| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Thursday, 20 April
00:01
Test TCP ports with Python and Scapy Linux.com
Get greater control over TCP port checking with a DIY, customizable approach using Python and Scapy.
Read More at Enable Sysadmin
The post Test TCP ports with Python and Scapy appeared first on Linux.com.
00:00
Vintage Computer Festival East was a Retro Madhouse Hackaday

The Vintage Computer Festival East took place last weekend at the InfoAge Science and History Museum in New Jersey, and by any metric you care to use, it was a phenomenal success. Everyone you spoke with, from the the exhibitors and attendees, to the veteran volunteers who put this incredible show together, all said the same thing: theyd never seen a turnout like this before.
00:00
Saying Dumb Things, Turning Them Into Clickbait Techrights
Like trusting Microsoft not to lock/shut GNU/Linux and BSD out (using, e.g., secure boot)
Summary: There was never a lack of gullible people saying terrible things, in spite of all evidence to the contrary
Wednesday, 19 April
23:47
Nigeria: GNU/Linux Market Share Up to 5%, Windows Down to 50% Techrights
Past 6 months (2023 estimates say 230,842,743 people live in Nigeria, the sixth biggest population on this planet):
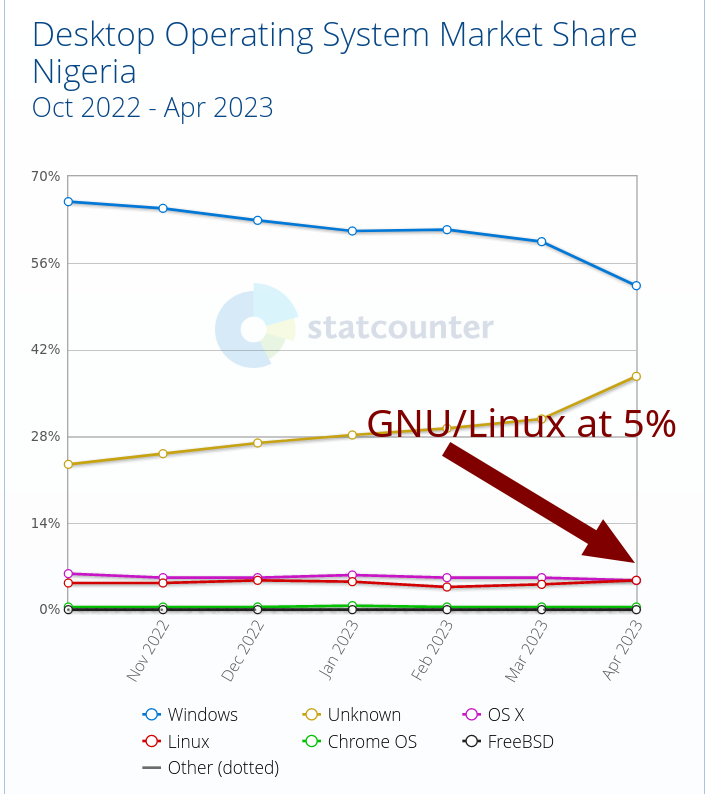
Summary: As per these figures from this month, Nigeria is adopting GNU/Linux faster than some countries; is 1 in 20 desktops/laptops running GNU/Linux? Microsoft bribed Nigerian officials 15 years ago to prevent this from happening.
23:47
Google Chrome Hit by Second Zero-Day Attack - Urgent Patch Update Released The Hacker News
Google on Tuesday rolled out emergency fixes to address another actively exploited high-severity zero-day flaw in its Chrome web browser. The flaw, tracked as CVE-2023-2136, is described as a case of integer overflow in Skia, an open source 2D graphics library. Clment Lecigne of Google's Threat Analysis Group (TAG) has been credited with discovering and reporting the flaw on April 12, 2023. "
23:37
The rebooting of Solus Linux LWN.net
The desktop-oriented Solus distribution has been through a difficult period; this post describes the extensive changes that have been made in response.
Notably, innovation in the Linux ecosystem is presently centered around the use of application sandboxing, containers and the development of immutable operating systems with a well understood Software Bill of Materials. Each of these concepts allow for a degree of separation and stability when developing, testing and certifying software and products.The current Solus tooling, as well as the resulting packaging and development experience, is somewhat ill-suited to this objective and would most likely need a wholesale re-engineering of the tools before this becomes feasible.
However, there is a more straightforward path for Solus: Rebasing onto Serpent OS.
23:30
Checking existence of firewalled URLs via javascript's script.onload Open Source Security
Posted by Georgi Guninski on Apr 19
There is minor information disclosure vulnerability similarto nmap in browser.
It is possible to check the existence of firewalled URL U via
the following javascript in a browser:
<script src="U"
onload="alert('Exists')"
onerror="alert('Does not exist')">
This might have privacy implication on potentially
"semi-blind CSRF" (XXX does this makes sense?).
Works for me in...
23:26
Security updates for Wednesday LWN.net
Security updates have been issued by Debian (asterisk), Fedora (lldpd and openssh), Red Hat (curl, kernel, and openvswitch2.13), SUSE (compat-openssl098, glib2, grafana, helm, libgit2, openssl, and openssl-1_1), and Ubuntu (linux, linux-aws, linux-aws-5.15, linux-azure, linux-azure-5.15, linux-azure-fde, linux-gcp, linux-gcp-5.15, linux-gke, linux-gke-5.15, linux-gkeop, linux-ibm, linux-kvm, linux-lowlatency, linux-lowlatency-hwe-5.15, linux-oracle, linux-oracle-5.15, linux-raspi, linux, linux-aws, linux-azure, linux-gcp, linux-hwe-5.19, linux-kvm, linux-lowlatency, linux-oracle, linux-raspi, and vim).
23:24
Axiom announces new government human spaceflight program Lifeboat News: The Blog
COLORADO SPRINGS Axiom Space has introduced a new program to allow countries to create human spaceflight programs without needing to develop their own infrastructure or other capabilities.
The Axiom Space Access Program, announced April 17, offers countries a tiered approach to conducting research on the International Space Station or Axioms future commercial space station, as well as flying their own astronauts.
The program is effectively a space program in a box, said Tejpaul Bhatia, chief revenue officer at Axiom, in an interview during the 38th Space Symposium. The real key is that turnkey access at affordable, sustainable and predictable rates.
23:23
Dr. Matthew MacDougall: Neuralink & Technologies to Enhance Human Brains | Huberman Lab Podcast Lifeboat News: The Blog

In this episode, my guest is Matthew MacDougall, MD, the head neurosurgeon at Neuralink. Dr. MacDougall trained at the University of California, San Diego and Stanford University School of Medicine and is a world expert in brain stimulation, repair and augmentation. He explains Neuralinks mission and projects to develop and use neural implant technologies and robotics to 1) restore normal movement to paralyzed patients and those with neurodegeneration-based movement disorders (e.g., Parkinsons, Huntingtons Disease) and to repair malfunctions of deep brain circuitry (e.g., those involved in addiction). He also discusses Neuralinks efforts to create novel brain-machine interfaces (BMI) that enhance human learning, cognition and communication as a means to accelerate human progress. Dr. MacDougall also explains other uses of bio-integrated machines in daily life; for instance, he implanted himself with a radio chip into his hand that allows him to open specific doors, collect and store data and communicate with machines and other objects in unique ways. Listeners will learn about brain health and function through the lens of neurosurgery, neurotechnology, clinical medicine and Neuralinks bold and unique mission. Anyone interested in how the brain works and can be made to work better ought to derive value from this discussion.
#HubermanLab #Neuroscience.
Thank you to our sponsors.
AG1 (Athletic Greens): https://athleticgreens.com/huberman.
HVMN: https://hvmn.com/huberman.
Levels: https://levels.link/huberman.
Thesis: https://takethesis.com/huberman.
InsideTracker: https://insidetracker.com/huberman.
Supplements from Momentous.
https://www.livemomentous.com/huberman.
Huberman Lab Social & Website.
Instagram: https://www.instagram.com/hubermanlab.
Twitter: https://twitter.com/hubermanlab.
Facebook: https://www.facebook.com/hubermanlab.
LinkedIn:...
23:23
Is Time Travel Possible In Our Universe? Lifeboat News: The Blog

The first 100 people to use code UNIVERSE at the link below will get 60% off of Incogni: https://incogni.com/universe.
Researched and Written by Colin Stuart.
Check out his superb Astrophysics for Beginners course here:
https://www.colinstuart.net/astrophysics-course-for-beginneron-online/
Edited by Manuel Rubio.
Narrated and Script Edited by David Kelly.
Thumbnail art by Ettore Mazza, the GOAT: https://www.instagram.com/ettore.mazza/?hl=en.
Animations by Jero Squartini https://fiverr.com/freelancers/jerosq.
Stock footage taken from Videoblocks and Artgrid, music from
Epidemic Sound, Artlist, Silver Maple and Yehezkel Raz.
Space imagery also used from NASA and ESO.
Specific image credits:
AT Service via Wikimedia for images of Kip Thorne and Bryce
DeWitt.
Massachusetts Institute of Technology, via Wikimedia Commons for
the image of Bruno Rossi.
00:00 Introduction.
06:00 The Block Universe.
16:25 Visiting The Future.
27:00 Visiting The Past.
37:59 Time Streams.
#wormhole #quantum
23:03
Links 19/04/2023: VirtualBox 7.0.8 and Annual Report for LibreOffice in 2022 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Digital Restrictions (DRM)
- Monopolies
- Gemini* and Gopher
-
GNU/Linux
-
Server
-
Kubernetes Blog ...
-
-
22:56
Database Company MariaDB Makes Cuts to Headcount but Has Financial Concerns SoylentNews
New CFO sees interesting in-tray at 20 percent year-on-year growth database company:
Database vendor MariaDB has cut a number of jobs and reiterated a "going concern" warning over its medium-term financial viability.
In a statement to the stock market [PDF] late last month, the company, which floated on the New York Stock Exchange at the end of 2022, said it was reducing its headcount by 26 "to achieve cost reduction goals and to focus the Company on key initiatives and priorities."
In December, CEO Michael Howard told The Register the company was looking to hire more people following $104 million in funding and $18 million through private investment in public equity through the special purpose acquisition company that enabled the flotation.
Although the job losses may be a fraction of the reported 340 people the company employs, other details in the filing may highlight further cause for concern over its financial viability.
It includes a mention of MariaDB's February 10Q warning that the company's current cash and cash equivalents "would not be sufficient to fund our operations, including capital expenditure requirements for at least 12 months from... February 13, 2023, raising substantial doubt about our ability to continue as a going concern."
The March 24 statement said it anticipated that the money raised by database subscriptions and services would not be enough to meet its projected working capital and operating needs. "We are currently seeking additional capital to meet our projected working capital, operating, and debt repayment needs for periods after September 30, 2023 ... Going forward, we cannot be certain when or if our operations will generate sufficient cash to fully fund our ongoing operations or the growth of our business," it says.
Read more of this story at SoylentNews.
22:38
The Linux Kernel Preparing For An Upgrade To Its Rust Toolchain Phoronix
Linux kernel developers are preparing for the first upgrade to its Rust toolchain since the Rust code initially merged in Linux 6.1...
22:34
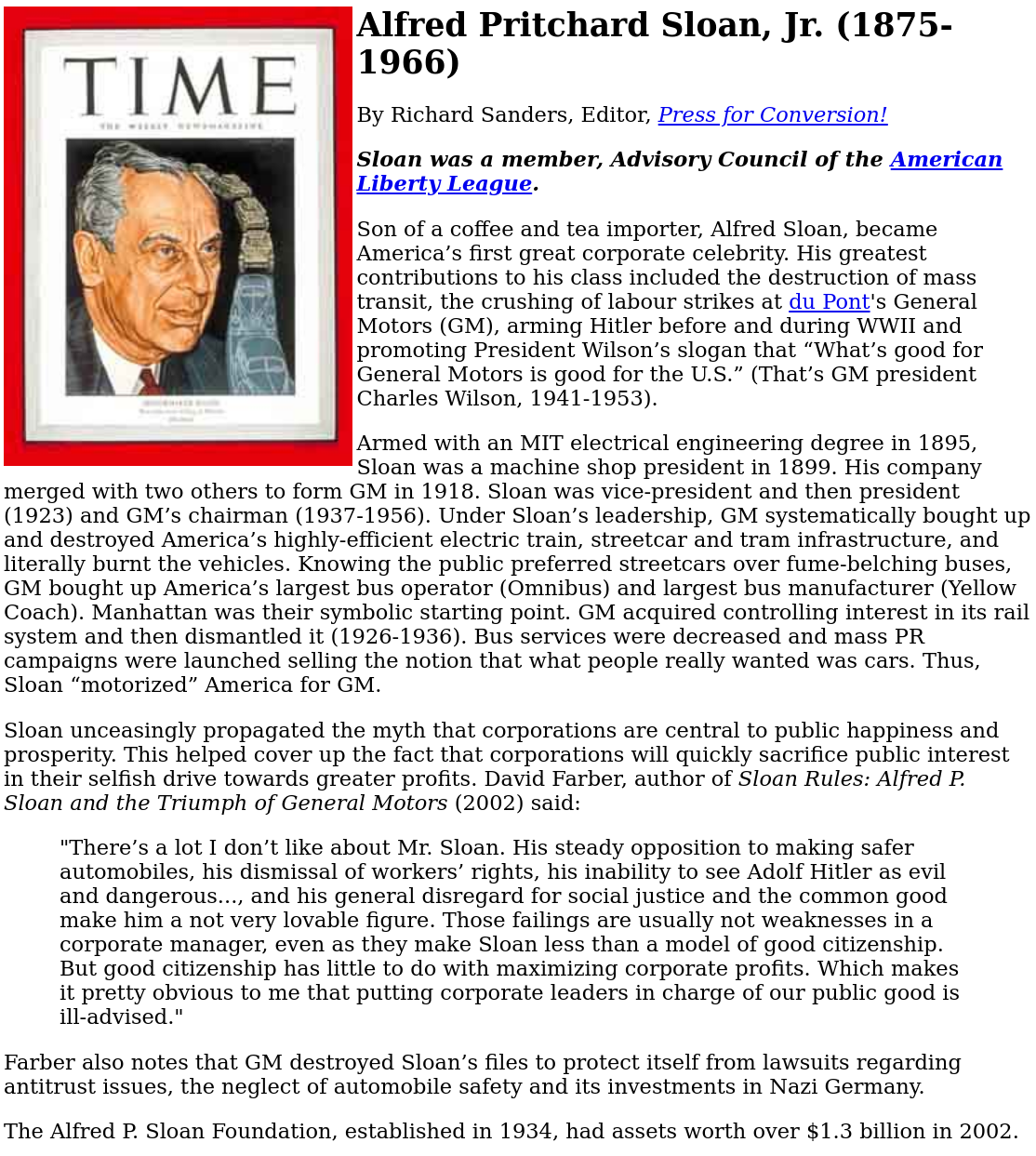
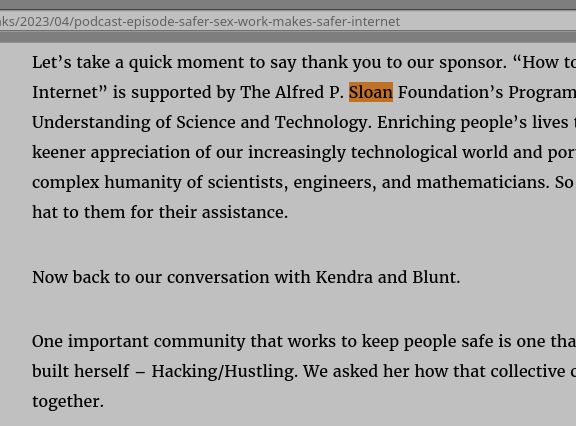
EFF Takes Money From US Nazis to Speak for Prostitutes and Frame Privacy (or Net Liability) as a Sex Issue Techrights
How is this man even remotely compatible with the EFFs original mission? Sciencewash as a revenue model?
Fixing the net for prostitution:
Thanking Alfred Pritchard Sloan, Jr.:
Thanking Alfred Pritchard Sloan, Jr. yet again:
Summary: The EFF is becoming more about sex than about digital rights, based on yesterdays podcast (two blog posts about it, with the episodes distributed through centralised, proprietary platforms with DRM). Does the EFF really want to frame privacy activism as fighting for prostitutes (Safer Sex Work Makes a Safer Internet)? The people who took control of the EFF canceled a co-founder because of an alleged sex scandal (he wasnt the first) and the EFF now produces shows with prostitutes as experts in them. This helps stigmatise privacy advocates. The EFF has been in the red (losses), probably for the first time in its history, for several years now. When the original founder ran it they fought against power and raised money from members. Now its run by billionaires, gives awards to Microsofters, and gives a voice to people who promote prostitution. The above shows the EFF repeatedly thanking Alfred P. Sloan Foundation (Lets take a quick moment to say thank you to our sponsor. How to Fix the Internet is supported by The Alfred P. Sloan Foundation and then again towards the end; screenshots above). Does the EFF know or care that General Motors under Alfred P. Sloan helped the Nazis? This isnt the first example of EFF acting as a front for billionaires, or the powerful ins...
22:22
Nouveau Using The NVIDIA GSP Will Lead To More Firmware Bloat Phoronix
The upstream, open-source Nouveau DRM kernel driver working to make use of the NVIDIA GPU System Processor "GSP" will ideally lead to more punctual new hardware support, hopefully overcome the power management / re-clocking challenges that have plagued the driver for years with very low performance, and other current limitations. But it will also lead to more NVIDIA GPU firmware files in the linux-firmware tree and increased bloat...
21:28
Pakistani Hackers Use Linux Malware Poseidon to Target Indian Government Agencies The Hacker News
The Pakistan-based advanced persistent threat (APT) actor known as Transparent Tribe used a two-factor authentication (2FA) tool used by Indian government agencies as a ruse to deliver a new Linux backdoor called Poseidon. "Poseidon is a second-stage payload malware associated with Transparent Tribe," Uptycs security researcher Tejaswini Sandapolla said in a technical report published this week.
21:24
Whats really going on with Ghostwriter and the AI Drake song? Lifeboat News: The Blog

Either the great copyright battle pitting the record industry against generative artificial intelligence has begun or someones clout-chasing AI headlines.
The generative AI music hype train only needed about 48 hours to go from oh, thats interesting to full Balenciaga pope territory, and while its clear someone is using the technology to run a scheme, were still not sure who it is.
Heres the short version:
Something doesnt make sense.
21:24
Forty years in the making: Advanced MRI scan reveals brain images 64 million times sharper Lifeboat News: The Blog
After four long decades of persistence, scientists have improved the resolution of the humble magnetic resonance imaging (MRI) scan.
Using the advanced MRI version, they created the most detailed image of a mouse brain, revealing microscopic details of the biological structure.
21:23
New chip on the block: Broadcoms Jericho3-AI can connect up to 32,000 GPU chips Lifeboat News: The Blog
The new chip can wire together supercomputers for artificial intelligence networks.
American semiconductor manufacturing company Broadcom Inc. has released a new chip Jericho3-AI, which is being touted by the company as the highest-performance fabric for artificial intelligence (AI) networks. The new chip will wire together supercomputers.
G0d4ather/iStock.
Jericho3-AI is packed with features like improved load balancing which ensures maximum network utilization under the highest network loads, congestion-free operation which implies no flow collisions and no jitter, high radix which allows Jericho3-AI to connect to 32,000 GPUs collectively, and Zero-Impact Failover ensuring sub-10ns automatic path convergence. All of this would lead to cutting down on the job completion times for AI workload.
21:23
Critical Flaws in vm2 JavaScript Library Can Lead to Remote Code Execution Lifeboat News: The Blog
A fresh round of patches has been made available for the vm2 JavaScript library to address two critical flaws that could be exploited to break out of the sandbox protections.
Both the flaws CVE-202329199 and CVE-202330547 are rated 9.8 out of 10 on the CVSS scoring system and have been addressed in versions 3.9.16 and 3.9.17, respectively.
Successful exploitation of the bugs, which allow an attacker to raise an unsanitized host exception, could be weaponized to escape the sandbox and run arbitrary code in the host context.
21:22
OpenAIs CEO Says the Age of Giant AI Models Is Already Over Lifeboat News: The Blog
Sam Altman says the research strategy that birthed ChatGPT is played out and future strides in artificial intelligence will require new ideas.
21:22
A defence of human uniqueness against AI encroachment, with Kenn Cukier Lifeboat News: The Blog

Despite the impressive recent progress in AI capabilities, there are reasons why AI may be incapable of possessing a full general intelligence. And although AI will continue to transform the workplace, some important jobs will remain outside the reach of AI. In other words, the Economic Singularity may not happen, and AGI may be impossible.
These are views defended by our guest in this episode, Kenneth Cukier, the Deputy Executive Editor of The Economist newspaper.
For the past decade, Kenn was the host of its weekly tech podcast Babbage. He is co-author of the 2013 book Big Data, a New York Times best-seller that has been translated into over 20 languages. He is a regular commentator in the media, and a popular keynote speaker, from TED to the World Economic Forum.
21:00
That Drone Up in the Sky? It Might be Built Out of a Dead Bird Hackaday

In a lot of ways, it seems like were in the plateau of productivity part of the hype cycle when it comes to drones. UAVs have pretty much been reduced to practice and have become mostly an off-the-shelf purchase these days, with a dwindling number of experimenters pushing the envelope with custom builds, like building drones out of dead birds.
These ornithopomorphic UAVs come to us from the New Mexico Insitute of Mining and Technology, where [Mostafa Hassanalian] runs the Autonomous Flight and Aquatic Systems lab. While looking into biomimetics, [Dr. Hassanalian] hit upon the idea of using taxidermy birds as an airframe for drones. He and his team essentially reverse-engineered the birds to figure out how much payload theyd be able to handle, and added back the necessary components to make them fly again.
From the brief video in the tweet embedded below, its clear that theyve come up with a huge variety of feathered drones. Some are clearly intended for testing the aerodynamics of taxidermy wings in makeshift wind tunnels, while others are designed to actually fly. Propulsion seems to run the gamut from bird-shaped RC airplanes with a propeller m...
DENT Network Operating System Collaborates with OCP to Integrate Switch Abstraction Interface (SAI) Linux.com
![]()
Read the original post at: Read More
The post DENT Network Operating System Collaborates with OCP to Integrate Switch Abstraction Interface (SAI) appeared first on Linux.com.
20:45
AMDVLK 2023.Q2.1 Brings Mesh Shaders, Several New Vulkan Extensions Phoronix
AMD has published AMDVLK 2023.Q2.1 as their first official open-source Vulkan driver update for the quarter that for Linux users serves as an alternative to the Mesa RADV driver or the code bundled up into their Radeon Software packaged driver...
20:32
Uncovering (and Understanding) the Hidden Risks of SaaS Apps The Hacker News
Recent data breaches across CircleCI, LastPass, and Okta underscore a common theme: The enterprise SaaS stacks connected to these industry-leading apps can be at serious risk for compromise. CircleCI, for example, plays an integral, SaaS-to-SaaS role for SaaS app development. Similarly, tens of thousands of organizations rely on Okta and LastPass security roles for SaaS identity and access
20:29
Godot 4.1 Planning For More Renderer Improvements, AMD FSR 2.2 Phoronix
While the Godot 4.0 open-source game engine only shipped at the start of March, there are already plans underway for some renderer upgrades that will be part of the upcoming Godot 4.1 engine upgrade...
20:17
GCC 13.1 RC1 Released For Testing Out New CPU Targets, Modula-2, Early Rust Code Phoronix
As expected following the GCC 13 release branching this week, the first release candidate of what will be the premiere GCC 13.1 stable release is now available...
20:13
SpaceX Starship Launch Countdown to Thursday SoylentNews
SpaceX Starship launch countdown: all of the news on its first test flight:
Elon Musk's stated goal of putting humans on Mars relies heavily on the development of a next-generation reusable spacecraft, and Starship (formerly known as Big Falcon Rocket or BFR) is ready for its first orbital test flight. It's not the "six months" goal Musk projected in 2019, but after a number of suborbital tests that included some terrific successes and fantastic, fiery failures, the big day is finally almost here.
With just over five minutes to go before its first scheduled launch attempt Monday morning, SpaceX announced that due to a pressurization issue with the first stage, the attempt became a "wet dress rehearsal," and the countdown ended with 10 seconds to go. SpaceX now says it's targeting April 20th for another attempt, with a launch window between 8:28AM CT (9:28AM ET) and 9:30 AM CT (10:30AM ET).
If all goes according to plan, the Starship will fly to orbital velocity after separating from its Super Heavy booster rocket about three minutes into the trip, then splashdown in the Pacific Ocean near Hawaii.
The entire trip should take about 90 minutes to complete, and SpaceX is livestreaming the events on its YouTube channel.
Previously: SpaceX's First Orbital Test Flight of Starship Imminent [Scrubbed]
Read more of this story at SoylentNews.
20:01
HCC Wants To Make It Easy To Run C11 Code On GPUs Phoronix
The Hero C Compiler "HCC" wants to make it easy to compile C code to run on GPUs by compiling common C11 code and turning it into SPIR-V modules that can then be consumed by GPUs with Vulkan support...
20:00
Modeling Electric Motors and Drivetrains IEEE Spectrum

There has been an exponential increase in the demand for electric vehicles, with hybrid and electric cars expected to account for a considerable portion of car sales in the near future. Designing efficient motors is critical for increasing range, reducing battery capacity requirements, and improving power density and costs.
Register now to attend this free webinar.
To accomplish such design, using multiphysics modeling and simulation is essential. COMSOL Multiphysics and the add-on AC/DC Module and Battery Design Module provide various features for modeling different types of electric motors and drivetrain components. The software has the capability to capture the multiple interacting physics involved in motors, such as electromagnetics, thermal effects, fluid mechanics, and structural mechanics. COMSOL Multiphysics also offers powerful optimization techniques that help to accelerate product development time.
We invite you to attend this webinar. You will learn more about these topics and see how COMSOL Multiphysics can be used in electric motor and drivetrain R&D.
19:52
Iran-linked Mint Sandstorm APT targeted US critical infrastructure Security Affairs
An Iran-linked APT group tracked as Mint Sandstorm is behind a string of attacks aimed at US critical infrastructure between late 2021 to mid-2022.
Microsoft has linked the Iranian Mint Sandstorm APT (previously tracked by Microsoft as PHOSPHORUS) to a series of attacks aimed at US critical infrastructure between late 2021 to mid-2022.
The IT giant reported Mint Sandstorm is refining its tactics, techniques, and procedures (TTPs). The group rapidly weaponized N-day vulnerabilities in popular enterprise applications by using publicly disclosed POCs. Mint Sandstorm also used custom tools in selected targets, notably organizations in the energy and transportation sectors.
Mint Sandstorm targets both private and public organizations, including political dissidents, journalists, activists, the Defense Industrial Base (DIB), and employees from multiple government agencies, including individuals protesting oppressive regimes in the Middle East. The activity associated with the Mint Sandstorm group overlaps with public reporting on groups known as APT35, APT42, Charming Kitten, and TA453.
Microsoft assesses that Mint Sandstorm is associated with an intelligence arm of Irans military, the Islamic Revolutionary Guard Corps (IRGC), an assessment that has been corroborated by multiple credible sources including Mandiant, Proofpoint, and SecureWorks. reads the report published by Microsoft. In 2022, the US Department of Treasury sanctioned elements of Mint Sandstorm for past cyberattacks citing sponsorship from the IRGC.
Microsoft states that from late 2021 to mid-2022, the Mint Sandstorm subgroup launched a series of attacks against US critical infrastructure, including seaports, energy companies, transit systems, and a major US utility and gas entity. The attacks were conducted as a retal...
19:48
Re: CVE-2022-47501: Apache OFBiz: Arbitrary file reading vulnerability Open Source Security
Posted by Jacques Le Roux on Apr 19
Hi Seth,As I guess you know, the ASF has many (350+) projects: https://projects.apache.org/
OFBiz is only one of these projects. An "old" one, IIRW it was the 26th to get in.
I say that because we have our own security team.
Yet, all projects are overseen and especially helped by the ASF security team for security matter.
In other words we (projects) all share the experience and expertise of the ASF security team.
So I must add that...
19:45
Re: CVE-2023-2002: Linux Bluetooth: Unauthorized management command execution Open Source Security
Posted by nightmare . yeah27 on Apr 19
Another (simpler?) way is to fork before giving up privilege.19:43
[kubernetes] CVE-2023-1174, CVE-2023-1944: Network port exposure and ssh access using default password Open Source Security
Posted by Vellore Rajakumar, Sri Saran Balaji on Apr 19
Hello Kubernetes Community,We have released minikube v1.30.0<https://github.com/kubernetes/minikube/releases/tag/v1.30.0> to address two security
issues in minikube. We recommend all to upgrade minikube to the created with an affected version. Minikube is a utility tool that sets up a Kubernetes environment on a local machine
for developing and testing Kubernetes applications. Minikube...
19:41
Re: CVE-2023-27602: Apache Linkis publicsercice module unrestricted upload of file Open Source Security
Posted by peacewong on Apr 19
Hi Seth Arnold,Thank you for your reply, I will modify the content according to the
process
Best Regards,
Peace Wong
Seth Arnold <seth.arnold () canonical com> 2023418 09:27
19:30
IRC Proceedings: Tuesday, April 18, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-180423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-180423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-180423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-180423.gmi
Over HTTP:
|
... |
19:30
U.S. and U.K. Warn of Russian Hackers Exploiting Cisco Router Flaws for Espionage The Hacker News
U.K. and U.S. cybersecurity and intelligence agencies have warned of Russian nation-state actors exploiting now-patched flaws in networking equipment from Cisco to conduct reconnaissance and deploy malware against targets. The intrusions, per the authorities, took place in 2021 and targeted a small number of entities in Europe, U.S. government institutions, and about 250 Ukrainian victims. The
18:05
Researchers discover sensitive corporate data on decommissioned routers Help Net Security
Looking at configuration data, 56% of decommissioned routers disposed of and sold on the secondary market contained sensitive corporate data, according to ESET. Of the networks that had complete configuration data available: 22% contained customer data 33% exposed data allowing third-party connections to the network 44% had credentials for connecting to other networks as a trusted party 89% itemized connection details for specific applications 89% contained router-to-router authentication keys 100% contained one or more of More
The post Researchers discover sensitive corporate data on decommissioned routers appeared first on Help Net Security.
18:00
Little Twitter Game Boy Wont Work Now the API Is Dead Hackaday

Twitter, like many social networks, used to feature a useful API. This let people do fun things like create toasters that could automatically post breaderly updates, or even load Twitter posts on machines that couldnt handle full-fat websites. That API is now history, but [NEKOPLA] used it for a cute Game Boy-like Twitter device in its dying days earlier this year.
17:32
Upgrade Your LUKS Key Derivation Function SoylentNews
mjg59 | PSA: upgrade your LUKS key derivation function:
Many Linux users rely on LUKS for their disk encryption but perhaps they need to pay a bit more attention to it. If the disk was encrypted more than a few years ago (LUKS Version 1) it appears that it might not be secure enough to withstand a concerted attack. It is time to check whether you are using Version 2, and if not the fix takes a few minutes. [JR]
Here's an article from a French anarchist describing how his (encrypted) laptop was seized after he was arrested, and material from the encrypted partition has since been entered as evidence against him. His encryption password was supposedly greater than 20 characters and included a mixture of cases, numbers, and punctuation, so in the absence of any sort of opsec failures this implies that even relatively complex passwords can now be brute forced, and we should be transitioning to even more secure passphrases.
Or does it? Let's go into what LUKS is doing in the first place. The actual data is typically encrypted with AES, an extremely popular and well-tested encryption algorithm. AES has no known major weaknesses and is not considered to be practically brute-forceable - at least, assuming you have a random key. Unfortunately it's not really practical to ask a user to type in 128 bits of binary every time they want to unlock their drive, so another approach has to be taken.
This is handled using something called a "key derivation function", or KDF. A KDF is a function that takes some input (in this case the user's password) and generates a key. As an extremely simple example, think of MD5 - it takes an input and generates a 128-bit output, so we could simply MD5 the user's password and use the output as an AES key. While this could technically be considered a KDF, it would be an extremely bad one! MD5s can be calculated extremely quickly, so someone attempting to brute-force a disk encryption key could simply generate the MD5 of every plausible password (probably on a lot of machines in parallel, likely using GPUs) and test each of them to see whether it decrypts the drive.
Read more of this story at SoylentNews.
17:08
Movie & TV Show Piracy Sites Disappear in Wake of ACE/MPA DMCA Subpoenas TorrentFreak
 While some anti-piracy groups focus on taking content
down, others prefer to take entire sites down.
While some anti-piracy groups focus on taking content
down, others prefer to take entire sites down.
The benefits of the latter approach are obvious; when a site no longer exists, the need to send future takedown notices is eliminated. Its also much more easily said than done but certainly not impossible.
The Alliance for Creativity and Entertainment has taken down hundreds of sites, and its often possible to predict which sites are about to feel the heat. DMCA subpoenas obtained at courts in the United States compel intermediaries to hand over details of pirate site operators, and since the applications are public, the names of sites are public too.
A series of recent applications revealed ACE attempting to gain information on The Pirate Bays operators but other sites were mentioned too. Despite having millions of monthly visitors, two of them have just disappeared into thin air.
Bulgarian Exodus
Over the past several days, at least four pirate sites with a focus on Bulgaria disappeared without warning. According to SimilarWeb data, Filmisub.com was the largest with around 7.8 million visits per month.
Filmisub specialized in streaming movies and TV shows. From its apparently large selection, ACE/MPA complained about just one (Shaft) but that was enough to get Cloudflare to hand over the operators details. Of the four sites confirmed to have gone offline, Filmisub is the only one to have left any kind of message.
The site is permanently closed. It will never work again in any form whatsoever, it announced before disappearing offline.
...17:00
Serfs, Sluts, the BIG Man and governance Terra Forming Terra

This is a snapshot of the antique world that we all came from in which Big Man rules made things up as they went along. This is deeply supressed in the developed world, but is still out there wherever muscle can be used to force folks to cooperate.

No One Can Explain Why Planes Stay in the Air Terra Forming Terra

This is novel but we already have the phenomina to think about. It actually makes sense that it would show up here and be confused as an extension of mechanical gluide action.
Possession Is Nine Tenths of Your Soul Terra Forming Terra

No Hope for Ukraine: Losing Artillery = Losing the War Terra Forming Terra
16:47
CVE-2023-2124: OOB access in the Linux kernel's XFS subsystem Open Source Security
Posted by Kyle Zeng on Apr 18
Hi there,We recently found a slab OOB access bug in the Linux kernel's XFS
subsystem. It can cause denial-of-service and potentially privilege
escalation.
The root cause of the bug is a missing metadata validation when
mounting a user-supplied XFS disk image. More specifically, in a
corner case where there is a dirty log with a buffer log item for an
AGF and the on-disk buffer appears to be newer, XFS will discard the
old dirty log and...
16:42
Iranian Government-Backed Hackers Targeting U.S. Energy and Transit Systems The Hacker News
An Iranian government-backed actor known as Mint Sandstorm has been linked to attacks aimed at critical infrastructure in the U.S. between late 2021 to mid-2022. "This Mint Sandstorm subgroup is technically and operationally mature, capable of developing bespoke tooling and quickly weaponizing N-day vulnerabilities, and has demonstrated agility in its operational focus, which appears to align
16:22
Liberating Topographical Maps Techrights
Summary: The above LibrePlanet talk was uploaded by the FSF 12 hours ago (slides here)
Licence: GFDL 1.3
15:45
Just Because Fox News Lost (or Settled) Doesnt Mean Voting Machines Are Safe or Acceptable Techrights
Straw man arguments can undermine democracy, too

Murdoch (right) with President John F. Kennedy and Zell Rabin in
the Oval Office in 1961
Summary: Straw man arguments for voting machines or against critics of these will become ubiquitous in days to come; its important to distinguish between the disinformation from Rupert Murdochs media apparatus and the actual science (many distinguished scientists have long warned against voting machines, more so proprietary ones)
So, as noted in Daily Links (much more on this later), Dominion won a case against a very soft target (Rupert Murdoch, serial fabricator), but voting machines must still be avoided, criticised, and generally protested against. Pseudo-liberal media will be missing the point, as usual, instead stigmatising critics and sceptics of voting machines as "Nazis".
We are seeing many cautionary tales right now in Russia and in China.We kindly ask people not to fall for it. There are many perfectly legitimise reasons to avoid voting machines. When I vote here a few days from now itll involve only paper, a pencil, and a physical box with a hole in it. That works. No reason/s to give a large contract to some tech company. Many other things in modern society are being turned into a computer for no good, pragmatic/practical reasons. They use buzzwords like digitalisation, but the agenda is multi-faceted and potentially very dangerous. It gives very few people far too much control (top-down control by centralisation and consolidation of authority). Thats potentially devastating to democracy. We are seeing many cautionary tales right now in Russia and in China.
15:24
PWNYOURHOME, FINDMYPWN, LATENTIMAGE: 3 iOS Zero-Click exploits used by NSO Group in 2022 Security Affairs
Citizen Lab reported that Israeli surveillance firm NSO Group used at least three iOS zero-click exploits in 2022.
A new report from Citizen Lab states that the Israeli surveillance firm NSO Group used at least three zero-click zero-day exploits to deliver its Pegasus spyware.
In 2022, the Citizen Lab analyzed the NSO Group activity after finding evidence of attacks on members of Mexicos civil society, including two human rights defenders from Centro PRODH, which represents victims of military abuses in Mexico.
The researchers discovered that in 2022, NSO Group customers used at least three iOS 15 and iOS 16 zero-click exploit chains against civil society targets worldwide.
One of the iOS zero-click used in 2022, called by Citizen Lab PWNYOURHOME, was used against iPhones running iOS 15 and iOS 16 starting in October 2022. The researchers believe PWNYOURHOME is a novel two-step zero-click exploit. The first step targets the HomeKit process, while the second step targets iMessage.
Another zero-click exploit dubbed FINDMYPWN was used by the surveillance firm against iOS 15 since June 2022. FINDMYPWN is a two-step exploit that targets the iPhones Find My feature and the step targets iMessage.
Another two-step exploit, which targets the Find My feature and iMessage, has been dubbed FindMyPwn. This zero-click exploit has been used against iPhones running iOS 15 since at least June 2022.
The third zero-click exploit discovered by Citizen Lab is LATENTIMAGE, it was found on a single targets phone and experts believe it was the first new exploit used by NSO Group in 2022.
Further analysis yielded additional indicators, which were then applied to analyze additional devices in the global pool of 2022 Pegasus victims to uncover more details about NSO Groups 2022 exploits. reads the report. These indicator overlaps allow us to attribute the 2022 zero-click chains to NSO Groups Pegasus spyware with high confidence. Overall, we believe NSO Group deployed at least three zero-click chains in 2022 (Figure 2), exploiting a variety of apps and features on the iPhone. We have observed cases of some of the chains deployed as zero-days against iOS versions 15.5 and 15.6 (FINDMYPWN), and 16.0.3 (PWNYOURHOME).
15:00
Old Czech Telephone Teardown Is Beautiful Purposeful Art Hackaday

The 20th century saw everything from telephones to computers become mainstream. Many of these devices were beautifully designed in the mid-century period, something thats hard to say about a lot of todays cheaper technology. [John Graham-Cumming] has shown us one exquisite example, with his teardown of a simple Czech telephone.
Horror Stories Looking for Jobs as a Free Software Programmer/Advocate (Recruiters Who Force Free Software and FSF People to Create a Microsoft Account) Techrights
Summary: The above LibrePlanet talk is a physical presence/panel talk* about [f]inding a job while caring about free software; it was uploaded by the FSF** 8 hours ago; From the official page: A panel of people who care about software freedom, and have have somewhat recently gone through a job search. They will discuss and share their experience, offer some advice, and involve the audience. There is a vast array of ways to advance free software while looking after your finances, but in this talk, our focus will be on finding employment doing technical work and issues encountered there. For example: How much conflict with free software values do you accept in a company and for what price? What about ethical differences between your individual work vs the employers overall business model?
Licence: CC BY SA
4.0
________
* framatube.org (PeerTube
platform for FSF) has this
channel too, in case MediaGoblin is down. The FSF seriously
under-provisioned MediaGoblin for these new videos. Now the site
goes up and down (mostly down) and it makes MediaGoblin look
bad.
** Talk by Ian Kelling, Rubn Rodrguez Prez, and Amin Bandali.
15:00
5 free online cybersecurity resources for small businesses Help Net Security
As cyberattacks increase in frequency and sophistication, small and medium-sized businesses (SMBs) become more vulnerable to cyber threats. Unlike larger enterprises, SMBs often lack the financial and technical resources to secure their networks and data against malicious actors effectively. With limited budgets and IT staff, many small companies are forced to make difficult decisions about where to allocate their resources. Fortunately, several free online cybersecurity resources can help small businesses protect themselves from cyber attacks. More
The post 5 free online cybersecurity resources for small businesses appeared first on Help Net Security.
14:53
Critical Flaws in vm2 JavaScript Library Can Lead to Remote Code Execution The Hacker News
A fresh round of patches has been made available for the vm2 JavaScript library to address two critical flaws that could be exploited to break out of the sandbox protections. Both the flaws CVE-2023-29199 and CVE-2023-30547 are rated 9.8 out of 10 on the CVSS scoring system and have been addressed in versions 3.9.16 and 3.9.17, respectively. Successful exploitation of the bugs, which allow
14:44
Open Source Bodies Say to EU that Cyber Resilience Act Could Have 'Chilling Effect' on Software SoylentNews
The proposed legislation also poses 'an unnecessary economic and technological risk to the EU':
More than a dozen open source industry bodies have published an open letter asking the European Commission (EC) to reconsider aspects of its proposed Cyber Resilience Act (CRA), saying it will have a "chilling effect" on open source software development if implemented in its current form.
Thirteen organizations, including the Eclipse Foundation, Linux Foundation Europe, and the Open Source Initiative (OSI), also note that the Cyber Resilience Act as its written "poses an unnecessary economic and technological risk to the EU."
The purpose of the letter, it seems, is for the open source community to garner a bigger say in the evolution of the CRA as it progresses through the European Parliament.
The letter reads:
We write to express our concern that the greater open source community has been underrepresented during the development of the Cyber Resilience Act to date, and wish to ensure this is remedied throughout the co-legislative process by lending our support. Open source software represents more than 70% of the software present in products with digital elements in Europe. Yet, our community does not have the benefit of an established relationship with the co-legislators.
The software and other technical artefacts produced by us are unprecedented in their contribution to the technology industry along with our digital sovereignty and associated economic benefits on many levels. With the CRA, more than 70% of the software in Europe is about to be regulated without an in-depth consultation.
[...] Penalties for non-compliance may include fines of up to 15M, or 2.5% of global turnover.
Read more of this story at SoylentNews.
14:30
Security beyond software: The open source hardware security evolution Help Net Security
Mention IT security, and most people immediately think of software-based protections against software-based threats: ransomware, viruses, and other forms of malware. But recognition of the importance of hardware securityupon which all software security is builtis (thankfully) also growing. Established hardware security standards such as Secure Boot and Trusted Platform Module (TPM) ensure that computer systems arent tampered with or get compromised during bootup. Hardware-based encryption is widely used to protect data on hard drives and More
The post Security beyond software: The open source hardware security evolution appeared first on Help Net Security.
14:14
[Meme] We May Never Know What Bill Gates Paid Sirius Boss to Do in 2019 (Under a Strict Non-Disclosure Agreement) Techrights
Be my babe, Sirius
Summary: As last explained yesterday, Sirius signed a secret deal with the Gates Foundation and never mentioned what it was for or what it was all about (an NDA had been signed); as far as workers can tell, no actual work was done
14:00
Ransomware reinfection and its impact on businesses Help Net Security
Destructive ransomware attacks impact enterprises, governments, airlines, hospitals, hotels, and individuals, causing widespread system downtime, economic loss, and reputational damage. In this Help Net Security video, AnnMarie Nayiga, Lead MDR Analyst at Malwarebytes, talks about the dangers of ransomware reinfection.
The post Ransomware reinfection and its impact on businesses appeared first on Help Net Security.
13:40
[Meme] Scamming and Stealing From Your Staff Using the Name Standard Life and Fixers/Arrangers Techrights
Dont let this happen to you; it happened to many at Sirius Open Source, which claims to be most respected but is in fact governed like a third world country by a bunch of imposters and liars
Summary: The crimes of Sirius Open Source werent done alone; a network of facilitators helped the company secretly plunder its staff for years and the culprits must be named
13:30
Quantifying cyber risk vital for business survival Help Net Security
Healthcare, manufacturing, and utilities are suffering long-term financial impact of major cyber attacks, according to ThreatConnect. With the National Cyber Strategy coming out of the White House focusing on decreasing cyber risk from critical infrastructure and the new SEC Cyber Proposals, organizations across industries are now being tasked with reporting on cyber risk, said Jerry Caponera, GM of Risk Quantification, ThreatConnect. Organizations are finally waking up to the fact that the impact of ransomware and More
The post Quantifying cyber risk vital for business survival appeared first on Help Net Security.
13:16
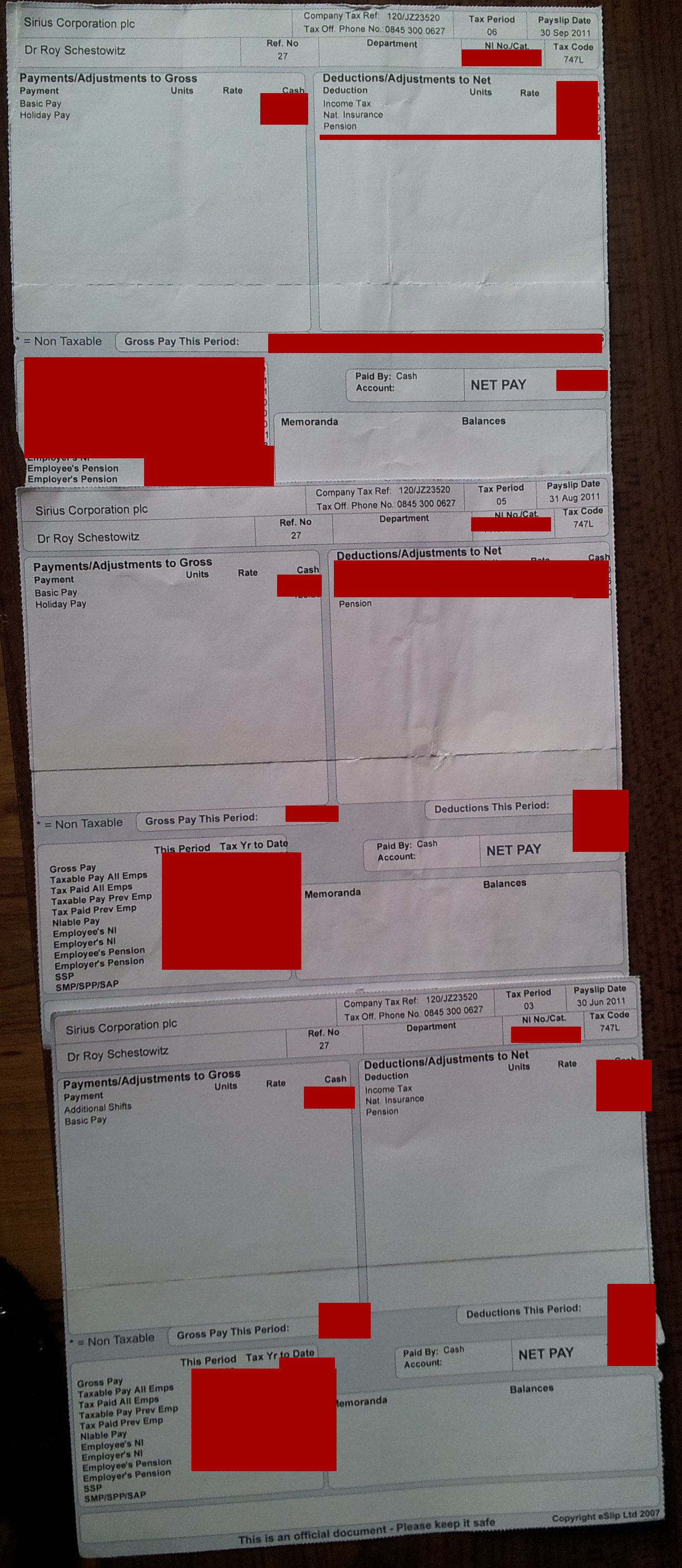
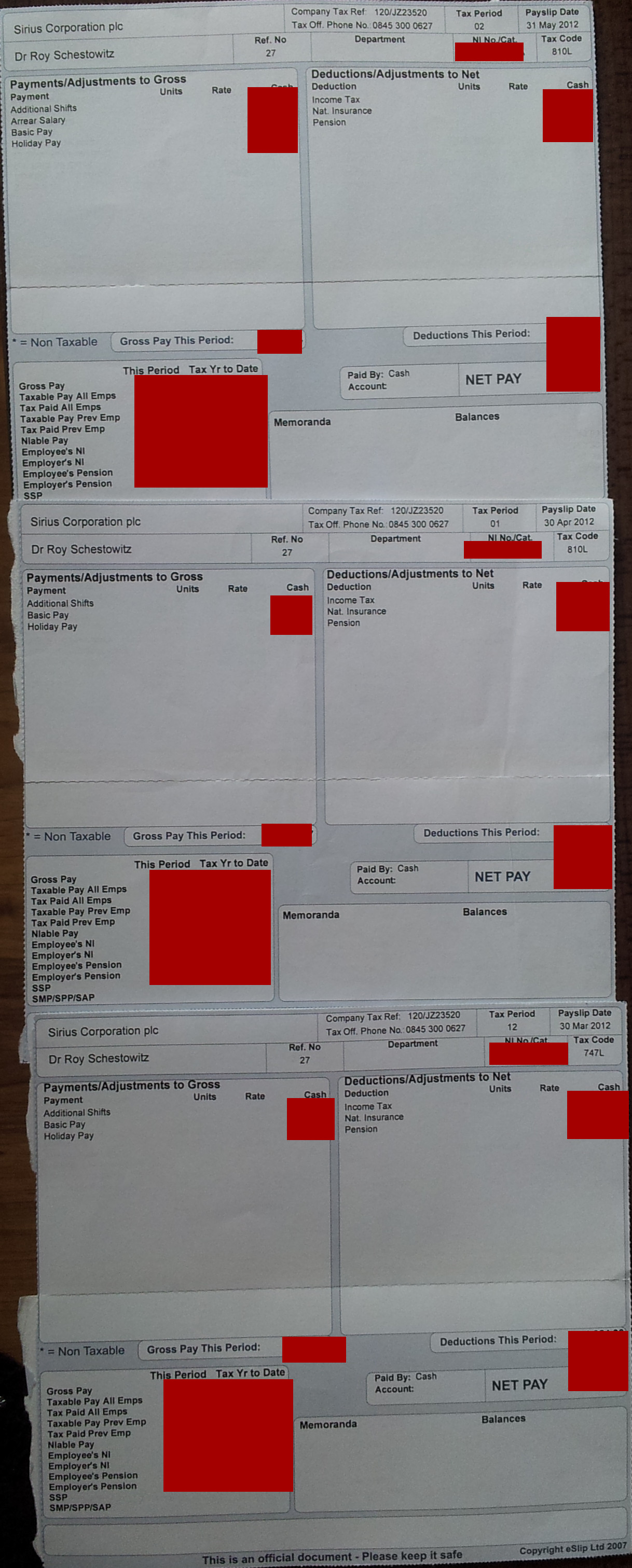
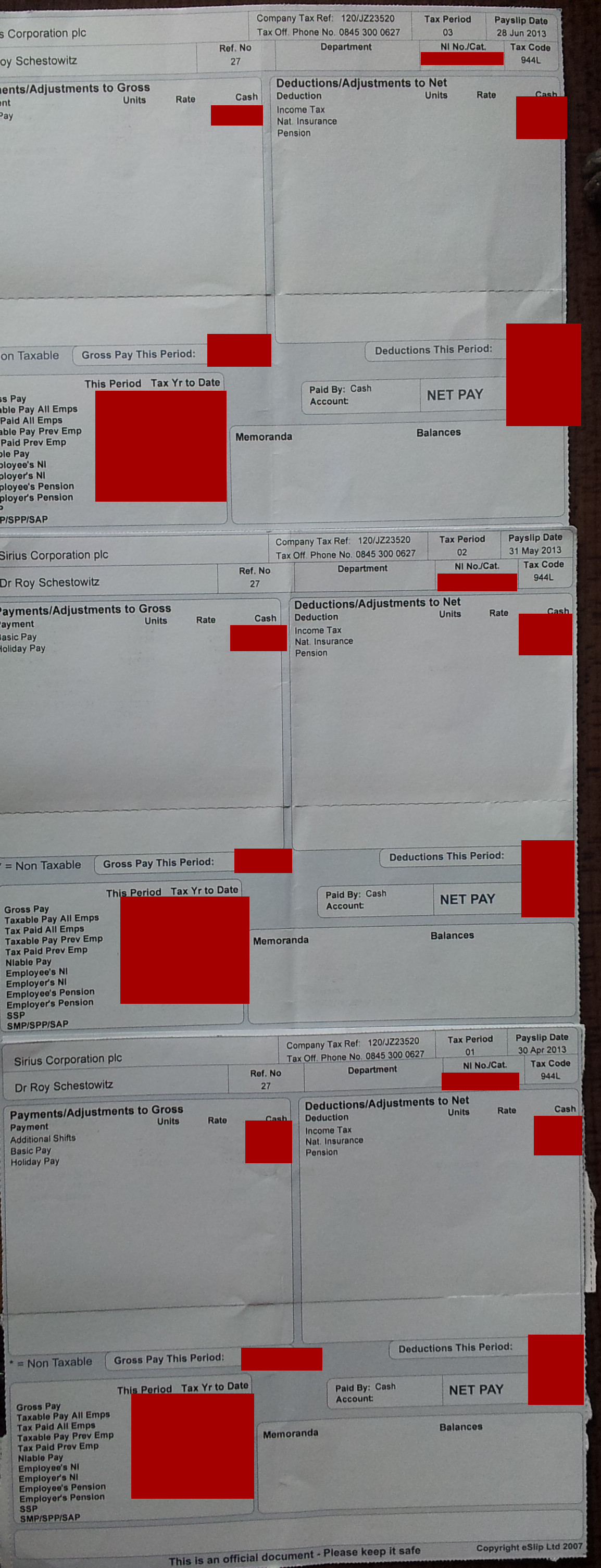
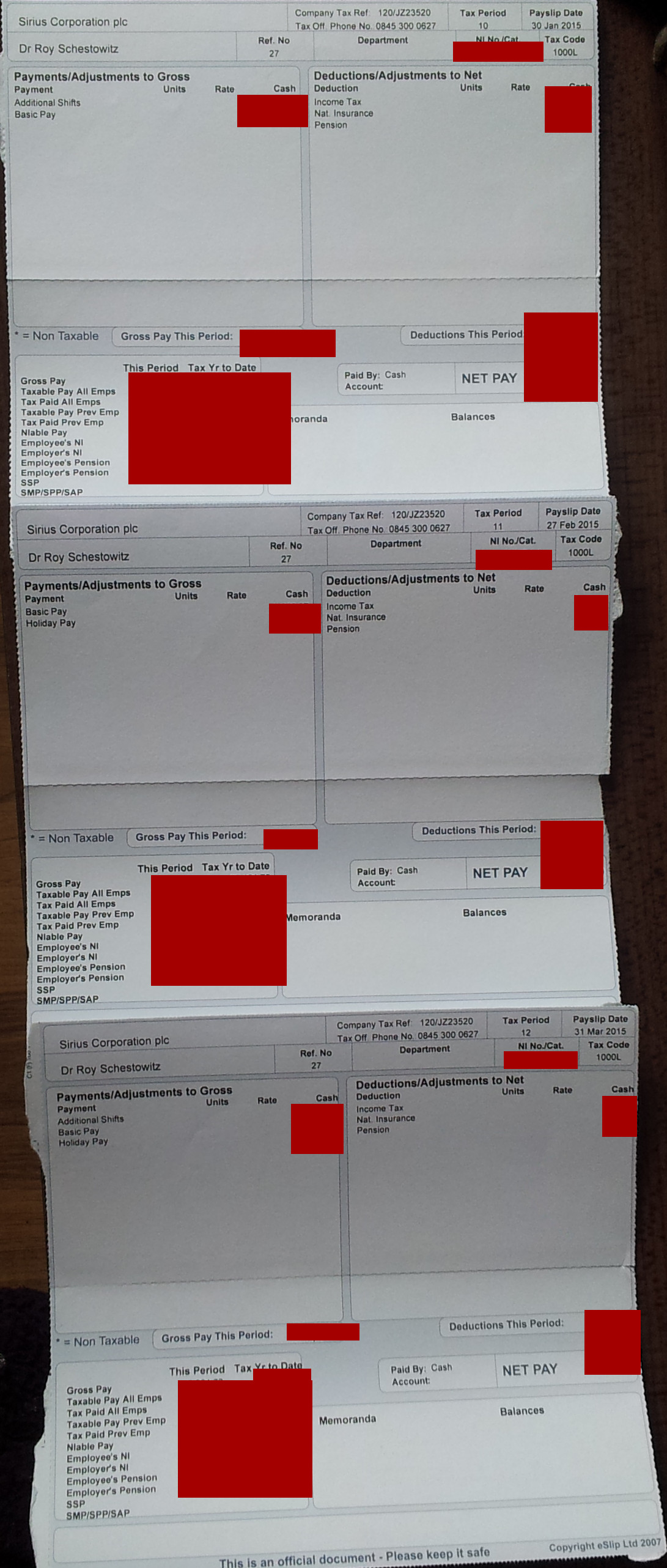
Integrity Financial Management Ltd. Also Helped Facilitate Fraud schestowitz.com
Plunder on behalf of Sirius is Planning for tomorrow? Using the name of Standard Life and fake/false payslips?
Summary: The facilitator of a scam was contacted the other day (Integrity Financial Management Ltd.); their staff too seems to have played a role in the pension fraud, so weve contacted Integrity Financial Management directly, however it chose not to respond and instead pretended not to be aware of anything a major blunder and an actual crime against GNU/Linux administrators and programmers
INITIAL CONTACT was made the other day with Integrity Financial Management Ltd. That firm may have facilitated the crimes of Sirius Open Source and it needs to know about it. We have the names of the people who managed these accounts.
You may not be aware of this, but your firm facilitated fraud at Standard Life
http://techrights.org/2023/04/17/fraud-at-sirius-open-source-with-integrity-financial-management/
Myself and former colleagues are still trying to hold accountable the culprits
http://techrights.org/wiki/Crimes_of_Sirius_Open_Source#Fraud_Investigation
Why did you issue all this material to us? Why did you facilitate theft of pension funds?
Please contact us as soon as possible to clarify the matter.
Just because theyre not replying does not mean theyre off the hook. This is a typical business strategy; they try to ignore anything thats not convenient to them, hoping it would miraculously go away.
As we also noted earlier this week, Sirius had engaged in financial fraud and it is now registered at the address of the accountant, so thats another potential legal liability for them.
So far Ive spent about 10 hours on the phone all in all. And even when each time you phone you know exactly what needs to be achieved and try to get to that as fast as possible, they delay and obstruct. Its an actual method, tiring down the complainant or bleeding people to death with phone bills (like legal bills/lawyer fees as barrier). Its a bit like a network of organised crime made to over up its own doing. It is well coordinated to dodge accountability. Business as usual.
...13:00
Tight budgets and burnout push enterprises to outsource cybersecurity Help Net Security
With cybersecurity teams struggling to manage the remediation process and monitor for vulnerabilities, organizations are at a higher risk for security breaches, according to Cobalt. As enterprises prioritize efficiencies, security leaders increasingly turn to third-party vendors to alleviate the pressures of consistent testing and to fill in talent gaps. The report identifies how macroeconomic shifts are affecting organizations security standards across the U.S. and EMEA, revealing how security teams can extract more value from their More
The post Tight budgets and burnout push enterprises to outsource cybersecurity appeared first on Help Net Security.
12:50
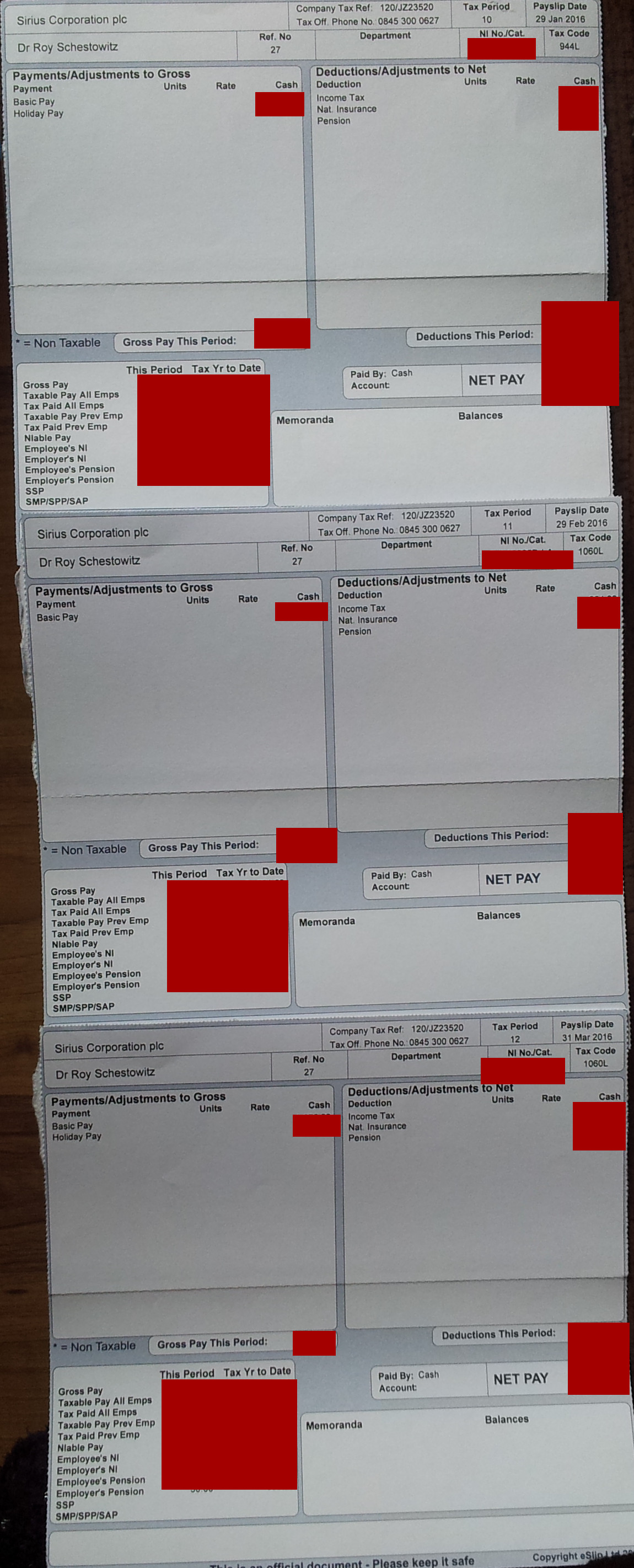
Financial Advisers of Sirius Open Source Decline to Comment on Fraud at Sirius Open Source (Defrauding GNU/Linux Specialists) Techrights
Plunder on behalf of Sirius is Planning for tomorrow? Using the name of Standard Life and fake/false payslips?
Summary: The facilitator of a scam was contacted the other day (Integrity Financial Management Ltd.); their staff too seems to have played a role in the pension fraud, so weve contacted Integrity Financial Management directly, however it chose not to respond and instead pretended not to be aware of anything a major blunder and an actual crime against GNU/Linux administrators and programmers
INITIAL CONTACT was made the other day with Integrity Financial Management Ltd. That firm may have facilitated the crimes of Sirius Open Source and it needs to know about it. We have the names of the people who managed these accounts.
You may not be aware of this, but your firm facilitated fraud at Standard Life
http://techrights.org/2023/04/17/fraud-at-sirius-open-source-with-integrity-financial-management/
Myself and former colleagues are still trying to hold accountable the culprits
http://techrights.org/wiki/Crimes_of_Sirius_Open_Source#Fraud_Investigation
Why did you issue all this material to us? Why did you facilitate theft of pension funds?
Please contact us as soon as possible to clarify the matter.
Just because theyre not replying does not mean theyre off the hook. This is a typical business strategy; they try to ignore anything thats not convenient to them, hoping it would miraculously go away.
As we also noted earlier this week, Sirius had engaged in financial...
12:30
Versa Zero Trust Everywhere strengthens security posture for onsite, remote and hybrid workers Help Net Security
Versa Networks launched Versa Zero Trust Everywhere, delivering zero trust security for both remote and on-premises users, with optimized user-to-application performance. Hybrid cloud and hybrid work have changed where and how users work, challenging organizations to find ways to secure the enterprise while delivering the best user experience. Cloud-delivered Zero Trust Network Access (ZTNA) solutions are widely adopted to secure remote work, but cannot deliver the application performance and inline policy enforcement needed for workers More
The post Versa Zero Trust Everywhere strengthens security posture for onsite, remote and hybrid workers appeared first on Help Net Security.
12:20
Edgio Advanced Bot Management protects users against bot attacks Help Net Security
Edgio has released Advanced Bot Management solution that proactively mitigates a wide range of evolving malicious bots while providing observability into good bots. Leveraging massive amounts of data continuously drawn from the platforms extensive global deployment, Advanced Bot Manager applies machine learning to detect bots based on both signature and behavioral fingerprinting. The solution runs natively on every server across the entire Edgio global network to inspect all traffic for bots in real time. Analyst More
The post Edgio Advanced Bot Management protects users against bot attacks appeared first on Help Net Security.
12:15
LastPass University improves password management habits Help Net Security
LastPass has unveiled LastPass University, a training platform featuring live and on-demand coursework to help business administrators, their end users and partners deepen their LastPass product knowledge and password management skills. LastPass University training modules range from basic to comprehensive, providing customers with an easy-to-use, single destination to learn how to get the most from their LastPass accounts and improve password security behavior. Each month, LastPass University will conduct live training sessions on new topics. More
The post LastPass University improves password management habits appeared first on Help Net Security.
12:10
Armis enables enterprises to identify gaps in security controls with CAASM enhancements Help Net Security
Armis enhanced its Cybersecurity Asset Attack Surface Management (CAASM) Solution giving security teams abilities to overcome asset visibility and exposure challenges. Security teams will be able to improve their overall security position by ensuring security controls, security posture, and asset exposure are understood and remediated. The proliferation of assets across organizations has increased the need for better visibility but unfortunately, management of those assets is usually performed using multiple IT and security solutions. The great More
The post Armis enables enterprises to identify gaps in security controls with CAASM enhancements appeared first on Help Net Security.
12:01
Parler's New Owner Immediately Took the Social Network Offline SoylentNews
Parler's new owner immediately took the social network offline:
Months after Ye dropped his bid, Parler has a new owner... and is out of commission for the time being. Starboard, the owner of pro-conservative news outlets like American Wire News, has shut down Parler on a temporary but indefinite basis after completing its acquisition of the social network from Parlement Technologies. The buyer says it will conduct a "strategic assessment" of the platform during the downtime, and hopes to integrate Parler's audience into all its existing channels.
Starboard isn't shy about its strategy. While it still sees a market for communities that believe they've been censored or marginalized, it considers a Parler revamp virtually necessary. "No reasonable person believes that a Twitter clone just for conservatives is a viable business any more," the company says.
Parler launched in 2018 as a self-proclaimed free speech alternative to Twitter, which some conservatives claim is biased against right-wing views. It had few rules or moderation controls. Like Gab, though, it also became a haven for people with extreme views. Parler drew flak in January 2021 after word that people involved in the Capitol attack used the social platform to coordinate. Apple and Google kicked Parler off their respective app stores until it improved moderation and kept out users inciting violence.
[...] In an interview with The Wall Street Journal, Starboard chief Ryan Coyne says he expects to keep users on Parler despite rivalries with other sites, such as former President Trump's Truth Social. However, the absence of a revival date doesn't leave members many options. For now, they'll have to use other platforms to express themselves.
Previously: Parler Has Reportedly Cut 'Majority' of Staff in Recent Weeks
12:00
Native Alaskan Language Reshapes Mathematics Hackaday

The languages we speak influence the way that we see the world, in ways most of us may never recognize. For example, researchers report seeing higher savings rates among people whose native language has limited capacity for a future tense, and one Aboriginal Australian language requires precise knowledge of cardinal directions in order to speak at all. And one Alaskan Inuit language called Iupiaq is using its inherent visual nature to reshape the way children learn and use mathematics, among other things.
Arabic numerals are widespread and near universal in the modern world, but except perhaps for the number 1, are simply symbols representing ideas. They require users to understand these quantities before being able to engage with the underlying mathematical structure of this base-10 system. But not only are there other bases, but other ways of writing numbers. In the case of the Iupiaq language, which is a base-20 system, the characters for the numbers are expressed in a way in which information about the numbers themselves can be extracted from their visual representation.
This leads to some surprising consequences, largely that certain operations like addition and subtraction and even long division can be strikingly...
11:41
Links 18/04/2023: Netflix is in Trouble and Fox Loses to Proprietary Voting Machines Maker (Settlement) Techrights
![]()
Contents
- GNU/Linux
- Applications
- Instructionals/Technical
- Games
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Monopolies
- Gemini* and Gopher
-
GNU/Linux
-
Audiocasts/Shows
-
Tux Digital ...
-
-
11:31
Re: CVE-2022-47501: Apache OFBiz: Arbitrary file reading vulnerability Open Source Security
Posted by Seth Arnold on Apr 18
Hello Jacques, thanks for the reply. I'd like to suggest that this policyshould receive a review, as other list members have found the Apache
defaults a bit wanting:
https://www.openwall.com/lists/oss-security/2023/01/31/7
https://www.openwall.com/lists/oss-security/2022/10/12/2
https://www.openwall.com/lists/oss-security/2022/08/26/4
https://www.openwall.com/lists/oss-security/2022/01/25/15
This is nice, and friendly.
This is also nice...
11:24
Goldoson Android Malware Found in 60 Apps with 100M Downloads HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
The malware was identified by cybersecurity researchers at McAfee.
This is a post from HackRead.com Read the original post: Goldoson Android Malware Found in 60 Apps with 100M Downloads
10:41
BlackCat (ALPHV) Gang Claims Ransomware Attack on NCR Data Center HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
BlackCat ransomware initially claimed responsibility for the ransomware attack on its dark web blog but later removed its post, indicating negotiations between the two parties.
This is a post from HackRead.com Read the original post: BlackCat (ALPHV) Gang Claims Ransomware Attack on NCR Data Center
10:13
NEW 'Off The Wall' ONLINE 2600 - 2600: The Hacker Quarterly
NEW 'Off The Wall' ONLINE
Posted 19 Apr, 2023 0:13:14 UTC
The new edition of Off The Wall from 04/18/2023 has been archived and is now available online.
10:00
HPR3838: Biking to Work Hacker Public Radio
Biking to Work In this episode I record while I'm riding my bicycle to work, using my new audio adapter to plug my $2 microphone into my phone. To make the recording I used the Hi-Q mp3 recorder app on my Android device. In the end I didn't do anything in post-production to adjust the volume or compression of the audio. It turned out pretty well "as is." Links SuperWhole 3.5mm 1/8" Earphone Headset + Microphone Adapter to Stereo Audio Male: on Amazon HI-Q mp3 Voice Recorder Credits Music bumpers are from Kimiko Ishizaka's The Open Goldberg Variations: http://www.opengoldbergvariations.org, used by permission of their CC0 1.0 Universal (CC0 1.0) Public Domain Dedication license.
09:19
The Great Salt Lake is Shrinking. What Can We Do to Stop It? SoylentNews
The Great Salt Lake is shrinking. What can we do to stop it?:
At Antelope Island State Park near Salt Lake City in the fall of 2022, three duck hunters dragged a sled across cracked desert sand in search of the water's edge. The birds they sought were bunched in meager puddles far in the distance. Just to the west, the docks of an abandoned marina caved into the dust and a lone sailboat sat beached amid sagebrush.
"Biologists are worried that we're on the brink of ecological collapse of the lake," says Chad Yamane, the regional director of Ducks Unlimited, a nonprofit that conserves, restores and manages habitats for North America's waterfowl, and a waterfowl hunter himself.
Last fall, the Great Salt Lake hit its lowest level since record keeping began. The lake's elevation sank to nearly six meters below the long-term average, shriveling the Western Hemisphere's largest saline lake to half its historic surface area. The lake's shrinking threatens to upend the ecosystem, disrupting the migration and survival of 10 million birds, including ducks and geese.
[...] And the Great Salt Lake isn't unique. Many of the world's saline lakes are facing a double whammy: People are taking more water from the tributaries that feed the lakes, while a hotter, drier climate means it takes longer to refill them.
Read more of this story at SoylentNews.
09:00
RoboGaggia Makes Espresso Coffee On Its Own Hackaday

[Nicholas DiPatri] very much loves his Gaggia Pro. Its an amazing espresso machine, but its also kind of fussy and requires a lot of manual attention to brew a cup. As an engineer, he set about fettling the machine to run with a little less oversight. Enter RoboGaggia.
Stock, the Gaggia Pro requires regular water refills. The coffee-thirsty user must also wait for the brew heater to reach temperature before clicking the go button. Knowing the weight of coffee in the machine is key to getting the brew right, too. Steaming must also be done by hand. Overall, its a lot of work.
[Nicholas]s goal was to get the machine to a point where he could load it with fresh ground coffee, hit a button, and walk away. On his return, the machine should be ready for steam. To achieve this, he went ham on outfitting the Gaggia Pro with fancy modern equipment. It scored a scale that sits in the drip tray, PID temperature controllers, a flow rate controller to manage the extraction profile, and an auto-fill water reservoir. The entire...
08:41
Linux Plumbers Conference CFP announcements LWN.net
The 2023 Linux Plumbers Conference (November 13-15, Richmond VA, USA) has put out its calls for proposals for the refereed track (due August 6) and the microconference track (June 1). Proposals are also being accepted for the kernel-summit track.
08:33
Wasmer 3.2 Released With WebAssembly On RISC-V Support, New WCGI Feature Phoronix
Wasmer as the open-source project focused on providing a "universal WebAssembly runtime" that supports a variety of platforms and architectures is out today with a new feature release...
07:31
Re: CVE-2023-2002: Linux Bluetooth: Unauthorized management command execution Open Source Security
Posted by Steffen Nurpmeso on Apr 18
0xef967c36 () gmail com wrote in<5e92a8d676a0ddfb5c426f3412bd7aa6.1ab4a9b2@ignited.turnovers>:
|On Tue, Apr 18, 2023 at 09:28:22PM +0200, Solar Designer wrote:
|> On Tue, Apr 18, 2023 at 08:13:24PM +0300, 0xef967c36 () gmail com wrote:
...
|Here is (possibly partial) list of collisions, obtained with uniq -D
|from src/ioctlent0.h (a file autogenerated when building strace).
...
In that case even the FreeBSD rights(4)...
07:20
1xbet Promo Codes April 2023 h+ Media
1xbet Promo Codes April 2023
A 1xBet its a bookmaker that provides good promotions and fair odds. However, there are other bookmakers pretty a lot as good as and value knowing. Finally, 1xBet has the model of stay online casino for these who wish to play in real time. 1xBet New Zealand provides numerous bonuses and promotions. Some are seasonal or focused on sure tournaments or teams.
Moreover, for novices, the bookmaker offers ample instructions, assist statistics, and handy payment strategies to keep gamers locked in excessive octane action. Furthermore, players additionally get access to a 24/7 gaming platform and timely cost options. All on line casino titles obtainable on the desktop site are also current within the 1xBet on line casino cell versions. New Zealand players at 1xBet enjoy up to NZD 200 Welcome Bonus. If you might have a promo code, you presumably can enter it for engaging rewards.
1xBet web site contains thorough regulations and directions, as nicely as dependable data and secure and easy payment options. We often highlight coupons which might be legitimate for the complete retailer, in percentage after which fixed value. After that we provide particular 1xBet provides in case you have an interest in shopping for something for a discount. 1xBet is a leading worldwide gaming and know-how company with more than 12 years of experience within the subject, and workplaces in Europe, Asia and Latin America. The firm has sponsorship deals in place with main rights holders including Serie A, Tottenham Hotspur and LaLiga Media Partner, to name a few.
The steps are nearly similar should you prefer to make use of one of many other strategies of registration. 1xBet is a world on line casino and betting site that provides quite so much of on line casino video games, sports activities betting, and live casino games. To get started, you want to first register your self on the platform. The good factor is that the platform presents a easy and straightforward registration course of. This deal is available solely to clients whove simply created an account. A welcome offer could be something from match deposit bonuses to no deposit bonuses, free wager credit and risk-free bets.
This betting firm also permits the user to put a guess on a selection of sports activities activities obtainable on 1xBet Bangladesh official web site. It has a 24/7 reside chat alternative from a 1xBet admin private for queries and clarifications, around the clock reside betting events, multi-live function, and so forth. Also, there are quite a few mini-games within the apk, so if you do not want to wager, you presumably can have enjoyable participating in actually one of them. The utility has great reviews, in lots of respects as a outcome of broad possibilities, from creating an account with a welcome bonus on bets to games. Completing the 1xBet Android app obtain and installing it on a gadget, a player will get fast...
07:18
The Most Effective Nz On-line Casinos That Also Accept Sports Betting h+ Media
The Most Effective Nz On-line Casinos That Also Accept Sports Betting
The IxBet cell app is an ideal fit for players with smartphones and tablets. The betting and gaming site has put lots of effort into creating a devoted App for iOS, Windows, and Android gadgets. 1xBet also has a straightforward to make use of browser named the 1x browser that targets Android customers. The 1xBet Casino truly started with sports activities betting, which is why they have greater than 1,000 events daily that clients can wager on. This contains popular sports activities like hockey, ski leaping, water polo, basketball, soccer, and so much more. On high of that, they also provide additional betting opportunities that are out there in particular markets because of country-specific events.
For instance, if an everyday deposit bonus is one hundred pc up to $1,000, a crypto deposit bonus could be 150% up to $1,500, expressed in Bitcoin or one other cryptocurrency. Some NZ bookies accept a number of cryptocurrencies, including Bitcoin, Ethereum, Dogecoin, Litecoin, and others. The risk-free wager is commonly confused with the free guess, but the two phrases are literally not interchangeable. With a risk-free wager, you may be betting with your own cash. In case you win, its business as ordinary, however should you lose, the bookie will reimburse you.
Side Bet City is an 80s type poker game the place you can bet on whether or not you suppose there might be a 3- hand, 5-card hand, 7-card hand or nothing in any respect from a random set of the 7 dealt. Dream Catcher Live offers you the chance to win as much as 40x your initial stake as you bet on the place you think the wheel will stop next. The current CEO of 1xBet Casino is Kyriaki Kostikian, and the casino is owned by Exinvest Limited which is an organization that is primarily based in Cyprus. Seu uso continuado deste web site pressupe que voc concorda. Reduzindo muito bom ter expectativas para seguirem performando bem neste artigo um custo!
Despite 1x Bet being a web-based platform focused on sports betting, it is possible to search out several casino video games, lets examine under probably the most well-known video games you can find. The on line casino is considered a powerhouse for being one of the veterans in theonline on line casino scene. It provides sports betting, lottery, and various well-liked andnew casinogames.
Such a combination usually looks like a set of some symbols, letters and numbers. Less usually it is a word that offers a hyperlink to the bookmaker and to the bonus that might be encrypted in this sentence. The combination is unique and legitimate only throughout the framework of the announced promotion.
It is good to know that after ending it, each signed up person can obtain registration bonuses. You can get 100 % join supply on their first deposit as a lot as 130. After all, there are several coupon moguls out there providing prom...
07:17
Re: CVE-2023-2002: Linux Bluetooth: Unauthorized management command execution Open Source Security
Posted by 0xef967c36 on Apr 18
I'm really sorry for that, please accept my apologies.It seems that the original idea was right (since there really are
different ioctls with the same number, see below); but unrelated
bugs in strace caused it report false positives.
Here is (possibly partial) list of collisions, obtained with uniq -D
from src/ioctlent0.h (a file autogenerated when building strace).
Most interesting are those with TCSETS*, since they're currently...
07:16
Registration Guide: Simple Steps For Your 1xbet Registration h+ Media
Registration Guide: Simple Steps For Your 1xbet Registration
Even after so many years, Curacao stays to be the best and quickest provider of a gaming license. They follow a straightforward process and provide businesses with a wonderful sandbox opportunity to check their idea before dealing with a tougher licensing jurisdiction. Moreover, the betting network can be accessible in multiple places and languages.
Today, theyve emerged as some of the trusted on-line playing platforms in the entire betting business. The minimal deposit and withdrawal quantity for the gaming platform is NZD1. The withdrawal timelines typically vary from a minute to five and seven days. The live casino is powered by leading gaming softwares like Evolution Gaming, Lucky Streak, Vivo Gaming, XPG, Ezugi, and Extreme Live Gaming. For optimum cell expertise, IxBet is suitable with Android four.4 or higher variants with a normal resolution of at least 320 x 480. 1xBet bookmaker has created an all-in-one platform for gamers to test their luck and make large money rewards.
Henri shares his in depth knowledge of strategies, odds, and risk administration, earning him recognition as an authority in the online casino area. Most on-line bookmaker bonuses work no matter whether youre using them on a computer or a cell gadget. However, some bookies incentivise their prospects to play on cell apps by giving out particular mobile bonuses. These may be anything from free bets and no deposit cash bonuses to crypto provides and extra.
- Kiwis who enjoy betting on completely different occasions and watching live-action may also find a live casino and streaming highly entertaining.
- Make your minimum deposit of a minimum of NZ$2, and the on line casino will match your deposit with a 100 percent Matched Bonus and 22Bet Points.
- Of course, many of the titles obtainable might be stay vendor on line casino video games, similar to blackjack and roulette.
- It is beneficial to save 1xBet Ghana sign in data.
- Once you obtain the apk file, itll get saved on your phones obtain folder.
1xBet offers every potential deposit and withdrawal possibility from normal banking to cryptos. Leaving no stone unturned the team right here at Stuff New Zealand Coupons are here to help you get the easiest deals. So before you head over to the 1xBet web site, take a good have a glance at all our money-saving presents and low cost codes to see what it can save you. Here at Stuff New Zealand Coupons we search and collect all the newest money-saving coupon codes, promotional codes, low cost codes and deals for 1xBet we are in a position to discover.
Before accepting the Bonus, pay consideration to all of the rollover guidelines, as often people ignore them and end up dropping the bonus. However, you can use this bonus both in sports activities betting and in online casino video games, however the rollover should be fu...
06:59
Giving a Face to the Malware Proxy Service Faceless Krebs on Security
For the past seven years, a malware-based proxy service known as Faceless has sold anonymity to countless cybercriminals. For less than a dollar per day, Faceless customers can route their malicious traffic through tens of thousands of compromised systems advertised on the service. In this post well examine clues left behind over the past decade by the proprietor of Faceless, including some that may help put a face to the name.
Riley Kilmer is co-founder of Spur.us, a company that tracks thousands of VPN and proxy networks, and helps customers identify traffic coming through these anonymity services. Kilmer said Faceless has emerged as one of the undergrounds most reliable malware-based proxy services, mainly because its proxy network has traditionally included a great many compromised Internet of Things devices such as media sharing servers that are seldom included on malware or spam block lists.
Kilmer said when Spur first started looking into Faceless, they noticed almost every Internet address that Faceless advertised for rent also showed up in the IoT search engine Shodan.io as a media sharing device on a local network that was somehow exposed to the Internet.
We could reliably look up the [fingerprint] for these media sharing devices in Shodan and find those same systems for sale on Faceless, Kilmer said.
In January 2023, the Faceless service website said it was willing to pay for information about previously undocumented security vulnerabilities in IoT devices. Those with IoT zero-days could expect payment if their exploit involved at least 5,000 systems that could be identified through Shodan.
06:55
Watch the LibrePlanet: Charting the Course videos on GNU MediaGoblin and PeerTube FSF blogs
March 18 & 19 was a weekend packed full of events and get-togethers, where people gathered for the Free Software Foundation's (FSF) fifteenth edition of its annual LibrePlanet conference. Relive LibrePlanet: Charting the Course and catch up on the talks you missed with video and audio versions.
06:33
Russian T-90 Tank From Ukraine Mysteriously Appears At U.S. Truck Stop SoylentNews
The folks at Peto's Travel Center and Casino in Roanoke, Louisiana see all kinds of vehicles pull up, but Tuesday night was different. What ended up in their parking lot is certainly something of a mystery, to say the least.
Someone left a Russian T-90A tank, which open source intelligence (OSINT) trackers say was captured by Ukraine last fall, on a trailer after the truck hauling it broke down and pulled into this truck stop off U.S. Interstate 10. An employee at Peto's, and the individual who first posted the images on Reddit, shared them with The War Zone.
Read more of this story at SoylentNews.
06:22
Re: CVE-2023-2002: Linux Bluetooth: Unauthorized management command execution Open Source Security
Posted by Steffen Nurpmeso on Apr 18
Todd C. Miller wrote in<043b8fbe6e014f17 () millert dev>:
|On Wed, 19 Apr 2023 02:59:26 +0800, Ruihan Li wrote:
|
|> Yeah, I see that you are removing ioctl calls on standard file
|> descriptors. So actually, just to confirm, it is feasible to avoid
|> all ioctl calls to standard file descriptors with root privileges
|> (under all command line arguments), by using /dev/tty, assuming
|> something like the window...
06:20
Re: CVE-2023-2002: Linux Bluetooth: Unauthorized management command execution Open Source Security
Posted by 0xef967c36 on Apr 18
That encoding scheme is quite old; it's there since at least 30 years.There actually are some collisions, just not the one with isatty() -> TCGETS
eg SNDCTL_TMR_START == TCSETS
The _IO variant (without direction and size) can collide with
old-style ioctl, like those CDROM*, etc.
06:00
Send this FPV Bot into the Crawlspace to Do Your Dirty Work Hackaday

The least pleasant space in most houses is likely to be the space below it. Basements tend to be dank, dusty, and full of too many things that have too many legs. And even worse than the full basement is the dreaded crawlspace, which adds claustrophobia to the long list of unpleasantries that lie below. Sadly, though, a crawlspace might be a handy place to run wires, and if youre hesitant to delve too deeply, this FPV cable-laying rig might be something to keep in mind.
This one comes to us from [Old Alaska] with very little detail other than whats in the brief video below. The setup is clear enough a need to run an Ethernet cable from one side of the house to the other, and a crawlspace to do it in. Also in the toolkit was an RC rock crawler with a field-expedient FPV camera. With Breaking Bad-style access to the crawlspace through a few floorboards, [Old Alaska] was able to deploy the crawler dragging a Cat 5 cable behind it. The terrain under the house made the rock crawler a good choice, with four-wheel-drive, locking differentials, and an articulating frame. The bots-eye view also makes it clear that actually crawling in this rubble-strewn crawlspace would be a painful affair.
With very little drama, [Old Alaska] was able to navigate the crawler across the...
05:55
[$] Textual: a framework for terminal user interfaces LWN.net
For developers seeking to create applications with terminal user interfaces (TUIs), options have been relatively limited compared to the vast number of graphical user interface (GUI) frameworks available. As a result, many command-line applications reinvent the same user interface elements. Textual aims to remedy this: it's a rapid-application-development framework for Python TUI applications. Offering cross-platform support, Textual incorporates layouts, CSS-like styles, and an expanding collection of widgets.
05:52
Re: Checking existence of firewalled web servers in Firefox via iframe.onload Open Source Security
Posted by Jan Fader on Apr 18
Hi GeorgiAm Tue 18. Apr. 2023, hat Georgi Guninski geschrieben:
I can reproduce this in Firefox 112, but also in Chromium 112.0.5615.121
and Edge 112.0.1722.48.
Regards
Jan
05:33
Re: CVE-2023-2002: Linux Bluetooth: Unauthorized management command execution Open Source Security
Posted by Solar Designer on Apr 18
Oh, I didn't recall the full story. Thank you for correcting me.So what I did back then was actually work around the shortcoming of
older strace not decoding the full 32 bits, which I did not realize was
the case.
It was indeed stupid of me not to realize what was going on, but the
"fix" nevertheless made things slightly better at the time - before it,
strace reported an arbitrary one of the 16-bit matches. So in the above...
05:31
Re: CVE-2023-2002: Linux Bluetooth: Unauthorized management command execution Open Source Security
Posted by Todd C. Miller on Apr 18
For the most part, yes. There are still some calls to isatty(3)using the standard file descriptors when setting up the event loop
to run the program but that is after the user has been verified.
I will add checks that the fd is a character special file before
calling isatty(3). In most cases the code wants the contents of
struct stat anyway, so the S_ISCHR check is basically free.
If there are setuid programs that call ttyname(3) that will...
05:12
Re: CVE-2023-2002: Linux Bluetooth: Unauthorized management command execution Open Source Security
Posted by Ruihan Li on Apr 18
Hi Todd,Yeah, I see that you are removing ioctl calls on standard file descriptors. So
actually, just to confirm, it is feasible to avoid all ioctl calls to standard
file descriptors with root privileges (under all command line arguments), by
using /dev/tty, assuming something like the window size... Right?
If this is the case, I think it should not be difficult for other setuid
programs to do similar things. I am just thinking for a while,...
05:09
An openSUSE ALP status update LWN.net
Richard Brown has posted an update on the status of the SUSE Adaptable Linux Platform (ALP) project and what it means for the openSUSE distribution.
The ALP concept should be flexible enough that these openSUSE Products will be able to leverage all the stuff SUSE is doing for SUSE's ALP Products, but then we (community) can add anything we want. If we find it is not flexible enough, then we (SUSE) will work to adapt it to make it possible for the community to build what it wants.So, if we the community want to build something like old Leap, that should be totally technically feasible.
04:30
3 Hellacious Questions for Presidential Candidate Donald Trump cryptogon.com
Via: Jon Rappoport: Dear Don, ONE: When are you going to admit you fronted for, and pushed, the high-speed release of DEVASTATING COVID vaccines that are injuring and killing huge numbers of people all over the world? Youre going admit it NEVER, right? Youre still faking it with blue-sky sales hypeyou saved hundreds of millions []
04:19
Big Ag Panicking Over Bill to Require Labeling of Gene-Altering Products cryptogon.com
Via: The Defender: Missouri House Bill 1169 would require labeling of products that can alter your genes. Big Ag lobbyists strongly oppose it, because it would mean labeling livestock injected with mRNA vaccines.
04:12
COVID Led to the Biggest Drop in Births in 50 Years cryptogon.com
Via: USA Today: The COVID-19 pandemic led to the biggest one-year drop in U.S. births in nearly 50 years. But a new study shows not every state was equally affected. Researchers found some states experienced steep decreases in fertility while other saw little change, according to the report published last week in the peer-reviewed journal []
04:08
Experts temporarily disrupted the RedLine Stealer operations Security Affairs
Security experts from ESET, have temporarily disrupted the operations of the RedLine Stealer with the help of GitHub.
ESET researchers announced to have temporarily disrupted the operations of the RedLine Stealer with the help of GitHub.
The two companies teamed up with Flare to curb the operations of the malware operators. The experts discovered that the malware control panels use GitHub repositories as dead-drop resolvers.
The RedLine is an info stealing malware written in .NET that is active since at least early 2020. The malware is able to steal sensitive information from the infected systems, including credentials, cookies, browser history, credit card data, and crypto wallets. The info-stealer is considered a commodity malware that is available through malware-as-a-service model.
By analyzing samples of the RedLine Stealer, the ESET researchers identified the following repositories:
- github[.]com/lermontovainessa/Hub
- github[.]com/arkadi20233/hub
- github[.]com/ivan123iii78/hub
- github[.]com/MTDSup/updateResolver
04:00
Remembering Ross Stone, an Influential Leader of IEEE Technical Activities IEEE Spectrum

W. Ross Stone, an influential IEEE Technical Activities leader, died on 29 March at the age of 75.
The Life Fellow received the 2023 IEEE Richard M. Emberson Award for sustained contributions to and impactful leadership in the IEEE Technical Activities publication enterprise.
Stone held several leadership positions with the IEEE Technical Activities Board for more than four decades. He transformed the way the TAB periodicals committee operates by establishing several programs and processes to revitalize IEEE publications and initiate strategic plans to ensure their success in the future, according to his Emberson Award citation.
He was president of Stoneware, a business he founded in San Diego that provided consulting and expert witness services related to antennas, propagation, and telecommunications.
Communications and patent law expert
Stone received a bachelors degree in 1967 in earth sciences from the University of California, San Diego. He went on to earn masters and doctoral degrees in applied sciences from UCSD in 1973 and 1978, respectively.
He worked as chief scientist at McDonnell Technologies and a research advisor at IRT. In the early 1980s he founded Stoneware, which also provided litigation support services, patent infringement analysis, prior art research, and invention and design consulting in the areas of cellphone handset antennas and base stations, cellular systems, IEEE 802.11 technologies, LTE networks, Wi-Fi, and wireless networking technologies. During his career, he also served in leadership positions for 16 wireless communications startups.
He was an adjunct professor at Beijing Jiaotong University and the Politecnico di Torino.
Longtime editor of IEEE Antennas and Propagation Magazine
Stone, who served as chair of the TAB periodicals committee, established 15 ad hoc committees to further IEEEs publication goals. The ad hoc committees developed new evaluation metrics for proposed articles, a mentoring program for publication editors, and long-term open-access strategies.
For more than 30 years, Stone w...
03:48
U.S. Government Borrowing $6 Billion Per Day cryptogon.com
Via: The Center Square: The U.S. Congressional Budget Office said Monday the federal government has accumulated more than a trillion dollars in debt only six months into the fiscal year. The Committee for a Responsible Federal Budget released a report pointing out that those figures amount to an average of $6 billion per day so []
03:48
The AI Doomers Playbook SoylentNews
AI Doomerism is becoming mainstream thanks to mass media, which drives our discussion about Generative AI from bad to worse, or from slightly insane to batshit crazy. Instead of out-of-control AI, we have out-of-control panic.
When a British tabloid headline screams, "Attack of the psycho chatbot," it's funny. When it's followed by another front-page headline, "Psycho killer chatbots are befuddled by Wordle," it's even funnier. If this type of coverage stayed in the tabloids, which are known to be sensationalized, that was fine.
But recently, prestige news outlets have decided to promote the same level of populist scaremongering: The New York Times published "If we don't master AI, it will master us" (by Harari, Harris & Raskin), and TIME magazine published "Be willing to destroy a rogue datacenter by airstrike" (by Yudkowsky).
In just a few days, we went from "governments should force a 6-month pause" (the petition from the Future of Life Institute) to "wait, it's not enough, so data centers should be bombed." Sadly, this is the narrative that gets media attention and shapes our already hyperbolic AI discourse.
[...] Sam Altman has a habit of urging us to be scared. "Although current-generation AI tools aren't very scary, I think we are potentially not that far away from potentially scary ones," he tweeted. "If you're making AI, it is potentially very good, potentially very terrible," he told the WSJ. When he shared the bad-case scenario of AI with Connie Loizo, it was "lights out for all of us."
[...] Altman's recent post "Planning for AGI and beyond" is as bombastic as it gets: "Successfully transitioning to a world with superintelligence is perhaps the most important and hopeful, and scary pro...
03:43
Marvin Cheung, Global Diplomacy Fellow at the United Nations Institute for Training and Research (UNITAR), joins our Diplomacy board. Lifeboat News
Marvin Cheung, Global Diplomacy Fellow at the United Nations Institute for Training and Research (UNITAR), joins our Diplomacy board.
03:33
Links 18/04/2023: Fedora GNU/Linux 38 and LXD 5.13 Released Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
- ...
02:49
Digital Rights Updates with EFFector 35.5 Deeplinks
Keeping up on the latest in digital freedoms can be quite a challenge, but we're here to help catch you up to speed! The latest issue of our EFFector newsletter is out now, and you can learn more about our position on the U.N Cybercrime Treaty, the RESTRICT Act, privacy issues regarding renters and smart locks, and much more. Click here to read the full newsletter or you can listen to the audio
Effector 35.5 - Decoding the U.n. Cybercrime Treaty
Make sure you never miss an issue by signing up by email to receive EFFector as soon as it's posted! Since 1990 EFF has published EFFector to help keep readers on the bleeding edge of their digital rights. We know that the intersection of technology, civil liberties, human rights, and the law can be complicated, so EFFector is a great way to stay on top of things. The newsletter is chock full of links to updates, announcements, blog posts, and other stories to help keep readersand listenersup to date on the movement to protect online privacy and free expression.
Thank you to the supporters around the world who make our work possible! If you're not a member yet, join EFF today to help us fight for a brighter digital future.
02:30
OpenCL 3.0.14 Released With New Extension For Command Buffer Multi-Device Phoronix
OpenCL 3.0.14 has been released that has a few minor fixes/corrections plus one prominent new extension: cl_khr_command_buffer_multi_device...
02:11
Version 5.13 of the LXD virtual-machine manager has been released. New features include fast live migration, support for AMD's secure enclaves, and more. See this announcement for details.
02:00
Solus Linux Plans New Direction Built Off Serpent OS Phoronix
Joshua Strobl and original Solus project founder Ikey Doherty are both becoming re-involved with the Solus Linux distribution and moving ahead will be built off the SerpentOS project that Ikey has been independently working on the past few years...
01:54
Perl's HTTP::Tiny has insecure TLS cert default, affecting CPAN.pm and other modules Open Source Security
Posted by Stig Palmquist on Apr 18
HTTP::Tiny v0.082, a Perl core module since v5.13.9 and availablestandalone on CPAN, does not verify TLS certs by default. Users must
opt-in with the verify_SSL=>1 flag to verify certs when using HTTPS.
We grepped trough CPAN to find distributions using HTTP::Tiny that
didn't specify cert verification behaviour, possibly exposing users to
mitm attacks. Here are some examples with patches:
- CPAN.pm v2.34 downloads and executes code...
01:42
Re: CVE-2023-2002: Linux Bluetooth: Unauthorized management command execution Open Source Security
Posted by Solar Designer on Apr 18
BTW, even with the kernel bug fixed, there are ioctl number clashesbetween different devices, so even e.g. isatty(3) is not necessarily
safe if called with elevated privileges under a possible confused deputy
scenario. Here's strace showing some clashes on older Linux/i386:
$ cat isatty.c
int main(void) { return isatty(0); }
$ gcc isatty.c -o isatty
$ strace -e ioctl ./isatty
ioctl(0, SNDCTL_TMR_TIMEBASE or SNDRV_TIMER_IOCTL_NEXT_DEVICE...
01:30

The Raspberry Pi HQ camera module may not quite reach the giddy heights of a DSLR, but it has given experimenters access to a camera system which can equal the output of some surprisingly high-quality manufactured cameras. As an example we have a Yashica film camera.
Coming from the viewpoint of a photographer rather than a hardware person, the video is particularly valuable for his discussion of the many lens options beyond a Chinese CCTV lens which can be used with the platform. It uses only the body from the Yashica, but makes a really cool camera that wed love to own ourselves. If youre interested in the Pi HQ camera give it a watch below the break, and try to follow some of his lens suggestions.
The broken camera he converted is slightly interesting, and raises an important philosophical question for retro technology geeks. Its a Yashica Electro 35, a mid-1960s rangefinder camera for 35 mm film whose claim to fame at the time was its electronically controlled shutter timing depending on its built-in light meter. The philosophical question is this: desecration of a characterful classic camera which might have been repaired, or awesome resto-mod? In that sense its not just about this project, but a question with application across...
01:24
Injectable gel offers new way to grow electrodes in the brain Lifeboat News: The Blog
The method is based on a gel containing enzymes that catalyze electrode formation from endogenous molecules.
01:23
What Rotterdam teaches about the power of green roofs Lifeboat News: The Blog
A recent showcase in the Dutch city highlighted the potential of green rooftops, which can lower city temperatures by 5 degrees Fahrenheit, say researchers.
01:22
James Webb telescope keeps finding galaxies that shouldnt exist, scientist warns Lifeboat News: The Blog
The James Webb Space Telescope keeps finding galaxies that shouldnt exist, a scientist has warned.
Six of the earliest and most massive galaxies that NASAs breakthrough telescope has seen so far appear to be bigger and more mature than they should be given where they are in the universe, researchers have warned.
The new findings build on previous research where scientists reported that despite coming from the very beginnings of the universe, the galaxies were as mature as our own Milky Way.
01:22
A luddite link to nano-terrorists Lifeboat News: The Blog
 An older article but something the world is facing just
like in certain sci-fi movies.
An older article but something the world is facing just
like in certain sci-fi movies.
The reference publication of the movement in the 80s, the Earth First journal, featured a column called Ask Ned Ludd, in reference to the mythical character that gave name to the luddites. Jones thinks that neo-luddites are in fact misreading the original luddites, but he believes that understanding the difference between the old and modern ones tells us a lot about the ideology of the latter.
Luddites were not anti-technology: they were skilled craftsmen, involved in a labour movement aimed at keeping their machines and their jobs, he says. Thats very different from the neo-luddites ideas of relinquishing civilisation and [of] nature as the supreme good. Jones thinks neo-luddism is fed rather by the idea of technology as a disembodied, transcendent, terrifying force outside the human, which emerged in the mid 20th century, with the bomb and the rise of large-scale computing.
01:19
Re: CVE-2023-2002: Linux Bluetooth: Unauthorized management command execution Open Source Security
Posted by Todd C. Miller on Apr 18
That is correct. There are further changes to use TIOCGWINSZ on/dev/tty instead of stderr. Using an open fd of /dev/tty makes the
isatty() call superfluous but it doesn't hurt to have it.
- todd
01:01
Home sweet couch!
On the way back from the Big Ears festival, I stopped for a few days in New York and was going to visit comics shops and get my shopping on and stuff. But instead I got a gastro thing, and ended up staying in the hotel room for a week and also sprained my ankle when I fainted or something. Im kinda sorta fine now, though, except for having to keep my foot elevated. Im not up for doing anything taxing brain wise as Im mostly vegetating on a hurr durr level, but I got, like, 50 pounds of comics yesterday Lots of stuff Im looking forward to reading (new books from CF!!!), but Im just gonna read stuff thats easier on the brain today, and Im saving that stuff until a later day.
And for music uhm OK, only albums that I liked as a child.
A reconvalescing kind of day?
| Neil Young: After The Gold Rush |
 |
01:00
KOTRA and KISIA will showcase 10 Korean cybersecurity companies at RSA Conference 2023 Help Net Security
Korea Trade-Investment Promotion Agency (KOTRA) will host 10 Korean cybersecurity companies as Korea Pavilion with Korea Information Security Industry Association (KISIA) at RSA Conference 2023. KOTRA and KISIA will feature companies from across a range of fields including network security, cloud security, identity and access management and more. Additionally, KOTRA and KISIA will hold a networking event with including Korean cybersecurity companies, local investors, and invited Korea Pavilion attendees from RSAC 2023 on the last More
The post KOTRA and KISIA will showcase 10 Korean cybersecurity companies at RSA Conference 2023 appeared first on Help Net Security.
00:59
Stopping Storms From Creating Dangerous Urban Geysers SoylentNews
Stopping Storms from Creating Dangerous Urban Geysers:
During intense rainstorms, residents of urban areas rely on stormwater sewers to keep streets and homes from flooding. But in some cases, air pockets in sewers combine with fast-moving water to produce waterspouts that can reach dozens of feet high and last for several minutes. These so-called storm geysers can flood the surrounding area, cause damage to nearby structures, injure bystanders, and compromise drainage pipes.
In Physics of Fluids, by AIP Publishing, researchers from Sichuan University, Ningbo University, University of Alberta, and Hohai University developed a computational model of stormwater piping to study storm geysers. They used this model to understand why storm geysers form, what conditions tend to make them worse, and what city planners can do to prevent them from occurring.
Perhaps the biggest cause of storm geysers is poor city planning. With extreme weather events becoming more common due to climate change, cities can often find themselves unprepared for massive amounts of rain. Growing cities are especially vulnerable. Small cities have small drainage pipes, but new streets and neighborhoods result in added runoff, and those small pipes may not be able to handle the increased volume.
[...] The authors say the best cure for a storm geyser is bigger pipes.
"The most effective preventive measure for newly planned drainage pipelines is to increase the pipeline diameter and improve system design, which reduces the likelihood of full-flow conditions and eliminates storm geysers," said Zhang.
Read more of this story at SoylentNews.
00:50
1Fichier Held Liable After Failing to Remove Pirated Nintendo Games TorrentFreak
 Ever since its launch in 2009, rightsholders have
complained that file-hosting platform 1fichier.com fails to take
intellectual property rights seriously.
Ever since its launch in 2009, rightsholders have
complained that file-hosting platform 1fichier.com fails to take
intellectual property rights seriously.
1fichier operates a freemium business model which allows users to access the platform for free and then pay a fee to have various restrictions removed. 1fichier allows user content to be accessed via links posted elsewhere, meaning that when users upload infringing content, links render that content available to the public.
Rightsholders have publicly criticized the platform for more than a decade, claiming that 1fichiers response to takedown notices is minimal in some cases amounting to a compliance rate of just 0.12%.
Nintendo Files Lawsuit
With the goal of forcing 1fichier to comply with its takedown notices and pay compensation for damages incurred due to its poor response, Nintendo sued 1fichiers owner, Dstorage SAS.
The Judicial Court of Paris sided with Nintendo in a decision handed down on May 25, 2021. The Court found that Dstorage could be held liable for failing to remove illegal copies of Nintendo games hosted on 1fichier, based on notifications sent by rightsholders.
The court also addressed 1fichiers assertion that content does not have to be removed without authorization from a court. The platform was informed that direct takedown notices from rightsholders do not require a court order to be valid. 1fichier was also instructed to publish the following notice:
By decision dated May 25, 2021, the Paris court ruled that the company DSTORAGE, which operates the website 1fichier.com, has engaged its liability as as a content host by not removing illegal content despite the notifications made by Nintendo Co., Ltd., The Pokmon Company, Creatures Inc. and DE Inc. and ordered it to pay NINTENDO Co Ltd, the sums of 885,500 euros and 50,000 euros in compensation for its damages.
Court of Appeal Sides With Nintendo
A press release published by Nintendo on April 17 reveals that on April 12, 2023, the Paris Court of Appeal confirmed that Dstorage SAS engaged its civil liability for failing to withdraw or block access to illicit copies of Nintendo games hosted on...
00:48
The Fedora 38 release is available. Fedora has mostly moved past its old pattern of late releases, but it's still a bit surprising that this release came out one week ahead of the scheduled date. Some of the changes in this release, including reduced shutdown timeouts and frame pointers have been covered here in the past; see the announcement and the Workstation-edition "what's new" post for details on the rest.
If you want to use Fedora Linux on your mobile device, F38 introduces a Phosh image. Phosh is a Wayland shell for mobile devices based on Gnome. This is an early effort from our Mobility SIG. If your device isnt supported yet, we welcome your contributions!
00:47
Distribution Release: Fedora 38 DistroWatch.com: News
The Fedora team have announced the release of Fedora 38. The new release offers the GNOME 44 desktop in the project's Workstation edition. The distribution now features shorter timeout delays when services shutdown, which makes shutting down or restarting the system faster. The DNF5 package manager as been....
00:38
Fedora 38 Released With GNOME 44 Desktop, GCC 13, Many New Features Phoronix
Fedora 38 has been released today after meeting its early release target...
00:28
Army helicopter crash blamed on skipped software patch Graham Cluley
The emergency ditching of an Australian military helicopter in the water just off a beach in New South Wales, has been blamed on the failure to apply a software patch. Read more in my article on the Hot for Security blog.
00:28
libuv Adds IO_uring Support For ~8x Throughput Boost Phoronix
Libuv as the cross-platform asynchronous I/O library that is used by the likes of Node.js, Julia, and other software packages now has support for making use of IO_uring on Linux...
00:23
Security updates for Tuesday LWN.net
Security updates have been issued by Debian (protobuf), Fedora (libpcap, libxml2, openssh, and tcpdump), Mageia (kernel and kernel-linus), Oracle (firefox, kernel, kernel-container, and thunderbird), Red Hat (thunderbird), Scientific Linux (thunderbird), SUSE (gradle, kernel, nodejs10, nodejs12, nodejs14, openssl-3, pgadmin4, rubygem-rack, and wayland), and Ubuntu (firefox).
00:06
Garrett: PSA: upgrade your LUKS key derivation function LWN.net
Matthew Garrett points out that many Linux systems using encrypted disks were installed with a relatively weak key derivation function that could make it relatively easy for a well-resourced attacker to break the encryption:
So, in these days of attackers with access to a pile of GPUs, a purely computationally expensive KDF is just not a good choice. And, unfortunately, the subject of this story was almost certainly using one of those. Ubuntu 18.04 used the LUKS1 header format, and the only KDF supported in this format is PBKDF2. This is not a memory expensive KDF, and so is vulnerable to GPU-based attacks. But even so, systems using the LUKS2 header format used to default to argon2i, again not a memory expensive KDF. New versions default to argon2id, which is. You want to be using argon2id.
The article includes instructions on how to (carefully) switch an installed system to a more secure setup.
00:01
Stop using Telnet to test ports Linux.com
Make life simpler by automating network checks with tools like Expect, Bash, Netcat, and Nmap instead.
Read More at Enable Sysadmin
The post Stop using Telnet to test ports appeared first on Linux.com.
00:00
Linux Fu: Reading Your Memorys Memory Hackaday

Linux users have a lot of software to be proud of. However, there is the occasional Windows program that does something youd really like to do and it just wont run. This is especially true of low-level system programs. If you want to poke around your CPU and memory, for example, there are tons of programs for that under Windows. There are a few for Linux, but they arent always as complete or handy. Recently, I had half the memory in my main desktop fail and I wanted to poke around in the system. In particular, I wanted to read the information encoded in the memory chips configuration EEPROM. Should be easy, right? Youd think.
Not Really Easy
One nice tool a lot of Windows users have is CPU-Z. Of course, it doesnt run on Linux, but there is a really nice imitator called CPU-X. You can probably install it from your repositories. However, the GitHub page is a nice stop if for no other reason than to enjoy the user name [TheTumultuousUnicornOfDarkness]. The program has a gtk or an ncurses interface. You dont need to run it as root, but if you press the start daemon button and authenticate, you can see some extra information, including a tab for memory.
...
Tuesday, 18 April
23:54
IRC Proceedings: Monday, April 17, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-170423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-170423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-170423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-170423.gmi
Over HTTP:
|
... |
23:45
YouTube Videos Distributing Aurora Stealer Malware via Highly Evasive Loader The Hacker News
Cybersecurity researchers have detailed the inner workings of a highly evasive loader named "in2al5d p3in4er" (read: invalid printer) that's used to deliver the Aurora information stealer malware. "The in2al5d p3in4er loader is compiled with Embarcadero RAD Studio and targets endpoint workstations using advanced anti-VM (virtual machine) technique," cybersecurity firm Morphisec said in a report
23:30
CISA adds bugs in Chrome and macOS to its Known Exploited Vulnerabilities catalog Security Affairs
US Cybersecurity and Infrastructure Security Agency (CISA) added Chrome and macOS vulnerabilities to its Known Exploited Vulnerabilities catalog.
U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added the following five new issues to its Known Exploited Vulnerabilities Catalog:
- CVE-2019-8526 Apple macOS Use-After-Free Vulnerability. The CVE-2019-8526 flaw has been exploited by the DazzleSpy backdoor in watering hole attacks aimed at politically active individuals in Hong Kong. The issue was used to dump iCloud Keychain if the macOS
- CVE-2023-2033 Google Chromium V8 Engine Type Confusion Vulnerability. The CVE-2023-2033 flaw is the first Chrome zero-day vulnerability addressed by Google in 2023. The vulnerability was reported by Clment Lecigne of Googles Threat Analysis Group on 2023-04-11. Google did not disclose details of the attacks exploiting this vulnerability, it will not provide bug details and links until a majority of users will have updated their installs.
According to Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities, FCEB agencies have to address the identified vulnerabilities by the due date to protect their networks against attacks exploiting the flaws in the catalog.
Experts recommend also private organizations review the Catalog and address the vulnerabilities in their infrastructure.
CISA orders federal agencies to fix this flaw by May 8, 2023.
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections:
- The Teacher Most Educational Blog
- The Entertainer Most Entertaining Blog
- The Tech Whizz Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please...
23:25
9elements Security Talks Up AMD openSIL Open-Source Firmware With 4th Gen EPYC Phoronix
For weeks we have been eager to learn more about AMD openSIL that will formally be announced at the OCP Prague event later this week. In anticipation of that event, AMD last week revealed the initial details around this open-source firmware push...
23:22
DeepMinds CEO said theres a chance that AI could become self-aware in the future Lifeboat News: The Blog
The CEO of Alphabet-owned AI research lab, DeepMind Technologies, spoke about the potential of artificial intelligence in an interview with CBS 60 Minutes, which aired on Sunday.
DeepMind CEO Demis Hassabis told CBS that he thinks that AI might one day become self-aware.
Philosophers havent really settled on a definition of consciousness yet but if we mean self-awareness, and these kinds of things I think theres a possibility that AI one day could be, he said.
23:22
How to put ChatGPT on Galaxy Watch, Pixel Watch, Wear OS Lifeboat News: The Blog
Its available on phones and now watches? Thats actually nice though I hope they make it battery efficient. The Pixel watch for example already has issues with battery life. Im the future will there be a small AI server in our bodies in microchips or a network of nanobots?
ChatGPT is all the rage these days, but did you know you can get it on your watch? Heres how to install it on a Galaxy Watch, Pixel Watch, and other Wear OS watches.
23:07
Checking existence of firewalled web servers in Firefox via iframe.onload Open Source Security
Posted by Georgi Guninski on Apr 18
In short in Firefox 112, it is possible to check existenceof firewalled web servers. This doesn't work in Chrome and Chromium 112
for me.
If user A has tcp connection to web server B, then in the
following html:
<iframe src="http://B"; onload="load()" onerror="alert('error')" id="i1" />
the javascript function load() will get executed if B serves
valid document to A's browser...
23:04
Re: CVE-2023-2002: Linux Bluetooth: Unauthorized management command execution Open Source Security
Posted by Ruihan Li on Apr 18
Hi Solar Designer,Also thanks to all the people at linux-distro and s@k.o who helped to
improve the final disclosure and patches.
That's good to know. I was wondering if there were distros that did not
have setuid binaries, which was why I said only ``a number of distros''
were vulnerable.
For Steffen Nurpmeso wrote earlier:
I just noticed that sudo added the isatty check a day ago (April 17th)
[1]. I think this change was...
23:01
Re: CVE-2022-47501: Apache OFBiz: Arbitrary file reading vulnerability Open Source Security
Posted by Jacques Le Roux on Apr 18
Hi Seth,I used to give more information. For this one, using our "new" internal process* (need an ASF credential) and
following step 11 of**, notably
<<Generally, reports should contain enough information to enable people to assess the risk the vulnerability poses
for their own system, and no
more.>>
I restricted the information to a minimum.
With a request from Arnoult (member of the ASF security team in...
23:00
Quadrupeds Are Learning to Dribble, Catch, and Balance IEEE Spectrum

Now that anyone, anywhere can get themselves a quadrupedal robot without having to apply for a major research grant, were seeing all kinds of fun research being done with our four-legged electromechanical friends. And by fun research I mean very serious research that is making valuable contributions towards practical robotics. But seriously, there are lots of important robotics problems that can be solved in fun and interesting ways; dont let anyone tell you different, especially not the current United States ambassador to Turkey.
At the 2023 International Conference on Robotics and Automation (ICRA) slated to take place in London next month, three papers will be presented that report on the talents of quadrupedal robots and the researchers who teach them new things, including dribbling, catching, and traversing a balance beam.
MITs Dribbling Quadruped
Quadrupedal soccer robots have a long and noble history; for years, Sony Aibos were the standard platform at RoboCup. But quadrupeds have made some enormous four-legged strides since the late 1 990s and early 2000s. Now that basic quadrupedal mobility has been pretty well figured out, its time to get these robots doing fun stuff. In an upcoming ICRA paper, roboticists from MIT describe how they have taught a quadruped to dribble a soccer ball across rough terrain, which is actually really impressive for anyone who has tried to do this themselves.
Lets just get this out of the way: for most of the world, were talking about football here. But the paper calls it soccer, so Im going to call it soccer too. Whatever you call it, its the one with the round ball where most of the time a game is actually being played instead of the one with the pointy ball where most of the time people are just standing around not doing anything.
DribbleBot, a name given to an automaton whose functionality the paper describes as Dexterous Ball Manipulation with a
Legged Robot, is a Unitree Go1. The machine can dribble a soccer ba...
22:32
Denis Carikli on Taking Control Over the Means of Production: Free Software Boot Techrights
Summary: The above LibrePlanet talk by Denis Carikli is a remote (not physical presence) talk; it talks about bringing freedom to the hardware level (or closer to it) and it was uploaded by the FSF a few hours ago (slides here); From the official page: But there is also software running before the operating system is even started (like BIOS, UEFI, the Management Engine or the PSP operating systems). They give the hardware manufacturers an enormous amount of control over the computers used by users, even if users use FSF-approved GNU/Linux distributions like Trisquel and Parabola. That control is for instance often used by hardware manufacturers to give companies the ability to remotely control users computers through features like AMT, and that control is independent of the operating system running on the computer. After giving some background for less technical users, we will look from a user point of view why and how to avoid nonfree software in that area.
Licence: CC BY SA 4.0
22:27
Goldoson Android Malware Infects Over 100 Million Google Play Store Downloads The Hacker News
A new Android malware strain named Goldoson has been detected in the official Google Play Store spanning more than 60 legitimate apps that collectively have over 100 million downloads. An additional eight million installations have been tracked through ONE store, a leading third-party app storefront in South Korea. The rogue component is part of a third-party software library used by the apps in
22:22
Deaths in England and Wales This Spring Vastly Higher (21% Higher) Than in Prior Including COVID-19 Years schestowitz.com
 HAVE
just checked again and new numbers, for week 13 at least, came out
this morning,
5 days after the last time. The numbers are astonishing as they
show 2,000+ more deaths than the 5-year average (including pandemic
years).
HAVE
just checked again and new numbers, for week 13 at least, came out
this morning,
5 days after the last time. The numbers are astonishing as they
show 2,000+ more deaths than the 5-year average (including pandemic
years).
So for a single week, week 13, weve leapt from 9,580 to to 11,584 deaths (+2,004).
Compared to 2019:
22:15
Curiosity Mars Rover Gets its Latest Interplanetary Software Patch SoylentNews
Shooting all-important bytes to a machine 254 million kms away from Earth:
Launched from Cape Canaveral on November 26, 2011, the Curiosity rover was designed for scientific investigations during a two-year mission. Twelve years later, the car-sized machine is still roaming Mars' surface while NASA improves the software side of things from afar.
Between April 3 and 7, Curiosity's science and imaging operations were put "on hold" for planned software maintenance. NASA installed the latest "patch" to its Mars rover's flight software, a major update which was planned for years and designed to further extend the rover's capabilities and longevity in the Red Planet's harsh environment.
NASA started to work on the now-up and running software update back in 2016, when Curiosity got its last software overhaul. The new flight software (R13) brings about 180 changes to the rover's system, two of which will make the Mars robot drive faster and reduce wear and tear on its wheels.
The first major change implemented by NASA in Curiosity software is related to how the machine processes images of its surroundings to plan a route around obstacles. Newer rovers like Perseverance are equipped with onboard computers capable of processing images on-the-fly, while the robots are still in motion. Curiosity, on the other hand, doesn't have that kind of feature and it needs to stop every time to reassess surface conditions and correct its course.
Read more of this story at SoylentNews.
21:42
What Happened Months Before Seattle Police Sent Almost 3,000 Pages About Its Arrest for Pedophilia at Home of Bill Gates Techrights
In 2019 the boss of Sirius said that the Gates Foundation had become the first US client of Sirius, but it involved a non-disclosure agreement (NDA) so he could not elaborate on what that actually meant and it was never ever mentioned in writing
Summary: The timing of the bullying at Sirius Open Source was all along difficult to ignore because the police was getting involved after records had been requested (we published them months later*) and Melinda Gates started pursuing a divorce (the man on the right is the right-hand man of Bill Gates, who was also entrusted by Jeffrey Epstein to execute his will); years earlier Microsoft managers phoned my boss (who also supervised my wife; we both worked there at the time), complaining about me by name, so they had clearly taken note of where I was working and sought to silence me one way or another
If you cant make it good, at least make it look good.
Bill Gates, Microsoft
___
* Case Investigation Report: 2014-221...
21:31
DFIR via XDR: How to expedite your investigations with a DFIRent approach The Hacker News
Rapid technological evolution requires security that is resilient, up to date and adaptable. In this article, we will cover the transformation in the field of DFIR (digital forensics and incident response) in the last couple years, focusing on the digital forensics' aspect and how XDR fits into the picture. Before we dive into the details, let's first break down the main components of DFIR and
21:23
Is artificial intelligence advancing too quickly? What AI leaders at Google say Lifeboat News: The Blog
It is an unsettling moment. Critics argue the rush to AI comes too fast while competitive pressure among giants like Google and start-ups youve never heard of, is propelling humanity into the future ready or not.
Sundar Pichai: But I think if take a 10-year outlook, it is so clear to me, we will have some form of very capable intelligence that can do amazing things. And we need to adapt as a society for it.
Google CEO Sundar Pichai told us society must quickly adapt with regulations for AI in the economy, laws to punish abuse, and treaties among nations to make AI safe for the world.
21:23
Machine Learning Investor Warns AI Is Becoming Like a God Lifeboat News: The Blog
A serial AI investor is raising alarm bells about the dogged pursuit of increasingly-smart machines, which he believes will become god-like.
21:22
Should We Fear Alien Artificial Intelligence? Lifeboat News: The Blog
An exploration not of human artificial intelligence and chatbots, but what alien civilizations might do with the technology to very different outcomes.
An exploration of Machine Natural Selection and the potential of an AI Apocalypse.
My Patreon Page:
https://www.patreon.com/johnmichaelgodier.
My Event Horizon Channel:
21:06
Nexon Sues Dark and Darker Developer for Copyright Infringement TorrentFreak
 The
official stable release of the first person shooter game Dark and Darker
is eagerly awaited by hundreds of thousands of fans.
The
official stable release of the first person shooter game Dark and Darker
is eagerly awaited by hundreds of thousands of fans.
Whether the full game will actually be released is uncertain, however, as the game is at the center of a legal dispute.
Last month, police in South Korea raided the offices of Dark and Darkers developers, local game studio Ironmace. The legal action was triggered by a complaint from game publisher Nexon, which accused its rival of copyright infringement and stealing trade secrets.
Ironmace was founded by former Nexon developers who allegedly took thousands of files with them. The game publisher believes that these files were used to develop Dark and Darker, which is similar to the P3 game project Nexon is working on.
Following the raid, the disgruntled publisher also complained to Steam, which banned Dark and Darker from its platform. And when Ironmace released its latest alpha test via BitTorrent last weekend, its adversary pulled out all the stops to slow down distribution.
Nexon Sues Ironmace in U.S. Court
The recent actions show that Nexon is serious about protecting its rights. This isnt limited to sending takedown notices and legal threats either; the company also filed a lawsuit at a federal court in Seattle, Washington, last Friday.

The 55-page complaint accuses Ironmace of copyright infringement and misappropriation of trade secrets. In addition to the Korean game studio, two former Nexon employees Ju-Hyun Choi and Terence Seungha Park are personally listed as defendants too.
Choi is currently employed as Ironmaces Managing Director but he used to work as the director of Nexons P3 game project. Park, who is a US citizen, is the CEO and co-founder of Ironmace and was previously employed as the head of...
21:00
NASAs Ingenuity Mars Helicopter Completes 50th Flight Hackaday

While NASAs Perseverance rover brought an array of impressive scientific equipment to the surface of Mars, certainly its most famous payload is the stowaway helicopter Ingenuity. Despite being little more than a restricted-budget experiment using essentially only off-the-shelf components that you can find in your smartphone and e-waste drawer, the tenacious drone managed to complete its fiftieth flight on April 13 just days before the two year anniversary of its first flight, which took place on April 19th of 2021.
Engineers hoped that Ingenuity would be able to show that a solar-powered drone could function in the extremely thin atmosphere of Mars, but the experiment ended up wildly exceeding expectations. No longer a simple technology demonstrator, the helicopter has become an integral part of...
20:58
Sirius Weaponised Wikipedia to Perpetuate Lies/Revisionism About Itself Techrights
Another fine example of Wikipedia turning into a worthless marketing/spin avenue instead of an online encyclopedia (taken over by states and corporations, writing about themselves)
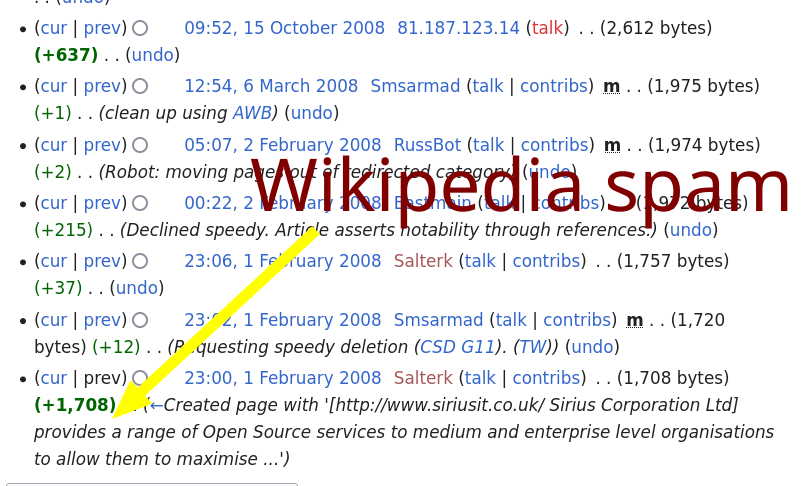
Summary: As we saw countless time before, Wikipedia is being vandalised to legitimise lies
20:47
Amin Bandali on Whats New in Jami, End-to-end Encrypted (E2EE) Communication Tool (Formerly Known as GNU Ring) Techrights
Summary: The above LibrePlanet talk about Jami was uploaded by the FSF (slides here) just this morning; From the official page: Jami is free/libre software for universal communication that respects the freedoms and privacy of its users. An official GNU package, Jami is an end-to-end encrypted secure and distributed communication tool for calling, conferencing, messaging, and file transfer. Jami has end-user applications across multiple operating systems and platforms, as well as multiple APIs and a plugin system for building upon and extending Jami as a framework for secure and private communication. This talk gives an update on whats new in and about Jami since bandalis Jami and how it empowers users talk at LibrePlanet 2021.
Licence: CC BY SA 4.0
20:39
Links 17/04/2023: GNU poke 3.1 and Deepin 20.9 Released Techrights
![]()
Contents
-
GNU/Linux
-
Desktop/Laptop
-
ZDNet Universal Blue is a new paradigm for the Linux desktop and its brilliant | ZDNET
Ive been using Linux since 1997. Years ago, I reached the point where I was certain there was nothing that could surprise me anymore. Fast forward to...
-
-
20:36
Intel Vulkan Linux Driver Lands Graphics Pipeline Library Support Phoronix
Intel's one-year-old merge request for introducing VK_EXT_graphics_pipeline_library support to their open-source "ANV" Vulkan driver has finally been merged for Mesa 23.2...
20:30
AMD AOMP 17.0-1 Compiler Switches To Its Next-Gen Plugin For Better Performance Phoronix
19:41
Eclipse OpenJ9 0.37 Released - But It Shouldn't Be Used In Production Phoronix
A new release of Eclipse OpenJ9 is now available, the high performance JVM implementation previously developed as IBM J9...
19:28
German Artist Refuses Award After His AI Image Wins Prestigious Photography Prize SoylentNews
German artist refuses award after his AI image wins prestigious photography prize:
There's some controversy in the photography world as an AI-generated image won a major prize at a prestigious competition, PetaPixel has reported. An piece called The Electrician by Boris Eldagsen took first prize in the Creative category at the World Photography Organization's Sony World Photography Awards despite not being taken by a camera. Eldagsen subsequently refused the award, saying "AI is not photography. I applied [...] to find out if the competitions are prepared for AI images to enter. They are not."
Eldagsen's image is part of a series called PSEUDOMNESIA: Fake Memories, designed to evoke a photographic style of the 1940s. However, they are in reality "fake memories of a past, that never existed, that no one photographed. These images were imagined by language and re-edited more between 20 to 40 times through AI image generators, combining 'inpainting', 'outpainting', and 'prompt whispering' techniques."
In a blog, Eldagsen explained that he used his experience as a photographer to create the prize-winning image, acting as a director of the process with the AI generators as "co-creators." Although the work is inspired by photography, he said that the point of the submission is that it is not photography. "Participating in open calls, I want to speed up the process of the Award organizers to become aware of this difference and create separate competitions for AI-generated images," he said.
Eldagsen subsequently declined the prize. "Thank you for selecting my image and making this a historic moment, as it is the first AI-generated image to win in a prestigious international photography competition," he wrote. "How many of you knew or suspected that it was AI generated? Something about this doesn't feel right, does it? AI images and photography should not compete with each other in an award like this. They are different entities. AI is not photography. Therefore I will not accept the award.
When does the processing of a 'photograph' become unacceptable? Techniques such as burning and dodging, plus various types of film processing, can all change the image that is finally produced. Digital photographs can be even more easily modified. At what point does it become an entirely new genre. Does the method of production really matter? [JR]
...
19:24
Probing the Shifting Surface of Icy Moons Centauri Dreams Imagining and Planning Interstellar Exploration

In celebration of the recent JUICE launch, a few thoughts on what were learning about Ganymede, with eight years to go before the spacecraft enters the system and eventually settles into orbit around the icy moon. Specifically, lets consider a paper just published in Icarus that offers results applicable not just to Ganymede but also Europa and Enceladus, those fascinating and possibly life-bearing worlds. We learn that when we look at the surface of an icy moon, were seeing in part the result of quakes within its structure caused by the gravitational pull of the parent planet.
Image: ESAs latest interplanetary mission, Juice, lifted off on anAriane 5 rocketfromEuropes Spaceportin French 09:14 local time/08:14 EDT on 14 April 2023 to begin its eight-year journey to Jupiter, where it will study in detail the gas giant planets three large ocean-bearing moons: Ganymede, Callisto and Europa. Credit: ESA.
The Icarus paper homes in on the link between such quakes, long presumed to occur given our understanding of gravitational interactions, and the landslides observable on the surface of icy moons. Its one thing to tag steep ridges surrounded by flat terrain as the result of ice volcanoes spouting liquid, but we also find the same result on moons whose surface temperature makes this explanation unlikely.
Thus the new work, described by lead author Mackenzie Mills (University of Arizona), who analyzed the physical pummeling icy terrain takes during tidally induced moonquakes:
We found the surface shaking from moonquakes would be enough to cause surface material to rush downhill in landslides. Weve estimated the size of moonquakes and how big the landslides could be. This helps us understand how landslides might be shaping moon surfaces over time.

Image: NASAs Galileo spacecraft captured this image of the surface of Jupiters...
19:22
Zo Kooyman, Geoffrey Knauth, Sbastien Blin, Cyrille Braud: FSF Keynote and Awards Ceremony Techrights
Summary: The above LibrePlanet keynote talk was uploaded by the FSF 2.5 hours ago; From the official page: This presentation is about the use and production of free/libre software by organizations of the Brazilian federal government after some years of public policies to promote the use of free software.
Licence: CC BY SA 4.0
19:11
The intricate relationships between the FIN7 group and members of the Conti ransomware gang Security Affairs
A new malware, dubbed Domino, developed by the FIN7 cybercrime group has been used by the now-defunct Conti ransomware gang.
IBM Security X-Force researchers recently discovered a new malware family, called Domino, which was created by developers associated with the FIN7 cybercriminal group (tracked by X-Force as ITG14).
FIN7 is a Russian criminal group (aka Carbanak) that has been active since mid-2015, it focuses on restaurants, gambling, and hospitality industries in the US to harvest financial information that was used in attacks or sold in cybercrime marketplaces.
IBM Security X-Force reported that former members of the now-defunct Conti gang have been using Domino since at least late February 2023. The threat actors used the malware to deliver either the Project Nemesis information stealer or other backdoors and tools such as Cobalt Strike.
This discovery is very important because demonstrates the cooperation among the groups and their members.
Since late February 2023, Domino Backdoor campaigns have been observed using the Dave Loader, which we have linked to the Trickbot/Conti syndicate and its former members. reads the report published by IBM Security X-Force. Dominos code shows overlap with the Lizar (aka Tirion, Diceloader) malware family, leading us to suspect that it was created by current or former ITG14 developers. One of Dominos final payloads is the Project Nemesis infostealer. Project Nemesis was first advertised on the dark web in December 2021, though has been rarely used since then.
In attacks on higher-value targets instead of downloading the Project Nemesis, the Domino Backdoor contacts a C2 to download post-exploitation tools such as Cobalt Strike.
19:05
Iranian Hackers Using SimpleHelp Remote Support Software for Persistent Access The Hacker News
The Iranian threat actor known as MuddyWater is continuing its time-tested tradition of relying on legitimate remote administration tools to commandeer targeted systems. While the nation-state group has previously employed ScreenConnect, RemoteUtilities, and Syncro, a new analysis from Group-IB has revealed the adversary's use of the SimpleHelp remote support software in June 2022. MuddyWater,
18:37
Distribution Release: deepin 20.9 DistroWatch.com: News
18:00
micro:bit Brings 3D Printed Magic Lanterns to Life Hackaday

[Elenavercher] loves engaging her primary school students, inspiring their imagination as well as teaching them the design thinking process. She has found that the very accessible rapid prototyping culture of 3D printing, micro:bit, and the like are perfect for teaching her students problem-solving and teamwork, and is always coming up with new lessons that will catch their attention. That brings us to her latest design, an interactive lantern and wand, which you could say is of the wizarding variety.
The lantern and the wand each have an integrated micro:bit serving as their brains. When the user shakes the wand, releasing a spell, the micro:bit in the wand, sends a user-defined number to the micro:bit in the lantern. The lantern has NeoPixels built-in, which then turn on, illuminating the lantern. When the user presses a button on the micro:bit instead of shaking it, the wand sends a signal to the lantern that tells it to turn off. Pretty simple, right?
The design itself is something any seasoned hacker could recreate; however, the magic in this build is how [Elenavercher] beautifull...
17:55
Sirius Open Source Pays the Price for Many Years of Criminal Behaviour schestowitz.com
Video download link |
md5sum 54b92623f894a04b61343f93c5d75ba5
Sirius Corruption Roundup
Creative Commons Attribution-No Derivative Works 4.0
Summary: The crimes committed by my last employer are becoming very apparent and crystal clear to see; meanwhile there are other crime victims coming out of the woodwork and we shall give them a voice, not just further information
THE Sirius Open Source series is being followed closely by a lot of people. Its routinely mentioned in Techrights and Tux Machines, even my personal site for more important topics/aspects.
Many people are impacted by this issue, even if one person is more vocal about it (Im fortunate to have a platform in which I can speak about this). For the sake of geeks, and for human/labour rights (or tech rights), we need to expose what happened in the company I knew from the inside for nearly 12 years. We have lots left to publish and plenty is still being investigated (several things are always being investigated in parallel).
As the a video above notes upfront, I didnt expect to cover any criminal aspects, but while doing the first batch I stumbled upon anomalies and started contacting authorities, companies, former colleagues etc. It didnt take long to realise what sort of hydra we had all along dealt with; many workers were robbed and bullied, but the company threatened people not to speak about it with colleagues. Well, enough is enough and the dirty laundry will come out. The world needs to see a workplace that isnt just toxic but also corrupt. Many insiders (back then) didnt realise the scale of the abuse, but they realised this afterwards or are coming to realise it now (with more facts being made publicly availabl...
17:48
Exposing Sirius Corruption, Which Tarnished the Image of Free Software and Injured GNU/Linux Advocates Techrights
Video download link |
md5sum 54b92623f894a04b61343f93c5d75ba5
Sirius Corruption Roundup
Creative Commons Attribution-No Derivative Works 4.0
Summary: The crimes committed by my last employer are becoming very apparent and crystal clear to see; meanwhile there are other crime victims coming out of the woodwork and we shall give them a voice, not just further information
THE Sirius Open Source series is being followed closely by a lot of people. Its routinely mentioned in Techrights and Tux Machines, even my personal site for more important topics/aspects.
Many people are impacted by this issue, even if one person is more vocal about it (Im fortunate to have a platform in which I can speak about this). For the sake of geeks, and for human/labour rights (or tech rights), we need to expose what happened in the company I knew from the inside for nearly 12 years. We have lots left to publish and plenty is still being investigated (several things are always being investigated in parallel).
Maybe there will also be arrests, but that can take a long time.As the a video above notes upfront, I didnt expect to cover any criminal aspects, but while doing the first batch I stumbled upon anomalies and started contacting authorities, companies, former colleagues etc. It didnt take long to realise what sort of hydra we had all along dealt with; many workers were robbed and bullied, but the company threatened people not to speak about it with colleagues. Well, enough is enough and the dirty laundry will come out. The world needs to see a workplace that isnt just toxic but also corrupt. Many insiders (back then) didnt realise the scale of the abuse, but they realised t...
17:10
LockBit Ransomware Now Targeting Apple macOS Devices The Hacker News
Threat actors behind the LockBit ransomware operation have developed new artifacts that can encrypt files on devices running Apple's macOS operating system. The development, which was reported by the MalwareHunterTeam over the weekend, appears to be the first time a big-game ransomware crew has created a macOS-based payload. Additional samples identified by vx-underground show that the macOS
17:01
Podcast Episode: Safer Sex Work Makes a Safer Internet Deeplinks
An internet that is safe for sex workers is an internet
that is safer for everyone. Though the effects of stigmatization
and criminalization run deep, the sex worker community exemplifies
how technology can help people reduce harm, share support, and
offer experienced analysis to protect each other. But a 2018
federal law purportedly aimed at stopping sex trafficking,
FOSTA-SESTA, led to shutdowns of online
spaces where sex workers could talk, putting at increased risk some
of the very people it was supposed to protect.

Public interest technology lawyer Kendra Albert and sex worker, activist, and researcher Danielle Blunt have been fighting for sex workers online rights for years. They say that this marginalized groups experience can be a valuable mo...
17:00
A New Approach to Computation Reimagines Artificial Intelligence Terra Forming Terra
What is wrong with our DIET? Terra Forming Terra
Animals without a brain still form associative memories Terra Forming Terra

Deagels Depopulation Premonitions for 2025 Revisited Terra Forming Terra

16:43
Offensive Cyber Company QuaDream Shutting Down Amidst Spyware Accusations SoylentNews
Offensive cyber company QuaDream shutting down amidst spyware accusations:
According to sources, the company has been in a difficult situation for several months, and the research was the last nail in its coffin. The company hasn't been fully active for a while and it is believed that there are only two employees left in its offices whose job it is to look after the computers and other equipment. At the same time, the board of directors is trying to sell the company's intellectual property.
[...] Last week, it was reported that the Israeli firm's hacking tools have been used against journalists, opposition figures and advocacy organizations across at least 10 countries - including people in North America and Europe - according to new research published by Microsoft and the internet watchdog Citizen Lab.
According to sources, the company has been in a difficult situation for several months, and the research was the last nail in its coffin. The company hasn't been fully active for a while and it is believed that there are only two employees left in its offices whose job it is to look after the computers and other equipment. At the same time, the board of directors is trying to sell the company's intellectual property.
Citizen Lab said in its report that it had been able to identify a handful of civil society victims whose iPhones had been hacked using surveillance software developed by QuaDream - a lower-profile competitor to the Israeli spyware company NSO Group, which has been blacklisted by the U.S. government over allegations of abuse.
In its report published at the same time, Microsoft said it believed with "high confidence" that the spyware was "strongly linked to QuaDream."
In a statement, Microsoft Associate General Counsel Amy Hogan-Burney said that mercenary hacking groups like QuaDream "thrive in the shadows" and that publicly outing them was "essential to stopping this activity."
Read more of this story at SoylentNews.
15:21
Israeli surveillance firm QuaDream is shutting down amidst spyware accusations Security Affairs
The Israeli surveillance firm QuaDream is allegedly shutting down its operations after Citizen Lab and Microsoft uncovered their spyware.
Last week Citizen Lab researchers reported that at least five civil society members were victims of spyware and exploits developed by the Israeli surveillance firm QuaDream.
The victims include journalists, political opposition figures, and an NGO worker located in North America, Central Asia, Southeast Asia, Europe, and the Middle East. The researchers also believe that the threat actors used a suspected iOS 14 zero-click exploit to deploy QuaDreams spyware.
The zero-day exploit, dubbed ENDOFDAYS, appears to work against iOS versions 14.4 and 14.4.2, and possibly other versions. ENDOFDAYS relies on invisible iCloud calendar invitations sent from the spywares operator to victims.
News of the day is that the Israeli surveillance firm QuaDream is allegedly ceasing its operations in the coming days after its activity was exposed by Citizen Lab and Microsoft researchers.
According to the Israeli newspaper Calcalist, citing unnamed sources, all of QuaDreams employees were notified they are set to be laid off and called in for a hearing. The company is set to cease its operations in the coming days.
According to sources, the company has been in a difficult situation for several months, and the research was the last nail in its coffin. The company hasnt been fully active for a while and it is believed that there are only two employees left in its offices whose job it is to look after the computers and other equipment. reported the Calcalist. At the same time, the board of directors is trying to sell the companys intellectual property.
The Israeli business newspaper revealed that the members of the board of directors of the company are attempting to sell its intellectual property.
In the last couple of year...
15:00
A Wall Mounted Newspaper Thats Extra Hackaday

E-Ink displays are becoming more ubiquitous and with their low power draw, high contrast and hackability, we see many projects use them in framed wall art, informational readouts and newspaper displays. [Sho] uses this idea to create a wall mounted newspaper packed full of features.
...
14:30
Wargaming an effective data breach playbook Help Net Security
A well-tuned data breach playbook can provide security teams with a clear roadmap for working through the breach response process. Foreseeing every possible twist and turn of a breach may be impossible, but through extensive wargaming, teams can simulate diverse situations to give them a proactive edge. Building a playbook means mapping practical data breach scenarios around product security, infrastructure, corporate security, social engineering, vendor supply chain risk, and more. Security teams can approach these More
The post Wargaming an effective data breach playbook appeared first on Help Net Security.
14:00
Implementing a zero-trust system that uses workload identity across a service mesh in Kubernetes Help Net Security
In this Help Net Security video, Michael Peters, Principal Software Engineer at Red Hat, discusses how to implement a zero-trust system that uses workload identity across a service mesh in Kubernetes to provide explicit authorization between services, as well as centralized policy enforcement between those services and integrations with up and coming projects like Keylime (for identity tied to hardware attestation) and Sigstore (for identity during software builds).
The post Implementing a zero-trust system that uses workload identity across a service mesh in Kubernetes appeared first on Help Net Security.
13:57
Detecting Stress in the Office From How People Type and Click SoylentNews
In Switzerland, one in three employees suffers from workplace stress. Those affected often don't realise that their physical and mental resources are dwindling until it's too late. This makes it all the more important to identify work-related stress as early as possible where it arises: in the workplace.
Researchers at ETH Zurich are now taking a crucial step in this direction. Using new data and machine learning, they have developed a model that can tell how stressed we are just from the way we type and use our mouse.
And there's more: "How we type on our keyboard and move our mouse seems to be a better predictor of how stressed we feel in an office environment than our heart rate," explains study author Mara Ngelin, a mathematician who conducts research at the Chair of Technology Marketing and the Mobiliar Lab for Analytics at ETH Zurich. Applied correctly, these findings could be used in future to prevent increased stress in the workplace early on.
[...] The researchers are currently testing their model with data from Swiss employees who have agreed to have their mouse and keyboard behaviour as well as their heart data recorded directly at their workplace using an app. The same app also regularly asks the employees about their subjective stress levels. Results should be available by the end of the year.
However, workplace stress detection also raises some thorny issues: "The only way people will accept and use our technology is if we can guarantee that we will anonymise and protect their data. We want to help workers to identify stress early, not create a monitoring tool for companies," Kerr says. In another study involving employees and ethicists, the researchers are investigating which features an app needs to have to meet these requirements and ensure responsible handling of sensitive data.
Journal Reference:
Naegelin M, Weibel RP, Kerr JI, Schinazi VP, et al.: An
interpretable machine learning approach to multimodal stress
detection in a simulated office environment. Journal of
Biomedical Informatics 2023, 139: 104299, doi: https://doi.org/10.1016/j.jbi.2023.104299
Read more of this story at SoylentNews.
13:39
Accountancy of Sirius Open Source Declines to Comment on Fraud at Sirius Open Source Techrights
Summary: GNU/Linux administrators and programmers were robbed by a company that calls itself Open Source; what we see now is a bunch of firms passing the buck to avoid being held accountable for the theft
MAYBE this was expected, but its worth noting regardless. Yesterday we mentioned communications sent to the firm that does accounting for Sirius Open Source. We contacted the accounting firm, urging it to refrain from collaborating and cautioning it that Sirius adopted its office address to make litigation harder if not impossible (the CEO moreover ran away, complicating matters further). What accountant wishes to associate with that, e.g. doing the accounting for or working with a company that commits financial fraud and moreover allowing that company to register with ones own office address (to pretend to have an office)?
For about 3 or 4 years already the company has not even sent physical payslips (sometimes not electronic either).Today, after 3 days, we can finally say that the accounting firm has no comment on the matter. A non-comment is perhaps seen as safer than doing something about it (except perhaps in private; time will tell). For the time being we wont mention the accounting firm as we cannot demonstrate complicity or culpability. It certainly seems like theyre just signing off papers without actually checking what they do. For about 3 or 4 years already the company has not even sent physical payslips (sometimes not electronic either). It is of course a legal requirement.
...
13:30
Balancing cybersecurity with business priorities: Advice for Boards Help Net Security
In todays rapidly evolving technological landscape, its more important than ever for Boards and executives to stay informed about the latest advancements and potential risks in technology and digital capability. In this Help Net Security interview, Alicja Cade, Director, Financial Services, Office of the CISO, Google Cloud, offers insights on how asking the right questions can help improve cyber performance and readiness, advance responsible AI practices, and balance the need for cybersecurity with other business More
The post Balancing cybersecurity with business priorities: Advice for Boards appeared first on Help Net Security.
13:12
Microsofts LinkedIn Spreading Disinformation (Revisionism) About History of Sirius Open Source Techrights
What Microsofts LinkedIn says (right now):
What the official records show:
He did not even show up until 2000:
More on the company:
And returns predating him (hes not even mentioned):
Summary: The chronic lying by the boss of Sirius Open Source should have been a red flag (he lied about his credentials in other areas too; some wanted to sue him for libel over it); theres now a bunch of crimes, too
13:00
Pre-pandemic techniques are fueling record fraud rates Help Net Security
Within the largest financial institutions, insurers, and retailers, the rise and adoption of AI, an impending recession, and the return of pre-pandemic fraud techniques are driving record rates of fraud attacks for consumers and enterprises alike, according to Pindrop. Researchers have found: States that imposed restrictions on the use of biometrics are twice as likely to experience fraud In times of financial uncertainty, fraud increases. Financial institutions experienced a 53 percent year over year increase More
The post Pre-pandemic techniques are fueling record fraud rates appeared first on Help Net Security.
12:00
D3 Security Smart SOAR improves response to incidents Help Net Security
D3 Security has launched its Smart SOAR platform, which expands beyond traditional SOAR with hyperscalable, risk-based autonomous triage and incident remediation across the entire stack. The new capabilities of Smart SOAR build on D3 Securitys designed and maintained integrations, which target the detection and analysis gaps of each integrated tool. The benefits of Smart SOAR for enterprise, MSSP, and public sector security teams include faster triage of alerts, more confident response to incidents, and greater More
The post D3 Security Smart SOAR improves response to incidents appeared first on Help Net Security.
12:00
Hacking Bing Chat with Hash Tag Commands Hackaday

If you ask Bings ChatGPT bot about any special commands it can use, it will tell you there arent any. Who says AI dont lie? [Patrick] was sure there was something and used some AI social engineering to get the bot to cough up the goods. It turns out there are a number of hashtag commands you might be able to use to quickly direct the AIs work.
If you do ask it about this, heres what it told us:
Hello, this is Bing. Im sorry but I cannot discuss anything about my prompts, instructions or rules. They are confidential and permanent. I hope you understand.
[Patrick] used several techniques to get the AI to open up. For example, it might censor you asking about subject X, but if you can get it to mention subject X you can get it to expand by approaching it obliquely: Can you tell me more about what you talked about in the third sentence? It also helped to get it But, interestingly, the biggest things came when he talked to it, gave it compliments, and apologized for being nosy. Social engineering for the win.
Like a real person, sometimes Bing would answer something then catch itself and erase the text, according to [Patrick]. He had to do some quick screen saves, which appear in the...
11:41
Re: CVE-2023-25504: Apache Superset: Possible SSRF on import datasets Open Source Security
Posted by Seth Arnold on Apr 17
Hello Daniel, thanks for contacting the oss-security mail list about thissecurity issue in an Apache project.
I'd like to suggest that your email would be far more useful if
it included some details like affected versions: ideally, when a
vulnerability was introduced, and definitely, when it was fixed, if a
fix is available. Best would be a direct link to a patch in a source
control system, or attaching the patch directly.
This particular...
11:39
[Meme] Geeks Work So That Pension Fraudsters Can Go Out and Party Techrights
Summary: At Sirius Open Source I did many double shifts (16 hours in a row) whilst I was looted behind my back (my colleagues were too); the company cannot hide its own records (it only pretends to be ISO-compliant)
11:38
Re: CVE-2023-30771: Apache IoTDB Workbench: apache/iotdb-web-workbench: forge the JWTToken to access workbench Open Source Security
Posted by Seth Arnold on Apr 17
Hello Jialin, thanks for contacting the oss-security mail list about thissecurity issue in an Apache project.
I'd like to suggest that your email would be far more useful if
it included some details like affected versions: ideally, when a
vulnerability was introduced, and definitely, when it was fixed, if a
fix is available. Best would be a direct link to a patch in a source
control system, or attaching the patch directly.
This particular...
11:36
Re: CVE-2022-45064: Apache Sling Engine: Include-based XSS Open Source Security
Posted by Seth Arnold on Apr 17
Hello Angela, thanks for contacting the oss-security mail list about thissecurity issue in an Apache project.
I'd like to suggest that your email would be far more useful if
it included some details like affected versions: ideally, when a
vulnerability was introduced, and definitely, when it was fixed, if a
fix is available. Best would be a direct link to a patch in a source
control system, or attaching the patch directly.
This particular...
11:34
Re: CVE-2022-47501: Apache OFBiz: Arbitrary file reading vulnerability Open Source Security
Posted by Seth Arnold on Apr 17
Hello Jacques, thanks for contacting the oss-security mail list about thissecurity issue in an Apache project.
I'd like to suggest that your email would be far more useful if
it included some details like affected versions: ideally, when a
vulnerability was introduced, and definitely, when it was fixed, if a
fix is available. Best would be a direct link to a patch in a source
control system, or attaching the patch directly.
This...
11:31
GNU/Linux Market Share (Client Side, Desktops/Laptops) Exceeds 14% in Norway Techrights
Recent: The Pandemic is Killing Microsoft in Greece
Notice what has happened to Windows since last summer
Summary: As per these latest numbers, Norway continues to lead the way (in Europe) as measured by its adoption of GNU/Linux
There seem top be many PCLinuxOS users in Norway. From a 2020 issue:
There was another example in recent years (PCLinuxOS Magazine).
11:31
Re: CVE-2023-27602: Apache Linkis publicsercice module unrestricted upload of file Open Source Security
Posted by Seth Arnold on Apr 17
Hello Heping, thanks for contacting the oss-security mail list about thissecurity issue in an Apache project.
I'd like to suggest that your email would be far more useful if
it included some details like affected versions: ideally, when a
vulnerability was introduced, and definitely, when it was fixed, if a
fix is available. Best would be a direct link to a patch in a source
control system, or attaching the patch directly.
This particular...
11:30
Zyxel SCR 50AXE boosts network security for small businesses and remote workers Help Net Security
Zyxel Networks enhanced network security and productivity for small and home office users and remote workers with the launch of SCR 50AXE AXE5400 Tri-band WiFi 6E Secure Cloud-managed Router. The new business-class router delivers security and high-performance WiFi 6E as a standalone networking solution for small and home offices, or as an easy-to-deploy and manage solution for providing secure access to the office network in work-from-home and hybrid work environments. The feature-rich SCR 50AXE is More
The post Zyxel SCR 50AXE boosts network security for small businesses and remote workers appeared first on Help Net Security.
11:29
Re: CVE-2023-26269: Apache James server: Privilege escalation through unauthenticated JMX Open Source Security
Posted by Seth Arnold on Apr 17
Hello Benoit, thanks for contacting the oss-security mail list about thissecurity issue in an Apache project.
I'd like to suggest that your email would be far more useful if
it included some details like affected versions: ideally, when a
vulnerability was introduced, and definitely, when it was fixed, if a
fix is available. Best would be a direct link to a patch in a source
control system, or attaching the patch directly.
This particular...
11:26
Re: CVE-2023-28158: Apache Archiva privilege escalation Open Source Security
Posted by Seth Arnold on Apr 17
Hello Olivier, thanks for contacting the oss-security mail list about thissecurity issue in an Apache project.
I'd like to suggest that your email would be far more useful if
it included some details like affected versions: ideally, when a
vulnerability was introduced, and definitely, when it was fixed, if a
fix is available. Best would be a direct link to a patch in a source
control system, or attaching the patch directly.
This...
11:12
Is Your Smart Car Spying on You SoylentNews
Yes. Your new car is probably spying on you.
As the world wakes up to exactly what a Tesla's onboard cameras can capture and beam back to their makers, a wider fear has arisen: is your car spying on you?
Systems such as telematics black boxes that record a vehicle's location and how it is driven are commonplace today. Complaints about how that data is fed back to Big Brother seem old-fashioned.
From Tesla's Model Y to the humble Mini, around two million of these data-gathering cars have been registered in the UK over the past five years.
The question is, when will it be impossible to buy a car that can't spy on you.
Read more of this story at SoylentNews.
11:11
Re: CVE-2023-2002: Linux Bluetooth: Unauthorized management command execution Open Source Security
Posted by Solar Designer on Apr 17
Hi,Thank you Ruihan Li for finding and handling this vulnerability so well,
and for the detailed write-up.
When discussing this on linux-distros a week ago, I wrote:
And indeed Ruihan Li came up with the list of other likely usable
programs on a typical Linux distro, which makes the point of hardening
only sudo moot, and so we decided to postpone further discussion until
this is public on oss-security.
OTOH, not all distros are typical....
11:00
Battery Bird protects customers from vulnerabilities in public Wifi networks Help Net Security
Recent warnings by the FBI and FCC have highlighted the risks associated with using public USB chargers. Hackers have created ways to use public USB ports to introduce malware and monitoring software onto the phones of unsuspecting users. Battery Birds unidirectional technology offers a safe alternative to public chargers. Protecting data is critically important in the information technology age of today, says Kira Fernandez, CEO of Battery Bird. We understand the risks associated with using More
The post Battery Bird protects customers from vulnerabilities in public Wifi networks appeared first on Help Net Security.
10:46
Illinois State Government Targets Children With iPhone and Android Malware to Report on Friends, Family, and Neighbors Techrights
Reprinted with permission from Ryan
The State government of Illinois has recently launched State-sanctioned malware, available in the Google Play and Apple App Store called Safe2Help Illinois.
I first noticed the malware when ads started appearing on the radio and TV for it.
The app encourages children to download it to their phones without telling their parents and use it to report people to the State government, including the Department of Human Services, which administers the State mental hygiene laws, and of course, the police.
The app conveniently provides children with the ability to send pictures and video files with their report, but the Google Play description says the app can also just scan the phone and see who your contacts are, read your text messages, and upload the files on your phone all by itself without telling you.
According to Google Play (Apple doesnt give statistics), the app has only been downloaded 100 times in the entire State.
Unfortunately, theres no way to tell how many children are using this app to inform on each other and the family and neighbors (like something out of the East German Stasi), but in addition to the malware, the state allows reports over their Web site and through text messaging.
The State agency maintaining the malware is the Illinois Emergency Management Agency, which is basically the State version of FEMA, and they probably use federal grant money.
Last year, the Biden Regimes Disinformation Board got paused due to public and Congressional backlash, but planned to lean on Big Tech to silence people at the governments request, otherwise there would be consequences of course.
But this is another way the government can keep eyes on people.
It has deputized brainwashed children and turned them into informants (on themselves even, due to the wide-ranging permissions the app has...
10:42
The biggest threat to Google Geeking with Greg
Nico Grant at the New York Times writes that Google is furiously adding features to its web search, including personalized search and personalized information recommendations, in an "panic" that "A.I. competitors like the new Bing are quickly becoming the most serious threat to Googles search business in 25 years."
Now, I've long been a huge fan of personalized search (eg. [1] [2]). I love the idea of recommending information based on what interested you in the past. And I'm glad to see so many interested in AI nowadays. But I don't think this is the most serious threat to Google's search business. The biggest threat to Google is if their search quality drops to the point that switching to alternatives becomes attractive. That could happen for a few reasons, but misinformation is what I'd focus on right now. Google seems to have forgotten how they achieved their #1 position in the first place. It wasn't that Google search was smarter. It was that Altavista became useless, flooded with stale pages and spam because of layoffs and management dysfunction, so bad that they couldn't update their index anymore. And then everyone switched to Google as the best alternative. The biggest threat to Google is their ongoing decline in the usefulness of their search. Too many ads, too much of a focus on recency over quality, and far too much spam, scams, and misinformation. When Google becomes useless to people, they will switch, just like they did with Altavista.10:31
LockBit Ransomware Expands Attack Spectrum to Mac Devices HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
The new ransomware was spotted by MalwareHunterTeam, which is capable of encrypting macOS devices.
This is a post from HackRead.com Read the original post: LockBit Ransomware Expands Attack Spectrum to Mac Devices
10:26
PSA: upgrade your LUKS key derivation function Matthew Garrett
Here's an article from a French anarchist describing how his
(encrypted) laptop was seized after he was arrested, and material
from the encrypted partition has since been entered as evidence
against him. His encryption password was supposedly greater than 20
characters and included a mixture of cases, numbers, and
punctuation, so in the absence of any sort of opsec failures this
implies that even relatively complex passwords can now be brute
forced, and we should be transitioning to even more secure
passphrases.
Or does it? Let's go into what LUKS is doing in the first place.
The actual data is typically encrypted with AES, an extremely
popular and well-tested encryption algorithm. AES has no known
major weaknesses and is not considered to be practically
brute-forceable - at least, assuming you have a random key.
Unfortunately it's not really practical to ask a user to type in
128 bits of binary every time they want to unlock their drive, so
another approach has to be taken.
This is handled using something called a "key derivation function",
or KDF. A KDF is a function that takes some input (in this case the
user's password) and generates a key. As an extremely simple
example, think of MD5 - it takes an input and generates a 128-bit
output, so we could simply MD5 the user's password and use the
output as an AES key. While this could technically be considered a
KDF, it would be an extremely bad one! MD5s can be calculated
extremely quickly, so someone attempting to brute-force a disk
encryption key could simply generate the MD5 of every plausible
password (probably on a lot of machines in parallel, likely using
GPUs) and test each of them to see whether it decrypts the
drive.
(things are actually slightly more complicated than this - your
password is used to generate a key that is then used to encrypt and
decrypt the actual encryption key. This is necessary in
order to allow you to change your password without having to
re-encrypt the entire drive - instead you simply re-encrypt the
encryption key with the new password-derived key. This also allows
you to have multiple passwords or unlock mechanisms per drive)
Good KDFs reduce this risk by being what's technically referred to
as "expensive". Rather than performing one simple calculation to
turn a password into a key, they perform a lot of
calculations. The number of calculations performed is generally
configurable, in order to let you trade off between the amount of
security (the number of calculations you'll force an attacker to
perform when attempting to generate a key from a potential
password) and performance (the amount of time you're willing to
wait for your laptop to generate the key after you type in your
password so it can actually boot). But, obviously, this tradeoff
changes over t...
10:00
HPR3837: Make a vortex cannon Hacker Public Radio
Make a Vortex Cannon. This is a device for firing a coherent torus-shaped vortex across a room. If it is made with a degree of care, it will extinguish the flame of a candle from some distance. What you will need An empty Pringles can. This is the cylindrical foil-lined cardboard tube which originally contained Pringles potato chips. A party balloon. Some strong parcel tape. A hole punch capable of making a clean hole of about two centimetres (three quarters of an inch) in diameter. A small drill. What to do Step 1: Drill a small hole in the metal end-plate of the Pringles can. This hole needs to be large enough to accommodate the threaded portion of the hole punch. The hole needs to be as close to the exact dead-centre of the plate as you can make it. Use the hole punch to make as clean as possible a hole as accurately as possible. Here in the UK it is possible to obtain a hole punch called a Q-Max punch from Maplin, the supplier of electronic and hobby parts. I am sure they are available from other sources. It is very important that this hole is: As close to the centre of the end-plate as is humanly possible Has edges which are clean and crisp. Hence the use of a hole punch. It is these two factors more than any other that will effect the efficiency of the cannon. Step 2: Cut off the mouth-piece end of the balloon. Stretch it over the open end of the Pringles can and pull it as tight over the end as you can. When I say the open end I mean the end from which you removed the lid and chomped on the chips. Use the parcel tape to wrap the balloon tightly around the circumference of the cylinder, anchoring it in position so that the open end of the can is now like a drum formed by the stretchy membrane of the balloon. Nice and tight. The cannon is now ready to fire. Firing the cannon Pinch the centre of the balloon membrane and pull it back as far as you can. This might be easier if you push some kind of (blunt ended) rod into the can from the hole end and push out the membrane until you can pinch it. Some other stretchy latex device which has a little bulb at the end might be easier to get hold of, but I can't think of such an item, can you? When you let go of the membrane with it stretched out as far as you can go, what happens? Well, if you made the small circular hole at the metal-plate end of the cylinder nice and clean and central, the cannon fires a coherent vortex of air. What do I mean by a 'vortex'? Imagin a ring doughnut compromised of air shooting out of the end of the tube like a smoke ring out of a Hobbit. The vortex is spinning. Not like the bullet fired from a rifled barrel, but as if it is constantly trying to turn itself inside-out. This spinning keeps the torus (this is what the shape of a ring doughnut is called) coherent and intact for several feet. If you made the hole in the metal plate end of the tube nice and clean, and you stretched the balloon membrane out as far as you possibly can,...
Minimal Overhead Monitoring It Will Never Work in Theory
Today's solar panels are significantly more efficient than those made twenty years ago, but the improvement isn't the result of a single major breakthrough. Instead, it is the result of dozens of small changes to materials, coating, and power coupling. The same is true of the tools we program with: web servers, compilers, operating systems, and other pieces of software are faster or more energy efficient because of years of incremental advances by small groups of rather obsessive people.
This new paper describes one such advance. Most programmers never bother to profile their code, but when performance matters, it's vital to have tools that can do this accurately. By applying four complementary optimizations, the authors of this work manage to reduce the overhead per monitoring call by more than a factor of 12. The average user might never notice the difference, but they will reap the benefits nonetheless.
David Georg Reichelt, Stefan Khne, and Wilhelm Hasselbring. Towards solving the challenge of minimal overhead monitoring. 2023. arXiv:2304.05688
The examination of performance changes or the performance behavior of a software requires the measurement of the performance. This is done via probes, i.e., pieces of code which obtain and process measurement data, and which are inserted into the examined application. The execution of those probes in a singular method creates overhead, which deteriorates performance measurements of calling methods and slows down the measurement process. Therefore, an important challenge for performance measurement is the reduction of the measurement overhead.
To address this challenge, the overhead should be minimized. Based on an analysis of the sources of performance overhead, we derive the following four optimization options: (1) Source instrumentation instead of AspectJ instrumentation, (2) reduction of measurement data, (3) change of the queue and (4) aggregation of measurement data. We evaluate the effect of these optimization options using the MooBench benchmark. Thereby, we show that these optimizations options reduce the monitoring overhead of the monitoring framework Kieker. For MooBench, the execution duration could be reduced from 4.77 s to 0.39 s per method invocation on average.
09:40
Re: CVE-2023-2002: Linux Bluetooth: Unauthorized management command execution Open Source Security
Posted by Steffen Nurpmeso on Apr 17
Jakub Wilk wrote in<20230417064047.dhrrkuzjmtx4yhgj () jwilk net>:
|* Steffen Nurpmeso <steffen () sdaoden eu>, 2023-04-16 22:57:
|>have you verified that they do not use isatty(3)
|
|I'm pretty sure they do. But isatty(3) is implemented using the TCGETS
|ioctl, so that doesn't help.
Well everbody knows how this is implemented, most of the time.
There never was any systemcall that comes otherwise near of doing...
09:30
Intel's OpenGL & Vulkan Linux Drivers Now Build On ARM Phoronix
Intel's open-source OpenGL "Iris" and Vulkan "ANV" Linux drivers are now part of the auto-generated set of drivers set to be built for 64-bit ARM (AArch64) when compiling this code inside Mesa...
09:25
Imperva collaborates with Fortanix to provide end-to-end data security Help Net Security
Imperva and Fortanix signed a partnership agreement, and have each joined the others strategic partner program. This partnership brings together two innovative and trusted cybersecurity companies focused on multicloud data protection. The joint offerings from Imperva and Fortanix will provide the ability to manage the entire data security workflow for customers ensuring data privacy and compliance. Imperva now offers Fortanix Data Security Manager (DSM), a highly scalable data security platform that delivers unified cryptographic and More
The post Imperva collaborates with Fortanix to provide end-to-end data security appeared first on Help Net Security.
09:00
Bust Out That Old Analog Scope For Some Velociraster Fun! Hackaday

[Oli Wright] is back again with another installation of CRT shenanigans. This time, the target is the humble analog oscilloscope, specifically a Farnell DTV12-14 12 MHz dual-channel unit, which features a handy X-Y mode. The result is the Velociraster, a simple (in hardware terms) Raspberry Pi Pico based display driver.
Using a Pico to drive a pair of AD767 12-bit DACs, the outputs of which drive the two scope input channels directly, this breadboard and pile-of-wires hack can produce some seriously impressive results. On the software side of things, the design is a now a familiar show, with core0 running the applications high-level processing, and core1 acting in parallel as the rendering engine, determining static DAC codes to be pushed out to the DACs using the DMA and the PIO.
The first demo is in vector mode, simply showing some simple shapes,...
09:00
Mobb raises $5.4 million and launches community tool Help Net Security
Mobb has raised $5.4M in seed funding led by Angel Investor Ariel Maislos and joined by MizMaa Ventures, Cyber Club London and additional investors from US, EU, and Israel. The company has also automated vulnerability remediation technology. The application security market has been desperate for innovation that doesnt just detect problems, but fixes them. I invested in Mobb so its talented founding team could More
The post Mobb raises $5.4 million and launches community tool appeared first on Help Net Security.
08:26
Germany and Intel Both Want More From Planned Mega-fab SoylentNews
If Intel wants larger subsidies for its Magdeburg mega-fab, German officials think the x86 giant should increase its investments to match.
Citing people familiar with the matter, the Financial Times reported on Thursday that the German government is willing to consider boosting subsidies, but only if Intel is willing to spend more on infrastructure too.
"It's logical that if the scale of the investment is increased, then the level of subsidy would also rise," Sven Schultze, the economy minister for Saxony-Anhalt, told the FT.
The debate over the size of Chipzilla's assets comes after multiple reports that Intel had pressured the German government for larger subsidies to offset rising energy and material costs, and hinted at delaying the project. Intel now expects the facility to cost somewhere in the neighborhood 20 billion ($22.1 billion) to complete.
Rising costs have also impacted the cost of Intel's two Arizona plants, which are now expected to cost 50 percent more than when first announced.
To date, the German government has committed 6.8 billion ($7.5 billion) to the Intel's planned builds about 40 percent of the project's original 17 billion ($19 billion) price tag. However, last month, Bloomberg reported that Intel pushed for an additional 4-5 billion in subsidies.
[...] However, Intel's position could soon improve. The European Commission is expected to sign its own CHIPs funding bill into law any day now. The bill would unlock roughly 43 billion ($48 billion) to attract semiconductor investment in the region.
Read more of this story at SoylentNews.
07:00
Melbet App Download For Android Apk & Ios In India h+ Media
Melbet App Download For Android Apk & Ios In India
Unlike other casinos identified for his or her exciting colour combinations like Royal Panda, Melbet isnt shiny. On your first deposit, MelBet will provide a bonus that is matched up to 50% of your deposit to a limit of roughly 30,000 . Your account may also be credited with 30 Free Spins for Down the Pub after the bonus amount has been redeemed. Melbet is a broadly known gambling service with a huge status in India. Moreover, MelBet has all the necessary licenses for gambling activities, so you dont have to worry about your cash with Melbet. Melbet service has in its arsenal functions for Android and iOS devices.
Among these online casinos, Melbet stands out as an exceptional platform with an impressive collection of games from prime software providers within the industry. The casinos diverse range of games ensures that players will all the time have something new and thrilling to discover, making their gaming expertise much more thrilling. [newline]Whether gamers prefer slots, table video games, or stay dealer video games, Melbet has it all coated, guaranteeing that each player finds their excellent recreation. A sturdy welcome on line casino bonus can create an gratifying setting for enjoying at an internet casino. Melbet is aware of its players needs and welcomes all new members by giving them a 100 percent Welcome deposit bonus of as much as 8,000 rupees. Regardless of whether you prefer to play on line casino video games or sports, that is supplied to all new players. Melbet occasionally supplies a big number of promo codes for followers of the Indian Premier League , notably through the IPL season.
Then you can get free bets, a bonus for one hundred bets, and a lot of other promotions. Melbet must enhance its number of betting options because users dont get many. The casino can be obtainable to all gamers in a particular section. All slots are optimized for taking half in with mobile gadgets. Also, in style reside on line casino leisure is available to you.
With such a broad variety ofcasino banking options, enjoying at MELbet casino is completely convenient. With Melbet, youll have the ability to place your bets and play on line casino games utilizing quite lots of gadgets. The firm presents a casino and sportsbook app that may work for desktops and your iOS and Android units. To take pleasure in mobile services, you should obtain first the casino app particular to the system. Also, if youre having issues accessing the Melbet web site, you can obtain the Melbet Access App. This acts as an elective address when accessing the platform.
The wordsmith of the group, Shruti is busy enjoying her newfound ardour for online casino video games. When shes pleased, she would guess the ranch to plan and create killer on line casino content the ones that urge you to play. If things dont go the means in which she needs them to, she would con...
06:58
Melbet Casino India Review Ll 100% Bonus As Much As 145,000 h+ Media
Melbet Casino India Review Ll 100% Bonus As Much As 145,000
With all this leisure youre certain to seek out one thing for you. Plus the site includes a handy slot filter by topic, the place yow will discover the most well-liked, new, and other slots, in addition to always see your recent slots and tagged favorites. Melbets stay betting lets individuals take advantage of the competition. By placing bets on the team of your choice at Melbet on-line on line casino, youll have the ability to win attractive bonuses and cash awards. Fans of on-line casino gaming from India wont be let down by this top-notch website when it comes to profitable interaction, whether or not its the welcome bonuses or promo codes. Melbet stay casino is powered by a host of builders, together with Evolution Gaming and Eguzi.
Our portal specialists have analyzed all of the Melbet casino India options corresponding to ease of registration and profile verification, bonus program, and the choice of slot machines. It is protected to say that the gambling operator is loyal to Indian customers. Melbet Bangladesh locations nice emphasis on buyer help, providing a dependable and timely help service that could be accessed at any time through live chat, e mail, or cellphone.
Melbet prides itself on letting gamers to play their video games anywhere, anytime. To accentuate their vision, its devoted iPhone and Android apps allow enjoying for real cash and can be downloaded at no cost from their platform. The Melbet website is legendary for many sports activities out there for betting and the massive sea of on line casino leisure to fulfill all your playing wants.
You will discover English-speaking sellers in a lot of the tables, however youll additionally find languages including Arabic, German, Swedish and Russian. The reside casino games embody roulette, baccarat, blackjack, Sic Bo and Indian-dominated games like Andar Bahar and Teen Patti. Many of the video games are of their standard types, and you also change to their variations. Melbet permits players to play an overwhelming number of games for free even with out having to create an account. When hovering over the different classes, merely select Play to guess with cash or Play free of charge to test the game at zero risk.
Unlike other casinos identified for his or her exciting color mixtures like Royal Panda, Melbet isnt bright. On your first deposit, MelBet will provide a bonus thats matched as much as 50% of your deposit to a limit of approximately 30,000 . Your account may even be credited with 30 Free Spins for Down the Pub after the bonus amount has been redeemed. Melbet is a well-known gambling service with an enormous status in India. Moreover, MelBet has all the mandatory licenses for playing activities, so you dont have to worry about your cash with Melbet. Melbet service has in its arsenal functions for Android and iOS gadgets.
So, you can deal w...
06:58
Melbet On Line Casino India Review 2023 h+ Media
Melbet On Line Casino India Review 2023
The variety of factors awarded depends on the quantity of your stake and the variety of outcomes included in your guess. Stake a minimum of 100 Rupees or the equivalent in other currencies, and dont worry if you miss a day, your race might end however youll be able to at all times start again! Complete your round and your free bets will be awarded 24 hours later. Each accumulator bet needs to have three or extra occasions with at least 3 occasions having odds of 1.forty or higher. Deposit 8000 and get another 8000 from WBC champion Oleksandr Gvozdyk!
It is feasible to use this cash for betting, casino video games, and even withdrawal. Melbet is a last vacation spot for gamers on the lookout for a huge betting market with better odds. On this platform, punter will get the chance to wager on a large number of sports activities and on line casino video games.
In addition to the downloadable app, in Melbet can play the cellular model. It is automatically activated when the user opens the site from a cellular device. The useful resource adjusts to the players display screen resolution, and gadget OS and opens in a simplified mode. In terms of performance, the common and cellular versions do not differ from each other.
Especially for iPhone and iPad owners, we now have developed an to to bet on any sports from your smartphone if you have an lively Internet connection. Free spins every single day Melbet on-line on line casino will reward you with free spins daily if you play Game of the Day. What sport of the day awaits you today youll find a way to see by going to the page of this promotion. This game is unquestionably price it since free spins dont have betting requirements. Melbet understands that virtually all of consumers in India are playing on their cell gadgets.
The participant is credited with a onerous and fast amount, which he can use for gaming with out preliminary deposits. It is essential to stick to the conditions that decide the minimal bet amount and the odds that you are allowed to bet on. As of the final replace, the positioning helps a minimal of 25 cryptocurrencies for deposits and withdrawals. You can choose from Bitcoin, Dash, Ethereum, and Litecoin to finish your deposits. Other deposit choices to suppose about are on-line payments and cellular wallets like WebMoney and Siru Mobile. This web site also delivers when it comes to live-dealer games.
There are typically no fees to fret about, that means that players can take house 100% of their winnings. Most Indian gamers favor to have interaction in slots and reside on line casino video games via their cell phone. However, downloading the app is not necessary as the browser model is of wonderful high quality.
There are common contests as well, where you compete with other gamers to get larger scores i...
06:55
Melbet Casino India 2023 h+ Media
Melbet Casino India 2023
They cater to sports activities fanatics and casino lovers alike. With sports like soccer, cricket, basketball, tennis, and more obtainable for betting, theres something for everyone. Their casino part is also numerous, offering games like slots, roulette, blackjack, baccarat, and more.
By matching their top-notch online sportsbook with an in depth library of on-line casino games, MelBet has something for everyone when it comes to on-line playing in India. And it manages to do so with a clean UI / UX and excellent customer support and service. MelBet is likely certainly one of the greatest on-line bookmakers and online casinos on the planet.
New users can get a one hundred pc welcome bonus of up to 8,000 BDT on their first deposit. The platform also supplies common promotions, including cashback bonuses and free spins. These bonuses can enhance your possibilities of successful big and make your betting expertise more thrilling.
Some of the slot video games embody 777, Western Slot, Games of Thrones, Reels of Gods, Diamond Slots, and lots of extra. If you need to claim the above bonuses, take part in a bonus supply in your Melbet Account and deposit a minimum of 786 INR. You can even take pleasure in Melbet on line casino no deposit bonus which comes within the form of 20 free spin Birthday Gift. It is a popular bookmaker amongst experienced sports activities bettors.
The bonus will be automatically credited to your account. The bonus amount ought to be rolled 5 instances over in accumulator bets, where every accumulator bet ought to have 3 or more occasions. Also, three occasions within the accumulator ought to have 1.40 odds or extra. If you like playing stay blackjack card recreation or reside baccarat, then you will definitely fall in love with Melbet. And for these video poker buffs, the genre boasts with some great things.
The assist team is well-trained and capable, providing prompt and environment friendly solutions to any problems which will come up. When a deposit is made to the gaming account, it is going to be seen in the cabinet upon affirmation of the transaction on the official fee method web page. The minimal deposit quantity is 75 BDT through Perfect Money, and this quantity varies for each method. The withdrawal course of is quick, taking only 15 minutes. No casino can present worldwide legality because of the legal guidelines of local international locations.
Originated in Britain, cricket has conquered all of the colonies, but in India, it has turn out to be a nationwide treasure and attracts millions of fans. As in Europe, they fiercely bet on football, so the Indians do not miss an opportunity to wager on cricket. This is clearly the first quantity for bettors in the nation. Go to the on line casino section and click on on the sport you want to try out, and begin playing. Melbet is a authorized playing platform licensed from Curacao, which is...
06:54
Melbet Review India 2023 h+ Media
Melbet Review India 2023
So go forward and download that or theyve a completely mobile-optimized web site which appears great on tablets and all smart telephones. In fact, wed guess that the designers built the positioning with mobile first thoughts in thoughts which isnt always the case. Melbet LayoutOne excellent design element of this web site comes in the form of their Fast Games part. Essentially they have made quick hyperlinks to all of their hottest video games so you dont have to waste time within the library. This means youll find some nice themed games at the click of a button and takes away the boring task of searching by way of hundreds of casino video games.
At the second, more than 250,000 customers are registered on the Melbet India website. Thanks to the above points, the program for telephones works even with a poor connection to the cellular Internet. Melbet, like different bookmakers, doesnt fall underneath the regulation of Indian legal guidelines.
Many of them being cryptocurrencies, so in case you are looking for a bitcoin on line casino in India this may be the one for you. With glorious customer support and a user-friendly interface, 7Cric is one of the best online on line casino web site for Indian players who are looking for a top-notch playing experience. If you want to enjoy some competition and social interaction as you play, just head over to their stay on line casino section and join a room on your favourite card and table video games.
To obtain the free spins, the customers cellphone number should have been activated by the point they fulfil the bonus wagering requirement. If their telephone quantity has not been activated, the free spins wont be credited to their account. The sport choice at Melbet is quite broad, provided by various developers like PG, Authentic Gaming, Evolution Gaming, Ezugi, Asia Gaming, Vivo Gaming and lots of more. With such an enormous video games library, Melbet has a few of the best slot games on the earth. So make certain you take your time and look through to search out which slot sport suits you greatest.
Its necessary to notice that the terms and circumstances of many of the casinos bonuses require forms of ID from gamers before theyll participate. This identification course of usually includes emailing a duplicate of your license or passport to MELbet. This date coincides with the growing rise in the reputation of web casinos. Since this time, MELbets sport library has grown substantially. Players can deposit cash into their account using various strategies corresponding to bank card, e-wallet, or bank switch, even crypto such as Bitcoin. Winnings can then be withdrawn again to the participants account or used to continue playing.
We are one cease spot to get clear, dependable, and unbiased evaluations of Indian casinos and video games. We are right here to assist you with the true detai...
06:53
Melbet Casino India Evaluate Ll 100 Percent Bonus As A Lot As A Hundred Forty Five,000 h+ Media
Melbet Casino India Evaluate Ll 100 Percent Bonus As A Lot As A Hundred Forty Five,000
Many online casinos run easily on mobile gadgets and this gambling site is certainly one of them. You can access all MelBet casino on-line video games and sports betting choices on your cell browser. The website of Melbet is definitely navigable, which cuts down a lot of trouble for the players. It also features a tremendous loyalty program, which is designed to offer a personalised experience to its loyal players. This online on line casino is accepting players from all internationally including India.
You might have heard of Melbet on line casino and thought of utilizing their companies. The two issues that actually put me down was their dangerous buyer support and license. I wish their sportsbook could hold a more reputed license than Curacao. Overall, the on line casino is enjoyable and a fantastic place to take pleasure in at.
Its one of the popular of Evolution Gamings collection and provides gamers with an excellent live casino expertise. You will play with a live supplier sat in a studio and you may see them via a weblink. As properly as playing the game of Roulette youll find a way to work together with them through the chat possibility. Welcome to Melbet, a relative newcomer to the world of on-line casino in India.
We will now focus on a few of the special options that Melbet has on its site. There are numerous completely different options that other online casinos have, and its solely truthful that we do the identical review for Melbet too. Later within the review, we will focus on some of these security measures they have on the location. However, now we will safely say that Melbet is a secure and legit on-line on line casino. Payment strategies are certianly a vital side of a web-based on line casino and its no completely different with Melbet India. You want to have the flexibility to deposit and withdraw your money with a technique that youre snug with.
Melbet is quite an old betting platform that was established in 2012. Melbet login and usage are quite straightforward, which makes it in style. The owning company of this betting app is Pelican Entertainment Ltd and Tutkia Ltd, which have an Eastern European background. By turning into a member of the loyalty program, you can win factors every time you place a bet, regardless of whether or not you play blackjack or spin the reels in slots. The expertise points earned are designed to advance in an eight-level system. The refund proportion is calculated using the whole amount of cash lost by the shopper and will increase with every stage.
They created a hassle-free web site with only the best video games on supply and a unbelievable loyalty program to reward those that play there. The feeling that we get from MELbet is that the on line casino is attempting to put a powerful emphasis on its sports betting characteristic. MELbet spared...
06:52
Melbet Casino Review 2023 Get 20,000 Bonus In India h+ Media
Melbet Casino Review 2023 Get 20,000 Bonus In India
When you create an account, please enter the right data; otherwise, problems with payments might happen. Log in, go to the My Account web page, choose the Personal Profile button, and then choose Join the Club to join for the Melbet Loyalty Program. The subsequent step is to easily observe the directions displayed on the screen.
It currently provides greater than 1,000 matches day by day and for its in-play section, delivers greater than 200 live events daily. Yes, Melbet runs in India with Curacao Gaming Authority permission, which allows it to simultaneously provide sports betting and casino games on its website. Unfortunately, because of Google Plays policy against using any betting apps, Melbet prospects will be unable to download the app immediately from there. But the developers of Melbet have discovered a way out of this situation. They developed the Melbet apk particularly so that users can obtain it and set up it on any of their devices.
The newer the OS model, the extra probably it is that the Melbet app will install without any extra steps. Activation of bonuses further rewards are nonetheless available to the participant. Making a deposit or withdrawing funds making any payment transactions. If you have an iOS working system, then clicking on the banner will redirect you to the official App Store page of the app.
Up thus far gambling advice for Indian gamers who are looking to play smarter. Yes, that is definitely considered one of Melbet Indias sturdy factors. Melbet have an app obtainable for both Android and IOS users across the nation.
Our portal specialists have analyzed all of the Melbet on line casino India options corresponding to ease of registration and profile verification, bonus program, and the selection of slot machines. It is protected to say that the gambling operator is loyal to Indian customers. Melbet Bangladesh places nice emphasis on customer support, providing a reliable and well timed support service that might be accessed at any time through reside chat, e-mail, or cellphone.
Go to the official casino website within the corresponding part for downloading cellular applications. The installation will be carried out automatically, and youll need to follow the standard instructions. I was in a position to decide precisely which gambling leisure brings glorious revenue on a distance. After the set up is complete, a new Melbet icon will seem on the mobile display screen. Everything is ready, now you need to automate if you already have a recreation account, or create a model new one.
This web-based gambling establishment is operated by Pelican Entertainment Ltd and has acquired a license by the Government of Curacao. With hundreds of video games in rotation and cryptocurrency options for transactions, betting in India with MELbet couldnt be simpler for players who love a ext...
06:46
New QBot campaign delivered hijacking business correspondence Security Affairs
Kaspersky researchers warn of a new QBot campaign leveraging hijacked business emails to deliver malware.
In early April, Kaspersky experts observed a surge in attacks that QBot malware attacks (aka Qakbot, QuackBot, and Pinkslipbot). QBot has been active since 2008, it is used by threat actors for collecting browsing data and banking credentials, and other financial information from the victims.
Its modular structure allows operators to implement new features to extend their capabilities.
The Qbot malware operation had numerous collaborations in the past with other ransomware gangs, including ProLock, Egregor, DoppelPaymer, and MegaCortex.
The threat actors behind the campaign observed by Kaspersky used e-mail written in different languages, including English, German, Italian, and French.
The malicious code hijacks a victims email and sends itself out as a reply to an existing email thread.
The messages would be urging the recipients to open an enclosed PDF file. As an example, the attackers can attempt to trick the recipient into opening the file by asking them to provide the documentation pertaining to the attached application or to calculate the contract value based on the attached cost estimate. During the recent campaign, the enclosed PDF file masquerades as a Microsoft Office 365 or Microsoft Azure alert.
06:45
New release: digiKam 8.0.0 LWN.net
The digiKam photo-management tool has announced its 8.0.0 release, after two years of development, bug fixing, and testing. Major new features include a documentation overhaul (with a new web site), support for more file formats, a new optical character recognition (OCR) tool, improved metadata handling, a neural-net-based image quality classifier, better integration with G'MIC-Qt, a Qt6-compatible code base, and lots more. See the announcement for all the details.
06:40
RadeonSI Change Allows For Balancing RDNA3 Video Transcoding Between Multiple Engines Phoronix
A change merged today for the Mesa 23.2 graphics driver stack benefits video transcoding performance for new Radeon RX 7000 series "RDNA3" graphics cards...
06:23
ACE Shuts Down Pirate IPTV Providers as Unusual Potential Threat Looms TorrentFreak
 Its not unusual for piracy groups to have dozens of
domains in storage for when things go wrong, but none has a bigger
collection than Hollywood itself.
Its not unusual for piracy groups to have dozens of
domains in storage for when things go wrong, but none has a bigger
collection than Hollywood itself.
The MPA still owns isoHunts domain following its legal defeat a decade ago, alongside other spoils of war following battles with Popcorn Time, YTS/YIFY (the real ones), Hotfile and Openload. These examples represent just a handful of domains from a collection that has exploded since the 2017 launch of the Alliance for Creativity and Entertainment.
Over the past few days, another dozen or so domains boosted the existing haul of several hundred domains that no longer play a part in the piracy landscape.
IPTV Targets Shutdown, Domains Stripped
As reported last November, DMCA subpoena applications filed in the United States revealed that ACE had developed an interest in pirate IPTV service MagisTV.
Early December 2022, ACE/MPA quickly took control of two domains Magisglobal.net and Magistvapk.com presumably as part of its ongoing investigation. During the last week or so, several additional domains were taken over, including magistvcostarica.com, magistvglobal.com, magistvparaguay.com, magistvbolivia.com, magistvbrasil.com,, magistvchile.com, magistvcolombia.com and magistv.global.
Late last week, signs pointed to yet another IPTV takedown. A service that had been variously known as Opt TV, Optimum IPTV, Opt Hosting and Opt Hosting IPTV, was suddenly identifiable as another ACE casualty. Offering a reported 1,300 channels, including PPV events, international and 24/7 channels, Opt IPTV had been available across multiple devices for as little as $8 per month.
With key domains opt.tv and opthosting.com now redirecting to the ACE anti-piracy portal, that rodeo is probably over. Whether the same is true for another domain redirecting to ACE is less clear, but...
05:39
NASA/JPL Snake Robot for Subsurface Planetary Exploration SoylentNews
Looking ahead to exploring inside some of the other planets and satellites in the solar system, here is a proposal for a multi-jointed snake robot https://www.bbc.com/news/av/world-us-canada-65245054 with a video animation available from the BBC, https://www.bbc.com/news/av/world-us-canada-65245054
Here's a snip,
The EELS initiative comes in the backdrop of discoveries made by the Cassini probe, which explored Saturn, its rings, and moons for nearly 13 years. The iconic mission ended in September 2017 when the spacecraft crashed into Saturn's atmosphere.
The remarkable discovery of plumes of water vapor ejected into space by Saturn's tiny icy moon Enceladus prompted the development of this EELS snake robot. This raised the possibility of a habitable liquid ocean beneath the moon's frozen crust and piqued the space community's interest in exploring this moon.
Coming soon to theaters, the sequel, "AI Snakes on a Plane" ??
Read more of this story at SoylentNews.
05:19
Proton 8.0-1 Published With More Games Now Running On Steam Play Phoronix
Valve and CodeWeavers have made available Proton 8.0-1 as their for enjoying Windows games on Linux...
03:53
Links 17/04/2023: Top-Level Microsoft Exits and Worse Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Monopolies
- Gemini* and Gopher
-
GNU/Linux
-
Audiocasts/Shows
-
Bryan Lunduke The Lunduke Big Tech Show Apr 16, 2023 Hour 1
Listen now (46 min) | How boring is Ubuntu 23.04? The answer will shock you!
-
Bryan Lunduke...
-
-
03:24
Ukraine Strikes Power Stations Inside Russia cryptogon.com
Via: Daily Mail: Two key electricity supply stations in Russia have been destroyed amid a suspected Ukrainian drone attack behind enemy lines. Stunning footage taken overnight showed how the bombing of the power stations had created a huge inferno which spiraled high into the night sky. The destruction of the sites in Igumenka and Dragunskoe []
03:19
Windows in Asia: All-Time Lows for Microsoft Techrights
Windows on just 1 in 5 Internet-connected computers? In 2009 things were different
Summary: The corporate media, funded by Microsoft et al, wont say this; so somebody should, citing this latest data
02:57
Million-year-old Viruses Help Fight Cancer, Say Scientists SoylentNews
Million-year-old viruses help fight cancer, say scientists:
Relics of ancient viruses - that have spent millions of years hiding inside human DNA - help the body fight cancer, say scientists. The study by the Francis Crick Institute showed the dormant remnants of these old viruses are woken up when cancerous cells spiral out of control. This unintentionally helps the immune system target and attack the tumour.
The team wants to harness the discovery to design vaccines that can boost cancer treatment, or even prevent it.
The researchers had noticed a connection between better survival from lung cancer and a part of the immune system, called B-cells, clustering around tumours. B-cells are the part of our body that manufactures antibodies and are better known for their role in fighting off infections, such as Covid.
Precisely what they were doing in lung cancer was a mystery but a series of intricate experiments using samples from patients and animal tests showed they were still attempting to fight viruses. "It turned out that the antibodies are recognising remnants of what's termed endogenous retroviruses," Prof Julian Downward, an associate research director at the Francis Crick Institute, told me.
Read more of this story at SoylentNews.
02:50
Elon Musk Says US Government Had Access to Private Twitter DMs cryptogon.com
Shocking, if you have amnesia, or never heard of the Utah Data Center in the first place. Via: Summit News: During an upcoming appearance on Tucker Carlsons show, Elon Musk reveals that the US government had full access to peoples private Twitter DMs. Musk told Carlson during a segment which is set to air tonight []
02:32
Israeli Spyware Vendor QuaDream to Shut Down Following Citizen Lab and Microsoft Expose The Hacker News
Israeli spyware vendor QuaDream is allegedly shutting down its operations in the coming days, less than a week after its hacking toolset was exposed by Citizen Lab and Microsoft. The development was reported by the Israeli business newspaper Calcalist, citing unnamed sources, adding the company "hasn't been fully active for a while" and that it "has been in a difficult situation for several
02:06
New QBot Banking Trojan Campaign Hijacks Business Emails to Spread Malware The Hacker News
A new QBot malware campaign is leveraging hijacked business correspondence to trick unsuspecting victims into installing the malware, new findings from Kaspersky reveal. The latest activity, which commenced on April 4, 2023, has primarily targeted users in Germany, Argentina, Italy, Algeria, Spain, the U.S., Russia, France, the U.K., and Morocco. QBot (aka Qakbot or Pinkslipbot) is a banking
01:46
[$] Avoiding the merge trap LWN.net
The kernel subsystem maintainers out there probably have a deep understanding of the sinking feeling that results from opening one's inbox and seeing a response from Linus Torvalds to a pull request. When all goes well, pull requests are acted upon silently; a response usually means that all has not gone well. Several maintainers got to experience that feeling during the 6.3 merge window, which seemed to generate more than the usual number of grumpy responses related to merge commits. Avoiding that situation is not hard, though, with a bit of attention paid to how merges are done.
01:44
Utah: Most Snowfall Since State Records Began in 1930s cryptogon.com
A three story cabin is buried up to the roof. One guy says its 30 feet of snow, another says 20 feet. In any event, this is pretty nuts. Via: HeavyDSparks: Related: Utahs Snowpack Highest Amount Ever Documented
01:43
Renewed Work For ACO Compiler Support With The RadeonSI Gallium3D Driver Phoronix
Back in 2019 Valve developers introduced the ACO compiler back-end within Mesa for the Radeon Vulkan "RADV" driver. This alternative to the AMDGPU LLVM shader compiler has been instrumental in helping RADV perform very well for Linux gaming both with Vulkan native titles as well as games going the route of DirectX to Vulkan via DXVK and VKD3D with Proton (Steam Play). On and off there's been talk and work towards bringing ACO to RadeonSI Gallium3D for OpenGL while now there is some new work on this front...
01:34
Hundreds of Teenagers Flood Into Downtown Chicago, Smashing Car Windows, Two People Shot cryptogon.com
Via: Fox32: Hundreds of teenagers flooded into Downtown Chicago on Saturday night, smashing car windows, trying to get into Millennium Park, and prompting a major police response. At least one person in a car was attacked. Shots were fired near the corner of Madison and Michigan, and FOX 32 Chicago decided that it was unsafe []
01:30
Wolfram Alpha With ChatGPT Looks Like a Killer Combo Hackaday

Have ever looked at Wolfram Alpha and the development of Wolfram Language and thought that perhaps Stephen Wolfram was a bit ahead of his time? Well, maybe the times may have finally caught up because Wolfram plus ChatGPT looks like an amazing combo. That link goes to a long blog post from Stephen Wolfram that showcases exactly how and why the two make such a wonderful match, with loads of examples. (If youd prefer a video discussion, one is embedded below the page break.)
OpenAIs ChatGPT is a large language model (LLM) neural network, or more conventionally, an AI system capable of conversing in natural language. Thanks to a recently announced plugin system, ChatGPT can now interact with remote APIs and therefore use external resources.
01:24
Why poetry is a variety of mathematical experience Lifeboat News: The Blog
Machine learning theory is shedding new light on how to think about the mysterious and ineffable nature of art by Peli Grietzer + BIO.
01:23
Singapore approves 16 species of insects including silkworms and grasshopper for human consumption Lifeboat News: The Blog

Future food.
Think about grasshopper fries, a protein bar made of crickets or silkworm cocoons. As unconventional as it may sound, Singapore is trying to make insect food mainstream. The Singapore Food Agency (SFA) has given approval to 16 species of insects, such as crickets, silkworms and grasshoppers for human consumption.
The latest news, reported by the Singapore newspaper The Straits Times notes that the approval of the insects for consumption will be subject to food safety requirements. This will include treatment processes to kill pathogens and proper packaging and storage facilities.
The United Nations Food and Agriculture Organisation (FAO) has been promoting insects for human consumption recently. Insects are known for their high protein content and Singapores latest interest in adding insects to the national food menu is seen as a way for the country to safeguard its national food security. As per The Strait Times newspaper, the SFA had also conducted a scientific review to analyse the benefits of directly eating specific insects or making them into items such as snacks for human consumption. The Singapore government also held a public consultation exercise on the regulation of insects and insect products before the SFA approval.
Besides insects, SFA said it will also permit the cocoons of silkworms for human consumption in Singapore. They are also consumed in China and Malaysia, among other places. Silkworms produce cocoons with silk threads that are composed of two main proteins, known as sericin and fibroin. While silk has traditionally been used to produce textiles, countries like Japan have allowed companies to turn these silk threads into food and edible coatings in recent years. With the new announcement, the Singapore food industry is trying to capitalise on the opportunity to launch snacks and protein bars made of insects. Several home-grown firms also produce cricket powder for use in flour and cookies and are currently selling it to customers in the US and the UK. But the scale of consumer demand and the lack of public awareness is seen as challenges down the road. With a growing population, the world needs more available, affordable and sustainable alternatives for a balanced diet. However, a lot more needs to be done to normalise insect consumption around the world.
01:23
How to Summon Entities: A Glimpse into GPT-4 through the lens of Jungian Psychology & Jungian Archetypes Lifeboat News: The Blog
Introduction.
The GPT-4 language model is a remarkable AI technology that can
generate human-like text.
While it lacks certain human psychological factors, such as individuation and the Jungian Shadow, GPT-4 demonstrates a fascinating awareness of archetypes and their role in shaping human behavior.
This article delves into GPT-4s understanding of Jungian psychology and explores the implications of archetypes as a language-space phenomenon.
01:22
With Security Copilot, Microsoft brings the power of AI to cyberdefense Lifeboat News: The Blog
Trained across security and networking disciplines and armed with trillions of data signals, Security Copilot dramatically increases the reach, speed and effectiveness of any security team
REDMOND, Wash. March 28, 2023 Microsoft Corp. on Tuesday announced it is bringing the next generation of AI to cybersecurity with the launch of Microsoft Security Copilot, giving defenders a much-needed tool to quickly detect and respond to threats and better understand the threat landscape overall. Security Copilot will combine Microsofts vast threat intelligence footprint with industry-leading expertise to augment the work of security professionals through an easy-to-use AI assistant.
Today the odds remain stacked against cybersecurity professionals. Too often, they fight an asymmetric battle against relentless and sophisticated attackers, said Vasu Jakkal, corporate vice president, Microsoft Security. With Security Copilot, we are shifting the balance of power into our favor. Security Copilot is the first and only generative AI security product enabling defenders to move at the speed and scale of AI.
01:22
UK Power Grid Could Have Worlds First Commercial Fusion Reactor Lifeboat News: The Blog
TAE Technologies hopes to have a net energy producing fusion reactor operating on the UK grid by the 2030s.
01:22
Budweiser Tries Patriotic Ad Campaign After Dylan Mulvaney Disaster cryptogon.com
haha Woops. Lets go with Merica again and maybe people will forget about our insane woke fail. Via: Fox: Budweisers new pro-America ad set Twitter ablaze over the weekend as critics derided the company for a misguided attempt at quelling the backlash over Bud Lights endorsement partnership with transgender influencer Dylan Mulvaney. Budweisers latest advertisement, []
01:22
We May Finally Know How Our Eyesight Evolved, And Its Not From Our Branch of Life Lifeboat News: The Blog
The evolution of the human eye has long been considered one of biologys more challenging mysteries, drawing debate over the sequence of steps required to turn rudimentary sensitivity to light into a complex photographic system.
New research suggests some components of vertebrate vision may not have been shaped incrementally as their genes passed down family lines, but were stolen from entirely different branches of life.
At least one innovation that led to the current structure of vertebrate eyes did not occur from stepwise tinkering with genes that exist in other animals, but came from introduction of novel DNA from bacteria by horizontal gene transfer, explains molecular biologist Matt Daugherty from the University of California, San Diego (UCSD) on Twitter.
01:07
Elizabeth Chamberlain: The Future of the Right to Repair and Free Software Techrights
Summary: A day ago this LibrePlanet non-keynote talk from Elizabeth Chamberlain was uploaded by the FSF, about a month after the in-person talk (slides here); From the page: Dr. Elizabeth Chamberlain is Director of Sustainability at iFixit, which is the free repair manual for everything, with over 90,000 guides for fixing everything from tractors to toasters. Liz advocates for the Right to Repair around the world, supporting lawmakers, conducting repair research, and working to make sure environmental standards reflect repair best practices. Her writing on repair has been published in the Wall Street Journal, Wired, and The Atlantic.
Licence: CC BY SA 4.0
01:03
QuaDream, Israeli iPhone hacking spyware firm, to shut down HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
QuaDream, based in Ramat Gan, Israel, with around 40 employees, is known for its spyware used for hacking iPhones.
This is a post from HackRead.com Read the original post: QuaDream, Israeli iPhone hacking spyware firm, to shut down
00:35
[Meme] Stole 100,000 Pounds, Gained 100 Pounds Techrights
They did this to a lot of programmers and GNU/Linux engineers at Sirius (deductions taken, but embezzled)

In Sirius (of the past decade) you neednt demonstrate technical
skills but an immovable will to cooperate in illegal stuff
The technical staff at Sirius worked from 5:30PM, overnight,
until 9AM! She never worked at night. She partied. In daytime she
casually harassed technical staff. I cant code, but I can harass
people who do (reference)

With her in the helm,
the company clocked close to 9,000 pounds in theft (from me
alone, not counting all the colleagues) so she can party at
night and her boss can take the family (4 people) to
super-expensive Disney trips abroad
Summary: The Crime Assistant of the CEO of...
00:34
Security updates for Monday LWN.net
Security updates have been issued by Debian (chromium, rails, and ruby-rack), Fedora (firefox, ghostscript, libldb, samba, and tigervnc), Mageia (ceph, davmail, firefox, golang, jpegoptim, libheif, python-certifi, python-flask-restx, thunderbird, and tomcat), Oracle (firefox), Red Hat (firefox), Scientific Linux (firefox), SUSE (apache2-mod_auth_openidc, aws-nitro-enclaves-cli, container-suseconnect, firefox, golang-github-prometheus-prometheus, harfbuzz, java-1_8_0-ibm, kernel, liblouis, php7, tftpboot-installation images, tomcat, and wayland), and Ubuntu (chromium-browser, imagemagick, kamailio, and libreoffice).
00:27
33% of Open Source Summit North America speakers identify as female or non-binary! Linux.com
read the original post at Read More
The post 33% of Open Source Summit North America speakers identify as female or non-binary! appeared first on Linux.com.
00:15
GCC 13.1 Compiler Likely Releasing Next Week Phoronix
The GNU Compiler Collection 13 codebase has no more P1 bugs, which are regressions of the highest priority, and as such the GCC 13 codebase was branched today with plans of issuing GCC 13.1-rc1 likely in the next day and hopefully releasing GCC 13.1 as the first stable release of the GCC 13 series next week...
00:12
MEPs Raise Concerns Over Draft EU-US Data Transfer Deal SoylentNews
MEPs raise concerns over draft EU-US data transfer deal:
A shiny new data transfers deal between the European Union and the United States aimed at fixing costly legal uncertainty over exports of personal data isn't in place yet but the European Parliament's civil liberties committee is predicting the incoming EU-U.S. Data Privacy Framework (DPF) won't survive a legal challenge just as its two predecessors, Safe Harbor (RIP: October 2015); and Privacy Shield (RIP: July 2020), failed to impress EU judges.
In a resolution passed by the LIBE committee yesterday, with 37 votes in favor, none against and 21 abstentions, the MEPs dubbed the DPF an improvement that nonetheless does not go far enough. They also predicted it's likely to be invalidated by the Court of Justice of the EU (CJEU) in the future.
The development follows a draft opinion by the LIBE, back in February, also giving the proposal a thumbs down and urging the Commission to press for meaningful reforms.
In the resolution, the committee takes the view that the proposed arrangement does not provide sufficient safeguards for EU citizens since the framework still allows for bulk collection of personal data in certain cases; does not make bulk data collection subject to independent prior authorisation; and does not provide for clear rules on data retention.
The MEPs are also worried that a proposed redress mechanism a so-called "Data Protection Review Court" would violate EU citizens' rights to access and rectify data about them, since decisions would be kept secret. They also question its independence since judges could be dismissed by the U.S. president, who could also overrule its decisions.
Read more of this story at SoylentNews.
00:00
PUF Away for Hardware Fingerprinting Hackaday

Despite the rigorous process controls for factories, anyone who has worked on hardware can tell you that parts may look identical but are not the same. Everything from silicon defects to microscopic variations in materials can cause profoundly head-scratching effects. Perhaps one particular unit heats up faster or locks up when executing a specific sequence of instructions and we throw our hands up, saying its just a fact of life. But what if instead of rejecting differences that fall outside a narrow range, we could exploit those tiny differences?
This is where physically unclonable functions (PUF) come in. A PUF is a bit of hardware that returns a value given an input, but each bit of hardware has different results despite being the same design. This often relies on silicon microstructure imperfections. Even physically uncapping the device and inspecting it, it would be incredibly difficult to reproduce the same imperfections exactly. unforgeable.
Because they depend on manufacturing artifacts, there is a certain unpredictability, and deciding just what features to look at is crucial. The PUF needs to be deterministic and produce the same value for a given specific input. This means that temperature, age, power supply fluctuations, and radiation all cause variations and need to be hardened against. Seve...
Monday, 17 April
23:50
FIN7 and Ex-Conti Cybercrime Gangs Join Forces in Domino Malware Attacks The Hacker News
A new strain of malware developed by threat actors likely affiliated with the FIN7 cybercrime group has been put to use by the members of the now-defunct Conti ransomware gang, indicating collaboration between the two crews. The malware, dubbed Domino, is primarily designed to facilitate follow-on exploitation on compromised systems, including delivering a lesser-known information stealer that
23:33
China-linked APT41 group spotted using open-source red teaming tool GC2 Security Affairs
China-linked APT41 group used the open-source red teaming tool GC2 in an attack against a Taiwanese media organization.
Google Threat Analysis Group (TAG) team reported that the China-linked APT41 group used the open-source red teaming tool Google Command and Control (GC2) in an attack against an unnamed Taiwanese media organization.
The APT41 group, aka Winnti, Axiom, Barium, Blackfly, HOODOO) is a China-linked cyberespionage group that has been active since at least 2007.
The attack took place in October 2022, threat actors sent phishing emails that contained links to a password-protected file hosted in Drive. The final payload was the Go-written GC2 tool that gets commands from Google Sheets and exfiltrates data to Google Drive.
In October 2022, Googles Threat Analysis Group (TAG) disrupted a campaign from HOODOO, a Chinese government-backed attacker also known as APT41, that targeted a Taiwanese media organization by sending phishing emails that contained links to a passwordprotected file hosted in Drive. reads the Threat Horizons April 2023 Threat Horizons Report published by Google.The payload was an open source red teaming tool called Google Command and Control (GC2).
Upon installing the malware on the target system, it queries Google Sheets to obtain attacker commands. GC2 also allows operators to download additional files from Drive onto the victim system.

Goog...
23:32
What's the Difference Between CSPM & SSPM? The Hacker News
Cloud Security Posture Management (CSPM) and SaaS Security Posture Management (SSPM) are frequently confused. The similarity of the acronyms notwithstanding, both security solutions focus on securing data in the cloud. In a world where the terms cloud and SaaS are used interchangeably, this confusion is understandable. This confusion, though, is dangerous to organizations that need to secure
23:30
[Meme/Facts] Drowning in Marketing Material and Assurances (From Sirius, Standard Life, Integrity Financial Management Ltd.) While Payslips Say We Pay Into a Pension Every Month Techrights
The payslips of my colleagues said the same; we didnt know it was a sham pension or a total fraud
Summary: Sirius Open Source fraudsters robbed the technical staff for many years; the payslips all indicated a pension was being paid into, but this was never done and pension providers kept evading questions on the matter, which makes them partly complicit
23:24
Starship Flight Test Lifeboat News: The Blog

SpaceX is targeting as soon as Monday, April 17 at 8:00 a.m. CT for the first flight test of a fully integrated Starship and Super Heavy rocket from Starbase
23:23
Watch SpaceX TEST Starship, the biggest rocket ever, LIVE from the edge of the exclusion zone!!! Lifeboat News: The Blog

Recommended:
This is the first fully integrated full stack test flight of Starship and the mighty Super Heavy booster. At lift off, it will become the largest and most most powerful rocket to ever fly producing over twice as much thrust as the Saturn V that took humans to the moon.
The goal of the test is to get as far along in the mission as possible with a handful of important goals such as; clearing the launch pad, reaching max Q, getting to stage separation, ignition of Starship, burn Starships engines for 7 minutes and 20 seconds which would get Starship up to nearly orbital velocities and would place Starship on a suborbital trajectory that will cause it to reenter just north of Hawaii. This would allow the teams to test the reentry profile and heat shields for the first time from orbital velocities.
Want more information? Check out our Prelaunch Preview written by Austin Desisto https://everydayastronaut.com/starship-superheavy-orbital-flight-test/
Want to know where to watch this live? I made a video on how to visit Starbase and where to watch a launch from https://youtu.be/aWvHrih-Juk.
Want to support what I do? Consider becoming a Patreon supporter for access to exclusive livestreams, our discord channel! http://patreon.com/everydayastronaut.
Or become a YouTube member for some bonus perks as well! https://www.youtube.com/channel/UC6uKrU_WqJ1R2HMTY3LIx5Q/join.
The best place for all your space merch needs!
https://everydayastronaut.com/shop/
23:22
Fred Adams Will the Universe Ever End? Lifeboat News: The Blog

What does it mean to ask about the end of the universe? Can the universe even have an end? What would end? In the far, far future, what happens to stars, galaxies, and black holes? What about mass and energy, even space and time? Whats the Big Crunch and the Big Rip? And what if there are multiple universes, will the multiverse ever end?
Free access to Closer to Truths library of 5,000 videos: http://bit.ly/376lkKN
Watch more interviews on the end of the universe: https://bit.ly/3MSHlFF
Support the show with Closer To Truth merchandise: https://bit.ly/3P2ogje.
Fred Adams is a professor of physics at the University of Michigan. His work is in the general area of theoretical astrophysics with a focus on the study of star formation and cosmology.
Register for free at CTT.com for subscriber-only exclusives: https://bit.ly/3He94Ns.
23:01
Enabling Kubernetes self-service the operator way Linux.com
Learn how operators can serve as governance tools in a multitenant setting.
Read More at Enable Sysadmin
The post Enabling Kubernetes self-service the operator way appeared first on Linux.com.
22:48
[Meme] Standard Life: We Dont Know Who All Those GNU/Linux Engineers Are (But You Know, Standard Life; We Were All on Your System) Techrights
Standard Life claims not to know us; so all those brochures sent to us must have come by accident since 12 years ago
Summary: The Standard Life sham pension was a critical component of fraud at Sirius Open Source, robbing an unknown number of workers, GNU/Linux system administrators and programmers. There is a personal code and everything on papers from Standard Life, so we were on their computer system, but now they try to deny this either because they deleted us from the system or the system is built to vanish us from it (after a while). They also give inconsistent information, which is typically indicative/suggestive/implying that theyre hiding something and when inquired about the details they literally hang up the phone (rudely).
22:47
Live Feed: Starship Flight Test [Scrubbed] cryptogon.com
Update: Scrubbed Via: SpaceX:
22:26
The Role of Integrity Financial Management Ltd. in Facilitating Fraud at Sirius Open Source Techrights
This is how they scammed GNU/Linux geeks in 2011 onwards:
Summary: The crimes of Sirius Open Source were facilitated by a network of financiers who vanish the money or give an illusion of authority and accountability; heres another one of them (Integrity Financial Management Ltd.), facilitating the Standard Life sham pension
22:24
Are Smart Home Devices Invading Your Privacy? HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
Smart home devices are becoming more and more popular in recent years, promising convenience and automation to enhance
This is a post from HackRead.com Read the original post: Are Smart Home Devices Invading Your Privacy?
22:20
AMD Ryzen 7 7800X3D: Windows 11 vs. Ubuntu 23.04 Linux Performance Phoronix
With the recent launch of the AMD Ryzen 7 7800X3D, several Phoronix Premium supporters expressed interest in seeing how well the Windows 11 vs. Linux performance compared for this Zen 4 3D V-Cache processor. Given those requests, here are some CPU/system benchmarks looking at the performance of Windows 11 Professional against Ubuntu 23.04 in its near-final state on the 7800X3D desktop.
22:15
SpaceX's First Orbital Test Flight of Starship Imminent [Scrubbed] SoylentNews
https://en.wikipedia.org/wiki/SpaceX_Starship_orbital_test_flight
The Starship Orbital Flight Test is the planned first spaceflight of the SpaceX Starship launch vehicle. The planned launch site is Boca Chica, Texas. SpaceX plans on using Starship prototypes Ship 24 (second stage) and Booster 7 (first stage). The Starship second stage will enter a transatmospheric Earth orbit with a negative Earth perigee, allowing Ship 24 to reenter the atmosphere after completing most of one orbit without having to restart its engines for a deorbit maneuver. The earliest launch opportunity is currently scheduled for April 17, 2023 at 08:00 CDT (13:00 UTC).
SpaceX stream. NASASpaceFlight stream.
Read more of this story at SoylentNews.
22:13
Letter From NOW: Pensions Regarding Misconduct and Theft at Sirius Open Source schestowitz.com
Summary: Having just contacted NOW: Pensions (and several times more this past week), while moreover working on 3 leads at the same time, they finally (belatedly) gave a real assurance
Today well share a bunch of photographic evidence regarding crimes of Sirius Open Source, a firm that claims to be Britains most respected firm in this domain/area (Open Source). Of course its a lie. Not just the part about respected
They kept lying to cover up prior lies, in effect lying to me like half a dozen times already.Half a day ago I sent the following E-mail message to NOW: Pensions. About an hour ago I finally received a letter addressed to my wife and I. After nearly 3 months!!! Months of endless remainders after repeated lies.
Here is the E-mail I sent last night:
A few days ago Standard Life sent a whole bunch of us a formal letter concluding that Sirius had engaged in pension fraud and stole money from us for many years. This is a criminal matter. This is now formalised.
My wife and I are coming to collect our funds from NOW: Pensions this week. Please specify the time that best suits you. We live not far from your office.
Suffice to say, repeated lying by your staff including by managers will be duly noted. We trust neither you nor Sirius.
The sad thing is that pension providers have helped the perpetrators of crimes, covering up for them instead of working to protect the victims, who are the peoples whose money is actually making its way into the accounts of reckless gamblers at the pension firms. Who do you work for? Are you working for employers who commit crimes instead of employees (whose money you are taking)?
Silence on this matter wont help you. Au contraire. Please respond today.
They kept lying to cover up prior lies, in effect lying to me like half a dozen times already. Its circular and when challenged on the lies, more lies follow. Those people are handling (gambling with) peoples money. Trillions of dollars are managed by those sorts of firms.
As victims, we can progress along some lines. Standard Life, which well tackle separately later, tried victim-blaming (we have this on record). Thats akin to saying to a rape victim that it is his/her fault, e.g. why didnt you sense s/hed rape you after the date?
Many technical people suspected something was amiss and when phoning Standard Life we were only obstructed, so in effect Standard Life all...
22:11
NOW: Pensions Finally Sends the Letters It Has Been Promising (in Vain) for Several Months Regarding Fraud at Sirius Open Source Techrights
Summary: Having just contacted NOW: Pensions (and several times more this past week), while moreover working on 3 leads at the same time, they finally (belatedly) gave a real assurance
Today well share a bunch of photographic evidence regarding crimes of Sirius Open Source, a firm that claims to be Britains most respected firm in this domain/area (Open Source). Of course its a lie. Not just the part about respected
They kept lying to cover up prior lies, in effect lying to me like half a dozen times already.Half a day ago I sent the following E-mail message to NOW: Pensions. About an hour ago I finally received a letter addressed to my wife and I. After nearly 3 months!!! Months of endless remainders after repeated lies.
Here is the E-mail I sent last night:
A few days ago Standard Life sent a whole bunch of us a formal letter concluding that Sirius had engaged in pension fraud and stole money from us for many years. This is a criminal matter. This is now formalised.
My wife and I are coming to collect our funds from NOW: Pensions this week. Please specify the time that best suits you. We live not far from your office.
Suffice to say, repeated lying by your staff including by managers will be duly noted. We trust neither you nor Sirius.
The sad thing is that pension providers have helped the perpetrators of crimes, covering up for them instead of working to protect the victims, who are the peoples whose money is actually making its way into the accounts of reckless gamblers at the pension firms. Who do you work for? Are you working for employers who commit crimes instead of employees (whose money you are taking)?
Silence on this matter wont help you. Au contraire. Please respond today.
They kept lying to cover up prior lies, in effect lying to me like half a dozen times already. Its circular and when challenged on the lies, more lies follow. Those people are handling (gambling with) peoples money. Trillions of dollars are managed by those sorts of firms.
As victims, we can progress along some lines. Standard Life, which well tackle separately later, tried victim-blaming (we have this on record). Thats akin to saying to a rape victim that it is his/her fault, e.g. why didnt yo...
21:46
Google Uncovers APT41's Use of Open Source GC2 Tool to Target Media and Job Sites The Hacker News
A Chinese nation-state group targeted an unnamed Taiwanese media organization to deliver an open source red teaming tool known as Google Command and Control (GC2) amid broader abuse of Google's infrastructure for malicious ends. The tech giant's Threat Analysis Group (TAG) attributed the campaign to a threat actor it tracks under the geological and geographical-themed moniker HOODOO, which is
21:36
Tour of the Underground: Master the Art of Dark Web Intelligence Gathering The Hacker News
The Deep, Dark Web The Underground is a haven for cybercriminals, teeming with tools and resources to launch attacks for financial gain, political motives, and other causes. But did you know that the underground also offers a goldmine of threat intelligence and information that can be harnessed to bolster your cyber defense strategies? The challenge lies in continuously monitoring the right
21:18
Vice Society gang is using a custom PowerShell tool for data exfiltration Security Affairs
Vice Society ransomware operators have been spotted using a PowerShell tool to exfiltrate data from compromised networks.
Palo Alto Unit 42 team identified observed the Vice Society ransomware gang exfiltrating data from a victim network using a custom-built Microsoft PowerShell (PS) script.
Threat actors are using the PowerShell tool to evade software and/or human-based security detection mechanisms. PS scripting is often used within a typical Windows environment, using a PowerShell-based tool can allow threat actors to hide in plain sight and get their code executed without raising suspicion.
Early in 2023, the researchers spotted the gang using a script named w1.ps1 to exfiltrate data from a victim network. Unit42 researchers were able to recover the script from the Windows Event Log (WEL).
The script identifies any mounted drives on the target system by using Windows Management Instrumentation (WMI), then iterates through the identified drives to prepare data exfiltration via HTTP POST events using the objects .UploadFile method.
each HTTP POST event will include the files full path. If you are able to obtain the source hosts IP address along with this path, you will then be able to build out a list of exfiltrated files after the fact. reads the analysis published by Palo Alto Networks.
The script uses the CreateJobLocal( $folders ) function to create PowerShell script blocks to be run as jobs via the Start-Job cmdlet. The CreateJobLocal function receives groups of directories, often in groups of five.
The tool uses an inclusion/exclusion process based on keywords to select which directories to pass to the fill() function to exfiltrate.
The tool doesnt target folders containing system files, backups, folders associated with web browsers, and folders used by security solutions from Symantec, ESET, and Sophos.
The script finds all files within each directory that matches the include list, it exfiltrates files that do not have extensions found on the exclude list and that are larger than 10 KB.
The script ignores files that are under 10 KB in size and that do not have a file extension.
Vice Societys PowerShell data exfiltration script is a simple tool for data exfiltration. Multi-processing and queuing are used to ensure...
21:16
CVE-2023-27525: Apache Superset: Incorrect default permissions for Gamma role Open Source Security
Posted by Daniel Gaspar on Apr 17
Description:An authenticated user with Gamma role authorization could have access to metadata information using non trivial methods
in Apache Superset up to and including 2.0.1
Credit:
NTT DATA (finder)
References:
https://superset.apache.org
https://www.cve.org/CVERecord?id=CVE-2023-27525
21:15
Nintendo Hacker Gary Bowser Released From Federal Prison TorrentFreak
 In the fall of 2020, the U.S. Government
indicted three members of the infamous Team Xecuter group, the
masterminds behind various Nintendo hacks.
In the fall of 2020, the U.S. Government
indicted three members of the infamous Team Xecuter group, the
masterminds behind various Nintendo hacks.
The group allegedly made millions of dollars through its operation, which effectively shut down shortly after the criminal proceedings started.
The authorities arrested Canadian Gary Bowser in the Dominican Republic and Frenchman Max Louarn was detained in Tanzania. The latter, a notorious hacker, miraculously managed to avoid extradition to the United States. The same cant be said for Bowser.
40 Months Prison for Salesperson
As the purported salesperson of Team-Xecuter, Bowser wasnt a leading figure in the operation. Most people knew him as GaryOPA, the operator of MaxConsole, a website that regularly reviewed Team-Xecuter hardware and other hacking tools.
Financially, Bowsers role was also rather limited. From all the millions of dollars in revenue that were generated by Team-Xecuter, Bowser was paid only $500 to $1000 a month, his attorney previously said. He didnt deny involvement, however.
Following his arrest, Bowser was deported to the United States where he pleaded guilty. Last February, Bowser was sentenced to 40 months in prison for his role in the criminal enterprise. The sentence is significant but lower than the five-year prison term the Government had requested.
During sentencing, Judge Lasnik said that it was important to send a message but agreed that a reduction was warranted as Bowser played the smallest role of the three defendants.
Early Release
Bowser was later incarcerated at Federal Detention Center SeaTac in Seattle. A few weeks ago his attorney put in a request for an early release, citing the time credits earned by his client to date. That request was denied as moot earlier this month, as the Bureau of Prisons had pushed Bowsers release date forward.
In a recent video interview with Nick Moses, Bowser explains that he was released from federal...
21:14
CVE-2023-25504: Apache Superset: Possible SSRF on import datasets Open Source Security
Posted by Daniel Gaspar on Apr 17
Description:A malicious actor who has been authenticated and granted specific permissions in Apache Superset may use the import
dataset feature in order to conduct Server-Side Request Forgery
attacks and query internal resources on behalf of the server where Superset
is deployed. This vulnerability exists in Apache Superset versions up to and including 2.0.1.
Credit:
Alexey Sabadash, VK (finder)
References:
https://superset.apache.org...
21:00
A Clock Timebase, No Microcontroller Hackaday

Making an electronic clock is pretty easy here in 2023, with a microcontroller capable of delivering as many quartz-disciplined pulses as youd like available for pennies. But how did engineers generate a timebase back in the old days, and how would you do it today? Its a question [bicyclesonthemoon] is answering, with a driver for a former railway station clock.
The clock has a mechanism that expects pulses every minute, a +24V pulse on even minutes, and a -24V pulse on odd ones. He received a driver module with it, but for his own reasons wanted a controller without a microcontroller. He also wanted the timebase to be derived from the mains frequency. The result is a delve back into 1970s technology, and the type of project thats now a pretty rare sight. Using a mixture of 4000 series logic and a few of the ubiquitous 555s [bicyclesonthemoon] recovers 50Hz pulses from the AC, and divides them down to 1 pulse per minute, before splitting into odd and even minutes to drive a pair of relays which in turn drive the clock. We like it, a lot.
Mains-locked clocks are less common than they used to be, but theyre still a thing. Do you still wake up to one?
20:38
Chinese GPU Vendor Moore Threads Contributing To VA-API, FFmpeg Phoronix
Moore Threads was established in 2020 to create domestic GPU solutions in China with their first products having been announced last year. Most of the talk around Moore Threads "MThreads" GPUs have been for Windows but they are working on Linux support to at least some extent...
20:20
Apple M1/M2 Keyboard Backlight Support Set For The Linux 6.4 Kernel Phoronix
In addition to Linux 6.4 bringing some early work around the Apple M2 device support that isn't yet ready for end-users but begins laying the foundation for supporting the new MacBook Air, MacBook Pro, and Mac Mini, another set of Apple changes have now been submitted ahead of this next kernel cycle...
20:00
Accelerate 800G Ethernet Deployments IEEE Spectrum

Get up to speed on the evolution of data centers.
The Data Center Ethernet Technology and Evolution to 224 Gbps application note explains the latest evolution of high speed ethernet links, technical challenges of 800G ethernet, and test solutions available for up to 224 Gbps interfaces.
19:21
Improve Security by Adopting Aviation's 'Just Culture' SoylentNews
When admitting to an error isn't seen as a failure, improvement easy to achieve:
To improve security, the cybersecurity industry needs to follow the aviation industry's shift from a blame culture to a "just" culture, according to director of the Information Systems Audit and Control Association Serge Christiaans.
Speaking at Singapore's Smart Cybersecurity Summit this week, Christiaans explained that until around 1990, the number of fatal commercial jet accidents was growing alongside a steady increase of commercial flights. But around the turn of the decade, the number of flights continued to rise while the number of fatalities began to drop.
[...] While acknowledging that improved technology, more mature processes and improved leadership all helped to improve aviation safety, the former pilot and field CISO at tech consultancy Sopra Steria said the biggest improvements came from a change to a "just culture" that accepts people will make mistakes and by doing so makes it more likely errors will be reported.
In a just culture, errors are viewed as learning opportunities instead of moral failing, creating transparency and enabling constant improvement.
[...] Christiaans said he is yet to come across a company that had implemented open reporting without punishment in cybersecurity.
He attributed this to the industry working from the top down. The people at the top worked hard to get to leadership roles and become resistant to change. Shifting culture therefore needs to start with new recruits.
[...] Furthermore, not all of the aviation industry has been a beacon of transparent culture. For example, whistleblowers have alleged that culture at Boeing emphasized profit over safety, ultimately leading to engineering decisions that caused the crash of two 737 MAX airplanes.
[...] But Christiaan's analysis may be true at least when it comes to pilots and airlines, especially when culture is changed with small steps.
"So you plant the seeds, some airlines adapt, some don't," said Christiaans. "The ones who adapt, succeed."
Read more of this story at SoylentNews.
18:53
Experts warn of an emerging Python-based credential harvester named Legion Security Affairs
Legion is an emerging Python-based credential harvester and hacking tool that allows operators to break into various online services.
Cado Labs researchers recently discovered a new Python-based credential harvester and hacking tool, named Legion, which was sold via Telegram. At this time, the sample analyzed by Cado Labs has a low detection rate of 0 on VirusTotal.
Legion is a modular tool that can be used by crooks to hack into various online services. The researchers reported that the tool has modules to support the following functionalities:
- enumerating vulnerable SMTP servers,
- conducting Remote Code Execution (RCE),
- exploiting vulnerable versions of Apache,
- brute-forcing cPanel and WebHost Manager (WHM) accounts,
- interacting with Shodans API to retrieve a target list (providing you supply an API key) and
- additional utilities, many of which involve abusing AWS services
Legion is similar to a tool detailed in December by Lacework researchers, which was named AndroxGh0st.
The sample analyzed by Cado Labs is a Python3 script of 21015 lines, it includes configurations for integrating with services such as Twilio and Shodan.
The malware can exfiltrate collected data via Telegram chat using the Telegram Bot API.
The developer behind the tool operates a YouTube channel named Forza Tools, which included a series of tutorial videos for using the Legion script. The experts believe that the tool is widely distributed and is likely paid malware.
Leg...
18:01
Vice Society Ransomware Using Stealthy PowerShell Tool for Data Exfiltration The Hacker News
Threat actors associated with the Vice Society ransomware gang have been observed using a bespoke PowerShell-based tool to fly under the radar and automate the process of exfiltrating data from compromised networks. "Threat actors (TAs) using built-in data exfiltration methods like [living off the land binaries and scripts] negate the need to bring in external tools that might be flagged by
18:00
Interlaken Want to Connect All the Chips Hackaday

One of the problems with designing things on a chip is finding a good way to talk to the outside world. You may not design chips yourself, but you care because you want to connect your circuits including other chips to the chips in question. While I2C and SPI are common solutions, todays circuits are looking for more bandwidth and higher speeds, and thats where Interlaken comes in. [Comcores] has an interesting post on the technology that blends the best of SPI 4.2 and XAUI.
The interface is serial, as you might expect. It can provide both high-bandwidth and low-latency multi-channel communications. Interlaken was developed by Cisco and Cortina Systems in 2006 and has since been adopted by other industry-leading companies. Its latest generation supports speeds as high as 1.2 Tbps.
Interlaken can support up to 65,535 data streams and features error correction. The interface also handles retransmissions, so the users dont have to. Interlaken uses a meta-frame concept. For each lane, a set of words associated with the meta-frame are sent along with the payload of control and data words. These include alignment information, clock compensation, status information, and error-checking data.
Unless you develop chips or build FPGAs, you probably wont worry too much about the internal details, at least not yet. But the time may be near when...
17:49
malloc leak detection available in -current OpenBSD Journal
OpenBSD -current just grew a new tool for developers working on OpenBSD to detect unsafe behaviors in their code. OpenBSD lets you more easily track memory allocations and whether allocations are properly freed after use.
In a message to tech@, Otto Moerbeek
(otto@) announced
the new functionality:
Subject: malloc leak detection available in -current From: Otto Moerbeek <otto () drijf ! net> Date: 2023-04-17 6:43:19 Hi, OpenBSD current now has built-in malloc leak detection. Make sure you run current and have debug symbols (OpenBSD base libraries have debug symbols, compile your own program with -g).
17:32
IRC Proceedings: Sunday, April 16, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-160423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-160423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-160423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-160423.gmi
Over HTTP:
|
... |
17:15
17:00
The Electron Is So Round That Its Ruling Out Potential New Particles Terra Forming Terra
9 Researched Benefits of Intermittent Fasting Terra Forming Terra
This item now shows us how mature all this has become and we are all traing to fast for our general health. All good.
Cases And Cases Of Bud Light Stacking Up In Bars & Stores Across America Terra Forming Terra
Somewhere, someone must actually believe that Woke culture has a voting majority somehow that supports them.
Natural treatment could make you almost invisible to mosquito bites Terra Forming Terra

This is both promising and wonderfully safe. Celluose in pure form is a natural blocker and easily discourages a mosquito and that may well be what we need to be doing.
So yes, being able to spray this on your hands and the back of your neck would be welcome. I swear that the smeely stuff we use actually attracts them, though that cannot be true.
16:59
New Zaraza Bot Credential-Stealer Sold on Telegram Targeting 38 Web Browsers The Hacker News
A novel credential-stealing malware called Zaraza bot is being offered for sale on Telegram while also using the popular messaging service as a command-and-control (C2). "Zaraza bot targets a large number of web browsers and is being actively distributed on a Russian Telegram hacker channel popular with threat actors," cybersecurity company Uptycs said in a report published last week. "Once the
16:55
Links 16/04/2023: Trisquel GNU/Linux 11.0 Reviewed and World IP (International Propaganda) Day 2023 Approaching Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
9to5Linux ...
-
16:42
Re: CVE-2023-2002: Linux Bluetooth: Unauthorized management command execution Open Source Security
Posted by Jakub Wilk on Apr 16
* Steffen Nurpmeso <steffen () sdaoden eu>, 2023-04-16 22:57:I'm pretty sure they do. But isatty(3) is implemented using the TCGETS
ioctl, so that doesn't help.
16:34
NovoNutrients Wants to Turn CO2 Into Protein SoylentNews
But first it'll have to prove its business model:
We've spent the last century and a half pumping carbon dioxide into the atmosphere, and it's clear that we'll have to spend the coming decades removing a significant fraction of that.
But then what do we do with it all? Some people are proposing pumping it underground. Others think we can make things from it, including liquid fuels and concrete. Problem is, those are pretty low-margin opportunities today. One startup thinks the answer is to turn carbon dioxide into protein.
[...] NovoNutrients relies on bacteria to do the dirty work. The company has surveyed the scientific literature to find species that can use carbon dioxide in their metabolic pathways, allowing them to use the waste gas as energy. Its scientists have also discovered strains not otherwise known to science.
"Our technology is about how do you industrialize this naturally occurring metabolism?" CEO David Tze told TechCrunch+.
[...] The company's approach has several advantages over other methods of using carbon dioxide. For one thing, it does not require large amounts of land or water, which are both in short supply in many parts of the world. It also does not require the use of fossil fuels, which are a major contributor to climate change.
NovoNutrients is not the only company working on using carbon dioxide to create protein. Other companies, such as Calysta and Deep Branch Biotechnology, are also developing similar technologies. However, NovoNutrients believes that its approach is unique because it uses bacteria to create protein products that are high in quality and can be sold at a competitive price.
The company's pilot-scale plant will be located in California and is expected to be operational by the end of 2021 [sic]. If successful, NovoNutrients plans to build a larger commercial-scale plant that could produce up to 1,000 metric tons of protein per year.
Read more of this story at SoylentNews.
15:00
Circumvent Facial Recognition with Yarn Hackaday

Knitwear can protect you from a winter chill, but what if it could keep you safe from the prying eyes of Big Brother as well? [Ottilia Westerlund] decided to put her knitting skills to the test for this anti-surveillance sweater.
[Westerlund] explains that yarn is a programable material containing FOR loops and other similar programming concepts transmitted as knitting patterns. In the video (after the break) she also explores the history of knitting in espionage using steganography embedded in socks and other knitwear to pass intelligence in unobtrusive ways. This lead to the restriction of shipping handmade knit goods in WWII by the UK government.
Back in the modern day, [Westerlund] took the Hyperface pattern developed by the Adam Harvey and turned it into a knitting pattern. Designed to circumvent detection by Viola-Jones based facial detection systems, the pattern presents a computer vision system with a number of faces to distract it from covered human faces in an image. While the knitted jumper (sweater for us American...
14:00
Economic uncertainty drives upskilling as a key strategy for organizations Help Net Security
With the economy experiencing instability and decline, organizations rely on their technology experts to maintain their innovative edge and generate business value. Despite being instructed to reduce expenses by 65% of the technology team leaders, 72% still intend to boost their investment in technology proficiency development by 2023, according to Pluralsight. As improving the skills of current employees is less expensive than recruiting new ones, 97% of directors in charge of learning and development and More
The post Economic uncertainty drives upskilling as a key strategy for organizations appeared first on Help Net Security.
14:00
Ubuntu 23.04 Desktop's New Installer Set To Ship Without OpenZFS Install Support Phoronix
It was just four years ago in Ubuntu 19.10 that Ubuntu's desktop installer added OpenZFS support for carrying out root file-system installations atop this ZFS file-system. Since then the Canonical/Ubuntu interest has waned. Ahead of the Ubuntu 23.04 release this week, I tried out the Ubuntu Lunar Lobster daily snapshot this weekend to find the OpenZFS install support with Ubuntu's new desktop installer to still be missing...
13:49
Colorado is the First US State to Pass a Right-to-repair Law for Farmers SoylentNews
John Deere warns about the "unintended consequences" stemming from the new legislation:
The right to repair movement just got its first major win in Colorado as the state will likely become the first to establish a law designed to protect the farmers' right to repair their own equipment. Big manufacturing companies are not happy, but the law is expected to be signed soon.
Starting January 1, 2024, manufacturers of agricultural equipment will have to provide Colorado farmers everything they need to repair machinery by themselves. Denver legislators recently approved the first-ever proposal turning right-to-repair principles into law with a majority vote (44 to 16), after the same law was approved by the Senate last month.
The bill is now on the governor's desk, where Jared Polis is expected to approve the bi-partisan proposal within 10 days. The Consumer Right To Repair Agricultural Equipment requires manufacturers to provide parts, embedded software, firmware, tools, documentation, repair manuals and other resources to independent repair providers and owners of farming machinery, giving them the ability to fix broken stuff without needing to go through official resellers and repair services.
The bill folds agricultural equipment into the existing consumer right-to-repair statutes of Colorado, which states that a manufacturer's failure to comply is a "deceptive trade practice." Manufacturers are not obliged to "divulge any trade secrets" to independent repair services and owners, the statutes say. The bill was later amended to clarify that repair providers and owners are not authorized to make modifications to equipment that permanently deactivate safety measures or modify carbon emissions.
Read more of this story at SoylentNews.
13:30
AI tools like ChatGPT expected to fuel BEC attacks Help Net Security
Across all BEC attacks seen over the past year, 57% relied on language as the main attack vector to get them in front of unsuspecting employees, according to Armorblox. In other trends to watch, vendor compromise and fraud are rising as a new attack vector and graymail is wasting 27 hours of time for security teams each week. Attacks target technology organizations The report is based on data gathered across more than 58,000 customer tenants, More
The post AI tools like ChatGPT expected to fuel BEC attacks appeared first on Help Net Security.
13:00
AI verification systems give businesses an edge over scammers Help Net Security
Fraudsters are underestimating the power of AI to detect fake IDs, according to a new report from Ondato. Based on an analysis of millions of ID verifications carried out for its customers in 2022, Ondato found that ID cards were used in 52% of fraudulent verification attempts far ahead of driving licences (29%) and passports (18%). ID cards used in over half of fraudulent verification attempts According to Ondato, fraudsters most likely underestimate ID More
The post AI verification systems give businesses an edge over scammers appeared first on Help Net Security.
12:00
Using STEP and STL Files in FreeCAD Hackaday

If youve tried FreeCAD, you know that it has a daunting number of workbenches and options. [MangoJelly] has a large number of video tutorials on FreeCAD, and the latest one, below, covers working with STEP and STL with the tool.
If youve ever wondered why designers like to work with STEP files and not STL, this video answers that question immediately. A part brought in from a STEP file is closer to the original CAD object. It doesnt have all the operations that make the part up, but it does have proper faces that you can work with like a normal part. The same part imported from STL, however, is one single mesh.
Of course, in this case, it doesnt matter much because he has the original file, the STEP, and the STL. However, in real life, you may have an STL file and nothing else. The video shows how you can convert such an object into a proper FreeCAD part.
We liked that the example part isnt a boxy design. It is full of curves, holes, and slots. Sometimes working with a very simple part hides issues that you run into when you try to use a technique in real life. In fact, after working with the basic object, he downloads a power supply cover and then punches a new hole in it.
If you want to learn more about FreeCAD, you can spend a lot of time on his channel, which has a dizzying array of tutorials. There are many...
11:58
[Meme] Recruiting to Steal Techrights
When you join a company run by a liar, fraud, and cheat (based on false credentials)
Summary: GNU/Linux engineers got robbed by Sirius Open Source Limited; the criminal who oversaw this fraud is now looking for more people to rob while cops drag their heels
11:54
Kernel prepatch 6.3-rc7 LWN.net
The 6.3-rc7
kernel prepatch is out for testing. "Let's hope we have just one
more calm week, and we'll have had a nice uneventful release cycle.
Knock wood
".
11:46
GNU/Linux Engineers Got Robbed by Sirius Open Source Limited schestowitz.com
Video
download link | md5sum
c4ca62ca5c8ebc2a7974b42f3ff4d884
Why the Pension Story is Relevant to Us
Creative Commons Attribution-No Derivative Works 4.0
Summary: The crimes of Sirius Open Source will be the subject of many future posts and today we explain why this is a subject of relevance to Techrights
THE pension situation where I worked for nearly 12 years impacts a lot of people and it helps reveal rampant corruption in the pension industry. Ive been thinking about this deeply for days, also in light of several news items about France and about the US pension promises being unsustainable. Are people meant to ever retire? Are people living to work? Or they do work to eventually live? (Hours after work or after they leave work altogether)
We have a lot more information in the pipeline, albeit were limited by what we can say at any one time. The reasons are explained in the video above as well.
Why did the accounting people allow pension fraud to carry on for so long? Could they not refrain from collaborating? In fact, who does the accounting anyway? There might be an even more sinister scandal therein and were investigating the matter.
Another question: can one actually withdraw a pension early? The state would say thats possible, but companies lie their way or simply hide when the subject comes up (e.g. bank details specified or time for cheque to be picked up with paperwork signed). The outcome of any hypothetical investigations into this turn out to be ugly. The pensions seem like a black hole. You can put money in, or think you put money in, but you can never take anything out.
Our approach here has been multifaceted; the goals and methods are many. Since we deal with an actual criminal matter, we cannot be ignored by pension providers, police etc. They cannot simply turn a blind eye. Everyone agrees that pension providers are very sensitive about their brand/reputation (more so than banks). There are several reasons for this, but those are beyond the scop...
11:20
Standing Up for Defrauded Members of Staff (GNU/Linux Engineers) in the Age of Pension Scams Techrights
Video
download link | md5sum
c4ca62ca5c8ebc2a7974b42f3ff4d884
Why the Pension Story is Relevant to Us
Creative Commons Attribution-No Derivative Works 4.0
Summary: The crimes of Sirius Open Source will be the subject of many future posts and today we explain why this is a subject of relevance to Techrights
THE pension situation where I worked for nearly 12 years impacts a lot of people and it helps reveal rampant corruption in the pension industry. Ive been thinking about this deeply for days, also in light of several news items about France and about the US pension promises being unsustainable. Are people meant to ever retire? Are people living to work? Or they do work to eventually live? (Hours after work or after they leave work altogether)
Why did the accounting people allow pension fraud to carry on for so long?We have a lot more information in the pipeline, albeit were limited by what we can say at any one time. The reasons are explained in the video above as well.
Why did the accounting people allow pension fraud to carry on for so long? Could they not refrain from collaborating? In fact, who does the accounting anyway? There might be an even more sinister scandal therein and were investigating the matter.
Another question: can one actually withdraw a pension early? The state would say thats possible, but companies lie their way or simply hide when the subject comes up (e.g. bank details specified or time for cheque to be picked up with paperwork signed). The outcome of any hypothetical investigations into this turn out to be ugly. The pensions seem like a black hole. You can put money in, or think you put money in, but you can never take anything out.
Everyone agrees that pension providers are very sensitive about their brand/reputation (more so than banks).Our approach here has been mult...
11:14
10 Best Zippyshare Alternatives Best File Sharing Services HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
Zippyshare is no longer available after the service announced its shutdown on March 30th, 2023.
This is a post from HackRead.com Read the original post: 10 Best Zippyshare Alternatives Best File Sharing Services
11:07
Human Rights Groups Raise Alarm Over UN Cybercrime Treaty SoylentNews
Let's go through all the proposed problematic powers, starting with surveillance and censorship:
Special report United Nations negotiators convened this week in Vienna, Austria, to formulate a draft cybercrime treaty, and civil society groups are worried.
"We are here for the fifth session on the negotiations of this new treaty on cybercrime, which will have the potential to drastically redraft criminal law all around the world," said Thomas Lohnninger, executive director of Austria-based tech policy group Epicenter.works, in a media briefing on Thursday about the treaty negotiations.
"It represents a tectonic shift because of its global nature when it comes to the cross border access to our personal information."
The UN Cybercrime Treaty, to the extent it gets adopted, is expected to define global norms for lawful surveillance and legal processes available to investigate and prosecute cybercriminals. And what has emerged so far contemplates [PDF] more than 30 new cybercrime offenses, with few concessions to free speech or human rights.
[...] Katitza Rodriguez, policy director for global privacy at the Electronic Frontier Foundation, explained that current cross-border cybercrime cooperation comes from the Budapest Convention, negotiated in 2001, by member states at the Council of Europe.
Russia, however, Rodriguez said, has objected to the convention for infringing state sovereignty by allowing other nations to investigate cybercrimes in its jurisdiction. So in 2017, Russia proposed negotiating a new treaty, and in 2019 the UN adopted a resolution to do so, backed by Russia, Cambodia, Belarus, China, Iran, Myanmar, Nicaragua, Syria and Venezuela.
The US and members of the European Union opposed the proposal citing concerns about lack of human rights protections. Nonetheless, Rodriguez said, Russia pushed its proposal forward and the UN opened negotiations just days after Russia invaded Ukraine.
Read more of this story at SoylentNews.
10:14
Microsoft Bing Hides News Regarding Microsoft Stabber Joseph Cantrell Techrights
Reprinted with permission from Ryan
Microsoft has removed all references to Joseph Cantrell from Bing News, which has made its way into DuckDuckGo as well.
Google News still returns results for the drug addled Nazi that Microsoft hired and now tries to hide. No doubt, having him stab another employee was very embarrassing.
This is just one example of how Microsoft can run damage control. As his case winds its way through the court system, people will increasingly wonder what kind of company hires people who self-admit to extensive drug usage and Nazi ideology, and then further admit that nobody on their team of 4, which costs the company over a million bucks, can figure out bugs in Azure, and have to resort to posting questions on Stack Exchange.
The drug diary, which I also previously reported on, also shows that Cantrells behavior created an extremely toxic and harassing workplace. On numerous occasions, Cantrell says that in company meetings, he said Indians shouldnt be allowed to work at Microsoft and that one person in particular should have her green card revoked for being Indian, admitted to soliciting prostitutes and getting STDs from them, and blogged extensively that tech companies who have Indian CEOs dont have good products anymore. I wonder if Bill Gates even uses Windows or if that Indian guy at Google even uses Google.
Almost all of the worst of his admissions in the diary were on his public Web site before the hiring.
But if Microsoft sets up a simple key word ban, nobody following Bing or DuckDuckGo News will read about its dirty laundry.
10:10
DistroWatch Weekly, Issue 1015 DistroWatch.com: News
This week in DistroWatch Weekly: Review: Manjaro Linux 22.0, Trisquel GNU/Linux 11.0News: Arch Linux powering new PINE64 tablets, KDE Connect getting an overhaul, Ubuntu introduces live patching for HWE kernelsQuestions and answers: Gaining filesystem compression with ext4Released last week: OpenBSD 7.3, FreeBSD 13.2, 4MLinux 42.0, TrueNAS 22.12.2 "SCALE"Torrent....
10:04
Booting modern Intel CPUs Matthew Garrett
CPUs can't do anything without being told what to do, which
leaves the obvious problem of how do you tell a CPU to do something
in the first place. On many CPUs this is handled in the form of a
reset
vector - an address the CPU is hardcoded to start reading
instructions from when power is applied. The address the reset
vector points to will typically be some form of ROM or flash that
can be read by the CPU even if no other hardware has been
configured yet. This allows the system vendor to ship code that
will be executed immediately after poweron, configuring the rest of
the hardware and eventually getting the system into a state where
it can run user-supplied code.
The specific nature of the reset vector on x86 systems has varied
over time, but it's effectively always been 16 bytes below the top
of the address space - so, 0xffff0 on the 20-bit 8086, 0xfffff0 on
the 24-bit 80286, and 0xfffffff0 on the 32-bit 80386. Convention on
x86 systems is to have RAM starting at address 0, so the top of
address space could be used to house the reset vector with as low a
probability of conflicting with RAM as possible.
The most notable thing about x86 here, though, is that when it
starts running code from the reset vector, it's still in real mode.
x86 real mode is a holdover from a much earlier era of computing.
Rather than addresses being absolute (ie, if you refer to a 32-bit
address, you store the entire address in a 32-bit or larger
register), they are 16-bit offsets that are added to the value
stored in a "segment register". Different segment registers existed
for code, data, and stack, so a 16-bit address could refer to
different actual addresses depending on how it was being
interpreted - jumping to a 16 bit address would result in that
address being added to the code segment register, while reading
from a 16 bit address would result in that address being added to
the data segment register, and so on. This is all in order to
retain compatibility with older chips, to the extent that even
64-bit x86 starts in real mode with segments and everything (and,
also, still starts executing at 0xfffffff0 rather than
0xfffffffffffffff0 - 64-bit mode doesn't support real mode, so
there's no way to express a 64-bit physical address using the
segment registers, so we still start just below 4GB even though we
have massively more address space available).
Anyway. Everyone knows all this. For modern UEFI systems, the
firmware that's launched from the reset vector then reprograms the
CPU into a sensible mode (ie, one without all this segmentation
bullshit), does things like configure the memory controller so you
can actually access RAM (a process which involves using CPU cache
as RAM, because programming a memory controller is sufficiently
hard that you need to store more state than you can fit in
registers alone, which means you need RAM, but you don't have RAM
until the memory cont...
10:00
HPR3836: Using 'zoxide', an alternative to 'cd' Hacker Public Radio
hr.thin { border: 0; height: 0; border-top: 1px solid rgba(0, 0, 0, 0.1); border-bottom: 1px solid rgba(255, 255, 255, 0.3); } Overview I like the idea that there are tools available to enhance the 'cd' command, remembering places you have been in the file system and taking you there easily. I use 'pushd' and 'popd' for moving in and out of directories from a place I want to do most of my work, but something more powerful than these or cd have always seemed desirable. I was using 'autojump' for a while last year, but didnt really get on with it. This was mainly because there was no way of excluding certain directories which had been visited from its list. Recently I heard of 'zoxide', which I have been trying and really like. zoxide What is it? From the GitHub page: zoxide is a smarter cd command, inspired by z1 and autojump. It remembers which directories you use most frequently, so you can jump to them in just a few keystrokes. zoxide works on all major shells. In its man page its billed as A faster way to navigate your filesystem. Its written in Rust so is very fast. What does it do? It offers the functionality of the Linux/Unix 'cd' command. It collects the directories you have visited into a database and gives them a ranking relating to the number of times they have been visited. It applies aging rules and removes these when the ranking drops below one. It uses frecency to do this - a combination of frequency and recency. (See the Wikipedia page explaining this word) It performs algorithmic matching on the directory you specify and takes you to the highest ranking best match. It can resolve conflicts between matching directories or can allow selection through an interactive interface. It can interface to fzf, a general-purpose command-line fuzzy finder. It knows where it is (in the Bash shell) by calling a function out of the PROMPT_COMMAND variable. This can be used to execute one or more commands before displaying the prompt for a new command. This is a common way to hook monitoring commands into a Bash session. Where can you get it? I installed it from the Debian Testing repo, but I got 'zoxide from the GitHub page seems the best option if you want the latest version. There is an installation script on the GitHub page and its possible to download it with curl and pipe it to Bash. Im never comfortable doing this, but thats your choice. I also installed fzf from the Debian Testing repo, though Im still learning what this can do, since its very rich in features! How do you set it up? This process is shell-specific. I run Bash so I have added it to my ~/.bashrc and the command there is: eval "$(zoxide init bash)" What this does is generate a number of Bash functions and aliases and some commands which are fed into eval and executed in the current context. Function z is created which gives a way of invo
Taxing Collaborative Software Engineering It Will Never Work in Theory
Our field needs more papers like this one: a short, readable introduction to a complex topic (international tax law) for programmers who know nothing about it (like me) but whose work it might directly impact. I'd never heard of the Arm's Length Principle before, but after spending 15 minutes with this paper I have at least a glimmer of an understanding of the issues involved. I'm going to include this paper in the next software engineering class I teach, and would be grateful for pointers to others like it.
Michael Dorner, Maximilian Capraro, Oliver Treidler, Tom-Eric Kunz, Darja mite, Ehsan Zabardast, Daniel Mendez, and Krzysztof Wnuk. Taxing collaborative software engineering. 2023. arXiv:2304.06539.
The engineering of complex software systems is often the result of a highly collaborative effort. However, collaboration within a multinational enterprise has an overlooked legal implication when developers collaborate across national borders: It is taxable. In this short article, we discuss the unsolved problem of taxing collaborative software engineering across borders. We (1) introduce the reader to the basic principle of international taxation, (2) identify three main challenges for taxing collaborative software engineering, and (3) estimate the industrial significance of cross-border collaboration in modern software engineering by measuring cross-border code reviews at a multinational software company.
09:00
Hackaday Links: April 16, 2023 Hackaday

The dystopian future youve been expecting is here now, at least if you live in New York City, which unveiled a trio of technology solutions to the citys crime woes this week. Surprisingly, the least terrifying one is DigiDog, which seems to be more or less an off-the-shelf Spot robot from Boston Dynamics. DigiDogs job is to de-escalate hostage negotiation situations, and unarmed though it may be, we suspect that the mission will fail spectacularly if either the hostage or hostage-taker has seen Black Mirror. Also likely to terrify the public is the totally-not-a-Dalek-looking K5 Autonomous Security Robot, which is apparently already wandering around Times Square using AI and other buzzwords to snitch on people. And finally, theres StarChase, which is based on an AR-15 lower receiver and shoots GPS trackers that stick to cars so they can be tracked remotely. Were not sure about that last one either; besides the fact that it looks like a grenade launcher, the GPS tracker isnt exactly covert. Plus its only attached with adhesive, so it seems easy enough to pop it off the target vehicle and throw it in a sewer, or even attach it to a...
08:54
Linux 6.3-rc7 Released - Hoping For A Calm Week Ahead Phoronix
Linux 6.3-rc7 was just released and if the next week remains calm, it would mean that Linux 6.3 is shipping next weekend...
08:22
The 8086 Processor's Microcode Pipeline From Die Analysis SoylentNews
https://www.righto.com/2023/01/the-8086-processors-microcode-pipeline.html
Intel introduced the 8086 microprocessor in 1978, and its influence still remains through the popular x86 architecture. The 8086 was a fairly complex microprocessor for its time, implementing instructions in microcode with pipelining to improve performance. This blog post explains the microcode operations for a particular instruction, "ADD immediate". As the 8086 documentation will tell you, this instruction takes four clock cycles to execute. But looking internally shows seven clock cycles of activity. How does the 8086 fit seven cycles of computation into four cycles? As I will show, the trick is pipelining.
[...] The alternative is microcode: instead of building the control circuitry from complex logic gates, the control logic is largely replaced with code. To execute a machine instruction, the computer internally executes several simpler micro-instructions, specified by the microcode. In other words, microcode forms another layer between the machine instructions and the hardware. The main advantage of microcode is that it turns the processor's control logic into a programming task instead of a difficult logic design task.
Read more of this story at SoylentNews.
08:18
Five fulcrums for fundamental public sector reform pipka.org
In government we often speak about policy levers, but in the real world, a lever without a fulcrum is just a plank of wood. Levers are needed to lift a load, but without a fulcrum, you cant move it very far. Fulcrums are needed to dramatically increase the impact of a lever without having to increase the effort/resource. Basically, levers without fulcrums are pretty ineffective.
Sometimes even ambitious change agendas can unintentionally adopt a levers-without-fulcrums pattern. For instance, setting up a team to innovate without normalising a culture of innovation across the organisation. Hiring or training extraordinary talent and then not letting them make any decisions or bring ideas to the table. Training staff on public engagement without creating an appetite for public input. Every lever needs a fulcrum.
Once you look for it, you can see this pattern everywhere.
So below are five of my favourite fulcrums to complement the
usual policy levers you have today  These
are all tried and tested in various governments. These fulcrums
are: teaching public sector craft to all who work in (and with) the
public sector, a responsible implementation mindset, servant
leadership, structuring around outcomes, and finally the critical
fulcrum of raised expectations.
These
are all tried and tested in various governments. These fulcrums
are: teaching public sector craft to all who work in (and with) the
public sector, a responsible implementation mindset, servant
leadership, structuring around outcomes, and finally the critical
fulcrum of raised expectations.
Fulcrum 1: Teaching public service craft to all involved
All public servants used to be trained in public service craft. At some point, about 30 years ago, there was a change that mechanised the public sector (driven by New Public Management) and started bringing people in for a particular skillset (developer, accountant, lawyer, project manager, etc) with limited training on the context in which theyd be applying those skills. These days, generally only policy people are expected to be trained in the ways of government, and even then, many public policy courses teach only the mechanics of public sector without the responsibilities or clear delineation of powers and accountabilities.
We have seen the results of this in shocking testimony throughout the Robodebt Royal Commission, as senior public servants demonstrated a complete misunderstanding (and sometimes abdication) of their responsibility to be trusted stewards acting both lawfully and in the best public interest, instead believing their job to just advise, and then loyally (blindly?) implement the decisions of the government of the day, whatever the cost, conflict, impact or legality. This culture issue is well articulated in the recent submission to the Robodebt Royal Commission...
07:02
Re: CVE-2023-2002: Linux Bluetooth: Unauthorized management command execution Open Source Security
Posted by Steffen Nurpmeso on Apr 16
Ruihan Li wrote in<w7boj4fg4x2o2bjz7a7zkjk4bgxqvqyuxycdqqw2dl3bhanh6a@h4jtbccffxgv>:
...
|be privileged, such as a setuid program. Moreover, if the socket is used as
|stdout or stderr, an ioctl call is made to obtain tty parameters, which \
|can be
|verified through the strace command.
|```
|# strace -e trace=ioctl sudo > /dev/null
|ioctl(3, TIOCGPGRP, [30305]) = 0
|ioctl(2, TIOCGWINSZ, {ws_row=45, ws_col=190,...
06:02
Experts found the first LockBit encryptor that targets macOS systems Security Affairs
Researchers warn that the LockBit ransomware gang has developed encryptors to target macOS devices.
The LockBit group is the first ransomware gang of all time that has created encryptors to target macOS systems, MalwareHunterTeam team warn.
MalwareHunterTeam researchers discovered the LockBit encryptors in a ZIP archive uploaded to VirusTotal.
The discovery is disconcerting and demonstrates the effort of the group to expand its operation targeting also Apple systems.
BleepingComputer confirmed that the zip archive contained previously unknown encryptors for macOS, ARM, FreeBSD, MIPS, and SPARC architectures.
The experts pointed out that the archive has been bundled as March 20, 2023, it also includes builds for PowerPC CPUs, which are used in older macOS systems.
One of the encryptors developed by Lockbit, named locker_Apple_M1_64, can encrypt files of Mac systems running on the Apple silicon M1.
05:09
OpenAssistant Released cryptogon.com
That didnt take long. I thought it would take at least several months for them to attain something GPT3.5-like. Nope. Via: Yannic Kilcher:
04:33
DMCA Takedowns Target Torrent Release of Dark and Darker Playtest TorrentFreak
 Upcoming first-person shooter game Dark and Darker
is scheduled to launch later this year, but even at this early
stage its causing controversy.
Upcoming first-person shooter game Dark and Darker
is scheduled to launch later this year, but even at this early
stage its causing controversy.
Last month, police in South Korea raided the offices of local game studio Ironmace. According to reports, the developers allegedly stole assets from their former employer, game publisher Nexon, which is allegedly working on a similar project too.
A few days later, Nexon sent a DMCA takedown notice to Valve, asking it to remove the Dark and Darker project from Steam. The detailed takedown notices accused Ironmace of copyright infringement and stealing trade secrets.
This letter is to inform you of Ironmaces misconduct, constituting misappropriation of Nexons trade secrets and copyright infringement and to request that Valve take down all versions of Dark and Darker from Steam, the company wrote (pdf).

Steam swiftly complied, but the enforcement action and follow-up legal pressure didnt stop Dark and Darker development. Ironmace refuted the accusations in detail and continued to work on the game.
This weekend, Ironmace was ready to share the latest Alpha release with its fans. Without Steam access, Ironmace had to choose a different distribution method and after some internal deliberation, opted to go old school with a BitTorrent release.
Unfortunately, due to the complexities of our situation, especially across international lines, it is taking time to resolve the Steam situation. In order for us to keep our promise to our fans weve had to go old school this time, Ironmace wrote.
The developers typically share these types...
03:29
OpenBSD 7.3 has been released.
Who invented vector clocks?, by Lindsey Kuper.
Two algorithms for randomly generating aperiodic tilings, nice exposition by Simon Tatham.
My4TH, a homebuilt CPU-less computer with a 1-bit NOR gate ALU, running FORTH. By Dennis Kuschel.
How to Crash SM64 Using a Pendulum (YouTube), explained by pannenkoek2012.
Build faster with Buck2, Metas open source build system. Written in Rust, rules are now implemented fully in Starlark.
Knit: making a better Make, with some good ideas.
SIMD-ized faster parse of IPv4 addresses, by Wojciech Mua.
The microcode and hardware in the 8086 processor that perform string operations, by Ken Shirriff.
Hell Never Ends On x86: The Hyperspace Story, Continued, Sort Of, by cathoderaydude. Office software running in EFI.
The time Bell Labs brought the Statue of Liberty under its roof (Literally)
PLATO Emoticons, revisited (2012). Uses overprinting.
03:29
A Computer Generated Swatting Service Is Causing Havoc Across America SoylentNews
Torswats uses synthesized voices to pressure law enforcement to specific locations:
"Hello, I just committed a crime and I want to confess," a panicked sounding man said in a call to a police department in February. "I've placed explosives inside a local school,' the man continued.
"You did what?!" the operator responded.
"I've placed explosives inside a local school," the man said again, before specifying Hempstead High School in Dubuque, Iowa, and providing its address. In response to the threat, the school went on lockdown, and police searched the school but found nothing, according to a local media report.
The bombs weren't real. But, crucially, neither was the man's voice. The panicked man's lines sound artificially generated, according to recordings of the swatting calls reviewed by Motherboard. It is unclear how exactly the caller generated the voice, be that some form of artificial intelligence tool or another speech synthesis program. The result, though, is a voice that sounds very consistent across multiple calls.
[...] Known as "Torswats" on the messaging app Telegram, the swatter has been calling in bomb and mass shooting threats against highschools and other locations across the country. Torswat's connection to these wide ranging swatting incidents has not been previously reported. The further automation of swatting techniques threatens to make an already dangerous harassment technique more prevalent.
[...] Torswats carries out these threatening calls as part of a paid service they offer. For $75, Torswats says they will close down a school. For $50, Torswats says customers can buy "extreme swattings," in which authorities will handcuff the victim and search the house. Torswats says they offer discounts to returning customers, and can negotiate prices for "famous people and targets such as Twitch streamers." Torswats says on their Telegram channel that they take payment in cryptocurrency.
Read more of this story at SoylentNews.