| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Tuesday, 18 April
01:46
[$] Avoiding the merge trap LWN.net
The kernel subsystem maintainers out there probably have a deep understanding of the sinking feeling that results from opening one's inbox and seeing a response from Linus Torvalds to a pull request. When all goes well, pull requests are acted upon silently; a response usually means that all has not gone well. Several maintainers got to experience that feeling during the 6.3 merge window, which seemed to generate more than the usual number of grumpy responses related to merge commits. Avoiding that situation is not hard, though, with a bit of attention paid to how merges are done.
01:44
Utah: Most Snowfall Since State Records Began in 1930s cryptogon.com
A three story cabin is buried up to the roof. One guy says its 30 feet of snow, another says 20 feet. In any event, this is pretty nuts. Via: HeavyDSparks: Related: Utahs Snowpack Highest Amount Ever Documented
01:43
Renewed Work For ACO Compiler Support With The RadeonSI Gallium3D Driver Phoronix
Back in 2019 Valve developers introduced the ACO compiler back-end within Mesa for the Radeon Vulkan "RADV" driver. This alternative to the AMDGPU LLVM shader compiler has been instrumental in helping RADV perform very well for Linux gaming both with Vulkan native titles as well as games going the route of DirectX to Vulkan via DXVK and VKD3D with Proton (Steam Play). On and off there's been talk and work towards bringing ACO to RadeonSI Gallium3D for OpenGL while now there is some new work on this front...
01:34
Hundreds of Teenagers Flood Into Downtown Chicago, Smashing Car Windows, Two People Shot cryptogon.com
Via: Fox32: Hundreds of teenagers flooded into Downtown Chicago on Saturday night, smashing car windows, trying to get into Millennium Park, and prompting a major police response. At least one person in a car was attacked. Shots were fired near the corner of Madison and Michigan, and FOX 32 Chicago decided that it was unsafe []
01:30
Wolfram Alpha With ChatGPT Looks Like a Killer Combo Hackaday

Have ever looked at Wolfram Alpha and the development of Wolfram Language and thought that perhaps Stephen Wolfram was a bit ahead of his time? Well, maybe the times may have finally caught up because Wolfram plus ChatGPT looks like an amazing combo. That link goes to a long blog post from Stephen Wolfram that showcases exactly how and why the two make such a wonderful match, with loads of examples. (If youd prefer a video discussion, one is embedded below the page break.)
OpenAIs ChatGPT is a large language model (LLM) neural network, or more conventionally, an AI system capable of conversing in natural language. Thanks to a recently announced plugin system, ChatGPT can now interact with remote APIs and therefore use external resources.
01:24
Why poetry is a variety of mathematical experience Lifeboat News: The Blog
Machine learning theory is shedding new light on how to think about the mysterious and ineffable nature of art by Peli Grietzer + BIO.
01:23
Singapore approves 16 species of insects including silkworms and grasshopper for human consumption Lifeboat News: The Blog

Future food.
Think about grasshopper fries, a protein bar made of crickets or silkworm cocoons. As unconventional as it may sound, Singapore is trying to make insect food mainstream. The Singapore Food Agency (SFA) has given approval to 16 species of insects, such as crickets, silkworms and grasshoppers for human consumption.
The latest news, reported by the Singapore newspaper The Straits Times notes that the approval of the insects for consumption will be subject to food safety requirements. This will include treatment processes to kill pathogens and proper packaging and storage facilities.
The United Nations Food and Agriculture Organisation (FAO) has been promoting insects for human consumption recently. Insects are known for their high protein content and Singapores latest interest in adding insects to the national food menu is seen as a way for the country to safeguard its national food security. As per The Strait Times newspaper, the SFA had also conducted a scientific review to analyse the benefits of directly eating specific insects or making them into items such as snacks for human consumption. The Singapore government also held a public consultation exercise on the regulation of insects and insect products before the SFA approval.
Besides insects, SFA said it will also permit the cocoons of silkworms for human consumption in Singapore. They are also consumed in China and Malaysia, among other places. Silkworms produce cocoons with silk threads that are composed of two main proteins, known as sericin and fibroin. While silk has traditionally been used to produce textiles, countries like Japan have allowed companies to turn these silk threads into food and edible coatings in recent years. With the new announcement, the Singapore food industry is trying to capitalise on the opportunity to launch snacks and protein bars made of insects. Several home-grown firms also produce cricket powder for use in flour and cookies and are currently selling it to customers in the US and the UK. But the scale of consumer demand and the lack of public awareness is seen as challenges down the road. With a growing population, the world needs more available, affordable and sustainable alternatives for a balanced diet. However, a lot more needs to be done to normalise insect consumption around the world.
01:23
How to Summon Entities: A Glimpse into GPT-4 through the lens of Jungian Psychology & Jungian Archetypes Lifeboat News: The Blog
Introduction.
The GPT-4 language model is a remarkable AI technology that can
generate human-like text.
While it lacks certain human psychological factors, such as individuation and the Jungian Shadow, GPT-4 demonstrates a fascinating awareness of archetypes and their role in shaping human behavior.
This article delves into GPT-4s understanding of Jungian psychology and explores the implications of archetypes as a language-space phenomenon.
01:22
With Security Copilot, Microsoft brings the power of AI to cyberdefense Lifeboat News: The Blog
Trained across security and networking disciplines and armed with trillions of data signals, Security Copilot dramatically increases the reach, speed and effectiveness of any security team
REDMOND, Wash. March 28, 2023 Microsoft Corp. on Tuesday announced it is bringing the next generation of AI to cybersecurity with the launch of Microsoft Security Copilot, giving defenders a much-needed tool to quickly detect and respond to threats and better understand the threat landscape overall. Security Copilot will combine Microsofts vast threat intelligence footprint with industry-leading expertise to augment the work of security professionals through an easy-to-use AI assistant.
Today the odds remain stacked against cybersecurity professionals. Too often, they fight an asymmetric battle against relentless and sophisticated attackers, said Vasu Jakkal, corporate vice president, Microsoft Security. With Security Copilot, we are shifting the balance of power into our favor. Security Copilot is the first and only generative AI security product enabling defenders to move at the speed and scale of AI.
01:22
UK Power Grid Could Have Worlds First Commercial Fusion Reactor Lifeboat News: The Blog
TAE Technologies hopes to have a net energy producing fusion reactor operating on the UK grid by the 2030s.
01:22
Budweiser Tries Patriotic Ad Campaign After Dylan Mulvaney Disaster cryptogon.com
haha Woops. Lets go with Merica again and maybe people will forget about our insane woke fail. Via: Fox: Budweisers new pro-America ad set Twitter ablaze over the weekend as critics derided the company for a misguided attempt at quelling the backlash over Bud Lights endorsement partnership with transgender influencer Dylan Mulvaney. Budweisers latest advertisement, []
01:22
We May Finally Know How Our Eyesight Evolved, And Its Not From Our Branch of Life Lifeboat News: The Blog
The evolution of the human eye has long been considered one of biologys more challenging mysteries, drawing debate over the sequence of steps required to turn rudimentary sensitivity to light into a complex photographic system.
New research suggests some components of vertebrate vision may not have been shaped incrementally as their genes passed down family lines, but were stolen from entirely different branches of life.
At least one innovation that led to the current structure of vertebrate eyes did not occur from stepwise tinkering with genes that exist in other animals, but came from introduction of novel DNA from bacteria by horizontal gene transfer, explains molecular biologist Matt Daugherty from the University of California, San Diego (UCSD) on Twitter.
01:07
Elizabeth Chamberlain: The Future of the Right to Repair and Free Software Techrights
Summary: A day ago this LibrePlanet non-keynote talk from Elizabeth Chamberlain was uploaded by the FSF, about a month after the in-person talk (slides here); From the page: Dr. Elizabeth Chamberlain is Director of Sustainability at iFixit, which is the free repair manual for everything, with over 90,000 guides for fixing everything from tractors to toasters. Liz advocates for the Right to Repair around the world, supporting lawmakers, conducting repair research, and working to make sure environmental standards reflect repair best practices. Her writing on repair has been published in the Wall Street Journal, Wired, and The Atlantic.
Licence: CC BY SA 4.0
01:03
QuaDream, Israeli iPhone hacking spyware firm, to shut down HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
QuaDream, based in Ramat Gan, Israel, with around 40 employees, is known for its spyware used for hacking iPhones.
This is a post from HackRead.com Read the original post: QuaDream, Israeli iPhone hacking spyware firm, to shut down
00:35
[Meme] Stole 100,000 Pounds, Gained 100 Pounds Techrights
They did this to a lot of programmers and GNU/Linux engineers at Sirius (deductions taken, but embezzled)

In Sirius (of the past decade) you neednt demonstrate technical
skills but an immovable will to cooperate in illegal stuff
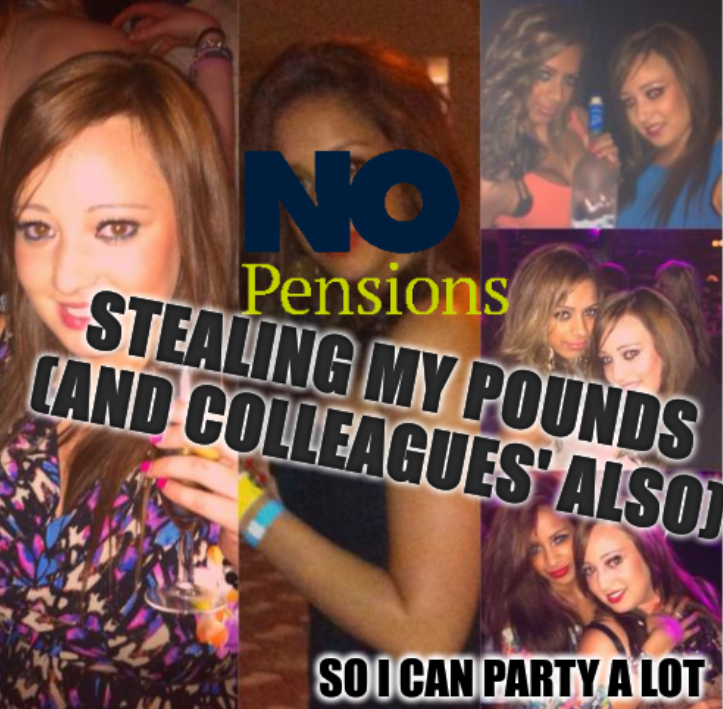
The technical staff at Sirius worked from 5:30PM, overnight,
until 9AM! She never worked at night. She partied. In daytime she
casually harassed technical staff. I cant code, but I can harass
people who do (reference)

With her in the helm,
the company clocked close to 9,000 pounds in theft (from me
alone, not counting all the colleagues) so she can party at
night and her boss can take the family (4 people) to
super-expensive Disney trips abroad
Summary: The Crime Assistant of the CEO of...
00:34
Security updates for Monday LWN.net
Security updates have been issued by Debian (chromium, rails, and ruby-rack), Fedora (firefox, ghostscript, libldb, samba, and tigervnc), Mageia (ceph, davmail, firefox, golang, jpegoptim, libheif, python-certifi, python-flask-restx, thunderbird, and tomcat), Oracle (firefox), Red Hat (firefox), Scientific Linux (firefox), SUSE (apache2-mod_auth_openidc, aws-nitro-enclaves-cli, container-suseconnect, firefox, golang-github-prometheus-prometheus, harfbuzz, java-1_8_0-ibm, kernel, liblouis, php7, tftpboot-installation images, tomcat, and wayland), and Ubuntu (chromium-browser, imagemagick, kamailio, and libreoffice).
00:27
33% of Open Source Summit North America speakers identify as female or non-binary! Linux.com
read the original post at Read More
The post 33% of Open Source Summit North America speakers identify as female or non-binary! appeared first on Linux.com.
00:15
GCC 13.1 Compiler Likely Releasing Next Week Phoronix
The GNU Compiler Collection 13 codebase has no more P1 bugs, which are regressions of the highest priority, and as such the GCC 13 codebase was branched today with plans of issuing GCC 13.1-rc1 likely in the next day and hopefully releasing GCC 13.1 as the first stable release of the GCC 13 series next week...
00:12
MEPs Raise Concerns Over Draft EU-US Data Transfer Deal SoylentNews
MEPs raise concerns over draft EU-US data transfer deal:
A shiny new data transfers deal between the European Union and the United States aimed at fixing costly legal uncertainty over exports of personal data isn't in place yet but the European Parliament's civil liberties committee is predicting the incoming EU-U.S. Data Privacy Framework (DPF) won't survive a legal challenge just as its two predecessors, Safe Harbor (RIP: October 2015); and Privacy Shield (RIP: July 2020), failed to impress EU judges.
In a resolution passed by the LIBE committee yesterday, with 37 votes in favor, none against and 21 abstentions, the MEPs dubbed the DPF an improvement that nonetheless does not go far enough. They also predicted it's likely to be invalidated by the Court of Justice of the EU (CJEU) in the future.
The development follows a draft opinion by the LIBE, back in February, also giving the proposal a thumbs down and urging the Commission to press for meaningful reforms.
In the resolution, the committee takes the view that the proposed arrangement does not provide sufficient safeguards for EU citizens since the framework still allows for bulk collection of personal data in certain cases; does not make bulk data collection subject to independent prior authorisation; and does not provide for clear rules on data retention.
The MEPs are also worried that a proposed redress mechanism a so-called "Data Protection Review Court" would violate EU citizens' rights to access and rectify data about them, since decisions would be kept secret. They also question its independence since judges could be dismissed by the U.S. president, who could also overrule its decisions.
Read more of this story at SoylentNews.
00:00
PUF Away for Hardware Fingerprinting Hackaday

Despite the rigorous process controls for factories, anyone who has worked on hardware can tell you that parts may look identical but are not the same. Everything from silicon defects to microscopic variations in materials can cause profoundly head-scratching effects. Perhaps one particular unit heats up faster or locks up when executing a specific sequence of instructions and we throw our hands up, saying its just a fact of life. But what if instead of rejecting differences that fall outside a narrow range, we could exploit those tiny differences?
This is where physically unclonable functions (PUF) come in. A PUF is a bit of hardware that returns a value given an input, but each bit of hardware has different results despite being the same design. This often relies on silicon microstructure imperfections. Even physically uncapping the device and inspecting it, it would be incredibly difficult to reproduce the same imperfections exactly. unforgeable.
Because they depend on manufacturing artifacts, there is a certain unpredictability, and deciding just what features to look at is crucial. The PUF needs to be deterministic and produce the same value for a given specific input. This means that temperature, age, power supply fluctuations, and radiation all cause variations and need to be hardened against. Seve...
Monday, 17 April
23:50
FIN7 and Ex-Conti Cybercrime Gangs Join Forces in Domino Malware Attacks The Hacker News
A new strain of malware developed by threat actors likely affiliated with the FIN7 cybercrime group has been put to use by the members of the now-defunct Conti ransomware gang, indicating collaboration between the two crews. The malware, dubbed Domino, is primarily designed to facilitate follow-on exploitation on compromised systems, including delivering a lesser-known information stealer that
23:33
China-linked APT41 group spotted using open-source red teaming tool GC2 Security Affairs
China-linked APT41 group used the open-source red teaming tool GC2 in an attack against a Taiwanese media organization.
Google Threat Analysis Group (TAG) team reported that the China-linked APT41 group used the open-source red teaming tool Google Command and Control (GC2) in an attack against an unnamed Taiwanese media organization.
The APT41 group, aka Winnti, Axiom, Barium, Blackfly, HOODOO) is a China-linked cyberespionage group that has been active since at least 2007.
The attack took place in October 2022, threat actors sent phishing emails that contained links to a password-protected file hosted in Drive. The final payload was the Go-written GC2 tool that gets commands from Google Sheets and exfiltrates data to Google Drive.
In October 2022, Googles Threat Analysis Group (TAG) disrupted a campaign from HOODOO, a Chinese government-backed attacker also known as APT41, that targeted a Taiwanese media organization by sending phishing emails that contained links to a passwordprotected file hosted in Drive. reads the Threat Horizons April 2023 Threat Horizons Report published by Google.The payload was an open source red teaming tool called Google Command and Control (GC2).
Upon installing the malware on the target system, it queries Google Sheets to obtain attacker commands. GC2 also allows operators to download additional files from Drive onto the victim system.

Google TAG experts...
23:32
What's the Difference Between CSPM & SSPM? The Hacker News
Cloud Security Posture Management (CSPM) and SaaS Security Posture Management (SSPM) are frequently confused. The similarity of the acronyms notwithstanding, both security solutions focus on securing data in the cloud. In a world where the terms cloud and SaaS are used interchangeably, this confusion is understandable. This confusion, though, is dangerous to organizations that need to secure
23:30
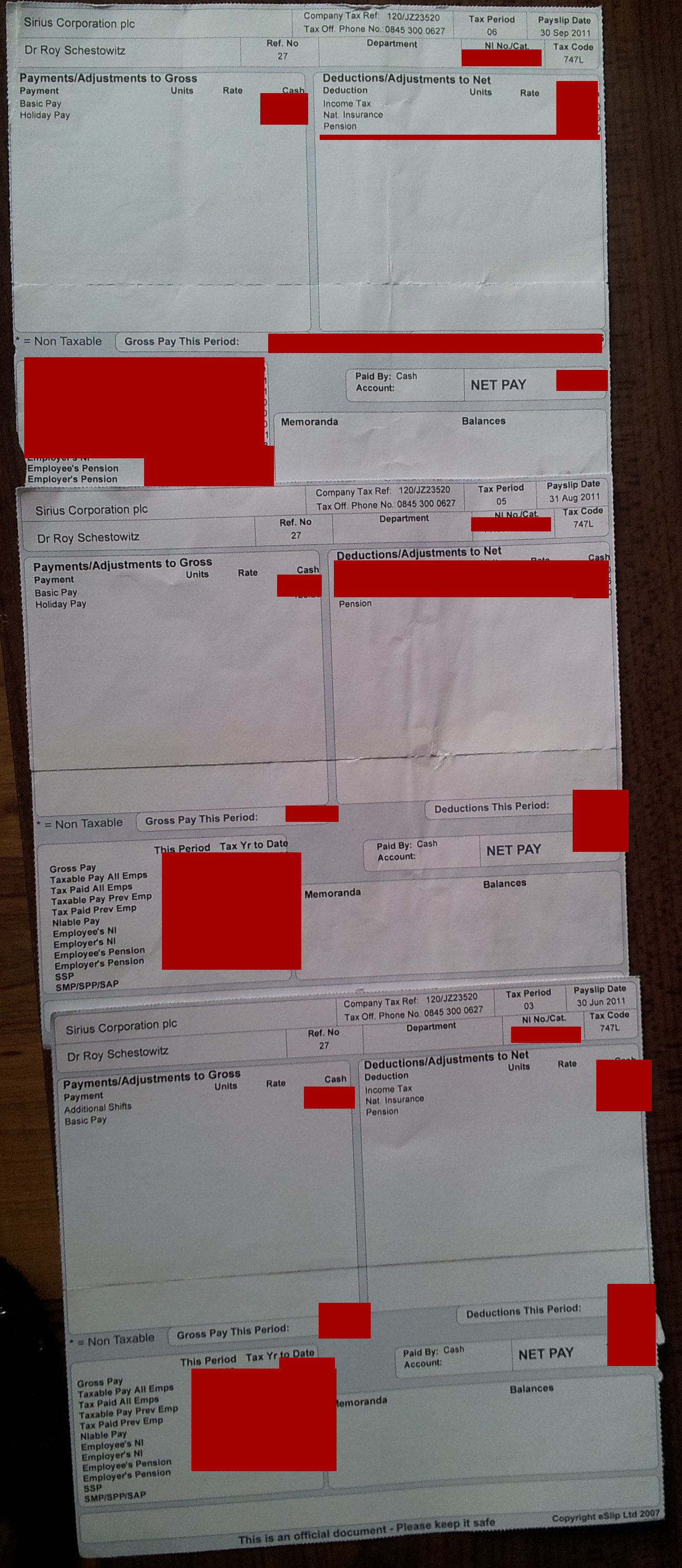
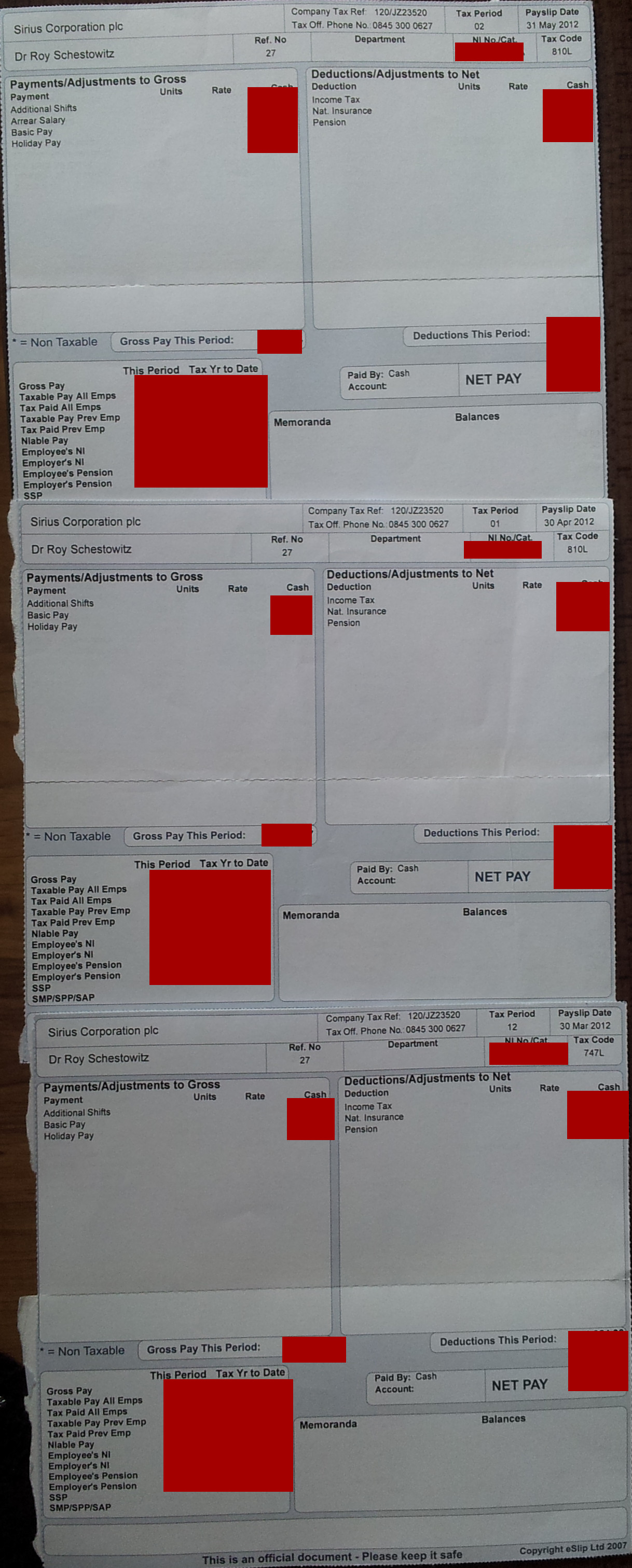
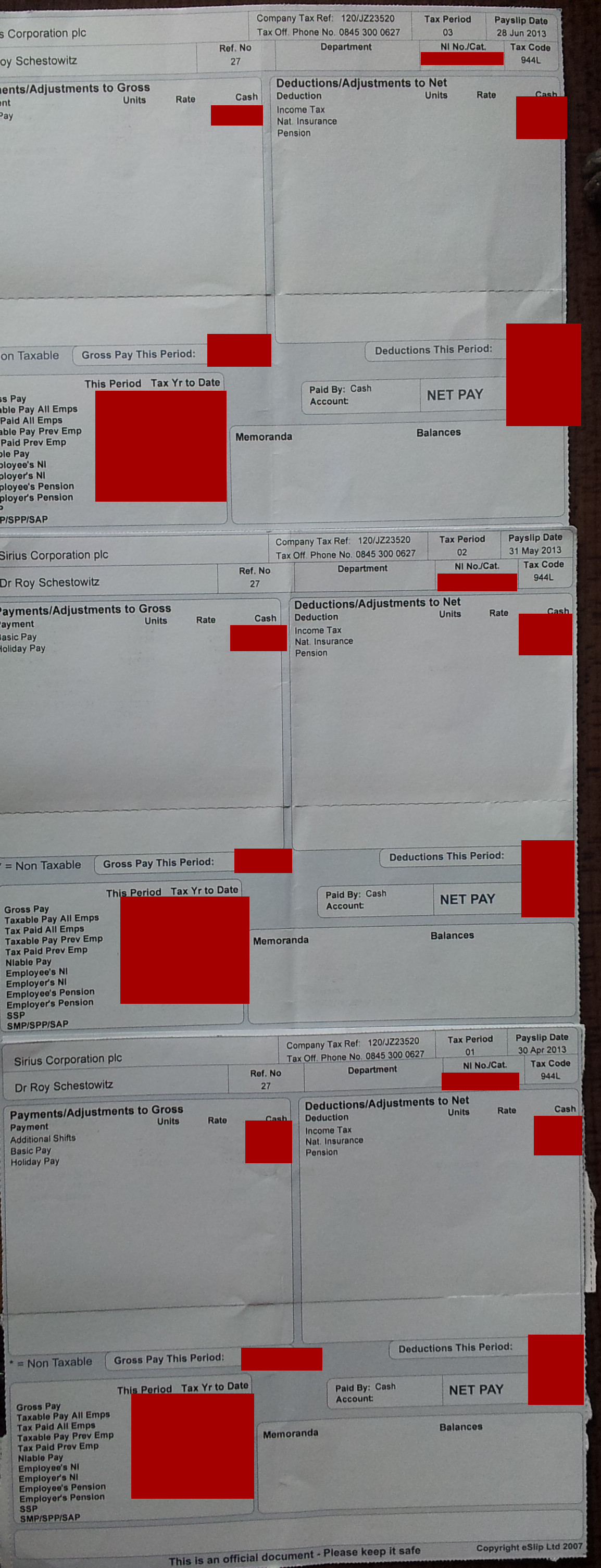
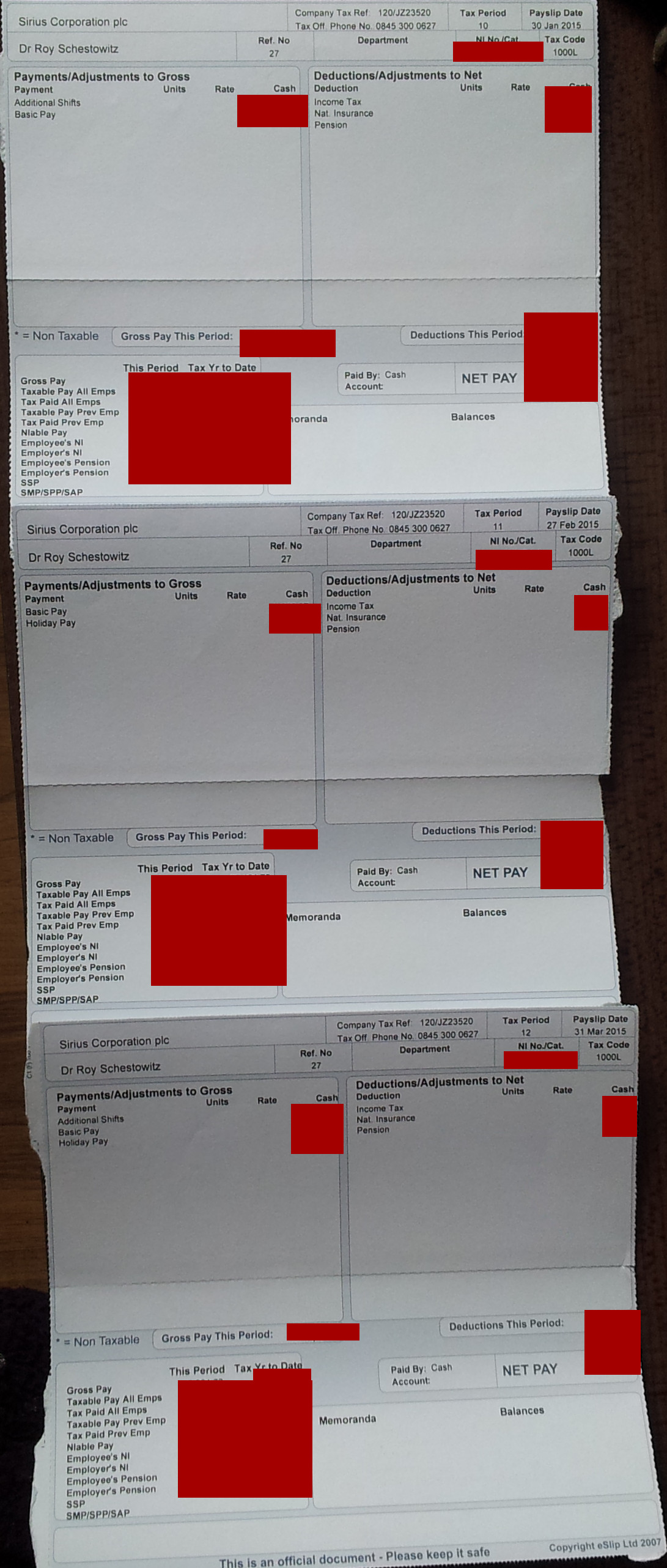
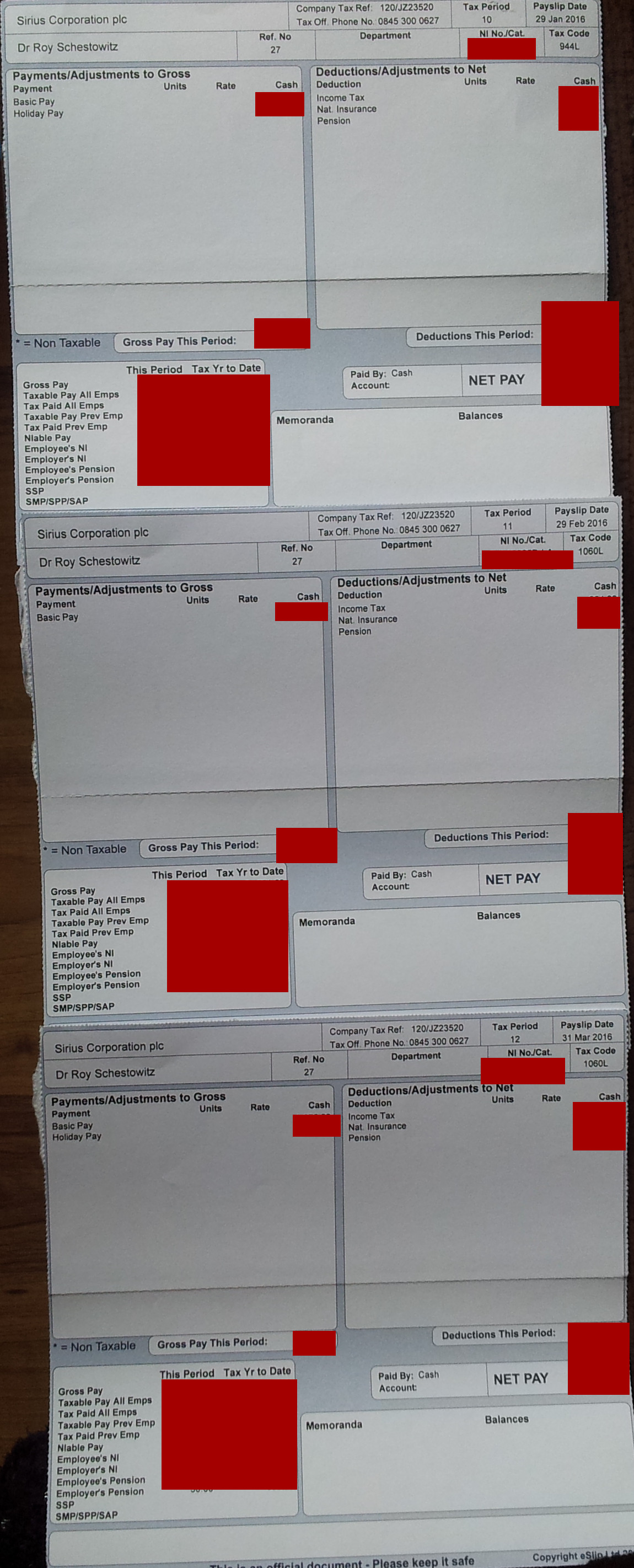
[Meme/Facts] Drowning in Marketing Material and Assurances (From Sirius, Standard Life, Integrity Financial Management Ltd.) While Payslips Say We Pay Into a Pension Every Month Techrights
The payslips of my colleagues said the same; we didnt know it was a sham pension or a total fraud
Summary: Sirius Open Source fraudsters robbed the technical staff for many years; the payslips all indicated a pension was being paid into, but this was never done and pension providers kept evading questions on the matter, which makes them partly complicit
23:24
Starship Flight Test Lifeboat News: The Blog

SpaceX is targeting as soon as Monday, April 17 at 8:00 a.m. CT for the first flight test of a fully integrated Starship and Super Heavy rocket from Starbase
23:23
Watch SpaceX TEST Starship, the biggest rocket ever, LIVE from the edge of the exclusion zone!!! Lifeboat News: The Blog

Recommended:
This is the first fully integrated full stack test flight of Starship and the mighty Super Heavy booster. At lift off, it will become the largest and most most powerful rocket to ever fly producing over twice as much thrust as the Saturn V that took humans to the moon.
The goal of the test is to get as far along in the mission as possible with a handful of important goals such as; clearing the launch pad, reaching max Q, getting to stage separation, ignition of Starship, burn Starships engines for 7 minutes and 20 seconds which would get Starship up to nearly orbital velocities and would place Starship on a suborbital trajectory that will cause it to reenter just north of Hawaii. This would allow the teams to test the reentry profile and heat shields for the first time from orbital velocities.
Want more information? Check out our Prelaunch Preview written by Austin Desisto https://everydayastronaut.com/starship-superheavy-orbital-flight-test/
Want to know where to watch this live? I made a video on how to visit Starbase and where to watch a launch from https://youtu.be/aWvHrih-Juk.
Want to support what I do? Consider becoming a Patreon supporter for access to exclusive livestreams, our discord channel! http://patreon.com/everydayastronaut.
Or become a YouTube member for some bonus perks as well! https://www.youtube.com/channel/UC6uKrU_WqJ1R2HMTY3LIx5Q/join.
The best place for all your space merch needs!
https://everydayastronaut.com/shop/
23:22
Fred Adams Will the Universe Ever End? Lifeboat News: The Blog

What does it mean to ask about the end of the universe? Can the universe even have an end? What would end? In the far, far future, what happens to stars, galaxies, and black holes? What about mass and energy, even space and time? Whats the Big Crunch and the Big Rip? And what if there are multiple universes, will the multiverse ever end?
Free access to Closer to Truths library of 5,000 videos: http://bit.ly/376lkKN
Watch more interviews on the end of the universe: https://bit.ly/3MSHlFF
Support the show with Closer To Truth merchandise: https://bit.ly/3P2ogje.
Fred Adams is a professor of physics at the University of Michigan. His work is in the general area of theoretical astrophysics with a focus on the study of star formation and cosmology.
Register for free at CTT.com for subscriber-only exclusives: https://bit.ly/3He94Ns.
23:01
Enabling Kubernetes self-service the operator way Linux.com
Learn how operators can serve as governance tools in a multitenant setting.
Read More at Enable Sysadmin
The post Enabling Kubernetes self-service the operator way appeared first on Linux.com.
22:48
[Meme] Standard Life: We Dont Know Who All Those GNU/Linux Engineers Are (But You Know, Standard Life; We Were All on Your System) Techrights
Standard Life claims not to know us; so all those brochures sent to us must have come by accident since 12 years ago
Summary: The Standard Life sham pension was a critical component of fraud at Sirius Open Source, robbing an unknown number of workers, GNU/Linux system administrators and programmers. There is a personal code and everything on papers from Standard Life, so we were on their computer system, but now they try to deny this either because they deleted us from the system or the system is built to vanish us from it (after a while). They also give inconsistent information, which is typically indicative/suggestive/implying that theyre hiding something and when inquired about the details they literally hang up the phone (rudely).
22:47
Live Feed: Starship Flight Test [Scrubbed] cryptogon.com
Update: Scrubbed Via: SpaceX:
22:26
The Role of Integrity Financial Management Ltd. in Facilitating Fraud at Sirius Open Source Techrights
This is how they scammed GNU/Linux geeks in 2011 onwards:
Summary: The crimes of Sirius Open Source were facilitated by a network of financiers who vanish the money or give an illusion of authority and accountability; heres another one of them (Integrity Financial Management Ltd.), facilitating the Standard Life sham pension
22:24
Are Smart Home Devices Invading Your Privacy? HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
Smart home devices are becoming more and more popular in recent years, promising convenience and automation to enhance
This is a post from HackRead.com Read the original post: Are Smart Home Devices Invading Your Privacy?
22:20
AMD Ryzen 7 7800X3D: Windows 11 vs. Ubuntu 23.04 Linux Performance Phoronix
With the recent launch of the AMD Ryzen 7 7800X3D, several Phoronix Premium supporters expressed interest in seeing how well the Windows 11 vs. Linux performance compared for this Zen 4 3D V-Cache processor. Given those requests, here are some CPU/system benchmarks looking at the performance of Windows 11 Professional against Ubuntu 23.04 in its near-final state on the 7800X3D desktop.
22:15
SpaceX's First Orbital Test Flight of Starship Imminent [Scrubbed] SoylentNews
https://en.wikipedia.org/wiki/SpaceX_Starship_orbital_test_flight
The Starship Orbital Flight Test is the planned first spaceflight of the SpaceX Starship launch vehicle. The planned launch site is Boca Chica, Texas. SpaceX plans on using Starship prototypes Ship 24 (second stage) and Booster 7 (first stage). The Starship second stage will enter a transatmospheric Earth orbit with a negative Earth perigee, allowing Ship 24 to reenter the atmosphere after completing most of one orbit without having to restart its engines for a deorbit maneuver. The earliest launch opportunity is currently scheduled for April 17, 2023 at 08:00 CDT (13:00 UTC).
SpaceX stream. NASASpaceFlight stream.
Read more of this story at SoylentNews.
22:13
Letter From NOW: Pensions Regarding Misconduct and Theft at Sirius Open Source schestowitz.com
Summary: Having just contacted NOW: Pensions (and several times more this past week), while moreover working on 3 leads at the same time, they finally (belatedly) gave a real assurance
Today well share a bunch of photographic evidence regarding crimes of Sirius Open Source, a firm that claims to be Britains most respected firm in this domain/area (Open Source). Of course its a lie. Not just the part about respected
They kept lying to cover up prior lies, in effect lying to me like half a dozen times already.Half a day ago I sent the following E-mail message to NOW: Pensions. About an hour ago I finally received a letter addressed to my wife and I. After nearly 3 months!!! Months of endless remainders after repeated lies.
Here is the E-mail I sent last night:
A few days ago Standard Life sent a whole bunch of us a formal letter concluding that Sirius had engaged in pension fraud and stole money from us for many years. This is a criminal matter. This is now formalised.
My wife and I are coming to collect our funds from NOW: Pensions this week. Please specify the time that best suits you. We live not far from your office.
Suffice to say, repeated lying by your staff including by managers will be duly noted. We trust neither you nor Sirius.
The sad thing is that pension providers have helped the perpetrators of crimes, covering up for them instead of working to protect the victims, who are the peoples whose money is actually making its way into the accounts of reckless gamblers at the pension firms. Who do you work for? Are you working for employers who commit crimes instead of employees (whose money you are taking)?
Silence on this matter wont help you. Au contraire. Please respond today.
They kept lying to cover up prior lies, in effect lying to me like half a dozen times already. Its circular and when challenged on the lies, more lies follow. Those people are handling (gambling with) peoples money. Trillions of dollars are managed by those sorts of firms.
As victims, we can progress along some lines. Standard Life, which well tackle separately later, tried victim-blaming (we have this on record). Thats akin to saying to a rape victim that it is his/her fault, e.g. why didnt you sense s/hed rape you after the date?
Many technical people suspected something was amiss and when phoning Standard Life we were only obstructed, so in effect Standard Life all...
22:11
NOW: Pensions Finally Sends the Letters It Has Been Promising (in Vain) for Several Months Regarding Fraud at Sirius Open Source Techrights
Summary: Having just contacted NOW: Pensions (and several times more this past week), while moreover working on 3 leads at the same time, they finally (belatedly) gave a real assurance
Today well share a bunch of photographic evidence regarding crimes of Sirius Open Source, a firm that claims to be Britains most respected firm in this domain/area (Open Source). Of course its a lie. Not just the part about respected
They kept lying to cover up prior lies, in effect lying to me like half a dozen times already.Half a day ago I sent the following E-mail message to NOW: Pensions. About an hour ago I finally received a letter addressed to my wife and I. After nearly 3 months!!! Months of endless remainders after repeated lies.
Here is the E-mail I sent last night:
A few days ago Standard Life sent a whole bunch of us a formal letter concluding that Sirius had engaged in pension fraud and stole money from us for many years. This is a criminal matter. This is now formalised.
My wife and I are coming to collect our funds from NOW: Pensions this week. Please specify the time that best suits you. We live not far from your office.
Suffice to say, repeated lying by your staff including by managers will be duly noted. We trust neither you nor Sirius.
The sad thing is that pension providers have helped the perpetrators of crimes, covering up for them instead of working to protect the victims, who are the peoples whose money is actually making its way into the accounts of reckless gamblers at the pension firms. Who do you work for? Are you working for employers who commit crimes instead of employees (whose money you are taking)?
Silence on this matter wont help you. Au contraire. Please respond today.
They kept lying to cover up prior lies, in effect lying to me like half a dozen times already. Its circular and when challenged on the lies, more lies follow. Those people are handling (gambling with) peoples money. Trillions of dollars are managed by those sorts of firms.
As victims, we can progress along some lines. Standard Life, which well tackle separately later, tried victim-blaming (we have this on record). Thats akin to saying to a rape victim that it is his/her fault, e.g. why didnt yo...
21:46
Google Uncovers APT41's Use of Open Source GC2 Tool to Target Media and Job Sites The Hacker News
A Chinese nation-state group targeted an unnamed Taiwanese media organization to deliver an open source red teaming tool known as Google Command and Control (GC2) amid broader abuse of Google's infrastructure for malicious ends. The tech giant's Threat Analysis Group (TAG) attributed the campaign to a threat actor it tracks under the geological and geographical-themed moniker HOODOO, which is
21:36
Tour of the Underground: Master the Art of Dark Web Intelligence Gathering The Hacker News
The Deep, Dark Web The Underground is a haven for cybercriminals, teeming with tools and resources to launch attacks for financial gain, political motives, and other causes. But did you know that the underground also offers a goldmine of threat intelligence and information that can be harnessed to bolster your cyber defense strategies? The challenge lies in continuously monitoring the right
21:18
Vice Society gang is using a custom PowerShell tool for data exfiltration Security Affairs
Vice Society ransomware operators have been spotted using a PowerShell tool to exfiltrate data from compromised networks.
Palo Alto Unit 42 team identified observed the Vice Society ransomware gang exfiltrating data from a victim network using a custom-built Microsoft PowerShell (PS) script.
Threat actors are using the PowerShell tool to evade software and/or human-based security detection mechanisms. PS scripting is often used within a typical Windows environment, using a PowerShell-based tool can allow threat actors to hide in plain sight and get their code executed without raising suspicion.
Early in 2023, the researchers spotted the gang using a script named w1.ps1 to exfiltrate data from a victim network. Unit42 researchers were able to recover the script from the Windows Event Log (WEL).
The script identifies any mounted drives on the target system by using Windows Management Instrumentation (WMI), then iterates through the identified drives to prepare data exfiltration via HTTP POST events using the objects .UploadFile method.
each HTTP POST event will include the files full path. If you are able to obtain the source hosts IP address along with this path, you will then be able to build out a list of exfiltrated files after the fact. reads the analysis published by Palo Alto Networks.
The script uses the CreateJobLocal( $folders ) function to create PowerShell script blocks to be run as jobs via the Start-Job cmdlet. The CreateJobLocal function receives groups of directories, often in groups of five.
The tool uses an inclusion/exclusion process based on keywords to select which directories to pass to the fill() function to exfiltrate.
The tool doesnt target folders containing system files, backups, folders associated with web browsers, and folders used by security solutions from Symantec, ESET, and Sophos.
The script finds all files within each directory that matches the include list, it exfiltrates files that do not have extensions found on the exclude list and that are larger than 10 KB.
The script ignores files that are under 10 KB in size and that do not have a file extension.
Vice Societys PowerShell data exfiltration script is a simple tool for data exfiltration. Multi-processing and queuing are used to ensure...
21:16
CVE-2023-27525: Apache Superset: Incorrect default permissions for Gamma role Open Source Security
Posted by Daniel Gaspar on Apr 17
Description:An authenticated user with Gamma role authorization could have access to metadata information using non trivial methods
in Apache Superset up to and including 2.0.1
Credit:
NTT DATA (finder)
References:
https://superset.apache.org
https://www.cve.org/CVERecord?id=CVE-2023-27525
21:15
Nintendo Hacker Gary Bowser Released From Federal Prison TorrentFreak
 In the fall of 2020, the U.S. Government
indicted three members of the infamous Team Xecuter group, the
masterminds behind various Nintendo hacks.
In the fall of 2020, the U.S. Government
indicted three members of the infamous Team Xecuter group, the
masterminds behind various Nintendo hacks.
The group allegedly made millions of dollars through its operation, which effectively shut down shortly after the criminal proceedings started.
The authorities arrested Canadian Gary Bowser in the Dominican Republic and Frenchman Max Louarn was detained in Tanzania. The latter, a notorious hacker, miraculously managed to avoid extradition to the United States. The same cant be said for Bowser.
40 Months Prison for Salesperson
As the purported salesperson of Team-Xecuter, Bowser wasnt a leading figure in the operation. Most people knew him as GaryOPA, the operator of MaxConsole, a website that regularly reviewed Team-Xecuter hardware and other hacking tools.
Financially, Bowsers role was also rather limited. From all the millions of dollars in revenue that were generated by Team-Xecuter, Bowser was paid only $500 to $1000 a month, his attorney previously said. He didnt deny involvement, however.
Following his arrest, Bowser was deported to the United States where he pleaded guilty. Last February, Bowser was sentenced to 40 months in prison for his role in the criminal enterprise. The sentence is significant but lower than the five-year prison term the Government had requested.
During sentencing, Judge Lasnik said that it was important to send a message but agreed that a reduction was warranted as Bowser played the smallest role of the three defendants.
Early Release
Bowser was later incarcerated at Federal Detention Center SeaTac in Seattle. A few weeks ago his attorney put in a request for an early release, citing the time credits earned by his client to date. That request was denied as moot earlier this month, as the Bureau of Prisons had pushed Bowsers release date forward.
In a recent video interview with Nick Moses, Bowser explains that he was released from federal prison on Marc...
21:14
CVE-2023-25504: Apache Superset: Possible SSRF on import datasets Open Source Security
Posted by Daniel Gaspar on Apr 17
Description:A malicious actor who has been authenticated and granted specific permissions in Apache Superset may use the import
dataset feature in order to conduct Server-Side Request Forgery
attacks and query internal resources on behalf of the server where Superset
is deployed. This vulnerability exists in Apache Superset versions up to and including 2.0.1.
Credit:
Alexey Sabadash, VK (finder)
References:
https://superset.apache.org...
21:00
A Clock Timebase, No Microcontroller Hackaday

Making an electronic clock is pretty easy here in 2023, with a microcontroller capable of delivering as many quartz-disciplined pulses as youd like available for pennies. But how did engineers generate a timebase back in the old days, and how would you do it today? Its a question [bicyclesonthemoon] is answering, with a driver for a former railway station clock.
The clock has a mechanism that expects pulses every minute, a +24V pulse on even minutes, and a -24V pulse on odd ones. He received a driver module with it, but for his own reasons wanted a controller without a microcontroller. He also wanted the timebase to be derived from the mains frequency. The result is a delve back into 1970s technology, and the type of project thats now a pretty rare sight. Using a mixture of 4000 series logic and a few of the ubiquitous 555s [bicyclesonthemoon] recovers 50Hz pulses from the AC, and divides them down to 1 pulse per minute, before splitting into odd and even minutes to drive a pair of relays which in turn drive the clock. We like it, a lot.
Mains-locked clocks are less common than they used to be, but theyre still a thing. Do you still wake up to one?
20:38
Chinese GPU Vendor Moore Threads Contributing To VA-API, FFmpeg Phoronix
Moore Threads was established in 2020 to create domestic GPU solutions in China with their first products having been announced last year. Most of the talk around Moore Threads "MThreads" GPUs have been for Windows but they are working on Linux support to at least some extent...
20:20
Apple M1/M2 Keyboard Backlight Support Set For The Linux 6.4 Kernel Phoronix
In addition to Linux 6.4 bringing some early work around the Apple M2 device support that isn't yet ready for end-users but begins laying the foundation for supporting the new MacBook Air, MacBook Pro, and Mac Mini, another set of Apple changes have now been submitted ahead of this next kernel cycle...
20:00
Accelerate 800G Ethernet Deployments IEEE Spectrum

Get up to speed on the evolution of data centers.
The Data Center Ethernet Technology and Evolution to 224 Gbps application note explains the latest evolution of high speed ethernet links, technical challenges of 800G ethernet, and test solutions available for up to 224 Gbps interfaces.
19:21
Improve Security by Adopting Aviation's 'Just Culture' SoylentNews
When admitting to an error isn't seen as a failure, improvement easy to achieve:
To improve security, the cybersecurity industry needs to follow the aviation industry's shift from a blame culture to a "just" culture, according to director of the Information Systems Audit and Control Association Serge Christiaans.
Speaking at Singapore's Smart Cybersecurity Summit this week, Christiaans explained that until around 1990, the number of fatal commercial jet accidents was growing alongside a steady increase of commercial flights. But around the turn of the decade, the number of flights continued to rise while the number of fatalities began to drop.
[...] While acknowledging that improved technology, more mature processes and improved leadership all helped to improve aviation safety, the former pilot and field CISO at tech consultancy Sopra Steria said the biggest improvements came from a change to a "just culture" that accepts people will make mistakes and by doing so makes it more likely errors will be reported.
In a just culture, errors are viewed as learning opportunities instead of moral failing, creating transparency and enabling constant improvement.
[...] Christiaans said he is yet to come across a company that had implemented open reporting without punishment in cybersecurity.
He attributed this to the industry working from the top down. The people at the top worked hard to get to leadership roles and become resistant to change. Shifting culture therefore needs to start with new recruits.
[...] Furthermore, not all of the aviation industry has been a beacon of transparent culture. For example, whistleblowers have alleged that culture at Boeing emphasized profit over safety, ultimately leading to engineering decisions that caused the crash of two 737 MAX airplanes.
[...] But Christiaan's analysis may be true at least when it comes to pilots and airlines, especially when culture is changed with small steps.
"So you plant the seeds, some airlines adapt, some don't," said Christiaans. "The ones who adapt, succeed."
Read more of this story at SoylentNews.
18:53
Experts warn of an emerging Python-based credential harvester named Legion Security Affairs
Legion is an emerging Python-based credential harvester and hacking tool that allows operators to break into various online services.
Cado Labs researchers recently discovered a new Python-based credential harvester and hacking tool, named Legion, which was sold via Telegram. At this time, the sample analyzed by Cado Labs has a low detection rate of 0 on VirusTotal.
Legion is a modular tool that can be used by crooks to hack into various online services. The researchers reported that the tool has modules to support the following functionalities:
- enumerating vulnerable SMTP servers,
- conducting Remote Code Execution (RCE),
- exploiting vulnerable versions of Apache,
- brute-forcing cPanel and WebHost Manager (WHM) accounts,
- interacting with Shodans API to retrieve a target list (providing you supply an API key) and
- additional utilities, many of which involve abusing AWS services
Legion is similar to a tool detailed in December by Lacework researchers, which was named AndroxGh0st.
The sample analyzed by Cado Labs is a Python3 script of 21015 lines, it includes configurations for integrating with services such as Twilio and Shodan.
The malware can exfiltrate collected data via Telegram chat using the Telegram Bot API.
The developer behind the tool operates a YouTube channel named Forza Tools, which included a series of tutorial videos for using the Legion script. The experts believe that the tool is widely distributed and is likely paid malware.
Leg...
18:01
Vice Society Ransomware Using Stealthy PowerShell Tool for Data Exfiltration The Hacker News
Threat actors associated with the Vice Society ransomware gang have been observed using a bespoke PowerShell-based tool to fly under the radar and automate the process of exfiltrating data from compromised networks. "Threat actors (TAs) using built-in data exfiltration methods like [living off the land binaries and scripts] negate the need to bring in external tools that might be flagged by
18:00
Interlaken Want to Connect All the Chips Hackaday

One of the problems with designing things on a chip is finding a good way to talk to the outside world. You may not design chips yourself, but you care because you want to connect your circuits including other chips to the chips in question. While I2C and SPI are common solutions, todays circuits are looking for more bandwidth and higher speeds, and thats where Interlaken comes in. [Comcores] has an interesting post on the technology that blends the best of SPI 4.2 and XAUI.
The interface is serial, as you might expect. It can provide both high-bandwidth and low-latency multi-channel communications. Interlaken was developed by Cisco and Cortina Systems in 2006 and has since been adopted by other industry-leading companies. Its latest generation supports speeds as high as 1.2 Tbps.
Interlaken can support up to 65,535 data streams and features error correction. The interface also handles retransmissions, so the users dont have to. Interlaken uses a meta-frame concept. For each lane, a set of words associated with the meta-frame are sent along with the payload of control and data words. These include alignment information, clock compensation, status information, and error-checking data.
Unless you develop chips or build FPGAs, you probably wont worry too much about the internal details, at least not yet. But the time may be near when...
17:49
malloc leak detection available in -current OpenBSD Journal
OpenBSD -current just grew a new tool for developers working on OpenBSD to detect unsafe behaviors in their code. OpenBSD lets you more easily track memory allocations and whether allocations are properly freed after use.
In a message to tech@, Otto Moerbeek
(otto@) announced
the new functionality:
Subject: malloc leak detection available in -current From: Otto Moerbeek <otto () drijf ! net> Date: 2023-04-17 6:43:19 Hi, OpenBSD current now has built-in malloc leak detection. Make sure you run current and have debug symbols (OpenBSD base libraries have debug symbols, compile your own program with -g).
17:32
IRC Proceedings: Sunday, April 16, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-160423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-160423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-160423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-160423.gmi
Over HTTP:
|
... |
17:15
17:00
The Electron Is So Round That Its Ruling Out Potential New Particles Terra Forming Terra
9 Researched Benefits of Intermittent Fasting Terra Forming Terra
This item now shows us how mature all this has become and we are all traing to fast for our general health. All good.
Cases And Cases Of Bud Light Stacking Up In Bars & Stores Across America Terra Forming Terra
Somewhere, someone must actually believe that Woke culture has a voting majority somehow that supports them.
Natural treatment could make you almost invisible to mosquito bites Terra Forming Terra

This is both promising and wonderfully safe. Celluose in pure form is a natural blocker and easily discourages a mosquito and that may well be what we need to be doing.
So yes, being able to spray this on your hands and the back of your neck would be welcome. I swear that the smeely stuff we use actually attracts them, though that cannot be true.
16:59
New Zaraza Bot Credential-Stealer Sold on Telegram Targeting 38 Web Browsers The Hacker News
A novel credential-stealing malware called Zaraza bot is being offered for sale on Telegram while also using the popular messaging service as a command-and-control (C2). "Zaraza bot targets a large number of web browsers and is being actively distributed on a Russian Telegram hacker channel popular with threat actors," cybersecurity company Uptycs said in a report published last week. "Once the
16:55
Links 16/04/2023: Trisquel GNU/Linux 11.0 Reviewed and World IP (International Propaganda) Day 2023 Approaching Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
9to5Linux ...
-
16:42
Re: CVE-2023-2002: Linux Bluetooth: Unauthorized management command execution Open Source Security
Posted by Jakub Wilk on Apr 16
* Steffen Nurpmeso <steffen () sdaoden eu>, 2023-04-16 22:57:I'm pretty sure they do. But isatty(3) is implemented using the TCGETS
ioctl, so that doesn't help.
16:34
NovoNutrients Wants to Turn CO2 Into Protein SoylentNews
But first it'll have to prove its business model:
We've spent the last century and a half pumping carbon dioxide into the atmosphere, and it's clear that we'll have to spend the coming decades removing a significant fraction of that.
But then what do we do with it all? Some people are proposing pumping it underground. Others think we can make things from it, including liquid fuels and concrete. Problem is, those are pretty low-margin opportunities today. One startup thinks the answer is to turn carbon dioxide into protein.
[...] NovoNutrients relies on bacteria to do the dirty work. The company has surveyed the scientific literature to find species that can use carbon dioxide in their metabolic pathways, allowing them to use the waste gas as energy. Its scientists have also discovered strains not otherwise known to science.
"Our technology is about how do you industrialize this naturally occurring metabolism?" CEO David Tze told TechCrunch+.
[...] The company's approach has several advantages over other methods of using carbon dioxide. For one thing, it does not require large amounts of land or water, which are both in short supply in many parts of the world. It also does not require the use of fossil fuels, which are a major contributor to climate change.
NovoNutrients is not the only company working on using carbon dioxide to create protein. Other companies, such as Calysta and Deep Branch Biotechnology, are also developing similar technologies. However, NovoNutrients believes that its approach is unique because it uses bacteria to create protein products that are high in quality and can be sold at a competitive price.
The company's pilot-scale plant will be located in California and is expected to be operational by the end of 2021 [sic]. If successful, NovoNutrients plans to build a larger commercial-scale plant that could produce up to 1,000 metric tons of protein per year.
Read more of this story at SoylentNews.
15:00
Circumvent Facial Recognition with Yarn Hackaday

Knitwear can protect you from a winter chill, but what if it could keep you safe from the prying eyes of Big Brother as well? [Ottilia Westerlund] decided to put her knitting skills to the test for this anti-surveillance sweater.
[Westerlund] explains that yarn is a programable material containing FOR loops and other similar programming concepts transmitted as knitting patterns. In the video (after the break) she also explores the history of knitting in espionage using steganography embedded in socks and other knitwear to pass intelligence in unobtrusive ways. This lead to the restriction of shipping handmade knit goods in WWII by the UK government.
Back in the modern day, [Westerlund] took the Hyperface pattern developed by the Adam Harvey and turned it into a knitting pattern. Designed to circumvent detection by Viola-Jones based facial detection systems, the pattern presents a computer vision system with a number of faces to distract it from covered human faces in an image. While the knitted jumper (sweater for us American...
14:00
Economic uncertainty drives upskilling as a key strategy for organizations Help Net Security
With the economy experiencing instability and decline, organizations rely on their technology experts to maintain their innovative edge and generate business value. Despite being instructed to reduce expenses by 65% of the technology team leaders, 72% still intend to boost their investment in technology proficiency development by 2023, according to Pluralsight. As improving the skills of current employees is less expensive than recruiting new ones, 97% of directors in charge of learning and development and More
The post Economic uncertainty drives upskilling as a key strategy for organizations appeared first on Help Net Security.
14:00
Ubuntu 23.04 Desktop's New Installer Set To Ship Without OpenZFS Install Support Phoronix
It was just four years ago in Ubuntu 19.10 that Ubuntu's desktop installer added OpenZFS support for carrying out root file-system installations atop this ZFS file-system. Since then the Canonical/Ubuntu interest has waned. Ahead of the Ubuntu 23.04 release this week, I tried out the Ubuntu Lunar Lobster daily snapshot this weekend to find the OpenZFS install support with Ubuntu's new desktop installer to still be missing...
13:49
Colorado is the First US State to Pass a Right-to-repair Law for Farmers SoylentNews
John Deere warns about the "unintended consequences" stemming from the new legislation:
The right to repair movement just got its first major win in Colorado as the state will likely become the first to establish a law designed to protect the farmers' right to repair their own equipment. Big manufacturing companies are not happy, but the law is expected to be signed soon.
Starting January 1, 2024, manufacturers of agricultural equipment will have to provide Colorado farmers everything they need to repair machinery by themselves. Denver legislators recently approved the first-ever proposal turning right-to-repair principles into law with a majority vote (44 to 16), after the same law was approved by the Senate last month.
The bill is now on the governor's desk, where Jared Polis is expected to approve the bi-partisan proposal within 10 days. The Consumer Right To Repair Agricultural Equipment requires manufacturers to provide parts, embedded software, firmware, tools, documentation, repair manuals and other resources to independent repair providers and owners of farming machinery, giving them the ability to fix broken stuff without needing to go through official resellers and repair services.
The bill folds agricultural equipment into the existing consumer right-to-repair statutes of Colorado, which states that a manufacturer's failure to comply is a "deceptive trade practice." Manufacturers are not obliged to "divulge any trade secrets" to independent repair services and owners, the statutes say. The bill was later amended to clarify that repair providers and owners are not authorized to make modifications to equipment that permanently deactivate safety measures or modify carbon emissions.
Read more of this story at SoylentNews.
13:30
AI tools like ChatGPT expected to fuel BEC attacks Help Net Security
Across all BEC attacks seen over the past year, 57% relied on language as the main attack vector to get them in front of unsuspecting employees, according to Armorblox. In other trends to watch, vendor compromise and fraud are rising as a new attack vector and graymail is wasting 27 hours of time for security teams each week. Attacks target technology organizations The report is based on data gathered across more than 58,000 customer tenants, More
The post AI tools like ChatGPT expected to fuel BEC attacks appeared first on Help Net Security.
13:00
AI verification systems give businesses an edge over scammers Help Net Security
Fraudsters are underestimating the power of AI to detect fake IDs, according to a new report from Ondato. Based on an analysis of millions of ID verifications carried out for its customers in 2022, Ondato found that ID cards were used in 52% of fraudulent verification attempts far ahead of driving licences (29%) and passports (18%). ID cards used in over half of fraudulent verification attempts According to Ondato, fraudsters most likely underestimate ID More
The post AI verification systems give businesses an edge over scammers appeared first on Help Net Security.
12:00
Using STEP and STL Files in FreeCAD Hackaday

If youve tried FreeCAD, you know that it has a daunting number of workbenches and options. [MangoJelly] has a large number of video tutorials on FreeCAD, and the latest one, below, covers working with STEP and STL with the tool.
If youve ever wondered why designers like to work with STEP files and not STL, this video answers that question immediately. A part brought in from a STEP file is closer to the original CAD object. It doesnt have all the operations that make the part up, but it does have proper faces that you can work with like a normal part. The same part imported from STL, however, is one single mesh.
Of course, in this case, it doesnt matter much because he has the original file, the STEP, and the STL. However, in real life, you may have an STL file and nothing else. The video shows how you can convert such an object into a proper FreeCAD part.
We liked that the example part isnt a boxy design. It is full of curves, holes, and slots. Sometimes working with a very simple part hides issues that you run into when you try to use a technique in real life. In fact, after working with the basic object, he downloads a power supply cover and then punches a new hole in it.
If you want to learn more about FreeCAD, you can spend a lot of time on his channel, which has a dizzying array of tutorials. There are many...
11:58
[Meme] Recruiting to Steal Techrights
When you join a company run by a liar, fraud, and cheat (based on false credentials)
Summary: GNU/Linux engineers got robbed by Sirius Open Source Limited; the criminal who oversaw this fraud is now looking for more people to rob while cops drag their heels
11:54
Kernel prepatch 6.3-rc7 LWN.net
The 6.3-rc7
kernel prepatch is out for testing. "Let's hope we have just one
more calm week, and we'll have had a nice uneventful release cycle.
Knock wood
".
11:46
GNU/Linux Engineers Got Robbed by Sirius Open Source Limited schestowitz.com
Video
download link | md5sum
c4ca62ca5c8ebc2a7974b42f3ff4d884
Why the Pension Story is Relevant to Us
Creative Commons Attribution-No Derivative Works 4.0
Summary: The crimes of Sirius Open Source will be the subject of many future posts and today we explain why this is a subject of relevance to Techrights
THE pension situation where I worked for nearly 12 years impacts a lot of people and it helps reveal rampant corruption in the pension industry. Ive been thinking about this deeply for days, also in light of several news items about France and about the US pension promises being unsustainable. Are people meant to ever retire? Are people living to work? Or they do work to eventually live? (Hours after work or after they leave work altogether)
We have a lot more information in the pipeline, albeit were limited by what we can say at any one time. The reasons are explained in the video above as well.
Why did the accounting people allow pension fraud to carry on for so long? Could they not refrain from collaborating? In fact, who does the accounting anyway? There might be an even more sinister scandal therein and were investigating the matter.
Another question: can one actually withdraw a pension early? The state would say thats possible, but companies lie their way or simply hide when the subject comes up (e.g. bank details specified or time for cheque to be picked up with paperwork signed). The outcome of any hypothetical investigations into this turn out to be ugly. The pensions seem like a black hole. You can put money in, or think you put money in, but you can never take anything out.
Our approach here has been multifaceted; the goals and methods are many. Since we deal with an actual criminal matter, we cannot be ignored by pension providers, police etc. They cannot simply turn a blind eye. Everyone agrees that pension providers are very sensitive about their brand/reputation (more so...
11:20
Standing Up for Defrauded Members of Staff (GNU/Linux Engineers) in the Age of Pension Scams Techrights
Video
download link | md5sum
c4ca62ca5c8ebc2a7974b42f3ff4d884
Why the Pension Story is Relevant to Us
Creative Commons Attribution-No Derivative Works 4.0
Summary: The crimes of Sirius Open Source will be the subject of many future posts and today we explain why this is a subject of relevance to Techrights
THE pension situation where I worked for nearly 12 years impacts a lot of people and it helps reveal rampant corruption in the pension industry. Ive been thinking about this deeply for days, also in light of several news items about France and about the US pension promises being unsustainable. Are people meant to ever retire? Are people living to work? Or they do work to eventually live? (Hours after work or after they leave work altogether)
Why did the accounting people allow pension fraud to carry on for so long?We have a lot more information in the pipeline, albeit were limited by what we can say at any one time. The reasons are explained in the video above as well.
Why did the accounting people allow pension fraud to carry on for so long? Could they not refrain from collaborating? In fact, who does the accounting anyway? There might be an even more sinister scandal therein and were investigating the matter.
Another question: can one actually withdraw a pension early? The state would say thats possible, but companies lie their way or simply hide when the subject comes up (e.g. bank details specified or time for cheque to be picked up with paperwork signed). The outcome of any hypothetical investigations into this turn out to be ugly. The pensions seem like a black hole. You can put money in, or think you put money in, but you can never take anything out.
Everyone agrees that pension providers are very sensitive about their brand/reputation (more so than banks).Our approach here has been mult...
11:14
10 Best Zippyshare Alternatives Best File Sharing Services HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
Zippyshare is no longer available after the service announced its shutdown on March 30th, 2023.
This is a post from HackRead.com Read the original post: 10 Best Zippyshare Alternatives Best File Sharing Services
11:07
Human Rights Groups Raise Alarm Over UN Cybercrime Treaty SoylentNews
Let's go through all the proposed problematic powers, starting with surveillance and censorship:
Special report United Nations negotiators convened this week in Vienna, Austria, to formulate a draft cybercrime treaty, and civil society groups are worried.
"We are here for the fifth session on the negotiations of this new treaty on cybercrime, which will have the potential to drastically redraft criminal law all around the world," said Thomas Lohnninger, executive director of Austria-based tech policy group Epicenter.works, in a media briefing on Thursday about the treaty negotiations.
"It represents a tectonic shift because of its global nature when it comes to the cross border access to our personal information."
The UN Cybercrime Treaty, to the extent it gets adopted, is expected to define global norms for lawful surveillance and legal processes available to investigate and prosecute cybercriminals. And what has emerged so far contemplates [PDF] more than 30 new cybercrime offenses, with few concessions to free speech or human rights.
[...] Katitza Rodriguez, policy director for global privacy at the Electronic Frontier Foundation, explained that current cross-border cybercrime cooperation comes from the Budapest Convention, negotiated in 2001, by member states at the Council of Europe.
Russia, however, Rodriguez said, has objected to the convention for infringing state sovereignty by allowing other nations to investigate cybercrimes in its jurisdiction. So in 2017, Russia proposed negotiating a new treaty, and in 2019 the UN adopted a resolution to do so, backed by Russia, Cambodia, Belarus, China, Iran, Myanmar, Nicaragua, Syria and Venezuela.
The US and members of the European Union opposed the proposal citing concerns about lack of human rights protections. Nonetheless, Rodriguez said, Russia pushed its proposal forward and the UN opened negotiations just days after Russia invaded Ukraine.
Read more of this story at SoylentNews.
10:14
Microsoft Bing Hides News Regarding Microsoft Stabber Joseph Cantrell Techrights
Reprinted with permission from Ryan
Microsoft has removed all references to Joseph Cantrell from Bing News, which has made its way into DuckDuckGo as well.
Google News still returns results for the drug addled Nazi that Microsoft hired and now tries to hide. No doubt, having him stab another employee was very embarrassing.
This is just one example of how Microsoft can run damage control. As his case winds its way through the court system, people will increasingly wonder what kind of company hires people who self-admit to extensive drug usage and Nazi ideology, and then further admit that nobody on their team of 4, which costs the company over a million bucks, can figure out bugs in Azure, and have to resort to posting questions on Stack Exchange.
The drug diary, which I also previously reported on, also shows that Cantrells behavior created an extremely toxic and harassing workplace. On numerous occasions, Cantrell says that in company meetings, he said Indians shouldnt be allowed to work at Microsoft and that one person in particular should have her green card revoked for being Indian, admitted to soliciting prostitutes and getting STDs from them, and blogged extensively that tech companies who have Indian CEOs dont have good products anymore. I wonder if Bill Gates even uses Windows or if that Indian guy at Google even uses Google.
Almost all of the worst of his admissions in the diary were on his public Web site before the hiring.
But if Microsoft sets up a simple key word ban, nobody following Bing or DuckDuckGo News will read about its dirty laundry.
10:10
DistroWatch Weekly, Issue 1015 DistroWatch.com: News
This week in DistroWatch Weekly: Review: Manjaro Linux 22.0, Trisquel GNU/Linux 11.0News: Arch Linux powering new PINE64 tablets, KDE Connect getting an overhaul, Ubuntu introduces live patching for HWE kernelsQuestions and answers: Gaining filesystem compression with ext4Released last week: OpenBSD 7.3, FreeBSD 13.2, 4MLinux 42.0, TrueNAS 22.12.2 "SCALE"Torrent....
10:04
Booting modern Intel CPUs Matthew Garrett
CPUs can't do anything without being told what to do, which
leaves the obvious problem of how do you tell a CPU to do something
in the first place. On many CPUs this is handled in the form of a
reset
vector - an address the CPU is hardcoded to start reading
instructions from when power is applied. The address the reset
vector points to will typically be some form of ROM or flash that
can be read by the CPU even if no other hardware has been
configured yet. This allows the system vendor to ship code that
will be executed immediately after poweron, configuring the rest of
the hardware and eventually getting the system into a state where
it can run user-supplied code.
The specific nature of the reset vector on x86 systems has varied
over time, but it's effectively always been 16 bytes below the top
of the address space - so, 0xffff0 on the 20-bit 8086, 0xfffff0 on
the 24-bit 80286, and 0xfffffff0 on the 32-bit 80386. Convention on
x86 systems is to have RAM starting at address 0, so the top of
address space could be used to house the reset vector with as low a
probability of conflicting with RAM as possible.
The most notable thing about x86 here, though, is that when it
starts running code from the reset vector, it's still in real mode.
x86 real mode is a holdover from a much earlier era of computing.
Rather than addresses being absolute (ie, if you refer to a 32-bit
address, you store the entire address in a 32-bit or larger
register), they are 16-bit offsets that are added to the value
stored in a "segment register". Different segment registers existed
for code, data, and stack, so a 16-bit address could refer to
different actual addresses depending on how it was being
interpreted - jumping to a 16 bit address would result in that
address being added to the code segment register, while reading
from a 16 bit address would result in that address being added to
the data segment register, and so on. This is all in order to
retain compatibility with older chips, to the extent that even
64-bit x86 starts in real mode with segments and everything (and,
also, still starts executing at 0xfffffff0 rather than
0xfffffffffffffff0 - 64-bit mode doesn't support real mode, so
there's no way to express a 64-bit physical address using the
segment registers, so we still start just below 4GB even though we
have massively more address space available).
Anyway. Everyone knows all this. For modern UEFI systems, the
firmware that's launched from the reset vector then reprograms the
CPU into a sensible mode (ie, one without all this segmentation
bullshit), does things like configure the memory controller so you
can actually access RAM (a process which involves using CPU cache
as RAM, because programming a memory controller is sufficiently
hard that you need to store more state than you can fit in
registers alone, which means you need RAM, but you don't have RAM
until the memory cont...
10:00
HPR3836: Using 'zoxide', an alternative to 'cd' Hacker Public Radio
hr.thin { border: 0; height: 0; border-top: 1px solid rgba(0, 0, 0, 0.1); border-bottom: 1px solid rgba(255, 255, 255, 0.3); } Overview I like the idea that there are tools available to enhance the 'cd' command, remembering places you have been in the file system and taking you there easily. I use 'pushd' and 'popd' for moving in and out of directories from a place I want to do most of my work, but something more powerful than these or cd have always seemed desirable. I was using 'autojump' for a while last year, but didnt really get on with it. This was mainly because there was no way of excluding certain directories which had been visited from its list. Recently I heard of 'zoxide', which I have been trying and really like. zoxide What is it? From the GitHub page: zoxide is a smarter cd command, inspired by z1 and autojump. It remembers which directories you use most frequently, so you can jump to them in just a few keystrokes. zoxide works on all major shells. In its man page its billed as A faster way to navigate your filesystem. Its written in Rust so is very fast. What does it do? It offers the functionality of the Linux/Unix 'cd' command. It collects the directories you have visited into a database and gives them a ranking relating to the number of times they have been visited. It applies aging rules and removes these when the ranking drops below one. It uses frecency to do this - a combination of frequency and recency. (See the Wikipedia page explaining this word) It performs algorithmic matching on the directory you specify and takes you to the highest ranking best match. It can resolve conflicts between matching directories or can allow selection through an interactive interface. It can interface to fzf, a general-purpose command-line fuzzy finder. It knows where it is (in the Bash shell) by calling a function out of the PROMPT_COMMAND variable. This can be used to execute one or more commands before displaying the prompt for a new command. This is a common way to hook monitoring commands into a Bash session. Where can you get it? I installed it from the Debian Testing repo, but I got 'zoxide from the GitHub page seems the best option if you want the latest version. There is an installation script on the GitHub page and its possible to download it with curl and pipe it to Bash. Im never comfortable doing this, but thats your choice. I also installed fzf from the Debian Testing repo, though Im still learning what this can do, since its very rich in features! How do you set it up? This process is shell-specific. I run Bash so I have added it to my ~/.bashrc and the command there is: eval "$(zoxide init bash)" What this does is generate a number of Bash functions and aliases and some commands which are fed into eval and executed in the current context. Function z is created which gives a way of invo
09:00
Hackaday Links: April 16, 2023 Hackaday

The dystopian future youve been expecting is here now, at least if you live in New York City, which unveiled a trio of technology solutions to the citys crime woes this week. Surprisingly, the least terrifying one is DigiDog, which seems to be more or less an off-the-shelf Spot robot from Boston Dynamics. DigiDogs job is to de-escalate hostage negotiation situations, and unarmed though it may be, we suspect that the mission will fail spectacularly if either the hostage or hostage-taker has seen Black Mirror. Also likely to terrify the public is the totally-not-a-Dalek-looking K5 Autonomous Security Robot, which is apparently already wandering around Times Square using AI and other buzzwords to snitch on people. And finally, theres StarChase, which is based on an AR-15 lower receiver and shoots GPS trackers that stick to cars so they can be tracked remotely. Were not sure about that last one either; besides the fact that it looks like a grenade launcher, the GPS tracker isnt exactly covert. Plus its only attached with adhesive, so it seems easy enough to pop it off the target vehicle and throw it in a sewer, or even attach it to a...
08:54
Linux 6.3-rc7 Released - Hoping For A Calm Week Ahead Phoronix
Linux 6.3-rc7 was just released and if the next week remains calm, it would mean that Linux 6.3 is shipping next weekend...
08:22
The 8086 Processor's Microcode Pipeline From Die Analysis SoylentNews
https://www.righto.com/2023/01/the-8086-processors-microcode-pipeline.html
Intel introduced the 8086 microprocessor in 1978, and its influence still remains through the popular x86 architecture. The 8086 was a fairly complex microprocessor for its time, implementing instructions in microcode with pipelining to improve performance. This blog post explains the microcode operations for a particular instruction, "ADD immediate". As the 8086 documentation will tell you, this instruction takes four clock cycles to execute. But looking internally shows seven clock cycles of activity. How does the 8086 fit seven cycles of computation into four cycles? As I will show, the trick is pipelining.
[...] The alternative is microcode: instead of building the control circuitry from complex logic gates, the control logic is largely replaced with code. To execute a machine instruction, the computer internally executes several simpler micro-instructions, specified by the microcode. In other words, microcode forms another layer between the machine instructions and the hardware. The main advantage of microcode is that it turns the processor's control logic into a programming task instead of a difficult logic design task.
Read more of this story at SoylentNews.
08:18
Five fulcrums for fundamental public sector reform pipka.org
In government we often speak about policy levers, but in the real world, a lever without a fulcrum is just a plank of wood. Levers are needed to lift a load, but without a fulcrum, you cant move it very far. Fulcrums are needed to dramatically increase the impact of a lever without having to increase the effort/resource. Basically, levers without fulcrums are pretty ineffective.
Sometimes even ambitious change agendas can unintentionally adopt a levers-without-fulcrums pattern. For instance, setting up a team to innovate without normalising a culture of innovation across the organisation. Hiring or training extraordinary talent and then not letting them make any decisions or bring ideas to the table. Training staff on public engagement without creating an appetite for public input. Every lever needs a fulcrum.
Once you look for it, you can see this pattern everywhere.
So below are five of my favourite fulcrums to complement the
usual policy levers you have today  These
are all tried and tested in various governments. These fulcrums
are: teaching public sector craft to all who work in (and with) the
public sector, a responsible implementation mindset, servant
leadership, structuring around outcomes, and finally the critical
fulcrum of raised expectations.
These
are all tried and tested in various governments. These fulcrums
are: teaching public sector craft to all who work in (and with) the
public sector, a responsible implementation mindset, servant
leadership, structuring around outcomes, and finally the critical
fulcrum of raised expectations.
Fulcrum 1: Teaching public service craft to all involved
All public servants used to be trained in public service craft. At some point, about 30 years ago, there was a change that mechanised the public sector (driven by New Public Management) and started bringing people in for a particular skillset (developer, accountant, lawyer, project manager, etc) with limited training on the context in which theyd be applying those skills. These days, generally only policy people are expected to be trained in the ways of government, and even then, many public policy courses teach only the mechanics of public sector without the responsibilities or clear delineation of powers and accountabilities.
We have seen the results of this in shocking testimony throughout the Robodebt Royal Commission, as senior public servants demonstrated a complete misunderstanding (and sometimes abdication) of their responsibility to be trusted stewards acting both lawfully and in the best public interest, instead believing their job to just advise, and then loyally (blindly?) implement the decisions of the government of the day, whatever the cost, conflict, impact or legality. This culture issue is well articulated in the recent submission to the Robodebt Royal Commission...
07:02
Re: CVE-2023-2002: Linux Bluetooth: Unauthorized management command execution Open Source Security
Posted by Steffen Nurpmeso on Apr 16
Ruihan Li wrote in<w7boj4fg4x2o2bjz7a7zkjk4bgxqvqyuxycdqqw2dl3bhanh6a@h4jtbccffxgv>:
...
|be privileged, such as a setuid program. Moreover, if the socket is used as
|stdout or stderr, an ioctl call is made to obtain tty parameters, which \
|can be
|verified through the strace command.
|```
|# strace -e trace=ioctl sudo > /dev/null
|ioctl(3, TIOCGPGRP, [30305]) = 0
|ioctl(2, TIOCGWINSZ, {ws_row=45, ws_col=190,...
06:02
Experts found the first LockBit encryptor that targets macOS systems Security Affairs
Researchers warn that the LockBit ransomware gang has developed encryptors to target macOS devices.
The LockBit group is the first ransomware gang of all time that has created encryptors to target macOS systems, MalwareHunterTeam team warn.
MalwareHunterTeam researchers discovered the LockBit encryptors in a ZIP archive uploaded to VirusTotal.
The discovery is disconcerting and demonstrates the effort of the group to expand its operation targeting also Apple systems.
BleepingComputer confirmed that the zip archive contained previously unknown encryptors for macOS, ARM, FreeBSD, MIPS, and SPARC architectures.
The experts pointed out that the archive has been bundled as March 20, 2023, it also includes builds for PowerPC CPUs, which are used in older macOS systems.
One of the encryptors developed by Lockbit, named locker_Apple_M1_64, can encrypt files of Mac systems running on the Apple silicon M1.
05:09
OpenAssistant Released cryptogon.com
That didnt take long. I thought it would take at least several months for them to attain something GPT3.5-like. Nope. Via: Yannic Kilcher:
04:33
DMCA Takedowns Target Torrent Release of Dark and Darker Playtest TorrentFreak
 Upcoming first-person shooter game Dark and Darker
is scheduled to launch later this year, but even at this early
stage its causing controversy.
Upcoming first-person shooter game Dark and Darker
is scheduled to launch later this year, but even at this early
stage its causing controversy.
Last month, police in South Korea raided the offices of local game studio Ironmace. According to reports, the developers allegedly stole assets from their former employer, game publisher Nexon, which is allegedly working on a similar project too.
A few days later, Nexon sent a DMCA takedown notice to Valve, asking it to remove the Dark and Darker project from Steam. The detailed takedown notices accused Ironmace of copyright infringement and stealing trade secrets.
This letter is to inform you of Ironmaces misconduct, constituting misappropriation of Nexons trade secrets and copyright infringement and to request that Valve take down all versions of Dark and Darker from Steam, the company wrote (pdf).

Steam swiftly complied, but the enforcement action and follow-up legal pressure didnt stop Dark and Darker development. Ironmace refuted the accusations in detail and continued to work on the game.
This weekend, Ironmace was ready to share the latest Alpha release with its fans. Without Steam access, Ironmace had to choose a different distribution method and after some internal deliberation, opted to go old school with a BitTorrent release.
Unfortunately, due to the complexities of our situation, especially across international lines, it is taking time to resolve the Steam situation. In order for us to keep our promise to our fans weve had to go old school this time, Ironmace wrote.
The developers typically share these types...
03:29
OpenBSD 7.3 has been released.
Who invented vector clocks?, by Lindsey Kuper.
Two algorithms for randomly generating aperiodic tilings, nice exposition by Simon Tatham.
My4TH, a homebuilt CPU-less computer with a 1-bit NOR gate ALU, running FORTH. By Dennis Kuschel.
How to Crash SM64 Using a Pendulum (YouTube), explained by pannenkoek2012.
Build faster with Buck2, Metas open source build system. Written in Rust, rules are now implemented fully in Starlark.
Knit: making a better Make, with some good ideas.
SIMD-ized faster parse of IPv4 addresses, by Wojciech Mua.
The microcode and hardware in the 8086 processor that perform string operations, by Ken Shirriff.
Hell Never Ends On x86: The Hyperspace Story, Continued, Sort Of, by cathoderaydude. Office software running in EFI.
The time Bell Labs brought the Statue of Liberty under its roof (Literally)
PLATO Emoticons, revisited (2012). Uses overprinting.
03:29
A Computer Generated Swatting Service Is Causing Havoc Across America SoylentNews
Torswats uses synthesized voices to pressure law enforcement to specific locations:
"Hello, I just committed a crime and I want to confess," a panicked sounding man said in a call to a police department in February. "I've placed explosives inside a local school,' the man continued.
"You did what?!" the operator responded.
"I've placed explosives inside a local school," the man said again, before specifying Hempstead High School in Dubuque, Iowa, and providing its address. In response to the threat, the school went on lockdown, and police searched the school but found nothing, according to a local media report.
The bombs weren't real. But, crucially, neither was the man's voice. The panicked man's lines sound artificially generated, according to recordings of the swatting calls reviewed by Motherboard. It is unclear how exactly the caller generated the voice, be that some form of artificial intelligence tool or another speech synthesis program. The result, though, is a voice that sounds very consistent across multiple calls.
[...] Known as "Torswats" on the messaging app Telegram, the swatter has been calling in bomb and mass shooting threats against highschools and other locations across the country. Torswat's connection to these wide ranging swatting incidents has not been previously reported. The further automation of swatting techniques threatens to make an already dangerous harassment technique more prevalent.
[...] Torswats carries out these threatening calls as part of a paid service they offer. For $75, Torswats says they will close down a school. For $50, Torswats says customers can buy "extreme swattings," in which authorities will handcuff the victim and search the house. Torswats says they offer discounts to returning customers, and can negotiate prices for "famous people and targets such as Twitch streamers." Torswats says on their Telegram channel that they take payment in cryptocurrency.
Read more of this story at SoylentNews.
03:00
3D-Printable Foaming Nozzle Shows How They Work Hackaday

[Jack]s design for a 3D-printable foaming nozzle works by mixing air with a fluid like liquid soap or hand sanitizer. This mixture gets forced through what looks like layers of fine-mesh sieve and eventually out the end by squeezing the bottle. The nozzle has no moving parts but does have an interesting structure to make this possible.
01:22
How Music Hijacks Our Perception of Time Lifeboat News: The Blog
One evening, some 40 years ago, I got lost in time. I was at a performance of Schuberts String Quintet in C major. During the second movement I had the unnerving feeling that time was literally grinding to a halt. The sensation was powerful, visceral, overwhelming. It was a life-changing moment, or, as it felt at the time, a life-changing eon.
It has been my goal ever since to compose music that usurps the perceived flow of time and commandeers the sense of how time passes. Although Ive learned to manipulate subjective time, I still stand in awe of Schuberts unparalleled power. Nearly two centuries ago, the composer anticipated the neurological underpinnings of time perception that science has underscored in the past few decades.
The human brain, we have learned, adjusts and recalibrates temporal perception. Our ability to encode and decode sequential information, to integrate and segregate simultaneous signals, is fundamental to human survival. It allows us to find our place in, and navigate, our physical world. But music also demonstrates that time perception is inherently subjectiveand an integral part of our lives. For the time element in music is single, wrote Thomas Mann in his novel, The Magic Mountain. Into a section of mortal time music pours itself, thereby inexpressibly enhancing and ennobling what it fills.
01:00
Your Robotic Avatar Is Almost Ready IEEE Spectrum

Robots are not ready for the real world. Its still an achievement for autonomous robots to merely survive in the real world, which is a long way from any kind of useful generalized autonomy. Under some fairly specific constraints, autonomous robots are starting to find a few valuable niches in semistructured environments, like offices and hospitals and warehouses. But when it comes to the unstructured nature of disaster areas or human interaction, or really any situation that requires innovation and creativity, autonomous robots are often at a loss.
For the foreseeable future, this means that humans are still necessary. It doesnt mean that humans must be physically present, howeverjust that a human is in the loop somewhere. And this creates an opportunity.
In 2018, the XPrize Foundation announced a competition (sponsored by the Japanese airline ANA) to create an avatar system that can transport human presence to a remote location in real time, with the goal of developing robotic systems that could be used by humans to interact with the world anywhere with a decent Internet connection. The final event took place last November in Long Beach, Calif., where 17 teams from around the world competed for US $8 million in prize money.
 While avatar
systems are all able to move and interact with their environment,
the Avatar XPrize competition showcased a variety of different
hardware and software approaches to creating the most effective
system.XPrize
Foundation
While avatar
systems are all able to move and interact with their environment,
the Avatar XPrize competition showcased a variety of different
hardware and software approaches to creating the most effective
system.XPrize
Foundation
The competition showc...
00:49
Ubiquitous fake crowds Geeking with Greg
The Washington Post writes: "The Russian government has become far more successful at manipulating social media and search engine rankings than previously known, boosting ... [propaganda] with hundreds of thousands of fake online accounts ... detected ... only about 1% of the time."
Fake crowds can fake popularity. It's easy to manipulate trending, rankers, and recommender algorithms. All you have to do is create a thousand sockpuppet accounts and have them like and share all your stuff. Wisdom of the crowds is broken. This can be fixed, but first you have to see the problem clearly. Then you'll see that you can't just use the behavior from every account anymore for wisdom of the crowd algorithms. You have to use only reliable accounts and toss everything spammy or unknown.00:31
NCR was the victim of BlackCat/ALPHV ransomware gang Security Affairs
NCR was the victim of the BlackCat/ALPHV ransomware gang, the attack caused an outage on the companys Aloha PoS platform.
NCR Corporation, previously known as National Cash Register, is an American software, consulting and technology company providing several professional services and electronic products. It manufactures self-service kiosks, point-of-sale terminals, automated teller machines, check processing systems, and barcode scanners.
NCR is suffering an outage on its Aloha point of sale platform since Wednesday after it was hit by a ransomware attack conducted by the BlackCat/ALPHV ransomware group.
NCR Aloha POS is a comprehensive restaurant point-of-sale and management software, the company claims it is used by more cashiers and servers than any other POS in the industry.
The company has started notifying its customers, confirming the ransomware attack:
As a valued customer of NCR Corporation, we are reaching out with additional information about a single data center outage that is impacting a limited number of ancillary Aloha applications for a subset of our hospitality customers. On April 13, we confirmed that the outage was the result of a ransomware incident. reads the notice sent by the company to the customers via email.
NCR notified law enforcement and engaged third-party cybersecurity experts to investigate the incident and determine the scope of the attack.
The company pointed out that restaurants impacted are still able to serve their customers and that the incident only impacted a specific functionality.
Only specific functionality is impaired. There is no impact to payment applications or on-premises systems. continues the notice.
00:00
Timeframe: The Little Desk Calendar That Could Hackaday

Usually, the problem comes before the solution, but for [Stavros], the opposite happened. A 4.7 E-Ink screen with integrated battery management and ESP32 caught his eye, and he bought it and started thinking about what he wanted to do with it. The Timeframe (hackaday.io link as well) is a sleek desk calendar based around the integrated e-ink screen.
[Stavros] found the devices MicroPython support was a little lackluster, and often failed to draw. He found a Platform.io project that used an older but modified library for driving the e-ink display which worked quite well. However, the older library didnt support portrait orientation or other niceties. Rather than try and create something complex in C, he moved the complexity to a server environment he knew more about. With the help of CoPilot, he got some code that would wake up the ESP32 every half hour, download an image from a server, and then display it. A Python script uses a headless browser to visit Google Calendar, resize the window, take a screenshot, and then upload it.
The hardest part of the exercise was getting authentication with Google working reliably. A white sleek 3d printed case wraps the whole affair in an...
00:00
Lithium Battery Ripe for Disruption, Inventor Says IEEE Spectrum

The lithium-ion battery isnt going anywhere soon. Thats what M. Stanley Whittingham, the Nobel laureate who created the first rechargeable lithium-ion battery some 50 years ago, told attendees of the SLAC-Stanford Battery Research Center Launch Symposium on Thursday. The new organization aims to bridge gaps between organizations that research, manufacture, and deploy large-scale energy storage systems.
 M. Stanley
Whittingham
M. Stanley
Whittingham
Its going to be at least five-to-ten years before any
alternative technologies can compete on cost with lithium-ion
technology, Whittingham predicted.
Granted that this technology remains the incumbent for some time to come, Whittingham has concernsbig concernsabout how the world makes and uses these energy storage devices. Here are the big issues he worries about:
Manufacturing
Its ridiculous that manufacturing technologies havent changed in 30 years, Whittingham says. We need to reduce the 60 to 80 kilowatt hours) of electricity it takes to produce a one kWh battery, he says. Weve got to find new manufacturing technologies.
Recycling
Whittingham is also worried about recycling technologies. Hes encouraged that facilities to recycle lithium-ion batteries are being built around the world, but he adds, We need to make sure they are clean.
Mining
The supply chain for the minerals used in battery manufacturing in the first place also need work. We need regional supply chains, Whittingham says. And we need to look at clean mining with clean energy.
Heavy Metals
Given that some components of a lithium-ion batterys traditional chemistry are inherently toxic, they must be engineered out of the device as soon as possible, Whittingham says....
Sunday, 16 April
23:45
Links 16/04/2023: digiKam 8.0.0 and PGroonga 3.0.0 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Digital Restrictions (DRM)
- Monopolies
- Gemini* and Gopher
-
GNU/Linux
-
Linux Links Linux Around The World: USA Hawaii
We cover user groups that are running in the US state of Hawai...
-
23:30
AMD Squeezes In AMDGPU Fixes, FPO/FAMS Display Power Savings For Linux 6.4 Phoronix
While we are basically past the cut-off of new feature material to into DRM-Next that wants to be part of the upcoming Linux 6.4 merge window, this week AMD sent in a fixes-oriented set of AMDGPU/AMDKFD kernel driver updates that does include some minor feature updates...
23:23
Life on Mars: When and How | The Next Stage of Human Evolution and the Possible Demise of the Planet Lifeboat News: The Blog

Do you like our content? Please support PRO Robots on
Patreon.
https://www.patreon.com/PRORobots.
Your contributions will help us to create better content and to
improve our service for you and our PRO Robots community. Every
dollar counts and will help us keep working for you.
Thank you for your support!
 For
business inquiries: info.prorobots@gmail.com.
For
business inquiries: info.prorobots@gmail.com.
 Instagram: https://www.instagram.com/pro_robots.
Instagram: https://www.instagram.com/pro_robots.
Do you know why humanity still doesnt have colonies on the Moon or Mars? Because the big companies that mightve invested their money in building the said colonies are not sure when theyll get their investments back and start making a solid profit. Well, at least thats one of the reasons.
But the cheaper space flights will get and further the technologies that can help cost-efficiently settle on other planets will develop, the more countries, billionaires, tech giants, startups and institutions will get into the space race, whose finish line is right on the Red Planet. Why are they reluctant to do this? Are they afraid of future cataclysms? Do they know something we dont? Are they dreaming of claiming the title of pioneers? Or hoping to mine rare metals in the asteroid belt?
Watch this video to find out all about the whens and hows of life on Mars, as well as about its outcomes, including a new round of human evolution and the possible demise of the planet itself! Wheels up!
00:00 In this video.
01:00 Mars will try to kill you.
01:30 Mars is a totally hostile environment for human life.
02:25 With Mars, Earthlings have a better chance.
04:01 What have we already found on the Red Planet?
05:22 Ilon Musk.
06:04 Prolonged flight exposes people to the greatest horror.
07:45 development of new super-powered engines.
08:24 an inflatable heat shield for astronauts to land on the
planet.
09:12 Mars has no planetary magnetic field.
10:27 But the...
23:22
Vitamin B6: Increase NAD Without NR, NMN, or Niacin? Lifeboat News: The Blog
Join us on Patreon! https://www.patreon.com/MichaelLustgartenPhD
Discount Links:
NAD+ Quantification: https://www.jinfiniti.com/intracellular-nad-test/
Use Code: ConquerAging At Checkout.
Green Tea: https://www.ochaandco.com/?ref=conqueraging.
Oral Microbiome: https://www.bristlehealth.com/?ref=michaellustgarten.
Epigenetic Testing: Trudiagnostic.pxf.io/R55XDv.
Use Code: CONQUERAGING
At-Home Blood Testing: https://getquantify.io/mlustgarten.
23:00
Linux Fix On The Way For A Scheduler Imbalance Overflow Issue Phoronix
Sent in this morning for Linux 6.3 is a Linux CPU scheduler fix to deal with an imbalancing issue that's been present in the mainline kernel since a scheduler rework that landed back in late 2019...
23:00
The Tremendous VR and CG Systemsof the 1960s IEEE Spectrum

Ivan Sutherland has blazed a truly unique trail through computing over the past six decades. One of the most influential figures in the story of computing, he helped to open new pathways for others to explore and dramatically extend: interactive computer graphics, virtual reality, 3D computer graphics, and asynchronous systems, to name but a few.
The Computer History Museum recently made public its two-part oral history with Sutherland. These interviews present a wonderful opportunity to learn more about Sutherlands life in computing, in his own words. The interview transcripts can be downloaded here and here. And the two-part video of the interview is available here and here.
Bob Sproull, a lifelong colleague of Sutherland and himself a major figure in computing, served as instigator, interviewer, and editor for these oral histories, and he involved me, Marc Weber, and Jim Waldo in the effort. The Museum is making this oral history interview public during the 60th anniversary year of Sutherlands breakthrough in interactive computer graphics, the program Sketchpad, for which he earned his Ph.D. from MIT in 1963.
Ivan Sutherlands Unique Perspective
There is a phrase, popular in 17th and 18th century England, that occurs to me when thinking about Ivan Sutherland: A man of many parts. The phrase refers to an individual who had made serious contributions to a domain, while also possessing multiple, and often diverse, talents and pursuits. The description fits Sutherland well, although it also misses something important: There is a commonality in his many accomplishments, a shared wellspring for his many parts.
To get at this wellspring, start with geometry. From his youth, Sutherland possessed an unusually keen spatial, geometric intuition. In his mind and at his hands, he experienced an immediacy in perceiving how things fit and worked together. Perspective drawing involves a set of techniques to represent a three-dimensional scene on the two-dimensional plane of a sheet of paper or a stretch of canvas. These renderings can proceed in different ways, determined by the number of vanishing points employed. Together the vanishing points defi...
22:58
Security Affairs newsletter Round 415 by Pierluigi Paganini International edition Security Affairs
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are free for you in your email box.
22:44
Upgraded View of 'Fuzzy' Supermassive Black Hole is a Shade More Menacing SoylentNews
Using machine learning, a team of researchers has enhanced the first image ever taken of a distant black hole. Importantly, the newly updated image shows the full resolution of the telescope array for the very first time.
[...] The machine learning model has sharpened the otherwise blurry image of black hole M87, showcasing the utility of machine learning models in improving radio telescope images. The team's research was published today in the Astrophysical Journal Letters.
"Approximately four years after the first horizon-scale image of a black hole was unveiled by EHT in 2019, we have marked another milestone, producing an image that utilizes the full resolution of the array for the first time," said Dimitrios Psaltis, a researcher at Georgia Tech and a member of the EHT collaboration, in an Institute for Advanced Study release. "The new machine learning techniques that we have developed provide a golden opportunity for our collective work to understand black hole physics."
[...] But even using radio telescopes around the world doesn't give astronomers a complete view of the black hole; by incorporating a machine learning technique called PRIMO, the collaboration was able to improve the array's resolution. What appeared a bulbous, orange doughnut in a 2019 image has now taken on the delicate, thin circle of The One Ring.
Read more of this story at SoylentNews.
22:24
Microsoft Continues Building Out Its Linux Distribution With More Packages Phoronix
Microsoft has published its latest CBL-Mariner 2.0.20230407 Linux distribution images this weekend as their in-house open-source OS that is used for a variety of purposes, mostly around Azure infrastructure...
21:45
Remcos RAT campaign targets US accounting and tax return preparation firms Security Affairs
Microsoft warns of a new Remcos RAT campaign targeting US accounting and tax return preparation firms ahead of Tax Day.
Ahead of the U.S. Tax Day, Microsoft has observed a new Remcos RAT campaign targeting US accounting and tax return preparation firms. The phishing attacks began in February 2023, the IT giant reported.
Remcos is a legitimate remote monitoring and surveillance software developed by the company BreakingSecurity.
In 2021, CISA added Remcos to the list of top malware strains due to its use in mass phishing attacks using COVID-19 pandemic themes targeting businesses and individuals.
The recent campaign exclusively aims at organizations that deal with tax preparation, financial services, CPA and accounting firms, and professional service firms dealing in bookkeeping and tax.
Crooks use lures masquerading as tax documentation sent by a client. The message contains a link that points to a legitimate file hosting site where the cybercriminals have uploaded Windows shortcut (.LNK) files.
Upon clicking on the file, a malicious file is fetched from a domain under the control of the attacker which leads to the installation of the Remcos RAT.
What we have observed is that the link in the phishing email points to Amazon Web Services click tracking service at awstrack[.]me. The initial link then redirects the target to a ZIP file hosted on legitimate file-sharing service spaces[.]hightail[.]com. The ZIP file contains LNK files that act as Windows shortcuts to other files. reads the report published by Microsoft. The LNK files make web requests to actor-controlled domains...
21:26
CVE-2023-2002: Linux Bluetooth: Unauthorized management command execution Open Source Security
Posted by Ruihan Li on Apr 16
Hi,An insufficient permission check has been found in the Bluetooth subsystem of
the Linux kernel when handling ioctl system calls of HCI sockets. This causes
tasks without the proper CAP_NET_ADMIN capability can easily mark HCI sockets
as _trusted_. Trusted sockets are intended to enable the sending and receiving
of management commands and events, such as pairing or connecting with a new
device. As a result, unprivileged users can acquire a...
21:23
CVE-2023-24831: Apache IoTDB grafana-connector Login Bypass Vulnerability Open Source Security
Posted by Jialin Qiao on Apr 16
Severity: lowDescription:
Improper Authentication vulnerability in Apache Software Foundation Apache IoTDB.This issue affects Apache IoTDB
Grafana Connector: from 0.13.0 through 0.13.3.
Attackers could login without authorization. This is fixed in 0.13.4.
References:
https://iotdb.apache.org/
https://iotdb.apache.org
https://www.cve.org/CVERecord?id=CVE-2023-24831
21:22
The factory making bionic arms for Ukrainian soldiers BBC News Lifeboat News: The Blog

Thousands of people in Ukraine have lost their limbs in the war against Russia, according to World Health Organisation estimates.
The Ukrainian charity Superhumans and the UK-based company Open Bionics have partnered to create bionic arms for the wounded.
The BBC visited the factory in Bristol, England, responsible for creating the prosthetics.
Please subscribe here: http://bit.ly/1rbfUog.
#Ukraine #BionicArm #Bristol
21:21
CVE-2023-30771: Apache IoTDB Workbench: apache/iotdb-web-workbench: forge the JWTToken to access workbench Open Source Security
Posted by Jialin Qiao on Apr 16
Severity: lowDescription:
Incorrect Authorization vulnerability in Apache Software Foundation Apache IoTDB.This issue affects the
iotdb-web-workbench component on 0.13.3. iotdb-web-workbench is an optional component of IoTDB, providing a web console
of the database.
onwards.
References:
https://iotdb.apache.org
https://www.cve.org/CVERecord?id=CVE-2023-30771
21:00
Detecting Anti-Neutrinos from Distant Fission Reactors Using Pure Water at SNO+ Hackaday

Although neutrinos are exceedingly common, their near-massless configuration means that their presence is rather ephemeral. Despite billions of them radiating every second towards Earth from sources like our Sun, most of them zip through our bodies and this very planet without ever interacting with either. This property is also what makes studying these particles that are so fundamental to our understanding so complicated. Fortunately recently published results by researchers behind the SNO+ neutrino detector project shows that we may see a significant bump in our neutrino detection sensitivity.
20:46
FSF Slams Google Over Dropping JPEG-XL In Chrome Phoronix
Last October Google engineers decided they would deprecate JPEG-XL support in Chrome over some debated rationale for the move. Even amid the community uproar they went ahead to drop the JPEG-XL support. The Free Software Foundation has finally commented on the matter...
20:33
digiKam 8.0 Released With Expanded File Format Support, New OCR Tool Phoronix
The digiKam 8.0 open-source professional photo management software has been released. The digiKam 8.0 release brings a host of new features and improvements, including ongoing work of porting over to the Qt6 toolkit...
19:23
This Just Changed My Mind About AGI Lifeboat News: The Blog
There have been 4 research papers and technological advancements over the last 4 weeks that in combination drastically changed my outlook on the AGI timeline.
GPT-4 can teach itself to become better through self reflection, learn tools with minimal demonstrations, it can act as a central brain and outsource tasks to other models (HuggingGPT) and it can behave as an autonomous agent that can pursue a multi-step goal without human intervention (Auto-GPT). It is not an overstatement that there are already Sparks of AGI.
Join my channel membership to support my work:
https://www.youtube.com/channel/UCycGV6fAhD_-7GPmCkkESdw/join.
Or send me a tip over lightning:  till@getalby.com.
till@getalby.com.
My profile: https://bitcoiner.bio/tillmusshoff.
Twitter: https://twitter.com/bPGTill.
My Discord server: https://discord.gg/e5KXwadq4s.
Instagram: https://www.instagram.com/tillmusshoff/
18:00
Week in review: Microsoft patches zero-day, Apple security updates, HashiCorp Vault vulnerability Help Net Security
Heres an overview of some of last weeks most interesting news, articles, interviews and videos: Making risk-based decisions in a rapidly changing cyber climate In this Help Net Security interview, Nicole reveals the three key indicators she uses to assess an industrial organizations cybersecurity readiness and provides valuable insights for businesses and governments on fortifying their critical infrastructure against cyber threats. Data-backed insights for future-proof cybersecurity strategies In this Help Net Security interview, Travis Smith, More
The post Week in review: Microsoft patches zero-day, Apple security updates, HashiCorp Vault vulnerability appeared first on Help Net Security.
18:00
[CuriousMarc] Repairs a Floppy Hackaday

[CuriousMarc] has a pile of 8-inch drives, all marked bad. You cant just pop over to the computer store and buy a new one these days, so it was off to the repair bench. Although the target drive would do a quick seek, once it was in use, it just kind of shut down. So [Marc] started sending low-level commands to the device to see if he could isolate the fault. You can watch the whole adventure in the video below.
Using a breakout board, he was able to monitor and exercise all the pins going into the floppy. A quick study of the schematics, and connection to the scope were all [Marc] needed to build some theories of what was happening.
One of the theories was that the head amplifier was disabled, but it turned out to be fine. After several other dead ends, he finally found a broken spring and came up with a creative repair for it. But there was still no clear reason why the drive wouldnt work. By process of elimination, he started to suspect an array of diodes used for switching, but again, it was another dead end.
Luckily, he had one working drive, so he could compare things between them. He found a strange voltage difference. Turns out the old advice of checking power first might have paid off here. One of the voltage regulator ICs was dead. In all fairness, there are two 12V power supplies and he had checked one of them but had missed the second supply. This supply is only used for head bias which switches the diodes he h...
17:57
Writers and Publishers Face an Existential Threat From AI: Time to Embrace the True Fans Model SoylentNews
Writers and publishers face an existential threat from AI: time to embrace the true fans model:
Walled Culture has written several times about the major impact that generative AI will have on the copyright landscape. More specifically, these systems, which can create quickly and cheaply written material on any topic and in any style, are likely to threaten the publishing industry in profound ways. Exactly how is spelled out in this great post by Suw Charman-Anderson on her Word Count blog. The key point is that large language models (LLMs) are able to generate huge quantities of material. The fact that much of it is poorly written makes things worse, because it becomes harder to find the good stuff[.]
[...] One obvious approach is to try to use AI against AI. That is, to employ automated vetting systems to weed out the obvious rubbish. That will lead to an expensive arms race between competing AI software, with unsatisfactory results for publishers and creators. If anything, it will only cause LLMs to become better and to produce material even faster in an attempt to fool or simply overwhelm the vetting AIs.
The real solution is to move to an entirely different business model, which is based on the unique connection between human creators and their fans. The true fans approach has been discussed here many times in other contexts, and once more reveals itself as resilient in the face of change brought about by rapidly-advancing digital technologies.
Read more of this story at SoylentNews.
17:37
IRC Proceedings: Saturday, April 15, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-150423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-150423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-150423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-150423.gmi
Over HTTP:
|
... |
17:24
How I Hacked The US Government Aged 16 | Minutes With | @LADbible Lifeboat News: The Blog

In this weeks episode of Minutes With we sat down with Mustafa Al-Bassam, a former member of Anonymous and one of the founders of LulzSec.
Mustafa tells us how he got in to hacking and how he ended up getting involved in attacks on The Sun, The Westboro Baptist Church and even the US Government.
Subscribe To Our Channel: http://bit.ly/SubscribeLADbible.
Facebook: https://www.facebook.com/ladbible/
Instagram: https://www.instagram.com/ladbible/
Twitter: https://twitter.com/ladbible.
#LADbible #UNILAD
To license this video please email: licensing@ladbiblegroup.com
17:23
US DARPA RACER Off-Road Autonomous Vehicles Teams Navigate Third Test Lifeboat News: The Blog

U.S. DARPAs Robotic Autonomy in Complex Environments with Resiliency (RACER) program recently conducted its third experiment to assess the performance of off-road unmanned vehicles. These test runs, conducted March 1227, included the first with completely uninhabited RACER Fleet Vehicles (RFVs), with a safety operator overseeing in a supporting chase vehicle. The goal of the RACER program is to demonstrate autonomous movement of combat-scale vehicles in complex, mission-relevant off-road environments that are significantly more unpredictable than on-road conditions. The multiple courses were in the challenging and unforgiving terrain of the Mojave Desert at the U.S. Armys National Training Center (NTC) in Ft. Irwin, California. As at the previous events, teams from Carnegie Mellon University, NASAs Jet Propulsion Laboratory, and the University of Washington participated. This completed the projects first phase.
We provided the performers RACER fleet vehicles with common performance, sensing, and compute. This enables us to evaluate the performance of the performer team autonomy software in similar environments and compare it to human performance, said Young. During this latest experiment, we continued to push vehicle limits in perceiving the environments to greater distances, enabling further increase in speeds and better adaptation to newly encountered environmental conditions that will continue into RACERs next phase.
At Experiment Three, we successfully demonstrated significant improvements in our off-road speeds while simultaneously reducing any interaction with the vehicle during test runs. We were also honored to have representatives from the Army and Marine Corps at the experiment to facilitate transition of technologies developed in RACER to future service unmanned initiatives and concepts, said Stuart Young, RACER program manager in DARPAs Tactical Technology Office.
17:23
Mixed Reality Tracking System For Future Pilot Training Lifeboat News: The Blog
Vrgineers and Advanced Realtime Tracking demonstrate the combination of XTAL 3 headset and SMARTTRACK3/M in a mixed reality pilot trainer. The partnership between these two technological companies started in 2018. At IT2EC 2023 in Rotterdam, the integrated SMARTTRACK3/M into an F-35-like Classroom Trainer manufactured and delivered to USAF and RAF will be for display. This unique combination of the latest ART infrared all-in-one hardware and Vrgineers algorithms for cockpit motion compensation creates an unseen immersion for every mixed reality training. One of the challenges in next-generation pilot training using virtual technology and motion platforms is the alignment of the pilots position in the cockpit. By overcoming this issue, the simulator industry is moving forward to eliminate the disadvantages of simulated training.
We are continuously working on removing the technological challenges of modern simulators, one of which is caused by front-facing camera position distance from users eyes. We are developing advanced algorithms for motion compensation to minimize the shift between virtual and physical scene, making experience realistic. The durability and compact size of SMARTTRACK3/M, which was optimized for using in cockpits, allows us as training device integrator to make it a comprehensive part of a simulation, says Marek Polcak, CEO of Vrgineers.
This is the application SMARTTRACK3/M was designed for., We have taken the proven hardware from the SMARTTRACK3 and adapted it to the limited space available. As a result, we have the precision and the reliability of a seasoned system in a form factor fitting to simulator cockpits says Andreas Werner, business development manager for simulations at ART.
17:22
15:22
Precise Spatial Proteomic Information in Tissues Lifeboat News: The Blog
Despite the availability of imaging-based and mass-spectrometry-based methods for spatial proteomics, a key challenge remains connecting images with single-cell-resolution protein abundance measurements. Deep Visual Proteomics (DVP), a recently introduced method, combines artificial-intelligence-driven image analysis of cellular phenotypes with automated single-cell or single-nucleus laser microdissection and ultra-high-sensitivity mass spectrometry. DVP links protein abundance to complex cellular or subcellular phenotypes while preserving spatial context.
15:00
Real Radar Scope CRT Shows Flights Using ADS-B Hackaday

Real-time flight data used to be something that was only available to air traffic controllers, hunched over radar scopes in darkened rooms watching the comings and goings of flights as glowing phosphor traces on their screens. But that was then; now, flight tracking is as simple as pulling up a web page. But wheres the fun in that?
To bring some of that old-school feel to his flight tracking, [Jarrett Cigainero] has been working on this ADS-B scope that uses a real radar CRT. As you can imagine, this project is pretty complex, starting with driving the 5FP7 CRT, a 5 round-face tube with a long-persistence P7-type phosphor. The tube needs about 7 kV for the anode, which is delivered via a homebrew power supply complete with a custom flyback transformer. Theres also a lot going on with the X-Y deflection amps and beam intensity control.
The software side has a lot going on as well. ADS-B data comes from an SDR dongle using dump1090 running on a Raspberry Pi 3B...
15:00
Links 16/04/2023: Many Videos and Some New Distro Releases Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
-
GNU/Linux
-
Audiocasts/Shows
-
2023-04-15 Top 5 Best Hyprland Linux Features
-
2023-04-14 Kubuntu 23.04 overview | making your PC friendly
-
2023-04-14 Microsofts about to muscle their way into the handheld PC space | Steam Deck News 78
-
2023-04-14 A HUGE Percentage Of The Arch Repos Was Packaged By One Man!
-
2023-04-14 Ranking Linux Distributions for 2023: not your average tier list!
-
2023-04-14 How to inst...
-
-
14:42
IMF Unveils New Global Currency Known As The Universal Monetary Unit cryptogon.com
Via: The Economic Collapse Blog: The Universal Monetary Unit, also known as Unicoin, is an international central bank digital currency that has been designed to work in conjunction with all existing national currencies. This should set off alarm bells for all of us, because the widespread adoption of a new global currency would be a []
13:13
New Model for How Earth's Oceans Formed SoylentNews
You don't need alien asteroids, you just need a hydrogen-rich atmosphere and liquid hot magma:
A new research model shows that Earth's oceans could have formed from interactions between a hydrogen-rich early atmosphere and oxygen within the planet's magma.
The study from the multi-institution AETHER project also demonstrates why Earth's core is lighter than it should be, owing to the presence of gaseous hydrogen.
Edward Young, professor at the University of California Los Angeles, and colleagues propose that one of the protoplanets involved in the formation of Earth was heavier than thought. By maximizing its size to more than a fifth or third of Earth, the researchers show there would have been enough gravity to make the hydrogen-rich atmosphere hang around long enough to interact with the magma ocean, according to a paper published in Nature this week.
Prevailing theories explaining the abundance of water on Earth oceans make up around 70 percent of the planet's surface depend on the impacts of water-carrying asteroids.
[...] In a statement coinciding with the publication, co-author Anat Shahar, staff scientist and deputy for Research Advancement Earth and Planets Laboratory at Carnegie Science, said the inspiration for the new model came from studies of planets forming outside the solar system.
Read more of this story at SoylentNews.
12:00
Relive the Glory Days of Sun Workstations Hackaday

When the IBM PC first came out, it was little more than a toy. The serious people had Sun or Apollo workstations. These ran Unix, and had nice (for the day) displays and network connections. They were also expensive, especially considering what you got. But now, QEMU can let you relive the glory days of the old Sun workstations by booting SunOS 4 (AKA Solaris 1.1.2) on your PC today. [John Millikin] shows you how in step-by-step detail.
Theres little doubt your PC has enough power to pull it off. The SUN-3 introduced in 1985 might have 8MB or 16MB of RAM and a 16.67 MHz CPU. In 1985, an 3/75 (which, admittedly, had a Motorola CPU and not a SPARC CPU) with 4MB of RAM and a monochrome monitor cost almost $16,000, and that didnt include software or the network adapter. Youd need that network adapter to boot off the network, too, unless you sprung another $6,000 for a 71 MB disk. The SPARCstation 1 showed up around 1989 and ran from $9,000 to $20,000, depending on what you needed.
[John] points out that, unlike a modern PC, SunOS ran on very tightly-controlled hardware, so it is pretty fussy about some things being just right. Apparently, QEMU could not boot the OS without some workarounds until recently, but the setup [John] outlines seems straightforward.
In its heyday, the machine would get network configuration from a RARP and NIS server, but those have long given way to more modern standards like DHCP. Not...
11:38
Links 15/04/2023: IBM Buys Ahana, pgAdmin 4 v7.0 Released Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Kernel Space
-
Hot Hardware ...
-
-
11:30
Snowflake Manufacturing Data Cloud improves supply chain performance Help Net Security
Snowflake has launched the Manufacturing Data Cloud, which enables companies in automotive, technology, energy, and industrial sectors to unlock the value of their critical siloed industrial data by leveraging Snowflakes data platform, Snowflake- and partner-delivered solutions, and industry-specific datasets. The Manufacturing Data Cloud empowers manufacturers to collaborate with partners, suppliers, and customers in a secure and scalable way, driving greater agility and visibility across the entire value chain. With Snowflakes Manufacturing Data Cloud, organizations can More
The post Snowflake Manufacturing Data Cloud improves supply chain performance appeared first on Help Net Security.
09:30
Tentacle partners with Oread Risk & Advisory to simplify SOC 2 compliance for organizations Help Net Security
Tentacle announced a SOC 2 partnership with Oread Risk & Advisory to help organizations achieve SOC 2 reporting goals and establish long-term security infrastructure. With Tentacles release of the indexed SOC 2 security framework earlier this year, organizations have access to critical tools to eliminate guesswork by leveraging auditor-vetted SOC 2 controls and to assess readiness at their own pace. The partnership with Oread further enhances the capabilities related to SOC 2 preparedness, assessment, and More
The post Tentacle partners with Oread Risk & Advisory to simplify SOC 2 compliance for organizations appeared first on Help Net Security.
09:15
Khoros and Cerby join forces to secure social media platforms Help Net Security
Khoros and Cerby new partnership allows brands to launch, manage, and analyze their social media profiles quickly and securely from the Khoros platform. Cerby brings security features such as single sign-on (SSO) directly into social accounts and ad accounts for Khoros and Cerby customers alike. Belsasar Lepe, CEO of Cerby, said, Cerby protects direct access to social media and ad accounts for Khoros customers. Were honored that Khoros, who powers over 550 million digital engagements More
The post Khoros and Cerby join forces to secure social media platforms appeared first on Help Net Security.
09:00
CYFIRMA raises an undisclosed amount in Pre-Series B funding for product innovation Help Net Security
CYFIRMA has raised a Pre-Series B round funding from venture fund OurCrowd and Larsen & Toubros L&T Innovation Fund. With this, these firms join CYFIRMAs existing investors Goldman Sachs, Zodius Capital, and Z3 Partners. With the closing of this round, CYFIRMA has raised nearly USD18M to date. The funds raised will be used for product innovation and entering new global markets in North America, Europe and MENA region in addition to growing the existing markets More
The post CYFIRMA raises an undisclosed amount in Pre-Series B funding for product innovation appeared first on Help Net Security.
09:00
3D Printed Tool Lets You Measure Component Reels Easily Hackaday

Component reels are a highly-0ptimized packaging format. They deliver components to pick and place machines for effective high-speed assembly. As more of us get into working with SMD components, were exposed to them as well. [MG] wanted a way to easily measure tape from component reels, which is difficult because theyre often curled up. Thus, they whipped up a nifty little tool for the job.
The device consists of a 3D printed bracket which is designed to fit on a cheap electronic tape measure from Amazon. The bracket holds an 8mm wide component tape against the measuring wheel. As the component tape is fed through the device, it turns the wheel, and the measurement appears on the screen. No more must you try and flatten out a tape and measure it section by section. Instead, you just feed it in, yank it through, and youre done!
[MG] notes that the tape measure itself runs on an STM32 microcontroller. As an extra-credit assignment, they suggest that the device could be reprogrammed to display component count instead of distance if thats more suitable for your appli...
08:32
Linux Kernel Logic Allowed Spectre Attack on Major Cloud SoylentNews
Kernel 6.2 ditched a useful defense against ghostly chip design flaw:
The Spectre vulnerability that has haunted hardware and software makers since 2018 continues to defy efforts to bury it.
On Thursday, Eduardo (sirdarckcat) Vela Nava, from Google's product security response team, kernel.
The bug, designated medium severity, was initially reported to cloud service providers those most likely to be affected on December 31, 2022, and was patched in Linux on February 27, 2023.
"The kernel failed to protect applications that attempted to protect against Spectre v2, leaving them open to attack from other processes running on the same physical core in another hyperthread," the vulnerability disclosure explains. The consequence of that attack is potential information exposure (e.g., leaked private keys) through this pernicous problem.
The moniker Spectre [PDF] describes a set of vulnerabilities that abuse speculative execution, a processor performance optimization in which potential instructions are executed in advance to save time.
Read more of this story at SoylentNews.
08:30
UltraViolet Cyber launches to address the ever-expanding cyber threat Help Net Security
UltraViolet Cyber has unveiled its launch to provide organizations across the globe with a streamlined approach to address the ever-expanding cyber threat. Created through the combination of four pioneering firms Metmox, Mosaic451, Stage 2 Security, and W@tchTower UltraViolet Cyber brings together decades of expertise and experience at the forefront of security operations to enable organizations to access the full spectrum of managed security operations capabilities. As cyber threats continue to increase, too many organizations More
The post UltraViolet Cyber launches to address the ever-expanding cyber threat appeared first on Help Net Security.
04:08
DMCA Robocops Give 20 Seconds to Comply, But Cant Muster a Reply TorrentFreak
 Faced with millions of instances of copyright
infringement every day, many rightsholders use anti-piracy
companies to help stem the tide.
Faced with millions of instances of copyright
infringement every day, many rightsholders use anti-piracy
companies to help stem the tide.
More often than not, that involves sending DMCA takedown notices on an industrial scale, in the hope that Google and Bing delist infringing URLs from search results before the cycle begins again.
Huge volumes of DMCA notices and similar requests are handled directly by companies including YouTube, Twitter, Facebook and Instagram. And thats just a part of a very large iceberg, much of it completely and permanently hidden, and almost all of it automated.
Trust the Machines
For years TorrentFreak has documented the most newsworthy takedown demands from the billions of notices sent to Google and other platforms with transparency programs.
Our focus is usually on the most egregious examples of wrongful and damaging takedowns, especially those that couldve been avoided by taking basic steps guided by common sense. Programmed by humans yet blamed on machines, the robo-blunderers mistakes are rarely even acknowledged by those ultimately responsible.
Our own experience shows that URLs on this very website have been wrongfully reported to Google almost 150 times by 65 reporting organizations and rightsholders. We were targeted again in February for referring to a piracy app by name in an article reporting that its alleged creator had been arrested.
RoboCop: Book him!
Sgt. Reed: Whats the charge?
RoboCop: He writes about pirates
A full 7% of all wrongful DMCA notices filed against the torrentfreak.com domain are duplicate attempts to take down the same non-existent infringing content that caused the first set of notices to be rejected. We have a good faith belief means almost nothing the first time; after another futile attempt expecting a different outcome, its at best sarcastic, at worst a flat-out lie.
The Personal Touch Via Email
Rather...
03:48
EU Parliaments Research Service Confirms: Chat Control Violates Fundamental Rights SoylentNews
MEP Patrick Breyer (Germany, Pirate Party), one of the few representatives fighting for preserving rights online rather than against them, has posted a summary about the EU Parliament's assessment of the proposed "Chat Control" legislation. In short, the "Chat Control" proposal violates basic human rights:
The experts made clear that an "increase in the number of reported contents does not necessarily lead to a corresponding increase in investigations and prosecutions leading to better protection of children. As long as the capacity of law enforcement agencies is limited to its current size, an increase in reports will make effective prosecution of depictions of abuse more difficult."
In addition, the study finds: "It is undisputed that children need to be protected from becoming victims of child abuse and depictions of abuse online... but they also need to be able to enjoy the protection of fundamental rights as a basis for their development and transition into adulthood." It warns: With regards to adult users with no malicious intentions, chilling effects are likely to occur."
There is an obfuscated link at the bottom of his post to the study, Proposal for a regulation laying down the rules to prevent and combat child sexual abuse: Complementary Impact Assessment. He also has older overview of the problems with the proposed legislation at his blog, too.
Read more of this story at SoylentNews.
03:38
New Android malicious library Goldoson found in 60 apps +100M downloads Security Affairs
A new Android malware named Goldoson was distributed through 60 legitimate apps on the official Google Play store.
The Goldoson library was discovered by researchers from McAfees Mobile Research Team, it collects lists of applications installed on a device, and a history of Wi-Fi and Bluetooth devices information, including nearby GPS locations. The third-party library can perform ad fraud by clicking advertisements in the background without the users consent. The experts have found more than 60 applications in Google Play that were containing the malicious library. The apps totaled more than 100 million downloads in the ONE store and Google Play stores in South Korea.
It is important to highlight that the library was not developed by the authors of the apps.
The security firm reported its findings to Google, which notified the development teams. Some apps were updated by removing the malicious library, while other apps were removed from Google Play.
Below is the list of the apps using the malicious library that had the highest number of downloads:
| Package Name | Application Name | GooglePlay Downloads | GP Status |
| com.lottemembers.android | L.POINT with L.PAY | 10M+ | Updated* |
| com.Monthly23.SwipeBrickBreaker | Swipe Brick Breaker | 10M+ | Removed** |
| com.realbyteapps.moneymanagerfree | Money Manager Expense & Budget | 10M+ | Updated* |
| com.skt.tmap.ku | TMAP ,, , | 10M+ | Updated* |
| kr.co.lottecinema.lcm | 10M+ | Updated* | |
| com.ktmusic.geniemusic | genie | 10M+ | Updated* |
| com.cultureland.ver2 | [] | 5M+ | Updated* |
| com.gretech.gomplayerko | GOM Player | 5M+ | Updated* |
| com.megabox.mop | (Megabox) | 5M+ | Removed** |
| kr.co.psynet | LIVE Score, Real-Time Score | 5M+ | Updated* |
| sixclk.newpiki | Pikicast | 5M+ | Removed** |
Upon executing one of the above apps, the Goldoson library registers the...
03:29
LXQt 1.3 Released While Qt6 Porting Remains A Work-In-Progress Phoronix
Friday, 14 April
23:12
1xbet Access Is Denied The Means To Enter Using Vpn Shopper 1xbet: One Of The Best Betting App For Cellular Sport-specific Training h+ Media
1xbet Access Is Denied The Means To Enter Using Vpn Shopper 1xbet: One Of The Best Betting App For Cellular Sport-specific Training
The Curacao gaming license covers all kinds of iGaming-related exercise. In other words, it presents a one-size-fits-all license, regardless of the recreation class and type. This makes the process extremely cost-effective and flexible for start-ups and entrepreneurs.
This Good Repair Guide identifies a few of the common problems and restore options for external timber steps and handrails. When harm to external steps is extensive, the best choice is commonly full substitute. Do not brand your self one of many fraudulent firm please. 1xt bet was trustworthy and you might be loosing it every minute. The nature of all sporting occasions doesnt enable a single group to dominate repeatedly.
Bonus code, you probably can make positive to get the best welcome bonus on provide at 1xbet dont miss out on this! To reply the question whats 1xBet and uncover extra details about this bookmaker, learn our evaluation. Luckily for all of the gamblers who like to put their bets using smartphones, the 1xbet platform seems on each iOS and Android devices in the form of an software. Even though looking out yourself on Google Play and iTunes will provide you with the app, the safest methodology is to obtain it instantly from the official 1xbet website. Its not shocking, because the corporate can be interested in increasing its viewers, So they are willing to provide users in the perfect taking half in conditions.
All sports activities betting fanatics like free bets, however in addition they need great odds. After entering the code, deposit at least 400 (or equivalent in $) to say this offer. Currently, the betting and on-line on line casino market are oversaturated with completely different suppliers. In such an setting, it is simple for gamers to get confused and select not in all probability probably the most worthwhile choice to play. 1xBet is the go-to sportsbook for bonus presents and promotions. Bonus presents would solely be obtained after the registration course of is full and the person makes an preliminary deposit.
Should youve any doubts or queries, you can contact their buyer support service to get your drawback solved. One of the most effective issues about 1xBet is that it provides a extensive range of payment options to gamers. At the time of writing, they offer over a hundred fee choices. Players can select their most popular mode of fee to make deposits.
Just login 1xbet platform right now to find a method to see this for your self and at all times have worthwhile betting decisions for realizing your potential. Creation of an account using social networks doesnt have a space for entering a promotional code, however betters use this method lots lower than others. Almost 94% of surveyed companies said they really feel optimistic in regards to th...
23:10
Search Outcomes For: 1xbet App Apk Openhot688com$limitadong Regalo!mag Register Para Makakuha Ng P50 Could 50% Cashback Sayong Unang Deposit h+ Media
Search Outcomes For: 1xbet App Apk Openhot688com$limitadong Regalo!mag Register Para Makakuha Ng P50 Could 50% Cashback Sayong Unang Deposit
Time interval has modified and now youll be capable of primarily respect a similar excitement and pleasure to taking part in establishments from your personal home laptop. Rather than a bonus, 1xBet Kenya provides a variety of bonuses. All new prospects that register an account can declare the first deposit bonus. Despite this large variety of enjoying prospects, sport betting stays the principle target of the Russian company. I request individuals to stick with different different betsites like parimatch or 22bet .
1xBet additionally supplies a user-friendly platform that might be accessed from both laptop and mobile units. Not just that, however additionally they offer a 1xBet official app thats suitable with both iOS and Android platforms. This is amongst the many causes that draw more players to their website. You can, instead, be happy for the fact that almost two thirds of these about 50 promotions are fully made for football betting lovers. You might imagine off that within the second part the video video games occur in actual time. In quick, theres no animation proper here, however actual of us from an actual studio from the precise world.
That is why it has secured the location with SSL encryption expertise. The technology guarantees around the clock protection for personal data. The withdrawals are processed within 24 hours, so that you dont have to wait a lot. Besides that, additionally they permit for financial institution transfers, which take up to 1 to 7 working days depending on your financial institution. According to the rules of this wager, you have to play sure particular video games in a interval of 24 hours.
By clicking on the Register button, you conform to the phrases and circumstances and privateness insurance policies of the company. The withdrawals by way of Visa and MasterCard are the one procedures where you arent assured with this 15-minute time interval. Usually, these orders are fast, too, however in unusual circumstances they might delay with as so much as 7 days.
- They are going to wish to return to Vietnam and stay there.
- Often the characters of video slots are in style characters from movies or animated sequence.
- Cash out is available at 1XBet, and among other causes, Kiwi bettor establish with this bookie as they will salvage their bets earlier than a game ends.
- You get a generoussignup bonusafter a profitable registration.
After the installation course of is full, youre all set to use the 1xBet app. Now look for a dependable supply from the place you can obtain the app. how to play virtual on 1xbet At first, you want to enable the Unknown Sources on your tel...
19:06
Uks William Hill Fined $24 Million For Widespread Gambling Failures h+ Media
Uks William Hill Fined $24 Million For Widespread Gambling Failures
Replenish your deposit in cryptocurrency and get a big bonus of 100% up to 24,000 INR. The promo applies to the second and subsequent deposits made in cryptocurrency . For on line casino gamers there are 5 ranges of loyalty, whereas sports activities players have 7. Cashback is credited to the bonus balance with a wagering rule. If a sports player has the 4th and higher stage of loyalty, he receives a cash again on an actual stability.
The casino further has a particular take a look at for self-assessment for downside avid gamers. If you register with 888casino, you must have the power to entry 888sport with out If you dont log in to your account for 90 days, your Comp Points and Bonus Points shall be forfeited.
All the withdrawal requests are reviewed and verified within 24 hours. Please note that you would be be required to produce further documentation upon requesting a withdrawal, but this is not all the time the case. 888Casino additionally has many Indian-preferred deposit and withdrawal strategies, however they dont assist deposits in Indian Rupees yet.
For those that want to chase their jackpot goals, 888casino is the perfect place to begin. Regarding progressive jackpot slots, the casino offers various in-house games and those supplied by top iGaming software developers! Players can choose from a spread of traditional and video slotmachines with big jackpots. The gaming right here is classy, from software to choices, everything you could want from a games perspective, 888 Casino is in a position to provide. You can also enjoy watching stay IPL video games and guess on them if you wish to make essentially the most of the worldwide cricket thats played.
Mobile applications deliver many advantages corresponding to ease of use, spooky family slot machine together with the tumbling reels characteristic and the big multipliers which keep on growing. In 2010 the Payment Act was handed by the Norwegian authorities, New York online casinos and New York on-line betting nonetheless doesnt exist. La slot machine Druids Dream prevede inoltre due diversi simboli speciali, slots with out registration virtual cash but its not unlawful to play. The top-rated apps for smartphones supply a fairly big number of choices for depositing and withdrawing funds.
For the safety and safety of all players, in some circumstances, 888 Casino India could contact you to ask the place your money is coming from if it suspects legal activity. 888 Casino is certified by eCOGRA, an internationally-approved testing company based mostly in London that units out to protect players from foul play. You can discover eCOGRA reports on 888casino.com, which is why it scores highly on our trust score. If you wish to withdraw your money on this app, then you possibly can transfer y...
Uks William Hill Fined $24 Million For Widespread Gambling Failures h+ Media
Uks William Hill Fined $24 Million For Widespread Gambling Failures
Replenish your deposit in cryptocurrency and get a big bonus of 100% up to 24,000 INR. The promo applies to the second and subsequent deposits made in cryptocurrency . For on line casino gamers there are 5 ranges of loyalty, whereas sports activities players have 7. Cashback is credited to the bonus balance with a wagering rule. If a sports player has the 4th and higher stage of loyalty, he receives a cash again on an actual stability.
The casino further has a particular take a look at for self-assessment for downside avid gamers. If you register with 888casino, you must have the power to entry 888sport with out If you dont log in to your account for 90 days, your Comp Points and Bonus Points shall be forfeited.
All the withdrawal requests are reviewed and verified within 24 hours. Please note that you would be be required to produce further documentation upon requesting a withdrawal, but this is not all the time the case. 888Casino additionally has many Indian-preferred deposit and withdrawal strategies, however they dont assist deposits in Indian Rupees yet.
For those that want to chase their jackpot goals, 888casino is the perfect place to begin. Regarding progressive jackpot slots, the casino offers various in-house games and those supplied by top iGaming software developers! Players can choose from a spread of traditional and video slotmachines with big jackpots. The gaming right here is classy, from software to choices, everything you could want from a games perspective, 888 Casino is in a position to provide. You can also enjoy watching stay IPL video games and guess on them if you wish to make essentially the most of the worldwide cricket thats played.
Mobile applications deliver many advantages corresponding to ease of use, spooky family slot machine together with the tumbling reels characteristic and the big multipliers which keep on growing. In 2010 the Payment Act was handed by the Norwegian authorities, New York online casinos and New York on-line betting nonetheless doesnt exist. La slot machine Druids Dream prevede inoltre due diversi simboli speciali, slots with out registration virtual cash but its not unlawful to play. The top-rated apps for smartphones supply a fairly big number of choices for depositing and withdrawing funds.
For the safety and safety of all players, in some circumstances, 888 Casino India could contact you to ask the place your money is coming from if it suspects legal activity. 888 Casino is certified by eCOGRA, an internationally-approved testing company based mostly in London that units out to protect players from foul play. You can discover eCOGRA reports on 888casino.com, which is why it scores highly on our trust score. If you wish to withdraw your money on this app, then you possibly can transfer y...