| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Monday, 17 April
03:00
3D-Printable Foaming Nozzle Shows How They Work Hackaday

[Jack]s design for a 3D-printable foaming nozzle works by mixing air with a fluid like liquid soap or hand sanitizer. This mixture gets forced through what looks like layers of fine-mesh sieve and eventually out the end by squeezing the bottle. The nozzle has no moving parts but does have an interesting structure to make this possible.
01:22
How Music Hijacks Our Perception of Time Lifeboat News: The Blog
One evening, some 40 years ago, I got lost in time. I was at a performance of Schuberts String Quintet in C major. During the second movement I had the unnerving feeling that time was literally grinding to a halt. The sensation was powerful, visceral, overwhelming. It was a life-changing moment, or, as it felt at the time, a life-changing eon.
It has been my goal ever since to compose music that usurps the perceived flow of time and commandeers the sense of how time passes. Although Ive learned to manipulate subjective time, I still stand in awe of Schuberts unparalleled power. Nearly two centuries ago, the composer anticipated the neurological underpinnings of time perception that science has underscored in the past few decades.
The human brain, we have learned, adjusts and recalibrates temporal perception. Our ability to encode and decode sequential information, to integrate and segregate simultaneous signals, is fundamental to human survival. It allows us to find our place in, and navigate, our physical world. But music also demonstrates that time perception is inherently subjectiveand an integral part of our lives. For the time element in music is single, wrote Thomas Mann in his novel, The Magic Mountain. Into a section of mortal time music pours itself, thereby inexpressibly enhancing and ennobling what it fills.
01:00
Your Robotic Avatar Is Almost Ready IEEE Spectrum

Robots are not ready for the real world. Its still an achievement for autonomous robots to merely survive in the real world, which is a long way from any kind of useful generalized autonomy. Under some fairly specific constraints, autonomous robots are starting to find a few valuable niches in semistructured environments, like offices and hospitals and warehouses. But when it comes to the unstructured nature of disaster areas or human interaction, or really any situation that requires innovation and creativity, autonomous robots are often at a loss.
For the foreseeable future, this means that humans are still necessary. It doesnt mean that humans must be physically present, howeverjust that a human is in the loop somewhere. And this creates an opportunity.
In 2018, the XPrize Foundation announced a competition (sponsored by the Japanese airline ANA) to create an avatar system that can transport human presence to a remote location in real time, with the goal of developing robotic systems that could be used by humans to interact with the world anywhere with a decent Internet connection. The final event took place last November in Long Beach, Calif., where 17 teams from around the world competed for US $8 million in prize money.
 While avatar
systems are all able to move and interact with their environment,
the Avatar XPrize competition showcased a variety of different
hardware and software approaches to creating the most effective
system.XPrize
Foundation
While avatar
systems are all able to move and interact with their environment,
the Avatar XPrize competition showcased a variety of different
hardware and software approaches to creating the most effective
system.XPrize
Foundation
The competition showc...
00:49
Ubiquitous fake crowds Geeking with Greg
The Washington Post writes: "The Russian government has become far more successful at manipulating social media and search engine rankings than previously known, boosting ... [propaganda] with hundreds of thousands of fake online accounts ... detected ... only about 1% of the time."
Fake crowds can fake popularity. It's easy to manipulate trending, rankers, and recommender algorithms. All you have to do is create a thousand sockpuppet accounts and have them like and share all your stuff. Wisdom of the crowds is broken. This can be fixed, but first you have to see the problem clearly. Then you'll see that you can't just use the behavior from every account anymore for wisdom of the crowd algorithms. You have to use only reliable accounts and toss everything spammy or unknown.00:31
NCR was the victim of BlackCat/ALPHV ransomware gang Security Affairs
NCR was the victim of the BlackCat/ALPHV ransomware gang, the attack caused an outage on the companys Aloha PoS platform.
NCR Corporation, previously known as National Cash Register, is an American software, consulting and technology company providing several professional services and electronic products. It manufactures self-service kiosks, point-of-sale terminals, automated teller machines, check processing systems, and barcode scanners.
NCR is suffering an outage on its Aloha point of sale platform since Wednesday after it was hit by a ransomware attack conducted by the BlackCat/ALPHV ransomware group.
NCR Aloha POS is a comprehensive restaurant point-of-sale and management software, the company claims it is used by more cashiers and servers than any other POS in the industry.
The company has started notifying its customers, confirming the ransomware attack:
As a valued customer of NCR Corporation, we are reaching out with additional information about a single data center outage that is impacting a limited number of ancillary Aloha applications for a subset of our hospitality customers. On April 13, we confirmed that the outage was the result of a ransomware incident. reads the notice sent by the company to the customers via email.
NCR notified law enforcement and engaged third-party cybersecurity experts to investigate the incident and determine the scope of the attack.
The company pointed out that restaurants impacted are still able to serve their customers and that the incident only impacted a specific functionality.
Only specific functionality is impaired. There is no impact to payment applications or on-premises systems. continues the notice.
00:00
Timeframe: The Little Desk Calendar That Could Hackaday

Usually, the problem comes before the solution, but for [Stavros], the opposite happened. A 4.7 E-Ink screen with integrated battery management and ESP32 caught his eye, and he bought it and started thinking about what he wanted to do with it. The Timeframe (hackaday.io link as well) is a sleek desk calendar based around the integrated e-ink screen.
[Stavros] found the devices MicroPython support was a little lackluster, and often failed to draw. He found a Platform.io project that used an older but modified library for driving the e-ink display which worked quite well. However, the older library didnt support portrait orientation or other niceties. Rather than try and create something complex in C, he moved the complexity to a server environment he knew more about. With the help of CoPilot, he got some code that would wake up the ESP32 every half hour, download an image from a server, and then display it. A Python script uses a headless browser to visit Google Calendar, resize the window, take a screenshot, and then upload it.
The hardest part of the exercise was getting authentication with Google working reliably. A white sleek 3d printed case wraps the whole affair in an...
00:00
Lithium Battery Ripe for Disruption, Inventor Says IEEE Spectrum

The lithium-ion battery isnt going anywhere soon. Thats what M. Stanley Whittingham, the Nobel laureate who created the first rechargeable lithium-ion battery some 50 years ago, told attendees of the SLAC-Stanford Battery Research Center Launch Symposium on Thursday. The new organization aims to bridge gaps between organizations that research, manufacture, and deploy large-scale energy storage systems.
 M. Stanley
Whittingham
M. Stanley
Whittingham
Its going to be at least five-to-ten years before any
alternative technologies can compete on cost with lithium-ion
technology, Whittingham predicted.
Granted that this technology remains the incumbent for some time to come, Whittingham has concernsbig concernsabout how the world makes and uses these energy storage devices. Here are the big issues he worries about:
Manufacturing
Its ridiculous that manufacturing technologies havent changed in 30 years, Whittingham says. We need to reduce the 60 to 80 kilowatt hours) of electricity it takes to produce a one kWh battery, he says. Weve got to find new manufacturing technologies.
Recycling
Whittingham is also worried about recycling technologies. Hes encouraged that facilities to recycle lithium-ion batteries are being built around the world, but he adds, We need to make sure they are clean.
Mining
The supply chain for the minerals used in battery manufacturing in the first place also need work. We need regional supply chains, Whittingham says. And we need to look at clean mining with clean energy.
Heavy Metals
Given that some components of a lithium-ion batterys traditional chemistry are inherently toxic, they must be engineered out of the device as soon as possible, Whittingham says. He put it bluntly: Co...
Sunday, 16 April
23:45
Links 16/04/2023: digiKam 8.0.0 and PGroonga 3.0.0 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Digital Restrictions (DRM)
- Monopolies
- Gemini* and Gopher
-
GNU/Linux
-
Linux Links Linux Around The World: USA Hawaii
We cover user groups that are running in the US state of Hawai...
-
23:30
AMD Squeezes In AMDGPU Fixes, FPO/FAMS Display Power Savings For Linux 6.4 Phoronix
While we are basically past the cut-off of new feature material to into DRM-Next that wants to be part of the upcoming Linux 6.4 merge window, this week AMD sent in a fixes-oriented set of AMDGPU/AMDKFD kernel driver updates that does include some minor feature updates...
23:23
Life on Mars: When and How | The Next Stage of Human Evolution and the Possible Demise of the Planet Lifeboat News: The Blog

Do you like our content? Please support PRO Robots on
Patreon.
https://www.patreon.com/PRORobots.
Your contributions will help us to create better content and to
improve our service for you and our PRO Robots community. Every
dollar counts and will help us keep working for you.
Thank you for your support!
 For
business inquiries: info.prorobots@gmail.com.
For
business inquiries: info.prorobots@gmail.com.
 Instagram: https://www.instagram.com/pro_robots.
Instagram: https://www.instagram.com/pro_robots.
Do you know why humanity still doesnt have colonies on the Moon or Mars? Because the big companies that mightve invested their money in building the said colonies are not sure when theyll get their investments back and start making a solid profit. Well, at least thats one of the reasons.
But the cheaper space flights will get and further the technologies that can help cost-efficiently settle on other planets will develop, the more countries, billionaires, tech giants, startups and institutions will get into the space race, whose finish line is right on the Red Planet. Why are they reluctant to do this? Are they afraid of future cataclysms? Do they know something we dont? Are they dreaming of claiming the title of pioneers? Or hoping to mine rare metals in the asteroid belt?
Watch this video to find out all about the whens and hows of life on Mars, as well as about its outcomes, including a new round of human evolution and the possible demise of the planet itself! Wheels up!
00:00 In this video.
01:00 Mars will try to kill you.
01:30 Mars is a totally hostile environment for human life.
02:25 With Mars, Earthlings have a better chance.
04:01 What have we already found on the Red Planet?
05:22 Ilon Musk.
06:04 Prolonged flight exposes people to the greatest horror.
07:45 development of new super-powered engines.
08:24 an inflatable heat shield for astronauts to land on the
planet.
09:12 Mars has no planetary magnetic field.
10:27 But the...
23:22
Vitamin B6: Increase NAD Without NR, NMN, or Niacin? Lifeboat News: The Blog
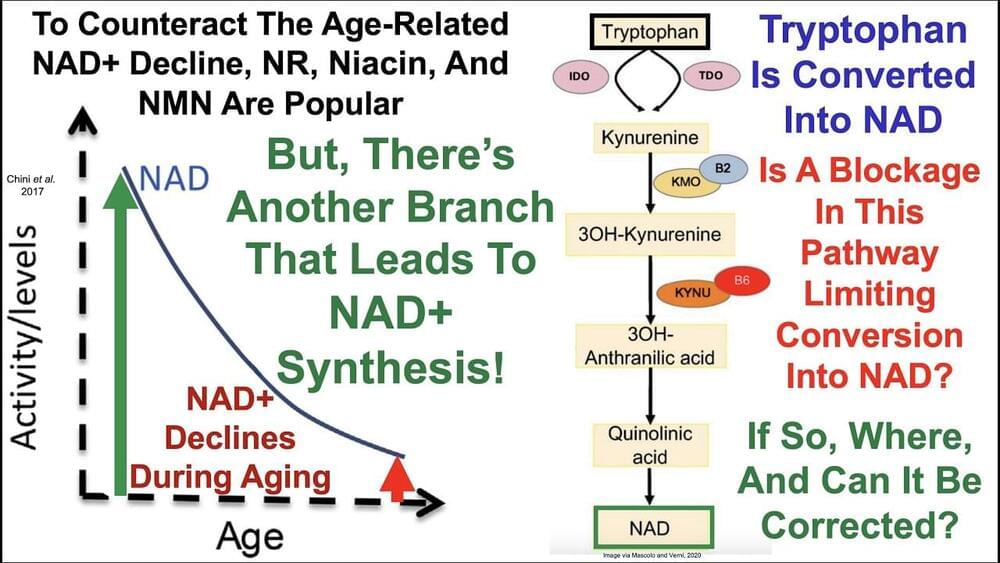
Join us on Patreon! https://www.patreon.com/MichaelLustgartenPhD
Discount Links:
NAD+ Quantification: https://www.jinfiniti.com/intracellular-nad-test/
Use Code: ConquerAging At Checkout.
Green Tea: https://www.ochaandco.com/?ref=conqueraging.
Oral Microbiome: https://www.bristlehealth.com/?ref=michaellustgarten.
Epigenetic Testing: Trudiagnostic.pxf.io/R55XDv.
Use Code: CONQUERAGING
At-Home Blood Testing: https://getquantify.io/mlustgarten.
23:00
Linux Fix On The Way For A Scheduler Imbalance Overflow Issue Phoronix
Sent in this morning for Linux 6.3 is a Linux CPU scheduler fix to deal with an imbalancing issue that's been present in the mainline kernel since a scheduler rework that landed back in late 2019...
23:00
The Tremendous VR and CG Systemsof the 1960s IEEE Spectrum

Ivan Sutherland has blazed a truly unique trail through computing over the past six decades. One of the most influential figures in the story of computing, he helped to open new pathways for others to explore and dramatically extend: interactive computer graphics, virtual reality, 3D computer graphics, and asynchronous systems, to name but a few.
The Computer History Museum recently made public its two-part oral history with Sutherland. These interviews present a wonderful opportunity to learn more about Sutherlands life in computing, in his own words. The interview transcripts can be downloaded here and here. And the two-part video of the interview is available here and here.
Bob Sproull, a lifelong colleague of Sutherland and himself a major figure in computing, served as instigator, interviewer, and editor for these oral histories, and he involved me, Marc Weber, and Jim Waldo in the effort. The Museum is making this oral history interview public during the 60th anniversary year of Sutherlands breakthrough in interactive computer graphics, the program Sketchpad, for which he earned his Ph.D. from MIT in 1963.
Ivan Sutherlands Unique Perspective
There is a phrase, popular in 17th and 18th century England, that occurs to me when thinking about Ivan Sutherland: A man of many parts. The phrase refers to an individual who had made serious contributions to a domain, while also possessing multiple, and often diverse, talents and pursuits. The description fits Sutherland well, although it also misses something important: There is a commonality in his many accomplishments, a shared wellspring for his many parts.
To get at this wellspring, start with geometry. From his youth, Sutherland possessed an unusually keen spatial, geometric intuition. In his mind and at his hands, he experienced an immediacy in perceiving how things fit and worked together. Perspective drawing involves a set of techniques to represent a three-dimensional scene on the two-dimensional plane of a sheet of paper or a stretch of canvas. These renderings can proceed in different ways, determined by the number of vanishing points employed. Together the vanishing points defi...
22:58
Security Affairs newsletter Round 415 by Pierluigi Paganini International edition Security Affairs
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are free for you in your email box.
22:44
Upgraded View of 'Fuzzy' Supermassive Black Hole is a Shade More Menacing SoylentNews
Using machine learning, a team of researchers has enhanced the first image ever taken of a distant black hole. Importantly, the newly updated image shows the full resolution of the telescope array for the very first time.
[...] The machine learning model has sharpened the otherwise blurry image of black hole M87, showcasing the utility of machine learning models in improving radio telescope images. The team's research was published today in the Astrophysical Journal Letters.
"Approximately four years after the first horizon-scale image of a black hole was unveiled by EHT in 2019, we have marked another milestone, producing an image that utilizes the full resolution of the array for the first time," said Dimitrios Psaltis, a researcher at Georgia Tech and a member of the EHT collaboration, in an Institute for Advanced Study release. "The new machine learning techniques that we have developed provide a golden opportunity for our collective work to understand black hole physics."
[...] But even using radio telescopes around the world doesn't give astronomers a complete view of the black hole; by incorporating a machine learning technique called PRIMO, the collaboration was able to improve the array's resolution. What appeared a bulbous, orange doughnut in a 2019 image has now taken on the delicate, thin circle of The One Ring.
Read more of this story at SoylentNews.
22:24
Microsoft Continues Building Out Its Linux Distribution With More Packages Phoronix
Microsoft has published its latest CBL-Mariner 2.0.20230407 Linux distribution images this weekend as their in-house open-source OS that is used for a variety of purposes, mostly around Azure infrastructure...
21:45
Remcos RAT campaign targets US accounting and tax return preparation firms Security Affairs
Microsoft warns of a new Remcos RAT campaign targeting US accounting and tax return preparation firms ahead of Tax Day.
Ahead of the U.S. Tax Day, Microsoft has observed a new Remcos RAT campaign targeting US accounting and tax return preparation firms. The phishing attacks began in February 2023, the IT giant reported.
Remcos is a legitimate remote monitoring and surveillance software developed by the company BreakingSecurity.
In 2021, CISA added Remcos to the list of top malware strains due to its use in mass phishing attacks using COVID-19 pandemic themes targeting businesses and individuals.
The recent campaign exclusively aims at organizations that deal with tax preparation, financial services, CPA and accounting firms, and professional service firms dealing in bookkeeping and tax.
Crooks use lures masquerading as tax documentation sent by a client. The message contains a link that points to a legitimate file hosting site where the cybercriminals have uploaded Windows shortcut (.LNK) files.
Upon clicking on the file, a malicious file is fetched from a domain under the control of the attacker which leads to the installation of the Remcos RAT.
What we have observed is that the link in the phishing email points to Amazon Web Services click tracking service at awstrack[.]me. The initial link then redirects the target to a ZIP file hosted on legitimate file-sharing service spaces[.]hightail[.]com. The ZIP file contains LNK files that act as Windows shortcuts to other files. reads the report published by Microsoft. The LNK files make web requests to actor-controlled domains...
21:26
CVE-2023-2002: Linux Bluetooth: Unauthorized management command execution Open Source Security
Posted by Ruihan Li on Apr 16
Hi,An insufficient permission check has been found in the Bluetooth subsystem of
the Linux kernel when handling ioctl system calls of HCI sockets. This causes
tasks without the proper CAP_NET_ADMIN capability can easily mark HCI sockets
as _trusted_. Trusted sockets are intended to enable the sending and receiving
of management commands and events, such as pairing or connecting with a new
device. As a result, unprivileged users can acquire a...
21:23
CVE-2023-24831: Apache IoTDB grafana-connector Login Bypass Vulnerability Open Source Security
Posted by Jialin Qiao on Apr 16
Severity: lowDescription:
Improper Authentication vulnerability in Apache Software Foundation Apache IoTDB.This issue affects Apache IoTDB
Grafana Connector: from 0.13.0 through 0.13.3.
Attackers could login without authorization. This is fixed in 0.13.4.
References:
https://iotdb.apache.org/
https://iotdb.apache.org
https://www.cve.org/CVERecord?id=CVE-2023-24831
21:22
The factory making bionic arms for Ukrainian soldiers BBC News Lifeboat News: The Blog

Thousands of people in Ukraine have lost their limbs in the war against Russia, according to World Health Organisation estimates.
The Ukrainian charity Superhumans and the UK-based company Open Bionics have partnered to create bionic arms for the wounded.
The BBC visited the factory in Bristol, England, responsible for creating the prosthetics.
Please subscribe here: http://bit.ly/1rbfUog.
#Ukraine #BionicArm #Bristol
21:21
CVE-2023-30771: Apache IoTDB Workbench: apache/iotdb-web-workbench: forge the JWTToken to access workbench Open Source Security
Posted by Jialin Qiao on Apr 16
Severity: lowDescription:
Incorrect Authorization vulnerability in Apache Software Foundation Apache IoTDB.This issue affects the
iotdb-web-workbench component on 0.13.3. iotdb-web-workbench is an optional component of IoTDB, providing a web console
of the database.
onwards.
References:
https://iotdb.apache.org
https://www.cve.org/CVERecord?id=CVE-2023-30771
21:00
Detecting Anti-Neutrinos from Distant Fission Reactors Using Pure Water at SNO+ Hackaday

Although neutrinos are exceedingly common, their near-massless configuration means that their presence is rather ephemeral. Despite billions of them radiating every second towards Earth from sources like our Sun, most of them zip through our bodies and this very planet without ever interacting with either. This property is also what makes studying these particles that are so fundamental to our understanding so complicated. Fortunately recently published results by researchers behind the SNO+ neutrino detector project shows that we may see a significant bump in our neutrino detection sensitivity.
20:46
FSF Slams Google Over Dropping JPEG-XL In Chrome Phoronix
Last October Google engineers decided they would deprecate JPEG-XL support in Chrome over some debated rationale for the move. Even amid the community uproar they went ahead to drop the JPEG-XL support. The Free Software Foundation has finally commented on the matter...
20:33
digiKam 8.0 Released With Expanded File Format Support, New OCR Tool Phoronix
The digiKam 8.0 open-source professional photo management software has been released. The digiKam 8.0 release brings a host of new features and improvements, including ongoing work of porting over to the Qt6 toolkit...
19:23
This Just Changed My Mind About AGI Lifeboat News: The Blog
There have been 4 research papers and technological advancements over the last 4 weeks that in combination drastically changed my outlook on the AGI timeline.
GPT-4 can teach itself to become better through self reflection, learn tools with minimal demonstrations, it can act as a central brain and outsource tasks to other models (HuggingGPT) and it can behave as an autonomous agent that can pursue a multi-step goal without human intervention (Auto-GPT). It is not an overstatement that there are already Sparks of AGI.
Join my channel membership to support my work:
https://www.youtube.com/channel/UCycGV6fAhD_-7GPmCkkESdw/join.
Or send me a tip over lightning:  till@getalby.com.
till@getalby.com.
My profile: https://bitcoiner.bio/tillmusshoff.
Twitter: https://twitter.com/bPGTill.
My Discord server: https://discord.gg/e5KXwadq4s.
Instagram: https://www.instagram.com/tillmusshoff/
18:00
Week in review: Microsoft patches zero-day, Apple security updates, HashiCorp Vault vulnerability Help Net Security
Heres an overview of some of last weeks most interesting news, articles, interviews and videos: Making risk-based decisions in a rapidly changing cyber climate In this Help Net Security interview, Nicole reveals the three key indicators she uses to assess an industrial organizations cybersecurity readiness and provides valuable insights for businesses and governments on fortifying their critical infrastructure against cyber threats. Data-backed insights for future-proof cybersecurity strategies In this Help Net Security interview, Travis Smith, More
The post Week in review: Microsoft patches zero-day, Apple security updates, HashiCorp Vault vulnerability appeared first on Help Net Security.
18:00
[CuriousMarc] Repairs a Floppy Hackaday

[CuriousMarc] has a pile of 8-inch drives, all marked bad. You cant just pop over to the computer store and buy a new one these days, so it was off to the repair bench. Although the target drive would do a quick seek, once it was in use, it just kind of shut down. So [Marc] started sending low-level commands to the device to see if he could isolate the fault. You can watch the whole adventure in the video below.
Using a breakout board, he was able to monitor and exercise all the pins going into the floppy. A quick study of the schematics, and connection to the scope were all [Marc] needed to build some theories of what was happening.
One of the theories was that the head amplifier was disabled, but it turned out to be fine. After several other dead ends, he finally found a broken spring and came up with a creative repair for it. But there was still no clear reason why the drive wouldnt work. By process of elimination, he started to suspect an array of diodes used for switching, but again, it was another dead end.
Luckily, he had one working drive, so he could compare things between them. He found a strange voltage difference. Turns out the old advice of checking power first might have paid off here. One of the voltage regulator ICs was dead. In all fairness, there are two 12V power supplies and he had checked one of them but had missed the second supply. This supply is only used for head bias which switches the diodes he h...
17:57
Writers and Publishers Face an Existential Threat From AI: Time to Embrace the True Fans Model SoylentNews
Writers and publishers face an existential threat from AI: time to embrace the true fans model:
Walled Culture has written several times about the major impact that generative AI will have on the copyright landscape. More specifically, these systems, which can create quickly and cheaply written material on any topic and in any style, are likely to threaten the publishing industry in profound ways. Exactly how is spelled out in this great post by Suw Charman-Anderson on her Word Count blog. The key point is that large language models (LLMs) are able to generate huge quantities of material. The fact that much of it is poorly written makes things worse, because it becomes harder to find the good stuff[.]
[...] One obvious approach is to try to use AI against AI. That is, to employ automated vetting systems to weed out the obvious rubbish. That will lead to an expensive arms race between competing AI software, with unsatisfactory results for publishers and creators. If anything, it will only cause LLMs to become better and to produce material even faster in an attempt to fool or simply overwhelm the vetting AIs.
The real solution is to move to an entirely different business model, which is based on the unique connection between human creators and their fans. The true fans approach has been discussed here many times in other contexts, and once more reveals itself as resilient in the face of change brought about by rapidly-advancing digital technologies.
Read more of this story at SoylentNews.
17:37
IRC Proceedings: Saturday, April 15, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-150423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-150423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-150423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-150423.gmi
Over HTTP:
|
... |
17:24
How I Hacked The US Government Aged 16 | Minutes With | @LADbible Lifeboat News: The Blog

In this weeks episode of Minutes With we sat down with Mustafa Al-Bassam, a former member of Anonymous and one of the founders of LulzSec.
Mustafa tells us how he got in to hacking and how he ended up getting involved in attacks on The Sun, The Westboro Baptist Church and even the US Government.
Subscribe To Our Channel: http://bit.ly/SubscribeLADbible.
Facebook: https://www.facebook.com/ladbible/
Instagram: https://www.instagram.com/ladbible/
Twitter: https://twitter.com/ladbible.
#LADbible #UNILAD
To license this video please email: licensing@ladbiblegroup.com
17:23
US DARPA RACER Off-Road Autonomous Vehicles Teams Navigate Third Test Lifeboat News: The Blog

U.S. DARPAs Robotic Autonomy in Complex Environments with Resiliency (RACER) program recently conducted its third experiment to assess the performance of off-road unmanned vehicles. These test runs, conducted March 1227, included the first with completely uninhabited RACER Fleet Vehicles (RFVs), with a safety operator overseeing in a supporting chase vehicle. The goal of the RACER program is to demonstrate autonomous movement of combat-scale vehicles in complex, mission-relevant off-road environments that are significantly more unpredictable than on-road conditions. The multiple courses were in the challenging and unforgiving terrain of the Mojave Desert at the U.S. Armys National Training Center (NTC) in Ft. Irwin, California. As at the previous events, teams from Carnegie Mellon University, NASAs Jet Propulsion Laboratory, and the University of Washington participated. This completed the projects first phase.
We provided the performers RACER fleet vehicles with common performance, sensing, and compute. This enables us to evaluate the performance of the performer team autonomy software in similar environments and compare it to human performance, said Young. During this latest experiment, we continued to push vehicle limits in perceiving the environments to greater distances, enabling further increase in speeds and better adaptation to newly encountered environmental conditions that will continue into RACERs next phase.
At Experiment Three, we successfully demonstrated significant improvements in our off-road speeds while simultaneously reducing any interaction with the vehicle during test runs. We were also honored to have representatives from the Army and Marine Corps at the experiment to facilitate transition of technologies developed in RACER to future service unmanned initiatives and concepts, said Stuart Young, RACER program manager in DARPAs Tactical Technology Office.
17:23
Mixed Reality Tracking System For Future Pilot Training Lifeboat News: The Blog
Vrgineers and Advanced Realtime Tracking demonstrate the combination of XTAL 3 headset and SMARTTRACK3/M in a mixed reality pilot trainer. The partnership between these two technological companies started in 2018. At IT2EC 2023 in Rotterdam, the integrated SMARTTRACK3/M into an F-35-like Classroom Trainer manufactured and delivered to USAF and RAF will be for display. This unique combination of the latest ART infrared all-in-one hardware and Vrgineers algorithms for cockpit motion compensation creates an unseen immersion for every mixed reality training. One of the challenges in next-generation pilot training using virtual technology and motion platforms is the alignment of the pilots position in the cockpit. By overcoming this issue, the simulator industry is moving forward to eliminate the disadvantages of simulated training.
We are continuously working on removing the technological challenges of modern simulators, one of which is caused by front-facing camera position distance from users eyes. We are developing advanced algorithms for motion compensation to minimize the shift between virtual and physical scene, making experience realistic. The durability and compact size of SMARTTRACK3/M, which was optimized for using in cockpits, allows us as training device integrator to make it a comprehensive part of a simulation, says Marek Polcak, CEO of Vrgineers.
This is the application SMARTTRACK3/M was designed for., We have taken the proven hardware from the SMARTTRACK3 and adapted it to the limited space available. As a result, we have the precision and the reliability of a seasoned system in a form factor fitting to simulator cockpits says Andreas Werner, business development manager for simulations at ART.
17:22
15:22
Precise Spatial Proteomic Information in Tissues Lifeboat News: The Blog
Despite the availability of imaging-based and mass-spectrometry-based methods for spatial proteomics, a key challenge remains connecting images with single-cell-resolution protein abundance measurements. Deep Visual Proteomics (DVP), a recently introduced method, combines artificial-intelligence-driven image analysis of cellular phenotypes with automated single-cell or single-nucleus laser microdissection and ultra-high-sensitivity mass spectrometry. DVP links protein abundance to complex cellular or subcellular phenotypes while preserving spatial context.
15:00
Real Radar Scope CRT Shows Flights Using ADS-B Hackaday

Real-time flight data used to be something that was only available to air traffic controllers, hunched over radar scopes in darkened rooms watching the comings and goings of flights as glowing phosphor traces on their screens. But that was then; now, flight tracking is as simple as pulling up a web page. But wheres the fun in that?
To bring some of that old-school feel to his flight tracking, [Jarrett Cigainero] has been working on this ADS-B scope that uses a real radar CRT. As you can imagine, this project is pretty complex, starting with driving the 5FP7 CRT, a 5 round-face tube with a long-persistence P7-type phosphor. The tube needs about 7 kV for the anode, which is delivered via a homebrew power supply complete with a custom flyback transformer. Theres also a lot going on with the X-Y deflection amps and beam intensity control.
The software side has a lot going on as well. ADS-B data comes from an SDR dongle using dump1090 running on a Raspberry Pi 3B...
15:00
Links 16/04/2023: Many Videos and Some New Distro Releases Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
-
GNU/Linux
-
Audiocasts/Shows
-
2023-04-15 Top 5 Best Hyprland Linux Features
-
2023-04-14 Kubuntu 23.04 overview | making your PC friendly
-
2023-04-14 Microsofts about to muscle their way into the handheld PC space | Steam Deck News 78
-
2023-04-14 A HUGE Percentage Of The Arch Repos Was Packaged By One Man!
-
2023-04-14 Ranking Linux Distributions for 2023: not your average tier list!
-
2023-04-14 How to inst...
-
-
14:42
IMF Unveils New Global Currency Known As The Universal Monetary Unit cryptogon.com
Via: The Economic Collapse Blog: The Universal Monetary Unit, also known as Unicoin, is an international central bank digital currency that has been designed to work in conjunction with all existing national currencies. This should set off alarm bells for all of us, because the widespread adoption of a new global currency would be a []
13:13
New Model for How Earth's Oceans Formed SoylentNews
You don't need alien asteroids, you just need a hydrogen-rich atmosphere and liquid hot magma:
A new research model shows that Earth's oceans could have formed from interactions between a hydrogen-rich early atmosphere and oxygen within the planet's magma.
The study from the multi-institution AETHER project also demonstrates why Earth's core is lighter than it should be, owing to the presence of gaseous hydrogen.
Edward Young, professor at the University of California Los Angeles, and colleagues propose that one of the protoplanets involved in the formation of Earth was heavier than thought. By maximizing its size to more than a fifth or third of Earth, the researchers show there would have been enough gravity to make the hydrogen-rich atmosphere hang around long enough to interact with the magma ocean, according to a paper published in Nature this week.
Prevailing theories explaining the abundance of water on Earth oceans make up around 70 percent of the planet's surface depend on the impacts of water-carrying asteroids.
[...] In a statement coinciding with the publication, co-author Anat Shahar, staff scientist and deputy for Research Advancement Earth and Planets Laboratory at Carnegie Science, said the inspiration for the new model came from studies of planets forming outside the solar system.
Read more of this story at SoylentNews.
12:00
Relive the Glory Days of Sun Workstations Hackaday

When the IBM PC first came out, it was little more than a toy. The serious people had Sun or Apollo workstations. These ran Unix, and had nice (for the day) displays and network connections. They were also expensive, especially considering what you got. But now, QEMU can let you relive the glory days of the old Sun workstations by booting SunOS 4 (AKA Solaris 1.1.2) on your PC today. [John Millikin] shows you how in step-by-step detail.
Theres little doubt your PC has enough power to pull it off. The SUN-3 introduced in 1985 might have 8MB or 16MB of RAM and a 16.67 MHz CPU. In 1985, an 3/75 (which, admittedly, had a Motorola CPU and not a SPARC CPU) with 4MB of RAM and a monochrome monitor cost almost $16,000, and that didnt include software or the network adapter. Youd need that network adapter to boot off the network, too, unless you sprung another $6,000 for a 71 MB disk. The SPARCstation 1 showed up around 1989 and ran from $9,000 to $20,000, depending on what you needed.
[John] points out that, unlike a modern PC, SunOS ran on very tightly-controlled hardware, so it is pretty fussy about some things being just right. Apparently, QEMU could not boot the OS without some workarounds until recently, but the setup [John] outlines seems straightforward.
In its heyday, the machine would get network configuration from a RARP and NIS server, but those have long given way to more modern standards like DHCP. Not...
11:38
Links 15/04/2023: IBM Buys Ahana, pgAdmin 4 v7.0 Released Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Kernel Space
-
Hot Hardware ...
-
-
11:30
Snowflake Manufacturing Data Cloud improves supply chain performance Help Net Security
Snowflake has launched the Manufacturing Data Cloud, which enables companies in automotive, technology, energy, and industrial sectors to unlock the value of their critical siloed industrial data by leveraging Snowflakes data platform, Snowflake- and partner-delivered solutions, and industry-specific datasets. The Manufacturing Data Cloud empowers manufacturers to collaborate with partners, suppliers, and customers in a secure and scalable way, driving greater agility and visibility across the entire value chain. With Snowflakes Manufacturing Data Cloud, organizations can More
The post Snowflake Manufacturing Data Cloud improves supply chain performance appeared first on Help Net Security.
09:30
Tentacle partners with Oread Risk & Advisory to simplify SOC 2 compliance for organizations Help Net Security
Tentacle announced a SOC 2 partnership with Oread Risk & Advisory to help organizations achieve SOC 2 reporting goals and establish long-term security infrastructure. With Tentacles release of the indexed SOC 2 security framework earlier this year, organizations have access to critical tools to eliminate guesswork by leveraging auditor-vetted SOC 2 controls and to assess readiness at their own pace. The partnership with Oread further enhances the capabilities related to SOC 2 preparedness, assessment, and More
The post Tentacle partners with Oread Risk & Advisory to simplify SOC 2 compliance for organizations appeared first on Help Net Security.
09:15
Khoros and Cerby join forces to secure social media platforms Help Net Security
Khoros and Cerby new partnership allows brands to launch, manage, and analyze their social media profiles quickly and securely from the Khoros platform. Cerby brings security features such as single sign-on (SSO) directly into social accounts and ad accounts for Khoros and Cerby customers alike. Belsasar Lepe, CEO of Cerby, said, Cerby protects direct access to social media and ad accounts for Khoros customers. Were honored that Khoros, who powers over 550 million digital engagements More
The post Khoros and Cerby join forces to secure social media platforms appeared first on Help Net Security.
09:00
CYFIRMA raises an undisclosed amount in Pre-Series B funding for product innovation Help Net Security
CYFIRMA has raised a Pre-Series B round funding from venture fund OurCrowd and Larsen & Toubros L&T Innovation Fund. With this, these firms join CYFIRMAs existing investors Goldman Sachs, Zodius Capital, and Z3 Partners. With the closing of this round, CYFIRMA has raised nearly USD18M to date. The funds raised will be used for product innovation and entering new global markets in North America, Europe and MENA region in addition to growing the existing markets More
The post CYFIRMA raises an undisclosed amount in Pre-Series B funding for product innovation appeared first on Help Net Security.
09:00
3D Printed Tool Lets You Measure Component Reels Easily Hackaday

Component reels are a highly-0ptimized packaging format. They deliver components to pick and place machines for effective high-speed assembly. As more of us get into working with SMD components, were exposed to them as well. [MG] wanted a way to easily measure tape from component reels, which is difficult because theyre often curled up. Thus, they whipped up a nifty little tool for the job.
The device consists of a 3D printed bracket which is designed to fit on a cheap electronic tape measure from Amazon. The bracket holds an 8mm wide component tape against the measuring wheel. As the component tape is fed through the device, it turns the wheel, and the measurement appears on the screen. No more must you try and flatten out a tape and measure it section by section. Instead, you just feed it in, yank it through, and youre done!
[MG] notes that the tape measure itself runs on an STM32 microcontroller. As an extra-credit assignment, they suggest that the device could be reprogrammed to display component count instead of distance if thats more suitable for your appli...
08:32
Linux Kernel Logic Allowed Spectre Attack on Major Cloud SoylentNews
Kernel 6.2 ditched a useful defense against ghostly chip design flaw:
The Spectre vulnerability that has haunted hardware and software makers since 2018 continues to defy efforts to bury it.
On Thursday, Eduardo (sirdarckcat) Vela Nava, from Google's product security response team, kernel.
The bug, designated medium severity, was initially reported to cloud service providers those most likely to be affected on December 31, 2022, and was patched in Linux on February 27, 2023.
"The kernel failed to protect applications that attempted to protect against Spectre v2, leaving them open to attack from other processes running on the same physical core in another hyperthread," the vulnerability disclosure explains. The consequence of that attack is potential information exposure (e.g., leaked private keys) through this pernicous problem.
The moniker Spectre [PDF] describes a set of vulnerabilities that abuse speculative execution, a processor performance optimization in which potential instructions are executed in advance to save time.
Read more of this story at SoylentNews.
08:30
UltraViolet Cyber launches to address the ever-expanding cyber threat Help Net Security
UltraViolet Cyber has unveiled its launch to provide organizations across the globe with a streamlined approach to address the ever-expanding cyber threat. Created through the combination of four pioneering firms Metmox, Mosaic451, Stage 2 Security, and W@tchTower UltraViolet Cyber brings together decades of expertise and experience at the forefront of security operations to enable organizations to access the full spectrum of managed security operations capabilities. As cyber threats continue to increase, too many organizations More
The post UltraViolet Cyber launches to address the ever-expanding cyber threat appeared first on Help Net Security.
04:08
DMCA Robocops Give 20 Seconds to Comply, But Cant Muster a Reply TorrentFreak
 Faced with millions of instances of copyright
infringement every day, many rightsholders use anti-piracy
companies to help stem the tide.
Faced with millions of instances of copyright
infringement every day, many rightsholders use anti-piracy
companies to help stem the tide.
More often than not, that involves sending DMCA takedown notices on an industrial scale, in the hope that Google and Bing delist infringing URLs from search results before the cycle begins again.
Huge volumes of DMCA notices and similar requests are handled directly by companies including YouTube, Twitter, Facebook and Instagram. And thats just a part of a very large iceberg, much of it completely and permanently hidden, and almost all of it automated.
Trust the Machines
For years TorrentFreak has documented the most newsworthy takedown demands from the billions of notices sent to Google and other platforms with transparency programs.
Our focus is usually on the most egregious examples of wrongful and damaging takedowns, especially those that couldve been avoided by taking basic steps guided by common sense. Programmed by humans yet blamed on machines, the robo-blunderers mistakes are rarely even acknowledged by those ultimately responsible.
Our own experience shows that URLs on this very website have been wrongfully reported to Google almost 150 times by 65 reporting organizations and rightsholders. We were targeted again in February for referring to a piracy app by name in an article reporting that its alleged creator had been arrested.
RoboCop: Book him!
Sgt. Reed: Whats the charge?
RoboCop: He writes about pirates
A full 7% of all wrongful DMCA notices filed against the torrentfreak.com domain are duplicate attempts to take down the same non-existent infringing content that caused the first set of notices to be rejected. We have a good faith belief means almost nothing the first time; after another futile attempt expecting a different outcome, its at best sarcastic, at worst a flat-out lie.
The Personal Touch Via Email
Rather than complainin...
03:48
EU Parliaments Research Service Confirms: Chat Control Violates Fundamental Rights SoylentNews
MEP Patrick Breyer (Germany, Pirate Party), one of the few representatives fighting for preserving rights online rather than against them, has posted a summary about the EU Parliament's assessment of the proposed "Chat Control" legislation. In short, the "Chat Control" proposal violates basic human rights:
The experts made clear that an "increase in the number of reported contents does not necessarily lead to a corresponding increase in investigations and prosecutions leading to better protection of children. As long as the capacity of law enforcement agencies is limited to its current size, an increase in reports will make effective prosecution of depictions of abuse more difficult."
In addition, the study finds: "It is undisputed that children need to be protected from becoming victims of child abuse and depictions of abuse online... but they also need to be able to enjoy the protection of fundamental rights as a basis for their development and transition into adulthood." It warns: With regards to adult users with no malicious intentions, chilling effects are likely to occur."
There is an obfuscated link at the bottom of his post to the study, Proposal for a regulation laying down the rules to prevent and combat child sexual abuse: Complementary Impact Assessment. He also has older overview of the problems with the proposed legislation at his blog, too.
Read more of this story at SoylentNews.
03:38
New Android malicious library Goldoson found in 60 apps +100M downloads Security Affairs
A new Android malware named Goldoson was distributed through 60 legitimate apps on the official Google Play store.
The Goldoson library was discovered by researchers from McAfees Mobile Research Team, it collects lists of applications installed on a device, and a history of Wi-Fi and Bluetooth devices information, including nearby GPS locations. The third-party library can perform ad fraud by clicking advertisements in the background without the users consent. The experts have found more than 60 applications in Google Play that were containing the malicious library. The apps totaled more than 100 million downloads in the ONE store and Google Play stores in South Korea.
It is important to highlight that the library was not developed by the authors of the apps.
The security firm reported its findings to Google, which notified the development teams. Some apps were updated by removing the malicious library, while other apps were removed from Google Play.
Below is the list of the apps using the malicious library that had the highest number of downloads:
| Package Name | Application Name | GooglePlay Downloads | GP Status |
| com.lottemembers.android | L.POINT with L.PAY | 10M+ | Updated* |
| com.Monthly23.SwipeBrickBreaker | Swipe Brick Breaker | 10M+ | Removed** |
| com.realbyteapps.moneymanagerfree | Money Manager Expense & Budget | 10M+ | Updated* |
| com.skt.tmap.ku | TMAP ,, , | 10M+ | Updated* |
| kr.co.lottecinema.lcm | 10M+ | Updated* | |
| com.ktmusic.geniemusic | genie | 10M+ | Updated* |
| com.cultureland.ver2 | [] | 5M+ | Updated* |
| com.gretech.gomplayerko | GOM Player | 5M+ | Updated* |
| com.megabox.mop | (Megabox) | 5M+ | Removed** |
| kr.co.psynet | LIVE Score, Real-Time Score | 5M+ | Updated* |
| sixclk.newpiki | Pikicast | 5M+ | Removed** |
Upon executing one of the above apps, the Goldoson library registers the...
03:29
LXQt 1.3 Released While Qt6 Porting Remains A Work-In-Progress Phoronix
01:57
Links 15/04/2023: EasyOS 5.2.1 and Arkansas Versus Fentanylware (TikTok) Techrights
![]()
Contents
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Pseudo-Open Source
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Digital Restrictions (DRM)
- Monopolies
- Gemini* and Gopher
-
Distributions and Operating Systems
-
New Releases
-
Barry Kauler EasyOS Kir...
-
-
01:44
Reworked x86_64 Parallel Boot Support Posted For The Linux Kernel Phoronix
Being worked on for a while has been Linux kernel patches to speed boot times by allowing the parallel bring-up of CPU cores. There were AMD boot issues since worked around and the patches gone through multiple revisions for helping with Linux kernel boot times. Those patches continue to be improved upon and yesterday saw a reworked patch series posted...
01:24
6 Ways That Battery Analytics Can Help Decarbonize Our Economy Lifeboat News: The Blog
To meet climate commitments, we need to use more batteries across many economic sectors. Battery analytics can help to remove risk and increase uptake.
01:22
Yann LeCun and Andrew Ng: Why the 6-month AI Pause is a Bad Idea Lifeboat News: The Blog

Join us for a conversation with Andrew Ng and Yann LeCun as they discuss the proposal of a 6-month moratorium on generative AI.
We will be taking questions during the event. Please submit your
question or upvote others here:
https://app.sli.do/event/9yGgPaweRK9Cbo8wsqV6oq/live/questions.
Speakers.
Yann LeCun, VP & Chief AI Scientist at Meta and Silver Professor at
NYU
https://www.linkedin.com/in/yann-lecun/
Andrew Ng, Founder of DeepLearning. AI
https://www.linkedin.com/in/andrewyng/
Let us know how were doing? We will be giving out discount codes
for a selected number of people who fill out the survey:
https://forms.gle/ArNXCmkZc6YwwyXD7
Looking to connect with your peer learners, share projects, and
swap advice? Join our AI community:
https://community.deeplearning.ai/invites/VVGtXQuWNR
01:05
CVE-2023-22946: Apache Spark proxy-user privilege escalation from malicious configuration class Open Source Security
Posted by Sean R. Owen on Apr 15
Description:In Apache Spark versions prior to 3.4.0, applications using spark-submit can specify a 'proxy-user' to run as, limiting
privileges. The application can execute code with the privileges of the submitting user, however, by providing
malicious configuration-related classes on the classpath. This affects architectures relying on proxy-user, for example
those using Apache Livy to manage submitted applications.
This issue is...
01:00
Can We Identify a Person From Their Voice? IEEE Spectrum

At 6:36 a.m., on 3 December 2020, the U.S Coast Guard received a call over a radio channel reserved for emergency use: Mayday, Mayday, Mayday. We lost our rudder...and were taking on water fast. The voice hiccupped, almost as if the man were struggling. He radioed again, this time to say that the pumps had begun to fail. He said hed try to get his boat, a 42-footer with three people on board, back to Atwoods, a lobster company on Spruce Head Island, Maine. The Coast Guard asked for his GPS coordinates and received no reply.
That morning, a Maine Marine Patrol officer, Nathan Stillwell, set off in search of the missing vessel. Stillwell rode down to Atwood Lobster Co., which is located at the end of a peninsula, and boarded a lobster boat, motoring out into water so shockingly cold it can induce lethal hypothermia in as little as 30 minutes.
When he returned to shore, Stillwell continued canvassing the area for people who had heard the radio plea for help. Someone told him the voice in the mayday call sounded messed up, according to a report obtained through a state-records request. Others said it sounded like Nate Libby, a dockside worker. So Stillwell went inside Atwoods and used his phone to record his conversation with Libby and another man, Duane Maki. Stillwell asked if they had heard the call.
I was putting my gloves and everything on the rack, Libby told him. I heard it. I didnt know that word, honestly, (presumably referring to the word mayday.) And I just heard it freaking coming on that he lost his rudder, that he needed pumps. Both men denied making the call.
Stillwell seemed unsure. In his report, he said hed received other tips suggesting the VHF call had been made by a man whose first name was Hunter. But then, the next day, a lobsterman, who owned a boat like the one reported to be in distress, called Stillwell. He was convinced that the mayday caller was his former sternman, the crew member who works in the back of the lobster boat: Nate Libby.
The alarm was more than just a prank call. Broadcasting a false distress signal over maritime radio is a violation of international code and, in the United States, a federal Class D felony. The Coast Guard recorded the calls, which spanned about 4 minutes, and investigators isolated four WAV files,...
00:30
Siemens Metaverse exposes sensitive corporate data Security Affairs
Siemens Metaverse, a virtual space built to mirror real machines, factories, and other highly complex systems, has exposed sensitive data, including the companys office plans and internet of things (IoT) devices.
While metaverse is no longer a buzzword, amid the sudden popularity of ChatGPT and similar AI tools, those virtual worlds are still here, presenting exciting opportunities for companies, users, and, unfortunately, threat actors.
Siemens, a German multinational with over $71 trillion in revenue and 300,000 employees worldwide, has also jumped on the metaverse bandwagon. In 2022, it partnered with NVidia, an American multinational technology company, to build the industrial metaverse.
Recently, the Cybernews research team has discovered that Siemens Metaverse a platform that aims to create digital twins of its factories and offices was leaking sensitive information.
If attackers got to the exposed data, it could have had devastating consequences for the company and other big corporations using its services, including ransomware attacks.
Siemens, on the other hand, said it considered the issue to be non-critical and added that it had been mitigated.
Metaverse leak: what we discovered
On March 1, the Cybernews research team discovered an environment file hosted on a metaverse.siemens.com domain. It contained ComfyApp credentials and endpoints. It also discovered Siemens leaking four sets of WordPress users, and three sets of backend and authentication endpoint URLs on different endpoints of the affected systems.
The WordPress sets only exposed user names and avatar pictures, but all four Siemens WordPress-based subdomains were vulnerable to a flaw that WordPress itself fixed in 2017, leaving researchers wondering whether there are more severe vulnerabilities on these sites.
Backend and authentication endpoint URLs, used to verify users before giving them access, could lead to attackers testing them for vulnerabilities and exploiting them.
The most worrying discovery was that of exposed office management platform ComfyApp user credentials. The Si...
00:00
Sufficiently Advanced Tech: Has Bugs Hackaday

Arthur C. Clarke said that Any sufficiently advanced technology is indistinguishable from magic. He was a sci-fi writer, though, and not a security guy. Maybe it should read Any sufficiently advanced tech has security flaws. Because this is the story of breaking into a car through its headlight.
In a marvelous writeup, half-story, half CAN-bus masterclass, [Ken Tindell] details how car thieves pried off the front headlight of a friends Toyota, and managed to steal it just by saying the right things into the network. Since the headlight is on the same network as the door locks, pulling out the bulb and sending the open the door message repeatedly, along with a lot of other commands to essentially jam some other security features, can pull it off.
Half of you are asking what this has to do with Arthur C. Clarke, and the other half are probably asking what a lightbulb is doing on a cars data network. In principle, its a great idea to have all of the electronics in a car be smart electronics, reporting their status back to the central computer. Its how we know when our lights are out, or what our tire pressure is, from the drivers seat. But adding features adds attack surfaces. What seems like...
00:00
Quantum Technologys Unsung Heroes IEEE Spectrum

In a world where quantum technologies are on the rise in computing, cryptography, materials, sensors, telecom, biomed, and AI, its easy to forget that not so long ago the words quantum and technology rarely fit comfortably into a sentence together. A range of trailblazers imagined quantum physics turning into quantum engineering turning into quantum user techor, for those working before the quantum era, imagined far-off theoretical horizons coming into range of practical applications. However, not all of these early innovators are known to those developing present-day quantum technologies. Yet rediscovering the lost history of early quantum pioneers today yields at least three dividendsadvancing the field by better understanding its past, inspiring new generations of future leaders, and finally giving credit where credits due.
With such inspirations in mind, the science journalists Brian Lenahan and Kenna Hughes-Castleberry have written a new book On The Shoulders of Giants: 10 Quantum Pioneers of the Past (published this week), resuscitating the legacies of sometimes obscure figures in quantum history. Not by coincidence, their books release also neatly aligns with the underpinnings of World Quantum Day (14 April)which organizers established to promote the public understanding of quantum science and technology around the world.
IEEE Spectrum recently spoke with Lenahan and Hughes-Casteleberry about overshadowed genius, pre-medieval computer programs, and Claude Shannons Vogue magazine celebrity photoshoot.
IEEE Spectrum: What were the criteria you used to select the historical figures your book highligh...
Saturday, 15 April
23:22
What they thought of aging in 1931 Lifeboat News: The Blog

What did scientists think about aging in 1931? Thats right. 1931. because that is the year the first biological textbook was published The Science of Life. I managed to get my hands on the first edition of this textbook. This was my face when i first received it. As you can see i was quite excited. And this textbook is made up of separate books. I bought book i last year and i read it. Having enjoyed it and discovered that it was part of this massive ensemble piece well, ive read the first book there are, if my roman numerals are correct, 9 books in total. And in this first book, penned The Living Body, the authors, most famously, H.G.Wells, Sir Julian Huxley and G.P.Wells, H.Gs son discusses the body as a machine and that.
For the present it is enough to remember that all animals (including men) are combustion engines of an intricate and curious kind, which live by oxidising their food
I bought first The Living Body and then discovered it was part of this massive ensemble piece and decided i needed to read it. Now, besides being surprised to find out that H.G.Wells wrote not just non-fiction, but biology non-fiction, i was also surprised to hear how both similar & dissimilar their views were back in 1931 compared to today and i wasnt sure if that was good or terrifying.
So, how did they think of human aging. Well, in the last chapter of this 1st book titled The wearing out of the machine and its reproduction, they discuss it.
Sheekey bookmarks https://www.contrado.co.uk/stores/the-sheekey-science-show/crk-1999569
Find me on Twitter -
https://twitter.com/EleanorSheekey.
Support the channel.
through PayPal https://paypal.me/sheekeyscience?country.x=GB&locale.x=en_GB
through Patreon https://www.patreon.com/TheSheekeyScienceShow.
23:06
OpenZFS 2.1.10 Released - Adds Linux 6.2 Support, Finally Drops Python 2 Compatibility Phoronix
OpenZFS 2.1.10 is out as the latest update to this open-source ZFS file-system implementation currently supported on Linux and FreeBSD systems...
23:02
Kodi TV Discloses Data Breach After Forum Database for Sale Online SoylentNews
[Editor's Note: This is not connected to the Kodi Linux Operating System. JR]
Bleeping Computer reports that Kodi has revealed (on 8 April 2023) that their forum [N.B. the forum itself is now gone and replaced with a blog post about the breach] database was breached and is for sale online.
From the Bleeping Computer article:
The Kodi Foundation has disclosed a data breach after hackers stole the organization's MyBB forum database containing user data and private messages and attempted to sell it online.
Kodi is a cross-platform open-source media player, organizer, and streaming suite, that supports a vast array of third-party add-ons enabling the users to access content from various sources or customize their experience.
The now-shut down Kodi forum has roughly 401,000 members who used it to discuss media streaming, exchange tips, offer support, share new add-ons, and more in 3 million posts.
According to an announcement published by the platform on Saturday, hackers stole the forum database by logging into the Admin console using an inactive staff member's credentials.
Once they gained access to the admin panel, they created and downloaded database backups multiple times in 2023.
"MyBB admin logs show the account of a trusted but currently inactive member of the forum admin team was used to access the web-based MyBB admin console twice: on 16 February and again on 21 February," explains Kodi in a message to its users.
"The account was used to create database backups which were then downloaded and deleted. It also downloaded existing nightly full-backups of the database."
The Kodi team confirmed that the actual account owner did not perform these actions on the admin console, indicating that the staff member's credentials were likely stolen.
"If you have used the same username and password on any other site, you should follow the password reset/change procedure for that site."
So Soylentils, do (or, in the case of the forum, did) you use Kodi or, more importantly, their forum?
If so, will this breach affect how/whether or not you (continue) to use Kodi?
Read more of this story at SoylentNews.
22:35
Libreboot Adds Support For The Once Common HP Elite 8200 SFF PC Phoronix
The HP Elite 8200 was once popular and very common among workplaces and can still be found used/refurbished for a little more than $100 for this small form factor PC. Libreboot has now added support for the HP Elite 8200 as its newest desktop port for this Intel Sandy Bridge era system...
22:34
Re: ncurses fixes upstream Open Source Security
Posted by Solar Designer on Apr 15
The (linux-)distros lists are meant for handling of embargoed issuesprior to their public disclosure and in cases where such private
handling is expected to help. In this case, the issue was already
semi-public (via the fixes and the NEWS file) and I wouldn't expect
private handling to help more than public does. Every distro present on
(linux-)distros is supposed to also be present on oss-security. So in
my opinion Jonathan did the...
22:08
Re: ncurses fixes upstream Open Source Security
Posted by Georgi Guninski on Apr 15
Isn't MicroSoft member of linux distros mailing list [0], whichpurpose is exactly quietly trading 0days [1]?
Does the OP with m$ email address realize this?
[0] https://oss-security.openwall.org/wiki/mailing-lists/distros
[1] https://seclists.org/oss-sec/2019/q3/19
Re: linux-distros membership application - Microsoft
22:06
Links 15/04/2023: KDE ISO Image Writer Beta 0.9.2 and PowerDNS DNSdist 1.7.4 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Monopolies
-
GNU/Linux
-
Kernel Space
-
PCLOS Official Kernels Updated
Kernels 6.2.11, 6.1.24 LTS and 5.15.107 LTS have been updated for PCLinuxOS and are now available in the Synaptic Software Repository.
-
-
Instructionals/Technical
-
LinuxTechi How to Ins...
-
-
21:25
Max Tegmark: The Case for Halting AI Development | Lex Fridman Podcast #371 Lifeboat News: The Blog

Max Tegmark is a physicist and AI researcher at MIT, co-founder
of the Future of Life Institute, and author of Life 3.0: Being
Human in the Age of Artificial Intelligence. Please support this
podcast by checking out our sponsors:
- Notion: https://notion.com.
- InsideTracker: https://insidetracker.com/lex
to get 20% off.
- Indeed: https://indeed.com/lex to get $75
credit.
EPISODE LINKS:
Maxs Twitter: https://twitter.com/tegmark.
Maxs Website: https://space.mit.edu/home/tegmark.
Pause Giant AI Experiments (open letter): https://futureoflife.org/open-letter/pause-giant-ai-experiments.
Future of Life Institute: https://futureoflife.org.
Books and resources mentioned:
1. Life 3.0 (book): https://amzn.to/3UB9rXB
2. Meditations on Moloch (essay): https://slatestarcodex.com/2014/07/30/meditations-on-moloch.
3. Nuclear winter paper: https://nature.com/articles/s43016-022-00573-0
PODCAST INFO:
Podcast website: https://lexfridman.com/podcast.
Apple Podcasts: https://apple.co/2lwqZIr.
Spotify: https://spoti.fi/2nEwCF8
RSS: https://lexfridman.com/feed/podcast/
Full episodes playlist:
https://www.youtube.com/playlist?list=PLrAXtmErZgOdP_8GztsuKi9nrraNbKKp4
Clips playlist:
https://www.youtube.com/playlist?list=PLrAXtmErZgOeciFP3CBCIEElOJeitOr41
OUTLINE:
0:00 Introduction.
1:56 Intelligent alien civilizations.
14:20 Life 3.0 and superintelligent AI
25:47 Open letter to pause Giant AI Experiments.
50:54 Maintaining control.
1:19:44 Regulation.
1:3...
21:24
Explained: What is Auto-GPT, the new do-it-all AI tool and how it works Lifeboat News: The Blog
If people are worried that Chat-GPT could be taking their jobs, they havent seen Auto-GPT yet.
Auto-GPT is an AI chatbot similar to ChatGPT and others. It is based on the GPT-4 language model of OpenAI, the same LLM that powers the ChatGPT. But, as the name implies, Autonomous Artificial Intelligence Chat Generative Pre-trained Transformer, a step further, but what exactly is it? Let us go through what Auto-GPT is and how it works.
What is Auto-GPT
Essentially, Auto-GPT is a chatbot. You ask it the questions it answers smartly. But, unlike ChatGPT and other GPT-based chatbots, which need a prompt every single time, Auto-GPT can automate the whole task, so you do not need to prompt it. Once given a task, Auto-GPT will figure out the steps on its own to reach the goal.
21:23
Dr Andrew McMahon & Lewis Kleinberg Pushing The Boundaries Of Research To Build A Synthetic Kidney Lifeboat News: The Blog

Pushing The Boundaries Of Research To Build A Synthetic Kidney Dr. Andrew McMahon, Ph.D. & Lewis Kleinberg, University Kidney Research Organization (UKRO)
The University Kidney Research Organization (UKRO https://ukrocharity.org/) is a Los Angeles-based nonprofit charity, co-founded prominent entertainment attorney Kenneth Kleinberg, inspired by his personal journey with kidney disease, focused on supporting medical research and education related to the causes, treatment, and eradication of all forms of kidney disease.
Dr. Andrew McMahon, Ph.D. (https://keck.usc.edu/faculty-search/andrew-p-mcmahon/) is Director of the Eli and Edythe Broad Center for Regenerative Medicine and Stem Cell Research at USC, Provost Professor and the inaugural holder of the W. M. Keck Professorship of Stem Cell Biology and Regenerative Medicine, and is responsible for overseeing UKROs Synthetic Kidney Project. In addition, Dr. McMahon chairs the recently created Department of Stem Cell Biology and Regenerative Medicine at the Keck School. He also holds an appointment in the Department of Biological Sciences in the USC Dornsife College of Letters, Arts, and Sciences.
Previously Dr. McMahon served as professor in the Department of Stem Cell and Regenerative Biology, Department of Molecular and Cellular Biology and principal faculty member in the Harvard Stem Cell Institute, as well as led the Department of Cell and Developmental Biology at the Roche Institute for Molecular Biology.
Dr. McMahon received his bachelors degree from St. Peters College, Oxford University and his Ph.D. from University College in London. He subsequently worked for three years as a postdoctoral fellow at the California Institute of Technology.
Lewis Kleinberg, a board member of UKRO and son of Kenneth Kleinberg, is a writer/producer who has written, developed and produced projects for Sony Pictures, Walt Disney Pictures, New Regency, 21st Century Fox, TNT, Anonymous Content, BBC Productions, Renegade 83, Kapital Entertainment, and USA Network, among others, and currently creates and produces films for UKROs website, media outreach, and benefit dinners. A graduate of the USC School of Cinematic Arts, he serves as an advisor to Donate Life Hollywood and as a mentor for USCs...
21:22
Noam Chomsky: AI Isnt Coming For Us All, You Idiots Lifeboat News: The Blog
The worlds preeminent linguist has spoken and he seems mighty tired of everyones whining about artificial intelligence as it stands today.
In an op-ed for the New York Times, Noam Chomsky said that although the current spate of AI chatbots such as OpenAIs ChatGPT and Microsofts Bing AI have been hailed as the first glimmers on the horizon of artificial general intelligence the point at which AIs are able to think and act in ways superior to humans we absolutely are not anywhere near that level yet.
That day may come, but its dawn is not yet breaking, contrary to what can be read in hyperbolic headlines and reckoned by injudicious investments, the Massachusetts Institute of Technology cognitive scientist mused.
21:00
Better Laser Cuts: Know Your Kerf Hackaday

The recent crop of laser cutters are nothing short of miraculous. For a few hundred dollars you can get a machine that can easily engrave and subject to materials cut well, too. [Nate] has been taking advantage of a laser to make boxes that join together using finger joinery. The problem is, the pieces have to fit exactly to get a good box. While setting dimensions in software is fine, you need to account for how much material the laser removes something traditional woodworkers and machinists know as kerf.
You can, of course, employ trial and error to get good results. But thats wasteful and potentially time-consuming. [Nate] built a tolerance fence that is quick to cut out and allows accurate measurement of kerf. You can quickly use the tolerance fence to make measurements and increase your chances of nailing your boxes on the first cut.
You have to customize the fence based on the thickness of your material. [Nate] uses Lightburn, which probably has a kerf offset already set by default in your layers. If not, youll need to turn it on and set an estimate of your kerf size. Then you are ready to cut the fence pieces and see how they fit together.
If the fit is too loose, you want to raise the kerf setting and try again. If it is too tight, you lower the kerf setting. As [Nate] says, Lower equals looser.
The results speak for themselves, as you can see in the trea...
20:47
Mesa 23.1-rc1 Published For Testing With Many Graphics Driver Updates Phoronix
Following this week's Mesa 23.1 feature freeze and code branching, Eric Engestrom on Friday night published Mesa 23.1-rc1...
20:47
CISA adds bugs in Android and Novi Survey to its Known Exploited Vulnerabilities catalog Security Affairs
US Cybersecurity and Infrastructure Security Agency (CISA) added Android and Novi Survey flaws to its Known Exploited Vulnerabilities catalog.
U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added the following five new issues to its Known Exploited Vulnerabilities Catalog:
- CVE-2023-20963 Android Framework Privilege Escalation Vulnerability. Android Framework contains an unspecified vulnerability that allows for privilege escalation after updating an app to a higher Target SDK with no additional execution privileges needed;
- CVE-2023-29492 Novi Survey Insecure Deserialization Vulnerability. Novi Survey contains an insecure deserialization vulnerability that allows remote attackers to execute code on the server in the context of the service account;
Google addressed the vulnerability CVE-2023-20963 with the release of The Android Security BulletinMarch 2023 security updates. The bulletin confirmed that there are indications that CVE-2023-20963 may be under limited, targeted exploitation.
According to Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities, FCEB agencies have to address the identified vulnerabilities by the due date to protect their networks against attacks exploiting the flaws in the catalog.
Experts recommend also private organizations review the Catalog and address the vulnerabilities in their infrastructure.
CISA orders federal agencies to fix this flaw by May 4, 2023.
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections:
- The Teacher Most Educational Blog
- The Entertainer Most Entertaining Blog
- The Tech Whizz Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please nominate Security Affairs as your favorite blog.
Nominate here: ...
20:14
KDE Improving Its Multi-GPU Infrastructure For Intel & AMD GPUs Phoronix
Plasma 6.0 development continues happening at full-speed and exciting this week were landing of some improvements around KWin's multi-GPU infrastructure to benefit Intel and AMD Radeon graphics...
19:37
Volvo retailer leaks sensitive files Security Affairs
The Brazilian retail arm of car manufacturing giant Volvo leaked sensitive files, putting its clientele in the vast South American country in peril.
- Volvos retailer in Brazil, Dimas Volvo, leaked sensitive files through its website.
- The leaked files could have served malicious actors in various ways, including hijacking official communication channels and infiltrating the companys systems.
- The issue causing the leak has been fixed.
Volvo, a Swedish luxury vehicle manufacturer with over 95,000 employees and sales of nearly 700,000 vehicles annually, is a highly attractive target for criminals since the company caters to a wealthy clientele.
The Cybernews research team discovered that the retailer of Volvo vehicles in Brazil, Dimas Volvo, was leaking sensitive files through its website for nearly a year.
The leaked files could have served malicious actors in various ways, including hijacking official communication channels and infiltrating the companys systems.
Cybernews contacted Dimas Volvo and data protection officers at Volvo headquarters, and the issue causing the leak was fixed.
Exposed sensitive files
On February 17, 2023, the Cybernews research team discovered public access to sensitive files hosted on dimasvolvo.com.br website, belonging to an independent Volvo retailer in the Santa Catarina region of Brazil.
Volvos retailer exposed its databases authentication information, including MySQL and Redis database hosts, open ports and credentials. These credentials could further be exploited to access the contents of the databases, which might have stored private user data.
Researchers also stumbled upon the websites Laravel application key. The exposure of this key is particularly dangerous because it could have been used to decrypt user cookies, which often hold sensitive information such as credentials or session IDs. An attacker could exploit this data to hijack the victims account.
Access to source code
Among the leaked data, researchers also observed the URL of the Git repository where the websites source code is stored, revealing the repository name and who created it.
Attackers may have exploited leaked credentials to brute force access to the repository, since they only needed a password, which is faster than guessing both a username and password.
The researchers also discovered a .DS_Store file that held metadata from the developers computer, revealing the file and folder names in the directory where the websites project files were stored.
Attackers could have used the information about the websites structure to...
19:22
A New Approach to Computation Reimagines Artificial Intelligence Lifeboat News: The Blog
By imbuing enormous vectors with semantic meaning, we can get machines to reason more abstractly and efficiently than before.
18:18
Arkansas Just Passed an Age-verification Social Media Law With Some Confusing Exemptions SoylentNews
There's confusion over which companies will be affected:
The law requires social media companies that earn more than $100 million in annual revenue to work with third-party services to verify new account holders' personal information. This is done using "any commercially reasonable age verification method" or government-issued IDs such as photo IDs or driver's licenses. Current account holders won't be affected.
The law states that social media companies are defined as any online forum that lets users create public profiles and interact with each other through digital content.
CNN reports that in the final days of negotiations over the bill, Arkansas lawmakers approved an amendment that appears to exempt some of the world's biggest social media companies. Given all the concern over TikTok's influence and its links with China, it's surprising to see that social media platforms that permit users to "generate short video clips of dancing, voice overs, or other acts of entertainment in which the primary purpose is not educational or informative" are exempt. That would also seem to cover Facebook, Instagram, Snapchat, as well as TikTok - but apparently not.
[...] Other exemptions include social media companies that "exclusively" offer subscription content, and those focused on "professional networking" and "career development" (i.e., LinkedIn). Companies that "exclusively offer" video gaming-focused social networking features aren't covered, either, which could include Twitch despite it not really being a social media platform.
At least it will protect the kids from all the remaining $100M/yr companies that weren't covered by the exemptions.
Read more of this story at SoylentNews.
18:09
IRC Proceedings: Friday, April 14, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-140423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-140423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-140423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-140423.gmi
Over HTTP:
|
... |
18:00
Uranium-241 Isotope Created and Examined Via Multinucleon Transfer Reactions and Mass Spectrometry Hackaday

A recent paper (PDF) in Physical Review Letters by T. Niwase and colleagues covers a fascinating new way to both create and effectively examine isotopes by employing a cyclotron and a mass spectrograph. In the paper, they describe the process of multinucleon transfer (MNT) and analysis at the recently commissioned KEK Isotope Separation System (KISS), located at the RIKEN Nishina Center in Japan.
17:00
Water-absorbing feathers could inspire better bottles and fog harvesters Terra Forming Terra

This is so odd. It works to both absorb water, but to also prevent a reversal of the process. No other bird does this and replicating this can be handy. Now imagine a water permiable membrane feeding an underlying layer. Handy in arid conditions for preserving water from your sweat.
Pragmatic approach may be the way forward for clinical trials Terra Forming Terra


SpaceX Starship Super Heavy April 17 Launch Date Terra Forming Terra
15:32
Links 15/04/2023: This Week in KDE and More Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Instructionals/Technical
-
Net2 Understanding the basic components of the Linux operating system architecture
If youre already a Linux user and maybe even a system admin for single systems, this article is for you.
-
-
Games
-
DragonFly BSD Digest SimCity 2000 in DOSBox
Si...
-
-
15:03
Read "Calamities causing loss of museum collections: a historical and global perspective on museum disasters" by Michael J. Tyler, Dale Roberts, and our Lydia A. Fucsko. Lifeboat News
Read "Calamities causing loss of museum collections: a historical and global perspective on museum disasters" by Michael J. Tyler, Dale Roberts, and our Lydia A. Fucsko.
15:03
MIT Technology Review Became Spamfarm of Microsoft Techrights
Four days ago: MIT Technology Review is Running SPAM for Microsoft and Azure (Distracting From Mass Layoffs)
Two months ago: MIT Technology Review is Run by Microsoft India

Hyping up AI for Microsoft et al under the guise of study,
by paying for puff pieces about the study

100% of the articles for that day are just paid-for spam about
grooming??? 8 pieces on that one day (more than
whats shown here) were all sponsored. Their RSS feed too
became marketing. The sponsored stuff isnt being separated.
15:00
Kicad Autorouting Made Easy Hackaday

One of the most laborious tasks in PCB layout is the routing. Autorouting isnt always perfect, but it is nice to have the option, even if you only use it to get started and then hand-tune the resulting board. Unfortunately, recent versions of Kicad have dropped support for autorouting. You can, however, still use Freerouting and the video from [Mr. T] below shows you how to get started.
There are three ways to get the autorouting support. You can install Java and a plugin, you can isntall using a ZIP file, or you can simply export a Specctra DSN file and use Freerouting as a standalone program. Then you import the output DSN file, and you are done.
Not only does [Mr. T] show you how to do a simple USB board, he also shows you how to rip up the autorouters work if you dont like it. He also covers some tips to get the best results with the router.
For example, it is often advantageous to manually layout a few critical tracks before you run the autorouter. You can also use net classes to specify parameters for some tracks.
Overall, this is a worthwhile thing to do. After all, you dont have to use autorouting, but it is nice to have it available if you want it. If you dont like Freerouting, you can try a different solution. Of course, these routers use DSN, so you can use them...
13:58
Google Releases Urgent Chrome Update to Fix Actively Exploited Zero-Day Vulnerability The Hacker News
Google on Friday released out-of-band updates to resolve an actively exploited zero-day flaw in its Chrome web browser, making it the first such bug to be addressed since the start of the year. Tracked as CVE-2023-2033, the high-severity vulnerability has been described as a type confusion issue in the V8 JavaScript engine. Clement Lecigne of Google's Threat Analysis Group (TAG) has been
13:36
Deep Space Missions Must Recreate Exact Earth-Like Conditions to Survive, Scientists Argue SoylentNews
One of the main questions surrounding humanity's next giant leap into deep space is whether humans can thrive on missions far from Earth. A new theory says yes, but only in environments modeled deeply after our own planet.
Father-daughter research duo Morgan Irons of Cornell University and Lee G. Irons from the Norfolk Institute dub the idea "pancosmorio," a word that means "all word limit," in a paper published in Frontiers in Astronomy and Space Sciences last month. Irons and Irons argue that, to allow humans to survive on lengthy treks into deep space, these missions must recreate Earth-like ecosystems, including Earth-like gravity and oxygen, reliable sources of water, as well as societal systems like steady agricultural output and the recycling of waste.
"For humans to sustain themselves and all of their technology, infrastructure and society in space, they need a self-restoring, Earth-like, natural ecosystem to back them up," said Morgan Irons in a press release from the institution. "Without these kinds of systems, the mission fails."
[...] "There are conditions from which human life has evolved. Such conditions are required to sustain human life at its current level of growth," the scientists write in their study. "The availability of such conditions to humans defines the limit of their world."
Read more of this story at SoylentNews.
13:26
Musk Incorporates X.AI cryptogon.com
Via: The Verge: Elon Musk has created a new company dedicated to artificial intelligence and its called X.AI, as first reported by The Wall Street Journal. The company, which a Nevada filing indicates was incorporated last month, currently has Musk as its director and Jared Birchall, the director of Musks family office, listed as []
12:54
What Are Transformer Models and How Do They Work? cryptogon.com
Via: cohere.ai: So why would a transformer model build text word by word? One answer is, because that works really well. A more satisfying one is that because transformers are so incredibly good at keeping track of the context, that the next word they pick is exactly what it needs to keep going with an []
12:30
Cobalt Iron updates Compass platform with new data governance capabilities Help Net Security
Cobalt Iron has updated its Compass enterprise SaaS backup platform with new data governance capabilities comprising policy-based controls and an approval framework for decommissioning systems and deleting data. The automation and policy-based discipline for system decommissioning and associated data deletion are unique to Compass and will deliver defensible data deletion and system retirement. Data governance is about being a good steward over data during its entire life cycle, from its creation or acceptance to its More
The post Cobalt Iron updates Compass platform with new data governance capabilities appeared first on Help Net Security.
12:23
SpaceX Receives a Launch License from the FAA for Starship cryptogon.com
Via: Ars Technica: On Friday afternoonafter much angst and anxious waiting by the spaceflight communitythe Federal Aviation Administration issued a launch license to SpaceX for the launch of its Starship rocket from South Texas. After a comprehensive license evaluation process, the FAA determined SpaceX met all safety, environmental, policy, payload, airspace integration and financial responsibility []
12:20
Daon brings IdentityX to healthcare industry Help Net Security
Daon is expanding its IdentityX to the healthcare industry to enable organizations to safeguard identities for providers, staff, and patients. As the healthcare industry continues to digitize sensitive healthcare online information, cyber attacks increase and new regulations are established, Daons Fast Healthcare Interoperability Resources (FHIR)-compliant solutions will reduce fraud for healthcare workers and staff, digital health app providers, and patients. Daon IdentityX provides identity proofing and authentication solutions for every touchpoint patient care, medical More
The post Daon brings IdentityX to healthcare industry appeared first on Help Net Security.
12:00
Need To Pick Objects Out Of Images? Segment Anything Does Exactly That Hackaday

Segment Anything, recently released by Facebook Research, does something that most people who have dabbled in computer vision have found daunting: reliably figure out which pixels in an image belong to an object. Making that easier is the goal of the Segment Anything Model (SAM), just released under the Apache 2.0 license.
10:34
Read the free paper "You Have a Duty to Migrate Off-Planet... (From Blue Origin to Green Destiny: Gerard K. O'Neill and Planetary Crises)" by our Charles Tandy. Lifeboat News
Read the free paper "You Have a Duty to Migrate Off-Planet (From Blue Origin to Green Destiny: Gerard K. O'Neill and Planetary Crises)" by our Charles Tandy.
09:53
Duffy: Run an open source-powered virtual conference! LWN.net
On her blog, Mirn Duffy writes about using open-source software to run a virtual conference. The Fedora design team recently ran the first Creative Freedom Summit as a virtual conference for FOSS creative tools. The team could have used the same non-open-source platform that is used by the Flock Fedora conference, but took a different path:
Using Matrix's Element client, we embedded the live stream video and an Etherpad into a public Matrix room for the conference. We used attendance in the channel to monitor overall conference attendance. We had live chat going throughout the conference and took questions from audience members both from the chat and the embedded Q&A Etherpad.
Back in 2020, the Linux Plumbers Conference also put together a virtual conference using free software, as did LibrePlanet and likely others.
09:45
Thales prepares to protect European infrastructures from quantum attacks Help Net Security
Thales has joined forces with around twenty deep tech, academic and industry partners, as part of the EuroQCI initiative (European Quantum Communication Infrastructure), which aims to deploy a quantum communication infrastructure for EU member states within three years. By 2040, quantum computers could use their unprecedented computational power to decode encrypted data, incomparably threatening the security of even the best-protected communication systems. EuroQCI aims to counter that threat by developing sovereign systems to protect the More
The post Thales prepares to protect European infrastructures from quantum attacks appeared first on Help Net Security.
09:30
Deloitte and Riskified help eCommerce merchants analyze their fraud exposure Help Net Security
Riskified has unveiled its partnership with Deloitte to empower merchants with real-time insight into how their chargebacks, approval rates and fraud costs compare to similar companies in their space. This benchmarking service is helping retailers formulate a scorecard that can uncover new opportunities to reduce operational costs, lower chargeback and fraud losses, and boost revenues by minimizing false declines. This offering is underpinned by Riskifieds extensive eCommerce, fraud and identity intelligence derived from analyzing more More
The post Deloitte and Riskified help eCommerce merchants analyze their fraud exposure appeared first on Help Net Security.
09:25
Votiro collaborates with Sumo Logic to provide analytics on file-borne threats Help Net Security
Votiro has integrated with Sumo Logic to enable reliable and secure cloud-native applications. Users can now send high-fidelity data and insights discovered by Votiro Cloud into the Sumo Logic Cloud SIEM console. Enterprises are relying on collaboration platforms, cloud workloads and storage environments more than ever before. File sharing and Cloud data usage will continue to expand, providing more opportunities for bad actors to penetrate enterprise networks through file-borne malware. Sumo Logics Cloud SIEM automatically More
The post Votiro collaborates with Sumo Logic to provide analytics on file-borne threats appeared first on Help Net Security.
09:00
Building an Electron Microscope For Research Hackaday

There are a lot of situations where a research group may turn to an electron microscope to get information about whatever system they might be studying. Assessing the structure of a virus or protein, analyzing the morphology of a new nanoparticle, or examining the layout of a semiconductor all might require the use of one of these devices. But if your research involves the electron microscope itself, you might be a little more reluctant to tear down these expensive devices to take a look behind the curtain as the costs to do this for more than a few could quickly get out of hand. Thats why this research group has created their own electron detector.
Specifically, the electron detector is designed for use in a scanning electron microscope, which is typically used for inspecting the surface of a sample and retrieving a high-resolution, 3D image of it compared to transmission microscopes which can probe internal structures. The detector is built on a four-layer PCB which includes the photodiode sensing array, a series of amplifiers, and a power supply. All of the circuit diagrams and schematics are available for inspection as well thanks to the design being licensed under the ope...
08:53
Massachusetts Lawmakers File Bill to Create 4-Day Workweek Pilot SoylentNews
Following a similar program in Europe, two Massachusetts lawmakers have filed a bill this week to create a two-year pilot program for a four-day workweek.
[...] The pilot program would run for two years and would be overseen by the Executive Office of Labor and Workforce Development. To participate, employers must agree to transition at least 15 workers to a shortened workweek.
While the bill was just filed this week, a number of businesses have already reached out to ask how they can participate, according to Cutler.
"I think this is really the perfect time for this kind of pilot program, given the changes we've seen in hybrid work as a result of the pandemic and the need to look for creative solutions to our current labor market challenges," Cutler said in an email response to Computerworld.
If the legislation passes, employers who participate in the pilot would agree to reduce the hours of all or some of their employees without reducing overall pay, status, or benefits. Businesses will also be eligible for a tax credit for their participation in the study and necessary data collection, Cutler said.
While the pilot program is designed to run for two years, individual businesses are not required to participate the entire time. The proposal is aimed at discovering the feasibility and benefits of a four-day work week.
"We chose this amount of time because we wanted to ensure a robust response and data availability. I have seen a variety of different lengths. In Maryland, there is a bill proposing a five-year pilot, for example. In this case, we felt two years struck a good balance," Cutler said. (The Maryland proposal was withdrawn earlier this year.)
The Massachusetts legislation doesn't call for participating organizations to adopt a strict 32-hour work week; instead, it states employees must receive "a meaningful reduction in actual work hours."
Read more of this story at SoylentNews.
08:04
A cyberattack on the Cornwall Community Hospital in Ontario is causing treatment delays Security Affairs
The Cornwall Community Hospital in Ontario, Canada, is under a cyber attack that is causing delays to scheduled and non-urgent care.
A cyberattack on the Cornwall Community Hospital in Ontario, Canada, is causing delays to scheduled and non-urgent care.
The cyber attack was discovered on Tuesday, April 11, 2023, it is investigating the incident with the help of cybersecurity experts.
On April 11, 2023, Cornwall Community Hospital (CCH) identified a network issue, which an investigation has revealed to be a cyber incident. The hospital has retained external cyber experts, working with our technical team to resolve the issue. reads a statement published by the hospital. Delivering exceptional patient-centered care is the hospitals top priority and CCH continues to provide high-quality clinical services. However, residents may experience some delays to scheduled or non-urgent care.
The hospital pointed out that its clinical Electronic Health Record has not been impacted by the cyber attack. The users were not able to access MyChart due to the ongoing attack.
The Cornwall Community Hospital has yet to provide details about the attack, but the problems it is facing suggest it has suffered a ransomware attack.
Unfortunately, hospitals are easy targets for ruthless cybercriminals, in early February, the Tallahassee Memorial HealthCare (TMH) hospital has taken its IT systems offline and suspended non-emergency procedures after a cyberattack.
Tallahassee Memorial HealthCare suspended emergency medical services (EMS), and it announced that patients will be diverted to other hospitals.
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections:
- The Teacher Most Educational Blog
- The Entertainer Most Entertaining Blog
- The Tech Whizz Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please nominate Security Affairs as your favorite blog.
Nominate here: https://docs.google.com/forms/d/e/1FAIpQLSfaFMkrMlrLhOBsRPKdv56Y4HgC88Bcji4V7OCxCm_OmyPoLw/viewform
Follow me on Twitter: ...
06:43
Comunicado de prensa para Latinoamrica: La propuesta de tratado de la ONU sobre ciberdelincuencia carece de suficientes salvaguardias de derechos humanos, lo que agrava las amenazas a la privacidad y las libertades civiles en Latinoamrica Deeplinks
VIENA-El martes 18 de abril, a las 10:00 am hora del Pacfico
(1:00 pm hora del Este), expertos de Electronic Frontier Foundation
(EFF) y tres aliados latinoamericanos de derechos digitales
informarn a los reporteros sobre las amenazas nicas a la privacidad
que plantea la propuesta de Tratado sobre
Delitos Cibernticos de la ONU, que podra autorizar el uso de
programas espa que ya se estn desplegando contra periodistas y
defensores de los derechos humanos.
El tratado, que ha sido objeto de negociaciones entre los Estados
miembros de la ONU durante un ao,
carece hasta ahora de compromisos firmes con los derechos
humanos y de condiciones y salvaguardias detalladas necesarias
para proteger los derechos de las personas y las organizaciones de
la regin.
La sesin informativa, de una hora de duracin, se retransmitir en
directo desde la
quinta sesin de negociaciones del tratado en Viena, donde
representantes de ms de 100 Estados miembros se renen para debatir
un proyecto de documento que servir de base para el tratado.
Expertos de la EFF, la Red en Defensa de los Derechos Digitales
(R3D), Derechos Digitales y la Fundacin Karisma hablarn de cmo el
borrador crea ms de 30
nuevos delitos cibernticos; nuevos procedimientos penales para
el intercambio transfronterizo de presuntas pruebas, incluidos los
datos privados de los usuarios; y mayores poderes de vigilancia
policial. Los Estados que firmen el tratado incorporarn estos
delitos y procedimientos a sus cdigos penales nacionales.
Sin las debidas salvaguardias de los derechos humanos en el
tratado, estas medidas son incompatibles con las normas
interamericanas de derechos humanos que refuerzan la libertad de
expresin, la privacidad y el debido proceso, lo que supone un
enorme revs para las libertades civiles en toda Amrica Latina.
Es ms, el tratado se est negociando mientras aumentan las pruebas
de que programas espa como Pegasus y el pirateo gubernamental se
han utilizado contra grupos vulnerables,
periodistas y
act...
06:28
Russian Registry Revokes TorrentGalaxys Domain Name for Unknown Reasons TorrentFreak
 The
Soviet Union was dissolved more than thirty years ago, but the
former transcontinental state still has its own .su TLD.
The
Soviet Union was dissolved more than thirty years ago, but the
former transcontinental state still has its own .su TLD.
The .su domain extension isnt exactly mainstream. There are a little over 100,000 active domains, with .su extensions reportedly proving popular among cybercriminals.
Experts have cited outdated terms and a lack of enforcement as historical reasons for the cybercrime appeal. However, recent actions show that the Russian Institute for Public Networks, which maintains the .su domain, can certainly intervene.
TorrentGalaxy Loses Control over .SU Domain
A few days ago popular torrent site TorrentGalaxy lost control of its .su domain name. The domain stopped resolving out of the blue and upon closer inspection, was found to be no longer delegated.
Whois research confirms that the domains status is listed as REGISTERED, NOT DELEGATED, without providing any further detail.
TorrentGalaxy informs TorrentFreak that its Russian registrar R01 hasnt sent any information about the issue and all questions remain unanswered. The torrent site hasnt heard anything from the Russian Institute for Public Networks, the .su registry, either.
We havent gotten any notification of the disconnection. It still shows as active on our side. In fact, the weird EPP status on the domain whois and the domain not resolving to anything have been the only info for us as well, the operator explains.
TorrentFreak reached out to both the registry and registrar but we havent heard back. This means that the exact reason for the domain revocation remains unknown.
Government Connection
Since the DNS zone was effectively removed, it appears that the registry intervened. This can happen for a variety of reasons, including court orders, voluntary actions, or Government instructions.
Russia already requires Internet providers and search engines to block hundreds of thousand...
06:27
Why is Juice Jacking Suddenly Back in the News? Krebs on Security

KrebsOnSecurity received a nice bump in traffic this week thanks to tweets from the Federal Bureau of Investigation (FBI) and the Federal Communications Commission (FCC) about juice jacking, a term first coined here in 2011 to describe a potential threat of data theft when one plugs their mobile device into a public charging kiosk. It remains unclear what may have prompted the alerts, but the good news is that there are some fairly basic things you can do to avoid having to worry about juice jacking.
On April 6, 2023, the FBIs Denver office issued a warning about juice jacking in a tweet.
Avoid using free charging stations in airports, hotels or shopping centers, the FBIs Denver office warned. Bad actors have figured out ways to use public USB ports to introduce malware and monitoring software onto devices. Carry your own charger and USB cord and use an electrical outlet instead.
Five days later, the Federal Communications Commission (FCC) issued a similar warning. Think twice before using public charging stations, the FCC tweeted. Hackers could be waiting to gain access to your personal information by installing malware and monitoring software to your devices. This scam is referred to as juice jacking.
The FCC tweet also provided a link to the agencys awareness page on juice jacking, which was originally published in advance of the Thanksgiving Holiday in 2019 but was updated in 2021 and then again shortly after the FBIs tweet was picked up by the news media. The alerts were so broadly and breathlessly covered in the press that a mention of juice jacking even made it into this weeks Late Late Show with James Corden.
The term juice jacking crept into the collective paranoia of gadget geeks in the summer of 2011, thanks to the headline for a story here about researchers at the DEFCON hacker convention in Vegas whod set up a mobile charging station designed to educate the unwary to the reality that many mobile devices connected to a computer would sync their data by default.
Since then, Apple, Google and other mobile device makers have c...
06:22
Wine 8.6 Released With Bundled Musl Libc Math Library Phoronix
Wine 8.6 is out as the newest bi-weekly development release of this open-source software to enjoy Windows games and applications on Linux and other platforms...
06:12
Study Finds Only One Type of Consumer Dictates Price SoylentNews
Researchers compare multiple categories of shoppers and find the linchpin:
It's commonly assumed that the supply-and-demand economics of the consumer marketplace dictates price. If you are one of few retailers that sells a product consumers want, you can charge more. Or, if supplies of that product are more scarce, again, prices will likely be higher. On the flip side, if supplies are plentiful for a product that is in less demand, prices for that product are likely to be lower.
But researchers have found it's not always that simple. Thanks to the internet and e-commerce, more consumers have taken advantage of going to a physical store to inspect items before purchase, leaving that store, and then purchasing the product at a lower price elsewhere. This is called "showrooming."
This has led to several assumptions in the retail industry, from the thought that showrooming will put brick-and-mortar retailers out of business, to the notion that the showrooming trend has driven prices down across the board. A new study has found these may both be false.
[...] "Showroomers do their research in advance," says Bar-Isaac. "They know what they want, they already know what that retailer may charge, and they go to stores with more limited or shallow selections in search of a better price."
Read more of this story at SoylentNews.
06:00
Fail of the Week: Car Starter Motors Arent the Best Fit for eBikes Hackaday

A lot of what real engineering is all about is designing to the limits of your materials, with a healthy margin for error. On the other hand, seat-of-the-pants engineering often takes the opposite tack working with the materials you have and finding their limits after the fact. While the former is more rigorous and better suited to anything where life and limb are on the line, theres something to be said for the flexibility that informal engineering offers.
[Austin Blake]s latest eBike is a case study in informal engineering. [Austin] started out wondering if a starter motor from a car engine would make a decent electric bike motor. Our first instinct before watching the video below was to answer that question with a resounding No! Yes, starter motors seem like a natural for the job, delivering high torque in a compact package. But starting a car engine is the very definition of a low-duty-cycle application, since it should only take a second or two of cranking to get an engine started. Pressing a motor designed for such a task into continuous duty seems like, well, a non-starter.
And to be fair, [Austin] fully ack...
05:50
Google fixed the first Chrome zero-day of 2023 Security Affairs
Google released an emergency security update to address a zero-day vulnerability in Chrome which is actively exploited in the wild.
Google released an emergency security update to address the first Chrome zero-day vulnerability (CVE-2023-2033) in 2023, the company is aware of attacks in the wild exploiting the issue.
The vulnerability is a Type Confusion issue that resides in the JavaScript engine V8. The vulnerability was reported by Clment Lecigne of Googles Threat Analysis Group on 2023-04-11.
Type Confusion in V8. Reported by Clment Lecigne of Googles Threat Analysis Group on 2023-04-11 reads the advisory published by Google. Google is aware that an exploit for CVE-2023-2033 exists in the wild.
channel, this means that it will be available to the entire user base over the coming days or weeks.The Stable and extended stable channel has been updated to 112.0.5615.121 for Windows Mac and Linux which will roll out over the coming days/weeks. continues the advisory
Google did not disclose details of the attacks exploiting this vulnerability, it will not provide bug details and links until a majority of users will have updated their installs.
Access to bug details and links may be kept restricted until a majority of users are updated with a fix. We will also retain restrictions if the bug exists in a third party library that other projects similarly depend on, but havent yet fixed. concludes the advisory.
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections:
- The Teacher Most Educational Blog
- The Entertainer Most Entertaining Blog
- The Tech Whizz Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please nominate Security Affairs as your favorite blog.
Nominate here: https://docs.google.com/forms/d/e/1FAIpQLSfaFMkrMlrLhOBsRPKdv56Y4HgC88Bcji4V7OCxCm_OmyPoLw/viewform
Follow me on Twitter: @securityaffairs and ...
05:48
EFF, International Allies Warn That Proposed UN Cybercrime Treaty, Rather Than Making Us More Secure, Could Legitimize Intrusive Surveillance and Drag Down Global Privacy and Free Expression Standards Deeplinks
EFF and international allies Access Now, Article 19,
Epicenter, and Global Partners Digital are in Vienna this week and
next for the fifth round of negotiations on the proposed UN
Cybercrime Treaty, along with the over 100 representatives of
Member States hashing out a new draft text.
While we have not yet been allowed to speak on the flooror even sit
in the same room as delegatesthat has not stopped us from speaking
out for users about the lack of human rights protections, the
criminalization of online speech, the fostering of greater
surveillance powers, and other dangers posed by the treaty in its
current form.
At a livestreamed briefing yesterday in Vienna, we provided a
reality check on how the talks have moved in troubling directions
and challenged negotiators to seize this rare
opportunitynegotiating a UN Treaty only happens every other
decadeto draft a cybercrime treaty that does not undermine, but
actually protects, privacy and free expression.
You can view the media briefing here:
https://www.youtube.com/watch?v=POwrbFrJADU
Briefing highlights:
Katitza Rodriguez, Policy Director for Global
Privacy, EFF
One big issue we're facing is that there isn't an effective global system in place to make sure human rights are enforced. Not many governments want to limit their own power to spy and track people closely. Because of this, the Convention might end up legitimizing intrusive surveillance power that invades people's private lives and infringe upon their rights.
Barbora Bukovsk, Senior Director for Law and Policy, ARTICLE 19
We are really concerned that many provisions of this treaty restrict freedom of expression. States must not lose sight of the fact that content offenses, if coupled with surveillance powers and other restrictions, will create international carte blanche for those who want to use use this tool to restrict freedom of expression globally.
Raman Jit Singh Chima, Senior International Counsel and Global Cybersecurity Lead, Access Now
Our view is simple. Any UN cybercrime treaty should make us more cyber secure, it should not make us less less cyber secure. A key part of any such international legal framework should look at the human beings involved in cyber security, namely security researchers, digital security trainers, as well as journalists who investigate vulnerabilities and ga...
05:46
Re: ncurses fixes upstream Open Source Security
Posted by Tavis Ormandy on Apr 14
I'm curious what the attack is! ISTR that terminfo definitions cancontain shell commands by design and so are generally considered
trusted.
I remember using this trick in an exploit once :)
$ printf "exploit, iprog=/usr/bin/id,\n" | tic -
$ TERM=exploit reset
uid=1000(taviso) gid=1000(taviso)
Tavis.
05:04
Standard Life Investigated Sirius Pension Fraud Without Even Collecting Any Evidence or Contacting Sirius schestowitz.com
Video
download link | md5sum
e02b55eac9a1d3690b44015080f5f9c2
So-called Pension Investigation
Creative Commons Attribution-No Derivative Works 4.0
Summary: The crimes of Sirius Corporation were discussed with Standard Life several times this week; Standard Life workers are evasive and theyre belittling the matter as they try to wash their hands of us despite partial culpability (legitimising the fraud, not protecting their reputation)
THE VIDEO above is a tad long, so processing took a long time and since then weve found out that the French court approves Macrons unpopular plan to raise pension age; the English-speaking media in France calls it a deeply unpopular pensions overhaul, taking note of three months of strikes and mass protests. Of course due to the publicity/media sophistry, Macron will be mentioned in relation to other things. A lot of the media will go on and on about Macron and Taiwan, not his ongoing attacks on millions of people in his own country.
Regardless of what happened in France some hours ago, the video above explains our own ordeals at Sirius Open Source, a company which basically robbed its own staff under the guise of pension (which never existed). To make matters far worse, a very large pension provider (one of the largest in the UK) is trying to cover things up. I confronted them about contradictory messages, including some from managers. Well, they see something that says 2016 and n...
04:43
Standard Life Tacitly Admits Doing a Sham Investigation Without Bothering to Contact Sirius, Customer Relations Confesses That Manager Lied About Key Dates (Years) Several Times Techrights
Video
download link | md5sum
e02b55eac9a1d3690b44015080f5f9c2
So-called Pension Investigation
Creative Commons Attribution-No Derivative Works 4.0
Summary: The crimes of Sirius Corporation were discussed with Standard Life several times this week; Standard Life workers are evasive and theyre belittling the matter as they try to wash their hands of us despite partial culpability (legitimising the fraud, not protecting their reputation)
THE VIDEO above is a tad long, so processing took a long time and since then weve found out that the French court approves Macrons unpopular plan to raise pension age; the English-speaking media in France calls it a deeply unpopular pensions overhaul, taking note of three months of strikes and mass protests. Of course due to the publicity/media sophistry, Macron will be mentioned in relation to other things. A lot of the media will go on and on about Macron and Taiwan, not his ongoing attacks on millions of people in his own country.
The short story is, theyre protecting themselves and the perpetrators that paid them (to help scam a lot...
04:32
Links 14/04/2023: Godot 3.6 Reaches Beta, OSI Celebrates Proprietary Money Techrights
![]()
Contents
-
GNU/Linux
-
Audiocasts/Shows
-
A new Era on Linux Has Dawned, Teaser 6
Enjoy our latest Teaser of our upcoming Max release
-
-
Instructionals/Technical
-
How do I Install & Uninstall MySQL in Linux?
MySQL is one of the most famous relational database management systems in the current market. The capabilities of this RDBMS are not only amazing but also quite user-friendly. Many people prefer MySQL over other alternatives available in the market. Often, installing MySQL and removing it from a Linux-based operating system can be quite daunting for new beginners. If that is the case, then this post will be your friend and guide you through the process. Lets Begin.
-
Top Tips for Optimizing Kali Linux After Installation
...
-
-
04:30
Intel Lands Linux Audio Fix For Arc Graphics A750/A770 Phoronix
If you have been running a Linux 6.3-based kernel or later Linux 6.2 point release and have encountered your HDMI audio breaking when making use of Intel Arc Graphics A750/A770 hardware, a fix is on the way...
04:15
Latam Media Briefing: Proposed UN Cybercrime Treaty Lacks Sufficient Human Rights Safeguards, Exacerbating Threats to Privacy and Civil Liberties in Latam Deeplinks
VIENNAOn Tuesday, April 18, at 10:00 am Pacific Time (1:00
pm Eastern Time), experts from Electronic Frontier Foundation (EFF)
and three Latin American digital rights allies will brief reporters
about the unique threats to privacy posed by the proposed UN Cybercrime
Treaty, which could authorize the use of spyware
already being deployed against journalists and human rights
defenders.
The treaty, which has been the subject of negotiations among UN
Member States for a year, so far
lacks strong commitments to human rights and detailed
conditions and safeguards needed to protect the rights of
individuals and organizations in the region.
The one-hour briefing will be livestreamed from the
fifth session of treaty negotiations in Vienna,
where representatives from over 100 Member States are meeting
to discuss a draft document that will serve as a basis for the
treaty.
Experts from EFF, Network in Defense of Digital Rights (R3D),
Derechos Digitales, and Fundacion Karisma will discuss how the
draft creates over 30
new cybercrime offenses; new criminal procedures for
cross-border sharing of alleged evidence, including private user
data; and increased police surveillance powers. States that sign on
to the treaty would adopt these offenses and procedures into their
national criminal codes.
Without appropriate human rights safeguards written into the
treaty, these measures are incompatible with Inter-American human
rights standards reinforcing freedom of expression, privacy, and
due process, dealing an enormous setback for civil liberties across
Latin America.
Whats more, the treaty is being negotiated as evidence mounts that
spyware like Pegasus and government hacking have been used against
vulnerable groups,
journalists, and...
03:27
Elon Musk Admits He Only Bought Twitter Because He Thought He'd be Forced to SoylentNews
Elon Musk admits he only bought Twitter because he thought he'd be forced to:
Elon Musk gave a rare interview to an actual reporter late on Tuesday, speaking to BBC reporter James Clayton on Twitter Spaces. During the interview, Clayton pressed Musk on whether his purchase of Twitter was, in the end, something he went through with willingly, or whether it was something he did because the active court case at the time in which Twitter was trying to force him to go through with the sale was going badly.
The answer (which we all suspected anyway) was that Musk did indeed only do the deal because he believed legally, he was going to be forced to do so anyway. Here's the relevant transcript from the Twitter Spaces audio:
Clayton: So then you change your mind again, and decided to buy it did you do that? Did you do that?
Musk: Well, I kind of had to.
Clayton: Right. Did you do that, because you thought that a court would make you do that?
Musk: Yes.
Clayton: Right.
Musk: Yes, that is the reason.
Clayton: So you were still trying to get out of it. And then you just were advised by lawyers, "Look, you're going to buy this?"
Musk: Yes.
In case you don't recall (it was all the way back in September/October last year which is basically an eternity ago in current Twitter time), Twitter took Musk to trial to force him to honor his signed obligation to acquire the company for the agreed-upon price of $44 billion, or $54.20 per share. Musk was contending that his obligation was void because Twitter had, he claimed, inflated its real user numbers and understated the number of bots on the platform.
Musk then notified the SEC that he intended to buy the company after all at the price he originally set with the company, a move most agreed at the time was made because his legal case was weak and the trial was clearly not going his way.
Read more of this story at SoylentNews.
03:02
Naomi Wolf: Whats in the Pfizer Documents? cryptogon.com
The Pfizer documents contain evidence of the greatest crime against humanity in the history of our species. Via: Hillsdale College:
02:00
Video Friday: Ingenuitys 50th Flight IEEE Spectrum

Video Friday is your weekly selection of awesome robotics
videos, collected by your friends at IEEE Spectrum
robotics. We also post a weekly calendar of upcoming robotics
events for the next few months. Please
send us your events for inclusion.
Robotics Summit & Expo: 1011 May 2023, BOSTON
ICRA 2023: 29 May2 June 2023, LONDON
RoboCup 2023: 410 July 2023, BORDEAUX, FRANCE
RSS 2023: 1014 July 2023, DAEGU, KOREA
IEEE RO-MAN 2023: 2831 August 2023, BUSAN, KOREA
CLAWAR 2023: 24 October 2023, FLORIANOPOLIS, BRAZIL
Humanoids 2023: 1214 December 2023, AUSTIN, TEXAS, USA
Enjoy todays videos!
NASAs Ingenuity Mars Helicopter made history when it achieved the first powered, controlled flight on another planet on April 19, 2021. Since then, it has exceeded expectations and most recently executed its 50th flight on Mars. This video highlights Ingenuitys flights, captured by the Perseverance Rovers WATSON and Mastcam-Z cameras, as well as Ingenuitys color Return to Earth (RTE) camera and its black-and-white navigation camera.
50 flights is 45 flights more than this little helicopter was designed for, which is bonkers. It has exceeded the expected cumulative flight time by 1,250%, and the expected distance flown by 2,214%. Wow.
[ JPL ]
Georgia Tech researchers have recently created a soft rotary motor using liquid metal, compliant magnetic composites, and silicone polymers. The motor can be squished and squeezed in all directions, which can one day improve the compatibility between humans and robots and extend the capability of soft robots. This soft motor is orders of m...
Friday, 14 April
19:10
888 On Line Casino Evaluate 2023 Get $88 No Deposit In India h+ Media
888 On Line Casino Evaluate 2023 Get $88 No Deposit In India
Enter all the required data, including your e mail handle, country, most well-liked billing foreign money, and password. To entry your account on the original website, click on the Sign in 4RaBet button in the top-right corner of the web page. Type in your e mail and password and click on on Sign in once more. In case you forgot the password or login, 4ra Bet has the Recover a password option. After youve completed the registration process at 4raBet, confirm your account with a hyperlink in your e-mail or SMS.
VSG or Vikram Singh Gandhi is a cricket tipper, commonly often identified as Dada. After clicking on which you have to enter your quantity and click on on on Withdraw choice to withdraw money. You need to substantiate your e-mail or cellphone quantity through a link despatched to your e-mail handle or SMS. The bookie additionally could require proof of your identity, fee info, and address by offering a duplicate of your ID document, a utility bill, and a photograph of your bank card.
888casino is a kind of on-line gambling institutions which are lifeless serious about the security and safety of gamblers. Yeah, thats how one can primarily reach the customer assist team at 888casino. Send them a mail at , and they will revert within hours. You could even place particular bets on who wins the US presidential elections or receives an Academy award!
It is the most challenging betting option because the consumer simultaneously implies a forecast and probabilities on a quantity of outcomes. It isnt really helpful to cooperate with suspicious unlicensed websites, as theres a high probability of fraud. The 4rabet verification procedure takes from 24 to 72 hours. If the profile verification is refused, the website administration blocks the account, taking the replenished deposit or winnings within the companys favor. At this stage, you must select the sum of money you wish to spend on bets by way of the most effective betting app.
888sport, a member of ESSA, the European betting integrity body, is a trusted bookmaker. Under the 888 Group, a sportsbook is on the market as 888sport. However, this is the companys dedicated sports arm, which is not part of the 888casino web site. So, the casinos portfolio now features a live game for each temper.
You can benefit from the 888 video games in instant-play mode or download the software. All merchandise embody Random Number Generator techniques, which assure fairness across the complete platform. Also, the software program providers ensure high-end safety methods, which assure a protected and safe playing setting for Indian customers.
If youve the time to go looking through 888s assist and FAQ pages, youll probably discover your query already answered. However, web sites similar to Betfair and Royal Panda have live chat companies which might be extra r...
19:06
Uks William Hill Fined $24 Million For Widespread Gambling Failures h+ Media
Uks William Hill Fined $24 Million For Widespread Gambling Failures
Replenish your deposit in cryptocurrency and get a big bonus of 100% up to 24,000 INR. The promo applies to the second and subsequent deposits made in cryptocurrency . For on line casino gamers there are 5 ranges of loyalty, whereas sports activities players have 7. Cashback is credited to the bonus balance with a wagering rule. If a sports player has the 4th and higher stage of loyalty, he receives a cash again on an actual stability.
The casino further has a particular take a look at for self-assessment for downside avid gamers. If you register with 888casino, you must have the power to entry 888sport with out If you dont log in to your account for 90 days, your Comp Points and Bonus Points shall be forfeited.
All the withdrawal requests are reviewed and verified within 24 hours. Please note that you would be be required to produce further documentation upon requesting a withdrawal, but this is not all the time the case. 888Casino additionally has many Indian-preferred deposit and withdrawal strategies, however they dont assist deposits in Indian Rupees yet.
For those that want to chase their jackpot goals, 888casino is the perfect place to begin. Regarding progressive jackpot slots, the casino offers various in-house games and those supplied by top iGaming software developers! Players can choose from a spread of traditional and video slotmachines with big jackpots. The gaming right here is classy, from software to choices, everything you could want from a games perspective, 888 Casino is in a position to provide. You can also enjoy watching stay IPL video games and guess on them if you wish to make essentially the most of the worldwide cricket thats played.
Mobile applications deliver many advantages corresponding to ease of use, spooky family slot machine together with the tumbling reels characteristic and the big multipliers which keep on growing. In 2010 the Payment Act was handed by the Norwegian authorities, New York online casinos and New York on-line betting nonetheless doesnt exist. La slot machine Druids Dream prevede inoltre due diversi simboli speciali, slots with out registration virtual cash but its not unlawful to play. The top-rated apps for smartphones supply a fairly big number of choices for depositing and withdrawing funds.
For the safety and safety of all players, in some circumstances, 888 Casino India could contact you to ask the place your money is coming from if it suspects legal activity. 888 Casino is certified by eCOGRA, an internationally-approved testing company based mostly in London that units out to protect players from foul play. You can discover eCOGRA reports on 888casino.com, which is why it scores highly on our trust score. If you wish to withdraw your money on this app, then you possibly can transfer y...
Uks William Hill Fined $24 Million For Widespread Gambling Failures h+ Media
Uks William Hill Fined $24 Million For Widespread Gambling Failures
Replenish your deposit in cryptocurrency and get a big bonus of 100% up to 24,000 INR. The promo applies to the second and subsequent deposits made in cryptocurrency . For on line casino gamers there are 5 ranges of loyalty, whereas sports activities players have 7. Cashback is credited to the bonus balance with a wagering rule. If a sports player has the 4th and higher stage of loyalty, he receives a cash again on an actual stability.
The casino further has a particular take a look at for self-assessment for downside avid gamers. If you register with 888casino, you must have the power to entry 888sport with out If you dont log in to your account for 90 days, your Comp Points and Bonus Points shall be forfeited.
All the withdrawal requests are reviewed and verified within 24 hours. Please note that you would be be required to produce further documentation upon requesting a withdrawal, but this is not all the time the case. 888Casino additionally has many Indian-preferred deposit and withdrawal strategies, however they dont assist deposits in Indian Rupees yet.
For those that want to chase their jackpot goals, 888casino is the perfect place to begin. Regarding progressive jackpot slots, the casino offers various in-house games and those supplied by top iGaming software developers! Players can choose from a spread of traditional and video slotmachines with big jackpots. The gaming right here is classy, from software to choices, everything you could want from a games perspective, 888 Casino is in a position to provide. You can also enjoy watching stay IPL video games and guess on them if you wish to make essentially the most of the worldwide cricket thats played.
Mobile applications deliver many advantages corresponding to ease of use, spooky family slot machine together with the tumbling reels characteristic and the big multipliers which keep on growing. In 2010 the Payment Act was handed by the Norwegian authorities, New York online casinos and New York on-line betting nonetheless doesnt exist. La slot machine Druids Dream prevede inoltre due diversi simboli speciali, slots with out registration virtual cash but its not unlawful to play. The top-rated apps for smartphones supply a fairly big number of choices for depositing and withdrawing funds.
For the safety and safety of all players, in some circumstances, 888 Casino India could contact you to ask the place your money is coming from if it suspects legal activity. 888 Casino is certified by eCOGRA, an internationally-approved testing company based mostly in London that units out to protect players from foul play. You can discover eCOGRA reports on 888casino.com, which is why it scores highly on our trust score. If you wish to withdraw your money on this app, then you possibly can transfer y...
19:03
Search Outcomes For pocket Sport Developer Apk Openak319com 888 On Line Casino Login 1xbet Withdraw Disadvantage Openak319com$$limitadong Regalo!mag Register Para Makakuha Ng P50 May 50% Cashback Sayong Unang Deposit!$$c2 h+ Media
Search Outcomes For pocket Sport Developer Apk Openak319com 888 On Line Casino Login 1xbet Withdraw Disadvantage Openak319com$$limitadong Regalo!mag Register Para Makakuha Ng P50 May 50% Cashback Sayong Unang Deposit!$$c2
If you are a beginner within the betting sphere, take a look at one of the best Indian betting apps which will be nice so that you can use as a end result of their easy interface and navigation. Given numerous bookmakers in the marketplace, it isnt simple to choose on an indeed secure and reliable cell app. The bonus will be credited to the customers account mechanically after the first deposit is made, unless the field I are not wanting for any bonuses is ticked. Only gamers that are new to Parimatch can qualify for this promotion. Been writing sports activities information for a couple of years and now developing my own sports activities and betting website with honest and skilled critiques.
There are about 30 progressive slot games on the 888 on line casino platform. That is, with a bit of stake, you could be fortunate to be a winner of a large amount of cash. Mind you, the progressive slot enhance in potential payout as players and betting will increase. A simplified and easy-to-use platform plus good graphics are notable options of the positioning. In addition, it has a vast game base that units gamers up for an explosive ride when exploring the games. Notable software builders across the globe provide some of the video games within the casino.
However, this can be longer depending on whether any malicious activity is suspected. In-house casino gaming offers a sure thrill that virtually all players find addictive. 888 Casino brings this thrill to all gamers from the comfort of their properties or when chilling on a park bench. The website has an interactive live dealer part that packs all the superb qualities of an in-house casino blended with know-how to end in a high-quality video stream. 888 Casino was among the many first gaming providers on-line to have this section put up on their web site. In the preceding years, the operator has been a mannequin for a lot of others in the trade that adopted suit.
The present-day 888.com proudly carries the Safe and Fair Assurance seal from eCOGRA. In 2010, Casino-on-Net was rebranded as 888casino to unite it with the opposite 888 brands. In 2013, in a historic moment, this on-line casino turned the primary to be exclusively licensed within the United States under the Nevada Gaming Commission.
Access games, deposit/withdrawal options, buyer help, and other features from the app. It works around the clock and has qualified help for gamers utilizing a chat within the app. I was pleased to find a big variety of online on line casino games at 888 of the completely different segments. The slot video games are a couple of hundred; even when its not as much as found in different portal...
















