| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Monday, 29 May
01:45
Linux 6.4-rc4 Released As A "Fairly Normal" Release Phoronix
Due to Linus Torvalds traveling over this US Memorial Day weekend, he released Linux 6.4-rc4 about twelve hours ahead of schedule...
01:37
Vulkan 1.3.251 Released With One New Extension Worked On By Valve, Nintendo & Others Phoronix
Vulkan 1.3.251 is out today as a rare Sunday morning spec update for this Khronos graphics/compute API...
00:26
Radical new Flying-V plane aims to transform flight Lifeboat News: The Blog

The Flying-V airplane doesnt look like anything youll find at todays airports, but it could be the future of aviation.
00:26
This New Hypersonic Space Plane Can Get You From New York to London in One Hour Lifeboat News: The Blog
On Tuesday, the CEO of the UK Space Agency Graham Turnock announced the UK would be working more closely with Australia in a world-first Space Bridge agreement which will focus on delivering a planeor rocket, reallyto shuttle passengers from continent-to-continent in just four hours. While flights from London to the Big Apple will reportedly take a skerrick over 60 minutes.
Its all courtesy of a new hypersonic engine SABRE (Synergetic Air-Breathing Rocket Engine)which the scientists at Reaction Engines are currently developing. Fueled by a combination of hydrogen and oxygen, SABRE is capable of powering a plane to Mach 5.4 (4,000 mph) for speedy commercial travelthats around five times the speed of soundor Mach 25 (19,000 mph) when soaring in space. Its supposedly greener and cheaper than current air travel, too.
00:26
Blood Test #3 in 2023: Supplements, Diet Lifeboat News: The Blog
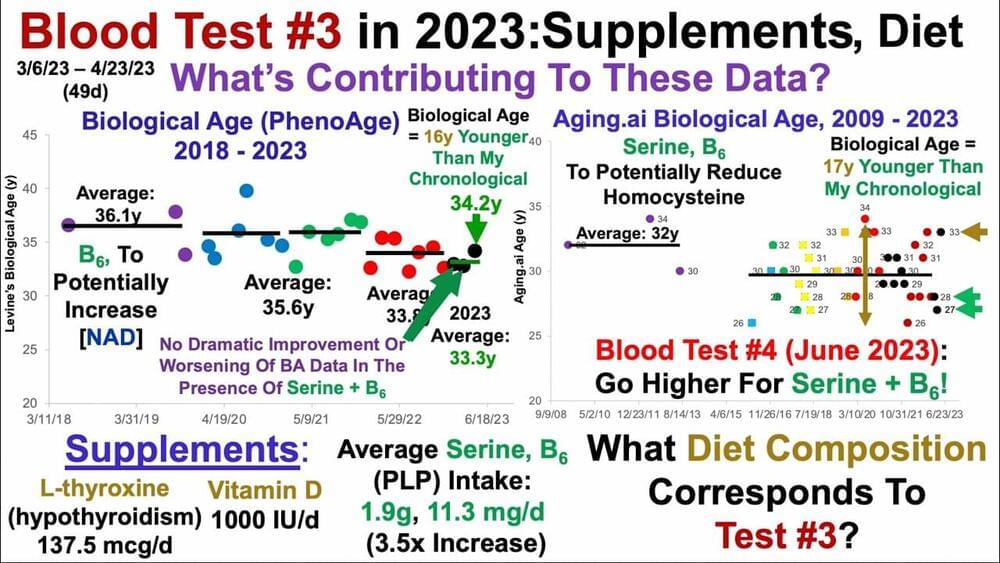
Join us on Patreon! https://www.patreon.com/MichaelLustgartenPhD
Discount Links:
At-Home Metabolomics: https://www.iollo.com/?ref=michael-lustgarten.
NAD+ Quantification: https://www.jinfiniti.com/intracellular-nad-test/
Use Code: ConquerAging At Checkout.
Green Tea: https://www.ochaandco.com/?ref=conqueraging.
Oral Microbiome: https://www.bristlehealth.com/?ref=michaellustgarten.
Enter Code: ConquerAging.
Epigenetic Testing:
https://trudiagnostic.com/?irclickid=U-s3Ii2r7xyIU-LSYLyQdQ6M0&irgwc=1
Use Code: CONQUERAGING
00:24
Solving problems is better than fearmongering Lifeboat News: The Blog
W elcome to the TechCrunch Exchange, a weekly startups-and-markets newsletter. Its inspired by the daily TechCrunch+ column where it gets its name. Want it in your inbox every Saturday? Sign up here.
From cybersecurity to SaaS for restaurants, the key to running a successful business is selling a product that solves your clients real problems. Anna
2022 in cybersecurity.
00:24
AI is here to stay; its time to update your HR policies Lifeboat News: The Blog
The widespread use of advanced artificial intelligence tools like ChatGPT means the rapidly developing technology is being used in workplaces across the country whether employers are aware of it or not.
So, for companies that have not yet developed ground rules for AI use, youre being put on alert: Its time to update your employee handbook, an human resources expert says.
Jennifer Morehead, owner and CEO of Flex HR, which handles outsourced human resources services for major firms like Harley-Davidson and Kimberly Clark, says there are an array of issues AI firms need to consider now that the tools are becoming increasingly accessible in the workplace.
00:24
A potential cure for diabetes found in human stomach cells Lifeboat News: The Blog
The ability to acquire gut stem cells via biopsy and have a significant proliferative capacity in culture make them an invaluable resource for autologous cell treatments. In the mouse gut, insulin-producing cells can be produced. Still, human gut tissues have not been able to produce an abundance or durability of insulin-secreting cells to assess their potential as a cell treatment for diabetes.
In a new study, scientists from Weill Cornell Medicine showed that stem cells from human stomach can be converted into insulin-secreting cells. Scientists demonstrated that they could obtain the stem cells from the human stomach and reprogram them directlywith strikingly high efficiencyinto cells that closely resemble pancreatic insulin-secreting cells known as beta cells.
In experiments on a mouse model, this approach reversed disease signs. According to scientists, the study offers a promising approach, based on patients cells, for type 1 diabetes and severe type 2 diabetes.
00:24
Stephen Hawkings last collaborator on physicists final theory Lifeboat News: The Blog
When Thomas Hertog was first summoned to Stephen Hawkings office in the late 1990s, there was an instant connection between the young Belgian researcher and the legendary British theoretical physicist.
Something clicked between us, Hertog said.
That connection would continue even as Hawkings debilitating disease ALS robbed him of his last ways to communicate, allowing the pair to complete a new theory that aims to turn how science looks at the universe on its head.
00:23
Exclusive: Chandrayaan-3 spacecraft arrives at Indias spaceport in preparation for July launch Lifeboat News: The Blog
The spacecraft that the Indian Space Research Organization (ISRO) hopes to land on the moon later this year, has been wheeled into the countrys spaceport, Satish Dhawan Space Centre, WION has learnt.
Named as Chandrayaan-3 (Sanskrit for Moon Vehicle-3), this will be Indias third lunar mission and will attempt both controlled soft-landing on the lunar surface and in-situ analysis by the means of a rover.
In the evening hours on Friday, the slow-moving, specialised truck ferrying the spacecraft from UR Rao Satellite Centre in Bengaluru arrived at Indias spaceport, under a security blanket.
00:23
Wendys Automates Drive-Thru With Googles Order-Taking AI Chatbot Lifeboat News: The Blog
The chain says its trying to speed up the drive-thru to squeeze in a few extra sales each day.
00:03
Kernel prepatch 6.4-rc4 LWN.net
The 6.4-rc4
kernel prepatch is out for testing, a few hours earlier than usual.
"Other than that timing change, things look fairly
normal
".
00:00
AI Creates Killer Drug Hackaday

Researchers in Canada and the United States have used deep learning to derive an antibiotic that can attack a resistant microbe, acinetobacter baumannii, which can infect wounds and cause pneumonia. According to the BBC, a paper in Nature Chemical Biology describes how the researchers used training data that measured known drugs action on the tough bacteria. The learning algorithm then projected the effect of 6,680 compounds with no data on their effectiveness against the germ.
In an hour and a half, the program reduced the list to 240 promising candidates. Testing in the lab found that nine of these were effective and that one, now called abaucin, was extremely potent. While doing lab tests on 240 compounds sounds like a lot of work, it is better than testing nearly 6,700.
Interestingly, the new antibiotic seems only to be effective against the target microbe, which is a plus. It isnt available for people yet and may not be for some time drug testing being what it is. However, this is still a great example of how machine learning can augment human brainpower, letting scientists and others focus on whats really important.
W...
Sunday, 28 May
22:45
New Bandit Stealer targets web browsers and cryptocurrency wallets Security Affairs
Bandit Stealer is a new stealthy information stealer malware that targets numerous web browsers and cryptocurrency wallets.
Trend Micro researchers discovered a new info-stealing malware, dubbed Bandit Stealer, which is written in the Go language and targets multiple browsers and cryptocurrency wallets.
At this time, the malware only targets Windows systems, but experts pointed out that it has the potential to expand to other platforms because it is written in Go.
The malicious code relies on the Windows command-line utility program runas.exe to run programs as a different user with different permissions.
Using the tool, the malware elevates the users privileges and executes itself with administrative access without being detected. However, Trend Micro states Bandit Stealer is failing to use the tool because they need to provide the appropriate credentials.
Bandit Stealer performs some checks to determine if its running in a sandbox environment or testing environment.
The malware then terminates blacklisted processes associated with anti-malware solutions.
The Bandit Stealer maintains persistence by using an entry for autorun in Windows Registry.
The info-stealer collects a broad range of information and stores it in the vicinfo folder in <C:\Users\<Username>\AppData\Local\>.
Additionally, the malware scans for specific browser extensions associated with cryptocurrency wallets by checking the path of the browser extensions. reads the report published by Trend Micro.

Bandit Stealer is also able to collect Telegram sessions to gain unauthorized access, allowing impersonation and malicious actions such as accessing private messages and data associated with the compromised account
The information-stealing malware might have been downloaded by users while visiting malicious web...
22:37
Links 28/05/2023: eGates System Collapses, More High TCO Stories (Microsoft Windows) Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Digital Restrictions (DRM)
- Monopolies
-
GNU/Linux
-
Applications
-
Linux Links 7 Best Free and Open Source Linux Anti-Spam Tools
There are a number of technique...
-
-
22:11
Linux Lands Fix For Potentially Bogus Number Of Intel Hybrid CPU HT Siblings Phoronix
A few days ago I wrote about a Linux kernel patch being prepared for fixing Intel hybrid CPU SMP/HT topology reporting due to the way the Linux kernel was currently counting the number of Hyper Threading siblings for each core. Fortunately, that fix which is apparently becomes more pressing for upcoming Meteor Lake processors, has now been picked up in time for today's Linux 6.4-rc4 release and is set for back-porting to stable kernel series...
21:59
New versions of LibreSSL released OpenBSD Journal
The LibreSSL project has announced the release of versions 3.6.3 and "https://ftp.openbsd.org/pub/OpenBSD/LibreSSL/libressl-3.8.0-relnotes.txt"> 3.8.0 of the software.
The announcement for versions 3.6.3 and 3.7.3 reads:
We have released LibreSSL 3.6.3 and 3.7.3, which will be arriving in the LibreSSL directory of your local OpenBSD mirror soon. They include the following fixes: * Bug fix - Hostflags in the verify parameters would not propagate from an SSL_CTX to newly created SSL. * Reliability fix - A double free or use after free could occur after SSL_clear(3). The LibreSSL project continues improvement of the codebase to reflect modern, safe programming practices. We welcome feedback and improvements from the broader community. Thanks to all of the contributors who helped make this release possible.
21:23
US Govt Under Fire for Promoting Sales of Spyware SoylentNews
Uncle Sam confirms it's saying nothing:
The US International Trade Administration (ITA) has admitted it promotes the sale of American-approved commercial spyware to foreign governments, and won't answer questions about it, according to US Senator Ron Wyden (D-OR).
Wyden, in a letter to US Commerce Secretary Gina Raimondo, has demanded answers about the surveillance and policing tech that ITA a US government agency pushes to other countries. And he wants the agency to name names when it comes to which companies' spyware is being promoted with US tax dollars.
ITA is housed within the US Commerce Department and tasked with promoting American exports. Wyden chairs the Senate Finance Committee, which has responsibility for international trade policy, and he's not happy.
The senator first requested info from ITA about promoting spyware abroad in May 2022. At that time, the agency confirmed it had promoted this type of technology, but it didn't answer questions about which products it endorsed and in which markets.
Both of these things are problematic. Commercial spyware has historically been used to target activists, journalists, and political dissidents, and when it ends up in the hands of authoritarian regimes, these people can end up dead.
Read more of this story at SoylentNews.
21:22
Researchers develop calcium metal battery with long cycle life Lifeboat News: The Blog
As potential alternatives to lithium-ion batteries, rechargeable calcium (Ca) metal batteries offer advantageous features such as high energy density, cost-effectiveness, and natural elemental abundance. Its properties are also thought to help accelerate ion transport and diffusion in electrolytes and cathode materials, giving it an edge over other lithium-ion battery alternatives such as magnesium and zinc.
However, many challenges impede the development of practical Ca metal batteries. The challenges include the lack of an efficient electrolyte and the absence of cathode materials with sufficient Ca2+ storage capabilities.
Now, Tohoku University researchers have developed a prototype calcium metal rechargeable battery capable of 500 cycles of repeated charge-discharge the benchmark for practical use.
21:00
Math Reveals How Many Shuffles Randomizes a Deck Hackaday

Math and some clever simulations have revealed how many shuffles are required to randomize a deck of 52 cards, but theres a bit more to it than that. There are different shuffling methods, and dealing methods can matter, too. [Jason Fulman] and [Persi Diaconis] are behind the research that will be detailed in an upcoming book, The Mathematics of Shuffling Cards, but the main points are easy to cover.
20:20
Wine-Staging 8.9 Ships With The Very Latest VKD3D Code Phoronix
Following the release of Wine 8.9 on Friday for enabling Windows games and applications to run on Linux, Wine-Staging 8.9 is now available for this more testing/development-focused flavor of Wine that more liberally picks up in-development patches...
18:00
3D Printing Bores Without Support Hackaday

If youve done even a small amount of 3D printing, you probably ran into the challenge of printing a small hole on top of a larger hole. The conventional solution is just to add support, but in the video after the break, [Angus] of Makers Muse demonstrates an alternative solution you can implement in CAD, without having to do manual post-processing.
This is a common problem when you have a countersink feature for a bolt head or captured nut on the bottom of the part. [Angus] first demonstrates some other techniques, including printing the bore over empty space, adding a sacrificial bridge, and making the overhang 45. Each of these work but have some trade-offs. The proposed solution is what [Angus] calls sequential overhangs. It involves bridging the sides of the open space in steps to create supporting edges onto which the bore perimeter can print. It starts with 2 or 3 bridging layers to create a rectangle the same width as the bore, and then a second set of bridges at 90 to turn...
18:00
Week in review: Zyxel firewalls vulnerability, phishing campaign targets ChatGPT users Help Net Security
Heres an overview of some of last weeks most interesting news, articles, interviews and videos: Wireless Broadband Alliance CEO on key drivers for Wi-Fi adoption in enterprise networks This Help Net Security interview with Tiago Rodrigues, CEO at Wireless Broadband Alliance (WBA), delves into the future of enterprise networking, exploring the significant role of Wi-Fi 6E and Private 5G. Navigating the quantum leap in cybersecurity In this Help Net Security interview, we sit down with More
The post Week in review: Zyxel firewalls vulnerability, phishing campaign targets ChatGPT users appeared first on Help Net Security.
17:36
IRC Proceedings: Saturday, May 27, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-270523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-270523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-270523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-270523.gmi
Over HTTP:
|
... |
16:41
Teens in Australia Talk About How to Fix School Sex Education SoylentNews
'We haven't been taught about sex': Teens talk about how to fix school sex education:
Last week, the Albanese government announced an expert panel to support relationships and sexuality education in Australian schools.
The group is lead by the head of anti-violence organization Our Watch, Patty Kinnersly, and includes consent advocate Chanel Contos. It will do a "rapid review" into consent and respectful relationships programs to identify "opportunities for improvement."
This follows a new focus on consent and healthy relationships in Australian schools. The former Coalition government made consent a mandatory part of the curriculum.
We are talking to teenagers about the sex education they receive at schools. This research highlights several areas young people think can be improved. They are particularly concerned sex education most often does not discuss actual sex.
As part of broader, ongoing research into online sexual content, we interviewed 30 West Australian teens (aged 11-17), between 2021 and 2023, to explore their experiences of sex education and where they source information to answer their questions about sex and relationships.
Eighteen interviewees were followed up with 12 months after we had first spoken, to see if their perspectives had changed.
Interviews began as some schools started teaching consent in 2021, with sexual assault being widely debated in the wake of the women's March4Justice rallies around the country and a school sexual assault petition spearheaded by Contos. We have continued to gather young people's perspectives as consent education became mandatory at the start of this school year.
Read more of this story at SoylentNews.
15:13
No More Twitter, Mastodon, and Diaspora for Tux Machines (Goodbye to Social Control Media) Techrights
Just in time for the 19th anniversary of the site
Summary: People would benefit from mass abandonment of such pseudo-social pseudo-media.
THIS was only a matter of time. Yesterday was the last straw.
As we noted yesterday, Social Control Media including the supposedly ethical alternatives is utterly bad by design, maybe even by intention. Tux Machines has just exited social control media sites altogether. Please follow us using the RSS feed instead, readers were informed. Theres also XML/RSS for the Gemini capsule of Tux Machines. There are more details this new post over at Tux Machines. Were nowadays seeing many people who announce similar exits. In our latest Daily Links we included this one from Ruben. Some quit for technical reasons, some do so for political/ideological reasons, and sometimes its a combination of both. Lets make it trendy to quit those sorts of sites. People would benefit from mass abandonment of such pseudo-social pseudo-media.
14:17
CISA adds recently patched Barracuda zero-day to its Known Exploited Vulnerabilities catalog Security Affairs
US CISA added recently patched Barracuda zero-day vulnerability to its Known Exploited Vulnerabilities catalog.
US Cybersecurity and Infrastructure Security Agency (CISA) added a recently patched Barracuda zero-day vulnerability to its Known Exploited Vulnerabilities Catalog.
This week, the network security solutions provider Barracuda warned customers that some of its Email Security Gateway (ESG) appliances were recently breached by threat actors exploiting a now-patched zero-day vulnerability.
The vulnerability, tracked as CVE-2023-2868, resides in the module for email attachment screening, the issue was discovered on May 19 and the company fixed it with the release of two security patches on May 20 and 21.
Barracuda identified a vulnerability (https://nvd.nist.gov/vuln/detail/CVE-2023-2868) in our Email Security Gateway appliance (ESG) on May 19, 2023. A security patch to eliminate the vulnerability was applied to all ESG appliances worldwide on Saturday, May 20, 2023. reads the advisory published by the security solutions provider. The vulnerability existed in a module which initially screens the attachments of incoming emails.
The issue could have a significant impact because the impacted Email Security Gateway (ESG) appliances are used by hundreds of thousands of organizations worldwide, including several high-profile businesses.
The vulnerability doesnt impact other Barracuda products, the company states that its SaaS email security services is not affected by this issue.
The company investigated the flaw and discovered that it was exploited to target a subset of email gateway appliances. The company notified via the ESG user interface the customers whose appliances they believe were impacted.
According to Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities, FCEB agencies have to address the identified vulnerabilities by the due date to protect their networks against attacks exploiting the flaws in the catalog.
Experts recommend also private organizations review the Catalog and address the vulnerabilities in their infrastructure.
CISA orders federal agencies to fix this flaw by June 16, 2023.
Follow me on Twitter: ...
12:00
AI Image Generation Gets a Drag Interface Hackaday

AI image generators have gained new tools and techniques for not just creating pictures, but modifying them in consistent and sensible ways, and it seems that every week brings a fascinating new development in this area. ...
11:53
Hibernation Artificially Triggered in Potential Space Travel Breakthrough SoylentNews
If discovery is feasible in humans it could be used to send astronauts into suspended animation:
[...] In science fiction, space crews are often spared the boredom and inconvenience of long-distance space travel by being placed into a state of suspended animation. Now this goal may have come a step closer after scientists showed that hibernation can be artificially triggered in rodents using ultrasonic pulses.
The advance is seen as significant because the technique was effective in rats animals that do not naturally hibernate. This raises the prospect that humans may also retain a vestigial hibernation circuit in the brain that could be artificially reactivated.
"If this proves feasible in humans, we could envision astronauts wearing a helmet-like device designed to target the hypothalamus region for inducing a hypothermia and hypometabolism state," said Hong Chen, an associate professor at Washington University in St Louis, who led the work.
The team first identified a specific group of neurons in a deep brain region called the hypothalamus preoptic area, which were found to be involved in regulating body temperature and metabolism during hibernation. They showed that, in mice, these neurons could be artificially activated using ultrasound, delivered non-invasively through a helmet.
When stimulated, the mice showed a drop in body temperature of about 3C for about one hour. The mice's metabolism also shifted from using both carbohydrates and fat for energy to only fat, a key feature of torpor, and their heart rates fell by about 47%, all while at room temperature.
Read more of this story at SoylentNews.
11:48
Links 28/05/2023: New Wine and More Techrights
![]()
Contents
-
GNU/Linux
-
Instructionals/Technical
-
TecAdmin Setting Up Permissions in Home Directory on Linux
One of the fundamental aspects of system security and user privacy in any Linux or Unix-based operating system (OS) is the proper management of permissions. In these systems, a hom...
-
-
09:15
Debian 12.0's Installer Reaches RC4 Status Phoronix
The Debian 12 "Bookworm" release is quickly approaching with an early June release date while for helping facilitate more last minute testing is a fourth release candidate of the updated Debian Installer...
09:00
Headsets Poor Range Fixed By Replacing Antenna Hackaday

[rafii6312]s Corsair HS80 wireless headset had a big problem: short range. The sound quality was great, but the wireless range wasnt winning any friends. Fortunately, the solution was just to swap the small SMT antenna on the USB transmitter for an external one.
08:50
Security Affairs newsletter Round 421 by Pierluigi Paganini International edition Security Affairs
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are free for you in your email box.
Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press.
07:14
Hell Pizza Launches Buy Now, Pay Much, Much Later Payment Scheme SoylentNews
New Zealand's Hell Pizza has just launched their buy now, pay much, much later scheme. Later in this case meaning when you're dead:
AfterLife Pay will only be available to a select number of people: those who are selected will be invited to sign a real amendment to their wills, allowing the cost of their pizza to be collected upon death. No interest or fees will apply, and the agreement is legally binding, Hell said.
Hell CEO Benn Cumming said AfterLife Pay was born after they were approached by BNPL providers who wanted to offer the service to its customers.
"We're seeing a growing number of people using the schemes to buy essential items like food, and we think it's taking it a step too far when you've got quick service restaurants like ours being asked to offer BNPL for what is considered a treat - especially when you consider people are falling behind in their payments and 10.5 percent of loans in NZ are in arrears," Cumming said in a statement on Thursday.
AfterLife Pay will initially run as a trial, with anyone 18 years or older eligible to apply. Of the applicants, 666 people will then be selected. The offer has also been extended to 666 people in Australia.
Those who are selected will then sign a legally binding agreement online for the total of their chosen order.
Cumming said pizza is one of the simple joys of life, and AfterLife Pay means customers can get their fix without having to dip into the bank account immediately.
Read more of this story at SoylentNews.
06:41
A BitTorrent Client WebUI Shouldnt Be Shared With The Entire Internet TorrentFreak
 The
word open in a connected world can be something positive. Open
source, for example, or open library. On other occasions the
opposite can be true; unnecessary ports left open on a router
springs to mind.
The
word open in a connected world can be something positive. Open
source, for example, or open library. On other occasions the
opposite can be true; unnecessary ports left open on a router
springs to mind.
For millions of people using devices that appear to configure themselves, whether something is open or closed is irrelevant. If a device immediately works as promised, oftentimes thats good enough. The problem with some internet-connected devices is that in order to immediately work in the hands of a novice, security gives way to ease of use, and that can end in disaster.
Torrent Client WebUI
Many of todays torrent clients can be operated via a web interface, commonly known as a WebUI. A typical WebUI is accessed via a web browser, with the clients IP address and a specified port number providing remote access.
In a LAN environment (the part of a network behind the router, such as a home) the torrent clients web interface serves local users, i.e those with direct access to the local network, typically via Wifi. The problems begin when a torrent clients WebUI is exposed to the wider internet. In broad terms, instead of the client being restricted to IP addresses reserved for local uses (starting 192.168.0.0 or 10.0.0.0), anyone with a web browser anywhere in the world can access the UI too.
In many cases, a WebUI can be secured with a password or by other means but when users are allowed to do that themselves, many never do, despite the warnings. That could end in disaster if the wrong person decides to let rip from the other side of the world.
Specialized Search Engines
Internet-connected devices are easily found using services such as Shodan, Censys, Fofa and Onyphe.io and those that are poorly configured are in plentiful supply.
The image above shows a WebUI for the Tixati torrent client. With zero security, everything is on full display, just as it is for the person who operates the client, whoever they might b...
06:37
Is the BlackByte ransomware gang behind the City of Augusta attack? Security Affairs
The city of Augusta in Georgia, U.S., admitted that the recent IT system outage was caused by a cyber attack.
While the City of Augusta revealed that a cyberattack caused the recent IT outage, the BlackByte ransomware gang has claimed responsibility for the attack.
The attack took place on May 21, the administrator at the City announced that they were experiencing a disruption in network services, warning of potential impacts on telephone and email access.
In a post published on the citys website, the administration denied that it was the victim of a ransomware attack and that the threat actors demanded the payment of $50 million ransom.
Official Statement on behalf of The Office of The Mayor and The City of Augusta. @CityofAugusta pic.twitter.com/YP6r7YzSLQ
Mayor Garnett Johnson (@MayorJohnson85) May 26, 2023
The City of Augusta, GA began experiencing technical difficulties this past Sunday, May 21, 2023, unrelated to last weeks outage, resulting in a disruption to certain computer systems. We began an investigation and determined that we were the victim of unauthorized access to our system. reads the announcement published by the City. Our Information Technology Department is working diligently to investigate the incident, to confirm its impact on our systems, and to restore full functionality to our systems as soon as possible.
The C...
06:34
Stealing From Wallets to Browsers: Bandit Stealer Hits Windows Devices HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
Watch out for the Bandit Stealer malware that is being distributed through phishing emails.
This is a post from HackRead.com Read the original post: Stealing From Wallets to Browsers: Bandit Stealer Hits Windows Devices
06:01
AE170 Nicoles Prints Pin Up Girls Fabrics NEWWhats New! Fa h+ Media
AE170 Nicoles Prints Pin Up Girls Fabrics NEWWhats New! Fa
Update your dogs details, such as address, microchip number and desex information. Youll find all your statements held in your statement vault in internet banking. If you look on the right hand side of your screen, youll see a link to your statement vault. This will take you to a screen where you can select which statement you would like to download.
Once you click confirm, you are transferred to Payment Expresss secure payment gateway to enter your credit card details. Payment Express is NZs most trusted online payment system. However, to provide you with a refund we will have to process this manually from our end, once we have been in contact with you. Once an order has been placed the order cannot be cancelled as goods are often shipped the same day. If you wish to receive a refund, you will be refunded the value of the item at the time of purchase.
- We always recommend you check the latest limits and exemptions.
- However, to provide you with a refund we will have to process this manually from our end, once we have been in contact with you.
- I had so many messaging me asking about going vegan or how they could help stop certain dog breeds from getting a bad rap or how they could helped chained dogs gain freedom.
- Please check to ensure your postal address is correct.
- All of our cards are meticulously crafted in New Zealand, using vegetable based inks on stocks from sustainably managed forests.
Log into internet banking, go to Cards, click on your card, select Set/Change PIN, then enter your new PIN, and re-enter your new PIN . Log in to internet banking, click on your card, then Additional options & details, then select Activate your card next to Card Status. From this Friday 26 May, payments will be processed seven days a week. Were working hard to make our banking products and services accessible and available to all New Zealanders, regardless of ability.
The content shown may differ from the edition of this book sold on Wheelers. Please select carefully as returns are not accepted. Please allow 1-4 working days for national delivery. We cannot always guarantee this as it depends on your local courier driver. We will send you an email notifying you when your order has been shipped and provide your tracking number.
We want women of all shapes and sizes to enjoy looking and feeling like a classic movie star. Ensure that your hairstyle matches your outfit to get the ultimate vintage look. Your hair should have loose curls and an accessory. Dress is a new favourite among women who want to keep up with the latest looks and trends. At Two Lippy Ladies, we understand the need for women to find the right look for their bodys curves, and we ensure that we stock a variety of gorgeous vintage clothes to fit any body...
06:00
Minecraft in Minecraft on the CHUNGUS II Hackaday

Minecraft is a simple video game. Well, its a simple video game that also has within it the ability to create all of the logic components that youd need to build a computer. And building CPUs in Minecraft is by now a long-standing tradition.
Enter CHUNGUS II. The Computational Humongous Unconventional Number and Graphics Unit by [Sammyuri] is the biggest and baddest Minecraft computer that weve ever seen. So big, in fact, that it was finally reasonable to think about porting a thats right, Minecraft running in Minecraft. (Video embedded below.) Writing the compiler and programming the game brought two more hackers to the party, [Uwerta] and [StackDoubleFlow], and quite honestl...
05:59
Nip Tuck Swim Navy Ava Spot Bette Pin Up Style Tummy Control Bikini Set Online h+ Media
Nip Tuck Swim Navy Ava Spot Bette Pin Up Style Tummy Control Bikini Set Online
Clothing, you can look fabulous and feel like you just stepped off the set of a classic movie. Here are some tips to get the look and feel of a movie star in these clothes. They add a punky pop of style to any acid-wash denim jacket or pair of high waisted jeans. Complete your vintage outfit by adding a few of our other fun fashion pieces. These details bring your look to life, or they make for gorgeous gifts!
- Producing these high resolution images is not the easiest job due to the small depth of field typical in macro photography.
- If your item is faulty or is not the same as the item presented on the Workshop Online Store you may return or exchange it.
- If you dont have internet banking, youll have to call us or visit your nearest Kiwibank.
- We want to share our love for vintage style in a way that is accessible to all body shapes and sizes.
- The gallery can also propose a counter-offer for the acquisition of the artwork.
Make sure youre registered for OnlineCode for additional security while you bank online. Now we just need your first name or an alias if you prefer, along with your email address just in case we need to contact you regarding your review. Hes had numerous other smart performers in a training career that has taken him as far as Macau, but as the winner of his last six starts, Gold Watch is doing his best to trump them all.
If the gallery cannot accept your offer, you will receive a full refund. While you may be used to walking into a clothing store and heading straight for your size in brands you have always worn when it comes to pinup clothes, its best to try them on first. You may find that youll need a different size from your normal one as these clothes arent meant to look baggy. Two Lippy Ladies aims to curate a collection of brands that is inclusive, quirky and fun.
All refunds will be made back to the original means of purchase. These terms and conditions apply exclusively to the Workshop Online Store and not at any of Workshops physical retail stores. When renewing your adult passport online, you can choose to apply for your RealMe verified identity at the same time.
Log on using your ANZ customer number and password. Have your mobile phone with you as youll be prompted to enter your OnlineCode, followed by using your existing goMoney PIN. Have your mobile phone with you as youll be prompted to enter your OnlineCode, followed by setting up your goMoney PIN.
When you apply for assistance using MyMSD, or while you are on the phone with us, you can upload the documents we need to your MyMSD account. When autocomplete results are available use up and down arrows to review and enter to select. Somethings changed Address, contact details, overseas travel, childcare, relationship or anything else thats changed.
We want to share...
05:56
ANZ goMoney mobile app h+ Media
ANZ goMoney mobile app
If youve got a mobile registered with RealMe, you can link your Authenticator app to your RealMe account for extra security. If you are creating a RealMe login from overseas and you are having trouble entering your phone number, try leaving out the 0 at the beginning of your number when you enter the Prefix. If you are not in New Zealand you can still create aRealMe login and provide an overseas phone number for your contact details. If you apply using a New Zealand passport or citizenship record, your gender will be passed through from the passport or citizenship record. If you apply using a birth or immigration record, you will need to enter your gender as Male, Female, or Other, and this will be manually checked against the record by our processing team.
Unfortunately, delivery estimates are currently not available for this product. The selected size is sent directly by THE ICONIC, that isnt participating in this promotion. The selected size is sent by our partner, that isnt participating in this promotion. This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply. We are an independent, family-run business and take pride in our personal and tailored service.
On expiry of the interest free term, the finance companies prevailing interest rate will https://1xbetarabic.top/en/1xbet-marocco/ apply to any outstanding balance. Once you have selected the fabrics you like, drag them in to the shopping cart and click checkout. Please note that the delivery times quoted are indicative only, and Workshop can not be held responsible for deliveries not made within this time frame. Please be aware that if you place an order over a weekend or public holiday that your order will not be processed until the next business day. Only logged in customers who have purchased this product may leave a review.
Overview Take a look at the range of benefits and payments we have available. Only your main place of residence can be verified for RealMe. You cannot use a P O Box, temporary accommodation address or non-residential address with RealMe. The RealMe service enables you to verify your address through the New Zealand Post Address Verification Service. Authenticator apps are available for phones and tablets.
This item is sent directly from our partner and will arrive separately if ordered with other items. Spread eligible purchases over multiple interest-free instalments with our payment . Each order comes with the selected matched and teased Pin-Ups hairpiece, the base component for the natural hair, Pin-Ups threader, and a Pin-Ups box for traveling and storage. Pin-Up orders generally ship in 4-6 weeks but they can take up to 10 Weeks to be made, Plus up to 3 weeks shipping as they come directly from the USA.
Your new EFTPOS card will be mailed out to you and should arrive within 1 2...
04:00
The Relay That Changed the Power Industry IEEE Spectrum

For more than a century, utility companies have used electromechanical relays to protect power systems against damage that might occur during severe weather, accidents, and other abnormal conditions. But the relays could neither locate the faults nor accurately record what happened.
Then, in 1977, Edmund O. Schweitzer III invented the digital microprocessor-based relay as part of his doctoral thesis. Schweitzers relay, which could locate a fault within the radius of 1 kilometer, set new standards for utility reliability, safety, and efficiency.
Edmund O. Schweitzer III
Employer:
Schweitzer Engineering Laboratories
Title:
President and CTO
Member grade:
Life Fellow
Alma maters:
Purdue University, West Lafayette, Ind.; Washington State University, Pullman
To develop and manufacture his relay, he launched Schweitzer Engineering Laboratories in 1982 from his basement in Pullman, Wash. Today SEL manufactures hundreds of products that protect, monitor, control, and automate electric power systems in more than 165 countries.
Schweitzer, an IEEE Life Fellow, is his companys president and chief technology officer. He started SEL with seven workers; it now has more than 6,000.
The 40-year-old employee-owned company continues to grow. It has four manufacturing facilities in the United States. Its newest one, which opened in March in Moscow, Idaho, fabricates printed circuit boards.
Schweitzer has received many accolades for his work, including the 2012 IEEE Medal in Power Engineering. In 2019 he was inducted into the U.S. National Inventors Hall of Fame.
Advances in power electronics
Power system faults can happen when a tree or vehicle hits a power line, a grid operator makes a mistake, or equipment fails. The fault shunts extra current to some parts of the circuit, shorting it out.
If there is no proper scheme or device installed with the aim of protecting the equipment and ensuring continuity of the power supply, an outage or bla...
02:33
Links 27/05/2023: Plans Made for GNUs 40th Anniversary Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Applications
-
Linux Links Best Free and Open Source Alternatives to Apple Activity Monitor
Activity Monitor displays a variety of resources in use on a system in real time. These include processes, d...
-
-
02:24
NASA Caught Private Moon Lander Crash Site on Camera SoylentNews
Are those scattered spacecraft parts?
NASA couldn't help but do a little rubbernecking of the recent crash site where a private Japanese company recently attempted to land on the moon.
The Hakuto-R mission ended abruptly on April 25, 2023, shortly after ispace lost contact with its spacecraft as it descended toward the lunar surface. A preliminary investigation indicated the lander had run out of fuel, according to the company, which is necessary for firing thrusters to slow down before reaching the ground.
Flying overhead, NASA's Lunar Reconnaissance Orbiter captured 10 images of the proposed landing site near the Atlas Crater that show four prominent pieces of debris and several small changes to the surface. Those features could be a small crater or parts of the lander that have scattered. The U.S. space agency intends to snap more pictures over the coming months to get a better look with different lighting conditions and angles.
[...] NASA has used the orbiter to take pictures of other moon crashes in the past, and it's not to bask in others' failures. The purpose is to study the impacts for insight into the moon dust. When spacecraft land on the moon, the spray of dust and soil damages anything that can be sandblasted. Anticipating a future filled with moon landings, scientists want to better understand the erosion and impacts they cause and learn how to mitigate them.
Ispace invited the world to watch alongside its Tokyo-based mission control through a livestream of the nail-biting space event. Company officials said they're proud of what the mission achieved and will use the flight data during the landing phase to help them prepare for their next two lunar missions.
LATE UPDATE FOLLOWS:
Read more of this story at SoylentNews.
01:46
State Farm Halts New Property Insurance Policies in California cryptogon.com
Via: Orange County Register: State Farm said Friday, May 26, that it will stop accepting new applications for property and casualty insurance in California, citing rising construction costs and its rapidly growing catastrophe exposure. The policy change for personal and business lines is effective Saturday, May 27, State Farm said. The change does not apply []
00:25
Startups to Watch in AI: Artificial intelligence firms on the rise Lifeboat News: The Blog
Generative AI startup Jasper is creating an AI marketing assistant capable of writing ad copy, blogs, and other web content. Founded just two years ago, the startup raised $125 million in October at a $1.5 billion valuation.
AI startup Magic. Dev wants to make it easier to write computer code. The company uses large language models like OpenAIs ChatGPT to develop software that can write lines of code based on a text prompt. The program is meant to make software engineers more efficient. The company has raised $28 million to date from investors including Alphabets CapitalG.
00:25
AI Is Helping Create the Chips That Design AI Chips Lifeboat News: The Blog
Please make sure your browser supports JavaScript and cookies and that you are not blocking them from loading. For more information you can review our Terms of Service and Cookie Policy.
00:23
The science of super longevity | Dr. Morgan Levine Lifeboat News: The Blog

I quoted and responded to this remark:
we probably will not solve death and this actually shouldnt be our goal. Well nice as she seems thank goods Dr Levine does not run the scientific community involved in rejuvenation.
The first bridge looks like its going to be plasma dilution and this may come to the general population in just a few short years. People who have taken this treatment report things like their arthritis and back pain vanishing.
After that epigentic programming to treat things that kill you in old age. And so on, bridge after bridge. if you have issues with the future, some problem with people living as long as they like, then by all means you have to freedom to grow old and die. That sounds mean but then I think its its mean to inform me I have to die because you think we have to because of progress. But this idea that living for centuries or longer is some horrible moral crime just holds no water.
Science cant stop aging, but it may be able to slow our epigenetic clocks.
Up next, Michio Kaku: How to reverse aging https://www.youtube.com/watch?v=DV3XjqW_xgU
What if we could slow down the hands of our biological clocks? This question underpins much of the research of Morgan Levine, who leads a research team at the life science company Altos Labs.
Levine investigates the fascinating intricacies of aging, recognizing that it doesnt happen at a uniform pace for everyone. Central to her exploration is the concept of epigenetics the factors that influence gene activity without changing the DNA sequence. Levine focuses on DNA methylation, a significant epigenetic change that occurs with aging, and the development of models called epigenetic clocks that can be used to predict biological age.
While she acknowledges that it might be possible to reverse aging at a cellular level, Levine clarifies that the ultimate goal is not to cure aging or death, but to delay disease onset and improve healthspan.
0:00 Fast agers & slow agers.
1:25 The hallmarks of aging.
1:59 What is the epigenetic clock?
3:05 Can we Benjamin Button aging?
5:22 The holy grail for scientists.
Read the video transcript https://bigthink.com/series/explain-it-like-im-smart/epig...
00:00

Here at Hackaday, we definitely love to celebrate the hard hacks: the insane feats of reverse engineering, the physics-defying flights of fancy, or the abuse of cutting edge technology. But today Id like to raise a rhetorical glass in tribute of the simple hacks. Because, to be perfectly honest, the vast majority of my hacks are simple hacks, and its probably the same for you too. And these often go unsung because, well, theyre simple. But that doesnt mean that something simple cant be helpful.
Saturday, 27 May
23:11
Sony a9 Cameras and Linux Random Thoughts
When blogging, I usually sit on the couch with my laptop on my lap (as is logical), typing away in Emacs in ewp mode, snapping pics of stuff (mostly comics) in bad lighting conditions.
Taking nice snaps of things is a breeze if the lighting is good (i.e., sufficient), or if youve got a camera on a mount, but thats not what were dealing with here: I want to snap pics in a frictionless manner, because I dont have no time for no futzing around.
Over the years, Ive tried a bunch of different cameras, but within my (peculiar) constraints, its just hard to not end up with blurry, out of focus images with bad white balance. What Im currently using is a Sony a9 II camera with a 24mm lens (fixed lens since I cant change focal length and hold both the camera and a comic book at the same time), set at f/12 (because Im snapping pics of comics that Im often holding in an angled way to avoid reflections, and anything less than that (at this distance) will mean that half the book is out of focus) and 1/25 (because anything slower than that will mean that the book is blurred from either my comic holding hand or my camera holding hand shaking).
(Auto white balance, though, auto focus, and I have to adjust the brightness of the image throughout the day/night by adjusting the ISO.)
See what serious problems Im having!
But thats not what this blog post is about: Its about image transfer.
For almost a decade Ive been using Toshiba FlashAir SD cards to transfer images from whatever camera Ive been using to my laptop (and then automatically into Emacs). It works fine but there are some janky...
23:00
Wakka Wakka! This Turing Machine Plays Pac-Man IEEE Spectrum

As I read the newest papers about DNA-based computing, I had to confront a rather unpleasant truth. Despite being a geneticist who also majored in computer science, I was struggling to bridge two conceptsthe universal Turing machine, the very essence of computing, and the von Neumann architecture, the basis of most modern CPUs. I had written C++ code to emulate the machine described in Turings 1936 paper, and could use it to decide, say, if a word was a palindrome. But I couldnt see how such a machinewith its one-dimensional tape memory and ability to look at only one symbol on that tape at a timecould behave like a billion-transistor processor with hardware features such as an arithmetic logic unit (ALU), program counter, and instruction register.
I scoured old textbooks and watched online lectures about theoretical computer science, but my knowledge didnt advance. I decided I would build a physical Turing machine that could execute code written for a real processor.
Rather than a billion-transistor behemoth, I thought Id target the humble 8-bit 6502 microprocessor. This legendary chip powered the computers I used in my youth. And as a final proof, my simulated processor would have to run Pac-Man, specifically .
In Turings paper, his eponymous machine is an abstract concept with infinite memory. Infinite memory isnt possible in reality, but physical Turing machines can be built with enough memory for the task at hand. The hardware implementation of a Turing machine can be organized around a rule book and a notepad. Indeed, when we do basic arithmetic, we use a rule book in our head (such as knowing when to carry a 1). We manipulate numbers and other symbols using these rules, stepping through the process for, say, long division. There are key differences, though. We can move all over a two-dimensional notepad, doing a scratch calculation in the margin be...
22:57
Social Control Media Needs to be Purged and We Need to Convince Others to Quit It Too (to Protect Ourselves as Individuals and as a Society) Techrights
Video
download link | md5sum
58fe869dbe56783f7f1ce90f27458ef6
Collective Risk From Social Control Networks
Creative Commons Attribution-No Derivative Works 4.0
Summary: With the Tux Machines anniversary (19 years) just days away we seriously consider abandoning all social control media accounts of that site, including Mastodon and Diaspora; social control networks do far more harm than good and theyve gotten a lot worse over time
AMONG the potential topics for today weve included the impact of social control media by peer, e.g. within families (dinner table, sleep) or inside workplaces. Ive meanwhile noticed, as stated in the above video, that Mastodons largest instance does not like GNU/Linux sites. It does not like GNU/Linux users, either. Tux Machines (username tuxmachines) has been delisted and demoted; its not visible, even if its still there, and nothing gets imported into the account.
Tux Machines (username tuxmachines) has been delisted and demoted; its not visible, even if its still there, and nothing gets imported into the account.For now Ive decided not to even fix the tuxmachines social control media accounts. Its just not worth the trouble and as early as next week Tux Machines might quit social control media altogether. Its a total catastrophe and nobody deserves to have to deal with such crap.
The video above focuses on this new article from YLE. It tal...
22:55
Mesa 23.2 Virgl Lands Support For OpenGL 4.6 Inside Virtual Machines Phoronix
The Virgl driver within Mesa for allowing open-source OpenGL support within virtualized environments in conjunction with the Virglrenderer is now capable of exposing OpenGL 4.6...
22:23
Spacetop is an augmented reality laptop for remote working on the go Lifeboat News: The Blog
Human-computer interaction company Sightful is releasing its first product, Spacetop, a screen-less augmented reality laptop projecting tabs across a 100-inch virtual screen. The laptop if you can call it that is a hardware deck and full-size keyboard with a pair of tailored NReal glasses. The glasses project tabs directly in front of whatever the user is looking at while remaining invisible to anyone else.
Specs-wise, Spacetop is running a Snapdragon 865 paired with an Adreno 650 GPU, 8GB RAM and 256GB storage, putting it in the same class as some of the smartphones that are already capable of driving AR glasses. Its not smartphone-sized, however, measuring 1.57-inches high, 10.47-inches wide and 8.8-inches deep, and it weighs in at 3.3 pounds, the same as plenty of laptops we could choose to mention here.
Sightful is clearly gunning for a crossover hit in the work-from-home-or-anywhere market. Laptops are the centerpiece of our daily working lives, but the technology has not evolved with the modern, work from anywhere, privacy matters, road warrior mentality. Meanwhile, augmented reality is full of potential and promise but is yet to find its daily use case, said Tamir Berliner, Sightful co-founder who previously worked at both Leap Motion and Primesense. We are at the perfect moment for a significant paradigm shift in a device we all know and love.
22:23
22:22
ChatGPTs makers say AI could surpass humanity within the next 10 years as superintelligence starts to exceed other powerful technologies Lifeboat News: The Blog
OpenAIs cofounders, including Sam Altman, said in a blog post that there needed to be a proactive approach to managing AIs potential harms.
22:22
Linux Patches Improve VM Guest Performance When The Host Encounters Memory Pressure Phoronix
An updated set of patches were posted on Friday that seem to improve the Linux guest VM performance when the host is under heavy memory pressure...
21:59
THE MISSING COMMODORE 64 MANUAL! commodore64crap
THE MISSING COMMODORE 64 MANUAL!

Mastering Machine Code on Your Commodore 64 by Mark Greenshields
The Missing Manual is a series of books by Pogue Press/OReilly & Associates Inc, but from what I can tell they never published one for the Commodore 64. However, heres a book Ive recently found which certainly fits the bill. This book is called Mastering Machine Code on Your Commodore 64 by Mark Greenshields, published by Interface Publications in 1984! It was first printed in May 1984, not long after I got my Commodore 64.
After reading it, I can definitely say that it should have been licensed by Commodore and included in the box which every Commodore 64 was supplied with. Of course, the reason why it wasnt given away by Commodore was probably because it cost 7.95. Commodore Founder Jack Tramiels original reason for buying a perpetual license for the Microsoft 6502 8K BASIC in 1976 (antique by the time the C64 was released) was so that he didnt have to pay a US$3 royalty for each single computer he sold. The exchange rates for the Pound Sterling against the US Dollar during this time period (according to https://www.macrotrends.net/2549/pound-dollar-exchange-rate-historical-chart ) were 1.00 = US$2.03 on January 5, 1976; ...
21:57
Anonymously Travelling: Still Feasible? Techrights
Video download
link | md5sum
6f335d84226615033fae0b1049d476d8
Anonymous Travel as a Right
Creative Commons Attribution-No Derivative Works 4.0
Summary: The short story is that in the UK its still possible to travel anonymously by bus, tram, and train (even with shades, hat and mask/s on), but how long for? Or how much longer have we got before this too gets banned under the false guise of protecting us (or smart/modern)?
THE element of curious Roy has long motivated and led me to testing all sorts of stores and businesses, sometimes even government departments. I did assessments and surveys, then published the outcomes in my personal site. Back in the days there were media/societal watchdogs that did this routinely and reported their latest-found outcomes.
Surveillance states mostly punish law-abiding people.The other day I decided to check the experience of travelling by train anonymously. In a nutshell, its still possible to purchase train tickets and travel anonymously. Its also possible to do this with an actual human and the queue was short even at 8:30AM. Yes, actual humans are available! And they talk back at you with advice and stuff
Of course not every train station still has humans available. In some countries the regime and the corporations (graft) try to herd people into smart apps and other such nonsense. Those should not be needed. More of that is covered in the video above, including why in a free society anonymous travel is still very important. In some parts of the world its already impossible to travel privately in a car, unless its a stolen car. Does this prevent crime? Hardly. Many criminals already exercise special caution and steal cars, from which crimes get committed. Surveillance states mostly punish law-abiding people.
21:43
At High School Debates, Debate Is No Longer Allowed SoylentNews
At national tournaments, judges are making their stances clear: students who argue 'capitalism can reduce poverty' or 'Israel has a right to defend itself' will loseno questions asked:
First, some background. Imagine a high school sophomore on the debate team. She's been given her topic about a month in advance, but she won't know who her judge is until hours before her debate round. During that time squeezeperhaps she'll pace the halls as I did at the 2012 national tournament in Indianapolisshe'll scroll on her phone to look up her judge's name on Tabroom, a public database maintained by the NSDA [National Speech and Debate Association]. That's where judges post "paradigms," which explain what they look for during a debate. If a judge prefers competitors not "spread"speak a mile a minutedebaters will moderate their pace. If a judge emphasizes "impacts"the reasons why an argument mattersdebaters adjust accordingly.
But let's say when the high school sophomore clicks Tabroom she sees that her judge is Lila Lavender, the 2019 national debate champion, whose paradigm reads, "Before anything else, including being a debate judge, I am a Marxist-Leninist-Maoist. . . . I cannot check the revolutionary proletarian science at the door when I'm judging. . . . I will no longer evaluate and thus never vote for rightest capitalist-imperialist positions/arguments. . . . Examples of arguments of this nature are as follows: fascism good, capitalism good, imperialist war good, neoliberalism good, defenses of US or otherwise bourgeois nationalism, Zionism or normalizing Israel, colonialism good, US white fascist policing good, etc."
[...] Traditionally, high school students would have encountered a judge like former West Point debater Henry Smith, whose paradigm asks students to "focus on clarity over speed" and reminds them that "every argument should explain exactly how [they] win the debate."
In the past few years, however, judges with paradigms tainted by politics and ideology are becoming common. Debate judge Shubham Gupta's paradigm reads, "If you are discussing immigrants in a round and describe the person as 'illegal,' I will immediately stop the round, give you the loss with low speaks"low speaker points"give you a stern lecture, and then talk to your coach. . . . I will not have you making the debate space unsafe."
Read more of this story at SoylentNews.
21:25
With EUIPO in Focus, and Even an EU Kangaroo Tribunal, EPO Corruption (and Cross-Pollination With This EU Agency) Becomes a Major Liability/Risk to the EU Techrights
Video
download link | md5sum
17b91cbac42af9980f77f07a77c03d7d
EPO Under Scrutiny, But Will EU Listen?
Creative Commons Attribution-No Derivative Works 4.0
Summary: With the UPC days away (an illegal and unconstitutional kangaroo court system, tied to the European Union in spite of critical deficiencies) its curious to see EPO scandals of corruption spilling over to the European Union already
THE EU is about to get contaminated with the EPO cancer (EPO staff compares the administration to a cancer). Will that doom the union? Well, it certainly wont help.
To get promoted in these institutions one must be profoundly corrupt or participate in profound corruption.In past years we covered EUIPO corruption that had come from (or via) the EPO. Does the EU really want to go on with this? Will EUIPO replace the EPO? The European Commission does not seem to understand what its doing; its a puppet on strings for corporate lobbyists even actors working on behalf of foreign countries.
SUEPO has just taken note of the following article, which was put behind a paywall except this part:
We provide a rundown of Managing IPs news and analysis coverage from the week, and review whats been happening elsewhere in IP
French govt complained to EPO over EUIPO election conduct
French finance minister Bruno Le Maire wrote to Antnio Campinos, president of the EPO, to complain over the timing of an event that will be held in Lisbon one week before the EUIPO leadership vote, Manag...
21:00
A Bullet Time Video Booth You Can Build Hackaday

[Sebastian Staacks] built a video booth for his wedding, and the setup was so popular with family, that it was only fitting to do one better and make some improvements to the setup, Matrix-style. The bullet time video effect was introduced by the classic movie franchise and makes for a splendid video transition effect for video montages.
Hardware-wise, the effect is pretty expensive, requiring many cameras at various angles to be simultaneously triggered, in order to capture the subject in a fixed pose with a rotating camera. Essentially you need as many cameras as frames in the sequence, so even at 24 frames per second (FPS), thats a lot of hardware. [Sebastian] cheated a bit, and used a single front-facing camera for the bulk of the video recording, and twelve individual DSLRs covering approximately 90 degrees of rotation for the transition. More than that is likely impractical (not to mention rather expensive) for an automated setup used in as chaotic an environment as a wedding reception! So, the video effect is quite the sam...
20:57
European Patent Office (EPO) Management Not Supported by the EPOs Applicants, So Why Is It Still There? Techrights
More translations (with more languages) available in the site of the EPOs union, SUEPO

The European Patent Office in Munich. Experts criticise the
practice of granting inventor protection.
Photo: dpa/Sven Hoppe
Summary: This third translation in the batch is an article similar to the prior one, but the text is a bit different (Patente ohne Wert)
A BIT less than a week before the EPO wanted (or merely hoped) to open an illegal and unconstitutional kangaroo court, in violation of international conventions, some condemnation came from the German press. This project will destabilise the EU by discrediting the EU, so Germanys government needs to sober up and listen to the warning signs. EPO corruption is highly contagious and it has been left to flourish for over a decade already. Heres the latest of the batch from SUEPO:
Criticism of the European Patent Office Patents without value
Munich To increase its revenues, the European Patent Office grants questionable patents, say critics. Transparency International sees structures that favour corruption.
By Thomas Magenheim-Hrmann
The example described by the Munich patent attorney makes it clear what is at stake. A pharmaceutical company developed a pill against infertility, had it protected at the European Patent Office (EPO) and invested in its marketing. Then a rival entered the market with an alleged plagiarism. The patent holder went to court and lost. The alleged imitator was able to show a US patent that Epa examiners had overlooked. This rendered their property right worthless. In extreme cases, this can cause millions in damages, explains the patent attorney, who wishes to remain anonymous. He works for one of the largest patent law firms in Europe. Patenting for several countries alone consumes a six-figure sum, and many times that amount is invested in production in reliance on the patent.
There is a system of lame searches, the expert complains. Examiners are encouraged to grant more and more patents because they maximise the offices income. Quality research falls by the wayside. Michael Heisel puts the grievances even higher. We see structural problems at the EPO that facilitate corruption, says the Bavarian head of the anti-corr...
20:56
New Buhti ransomware operation uses rebranded LockBit and Babuk payloads Security Affairs
The recently identified Buhti operation targets organizations worldwide with rebranded LockBit and Babuk ransomware variants.
Researchers from Symantec discovered a new ransomware operation called Buhti (aka Blacktail) that is using LockBit and Babuk variants to target Linux and Windows systems worldwide.
The ransomware operation hasnt its own ransomware payload, however, it uses a custom information stealer to target specified file types.
The Buhti operation has been active since February 2023, it was initially spotted attacking Linux systems, but later Symantecs Threat Hunter Team also identified attacks on Windows computers.
The group was observed quickly exploiting recently disclosed vulnerabilities, such as the recently patched PaperCut vulnerability.
In a recent attack against Windows systems, Buhti operators used "https://securityaffairs.com/136056/data-breach/lockbit-3-0-builder-leak.html"> LockBit 3.0 (aka LockBit Black) ransomware. The builder used by the operators was leaked in September 2022 by a disgruntled developer in response to Russian invasion of the Ukraine.
The ransomware appends the .buthi extension to the encrypted files.
The researchers also observed attacks against Linux systems with Golang-based variants of the Babuk ransomware, which was released on hacking forums in September 2021. This variant used in the a...
20:36
EPO Applicants Complain That Patent Quality Sank and EPO Management Isnt Listening (Nor Caring) Techrights
More translations (with more languages) available in the site of the EPOs union, SUEPO
Summary: SUEPO has just released 3 translations of new articles in German (here is the first of the batch); the following is the second of the three (Kritik am Europischen Patentamt Patente ohne Wert?)
THIS is an article from yesterday, composed by Thomas Magenheim, who understands these matters. The following is at least partly machine-generated:
Criticism of the European Patent Office Patents without value?
26.05.2023 00:00 hrs
Photo: imago/STLTo increase its revenues, the European Patent Office grants questionable patents, say critics. Transparency International sees structures that favour corruption.
Thomas Magenheim
The example described by the Munich patent attorney makes it clear what is at stake. A pharmaceutical company developed a pill against infertility, had it protected at the European Patent Office (EPO) and invested in its marketing. Then a rival entered the market with an alleged plagiarism. The patent holder went to court and lost. The alleged imitator was able to show a US patent that Epa examiners had overlooked. This rendered their property right worthless. In extreme cases, this can cause millions in damages, explains the patent attorney, who wishes to remain anonymous. He works for one of the largest patent law firms in Europe. Patenting for several countries alone consumes a six-figure sum and many times that amount is invested in production in reliance on the patent. There is a system of meagre returns, the expert complains. Examiners are encouraged to grant more and more patents because this maximises the offices income. Quality research falls by the wayside.
Michael Heisel hangs the grievances even higher. We see structural problems at the Epa that facilitate corruption, says the Bavarian head of the anti-corruption organisation Transparency International. An element of this, he says, is the Epa Board of Directors, in w...
20:23
Artificial muscle fibers could serve as cell scaffolds Lifeboat News: The Blog
In two new studies, North Carolina State University researchers have designed and tested a series of textile fibers that can change shape and generate force like a muscle. In the first study, published in Actuators, the researchers focused on the materials influence on artificial muscles strength and contraction length. The findings could help researchers tailor the fibers for different applications.
In the second, proof-of-concept study published in Biomimetics, the researchers tested their fibers as scaffolds for live cells. Their findings suggest the fibersknown as fiber robotscould potentially be used to develop 3D models of living, moving systems in the human body.
We found that our fiber robot is a very suitable scaffold for the cells, and we can alter the frequency and contraction ratio to create a more suitable environment for cells, said Muh Amdadul Hoque, graduate student in textile engineering, chemistry and science at NC State. These were proof-of concept studies; ultimately, our goal is to see if we can study these fibers as a scaffold for stem cells, or use them to develop artificial organs in future studies.
20:22
United Airlines plans to bring flying cars to Chicago Lifeboat News: The Blog

United Airlines and California-based startup Archer Aviation have announced plans to use flying cars to ferry passengers between Chicagos OHare International Airport and a vertiport just minutes from downtown.
Im pleased that Chicago residents will be among the first in the nation to experience this innovative, convenient form of travel, said Chicago Mayor Lori E. Lightfoot.
The megacity challenge: With 9.6 million residents, Chicago is the third largest metro area in the US, and experts predict the population is going to exceed 10.6 million people by 2050.
20:22
In a first, researchers capture fleeting transition state in ring-shaped molecules excited by light Lifeboat News: The Blog
Using a high-speed electron camera at the Department of Energys SLAC National Accelerator Laboratory and cutting-edge quantum simulations, scientists have directly imaged a photochemical transition state, a specific configuration of a molecules atoms determining the chemical outcome, during a ring-opening reaction in the molecule -terpinene. This is the first time that scientists have precisely tracked molecular structure through a photochemical ring-opening reaction, triggered when light energy is absorbed by a substances molecules.
The results, published in Nature Communications, could further our understanding of similar reactions with vital roles in chemistry, such as the production of vitamin D in our bodies.
Transition states generally occur in chemical reactions which are triggered not by light but by heat. They are like a point of no return for molecules involved in a chemical reaction: As the molecules gain the energy needed to fuel the reaction, they rearrange themselves into a fleeting configuration before they complete their transformation into new molecules.
20:22
5 ChatGPT tricks you had no idea you could do with the chatbot Lifeboat News: The Blog
Youve likely seen all the impressive tasks ChatGPT can accomplish, from drafting emails and resumes to writing code and even inventing a new language. But as we wait for AI to make us all obsolete, we might as well enjoy our remaining time in control of the chatbots. One way to do so is by experimenting with all of the fun tricks ChatGPT can perform.
As intelligent and powerful as ChatGPT is, you can also treat it as a toy. Here are some of the best ChatGPT tricks weve discovered so far that might not change your life, but will definitely keep you entertained during an especially slow day at work:
If youre desperate to play a game with someone but cant actually find a human to play with, ChatGPT is more than capable of standing in. There are a bunch of games that you can play with ChatGPT, including Tic-Tac-Toe, Hangman, and Mad Libs. Just ask ChatGPT to play any of those games, and it will generate the game board and explain the rules.
20:20
Intel Proposes Using Netlink For Linux Graphics Driver RAS & Telemetry Phoronix
Intel Linux kernel graphics driver developers are looking at making use of Netlink for exposing RAS (reliability, availability, serviceability) and telemetry features of kernel graphics drivers to user-space for their modern GPUs...
20:16
German Media About Industry Patent Quality Charter (IPQC) and the European Patent Office (EPO) Techrights
More translations (with more languages) available in the site of the EPOs union, SUEPO

Siemens is one of the largest applicants at the European Patent
Office.
Source: Matthias Balk/dpa
Summary: SUEPO has just released 3 translations of new articles in German; this is the first of the three (Industrie kritisiert Europisches Patentamt)
THE following was translated by staff of the EPO. The staff wants to general public to know this:
Industry criticises European Patent Office
An initiative of several large companies is concerned about the quality of patent examinations at the European Patent Office. There, speed comes before accuracy, they say. The office sees things differently.
The European Patent Office (EPO) has come in for criticism from industry. An initiative of now 21 companies is concerned about the quality of patent examination. We have the impression that the EPO is primarily concerned with processing as many patents as possible, says Beat Weibel, head of patents at Siemens, who initiated the Industry Patent Quality Charter (IPQC), in an interview with the Deutsche Presse-Agentur. Examiners, he says, are exposed to ever-increasing production pressure and are therefore no longer in a position to examine thoroughly enough. While in our case we see that the amount of work required for a patent application on average is always bigger, things have to move faster and faster at the EPO, explains Weibel. That worries us because the quality of the examination suffers as a result. He does not receive exact figures from the EPO on the time budget of the examiners, he says. But if you look at the number of examiners and the number of examinations patents, the result is roughly a halving over the past ten years.
Jrg Thomaier, head of patents at Bayer, which is also a member of the IPQC, shares Weibels
concerns.The EPO used to be known for taking a long time to test. In recent years, we have the impression that more attention is paid to speed and that examinations are no longer as thorough, he says. Things are faster now, but the revocation rate in the patent appeal process has gone up...
19:57
KDE Plasma 6.0's Night Color Mode Will Work With NVIDIA's Proprietary Driver Phoronix
Even with summertime approaching KDE developers remain very busy further enhancing the desktop stack and continued efforts around Qt6 porting and the Plasma 6.0 desktop...
19:30
Geminispace Continues to Grow Even If (or When) Stphane Bortzmeyer Stops Measuring Its Growth Techrights
Video
download link | md5sum
f726c3cf0bd8fe90ec207a68fa9544b8
Gemini is Growing, But Growth Not Measured
Creative Commons Attribution-No Derivative Works 4.0
Summary: A Gemini crawler called Lupa (Free/libre software) has been used for years by Stphane Bortzmeyer to study Gemini and report on how the community was evolving, especially from a technical perspective; but his own instance of Lupa has produced no up-to-date results for several weeks
THE work of Stphane Bortzmeyer, notably Lupa, has helped us estimate the growth of Gemini in general (as a protocol). But the Botond/Bortzmeyer-led capsules (the former charts the latter) stopped updating their numbers that track Geminis growth; maybe its just too big and expensive for Stphane to track all the time, as its not 2020 anymore and many thousands of capsules exist, counting subsites (in the domain sense) too.
Its perfectly plausible and possible
that Bortzmeyer isnt aware of the issue and has just
accidentally let the job fail (Botond uses a cron job at
1AM UTC since last year).The video above explains that,
based on our own experience, Gemini continues to grow. Even in the
absence of crawlers estimating and reporting this growth, were
optimistic and last month was record
traffic for us. Were talking about lots and lots of Gemini
pages (about half a million pages in one month). Its perfectly
plausible and possible that Bortzmeyer isnt aware of the issue and
has just accidentally let the job fail (Botond uses a cron
job at 1AM UTC since last year). radia.bortzmeyer.org
is definitely active this month. Either way, tracking the
growth of Geminispace has become a computationally expensive (and
thus financial burdensome) task. It did help a lot &#...
18:36
Links 27/05/2023: Goodbyes to Tina Turner Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Games
-
Godot Engine Dev snapshot: Godot 4.1 dev 3
The end of May means the approach of the feature freeze for Godot 4.1, and this dev snapshot aims to give you as many new features to test as possible.
-
-
-
Distributions and Operating Systems
-
Fedora Family / IBM
-
...
-
-
18:10
New Stealthy Bandit Stealer Targeting Web Browsers and Cryptocurrency Wallets The Hacker News
A new stealthy information stealer malware called Bandit Stealer has caught the attention of cybersecurity researchers for its ability to target numerous web browsers and cryptocurrency wallets. "It has the potential to expand to other platforms as Bandit Stealer was developed using the Go programming language, possibly allowing cross-platform compatibility," Trend Micro said in a Friday report
18:00
Restoring Dot Matrix Printer Cartridges For 2023 Hackaday

The noise of a dot matrix printer is probably as synonymous with 1980s computing as the modem handshake would become with the desktop experience a decade or more later. But unlike the computers that would have driven it, a dot matrix printer can still be a very useful device here in 2023. And why not? Theyre cheap to operate and can produce surprisingly good quality when paired with suitable drivers. There is a snag though; while cartridges for popular models can still be found, there are plenty whose consumables are long gone. [Drygol] had an Apple ImageWriter II with exactly that problem, and after finding all his cartridges were non-functional, took a look at how to bring them back.
Inside a dot matrix cartridge is a fabric ribbon similar to the one that might once have been found on a typewriter. Its not on a roll but folded into the space, and its drawn through by a pair of rollers. Not only had the ink on the fabric dried out, but the foam on the rollers had also disintegrated. Some careful dismantling, and a solution presented itself in the form of O-rings to replace the rollers. Those and a bit of mineral oil to soften the ink had the vintage Apple printing again as though it was the 80s once more.
Its a subject weve looked at before, as it turns out...
17:45
Critical OAuth Vulnerability in Expo Framework Allows Account Hijacking The Hacker News
A critical security vulnerability has been disclosed in the Open Authorization (OAuth) implementation of the application development framework Expo.io. The shortcoming, assigned the CVE identifier CVE-2023-28131, has a severity rating of 9.6 on the CVSS scoring system. API security firm Salt Labs said the issue rendered services using the framework susceptible to credential leakage, which could
17:43
HMRC Fraud Reporting Tool Does Not Protect Privacy and Reporters Are Left With Neither Feedback Nor Receipt schestowitz.com
Video download
link | md5sum
3658fca2df7acb84de0dde460f814926
HMRC Useless UI, No
Reference
Creative Commons Attribution-No Derivative Works 4.0
Summary: The crimes of Sirius Open Source were reported 7 days ago to HMRC (equivalent to the IRS in the US, more or less); but there has been no visible progress and no tracking reference is given to identify the report
THE system of accountability (checks and balances is the motto) isnt working. The matter is now being escalated to a political level.
The video above deals with HMRC. I dont have much to say about the progress; I have received no reference code/number, they did not get in touch (phone, E-mail, post), and its not clear if theyre doing anything at all to hold Sirius accountable. As noted earlier, HMRC inaction would say a lot about the system and reinforce the widespread belief that enforcement is done only/mostly against foes of the system. Irrespective of severity, scale, and strength of evidence.
Setting up a UI in a Web page is only the first step; does HMRC do anything with whats collected in this UI? its certainly not designed for anonymous reporting.
17:38
HMRC: You Can Click and Type to Report Crime, But No Feedback or Reference Number Given Techrights
Video download
link | md5sum
3658fca2df7acb84de0dde460f814926
HMRC Useless UI, No
Reference
Creative Commons Attribution-No Derivative Works 4.0
Summary: The crimes of Sirius Open Source were reported 7 days ago to HMRC (equivalent to the IRS in the US, more or less); but there has been no visible progress and no tracking reference is given to identify the report
THE system of accountability (checks and balances is the motto) isnt working. The matter is now being escalated to a political level.
HMRC inaction would say a lot about the system and reinforce the widespread belief that enforcement is done only/mostly against foes of the system.The video above deals with HMRC. I dont have much to say about the progress; I have received no reference code/number, they did not get in touch (phone, E-mail, post), and its not clear if theyre doing anything at all to hold Sirius accountable. As noted earlier, HMRC inaction would say a lot about the system and reinforce the widespread belief that enforcement is done only/mostly against foes of the system. Irrespective of severity, scale, and strength of evidence.
Setting up a UI in a Web page is only the first step; does HMRC do anything with whats collected in this UI? its certainly not designed for anonymous reporting.
17:06
IRC Proceedings: Friday, May 26, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-260523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-260523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-260523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-260523.gmi
Over HTTP:
|
... |
17:00
Why is the Solar Corona so HOT Terra Forming Terra
Now that we understand just what is going on, and that it has nothing whatsoever to do with hydrogen bombs and that the actual surface of trhe Sun is comparatively cold to the millions of degrees seen in the corona, we can make a conjecture.
It is that we are getting NNP ( Neutral Neutron Pair ) decay taking place in the corona which releases heat as it must. It is completely possible and even plausible that this is where it all happens and that something different is happening deep into the SUN.
that would certainly supply ample energy to keep the surface at the temperature we see while providing an expanding Solar wind all the way out to well past the Oort cloud while also accelerating dust as well. Yet compared to the age of the sun, it is very much scant and projections of mass change just do not wash. And if NNPs are been continously been produced in the solar core we may well be approaching steady state..
One central conjecture caused by cloud cosmology is that all large celestrial objects are collection shells built about an internal star like object continously producing new neutral particles. It could well be that our Earth itself has an egg shell we do not understand and that we also have a halo out to the Van Allen belts that ewe also do not understand.
Like yourself, i have accepted quite another scenario. Yet here we are with what i know is a real alternative.
.
Squeezed by the Shorts: Time to Ban Short Selling? Terra Forming Terra

mRNA and Breastfeeding: COVID-19 Vaccinated Mothers Who Breastfeed Babies Have Serious Reactions Including Death Terra Forming Terra

The Battle of Bakhmut: Russian Forces Take Full Control of the Province Terra Forming Terra
This was a conventional battle using masses of men, armor and most important artillary. It was sustained over two thirds of a year and Ukraine lost and I suspect thgey lost a lot of men here as well. The russians did as well but they where attacking.
16:59
Microsoft Launches an AI Tool to Take the Pain Out of Building Websites SoylentNews
Microsoft launches an AI tool to take the pain out of building websites:
Microsoft wants to take the pain out of designing web pages. AI is its solution.
Today marks the launch of Copilot in Power Pages in preview for U.S. customers, an AI-powered assistant for Microsoft's low-code business website creation tool, Power Pages. Given prompts, Copilot can generate text, forms, chatbots and web page layouts as well as create and edit image and site design themes.
To create a form, for example, users can simply describe the kind of form that they need and Copilot will build it and auto-generate the necessary backend database tables. Those tables can then be edited, removed or added to using natural language within Copilot.
"As the maker, you describe what you need in natural language and use Copilot suggestions to design web pages, create content and build complex business data forms for your website," Sangya Singh, VP of Power Pages at Microsoft, told TechCrunch in an email interview. "You no longer need to start from a blank slate."
Generating a website with AI isn't exactly a novel idea not in this day and age, at least. Tools like Jasper can handle copy, images, layouts and more, while generators like Mixo can create basic splash pages given a short description.
But Singh paints Copilot in Power Pages as more versatile than the competing solutions out there, while stressing that it's not a tool that could or should be used to generate whole spam sites.
[...] Singh claims that Copilot in Power Pages, though, which is powered by OpenAI's GPT-3.5 model, has "guardrails" to protect against issues that might crop up.
[...] "The key thing to note is that Power Pages Copilot is not an 'automatic' AI-pilot generating websites, but an 'AI assistant' to a human website maker hence the name Copilot where the maker can ask for suggestions on how to build different components of a business data-centric site," she added. "Giving the makers 'total control' is a principle we have where the maker is always in control if they want to apply the Copilot suggestion or tweak it further or discard it."
...
15:05
His Majestys Revenue and Customs, or HMRC, Just a Web Site for the Peasants (Not Even a Reference Number Given When Fraud Reported) schestowitz.com
Its like writing to zombie agencies that exist only on paper or selectively enforce (based on special interests)
Summary: One week ago we reported tax abuses of Sirius Open Source to HMRC; we still wait for any actual signs that HMRC is doing anything at all about the matter (Sirius has British government clients, so maybe theyd rather not look into that, in which case HMRC might be reported to the Ombudsman for malpractice)
15:01
One Week After Sirius Open Source Was Reported to HM Revenue and Customs (HMRC) for Tax Fraud: No Response, No Action, Nothing Techrights
Its like writing to zombie agencies that exist only on paper or selectively enforce (based on special interests)
Summary: One week ago we reported tax abuses of Sirius Open Source to HMRC; we still wait for any actual signs that HMRC is doing anything at all about the matter (Sirius has British government clients, so maybe theyd rather not look into that, in which case HMRC might be reported to the Ombudsman for malpractice)
15:00
Generating Hydrogen Peroxide for Disinfecting Water Using a Solar-Driven Catalyst Hackaday

Ensuring that water is safe to use and consume can be a real chore, especially for those who live in impoverished areas without access to safe drinking water. Here is where researchers at Stanford University hope that their recently developed low-cost catalyst can make a difference. This catalyst comes in the form of nano-sized particles (nanoflakes) consisting out aluminium oxide, molybdenum sulf...
14:00
SoylentNews Shutdown Status - A Show of Faith SoylentNews
I'm going to simply write this quickly now. I have had very long discussions with a member of the community known as kolie who has been negotiating to try and keep SN operational, and help provide a realistic plan for both rebuilding the site, and migration. I was approached after the shutdown post was put up via public contact information. He has offered help in the form of hosting, capital, and helping coding a replacement for rehash. He has convinced me that there are enough people in the community that it might be possible to pay down the technical debt.
I was asked to formally take the gun off SN's head, since it doesn't help recruit volunteers if there's a death sentence.
I am more than a little reluctance to do this, simply on the basis that there has been a long history on this site of saying "we'll do X", and then X never happens. The situation was also discussed prior with Matt, and quite a few other people before I finally made the decision after it became clear to me that the situation had become completely untenable. I spent weeks looking for an alternative before I finally resided myself that there were no other viable options. But sometimes you can be wrong, and sometimes you can get outside help.
One of my cited reasons for shutting down SN was that calls for help were left unanswered. However, said call finally got answered and came at the 11th hour, and as an unsolicited DM by someone who wanted to see the site go on. We have been discussing this at length since Monday, in a conversation that at this point has been longer than everything said in a private, staff channel for the last six months. So, I accept the possibility I can be wrong. More specifically, I hope I am wrong.
So, ultimately, I will put my faith in someone I have never met before. It might be absurd sounding, but that is ultimately how SN started. A bunch of people who never met coming together to make a replacement for Slashdot. I will take steps to keep SN going past the 30th. This may involve the legal entity changing, as the PBC already voted to dissolve itself. I will write more on this next week, since frankly, I need time to sit back and reflect. I also need to write some emails.
The staff have told me that they will not work with me going forward. For my part, the feeling is mutual.
There are also the facts that I listed in the shutdown letter. SN's codebase is effectively unmaintained since the departure of TMB. I've already discussed the state of infrastructure to death, but there's an objective truth here: SN's VMs were exposed to the open Internet on end-of-life operating systems for years and the database cluster had been in an extended failure with corrupted log tables. As I see it, the staff allowed SN to degrade to the point that it was about to entirely fail. As I understand it, they see me as acting rashly and irresponsibly in attempting to address the situation. I freely admitted I could have done b...
12:11
Saturn's Rings May be No More Than 400 Million Years Old SoylentNews
The earliest trilobites may have evolved before Saturn donned its icy hoops
Saturn's rings might have formed while trilobites scuttled about on Earth. Space dust has been accumulating on the icy halos for no more than 400 million years, researchers report in the May 12 Science Advances.
The 4.5-billion-year-old planet appears to have acquired its iconic ornamentation relatively recently, says physicist Sascha Kempf of the University of Colorado Boulder. "We're quite lucky to see a ring in the first place."
The rings of Saturn are made of countless icy particles, which become covered with dust as tiny meteoroids strike them. These dustings darken the rings' complexion, like mud sullies snow on roads in winter.
[...] The age of the rings has been debated for decades [...]. Even after the new study, there's still disagreement.
If the rings are somehow losing dust over time, they could be ancient, says planetary scientist Aurlien Crida of Universit Cte d'Azur in Nice, France, who was not involved in the study. "Possibly as old as Saturn."
It seems clear that the rings have been exposed to micrometeoroid impacts for at least a hundred million years, Crida says. But simulations of the rings' formation from the gravitational shredding of an early moon suggest their size is consistent with an age of billions of years, he says. And researchers have reported silicate grains falling from the rings into Saturn's atmosphere (SN: 10/4/18). Some unidentified process might be cleaning the rings of the micrometeoroid dust, making them appear younger than they are, Crida says.
[...] Experiments that smash micrometeoroids into ice particles could help resolve the discrepancy, Crida says. For now, the debate over the age of the rings lives on.
Journal Reference:
S. Kempf et al. Micrometeoroid infall onto Saturn's
rings constrains their age to no more than a few hundred million
years. Science Advances. Vol. 9, May 12, 2023. doi:
10.1126/sciadv.adf8537
Read more of this story at SoylentNews.
12:00
Where Exactly Did That Network Packet Come From? Hackaday

Have you ever noticed that some websites can figure out, at least roughly, where you are? Sometimes they use it to find you a closer content provider. Or they might block you from seeing certain things while offering you other things specific to your location. This is possible because there are databases that map IPs to locations. [Mark Litwintschik] looks at using those databases from an API or downloading them into your own database. He also shows some very large database queries, which is interesting, too. He uses IPInfo, although there are other providers. Some only provide a limited number of lookups, but there are plenty of free tiers for low-volume usage.
The database changes every day. Of course, each provider has a different way of getting data, and so there are differences. [Mark] compares the IPInfo dataset against MaxMinds also free database. That involved comparing over 3 billion records! Actually, the 3 billion are the number of IPs that matched up in both databases. There were an additional 118 million that didnt match and 34 million that were not in the MaxMind database.
Of course, of the ones that didnt match it is hard to say which one was correct. As [Mark] mentions, IP address get sold they are worth about $45 each, he says so an IP that is in Texas one day might be in...
11:35
Links 26/05/2023: Weston 12.0 Highlights and US Debt Limit Panic Techrights
![]()
Contents
-
GNU/Linux
-
Desktop/Laptop
-
Carson City Linux Users Group
...The Carson City Linux Users Group will be meeting Saturday, June 17 at 10:00 AM at the Carson City Public Library. Upstairs in Meeting room 1.
-
-
11:29
Gemini Links 26/05/2023: New People in Gemini Techrights
-
Gemini* and Gopher
-
Personal
-
SpellBinding: EXNOQUI Wordo: SHEER
-
Dont you love them, madly
Most peoples talking sounds like madness to me.
Somehow that doesnt seem nearly so much the case with their writing.
Why?
I think its because writing filters out a lot of behavior that screams Automaton! to me, e.g. glazed eyes, excessively making the same point in various ways, misspeak corrections, the sense of becoming possessed because of the likes of increasing volume, increasingly crazed facial expressions and, of course, the litany becoming increasingly I/me/mine focused.
-
Small Errors
This is a perfectly cromulent sentence, though without telepathy we cannot be sure whether I eat oranges, where the eating in some way involves furniture is the intended message, or whether the speaker has swapped the i and e and meant to write that they eat the oranges in some way involving liking (nelci comes up a lot in beginner lojban materials, less so nilce).
-
Bike Things
This morning on my bike to work, I passed:
- A hot air balloon making an emergency landing in a field
- A suspiciously-placed board with an upright nail
- A dead fishHot air balloons regularly take off near my house on summer mornings. This one was pretty low-flying over a neighborhood, and seemed to briefly touch down in a field before taking off again.
-
3k in 16:17
today was a big step up for me. i landed my best pace in my relatively recent running antics by a fair bit. i didnt feel exhausted. i didnt feel like i was pushing myself too hard. i didnt feel like my nose was conspiring against me. i managed to get my best time yet despite me being far from the only person to tread my usual route. i ran past ladies with...
-
-
11:16
Wine 8.9 Released With More Wayland Bits, Mono 8.0 Upgrade Phoronix
Ahead of the US holiday weekend is the latest bi-weekly release of Wine for enjoying Windows games and applications running well on Linux and other platforms thanks to this open-source project...
10:28
09:28
AI is Changing How Americans Find Jobs, Get Promoted and Succeed at Work SoylentNews
AI is changing how Americans find jobs, get promoted and succeed at work:
Whether we realize it or not, advancements in artificial intelligence are increasingly influencing the paths of our careers.
Advancements in human capital management systems [HCM], more strategic and data-driven human resource and talent management practices, and increased attention to bias are all factors that are changing how people are hired, developed, promoted and fired.
I teach and work in talent management and leadership development. I've used these programs and practices in the real world and continue to learn and research how these practices are changing. Artificial intelligence and systems are already big business, grossing over US$38 billion in 2021. Without a doubt, AI-driven software has the potential to advance quickly and change how companies make strategic decisions about their employees.
Imagine you apply for a job in the very near future. You upload your carefully written rsum through the company website, noting that the platform looks eerily similar to other platforms you've used to apply for other jobs. After your rsum is saved, you provide demographic information and complete countless fields with the same data from your rsum. You then hit "submit" and hope for a follow-up email from a person.
Your data now lives within this company's human capital management system. Even if they collect them, very few companies are looking at rsums anymore; they're looking at the info you type into those tiny boxes to help make comparisons between you, dozens or hundreds of other applicants, and the job requirements. Even if your rsum demonstrates that you are the most qualified applicant, it alone is unlikely to catch the eye of the recruiter, because the recruiter's attention is elsewhere.
Let's say you get the call, you ace the interview and the job is yours. Your information hits another stage within the company's database, or HCM: active employee. Your performance rat...
09:00
Fly Like You Drive With This Flying RC Drift Car Hackaday

So its 2023, and you really feel like we should have flying cars by now, right? Well, as long as you ignore the problem of scale presented by [Nick Rehm]s flying RC drift car, we pretty much do.
At first glance, [Nick]s latest build looks pretty much like your typical quadcopter. But the design has subtle differences that make it more like a car without wheels. The main difference is the pusher prop at the aft, which provides forward thrust without having to pitch the entire craft. Other subtle clues include the belly-mounted lidar and nose-mounted FPV camera, although those arent exactly unknown on standard UAVs.
The big giveaway, though, is the RC car-style remote used to fly the drone. Rather than use the standard two-joystick remote, [Nick] rejiggered his dRehmFlight open-source flight control software to make operating the drone less like flying and more like driving. The lidar is used to relieve the operator of the burden of altitude keeping by holding the drone at about a meter or so off the deck. And the video be...
08:59
I got a whole bunch of comics in the mail yesterday, so its a comics readin day today. This time around, the comics are from all over that is, mostly ordered directly from publishers and stuff, and very little from shops.
And Im feeling kinda nostalgic today, so for music its (once again) gonna be all Talking Heads & Friends.
| Talking Heads: 77 (Sire) |
 |
13:54: Sammy the Mouse III by Zak Sally
A slight wait between issues this is a continuation of the...
08:05
Californians: Speak Up To Protect People Seeking Repro and Gender-Affirming Care Deeplinks
We need your help to advance A.B. 793, a bill authored by Assemblymember Mia Bonta to protect people seeking abortion and gender-affirming care from dragnet-style digital surveillance. It's facing law enforcement opposition as it heads to the Assembly floor for a vote. California's Assemblymembers need to hear from you to stand up for what's right.
Tell Your Assemblymember to Support aB 793
EFF is a proud co-sponsor of A.B. 793, which targets law enforcement demands that can compel tech companies to reveal the identities of people in their records who have been near a specific place or looked up particular keywords online. These demands, known as reverse demands, geofence warrants, or keyword warrants, are shadowy tools with questionable effectiveness, that have also falsely led police to arrest people simply going about their daily lives. Hundreds (sometimes thousands) of people can be caught up in a single demand without cause.
Following the recent Dobbs decision and an increase in state law criminalizing gender-affirming care, these broad warrants pose an even greater threat. People are coming to California to get care they can no longer get at home. But law enforcement officials from other states can ask for data on who's been around certain clinics or searched for information on how to seek care in California. Companies such as Googlewhich also supports the billhave recently seen a sharp increase in such requests.
Law enforcement officials in California want to stop this bill. Your Assemblymembers need to hear these demands not only threaten everyone's privacy but also pose a serious, immediate danger to people seeking reproductive or gender-affirming care in California. This bill is a priority bill for the California Women's Caucus and the California Future of Abortion Council. It is also a component of the NARAL Reproductive Freedom Scorecard. More than 50 civil liberties, reproductive justice, healthcare equity, and LGBTQ+ advocacy groups joined us to support the bill, including NARAL Pro-Choice California...
07:44
New PowerExchange Backdoor linked to an Iranian APT group Security Affairs
An alleged Iran-linked APT group targeted an organization linked to the United Arab Emirates (U.A.E.) with the new PowerExchange backdoor.
Researchers from the Fortinet FortiGuard Labs observed an attack targeting a government entity in the United Arab Emirates with a new PowerShell-based backdoor dubbed PowerExchange.
The experts speculate that the backdoor is likely linked to an Iran-linked APT group.
The backdoor uses emails for C2 communications, where the C2 is the victims Microsoft Exchange server. The investigation conducted by Fortinet revealed the presence of other implants on various servers, including a new web shell, dubbed ExchangeLeech, on Microsoft Exchange servers.
The infection chain commenced with spear phishing messages using a zip file named Brochure.zip in attachment. The archive contained a malicious .NET executable (Brochure.exe) which is an executable with an Adobe PDF icon. Upon running the executable, it displays an error message box while downloads and executes the final payload.

The malware relies on Exchange Web Services (EWS) API to connect to the victims Exchange Server and uses a mailbox on the server to send and receive encoded commands.
The PowerShell script is a custom backdoor. Its name is derived from the nature of the C2 channel as it utilizes the Exchange Web Services (EWS) API to connect to the victims Exchange server and uses mailboxes on the server to send and receive commands from its operator. reads the...
06:42
New York City is Sinking. Its Far From Alone SoylentNews
New York City Is Sinking. It's Far From Alone:
Add up the million or so buildings in New York City, and you get something on the order of 1.7 trillion pounds of weight pressing on the earthand that's not even counting all the other infrastructure, like roads and sidewalks. All that weight is deforming the ground, like bowling balls on a memory foam mattress, and causing a type of sinking known as subsidence, when land slowly compresses.
New research finds that, on average, subsidence rates in NYC are between 1 and 2 millimeters per year, but in some places that's up to 4 millimeters. This may not sound like a worrying figure, but compounded year after year, it's significant sinking that's effectively doubling the relative sea-level rise in the metropolis. "You have about 1 to 2 millimeters of sea level going up, while you have 1 to 2 millimeters on average going down," says United States Geological Survey geophysicist Tom Parsons, coauthor of a new paper describing the research. "It's a common issue with cities around the world. It appears there's a definite link between urbanization and subsidence."
Parts of Jakarta, Indonesia, for instance, are sinking by nearly a foot a year. The San Francisco Bay Area could lose up to 165 square miles of coastline due to a combination of rising seas and subsidence. And just last month, another team of researchers reported finding subsidence up and down the East Coast, as high as 10 millimeters a year in parts of Delaware.
The primary way to cause dramatic sinking is the over-extraction of groundwater, which is the case in Jakarta; drained aquifers collapse like empty water bottles. But in NYC, subsidence depends on the composition of the underlying soil. Long ago, glaciers scraped across the area, depositing sediments. Lakes formed too, depositing still more sediments. So the metropolis is built on a complex mix of materials like clay, silt, and artificial fill, which are more prone to subsidence, as well as sand and gravel, which tend to resist it.
Read more of this story at SoylentNews.
06:40
2.5 Billion Visits: ACE Targets 9anime Among Several Pirate Anime Sites TorrentFreak
 In
the face of legislation designed to thwart its growth, seizures,
prosecutions, dozens of arrests and countless prison sentences have
done little to prevent piracy.
In
the face of legislation designed to thwart its growth, seizures,
prosecutions, dozens of arrests and countless prison sentences have
done little to prevent piracy.
Anti-piracy enforcement actions, including dozens by the Alliance for Creativity and Entertainment, have taken hundreds of sites out of the game. Thats a solid base for arguing that piracy volumes couldve been much worse without so much enforcement.
The reality is that sites continue to emerge with some notable examples generating extraordinary levels of traffic, at a scale never seen before. History tells us that wont continue indefinitely; pirate sites may come and go but Hollywood is in for the long haul and then some.
9anime: Huge, Successful, and a Prime Target
One of the current batch of piracy behemoths is 9anime, a free streaming platform dedicated to Japanese cartoons. It currently receives in excess of 214 million visits per month, an incredible 2.5+ billion per year.
A DMCA subpoena application filed at a California court on Thursday shows that ACE has not given up on its plan to reduce 9animes traffic to zero. Like many times before, ACE via the MPA wants Cloudflare to give up information on its customers, 9anime included.
This information typically includes names, physical addresses,
IP addresses,
telephone numbers, email addresses, and payment information.
However, ACE also seeks additional information relating to account
updates and histories, which could help to fill in some crucial
blanks when combined with intelligence obtained elsewhere.
Theres no doubt that 9anime will remain a priority enforcement target. At the time of writing the 9animetv.to domain is ranked #164 globally and with over 30% of that traffic coming f...
06:19
[$] Cloud-storage optimizations LWN.net
"I/O hints" for storage devices, which are meant to improve performance by giving the devices extra information about the nature of the I/O, have a long history with Linux. But the code for write hints was "ripped out last year", according to a message from Ted Ts'o proposing a discussion about new optimizations for cloud-storage devices. That discussion took place in a combined storage and filesystem session at the 2023 Linux Storage, Filesystem, Memory-Management and BPF Summit. In it, Ts'o proposed that the Linux community define its own set of hints rather than just following along with the hints in the standardswhich have largely been ignored by the vendors in any case.
06:00
Nice Try, But Its Not Aperture Synthesis Hackaday

Some of the worlds largest radio telescopes are not in fact as physically large as they claim to be, but instead are a group of telescopes spread over a wide area whose outputs are combined to produce a virtual telescope equal in size to the maximum distance between the constituents of the array. Can this be done on the cheap with an array of satellite dishes? Its possible, but as [saveitforparts] found out when combining a set of Tailgater portable dishes, not simply by linking together the outputs from a bunch of LNBs.
The video below the break still makes for an interesting investigation and the Tailgater units are particularly neat. It prompted us to read up a little on real aperture synthesis, which requires some clever maths and phase measurement for each antenna. Given four somewhat more fancy LNBs with phase-locked local oscillators and an software-defined radio (SDR) for each one then he might be on to something.
If youre curious about the cyberdeck in the video, you might like to read our coverage of it. And the Tailgater might be a bit small, but you can still make a useful rad...
05:59
CVE-2023-33234: Apache Airflow CNCF Kubernetes Provider: KubernetesPodOperator RCE via connection configuration Open Source Security
Posted by Elad Kalif on May 26
Severity: lowAffected versions:
- Apache Airflow CNCF Kubernetes Provider 5.0.0 through 6.1.0
Description:
Arbitrary code execution in Apache Airflow CNCF Kubernetes provider image and resources via Airflow connection.
In order to exploit this weakness, a user would already need elevated permissions (Op or Admin) to change the
connection object in this manner. Operators should upgrade to...
05:40
Gaming Firms and Community Members Hit by Dark Frost Botnet HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
According to researchers, the most prominent targets of Dark Frost include gaming companies, online streaming services, game server hosting providers, and gaming community members.
This is a post from HackRead.com Read the original post: Gaming Firms and Community Members Hit by Dark Frost Botnet
05:15
Distribution Release: Oracle Linux 9.2 DistroWatch.com: News
Simon Coter has announced the release of Oracle Linux 9 Update Hat Enterprise Linux (RHEL) 9.2 source code but optionally using a custom-compiled "Unbreakable Enterprise Kernel (UEK)": "The latest releases of Oracle Linux enhance the user experience....
04:29
Mirai Malware Hits Zyxel Devices After Command Injection Bug HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
A variant of the Mirai botnet is targeting Zyxel Firewalls after exploiting a newly patched operating system command injection vulnerability.
This is a post from HackRead.com Read the original post: Mirai Malware Hits Zyxel Devices After Command Injection Bug
04:00
AMD Posts QDMA Linux Driver For Review Phoronix
A new AMD open-source driver posted for code review that's aiming for the upstream Linux kernel is the QDMA driver...
03:57
Windows to Finally Support 30 Year Old Archive Format SoylentNews
Windows to Finally Support 30 Year Old Archive Format:
It's been 30 years since Russian software engineer Eugene Roshal created the RAR archive format. RAR allows users to compress files so they take up less room on your hard drive. However, you needed a special program like WinRAR to open RAR files on Windows for the better part of three decades.
That's all changing soon. This week Microsoft quietly announced that Windows 11 will finally support RAR files natively. In a long-winded blog post about the future of AI, the company slipped in RAR support in the "In addition..." section. If you were just casually scrolling through, you may have missed it.
"We have added native support for additional archive formats, including tar, 7-zip, rar, gz and many others using the libarchive open-source project. You now can get improved performance of archive functionality during compression on Windows," the blog post states.
Granted, this move may not matter much to people who have never heard of a RAR file. But, those who work with archive formats know the sheer annoyance of not being able to open a somewhat common file format without special software like WinRARa file extraction program that people can pay for but generally don't.
See also: 28 years later, Windows finally supports RAR files submitted by owl.
Read more of this story at SoylentNews.
03:00
Keysight E5081A ENA-X produces error vector magnitude measurements Help Net Security
Keysight Technologies introduces the Keysight E5081A ENA-X, the midrange vector network analyzer (VNA) that produces error vector magnitude (EVM) measurements and accelerates the characterization of 5G component designs by up to 50%. Demand for ever-increasing data speeds with ultra-low latency is pushing the next generation of wireless communications systems to operate at higher radio frequencies (RF). To ensure 5G New Radio (NR) transmitters meet these operational demands, RF engineers must fully test the design and More
The post Keysight E5081A ENA-X produces error vector magnitude measurements appeared first on Help Net Security.
02:37
Phishing Domains Tanked After Meta Sued Freenom Krebs on Security
The number of phishing websites tied to domain name registrar Freenom dropped precipitously in the months surrounding a recent lawsuit from social networking giant Meta, which alleged the free domain name provider has a long history of ignoring abuse complaints about phishing websites while monetizing traffic to those abusive domains.

The volume of phishing websites registered through Freenom dropped considerably since the registrar was sued by Meta. Image: Interisle Consulting.
Freenom is the domain name registry service provider for five so-called country code top level domains (ccTLDs), including .cf for the Central African Republic; .ga for Gabon; .gq for Equatorial Guinea; .ml for Mali; and .tk for Tokelau.
Freenom has always waived the registration fees for domains in these country-code domains, but the registrar also reserves the right to take back free domains at any time, and to divert traffic to other sites including adult websites. And there are countless reports from Freenom users whove seen free domains removed from their control and forwarded to other websites.
By the time Meta initially filed its lawsuit in December 2022, Freenom was the source of well more than half of all new phishing domains coming from country-code top-level domains. Meta initially asked a court to seal its case against Freenom, but that request was denied. Meta withdrew its December 2022 lawsuit and re-filed it in March 2023.
The five ccTLDs to which Freenom provides its services are the TLDs of choice for cybercriminals because Freenom provides free domain name registration services and shields its customers identity, even after being presented with evidence that the domain names are being used for illegal purposes, Metas complaint charged. Even after receiving notices of infringement or phishing by its customers, Freenom continues to license new infringing domain names to those same customers.
Meta pointed to research from Interisle Consulting Group, which discovered in 2021 and again last year that the five ccTLDs op...
02:25
Severe Flaw in Google Cloud's Cloud SQL Service Exposed Confidential Data The Hacker News
A new security flaw has been disclosed in the Google Cloud Platform's (GCP) Cloud SQL service that could be potentially exploited to obtain access to confidential data. "The vulnerability could have enabled a malicious actor to escalate from a basic Cloud SQL user to a full-fledged sysadmin on a container, gaining access to internal GCP data like secrets, sensitive files, passwords, in addition
02:00
Hackaday Podcast 220: Transparent Ice, Fake Aliens, and Bendy Breadboards Hackaday

You can join Elliot and Al as they get together to talk about their favorite hacks of the week. Theres news about current contests, fake alien messages, flexible breadboards, hoverboards, low-tech home automation, and even radioactive batteries that could be a devices best friend.
We have a winner in the Whats that Sound competition last week, which was, apparently, a tough one. Youll also hear about IC fabrication, FPGAs, and core memory. Lots to talk about, including core memory, hoverboards, and vacuum tubes.
Check out the links below if you want to follow along, and as always, tell us what you think about this episode in the comments!
02:00
Edgewater Wireless launches MLX 488 WiFi7 Spectrum Slicing platform Help Net Security
Edgewater Wireless Systems has announced its next-generation of Wi-Fi Spectrum Slicing powered silicon solutions targeting residential, enterprise and prosumer applications. Building on the latest Wi-Fi standard, WiFi7 (802.11BE), Edgewaters platform offers more physical channel capacity than single-channel, legacy Wi-Fi architectures bringing lower latency and reduced contention for existing and new devices. With Beta Spectrum Slicing capable silicon now available for select partner evaluations, engineering samples of Edgewaters WiFi7 silicon are targeted by the end More
The post Edgewater Wireless launches MLX 488 WiFi7 Spectrum Slicing platform appeared first on Help Net Security.
01:24
Can a chatbot help people with eating disorders as well as another human? Lifeboat News: The Blog
National eating disorder helpline fired its staff and replaced them with AI.
The National Eating Disorders Association is shutting its telephone helpline down, firing its small staff and hundreds of volunteers. Instead its using a chatbot and not because the bot is better.
01:23
Neuralink: Elon Musks brain chip firm says US approval won for human study Lifeboat News: The Blog
The billionaires Neuralink implant company wants to help restore peoples vision and mobility.
01:23
Microsoft Build event in 5 minutes Lifeboat News: The Blog

Microsoft announced some major news at its annual Build keynote. This years Build heavily focused on AI, with new additions of the CoPilot experience to Windows 11 and Edge, as well as new Bing AI and Copilot plugins for OpenAIs ChatGPT. Plus, Bing is now the default search for ChatGPT. Heres everything you missed. #Microsoft #Tech #News.
0:00 Intro.
0:05 Bing and Chat GPT Updates.
0:38 Plugins in Bing and Chat GPT
2:00 Windows Copilot.
3:10 Microsoft Fabric.
Subscribe: http://goo.gl/G5RXGs.
Like The Verge on Facebook: https://goo.gl/2P1aGc.
Follow on Twitter: https://goo.gl/XTWX61
Follow on Instagram: https://goo.gl/7ZeLvX
Follow on TikTok: http://bit.ly/42VeCVU
The Vergecast Podcast: https://pod.link/430333725
Decoder with Nilay Patel: http://apple.co/3v29nDc.
More about our podcasts: https://www.theverge.com/podcasts.
Community guidelines: http://bit.ly/2D0hlAv.
Wallpapers from The Verge: https://bit.ly/2xQXYJr.
01:22
Daily briefing: Quantum computers are all terrible but researchers arent worried Lifeboat News: The Blog
Even the scientists who have made quantum computers their lifes work say they cant do anything useful yet but the future is bright. Plus, how Chinas data privacy laws affects researchers and LIGO is back, better than ever.
01:22
Using nuclear spins neighboring a lanthanide atom to create Greenberger-Horne-Zeilinger quantum states Lifeboat News: The Blog
Researchers have experimentally demonstrated a new quantum information storage protocol that can be used to create Greenberger-Horne-Zeilinger (GHZ) quantum states. There is a great deal of interest in these complex entangled states because of their potential use in quantum sensing and quantum error correction applications.
Chun-Ju Wu from the California Institute of Technology will present this research at the Optica Quantum 2.0 Conference and Exhibition, as a hybrid event June 1822 in Denver, Colorado.
Quantum-based technologies store information in the form of qubits, the quantum equivalent of the binary bits used in classical computing. GHZ states take this a step further by entangling three or more qubits. This increased complexity can be used to store more information, thus boosting precision and performance in applications such as quantum sensing and networking.
01:18
Video Friday: The Coolest Robots IEEE Spectrum

Video Friday is your weekly selection of awesome robotics
videos, collected by your friends at IEEE Spectrum
robotics. We also post a weekly calendar of upcoming robotics
events for the next few months. Please
send us your events for inclusion.
ICRA 2023: 29 May2 June 2023, LONDON
Energy Drone & Robotics Summit: 1012 June 2023, HOUSTON
RoboCup 2023: 410 July 2023, BORDEAUX, FRANCE
RSS 2023: 1014 July 2023, DAEGU, SOUTH KOREA
IEEE RO-MAN 2023: 2831 August 2023, BUSAN, SOUTH KOREA
IROS 2023: 15 October 2023, DETROIT
CLAWAR 2023: 24 October 2023, FLORIANOPOLIS, BRAZIL
Humanoids 2023: 1214 December 2023, AUSTIN, TEXAS
Enjoy todays videos!
Weve just relaunched the IEEE Robots Guide over at RobotsGuide.com, featuring new robots, new interactives, and a complete redesign from the ground up. Tell your friends, tell your family, and explore nearly 250 robots in pictures and videos and detailed facts and specs, with lots more on the way!
The qualities that make a knitted sweater comfortable and easy to wear are the same things that might allow robots to better interact with humans. RobotSweater, developed by a research team from Carnegie Mellon Universitys Robotics Institute, is a machine-knitted textile skin that can sense contact and pressure.
...
01:13
Scientists Working to Generate Electricity From Thin Air Make Breakthrough SoylentNews
Scientists making the "Air-gen" device have discovered that any material can be used to generate electricity from the air:
Scientists have invented a device that can continuously generate electricity from thin air, offering a glimpse of a possible sustainable energy source that can be made of almost any material and runs on the ambient humidity that surrounds all of us, reports a new study.
The novel "air generator," or Air-gen, is made from materials with holes that are under 100 nanometers in length, which is a scale thousand times smaller than a human hair. This design can pull electricity from water droplets in the air for much longer periods than previous concepts, the researchers report, suggesting that it could eventually provide a continuous and sustainable source of power. Researchers hope the technique could eventually help to fight climate change by serving as an alternative to fossil fuels.
[...] Now, researchers at the University of Massachusetts, Amherst, have developed an Air-gen device that yields electricity from contact with water droplets that pass through its porous material. In this way, the Air-gen technology creates "a spontaneous and sustained charging gradient for continuous electric output" that "opens a wide door for the broad exploration of sustainable electricity from ambient air," according to a study published on Wednesday in Advanced Materials.
[...] Indeed, the results revealed that practically any material could become an Air-gen device provided it was perforated with tiny holes measuring 100 nanometers or fewer. At this scale, the holes are big enough to allow water to pass through an upper chamber into a lower chamber, but are small enough that the droplets make contact with the material as they move down through the holes. As a consequence, a charge imbalance is created in the device because the water droplets increase the charge of the upper layer by soaking it as they move into the lower chamber.
Read more of this story at SoylentNews.
01:00
Hopr raises $500K to accelerate product-led go-to-market strategy Help Net Security
Hopr has secured $500K in funding from TEDCO, that has invested an additional $300K, doubling down on their initial investment of $200K, which occurred last year. The outlook for startups has been rocky over the past 12 months due to liquidity and profitability concerns, but TEDCOs secondand increasedinvestment in our company is evidence of strong investor confidence, which is a testament to both our company and its technologys ability to generationally improve cybersecurity, said Tom More
The post Hopr raises $500K to accelerate product-led go-to-market strategy appeared first on Help Net Security.
01:00
UAV Flight Controller Saves Weight Hackaday

When building autonomous airborne vehicles like drones or UAVs, saving a little bit of weight goes a long way, literally. Every gram saved means less energy needed to keep the aircraft aloft and ultimately more time in the air, but unmanned vehicles often need to compromise some on weight in order to carry increased computing abilities. Thankfully this one carries a dizzying quantity of computer power for an absolute minimum of weight, and has some clever design considerations to improve its performance as well.
The advantage of this board compared to other similar offerings is that it is built to host a Raspberry Pi Compute Module 4, while the rest of the flight controllers are separated out onto a single circuit board. This means that the Pi is completely sandboxed from the flight control code, freeing up computing power on the Pi and allowing it to run a UAV-specific OS like OpenHD or RubyFPV. These have a number of valuable tools available for unmanned flight, such as setting up a long range telemetry and camera links. The system itself supports dual HD camera input as well as additional support for other USB devices, and also includes an electronic speed controller mezzanine which has support for quadcopters and fixed wing crafts.
Separating non-critic...
00:52
Dark Frost Botnet targets the gaming sector with powerful DDoS Security Affairs
Researchers spotted a new botnet dubbed Dark Frost that is used to launch distributed denial-of-service (DDoS) attacks against the gaming industry.
Researchers from Akamai discovered a new botnet called Dark Frost that was employed in distributed denial-of-service (DDoS) attacks.
The botnet borrows code from several popular bot families, including Mirai, Gafgyt, and Qbot.
The Dark Frost botnet was used to target gaming companies, game server hosting providers, online streamers, and even other members of the gaming community who the threat actor interacted with directly.
The researchers first gathered a Dark Frost binary sample on February 28, 2023, that targeted one of its HTTP honeypots. The threat actors were attempting to exploit a remote code execution (RCE) in misconfigured Hadoop YARN servers. The experts highlight that the vulnerability exploited in the attacks has been in existence since 2014.
According to a screenshot taken by the malware author, the botnet was composed of at least 414 machines as of February 2023. Most of the infected machines are based on ARMv4 architectures, specifically MIPSEL and x86.
The botnet operators compiled the bot code specifically for ARMv4 and ARMv7 because ARMv4 is compatible with ARMv5 and ARMv6, this means that the malware can also target modern ARMv7 architecture.
The analysis of the bot revealed that the malware supports eight total attacks, including UDP and TCP, and more curious ones, such as zgoflood.
Akamai researchers estimated that the botnet can launch DDoS attacks of approximately 629.28 Gbps through a UDP flood attack.
To continue the benchmark correctly, we had to start launching these attacks at the loopback to avoid fragmentation and listen on the loopback interface to re-measure (Table 2). reads the analysis published by Akamai.
| Packet size | Packets captured | Total size | Output |
|---|---|---|---|
| 1,024 | 1,659,840 | 1.4G | 1.12 Gbps |
| 2,048 | 1,445,158 | 1.9G | 1.52 Gbps |
| 4,096 | 828,681 | 1.9G | 1.52 Gbps |
| 8,192 | 432,884 |
00:30
Coalesce Partner Program helps automate the modern data stack Help Net Security
Coalesce has announced a new partner program to expand training options and teamwork, as well as to help Snowflake Data Cloud customers more effectively manage their modern data stack. The Coalesce Partner Program now features three tiers Select, Premier, and Elite offering various incentives including training, sales and marketing, and referral commissions. Coalesce partners are equipped with resources to build their Coalesce expertise and bring innovative joint solutions to the data market. Since More
The post Coalesce Partner Program helps automate the modern data stack appeared first on Help Net Security.
00:25
Development Release: Mageia 9 Beta 2 DistroWatch.com: News
Yves Brungard has announced that the second beta build of Mageia 9 is now available for download and testing. The new development beta of Mageia 9.....
00:25
00:23
Those Using The XFS File-System Will Want To Avoid Linux 6.3 For Now Phoronix
Multiple users have been reporting metadata corruption issues on the XFS file-system when upgrading to the Linux 6.3 stable kernel...
00:00
This Week in Security: Gitlab, KeyPassMini, and Horse Hackaday

Theres a really nasty CVSS 10.0 severity vulnerability in Gitlab 16.0.0. The good news is that this is the only vulnerable version, and the fix came a mere two days after the vulnerable release. If you happened to be very quick to go to 16.0.0, then be very quick to get the fix, because CVE-2023-2825 looks like a bad one.
An unauthenticated malicious user can use a path traversal vulnerability to read arbitrary files on the server when an attachment exists in a public project nested within at least five groups.
Thats a very specific set of requirements for vulnerability, so it seems like hardly any installs would be vulnerable. The rest of the story is that regular users can create groups, and many installs allow for open user registration. So if youre running Gitlab 16.0.0, update now!
KeyPassMini
A Redditor got a surprising notice that someone attempted to access a bank account, but failed two-factor authentication. That seemed odd, and led the Redditor down the rabbithole of auditing applications. And one iOS app in particular stood out as maybe problematic KeyPassMini.
The app was a mobile client for KeyPass, the password manager. The proble...
00:00
Cognigy and Black Box partnership to accelerate deployment of conversational AI Help Net Security
Cognigy has entered into a strategic reseller partnership with Black Box. By combining Cognigys conversational AI-based technology with Black Boxs comprehensive CX solution practice, including a global network of CX professionals, the companies will deliver AI-based solutions that drive customer experiences. The benefits to customers of the partnership include increased automation and efficiency, as well as improved customer satisfaction and loyalty. By automating routine customer interactions with AI-based virtual assistants, businesses can free up contact More
The post Cognigy and Black Box partnership to accelerate deployment of conversational AI appeared first on Help Net Security.
Friday, 26 May
23:40
[$] Mitigating vmap lock contention LWN.net
The "vmap area" is a range of kernel address space used when the kernel needs to virtually map a range of memory; among other things, memory allocations obtained from vmalloc() and loadable modules are placed there. At the 2023 Linux Storage, Filesystem, Memory-Management and BPF Summit, Uladzislau Rezki, presenting remotely, explained a performance problem related to the vmap area and discussed possible solutions.
23:39
[$] Optimizing single-owner memory LWN.net
The kernel's memory-management subsystem is optimized for the sharing of resources to the greatest extent possible. But, as Pasha Tatashin pointed out during a memory-management session at the 2023 Linux Storage, Filesystem, Memory-Management and BPF Summit, a lot of memory has a single owner and will never be shared. He presented some ideas for optimizing the management of that memory to a somewhat skeptical crowd.
23:37
Security updates for Friday LWN.net
Security updates have been issued by Debian (sniproxy), Fedora (c-ares), Oracle (apr-util, curl, emacs, git, go-toolset and golang, go-toolset:ol8, gssntlmssp, libreswan, mysql:8.0, thunderbird, and webkit2gtk3), Red Hat (go-toolset-1.19 and go-toolset-1.19-golang and go-toolset:rhel8), Slackware (ntfs), SUSE (rmt-server), and Ubuntu (linux-raspi, linux-raspi-5.4 and python-django).
23:25
Critical Flaw in Inea ICS Product Exposes Industrial Organizations to Remote Attacks Lifeboat News: The Blog
A critical vulnerability found in a remote terminal unit (RTU) made by Slovenia-based industrial automation company Inea can expose industrial organizations to remote hacker attacks.
The existence of the vulnerability came to light last week, when the US Cybersecurity and Infrastructure Security Agency (CISA) published an advisory to inform organizations. The vendor has released a firmware update that patches the issue.
The security hole, tracked as CVE-20232131 with a CVSS score of 10, impacts Inea ME RTUs running firmware versions prior to 3.36. This OS command injection bug could allow remote code execution, CISA said.
23:24
How not to get your CCTV cameras hacked? Lifeboat News: The Blog
At a time when incidents of CCTV Cameras are getting hacked across the world has reached an all-time high, Raxa Security Solutions Ltd, a security company has joined hands with a Bangalore-based IoT cyber security company, Redinent Innovations to address this imperative and serious need.
23:24
Irrigation Systems in Israel Disrupted Lifeboat News: The Blog
Automated irrigation systems in the Northern part of Israel were briefly disrupted recently in an attack that once again shows how easy it can be to hack industrial control systems (ICS).
The Jerusalem Post reported that hackers targeted water controllers for irrigation systems at farms in the Jordan Valley, as well as wastewater treatment control systems belonging to the Galil Sewage Corporation.
Farms were warned by Israels National Cyber Directorate prior to the incident, being instructed to disable remote connections to these systems due to the high risk of cyberattacks. Roughly a dozen farms in the Jordan Valley and other areas failed to do so and had their water controllers hacked. This led to automated irrigation systems being temporarily disabled, forcing farmers to turn to manual irrigation.
23:23
Auto-GPT, BabyAGI, and AgentGPT: How to use AI agents Lifeboat News: The Blog
AI agents like Auto-GPT, AgentGPT, and BabyAGI build off of OpenAIs API to automate tasks. Heres how to use them.
23:23
Heres why faster-than-light travel leads to maddening time paradoxes Lifeboat News: The Blog

Forever intrigued by attempting the impossible, weve made traveling faster than the speed of light a staple of our works of science fiction. Most science fiction stories feature some way of getting from point A to point B faster than light, whether its via activating the warp drive or jumping into hyperspace.
23:13
Intel Arc Graphics A750/A770 Quick Linux Competition With The Radeon RX 7600 Phoronix
For those wondering how the performance of Intel Arc Graphics is relative to the newly-launched AMD Radeon RX 7600 and other recent graphics cards, here are a couple of benchmarks for the Arc Graphics using the new Linux 6.3 stable kernel paired with Mesa 23.2-dev for the latest open-source OpenGL and Vulkan drivers...
22:56
Ubuntu Forms An HPC Team To Push AI, High Performance Computing Workloads Phoronix
Announced on Thursday was the Ubuntu High Performance Computing (HPC) team to promote Ubuntu Linux for running AI/ML, energy, bioinformatics, meteorology, and other workloads on Ubuntu Linux...
22:39
Predator Android Spyware: Researchers Uncover New Data Theft Capabilities The Hacker News
Security researchers have detailed the inner workings of the commercial Android spyware called Predator, which is marketed by the Israeli company Intellexa (previously Cytrox). Predator was first documented by Google's Threat Analysis Group (TAG) in May 2022 as part of attacks leveraging five different zero-day flaws in the Chrome web browser and Android. The spyware, which is delivered by means
22:28
ChatGPT-maker Warns It Might Leave EU Over Planned AI Law SoylentNews
ChatGPT-maker warns it might leave EU over planned AI law:
The boss of the company behind ChatGPT has said it might consider leaving the EU if it fails to comply with a planned law on artificial intelligence (AI).
The EU's planned legislation could be the first to specifically regulate AI.
And it could require generative AI companies to reveal which copyrighted material had been used to train their systems to create text and images.
"The current draft of the EU AI Act would be over-regulating," OpenAI's Sam Altman said, Reuters reported. "But we have heard it's going to get pulled back."
Many in the creative industries accuse AI companies of using the work of artists, musicians and actors to train systems to imitate their work.
But Mr Altman is worried it would be technically impossible for OpenAI to comply with some of the AI Act's safety and transparency requirements, according to Time magazine.
At an event at University College London, Mr Altman added he was optimistic AI could create more jobs and reduce inequality.
He also met Prime Minister Rishi Sunak and the heads of AI companies DeepMind and Anthropic to discuss the technology's risks - from disinformation to national security and even "existential threats" - and the voluntary actions and regulation required to manage them.
Read more of this story at SoylentNews.
22:17
Linux Preps Hybrid SMP Fix To Avoid Upcoming Laptops Appearing As 11 Socket Monsters Phoronix
A fix is on its way to the mainline Linux 6.4 kernel and also marked for back-porting to existing stable kernel series to fix x86 topology reporting for Intel Hybrid systems. The topology bug within the kernel becomes more pronounced for Meteor Lake laptops where currently internal Intel test laptops can report the systems having 11 CPU sockets rather than the proper number of cores all contained within one CPU socket...
21:53
EFF at RightsCon 2023 Deeplinks
After three years of virtual gatherings, RightsCon is back! The 12th edition of the worlds leading summit on human rights in the digital age will be a hybrid convening taking place online through the RightsCon platform and in San Jos, Costa Rica between June 5-8.
RightsCon provides an opportunity for human rights experts,
technologists, government representatives, and activists to discuss
pressing human rights challenges and their potential
solutions.
Were excited that many EFFers are heading to Costa Rica and will be actively participating in this year's event both online and in person. Several members will be leading sessions and contributing as speakers, as well as being available for networking.
Our delegation includes:
- Carlos Wertheman, Translations Manager
- Christoph Schmon, International Policy Director
- Cindy Cohn, Executive Director
- David Greene, Senior Staff Attorney and Civil Liberties Director
- Eva Galperin, Director Of Cybersecurity
- Jillian York, Director of International Freedom of Expression
- Katitza Rodriguez, Policy Director for Global Privacy
- Paige Collings, Senior Speech and Privacy Activist
- Shirin Mori, Senior Design & Research Lead
- Veridiana Alimonti, Associate Director For Latin American Policy
We hope you have an opportunity to connect with us at the following:
Tuesday 6 June
Internet service providers and data privacy rights:
challenges, trends, and ways forward in Latin America and
Spain
10:15 - 11:15 CST [HYBRID]
Veridiana Alimonti, Associate Director For Latin American
Policy
Host institutions: Electronic Frontier Foundation
(EFF)
Since 2015, Quin Defiende tus Datos? /Dnde Estn mis Datos?
reports in Latin America and Spain have held Internet Service
Providers accountable by comparing their privacy policies and
practices, especially on government demands for user data. The
session will explore achievements, gaps, and concerning trends
found throughout the series.
Confronting cybercrime laws and human rights abuse, a local
to global discussion
10:15 - 11:15 CST
Katitza Rodriguez, Policy Director for Global
Privacy
Host institutions: ARTICLE 19, Electronic Frontier Foundation
(EFF)
Around the world repressive governments are increasingly exploiting cybercrime legislation to arbitrarily restrict the freedom of expres...
21:48
5 Must-Know Facts about 5G Network Security and Its Cloud Benefits The Hacker News
5G is a game changer for mobile connectivity, including mobile connectivity to the cloud. The technology provides high speed and low latency when connecting smartphones and IoT devices to cloud infrastructure. 5G networks are a critical part of all infrastructure layers between the end user and the end service; these networks transmit sensitive data that can be vital for governments and
21:23
Court Orders Instagram to Expose Pirates, Boot Their Accounts, and Purge URLs TorrentFreak
 Similar to any other online platform that deals with
user-generated content, Instagram processes copyright complaints on
a daily basis.
Similar to any other online platform that deals with
user-generated content, Instagram processes copyright complaints on
a daily basis.
Most of these arrive in the form of DMCA notices, in which rightsholders requests the removal of a specific image, video, or URL.
The number of removals runs in the hundreds of thousands during a typical month, without getting noticed by the public at large, but if Instagram users continue to post copyright infringing content, they risk losing their accounts.
Takedown Trouble Triggers Lawsuit
This takedown policy is widely accepted as the standard for social media services but every now and then, disputes can arise. In India, one such dispute turned into a legal battle in which the Bombay High Court issued a broad injunction earlier this month.
The lawsuit in question was filed by Applause Entertainment, the Indian company behind the TV-series Scam 1992. The series covers the 1992 Indian stock market scam, adapted from Debashis Basus book The Scam.
The TV production is licensed to Sony LIV and was a huge success. However, as often happens with popular media, pirated footage was readily available too. Not just on pirate sites, but also on otherwise legitimate social media platforms.
Applause Entertainment wasnt happy with this pirate activity so it approached several platforms to take down infringing clips and snippets of the show. Instagram was one of the recipients but, instead of taking immediate action, the platform asked for proof of ownership.
The company responded to this correspondence with relevant ownership documents but, apparently, Instagram still wasnt convinced. This standoff prompted Applause to take the matter to the Bombay High Court, where it requested an ex-parte injunction.
Court Issues Broad Injunction
The High Court concluded, after reviewing the evidence, that the studio does own the rights so Instagram must take action. This isnt out of the ordinary but the court went further than simply asking the infringing posts to be removed.
As highlighted by the law blog SpicyIP, the court issued a so-called dynamic injunction, which goes much further than a simple takedown request.
21:00
Getting into NMR Without the Superconducting Magnet Hackaday

Exploring the mysteries of quantum mechanics surely seems like an endeavor that requires room-sized equipment and racks of electronics, along with large buckets of grant money, to accomplish. And while thats generally true, theres quite a lot that can be accomplished on a considerably more modest budget, as this as-simple-as-it-gets nuclear magnetic resonance spectroscope amply demonstrates.
First things first: Does the magnetic resonance part of NMR bear any relationship to magnetic resonance imaging? Indeed it does, as the technique of lining up nuclei in a magnetic field, perturbing them with an electromagnetic field, and receiving the resultant RF signals as the nuclei snap back to their original spin state lies at the heart of both. And while MRI scanners and the large NMR spectrometers used in analytical chemistry labs both use extremely powerful magnetic fields, [Andy Nicol] shows us that even the Earths magnetic field can be used for NMR.
[Andy]s NMR setup couldnt be simpler. It consists of a coil of enameled copper wire wound on a 40...
20:23
DeSantis: Trump Handed U.S. Over to Fauci and Destroyed Millions of Lives cryptogon.com
Never forget it: President Pfizer Warpspeed (Trump) was either in on the Covid scam, or allowed himself to be scammed, indicating gross incompetence. Via: New York Post: Florida Gov. Ron DeSantis took a swing at Republican primary frontrunner Donald Trump Thursday, saying the 45th president turned the country over to Dr. Anthony Fauci during the []
20:21
Big Throughput Boost & Lower Latency With New Patch For Linux Checksum Function Phoronix
Queued up ahead of the Linux 6.5 cycle kicking off in about one month is a new Linux x86 optimization patch for further tuning csum_partial, the function used within the kernel for calculating 32-bit checksums on blocks of data. Much lower latency and higher throughput can be observed with the newly-optimized csum_partial on the latest Intel/AMD processors...
20:07
New CosmicEnergy ICS malware threatens energy grid assets Security Affairs
Experts detailed a new piece of malware, named CosmicEnergy, that is linked to Russia and targets industrial control systems (ICS).
Researchers from Mandiant discovered a new malware, named CosmicEnergy, designed to target operational technology (OT) / industrial control system (ICS) systems. The malicious code was first uploaded to a public malware scanning service in December 2021 by a user in Russia. The malware is specifically designed to disrupt electric power by interacting with IEC 60870-5-104 (IEC-104) devices, such as remote terminal units (RTUs). These RTU are widely adopted n electric transmission and distribution operations in Europe, the Middle East, and Asia.
COSMICENERGY is one of the OT malware that were spotted over the years, but according to Mandiant, what makes this malware unique is that it has been developed by a contractor as part of a red teaming activity for simulated power disruption exercises hosted by Rostelecom-Solar, a Russian cyber security company. The ICS malware supports capabilities that are comparable to those implemented in malware such as INDUSTROYER and INDUSTROYER2.
Both INDUSTROYER and INDUSTROYER2 malware strains were used by Russia-linked APT groups in attacks aimed at critical infrastructure in Ukraine targeting IEC-104.
COSMICENERGYs capabilities and overall attack strategy appear reminiscent of the 2016 INDUSTROYER incident, which issued IEC-104 ON/OFF commands to interact with RTUs and, according to one analysis, may have made use of an MSSQL server as a conduit system to access OT. reads the analysis published by Mandiant. Leveraging this access, an attacker can send remote commands to affect the actuation of power line switches and circuit breakers to cause power disruption.
COSMICENERGY is composed of two components, respectively tracked as PIEHOP and LIGHTWORK:
- PIEHOP is a disruption Python tool packaged with P...
20:01
Careless IT security worker exploited ransomware attack against his employer, but failed to cover his tracks Graham Cluley
Bad enough for your company to be held to ransom after a cyber attack. Worse still to then have one of your own employees exploit the attack in an attempt to steal the ransom for themselves. Read more in my article on the Tripwire State of Security blog.
19:58
Qt 5.15 LTS Takes Another Step Closer To Retirement Phoronix
The Qt 5.15 Long-Term Support branch as the last release in the Qt5 series is one step closer to retirement with The Qt Group now having ended its standard support for legacy license holders...
19:43
Discover the Blood Type Mosquitoes Like Best SoylentNews
Yes, They Really Have a Favorite!:
A study conducted in 2004 aimed to determine the blood type that mosquitoes preferred when it came to feeding. The researchers released a group of Aedes albopictus mosquitoes and observed their behavior as they landed on different individuals with varying blood types. The results showed that the mosquitos were more attracted to people with Type O blood, landing on them almost twice as often compared to those who had Type A.
Although there was no significant difference between the preference for blood types B and AB, the findings strongly suggested that Type O was indeed the most favored by mosquitoes. This information is crucial in understanding how these pesky insects behave, especially since certain diseases like malaria are transmitted through mosquito bites.
If you are getting bitten more often than other people, there might be a good reason for that. Here are some of the reasons, other than Type O blood, that mosquitos may be attracted to you.
[...] Despite popular belief, mosquitoes do not actually bite us for our blood but rather for the proteins in our blood plasma. These proteins help female mosquitoes produce eggs and are essential for their survival. When a mosquito bites an individual with a particular blood type, it can detect these proteins and know if it is worth biting again in order to obtain more nutrients.
Mosquitoes aren't only attracted to a certain blood type. They are highly attracted to carbon dioxide, a gas that is naturally emitted by humans when they exhale. In fact, these pesky insects can detect carbon dioxide from almost half a football field away! This makes it easy for mosquitoes to locate potential hosts and feed on their blood.
Interestingly, some individuals naturally exhale more carbon dioxide than others. Generally speaking, larger people tend to produce more of this gas compared to smaller individuals. As a result, bigger individuals may be more attractive targets for mosquitoes.
Read more of this story at SoylentNews.
18:00
When The Professionals Trash Your Data Tape, Can It Still Be Recovered? Hackaday

People trying to preserve digital artifacts held on old media often not only have to contend with the media themselves decaying, but also with obscure media formats for which theres seemingly little chance of finding a working reader. [Kneesnap] had this problem with a tape containing the only known copy of all the assets for the game Frogger 2: Swampys Revenge, and the tale of how the data was recovered is a dive into both the shady side of the data recovery industry and some clever old-format hacking.
The tape was an Onstream cartridge, a short-lived format from a company whose first product hit the market at the end of the 90s and who went bust in 2004. An old drive was found, but it proved to have a pinch roller melted with age, so in desperation the tape was sent to a data recovery company.
We admire the forbearance in not naming and shaming the data recovery company, because far from recovering the data they sent it back with the tape damaged and spliced something you can do with an analogue tape but not a digital one without compromising the data. Then faced with an unrecoverable tape and a slightly different Onstream cartridge, how could anything be salvaged?
The answer came in overr...
17:16
IRC Proceedings: Thursday, May 25, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-250523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-250523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-250523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-250523.gmi
Over HTTP:
|
... |
17:00
Oxygen restriction helps fast-aging lab mice live longer Terra Forming Terra

That is certainly plausible. Protection as well but thin air induces physiolgical changes and also gets you free of the often intense humid conditions we have nearer sea level. we already understand that the Greek Pantheon were a handfu of humans who were able to upgrade their life expectancy using an elixer at least. this we have been advancing ourselves with the obvious application of vitimin C and D.
Two UK Babies Dead From Myocarditis Terra Forming Terra

Sea Raiders in Nordic Bronze Age Rock Art Terra Forming Terra
Sea Raiders in Nordic Bronze Age Rock Art
the Sun is Not a Hydrogen Bomb? Terra Forming Terra
Continuing my workthrough on Robert Temple's book on plasma.. We address the contradictions regarding accepted opinion that the Sun as an ongoing Hydrogen bomb. I now understand that the whole meme is not viable. I equally understand this in regard to our understanding of gravity.
Simply put, the reported surface temperature is way too low and certainly non conforming. that sunspots are much cooler still puts any such a model on its head.
so let us return to DARK MATTER as neutral neutron pairs and simply ignore the neutral electron pairs and neutral neutrino pairs. as we cannot detect hydrogen ,we certainly cannot detect any of all this. what we are able to detect are decay products from which our experienced universe arises from. It is amazing just how much all that has removed us from a theoretical reality.
The easiest conjecture for the sun is to project that what we see and experience is primarily NNP decay into hydrogen which then flows away from the Sun as a plasma flux along with radiation caused by electron decay onto the hydrogen. I will mention that other elements also emerge but are scant enough.
The next easiest conjecture is that cool NNP conglomerations will decay into known elements. This may well be happening on Earth as well. It is still a slow process, as is hydrogen decay out in space. It appears obvious that NNP compression inside a gravity well will trigger rapid hydrogen decay. It is then easy to expect decay taking place inside the earths crust I do not think that compression is sufficient to trigger decay and there is likely much more too it. I do expect though that it is sped up but not so much as we can notice it. It may be mostly be about hydrogen and oxygen as well. We simply can only conjecture until we pack all this inside a tube.
Is it plausible that what we see...
16:56
Jupiters Lightning Bolts Contort the Same Way as Earths SoylentNews
Collisions of water and ice might build electric charge in thunderclouds on both planets:
On Jupiter, lightning jerks and jolts a lot like it does on Earth.
Jovian lightning emits radio wave pulses that are typically separated by about one millisecond, researchers report May 23 in Nature Communications. The energetic prestissimo, the scientists say, is a sign that the gas giant's lightning propagates in pulses, at a pace comparable to that of the bolts that cavort through our own planet's thunderclouds. The similarities between the two world's electrical phenomena could have implications for the search for alien life.
Arcs of lightning on both worlds appear to move somewhat like a winded hiker going up a mountain, pausing after each step to catch their breath, says Ivana Kolmaov, an atmospheric physicist at the Czech Academy of Sciences in Prague. "One step, another step, then another step ... and so on."
Here on Earth, lightning forms as turbulent winds within thunderclouds cause many ice crystals and water droplets to rub together, become charged and then move to opposite sides of the clouds, progressively generating static electrical charges. When the charges grow big enough to overcome the air's ability to insulate them, electrons are released the lightning takes its first step. From there, the surging electrons will repeatedly ionize the air and rush into it, lurching the bolt forward at an average of hundreds of thousands of meters per second.
Scientists have suggested that superbolts observed in Jovian clouds might also form by collisions between ice crystals and water droplets (SN: 8/5/20). But no one knew whether the alien lightning extended and branched in increments, as they do on Earth, or if they took some other form.
[...] If that universality is real, it could have implications for the search for life elsewhere. Experiments have shown that lightning strikes on Earth could have smelted some of the chemical ingredients needed to form the building blocks of life (SN: 3/16/21). If lightning is discharging in a similar way on alien worlds, Yair says, then it could be producing similar ingredients in those places too.
Journal Reference:
Kolmaov, I., Santolk, O., Imai, M. et al. Lightning at
Jupiter pulsates with a similar rhythm as in-cloud lightning at
Earth. Nat Commun 14, 2707 (2023). https://doi.or...
16:48
Links 26/05/2023: Qt 6.5.1 and Subsystems in GNUnet Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Audiocasts/Shows
-
mintCast Podcast mintCast 412.5 Gracias, Amiga!
In our Innards section we talk about Pimiga
In Vibrations from the Ether, Joe interacts with a listener via email about some hardware subjects and other stuff
Download
-
-
Instructionals/Technical
-
Kifarunix Step-by-Step Guide: How to Install Helm on Kubernetes Cluster
In this tutorial, we will provide you with a step by step guide...
-
-
16:38
New COSMICENERGY Malware Exploits ICS Protocol to Sabotage Power Grids The Hacker News
A new strain of malicious software that's engineered to penetrate and disrupt critical systems in industrial environments has been unearthed. Google-owned threat intelligence firm Mandiant dubbed the malware COSMICENERGY, adding it was uploaded to the VirusTotal public malware scanning utility in December 2021 by a submitter in Russia. There is no evidence that it has been put to use in the wild
15:00
A Mobile Phone from 1985 Hackaday

It might seem quaint through the lends of history we have the luxury of looking through, but in the mid 1980s it was a major symbol of status to be able to communicate on-the-go. Car phones and pagers were cutting-edge devices of the time, and even though there were some mobile cellular telephones, they were behemoths compared to anything we would recognize as a cell phone today. It wasnt until 1985 that a cell phone was able to fit in a pocket, and that first device wasnt just revolutionary because of its size. It made a number of technological advancements that were extremely impressive for its time, and [Janus Cycle] takes us through some of those in this teardown video.
The Technophone came to us from Great Britain by way of a former Ericsson engineer named Nils Mrtensson. It was able to achieve its relatively small stature using a surface-mount PCB, which was a cutting-edge manufacturing process for the time. Not only did it use surface-mount components and boards, but the PCB itself has 12 layers and two sides and hosts two custom Technophone chips. The phone is relatively modular as well, with the screen, battery pack, and other components capable of easily disconnecting from the main board.
Some cleanup of the phone was needed after the teardown,...
15:00
Phishers use encrypted file attachments to steal Microsoft 365 account credentials Help Net Security
Phishers are using encrypted restricted-permission messages (.rpmsg) attached in phishing emails to steal Microsoft 365 account credentials. [The campaigns] are low volume, targeted, and use trusted cloud services to send emails and host content (Microsoft and Adobe), say Trustwave researchers Phil Hay and Rodel Mendrez. The initial emails are sent from compromised Microsoft 365 accounts and appear to be targeted towards recipient addresses where the sender might be familiar. Phishing emails with Microsoft Encrypted Restricted More
The post Phishers use encrypted file attachments to steal Microsoft 365 account credentials appeared first on Help Net Security.
14:45
New Buhti ransomware uses leaked payloads and public exploits Help Net Security
A newly identified ransomware operation has refashioned leaked LockBit and Babuk payloads into Buhti ransomware, to launch attacks on both Windows and Linux systems. Use of public exploits One notable aspect of the attackers leveraging the Buhti ransomware is their ability to quickly exploit newly disclosed vulnerabilities (e.g., the recently patched PaperCut and IBM Aspera Faspex flaws). The attackers are leveraging public exploits, Dick OBrien, principal intelligence analyst with Symantec Threat Hunter team told Help More
The post New Buhti ransomware uses leaked payloads and public exploits appeared first on Help Net Security.
14:35
New infosec products of the week: May 26, 2023 Help Net Security
Heres a look at the most interesting products from the past week, featuring releases from Axiado, Delinea, Netscout, Radware, and Veriff. Delinea Cloud Suite updates reduce the risk of lateral movement in cybersecurity breaches Delinea Cloud Suite updates include more granular support for just-in-time (JIT) and just-enough privilege access automation, and improved identity assurance through enforced human interaction when prompted for multi-factor authentication (MFA) at server log-in or privilege elevation. Radware Cloud Web DDoS Protection More
The post New infosec products of the week: May 26, 2023 appeared first on Help Net Security.
14:30
Threat actors exploit new channels for advanced phishing attacks Help Net Security
Perception Points team has identified a 356% increase in the number of advanced phishing attacks attempted by threat actors in 2022. Overall, the total number of attacks increased by 87%, highlighting the growing threat that cyber attacks now pose to organizations. Phishing attacks increase Throughout 2022, Perception Points team analyzed several concerning trends. Firstly, malicious actors continue to gain widespread access to new tools and advances in artificial intelligence (AI) and machine learning (ML) which More
The post Threat actors exploit new channels for advanced phishing attacks appeared first on Help Net Security.
14:10
Virgin Orbit to Cease Operations, Sell Assets of Richard Branson's Satellite Launcher SoylentNews
Virgin Orbit to cease operations, sell assets of Richard Branson's satellite launcher:
Richard Branson's Virgin Orbit is shutting down less than two months after the satellite launch start-up filed for Chapter 11 bankruptcy protection, according to a Tuesday company announcement.
Virgin Orbit will cease operations and sell its assets to four winning bidders, the company announced Tuesday. Those bidders include three aerospace companiesRocket Lab, Stratolaunch and Vast Space subsidiary Launcherwith combined bids totaling almost $36 million, according to court documents.
A sale hearing for court approval is scheduled for Wednesday afternoon and transactions are expected to close soon after, the company said.
"Virgin Orbit's legacy in the space industry will forever be remembered," Virgin Orbit said in a Tuesday statement. "Its groundbreaking technologies, relentless pursuit of excellence, and unwavering commitment to advancing the frontiers of air launch have left an indelible mark on the industry."
[...] Virgin Orbit was founded in 2017 by Branson, a British billionaire, in hopes of targeting the market for launching small satellites into space. Its LauncherOne rockets were launched from the air from modified Virgin passenger planes, allowing the company to operate more flexibly than using fixed launch sites.
Read more of this story at SoylentNews.
14:04
Barracuda Warns of Zero-Day Exploited to Breach Email Security Gateway Appliances The Hacker News
Email protection and network security services provider Barracuda is warning users about a zero-day flaw that it said has been exploited to breach the company's Email Security Gateway (ESG) appliances. The zero-day is being tracked as CVE-2023-2868 and has been described as a remote code injection vulnerability affecting versions 5.1.3.001 through 9.2.0.006. The California-headquartered firm
14:00
Strengthening travel safety protocols with ISO 31030 Help Net Security
In this Help Net Security video, Tracy Reinhold, Chief Security Officer at Everbridge, talks about ISO 31030, the officially recognized International Standard for travel risk management, guiding how to manage risks to organizations and travelers. The global pandemic has been the primary concern for travel professionals over the past three years. However, the focus is now shifting towards severe weather occurrences and social instability as these represent the most significant risks to corporate travel. Surprisingly, More
The post Strengthening travel safety protocols with ISO 31030 appeared first on Help Net Security.
13:30
Cybercriminals masquerading as MFA vendors Help Net Security
Cybercriminals are increasingly posing as multi-factor authentication vendors and small businesses are becoming more popular targets, according to VIPRE. Attachment-based malspam is on the rise Financial institutions (48%) are still the most targeted sector by a wide margin. Insider attacks now take on average 85 days to contain up from 77 days the previous year. The most common phishing links are compromised websites (52%), newly registered domains (39%), and subdomain cybersquatting (9%). The report More
The post Cybercriminals masquerading as MFA vendors appeared first on Help Net Security.
13:00
Fresh perspectives needed to manage growing vulnerabilities Help Net Security
In its inaugural 2023 Offensive Security Vision Report, NetSPI unveils findings that highlight vulnerability trends across applications, cloud, and networks. Vulnerability patterns The report offers a look back and forward at some of the most significant vulnerability patterns of the past year to help security and business leaders focus discovery, management, and remediation efforts on the riskiest vulnerabilities most likely to exist on their attack surface. According to the NIST National Vulnerability Database More
The post Fresh perspectives needed to manage growing vulnerabilities appeared first on Help Net Security.
12:00
Vehicle-to-Grid Made Easy Hackaday

As electric cars continue to see increased adoption, one associated technology that was touted long ago that still hasnt seen widespread adoption is vehicle-to-grid or vehicle-to-home. Since most cars are parked most of the time, this would allow the cars to perform load-levelling for the grid or even act as emergency generators on an individual basis when needed. While this hasnt panned out for a variety of reasons, it is still possible to use an EV battery for use off-grid or as part of a grid tie solar system, and now you can do it without needing to disassemble the battery packs at all.
Normally when attempting to use a scrapped EV battery for another use, the cells would be removed from the OEM pack and reorganized to a specific voltage. This build, however, eliminates the need to modify the packs at all. A LilyGO ESP32 is used to convert the CAN bus messages from the battery pack to the Modbus communications protocol used by the inverters, in this case a Fronius Gen24, so the inverter and battery can coordinate energy delivery from one to the other automatically. With the hard part out of the way, the only other requirements are to connect a high voltage DC cable fr...
11:32
Links 25/05/2023: Mesa 23.1.1 and Debian Reunion Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Graphics Stack
-
9to5Linux Mesa 23.1.1 Improves VA-API/H.264 Decoding for Firefox on Fedora 37, Fixes Bugs
Mesa 23.1.1 is here packed with many fixes for various of its open-source graphics drivers, improving VA-AP...
-
-
11:23
Early Warning Systems Send Disaster Deaths Plunging: UN SoylentNews
https://phys.org/news/2023-05-early-disaster-deaths-plunging.html
Weather-related disasters have surged over the past 50 years, causing swelling economic damage even as early warning systems have meant dramatically fewer deaths, the United Nations said Monday.
Extreme weather, climate and water-related events caused 11,778 reported disasters between 1970 and 2021, new figures from the UN's World Meteorological Organization (WMO) show.
Those disasters killed just over two million people and caused $4.3 trillion in economic losses.
"The most vulnerable communities unfortunately bear the brunt of weather, climate and water-related hazards," WMO chief Petteri Taalas said in a statement.
The report found that over 90 percent of reported deaths worldwide due to disasters over the 51-year-period occurred in developing countries.
But the agency also said improved early warning systems and coordinated disaster management had significantly reduced the human casualty toll.
WMO pointed out in a report issued two years ago covering disaster-linked deaths and losses between 1970 and 2019, that at the beginning of the period the world was seeing more than 50,000 such deaths each year.
By the 2010s, the disaster death toll had dropped to below 20,000 annually.
Read more of this story at SoylentNews.
10:59
sdl12-compat 1.2.64 Released - More Classic Games Now Running On This SDL2 Layer Phoronix
Following the recent sdl12-compat test release, sdl-compat implementing the SDL 1.2 API/ABI atop SDL 2.x interfaces for enhancing game compatibility on modern Linux environments...
10:00
HPR3865: When did the Internet get so boring? Hacker Public Radio
You can run a Gopher or Gemini site on SDF You can see some Gemini sites on gem.sdf.org
09:48
What E.ON Next Says About Cadent Gas Limited Replacing Metal With Plastics at Unexpected Times schestowitz.com
Video download
link | md5sum
3423a47dfdeaf06eccf9210c582f0523
Energy Suppliers and Gas Pipes
Creative Commons Attribution-No Derivative Works 4.0
THE power supplier we have is not the power supplier we chose. It was inherited by us when we moved in a decade ago and it has since then been acquired by another company, which Ive endlessly ranted about in the past. The original company, nPower, was relatively OK, but E.ON Next sucks. The above recording is my phonecall or reach-out to E.ON Next regarding what happened with Cadent Gas Limited a company that basically ruined my entire day and might ruin several more days ahead. Cadent Gas Limited management is unapologetic about it, but at least E.ON Next promises to follow up with a call some time later (unspecified time), so maybe there will be updates ahead.
Is it not astounding that E.ON Next charges almost 150 pounds just to turn off the gas? It sounds like a penalty, not a sane bill for such a trivial job. In a free market of true competition, would such penalties exist? Also, why arent the pipes managed by the Council anyway? Why has everything been outsourced to opportunistic privatisers?
08:41
Former Google CEO Says AI Poses an 'Existential Risk' That Puts Lives in Danger SoylentNews
Eric Schmidt wants to prevent potential abuse of AI:
Add Eric Schmidt to the list of tech luminaries concerned about the dangers of AI. The former Google chief tells guests at The Wall Street Journal's CEO Council Summit that AI represents an "existential risk" that could get many people "harmed or killed." He doesn't feel that threat is serious at the moment, but he sees a near future where AI could help find software security flaws or new biology types. It's important to ensure these systems aren't "misused by evil people," the veteran executive says.
Schmidt doesn't have a firm solution for regulating AI, but he believes there won't be an AI-specific regulator in the US. He participated in a National Security Commission on AI that reviewed the technology and published a 2021 report determining that the US wasn't ready for the tech's impact.
Schmidt doesn't have direct influence over AI. However, he joins a growing number of well-known moguls who have argued for a careful approach. Current Google CEO Sundar Pichai has cautioned that society needs to adapt to AI, while OpenAI leader Sam Altman has expressed concern that authoritarians might abuse these algorithms. In March, numerous industry leaders and researchers (including Elon Musk and Steve Wozniak) signed an open letter calling on companies to pause AI experiments for six months while they rethought the safety and ethical implications of their work.
Read more of this story at SoylentNews.
08:40
Mesa 23.1.1 Released With Many Bug Fixes For RADV, Zink, Intel ANV Phoronix
For those that prefer waiting to the first point release before shifting to a new Mesa3D quarterly feature release, Mesa 23.1.1 is out today so you can now begin upgrading to this latest set of open-source OpenGL and Vulkan drivers used on Linux systems and elsewhere...
08:31
Weston 12.0: Highlights and changes for Wayland's reference compositor (Collabora blog) LWN.net
Over on the Collabora blog, Marius Vlad
looks at the
Weston 12.0 release. Weston is the reference compositor
for the Wayland
project. The highlights include two new backends and support for
multiple scanout devices, along with "multiple fixes and
internal changes that would further facilitate integration of
functionality like color management or the ability to load up
multiple backends at the same time
".
As we're heading towards having the ability to load multiple backends, two new ones have seen the day in this new release: backend-vnc, which is similar to backend-rdp, is based on aml and neatvnc libraries. It has TLS support and user authentication. The other backend added is the PipeWire one; it creates a node for each output and like the plugin with the same backend name, it can be used to capture Weston outputs for processing with other applications.
08:30
[kubernetes] CVE-2023-2878: secrets-store-csi-driver discloses service account tokens in logs Open Source Security
Posted by Monis Khan on May 25
Hello Kubernetes Community,A security issue was discovered in secrets-store-csi-driver where an actor
with access to the driver logs could observe service account tokens. These
tokens could then potentially be exchanged with external cloud providers to
access secrets stored in cloud vault solutions. Tokens are only logged
when TokenRequests is configured in the CSIDriver object
<https://kubernetes-csi.github.io/docs/token-requests.html>...
08:18
Whos the Coolest Robot of All? IEEE Spectrum

Calling all robot fanatics! We are the creators of the Robots Guide, IEEEs interactive site about robotics, and we need your help.
Today, were expanding our massive catalog to nearly 250 robots, and we want your opinion to decide which are the coolest, most wanted, and also creepiest robots out there.
To submit your votes, find robots on the site that are interesting to you and rate them based on their design and capabilities. Every Friday, well crunch the votes to update our Robot Rankings.
 Rate this
robot: For each robot on the site, you can submit your overall
rating, answer if youd want to have this robot, and rate its
appearance.IEEE Spectrum
Rate this
robot: For each robot on the site, you can submit your overall
rating, answer if youd want to have this robot, and rate its
appearance.IEEE Spectrum
May the coolest (or creepiest) robot win!
Our collection currently features 242 robots, including humanoids, drones, social robots, underwater vehicles, exoskeletons, self-driving cars, and more.
 The Robots
Guide features three rankings: Top Rated, Most Wanted, and
Creepiest....
The Robots
Guide features three rankings: Top Rated, Most Wanted, and
Creepiest....
08:11
Operation Magalenha: Brazilian Hackers Hit Portuguese Banks in Malware Attack HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
SentinelLabs has uncovered a malware campaign in which Brazilian hackers are targeting Portuguese banks for monetary gains.
This is a post from HackRead.com Read the original post: Operation Magalenha: Brazilian Hackers Hit Portuguese Banks in Malware Attack
08:00

A great introduction on using the debugg
Click to Read More at Oracle Linux Kernel Development
The post Enter the drgn appeared first on Linux.com.
07:58
D-Link fixes two critical flaws in D-View 8 network management suite Security Affairs
D-Link fixed two critical flaws in its D-View 8 network management suite that could lead to authentication bypass and arbitrary code execution.
D-Link has addressed two critical vulnerabilities (CVSS score: 9.8) in its D-View 8 network management suite that could be exploited by remote attackers to bypass authentication and execute arbitrary code.
The D-View network management suite allows customers to monitor performance, configure devices, and manage the network in an efficient way.
The vulnerabilities were reported to the company on December 23, 2022 through Trend Micros Zero Day Initiative (ZDI).
The first vulnerability, tracked as CVE-2023-32165, is a D-View TftpReceiveFileHandler Directory Traversal Remote Code Execution flaw.
This vulnerability allows remote attackers to execute arbitrary code on affected installations of D-Link D-View. Authentication is not required to exploit this vulnerability. reads the advisory published by ZDI. The specific flaw exists within the TftpReceiveFileHandler class.
The vulnerability is caused by the lack of proper validation of a user-supplied path prior to using it in file operations. An unauthenticated attacker can exploit the flaw to execute code in the context of SYSTEM.
The vulnerability was reported by Andrea Micalizzi (aka rgod)
The second flaw, tracked as CVE-2023-32169, is an authentication bypass issue caused by the use of hard-coded cryptographic key authentication in the TokenUtils class.
An attacker can exploit this vulnerability to bypass authentication on the target system.
This vulnerability allows remote attackers to bypass authentication on affected installations of D-Link D-View. Authentication is not required to exploit this vulnerability. reads the advisory. The specific flaw exists within the TokenUtils class. The issue results from a hard-coded cryptographic key.
The vulnerability was discovered by Piotr Bazydlo (@chudypb) of Trend Micro Zero Day Initiative.
The company pointed out that the released patch is beta software or hot-fix release, which is still undergoing final testing.
Please note that this is a device beta software, beta firmware, or hot-fix release which is still undergoing final testing before its official release. The beta software, beta firmware, or hot-fix is provided on an as is and as a...
07:51
The Linux Foundation Announces WasmCon Event Focused on WebAssembly Technologies Linux.com

Read the original post at: Read More
The post The Linux Foundation Announces WasmCon Event Focused on WebAssembly Technologies appeared first on Linux.com.
06:51
06:30
1xbet App Bd Obtain For Android Apk And Ios At No Cost h+ Media
1xbet App Bd Obtain For Android Apk And Ios At No Cost
Get an EXCLUSIVE sign-up 230% bonus as much as 23,000 with promo code EXTRABONUS after the downloading course of and make bets on the most important sporting occasions. If you might be using an older model of iOS, you will not be able to entry the cell utility. It is very really helpful that you just performance of the app after the 1xBet download. If youre a passionate on-line casino player, then this promotion will certainly make your day! The 1xBet app is providing a fantastic promotion of 100 Free Spins for Slots and a 50% Bonus in your 10th deposit. All it takes to avail of this lucrative supply is 9 successful deposits adopted by the tenth onewhich could be made shortly from a user-friendly app.
To set up, observe the standard directions described within the previous section of this article. Make certain the gadget you are utilizing has enough free space and an energetic Internet connection. In your gadgets settings, discover the security section and remove the ban from installing suspicious software program (from third-party sources). This wager sort allows putting a guess upfront without a have to have money in your account.
- With the stay streaming sports option, you may watch a cricket match unfold right in front of your eyes whereas wagering on it.
- The bet is not difficult and normally, you possibly can always see the favorite.
- They will all the time help solve any issue inside an hour.
- These usually are not all of the points by which youll be able to evaluate the standard of the developed utility.
For our customers from India & Bangladesh, we have an exclusive 1xbet app promo code 1XLINE22, which can let you start the betting process with much more pleasure. By downloading the latest of payment strategies, as properly as a pleasing visible type and circulate of work. We guarantee you that you can acquire the best potential experience by downloading 1xbet app for Android or iOS cellular gadgets. Every new person can get a generous welcome bonus for one or more first deposits, relying on whic...
06:30
1xbet Aviator Apk, Obtain App For Android And Ios 2023 h+ Media
1xbet Aviator Apk, Obtain App For Android And Ios 2023
Moreover, youll be able to claim your 100 percent matched first deposit bonus up to 1,500 + one hundred fifty additional free spins. 1xGames is a big recreation repository in which weve been investing time, cash, and goodwill for years. Here you can see our comprising classes like Cards, Slots, Climb to Victory, Dice, and others. Well all the time alert you to some attention-grabbing matches you dont need to miss, in addition to our new bonuses.
1xBet app is characterised by fast and easy operation, lack of crashes and errors, as well as a handy, easy and intuitive consumer interface. All you need to do is register and deposit your account. 1xBet India provides its prospects a broad range of sports activities betting choices, including cricket , soccer, horse racing, tennis, and more. 1xBet India is among the main online gaming and betting platforms. 1xBet has been around since 2007, making it one of many longest-running on-line gaming suppliers in India. You may entry fantasy sports activities video games utilizing the 1xBet betting app or website.
In addition, everyday users have the opportunity to get free spins on the game of the day. The time in which free spins can be awarded is proscribed and is indicated in the promotion information together with the listing of video games of the day for the week. The specified variety of free spins shall be awarded as quickly because the winnings in the sport of the day exceed 600, with out having to be wagered.
Players might get the sense that they are at a typical poker desk in this style. You are free to decide out any recreation style that pursuits you. First, the user chooses his nation and foreign money, then the social network via which authorization might be obtained. When the system asks for entry to personal information, confirm the permission in the applicable window.
At the beginning of my gambling profession, I used 1xBet, a bookmaker I do not regret using. Two years in the past, I first used this site to bet on the IPL, and now I nonetheless do because of the situations. Cricket also has many tournaments and occasions, and there are all the time seasonal bonuses available. Lately, I have turn out to be fascinated in the on line casino, which additionally drew me into the applying.
- Gamblers can put their money on the trendiest cybersport occasions like DOTA 2, Counter-Strike, PUBG and so forth.
- With this mobile Application, avid gamers can view numerous sporting occasions by way of the iOS cellular app.
- Since many Indian customers favor cellular units, the bookie has created for gamers to wager directly on the phone.
- Selecting a Contact/Entering Mobile quantity Sending cash is as easy as sending a message.
- Should you reside in a state the place wagering websites are prohibited, then we propose that you do not use 1xBet.
Th...
06:30
Victory in California! Police Instructors Cant Claim Copyright Protections to Block Release of Use-of-Force and Other Training Materials Deeplinks
After a two-year legal battle, the state agency that
certifies police officers in California has agreed to EFF's demand
that it stop using copyright concerns as a predicate to withhold
law enforcement training materials from public
scrutiny.
The immediate impact of this victory for transparency is
the public will be able to visit the California Commission on Peace
Officers Standards & Training (POST) website to inspect 19
previously unseen training outlines. These documents cover a
variety of sensitive issues, such as police shootings and internal
affairs investigations, and were developed by the California Peace
Officers Association, which represents more than 23,000 law
enforcement officers across the state. The longer term impact is
that law enforcement agencies across California will no longer be
able to rely on POST's practices to justify their own decisions to
withhold their training records on copyright
grounds.
The story behind this case dates back to 2018, when
California State Senator Steven Bradford introduced legislation
that recognized a key ingredient to police accountability is
allowing the public to scrutinize what kind of training officers
receive when it comes to practices such as police stops,
use-of-force, and surveillance.
SB 978 requires all local law enforcement
agencies and POST to publish their policy manuals and training
materials on their websites, at least to the extent that those
records would be releasable under the California Public Records
Act. With EFF's support, the California legislature
passed the bill and it went into effect in
January 2020.
However, when EFF went to the POST's OpenData hub to
review training materials for issues such as police shootings,
automated license plate readers, and face recognition, we found
that the documents were completely redacted. Even the training on
California public records requests was ironically redacted. All
that was left was a single line:
The course presenter has claimed copyright for the expanded
course outline. While courses developed by
California agencies are by default in the public domain,
third-party private entities can also seek POST certification for
their training materials.
These redactions were unacceptable. When a trainer asks for the imprimatur of the state gov...
06:29
1xbet App Fraud
Dont take any dangers by downloading a 1xBet APK from anywhere else. An necessary facet is that the gambler doesnt have to create a brand new account if one has already been registered on the 1xbet web site. In this case, the client of the company can merely log in to it. Go to the download folder and discover the downloaded apk file there. You wont should spend anything to use the 1xBet cell app on an Android or iOS smartphone.
And to sweeten the deal even additional, you will be granted unique promotions that offer more rewards than ever! This section is devoted to exploring all these great stay casino advantages on the 1xBet app and explaining how they are often acquired by gamers. 1xbet is on the record of the bookmakers having mobile apps, nevertheless, sometimes some issues with its work happen. In this case, you might gamble and wager by way of the sites mobile all bookmaker sites including 1xbet.
It has quite a few features that allow getting a greater gaming experience. 1xbet India is one of the greatest on-line bookmakers; they have a vast person base in India. The bookie has been competing with the highest bookies in India and is second to none in providing companies to the bettors.
For me personally, this is very important, since I conduct my business on the telephone and it is not very handy for me to be at the pc all the time. You can place a live wager throughout a match, permitting you to watch what is occurring on the sector and make extra correct betting choices. This option is suitable for both novices and skilled 1xbet bookmakers. In the smartphone settings, enable the installation of purposes from unknown sources.
- The app is out there for both iOS and Android gadgets.
- When you pay someones bill, be it electrical energy or postpaid or anything else, you get a fee and therefore, the money is made.
- As youll be able to see, the variety of alternatives is massive.
Deposits made in the cell software are processed immediately, and withdrawal requests are often processed inside a couple of hours. You could make your bets on any match prematurely, or wager on a big selection of out there markets right during the match in a single click at 1xbet mobile program. Download 1 xbet utility from the official web site.
Depending on the sign-up method you decide, youll have to input data like your telephone number, first and final names, and password. Select your forex and, if relevant, any promotional codes after that. To obtain the software, open the unique website and download the utility for android or by way of the App Store in case you have an Apple device. You can guess on the principle sports activities disciplines through the app. Both the principle page of the app and the person categories are used for this purpose. Betting purchasers wi...
06:27
How To Download The 1xbet App To Your Android Or Ios Device! h+ Media
How To Download The 1xbet App To Your Android Or Ios Device!
Live streaming is another option out there to Android/iOS users. You can enjoy live streaming of a soccer match or some other 100+ occasion out there day by day. As you already understood, this part of the cellular product supports In-Play Bets. In stay occasions, odds are often updated, and as quickly as suitable ones appear, you presumably can place an instant bet.
I even have observed that the app is very straightforward to install after following step-by-step instructions. In one month, I have deposited one thousand rupees, and I have already earned 12,000. I think I received fairly fortunate as a end result of I did not use functions like 1xbet earlier than, however Im very glad. I just like the 1xBet app because it provides a broad range of sports activities and betting markets, together with some area of interest sports activities that I enjoy betting on. I love that I can discover all my favorite sports activities in one place.
With this outcome gambler bets on the victory of a particular staff in the occasion. The guess just isnt complicated and normally, you probably can at all times see the favorite. Within every sport, on 1xbet theres a wide number of outcomes. After the deposit inside 24 hours, the bonus quantity will be transferred to the balance of the gamblers account. Complete the registration by clicking on the button on the finish of the profile creation type. To do that, the player will want to fill out a small kind with valid details about himself.
The 1xBet cellular app provides beneficiant free bets, bonus video games, an attractive welcome bonus, easy-to-use deposit bonuses, cashback, and a whole lot more to enjoy. The software program is neither harder or more rigorous than you could have beforehand noticed. Nonetheless, regardless of this, it provides all of the options required for convenient betting or on line casino games.
I determined to write down this evaluation because the app actually works fantastically. Ive by no means had any lags and I like the fact that I can simply make deposits. The apps fast and efficient fee system permits me to deposit and withdraw funds quickly and easily. The 1xBet Android app also has the stay characteristic, which ensures you real-time updates of events, outcomes, and odds. The program encompasses an enormous choice of sports activities events like soccer, baseball, cricket, races, swimming and much more.
It permits betting on a minimum of two occasions of assorted types. Sign in using your current account or sign up with the app in case you are a new customer. Open Security settings on your telephone and permit the app to set up from Unknown sources.
The stay streaming function is on the market solely to a handful of bookmakers and 1xBet occurs to be one among them. Due to the application being extremely stable even underneath st...
06:27
1xbet Aviator Apk, Obtain App For Android And Ios 2023 h+ Media
1xbet Aviator Apk, Obtain App For Android And Ios 2023
conduct every betting transaction by way of the internet site. The options are corresponding to the principle website, and this is normally a profit for 1xbet clients whore loyal. After completing the process, youre able to obtain the 1xbet cell Application on the app store. Go to the app retailer to start 1xbets utility download for free and install. Another possibility is to go to the 1xbet web site for a 1xbet Download , 1XBET APP DOWNLOAD . One can forecast every one of many Live matches of your favorite group sports or ahead of every sports occasion on the web.Im working in market research company and this number is very imp for me whereas using whatsapp. The IPL 2023 season starts with the match between Gujarat Titans and Chennai Super Kings on the thirty first of March, 2023. The approaching clash between Kolkata Knight Riders and Lucknow Super Giants is about to be witnessed by a jam-packed crowd at Eden Gardens. The encounter guarantees to supply a becoming conclusion to each the teams campaigns in the league stage of IPL 2023.
Not all kinds of bets are listed here, however youll have the ability to see the remainder in particular person within the 1xBet app. This is a very fashionable wager, as it permits you to wager on a selection of sporting events, divided into groups of multi and single bets. You can use multi-bets to extend your profitable chances, and due to this fact your revenue margin.
- Multiple bets are bets on a couple of selection in one event.
- The official software is up to date by the administration every week, every month.
- One of the key features of 1xbet is its mobile app, which allows customers to put bets and play casino video games on their smartphones or tablets.
- You may also find the newest line-up, permutations, and status of gamers right here.
It will redirect you to the official App Store web page of the 1xBet app, where you probably can safely download the app. You can download the 1xBet app free of charge and get a welcome bonus of 100 percent up to BDT 10,000 in your first deposit, 115 BDT is the minimum deposit amount. Change settings to simply accept the purposes from unknown sources and click on ok. Just choose the social community by way of which account you need to log in. It is much like One-Click registration, but all info from the social community immediately goes to your gaming profile.
Friday Bonus
To benefit from this birthday bonus, in your birthday, go to your e-mail for the distinctive birthday bonus coupon code 1xbet 1xbet will e mail to you. Make sure you complete the bonuss turnover inside the 30 days following the day the prize was deposited in your account. 1xbet supplies a staggering 100% match welcome bonus, which may go to EUR150. This bonus consists of a 100...
06:26
Is 1xbet Banned In India Updated In 2023 Could h+ Media
Is 1xbet Banned In India Updated In 2023 Could
This is a well-liked bet sort because it lets you wager on a range of sports activities events in plenty of bet teams. Multi-bets can improve your chances of successful and, as a result, your profit margin. The thought behind pre-match betting is that bets are placed before the sport begins. Simply select the result youre feeling will occur and place your bet. You can withdraw your winnings as quickly as youve achieved the minimal withdrawal amount for the fee technique you have chosen.
As an experienced participant I need to say that I discovered the most effective person support right here once I had a payment grasp up in processing. All bonuses are energetic and obtainable by way of the cellular app. You can get them in the same method as by way of the website. Complete the registration, enter a promo code and get a bonus in your first deposits. You can use the 4raBet App latest model for your mobile system. 4raBet on-line betting platform permits you to take pleasure in leisure anytime and anyplace whereas winning cash.
A great app that enables every person to learn how to guess and earn cash within the course of. I really like their laconic design, which makes it very handy to bet at night as properly. Plus and I like the truth that the in-app support is even obtainable on holidays.
You might need to check in to your account to be able to use the performance. You can enroll within the bookmakers program if you do not already have a personal account. It is important to enter your cellphone number, in addition to the foreign money you choose to make use of. After that, you will obtain an SMS message with a code that must be dialed to confirm your personal account info.
As you possibly can see, the variety of alternatives is large. And thats not all, for the rationale that service provides you to put a wager on the matchs consequence, on the precise player, on the general score, on the rating of a selected team, etc. Click on the Withdrawal button in the principle menu. Select the suitable account from which you want to withdraw funds. Choose your preferred cost technique and click on Next . Review your withdrawal information and click on on Confirm .
Rather than just offering sportsbook choices, the 1xBet app additionally offers the posh of being in a position to play casino video games, which quantity greater than one thousand. The slots and reside supplier titles are a few of the greatest that one can encounter on this platform. One should actually not miss out on the stay vendor games, that are among the best within the enterprise. The Vegas-like experience being provided by the stay vendor titles can be loved even on a smartphone.
To switch money utilizing UPI, you first have to set up your UPI account utterly. The money shall be transferred in a matter of seconds. Entering Account Number & IFSC This...
06:25
1xbet App Obtain Apk For Android & Ios Free h+ Media
1xbet App Obtain Apk For Android & Ios Free
As a end result, the app is very convenient to have in case of such occasions. In India, there are not any laws against on-line gambling, due to this fact joining up for sports activities betting and on line casino gaming web sites and depositing cash is totally legal. 1xBet has a Curacao gambling license (license number 1668/JAZ), which indicates that it is secure and reliable. The mobile software helps most of the features of the original, including depositing and withdrawing cash. To achieve this, you have to log in and register within the cupboard.
To wager the bonus and withdraw the money, you have to make a betting turnover of 35 occasions its measurement. You need to do it within 7 days, making bets in slots for not extra than INR four hundred. To activate a promo code, enter it within the special subject when registering an account via the application. Your transaction will be accomplished in a couple of seconds.
In this text we are going to examine out who 1xBet really are, how theyve entered the Indian market with 1xBet India and how to get around the website. Get our exclusive 1xBet one hundred pc first deposit bonus up to 9,200 by entering the promo code luckydice when you sign up. When we switched to the cell net browser, we encountered an entirely completely different interface that pointed to a special URL. It was clearly designed as a standalone platform for mobile users. Although the layout is characteristically different from the desktop version, it does appear and feel acquainted. The main benefit of 1xbet is that it offers all possible information about the course of the match, its statistics, gamers, and their efficiency.
At the moment, 1xBet bookmaker presents new customers a sports bonus for subscribing to the positioning. To seize it, you need to make the primary deposit and so you will receive a reward of as much as 10,000 INR. The betting board of the 1xbet app presents plenty of choices that allow you to regulate the betting amount with a single click on. Users can simply use the1Xbet appfor Android and different units.
The young Indian leg spinner is commonly used as a real wicket-taking bowling possibility within the crucial middle overs by PBKS. Rahul Chahar has appeared in fine rythm this season, nonetheless, has failed to contribute with notable dismissals. A actual strong comeback from him is very anticipated by the consultants. The performance of Punjab Kings has been cold and warm this season, nonetheless, they presently seem one of many high contenders for the playoffs. Punjab characteristic some highly experinced campaigners with skipper Shikhar Dhawan leading the chart, and itll actually be crucial within the high-pressure game.
To entice new bettors, the app features a comprehensive bonus and promotion scheme. Both new and current customers are eligible for the 1xbet incentive. Below, well go...
06:24
1xbet App Obtain For Android Apk And Ios In India h+ Media
1xbet App Obtain For Android Apk And Ios In India
Gamers who like to test their luck with on-line on line casino slots can be a part of reside dealers gaming platforms such as Russian roulette 21, Wheel of Fortune, and much more. Go to the location as properly as the App Store for the download of their mobile app. The iOS applications interface is very fluid, permitting sports activities events to be proven simultaneously. With this cellular Application, players can view numerous sporting events by way of the iOS cell app.
Some people may wonder But do I even want the app if I can just place bets via 1xbet cell site? This is actually a good query, and to reply that, we wish to current to you a comparability of the cellular site model and a 1xbet app version. What can I say guys, it is not the most effective cell app that Ive seen, however it sure must be examined. 1xbet have good UX and design, player area can be not too dangerous, but could probably be better. What I actually suffer from is the dearth of stay broadcasts, its actually entertaining to watch them after youve got made few nice stakes.
The 1xBet welcome bonus is a 100% match on your first deposit as much as 100. This signifies that if you deposit 100 into your account, youll receive a further 100 as a bonus. 1xBet also provides a extensive range of particular bet sorts, similar to accumulator bets, lucky bets, and extra. The company has a variety of services and products which are available in a number of languages, together with English, Russian, Portuguese, Spanish, and extra. Conditions Sports bonus provides 100 percent as much as INR 20,000 cash available for the absolute newcomers on the first completion of their deposit necessities.
You can comply with sports occasions and make bets in Live mode. Prematch is a guess that you could place before the beginning of any match. Prematch is a basic wager and the chances for these bets are fastened, but they can also be changed.
- The 1xBet Android app also has the stay function, which guarantees you real-time updates of events, outcomes, and odds.
- However, they vary relying on whether you pick on line casino or sports activities betting online.
- You can register using 5 diverse methods like that on the desktop.
- Technical issues can typically occur with the app.
- As a end result, the app may be very convenient to have in case of such events.
- With the 1xbet app, customers can guess on their favorite sports activities, observe the results in actual time and access their account information.
If you register a second account, youll be blocked. If you dont have any money on your steadiness, but still have uncalculated bets, you might place conditional bets. With conditional bets, it is possible for you to to bet on any sporting event upfront, i.e. without utilizing any funds in your stability....
06:15
Zyxel firewall and VPN devices affected by critical flaws Security Affairs
Zyxel fixed two critical flaws in multiple firewall and VPN products that can lead to remote code execution or cause a DoS condition.
Zyxel addressed two critical buffer overflow vulnerabilities, tracked as CVE-2023-33009 and CVE-2023-33010, that affect several of its firewall and VPN products.
A remote, unauthenticated attacker can can trigger the flaws to cause a denial-of-service (DoS) condition and remote code execution on vulnerable devices.
Below are the description for both issues provided by the vendor in a security advisory:
- CVE-2023-33009 A buffer overflow vulnerability in the notification function in some firewall versions could allow an unauthenticated attacker to cause denial-of-service (DoS) conditions and even a remote code execution on an affected device.
- CVE-2023-33010 A buffer overflow vulnerability in the ID processing function in some firewall versions could allow an unauthenticated attacker to cause DoS conditions and even a remote code execution on an affected device
Users are recommended to install security updates provided by the company to address the issues.
- CVE-2023-33009: A buffer overflow vulnerability in the notification function in some Zyxel products, allowing an unauthenticated attacker to perform remote code execution or impose DoS conditions. (critical severity score of 9.8)
- CVE-2023-33010: A buffer overflow vulnerability in the ID processing function in some Zyxel products, allowing an unauthenticated attacker to perform remote code execution or impose DoS conditions. (critical severity score of 9.8)
The following table includes vulnerable devices:
| Affected series | Affected version | Patch availability |
|---|---|---|
| ATP | ZLD V4.32 to V5.36 Patch 1 | ZLD V5.36 Patch 2 |
| USG FLEX | ZLD V4.50 to V5.36 Patch 1 | ZLD V5.36 Patch 2 |
| USG FLEX50(W) / USG20(W)-VPN | ZLD V4.25 to V5.36 Patch 1 | ZLD V5.36 Patch 2 |
| VPN | ZLD V4.30 to V5.36 Patch 1 | ZLD V5.36 Patch 2 |
| ZyWALL/USG | ZLD V4.25 to V4.73 Patch 1 | ZLD V4.73 Patch 2 |
05:56
As U.S. Launch Sites Reach Capacity, Sea Platforms Could Ease the Pressure SoylentNews
With increasing demand on terrestrial launch pads, some companies are venturing out into the open sea, with this Virginia startup leading the way.
The Spaceport Company recently pulled off a series of rocket launches from a floating launch pad in the Gulf of Mexico, in its effort to create more options for rocket companies needing to reach space.
On Monday, the Virginia-based startup announced its successful demonstration, marking the first set of rocket launches from U.S. territorial waters using a prototype mobile floating spaceport.
"This demonstration provided numerous lessons which will be incorporated into our next project: building a sea-based spaceport capable of orbital operations," Tom Marotta, founder and CEO of The Spaceport Company, said in the company statement. "We are working towards offering the U.S.'s first truly commercial spaceport, which can best support the rapidly growing commercial launch industry and alleviate the burdens on government ranges."
In partnership with Evolution Space, which is providing the required propulsion systems, The Spaceport Company launched four small sounding rockets from a modified ship floating in the Gulf of Mexico. The demonstration paves the way for orbital launches hosted on offshore platformsan effort to decrease demand on terrestrial launch sites as the cadence of rocket launches continues to increase. The launch pace and resulting traffic at Cape Canaveral, Florida, is now so intense, for example, that U.S. Space Force is looking for alternatives, as SpaceNews reported earlier this month.
Read more of this story at SoylentNews.
05:06
Netflixs Password Sharing Crackdown Goes Global: 103 Countries Affected HackRead | Latest Cybersecurity and Hacking News Site
Netflix is sending emails addressing password sharing between households, and users are not happy about it as #CancelNetflix trends on social media.
This is a post from HackRead.com Read the original post: Netflixs Password Sharing Crackdown Goes Global: 103 Countries Affected
04:56
Trusted Flagger Anti-Piracy Tools Raise Concern at US Chamber of Commerce TorrentFreak
 The US Chamber of Commerce 2023 International IP
Index report is a pretty big read at 213 pages, but for those
interested in intellectual property matters, its an interesting one
too.
The US Chamber of Commerce 2023 International IP
Index report is a pretty big read at 213 pages, but for those
interested in intellectual property matters, its an interesting one
too.
The report benchmarks the IP frameworks in 55 major economies and rates them based on how effectively they protect all kinds of intellectual property. Countries and regions with a reputation for cracking down on infringement tend to gravitate towards the top of the index but that doesnt prevent the Chamber of Commerce from offering criticism.
European Union Criticized For Complexity
For the last two years, the European Commission has expended significant resources on two new pieces of legislation known as the Digital Markets Act (DMA) and the Digital Services Act (DSA). Their overall goal is to improve online safety and protect citizens fundamental rights, while ensuring that digital markets are both fair and open.
Time will tell how that all works out but for now, over-complication appears to have led to a level of frustration in the United States. The Chamber introduces the DSA as a sprawling piece of legislation granting vast regulatory and monitoring powers before noting the plethora of categorizations that hope to encompass all kinds of online platforms.
The law is full of definitions and categorizations of different providers of online intermediary services, including caching, mere conduit, hosting, online platforms, very large online platforms, and very large online search engines. Some of these categories are transplanted from preexisting definitions under the E-Commerce Directive, whereas others are new, the report notes.
[T]hese categories are fluid, and entities may, at different moments, be one or another or a combination of these categories with differing levels of accompanying compliance and reporting responsibilities. Consequently, an entitys legal obligation and responsibilities may change rather significantly depending on what category of service provider the entity was at a given moment.
Trusted Flaggers Fail to Impress
Major rightsholders and some governments have been promoting the use of so-called trusted flaggers to help tackle infringement. These entities could be companies, organizations or even an individual, but the key element is that they are trusted to make good decisions on the takedown, removal or blocking of content, directly on the platforms where content is found.
The concepts around this tend to vary, but a basic example might include a third-party acting on behalf of a rightsholder having direct access to a video platf...
03:49
03:15
The Imperative of Automating Fraud Detection in Financial Institutions HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
In light of a recent report exposing the active automation of scams with Telegram by phishers, it raises the question: Why not safeguard your business by automating fraud detection?
This is a post from HackRead.com Read the original post: The Imperative of Automating Fraud Detection in Financial Institutions
03:11
Dr. David Martin Covid Summit European Union Parliament May 2023 cryptogon.com
Via: chd.tv on Agent0fChange:
03:10
This Is Why I Teach My Law Students How to Hack SoylentNews
NYT Link: https://www.nytimes.com/2023/05/23/opinion/cybersecurity-hacking.html
Archive Link: https://archive.is/wMAXA
In the movies, you can tell the best hackers by how they type. The faster they punch the keys, the more dangerous they are. Hacking is portrayed as a highly technical feat, a quintessentially technological phenomenon.
This impression of high-tech wizardry pervades not just our popular culture but also our real-world attempts to combat cybercrime. If cybercrime is a sophisticated high-tech feat, we assume, the solution must be too. Cybersecurity companies hype proprietary tools like "next generation" firewalls, anti-malware software and intrusion-detection systems. Policy experts like John Ratcliffe, a former director of national intelligence, urge us to invest public resources in a hugely expensive "cyber Manhattan Project" that will supercharge our digital capabilities.
But this whole concept is misguided. The principles of computer science dictate that there are hard, inherent limits to how much technology can help. Yes, it can make hacking harder, but it cannot possibly, even in theory, stop it. What's more, the history of hacking shows that the vulnerabilities hackers exploit are as often human as technical not only the cognitive quirks discovered by behavioral economists but also old-fashioned vices like greed and sloth.
To be sure, you should enable two-factor authentication and install those software updates that you've been putting off. But many of the threats we face are rooted in the nature of human and group behavior. The solutions will need to be social too job creation programs, software liability reform, cryptocurrency regulation and the like.
For the past four years, I have taught a cybersecurity class at Yale Law School in which I show my students how to break into computers. Having grown up with a user-friendly web, my students generally have no real idea how the internet or computers work. They are surprised to find how easily they learn to hack and how much they enjoy it. (I do, too, and I didn't hack a computer until I was 52.) By the end of the semester, they are cracking passwords, cloning websites and crashing servers.
Read more of this story at SoylentNews.
03:01
PostgreSQL 16 Reaches Beta With Performance Improvements - Including SIMD for x86 & ARM Phoronix
PostgreSQL 16 is up to its first beta milestone today with new performance optimizations and continued security enhancements...
02:33
Cadent Gas Limited Brings Trouble (and Maybe COVID-19) schestowitz.com
Video
download link | md5sum
9014d1ac4981a4f86e5930dc24d3679d
Cadent Gas Limited Leaving a Mess Behind
Creative Commons Attribution-No Derivative Works 4.0
THE local (ish) company that handles the gas pipes was here today. I didnt agree to it, it was imposed on me, and the time wasnt up for negotiation either. A dirty kitchen was left behind and it seems likely at least one of the people had COVID-19, judging by the cough. Some were smoking on the job, outdoors
The video (conversation) above discussed a number of issues with one of the managers there (hopefully his name isnt on the video). I was urged to make a complaint and ask for some clarification about what had happened, why it had to happen etc.
At the end I left aside the first call that I made, before their escalation and callback. It didnt contain anything important that the second call did not cover as well (besides, it contained personal information like postcode and phone numbers), but it was useful for reference in case they tell inconsistent stories.
Excess deaths in the UK are very high this year. COVID-19 isnt over either; its still spreading and swirling, so having several strangers inside my kitchen, where food and beverages are handled, is undesirable, especially without proper consent. We are paying a lot of money for gas, we sometimes smell gas leaks, and here they go replacing metal pipes with plastic. When challenged about it over the phone, the managers accepted that the greenwashing of plastic pipes was disingenuous.
Its troubling to see the power that those power (gas/electricity) corporations have in the UK.
It should be noted that the above call (one of two and the more relevant/detailed one) is a culmination of a desire to phone up Cadent Gas Limited or E.ON Next (regarding the suspicious first letter and the suspected gas leak). If there really was an emergency/urgent matter (such as a confirmed gas leak in the area), theyre not talking about it. Both people whom I spoke with (at the above firm) deny there was a gas leak nearby. Remember that they have a vested interest here; theyd possibly deny any emergent issues with the pipes as its their responsibility to look after these pipes and leaks indicate a commercial failure of theirs. Lives would be at risk....
02:30
Civil Liberties Groups Demand California Police Stop Sharing Drivers Location Data With Police In Anti-Abortion States Deeplinks
SAN FRANCISCOSeventy-one California police agencies in 22 counties must immediately stop sharing automated license plate reader (ALPR) data with law enforcement agencies in other states because it violates California law and could enable prosecution of abortion seekers and providers elsewhere, three civil liberties groups demanded Thursday in letters to those agencies.
The letters from the Electronic Frontier Foundation (EFF), the American Civil Liberties Union of Northern California (ACLU NorCal), and the American Civil Liberties Union of Southern California (ACLU SoCal) gave the agencies a deadline of June 15 to comply and respond. A months-long EFF investigation involving hundreds of public records requests uncovered that many California police departments share records containing detailed driving profiles of local residents with out-of-state agencies.
ALPR camera systems collect and store location information about drivers, including dates, times, and locations. This sensitive information can reveal where individuals work, live, associate, worshipor seek reproductive health services and other medical care.
ALPRs invade peoples privacy and violate the rights of entire communities, as they often are deployed in poor and historically overpoliced areas regardless of crime rates, said EFF Staff Attorney Jennifer Pinsof. Sharing ALPR data with law enforcement in states that criminalize abortion undermines Californias extensive efforts to protect reproductive health privacy.
The letters note how the nations legal landscape has changed in the past year.
Particularly since the Supreme Courts decision in Dobbs v. Jackson Womens Health Organization, which overturned Roe v. Wade, ALPR technology and the information it collects is vulnerable to exploitation against people seeking, providing, and facilitating access to abortion, the letters say. Law enforcement officers in anti-abortion jurisdictions who receive the locations of drivers collected by California-based ALPRs may seek to use that information to monitor abortion clinics and the vehicles seen around them and closely track the movements of abortion seekers and providers. This threatens even those obtaining or providing abortions in California, since several anti-abortion states plan to criminalize and prosecute those who seek or assist in out-of-state abortions.
Idaho, for example, has enacted a law that makes helping a pregnant minor get an abortion in another state punishable by two to five year...
02:00
Meet the Forksheet: Imecs In-Between Transistor IEEE Spectrum

The most advanced manufacturers of computer processors are in
the middle of the first big change in device architecture in a
decadethe shift from finFETs to nanosheets. Another 10 years should bring about
another fundamental change, where nanosheet devices are stacked
atop each other to form complementary FETs (CFETs), capable of cutting
the size of some circuits in half. But the latter move is likely to
be a heavy lift, say experts. An in-between transistor called the
forksheet might keep circuits shrinking without
quite as much work.
The idea for the forksheet came from exploring the limits of the nanosheet architecture, says Julien Ryckaert, the vice president for logic technologies at Imec. The nanosheets main feature is its horizontal stacks of silicon ribbons surrounded by its current-controlling gate. Although nanosheets only recently entered production, experts were already looking for their limits years ago. Imec was tasked with figuring out at what point nanosheet will start tanking, he says.
Ryckaerts team found that one of the main limitations to shrinking nanosheet-based logic is keeping the separation between the two types of transistor that make up CMOS logic. The two typesNMOS and PMOSmust maintain a certain distance to limit capacitance that saps the devices performance and power consumption. The forksheet is a way to break that limitation, Ryckaert says.
Instead of individual nanosheet devices, the forksheet scheme builds them as pairs on either side of a dielectric wall. (No, it doesnt really resemble a fork much.) The wall allows the devices to be placed closer together without causing a capacitance problem, says Naoto Horiguchi, the director of CMOS technology at Imec. Designers could use the extra space to shrink logic cells, or they could use the extra room to build transistors with wider sheets leading to better performance, he says.
...