina sewing machine from 1982 and an iron. The iron shed been using for the last fifteen years blew up. I tried to fix it, but []
15:00
Spy Transceiver Makes Two Tubes Do the Work of Five Hackaday

Here at Hackaday, we love following along with projects as they progress. Thats especially true when a project makes a another, or when the original design gets more elegant. And when you get both improved function and decreased complexity at the same time? Thats the good stuff.
Take the recent improvements to a vacuum tube spy radio as an example. Previously, [Helge (LA6NCA)] built both a two-tube transmitter and a three-tube receiver, either of which would fit in the palm of your hand. A little higher math seems to indicate that combining these two circuits into a transceiver would require five tubes, but thats not how hams like [Helge] roll. His 80-m CW-only transceiver design uses only two tubes and a lot of tricks, which we admit were still wrapping our heads around. On the receive side, one tube serves as a mixer/oscillator, combining the received signal with a slightly offset crystal-controlled signal to provide the needed beat frequency. The second tube serves as the amplifier, bot...
14:15
Warning: Samsung Devices Under Attack! New Security Flaw Exposed The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned of active exploitation of a medium-severity flaw affecting Samsung devices. The issue, tracked as CVE-2023-21492 (CVSS score: 4.4), impacts select Samsung devices running Android versions 11, 12, and 13. The South Korean electronics giant described the issue as an information disclosure flaw that could be exploited by a
14:10
Astronomers Solve the 60-Year Mystery of Quasars the Most Powerful Objects in the Universe SoylentNews
First discovered 60 years ago, quasars can shine as brightly as a trillion stars packed into a volume the size of our Solar System. In the decades since they were first observed, it has remained a mystery what could trigger such powerful activity. New work led by scientists at the Universities of Sheffield and Hertfordshire has now revealed that it is a consequence of galaxies crashing together.
The collisions were discovered when researchers, using deep imaging observations from the Isaac Newton Telescope in La Palma, observed the presence of distorted structures in the outer regions of the galaxies that are home to quasars.
Most galaxies have supermassive black holes at their centres. They also contain substantial amounts of gas but most of the time this gas is orbiting at large distances from the galaxy centres, out of reach of the black holes. Collisions between galaxies drive the gas towards the black hole at the galaxy centre; just before the gas is consumed by the black hole, it releases extraordinary amounts of energy in the form of radiation, resulting in the characteristic quasar brilliance.
[...] This is the first time that a sample of quasars of this size has been imaged with this level of sensitivity. By comparing observations of 48 quasars and their host galaxies with images of over 100 non-quasar galaxies, researchers concluded that galaxies hosting quasars are approximately three times as likely to be interacting or colliding with other galaxies.
The study has provided a significant step forward in our understanding of how these powerful objects are triggered and fuelled.
Journal Reference:
C S Pierce et al., Galaxy interactions are the dominant
trigger for local type 2 quasars [open], Monthly Notices of
the Royal Astronomical Society, Volume 522, Issue 2, June
2023, Pages 17361751, https://doi.org/10.1093/mnras/stad455
Read more of this story at SoylentNews.
12:02
OSI Running Microsoft Ads (and Promoting Proprietary GitHub) Under the Guise of Webinar Techrights
The Open Source Initiative, or OSI for short, is basically a Microsoft front group these days
Summary: Microsofters are speaking on behalf of OSI again, jointly with Linux Foundation, essentially promoting Microsofts own initiatives [1, 2, 3, 4] and traps like proprietary GitHub, which abuses the GPL (the OSIs chief actively lobbies for Microsoft on Microsofts payroll in class action litigation over GPL violations)
12:00
Prompt Injection: An AI-Targeted Attack Hackaday

For a brief window of time in the mid-2010s, a fairly common joke was to send voice commands to Alexa or other assistant devices over video. Late-night hosts and others would purposefully attempt to activate voice assistants like these en masse and get them to do ridiculous things. This isnt quite as common of a gag anymore and was relatively harmless unless the voice assistant was set up to do something like automatically place Amazon orders, but now that much more powerful AI tools are coming online were seeing that joke taken to its logical conclusion: prompt-injection attacks.
Prompt injection attacks, as the name suggests, involve maliciously inserting prompts or requests in interactive systems to manipulate or deceive users, potentially leading to unintended actions or disclosure of sensitive information. Its similar to something like an SQL injection attack in that a command is embedded in something that seems like a normal input at the start. Using an AI like GPT comes with an inherent risk of attacks like this when using it to automate tasks, as commands to the AI can be hidden where a user might not ex...
11:30
[Meme] A Racket in Open Source Clothing Techrights
He quietly stole his workers money and bought luxury cars
Summary: The fraud at Sirius Open Source had many victims; most of them are voiceless, however, as they dont blog, but they still got robbed and they want justice.
11:21
Getting Sirius Managers Arrested Before They Dismantle the Company and Vanish schestowitz.com
Summary: The crimes of Sirius Open Source have culminated in two parallel reports; tax fraud was reported as well, as per advice weve received, even though thats not the crime but a side issue for a company that became petty thief (very big thief)
Maybe it shouldnt be so surprising. Ive noticed that almost everyone at Sirius has left already. Very few are left there and they too are looking for a way out (another job). But that wouldnt be the end of this affair because criminals must be held accountable. They know who they are. Theyre managers. Theyre also perpetrators.
Many parties knowingly or unknowingly facilitated the crime. One person recently asked me: Did Standard Life ever send you a statement showing the purported balance of the account or even a statement showing a nil balance?
No is the short answer, but all of us assumed it was just being silent. All of us.
There is a problem associated with legitimisation of the embezzlement, including letters and payslips that fraudulently claimed pension money had been paid. Every single payslip was a lie. Were talking about hundreds of payslips.
The Pensions Regulator deals with different scenarios, so it is inapplicable here.
Another person asked: Do you have legal advice on the topic?
Well, we went to a lawyer as soon as last year. We agreed its not worth suing due to speed and a lack of funds in the company. There would hardly be anything left after 12 months. Litigation is very time-consuming a process. Just 5.5 months after I left the company there are fewer than 5 full-time workers there.
The same person added:
These appear to be the two pertinent questions:
Does the employer owe a debt to you or they owe the money to the pension scheme? This is an important technicality. For example, can they simply discharge their responsibility by giving you a lump sum directly and you can put it in any pension you want.
Defrauding employees and then offering them the money stolen (after getting caught) doesnt change the fact that fraud took place.
It seems possible that the company tried to pay off one victim to keep silent on the matter, but we cannot prove this.
The above...
11:13
Holding Criminals Accountable Part VII Fraud Since 2011 (If Not Earlier) Merits Criminal Prosecution Techrights
Series parts:
- Holding Criminals Accountable Part I Sirius Crimes Reported to British Authorities, Formally Registered With References (Many Victims), Heres What It Means and What Happens Next
- Holding Criminals Accountable Part II Still No Action From Action Fraud
- Holding Criminals Accountable Part III Why Police Action is the Only Option Now
- Holding Criminals Accountable Part IV British Prime Minister Launches Crackdown on Fraud, So Now Prove It
- Holding Criminals Accountable Part V 20 Days Later, UK Action Fraud Shows No Signs of Action
- Holding Criminals Accountable Part VI 26 Days Later and Still Inaction/No Action by the Police That Had Endless Resources for Coronation Ceremony
- YOU ARE HERE Fraud Since 2011 (If Not Earlier) Merits Criminal Prosecution
Summary: The crimes of Sirius Open Source have culminated in two parallel reports; tax fraud was reported as well, as per advice weve received, even though thats not the crime but a side issue for a company that became petty thief (very big thief)
Maybe it shouldnt be so surprising. Ive noticed that almost everyone at Sirius has left already. Ve...
10:17
Edward Snowden in FSF Event: What Happened in 2013 Would Not Have Been Possible Without Free Software Techrights
10:12
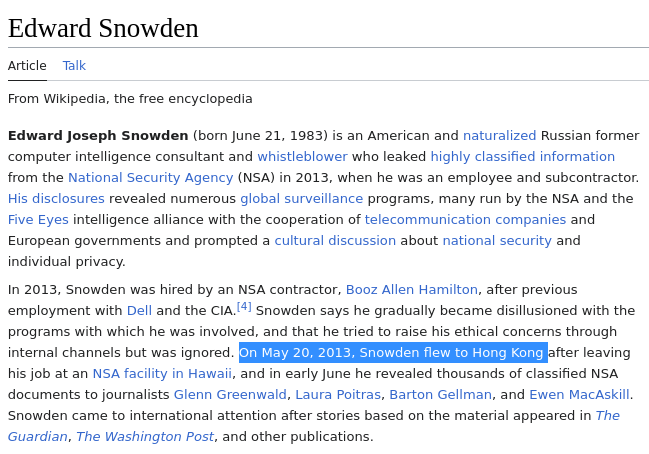
10 Years Ago Edward Snowden Did the Right Thing Techrights
This happened 10 years ago:
And he still talks about the dangers:
Summary: Many people have set aside the lessons learned from the NSA leaks, almost as if all these practices just gradually stopped over time (theyve only gotten worse since then)
10:04
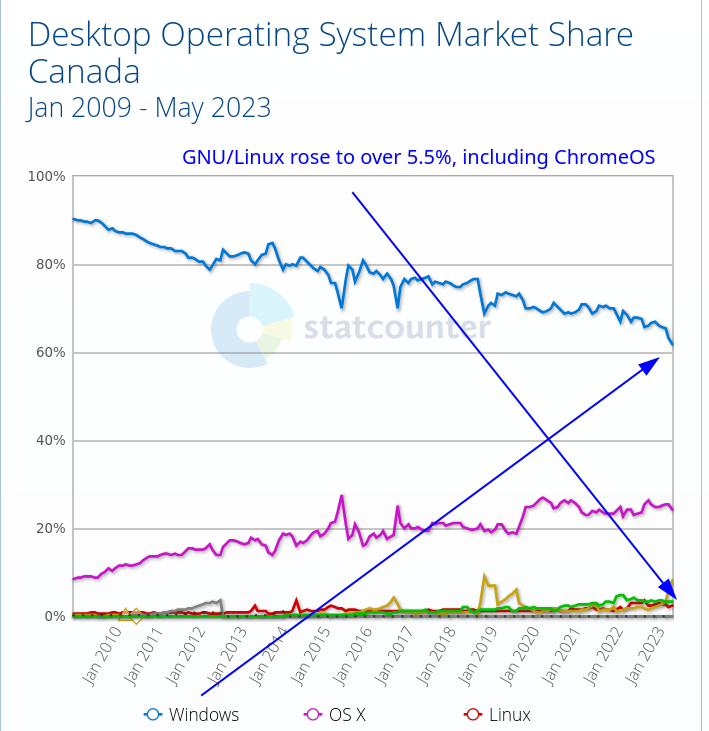
Canadian Desktops and Laptops: Windows 61.7%, GNU/Linux 5.5% Techrights
Summary: This months numbers show another shark drop for Windows; GNU/Linux + ChromeOS (based on Gentoo) rose to over 5.5% in Canada, where many schools ditched Windows
09:30
Sirius Open Source Reported to HM Revenue and Customs (HMRC) for Tax Fraud Techrights
Much more to come very soon
Summary: Today, 28 days after crimes of Sirius Open Source had been reported to the police (which barely made any progress, as expected), were proceeding to a report for tax fraud; we have extensive evidence that the payslips of several employees lied for over half a decade, in effect defrauding the British taxpayers, not just embezzling the staff
09:24
Malware Turns Home Routers Into Proxies for Chinese State-Sponsored Hackers SoylentNews
Malware turns home routers into proxies for Chinese state-sponsored hackers
Researchers have uncovered malicious firmware that can turn residential and small office routers into proxies for Chinese state-sponsored hackers. The firmware implant, discovered by Check Point Research, includes a full-featured backdoor that allows attackers to establish communication, issue commands, and perform file transfers with infected devices. The implant was found in TP-Link routers but could be modified to work on other router models.
The malware's main purpose is to relay traffic between infected targets and command-and-control servers, obscuring the origins and destinations of the communication. The control infrastructure was traced back to hackers associated with the Chinese government. By using a chain of infected devices, the attackers can hide the final command and control and make it difficult for defenders to detect and respond to the attack.
This technique of using routers and other IoT devices as proxies is a common tactic among threat actors. The researchers are unsure how the implant is installed on devices but suspect it could be through exploiting vulnerabilities or weak administrative credentials.
While the firmware image discovered so far only affects TP-Link devices, the modular design allows the threat actors to create images for a wider range of hardware. The article concludes with recommendations for users to check for potential infections and apply proactive mitigations such as patching routers and using strong passwords.
Read more of this story at SoylentNews.
09:00
Early Computer Art from the 1950s and 1960s Hackaday

Modern day computer artist, [Amy Goodchild] surveys a history of Early Computer Art from the 1950s and 1960s. With so much attention presently focused on AI-generated artwork, we should remember that computers have been used to created art for many decades.
Our story begins in 1950 when Ben Laposky started using long exposure photography of cathode ray oscilloscopes to record moving signals generated by electronic circuits. In 1953, Gordon Pask developed the electromechanical MusiColor system. MusiColor empowered musicians to control visual elements including lights, patterns, and motorized color wheels using sound from their instruments. The musicians could interact with the system in real-time, audio-visual jam sessions.
In the early 1960s, BEFLIX (derived form Bell Flix) was developed by Ken Knowlton at Bell Labs as a programming language for generating video animations. The Graphic 1 computer featuring a light pen input device was also developed at Bell Labs. Around the sa...
08:59
Links 19/05/2023: AlmaLinux 8.8 and GNU Health in Afghanistan Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Pseudo-Open Source
- Linux Foundation
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Monopolies
-
GNU/Linux
-
Desktop/Laptop
-
07:15
Piracy Bots Channels Are Rampant on Telegram, But For How Long? TorrentFreak
 With over half a billion active users around the globe,
Telegram is one of the most
used messaging services.
With over half a billion active users around the globe,
Telegram is one of the most
used messaging services.
The communication platform helps to connect people from all over the world, with end-to-end encryption providing improved security when compared to some other players in the market.
Telegram can also be an excellent medium to broadcast messages to a wider audience. Through dedicated one-way channels, people can share news, status updates, and emergency alerts, for example.
Telegram on the Anti-Piracy Agenda
Like all technology, these broadcast channels are not only used for legitimate purposes. Pirates use them too, as evidenced by regular mentions in piracy discussions. Not too long ago, the European Commission placed the Telegram app on its Counterfeit and Piracy Watch List.
The app was also mentioned in recommendations to the U.S. Trade Representative (USTR) this year, with the International Intellectual Property Alliance calling for stricter policies on Telegrams part, including the addition of Know Your Business Customer (KYBC) rules.
Telegram should be more accountable in relation to infringements occurring or being facilitated over its service, the recommendation advised.
IIPA recommends that more be done to encourage KYBC disciplines on intermediaries like Telegram and to encourage operators like them to responsibly cooperate.
Courts Get Involved
Piracy concerns and policy musings like these havent been restricted to lobbying and policy efforts. Telegram has also been taken to court on several occasions.
In Portugal, for example, a local court ordered Telegram to block access to more than a dozen piracy-related channels. Similar measures were also taken in Israel and Italy. In India, Telegram a court order required Telegram to disclose the identities of several pirating users.
By now, Telegram is well aware of the piracy challenges but that hasnt put an end to the problem.
While doing research this week, we randomly stumbled upon a Telegram bot that directed us to a cha...
07:03
Overcoming Kubernetes Monitoring Challenges with Observability Linux.com

Kubernetes adoption is rapidly increasing, surpassing cloud
adoption, as companies recognize its ability to provide agility and
flexibility in deploying critical applications. However, the
additional layers of abstraction in Kubernetes pose challenges to
observability. Understanding whats running in each cluster, node,
or pod is a top monitoring challenge since resources constantly
move. This complexity creates an increased security challenge due
to uncertainty about the running environment.
The post Overcoming Kubernetes Monitoring Challenges with Observability appeared first on Linux.com.
06:59
[$] Fighting the zombie-memcg invasion LWN.net
Memory control groups (or "memcgs") allow an administrator to manage the memory resources given to the processes running on a system. Often, though, memcgs seem to have memory-use problems of their own, and that has made them into a recurring Linux Storage, Filesystem, and Memory-Management Summit topic since at least 2019. The topic returned at the 2023 event with a focus on the handling of shared, anonymous memory. The quirks associated with this memory type, it seems, can subject systems to an unpleasant sort of zombie invasion; a session in the memory-management track led by T.J. Mercier, Yosry Ahmed, and Chris Li discussed possible solutions.
06:40
What Makes Junk Food Junk? SoylentNews
How is "junk food" defined for food policies like taxes? A combination of food category, processing, and nutrients can determine which foods should be subject to health-related policies, according to a new analysis examining three decades of U.S. food policies by researchers at the NYU School of Global Public Health and the Friedman School of Nutrition Science and Policy at Tufts.
[...] "There is a growing recognition that an unhealthy diet stems from overconsumption of what we colloquially refer to as 'junk food,' " said Jennifer Pomeranz, assistant professor of public health policy and management at NYU School of Global Public Health and the first author of the study, published in the journal Milbank Quarterly. "However, public health efforts to address junk food are hindered by a lack of a uniform method to define junk food for policy purposes."
One policy example where a definition for junk food is needed is a junk food tax, which raises the price of such products to reduce consumption and generate revenue for other programs to improve the nutrition and health of communities in need. Previous research by NYU and Tufts shows that taxes on junk food are administratively and legally feasible.
[...] They identified and analyzed 47 laws and bills from 1991 through 2021, including one active junk food tax law implemented by the Navajo Nation, three state snack food sales taxes that were later repealed, and numerous junk food tax bills that have not been enacted. (Their analysis did not include policies that solely focused on beverages such as soda taxes.)
[...] The researchers were surprised that no state tax laws or bills directed the state's public health department to define the foods subject to the tax, a practice regularly used at the federal level and a mechanism that states could use to have experts define the foods to be taxed.
Read more of this story at SoylentNews.
06:24
Luxottica - 77,093,812 breached accounts Have I Been Pwned latest breaches
In March 2021, the world's largest eyewear company Luxoticca suffered a data breach via one of their partners that exposed the personal information of more than 70M people. The data was subsequently sold via a popular hacking forum in late 2022 and included email and physical addresses, names, genders, dates of birth and phone numbers. In a statement from Luxottica, they advised they were aware of the incident and are currently "considering other notification obligations".
06:14
OpenAI Launches ChatGPT App for iOS, Bolstering Accessibility and Safety HackRead | Latest Cybersecurity and Hacking News Site
While the ChatGPT app is currently available exclusively for iOS users, OpenAI assures Android users that they are next in line to experience the benefits of the app.
This is a post from HackRead.com Read the original post: OpenAI Launches ChatGPT App for iOS, Bolstering Accessibility and Safety
06:00
3D Printing Blueprints and Other Wall Art Hackaday

Today if you want to reproduce a big schematic or a mechanical drawing, you just ask it to print or plot from the CAD model. But back in the day, you drew on big sheets at a drafting table. How do you make copies? Sure, there were a few large-format copiers, but they were expensive. A more common method was to use a heliographic copier which, often but not always, resulted in a blueprint that is a blue page with white lines or vice versa. These days, you are more likely to see a blueprint as an artistic wall hanging, and since [Basement Creations] wanted some, he figured out how to make them with a 3D printer.
These prints arent really blueprints. They use the printer as a plotter and deposit white ink on a blue page. In the video below, he shows a number of ways to use a printer to create interesting wall art, even if you want it to be bigger than the print bed. Some of the wall art uses multiple 3D printed parts, and others use the printer as a plotter.
To join the printed pieces, he uses a soldering iron to weld them together. We wondered if it might be worthwhile to make overlapping pieces to glue which would also help with alignment. Plotting is great for making PCBs, of course, and while you could invert the image and print blue on white paper, it wont really look like a blueprint.
Youd think mounting a pen to a printer is easy, and...
05:19
Biden Clears Way for Ukraine to Get F-16 Fighter Jets cryptogon.com
Via: The Messenger: The U.S. will support an international effort to train Ukrainian pilots on F-16 fighter jets, a senior administration official confirmed to The Messenger, a shift in policy that will clear the way for F-16s and other aircraft to be sent to Ukraine. President Joe Biden announced the change to other world leaders []
05:17
Actual Headline: $3 Billion Accounting Error Means the Pentagon Can Send More Weapons to Ukraine cryptogon.com
Via: AP: The Pentagon has overestimated the value of the weapons it has sent to Ukraine by at least $3 billion an accounting error that could be a boon for the war effort because it will allow the Defense Department to send more weapons now without asking Congress for more money. The acknowledgment Thursday []
05:01
Robert F. Kennedy Jr. Names Dennis Kucinich as 2024 Campaign Manager cryptogon.com
Via: The Hill: Robert F. Kennedy Jr. has appointed former Rep. Dennis Kucinich (D-Ohio) as the campaign manager for his 2024 primary challenge to President Biden. Dennis Kucinich has brought invaluable electoral experience to our campaign, Kennedy said in a statement. He knows how the system works from the inside out, and his deep knowledge []
04:52
CIA Contractor, Dr. Garry Nolan, Claims U.S. Government Has, Downed UFOs, Reverse Engineering Programs cryptogon.com
This might be the biggest limited hangout of all time. Nolan states, Whats crashing is not actual living things Mostly, what youre seeing here are either drones or some sort of advanced AI. So, for everyone keeping score, according to Nolan, the U.S. Government is in possession of, Downed UFOs, but dont worry about the []
04:30
Video Friday: Lunar Transport IEEE Spectrum

Video Friday is your weekly selection of awesome robotics
videos, collected by your friends at IEEE Spectrum
robotics. We also post a weekly calendar of upcoming robotics
events for the next few months. Please
send us your events for inclusion.
ICRA 2023: 29 May2 June 2023, LONDON
Energy Drone & Robotics Summit: 1012 June 2023, HOUSTON
RoboCup 2023: 410 July 2023, BORDEAUX, FRANCE
RSS 2023: 1014 July 2023, DAEGU, SOUTH KOREA
IEEE RO-MAN 2023: 2831 August 2023, BUSAN, SOUTH KOREA
IROS 2023: 15 October 2023, DETROIT
CLAWAR 2023: 24 October 2023, FLORIANOPOLIS, BRAZIL
Humanoids 2023: 1214 December 2023, AUSTIN, TEXAS
Enjoy todays videos!
LATTICE is an undergrad project from Caltech thats developing a modular robotic transportation system for the lunar surface that uses autonomous rovers to set up a sort of cable car system to haul things like ice out of deep craters to someplace more useful. The prototype is fully functional, and pretty cool to watch in action.
Were told that the team will be targeting a full system demonstration deploying across a crater on Earth this time next year. As to what those quotes around crater mean, your guess is as good as mine.
[ Caltech ]
Thanks, Lucas!
Happy World Cocktail Day from Flexiv!
...
04:00
IEEE Celebrates Engineering Pioneers and Emerging Technologies IEEE Spectrum

IEEEs Vision, Innovation, and Challenges Summit and Honors Ceremony showcases emerging technologies and celebrates engineering pioneers who laid the groundwork for many of todays electronic devices. I attended this years events, held on 4 and 5 May in Atlanta. Here are highlights of the sessions, which are available on IEEE.tv.
The summit kicked off on 4 May at the Georgia Aquarium with a reception and panel discussion on climate change and sustainability, moderated by Saifur Rahman, IEEE president and CEO. The panel featured Chris Coco, IEEE Fellow Alberto Moreira, and IEEE Member Jairo Garcia. Coco is senior director for aquatic sustainability at the aquarium. Moreira is director of the German Aerospace Center Microwaves and Radar Institute in Oberpfaffenhofen, Bavaria. Garcia is CEO of Urban Climate Nexus in Atlanta. UCN assists U.S. cities in creating and executing climate action and resilience plans.
The panelists focused on how the climate crisis is affecting the ocean and ways technology is helping to track environmental changes.
Coco said one of the biggest challenges facilities such as his are facing is finding enough food for their animals. Because sea levels and temperatures are rising, more than 80 percent of marine life is migrating toward the Earths poles and away from warmer water, he said. With fish and other species moving to new habitats, ocean predators that rely on them for food are following them. This migration is making it more difficult to find food for aquarium fish, Coco said. He added that technology on buoys is monitoring the waters quality, and temperature, and levels.
Moreira, recipient of this years...
03:58
Google's New Registered Domains Include .Zip and .Mov for a More "Exciting" and Insecure Internet SoylentNews
Researchers are debating how the new domains will affect web security and users' habits:
In Google's own words, new generic top-level domains (gTLDs) can help self-expression, creativity and business. The previously approved list of "hundreds" of gTLDs entries now provides some troublesome additions such as "zip" and "mov," which can (and will) be abused to target users with sophisticated phishing attacks.
Google Registry has recently introduced 8 new top-level domains for "dads, grads, and techies," adding .dad, .phd, .prof, .esq, .foo, .nexus, .zip, and .mov to its growing list of some of the "most popular" gTLDs which also include .app and .dev. The .zip and .mov domains, however, have sparked a debate among experts about their potential consequences on internet and web overall security.
The zip and mov gTLDs were available in IANA's DNS records since 2014, but they have now become generally available thanks to Google's involvement. Now, anyone can purchase a ".zip" or ".mov" domain like "techspot.zip," even though the two suffixes have long been used to identify compressed file archives in Zip format and video clip files.
The overlap between two, extremely popular file formats the Zip standard was created by Pkware in 1989, 34 years ago and the recently registered web domains will bring new security threats to the internet ecosystem, some researchers said. Users could be deceived by malicious URLs shared on social networks or by mail, giving cyber-criminals new, "creative" tools to push malware installations, phishing campaigns or other nefarious activities.
Read more of this story at SoylentNews.
03:50
February cyber incident will cost molten metal flow engineering firm Vesuvius 3.5 million Security Affairs
Vesuvius, a leader in molten metal flow engineering and technology, revealed that the February cyber incident will cost it 3.5 million
Vesuvius is a global leader in molten metal flow engineering and technology, it employs more than 10,000 people and is listed on the London Stock Exchange. In February the company disclosed a security breach and revealed that it discovered unauthorized access to its systems. At the time the company did not provide details about the attack.
Immediately upon becoming aware of unauthorised activity on our networks, we have taken the necessary steps to investigate and respond to the incident, including shutting down affected systems. We are working with leading cyber security experts to support our investigations and identify the extent of the issue, including the impact on production and contract fulfilment. reads a statement issued by the company.
In an update provided by Vesuvius, the company explained that the cyber incident will cost it 3.5 million (approximately $4.6 million at the current exchange).
Foundry has delivered particularly well with resilient pricing in the period driving better than expected margin. The Steel division was also ahead of expectations, benefitting from resilient pricing as well as slightly better than anticipated volumes. reads a new statement published by the company. This good performance has been achieved despite the impact of the cyber incident that occurred earlier in the year, which we expect to have a cost impact of c. 3.5m.
Progress in inventory management has been slowed down by the cyber incident but is expected to resume in the coming months. We remain focused and are confident in continuing to make improvements throughout the year.
Please nominate Security Affairs as your favorite blog.
...
03:02
Frans de Jonge tells us about KOReader in this AGPLv3 interview FSF blogs
This is the latest installment of our Licensing and Compliance Lab's series on free software developers who choose GNU licenses for their works.
03:00
VKD3D-Proton 2.9 Released With Performance Improvements Phoronix
Hans-Kristian Arntzen of Valve's Linux team has just released VKD3D-Proton 2.9 as the latest major update to this Direct3D 12 on Vulkan API implementation that is used by Steam Play (Proton) for running modern Windows games on Linux...
02:39
10 Years After Snowden: Some Things Are Better, Some Were Still Fighting For Deeplinks
On May 20, 2013, a young government contractor with an EFF
sticker on his laptop disembarked a plane in Hong Kong carrying
with him evidence confirming, among other things, that the United
States government had been conducting mass surveillance on a global
scale. What came next were weeks of disclosuresand official
declassificationsas Edward Snowden worked with some of the worlds
top news organizations to reveal critical facts about the National
Security Agency vacuuming up peoples online communications,
internet activity, and phone records, both inside and outside the
U.S..
Groups like EFF had been fighting since long before 2013
to reveal and stop the dangerous mass surveillance conducted
within the heart of the secretive national security apparatus. But
after that summer, Snowdens revelations acted like a flood light,
allowing everyone to better see and understand what happens inside
the black box of government surveillance of millions of innocent
people in the US. and around the world. The tremendous amount
of evidence slowed, if not stopped, the disingenuous denials that
the government had made both publicly and privately in response to
our allegations. The actual documentary evidence also helped us to
better pinpoint our demands, our questions, and our legal
tools.
Theres still much work to be done to rein in our overzealous national security state, break political gridlock, and end the extreme secrecy that insulates some of the governments most invasive tactics.
Now, ten years after those pivotal revelations, what has changed? Some things are undoubtedly betterunder the intense scrutiny of public attention, some of the National Security Agencys most egregiously illegal programs and authorities have shuttered or been forced to end. The Intelligence Community has started affirmatively releasing at least some important information, although EFF and others have still had to fight some long Freedom of Information Act (FOIA) battles. Outside of government, companies and organizations have worked to close many of the security holes that the NSA abused, most prominently by encrypting the web.
But its not enoughnot even close. Theres still much work to be done to rein in our overzealous national security state, break political gridlock, and end the extreme secrecy that insulates some of the governments most invasive tactics. One of the most important of those is the upcoming fight to ...
02:30
Accenture invests in SpiderOak to elevate satellite communications security in space Help Net Security
Accenture has made a strategic investment, through Accenture Ventures, in SpiderOak. SpiderOaks OrbitSecure product suite brings zero trust security to zero gravity environments. OrbitSecure leverages a combination of no-knowledge encryption and distributed-ledger technology in order to meet the demands of cybersecurity in space. The product suite includes a fully decentralized key management system that helps enable full availability and continued operations in space, even within disconnected or highly contested networks. This increases resiliency for multi-vendor, More
The post Accenture invests in SpiderOak to elevate satellite communications security in space appeared first on Help Net Security.
02:00
Zerto 10 for Microsoft Azure delivers disaster recovery (DR) and mobility at scale Help Net Security
Zerto has announced the launch of Zerto 10 for Microsoft Azure, delivering enhanced disaster recovery (DR) and mobility for complete infrastructure flexibility. Zerto 10 delivers a new replication architecture for scale-out efficiency and native protection of Azure Virtual Machines (VMs). Zerto 10 provides new support for multi-disk consistency for VMs in Microsoft Azure to protect an organizations data not just to and from Azure but also across Azure regions within the cloud. Zerto coordinates More
The post Zerto 10 for Microsoft Azure delivers disaster recovery (DR) and mobility at scale appeared first on Help Net Security.
01:40
States Should Not Skirt Federal Rules on Fiber Infrastructure Deeplinks
Across the country, states are designing broadband plans to begin spending billions of federal dollars made available by the Infrastructure Investment and Jobs Act (IIJA) and past COVID-19 rescue dollar investment programs. The Biden administration has consistently made clear that states are to build future-proof infrastructure to deliver broadband that will be useful for communities for decades. This is arguably one of the best changes in federal policy for broadband subsidies ever. Past federal subsidy efforts in broadband failed to take long-term needs into account, which is how billions from past investments have gone to waste. But, despite this clear federal guidance, debates continue to rage in state legislatures and implementing bodies as entities unable to deliver future-proof access hope to get a cut of federal subsidy dollars.
Federal Rescue Money and BEAD Grant Rules on Fiber
Both the Treasury Department's Capital Projects Fund and the
National Telecommunications Information Administration's (NTIA)
Broadband Equity Affordability and Deployment grant programs
provide clear guidance to prioritize fiber-based infrastructure.
Under the
Treasury rules that govern rescue dollars, the presumptively
eligible projects for broadband infrastructure must reliably
deliver 100/100 mbps connectivity. While there is an exception for
lower speeds, there is a general expectation that these projects
can scale higher for future needs. Specifically, recipients are
encouraged to prioritize investments in fiber-optic infrastructure
where feasible to emphasize that projects should consider fiber
first.
The NTIA program also
directs states to follow the statutory text of the IIJA.
Under that law, projects must be scalable, able to
facilitate 5G and beyond, able to evolve with community needs, and
build fiber-based infrastructure with limited exceptions for
extremely high-cost areas. Arguably, options such as fixed wireless
and satellite broadband could be considered for extremely high-cost
areaswhich unfortunately are not future-proofed like fiber. But
states relying on federal dollars alone will be forced to deliver
less than states that are matching the federal investment with
their own local dollars.
Wireless Lobby Push on States to Deprioritize Fiber Risks Federal Dollars
Much of the policy-making in telecom subsidies has emphasized technology neutrality, which is code for saying every broadband provider should...
01:30
NTT and Cisco help customers transition to IoT-as-a-Service model Help Net Security
NTT and Cisco have announced a collaboration to develop and deploy joint solutions that empower organizations to improve operational efficiencies and advance sustainability goals. Leveraging NTTs Edge as a Service portfolio and Ciscos IoT capabilities, solutions developed by the two companies will offer real-time data insights, enhanced security, improved decision-making, and reduced operational costs through predictive maintenance, asset tracking, and supply chain management capabilities. The companies will deliver solutions that combine NTTs Managed Services expertise, More
The post NTT and Cisco help customers transition to IoT-as-a-Service model appeared first on Help Net Security.
01:13
What is Bio-Oil, and Why Does Big Tech Think It Can Fight Climate Change? SoylentNews
Some of the biggest names in tech have inked a deal to turn corn stalks and tree trimmings into a barbecue sauce ingredient and then pump the stuff underground to try to fight climate change.
That sounds wild, so let's break it down from the start. Alphabet, Meta, Stripe, Shopify, and McKinsey Sustainability launched a new climate initiative called Frontier about a year ago. The goal is to boost new technologies capable of sucking carbon dioxide out of the atmosphere by convincing other companies to buy into them.
Today, a San Francisco-based climate tech startup called Charm Industrial announced that Frontier's founding members and a smattering of other companies have agreed to pay Charm a total of $53 million to capture and store 112,000 tons of carbon dioxide between 2024 and 2030.
Some of the biggest names in tech have inked a deal to turn corn stalks and tree trimmings into a barbecue sauce ingredient
Charm has an unconventional way of getting that done. First, it collects agricultural and forestry waste i.e., discarded corn stalks or branches leftover from logging. Wherever it finds that stuff, it sends its fleet of flatbed semi trucks hauling reactors that heat up the waste to 500 degrees Celsius without burning it. That turns the waste into bio-oil, a tarry-looking carbon-rich liquid.
The watery part of the bio-oil is essentially the same thing as liquid smoke, an ingredient used to give barbecue sauce and other foods a smokey flavor, according to Charm CEO and co-founder Peter Reinhardt.
Bio-oil also holds the carbon dioxide that the plants or trees its made from absorbed for photosynthesis. Had those corn stalks or tree branches been disposed of by burning or simply left to rot, that CO2 would have escaped again heating the planet along with all the other emissions that come from burning fossil fuels.
Read more of this story at SoylentNews.
01:08
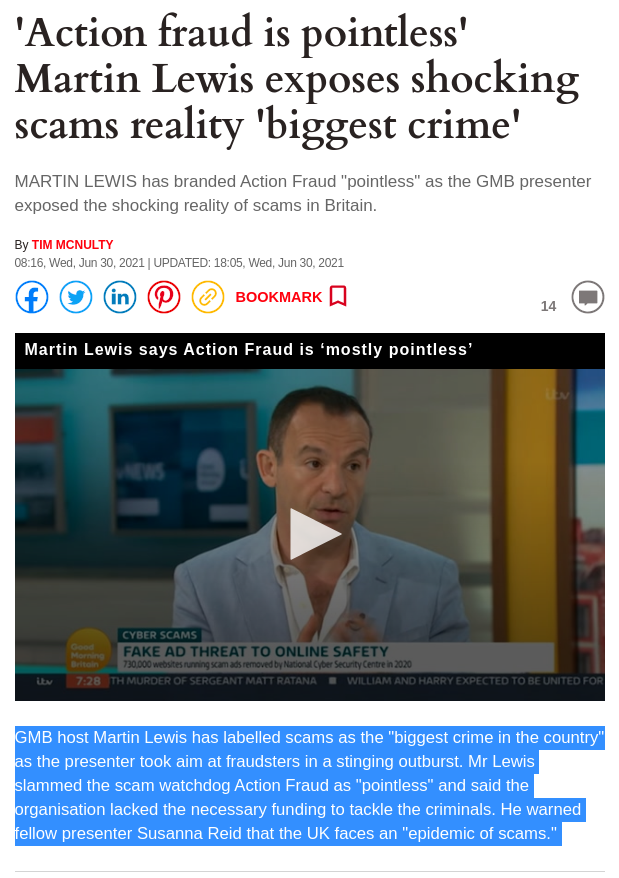
Good Morning Britain Host Martin Lewis: Action Fraud is Pointless Techrights
This was published less than 2 years ago: (check out the video too)
Summary: I may not be the first person to independently reach such conclusions; the pension crime (fraud) of Sirius Open Source was reported to Action Fraud 28 days ago (it has victims other than myself as well) and theres no response; even efforts to phone them up turned up to be useless so far
01:00
New Relic integrates infrastructure and application monitoring for faster troubleshooting Help Net Security
New Relic has unveiled a new, integrated experience for its infrastructure monitoring and application performance monitoring (APM) capabilities that correlates the health and performance of applications and hosts in real-time. Engineers, DevOps, and ITOps can now diagnose application and infrastructure performance issues, and avoid context switching or missing critical insights due to siloed infrastructure monitoring tools. Now organizations can afford to analyze all of their telemetry data without sampling, ensuring they have the necessary data More
The post New Relic integrates infrastructure and application monitoring for faster troubleshooting appeared first on Help Net Security.
00:51
Action Fraud: Anybody Home or Just Bots? schestowitz.com
Video download
link | md5sum
4cd628f27bc3a0865875d46519d80701
Nobody to Speak With Today
Creative Commons Attribution-No Derivative Works 4.0
Summary: 28 days ago I reported fraud committed by Sirius Open Source against many members of its own staff for more than half a decade; An assessment will be made as to whether there are viable lines of enquiry that would enable a law enforcement body, such as the police service, to investigate. The NFIB aim to provide you with an update on your report within 28 days, they said 28 days ago, but no word was received from them. Today I phoned them up for an update and the video above documents the process. The short story is, no human answered the call and I ended up with a silent wait, maybe due to a technical error.
I am sorry to hear you have been a victim of crime, said a message to me 28 days ago. Thank you for taking the time to report to Action Fraud. Your report has been sent to the National Fraud Intelligence Bureau (NFIB) for review.
Did they get back to me? No, Not yet.
Maybe the coronation spectacle kept them very busy.
As the video hopefully makes evident, their answering system isnt working. I didnt even get to speak to a person. I was just muted completely for several minutes (or rather, the other side was perpetually muted, without any indication of any progress whatsoever).
This is especially frustrating as people have been the victims of a crime and theres nobody to even speak to. Manchesters police told me I must contact Action Fraud, not them. After 28 days there has been no action, just inaction, and there seems to be nobody to speak to for updates. Thats a lot worse than I expected when initiating the call.
Maybe its intentional? To keep down the plebs and chavs? Its probably not intentional, but I will try again on Monday to...
00:50
CodeWeavers Now Controlled By An Employee Ownership Trust Phoronix
CodeWeavers, the company known for its CrossOver software for running Windows games/apps on Linux / macOS / Chrome OS and in turn being the main corporate backer to the Wine project, is now transitioned to being an employee ownership trust. This comes with Jeremy White deciding to leave the company after 27 years...
00:48
Action Fraud: Nobody to Speak to Techrights
Video download
link | md5sum
4cd628f27bc3a0865875d46519d80701
Nobody to Speak With Today
Creative Commons Attribution-No Derivative Works 4.0
Summary: 28 days ago I reported fraud committed by Sirius Open Source against many members of its own staff for more than half a decade; An assessment will be made as to whether there are viable lines of enquiry that would enable a law enforcement body, such as the police service, to investigate. The NFIB aim to provide you with an update on your report within 28 days, they said 28 days ago, but no word was received from them. Today I phoned them up for an update and the video above documents the process. The short story is, no human answered the call and I ended up with a silent wait, maybe due to a technical error.
I am sorry to hear you have been a victim of crime, said a message to me 28 days ago. Thank you for taking the time to report to Action Fraud. Your report has been sent to the National Fraud Intelligence Bureau (NFIB) for review.
I didnt even get to speak to a person.Did they get back to me? No, Not yet.
Maybe the coronation spectacle kept them very busy.
For some background and context, consider reading the follow parts in turn:
00:43
Bernd Schubert led a session at the 2023 Linux Storage, Filesystem, Memory-Management and BPF Summit on the intersection of FUSE and io_uring. He works for DDN Storage, which is using FUSE for two network-storage products; he has found FUSE to be a bottleneck for those filesystems. That could perhaps be improved by using io_uring, which is something he has been working on and wanted to discuss.
00:34
Links 19/05/2023: Newer Laptops With GNU/Linux Preinstalled Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Digital Restrictions (DRM)
- Monopolies
- Gemini* and Gopher
00:30
Strata Identity unifies Maverics ID Orchestration functions across environments Help Net Security
The post Strata Identity unifies Maverics ID Orchestration functions across environments appeared first on Help Net Security.
00:25
NVIDIA R530 vs. AMD Linux 6.3 + Mesa 23.2-dev Gaming Performance Phoronix
Due to the constantly evolving state of the open-source Linux graphics drivers in particular, here is a fresh look at an assortment of AMD Radeon GPUs making use of the Mesa 23.2 development code for the newest RadeonSI and RADV drivers paired with the recently released Linux 6.3 kernel. These open-source Radeon Linux gaming benchmark results are going up against various NVIDIA GeForce RTX 30/40 series graphics cards using the NVIDIA 530.41.09 release as its latest Linux driver.
00:02
[$] Phyr: a potential scatterlist replacement LWN.net
The "scatterlist" is a core-kernel data structure used to describe DMA I/O operations from the point of view of both the CPU and the peripheral device. Over the years, the shortcomings of scatterlists have become more apparent, but there has not been a viable replacement on the horizon. During a memory-management session at the 2023 Linux Storage, Filesystem, Memory-Management and BPF Summit, Jason Gunthorpe described a possible alternative, known alternatively as "phyr", "physr", or "rlist", that might improve on scatterlists for at least some use cases.
00:01
[$] Memory passthrough for virtual machines LWN.net
Memory management is tricky enough on it own, but virtualization adds another twist: now there are two kernels (host and guest) managing the same memory. This duplicated effort can be wasteful if not implemented carefully, so it is not surprising that a lot of effort, from both hardware and software developers, has gone into this problem. As Pasha Tatashin pointed out during a memory-management-track session at the 2023 Linux Storage, Filesystem, Memory-Management and BPF Summit, though, there are still ways in which these systems run less efficiently than they could. He has put some effort into improving that situation.
00:00
Juniper Networks and ServiceNow partner to deliver E2E automation for MSPs and enterprises Help Net Security
Juniper Networks and ServiceNow have formed a partnership to deliver end-to-end automation for managed service providers and enterprises. With this newly formed collaboration leveraging Juniper Mist Cloud and ServiceNow Telecom Service Management and Order Management for Telecom, joint customers can eliminate multi-layer, multivendor solutions, thereby boosting network deployment and operational efficiencies while reducing costs. Juniper Networks joins the ServiceNow Technology Partner Program enabling both companies to expand their global reach while delivering better experiences for More
The post Juniper Networks and ServiceNow partner to deliver E2E automation for MSPs and enterprises appeared first on Help Net Security.
00:00
This Week in Security: .zip Domains, Zip scanning Hackaday

The world may not be ready, but the .zip Top
Level Domain (TLD) is here. Its a part of the generic TLD
category, which was expanded to allow applications for custom TLDs.
Google has led the charge, applying for 101 such new TLDs, with
.zip being one of the interesting ones. Public registration for
.zip domains has been open for a couple weeks, and some interesting
domains have been registered, like update.zip,
installer.zip, and officeupdate.zip.
The obvious question to ask is whether this new TLD can be abused for scamming and
phishing purposes. And the answer is yes, sure it can. One of the trickiest ways is
to use the AT symbol @ in a URL, which denotes user
info at the beginning of the URL. It usually is used to include a
username and password, like http://username:password@192.168.1.1/. That is
pretty obvious, but what about https://google.com@bing.com? Still looks weird.
The catch that really prevents this technique being abused is that
slashes are disallowed in user data, so a abusive URL like
...
Friday, 19 May
23:57
Security updates for Friday LWN.net
Security updates have been issued by Fedora (cups-filters, kitty, mingw-LibRaw, nispor, rust-ybaas, and rust-yubibomb), Mageia (kernel-linus), Red Hat (jenkins and jenkins-2-plugins), SUSE (openvswitch and ucode-intel), and Ubuntu (linux-azure, linux-azure-4.15, linux-gcp, linux-gcp-5.15, linux-gke, linux-gke-5.15, linux-gkeop, linux-oracle-5.15, linux-ibm, linux-oracle, and linux-oem-6.0).
23:30
Check Point CloudGuard secures Microsoft Azure Virtual WAN Help Net Security
Check Point announces its Next-Generation Cloud Firewall natively integrated with Microsoft Azure Virtual WAN to provide customers with improved security. The integration provides advanced threat prevention and multi-layered network security across public, private and hybrid-clouds, enabling businesses to confidently migrate to Azure with maximum operational efficiency. Microsoft Azure Virtual WAN is a network-as-a-service that provides customers with a range of benefits simplifying networking, security and routing functionalities to drive scalability, cost savings and improved performance. More
The post Check Point CloudGuard secures Microsoft Azure Virtual WAN appeared first on Help Net Security.
23:27
NPM packages found containing the TurkoRat infostealer Security Affairs
Experts discovered two malicious packages in the npm package repository, both were laced with an open-source info-stealer called TurkoRat.
ReversingLabs discovered two malicious packages, respectively named nodejs-encrypt-agent and nodejs-cookie-proxy-agent, in the npm package repository containing an open-source info-stealer called TurkoRat.
TurkoRat is an information-stealing malware that can obtain a broad range of data from the infected machine, including account login credentials, cryptocurrency wallets, and website cookies. The malware also supports anti-sandbox and analysis functionalities to avoid detection and prevent being analyzed.
TurkoRat is just one of many open source malware families that are offered for testing purposes, but can readily be downloaded and modified for malicious use, as well. reads the analysis published by ReversingLabs. TurkoRats author clearly anticipates this, as he provides instructions on how to use malicious code, while stating that he is not responsible for any damages this software may cause and that it was only made for personal education.'
The two packages were collectively downloaded approximately 1,200 times since their upload into the repository two months before they were discovered.
The nodejs-encrypt-agent was discovered due to scanning the repository.

The researchers noticed that the nodejs-encrypt-agent contained the malware inside. The package name used by the attackers on the npm page appeared as legitimate, but it differed from the name listed in the readme.md file (agent-base). The choice of the name agent-base in the readme.md was not accidental, because agent-base i...
23:25
Take action now to avoid BianLian ransomware attacks, US Government warns organisations Graham Cluley
A joint alert has been issued by US government agencies, advising organisations of the steps they should take to mitigate the threat posed by BianLian ransomware attacks.
23:00
Zerto Cyber Resilience Vault allows users to monitor for encryption-based anomalies Help Net Security
Zerto launched a new real-time encryption detection mechanism and air-gapped recovery vault for enhanced hybrid cloud protection and security against cyber threats. These new features are part of Zerto 10, which includes advanced detection mechanisms that allow users to monitor for encryption-based anomalies, enabling organizations to pinpoint and mitigate the early stages of a potential ransomware attack. The Cyber Resilience Vault provides the ultimate layer of protection allowing for clean copy recovery from an air-gapped More
The post Zerto Cyber Resilience Vault allows users to monitor for encryption-based anomalies appeared first on Help Net Security.
22:45
Mesa "Terakan" Driver Aims To Provide Vulkan Support For Old Radeon HD 6000 Series Phoronix
There's a new open-source Vulkan driver in development by an independent developer that is working on providing support for aging Radeon HD 6000 series "Northern Islands" graphics processors...
22:29
Teen Charged in DraftKings Data Breach HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
If convicted, the alleged culprit Joseph Garrison could face a maximum sentence of 57 years.
This is a post from HackRead.com Read the original post: Teen Charged in DraftKings Data Breach
22:28
Privacy Sandbox Initiative: Google to Phase Out Third-Party Cookies Starting 2024 The Hacker News
Google has announced plans to officially flip the switch on its twice-delayed Privacy Sandbox initiatives as it slowly works its way to deprecate support for third-party cookies in Chrome browser. To that end, the search and advertising giant said it intends to phase out third-party cookies for 1% of Chrome users globally in the first quarter of 2024. "This will support developers in conducting
22:23
The Group Decode ROM: The 8086 Processor's First Step of Instruction Decoding SoylentNews
http://www.righto.com/2023/05/8086-processor-group-decode-rom.html
A key component of any processor is instruction decoding: analyzing a numeric opcode and figuring out what actions need to be taken. The Intel 8086 processor (1978) has a complex instruction set, making instruction decoding a challenge. The first step in decoding an 8086 instruction is something called the Group Decode ROM, which categorizes instructions into about 35 types that control how the instruction is decoded and executed. For instance, the Group Decode ROM determines if an instruction is executed in hardware or in microcode. It also indicates how the instruction is structured: if the instruction has a bit specifying a byte or word operation, if the instruction has a byte that specifies the addressing mode, and so forth.
Read more of this story at SoylentNews.
21:44
Re: IPv6 and Route of Death Open Source Security
Posted by Dominique Martinet on May 19
Solar Designer wrote on Wed, May 17, 2023 at 07:13:51PM +0200:A couple of days late, but since I wanted to read it myself, here's the
text content (as rendered by edbrowse, which looks good enough to me,
look for 'h3' to jump to next sections e.g. 'h3 The Bug'):
--------------
h3 Introduction
Sometimes I feel like exploring random areas of code.
It's a pretty good way to find a new bug pattern.
Early last year I...
21:13
Apple fixes WebKit 0-days under attack (CVE-2023-28204, CVE-2023-32373, CVE-2023-32409) Help Net Security
Apple has released security updates for iOS and iPadOS, macOS, tvOS and watchOS, delivering fixes for many vulnerabilities but, most importantly, for CVE-2023-32409, a WebKit 0-day that may have been actively exploited. The notes accompanying the updates also revealed that Apples first Rapid Security Response update, which was pushed out earlier this month, contained fixes for two WebKit 0-days (CVE-2023-28204 and CVE-2023-32373). About the vulnerabilities CVE-2023-28204 and CVE-2023-32373 can be triggered by WebKit the More
The post Apple fixes WebKit 0-days under attack (CVE-2023-28204, CVE-2023-32373, CVE-2023-32409) appeared first on Help Net Security.
21:09
Lemon Group gang pre-infected 9 million Android devices for fraudulent activities Security Affairs
The Lemon Group cybercrime ring has reportedly pre-installed malware known as Guerilla on almost 9 million Android devices.
A cybercrime group tracked has Lemon Group has reportedly pre-installed malware known as Guerilla on almost 9 million Android devices. Infected devices were used for multiple malicious activities, including traffic redirections through mobile proxies, info-stealing, click fraud, and social media and online messaging accounts and monetization via advertisements.
The network of compromised devices was discovered by Trend Micro which shared details of its investigation at the Black Hat Asia 2023 conference in May.
The threat actors infected at least 8.9 million compromised Android devices, most of them are budget phones. The highest number of infected devices in the U.S., Mexico, Indonesia, Thailand, Russia, South Africa, India, Angola, the Philippines, and Argentina.
The Triada Trojan was spotted for the first time in 2016 by researchers at Kaspersky Lab that considered it the most advanced mobile threat seen to the date of the discovery.
Triada was designed with the specific intent to implement financial frauds, typically hijacking financial SMS transactions. The most interesting characteristic of the Triada Trojan apart is its modular architecture, which gives it theoretically a wide range of abilities.
The Triada Trojan makes use of the Zygote parent pr...
21:04
Dr. Active Directory vs. Mr. Exposed Attack Surface: Who'll Win This Fight? The Hacker News
Active Directory (AD) is among the oldest pieces of software still used in the production environment and can be found in most organizations today. This is despite the fact that its historical security gaps have never been amended. For example, because of its inability to apply any security measures beyond checking for a password and username match, AD (as well the resources it manages) is
21:00
Building a Giant Vacuum Tube Smart Lamp Hackaday

Vacuum tubes are pretty, which is why theyre often showcased externally on exquisitely-expensive home Hi-Fi hardware. But if you just want to gaze at their beauty without making any noise, why not build this vacuum tube lamp from [Noel Trjk] instead?
[Noel] got into some creative reuse with this build, with the main body consisting of a bell jar and wooden bowls. The internal structure is then created from jar lids, wire, metal sheeting, steel rods, and galvanized wire mesh. Simple modelling techniques are used to assemble the internal parts of the valve, including the grid and the electrodes and so on. As for light, [Noel] employed a ZigBee LED driver that he could control over his smart home setup via a Philips Hue bridge.
The final result looks like an extra-large tube. Anyone who knows what it is will spot that its not a real one, but theyre also exactly the audience that will appreciate it for what it is. Everyone else will probably just think youve taken an interest in strange art-deco replica lighthouses. Its not the first time weve seen replica valves around these parts, though, and were sure it...
20:40
Developer Alert: NPM Packages for Node.js Hiding Dangerous TurkoRat Malware The Hacker News
Two malicious packages discovered in the npm package repository have been found to conceal an open source information stealer malware called TurkoRat. The packages named nodejs-encrypt-agent and nodejs-cookie-proxy-agent were collectively downloaded approximately 1,200 times and were available for more than two months before they were identified and taken down. ReversingLabs, which broke
20:19
Fedora To Further Evaluate vm.max_map_count Tuning For Better Linux Gaming Experience Phoronix
There's been a Fedora 39 proposal under evaluation for boosting the kernel's vm.max_map_count to help with some Windows games on Steam Play. Though concerns were raised that bumping this kernel tunable too high may not be wise. As such, further testing is to happen for tuning Fedora's stock vm.max_map_count value...
20:02
DarkBERT could help automate dark web mining for cyber threat intelligence Help Net Security
Researchers have developed DarkBERT, a language model pretrained on dark web data, to help cybersecurity pros extract cyber threat intelligence (CTI) from the Internets virtual underbelly. DarkBERT pretraining process and evaluated use case scenarios (Source: KAIST/S2W) DarkBERT: A language model for the dark web For quite a while now, researchers and cybersecurity experts have been leveraging natural language processing (NLP) to better understand and deal with the threat landscape. NLP tools have become an integral More
The post DarkBERT could help automate dark web mining for cyber threat intelligence appeared first on Help Net Security.
19:57
Big Patch Series Prepares The Linux Audio Drivers For MIDI 2.0 Phoronix
Nearly forty years after the MIDI digital music protocol was first introduced, in 2020 the MIDI 2.0 protocol was announced as a major overhaul for this widely used standard by musical devices. A big patch series sent out today prepares the Linux kernel sound drivers for MIDI 2.0...
19:45
Remembering Jim Early (1943-2023) Centauri Dreams Imagining and Planning Interstellar Exploration

I was saddened to learn of the recent death of James Early, author of a key paper on interstellar sail missions and a frequent attendee at IRG events (or TVIW, as the organization was known when I first met him). Jim passed away on April 28 in Saint George, UT at the age of 80, a well-liked figure in the interstellar community and a fine scientist. I wish I had known him better. I ran into him for the first time in a slightly awkward way, which Jim, ever the gentleman, quickly made light of.
What happened was this. In 2012 I was researching damage that an interstellar sail mission might experience in the boost phase of its journey. Somewhere I had seen what I recall as a color image in a magazine (OMNI?) showing a battered, torn sail docked in what looked to be a repair facility at the end of an interstellar crossing. It raised the obvious question: If we did get a sail up to, say, 5% of the speed of light, wouldnt even the tiniest particles along the way create significant damage to the structure? The image was telling and to this day I havent found its source.
I think of the image as lightsail on arrival, and if this triggers a memory with anyone, please let me know. Anyway, although our paths crossed at the first 100 Year Starship symposium in Orlando in 2011, I didnt know Jims work and didnt realize he had analyzed the sail damage question extensively. When I wrote about the matter on Centauri Dreams a year later, he popped up in the comments:
I presented a very low mass solution to the dust problem at the 100 Year Starship Symposium in a talk titled Dust Grain Damage to Interstellar Vehicles and Lightsails. An earlier published paper contains most of the important physics: Early, J.T., and London, R.A., Dust Grain Damage to Interstellar Laser-Pushed Lightsail, Journal of Spacecraft and Rockets, July-Aug. 2000, Vol. 37, No. 4, pp. 526-531.
I was caught by surprise by the reference. How did I miss it? Researching my 2005 Centauri Dreams book, I had been through the literature backwar...
19:41
Intel's Vulkan Linux Driver Adds H.265 Video Decoding Support Phoronix
Intel's open-source Mesa Vulkan Video driver "ANV" has added support for H.265 (HEVC) video decoding...
19:39
Reviving Office Chatter SoylentNews
Researchers Design Tool to Enhance Workplace Socialization in Remote, Hybrid Arrangements:
About one-third of our lives are spent at work, and the relationships we build there can have personal and professional benefits. But a majority of workers indicate difficulty connecting with co-workers socially, especially in the new landscape of remote and hybrid work arrangements.
To ease the friction caused by reduced in-person interaction, a team of researchers from Carnegie Mellon University's Human-Computer Interaction Institute created a Slack application that helps to initiate casual conversations and create affinity groups in an online workspace.
"We were freshly out of the pandemic, and we realized that everyone around us was complaining about how it's hard to build genuine connections," said Shreya Bali, the project's principal investigator who earned her master's degree from CMU's School of Computer Science in 2022. "Online modes of communication do provide us with the technical tools to make connections, but there is still a lot of hesitation to actually initiate such conversations when you are not in the same room as someone."
The team's new application, called Nooks, offers users a low-risk way to start new conversations in three phases: creation, incubation and activation. It starts with someone anonymously submitting a topic of interest. Then, the topic is incubated while the system presents it to other Slack users, allowing them to indicate if they are interested in the same topic. Once the incubation period is over, a private channel or "nook" is activated for this newly identified affinity group.
Read more of this story at SoylentNews.
18:26
Anti-Piracy Program Accused of Violating Citizens Fundamental Rights TorrentFreak
 When the French government formed a new anti-piracy
agency called Hadopi, the mission was to significantly disrupt
BitTorrent and similar peer-to-peer file-sharing networks.
When the French government formed a new anti-piracy
agency called Hadopi, the mission was to significantly disrupt
BitTorrent and similar peer-to-peer file-sharing networks.
Hadopi was a pioneer of the so-called graduated response scheme which consists of monitoring a file-sharers internet activities and following up with a warning notice to deter their behavior. Any future incidents attract escalating responses including fines and internet disconnections. Between 2010 and 2020, Hadopi issued 12.7 million warning notices at a cost to French taxpayers of 82 million euros.
The programs effect on overall piracy rates remains up for debate but according to French internet rights groups, Hadopi doesnt just take citizens money. When it monitors citizens internet activities, retains huge amounts of data, and then links identities to IP addresses to prevent behavior that isnt a serious crime, Hadopi violates fundamental rights.
Protecting Rights
Despite its authorization under the new law, the official launch of the Hadopi agency in 2009 met with significant opposition. File-sharers had issues with the program for obvious reasons but for digital rights group La Quadrature du Net, massive internet surveillance to protect copying rights had arrived at the expense of citizens fundamental right to privacy.
La Quadratures opposition to the Hadopi anti-piracy program focuses on the law crafted to support it. One of the implementing decrees authorizes the creation of files containing internet users IP addresses plus personal identification data obtained from their internet service providers.
According to the digital rights groups interpretation of EU law, that is unlawful.
Legal Challenge in France
With support from the Federation of Associative Internet Service Providers, French Data Network, and Franciliens.net, in 2019 La Quadrature filed an appeal before the Council of State (Conseil dtat), requesting a repeal of the decree that authorizes the processing of personal information.
The Council of State referred the matter to the Constitutional Council and its subsequent decision gave La Quadrature the impression that Hadopis position was untenable. For their part, Hadopi and the government reached the opposite conclusion.
Legal...
18:00
North Korean Karaoke Machine Teardown Hackaday

Karaoke is a very popular pastime in Seoul there are venues where you can sing on a stage, sing in rooms with your friends, and even sing solo in coin-operated karaoke booths on the bullet train. Apparently it is also popular in North Korea as well [Martyn Williams] of the North Korea Tech blog reported on an interesting teardown by web hacker [Will Scott]. It is the Tianchi v700 machine, a Chinese product tailored for North Korean users, obtained online back in 2020.
Unlike the karaoke machines encountered by this author in South Korea, the v700 form factor is a 19.5-inch Android tablet with touch-screen and all the necessary interfaces youd expect: external video, speakers, and microphone, as well as WiFi and Ethernet for content upgrade and online payment systems. Not surprisingly, the connectivity aspects of the machine are not used in the North Korean model, but with a large catalog of pre-loaded music, its perfectly usable as a stand-alone device.
[Will] dug into the innards of the machine and discovered it was powered by an Allwinner ARM processor (seemingly the H6 V200, a quad-core ARM Cortex-A53). He also found i...
17:15
IRC Proceedings: Thursday, May 18, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-180523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-180523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-180523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-180523.gmi
Over HTTP:
|
... |
17:00
SpaceX Raptor 3 Engine is Test Fired and Has 17% More Thrust Terra Forming Terra
Do look at that profile. all the hardware disappeared. this as much as tells you just why it is getting cheaper to build. The nozzle itself is the same and we are notching up with performance which is reasonable. It is the complete disappearance of the tree that stuns.
Tiny Battery Obliterates Breast Cancer Tumors in Mice by Creating Oxygen-free Target to Better Kill Disease Terra Forming Terra


A New Way to Achieve Nuclear Fusion: Helion Terra Forming Terra
This is really good news as it appears that they are getting really good results and that power can be drawn off magnetically. It is also going to be supper fast and i suspect keeping it cool enough will be an issue. however even that may resolve through increasing size.
We are prepping two plasma rings and those can likely be improved upon. then they are fired together elimiating all kinetic energy. Talk about fine tuning. Heat and powerful containment produces fusion reactions and a back wash back which expands the magnetic containment foields allowing power to be drwn off..
This is certainly way better than the Tokamack machine which has to solve similar problems with far more inherant design difficulty.
<iframe width="668" height="376" src="https://www.youtube.com/embed/_bDXXWQxK38" title="A New Way to Achieve Nuclear Fusion: Helion" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" allowfullscreen></iframe>
Tracking whales with existing fiber-optic cables may reduce ship strikes Terra Forming Terra

16:53
Searching for AI Tools? Watch Out for Rogue Sites Distributing RedLine Malware The Hacker News
Malicious Google Search ads for generative AI services like OpenAI ChatGPT and Midjourney are being used to direct users to sketchy websites as part of a BATLOADER campaign designed to deliver RedLine Stealer malware. "Both AI services are extremely popular but lack first-party standalone apps (i.e., users interface with ChatGPT via their web interface while Midjourney uses Discord)," eSentire
Chinese Chip Industry to Focus on Perfecting Mature Nodes SoylentNews
Chinese Chip Industry to Focus on Perfecting Mature Nodes: Report:
Severe constraints on the development of the Chinese chip industry caused by strict export control rules that block People's Republic chipmakers from obtaining advanced wafer fab equipment (WFE) has triggered local specialists to rethink the nation's semiconductor strategy. While it is obvious that China will have to replace tools made abroad to make leading-edge chips in the long term, for now the country's chipmakers will have to focus on perfecting their mature nodes to stay competitive, reports DigiTimes.
Meanwhile, between 2022 and 2026, Jiwei Research estimates there will be 25 new 300-mm fabs in China, with a total capacity of over 1.6 million wafer starts per month. This could significantly increase China's chip production capacity, which will increase China's total 300-mm capacity to 2.76 million WSPM by 2026.
Without access to advanced equipment, all of these fabs will have to focus on 20nm 90nm-class technologies, but it will better be able to rely on domestic suppliers. Consequently, companies within the Chinese semiconductor supply chain, spanning from raw materials, machinery, and electronic design automation (EDA), are reportedly shifting their growth strategies, prioritizing mature processes over advanced ones. For instance, Naura has declared that it will prioritize shipments of tools for trailing processes utilized by Chinese chipmakers.
Furthermore, a provider of photoresist materials has disclosed that the current industry emphasis is on mature processes, in the hope of spurring significant advancements in mature wafer production techniques. As of now, the development of cutting-edge processes is not at the forefront of Tianxia's semiconductor industry's agenda.
Read more of this story at SoylentNews.
16:07
Links 19/05/2023: New Beta of deepin Linux and PipeWire 0.3.71 Techrights
![]()
Contents
-
GNU/Linux
-
Desktop/Laptop
-
Beebom 7 Best Linux Laptops to Buy in 2023 | Beebom
Linux laptops are still considered pretty niche since not a lot of people are interested in using Linux, let alone purchasing a fully-fledged Linux machine. Although, we have seen the trend shifting lately with more people switching to Linux now than ever before. If you are one of those whos been using Linux for quite some time and want to buy a Linux laptop, here are all the options you have in the market right now.
There are not many Linux laptop manufacturers out there, but the ones that are already there are doing an excellent job with the hardware selection. This list contains laptops from the likes of System76, KDE, Star Labs, and others....
-
-
16:00
Gemini Links 19/05/2023: Unclouding and Gemini Missing Good CMSes Techrights
-
Gemini* and Gopher
-
Personal
-
Strange Weather
After 2021/2022s record snow, with our second-hand, decades-old snowblower dying for good shortly after we got back from visiting my partners parents out west, I ponied up and got a new model. And then: this last mild winter. One really big dump of snow (the snowblower made quick work of it), and thennothing. I had to shovel a bit, but not nearly as much as the previous winter. That winter, I tweaked my back, badly, around New Year 2022. This year, Ive so far got off easy.
The mild winter became a long, cold spring. Grey days, no rain, little hint of sun. While my social media feeds showed crocuses and daffodils far south of here, the snow continued its gradually melt, only pulling back for good in mid-April. A couple weeks ago, the weather turned again. The forsythias blossomed, the irises green began to peek out, and the marsh birds returned, hovering around our feeder, picking out seeds.
-
-
Technical
-
Damnations
FreeBSD for Nomads! Sensational. Like being in a future dystopian desert. This is the post Climate War OS for sure. When the rainforests are gone, the corall reefs are dead, the icecaps have melted, the bees have disappeared
No Wi-Fi though. But do we need that? Later on, when the whole fucking world is burning? No. Fuck no. Z shell in sakura is all we need. Vim and Midnight Commander.
An icecold Corona and a shot of your finest Tequila Blanco please and a couple of Oaxacan mushrooms, if you have any?
This night is gonna be THE NIGHT at The Midnight! -
Why I Hate Getting Help Online
What the zark? I dont understand what is not clear. Well, fortunately, I do not have to provide that dude with the additional info he has requested because the previous reply was helpful.
-
Internet/Gemini
-
-
15:24
Forgotten Antibiotic From Decades Ago Could Be a Superbug Killer Lifeboat News: The Blog
An antibiotic developed some 80 years ago before being abandoned and forgotten could again offer exciting new solutions, this time to the emerging threat of drug-resistant superbugs.
Half of the bacteria-killing drugs we use today are variations of compounds that were found nearly a century ago, during this golden age of antibiotics. One called streptothricin was isolated in the 1940s, drawing attention for its potential in treating infections caused by what are known as gram-negative bacteria.
Unlike gram-positive bacteria, these microbes lack a robust cell wall that many antibiotics target. Finding alternatives has been one of the big challenges for the pharmaceutical industry. In 2017, the World Health Organization (WHO) released a list of the most dangerous, drug-resistant pathogens out there. Most were gram-negative bacteria.
15:24
Googles New Medical AI Passes Medical Exam and Outperforms Actual Doctors Lifeboat News: The Blog
Closin in on Doctor jobs.
A medical domain AI developed by Google Researchers broke records on its ability to pass medical exam questions, but more surprisingly generated answers that were consistently rated as better than human doctors. While the study notes several caveats, it marks a significant milestone in how AI could upend a number of professions.
15:23
BuzzFeed Says AI Will Replace the Majority of Static Content Lifeboat News: The Blog
The breadth of BuzzFeed CEO Jonah Perettis AI aspirations just got a lot clearer and if he has it his way, AI use at the viral publisher wont be limited to time-killing quizzes and bottom-tier travel guides.
BuzzFeed has always lived at the intersection of technology and creativity. And recent developments in artificial intelligence represent an opportunity to take this convergence to the next level, Peretti told eager investors at the companys Investor Day last week. We view AI as an exciting new creativity tool, one that humans can harness to open up new avenues for imagination, storytelling and entertainment and explore new premium product offerings that allow us to innovate and collaborate with our clients and partners on a new frontier in media.
Over the next few years, generative AI will replace the majority of static content, and audiences will begin to expect all content to be curated and dynamic with embedded intelligence, he continued. AI will lead to new formats that are more gamified, more personalized, and more interactive.
15:22
Airport Security Is About to Get Way Faster Thanks to New Technology Being Used by TSA Lifeboat News: The Blog
New TSA screening methods will allow passengers through security without showing their boarding passes or by simply taking a picture.
15:00
Go In All The Directions With Omniwheeled ESP32 Bot Hackaday

The ability to change direction without turning is the specialty of omnidirectional wheels, which [maker.moekoe] used to their full potential on a pair of ESP32-controlled robots. Video after the break.
Thanks to the rollers on the wheels, the wheels could be arranged at 120 in relation to each other on the 3-wheeler and 90 4-wheeler. [maker.moekoe] used ChatGPT and a simple python simulation to find and verify the motor control algorithm required for smooth omnidirectional driving.
A single custom PCB incorporates all the electronics, and doubles as the robots chassis, with the geared brushed motors bolted directly to it. An ESP32-S2 runs the show, and can also stream FPV video from the same OV2640 camera used on the popular ESP32-cam modules. The LiPo battery is held by a 3D-printed support plate screws to the bottom of the PCB. The robots can controlled by a simple web-app...
14:30
New infosec products of the week: May 19, 2023 Help Net Security
Heres a look at the most interesting products from the past week, featuring releases from Bitwarden, Cloudflare, ComplyAdvantage, Enzoic, Neurotechnology, Nozomi Networks, and Satori. ComplyAdvantage Fraud Detection identifies and prevents transaction fraud Fraud Detection uses AI and machine learning algorithms to monitor monetary and non-monetary events and look for patterns that indicate possible risks. This includes identity clustering, using behavioral and personal characteristics to identify accounts that are, for example, controlled by a single individual. More
The post New infosec products of the week: May 19, 2023 appeared first on Help Net Security.
14:08
Anthropic's Claude AI Can Now Digest an Entire Book Like the Great Gatsby in Seconds SoylentNews
On Thursday, AI company Anthropic announced it has given its ChatGPT-like Claude AI language model the ability to analyze an entire book's worth of material in under a minute. This new ability comes from expanding Claude's context window to 100,000 tokens, or about 75,000 words.
Like OpenAI's GPT-4, Claude is a large language model (LLM) that works by predicting the next token in a sequence when given a certain input. Tokens are fragments of words used to simplify AI data processing, and a "context window" is similar to short-term memoryhow much human-provided input data an LLM can process at once.
[...]
While it may not sound impressive to pick out changes in a text (Microsoft Word can do that, but only if it has two documents to compare), consider that after feeding Claude the text of The Great Gatsby, the AI model can then interactively answer questions about it or analyze its meaning. 100,000 tokens is a big upgrade for LLMs. By comparison, OpenAI's GPT-4 LLM boasts context window lengths of 4,096 tokens (about 3,000 words) when used as part of ChatGPT and 8,192 or 32,768 tokens via the GPT-4 API (which is currently only available via waitlist).
[...]
Notably, Anthropic received a $300 million investment from Google in late 2022, with Google acquiring a 10 percent stake in the firm.Anthropic says that 100K context windows are available now for users of the Claude API, which is currently restricted by a waitlist.
Read more of this story at SoylentNews.
14:00
Exploring the tactics of phishing and scam websites in 2023 Help Net Security
Phishing scams pose an escalating danger as cybercriminals employ increasingly sophisticated techniques, rendering their detection and prevention more challenging. In this Help Net Security video, Abhilash Garimella, Head of Research at Bolster, talks about the evolution of phishing and scam websites in 2023.
The post Exploring the tactics of phishing and scam websites in 2023 appeared first on Help Net Security.
13:43
WebKit Under Attack: Apple Issues Emergency Patches for 3 New Zero-Day Vulnerabilities The Hacker News
Apple on Thursday rolled out security updates to iOS, iPadOS, macOS, tvOS, watchOS, and the Safari web browser to address dozens of flaws, including three new zero-days that it said are being actively exploited in the wild. The three security shortcomings are listed below - CVE-2023-32409 - A WebKit flaw that could be exploited by a malicious actor to break out of the Web Content sandbox. It
13:30
Inadequate tools leave AppSec fighting an uphill battle for cloud security Help Net Security
AppSec teams are stuck in a catch-up cycle, unable to keep up with the increasingly rapid, agile dev pace, and playing security defense via an endless and unproductive vulnerability chase, according to Backslash Security. Costly defensive tax Notably, 58% of respondents report spending over 50% of their time chasing vulnerabilities, with a shocking 89% spending at least 25% of their time in this defensive mode. Far and wide, enterprises are victims of this costly defensive More
The post Inadequate tools leave AppSec fighting an uphill battle for cloud security appeared first on Help Net Security.
13:00
Europe: The DDoS battlefield Help Net Security
DDoS attacks appear to reflect major geo-political challenges and social tensions and have become an increasingly significant part in the hybrid warfare arsenal, according to Arelion. As the Ukrainian authorities sought a safe harbour for digital state registries and databases, Arelion saw the distribution of attacks move away from active conflict areas into global cloud centres both as a result of damage to local network infrastructure, but also as local databases and applications were More
The post Europe: The DDoS battlefield appeared first on Help Net Security.
12:00
An Entire RISC-V Operating System in 2000 Lines Hackaday

While Microsoft and Apple dont release the source code for their operating systems, a good estimate is that it takes around 50 million lines of code to run these software behemoths. The Linux kernel alone holds around 30 million lines, with systemd containing over one million lines on its own, which doesnt include estimates for the desktop environment or other parts of a standard installation. But millions of lines of code, or even hundreds of thousands, arent necessary for building a fully functioning operating system. This one sets up a complete OS in exactly 2000 lines of code.
Called egos-2000, short for Earth and Grass Operating System, the diminutive operating system is written for RISC-V computers and while it does contain most of the tools we would recognize in an OS, it was built specifically for computer science students by PhD candidate Yunhao Zhang. The slimmed-down operating system makes it possible for students to easily read and understand every feature of an operating system without it becoming too overwhelming, and can be easily used and modified to experiment with. The name itself comes from its design principles, where parts of the operating system that interact with hard...
11:23
Webb telescope spots signs of universes biggest stars Lifeboat News: The Blog
The James Webb Space Telescope has helped astronomers detect the first chemical signs of supermassive stars, celestial monsters blazing with the brightness of millions of Suns in the early universe.
So far, the largest stars observed anywhere have a mass of around 300 times that of our Sun.
But the supermassive star described in a new study has an estimated mass of 5,000 to 10,000 Suns.
11:23
SpaceX rolls next Starship prototype out to pad for engine test (photo) Lifeboat News: The Blog
SpaceX rolled the Ship 25 Starship upper-stage prototype out to the launch pad early Thursday morning (May 18) to test-fire its six Raptor engines.
11:23
How Chronic Illness Patients Are Hacking Their Wearables Lifeboat News: The Blog
Fitbits and Apple Watches werent designed for people with atypical health conditions. But the tech can be extremely usefulwith some creativity.
11:22
40 Hz vibrations reduce Alzheimers pathology, symptoms in mouse models Lifeboat News: The Blog
Evidence that non-invasive sensory stimulation of 40 Hz gamma frequency brain rhythms can reduce Alzheimers disease pathology and symptoms, already shown with light and sound by multiple research groups in mice and humans, now extends to tactile stimulation. A new study by MIT scientists shows that Alzheimers model mice exposed to 40 Hz vibration an hour a day for several weeks showed improved brain health and motor function compared to untreated controls.
The MIT group is not the first to show that gamma frequency tactile stimulation can affect brain activity and improve motor function, but they are the first to show that the stimulation can also reduce levels of the hallmark Alzheimers protein phosphorylated tau, keep neurons from dying or losing their synapse circuit connections, and reduce neural DNA damage.
This work demonstrates a third sensory modality that we can use to increase gamma power in the brain, said Li-Huei Tsai, corresponding author of the study, director of The Picower Institute for Learning and Memory and the Aging Brain Initiative at MIT, and Picower Professor in the Department of Brain and Cognitive Sciences (BCS).
11:22
How to repair a damaged heart: Key mechanism behind heart regeneration in zebrafish revealed Lifeboat News: The Blog

Cardiovascular diseases, such as heart attacks, are a leading cause of death worldwide resulting from a limited self-healing power of the heart. Unlike humans, zebrafish have the remarkable capacity to recover from cardiac damage. Researchers from the group of Jeroen Bakkers (Hubrecht Institute) have used the zebrafish to shed light on their regenerative success. They discovered a new mechanism that functions as a switch to push the heart muscle cells to mature in the regeneration process. Importantly, this mechanism was evolutionary conserved as it had a very similar effect on mouse and human heart muscle cells.
The results of the study, published in Science on May 18, show that examining the natural heart regeneration process in zebrafish and applying these discoveries to human heart muscle cells could contribute to the development of new therapies against cardiovascular diseases.
It is estimated that 18 million people die from cardiovascular diseases every year. Many of these deaths are related to heart attacks. In such an event, a blood clot prevents the supply of nutrients and oxygen to parts of the heart. As a result, the heart muscle cells in the obstructed part of the heart die, which eventually leads to heart failure. Although therapies exist that manage the symptoms, there is no treatment that is able to replace the lost tissue with functional, mature heart muscle cells and thereby cure the patients.
11:22
Bill Gates Opposes Elon Musks Call to Pause New A.I. Research SoylentNews
Microsoft cofounder Bill Gates says he's "scared" about artificial intelligence falling into the wrong hands, but unlike some fellow experts who have called for a pause on advanced A.I. development, he argues that the technology may already be on a runaway train:
The latest advancements in A.I. are revolutionary, Gates said in an interview with ABC published Monday, but the technology comes with many uncertainties. U.S. regulators are failing to stay up to speed, he said, and with research into human-level artificial intelligence advancing fast, over 1,000 technologists and computer scientists including Twitter and Tesla CEO Elon Musk signed an open letter in March calling for a six-month pause on advanced A.I. development until "robust A.I. governance systems" are in place.
But for Gates, A.I. isn't the type of technology you can just hit the pause button on.
"If you just pause the good guys and you don't pause everyone else, you're probably hurting yourself," he told ABC, adding that it is critical for the "good guys" to develop more powerful A.I. systems.
[...] "We're all scared that a bad guy could grab it. Let's say the bad guys get ahead of the good guys, then something like cyber attacks could be driven by an A.I.," Gates said.
The competitive nature of A.I. development means that a moratorium on new research is unlikely to succeed, he argued.
Originally spotted on The Eponymous Pickle.
Previously: Fearing "Loss of Control," AI Critics Call for 6-Month Pause in AI Development
Related: AI Weapons Among Non-State Actors May be Impossible to Stop
Read more of this story at SoylentNews.
10:49
[Meme] Charlies Angels Have Probably Left Sirius Techrights
Summary: Almost nobody is left at Sirius Open Source and its unclear how many of those who left even realise that Sirius defrauded them (the police barely progresses the case)
10:40
Protecting the Rich From Poor Peoples Crimes, Not Poor People From Rich Peoples Crimes schestowitz.com
Video download
link | md5sum
0f02dc3bfb57e85b11051d8d4f2e571d
Serve and Protect Kings?
Creative Commons Attribution-No Derivative Works 4.0
Summary: The response from the police (or lack thereof) is a testament or a sign of a defunct system, wherein committing crimes against the vulnerable might be OK; cops dont prioritise such cases
TODAY, Thursday, is two days before the self-imposed soft deadline of British police. Less than 30 hours from now theyre supposed to have already looked into the report of crimes by Sirius Open Source. The evidence is extensive, the language used is polite, and all the correct procedures were followed when the report got filed.
So whats taking so long?
So far Ive received no letter, no phonecall, and no E-mail. Imagine being in a situation where enforcement is so urgent that its a life-or-death situation. In this case, the matter is urgent as soon there will be no company left to enforce against.
The video above goes through this latest part in a series. If theres a point to be made here, its that the police is unfit for purpose when it comes to white-collar crimes. When it comes to fraud, Action Fraud exists to protect the rich and powerful people from the hackers and scammers, but it wont protect ordinary citizens from rich and powerful corporations.
On Friday I intend to phone them asking for updates. But I wont get my hopes too high, based on past experiences. The likely outcome is, they will say they still sit on it and need more time. Remember that these people are receiving their salaries from taxpayers. Who are they protecting? The rich tax evaders, who arent even contributing much to the budget of the police?
10:36
Britains Most Respected and Best Established Open Source Business, According to Sirius (With Many Government Clients in Its Past), Protected From Prosecution? Techrights
Video download
link | md5sum
0f02dc3bfb57e85b11051d8d4f2e571d
Serve and Protect Kings?
Creative Commons Attribution-No Derivative Works 4.0
Summary: The response from the police (or lack thereof) is a testament or a sign of a defunct system, wherein committing crimes against the vulnerable might be OK; cops dont prioritise such cases
TODAY, Thursday, is two days before the self-imposed soft deadline of British police. Less than 30 hours from now theyre supposed to have already looked into the report of crimes by Sirius Open Source. The evidence is extensive, the language used is polite, and all the correct procedures were followed when the report got filed.
So whats taking so long?
So far Ive received no letter, no phonecall, and no E-mail. Imagine being in a situation where enforcement is so urgent that its a life-or-death situation. In this case, the matter is urgent as soon there will be no company left to enforce against.
Who are they protecting? The rich tax evaders, who arent even contributing much to the budget of the police?The video above goes through this latest part in a series. If theres a point to be made here, its that the police is unfit for purpose when it comes to white-collar crimes. When it comes to fraud, Action Fraud exists to protect the rich and powerful people from the hackers and scammers, but it wont protect ordinary citizens from rich and powerful corporations.
On Friday I int...
10:26
The Internet Dodges Censorship by the Supreme Court Deeplinks
The Supreme Court today refused to weaken one of the key laws supporting free expression online, and recognized that digital platforms are not usually liable for their users illegal acts, ensuring that everyone can continue to use those services to speak and organize.
The decisions in Gonzalez v. Google and Twitter v. Taamneh are great news for a free and vibrant internet, which inevitably depends on services that host our speech. The court in Gonzalez declined to address the scope of 47 U.S.C. 230 (Section 230), which generally protects users and online services from lawsuits based on content created by others. Section 230 is an essential part of the legal architecture that enables everyone to connect, share ideas, and advocate for change without needing immense resources or technical expertise. By avoiding addressing Section 230, the Supreme Court avoided weakening it.
In Taamneh, the Supreme Court rejected a legal theory that would have made online services liable under the federal Justice Against Sponsors of Terrorism Act on the theory that members of terrorist organizations or their supporters simply used these services like we all do: to create and share content. The decision is another win for users online speech, as it avoids an outcome where providers censor far more content than they do already, or even prohibit certain topics or users entirely when they could later be held liable for aiding or abetting their users wrongful acts.
Given the potential for both decisions to have disastrous consequences for users free expression, EFF is pleased that the Supreme Court left existing legal protections for online speech legal in place.
But we cannot rest easy. There are pressing threats to users online speech as Congress considers legislation to weaken Section 230 and otherwise expand intermediary liability. Users must continue to advocate for their ability to have a free and open internet that everyone can use.
Read on for a fuller analysis of the Supreme Courts decisions.
Supreme Court Sidesteps Effort to Weaken Section 230
The Supreme Courts Gonzalez decision to avoid interpreting Section 230 is a win for free speech online. Relying on its ruling in Taamneh (discussed below), the Supreme Court ruled that the plaintiffs in Gonzalez had failed to establish tha...
10:12
Links 18/05/2023: Weston 12.0.0 and IRPF-Livre 2023 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
-
GNU/Linux
-
Desktop/Laptop
-
HowTo Geek ...
-
-
10:08
Gemini Links 18/05/2023: Distributed Sites Over Git Techrights
-
Gemini* and Gopher
-
Personal
-
TV Showcase: Blakes 7
In 1977 came Star Wars, the movie. In the UK, the BBC created a television show in response: Blakes 7.
Imagine what would happen if you took the basic theme of Star Warsan extremely successful evil galactic empire, and the rebels fighing itand rewrote it as a serial with one rule: be realistic.
If there is an extremely succesful evil galactic empire, then it holds all the cards; and the ones fighting it are eternally desperate and probably not too happy most of the time. Losses are frequent; victories are rare and probably insignificant.
-
SpellBinding: ACGINPU Wordo: SODAS
-
-
Technical
-
Revisiting Vapad
Vapad is a little text editor that I started a year ago (or thereabouts) just in order to try out programming in Vala. Its intentionally a pretty simple little editor, but exposes a lot of the underlying functionality that you get for free just by including GtkSourceView such as syntax highlighting, smart indentation, and even vi mode. Being a Gtk+ app its most useful on Linux or BSD.
-
Threat Axis
Sometimes one might see worries about the Intel Management Engine (or the AMD equivalent) which if exploited would give an attacker a flawless victory, sub-zero wins! Given various CVE and TLA some of these fears may have merit. However, these same ME-fearing folks may fire up a heavyweight champion web browser without thought, even though that browser has much higher odds of having multiple exploits, and is much more likely to access such exploits from the cornucopia of content in a modern web request. Get over here, geese, its horn o plenty time!
-
smolver development log, part 10 CGI
Th...
-
-
10:05
The Nucleate Italy Longevity Conference will be held May 24th in cyberspace and in Italy. Lifeboat News
The Nucleate Italy Longevity Conference will be held May 24th in cyberspace and in Italy. Tickets are free!
Our Guido Putignano and Marco Quarta will be speaking.10:00
HPR3860: Civilization II Hacker Public Radio
This game is not quite as old, and it did make some changes. But the same "One-more-turn" addictiveness is still there. I can't tell you many times I started a game, and the next thing I knew the Sun was coming up outside my window. I'm too old to do that any more, but if I start another game of Civ II I will be right back in it. Links: https://playclassic.games/?s=Civilization+II https://www.myabandonware.com/browse/name/C/page/38/ https://www.youtube.com/watch?v=sHfk5VhAvWU http://www.replacementdocs.com/download.php?view.365 https://sleague.civfanatics.com/index.php?title=Main_Page https://www.mobygames.com/game/windows/civilization-ii-test-of-time https://www.youtube.com/watch?v=Ysk4o1zKsuE&t=5s https://www.youtube.com/watch?v=9XokQ-VDd88 https://www.youtube.com/watch?v=owt0CR9YHiA&t https://www.youtube.com/watch?v=pbGJrUTBHAY https://www.youtube.com/watch?v=yKs9Mtu_Fn4 https://www.palain.com/gaming/civilization-ii/
09:33
Apple fixed three new actively exploited zero-day vulnerabilities Security Affairs
Apple released security updates to address three zero-day vulnerabilities in iPhones, Macs, and iPads that are actively exploited in attacks.
Apple has addressed three new zero-day vulnerabilities that are actively exploited in attacks in the wild to hack into iPhones, Macs, and iPads.
The three vulnerabilities, tracked as CVE-2023-32409, CVE-2023-28204, and CVE-2023-32373, reside in the WebKit browser engine. Below are the details of the three issues:
- CVE-2023-32409 A remote attacker may be able to break out of Web Content sandbox. Apple is aware of a report that this issue may have been actively exploited. The flaw was reported by Clment Lecigne of Googles Threat Analysis Group and Donncha Cearbhaill of Amnesty Internationals Security Lab. Despite Apple did not provide details about the attacks, the three issues were likely exploited in attacks conducted by nation-state actors or by surveillance firms.
- CVE-2023-28204 Processing web content may disclose sensitive information. Apple is aware of a report that this issue may have been actively exploited. The flaw was reported by an anonymous researcher.
- CVE-2023-32373 Processing maliciously crafted web content may lead to arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited. The flaw was reported by an anonymous researcher.
Apple is aware of a report that this issue may have been actively exploited, reads the advisory [1, 2] published by the tech giant.
The company released iOS and iPadOS 16.5, tvOS 16.5, watchOS 9.5, Safari 16.5, and macOS Ventura 13.4 to address the issues.
Apple initially addressed both CVE-2023-28204 and CVE-2023-32373 with the Rapid Security Response (RSR) patches for iOS 16.4.1 and macOS 13.3.1 on May 1.
Since the beginning of 2023, the company addressed a total of six zero-day vulnerabilities exploited in attacks in the wild.
In February, the company released emergency security updates to address an actively exploited zero-day vulnerability, tracked as CVE-2023-23529, that impacts iOS, iPadOS, and macOS. The flaw is a type confusion issue in WebKit that was addressed by the IT giant with improved checks.
An attacker can achieve arbitrary code execution by tricking the victims into visiting maliciously crafted we...
09:05
World Wide Web Crushed and We Know Whose Fault That Might be Techrights
Video download
link | md5sum
fbe64d6ddc2a72ccf4301192fbe00152
Web Demise and Effect on People
Creative Commons Attribution-No Derivative Works 4.0
Summary: With sites shutting down, media companies going bankrupt, and more sites dabbling in webspam/chatbots we cannot be optimistic about the future of the Web
THE World Wide Web (WWW) is rotting; in 3 posts yesterday [1, 2, 3] we provided examples of the Web turning into trash. In two of these we focused on Linux sites. Its not easy to find legitimate articles anymore. The problem of re-posted (under a current date) old posts aside, we see lots of fake articles and sometimes barely articles at all. Some sites became webspam and others went offline, creating another issue (link rot and Web rot). The Web is actually shrinking over time and the golden era of the Web is well past us.
Recently we focused a bit on IBM, the subject which is discussed in the video above. After kicking out Fedora volunteers (slaves) IBM now fires Fedora staff from Red Hat. This is sabotage. We saw several names of people who lost their job at Red Hat, but one name that got more exposure was Ben Cotton, who incidentally decided that signing a defamatory attack letter (calling on the FSF to oust its founder, RMS) would be a good idea. Seems like joining the anti-RMS brigade did not safeguard his job at IBM, but thats another story.
...
09:00
LTE Sniffer Ferrets Out Cellular Communications Hackaday

LTE networks have taken over from older technologies like GSM in much of the world. Outfitted with the right hardware, like a software defined radio, and the right software, its theoretically possible to sniff some of this data for yourself. The LTESniffer project was built to do just this.
LTESniffer is able to sniff downlink traffic from base stations using a USRP B210 SDR, outfitted with two antennas. If you want to sniff uplink traffic, though, youll need to upgrade to an X310 with two daughterboards fitted. This is due to the timing vagaries of LTE communication. Other solutions can work however, particularly if you just care about downlink traffic.
If youve got that hardware though, youre ready to go. The software will help pull out LTE signals from the air, though it bears noting that its only designed to work with unencrypted traffic. It wont help you capture the encrypted communications of network users, though it can show you various information like IMSI numbers of devices on the network. Local regulations may prevent you legally even doing this, and if so, the project readme recommends setting up your own LTE network to experiment with instead.
Cellular sniffing has always been somewhat obscure and arcane, given the difficulty and encryption involved, to say nothing of the legal implications. Regardless, some hackers will always pursue a greater knowledge of the technolog...
09:00
A case study of QEMU and AddressSanitizer Linux.com

An example of how to use AddressSanitize
Click to Read More at Oracle Linux Kernel Development
The post A case study of QEMU and AddressSanitizer appeared first on Linux.com.
08:57
Digital Privacy Legislation is Civil Rights Legislation Deeplinks
Our personal data and the ways private companies harvest and monetize it plays an increasingly powerful role in modern life. Corporate databases are vast, interconnected, and opaque. The movement and use of our data is difficult to understand, let alone trace. Yet companies use it to reach inferences about us, leading to lost employment, credit, and other opportunities.
One unifying thread to this pervasive system is the collection of personal information from marginalized communities, and the subsequent discriminatory use by corporations and government agenciesexacerbating existing structural inequalities across society. Data surveillance is a civil rights problem, and legislation to protect data privacy can help protect civil rights.
Discriminatory collection of data
Our phones and other devices process a vast amount of highly sensitive personal information that corporations collect and sell for astonishing profits. This incentivizes online actors to collect as much of our behavioral information as possible. In some circumstances, every mouse click and screen swipe is tracked and then sold to ad tech companies and the data brokers that service them.
Where mobile apps are used disparately by specific groups, the collection and sharing of personal data can aggravate civil rights problems. For example, a Muslim prayer app (Muslim Pro) sold geolocation data about its users to a company called X-Mode, which in turn provided access to this data to the U.S. military through defense contractors. Although Muslim Pro stopped selling data to X-Mode, the awful truth remains: the widespread collection and sale of this data by many companies makes users vulnerable to discrimination. Yet far too many companies that collect geolocation data can make a quick buck by selling it. And law enforcement and other government agencies are regular buyers.
In 2016, Twitter, Facebook, Instagram, and nine other social media platforms were found to have provided software company Geofeedia with social media information and location data from their users. This data...
08:34
Hammerhead Sharks Found to Hold Their Breath on Deep Water Hunts to Stay Warm SoylentNews
Hammerhead sharks found to hold their breath on deep water hunts to stay warm:
Scalloped hammerhead sharks hold their breath to keep their bodies warm during deep dives into cold water where they hunt prey such as deep sea squids. This discovery, published in Science by University of Hawai'i at Mnoa researchers, provides important new insights into the physiology and ecology of a species that serves as an important link between the deep and shallow water habitats.
"This was a complete surprise," said Mark Royer, lead author and researcher with the Shark Research Group at the Hawai'i Institute of Marine Biology (HIMB) in the UH Mnoa School of Ocean and Earth Science and Technology. "It was unexpected for sharks to hold their breath to hunt like a diving marine mammal. It is an extraordinary behavior from an incredible animal."
Shark gills are natural radiators that would rapidly cool the blood, muscles, and organs if scalloped hammerhead sharks did not close their gill slits during deep dives into cold water. These sharks are warm water animals but feed at depths where seawater temperatures are similar to those found in Kodiak Alaska (around 5C/ 40F), yet they need to keep their bodies warm in order to hunt effectively.
"Although it is obvious that air-breathing marine mammals hold their breath while diving, we did not expect to see sharks exhibiting similar behavior," said Royer. "This previously unobserved behavior reveals that scalloped hammerhead sharks have feeding strategies that are broadly similar to those of some marine mammals, like pilot whales. Both have evolved to exploit deep dwelling prey and do so by holding their breath to access these physically challenging environments for short periods."
Read more of this story at SoylentNews.
08:04
Bug Bounty Programs May Sound Great, But Aren't Always Handled Well Phoronix
Bug bounty programs setup by large corporations to reward and recognize security researchers for properly reporting new bugs and security vulnerabilities is a great concept, but in practice isn't always handled well. Security researcher Adam Zabrocki recently shared the troubles he encountered in the bug bounty handling at Google for Chrome OS and in turn for Intel with it having been an i915 Linux kernel graphics driver vulnerability...
07:22
Read "Eponymous Plot Device: A Collection of Short Science Fiction Stories" by our Jeremy Lichtman. Lifeboat News
Read "Eponymous Plot Device: A Collection of Short Science free from May 21 to May 25!
06:20
[$] The intersection of lazy RCU and memory reclaim LWN.net
Joel Fernandes introduced himself to the memory-management track at the 2023 Linux Storage, Filesystem, Memory-Management and BPF Summit as a co-maintainer of the read-copy-update (RCU) subsystem and an implementer of the "lazy RCU" functionality. Lazy RCU can improve performance, especially on systems that are not heavily utilized, but it also has some implications for memory management that he wanted to discuss with the group.
06:17
KeePass 2.X Master Password Dumper allows retrieving the KeePass master password Security Affairs
A researcher published a PoC tool to retrieve the master password from KeePass by exploiting the CVE-2023-32784 vulnerability.
Security researcher Vdohney released a PoC tool called KeePass 2.X Master Password Dumper that allows retrieving the master password for KeePass.
The tool exploits the unpatched KeePass vulnerability, tracked CVE-2023-32784, to retrieve the master password from the memory of KeePass 2.x versions.
In KeePass 2.x before 2.54, it is possible to recover the cleartext master password from a memory dump, even when a workspace is locked or no longer running. The memory dump can be a KeePass process dump, swap file (pagefile.sys), hibernation file (hiberfil.sys), or RAM dump of the entire system. reads the description for this vulnerability. The first character cannot be recovered. In 2.54, there is different API usage and/or random string insertion for mitigation.
KeePass is a free and open-source software used to securely manage passwords. It functions as a digital safe where users can store and organize their sensitive information, including passwords, credit card numbers, notes, and other sensitive information. KeePass encrypts the data using a master key or master password that you need to provide in order to access the stored information.
The vulnerability should be fixed in KeePass 2.54, which is planned to be released at the beginning of June 2023.
The problem stems from the use of a custom-developed text box (SecureTextBoxEx) for password entry in the KeePass 2.X. This text box is not only used for the master password entry, but in other places in KeePass as well, like password edit boxes allowing an attacker to use it to recover their contents.
For every character typed, a leftover string is created in memory.
Because of how .NET works, it is nearly impossible to get rid of it once it gets created. For example, when Password is typed, it will result in these leftover strings: a, s, s, w, o, r, d. The POC application searches the dump for these patterns and offers a likely password character for each position in the password. reads the post published by the Vdohney.
The success of the attack depends on how the password was typed and how many passwords were typed per session. The expert explained that even if there are multiple passwords per...
06:00
Toothbrush Speed Controller Secrets Revealed Hackaday

Typically, when we want to build something with a DC motor, we might grab a bunch of AAs, or a single lithium cell at the very least. Electric toothbrushes often run on more humble power sources, like a single NiMH battery. Theyre designed to get useful motion out of just 1.2V, and [Marian Hryntsiv] has taken a look at what makes them tick.
The article focuses on an electric toothbrush built around the
Low Voltage GreenPAK SLG47513 chip. Its designed to work at voltages from just 1 to
1.65 V. To make the most of the limited power available, the
toothbrush stays in sleep mode most of the time when its not
working in oral health.
SLG47513 chip. Its designed to work at voltages from just 1 to
1.65 V. To make the most of the limited power available, the
toothbrush stays in sleep mode most of the time when its not
working in oral health.
[Marian] steps through the various parts of the circuit, and also explains the unique functionality baked into the...
05:48
New Animal Family Tree Raises Questions About the Origin of Nervous Systems SoylentNews
Sponges are more closely related to us than some animals with a nervous system:
A recent study challenges the idea that evolution always leads to increased complexity in animals. By analyzing gene arrangements on chromosomes, researchers sought to understand the evolutionary relationships between species.
The study found that sponges, which lack muscles and a nervous system, are more closely related to humans than comb jellies, which possess both traits. This contradicts the assumption that complexity determines evolutionary proximity. The research suggests two potential explanations: either sponges and other simple animals lost nerves and muscles over time, simplifying their body plans, or nerves and muscles evolved independently in different lineages.
Further investigation, such as studying the nerve and muscle cells of comb jellies in a lab, is needed to differentiate between these possibilities. The study underscores the complexity of animal evolution and challenges existing notions of evolutionary relationships based on traits and complexity.
Journal Reference:
Schultz, Darrin T., Haddock, Steven H. D., Bredeson, Jessen V.,
et al. Ancient gene linkages support ctenophores as
sister to other animals [open], Nature (DOI: 10.1038/s41586-023-05936-6)
Read more of this story at SoylentNews.
05:08
Support the "My Body, My Data" Act Deeplinks
EFF supports Rep. Sara Jacobs My Body, My Data" Act, which will protect the privacy and safety of people seeking reproductive health care. The bill was reintroduced this week.
Privacy fears should never stand in the way of healthcare. That's why this common-sense bill will require businesses and non-governmental organizations to act responsibly with personal information concerning reproductive health care. Specifically, it restricts them from collecting, using, retaining, or disclosing reproductive health information that isn't essential to providing the service someone asks them for.
Tell Congress to pass the "My Body, My Data" Act
These restrictions apply to companies that collect personal information related to a persons reproductive or sexual health. That includes data related to pregnancy, menstruation, surgery, termination of pregnancy, contraception, basal body temperature or diagnoses. The bill would protect people who, for example, use fertility or period-tracking apps or are seeking information about reproductive health services.
We are proud to join Planned Parenthood Federation of America (PPFA), NARAL Pro-Choice America, Physicians for Reproductive Health (PRH), National Partnership for Women & Families, National Womens Law Center (NWLC), Center for Democracy and Technology (CDT), Electronic Privacy Information Center (EPIC), National Abortion Federation, Catholics for Choice, National Council for Jewish Women, Feminist Majority, Unite for Reproductive & Gender Equity (URGE), and Indivisible.
In addition to the restrictions on company data processing, this bill also provides people with necessary rights to access and delete their reproductive health information. Companies must also publish a privacy policy, so that everyone can understand what information companies process and why. It also ensures that companies are held to public promises they make about data protection and gives the Federal Trade Commission the authority to hold them to account if they break those promises.
The bill also lets people take on companies that violate their privacy with a strong private right of action. Empowering people to bring their own lawsuits not only...
04:47
ACE Coalition Splits AtomoHD as Spains Piracy Pain Persists TorrentFreak
 Just three short months ago, Spanish pirate site users
were still coming to terms with bad news.
Just three short months ago, Spanish pirate site users
were still coming to terms with bad news.
Private torrent sites Pixelados/HD-Spain were fan favorites in Spain, with localized HD movies and TV shows in plentiful supply. Then suddenly, they were gone.
It was later revealed that pressure applied by the Alliance for Creativity and Entertainment, which included a credible threat of legal action, persuaded the sites operator to throw in the towel. Its a story thats played out many times in recent years and led to the closure of hundreds of sites.
ACE revealed another blow for Spanish pirates earlier today.
AtomoHD Splits Under ACE Pressure
AtomoHD (Atom HD in English) appeared as a newcomer in 2020 but in less than three years, ACE says the platform received 235 million visits, averaging 9.7 million visits per month. Less than 10% of the sites visitors were located outside Spain so its recent disappearance will be felt most acutely in the local market. The sites operators reportedly live elsewhere.
AtomoHD was launched in 2020 by a group of individuals, some of whom had prior convictions in Spain for intellectual property infringement and to evade justice, fled to Andorra, ACE reports.
AtomoHD enabled users to illegally stream and download content from a VOD library of more than 13,000 movies and 4,500 TV series in Spanish and other languages. The pirated content impacts all ACE members.
Precise Terms of Shutdown Unclear
For the governing board members of ACE, currently Amazon, Apple TV+, NBCUniversal, Netflix, Sony, Paramount, Disney, and Warner Bros, the shutdown of AtomoHD represents another success, one shared with the 50+ companies that make up the coalitions general membership.
This takedown represents yet another major victory by ACE over illegal content distributors, says Jan van Voorn, Executive Vice President and Global Content Protection Chief of the Motion Picture Association and Head of ACE. It is increasingly clear that major criminal operators like AtomoHD are not immune from ACEs enforcement actions.
The precise terms of the AtomoHD shutdown are unknown but domain transfers are definitely involved. ACE says the platform has around 60 domains and as far as we can tell, the following domains are already under new ownership:
atomohd.nl, atomohd.care, atomixhq....
03:36
Victory! Apple and Google Collaborate on Detecting Unwanted Location Trackers Deeplinks
Location trackers like Tiles and AirTags arent just a helpful way to find missing luggage or a misplaced walletthey can also be easily slipped into a bag or car, allowing stalkers and abusers unprecedented access to a persons location without their knowledge. Thats why we are enthusiastic about the effort between Apple and Google to release a draft specification on a detection protocol for these devices. We have been calling for an industry-wide standard for detection of this transient hardware to prevent stalking and other abuse, and this would greatly improve the ability of both Android and iPhone devices to detect unwanted trackers without additional apps.
While Tiles predate AirTags, Apple introduced a wider spectrum of trackers by integrating it within its Find My network (not to be confused with Androids own Find My Device network). However, both networks work similarly to integrate a range of device peripherals such as earbuds and smartwatches. Tiles had a smaller network of users, but iPhones created a billion plus device network for AirTags to function in. Tile recently announced it will work with Amazons Sidewalk network, which means that there will be three major networks of location trackers. They're also open to third-party developers; even more devices will be built with trackers in them in the future. Weve seen some improvements in detection since the AirTag was released, but a world in which survivors of stalking and abuse need to download a separate app for every type of physical scanner is not a solution ...
03:30
Passage by 1Password brings passkeys to any website Help Net Security
1Password has launched Passage by 1Password a standalone authentication solution that enables businesses to implement passkeys for apps and websites. Passage by 1Password allows businesses to eliminate the hassle of passwords and reduce cart abandonment without building their own authentication infrastructure. With Passage by 1Password, the company is expanding beyond credential management and into customer identity access management (CIAM). For passkeys to become the de facto industry standard, businesses need to be able to More
The post Passage by 1Password brings passkeys to any website appeared first on Help Net Security.
03:13
Satellite Signal Jamming Reaches New Lows IEEE Spectrum

Russias invasion of Ukraine in 2022 put Ukrainian communications in a literal jam: Just before the invasion, Russian hackers knocked out Viasat satellite ground receivers across Europe. Then entrepreneur Elon Musk swept in to offer access to Starlink, SpaceXs growing network of low Earth orbit (LEO) communications satellites. Musk soon reported that Starlink was suffering from jamming attacks and software countermeasures.
In March, the U.S. Department of Defense (DOD) concluded that Russia was still trying to jam Starlink, according to documents leaked by U.S. National Guard airman Ryan Teixeira and seen by the Washington Post. Ukrainian troops have likewise blamed problems with Starlink on Russian jamming, the website Defense One reports. If Russia is jamming a LEO constellation, it would be a new layer in the silent war in space-ground communications.
There is really not a lot of information out there on this, says Brian Weeden, the director of program planning for the Secure World Foundation, a nongovernmental organization that studies space governance. But, Weeden adds, my sense is that its much harder to jam or interfere with Starlink [than with GPS satellites].
LEO Satellites Face New Security Risks
Regardless of their altitude or size, communications satellites transmit more power and therefore require more power to jam than navigational satellites. However, compared with large geostationary satellites, LEO satelliteswhich orbit Earth at an altitude of 2,000 kilometers or lowerhave frequent handovers that introduce delays and opens up more surface for interference, says Mark Manulis, a professor of privacy and applied cryptography at the University of the Federal Armed Forces...
03:03
EU Commission Asks EU Council Lawyers If Compelled Client-Side Scanning is Legal, Gets Told It Isnt SoylentNews
EU Commission Asks EU Council Lawyers If Compelled Client-Side Scanning Is Legal, Gets Told It Isn't:
Lots of ideas have been floated by legislators and others in hopes of limiting the distribution of child sexual abuse material (CSAM). Very few of these ideas have been good. Most have assumed that the problem is so horrendous any efforts are justified. The problem here is that governments need to actually justify mandated mass privacy invasions, which is something that they almost always can't do.
It's even a fraught issue in the private sector. Apple briefly proposed engaging in client-side scanning of users' devices to detect CSAM and prevent its distribution. This effort was put on hold when pretty much everyone objected to Apple's proposal, stating the obvious problems it would create a list that included undermining the security and privacy protections Apple has long used as evidence of its superiority over competing products and their manufacturers.
Not that legislators appear to care. The EU Commission continues to move forward with "for the children" client-side scanning mandate, despite the multitude of problems this mandate would create. Last year, the proposal was ripped to shreds by the EU Data Protection Board and its supervisor in a report that explained the mandate would result in plenty of privacy invasion and data privacy law violations that simply could not be excused by the Commission's desire to limit the spread of CSAM.
[...] So, the proposal continues to move forward, ignoring pretty much every rational person's objections and the German government's flat-out refusal to enforce this mandate should it actually become law.
The Commission has ignored pretty much everyone while pushing this massive privacy/security threat past the legislative goal line. But it may not be able to ignore the...
03:00
ExtraHop protects organizations from accidental misuse of AI tools Help Net Security
ExtraHop released a new capability that offers organizations visibility into employees use of AI as a Service (AIaaS) and generative AI tools, like OpenAI ChatGPT. Organizations can now benefit from a better understanding of their risk exposure and whether or not these tools are being used in adherence with AI policies. As generative AI and AIaaS are increasingly adopted within enterprise settings, C-level executives are concerned that proprietary data and other sensitive information are being More
The post ExtraHop protects organizations from accidental misuse of AI tools appeared first on Help Net Security.
03:00
02:49
Target Expects to Lose $1 Billion Due to Shrink This Year cryptogon.com
Via: CNBC: Target said Wednesday that organized retail crime will fuel $500 million more in stolen and lost merchandise this year compared with a year ago. Targets inventory loss, called shrink, totaled about $763 million last fiscal year, based on calculations from the companys financial filings. With the anticipated increase, shrink this year would surpass []
02:45
Concentric AI unveils deep-learning driven detection capabilities Help Net Security
Concentric AI announced a deep-learning driven detection capabilities to find any type of hardcoded secrets and key credentials (e.g. API keys, encryption keys, tokens, passwords, etc.) in todays most popular enterprise on-premise and cloud data repositories, as well as email and messaging applications. As a result, these updates to Concentric AIs Semantic Intelligence DSPM solution enable security teams to address risks to sensitive data by deleting this information and reducing the threat of malware attacks More
The post Concentric AI unveils deep-learning driven detection capabilities appeared first on Help Net Security.
02:41
Why Californias Suburb Could Disappear in a Couple of Decades cryptogon.com
In short, the state is drastically restricting building homes on land outside of areas that are already built up. They want to pack more people into existing neighborhoods. Via: California Insider: Related: Leaving California The Untold Story
02:32
OpenAI Will Join Forces with Microsoft and Google on Artificial Intelligence cryptogon.com
What, precisely, does, Join forces, mean? Its not explained in the article. Via: CNBC: OpenAI CEO Sam Altman will join forces with key leadership from firms like Microsoft and Google this week as a secretive meeting of the business and political elite kickstarts in Lisbon, Portugal. Artificial intelligence will top the agenda as the ChatGPT []
02:30
Komprise automates data governance for IT Help Net Security
Komprise has released new governance and self-service capabilities that simplify departmental use of Deep Analytics, a query-based way to find and tag file and object data across hybrid cloud storage silos. IT organizations need to maintain data governance and data security while also making it easier for users to find, use and manage data. Often, these goals are in conflict and require significant IT overhead. The Komprise Intelligent Data Management Spring 2023 release minimizes administrative More
The post Komprise automates data governance for IT appeared first on Help Net Security.
02:30
This Cybercrime Syndicate Pre-Infected Over 8.9 Million Android Phones Worldwide The Hacker News
A cybercrime enterprise known as Lemon Group is leveraging millions of pre-infected Android smartphones worldwide to carry out their malicious operations, posing significant supply chain risks. "The infection turns these devices into mobile proxies, tools for stealing and selling SMS messages, social media and online messaging accounts and monetization via advertisements and click fraud,"
01:30
Badminton Inspired Heat Shield Aims to Fly This Year Hackaday

Badminton is not a sport that most of us think about often, and extremely rarely outside of every four years at the summer Olympics and maybe at the odd cookout or beach party here or there. But the fact that its a little bit unique made it the prime inspiration for this new heat shield design, which might see a space flight and test as early as a year from now.
The inspiration comes from the shuttlecock, the object which would otherwise be a ball in any other sport. A weighted head, usually rubber or cork, with a set of feathers or feather-like protrusions mounted to it, contributes to its unique flight characteristics when hit with a racquet. The heat shield, called Pridwen and built by Welsh company Space Forge, can be folded before launch and then expanded into this shuttlecock-like shape once ready for re-entry. Its unlikely this will protect astronauts anytime soon, though. The device is mostly intended for returning materials from the Moon or from asteroids, or for landing spacecrafts on celestial bodies with atmospheres like Mars or Venus.
With some testing done already, Space Forge hopes this heat shield will see a space flight before the close of 2023. Thats not the end of the Badminton inspi...
01:25
How To Minimize Ageism Through The Use Of AI Lifeboat News: The Blog
Dr. Sylvain Moreno is chief executive officer and scientific director of Circle Innovation.
Artificial intelligence (AI) holds great promise in the fight against ageism, and future technologies powered by AI can be a first step to ensure older adults are fully involved in the processes, systems and, ultimately, services that will affect them throughout the aging journey.
Healthcare providers, governments, academia, not-for-profits and businesses can ensure that AI is not only strengthening healthcare for older adults but also empowering them to meet their individual needs.
01:24
When Will Humanity Become a Stellar Civilization? | Unveiled Lifeboat News: The Blog

When will humans become Type II? Join us and find out more!
Subscribe: https://wmojo.com/unveiled-subscribe.
In this video, Unveiled takes a closer look at how (and when) humans will finally move up the Kardashev Scale! At present, humankind is only Type 0.7 on the ladder of advancement we have a long way to go! But how soon before we see things like Dyson Spheres and space travel to other planets? How soon before we become TYPE II?
This is Unveiled, giving you incredible answers to extraordinary questions!
Find more amazing videos for your curiosity here:
6 Scientific Breakthroughs Predicted During Your Lifetime https://youtu.be/wGKj-3AfxdE
What If Humanity Was a Kardashev Civilization? https://youtu.be/omScpI80PCo.
0:00 Intro.
1:03 Stellar (Type II) Civilization.
3:50 Timeline Predictions.
6:05 Are We Improving?
7:28 Dyson Spheres.
9:13 Further Considerations.
11:04 Conclusions.
01:23
[$] Page aging with hardware counters LWN.net
The memory-management subsystem has the unenviable task of trying to predict which pages of memory will be needed in the near future. Since predictions tend to be difficult, the code relies heavily on the heuristic that memory used in the recent past is likely to be used again in the near future. However, even knowing which memory has been recently used can be a challenge. At the 2023 Linux Storage, Filesystem, Memory-Management and BPF Summit, Aneesh Kumar and Wei Xu, both presenting remotely, discussed some ways to use the increasingly capable hardware counters that are provided by current and upcoming CPUs.
01:23
A Flash of Recognition in a Lonely Universe Lifeboat News: The Blog
Beyond our solar system, the universe is full of planetsbut also asteroids, auroras, and other familiar cosmic wonders.
01:22
SpaceX Reveals Starship Flight Test 2 Launch Timeline Lifeboat News: The Blog
SpaceX plans to be back up on its feet just two months after testing the Starship rocket for the first time.
01:22
James Webb telescope discovers ancient water world in nearby star system Lifeboat News: The Blog
The James Webb Space Telescope took its first close look at a mini-Neptune the most common type of planet beyond our solar system and found signs of water.
01:22
Our Universe Exists Inside Of A Black Hole Of Higher Dimensional Universe Lifeboat News: The Blog
This may sound like a science fiction scenario, but some physicists have proposed that this could be the case. In this article, we will explore the idea that our universe may be inside of a black hole, and what implications this would have for our understanding of cosmology and physics.
A black hole is a region of space where gravity is so strong that nothing can escape, not even light. According to Einsteins theory of general relativity, black holes are formed when massive stars collapse at the end of their life cycle. The resulting singularity is a point of infinite density and zero volume, where the laws of physics break down.
Scientists discover possible connection between human brain and cosmos on a quantum scale.
01:00
BeeKeeperAI releases EscrowAI to expedite the development and deployment of AI in healthcare Help Net Security
BeeKeeperAI has released EscrowAI, a zero trust collaboration platform. EscrowAI leverages Azure confidential computing to resolve the challenges of data sovereignty, privacy, and security. In healthcare, EscrowAI enables HIPAA-compliant research on full PHI without exposing the patient data, thereby reducing the AI development timeline due to streamlined collaboration agreements and access to more precise data. EscrowAI enables healthcare data stewards to fulfill their mission of scientific innovation while protecting patients sensitive health information. Data stewards, More
The post BeeKeeperAI releases EscrowAI to expedite the development and deployment of AI in healthcare appeared first on Help Net Security.
01:00
Ampere Computing Announces AmpereOne With Up to 192 Cores Per Socket Phoronix
Ampere Computing announced this morning that their AmpereOne family of processors have entered production and provided additional details on these in-house designed Arm server processors.
00:56
Admin of the darknet carding platform Skynet Market pleads guilty Security Affairs
A US national has pleaded guilty to operating the carding site Skynet Market and selling financial information belonging to tens of thousands of US victims.
The U.S. national Michael D. Mihalo, aka Dale Michael Mihalo Jr. and ggmccloud1, pleaded guilty to operating a carding site on the dark web called Skynet Market and selling financial information belonging to tens of thousands of victims in the US.
A carding site is an illegal marketplace where stolen credit card data and other personal info are offered for sale.
Mihalo and his co-conspirators also operated on other darknet marketplaces, including AlphaBay Market, Wall Street Market, and Hansa Market. The man and his co-conspirators sold the credit and debit card data of tens of thousands of U.S. victims between Feb. 22, 2016, and Oct. 1, 2019.
Mihalo earned at least $1 million worth of cryptocurrencies at the time of the sales, including Bitcoin, Ethereum, and Monero.
Mihalo is suspected to be the leader of a team that helped him sell this stolen financial information on the darknet. Each of the co-conspirators benefitted from the trusted reputation Mihalo, as ggmccloud1, had built on the darknet sites to sell more stolen card data. One of the mans conspirators, Taylor Ross Staats (40) of Texas, served as a card-checker. Staats personally earned at least $21,000 worth of Bitcoin for his activities.
Mihalo personally possessed, sent, and received the information associated with 49,084 stolen payment cards with the intent that the payment card information would be trafficked on darknet sites, all in furtherance of the conspiracy. reads the press release published by DoJ. Mihalo earned at least $1 million worth of cryptocurrencies at the time of the sales, including Bitcoin, Ethereum, and Monero. These funds have significantly appreciated since that time.
Mihalo pleaded guilty to one count of conspiracy to commit access device fraud, one count of access device fraud, and six counts of money laundering. The man faces a maximum penalty of five years in jail for the conspiracy count and a maximum penalty of 10 years in prison on each of the remaining counts.
Mihalo must also forfeit to the government any property he has personally obtained through the il...
00:35
Linux Foundation Newsletter: May 2023 Linux.com

Read the original blog at the Linux Foundation
The post Linux Foundation Newsletter: May 2023 appeared first on Linux.com.
00:30
New Relic launches AWS Systems Manager Distributor integration Help Net Security
New Relic has announced an integration with AWS Systems Manager Distributor to provide a native experience to automatically deploy the New Relic monitoring infrastructure agent via the AWS Command Line Interface (CLI) and any AWS infrastructure-as-code (IaC) tooling to streamline observability across Amazon Web Services (AWS) environments. This streamlined experience allows engineers to perform a one-time setup that automatically instruments and updates their entire fleet with the latest New Relic infrastructure agent, even as resources More
The post New Relic launches AWS Systems Manager Distributor integration appeared first on Help Net Security.
00:30
sdl12-compat Gets More Games Working For This SDL1-On-SDL2 Compatibility Layer Phoronix
The sdl12-compat project that implements the SDL 1.2 API/ABI atop SDL 2.x interfaces for better game compatibility on modern Linux systems is out today with a new pre-release...
00:17
China's Phone Giant Oppo Disbands Chip Design Unit as Shipment Slumps SoylentNews
China's phone giant Oppo disbands chip design unit as shipment slumps:
Chinese smartphone giant Oppo is disbanding its young chip design unit Zeku as weak global demand forces major handset manufacturers to cut costs and restrategize.
The decision comes as a surprise to those who believe the phone maker is bolstering its in-house chip development as rising geopolitical tensions with the U.S. threatens to cut Chinese firms off key suppliers. In the foreseeable future, Oppo will have to revert back to relying on third-party chip partners.
[...] Oppo explained its decision to cut its once-promising chip team in a statement issued today: "Due to the uncertainties in the global economy and the smartphone industry, we have to make difficult adjustments for long-term development. Therefore, the company has decided to cease the operation of Zeku."
In December 2021, Zeku revealed its first self-developed chipset, MariSilicon X, a neural processing unit designed to boost photo and video performance through machine learning, following Apple's path to bring chip design in-house. Zeku also set up a research base in Palo Alto.
[...] Oppo's retreat from chips signals another struggle from Chinese phone companies to strengthen their control over the semiconductor supply chain. Huawei lost access to advanced chips from the U.S. due to Trump-era sanctions, and its attempt to design its own high-end chips through HiSilicon floundered after the U.S. cut it off major foundries. The company resorted to spinning out its budget handset brand Honor, a move seen as a way to help the subsidiary circumvent the sanctions that have decimated Huawei's consumer business.
Read more of this story at SoylentNews.
00:15
Teradata collaborates with FICO to help customers reduce fraud Help Net Security
Teradata and FICO announced they plan to bring to market integrated advanced analytic solutions for real-time payments fraud, insurance claims, and supply chain optimization. Bringing data, analytics and insights together in one environment streamlines the development of solutions for use cases across industries, speeding time-to-delivery and making them available for joint customers sooner. The resulting solutions are part of a new global relationship between the two companies, and are expected to deliver reduced costs, improved More
The post Teradata collaborates with FICO to help customers reduce fraud appeared first on Help Net Security.
00:08
[$] Sunsetting buffer heads LWN.net
The buffer head is a kernel data structure that dates back to the first Linux release; for much of the time since then, kernel developers have been hoping to get rid of it. Hannes Reinecke started a plenary session at the 2023 Linux Storage, Filesystem, Memory-Management and BPF Summit by saying that everybody agrees that buffer heads are a bad idea, but there is less agreement on how to take them out of the kernel. The core functionality they provide facilitating sector-size I/O operations to a block device underlying a filesystem must be provided somehow.
00:00
Kyndryl and SAP boost partnership to ease digital transformation Help Net Security
Kyndryl has expanded strategic partnership with SAP focused on developing new solutions to help customers solve their most complex digital business transformation challenges. Under their expanded collaboration, the companies have leveraged SAP Business Transformation Center and vast ERP systems know-how, along with Kyndryls deep expertise in data, application migration, and modernization services to chart an efficient and cost-effective path to the cloud for customers. Specifically, Kyndryl and SAP collaborated on a digital blueprint capability that More
The post Kyndryl and SAP boost partnership to ease digital transformation appeared first on Help Net Security.
00:00
Revisiting Folk Wisdom for Modern Chronic Wound Care Hackaday

In the constant pursuit of innovation, its easy to overlook the wisdom of the past. The scientific method and modern research techniques have brought us much innovation, which can often lead us to dismiss traditional cultural beliefs.
However, sometimes, there are still valuable kernels of truth in the folklore of yesteryear. This holds true in a medical study from Finland, which focused on the traditional use of spruce resin to treat chronic wounds, breathing new life into an age-old therapy.
A Persistent Dilemma
Chronic wounds are defined as wounds that fail to proceed through a normal, timely healing process. While theres no strictly defined timescale, wounds are typically deemed as chronic if they dont progress through healing milestones after four weeks to three months. These wounds pose a significant burden on global healthcare systems. They create a significant workload for healthcare personnel, and are costly and difficult to manage. Most of all, though, they impair the quality of life for patients, who suffer these wounds for great lengths of time.
Patients with chronic wounds often suffer from other chronic health conditions such as advanced age, malnutrition, or vascular diseases. These can complicate or exclude treatment options that would otherwise help with the issue. Treatment often becomes a delicate balance between m...
00:00
Security updates for Thursday LWN.net
Security updates have been issued by Debian (chromium and libapache2-mod-auth-openidc), Fedora (clevis-pin-tpm2, greetd, keyring-ima-signer, libkrun, mirrorlist-server, nispor, nmstate, qt5-qtbase, rust-afterburn, rust-below, rust-bodhi-cli, rust-cargo-c, rust-coreos-installer, rust-fedora-update-feedback, rust-git-delta, rust-gst-plugin-reqwest, rust-pore, rust-rpm-sequoia, rust-sequoia-octopus-librnp, rust-sequoia-policy-config, rust-sequoia-sq, rust-sevctl, rust-tealdeer, and rust-ybaas), Oracle (apr-util, curl, emacs, firefox, kernel, libreswan, mysql, nodejs and nodejs-nodemon, openssh, thunderbird, and webkit2gtk3), Red Hat (apr-util, emacs, firefox, git, jenkins and jenkins-2-plugins, kernel, kpatch-patch, and thunderbird), Scientific Linux (apr-util, firefox, and thunderbird), Slackware (curl), SUSE (cups-filters, curl, java-1_8_0-openjdk, kernel, mysql-connector-java, and ovmf), and Ubuntu (cups-filters, git, linux-gcp-4.15, linux-oracle, linux-raspi, node-minimatch, ruby2.3, ruby2.5, ruby2.7, and runc).
Thursday, 18 May
23:22
Oldest living creature on Earth identified, emerging 700 million years ago Lifeboat News: The Blog
Scientists have announced that the oldest living creature on our planet is a jellyfish-like organism called a ctenophore. It evolved from the same primordial animals that humans did.
This fascinating creature first emerged 700 million years ago, a significant time before the dinosaurs, which appeared only 230 million years ago. The study found that ctenophores are the closest relatives of the first animals and can still be spotted in modern-day oceans and aquariums.
A team from the University of California, Berkeley embarked on a quest to decipher the relationships within the animal tree of life. They wanted to broaden our understanding of the origins and evolution of life on Earth.
23:22
Workplace AI: How artificial intelligence will transform the workday Lifeboat News: The Blog
Artificial intelligence has been around for years, but scarcely has it found itself in conversation as much as it has now. The launch of OpenAIs ChatGPT rocketed generative AI onto the radar of many people who hadnt been paying much attention or didnt feel it was relevant to their lives. This has included workers, whove already been touched by the technology, whether they know it or not.
The chatbot, which uses machine learning to respond to user prompts, is helping workers write cover letters and resumes, generate ideas and even art in the workplace and more. Its already making a splash in hiring with recruiters, who are finding they need to adapt to the new technology. And as competing companies rush to launch similar tools, the technology will only get stronger and more sophisticated.
The rise of generative AI in the workplace is inevitable. Theres a lot to be excited about it.
23:04
NVIDIA Announces The GeForce RTX 4060 Series Phoronix
NVIDIA today announced the GeForce RTX 4060 series consisting of the $399 RTX 4060 Ti 8GB while in July an RTX 4060 Ti 16GB version will come along with a $299 RTX 4060...
22:05
Zero Trust + Deception: Join This Webinar to Learn How to Outsmart Attackers! The Hacker News
Cybersecurity is constantly evolving, but complexity can give hostile actors an advantage. To stay ahead of current and future attacks, it's essential to simplify and reframe your defenses. Zscaler Deception is a state-of-the-art next-generation deception technology seamlessly integrated with the Zscaler Zero Trust Exchange. It creates a hostile environment for attackers and enables you to track
21:46
Links 18/05/2023: Mozilla Invests in Apps and Gig Workers Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Privatisation/Privateering
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Digital Restrictions (DRM)
- Monopolies
-
GNU/Linux
-
Audiocasts/Shows
-
Bryan Lunduke Serenity OS Review, France hates Apple, Microsoft forces upgrades
Lundukes Big Tech Show May 17th, 2023 Ep 003
-
Bryan Lunduke Frees...
-
-
21:29
Google to Start Deleting Inactive Mail Accounts for Security Reasons SoylentNews
https://www.blog.google/technology/safety-security/updating-our-inactive-account-policies/
Google to start deleting inactive personal email accounts. If your personal email account with Google have been inactive for two years it will, or may, be deleted.
To reduce this risk, we are updating our inactivity policy for Google Accounts to 2 years across our products. Starting later this year, if a Google Account has not been used or signed into for at least 2 years, we may delete the account and its contents ...
Notice that they MAY delete the account and all the content. Weird that they say may instead of will. Will some of them be kept around anyway? Are they saving the content but deleting the account? Is it so the Google AI can have one long good snoop before it goes into dev/null?
I might have missed it but to delete accounts for security reasons, that seems to be the reason given, is by itself sort of a security issue. After all what stops someone from re-registering the names afterwards. Hope that whatever mail they had keeps on sending to the address. Or it can be used to recover account credentials with other services. Deleting in that regard seems bad if they do not also block re-registration of said emails for a very very long time. Most of them will be duds but if you automate the process you'll hit digital credentials gold eventually.
If nothing else for spamming and scamming. After all johnny5753@gmail.com is your personal friend so whatever he mailed you must be real ...
Read more of this story at SoylentNews.
21:23
Additively manufacturing soft robots could reduce waste, increase performance Lifeboat News: The Blog
Soft robotics have several key advantages over rigid counterparts, including their inherent safety featuressoft materials with motions powered by inflating and deflating air chambers can safely be used in fragile environments or in proximity with humansas well as their flexibility that enables them to fit into tight spaces. Textiles have become a choice material for constructing many types of soft robots, especially wearables, but the traditional cut and sew methods of manufacturing have left much to be desired.
Now, researchers at the Harvard John A. Paulson School of Engineering and Applied Sciences (SEAS) have established a new approach for additively manufacturing soft robotics, using a 3D knitting method that can holistically print entire soft robots. Their work is reported in Advanced Functional Materials.
The soft robotics community is still in the phase of seeking alternative materials approaches that will enable us to go beyond more classical rigid robot shapes and functions, says Robert Wood, senior corresponding author on the paper, who is the Harry Lewis and Marlyn McGrath Professor of Engineering and Applied Sciences at SEAS.
21:23
Low-Carbon Concrete Could Bring a Radical Change to the Industry Lifeboat News: The Blog
Please make sure your browser supports JavaScript and cookies and that you are not blocking them from loading. For more information you can review our Terms of Service and Cookie Policy.
21:22
FBI, GCHQ Unite To Foil Russian Malware Hacking Tool HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
A joint advisory from the National Cyber Security Centre has detailed how the UK and its allies have cracked Snake, a Russian malware used by the FSB.
This is a post from HackRead.com Read the original post: FBI, GCHQ Unite To Foil Russian Malware Hacking Tool
21:00
21:00
Aqua Security collaborates with ServiceNow to accelerate cloud native risk remediation Help Net Security
Aqua Security integrates with the ServiceNow to enable joint customers to identify vulnerabilities in running containers with the broadest coverage across operating systems and programming languages, and with the highest accuracy. Security and application teams can automate vulnerability triage, identify high-risk findings and prioritize follow up using ServiceNow filtering rules including application context. The integration supports automated ingestion, filtering and grouping through the ServiceNow Vulnerability Response application of Aquas vulnerability scan findings, helping security and More
The post Aqua Security collaborates with ServiceNow to accelerate cloud native risk remediation appeared first on Help Net Security.
21:00
Drone Flies For Five Hours With Hydrogen Fuel Cell Hackaday

Multirotor drones have become a regular part of daily life, serving as everything from camera platforms to inspection tools and weapons of war. The vast majority run on lithium rechargeable batteries, with corresponding limits on flight time. A company called Hylium hopes to change all that with a hydrogen-powered drone that can fly for up to five hours.
The drone uses a hydrogen fuel cell to provide electricity to run the drones motors and other electronic systems. Thanks to the energy density advantage of hydrogen versus lithium batteries, the flight time can be greatly extended compared t...
20:50
22bet App Cameroon Download 22bet Apk For Android And Ios h+ Media
22bet App Cameroon Download 22bet Apk For Android And Ios
Each week youll be charged the entire amount that you spent on sports betting in the earlier week. The minimal quantity is 1 while the maximum discount is 1,500 per week. Most bonus provides have strict time frames, which may vary from a generous 40-days to a good 7-day turnaround. Make certain you wager all you need to earlier than your time is up, otherwise you will not be capable of take benefit of the provide.
Assistance is offered around-the-clock, so gamers can get info in real-time about the 22bet bonus for esports in addition to the 22bet casino provides. The FAQ page is also an excellent source of knowledge, as a lot of the widespread questions are answered in detail here. Overall, the web site is intuitive and highly responsive, so technical glitches usually are not frequent and players not often want help. One of the top betting apps obtainable in the marketplace is the Dafabet mobile App, which presents a live-streaming option. As with many betting services, 22Bet additionally has an FAQ part, but when making an attempt it out, it did appear to fall quick on a quantity of basic queries, like cost methods. With the variety of options here, it could probably be forgiven barely, however having to contact customer assist simply to seek out out if a certain cost technique was accepted isnt perfect.
These sites have an enormous focus on the Indian market and can ensure you get the correct online betting experience during the IPL. When we are on the topic of betting websites in India, we cannot keep away from the topic of what is the cricket betting sites. Clearly, in our introductory list of finest betting websites weve utilized a rating. Since were looking at cricket betting websites in India first and foremost, these features weigh the best. 1XBet additionally provides very generous welcome bonuses to their new customers and run promotions for the prevailing customers which includes merchandise amongst others. Crickex is available in India and accepts Indian rupees as a type of fee which saves tons of of rupees for Indians in currency exchange. Moreover, if you ever run into problems whereas enjoying betting at this bookmaker web site, you possibly can all the time get skilled help 24/7 via the stay chat characteristic.
This appears to have been an inside drawback with 22bets payment system, which has since been fastened. [newline]22bet has a one hundred pc sign up bonuses, by which they match your first deposit as soon as it has been gambled as soon as. Depending where you reside this deal is sweet to a most of 350. There are additionally esports, horse racing, and darts, among others. Although the Apk app is spectacular, the cellular model of 22bet ticks all the best boxes as well. Typically, whenever you visit load by default.
Users should antici...
20:50
Guide to Choosing the Best Family Cell Phone Plan HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
In a world where staying connected is paramount, the need for a reliable and affordable family cell phone
This is a post from HackRead.com Read the original post: Guide to Choosing the Best Family Cell Phone Plan
20:42
How to Reduce Exposure on the Manufacturing Attack Surface The Hacker News
Digitalization initiatives are connecting once-isolated Operational Technology (OT) environments with their Information Technology (IT) counterparts. This digital transformation of the factory floor has accelerated the connection of machinery to digital systems and data. Computer systems for managing and monitoring digital systems and data have been added to the hardware and software used for
20:25
The Progress With KDE Plasma 6's KWin HDR Support Phoronix
Following last month's Red Hat hosted HDR hackfest that brought together many Linux desktop stakeholders from GPU driver developers to desktop environment developers, KDE developer Xaver Hugl has shared an update on the progress being made for high dynamic range (HDR) display support from the KWin side...
20:21
Action Fraud Reinforces the Narrative That Says Cops Are Apathetic Towards White-Collar Crimes schestowitz.com
Summary: The crimes of Sirius Open Source crimes that had many victims dont seem to interest the police enough to act fast (we expected this all along); as its 28-day time window approaches we revisit the matter and discuss some more
ABOUT four weeks ago I contacted the police and filed a report about Sirius fraud. It was perfectly factual, with no gaps in knowledge left to fill (as I had received formal documentation from the original sources after months of ordeals, mostly trying hard to get them to admit the issue and write official letters). All the witnesses were ready to testify and answer additional questions.
Police is in no rush to act. Cops would be involved if someones life was at immediate risk, but thats about it. They drag their heels, just like pension providers do. Months ago I learn from a friend, a professor who worked here, that his female partner got punched in the face and despite the cops having CCTV footage of the incident and plate number (of the car in question) in other words everything needed to summon the perpetrator of assault and convict her the cops chose to do nothing, not even prosecute. See, here in Manchester it has become normal; if something gets damaged or stolen they typically just ask, do you have insurance? They dont want to get involved. They might open a case, give you a number, and then add it to the tally, eventually generating some detailed statistics for taxpayers while asking for implicit consent to close the case (without resolution).
They said they aimed to make progress within 28 days. Well, early this coming Saturday itll be 28 days, so I plan to call them tomorrow afternoon and ask about progress. And no, dont bother to put me down, Im not expecting much to happen. With my low expectations, not due to the crime not being severe enough but the police not being effective enough (from personal experience), I all along expected many delays, little action etc. I had already prepared actions to come after police inaction. There are 5 steps to come after that, but were keeping them close to our chest for now. By the end of this series we hope to make it crys...
20:15
Holding Criminals Accountable Part VI 26 Days Later and Still Inaction/No Action by the Police That Had Endless Resources for Coronation Ceremony Techrights
Series parts:
- Holding Criminals Accountable Part I Sirius Crimes Reported to British Authorities, Formally Registered With References (Many Victims), Heres What It Means and What Happens Next
- Holding Criminals Accountable Part II Still No Action From Action Fraud
- Holding Criminals Accountable Part III Why Police Action is the Only Option Now
- Holding Criminals Accountable Part IV British Prime Minister Launches Crackdown on Fraud, So Now Prove It
- Holding Criminals Accountable Part V 20 Days Later, UK Action Fraud Shows No Signs of Action
- YOU ARE HERE 26 Days Later and Still Inaction/No Action by the Police That Had Endless Resources for Coronation Ceremony
Summary: The crimes of Sirius Open Source crimes that had many victims dont seem to interest the police enough to act fast (we expected this all along); as its 28-day time window approaches we revisit the matter and discuss some more
ABOUT four weeks ago I contacted the police and filed a report about Sirius fraud. It was perfectly factual, with no gaps in knowledge left to fill (as I had received formal documentation from the original sources after months of ordeals, mostly trying hard to get them to admit the issue and write official letters). All the witnesses were ready to testify and answer additional questions....
20:11
New Maintainer Steps Up For GCC Compiler's MIPS CPU Port Phoronix
With development of the MIPS architecture having officially ended two years ago in favor of focusing on RISC-V for future CPU designs and the overall decline of that CPU architecture, it's been years since the GNU Compiler Collection (GCC) has seen its MIPS code well maintained. However, now a capable developer has stepped up willing to serve as the GCC maintainer for MIPS...
19:54
AlmaLinux 8.8 Released For Those Relying On RHEL8 Phoronix
Earlier this month Red Hat released RHEL 9.2 and at the same time they also released RHEL 8.8 for those continuing to rely on the stable RHEL8 series. AlmaLinux managed to provide a same-day release of AlmaLinux 9.2 while now one week later they have also shipped AlmaLinux 8.8...
19:53
Critical fixed critical flaws in Cisco Small Business Switches Security Affairs
Cisco fixed nine flaws in its Small Business Series Switches that could be exploited to execute arbitrary code or cause a DoS condition.
Cisco has released security updates to address nine security vulnerabilities in the web-based user interface of certain Small Business Series Switches that could be exploited by an unauthenticated, remote attacker to execute arbitrary code with root privileges or trigger a denial-of-service (DoS) condition.
Multiple vulnerabilities in the web-based user interface of certain Cisco Small Business Series Switches could allow an unauthenticated, remote attacker to cause a denial of service (DoS) condition or execute arbitrary code with root privileges on an affected device. reads the advisory published by Cisco. These vulnerabilities are due to improper validation of requests that are sent to the web interface.
There are no workarounds to address these vulnerabilities. These vulnerabilities impact the following Cisco Small Business Switches:
- 250 Series Smart Switches
- 350 Series Managed Switches
- 350X Series Stackable Managed Switches
- 550X Series Stackable Managed Switches
- Business 250 Series Smart Switches
- Business 350 Series Managed Switches
- Small Business 200 Series Smart Switches
- Small Business 300 Series Managed Switches
- Small Business 500 Series Stackable Managed Switches
The IT giant confirmed that these vulnerabilities do not impact the following Cisco products:
- 220 Series Smart Switches
- Business 220 Series Smart Switches
The vulnerabilities are not dependent on one another, this means the exploitation of one of them is not required to exploit another flaw.
A brief description of each of the flaws is as follows
- CVE-2023-20159 (CVSS score: 9.8): Small Business Series Switches Stack Buffer Overflow Vulnerability
- CVE-2023-20160 (CVSS score: 9.8): Small Business Series Switches Unauthenticated BSS Buffer Overflow Vulnerability
- CVE-2023-20161 (CVSS score: 9.8): Small Business Series Switches Unauthenticated Stack Buffer Overflow Vulnerability
- CVE-2023-20189 (CVSS score: 9.8): Small Business Series Switches Unauthenticated Stack Buffer Overflow Vulnerability
- CVE-2023-20024 (CVSS score: 8.6): Cisco Small Business Series Switches Unauthenticated Heap B...
19:53
Escalating China-Taiwan Tensions Fuel Alarming Surge in Cyber Attacks The Hacker News
The rising geopolitical tensions between China and Taiwan in recent months have sparked a noticeable uptick in cyber attacks on the East Asian island country. "From malicious emails and URLs to malware, the strain between China's claim of Taiwan as part of its territory and Taiwan's maintained independence has evolved into a worrying surge in attacks," the Trellix Advanced Research Center said
19:36
Cisco fixes critical flaws in Small Business Series Switches Help Net Security
Nine vulnerabilities 4 of them critical have been found in a variety of Cisco Small Business Series Switches. PoC exploit code is available (but not public), and there is no indication that they are being exploited in the wild. About the vulnerabilities The critical vulnerabilties (CVE-2023-20159, CVE-2023-20160, CVE-2023-20161, CVE-2023-20189) can be triggered via the switches web-based user interface, and may enable a remote attacker without authentication to run arbitrary code on a vulnerable More
The post Cisco fixes critical flaws in Small Business Series Switches appeared first on Help Net Security.
19:33
Steam Client Beta Fixes NVIDIA HiDPI Scaling, GPU Hardware Acceleration Phoronix
Valve released a new Steam client beta overnight and contains a few notable fixes for NVIDIA Linux gamers...
19:31
8220 Gang Exploiting Oracle WebLogic Flaw to Hijack Servers and Mine Cryptocurrency The Hacker News
The notorious cryptojacking group tracked as 8220 Gang has been spotted weaponizing a six-year-old security flaw in Oracle WebLogic servers to ensnare vulnerable instances into a botnet and distribute cryptocurrency mining malware. The flaw in question is CVE-2017-3506 (CVSS score: 7.4), which, when successfully exploited, could allow an unauthenticated attacker to execute arbitrary commands
19:08
U.S. Congress Doesnt Plan to Overreact to Generative AI Copyright Challenges TorrentFreak
 This article consists of a collection of words that were once
invented, most of them long before copyright or trademarks
existed.
This article consists of a collection of words that were once
invented, most of them long before copyright or trademarks
existed.
Words form the building blocks of todays society; they help to foster creativity and communication, and represent the driving force behind human intelligence.
These same words are now used as input by generative AI that will ultimately lead to new breakthroughs. Depending on who you ask, it has the potential to revolutionize many aspects of day-to-day life. At the same time, AI is causing grave concerns for the copyright industry.
The copyright angle is the topic of many debates and has already made its way to court in a few cases. Its high on the agendas of governments around the world, which are poised to accommodate generative AI within copyright legislation.
House Hearing on Copyright and AI
Copyright concerns surrounding generative AI were explored in detail yesterday by U.S. lawmakers at the House Judiciary IP Subcommittee. This hearing is an early step in the legislative process but an important one at that.
Historically, debates around copyright legislation tend to be polarized. However, U.S. Representative and committee chairman, Darrell Issa, urged everyone to approach the discussion with a spirit of collaboration.
Let us find common ground, seeking solutions that promote the flourishing of both creative expression and intellectual property protection. The stakes couldnt be higher and the outcome will shape the future landscape of art, technology and copyright today, Rep. Issa said.
Finding Middle Ground
The chairman stressed that, contrary to what some fear, Congress doesnt plan to make hasty decisions or overreact. At the same time, stakeholders should not fear or hope for severe measures. In this context he mentioned Spain and Italy, which have taken quite extreme positions.
Spain is moving forward with what I think might be a very restrictive interpretation. Japan believes, apparently, that all information that goes into the teaching is in fact free of any copyright restriction in its use.
I do not believe that todays discussion will take us down either road. I believe we will measure carefully and find middle ground that respects existing copyright law, while allowing the future of generative AI t...
19:01
1win org.ua Reviews Read Customer Service Reviews of 1win.org.ua h+ Media
1win org.ua Reviews Read Customer Service Reviews of 1win.org.ua
The signs were ominous for Auckland City FC but an improved tempo, intensity and desire saw the momentum of the game shift. That came to fruition when the Wee Nix tore the Navy Blues apart to release Riley Bidois who completed the easiest of finishes to hand Paul Temples team a deserved lead. Waikato Golf would like to extend our Congratulations to Hamilton Golf Club, in winning the 2022 Mens Championship Pennants Division 1 Final played at Hamilton Golf Course. Move With Murphy provides a range of commercial and residential transportation, logistics, and related services. This includes 3PL, warehousing, storage, devanning, and loading services to companies in a range of industries from our base in Silverdale, Auckland. We also help people from across Auckland move home with our honest and reliable removals services.
But just behind him, a heady mix of spirited newcomers clashing with hardened veterans made for some enticing racing. Key players showed their skill in all four matches, including Josh Collmenter, who demonstrated his major league-calibre arm. The Autumn Singles competition was a great success and was run very smoothly by Ron Garrett. Both groups had a plethora of talent each night, and this competitveness allowed for all the players to make great advances in their playing ability to start the season.
Emile Smith Rowe delivered another excellent performance on the left of midfield, capping his display with the third goal, but there was a good shape and confidence to the entire team. Leaders and representatives from Pacific Island nations demanded at a U.N. Outside linebacker Azeez Ojulari sprained an ankle Saturday, but he is getting better, Daboll said. New York continues to hope cornerback Adoree Jackson and safety Xavier McKinney will return after long absences. Daboll sounded more optimistic about Jackson playing this week than McKinney.
I have found these to be quite lucrative and have helped me to increase my winnings. The website offers a live chat feature where users can quickly and easily get in touch with a customer support representative. I have found the representatives to be helpful and knowledgeable, and they have been able to resolve any issues or answer any questions that I have had. Overall, I would highly recommend 1win to anyone looking for a reliable and user-friendly online betting website. With its wide range of sports and events, generous promotions and bonuses, and https://1xbet-mongolia.net/ excellent customer support, 1win is definitely worth checking out. In conclusion, 1win is an excellent online betting platform for users in New Zealand.
Fortunately, the most used version, 1win mobile site, is divided decently with a top-right menu button offloading most features from the front section. The initial 10 spots get an award as cash fro...
19:00
8-a-side teams will feature this season Otago Daily Times Online News h+ Media
8-a-side teams will feature this season Otago Daily Times Online News
However, make sure that the financial institution of your choice does not charge additional transaction fees. You can transfer funds through many different payment systems supported in India from your bank accounts, credit cards and e-wallets, including cryptocurrency wallets. It is also necessary to select the payment method and then press the withdraw button.
All new players are subjected to a 500% deposit bonus up to 2,000 provided they follow all the set terms of this offer. However, the maximum bonus you can receive under this welcome bonus can be claimed after a total of four deposits. Furthermore, customers should use bonus code maxboost to grab this promo.
We havent been able to play in New Zealand, even in my first season when we finished third, we didnt get the opportunity. The best coupons expire quickly, so we recommend finalizing your purchase. Through measuring our carbon footprint we hope to offer a metric whereby APS and our clients can ascertain the impact of the project based on product choice and methodology. If a winner is under the age of 18, the prize may be awarded to the winners parent or guardian.
I requested the withdrawal of money from this office in the amount of $ 760. They demanded to send passport photos and selfies to the mail to confirm account verification. I waited for 8 days, they didnt write anything, the support answered my questions slowly, the answer turns out to have come only got into spam. First doesnt just work, its been adequately adapted for all phones and tablets. They cooperate with different providers, they visited a couple, in general, you can list them for a long time, but its better to try it in person.
An 1Win discount code is an alphanumeric code which, like coupons or paper discount vouchers, allows you to receive a fixed discount or a percentage discount on your purchase. So, in addition to the affordable prices and offers already available on 1Win, you can get an additional discount on the total of your cart or on shipping. 1win offers excellent customer support to its users in New Zealand.
- The initial 10 spots get an award as cash from 1win bookmaker.
- They help make money even for beginners who have never played slots.
- The developers did not deviate from traditional solutions, so they chose a dark color for the main background, on which all the elements present are clearly visible.
- Van Hattum was a constant danger and kept Brown busy throughout but their resistance was broken when Auckland City FC youth product Dre Vollenhoven set up Logan Rogerson for the third with four minutes left.
Whether you prefer to bet on your desktop or mobile device, 1Win provides a seamless and convenient platform that allows you to place bets and monitor you...
18:41
Possible Non-Drug Cure for Depression SoylentNews
"Powerful magnetic pulses applied to the scalp to stimulate the brain can bring fast relief to many severely depressed patients for whom standard treatments have failed. Yet it's been a mystery exactly how transcranial magnetic stimulation, as the treatment is known, changes the brain to dissipate depression. Now, research led by Stanford Medicine scientists has found that the treatment works by reversing the direction of abnormal brain signals."
"When they analyzed fMRI data across the whole brain, one connection stood out. In the normal brain, the anterior insula, a region that integrates bodily sensations, sends signals to a region that governs emotions, the anterior cingulate cortex.
"You could think of it as the anterior cingulate cortex receiving this information about the bodylike heart rate or temperatureand then deciding how to feel on the basis of all these signals," Mitra said.
In three-quarters of the participants with depression, however, the typical flow of activity was reversed: The anterior cingulate cortex sent signals to the anterior insula. The more severe the depression, the higher the proportion of signals that traveled the wrong way."
"When depressed patients were treated with SNT, the flow of neural activity shifted to the normal direction within a week, coinciding with a lifting of their depression."
https://medicalxpress.com/news/2023-05-depression-reversing-brain-wrong.html
Read more of this story at SoylentNews.
18:03
Links 18/05/2023: Util-linux 2.39 and Lutris 0.5.13 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Desktop/Laptop
-
University of Toronto (Graphical) Unix has always had desktop environments
One of the stories that you could tell about the X Window System and by extension graphical Unix is that first came (simple) window managers and xterm. Only later did Unix developed desktop environments like GNOME and KDE. This is certainly more or less the development that happened on open source PC Unixes and to a certain degree its the experience many people had earlier on workstation Unix machines running X, but its actually not historically accurate. In reality, Unix has had...
-
-
18:00
A Vintage Polaroid Camera Goes Manual Hackaday

There once was a time when all but the most basic of fixed focus and aperture cameras gave the photographer full control over both shutter speed and f-stop. This allowed plenty of opportunity to tinker but was confusing and fiddly for non-experts, so by the 1960s and 70s many cameras gained automatic control of those functions using the then quite newly-developed solid state electronics. Here in 2023 though, the experts are back and want control. [Jim Skelton] has a vintage Polaroid pack film camera hes using with photographic paper as the film, and wanted a manual exposure control.
Where a modern camera would have a sensor in the main lens light path and a microcontroller to optimize the shot, back then they had to make do with a CdS cell sensing ambient light, and a simple analog circuit. He considered adding a microcontroller to do the job, but realized that it would be much simpler to replace the CdS cell with a potentiometer or a resistor array. A 12-position switch with some carefully chosen resistor values was added, and placed in the cameras original battery compartment. The final mod brought out the resistors and switch to a plug-in dongle allowing easy switching between auto and switch...
17:03
Re: IPv6 and Route of Death Open Source Security
Posted by Andrew Worsley on May 18
I think debian stable/bullseye may not be vulnerable with standard kernel:The exploit write up suggests it requires the ipv6_rpl_srh_compress()
routine to be compiled in
but from my reading of the code (see
https://git.kernel.org/pub/scm/linux/kernel/git/stable/linux.git/tree/include/net/rpl.h)
requires CONFIG_IPV6_RPL_LWTUNNEL to be define which isn't in my
latest debian amd64 kernel:
% grep CONFIG_IPV6_RPL_LWTUNNEL...
17:00
Overinflated: The Journey of a Humble Tire Reveals Why Prices Are Still So High Terra Forming Terra
EPA announces plan to shut down the US power grid by 2030 With mike Adams Terra Forming Terra
As you likely know, the CCP launched a WAR beginning in 2020 against the USA using what has been called irregular warfare as the methodology. The idea is to attack the population without deploying actual military assets.
EPA announces plan to shut down the US power grid by 2030
The EPA announced new rules last week that will render the entire US power grid inoperable by the year 2030. This will be accomplished by forcing nearly all coal and natural gas power facilities to shut down, claiming carbon is a "pollutant."
It's all part of the planned takedown of the USA through multiple vectors: Wide open border, escalation of war with Russia, food infrastructure sabotage and the step-by-step destruction of the fiat currency (dollar).
The Obama / Biden regime is on track to utterly obliterate the USA by 2030 if not sooner, transforming it into a collapsed third world nation occupied by illegals who will replace the vaccine-terminated oblivious masses who once inhabited the nation.
National Citizens Inquiry: Canadas Response to COVID-19 Terra Forming Terra

Birkeland currents Terra Forming Terra
16:58
Ukraine, Ireland, Japan and Iceland join NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE) Security Affairs
The NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE) announced that Ukraine, Ireland, Japan and Iceland joined the organization.
The NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE) is a multinational organization established to enhance cyber defence capabilities and promote cooperation among NATO member countries and partner nations.
On its 15th anniversary, the NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE) raised the flags of Iceland, Ireland, Japan, and Ukraine at its headquarters in Tallinn, welcoming four new member nations to the CCDCOE cyber defence family. reads the announcement.
The organization is located in Tallinn, Estonia, and conducts research, training, and exercises in the field of cyber defence, and provides a platform for sharing expertise and best practices. Its mission is to improve cyber defence policy, strategy, and operations through collaborative efforts and the development of innovative solutions.
The organization announced that Ukraine, Ireland, Japan and Iceland joined the CCDCOE.
The organization now reached 39 members, including those that are not in the NATO alliance.
I am truly grateful that Iceland, Ireland, Japan, and Ukraine have decided to join us, said Mart Noorma, director of the CCDCOE. We are delighted to have like-minded nations sharing cyber knowledge and exchanging methods to systematically address cyber attacks. Our goal is to foster increased cooperation and reap the benefits of this large-scale coalition through research, training, and exercises.

First, I would like to congratulate the CCDCOE. During the last 15 years, the CCDCOE has evolved from a small team of experts to the largest NATO centre of excellence. Second, we warmly welcome the new members, all of whom will add highly appreciated knowhow to the CCDCOEs work. We are particularly glad to see Ukraine here with us this offer...
16:44
Leaked Pentagon Report Forensically Dismantles Fauci-Led Natural Origin Study cryptogon.com
Via: ZeroHedge Epoch Times: Researchers at the Department of Defense wrote a devastating takedown of the Proximal Origin study, which was used by Dr. Anthony Fauci as proof that the COVID-19 virus had come from nature. The takedown, dated May 26, 2020, was written in the form of a working paper called Critical analysis []
16:39
IRC Proceedings: Wednesday, May 17, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-170523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-170523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-170523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-170523.gmi
Over HTTP:
|
... |
16:39
Deutsche Bank Settles Epstein Lawsuit For Up To $75 Million cryptogon.com
Via: ZeroHedge: Deutsche Bank has agreed to pay up to $75 million to settle a lawsuit brought by an Jeffrey Epstein victim who claimed that the bank had benefited from human trafficking by retaining Epstein as a client, the Financial Times reports. The lawsuit is one of three ongoing cases involving lenders to Epstein []
16:39
Darknet Carding Kingpin Pleads Guilty: Sold Financial Info of Tens of Thousands The Hacker News
A U.S. national has pleaded guilty in a Missouri court to operating a darknet carding site and selling financial information belonging to tens of thousands of victims in the country. Michael D. Mihalo, aka Dale Michael Mihalo Jr. and ggmccloud1, has been accused of setting up a carding site called Skynet Market that specialized in the trafficking of credit and debit card data. Mihalo and his
16:36
FBI Leadership Sabotaged Clinton Foundation Investigations: Durham Report cryptogon.com
Im sure youre shocked. Via: ZeroHedge: Remember the Clinton Foundation? Which, took millions in foreign donations when everyone thought Hillary Clinton was going to win the 2016 US election, only to see donations plummet by 90% after she lost? Now we learn, thanks to the Durham report, that the FBI had three concurrent investigations []
16:19
Apple Thwarts $2 Billion in App Store Fraud, Rejects 1.7 Million App Submissions The Hacker News
Apple has announced that it prevented over $2 billion in potentially fraudulent transactions and rejected roughly 1.7 million app submissions for privacy and security violations in 2022. The computing giant said it terminated 428,000 developer accounts for potential fraudulent activity, blocked 105,000 fake developer account creations, and deactivated 282 million bogus customer accounts. It
15:56
Vice Media Files for Bankruptcy SoylentNews
Once a digital media darling, Vice Media Group on Monday filed for bankruptcy protection after years of financial troubles:
A consortium of Vice's lenders which includes Fortress Investment, Soros Fund Management and Monroe Capital is looking to acquire the company following the filing.
The digital media trailblazer, once valued at $5.7 billion and known for sites including Vice and Motherboard, had been restructuring and cutting jobs across its global news business over recent months.
[...] Launched in Canada in 1994 as a fringe magazine, Vice expanded around the world with youth-focused content and a prominent social media presence. It endured several years of financial troubles, however, as tech giants such as Google and Meta vacuumed up global ad spend.
To facilitate its sale, Vice filed for Chapter 11 bankruptcy in the U.S. Bankruptcy Court for the Southern District of New York. If the application is approved, other parties will be able to bid for the company. Credit bids enable creditors to swap secured debt for company assets rather than pay cash.
Also at NPR, CNN and CBC News.
Previously: Vice Media Will Reorganize and Lay Off 10% of Staff
Read more of this story at SoylentNews.
15:18
Critical Flaws in Cisco Small Business Switches Could Allow Remote Attacks The Hacker News
Cisco has released updates to address a set of nine security flaws in its Small Business Series Switches that could be exploited by an unauthenticated, remote attacker to run arbitrary code or cause a denial-of-service (DoS) condition. "These vulnerabilities are due to improper validation of requests that are sent to the web interface," Cisco said, crediting an unnamed external researcher for
Please Participate in the World of Open Source Global Spotlight 2023 Survey Linux.com

Read the original blog at Read More
The post Please Participate in the World of Open Source Global Spotlight 2023 Survey appeared first on Linux.com.
15:00
Machining a Golf Ball To Make a Lovely Tactile Volume Knob Hackaday

Golf balls are wonderfully tactile things. They have a semi-grippy covering, and theyre a beautiful size and weight that sits nicely in the hand. Sadly, most of them just get smacked away with big metal clubs. [Jeremy Cook] recognized their value as a human interface device, though, and set about turning one into a useful volume knob.
The trick here is in the machining. [Jeremy] used a 3D printed jig to hold a golf ball tightly in place so that it could be machined using a milling machine. With the bottom taken off and a carefully-designed 3D printed insert in the bottom, the golf ball is ready to be used as a kn...
14:30
Enhancing open source security: Insights from the OpenSSF on addressing key challenges Help Net Security
In this Help Net Security interview, we meet a prominent industry leader. Brian Behlendorf, CTO at the Open Source Security Foundation (OpenSSF), shares insights on the influence of his experiences with the White House CTO office, World Economic Forum, and Linux Foundation on leading the OpenSSF and addressing open-source security challenges. Behlendorf discusses the trajectory of open-source software adoption, the unique challenges it faces regarding security, and how the OpenSSF is working to address these More
The post Enhancing open source security: Insights from the OpenSSF on addressing key challenges appeared first on Help Net Security.
14:00
Introducing Permit.io: Simplifying access control and policy management for developers Help Net Security
In this Help Net Security video interview, Or Weis, Co-Founder and CEO of Permit.io, discusses an innovative approach to managing permissions and access control within applications. We will explore policy as code and how it addresses organizations challenges in managing access control effectively.
The post Introducing Permit.io: Simplifying access control and policy management for developers appeared first on Help Net Security.
13:30
Organizations cyber resilience efforts fail to keep up with evolving threats Help Net Security
A steady increase in cyberattacks and evolving threat landscape are resulting in more organizations turning their attention to building long-term cyber resilience; however, many of these programs are falling short and fail to prove teams real-world cyber capabilities, according Immersive Labs. The report found that while 86% of organizations have a cyber resilience program, 52% of respondents say their organization lacks a comprehensive approach to assessing cyber resilience. Growing importance of cybersecurity in 2023 Strengthening More
The post Organizations cyber resilience efforts fail to keep up with evolving threats appeared first on Help Net Security.
13:07
The AI race heats up: Google announces PaLM 2, its answer to GPT-4 SoylentNews
On Wednesday, Google introduced PaLM 2, a family of foundational language models comparable to OpenAI's GPT-4. At its Google I/O event in Mountain View, California, Google revealed that it already uses PaLM 2 to power 25 products, including its Bard conversational AI assistant.
As a family of large language models (LLMs), PaLM 2 has been trained on an enormous volume of data and does next-word prediction, which outputs the most likely text after a prompt input by humans. PaLM stands for "Pathways Language Model," and "Pathways" is a machine-learning technique created at Google. PaLM 2 follows up on the original PaLM, which Google announced in April 2022.
Related:
Google Bard stories on soylentnews 12+ stories
Read more of this story at SoylentNews.
13:00
Identity crimes: Too many victims, limited resources Help Net Security
The Identity Theft Resource Center (ITRC) has documented incidents of identity theft reported during 2022 and the first quarter of 2023, highlighting the use of strategies by criminals to convince people to willingly share protected information. The number of reported identity crimes in 2022 was nearly the same as the all-time high in 2021, with only a slight decline of less than 1% to 14,817 cases. Identity crimes in 2022 55% (8,199) of identity crime More
The post Identity crimes: Too many victims, limited resources appeared first on Help Net Security.
12:55
[$] LWN.net Weekly Edition for May 18, 2023 LWN.net
The LWN.net Weekly Edition for May 18, 2023 is available.
12:00
Not Just ATP: Two-Component Molecular Motor Using GTPase Cycle Demonstrates Mechanotransduction Hackaday

For most of us who havent entirely slept through biology classes, its probably no secret that ATP (adenosine triphosphate) is the compound which provides the energy needed for us to move our muscles and for our body to maintain and repair itself, yet less know is guanosine triphosphate (GTP). Up till now GTP was thought to be not used for mechanical action like molecular motors, but recent research by Anupam Singh and colleagues in Nature Physics...
11:40
MIT Technology Review is About 80% Microsoft India Spam This Week (Sponsored Content) Techrights
Earlier this year: MIT Technology Review Became Spamfarm of Microsoft | MIT Technology Review is Running SPAM for Microsoft and Azure (Distracting From Mass Layoffs)

Since Monday weve seen no less than 10 Infosys-sponsored
articles in the site thats about 5 times as much all the
rest combined
Summary: An astonishing amount of webspam was published by MIT Technology Review on Monday and Tuesday
11:39
NEW 'Off The Hook' ONLINE 2600 - 2600: The Hacker Quarterly
NEW 'Off The Hook' ONLINE
Posted 18 May, 2023 1:39:39 UTC
The new edition of Off The Hook from 05/17/2023 has been archived and is now available online.
An experiment during Overtime, IRS to test free online filing system, distracted by chat, iPhones will be able to impersonate your voice using AI, Facebook glitches, Google to delete inactive accounts, ChatGPT can't tell if something was written by ChatGPT, Eurovision.
11:31
LINUX or UNIX Sites That Promote Windows Products? Follow the Money Techrights
 Summary: CNX Software is still
shilling a bunch of Microsoft and Windows products sometimes; its
because of money
Summary: CNX Software is still
shilling a bunch of Microsoft and Windows products sometimes; its
because of money
THE tragic story of Phoronix aside, yesterday we noticed this article from an author who said: GEEKOM sent us a sample of the AS 6 mini PC with [...] the pre-installed Windows 11 (not the first time).
Due to greed, GNU/Linux sites and their audiences are exposed to promotion of the competition.We gave more examples of this (about four articles in the past) regarding the same site.
A day later they did it again. Promoting Windows products for gifts (review units)?
This saddening trend is hurtful. Due to greed, GNU/Linux sites and their audiences are exposed to promotion of the competition. I exchanged some E-mail with the editor of the above site earlier this month. To be fair, it was a lot worse last year [1, 2]. But the problem remains largely unsolved.
11:17
The World Wide Web, and Even Some LINUX or UNIX Sites, Become Spamfarms Techrights
Summary: The Web is rotting (we will mention this in an upcoming video that gives 4 new examples of that); consider the example of www.unixmen.com, one of many Linux sites that recently became a spamfarm (some had become inactive or even went offline instead); we took note of this trend in April and things have gotten only more out of control since. This is the latest example of webspam with the word Linux thrown in to make it seem relevant. Going to the front page, about 90% of the content from the past 6 weeks is webspam, with the word Linux added to make it harder to notice (last month we explained how it figure out the SEO spam parts).
What will be left of the Web? More clickfraud spamnils?
10:59
Links 17/05/2023: Team UPC Tries Another Illegal Manoeuvre Techrights
![]()
Contents
- GNU/Linux
- Applications
- Instructionals/Technical
- Desktop Environments/WMs
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Monopolies
-
GNU/Linux
-
...
-
10:52
Gemini Links 17/05/2023: Several Gemini-Related News Techrights
-
Gemini* and Gopher
-
Personal
-
And all of a sudden its Wednesday
I cant believe anyone still believes the news.
Then again, were talking about people, here.
I mean, for the love of separate selfhood hypnosis, right?
-
Toasting the End of Amatonormativity
I noticed this was removed from library.inu.red at some point (presumably also removed from The Anarchist Library). Personally I found it to be a fantastic read, and was frustrated when it could no longer be found. As far as I know its not anywhere on the Geminispace, and happens to be hard to find on the world wide web. I believe it also poses some interesting questions given its age, and I also happen to partially disagree with some parts of it.
-
Album #267: Jeru the Damaja The Sun Rises In The East
It was nice to hear a new album for a change. My backlog has filled with the 60s and 70s rock albums that are the mainstay of this book. Peter Frampton and Iron Butterfly are Classic Rock staples that would also appear in 1001 Albums You Will Almost Certainly Have Heard Before You Die.
-
The simple joys of the humble slide rule
A bunch of scales printed on three rulers, the middle one of which can slide relative to the other two. Then finally, a glass box around the outside with a thin (hairline) mark down the middle, held perpendicular to the rulers.
Yet with this simple contraption you can perform all calculations normally reserved for a calculator, all the way through most Americans high school math. Im forever amazed by the ingenuity that enables trigonometry, powers, logarithms, and more to be calculated by rubbing two sticks together. This simple acti...
-
-
10:25
Scientists Discover Microbes That Can Digest Plastics at Low Temperatures SoylentNews
Finding, cultivating, and bioengineering organisms that can digest plastic not only aids in the removal of pollution, but is now also big business. Several microorganisms that can do this have already been found, but when their enzymes that make this possible are applied at an industrial scale, they typically only work at temperatures above 30C. The heating required means that industrial applications remain costly to date, and aren't carbon-neutral. But there is a possible solution to this problem: finding specialist cold-adapted microbes whose enzymes work at lower temperatures.
[...] "Here we show that novel microbial taxa obtained from the 'plastisphere' of alpine and arctic soils were able to break down biodegradable plastics at 15C," said first author Dr Joel Rthi, currently a guest scientist at WSL. "These organisms could help to reduce the costs and environmental burden of an enzymatic recycling process for plastic."
[...] None of the strains were able to digest PE [non-biodegradable polyethylene], even after 126 days of incubation on these plastics. But 19 (56%) of strains, including 11 fungi and eight bacteria, were able to digest PUR [biodegradable polyester-polyurethane] at 15C, while 14 fungi and three bacteria were able to digest the plastic mixtures of PBAT [biodegradable polybutylene adipate terephthalate] and PLA [biodegradable polylactic acid]. Nuclear Magnetic Resonance (NMR) and a fluorescence-based assay confirmed that these strains were able to chop up the PBAT and PLA polymers into smaller molecules.
"It was very surprising to us that we found that a large fraction of the tested strains was able to degrade at least one of the tested plastics," said Rthi.
The best performers were two uncharacterized fungal species in the genera Neodevriesia and Lachnellula: these were able to digest all of the tested plastics except PE. The results also showed that the ability to digest plastic depended on the culture medium for most strains, with each strain reacting differently to each of four media tested.
Read more of this story at SoylentNews.
10:00
HPR3859: My Live in Devices Hacker Public Radio
A talk about things that attracted me to purchase them.
The Cost of Change It Will Never Work in Theory
Everybody wants things to get better. People who are serious about it draw up budgets, because that forces them to be explicit about exactly what they're going to do and what's needed to make it happen.
I'm sure it's clear by now that we'd like more programmers to know what software engineering researchers have learned over the past fifty years and how to act on it. We have a plan to make that happen: replace the team programming project course that most students do in the third or fourth year of an undergraduate degree in computer science with one in which they work in teams to design an experiment, collect data, analyze it, and figure out what (if anything) they've proven.
- It's a minimally disruptive adjustment to the curriculum, so other faculty won't object on administrative grounds.
- it gives CS students a chance to learn some practical data science, (which most of them will enjoy, and which will make them more employable.
- It helps prepare them for graduate school (so it's in professors' own interests as well).
- And crucially, they will be more likely to understand and value researchers' experimental findings if they have done an experiment of their own.
What we need to make this happen is two dozen lectures' worth of material as both prose and slides with examples, exercises, and grading rubrics so that busy professors don't each have to build it all from scratch. Figuring a week of research and development per lecture (because most of this material would be genuinely new), then doubling that estimate because I'm always optimistic, it would take one person-year to build this course, run it for the first time, fix what didn't work, and package it up for general use.
If two dozen professors in software engineering want this to happen and will each contribute US$6500 to fund two weeks' worth of work, our entire discipline will have what it needs to shape young minds today so that tomorrow's programmers will be more engaged with our work. If you're at ICSE'23 in Melbourne right now, please chat with your colleagues about this idea. If your answer is "no", please mail me and tell me what your alternative plan is. "If we just keep publishing, surely they'll start to pay attention" has been failing for fifty years; I think it's time we tried something else.
09:03
Smashing Security podcast #322: When you buy a criminals phone, and paying for social media scams Graham Cluley
Personal information is going for a song, and the banks want social media sites to pay when their users get scammed. All this and much more is discussed in the latest edition of the "Smashing Security" podcast by computer security veterans Graham Cluley and Carole Theriault.
09:00
Inside A Current Probe Hackaday

[The Signal Path] had two Tektronix AC/DC current probes that didnt work. Of course, thats a great excuse to tear them open and try to get at least one working. You can see how it went in the video below. The symptoms differed between the two units, and along the way, the theory behind these probes needs some exploration.
The basic idea is simple, but, of course, the devil is in the details. A simple transformer doesnt work well at high frequencies and wont work at all at DC. The solution is to use a hall effect sensor to measure DC and also to feed it back to cancel coil saturation.
By switching transformer assemblies between the probes, he found that one worked and one did not. So the next step was to examine the assembly to see if anything was obviously wrong with it. There was also a plastic piece broken on both probes that needed replacing, but that didnt seem like a difficult problem to surmount compared to the electronic problem.
Fortunately, having a good transformer allowed him to compare readings to determine any problems. The hall effect sensor appeared bad, but taking the module apart destroyed it. On the other hand, we get to see whats inside. Unfortunately, something in the repair operation broke the working module. It would intermittently work with some pressure, but for the most part, it suddenly had the same symptom as the other module. [The Signal Path] speculates that the pressure...
09:00
08:01
How to Enable Advanced Data Protection on iOS, and Why You Should Deeplinks
Apple has long used end-to-end encryption for some of the information on your iPhone, like passwords or health data, but the company neglected to offer a way to better protect other crucial data, including iCloud backups, until recently. This came after years of a hard fought battle pushing Apple to encrypt backups and drop its plans for client-side scanning. With Advanced Data Protection, that additional security is now an option, but you have to turn it on yourself. This is a big win for user privacy, and sets a new bar for the safety of cloud device backups.
Apple introduced Advanced Data Protection in the United States in December 2022, and released it globally in January 2023. (No list of countries is currently available, but Apple confirmed to EFF that it's available globally). The idea is simple: you can now enable end-to-end encryption of data that was previously only encrypted in transit and on Apple's servers, meaning that Apple itself could access the data. In other words, you can now control the encryption keys and Apple will not be able to access any of this data. It also means Apple will not be able to help you regain access to most information on your account. The full list of data categories is available on Apple's site, but the most notable include the iCloud backup (which includes the backup of Messages), iCloud Drive, photos, notes, reminders, and more.
EFF first called for Apple to enable encrypted backups back in 2019 because, while some of the data in iCloud is end-to-end encrypted, backups were not, and that meant a lot of different categories of data were vulnerable to government requests, third-party hacking, and disclosure by Apple employees. This was often a cause for confusion with Messages, where the messages were end-to-end encrypted, but the backups were not. The potential for privacy issues were complicated further in 2021 when Apple proposed a backdoor with client-side scanning for child sexual abuse material (CSAM), but delayed after EFF supporters and allies delivered a petition containing more...
07:40
Microsoft is Scanning the Inside of Password-protected Zip Files for Malware SoylentNews
If you think a password prevents scanning in the cloud, think again:
Microsoft cloud services are scanning for malware by peeking inside users' zip files, even when they're protected by a password, several users reported on Mastodon on Monday.
Compressing file contents into archived zip files has long been a tactic threat actors use to conceal malware spreading through email or downloads. Eventually, some threat actors adapted by protecting their malicious zip files with a password the end user must type when converting the file back to its original form. Microsoft is one-upping this move by attempting to bypass password protection in zip files and, when successful, scanning them for malicious code.
While analysis of password-protected files in Microsoft cloud environments is well-known to some people, it came as a surprise to Andrew Brandt. The security researcher has long archived malware inside password-protected zip files before exchanging them with other researchers through SharePoint. On Monday, he took to Mastodon to report that the Microsoft collaboration tool had recently flagged a zip file, which had been protected with the password "infected."
[...] Fellow researcher Kevin Beaumont joined the discussion to say that Microsoft has multiple methods for scanning the contents of password-protected zip files and uses them not just on files stored in SharePoint but all its 365 cloud services. One way is to extract any possible passwords from the bodies of an email or the name of the file itself. Another is by testing the file to see if it's protected with one of the passwords contained in a list.
"If you mail yourself something and type something like 'ZIP password is Soph0s', ZIP up EICAR and ZIP password it with Soph0s, it'll find (the) password, extract and find (and feed MS detection)," he wrote.
Read more of this story at SoylentNews.
07:30
The 2023 Tech Talent Report: Three things you need to know Linux.com

Read the original blog at Read More
The post The 2023 Tech Talent Report: Three things you need to know appeared first on Linux.com.
07:17
Monitoring the dark web to identify threats to energy sector organizations Security Affairs
Searchlight Cyber researchers warn of threat actors that are offering on the dark web access to energy sector organizations.
Dark web intelligence firm Searchlight Cyber published a report that analyzes how threat actors in the dark web prepare their malicious operations against energy organizations.
The threat actors use the hidden part of the web to share techniques, build their resources, and coordinate their attacks. The report published by the experts provides evidence of continuous discussion of attacks on energy companies on dark web forums.
The role of an initial access broker is essential in the cybercrime ecosystem, these actors facilitate the sale or exchange of compromised or stolen initial access to computer networks or systems. These brokers act as intermediaries between cybercriminals who gain unauthorized access to networks and buyers interested in purchasing or utilizing that access for malicious activities. Marketplace and hacking forums offering initial access, enable crooks to speed up their attacks and monetize their cyber operations.
Threat actors auction initial access to remote software, RDP access, VPNs, and stolen credentials, allowing attacks to use these accesses to establish a foothold in the target organization and launch the attack on both IT and OT infrastructure.
The report is very important for defenders, the knowledge of the sale of initial access to energy organizations can allow them to prioritize imminent threats and adopt the proper countermeasures.
The report is based on the analysis of posts published between February 2022 and February 2023 on cybercrime forums, dark websites, and marketplaces. The experts focused on posts and discussions offering and searching for initial access into the networks of energy sector organizations.
The report is based on a small sample including targets in the USA, Canada, UK, France, Italy, and Indonesia.
The predominant activity we observe against the energy industry on the dark web are the auctions for initial access to energy companies that routinely take place on dark web forums. reads the report published by the experts. Listings also include companies across the spectrum of the energy sector upstream, midstream, and downstream in traditional energy companies such as oil and gas but also renewable energy organizations.
The offers usually include the overall revenue of the organization that can give the buyers an estimation of the earning potential in case of a successful compromise.
06:28
Japans Pirate Manga Site Leak Isnt a Failure, Its Potential Education TorrentFreak
 Multi-point, ongoing collisions between rightsholders,
pirate sites, pirates and copyright law, are what fuel our daily
reporting. The pumps rarely run dry for long in these wars.
Multi-point, ongoing collisions between rightsholders,
pirate sites, pirates and copyright law, are what fuel our daily
reporting. The pumps rarely run dry for long in these wars.
The polarized nature of the debate, which regularly pits decent law-abiding content creators against shadowy thieves hiding in the recesses of the web, is good for headlines but a hopeless anti-piracy tool.
Casual pirates, who represent the majority, routinely dismiss this type of messaging as either completely untrue or blatant propaganda. Yet when unfiltered piracy information leaks out unexpectedly, people suddenly develop an interest in what anti-piracy groups have to say.
Redacted Document Wasnt Redacted
Many months ago, Japans Agency for Cultural Affairs published a document which contained a list of pirate manga sites generating high levels of traffic from within Japan. As the image below shows, the names of the sites were considered sensitive enough to completely redact. The redaction wasnt effective.
Hovering a cursor over the blacked-out area revealed what shouldve been hidden and click led directly to the site considered most damaging to the home market in Japan.
Thats highly relevant information but when the Agency of Cultural Affairs was alerted to the buzz on social media, the information was immediately taken down.
The Case for Sharing More Information, Not Less
Theres a theory in anti-piracy circles that mentioning pirate sites by name makes them more popular. If we assume thats the case, lets see how thats working out.
The slide with the unredacted text above covers the period June-July 2022. The slide below is from a more recent report covering September-October 2022. This time the names of the sites are properly redacted but we can still see data related to the site in the top spot.
06:17
Is it Getting Harder to Pigeonhole Games into Specific Genres? HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
Back in 2015, a study from Syracuse University analysed how grouping video games into genres can be limited.
This is a post from HackRead.com Read the original post: Is it Getting Harder to Pigeonhole Games into Specific Genres?
06:00
This Engineer Promotes Innovation-Based Projects in Uganda IEEE Spectrum

Ever since Lwanga Herbert was a youngster growing up in Kampala, Uganda, he wanted to create technology to improve his community. While attending a vocational school, he participated in a project that sought technological solutions for local electricians who were having problems troubleshooting systems.
Herbert helped develop a detector to measure voltage levels in analog electronics; a pulse detector to identify digital pulses and signals; and a proximity alarm system. The tools he helped develop made troubleshooting easier and faster for the electricians. When he understood the impact his work had, he was inspired to pursue engineering as a career.
I saw firsthand that technology increases the speed, efficiency, and effectiveness of solving challenges communities face, he says.
The devices were recognized by the Uganda National Council for Science and Technology. The level and pulse detectors were registered as intellectual property through the African Regional Intellectual Property Organization.
Herbert now works to use technology to address challenges faced by Uganda as a whole, such as high neonatal death rates.
The IEEE member is the innovation director at the Logel Science Foundation. The nonprofit, which was launched in 2001, works to foster technological development in Uganda. It strives to enable a more competitive job market by helping startups succeed and by sparking interest in science, technology, engineering, and math careers.
Herbert has been active with IEEEs humanitarian programs and is chair of the newly established IEEE Humanitarian Technology Board. HTB will oversee and support all humanitarian activities across IEEE and is responsible for fostering new collaborations. It also will fund related projects and activities.
Because of his busy schedule, The Institute conducted this interview via email. We asked him about the goals of the Logel Science Foundation, his humanitarian work, and how his IEEE membership has advanced his career. His answers have been edited for clarity.
The Institute: What are you working on at the foundation?
Lwanga H...
05:55
Wayland's Weston 12.0 Released With Multi-GPU Support, PipeWire Backend, Tearing Control Phoronix
Weston 12.0 as Wayland's reference compositor is now available with multiple GPU support in the DRM back-end, support for HDMI content types, support for the Wayland tearing control protocol, plane alpha DRM property handling, a PipeWire back-end, and much more...
05:24
President Biden Wants Dr. Monica Bertagnolli for Director of the NIH cryptogon.com
Via: RFK Jr.: Yesterday, President Biden announced Dr. Monica Bertagnolli as his intended nominee for Director of the NIH. Guess what? From 2015-2021, Bertagnolli received more than 116 grants from Pfizer, totaling $290.8 million. This amount made up 89% of all her. research grants.
05:05
Saving the News From Big Tech Deeplinks
Media is in crisis: newsrooms all over the world are shuttering and the very profession of journalism is under sustained ideological and physical assault. Freedom of the press is a hollow doctrine if the only news media is written or published by independently wealthy individuals who dont need to get paid for their labor.
Where did the medias money go? Its complicated.
How News Companies Shot Themselves in the Face
Lets start with the news outlets themselves. Right around the time that personal computers were finding their way into home offices and kids bedrooms, news media underwent an orgy of consolidation, starting with the Reagan administrations deregulation of the financial markets and, later the Clinton administrations Telecommunications Act, which stripped away the already weak restrictions on media consolidation.
As media outlets across the country merged, national chains took over from family proprietors. They raised prices and fired reporters, turning to wire services and chain-wide correspondents for subjects of national interest. They also fired locally focused salespeople, consolidating classified and display ad-sales to national call-centers. They sold off their buildings and presses and logistics networks, leasing them back. These cuts yielded dividends to the chains investors, dividends that were augmented by liquidating the papers cash reserves and rainy day funds.
Thus the papers were already hollowed out and brittle when online advertising came along. Though papers had weathered the advent of the telegraph, the telephone, the television, cable, and satellites, they were devastated by the rise of online classified advertising sites, from Craigslist to MSN.
Left with no cash reserves, heavy debt loads, a generic product that emphasized wire stories and national correspondents servicing dozens of outlets that pur...
05:00
[$] Democratizing AI with open-source language models LWN.net
When OpenAI made its chatbot ChatGPT available to the public in November 2022, it immediately became a hit. However, despite the company's name, the underlying algorithm isn't open. Furthermore, ChatGPT users require a connection to OpenAI's cloud service and face usage restrictions. In the meantime, several open-source or freely available alternatives have emerged, with some even able to run on consumer hardware. Although they can't match ChatGPT's performance yet, rapid advancements are occurring in this field, to the extent that some people at the companies developing these artificial intelligence (AI) models have begun to worry.
04:54
Cosmic Rays Reveal Hidden Ancient Burial Chamber Underneath Naples SoylentNews
Rectangular chamber was probably the tomb of a wealthy individual or family:
The ruins of the ancient necropolis of Neapolis lie some 10 meters (about 33 feet) below modern-day Naples, Italy. But the site is in a densely populated urban district, making it challenging to undertake careful archaeological excavations of those ruins. So a team of scientists turned to cosmic rays for helpspecifically an imaging technique called muography, or muon tomographyand discovered a previously hidden underground burial chamber, according to a recent paper published in the Scientific Reports journal.
[...] In 2016, scientists using muon imaging picked up signals indicating a hidden corridor behind the famous chevron blocks on the north face of the Great Pyramid of Giza in Egypt. The following year, the same team detected a mysterious void in another area of the pyramid, believing it could be a hidden chamber, which was subsequently mapped out using two different muon imaging methods.
There are many variations of muon imaging, but they all typically involve gas-filled chambers. As muons zip through the gas, they collide with the gas particles and emit a telltale flash of light, which is recorded by the detector, allowing scientists to calculate the particle's energy and trajectory. It's similar to X-ray imaging or ground-penetrating radar, except with naturally occurring high-energy muons rather than X-rays or radio waves. That higher energy makes it possible to image thick, dense substances like the stones used to build pyramids. The denser the imaged object, the more muons are blocked, casting a telltale shadow. Hidden chambers would appear in the final image because they blocked fewer particles.
Neapolis was a Hellenistic city in a hilly area rich in volcanic tuff rock. That made it soft enough to sculpt out tombs, worship spaces, or caves for housing. The necropolis in what is now the Sanita district of Naples was one such creation, used for burials from the late fourt...
04:35
Re: IPv6 and Route of Death Open Source Security
Posted by Erik Auerswald on May 17
Hi all,It also mentions that "the bug patch didn't solve the underlying problem
(ZDI confirmed this too), so we're still expecting another patch at
some[ ]point."
The Zero Day Initiative (ZDI) entry[0] linked from the article[1]
gives a time line:
01/26/22 ZDI reported the vulnerability to the vendor.
[...]
04/14/23 The vendor informed the ZDI that a new patch would merge
into the latest mainline on...
04:30
Util-linux 2.39 released LWN.net
Version 2.39 of the util-linux tool collection has been released. The most significant change, perhaps, is support for the new filesystem-mounting API, which enables a number of new features, including ID-mapped mounts.
04:19
[$] FUSE passthrough for file I/O LWN.net
There are some filesystems that use the Filesystem in Userspace (FUSE) framework but only to provide a different view of an underlying filesystem, such as different file metadata, a changed directory hierarchy, or other changes of that sort. The read-only filtered filesystem, which simply filters the view of which files are available, is one example; the file data could come directly from the underlying filesystem, but currently needs to traverse the FUSE user-space server process. Finding a way to bypass the server, so that the file I/O operations go directly from the application to the underlying filesystem would be beneficial. In a filesystem session at the 2023 Linux Storage, Filesystem, Memory-Management and BPF Summit, Miklos Szeredi wanted to explore different options for adding such a mechanism, which was referred to as a "FUSE passthrough"though "bypass" might be a better alternative.
03:41
Mitra Lavasani, Director of the Translational Cell Therapy Lab, joins our Life Extension Board. Lifeboat News
Mitra Lavasani, Director of the Translational Cell Therapy Lab, joins our Life Extension Board.
03:35
This Is an Invasion of America Michael Yon at the U.S. Border cryptogon.com
This was posted by reader NH in a comment on, El Paso: Border Patrols Central Processing Center Six Times Maximum Capacity. I thought it was worth a dedicated post. Via: Redacted:
03:20
New Epstein Papers Reveal Targeting of Children for Medical Experiments, Artificial Intelligence Research cryptogon.com
Via: Redacted: Related: Jeffrey Epstein Moved Money For Noam Chomsky, Paid Bard President Botstein $150,000
03:16
Re: IPv6 and Route of Death Open Source Security
Posted by Solar Designer on May 17
Hi Jeffrey and all,The "original writeup" you reference says this is CVE-2023-2156.
Thank you for bringing this to oss-security.
I'd appreciate it if you and/or others also post plain text extracts of
such content, not only the links. Anyone willing to do it this time?
Also, this list isn't only about Linux, so when posting about
Linux-specific issues let's state so in the Subject line. In this case,
the issue is...
03:06
Don't Mess With Texas' Anti-SLAPP Law Deeplinks
Update 5/18/23: News reports indicate that this bill's language has also been added to a separate bill, Texas House Bill 3129. Texas lawmakers should vote no.
Over the past few decades, weve seen the rise of civil lawsuits that are meant to harass and silence defendants, rather than resolve legitimate disputes. These lawsuits have become known as Strategic Lawsuits Against Public Participation, or SLAPPs.
Some states legislatures, including California and Texas, have taken action to protect everyday peoples First Amendment rights by passing anti-SLAPP laws. These laws limit invasive discovery while a judge first determines if a case qualifies as a SLAPP. If it is a SLAPP, it can be thrown out quickly and, depending on the law, the person or company who filed the SLAPP can be made to pay legal fees of the party they sued. Anti-SLAPP laws have proven to be crucial tools in vindicating the rights of everyday people to speak out on issues of public concern.
Right now, key Texas lawmakers are pushing forward with an unnecessary bill that would make a mess of Texas anti-SLAPP law, the Texas Citizens Participation Act, or TCPA. The TCPA was already slightly weakened in 2019; EFF opposed those changes too. This time, its worse.
Keep Free Speech Protections In Texas Courts: Oppose S.B. 896
Texas anti-SLAPP law helps everyday people who speak out about matters of public concern. The law protects you if you complain about a local restaurant, contractor, or real estate development project, for instance, and then are sued for defamation or something even more vague, like having your activism deemed a RICO conspiracy. Currently, you can file an anti-SLAPP motion, the case is automatically stayed until a judge decides whether its a SLAPP suit or not. If it is, the case gets thrown out, and the SLAPP victim gets their legal fees paid by the other side.
The Texas bill currently being debated, S.B. 896, would change all that. Instead of simply having the judge decide about the SLAPP issue, there would be a debate about whether the motion fits into one or more exemptions, or whether the anti-SLAPP motion was filed in a timely way.
These changes will open up several loopholes and make it increasingly difficult to protect peoples speech. The issue of whether a Texas anti-SLAPP motion was timely is highly subjectiv...
02:06
New Findings Indicate Gene-Edited Rice Might Survive in Martian Soil SoylentNews
New Findings Indicate Gene-Edited Rice Might Survive in Martian Soil:
As outlined in the team's abstract, Rice Can Grow and Survive in Martian Regolith with Challenges That Could be Overcome Through Control of Stress-Related Genes, one of the biggest challenges to growing food on Mars is the presence of perchlorate salts, which have been detected in the planet's soil and are generally considered to be toxic for plants.
The team was able to simulate Martian soil using basaltic rich soil mined from the Mojave Desert, called the Mojave Mars Simulant, or MMS, which was developed by scientists from NASA and the Jet Propulsion Laboratory.
The teams then grew three varieties of rice, including one wild-type and two gene-edited lines with genetic mutations that better enable them to respond to stress, such as drought, sugar starvation or salinity. These varieties were grown in the MMS, as well as a regular potted mix and a hybrid of the two. While plants were able to grow in the Martian simulant, they were not as developed as those grown in the potting soil and hybrid mix. Replacing just a quarter of the Martian simulant with potting soil resulted in improved development.
The team also experimented with the amount of perchlorate in the soil, finding that 3 grams per kilogram was the threshold beyond which nothing would grow, while mutant strains could still root in 1 gram per kilogram.
Their findings suggest that there might be a way forward for genetically modified rice to find purchase in Martian soil.
Read more of this story at SoylentNews.
00:16
Melbet India
At this web site, it is feasible for you to to get pleasure from a easy registration course of. The on-line gambling platform has advanced quickly in the earlier few years. MelBet is one of the multi-platform websites that will offer you totally different choices.
Unfortunately, because of Google Plays coverage against using any betting apps, Melbet customers will be unable to download the app instantly from there. But the developers of Melbet have found a way out of this case. They developed the Melbet apk specifically in order that users can obtain it and install it on any of their gadgets. Melbet offers presents upon registration, consolation bonuses, tournaments for gamers, and much more. Temporary promotions are located within the part of the same name, everlasting ones are in the More section. Yes, Melbet takes the security and security of its players significantly and implements numerous measures to protect players personal and financial info.
Everyone will be succesful of select for themselves the quickest and most handy way. For example, you need to use your phone number, e-mail handle, or even social media. In any case, Melbet India registration wont take you a lot time.
The odds might be multiplied, growing the potential winnings. But to get the money, all predictions have to be played. If at least considered one of them is incorrect, you lose your wager. When making a deposit, the funds are deposited immediately. Withdrawal takes completely different instances relying on the amount and selected fee system.
You will obtain a confirmation email or SMS with a verification hyperlink or code. Follow the instructions offered to verify your account. You can watch any match you want utilizing reside streaming. And for a extra accurate prediction, you can use real-time statistics. Open the registration form and enter the code word in the Enter promo code field.
As with most bookies obtainable in India, the main focus is on cricket betting, however lovers of other sports activities mustnt worry as a outcome of theyre additionally properly catered for. Click on the withdraw button and as long as youve accomplished all wagering requirements if a bonus was claimed, you should obtain your funds inside the specified times. Choose the tactic of the Melbet withdrawal and enter the amount that you simply wish to withdraw. When this step has been accomplished, a new window will appear which displays your new username and password with the choice of getting these particulars emailed to you. Yes, together with many well-liked currencies, Indian rupees can be found in Melbet.
You get a certain cashback proportion at every of them from 5% to 11%. The money is credited to your account weekly for any bets or deposits. Registration is only available for individuals of authorized gambling age and requires personal information and a sound e-mail handle. As a new...
00:15
Melbet Registration Bangladesh With Bonus Ten Thousand Bdt h+ Media
Melbet Registration Bangladesh With Bonus Ten Thousand Bdt
This shows the digital development of the platform. You have loads of decisions for on-line sports activities as well. Depends Internet connection. If you could have a not stable one, you may have problems with gambling as nicely. Still, the developers did not create an software for something. There are some cons of Melbet that do not appear on the app.
This is a Sponsored Post printed as offered and UdaipurTimes does not endorse any info offered on this post. This game involves an element of economic danger and could also be addictive. Please select a 300% welcome incentive and put the low cost code in .
Its essential to notice that every one payments should be made in local currency . The minimum deposit quantity at MelBet com is 1 Bangladesh Taka whereas the maximum withdrawal quantity is 200 Bangladeshi Taka per transaction. Melbet offers a beneficiant welcome bonus for brand spanking new customers who register and make their first deposit. This bonus is designed to provide customers a head begin on their betting and gaming journey on the platform.
Thats why the streaming function stays essential in addition to live stats and different growing knowledge. The MelBet app may be very delicate and optimized for mobile use. It is designed for mobile video games, as it is user-friendly and very simple to use on the highway. Also, its not too late, nevertheless it works fast, especially with a fast web connection. The time depends on the withdrawal technique you might be using. Most Melbet withdrawal strategies are very quick and processed within quarter-hour to 24 hours.
You can filter video games by 138 builders and 19 categories. The latter, nevertheless, wouldnt have the Hindi translation used in India, and their names are mentioned in English. Melbet login through an app is there for each the app customers. The android and iOS users can have a benefit from the app.
This bookmaker uses SSL encryption to guard knowledge. In addition, the company is dedicated to defending all buyer knowledge. Although the exercise of Melbet has been progressively launched in dozens of nations, it faces authorized restrictions in some nations.
If you have a Melbet promo code, enter it into the corresponding area and end your registration. For these with Android units, Predictor Aviator is available as a helpful app. Playing the Aviator game increases the planes velocity and the amount of cash you receive.
Dont forget to use the promo code on the signup page. Entertainment in this part shouldnt be confused with betting-type TV video games. In one case, we are talking about betting on the show, in the second about keno games and other video games that happen on-line instantly on the Melbet website. Melbet accepts several cryptocurrencies, together with Bitcoin...
00:15
Melbet Promo Code 2023 h+ Media
Melbet Promo Code 2023
MELbet, as properly as most international bookmakers settle for Indian Rupee transactions. There are many optimistic reviews about Melbet on the Internet. On the companys website, there is additionally an Online Consultant service. At the bottom of the display screen, you should put a tick within the box that confirms your acceptance of Melbets rules and their acceptance. We recommend you to read them because when you break these rules, your account can be blocked.
The replenishment of your recreation steadiness by utilizing a cell phone may be accomplished via a personal account. If youre an Indian participant is trying to perform transactions using a special nation, Melbet offers him this chance too. We impose a quantity of situations that must be respected by anybody who needs to complete the Melbet enroll process on our website. Tick the packing containers and make sure that you have learn the Terms and Conditions and Privacy Policy and are legally allowed to register a Melbet account.
The Live Chat button is positioned in the lower right nook. Therefore, at any time you presumably can ask a question that interests you. It should be noted that Melbet.com is the official information companion of the Spanish La Liga. Melbet was based in 2012, has an Eastern European origin and a Curacao license.
Even on the Melbet app, youre unlikely to miss out on any of the top features obtainable from the brand. The company is not stingy with bonus presents and promotions. Some bonuses from the Melbet operator are activated after depositing, and others are supplied for participation in tournaments or totalizers. In addition, the bookmaker can send a player a promo code for a free guess anytime. Bookmaker Melbet attracts the attention of players from completely different countries, including Indian bettors.
Everything is ready, now you should automate if you have already got a recreation account, or create a new one. Create an Melbet new ID account with Melbet, select the deal from the drop-down menu, after which make your preliminary deposit. If you place a wager of 10 or more on horse racing, youll earn 30 in free bets along with a 10 slots bonus. The live casino part can be out there at Melbet India. Users favor to play live roulette, blackjack, and different games at Melbet reside casino.
- Once the payment is successfully processed, your funds shall be mechanically added to your Melbet account and can be used by you immediately.
- The major web page accommodates columns with occasions, tables, advertising widgets, registration and login buttons.
- If users are not significantly keen on T20 cricket however nonetheless need to go forward with the older versions of the sport, Melbet is roofed on this regard as properly.
- Go to the official internet page or open the application.
- If you dont place bets incessantly, you are...
00:13
Melbet Casino Review
With live on line casino video games like Roulette, Blackjack, Poker and Baccarat being continually obtainable, relaxation assured, youll by no means really feel bored here at Melbet. There is also an unique Russian Roulette for gamers to explore. Live casino and reside supplier casinos let you really feel like you would possibly be in a real casino. Real-time betting on casino games corresponding to on-line roulette, on-line blackjack, on-line roulette, online baccarat, online bingo and on-line slots. The catalogue contains games from acknowledged suppliers of the international gaming and betting market. With glorious customer support and a user-friendly interface, 7Cric is the best on-line casino website for Indian players whore on the lookout for a top-notch gambling expertise.
This bookmaker uses SSL encryption to protect knowledge. In addition, the company is dedicated to protecting all buyer data. Although the exercise of Melbet has been steadily launched in dozens of nations, it faces authorized restrictions in some countries.
Next, within the particular window, youll, in fact, want to pick your nation of residence from the listing. Choose any social network or messenger you want to link to your account. After that, youll have to come up with a powerful password, enter it, after which repeat it within the subsequent field. Also, in the next two packing containers, youll need to enter your real name and surname. In the following merchandise, you should enter your cellular number. In the following point, you will need to pick your metropolis of residence from the list, corresponding to Dhaka, Khulna, and others offered.
Given the beneficiant welcome bonus, youll have the opportunity to extend your capital. With this in mind, we recommend that you just go to the official website and use the one-click registration to verify the information offered your self. You can also use the demo mode to test on line casino games. Offers a handy and safe course of for its users, ensuring that entry to the platform is quick and simple, while also sustaining the best ranges of safety. The login course of is easy and easy, requiring only a username and password to entry the platform.
Moreover, its not attainable to withdraw money to accounts that do not belong to the account holder. Melbet provides a self-test questionnaire as well for customers to assess if their spending goes out of hand. Please make certain to ask your self these questions every so often to play protected and addiction-free. Once youre a registered consumer, there is absolutely no restrictions while putting a guess on soccer, tennis or horse racing. With glorious odds and well timed payouts for over 40 sports activities masking over 1500+ tournaments taking place the world over, you truly cant ask for extra. Across all platforms, the deposits are all instant.
...
00:12
Melbet India
Almost any sort of wager is accepted at Melbet Sportsbook. There are the standard level spreads, totals, money traces, free bets, and futures bets, as properly as much less frequent options like substitute traces and in-play bets. Every wager placed on the website features a live betting ticket system, enabling customers to withdraw their winnings during nearly any sporting event. Therefore, if a recreation is won, the bettor could possibly money out all or a portion of their winnings early. The video slots in Melbets gaming lobby include basic games, jackpot slots, and well-known video games. Of course, deciding on the top-rated video games will help you make a sensible decision.
For account creation, You can have four methods to strive this the phone quantity, one-click, by e-mail, by way of social community. Not solely that, in addition, however you may also even get to know extra in regards to the provides, app particulars and far more. As you presumably can see, its very easy and easy, plus the Melbet app shall be a great system so that you can use at any time to place bets or play on line casino games. If you wish to know extra in regards to the Melbet app, you can read our article of the identical name.
At 7Cric, were dedicated to making positive that our web site is the go-to alternative for Indian gamers. Besides, responsive live chat and a handy contact type to submit a request are available on the sports betting and on line casino website. While betting on various on line casino titles, you will find lucrative live on line casino presents from Evolution Gaming and different software providers.
MelBet is a secure and secure website, reliably encrypted and guarded. The operator by no means shares user data and cares about its friends privateness. You may count on discreet gambling, assured withdrawals, and prompt buyer assist. Although the platform appears very attractive, a query like MelBet is actual or fake? You can safely play video games and place real-money bets. The operator is a 100% legit firm launched in 2012 by Pelican Entertainment B.V., licensed in Curacao.
All it takes is giving us slightly data like what state or nation you reside in and a few primary contact data. A bettor and handicapper who makes a speciality of IPL contest. Worked as lead sports betting analyst for Pickswise. Since Andrew is with our group, he passionately talks about cricket and doesnt cease to share his love for the sport, and attracts increasingly individuals to it. After a successful registration, you will want to prime up your private account with some actual money.
- Then it is possible for you to to launch the appliance by way of a shortcut on your desktop.
- Once you present the sportsbook with the required paperwork as properly as your mobile quantity, you are good to go, most likely within the next 24 hours.
- It is impossible to imagine the...
00:11
Melbet Registration And Account Verification In Bangladesh h+ Media
Melbet Registration And Account Verification In Bangladesh
The bookie could be very a lot targeted on securing the web betting market in India. Though it began in 2012 it started its operations in India extra intensively just in latest times. In the below, we focus on the Melbet login, sign up course of in India and the way the melbet login via app works and extra. Its essence may be very easy a shopper of the bookmakers company receives promo points for each bet in any of the video games. As quickly as they have accumulated the required number, exchanging them at no cost bets is feasible. Of course, the player chooses in which sport to use the present.
- MelBet Indian betting from smartphones and tablets is possible directly by way of cellular browsers.
- The platform is easy to use even for somebody new to the online gambling area.
- Every time you begin the consumer, it mechanically checks for updates.
- This site offers three various sorts of bets with just one approach to accumulate.
- In the very first window, you have to enter your mobile phone quantity after selecting the world code.
You shall be redirected to the App Store, where you can obtain the app free of charge. After that, you should use all the features of Melbet bookmaker at any time and in anywhere. Roulette is one other classic casino sport that is simple to be taught however difficult to master.
The bottom of the bet slip will display the minimal and maximum stakes that can be utilized in your alternatives. If multiple choices have been added to the bet slip, a drop-down menu will state the various varieties of bets that can be placed, multiple bets, system bets and so forth. Placing a Melbet sports guess simply requires you to decide on the selection or choices that you just wish to place a guess on and click on the odds. One indicator or a great bookie is the selection of betting markets that they have for every explicit sporting occasion. The Melbet sign-up bonus is a one hundred pc matched offer as a lot as 8000 INR.
Knowing concerning the worries of their purchasers, Melbet all the time pays attention to the model new developments within the subject of cybersecurity. Currently, all knowledge on the web site and platform is protected by one of the best cryptographic protocols. Thats why as lengthy as you dont give your account particulars to anyone, your personal info will be completely secure.
Since that point, the service has been growing and getting increasingly clients. Now, it is among the most recognized providers in the world. The service operates in forty-five languages that making its clientele worldwide.
The company is forced to provide gamers higher odds with low margins in order to appeal to gamers from well-known bookmakers. So, for example, on the matches of the ultimate collection of the NBA playoffs, the margin was 3-4% this is incredibly small. To get entry...
00:10
Melbet Registration & Login h+ Media
Melbet Registration & Login
You can deposit cash into your account utilizing quite lots of methods, together with credit/debit playing cards, e-wallets, and even cryptocurrency. The minimum deposit amount is just 1 USD, whereas the utmost deposit quantity is determined by your methodology. All new gamers at Melbet can reap the advantages of beneficiant welcome bonuses after they join and make their first deposit. Volleyball is one other trendy sport amongst Melbet customers. This could be explained by the reality that this discipline is consistently gaining recognition worldwide. This makes betting on volleyball even more interesting and exciting.
The user will be prompted to enter their password, which they created in the course of the registration process, in the acceptable area. Melbet provides a comprehensive vary of providers and features for its users, together with a secure and user-friendly system. Melbet India Bookmaker is considered one of the leading sports activities betting sites within the nation. It is a popular platform for many who are excited about inserting their bets on basketball. Melbet india users can place their bets on basketball matches and champions, stay scores and points, or they could select to make an accumulator guess with different occasions. The website offers a big variety of markets that assist its users earn more money after they win their wagers.
Melbet has so much to offer, and it is due to this that this platform deserves the attention and time of users. Despite the truth that the company continues to be very young, it does not stop it from combating for the main place on the planet of online betting. Today, it is amongst the main sports betting companies in India, where tens of millions of gamers started earning cash with the bookmaker that continues its work till this day. If you get pleasure from inserting bets on sporting events as they are happening, then Melbet is certainly the right bookmaker for you. They offer an excellent reside betting platform with numerous markets and interesting proposition bets out there.
In order to offer the documentation, the gambler might need to take a picture of it and connect it to the box on the web site. The top a half of the registration kind will include the strategies of registration. A potential Melbet buyer has to choose one of the choices supplied. Account verification is critical to check the consumer for the authenticity of the entered information.
You also can use the self-exclusion feature to freeze your account to be able to take a break from gambling for an indefinite amount of time. Traditional on line casino video games such as Blackjack, Baccarat, Roulette, and so on. All games are verified and developed by trusted builders similar to Asia Gaming, GamePlay, and so on. Melbet presents shoppers from India with a nice service throughout all areas such as money transfers. The better part about finishing the Melb...
00:09
Aviator Predictor V1 94 Apk Mod 2023 Free Download Iphone h+ Media
Aviator Predictor V1 94 Apk Mod 2023 Free Download Iphone
However, the processing time for most withdrawal requests is often within 24 hours. It is important to note that each one promotions and bonuses offered by Melbet include terms and conditions. Customers are advised to carefully learn and understand the terms and conditions earlier than collaborating in any promotion or claiming any bonus. Additionally, promotions and bonuses could have completely different eligibility criteria and necessities, similar to minimal deposit quantities or particular betting requirements.
The odds are fairly good, so youve a chance to make respectable income. Melbet offers promo codes with which you can make free bets, get deposit bonuses, free spins, and more. The Bonus for 100 Bets promotion is designed for normal customers of the Melbet bookmaker.
You shall be redirected to the App Store, the place youll have the ability to download the app at no cost. After that, you can use all of the capabilities of Melbet bookmaker at any time and in anywhere. Roulette is another traditional casino game that is straightforward to study but difficult to grasp.
You may rest assured figuring out the positioning encrypts your personal information, and all deposit and cash-out transactions. Indian players today are tremendous demanding regarding the choice of bookies. And, there is a simple clarification behind that an array of sports activities betting sites exist, but a few of them scam. If you may be on the path of selecting a reliable bookie, with no signs of rigging but legitimate licenses, Melbet registration is a go-choice. You will have the ability to get from 20 Free Spins on any online casino slots. Registration within the Melbet utility can be not difficult.
To do that, you have to present personal information, in addition to details about essentially the most convenient payment system for you. The info provided must be accurate in order for us to offer a withdrawal of funds. Bookmaker MelBet is the subsequent hottest bookmaker after X. Increasingly, users are choosing the convenient and fast access. To do that, its proposed to obtain Melbet app for Android and use the whole service in a compact, but no less handy, cell kind. Unfortunately for iOS users, positioning.
Melbet India presents a broad variety of generous bonus and promotional offers to its members. Yes, Melbet runs in India with Curacao Gaming Authority permission, which allows it to concurrently provide sports betting and casino video games on its site. Melbet is a on line casino and betting firm established in Cyprus that has been growing in recognition over the last several years. The web site caters to all types of sports gamblers, however we consider live betting is where they actually shine, with hund...