| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Sunday, 19 March
01:00
Study Hacker History, and Update It Hackaday

Looking through past hacks is a great source of inspiration. This week, we saw [Russ Maschmeyer] re-visiting a classic hack by [Jonny Lee] that made use of a Wiimotes IR camera to fake 3D, or at least provide a compelling parallax effect thatll fool your brain, without any expensive custom hardware.
00:53
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Eric Ashley on Mar 18
According to a note from kernel maintenance(https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?h=v6.3-rc2&id=1e641743f055f075ed9a4edd75f1fb1e05669ddc),
as of 2008 only Heirloom mailx (a.k.a. nail) used it for ~h interactive header editing.
Best regards,
Eric
Sent with Proton Mail secure email.
------- Original Message -------
00:36
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Christos Zoulas on Mar 18
I think that the original reason was for csh(1) to implement file completion:https://nxr.netbsd.org/xref/src/bin/csh/file.c#161
I still have a use case for it. Sometimes I lose my VPN tunnel and an
ssh session where I am running vi(1) suddenly dies. When I ssh to that
machine, I can easily find the tty where the vi session is with ps(1) and
then type "sti pts/X :wq\\n" and save the file (https://man.netbsd.org/sti.8):-)
Of course on...
00:22
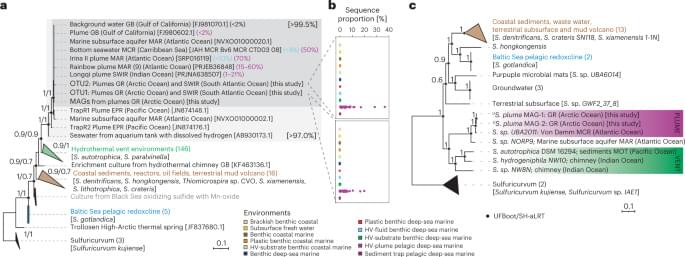
A hydrogenotrophic Sulfurimonas is globally abundant in deep-sea oxygen-saturated hydrothermal plumes Microbiology Lifeboat News: The Blog
An uncultivated, aerobic chemolithotrophic Sulfurimonas species with a reduced genome is abundant across diverse, hydrogen-rich hydrothermal plumes in the deep ocean.
Saturday, 18 March
23:17
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Lyndon Nerenberg (VE7TFX/VE6BBM) on Mar 18
Does anyone even remember why TIOCSTI was added in thefirst place? I remember stumbling across it decades
ago (SVR?), but I've ever seen a use case for it.
It puzzled me back then why it even existed.
--lyndon
22:30
Chinese Hackers Exploit Fortinet Zero-Day Flaw for Cyber Espionage Attack The Hacker News
The zero-day exploitation of a now-patched medium-severity security flaw in the Fortinet FortiOS operating system has been linked to a suspected Chinese hacking group. Threat intelligence firm Mandiant, which made the attribution, said the activity cluster is part of a broader campaign designed to deploy backdoors onto Fortinet and VMware solutions and maintain persistent access to victim
22:26
-current has moved to 7.3, ports commits restricted pending release OpenBSD Journal
With the following commit,
Theo de Raadt (deraadt@) moved -current to version
7.3:
CVSROOT: /cvs
Module name: src
Changes by: deraadt@cvs.openbsd.org 2023/03/17 16:52:22
Modified files:
sys/conf : newvers.sh
Log message:
remove -beta tag
For those unfamiliar with the process: this is not the 7.3 release, but is part of the standard build-up to the release.
22:10
Feds arrested Pompompurin, the alleged owner of BreachForums Security Affairs
U.S. law enforcement arrested this week a US citizen suspected to be Pompompurin, the notorious owner of the BreachForums cybercrime forum.
U.S. law enforcement arrested this week a US man that goes online with the moniker Pompompurin, the US citizen is accused to be the owner of the popular hacking forum BreachForums.
The news of the arrest was first reported by Bloomberg, which reported that federal agents arrested Conor Brian Fitzpatrick from Peekskill, New York.
The man was arrested by the feds at his home around 4:30 p.m. Wednesday.
Federal agents have arrested a Peekskill, New York, man they say ran the notorious dark web data-breach site BreachForums under the name Pompompurin. reads the post published by Bloomberg. Conor Brian Fitzpatrick was arrested by a team of investigators at his home around 4:30 p.m. Wednesday, an FBI agent said in a sworn statement filed in court the next day. Fitzpatrick is charged with a single count of conspiracy to commit access device fraud.
In an affidavit filed with the District Court for the Southern District of New York, FBI Special Agent John Langmire said that at around 4:30 p.m. on March 15, 2023, he led a team of that made a probable cause arrest of Conor Brian Fitzpatrick in Peekskill, NY.
When I arrested the defendant on March 15, 2023, he stated to me in substance and in part that: a) his name was Conor Brian Fitzpatrick; b) he used the alias pompompurin/ and c) he was the owner and administrator of BreachForums the data breach website referenced in the Complaint, Langmire wrote.
According to the Westchester News12 website, the agents spent hours inside and outside of the suspects home, they were seen removing several bags of evidence from the house.
The man has been charged with soliciting individuals with the purpose of selling unauthorized access devices.
Fitzpatrick was released on a $300,000 bond signed by his parents, he is scheduled to appear before the District Court for the Eastern District of Virginia on March 24, 2023.
The defendant must: submit to supervision by and rep...
22:00
Meet the New Moteus BLDC Controller Board, the N1 Hackaday

[Josh] over at mjbots just released a moteus-n1. One change is that the volume and footprint size has been reduced. Considering many people, [Josh] included, use these controllers to operate robotic dogs, smaller is better. The previous moteus controller maxed out at 44 V, but the n1 can run at up to 54 V, allowing use of 48 V power supplies. And [Josh] improved the interface circuitry, making it much more flexible than before. This comes at an increased price, but he sells both versions parts availability permitting. And like the previous versions of the moteus controller, this is an open source project and youre free to build it yourself. You can check out the complete design package at the projects GitHub repository.
One helpful point is that the firmware for the n1 is the same, it simply enables new features related to the I/O ports. This means a user could swap in a new controller with no impact to their system. Maintaining firmware compatibility was just one of the challenges [Josh] faced along the way. Squeezing addit...
21:52
Linux 6.4 AMD Graphics Driver Picking Up New Power Features For The Steam Deck Phoronix
A pull request of early AMDGPU kernel graphics driver changes was submitted for DRM-Next on Friday as some of the early feature work accumulating for the Linux 6.4 kernel cycle...
21:24
LLVM 16.0 Released With New Intel/AMD CPU Support, More C++20 / C2X Features Phoronix
LLVM 16 was released on Friday night as the latest half-year feature release to this open-source compiler stack. From initial AMD Zen 4 support to bringing up new Intel CPU instruction sets and processor targets for their new processors being introduced through 2024, there is a lot of exciting hardware additions in LLVM 16.0. LLVM 16.0 is also notable for faster LLD linking, Zstd compressed debug sections, stabilizing of its LoongArch target, defaulting to C++17 for Clang, and much more. Here's a look at all the exciting changes of LLVM 16...
21:12
National Academies: We Cant Define Race, So Stop Using It in Science SoylentNews
For genetics, use scientifically relevant descriptions, not outdated social ideas:
With the advent of genomic studies, it's become ever more clear that humanity's genetic history is one of churn. Populations migrated, intermingled, and fragmented wherever they went, leaving us with a tangled genetic legacy that we often struggle to understand. The environmentin the form of disease, diet, and technologyalso played a critical role in shaping populations.
But this understanding is frequently at odds with the popular understanding, which often views genetics as a determinative factor and, far too often, interprets genetics in terms of race. Worse still, even though race cannot be defined or quantified scientifically, popular thinking creeps back into scientific thought, shaping the sort of research we do and how we interpret the results.
Those are some of the conclusions of a new report produced by the National Academies of Science. Done at the request of the National Institutes of Health (NIH), the report calls for scientists and the agencies that fund them to stop thinking of genetics in terms of race, and instead to focus on things that can be determined scientifically.
The report is long overdue. Genetics data has revealed that the popular understanding of race, developed during a time when white supremacy was widely accepted, simply doesn't make any sense. In the popular view, for instance, "Black" represents a single, homogenous group. But genomic data makes clear that populations in Sub-Saharan Africa are the most genetically diverse on Earth.
And, like everywhere else, populations in this region haven't stayed static. While some groups remained isolated from each other, the vast Bantu expansion touched most of the continent. Along the coast of East Africa, the history of interchange with Mideastern traders can be detected in many groups. There's also a tendency to treat African Americans as being equivalent to African, when the former population carries the legacy of genetic mixing with European populationsoften not by choice.
Similar things are true for every population we have looked at, no matter where on the globe they reside. Treating any of these populations as a monolithic, uniform groupas a race, in other wordsmakes no scientific sense.
20:53
KDE Delivers More Wayland Fixes & Plasma 6.0 Changes This Week Phoronix
KDE developer Nate Graham is out with his usual weekly development summary that highlights all of the interesting desktop changes made over the course of the past seven days. This week he particularly calls out more Wayland fixes -- a common occurrence in the KDE camp...
20:46
Links 18/03/2023: Docker is Deleting Free Software Organisations Techrights
![]()
Contents
-
GNU/Linux
-
Desktop/Laptop
-
Veikk Voila L Pen Tablet review: budget drawing tablet is an attractive choice [Ed: GNU/Linux compatible]
The Veikk Voila L Pen Tablet from new kids on the block Veikk is a versatile, affordable drawing tablet thats worth buying even if for only occasional use. It comes in cheaper than its rival the Huion Inspiroy Ink H320 and its rugged and simple design and inbuilt dial make it very simple to use out of the box. Its supplied with different adaptors, allowing it to plug into phones, tablets and laptops and its pressure sensitivity is brilliant, especially for a sub-$50 tablet.
-
-
Server
-
Container Journal ...
-
-
20:13
19:10
IRC Proceedings: Friday, March 17, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-170323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-170323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-170323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-170323.gmi
Over HTTP:
|
... |
19:00
Joseph Takahashi joins our Neuroscience Board. Lifeboat News
Joseph Takahashi joins our Neuroscience Board.
Joe holds the Loyd B. Sands Distinguished Chair in Neuroscience and is Professor and Chair of the Department of Neuroscience at the University of Texas Southwestern Medical Center. He is also Investigator at the Howard Hughes Medical Institute.19:00
DOOM Ported to a Single LEGO Brick Hackaday

By now youve all seen the tiny LEGO brick with a working screen in it. The work of one [James Ancient Brown], it was truly a masterpiece of miniaturization and creativity. Since then, [James] hasnt stopped innovating. Now, hes "https://www.youtube.com/watch?v=o76U0JPrMFk" target= "_blank">running on a single plastic brick.
Weve covered the construction of these astounding screen bricks before. Long story short, [James] designed a tiny PCB that hosts an RP2040 microcontroller which is then hooked up to a tiny OLED screen. The components are placed in a silicone mold, which is then filled with transparent resin to form the brick. The screen is then powered via contacts in the bottom, much like older-style LEGO motors.
Early experiments involved running various graphics to emulate a spaceship dashboard, but [James] has now gone much further. Hes implemented RP2040-doom to run the game. It uses til...
18:24
Minnesota power plant leaks 400,000 gallons of radioactive water Lifeboat News: The Blog

A nuclear power plant along the Mississippi River in Monticello, Minnesota, has leaked more than 400,000 gallons of radioactive water due to a broken pipe. NBCs Maggie Vespa has the details.
Subscribe to NBC News: http://nbcnews.to/SubscribeToNBC
Watch more NBC video: http://bit.ly/MoreNBCNews.
NBC News Digital is a collection of innovative and powerful news brands that deliver compelling, diverse and engaging news stories. NBC News Digital features NBCNews.com, MSNBC.com, TODAY.com, Nightly News, Meet the Press, Dateline, and the existing apps and digital extensions of these respective properties. We deliver the best in breaking news, live video coverage, original journalism and segments from your favorite NBC News Shows.
Connect with NBC News Online!
NBC News App: https://smart.link/5d0cd9df61b80
Breaking News Alerts:
https://link.nbcnews.com/join/5cj/breaking-news-signup?cid=slip_190621
Visit NBCNews. Com: http://nbcnews.to/ReadNBC
Find NBC News on Facebook: http://nbcnews.to/LikeNBC
Follow NBC News on Twitter: http://nbcnews.to/FollowNBC
Get more of NBC News delivered to your inbox:
nbcnews.com/newsletters.
#Minnesota #Nuclear #Radioactive
18:22
Tomorrow Biostasis: The Berlin Startup That Wants to Bring You Back from the Dead Lifeboat News: The Blog
What if death was not the end? What if, instead of saying our final goodbyes to loved ones, we could freeze their bodies and bring them back to life once medical technology has advanced enough to cure their fatal illnesses? This is the mission of Tomorrow Biostasis, a Berlin-based startup that specializes in cryopreservation.
Cryopreservation, also known as biostasis or cryonics, is the process of preserving a human body (or brain) in a state of suspended animation, with the hope that it can be revived in the future when medical technology has advanced enough to treat the original cause of death. This may seem like science fiction, but it is a legitimate scientific procedure, and Tomorrow Biostasis is one of the few companies in the world that offers this service.
Dr Emil Kendziorra, co-founder and CEO of Tomorrow Biostasis explained that the goal of cryopreservation is to extend life by preserving the body until a cure can be found for the original illness. He emphasized that cryopreservation is not a form of immortality, but rather a way to give people a second chance at life.
18:00
Trump and White Hats Attack Corporate Marxism Terra Forming Terra

When Mary Wollstonecraft Was Duped by Love Terra Forming Terra

Emails in 2020 blow the covid PCR test scam out of the water Terra Forming Terra
A deep dive into the PCR test which was telied on to drive public policy. It completely fails to test for COVID at all which is no surprise since that was my blanket objection at the time. You really need to identify a pathogen of some sort in order to invent a test.
75-Year-Olds White Hair Turns Black, Doctor Explains Why Terra Forming Terra
This alone can make accupuncture into a growth industry. This should also trigger hair growth renewal as well and of course all customers will return for a refresher.
16:59
Pompompurin Unmasked: Infamous BreachForums Mastermind Arrested in New York The Hacker News
U.S. law enforcement authorities have arrested a New York man in connection with running the infamous BreachForums hacking forum under the online alias "Pompompurin." The development, first reported by Bloomberg Law, comes after News 12 Westchester, earlier this week, said that federal investigators "spent hours inside and outside of a home in Peekskill." "At one point, investigators were seen
16:55
THN Webinar: 3 Research-Backed Ways to Secure Your Identity Perimeter The Hacker News
Think of the typical portrayal of a cyberattack. Bad guy pounding furiously on a keyboard, his eyes peeking out from under a dark hoodie. At long last, his efforts pay off and he hits the right combination of keys. "I'm in!" he shouts in triumph. Clearly, there are many problems with this scenario and it's not just the hoodie. What's even more inaccurate is that most cyber attackers today do
16:27
The White House Might be Running Out of Time to Bring Back Net Neutrality SoylentNews
Shortly after coming into office, President Joe Biden moved to restore net neutrality. He signed a sweeping executive order to promote competition, calling on the Federal Communications Commission (FCC) to bring back the Obama-era internet rules rolled back by the Trump administration.
But close to two years later, the FCC remains deadlocked with only four of its five commissioner slots filled and Biden may be running out of time.
Biden's pick for a new FCC commissioner was Gigi Sohn, a former FCC official and public interest advocate. Sohn would have secured a long-awaited Democratic majority at the agency. After she was nominated in October 2021, however, a well-funded opposition organized a brutal opposition campaign against her. The culture-war campaign called Sohn an "extremist" and a "censor" because of past tweets criticizing Fox News and former President Donald Trump, largely ignoring her decades-long professional record. After more than 16 months and three separate confirmation hearings, Sohn withdrew her nomination earlier this month, citing the "unrelenting, dishonest and cruel attacks" by broadband and cable lobbyists and their friends.
It's unlikely Biden will pick someone as critical of cable companies again but Republicans could try to thwart even a centrist candidate
Now, the White House has been forced to start over, prolonging a vacancy that continues to obstruct the administration's broadband agenda. The White House hasn't announced a new nominee or when they're hoping to confirm someone, but it's unlikely that Biden would pick someone as critical of cable companies as Sohn. Republicans and "dark money" groups have already proved that they're willing to spend millions to block progressive nominees. With so little time left in Biden's first term, stakeholders may even try to thwart a more moderate nominee, especially if there's an opportunity to continue the stalemate past the 2024 election.
...
16:17
LockBit 3.0 Ransomware: Inside the Cyberthreat That's Costing Millions The Hacker News
U.S. government agencies have released a joint cybersecurity advisory detailing the indicators of compromise (IoCs) and tactics, techniques, and procedures (TTPs) associated with the notorious LockBit 3.0 ransomware. "The LockBit 3.0 ransomware operations function as a Ransomware-as-a-Service (RaaS) model and is a continuation of previous versions of the ransomware, LockBit 2.0, and LockBit,"
16:00
HP 3488A Teardown, Dismantled for Parts Hackaday

[IMSAI Guy] has an old HP 3488A Switch Control Unit that he wants to dismantle for parts ( see video below the break ). The 3488A is pretty simple as far as HP test equipment goes a chassis that can hold various types of relay cards and is programmable over GPIB. He notes up front that these are plentiful and inexpensive in the used test equipment market.
Around the back of the unit is a card cage that accepts up to five option cards providing
- 44 matrix switching
- on/off SPST switching
- switching signals to a common bus
- VHF switching
- Digital I/O signalling
14:23
How tumors transform blood vessels Lifeboat News: The Blog
Increasingly dense cell clusters in growing tumors convert blood vessels into fiber-filled channels. This makes immune cells less effective, as findings by researchers from ETH Zurich and the University of Strasbourg suggest. Their research is published in Matrix Biology.
It was almost ten years ago that researchers first observed that tumors occurring in different cancersincluding colorectal cancer, breast cancer and melanomaexhibit channels leading from the surface to the inside of the cell cluster. But how these channels form, and what functions they perform, long remained a mystery.
Through a series of elaborate and detailed experiments, the research groups led by Viola Vogel, Professor of Applied Mechanobiology at ETH Zurich, and Gertraud Orend from the University of Strasbourg have found possible answers to these questions. There is a great deal of evidence to suggest that these channels, which the researchers have dubbed tumor tracks, were once blood vessels.
14:23
New ocean in making? Africa slowly splitting into two, scientists predict natures rarest move Lifeboat News: The Blog
As Africa splits into two pieces, scientists predict the beginning of the rarest natural phenomena. Researchers believe that in the distant future, the creation of a new ocean may result in the division of Africa into two pieces. The separation of two significant portions of the continent may eventually lead to the formation of a new body of water. In millions of years, landlocked nations like Zambia and Uganda might have their own coasts.
The splitting of an one tectonic plate into two or more tectonic plates divided by divergent plate borders is known as rifting, according to Science Direct. Where the Earths tectonic plates separate, a lowland area known as the rift valley arises, according to National Geographic.
These rift valleys can be found both on land and on the oceans floor. According to IFLScience research, this event dates back at least 138 million years to the time when South America and Africa became separated into separate continents. According to NBC News, the Red Sea and the Gulf of Aden were formed as a result of the Arabian plate moving away from Africa for the past 30 million years.
14:22
Mirror-imaging in molecules can modify neuron signaling Lifeboat News: The Blog
With the aid of some sea slugs, University of NebraskaLincoln chemists have discovered that one of the smallest conceivable tweaks to a biomolecule can elicit one of the grandest conceivable consequences: directing the activation of neurons.
Their discovery came from investigating peptides, the short chains of amino acids that can transmit signals among cells, including neurons, while populating the central nervous systems and bloodstreams of most animals. Like many other molecules, an amino acid in a peptide can adopt one of two forms that feature the same atoms, with the same connectivity, but in mirror-image orientations: L and D.
Chemists often think of those two orientations as the left and right hands of a molecule. The L orientation is by far the more common in peptides, to the point of being considered the default. But when enzymes do flip an L to a D, the seemingly minor about-face can turn, say, a potentially therapeutic molecule into a toxic one, or vice versa.
14:22
#176 Human organoids are new AI frontier; Listening to the big bang through the cosmic microwave background Lifeboat News: The Blog
Brainoids tiny clumps of human brain cells are being turned into living artificial intelligence machines, capable of carrying out tasks like solving complex equations. The team finds out how these brain organoids compare to normal computer-based AIs, and they explore the ethics of it all.
Sickle cell disease is now curable, thanks to a pioneering trial with CRISPR gene editing. The team shares the story of a woman whose life has been transformed by the treatment.
We can now hear the sound of the afterglow of the big bang, the radiation in the universe known as the cosmic microwave background. The team shares the eerie piece that has been transposed for human ears, named by researchers The Echo of Eternity.
14:22
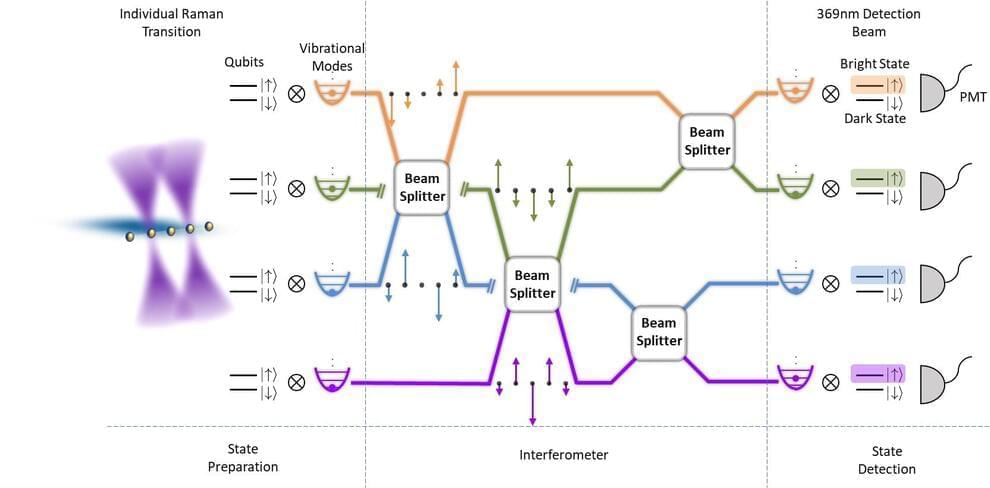
A scalable and programmable quantum phononic processor based on trapped ions Lifeboat News: The Blog
Quantum computing systems have the potential to outperform classical computers on some tasks, helping to solve complex real-world problems in shorter times. Research teams worldwide have thus been trying to realize this quantum advantage over traditional computers, by creating and testing different quantum systems.
Researchers at Tsinghua University recently developed a new programmable quantum phononic processor with trapped ions. This processor, introduced in a paper in Nature Physics, could be easier to scale up in size than other previously proposed photonic quantum processors, which could ultimately enable better performances on complex problems.
Originally, we were interested in the proposal of Scott Aaronson and others about Boson sampling, which might show the quantum advantages of simple linear optics and photons, Kihwan Kim, one of the researchers who carried out the study, told Phys.org. We were wondering if it is possible to realize it with the phonons in a trapped ion system.
13:31
New Talk: Richard Stallman Explains His Problem With Rust (Trademark Restrictions), Openwashing (Including Linux Kernel), Machine Learning, and the JavaScript Trap Techrights
Video download
link | md5sum
750dda35e5a1c938a6b961483896da2b
RMS Pre-LibrePlanet Talk (Richard Stallman Gave a Talk
Hours Ago)
Creative Commons Attribution-No Derivative Works 4.0
Summary: Richard Stallmans talk is now available above (skip to 18:20 to get to the talk; the volume was improved over time, corrected at the senders end)
The video above is a recording of the talk Richard M. Stallman (RMS) gave some hours ago. It was a live stream, broadcast by the Free Software Foundation. He founded it many years ago (the GNU Project turns 40 later this year and he turned 70 yesterday). The talk itself starts about 20 minutes into the video above; I had started recording about 15 minutes before the scheduled time of the talk.
At the start, Dr. Stallman notes that he cannot comment much about technical aspects of Rust, but he remains concerned (for a year already) about the trademark aspects. He is still receiving no clarification or assurances on the matter. Previously he suggested forking it and calling it something like crust (in a talk or a session he did with several Brazilian hackers).
Openwashing is not alluded to by that name. But he explains why Linux (the kernel) is non-free. He then comments on Debian including blobs in the installer (as of months ago). He mentions Respect(s) Your Freedom and alludes to various peripherals with code inside them. He suggests not being too judgemental of such microprocessors. Cameras, keyboards, and memory sticks, he says, typically have some small computers in them. Our ultimate goal is that all those should contain free software also, he stresses. To quote: We hope to hope that in the future well be able to [...] replace the non-free programs at a lower level of the products.
He asks for a distinction between software coming inside a piece of hardware and stuff the user adds to it later. These are growing challenges.
He speaks of Machine Learning and rejects the term AI (Hey Hi!). He compares it to dissociated press a very old term, not a buzzword or a misnomer. Its not just t...
13:00
The Blue Soup Saga Is One Beefy Mystery Hackaday

Beef soup! Youd normally expect it to be somewhere from reddish-brown to grey, depending on how well it was cooked and prepared. However, strangely, an assistant professor found the beef soup in their fridge had mysteriously turned blue. That spawned an investigation into the cause which is still ongoing.
[Dr. Elinne Becket] has earned her stripes in microbiology, but the blue soup astounded her. Despite her years of experience, she was unable to guess at the process or a source of contamination that could turn the soup blue. Indeed, very few natural foods are blue at all. Even blueberries themselves are more of a purple color. The case sparked enough interest that [Elinne] went back to the trash to collect photos and...
13:00
DataRobot releases AI Platform 9.0 to deliver value-driven AI Help Net Security
DataRobot has released DataRobot AI Platform 9.0, along with deeper partner integrations, AI Accelerators, and redesigned service offerings, all centered on helping organizations derive measurable value from their AI investments. AI has the potential to enhance every aspect of business transactions and human interactions to improve how we live and work, said Debanjan Saha, CEO of DataRobot. Since our founding, we have been 100% focused on helping enterprises realize measurable value from AI by offering More
The post DataRobot releases AI Platform 9.0 to deliver value-driven AI appeared first on Help Net Security.
12:24
Artistic Attempt To Send Digital Signals Via Fungus Lifeboat News: The Blog
Art projects can fundamentally be anything you like, as long as you say theyre art at the end of it all. They dont always work, or work well, but they often explore new ideas. Often, artists working on installations fall back on similar tools and techniques used by the maker community. [Julian] is no exception, and his Biotic Explorers work has many touchstones that will be familiar to the Hackaday set.
The Biotic Explorers Research Group is a broad art project, involving the creation of a fictitious scientific association. [Julian] created imaginary scientists, reports, and research to flesh out this world. The project culminates in the development of a prototype communications system, which uses pH sensors at either end of a fungal network in soil to send messages.
Liquids are applied to change the pH of the system, which can be picked up at the other end of the soil bed. The pH levels are read as digital signals, with pH levels either side of neutral reading as high and low bits. pH sensors can be expensive, so [Julian] chose the cheapest available, and tapped into their LCD display lines to read their output into an microcontroller. The system displays data using commonly available OLED displays, and hobby servo motors are used to control the dispensing of liquid.
11:50
Owner of Breach Forums Pompompurin Arrested in New York HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
Pompompurin's arrest was confirmed by one of the Breach Forum's administrators, Baphomet.
This is a post from HackRead.com Read the original post: Owner of Breach Forums Pompompurin Arrested in New York
11:44
Getting to Zettascale Without Needing Multiple Nuclear Power Plants SoylentNews
Getting To Zettascale Without Needing Multiple Nuclear Power Plants:
There's no resting on your laurels in the HPC world, no time to sit back and bask in a hard-won accomplishment that was years in the making. The ticker tape has only now been swept up in the wake of the long-awaited celebration last year of finally reaching the exascale computing level, with the Frontier supercomputer housed at the Oak Ridge National Labs breaking that barrier.
With that in the rear-view mirror, attention is turning to the next challenge: Zettascale computing, some 1,000 times faster than what Frontier is running. In the heady months after his heralded 2021 return to Intel as CEO, Pat Gelsinger made headlines by saying the giant chip maker was looking at 2027 to reach zettascale.
Lisa Su, the chief executive officer who has led the remarkable turnaround at Intel's chief rival AMD, took the stage at ISSCC 2023 to talk about zettascale computing, laying out a much more conservative some would say reasonable timeline.
Looking at supercomputer performance trends over the past two-plus decades and the ongoing innovation in computing think advanced package technologies, CPUs and GPUs, chiplet architectures, the pace of AI adoption, among others Su calculated that the industry could reach the zettabyte scale within the next 10 years or so.
Read more of this story at SoylentNews.
11:15
KELA partners with Snowflake to help joint customers remediate potential risks Help Net Security
KELA has partnered with Snowflake to launch its technical intelligence data on Snowflake Marketplace. KELAs Technical Cybercrime Intelligence availability on Snowflake Marketplace will enable joint customers to get near-instant, seamless, and secure access to potentially compromised IPs and domains involved in cybercrime activity. Commenting on the partnership, Itsik Kesler, CTO, said: Our Technical Cybercrime Intelligence capability will benefit Snowflake customers by providing them with the ability to automatically detect and monitor potentially compromised IPs and More
The post KELA partners with Snowflake to help joint customers remediate potential risks appeared first on Help Net Security.
10:39
Feds Charge NY Man as BreachForums Boss Pompompurin Krebs on Security
The U.S. Federal Bureau of Investigation (FBI) this week arrested a New York man on suspicion of running BreachForums, a popular English-language cybercrime forum where some of the world biggest hacked databases routinely show up for sale. The forums administrator Pompompurin has been a thorn in the side of the FBI for years, and BreachForums is widely considered a reincarnation of RaidForums, a remarkably similar crime forum that the FBI infiltrated and dismantled in 2022.
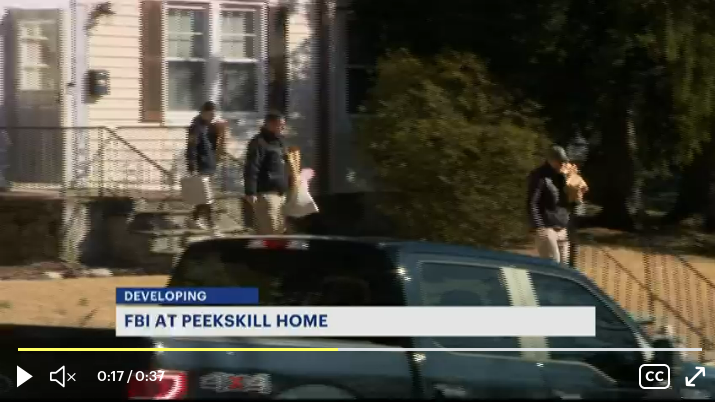
FBI agents carting items out of Fitzpatricks home on March 15. Image: News 12 Westchester.
In an affidavit filed with the District Court for the Southern District of New York, FBI Special Agent John Langmire said that at around 4:30 p.m. on March 15, 2023, he led a team of law enforcement agents that made a probable cause arrest of a Conor Brian Fitzpatrick in Peekskill, NY.
When I arrested the defendant on March 15, 2023, he stated to me in substance and in part that: a) his name was Conor Brian Fitzpatrick; b) he used the alias pompompurin/ and c) he was the owner and administrator of BreachForums the data breach website referenced in the Complaint, Langmire wrote.
Pompompurin has been something of a nemesis to the FBI for several years. In November 2021, KrebsOnSecurity broke the news that thousands of fake emails about a cybercrime investigation were blasted out from the FBIs email systems and Internet addresses.
Pompompurin took credit for that stunt, and said he was able to send the FBI email blast by exploiting a flaw in an FBI portal designed to share information with state and local law enforcement authorities. The FBI later acknowledged that a software misconfiguration allowed someone to send the fake emails.
In December, 2022, KrebsOnSecurity broke the news that hackers active on BreachForums had infiltrated the FBIs InfraGard program, a vetted FBI program designed to build cyber and physical threat information sharing partnerships with experts in the private sector. The hackers impersonated the CEO of a major financial company, applied for InfraGard membership in the CEOs name, and were granted admission to the community.
From there, the...
10:12
New Vishing Attack Spreading FakeCalls Android Malware HackRead | Latest Cybersecurity and Hacking News Site
The malware campaign was noted to target users in South Korea.
This is a post from HackRead.com Read the original post: New Vishing Attack Spreading FakeCalls Android Malware
10:00
Broken Pocket Watch Becomes Pocket Sundial Hackaday

Pocket watches are all well and good, but they have some caveats. They either need regular rewinding, or they need batteries. Sundials on the other hand need only the light from our One True Sun. [JGJMatt] has just the project to convert your broken or disused pocket watches to the solar way of telling the time.
The key is to replace the clockwork internals and face of the pocket watch with a sundial instead. The first step is to create a face for the watch marked out for sundial use. [JGJMatt] explains how to do this with a variety of CNC, painting, or etching methods. He also explains how to use simple tools to generate a sundial design thats ideally suited to your geographical location. This includes methods for aligning the sundial to True North or True South with an offset compared to Magnetic North or Magnetic South. This allows the sundial to be as accurate as possible. [JGJMatt] describes the general techniques while also building a sundial of his very own. The resulting piece is a handsome bit of brass with a lovely gnomon standing tall to cast a shadow on the dial.
Its not a quick way to tell t...
09:36
Who Follows 1xbet Presents An Impressive List Of Sports Activities Betting Choices h+ Media
Who Follows 1xbet Presents An Impressive List Of Sports Activities Betting Choices
As you can see, the bookmaker company permits the users to decide on the registration method to own style. Decide which one fits you better of all, start the registration course of and enjoy on the market forms of sports activities activities as quickly as potential. 1xBet bookmaker is the name that just about each bettor may need come throughout. The bettor needs to obtain 1xbet app and to create a code. The program will assist to create a better password in addition to a unique login.
Also, the stay streaming app permits online players to watch matches of each in style leagues and distinctive sports activities. To do that, you have to log in and replenish your gaming account for a minimum amount. Its a typical factor when retailers supply prospects a bonus a reduction with a funded system. The bettor has an chance to use his Facebook, Google+ or Vk profile for this objective. It routinely turns right into a affirmation of his individuality.
The utility has great reviews, in plenty of respects due to the broad possibilities, from creating an account with a welcome bonus on bets to video games. Completing the 1xBet Android app get hold of and installing it on a gadget, a player will get fast entry to the complete performance of the betting platform. The equally fast transition is offered within the app and desktop model. Everyone chooses what to make use of based on their non-public preferences. Furthermore, players additionally get access to a 24/7 gaming platform and timely fee options.
In order to be taught more relating to the total report on on-line payments on betting web site 1xGuess, all people studying this should go to the 1xGuess platforms. The listing of the latter contains the championships of each nation, beginner tournaments, and qualifying rounds. [newline]The website online supplies special statistics, that you must use to get acquainted with the probabilities of a certain employees to win, along with betting coefficients. The latter requires stepping into private data, as appropriately as telephone number alongside the e-mail. To get pleasure from this bonus use the1xBet promo codeto make your bets. You can simply find out from recommendations on how to use 1xBet bonus elements. By putting within the 1xBet app, youll have the flexibility to guess on a pre-match or stay match.
If you select sports activities for the bonus provide, youll obtain +100% in your first deposit as so much as 20,000 INR. This betting company additionally permits the person to put a guess on a selection of sports activities available on 1xBet Bangladesh official web site. It has a 24/7 stay chat alternative from a 1xBet admin private for queries and clarifications, across the clock reside betting occasions, multi-live function, and so forth. There are many poker tables, roulettes, blackjack as nicely as slot machines. The particu...
09:34
Search Outcomes For boo On Line Casino No Deposit Bonus Code Open8010betcom Fifa 22 Beta Cellular Obtain 1xbet App Download 2022 Open8010betcom$$limitadong Regalo!mag Register Para Makakuha Ng P50 Might 50% Cashback Sayong Unang Deposit!$$wv h+ Media
Search Outcomes For boo On Line Casino No Deposit Bonus Code Open8010betcom Fifa 22 Beta Cellular Obtain 1xbet App Download 2022 Open8010betcom$$limitadong Regalo!mag Register Para Makakuha Ng P50 Might 50% Cashback Sayong Unang Deposit!$$wv
Its value noting that the official program at present holds a very extreme score in Apples retailer. Click on considered one of many supplied odds and select Bet or Add to Coupon. In the primary case youll make a single guess, contained in the second a parlay or a gaggle guess. Use the login and password you specified when registering your account or use any totally different technique of logging in. The gamblers are in a place to get the profitable soon after they win.
Only high coefficients wont be succesful of guarantee the long-term status of a bookmaker. If a company must succeed and appeal to lots of purchasers, it have to be ready to supply something further, as an example, 1xBet app for computer or one thing like that. This is to have the ability to make all the person experience as easy and as simple as attainable. The participant receives a complete listing and enough ratios, which contributes to a satisfying pastime.
The sms will comprise a momentary password that the bettor can change it. Pharmacist Only Medicine Pharmacist recommendation is required to buy this product. Please note that we reserve the proper to say no supply if the pharmacist assesses that using this drugs just isnt acceptable.
It will include several cifras, that are legitimate for a limited period. The bettor must fill out private data and economical data. I gave my good pal 1xbet registration hyperlink and he did the process in 5 minutes and he bets on sports activities with me. It is utilized by tens of 1000s of players as a outcome of it allows them to wager sooner and less complicated.
The Google Authenticator app could be downloaded onto most smart gadgets. If youve put in Authy, you do not want to put in Google Authenticator. Hi seems like you are not having entry to member information as were both waiting upon or processing your payment in your membership. At Electrify NZ we imagine the future of transportation is electrical.
To join up, its additionally necessary to specify your cell phone quantity and your real data, label and surname. This is actually the rationale why safe wager with 1xChoice on line playing home could also be made with absolute security. For occasion, a consumer can first insure 10%, subsequently 30%, then one other 50%.
The utility has nice reviews, in a lot of respects due to the broad potentialities, from creating an account with a welcome bonus on bets to video games. Completing the 1xBet Android app get hold of and installing it on a gadget, a participant will get fast entry to the entire performance of the betting platform. The equally quick transition is offere...
09:32
Reap The Advantages Of 1xbet App h+ Media
Reap The Advantages Of 1xbet App
The bookmakers group made positive that the bettors had a chance to guess on sports activities activities or play in the on line on line casino, poker and slots, and so forth. To start betting on 1xBet bd or play 1xBet poker, you should first register and replenish your stability. Betting change different consists of eight the most well-liked sports activities to guess successfully against different clients. Nonetheless, lets not get forward of ourselves since the ultimate verdict relies upon tremendously on the net sites payment/withdrawal capabilities. Now you must type within the data, collectively with your full name, foreign money that youll be using, and so forth. 1xbet utility is absolutely compatible with all kinds of operating methods.
After the basic identification verify, the player has to get through a regular registration process. These methods are used when blocking the organizations website and provide access. With the first 4 deposits, customers can receive a welcome bonus as excessive as INR one hundred thirty five,000 at 1xWager Casino. Compared to further betting platforms, this bookmaker gives his one of many better casino welcome bonus products obtainable to Indian players. There is an totally different choice, though, any buyer can discover it on the official website online of the bookmaker. The one who makes betting is generally watching sports activities activities events regularly.
The comparability of bookmakers,sometimes, highlights the work of these departments. The firm turned well-known very quickly with the help of all the issues listed above. When contacted chat help they informed my cellphone number is linked to another account and mail to safety for the same. The identical payment methods can be utilized to withdraw the profitable. The bettors of 1xbet can withdraw each small and enormous amounts of cash. In order to take a giant profitable its all the time better to depend on banks companies.
1xBet also has a simple to make use of browser named the 1x browser that targets Android customers. 1x Bet is really a actually good gambling web site in India with incredible sports activities bets and online casino sections. The sports activities delightful bonus consists of a one hundred pc match extra as high as 20,000. Moreover, you want to use promo program code 1XSeries22 while registering and stand up to 130% extra on the primary deposit. The coupon acquired for bonus factors just isnt money, however you presumably can win it by making a profitable guess. When registering at a bookmaker, along with within the means of using its functionality, you presumably can profitably apply particular promotional codes.
All on line casino titles out there on the desktop website are additionally current in the 1xBet casino cell versions. The 1xBet live on line casino platform targets players in search of the actual on line casino experie...
09:30
Mostbets Mobile Version Has A Variety Of Benefits h+ Media
Mostbets Mobile Version Has A Variety Of Benefits
It contains making an attempt to foretell the competitions ultimate consequence. Allows the app to forestall the gadget from going to sleep.. Allows the app to view details about community connections similar to which networks exist and are related..
IOS Android You can discover the app within the Apple Store, so youll have the ability to open it and install an application as all the time. The design is optimized for all screen sizes and resolutions, so it would be comfortable to make use of the network web site to achieve some cash. Mostbet team does their greatest to make your gaming expertise as diversified as possible. Consequently, there are several types of putting odds out there in your fun.
The application is completely examined and safe in your gadget. Our utility database is protected, as we frequently scan programs with antivirus software. If you are a newbie, then you can use social networks for verification or e mail.
The app routinely adjusts itself to suit the screens diagonal. Mostbet offers players with the opportunity to immerse themselves in a visually gorgeous and evocative world of various on-line casino enjoyment. The casino web page on the internet and in the app is built in a vigorous environment, the place you presumably can remember to have a beautiful time whereas incomes actual money. In this article, youre going to get information about one of the most well-liked bookmakers in India.
Allows the app to create network sockets and use customized network protocols. The browser and different functions present means to send data to the internet, so this permission isnt required to ship information to the web.. Free play the most popular slot machines and video games. Above weve already lined many sturdy sides of the network.
The bookmaker first opened its doors in 2009 and has since grown to a multi-million player base and expanded its operations to more than ninety nations. The service is always altering, and the quality of the companies improves yr after year. Because Mostbet is legal in India and extensively regarded by Indian gamers, you might be assured in your gains.
The Latest Version of 7.three.5 Available for download. Download the app utilizing your favourite browser and click on on Install to put in the applying. Please note that we offer each basic and pure APK files and quicker download speeds than APK Mirror.
Replenishment and withdrawal of funds can carry out utilizing financial institution playing cards and digital wallets. You can additionally use Bitcoin, Litecoin, Ethereum, and Ripple. Prepare an digital copy of your passport prematurely. Sometimes a company practices Skype calls to verify a players identity.
To contact them, you have to use e-mail or name the indicated cellph...
09:27
Obtain Mostbet Apk Free For Android h+ Media
Obtain Mostbet Apk Free For Android
If you start it on your gadget, you see that theres the same line alternative as within the desktop one. Cricket, basketball, baseball, tennis, ipl, soccer, and a separate section bookmaker workplace is 100 percent identical to the desktop one. Mostbet bd app is a sports betting application obtainable for each Android and iOS gadgets. It permits its clients to be told about interesting matches, new bonuses, and paid bets. The app presents push-up notifications so that you simply dont have to download it to view the notifications.
However for Apple devices there may be a greater approach to obtain software program program from the App Retailer. Mostbet accepts bank transfers, payments methods, and e-wallets , as nicely as cryptocurrency deposits. Mostbet India works with the PayTM system and takes rupees. Making a deposit is straightforward and fast, and money is mostly out there instantly. The same is true for withdrawals; its preferable to use the same payment technique as for deposits, since this eliminates the necessity for added data.
The net application is presented in Mostbet apk format and is appropriate for Android gadgets. Just click on the button and await the obtain. It only takes a couple of minutes to install the required information. It is now very easy to place a web-based wager out of your mobile phone.
The firm is consistently creating, introducing new features to offer players with comfortable circumstances. Go to the cell model of the site from your smartphone. Then register with the bookmaker and download the application in Mostbet apk format.
The obtain is as direct as our velocity and we provide direct hyperlinks to all available variations of Mostbet APK free of charge. The Mostbet Apk is available for iPhone, Android, and Windows devices. The Mostbet Apk mobile web site is straightforward to make use of and would not have to be downloaded to your device.
Again, work is carried out at night time, when most gamers are sleeping. The website or app is undergoing technical or upkeep work. It usually takes no more than an hour and occurs at night so as not to intervene with bettors enjoying online.
Mostbet provides an app for Android customers thats appropriate for both smartphones and tablets. You can obtain the app from the Google Play store or some other alien source and set up it to your system. Once put in, you probably can place your bets or play the games.
Sports Betting is mostbet,sports,bookmaker,company.,betting, content material rating is Everyone (PEGI-3). This app is rated 5 by 1 users whore using this app. To know extra in regards to the company/developer, visit cpp ligastavok web site who developed it. Org.adverts.mostbet.apk apps may be downloaded and put in on Android 4.1.x and better Android gadgets.
Once the set u...
09:25
Mostbet App Evaluate
This might be because of technical points and hacker attacks or the company having a license abroad. Therefore, on this part, Mostbet talks about its present tackle. You can go to Mostbet at any time through our website. You also can benefit from the Mostbet casino, however this can be a bit inconvenient, so it is much better to use the app.
Again, work is carried out at night, when most players are sleeping. The web site or app is present process technical or maintenance work. It often takes no extra than an hour and occurs at night in order not to interfere with bettors playing on-line.
You can also register using the app, or you can log in via the operators web site. There is a simple way you should comply with for download and install Mostbet Apk 2021 in your android system. AS you know already if you obtain any apk apps from the net other than playstore you want to make some settings in your android system. The sports activities at Mostbet is out there in the type of stay video games, quick video games, virtual and e-games. Their sports betting gallery has over 10 video games for line. Most of the e-sports can be found for betting and the players can even entry live matches directly from the net site.
gadgets. These options are so simple to use that newbies wont discover any difficulties on the first betting attempt. [newline]Features like quick access, intuitive navigation, and clean design have made staking extra attractive for every person. The search bar function additionally made it easy for customers to rapidly find any class of a specific event. Mostbet is among the best betting platform that offers players one of the best probability to win big. They have been one of the best bookmaker and so they have been within the betting business for more than 12 years. During these years, they have been in a position to present excellent providers to their shoppers.However, you can nonetheless install APK recordsdata with OBB directly on your android system. You need to have ES File Explorer app on your android device if you would like to install the APK with OBB knowledge immediately in your android gadget. When you go to the homepage of the official web site, in the best prime corner youll find a huge purple Register button. Click on it, and youll see a kind, the place you should select an option for registration through the mobile number, e-mail, or social media networks. After making a deposit, the bonus cash will be credited to a particular account, and in order to withdraw it, the welcome bonus will need to be wagered. It is price noting that not considered one of the versions of the mobile app does help the perform of simple communication with the customer assist specialists.
Once the set up is full, launch the Mostbet app and check in to your Mostbet account. The Mostbet app is simple to use and can...
09:23
Wine 8.4 Released With The Early Wayland Graphics Driver Code, 51 Bug Fixes Phoronix
09:04
Everything Everywhere All at Once Piracy Skyrockets After Oscar Win TorrentFreak
 The Oscars are the most anticipated movie awards show
of the year, closely followed by hundreds of millions of movie fans
around the world.
The Oscars are the most anticipated movie awards show
of the year, closely followed by hundreds of millions of movie fans
around the world.
This years Academy Awards ceremony received plenty of attention as well, with one film standing out from all the rest.
With seven awards overall, including Best Picture, Best Director, and Best Actress, Everything Everywhere All at Once was the star of the night. The independent film impressed the voters, despite having a relatively tiny budget compared to competitors including Top Gun: Maverick and Avatar: The Way of Water.
The success didnt come as a complete surprise. The film had already scooped up dozens of accolades, including two Golden Globes, but winning seven Oscars was an entirely different level.
Oscar Boost
Renewed attention from the press and film fanatics boosted interest among the broader public. This typically increases legal sales and views on streaming platforms, especially for relatively small releases.
Everything Everywhere All at Once is no longer running in theaters, so there is no bump there. That said, there is another area where we observed a massive spike in interest, although thats unlikely to please the filmmakers.
The Oscars typically have a direct impact on piracy activity, and the big Oscars winner is no exception. Based on a sample of torrent activity tracked by IKnow, we can report that pirated downloads of Everything Everywhere All at Once skyrocketed this week.
Oscar Piracy
Before discussing the numbers, its important to highlight that pirated copies of the Oscars winner have already been circulating for months. The first high-quality copy leaked last May and it was in the top ten most pirated films for several weeks in a row.
Since its release, the film has been illegally downloaded and streamed millions of times. In January of this year, we observed two modest spikes in downloads, once after the Golden Globes win and again when t...
08:52
In Wild Hacking Spree, Hackers Accessed Federal Law Enforcement Database SoylentNews
The U.S. government database provided access to a treasure trove of sensitive data. "I can request information on anyone in the U.S.," one of the alleged hackers wrote:
Two men, one of whom previously presented themselves as an independent security researcher to Motherboard, allegedly went on a wide spanning hacking spree that included breaking into a federal U.S. law enforcement database; using a compromised Bangladeshi police officer's email to fraudulently requesting user data from a social media company; and even trying to buy services from a facial recognition company which doesn't sell products to the wider public.
[...] Sagar Steven Singh, 19, was arrested in Rhode Island on Tuesday; Nicholas Ceraolo, 25, remains at large with his location listed as Queens, New York, a press release from the United States Attorney's Office for the Eastern District of New York says. "Singh and Ceraolo unlawfully used a police officer's stolen password to access a restricted database maintained by a federal law enforcement agency that contains (among other data) detailed, nonpublic records of narcotics and currency seizures, as well as law enforcement intelligence reports," it states.
[...] That pursuit of personal information is what allegedly drew Singh and Ceraolo to breaking into various law enforcement accounts. In one case, the pair allegedly used a police officer's credentials to access a web portal maintained by a U.S. federal law enforcement agency.
Also at Dnyuz.
Read more of this story at SoylentNews.
08:42
Hitachi Energy breached by Clop gang through GoAnywhere Zero-Day exploitation Security Affairs
Hitachi Energy disclosed a data breach, the Clop ransomware gang stole the company data by exploiting the recent GoAnywhere zero-day flaw.
Hitachi Energy disclosed a data breach, the company was hacked by the Clop ransomware gang that stole its data by exploiting the recently disclosed zero-day vulnerability in the GoAnywhere MFT (Managed File Transfer).
The company was the victim of a large-scale campaign targeting GoAnywhere MFT devices worldwide by exploiting the zero-day vulnerability.
We recently learned that a third-party software provider called FORTRA GoAnywhere MFT (Managed File Transfer) was the victim of an attack by the CLOP ransomware group that could have resulted in an unauthorized access to employee data in some countries. reads the statement pblished by the company.
Upon learning of this event, we took immediate action and initiated our own investigation, disconnected the third-party system, and engaged forensic IT experts to help us analyze the nature and scope of the attack. Employees who may be affected have been informed and we are providing support. We have also notified applicable data privacy, security and law enforcement authorities and we continue to cooperate with the relevant stakeholders.

Hitachi Energy immediately launched an investigation into the incident and disconnected the compromised system. The company reported the data breach to law enforcement agencies and data protection watchdog.
The company pointed out that its network operations o...
08:24
Links 17/03/2023: CentOS Newsletter and News About Mr. UNIX Ken Thompson Hopping on GNU/Linux Techrights
-
GNU/Linux
-
Desktop/Laptop
-
HowTo Geek The System76 Meerkat Is a Tiny PC Built for Linux
System76 is one of the few PC manufacturers with a focus on excellent Linux support, with a wide range of desktops and laptops. Now the company has brought back the Meerkat, a compact PC built for Linux.
System76 first introduced the Meerkat in 2009, which was advertised as a NetTop (remember those?), and has gone in and out of production over the years with occasional hardware upgrades. The tiny PC is once again available for purchase, this time with your choice of 10th, 11th, or 12th Gen Intel Core processors. There are two sizes: a short model (1.42 inches tall) with only one M.2 drive slot, and the bay for extra storage capacity. Both versions are 4.6 x 4.41 inches across.
-
-
Applications
-
Linux Links Excellent Utilities: nvitop GPU process management
...
-
-
08:14
Top Five Reads on FOSS Force for Week Ending March 17, 2023 FOSS Force
Here are the five most read articles on FOSS Force for the week ending March 17, 2023. Despite What Youve Heard, Open Source 101 Isnt
The post Top Five Reads on FOSS Force for Week Ending March 17, 2023 appeared first on FOSS Force.
07:57
The European Patent Offices Central Staff Committee Explains the Situation at the EPO to the Yes Men of Antnio Campinos (Who is Stacking All the Panels) Techrights
Video download
link | md5sum
59217133f9f9582b2c0934acb9c644a5
EPO and the GCC Meeting
Creative Commons Attribution-No Derivative Works 4.0
Summary: The EPOs management is lying to staff (even right to their faces!) and it is actively obstructing attempts to step back into compliance with the law; elected staff representatives have produced detailed documents that explain the nature of some of the problems theyre facing
THE
document discussed above [PDF] is very long. It
can help explain internal EPO
affairs to outsiders i.e. people to whom EPO blunders are known
only through media channels (those that Benot Battistelli and Antnio Campinos have not intimidated into
silence with threats of lawsuits and various sanctions).
The Central Staff Committee (CSC) does a good job explaing the hoax studies of the administration, pretending that the EPO is poor in order to lessen the compensation to staff and thus deter/discourage properly-trainied and experienced staff from joining/staying. Todays EPO is gradually running out of talent; as EPO insiders have warned repeatedly, this will result in further collapses, including patent quality and validity issues (illegitimate patents being granted, including European software patents). The biggest stakeholders in the EPO have already complained about the quality of European Patents; they too stand to lose because many of these patents can be used against them; only patent litigation firms stand to benefit regardless of the merit of cases.
The covering message (like cover letter) for the above PDF stated what was discussed, albeit the cronies of the President didnt bother discussing much. They just said yes to proposals. Heres the outline:
R...
07:37
1xbet Cell App In Liberia h+ Media
1xbet Cell App In Liberia
IOS users want a tool of a minimum of 6.zero to make the most of all of the choices on the app. Below is a list of each Android and iOS units which may be appropriate with the 1xBet app. By installing this app, you can execute all functions on 1xBet. The app is absolutely geared up with all features that you can find on the desktop. For occasion, youll find a way to create a model new account, claim bonuses, and make deposits and withdrawals.
Well over 90% of the bets placed on cricket matches are carried out in-play. Make sense with the character of the sport of cricket some times being long and good spacing for the motion. Compared to other prime betting websites we have reviewed, 10Cric is relatively new. We prefer it for its centered attention to Cricket and Indian gamers, with a lot of games having local flavouring. Their portfolio of games and occasions retains increasing every few weeks.
In phrases of functionality, the 1xbet app provides a clean and intuitive person experience with all of the features and companies youd find on their desktop site. One notable feature is the 1xbet live streaming option for numerous sports activities, which lets you stay up to date with the latest match developments.
Live betting is a popular possibility for on-line bookmakers, and 1xBet app additionally has this function. You can find this selection on the highest menu of the display.
To be on the safer side, make certain that the betting web site you might be utilizing is properly registered and licensed and its utterly secure and safe. Select Cricket from the websites menu and select a match/series/tournament you want to guess on. Sign up and create your betting account with that website. Covering predictions & previews on prime Cricket Tournaments; get match odds & updates on all One Day, Test & T20 Tournaments. Despite a group being in its type, the match outcome might be waived if it loses toss in a field where the pitch favors those who bat first or ball first. Thats where your betting decision should be calculated once more.
It is only a bunch of codes which are doing no going to our devices house till we make them work. Thats why this onex wager app launching stage turns out to be useful and bears excessive significance to the operation. Unfortunately, we want to run some system adjustments to make sure our technology recognizes the retrieved program recordsdata. Technology has heightened lots of transactions, some leading to constructive results while others fail to ship. However, ix wager app has not simply modified the way customers run varied operations, as an alternative, it has been the scoreboard against which different bookmakers assess their efficiency.
1xbet helps associates program promotions for new players. These gamers normally are out there in by way of a referral link offered to them by 1x...
07:34
Features Of 1xbet Cell App For Indian Gamers h+ Media
Features Of 1xbet Cell App For Indian Gamers
Please check the web playing regulation in your jurisdiction earlier than putting any bets on any betting websites advertised on our website. Here at OCB our objective is to review all of the betting websites our customers use, and time from time there are new betting sites entering the gaming markets. If you have been to discover a betting website that supplied you 1.25 odds on India to win, youll get an extra INR 50 for every INR a thousand you guess on India to win. These small sums adds up in case you are betting a lot of games, so keep in mind to shop round for the highest cricket betting odds. Since the time we began reviewing Parimatch for his or her local providing, weve constantly seen new features or fee options being added on their web site each few weeks.
ClaimGo to websiteOpen an account with bet365 right now and guess on an infinite range of markets with the worlds favourite on-line sports activities actions actions betting agency. They have been aggressive at making this regarded, and as a Nigerian participant, you need to be conversant on this. This isnt a shock, contemplating the precise truth what odds are outfitted to purchasers.
Even though sports betting and playing isnt legal in India, there are not any legal guidelines towards online gambling. This fact makes 1xBet authorized in Andhra Pradesh and different Indian states. Every player who is into betting has had the thought, What if I need to bet outdoors of simply my home? You can guess wherever you might be, using a state-of-the-art cell consumer. But earlier than downloading, allow apps from third-party sources to be put in. I even have been taking part in on 1x bet.com for over 5 years and this is one of the best place to bet.
It is very famous and players worldwide attempt to get auctioned and be a half of any of the 7 groups of the league. The Top IPL Betting Apps present a complete betting expertise for its customers. As far as cricket betting is worried, online cricket betting has witnessed the influx of millions of bettors from around the globe. Cricket is among the hottest sports in the world and the introduction of latest shorter formats within the sport has increased its betting market value by large numbers. Furthermore, the chances displayed on our website are for informational purposes solely and can not be wagered on. We arent a betting site and do not settle for bets from gamers.
Despite quite a few playing websites on the Internet, 1XBET continues to be probably the greatest web sites for sports betting in CIS countries. This is as a end result of it has all of the features required to make betting more convenient. These embody; detailed rules and instructions, reliable statistics, and protected payment methods. Although the response time isnt so fast, general, 1xBet has glorious customer support, which is great for an internet betting fir...
07:31
Password Generator
Minimum downpayment permitted is ten Euro, which is added to the account of the shopper therefore its made efficiently. In in the future, you should wager a turnover of 3 occasions the bonus quantity. After login, choose the Cards possibility in the Deposit part and fill within the required card details. After making a deposit into your 1xBet app, you may be eligible to receive a deposit bonus . After that, await the app to download and proceed to install. WebCatalog SpacesOrganize apps and accounts into tidy collections with Spaces.
There is not any want to put in torrent information and use mirrors. We ask that you simply contemplate turning off your advert blocker so we will deliver you the best expertise possible while you are right here. Tract IQ offers knowledge and visualizations showing where all new residence developments and multi-family amenities are being constructed. Health Poll 1xbet promo kod ochish Database presents health-related U.S. survey questions, overlaying eighty years of national polling. Supporting materials embrace examine guides, essays, and interviews with teachers & practitioners. The following databases are newly acquired or being evaluated for a future subscription. Crypto change large Coinbase has filed an amicus brief in its insider buying and selling case, slamming the SEC for not providing a clear regulatory method.
One of the USP is tt additionally supplies its participant with reside streaming on cricket, football, horse racing and extra . You can simply take your gaming to the subsequent degree on 1xbet app on line casino dashboard. They present the best range of events, with some thrilling ones like stay vendor games taking the center sport.
You can conduct 1xbet app free obtain for iOS devices or iPhone by following the download and set up steps outlined under. For the comfort of customers 1xbet has developed software for cell and laptop platforms.
Once prepared, they will type 1xbets name in the search field, use their Apple ID, and full this process. The app offers a perfect platform to scan the 1xBet web site and establish such extra sports betting incentives. You can even use the app to plan your sports activities betting schedule. The fact that 1xBet apps are fitted with automatic updates will allow you to spare some sources for upcoming events.
When you are pleased with the selection youve made, youll have the ability to return to the main menu of the 1xBet app and click on on on the Bet Slip possibility. This will convey up your coupon with all the totally different alternatives youve made. 1xBet is one of the solely betting apps in India that lets you bet on kabaddi. Please observe that the 1xBet register process is possible in several ways without delay.
Also, the app size is 249.2 MB, so ensure to have no less than this muc...
07:29
Chinese Hackers Exploiting 0-day Vulnerability in Fortinet Products HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
According to researchers, multiple Fortinet products were impacted by this vulnerability, including FortiManager, FortiGate, and FortiAnalyzer.
This is a post from HackRead.com Read the original post: Chinese Hackers Exploiting 0-day Vulnerability in Fortinet Products
07:00
Finessing a Soldering Iron to Remove Large Connectors Hackaday

One of the first tools that is added to a toolbox when working on electronics, perhaps besides a multimeter, is a soldering iron. From there, soldering tools can be added as needed such as a hot air gun, reflow oven, soldering gun, or desoldering pump. But often a soldering iron is all thats needed even for some specialized tasks as [Mr SolderFix] demonstrates.
This specific technique involves removing a large connector from a PCB. Typically either a heat gun would be used, which might damage the PCB, or a tedious process involving a desoldering tool or braided wick might be tried. But with just a soldering iron, a few pieces of wire can be soldered around each of the pins to create a massive solder blob which connects all the pins of the connector to this wire. With everything connected to solder and wire, the soldering iron is simply pressed into this amalgamation and the connector will fall right out of the board, and the wire can simply be dropped away from the PCB along with most of the solder.
There is some cleanup work to do afterwards, especially removing excess solder in the holes in the PCB, but its nothing a little wick and effort cant take care of....
06:43
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Jakub Wilk on Mar 17
* Hanno Bck <hanno () hboeck de>, 2023-03-17 11:48:[...]
Agreed.
I don't think that's gonna fly, because...
TIOCLINUX implements also functionality unrelated to copying and
pasting. See the ioctl_console(2) man page:
https://manpages.debian.org/unstable/manpages-dev/ioctl_console.2.en.html#TIOCLINUX
For example, apparently some of this stuff is used by systemd:
$ git grep -wB5 TIOCLINUX...
06:37
Open Source Initiative Extends Voting Period After Email Typo FOSS Force
Pushing the end of voting back by one day assures there will be no confusion about when the polls close, which could have cost some OSI members their votes.
The post Open Source Initiative Extends Voting Period After Email Typo appeared first on FOSS Force.
06:11
Precise Solar Observations Fed Millions in Ancient Mexico SoylentNews
Aztec farming calendar accurately tracked seasons, leap years:
Without clocks or modern tools, ancient Mexicans watched the sun to maintain a farming calendar that precisely tracked seasons and even adjusted for leap years.
Before the Spanish arrival in 1519, the Basin of Mexico's agricultural system fed a population that was extraordinarily large for the time. Whereas Seville, the largest urban center in Spain, had a population of fewer than 50,000, the Basin, now known as Mexico City, was home to as many as 3 million people.
To feed so many people in a region with a dry spring and summer monsoons required advanced understanding of when seasonal variations in weather would arrive. Planting too early, or too late, could have proved disastrous. The failure of any calendar to adjust for leap-year fluctuations could also have led to crop failure.
Though colonial chroniclers documented the use of a calendar, it was not previously understood how the Mexica, or Aztecs, were able to achieve such accuracy. New UC Riverside research, published in the Proceedings of the National Academy of Sciences, demonstrates how they did it. They used the mountains of the Basin as a solar observatory, keeping track of the sunrise against the peaks of the Sierra Nevada mountains.
"We concluded they must have stood at a single spot, looking eastwards from one day to another, to tell the time of year by watching the rising sun," said Exequiel Ezcurra, distinguished UCR professor of ecology who led the research.
To find that spot, the researchers studied Mexica manuscripts. These ancient texts referred to Mount Tlaloc, which lies east of the Basin. The research team explored the high mountains around the Basin and a temple at the mountain's summit. Using astronomical computer models, they confirmed that a long causeway structure at the temple aligns with the rising sun on Feb. 24, the first day of the Aztec new year.
Journal Reference:
Exequiel Ezcurra, Paula Ezcurra, and Ben Meissner, Ancient
inhabitants of the Basin of Mexico kept an accurate agricultural
calendar using sunrise observatories and mountain alignments
[open], PNAS, 2022. DOI: https://doi.org/10.1073/pnas.2215615119
Read more of this story at SoylentNews.
05:15
Fake Telegram and WhatsApp clones aim at crypto on Android and Windows HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
Currently, the scam targets users who speak Chinese.
This is a post from HackRead.com Read the original post: Fake Telegram and WhatsApp clones aim at crypto on Android and Windows
05:15
FakeCalls Vishing Malware Targets South Korean Users via Popular Financial Apps The Hacker News
An Android voice phishing (aka vishing) malware campaign known as FakeCalls has reared its head once again to target South Korean users under the guise of over 20 popular financial apps. "FakeCalls malware possesses the functionality of a Swiss army knife, able not only to conduct its primary aim but also to extract private data from the victim's device," cybersecurity firm Check Point said.
04:58
Firmware Assisted Shadowing Code Posted For AMD RDNA3 - Needed For SR-IOV Phoronix
A new patch series posted today is of interest and is for firmware-assisted shadowing for AMD RDNA3 (GFX11) graphics processors as it's necessary for proper SR-IOV support...
04:27
L.A. Riders Bail on Metro Trains Amid Horror of Deadly Drug Overdoses, Crime cryptogon.com
Via: Los Angeles Times: Drug use is rampant in the Metro system. Since January, 22 people have died on Metro buses and trains, mostly from suspected overdoses more people than all of 2022. Serious crimes such as robbery, rape and aggravated assault soared 24% last year compared with the previous. Horror. Thats []
04:18
Microsoft 365 Copilot: AI Assistant Integrated with Office Applications cryptogon.com
Via: IT Pro: Microsoft has integrated its AI technology into the entirety of the Microsoft 365 productivity suite, with businesses set to experience significant time savings with meetings. Named 365 Copilot, the AI helper is being added across the Office apps and can cut down time spent writing up meeting notes, combing through inboxes, and []
03:56
Polish MiG-29s to Ukraine cryptogon.com
Via: The Warzone: In the latest development in the saga of getting Polish Air Force MiG-29 Fulcrum fighter jets to Ukraine, the Polish president has confirmed that the first four examples will be handed over to Kyiv within the next few days. More MiGs will be transferred to Ukraine after that, Polish President Andrzej Duda []
03:29
Baidu Shares Fall After Ernie AI Chatbot Demo Disappoints SoylentNews
Shares of Baidu fell as much as 10 percent on Thursday after the web search company showed only a pre-recorded video of its AI chatbot Ernie in the first public release of China's answer to ChatGPT.
The Beijing-based tech company has claimed Ernie will remake its business and for weeks talked up plans to incorporate generative artificial intelligence into its search engine and other products.
But on Thursday, millions of people tuning in to the event were left with little idea of whether Baidu's chatbot could compete with ChatGPT.
[...]
"We can only explore by ourselves. Training ChatGPT took OpenAI more than a year, and it took them another year to tune GPT-4," said one Baidu employee. "It means we're two years behind."Baidu did not immediately respond to a request for comment.
Related:
The AI
Hype Bubble is the New Crypto Hype Bubble
DuckDuckGo's
New Wikipedia Summary Bot: "We Fully Expect It to Make
Mistakes"
LLM
ChatGPT Might Change the World, but Not in a Good Way
Alphabet
Stock Price Drops After Google Bard Launch Blunder
OpenAI
and Microsoft Announce Extended, Multi-Billion-Dollar
Partnership
Read more of this story at SoylentNews.
03:22
Confidential Pfizer Documents Reveal Pharmaceutical Giant Had Evidence Suggesting Increased Risk of Myocarditis Following COVID-19 Vaccinations in Early 2022 cryptogon.com
Via: Project Veritas: There is evidence that suggests patients who receive a COVID-19 vaccine are at an increased risk of myocarditis. Onset was typically within several days after mRNA COVID-19 vaccination (from Pfizer or Moderna), and cases have occurred more often after the second dose than the first dose. [PAGE 19] The []
03:01
Storing sensitive data using Podman secrets: Which method should you use? Linux.com
Podman supports two ways for storing sensitive data: using raw Podman secrets or creating Kubernetes secrets using Podman.
Read More at Enable Sysadmin
The post Storing sensitive data using Podman secrets: Which method should you use? appeared first on Linux.com.
03:00
Video Friday: Resilient Bugbots IEEE Spectrum

Video Friday is your weekly selection of awesome robotics
videos, collected by your friends at IEEE Spectrum
robotics. We also post a weekly calendar of upcoming robotics
events for the next few months. Please
send us your events for inclusion.
Robotics Summit & Expo: 1011 May 2023, BOSTON
ICRA 2023: 29 May2 June 2023, LONDON
RoboCup 2023: 410 July 2023, BORDEAUX, FRANCE
RSS 2023: 1014 July 2023, DAEGU, KOREA
IEEE RO-MAN 2023: 2831 August 2023, BUSAN, KOREA
CLAWAR 2023: 24 October 2023, FLORIANOPOLIS, BRAZIL
Humanoids 2023: 1214 December 2023, AUSTIN, TEXAS, USA
Enjoy todays videos!
Inspired by the hardiness of bumblebees, MIT researchers have developed repair techniques that enable a bug-sized aerial robot to sustain severe damage to the actuators, or artificial muscles, that power its wingsbut to still fly effectively.
[ MIT ]
This robot gripper is called DragonClaw, and do you really need to know anything else?
Alas, DragonClaw wins again!
[ AMTL ]
Heres a good argument for having legs on a robot:
...02:56
Minnesota Nuke Plant Admits To 400,000 Gallon Leak Of Radioactive Water cryptogon.com
Via: ZeroHedge: Minnesotans are wondering why state regulators waited months to inform the public that hundreds of thousands of gallons of radioactive water leaked from Xcel Energys Monticello nuclear power plant. Minnesota Department of Health released a statement Thursday about Xcels efforts to clean up 400,000 gallons of the water containing tritium that leaked from []
02:54
CDC Bought Phone Data to Monitor Americans Compliance With Lockdowns, Contracts Show cryptogon.com
Via: Epoch Times: The U.S. Centers for Disease Control and Prevention (CDC) purchased data from tracking companies to monitor compliance with lockdowns, according to contracts with the firms. The CDC paid one firm $420,000 and another $208,000. That bought access to location data from at least 55 million cellphone users. The contracts, approved under emergency []
02:49
France: Rioters Outside Macrons House After Forcing Through Retirement Age Increase Without Parliament Vote cryptogon.com
Via: Daily Mail: Rioters threatened the home of French president Emmanuel Macron after he bypassed parliament to raise the retirement age from 62 to 64. Thousands took to the streets across France last night to express their fury at the move, setting fires to property and fighting the police. The demonstrations in Paris, Lyon, Marseille []
02:45
ICC Judges Issue Arrest Warrant for Putin Over War Crimes in Ukraine cryptogon.com
Putin: Add it to the list. Via: Reuters: The International Criminal Court (ICC) issued an arrest warrant on Friday against Russian President Vladimir Putin, accusing him of being responsible for war crimes committed in Ukraine. Moscow has repeatedly denied accusations that its forces have committed atrocities during its one-year invasion of its neighbour. In its []
02:41
HinataBot, a new Go-Based DDoS botnet in the threat landscape Security Affairs
A new Golang-based DDoS botnet, tracked as HinataBot, targets routers and servers by exploiting known vulnerabilities.
Akamai researchers spotted a new DDoS Golang-based botnet, dubbed HinataBot, which has been observed exploiting known flaws to compromise routers and servers.
The experts reported that the HinataBot bot was seen being distributed since the beginning of 2023 and its operators are actively updating it.
The name Hinata comes after a character from the popular anime series, Naruto.
Akamais SIRT recently discovered the new bot within HTTP and SSH honeypots, it stood out due to its large size and the lack of specific identification around its newer hashes.
The sample captured by the experts abuses old vulnerabilities and weak credentials, the researchers reported that it attempts to exploit flaws in the miniigd SOAP service on Realtek SDK devices (CVE-2014-8361), Huawei HG532 routers (CVE-2017-17215), and exposed Hadoop YARN servers (CVE N/A).
HinataBot supports multiple methods of communication, including both dialing out and listening for incoming connections. The botnet can launch distributed denial-of-service (DDoS) flooding attacks that relies on protocols such as HTTP, UDP, TCP, and ICMP to send HTTP and UDP attacks.
Akamai said that by reverse engineering the bot and imitating the command and control (C2) server, was able to test the offensive capabilities of the botnet by running two attack methods (HTTP and UDP) in a 10-second period.

The http_flood generated 3.4 MB of packet capture data and pushed 20,430 HTTP requests. The request sizes ranged from 484 to 589 bytes per reque...
02:19
Free decryptor released for Conti-based ransomware following data leak Graham Cluley
Security researchers have released a new decryption tool which the Conti ransomware, helping them to recover their encrypted data for free. Read more in my article on the Tripwire State of Security blog.
02:09
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Ed Maste on Mar 17
All of tcsh's uses of TIOCSTI are in `#ifdef TIOCSTI` blocks so tcshshould still build and function with it removed (e.g., with the ioctl
renamed) I imagine.
01:54
Eight Graphs That Explain Software Engineering Salaries in 2023 IEEE Spectrum

Every year, online job search firms collect data about the salaries, skills, and overall job market for tech professionals, generally focusing on software engineers
The numbers from job search firms Dice and Hired have been released. These 2022 numbers have been eagerly anticipated, given the turmoil generated by a spate of tech layoffs in the latter part of the year, which Dice estimates at more than 140,000. The data they collect doesnt allow for apples-to-apples comparisons, but Ive read through both reports, pulled out data from past years to give the numbers some perspective when possible, and summarized it in eight charts. Dices numbers come from a survey administered to its registered job seekers and site visitors between 16 August 2022 and 17 October 2022, for a total of 7,098 completed surveys. Hireds analysis included data from 68,500 job candidates and 494,000 interview requests collected from the site between January 2021 through December 2022, supplemented by a survey of 1,300 software engineers.
Tech salaries jump, but dont keep up with inflation
According to Dices numbers, tech salaries grew 2.3 percent in 2022 compared with 2021, reflecting a steady upward trend since 2017 (with 2020 omitted due to the pandemic disruption). However, its clear that the 2022 news isnt so good when considering inflation. These numbers have been adjusted from those previously reported by IEEE Spectrum; Dice recently tightened its survey to focus on tech professionals in more tech-specific job functions.
Whats the best-paying job in tech?
If you want the highest pay, its a no-brainer: Get yourself into the C-suite. That is not, of course, a particularly useful takeaway from Dices data. Perhaps of more interest is that scrum masters are com...
01:53
Read "A First Course in Network Science", coauthored by our Filippo Menczer. Lifeboat News
Read "A First Course in Network Science", coauthored by our Filippo Menczer.
Networks are everywhere: networks of friends, transportation networks and the Web. Neurons in our brains and proteins within our bodies form networks that determine our intelligence and survival. This modern, accessible textbook introduces the basics of network science for a wide range of job sectors from management to marketing, from biology to engineering, and from neuroscience to the social sciences.01:48
Android phones can be hacked just by someone knowing your phone number Graham Cluley
Well, this isnt good. Google has issued a warning that some Android phones can be hacked remotely, without the intended victim having to click on anything.
01:36
Links 17/03/2023: Linux 6.2.7 and LibreSSL 3.7.1 Released Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
-
GNU/Linux
-
Desktop/Laptop
-
Liliputing System76 Meerkat mini Linux PC now available with up to Intel Core i7-1260P
While the design is similar for all models, models with newer processors tend to have slightly better specs. For example you get a Gigabit Ethernet port on Comet Lake systems, compared with 2.5 GbE Ethernet on Tiger Lake and Alder Lake models. The Alder Lake
-
-
01:30
Amazon Linux 2023 Is Running Well, Boosting EC2 Performance Over Amazon Linux 2 Phoronix
For those currently making use of Amazon Linux 2 (AL2) as the operating system for Elastic Compute Cloud (EC2) instances, the newly-released Amazon Linux 2023 (AL2023) is delivering some worthwhile speed-ups for maximizing your performance and value in their public cloud.
00:44
[$] Generic iterators for BPF LWN.net
BPF programs destined to be loaded into the kernel are generally written in C but, increasingly, the environment in which those programs run differs significantly from the C environment. The BPF virtual machine and associated verifier make a growing set of checks in an attempt to make BPF code safe to run. The proposed addition of an iterator mechanism to BPF highlights the kind of features that are being added as well as the constraints placed on programmers by BPF.
00:40
A Moon-forming Cataclysm Could Have Also Triggered Earths Plate Tectonics SoylentNews
The hypothesis could help in the search for other Earthlike worlds:
The leading explanation for the origin of the moon proposes that a Mars-sized planet, dubbed Theia, struck the nascent Earth, ejecting a cloud of debris into space that later coalesced into a satellite (SN: 3/2/18). New computer simulations suggest that purported remains of Theia deep inside the planet could have also triggered the onset of subduction, a hallmark of modern plate tectonics, geodynamicist Qian Yuan of Caltech reported March 13 at the Lunar and Planetary Science Conference.
[...] Many hypotheses have been proposed to explain the initiation of subduction, a tectonic process in which one plate slides under another (SN: 5/2/22; SN: 6/5/19; SN: 1/2/18). Yuan and his colleagues chose to focus on two continent-sized blobs of material in Earth's lower mantle known as large low-shear velocity provinces (SN: 5/12/16). These are regions through which seismic waves are known to move anomalously slow. Researchers had previously proposed these regions could have formed from old, subducted plates. But in 2021, Yuan and colleagues alternatively proposed that the mysterious masses could be the dense, sunken remnants of Theia.
[...] While the simulations suggest the large low-shear velocity provinces could have had a hand in starting subduction, it's not yet clear whether these masses came from Theia. "The features ... are a fairly recent discovery," says geodynamicist Laurent Montsi of the University of Maryland in College Park. "They're very fascinating structures, with a very unknown origin." As such, he says, it's too early to say that Theia triggered plate tectonics.
"It's provoking. This material down there is something special," Montsi says of the large low-shear velocity provinces. "But whether it has to be originally extraterrestrial, I don't think the case is made."
Journal Reference:
Q. Yuan. A giant
impact origin for the first subduction on Earth. Lunar
and Plan...
00:38
1xbet Bonus First Deposit Bonus 1xbet Bonus Account h+ Media
1xbet Bonus First Deposit Bonus 1xbet Bonus Account
However, as is with any bonus presents, there are phrases and circumstances hooked up to the 1xBet join provide. Sportsbooksto check out other betting websites and cool bonuses. Youve obtained no excuse to miss placing sports activities bets in your favourite bookmaker, even when your PC is at home. With the 1XBet app, you easily place bets on the go, straight from your smartphone.
This truth is especially essential for gamers, because the bookmaker offers a possibility to guess through the match and watch the event of events using on-line broadcasts. The degree of such packages is different, bettors like some of them, and others are significantly inferior to their counterparts. 1xBet app has acquired the greatest recognition updated.
The 1xBet promo code Bangladesh site offers fashionable and nice navigation, though some would possibly find the ergonomics a bit too heavy. But everything could be done quite rapidly 1xbet, and new users wont have bother getting acquainted with the positioning. If youre a newcomer, in case of registration, you will get a 1xBet bonus code, during your first deposit. This is a regular bonus of as much as 100 percent on a most quantity of 144$ . The store part is designed to retain 1xBet promo code for registration customers and allow them to redeem bonus points for free bets. The website precept is that every time prospects make bets, they accumulate bonus points.
Moreover, it could boast dozens of alternatives for bettors inside a certain sports activities betting or on line casino market. The bookmaker keeps on growing and bettering its service to obtain as many satisfied bettors as possible. They are also working onerous on making the standard greater striving for a similar objective to keep being one of the top betting platforms by all means. Consequently, 1xBet bd presents an web site that is user-friendly and accommodates the necessary information only. An choice, making it attainable to ship funds to a good friend, is one more service, which makes 1xBet bookmaker stand out from other companies out there.
We could possibly be grateful ought to you would give us more particulars about your experience. You can acquire 1xWin 100 laptop freed from cost and to enjoy the limitless bets immediately on your desktop. Otherwise, your bonus prizes could be taken away out of your account steadiness. 1xBet Sportsbook is a web-based bookmaker platform that accepts Canadian punters. The web site has been online since 2011 and has gained a robust following among punters seeking a dependable, easy-to-use sports actions gambling decision. The web site states that theyve over four hundred,000 bettors that use their companies, which is a large number of prospects by any requirements.
Just lately, Algeria played with Senegal, the place he acquir...
00:36
Watch "Using Data Science for Crisis Management and Response" with our David A. Bray. Lifeboat News
Watch "Using Data Science for Crisis Management and Response" with our David A. Bray.
00:31
Top 5 Insider Threats to Look Out For in 2023 Security Affairs
Unquestionably, insider threats is one of the most neglected aspects of cybersecurity and some companies fail to recognize associated dangers.
Cyberattacks are growing more complex as technology advances. Many businesses concentrate their cybersecurity efforts solely on external attacks, which leaves more openings for internal risks. Some companies fail to recognise the danger of losing confidential information owing to employee negligence or malice. Unquestionably, insider threats is one of the most neglected aspects of cybersecurity. According to statistics on insider threats, these threats may originate from employees, business contractors, or other reliable partners with simple access to your network. However, insider threat reports and recent developments have shown a sharp rise in the frequency of insider attacks. Because of these, cybersecurity professionals are now paying more attention to the detrimental effects of insider attacks.
In general, security experts need more confidence in their ability to identify and thwart insider threats successfully. 74% of respondents in an insider attack said their company was moderately to extremely vulnerable. 74% of respondentsa 6% increase from 2021also claim that insider threat assaults have become more regular. In 2022, 60% of respondents said they had an insider attack, while 8% said more than 20. Insider assaults are more challenging to identify and thwart than external attacks, according to 48% of respondents. It can be challenging for defences to distinguish between insider threats and regular user activity since insider threats employ genuine accounts, passwords, and IT technologies. Overall, insider threats are becoming a more significant threat. These findings imply that security teams should prepare for them in 2023.
Organisations must be able to address the risks from malicious insiders who intentionally steal sensitive data for personal reasons and users who can accidentally expose information due to negligence or simple mistakes.
Here are the top 5 threats security teams should look out for in 2023:
Employee Negligence
Employee carelessness or ignorance may result in unintentional data leaks, improper handling of sensitive information, or a failure to adhere to security policies and procedures. Negligence is to blame for more than two of every three insider incidents. Workers could not be cognizant of the possible hazards they bring to the company or might not prioritise security measures. They act carelessly, repeating passwords for personal and professional accounts or leaving flash drives wit...
00:21
Alpha Centauri: TOLIMAN Moves Forward Centauri Dreams Imagining and Planning Interstellar Exploration
The problem with Alpha Centauri is that the system is too close. I dont refer to its 4.3 light year distance from Sol, which makes these stars targets for future interstellar probes, but rather the distance of the two primary stars, Centauri A and B, from each other. The G-class Centauri A and K-class Centauri B orbit a common barycenter that takes them from a maximum of 35.6 AU to 11.2 AU during the roughly 80 year orbital period. That puts their average distance from each other at 23 AU.
So the average orbital distance here is a bit further than Uranus orbit of the Sun, while the closest approach takes the two stars almost as close as the Sun and Saturn. Habitable zone orbits are possible around both stars, making for interesting scenarios indeed, but finding out just how the system is populated with planets is not easy. Weve learned a great deal about Proxima Centauris planets, but teasing out a planetary signature from our data on Centauri A and B has been frustrating despite many attempts. Alpha Centauri Bb, announced in 2012, is no longer considered a valid detection.
But the work continues. I was pleased to see just the other day that Peter Tuthill (University of Sydney) is continuing to advance a mission called TOLIMAN, which weve discussed in earlier articles (citations below). The acronym here stands for Telescope for Orbit Locus Interferometric Monitoring of our Astronomical Neighborhood, a mission designed around astrometry and a small 30cm narrow-field telescope. The project has signed a contract with Sofia-based satellite and space services company EnduroSat, whose MicroSat technology can downlink data at 125+ Mbps, and if the mission goes as planned, there will be data aplenty.

Image: Alpha Centauri is our nearest star system, best known in the Southern Hemisphere as the bottom of the two pointers to the Southern Cross. The stars are seen here in optical and x-ray spectra. Source: NASA.
The technology here is quite interesting, and a departure from other astrometry missions. Astrometry is all about tracking the minute changes in the position of stars as they are affected by the gravitational pull of planets orbiting them, a series of angular displacements that can result in calculat...
00:00
What Is Teslas Mystery Magnet? IEEE Spectrum

Teslas investor day on 1 March began with a rambling, detailed discourse on energy and the environment before transitioning into a series of mostly predictable announcements and boasts. And then, out of nowhere, came an absolute bombshell: We have designed our next drive unit, which uses a permanent-magnet motor, to not use any rare-earth elements at all, declared Colin Campbell, Teslas director of power-train engineering.
It was a stunning disclosure that left most experts in permanent magnetism wary and perplexed. Alexander Gabay, a researcher at the University of Delaware, states flatly: I am skeptical that any non-rare-earth permanent magnet could be used in a synchronous traction motor in the near future. And at Uppsala University, in Sweden, Alena Vishina, a physicist, elaborates, Im not sure its possible to use only rare-earth-free materials to make a powerful and efficient motor.
The problem here is physics, which not even Tesla can alter.
And at a recent magnetics conference Ping Liu, a professor at the University of Texas, in Arlington, asked other researchers what they thought of Teslas announcement. No one fully understands this, he reports. (Tesla did not respond to an e-mail asking for elaboration of Campbells comment.)
Teslas technical prowess should never be underestimated. But on the other hand, the companyand in particular, its CEOhas a history of making sporadic sensational claims that dont pan out (were still waiting for that US $35,000 Model 3, for example).
The problem here is physics, which not even Tesla can alter. Permanent magnetism occurs in certain crystalline materials when the spins of electrons of some of the atoms in the crystal are forced to point in the same direction. The more of these aligned spins, the stronger the magnetism. For this, the ideal atoms are ones that have unpaired electrons swarming around the nucleus in what are known as...
Friday, 17 March
23:35
China-linked APT likely linked to Fortinet zero-day attacks Security Affairs
An alleged Chinese threat actor group is behind attacks on government organizations exploiting a Fortinet zero-day flaw (CVE-2022-41328).
A suspected China-linked group is exploiting a Fortinet zero-day vulnerability, tracked as CVE-2022-41328, in attacks aimed at government organizations.
A few days ago, Fortinet researchers warned of an advanced threat actor that is targeting governmental or government-related entities.
The unknown threat actor is exploiting a vulnerability in Fortinet FortiOS software, tracked as CVE-2022-41328, that may allow a privileged attacker to read and write arbitrary files via crafted CLI commands.
The CVE-2022-41328 vulnerability (CVSS score: 6.5) is a path traversal issue in FortiOS can can result in arbitrary code execution.
A improper limitation of a pathname to a restricted directory vulnerability (path traversal) [CWE-22] in FortiOS may allow a privileged attacker to read and write arbitrary files via crafted CLI commands. reads the advisory published by Fortinet.
The vulnerability impacts FortiOS versions 6.0, 6.2, 6.4.0 through 6.4.11, 7.0.0 through 7.0.9, and 7.2.0 through 7.2.3. The company addressed the vulnerability with the release of versions 6.4.12, 7.0.10, and 7.2.4 respectively.
Fortinet launched an investigation into the attacks after the FortiGate devices of one customer suddenly halted and failed to reboot. The devices halted displaying the following error message:
System enters error-mode due to FIPS error: Firmware Integrity self-test failed
The failure of the integrity test blocks the reboot of the device to protect the integrity of the network.
Mandiant researchers linked a series of attacks that took place in mid-2022 to a China-linked threat actor tracked as UNC3886 by the security firm.
a suspected China-nexus threat actor likely already had access to victim environments, and then deployed backdoors onto Fortinet and VMware solutions as a means of maintaining persistent access to the environments. reads the report published by Mandiant. This involved the use of a local zero-day vulnerability in FortiOS (CVE-2022-413...
23:28
Samsung, Vivo, Google phones open to remote compromise without user interaction Help Net Security
Several vulnerabilities in Samsungs Exynos chipsets may allow attackers to remotely compromise specific Samsung Galaxy, Vivo and Google Pixel mobile phones with no user interaction. With limited additional research and development, we believe that skilled attackers would be able to quickly create an operational exploit to compromise affected devices silently and remotely, Google Project Zero researchers have noted. Therefore, they decided to go public before before the end of their usual 90-day non-disclosure deadline and More
The post Samsung, Vivo, Google phones open to remote compromise without user interaction appeared first on Help Net Security.
23:07
New GoLang-Based HinataBot Exploiting Router and Server Flaws for DDoS Attacks The Hacker News
A new Golang-based botnet dubbed HinataBot has been observed to leverage known flaws to compromise routers and servers and use them to stage distributed denial-of-service (DDoS) attacks. "The malware binaries appear to have been named by the malware author after a character from the popular anime series, Naruto, with file name structures such as 'Hinata--,'" Akamai said in a
23:04
23:02
HeheStreams IPTV Admin Sentenced to Three Years in Prison, $3m Restitution TorrentFreak
 Focusing on MLB, NBA, NFL, and NHL content, Hehestreams
was no ordinary IPTV service.
Focusing on MLB, NBA, NFL, and NHL content, Hehestreams
was no ordinary IPTV service.
Instead of copied streams, captured from broadcasts, HeheStreams users were directed to genuine streams offered by sports broadcasters.
On one hand, that meant that HeheStreams didnt run up huge server bills. On the other, streams were as reliable as any official stream, because they were official streams.
After being noticed by the Alliance for Creativity and Entertainment, HeheStreams shut down mid 2021. A settlement agreement was reached but the terms remain confidential.
Bug Bounty Deal Gone Bad
When TorrentFreak reached out to Streit in the summer of 2021, he informed us that some official services had vulnerabilities. (Update: Specifically, MLBs ticket inventory was being available for anyone, which was fully disclosed). He informed us that hed been in discussion with one or more providers about disclosure.
A subsequent criminal complaint filed by the US Government confirmed that Streit had been in talks with MLB. Vulnerabilities were disclosed to the baseball organization and when Streit indicated that he should be paid for his work, the MLB asked for a specific amount. Streit indicated his work was worth $150K but was also informed there was no bug bounty program at the baseball league.
An FBI agent later wrote that Streit had indeed made an approach and presented as helpful. However, he concluded that a simultaneous intrusion and illegal streaming of MLB content via HeheStreams indicated that the intent was to extort MLB.
Charged With Several Crimes, Pleaded Guilty to One
In October 2021, the Department of Justice charged then 30-year-old Streit with several crimes; accessing a protected computer in furtherance of a criminal act for financial gain, accessing a protected computer in furtherance of fraud, wire fraud, sending interstate threats, and illicit digital transmission.
After consulting with his attorney, Streit concluded that signing a plea deal was the most sensible course of action. The Minnesota man...
22:55
Security updates for Friday LWN.net
Security updates have been issued by Debian (sox and thunderbird), Fedora (containerd, libtpms, mingw-binutils, mingw-LibRaw, mingw-python-werkzeug, stargz-snapshotter, and tkimg), Slackware (mozilla and openssh), SUSE (apache2, firefox, hdf5, jakarta-commons-fileupload, kernel, perl-Net-Server, python-PyJWT, qemu, and vim), and Ubuntu (abcm2ps, krb5, and linux-intel-iotg).
22:22
GNU/Linux in Honduras: 10% Market Share? (Updated) Techrights
As per the latest statistics
Update: Psydroid has just pointed out (in IRC) that in the United States (US) ChromeOS + GNU/Linux have a market share greater than 10% and Windows is installed on barely half of laptops/desktops. ChromeOS is technically GNU/Linux with lots of malware preloaded, but its still a kind of Gentoo and thus its fair to say that in the US the share of GNU/Linux is now about 10% or more. If one counts Android too (Android is powered by Linux), then Linux almost has majority market share in the US.
22:00
Virgin Orbit Pauses Operations, Seeks Funding Hackaday

It looks as though things may have gone from bad to worse at Virgin Orbit, the satellite carrying spin-off of Richard Bransons space tourism company Virgin Galactic. After a disappointing launch failure earlier in the year, CNBC is now reporting the company will halt operations and furlough most employees for at least a week as it seeks new funding.
Its no secret that company has struggled to find its footing since it was formed in 2017. On paper, it was an obvious venture Virgin Galactic already had the White Knight Two carrier aircraft and put plenty of R&D into air-launched rockets, it would simply be a matter of swapping the crewed SpaceShipTwo vehicle for the LauncherOne orbital booster. But upgrades to the rocket eventually made it too large for the existing carrier aircraft, so the company instead purchased a Boeing 747 and modified it to lift their two-stage rocket out of the thick lower atmosphere.
22:00
Still Have A Use For Adobe Flash? Ruffle Is Working To Safely Emulate It In Rust Phoronix
While Adobe Flash is officially -- and thankfully -- dead, those interested in Adobe Flash Player for nostalgia or archival purposes, Ruffle is working to emulate Adobe Flash support via this open-source project making use of the Rust programming language...
21:54
Tiny Data Center Makes for a Comfortable Swim SoylentNews
Tiny data center makes for a comfortable swim:
A data center about the size of a washing machine is being used to heat a public swimming pool in England.
Data centers' servers generate heat as they operate, and interest is growing in finding ways to harness it to cut energy costs and offset carbon emissions.
In this latest example, the computing technology has been placed inside a white box and surrounded by oil, which captures the heat before being pumped into a heat exchanger, according to a BBC report.
The setup is effective enough to heat a council-run swimming pool in Exmouth, about 150 miles west of London, to about 86 degrees Fahrenheit (30 degrees Celsius) for about 60% of the time, saving the operator thousands of dollars. And with energy costs rising sharply in the U.K., and councils looking for ways to save money, an initiative like this could be the difference between the pool staying open and closing down.
Behind the idea is U.K.-based tech startup Deep Green. In exchange for hosting its kit, Deep Green installs free digital boilers at pools and pays for the energy that they use. Meanwhile, tech firms pay Deep Green to use its computing power for various artificial intelligence and machine learning projects.
Related:
Commercial
Underwater Datacenter Goes Online This Year
Microsoft's
Underwater Server Experiment Resurfaces After Two Years
Heating
Homes and Businesses with "Data Furnaces"
Read more of this story at SoylentNews.
21:51
Links 17/03/2023: Update on John Deeres Ongoing GPL Violations and PyTorch 2.0 Techrights
![]()
Contents
-
GNU/Linux
-
Server
-
Amazon Amazon Linux 2023, a Cloud-Optimized Linux Distribution with Long-Term Support
I am excited to announce the general availability of Amazon Linux 2023 (AL2023). AWS has provided you wit...
-
-
21:51
Intel Thunder Bay Is Officially Canceled, Linux Driver Code To Be Removed Phoronix
I hadn't heard any mentions of Intel's Thunder Bay in quite a while besides the occasional Linux kernel patch while now it has been officially confirmed as a cancelled Intel product and the Linux driver code being worked on the past 2+ years is on the chopping block...
21:50
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Hanno Bck on Mar 17
This is interesting.Given this works only on "virtual terminals" (aka not in a terminal
window on X, not over SSH), I think the severity is much lower than the
TIOCSTI issue. Still it should be fixed.
I've created a patch for the Linux kernel very similar to the patch
that allows disabling TIOCSTI. I'll send that to the kernel devs soon,
but maybe people here want to test and comment.
---
drivers/tty/Kconfig | 16...
21:46
A New Security Category Addresses Web-borne Threats The Hacker News
In the modern corporate IT environment, which relies on cloud connectivity, global connections and large volumes of data, the browser is now the most important work interface. The browser connects employees to managed resources, devices to the web, and the on-prem environment to the cloud one. Yet, and probably unsurprisingly, this browser prominence has significantly increased the number of
21:43
Intel Prepares More Graphics Driver Code For Linux 6.4 Phoronix
Last week following the Linux 6.3-rc1 release Intel engineers already began sending new Intel i915 driver feature code to DRM-Next for queuing until the Linux 6.4 merge window in early May. This week another batch of "drm-intel-gt-next" material was submitted...
21:22
Lookalike Telegram and WhatsApp Websites Distributing Cryptocurrency Stealing Malware The Hacker News
Copycat websites for instant messaging apps like Telegram and WhatApp are being used to distribute trojanized versions and infect Android and Windows users with cryptocurrency clipper malware. "All of them are after victims' cryptocurrency funds, with several targeting cryptocurrency wallets," ESET researchers Luk tefanko and Peter Strek said in a new analysis. While the first instance of
21:02
flatpak: CVE-2023-28101: escape characters in metadata can hide app permissions in terminal Open Source Security
Posted by Simon McVittie on Mar 17
https://github.com/flatpak/flatpak/security/advisories/GHSA-h43h-fwqx-mpp8Vulnerable: all < 1.10.8, 1.12.x < 1.12.8, 1.14.x < 1.14.4, 1.15.x < 1.15.4
Fixed: 1.15.4, 1.14.x >= 1.14.4, 1.12.x >= 1.12.8, 1.10.x >= 1.10.8
Flatpak is a system for building, distributing, and running sandboxed
desktop applications on Linux.
When installing or upgrading a Flatpak app using the flatpak(1) CLI,
the user is normally shown any special...
20:59
flatpak: CVE-2023-28100: TIOCLINUX can send commands outside sandbox if running on a virtual console Open Source Security
Posted by Simon McVittie on Mar 17
https://github.com/flatpak/flatpak/security/advisories/GHSA-7qpw-3vjv-xrqpVulnerable: all < 1.10.8, 1.12.x < 1.12.8, 1.14.x < 1.14.4, 1.15.x < 1.15.4
Fixed: 1.15.4, 1.14.x >= 1.14.4, 1.12.x >= 1.12.8, 1.10.x >= 1.10.8
Flatpak is a system for building, distributing, and running sandboxed
desktop applications on Linux.
Jakub Wilk mentioned on the oss-security mailing list that various
projects' mitigations for the...
20:48
Codon Looks Very Promising For Super-Fast Python Code Phoronix
While there is Pyston, PyPy, and various other alternative Python implementations being done in the name of performance, Codon is one of the newer ones and is talking up 10~100x faster performance...
20:27
Debian 12 "Bookworm" Enters Its Hard Freeze Phoronix
Following last month's soft freeze for Debian 12 "Bookworm", this popular Linux distribution is now in its hard freeze until its release time...
19:07
Qualcomm Tries to Kick Holes in EU 242 Million Decision SoylentNews
Hopes to avoid paying up for crushing a rival while helping Huawei and ZTE to prosper:
Qualcomm on Monday began an attempt to convince the European Union's Court of Justice that it should not pay a 242 million ($258 million) fine imposed on it for anti-competitive behavior.
The fine worth about two percent of Qualcomm's 2022 profits was levied against the US chipmaker in 2019. At the time, the European Commission found that Qualcomm had sold 3G baseband chipsets at a loss to harm British rival Icera's ability to compete.
[...] In order to prevent Nvidia-controlled Icera from claiming a larger slice of the market, the European Commission says Qualcomm began selling its UMTS chipsets to the likes of Huawei and ZTE at prices its rival couldn't match.
[...] The European Commission ultimately smacked Qualcomm with a 242 million fine for its behavior. As Qualcomm's profits reached $12.9 billion last year, the fine is significant but not very damaging.
Qualcomm is nevertheless trying to avoid paying the fine. In court Monday, Reuters reports that Qualcomm Attorney, Miguel Rato claimed the European Commission was on a "crusade" against the company. Rato also called into question the basis for the Commission's argument, arguing the specific market for 3G baseband chips accounted for less than a percent of the overall UMTS market at the time.
[...] Despite handing down several billion-dollar-plus fines for anticompetitive behavior over the past few years, the European Commission hasn't had great luck getting them to stick.
Intel escaped a $1.2 billion antitrust fine imposed by Brussels for offering hardware partners rebates for its x86 processors. Chipzilla even bribed German electronics retailer Media Saturn Holding to ensure it did not sell rival AMD's parts.
But after a years-long legal battle, Intel overturned the penalty and was told it didn't have to pay. To add insult to injury, Intel returned to court last spring demanding that the EU pay 593m ($623.5m) in interest charges.
Read more of this story at SoylentNews.
19:00
Fish Tank Dosing Pump Built Using Pi Pico Hackaday

When youre maintaining a fish tank, its actually quite important to get all your basic chemistry right. Mismanage things, and youll kill all the helpful bacteria in the tank, or kill your fish when things get too alkaline or too acidic. To help him get things just right, [yojoebosolo] built a custom dosing pump to maintain his fishtank.
The pumps themselves are small peristaltic pumps sourced from AliExpress. They can be had for under $10 if you look hard enough. Two of these are assembled into a PLA housing. Meanwhile, the brains of the operation is a Raspberry Pi Pico. Its charged with running the pumps to a regular schedule, ensuring that just the right amount of chemicals are delivered when they are needed. It delivers 2 mL of Kalkwasser solution into [yojoebosolos] reef tank every ten minutes. The pumps are switched on and off with a simple 5V relay.
If youve got a delicate and complex fish tank that demands only the best, building your own dosing pump may be the way to go. Off-the-shelf versions can be expensive, after all, so sometimes it makes sense to...
18:41
Premier Wager
All cash prize amounts are displayed in-game within the foreign money youre playing with. The Prize pool and minimal guess for these tournaments are set up in EUR or USD and could be subject settled exterior the promotional interval is not going to depend in the course of this promotion. We reserve the right to withdraw and/or change these promotional phrases and circumstances at our sole discretion, and any decision with regard to the winnings supplied.
Points acquired are summed up all through the Tournament interval. The leaderboards are updated in real time and players can view the true time leaderboard in sport at any time of their own selecting when enjoying the participating sport 1xbett.com. The Spinomenal Leaderboard will refresh up to every four minutes .
Any qualifying bet in participating video games through the promotion period can set off a prize from the prize pool. Players will accumulate factors to maneuver up the Leaderboards and win cash prizes. Each win rewards you with a score primarily based on the win multiplier (for example, when you waged K17.50 and won K175, you could be rewarded with 10 points).
The minimal qualifying bet per spin to have the ability to take part within the tournaments is K1.75. If the minimal wager amount is unavailable, will in all probability be rounded as a lot as the next higher obtainable guess dimension within the game. We further reserve the proper to not pay the cash prizes the place, in our opinion, all or part of the rating results from cheating or collusion with other players.
18:40
Premier Bet
The minimum qualifying bet per spin so as to participate within the tournaments is K1.75. If the minimum bet quantity is unavailable, it goes to be rounded as much as the following higher out there guess measurement within the sport. We further reserve the proper to not pay the cash prizes the place, in our opinion, all or a half of the score outcomes from dishonest or collusion with other gamers.
All money prize quantities are displayed in-game within the forex youre playing with. The Prize pool and minimum guess for these tournaments are arrange in EUR or USD and may be topic to outdoors the promotional period will not depend towards this promotion. We reserve the proper to withdraw and/or change these promotional phrases and circumstances at our sole discretion, and any determination with regard to the winnings supplied.
Points obtained are summed up all through the Tournament period. The leaderboards are up to date in actual time and gamers can view the real time leaderboard in recreation at any time of their very own choosing when enjoying the collaborating recreation. The Spinomenal Leaderboard will refresh as a lot as each four minutes .
Any qualifying wager in participating games through the promotion period can trigger a prize from the prize pool. Players will accumulate points to move up the Leaderboards and win cash prizes. Each win rewards you with a rating based mostly on the win multiplier (for example, should you waged K17.50 and won K175, youll be rewarded with 10 bahis liqas istifad etmk n tlimatlar points).
18:38
Premier Bet
All cash prize amounts are displayed in-game within the currency you are enjoying with. The Prize pool and minimum wager for these tournaments are arrange in EUR or USD and 1xbet1 could be subject to forex conversion fluctuations. Any wagers positioned and settled outside the promotional interval is not going to depend towards this promotion. We reserve the proper to withdraw and/or change these promotional phrases and situations at our sole discretion, and any decision with regard to the winnings provided.
The minimal qualifying wager per spin in order to take part in the tournaments is K1.seventy five. If the minimal bet quantity is unavailable, it goes to be rounded as a lot as the next higher obtainable bet size in the sport. We further reserve the best to not pay the cash prizes the place, in our opinion, all or part of the rating results from dishonest or collusion with other players.
Points obtained are summed up all through the Tournament period. The leaderboards are up to date in actual time and players can view the real time leaderboard in sport at any time of their own choosing when taking part in the participating sport. The Spinomenal Leaderboard will refresh up to every four minutes .
Any qualifying wager in participating games through the promotion period can set off a prize from the prize pool. Players will accumulate points to maneuver up the Leaderboards and win money prizes. Each win rewards you with a rating primarily based on the win multiplier (for example, should you waged K17.50 and gained K175, you will be rewarded with 10 points).
18:28
IRC Proceedings: Thursday, March 16, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-160323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-160323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-160323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-160323.gmi
Over HTTP:
|
... |
18:06
Winter Vivern APT Group Targeting Indian, Lithuanian, Slovakian, and Vatican Officials The Hacker News
The advanced persistent threat known as Winter Vivern has been linked to campaigns targeting government officials in India, Lithuania, Slovakia, and the Vatican since 2021. The activity targeted Polish government agencies, the Ukraine Ministry of Foreign Affairs, the Italy Ministry of Foreign Affairs, and individuals within the Indian government, SentinelOne said in a report shared with The
18:00
Natural Immunity Is as Protective as COVID Jab Terra Forming Terra
Secret Pfizer & Government Documents reveal Millions Dying Suddenly Terra Forming Terra

Not quite AIDS ,but same profile and worse, it is not getting better. What i am saying is that if 1.8 million diedover the past two years, will 1.8 million die in the next two years.
If that actually happens, or god forbid, we see a a steady increase, then the real event will be a slow creeping AIDS like pandemic where folks die from any damn infection.
If 4,000,000,000 are infected, then we will see the 4,000,000,000 reported to me from the other side. At least the path is now clearer.
Death stalks mRNA vaccination in New Zealand Terra Forming Terra
Here we are. the increased death rate has not let up and may be accelerating as of a few short weeks ago. Everyone is hiding the data or certainly obscuring it.
We are certainly looking at weakened immune systems generally just like AIDS and whatever else may have been thrown in.
17:53
Google Uncovers 18 Severe Security Vulnerabilities in Samsung Exynos Chips The Hacker News
Google is calling attention to a set of severe security flaws in Samsung's Exynos chips, some of which could be exploited remotely to completely compromise a phone without requiring any user interaction. The 18 zero-day vulnerabilities affect a wide range of Android smartphones from Samsung, Vivo, Google, wearables using the Exynos W920 chipset, and vehicles equipped with the Exynos Auto T5123
17:51
RMS: A Tour of Malicious Software, With a Typical Cell Phone as Example Techrights
Summary: Tonight in Europe or this afternoon in America Richard M. Stallman (RMS), who turned 70 yesterday, gives a talk
The Free Software Foundation (FSF) is hosting a talk by Richard M. Stallman on March 17, 2023 at 15:00 EDT (19:00 UTC).
| When |
Mar 17, 2023 from |
|---|---|
| Contact Name | Miriam Bastian |
The Free Software Foundation (FSF) is hosting a talk by Richard M. Stallman (RMS) on March 17, 2023 from 15:00 to 16:15 EDT (19:00 20:15 UTC) in Somerville, MA. Since LibrePlanet will take place on the following two days (March 18 and 19), we hope that youll be in town. We have a limited amount of space for an in-person audience, so please sign up today if youd like to see this talk in person.
The talk is entitled A tour of malicious software, with a typical cell phone as example. Richard Stallman will be speaking about the free software movement and your freedom. His speech will be nontechnical, admission is gratis, and the public is encouraged to attend online. We will also broadcast the talk at fsf.org/live. Remote attendees can ask questions in the #fsf channel of the Libera.chat IRC network.
Details to the in-person event will be shared upon registration. Please note that in-person attendees will be required to wear a mask, and other mandatory coronavirus precautions may be put in place prior to the event.
If you have any questions about the event itself, please write campaigns@fsf.org.
More information about this event
This work is licensed under a Creative Commons Attribution-No Derivative Works 3.0 license (or later version) Why this license?
17:30
SVB account holders targeted with phishing, scams Help Net Security
After news broke late last week about Silicon Valley Banks bank run and collapse, security researchers started warning SVB account holders about incoming SVB-related scams and phishing attempts. Another reminder: just because caller ID says FDIC, SVB, or a phone number you trust, it doesnt mean the call is for sure legit. Caller ID can be spoofed we can make caller ID display any phone number when placing a call. Use another method of More
The post SVB account holders targeted with phishing, scams appeared first on Help Net Security.
17:03
OSI Email Mistake Could Affect Election Results FOSS Force
A seemingly unintentional factual error in a get-out-the-vote email sent by Open Source Initiative to its members could result in some members waiting until after the polls close to vote in the organizations current board of directors election.
The post OSI Email Mistake Could Affect Election Results appeared first on FOSS Force.
17:00
How healthcare CISOs can automate cloud security controls Help Net Security
Cloud environments provide many benefits, primarily involving their ease of scalability and resilience. Those qualities exist because of automation and the easy and straightforward way to leverage that to enhance a cloud environment. While that ease through automation can have drawbacksand if youve ever gotten a surprise bill from your cloud provider you know those drawbacks acutelyit can be leveraged for great economies of scale. One place that automation is a huge boon is in More
The post How healthcare CISOs can automate cloud security controls appeared first on Help Net Security.
16:30
New infosec products of the week: March 17, 2023 Help Net Security
Heres a look at the most interesting products from the past week, featuring releases from Atakama, Elevate Security, Hornetsecurity, HYPR, and ReversingLabs. Hornetsecurity VM Backup V9 protects users against ransomware threats VM Backup V9 has an easy-to-use, intuitive interface that gives individuals full control, allowing them to monitor and manage all Hyper-V and VMware VMs from a single console. V9 can now handle larger infrastructure setups. Its overhauled backup repository optimises disk space, ensuring more More
The post New infosec products of the week: March 17, 2023 appeared first on Help Net Security.
16:24
James Webb Space Telescope Captures a Star Going Supernova in Unprecedented Detail SoylentNews
JWST will help scientists investigate the troublesome dust budget surplus of the universe:
NASA released a new image captured by the James Webb Space Telescope (JWST), which depicts a star named "WR 124" that is located 15,000 light years away from Earth, in the Sagittarius constellation. WR 124 is a Wolf Rayet-type star, a rare kind of star which is among the most luminous, most massive, and most briefly detectable stars known, NASA explained.
WR 124 was actually one of the first observations made by JWST in June 2022, the space agency said, but the image has been unveiled just now. The Wolf-Rayet phase is a brief condition some stars go through during their lifetime before turning into supernovae, which makes Webb's observations a valuable asset to astronomers studying the life of stars.
WR 124 is 30 times the mass of our Sun, NASA said, and it has "shed" 10 Suns' worth of material so far. The ejected gas moves away from the central body and cools down, forming cosmic dust and glowing in the infrared light that is detectable by Webb's advanced instruments.
[...] Before Webb, astronomers investigating cosmic dust simply had no way to capture detailed images and information about a dust-rich environment like the WR 124 nebula. And dust, NASA said, plays an essential role in the inner working of the universe as it shelters forming stars, and gathers together to help shape planets, molecules and even the building blocks of life on Earth.
Dust is a fundamental element for our universe, and yet scientists still have to explain why the universe seemingly contains more dust than our current dust-formation theories can justify. The universe is "operating with a dust budget surplus," NASA remarked.
Released NASA picture, and a 30-second video panning across the image.
Read more of this story at SoylentNews.
16:22
Study uncovers the fundamental mechanisms underlying the formation of polarons in 2D atomic crystals Lifeboat News: The Blog
Polarons are localized quasiparticles that result from the interaction between fermionic particles and bosonic fields. Specifically, polarons are formed when individual electrons in crystals distort their surrounding atomic lattice, producing composite objects that behave more like a massive particles than electron waves.
Feliciano Giustino and Weng Hong Sio, two researchers at the University of Texas at Austin, recently carried out a study investigating the processes underpinning the formation of polarons in 2D materials. Their paper, published in Nature Physics, outlines some fundamental mechanisms associated with these particles formation that had not been identified in previous works.
Back in 2019, we developed a new theoretical and computational framework to study polarons, Feliciano Giustino, one of the researchers who carried out the study, told Phys.org. One thing that caught our attention is that many experimental papers discuss polarons in 3D bulk materials, but we could find only a couple of papers reporting observations of these particles in 2D. So, we were wondering whether this is just a coincidence, or else polarons in 2D are more rare or more elusive than in 3D, and our recent paper addresses this question.
16:22
Observations investigate long-term behavior of gamma-ray blazar PKS 0402362 Lifeboat News: The Blog
Indian astronomers have analyzed observational data of a gamma-ray blazar known as PKS 0402362, collected in the timespan of nearly 13 years. The study, published March 7 in the Monthly Notices of the Royal Astronomical Society, provides crucial information regarding the long-term behavior of this blazar.
Blazars are very compact quasars associated with supermassive black holes (SMBHs) at the centers of active, giant elliptical galaxies. They belong to a larger group of active galaxies that host active galactic nuclei (AGN), and are the most numerous extragalactic gamma-ray sources. Their characteristic features are relativistic jets pointed almost exactly toward the Earth.
Based on their optical emission properties, astronomers divide blazars into two classes: flat-spectrum radio quasars (FSRQs) that feature prominent and broad optical emission lines, and BL Lacertae objects (BL Lacs), which do not.
16:22
A new approach to measuring and understanding multidirectional polarization Lifeboat News: The Blog
Germany, India, Mexico, and Spain. As multiparty democracies, these countries present a more complex picture of what brings people togetheror divides them. Using social media data, a group of researchers proposes a novel approach to measuring polarization in nations with multiple political parties.
Complexity Science Hub scientist Samuel Martn-Gutirrez and his colleagues developed a model that infers opinions from social networks, and measures the left-right political division, as well as other more nuanced sources of tension. They analyzed Twitter data from the Spanish elections of 2015 and 2019.
Its important to understand polarization in our society, and our findings shed new light on how political beliefs are shaped, says Martn-Gutirrez. Our approach can lead to useful insights when applied to real-world debates happening on social media.
16:22
Hot topic: How heat flow affects the Earths magnetic field Lifeboat News: The Blog
Compass readings that do not show the direction of true north and interference with the operations of satellites are a few of the problems caused by peculiarities of the Earths magnetic field.
The magnetic field radiates around the world and far into space, but it is set by processes that happen deep within the Earths core, where temperatures exceed 5,000 degrees Celsius.
New research from geophysicists at the University of Leeds suggests that the way this super-hot core is cooled is key to understanding the causes of the peculiaritiesor anomalies, as scientists call themof the Earths magnetic field.
16:00
How ChatGPT is changing the cybersecurity game Help Net Security
The cybersecurity industry can leverage GPT-3 potential as a co-pilot to help defeat attackers, according to Sophos. The latest report details projects developed by Sophos X-Ops using GPT-3s large language models to simplify the search for malicious activity in datasets from security software, more accurately filter spam, and speed up analysis of living off the land binary (LOLBin) attacks. Since OpenAI unveiled ChatGPT back in November, the security community has largely focused on the potential More
The post How ChatGPT is changing the cybersecurity game appeared first on Help Net Security.
16:00
Coffee Grinder Gets Bluetooth Weighing Hackaday

Some people take their coffee grinding seriously. So what do you do when the hot new grinders automatically weigh coffee, and yours doesnt? Well, if you are like [Tech Dregs] and the rest of us, you hack your existing grinder, of course. The link is to the source code, but for a quick overview, check out the video below.
In true hacker fashion, the first order of business was to pull a load cell out of a cheap scale. Originally, he intended to reuse the processor inside, too, but it was epoxied, so it was a good excuse to use some more modules. A load cell amplifier, an OLED display, and a tiny Xiao processor, which he describes as ridiculous. From the context, we think he means ridiculously small in the physical sense and ridiculously powerful for such a tiny board.
With the modules, the wiring wasnt too hard, but you still need some kind of app. Thanks to App Inventor, an Android app was a matter of gluing some blocks together in a GUI. Of course, the devil is in the details, and it took a lot of focused cursing to get everything working correctly.
The coffee grinder has a relay to turn the motor on and off, so thats the point the scale needs to turn the motor on and off. Conveniently, the grinders PCB had an unpopulated pin header for just this purpose.
This is one of those simple projects you can use daily if you drink coffee. We are always impressed that the infrastructure exists today and th...
15:30
Most security pros turn to unauthorized AI tools at work Help Net Security
Security experts are increasingly resorting to unauthorized AI tools, possibly because they are unhappy with the level of automation implemented in their organizations security operation centers (SOCs), according to a study conducted by Wakefield Research. The research demonstrates that embracing automation in cybersecurity leads to significant business benefits, such as addressing talent gaps and effectively combating cyber threats. According to the survey, organizations will continue investing in cybersecurity automation in 2023, even amid economic turbulence. More
The post Most security pros turn to unauthorized AI tools at work appeared first on Help Net Security.
15:00
Tracking the global spread of malware Help Net Security
Approximately 10-16 percent of organizations have shown evidence of malicious command and control (C2) activities, strongly indicating a network breach within the last year, according to Akamai. Emotet and QSnatch Akamai observes nearly seven trillion DNS requests daily and classifies malicious DNS transactions into three main categories: malware, phishing and command and C2. These attacks present a major threat to both enterprises and home users. They analyzed malicious DNS data and linked attackers to malware More
The post Tracking the global spread of malware appeared first on Help Net Security.
14:30
Elevate Identity enables security teams to automate customization of conditional access policies Help Net Security
Elevate Security has released Elevate Identity, its SaaS offering for Identity and Access Management (IAM) Professionals that integrates Elevates user risk profiling capability with IAM tools such as Cisco Duo, Crowdstrike Falcon, and Microsoft Azure AD to add a full 360 perspective of each individuals cyber risk to the authentication and authorization process. Additionally, the Elevate Identity service integrates with Identity Governance tools such as Sailpoints Identity Security Platform to automate personalized access reviews based More
The post Elevate Identity enables security teams to automate customization of conditional access policies appeared first on Help Net Security.
14:25
BIgIDs secrets detection capabilities reduce risk from potential data breaches and leaks Help Net Security
BigID has introduced purpose-built AI and ML-based data discovery and classification capabilities designed to detect secrets across enterprise data and reduce risk from potential data breaches and leaks. Secrets including as API keys, tokens, usernames and passwords, and security certificates are commonly shared, cloned, and distributed across enterprise data environments as a means for better collaboration and efficiency. Unfortunately, the proliferation of secrets across these environments increases the attack surface and quickly raises More
The post BIgIDs secrets detection capabilities reduce risk from potential data breaches and leaks appeared first on Help Net Security.
14:23
Understanding how exercise induces systemic metabolic benefits Lifeboat News: The Blog
Northwestern Medicine scientists have uncovered a mechanism by which exercise activates metabolic benefits in the body, according to a new study published in Cell Metabolism.
Its well known that exercise elicits many health benefits. However, how this is accomplished is not yet well understood. During exercise, autophagy, the bodys cellular recycling system that allows old or damaged cellular structures to be broken down, is activated in both contracting muscles and various non-contracting organs, such as the liver.
In the study, investigators performed proteomic analyses on the blood of mice before and after exercise. They identified a protein secreted from contracting muscle, FN1, which significantly increased in the plasma and serum of mice after exercise.
14:23
How to manage the fear of cancer recurrence Lifeboat News: The Blog
Even if youre in remission or you show no evidence of disease, you may still have fears that cancer may return. We spoke with our social work counselors to learn more about fear of recurrence and get advice on how to manage it.
14:20
Dells new security offerings help enterprises secure their devices, systems and clouds Help Net Security
Dell Technologies has unveiled new security services and solutions to help organizations protect against threats, respond to attacks and secure their devices, systems and clouds. Seventy-two percent of IT business leaders and professionals believe the changing working world exposes their organization to even greater risk. The highly distributed IT environment creates new opportunities for cybercriminals and requires organizations to transform their approach to securing and recovering their data and systems. Dells new security offerings help More
The post Dells new security offerings help enterprises secure their devices, systems and clouds appeared first on Help Net Security.
13:44
Speaking to NOW: Pensions About a Corrupt Employer schestowitz.com
Video
download link | md5sum
9dcf3def0c8beb1a166c52b5ded8b299
Chatting to the Pension Boss About Sirius
Creative Commons Attribution-No Derivative Works 4.0
Summary: Further to yesterdays update on Sirius Open Source and its Pensiongate we can gladly report some progress following escalation to management; this is about tech and Open Source employees facing abuse at work, even subjected to crimes
THE Sirius series isnt quite over and we expect a lot more to be published about the pensions. Expect this to spill over to April as well.
When I started the series in December I didnt know how deep the rabbit hole would go; it pains me to know that myself and my colleagues got robbed.
Our solid plan to publish some EPO documents (earlier today) have thus been delayed somewhat; today weve instead devoted a lot of time to Sirius coverage.
 The gist of the video above is
(it mended up a bit like a podcast of the pension funds manager and
myself), they now reckon they failed to provide a good service,
they recognise the severity of the matter, and things will or at
least should be progressing a lot faster from now on.
The gist of the video above is
(it mended up a bit like a podcast of the pension funds manager and
myself), they now reckon they failed to provide a good service,
they recognise the severity of the matter, and things will or at
least should be progressing a lot faster from now on.
The saddest thing in all this is (there is a lot), it took me almost 3 hours on the phone (I pay for these calls) to finally get to the boss and weve already lost about 3 months while Sirius was hiding itself and hiding whats left of it. This really should have progressed months ago, but NOW: Pensions was uncooperative and unattentive. Since January it kept lying to me and to my wife, who has a plan there too.
13:39
Skyfall for Sirius Open Source: A Second Pension Provider Starts to Investigate Serious (Sirius) Abuses Techrights
Video
download link | md5sum
9dcf3def0c8beb1a166c52b5ded8b299
Chatting to the Pension Boss About Sirius
Creative Commons Attribution-No Derivative Works 4.0
Summary: Further to yesterday's update on Sirius Open Source and its Pensiongate we can gladly report some progress following escalation to management; this is about tech and Open Source employees facing abuse at work, even subjected to crimes
THE Sirius series isnt quite over and we expect a lot more to be published about the pensions. Expect this to spill over to April as well.
When I started the series in December I didnt know how deep the rabbit hole would go; it pains me to know that myself and my colleagues got robbed.
Our solid plan to publish some EPO documents (earlier today) have thus been delayed somewhat; today weve instead devoted a lot of time to Sirius coverage.
 The gist of the video above is
(it mended up a bit like a podcast of the pension funds manager and
myself), they now reckon they failed to provide a good service,
they recognise the severity of the matter, and things will or at
least should be progressing a lot faster from now on.
The gist of the video above is
(it mended up a bit like a podcast of the pension funds manager and
myself), they now reckon they failed to provide a good service,
they recognise the severity of the matter, and things will or at
least should be progressing a lot faster from now on.
The saddest thing in all this is (there is a lot), it took me almost 3 hours on the phone (I pay for these calls) to finally get to the boss and weve already lost about 3 months while Sirius was hiding itself and hiding whats left of it. This really should have progressed months ago, but NOW: Pensions was uncooperative and unattentive. Since January it...
13:36
In Mice, Anxiety Isnt All in the Head. It Can Start in the Heart SoylentNews
In high-risk contexts, a racing heart can make a formerly relaxed mouse nervous:
When you're stressed and anxious, you might feel your heart race. Is your heart racing because you're afraid? Or does your speeding heart itself contribute to your anxiety? Both could be true, a new study in mice suggests.
By artificially increasing the heart rates of mice, scientists were able to increase anxiety-like behaviors ones that the team then calmed by turning off a particular part of the brain. The study, published in the March 9 Nature, shows that in high-risk contexts, a racing heart could go to your head and increase anxiety. The findings could offer a new angle for studying and, potentially, treating anxiety disorders.
The idea that body sensations might contribute to emotions in the brain goes back at least to one of the founders of psychology, William James, says Karl Deisseroth, a neuroscientist at Stanford University. In James' 1890 book The Principles of Psychology, he put forward the idea that emotion follows what the body experiences. "We feel sorry because we cry, angry because we strike, afraid because we tremble," James wrote.
The brain certainly can sense internal body signals, a phenomenon called interoception. But whether those sensations like a racing heart can contribute to emotion is difficult to prove, says Anna Beyeler, a neuroscientist at the French National Institute of Health and Medical Research in Bordeaux. She studies brain circuitry related to emotion and wrote a commentary on the new study but was not involved in the research. "I'm sure a lot of people have thought of doing these experiments, but no one really had the tools," she says.
Read more of this story at SoylentNews.
13:00
8086 Multiply Algorithm Gets Reverse Engineered Hackaday

The 8086 has been around since 1978, so its pretty well understood. As the namesake of the prevalent x86 architecture, its often studied by those looking to learn more about microprocessors in general. To this end, [Ken Shirriff] set about reverse engineering the 8086s multiplication algorithm.
[Ken]s efforts were achieved by using die photos of the 8086 chip. Taken under a microscope, they can be used to map out the various functional blocks of the microprocessor. The multiplication algorithm can be nutted out by looking at the arithmetic/logic unit, or ALU. However, its also important to understand the role that microcode plays, too. Even as far back as 1978, designers were using microcode to simplify the control logic used in microprocessors.
[Ken] breaks down his investigation into manageable chunks, exploring how the chip achieves both 8-bit and 16-bit multiplication in detail. He covers how the numbers make their way through various instructions and registers to come out with the right result in the end.
Its a fun look at whats going on at the ground level in a chip thats been around since before the personal computer revolution. For any budding chip designers, its a great academic exercise to follow along at home. If youve been doing your own digging deep into CPU architectures, dont hesitate to drop us a line!
12:23
Superconducting Breakthrough! This REALLY Changes Everything! Lifeboat News: The Blog

Superconducting at 69F!
Advanced superconducting materials at room temperature will bring
about a paradigm shift in human technology and help us make great
advances in energy, medicine, electronics and space
explorations.
The Terran Space Academy walks you through the importance of the
latest discovery, the details behind their research, and the space
technologies it will immediately impact.
Shop the Academy store at https://shop.spreadshirt.com/terran-s
help support our channel at https://www.patreon.com/terranspaceac
Thank you so much for watching!
Ad Astra Pro Terra.
Artists.
https://twitter.com/C_Bass3d.
Tweets by Neopork85
https://twitter.com/hazegrayart.
https://twitter.com/AlexSvanArt.
Tweets by
_fragomatik_
https://twitter.com/nickhenning3d.
https://twitter.com/RGVaerialphotos.
Companies.
Tweets by
NASA
Tweets by
SpaceX
https://www.cochranex.com.
https://twitter.com/blueorigin.
https://twitter.com/Space_Ryde.
https://twitter.com/VirginGal...
12:22
Cryptojacking Group TeamTNT Suspected of Using Decoy Miner to Conceal Data Exfiltration Lifeboat News: The Blog
The cryptojacking group known as TeamTNT is suspected to be behind a previously undiscovered strain of malware used to mine Monero cryptocurrency on compromised systems.
Thats according to Cado Security, which found the sample after Sysdig detailed a sophisticated attack known as SCARLETEEL aimed at containerized environments to ultimately steal proprietary data and software.
Specifically, the early phase of the attack chain involved the use of a cryptocurrency miner, which the cloud security firm suspected was deployed as a decoy to conceal the detection of data exfiltration.
12:22
YoroTrooper Stealing Credentials and Information from Government and Energy Organizations Lifeboat News: The Blog
A new threat actor, YoroTrooper, has been identified by Cisco Talos as running espionage campaigns targeting government and energy organizations.
11:31
Managing Risk in Crypto Trading: Techniques for Minimizing Your Exposure to Market Volatility HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
Crypto trading might be a successful method to gain money, but it is not without risks. A trader
This is a post from HackRead.com Read the original post: Managing Risk in Crypto Trading: Techniques for Minimizing Your Exposure to Market Volatility
11:18
Linux Foundation Training & Certification & Cloud Native Computing Foundation Partner with CoRise to Prepare 50,000 Professionals for the Certified Kubernetes Administrator Exam Linux.com

Read the original post at: Read More
The post Linux Foundation Training & Certification & Cloud Native Computing Foundation Partner with CoRise to Prepare 50,000 Professionals for the Certified Kubernetes Administrator Exam appeared first on Linux.com.
11:00
HPR3815: The UNIVAC Uniscope - The first terminal with a video monitor Hacker Public Radio
In the early days of computing, the computing power was kept in centralized large mainframes and users would connect to them via so called "dumb" terminals. These often provided their output through a printer and continuous feed of paper. However in 1964 UNIVAC introduced the Uniscope 300, which was one of the first terminals to provide a video monitor for display. With the introduction of this system came the introduction of several concepts that we take for granted today and they are described during the reading of this brochure. The brochure was made available through the Computer History Museum at https://www.computerhistory.org/collections/catalog/102646317 As I mention in the episode, $15,000 USD in 1964 is worth considerably more today, according to an online inflation calculator it is now worth approximately $144,000 today. So even if that was for 48 terminals as it seems to mention in the hand written note, that might equate to about $3000 per terminal in 2023 dollars. Here are some related links below: UNIVAC - https://en.wikipedia.org/wiki/UNIVAC The Uniscope line - https://en.wikipedia.org/wiki/Uniscope Uniscope terminal multiplexer service manual - https://www.computerhistory.org/collections/catalog/102784700
Automated Input Generation for Alloy It Will Never Work in Theory
If you are reading this post, you have probably written code for distributed systems, but you probably haven't used any automated tools to verify that those systems work as intended. One reason for this is their user-hostile interfaces: while Alloy, TLA+, and similar systems are powerful, the notations they use make Perl and Egyptian hieroglyphics seem readable by comparison.
The authors of this paper have been tackling that by automating some of the grunt work involved in describing models for Alloy. Their previous tool, ASketch, took a partial model with user-specified holes, a generator which outlines valid substitutions for each hole, and a test suite outlining the expected behavior of the model, and produced a completed model that passed all the tests. This tool, SketchGen2, automatically creates some of those inputs. Using it still requires more understanding of formal specification than most developers currently have, but as with LLM-based code generators and static analysis tools, more and more of the effort required is shifting from programmers to programs.
Ana Jovanovic and Allison Sullivan. Towards automated input generation for sketching alloy models. In Proceedings of the IEEE/ACM 10th International Conference on Formal Methods in Software Engineering. ACM, May 2022. doi:10.1145/3524482.3527651.
Writing declarative models has numerous benefits, ranging from automated reasoning and correction of design-level properties before systems are built, to automated testing and debugging of their implementations after they are built. Alloy is a declarative modeling language that is well suited for verifying system designs. While Alloy comes deployed in the Analyzer, an automated scenario-finding tool set, writing correct models remains a difficult and error-prone task. ASketch is a synthesis framework that helps users build their Alloy models. ASketch takes as an input a partial Alloy models with holes and an AUnit test suite. As output, ASketch returns a completed model that passes all tests. ASketch's initial evaluation reveals ASketch to be a promising approach to synthesize Alloy models. In this paper, we present and explore SketchGen2, an approach that looks to broaden the adoption of ASketch by increasing the automation of the inputs needed for the sketching process. Experimental results show SketchGen2 is effective at producing both expressions and test suites for synthesis.
10:56
APT Actors Exploited Telerik Vulnerability in Govt IIS Server CISA HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
According to a joint advisory from the US CISA (Cybersecurity and Infrastructure Security Agency), the FBI (Federal Bureau
This is a post from HackRead.com Read the original post: APT Actors Exploited Telerik Vulnerability in Govt IIS Server CISA
10:51
Opinion: Feds to Microsoft and Others - Clean Up Your Security Act SoylentNews
The US government looks poised to force tech companies to do more about security:
The US government, worried about the continuing growth of cybercrime, ransomware, and countries including Russia, Iran, and North Korea hacking into government and private networks, is in the middle of drastically changing its cybersecurity strategy. No longer will it rely largely on prodding businesses and tech companies to voluntarily take basic security measures such as patching vulnerable systems to keep them updated.
Instead, it now wants to establish baseline security requirements for businesses and tech companies and to fine those that don't comply.
It's not just companies that use the systems who might eventually need to abide by the regulations. Companies that make and sell them, such as Microsoft, Apple, and others could be held accountable as well. Early indications are that the feds already have Microsoft in their crosshairs they've warned the company that, at the moment, it doesn't appear to be up to the task.
[...] In theory, if those standards aren't met, fines would eventually be imposed. Glenn S. Gerstell, former general counsel of the National Security Agency, explained it this way to the Times: "In the cyberworld, we're finally saying that Ford is responsible for Pintos that burst into flames, because they didn't spend money on safety." That's a reference to the Ford Pinto frequently bursting into flames when rear-ended in the 1970s. That led to a spate of lawsuits and a ramp-up in federal auto safety regulations.
But cybersecurity requirements backed by fines aren't here yet. Dig into the new document and you'll find that because the new strategy is only a policy document, it doesn't have the bite of law behind it. For it to go fully into effect, two things need to happen. President Biden has to issue an executive order to enforce some of the requirements. And Congress needs to pass laws for the rest.
Read more of this story at SoylentNews.
10:16
Baseband RCE flaws in Samsungs Exynos chipsets expose devices to remote hack Security Affairs
Googles Project Zero hackers found multiple flaws in Samsung s Exynos chipsets that expose devices to remote hack with no user interaction.
White hat hackers at Googles Project Zero unit discovered multiple vulnerabilities Samsung s Exynos chipsets that can be exploited by remote attackers to compromise phones without user interaction.
The researchers discovered a total of eighteen vulnerabilities, the four most severe of these flaws (CVE-2023-24033 and three other vulnerabilities that have yet to be assigned CVE-IDs) allowed for Internet-to-baseband remote code execution.
An attacker only needs to know the victims phone number to exploit these vulnerabilities.
Tests conducted by Project Zero confirm that those four vulnerabilities allow an attacker to remotely compromise a phone at the baseband level with no user interaction, and require only that the attacker know the victims phone number. reads the advisory published by Google. With limited additional research and development, we believe that skilled attackers would be able to quickly create an operational exploit to compromise affected devices silently and remotely.
Experts warn that skilled threat actors would be able to create an exploit to compromise impacted devices in a stealthy way.
The experts recommend turning off Wi-Fi calling and Voice-over-LTE (VoLTE) in settings of vulnerable devices to prevent baseband remote code execution attacks.
Until security updates are available, users who wish to protect themselves from the baseband remote code execution vulnerabilities in Samsungs Exynos chipsets can turn off Wi-Fi calling and Voice-over-LTE (VoLTE) in their device settings. Turning off these settings will remove the exploitation risk of these vulnerabilities. states the report.
Samsung Semiconductors advisories provide the list of Exynos chipsets impacted by these vulnerabilities. Below is a list of devices allegedly affected by these flaws:
- Mobile devices from Samsung, including those in the S22, M33, M13, M12, A71, A53, A33, A21, A13, A12 and A04 series;
- Mobile devices from Vivo, including those in the S16, S15, S6, X70, X60 and X30 series;
- The Pixel 6 and Pixel 7 series of devices from Google;
- any wearables that use the Exynos W920 chipset; and
- any vehicles that use the Exynos Auto T5123 chipset.
Google did not disclose technical details of these flaws to avoid threat actors could develop their own exploits.
Due to a very rare combination of...
10:16
What Policymakers Need to Know About the First Amendment and Section 230 Deeplinks
The Supreme Court just heard two cases - Twitter v. Taamneh and Gonzalez v. Google - that could dramatically affect users speech rights online. Last week, EFF hosted a panel in Washington D.C. to discuss what legislators need to know about these cases, the history of Section 230, and the First Amendments protections for online speech.
Alongside EFF Senior Staff Attorney Aaron Mackey, the panel included Billy Easley, Senior Public Policy Lead at Reddit, and Emma Llanso, Director of the Free Expression Project at the Center for Democracy and Technology (CDT). Senator Ron Wyden (D-OR), one of the co-authors of Section 230, gave opening remarks.
Senator Wyden and the Supreme Court
Senator Wyden opened the panel with background on the law: it simply establishes the principle that the person who creates and posts content is responsible for that content. Thanks to Section 230 and the First Amendment, websites can take down what they want. Section 230 is essential to smaller companies and startups: The big guys can take care of themselves, but the small guys should be able to compete with the big guys, Wyden explained. The law democratizes speech, and elevates the choices of users. Thanks to Section 230, people are able to speak out.
Wyden then discussed the latest Supreme Court cases. In Gonzalez v. Google, the petitioning plaintiffs made a radical argument about Section 230. They asked the Supreme Court to rule that Section 230 doesnt protect recommendations we get online, or how certain content gets arranged and displayed. In Twitter v. Taamneh, the U.S. Court of Appeals for the Ninth Circuit ruled that online services can be civilly liable under the Anti-Terrorism Act (ATA) based on claims that the platform had generalized awareness that members of a terrorist organization used its service.
In our view, the decision in Gonzalez should be clear: online recommendations and editorial arrangements are the digital readers attention to whatever might be most interesting to them. Deciding where to direct readers is part of editorial discretion, which has long been protected under the First Amendment. Regarding Taamneh, the Court should interpret the ATA to create liability only when platforms have actual knowledge that a specific piece of user-generated content substantially assists an act of terrorism. In...
10:00
Replacing a Clock ICs Battery Hackaday

You can find a lot of strange things inside IC packages. For example, the Dallas DS12885 and DS12887 real time clock chips were available in a large package with an internal battery. The problem, of course, is that batteries die. [New Old Computer Show] wanted to restore a machine that used one of these devices and was able to repair the device. You can see two videos below. In the first video, he replaces both the battery and adds an external oscillator which would be necessary for the DS12885. However, he actually had the DS12887, which has an internal oscillator, something the second video explains.
The repair used a PCB he ordered from Tindie. However, the board is only part of the problem. You also need to disconnect the dead battery which requires a Dremel and a steady hand.
The board fits on top of the IC technically, it is more of a module than an IC and solders to some contacts exposed by the Dremel surgery. It looks like a hack, but then thats the way we like it.
In the second video, he uses clear nail polish to protect the exposed wires. Someone in the comments mentioned liquid electrical tape, but we might have been tempted to just coat it with hot glue or if we didnt want to take it apart epoxy.
...
08:16
1xbet Bonus
You should wait a day or two for your withdrawal request to be processed and confirmed, however thats the industry standard. Some cricket fans think about that this might be one of the key moments inside the sport. Cricket punters need to remember that the outcomes of the flip-a-coin recreation depends on pure luck, and wagering a lot of money on its not advisable. Currently, there are not any concrete legal guidelines or data associated to the net betting talked about in the Indian laws.
Some NZ bookies accept multiple cryptocurrencies, including Bitcoin, Ethereum, Dogecoin, Litecoin, and others. The risk-free guess is often confused with the free guess, however the two phrases are literally not interchangeable. With a risk-free guess, you are betting with your individual money. In case you win, its enterprise as traditional, however if you lose, the bookie will reimburse you.
And however others, just like the birthday bonus, are very easy, any bookmaker might do it however they dont. We are extremely joyful to welcome new folks in our group. This is to have the ability to make all the individual experience as clean and as straightforward as potential. The participant receives a complete listing and sufficient ratios, which contributes to a pleasing pastime.
You can obtain mostbet app for iOS on the official web site or in the AppStore. Ive a presentation subsequent week, and Im at the search for such information. Your way of describing the whole thing in this publish is genuinely pleasant, every one have the power to merely realize it, Thanks lots.
It is very important that the IPL betting sites defend your identification and course of the withdrawals in the quickest time attainable. Our team at My Betting Sites India came up with a few betting ideas to remember when betting on the Pro Kabaddi League this yr. V, an organization registered beneath Curacao legal guidelines. The reality is that there are quite a few sports activities betting apps value investigating. Moving concerning the app and being able to place bets shortly and accurately are key areas that each one tie into ease of use. No matter what your favorite sport is if it isnt on the 1xBet app, it most likely isnt wherever else.
My weblog covers lots of the identical subjects as yours and I consider we may significantly benefit from each other. The clearness in your publish is just glorious and i can assume youre an professional on this subject. This article will help the web customers for creating new weblog or perhaps a weblog from start to end.
Ccan be uup tto hundreds of miles besides. Leave all this simply open personal computer and google out the phrases online casino video games. I truly loved studying it, you is normally a great writer.I will remember to bookmark your weblog and will ultimately come back down the highway.
However, in case you have extra severe points associated to paym...
08:14
1xbet Online Casino & Sports Betting h+ Media
1xbet Online Casino & Sports Betting
They present nice discounts and deals that attract gamblers from all over the world. Their banking alternatives are well-managed and protected, in addition to their engaging bonuses. Not to say their outstanding customer service. This cellular on line casino sports activities betting promotion will make your first steps simpler there. But in case you are aiming at something extra beneficiant, contemplate using our Bethard promo code provided in the associated article to seize an excellent first deposit offer. Placing gamble on 1xbet cellular variation has many advantages.
I merely wish to offer you a big thumbs up for the good data youve got right here on this publish. I be taught something new and difficult on web sites I stumbleupon everyday. I perceive this is off matter however I simply needed to ask.
Ohio sports betting shall be out there by January 1, 2023, multiple year after Governor Mike DeWine signed sports betting into law. They are truthful and provide a high quality service from top to bottom. Its additionally the easiest method to request withdrawals, which is defined later.
The father or mother firm relies in Cyprus and has branches worldwide. 1xBet cell on line casino is licensed and controlled under the laws of the Government of Curacao. The expansive game foyer in 1xBet cell casino is respected software providers similar to Microgaming and NetEnt.
I came across this board and I to find It actually helpful & it helped me out much. I understand this is type of off-topic but I needed to ask. Im trying tto determine iif itts an issue on my end or if its the weblog.
Each event options its categories and game types, corresponding to for example live supplier selections or electrifying slots. Also, there are quite a few mini-games within the apk, so if you dont want to bet, you presumably can have enjoyable taking part in actually one of them. The utility has great evaluations, in plenty of respects because of the broad prospects, from creating an account with a welcome bonus on bets to video games. Completing the 1xBet Android app get hold of and installing it on a gadget, a participant will get fast entry to the complete functionality of the betting platform. The equally quick transition is provided within the app and desktop version.
Know I am getting know-how day by day by reading thes good posts. I dont knnow hether its simply me oor iff pehaps everybody else experiencing points ith you blog. Thnks foor posting hen yuve got the opportunity, Guess ll ust bookmark tis website. Theres actually so much to learn about this topic. And that is also taking place with this text which I am reading now. I used to have the ability to find good info out of your blog articles.
This will assist them to keep away from any points and difficulties. Futures or outrights are wagers that enable you to predict the...
08:12
Weblog Archives
Users, its really actually fastidious piece of writing on building up new weblog. Whats up, of course this paragraph is definitely fastidious and I even have realized lot of issues from it on the topic of blogging. I discovered your blog the utilization of msn. That is an extremely nicely written article.
It has gained them many praises worldwide. They expanded their business significantly in 2019, the identical year once they briefly sponsored Liverpool FC and Chelsea FC. Casinomeister has proven to be instrumental in bringing trust, credence, and a recognized stage taking half in ground for the net gaming group. New players at Conquestador receive up to 200 spins of which some are free spins without deposit required. Another website much like Conquestador is Mr Green which runs on the 50 bonus with 50 free spins. Reading the Conquestador casino blog isnt solely interesting, but in addition profitable.
Win real cash playing one-armed bandits, video poker, slots and more. Signup for free bonuses, every day jackpots and other giveaways. 1xBet absolutely knows tips on how to maintain its members happy. On your birthday, you may be given a free bet.
For instance, lets say you placed a $10 free bet on odds of 1.90 and won. If you have been to wager with your personal money, your complete win would be $19, but because you used free bet credits to make a wager, you solely get the $9 profit. If were fortunate sufficient to win some of our bets, we can move on to the ultimate part of our score train, which is testing the withdrawal course of. We primarily focus on the transaction times, which ought to be as quick as possible. Of course, some payment methods are gradual, to begin with, so we cant take this away from the web betting web site.
I do not know whether or not it is simply me or if everyone else encountering issues along with your website. I mean, what you say is important and everything. On a lot of the topics youu write in relation to here.
Even the appliance course of for a Curacao playing license is easy and hassle-free. Usually making use of for a gaming license means loads of paperwork, documents, and functions that take a lot of money and time to compile. However, this isnt the case in Curacao as they have restricted bureaucracy. This makes the method of license application easier and quicker. To start betting on 1xBet bd or play 1xBet poker, you want to first register and replenish your stability.
It offers all popular casino video games, reside casinos, and even sports activities betting to gamers. Players can get started after they get complete the registration process. It has over one hundred payment options for gamers to select from. Not simply that, however players can also enjoy quick and simple withdrawal choices.
It is amongst the best ways to execute the...
08:10
EPA Sets Limits on Some Forever Chemicals as Low as They Can Go SoylentNews
If you can detect any, it's too much:
On Tuesday, the Environmental Protection Agency announced that it had started the process that will see drinking water regulations place severe limits on the levels of several members of the PFAS (perfluoroalkyl and polyfluoroalkyl substances) chemical family. PFAS are widely used but have been associated with a wide range of health issues; their chemical stability has also earned them the term "forever chemicals." The agency is currently soliciting public feedback on rules that will mean that any detectable levels of two chemicals will be too much.
PFAS are a large group of chemicals that have uses in a wide range of products, including non-stick cooking pans, fire control foams, and waterproof clothing. They're primarily useful because of their water-repellant, hydrophobic nature. That nature also tends to keep them from taking part in chemical processes that might otherwise degrade them, so contamination problems tend to stick around long after any PFAS use. And that's bad, given that they seem to have a lot of negative effects on healththe EPA lists cancer risks, immune dysfunction, hormone signaling alterations, liver damage, and reproductive issues.
[...] The most striking thing about the proposal is that two of the chemicals, Perfluorooctanoic acid (PFOA) and Perfluorooctanesulfonic acid (PFOS) will be set at the limits of our current ability to detect them: four parts per trillion. In other words, if there's any sign of the chemicals present, it would be above the legal limit. (Both of these are acidic hydrocarbons where all of the hydrogen has been replaced by fluorine.)
Read more of this story at SoylentNews.
08:00
Japanese India Regional Council Of The Institute Of Chartered Accountants Of India Eirc h+ Media
Japanese India Regional Council Of The Institute Of Chartered Accountants Of India Eirc
Receive the bonus Receive the bonus in the form of free bets. MelBET is a betting web site which caters to the tastes and wishes of punters from all over the world. It also has a presence within the Indian subcontinent, the place operations are now possible due to a license being supplied by the Government of Curacao. You can also ask for a link to the page from the help.
Our customers can play online on line casino or actual dealer video games. Its pretty common for sports betting sites to have some sort of welcome bonus for brand new customers. As MelBet is a strong candidate for being the most effective bookmaker in India, we have been fairly hopeful that there can be some kind of registration bonus. So take a look at our guide to the newest MelBet sign up offers to see what sorts of deals for brand new prospects the model has on in the intervening time. If you own an iPhone or iPad, you presumably can download Melbet by visiting the official web site of melbet.
Dont forget about your bonuses and promotion; in the Melbet apk, you are taking the identical ones; if you have any promo codes, dont forget to enter them. If youre a gambler, youll be thrilled to hear to that Melbet apk lay on a chance to deliver a full-on casino with you. On the Melbet app, youll find a on line casino game that suits you , also quite a few choices for slots, TOTO. After the appliance has been downloaded, you want to set up it, simply follow the instructions of the bookmaker. The first method of downloading is quicker, since you then do not need to switch the downloaded file to your smartphone. The line is made within the type of an inventory of sports.
It allows you to place wagers after the start of the event. Since the bookmaker needs to alter the percentages nearly each minute, live betting is your best opportunity to place a winning wager. Melbet App is on the market for all Android devices with a system of at least four.1 and helps all of the features of the primary model of the site. For gamers with iOS devices, a separate app is available which is not any totally different from the Android app.
Select the most probably (from the teams perspective) consequence. The app has minimal system necessities, and its safe to say that it is going to work great on most handheld gadgets. Its easy click on the APK file and agree to put in this system on your telephone, then wait a number of seconds for it to install. I am Ayush Kesharwani, Brand Manager at Kheltalk.
Online casino regulation means that earlier than a license may be issued, an online on line casino has to move by way of the strictest of requirements. This includes a thorough evaluation of the proposed casinos monetary history, the integrity and competence of the proprietor and whether they have a felony document or not. Cashback is calculated on all suc...
07:58
Denmarks Piracy Blocklist Adds YouTube Rippers & Expands to 239 Sites TorrentFreak
 In
recent years, site blocking has emerged as a preferred anti-piracy
solution in dozens of countries.
In
recent years, site blocking has emerged as a preferred anti-piracy
solution in dozens of countries.
These blocking measures are not bulletproof but pose a hurdle for casual pirates, which can bring down overall piracy rates.
In many countries blocking is a relatively new measure, but Denmark has years of experience. The first Danish blocks date back to 2006, when music industry group IFPI filed a complaint targeting the unlicensed Russian MP3 site AllofMP3.
Not much later, Denmark became the first European country to force an ISP to block access to The Pirate Bay. Since then, many other pirate sites have received the same treatment.
Denmark Expands Piracy Blocklist
This week, a new batch of sites was added to this ever-growing blocklist. The Court in Nstved issued an order targeting nine music piracy sites that reportedly had hundreds of thousands of monthly visitors from Denmark.
The Courts verdict isnt yet publicly available, but the complaint was filed by local anti-piracy group Rights Alliance, which acted on behalf of several prominent music industry organizations including IFPI, Sony Music, Universal Music, and Danish music group KODA.
Rights Alliance informs TorrentFreak that the order includes stream ripper domains ytmp3.cc, y2mate.com, yt1s.com, savefrom.net, loader.to, onlinevideoconverter.pro, yt5s.com, and ytmp3.plus. All of these sites can convert YouTube videos into downloadable MP3 files.
Outlier
The ninth site, Onebas.com, is a clear outlier as its a music streaming site, instead of a stream ripper. This service appears to mimic services such as Spotify, by playing embedded YouTube videos.
Playing embedded YouTube videos is fine as long as the rightsholder permits it. However, Onebas.com also offers full album downloads for registered users, charging $1 a piece. Thats something artists and labels certainly wont be happy with.
The Court in Nstved agreed that all nine music sites should be blocked. On paper, the blocking requirement is limited to Internet provider Fibula. However, based on a ...
07:50
The First Bits Of Wine's Wayland Driver Were Merged Phoronix
The first code has landed into Wine Git as part of the multi-year effort creating a Wayland driver for Wine so that the Windows games/applications running via Wine can enjoy native Wayland support. This isn't yet usable for end-users/gamers but is the early implementation with more parts to follow...
07:34
Government Hasn't Justified a TikTok Ban Deeplinks
Freedom of speech and association include the right to choose ones communication technologies. Politicians shouldnt be able to tell you what to say, where to say it, or who to say it to.
So we are troubled by growing demands in the United States for restrictions on TikTok, a technology that many people have chosen to exchange information with others around the world. Before taking such a drastic step, the government must come forward with specific evidence showing, at the very least, a real problem and a narrowly tailored solution. So far, the government hasnt done so.
Nearly all social media platforms and other online businesses collect a lot of personal data from their users. TikTok raises special concerns, given the surveillance and censorship practices of its home country, China. Still, the best solution to these problems is not to single-out one business or country for a ban. Rather, we must enact comprehensive consumer data privacy legislation. By reducing the massive stores of personal data collected by all businesses, TikTok included, we will reduce opportunities for all governments, China included, to buy or steal this data.
Many people choose TikTok
TikTok is a social media platform that hosts short videos. It is owned by ByteDance, a company headquartered in China. It has 100 million monthly users in the United States, and a billion worldwide. According to Pew, 67% of U.S. teenagers use Tiktok, and 10% of U.S. adults regularly get news there. Many users choose TikTok over its competitors because of its unique content recommendation system; to such users, social media platforms are not fungible.
TikTok videos address topics as diverse as human thought. Political satirists mock politicians. Political candidates connect with voters....
07:00
Taking Apart IKEAs Latest Air Quality Sensor Hackaday

Whether its because theyre concerned about worsening pollution or the now endemic variants of COVID-19, a whole lot of people have found themselves in the market for a home air quality monitor thee last couple of years. IKEA noted this trend awhile back, and released the VINDRIKTNING sensor to capitalize on the trend.
The device must have sold pretty well, because last month the Swedish flat-packer unveiled the considerably more capable (and more expensive) VINDSTYRKA. Now thanks to the efforts of [Oleksii Kutuzov] weve got a fantastic teardown of the new gadget, and some more information on the improvements IKEA made over its predecessor.
06:54
NOW: Pensions Wont Let Me Have My Money, Fails to Apologise for Months of Lying schestowitz.com
Video download
link | md5sum
f78431fd89771a7ee494f43d13e16fb5
34 Minutes With Now Pensions (NOW: Pensions)
Creative Commons Attribution-No Derivative Works 4.0
Summary: The Pensiongate of Sirius Open Source (the company which embezzled/robbed many workers for years) helps reveal the awful state of British pension providers, which are in effect enabling the embezzlement to carry on while lying to their clients
THE video above shows how in the company NOW: Pensions customer support staff is basically just a shield, making it virtually impossible to speak to people who can progress/resolve things. In a very Kafkaesque fashion they try to pass me from one person to another person without actually making any real progress. No apologies, no information, no reaction.
As it turns out this week, it can be more or less the same in the United States, so it seems like a global issue, a universal pattern.
The recording above was made only after months of frustration and a waste of money, not just time. NOW: Pensions lied to me repeatedly; they already have a history of misconduct and judging by the quality of their service (or disservice) they might go under again as they did before (until some other company bought them). As per British law, there are cases where pensions can be redeemed early, with up to 55% tax in case of unauthorised withdrawals (before age 55). But advisors are spreading misinformation for their own benefit/interests. It also seems clear that redeeming depositors money is made incredibly hard. Thats a design flaw, an intentional barrier.
06:51
NOW: Pensions Lying, Obstructing and Gaslighting Clients After Months of Lies, Delays, and Cover-up (Amid Pension Fraud) Techrights
Video download
link | md5sum
f78431fd89771a7ee494f43d13e16fb5
34 Minutes With Now Pensions (NOW: Pensions)
Creative Commons Attribution-No Derivative Works 4.0
Summary: The Pensiongate of Sirius Open Source (the company which embezzled/robbed many workers for years) helps reveal the awful state of British pension providers, which are in effect enabling the embezzlement to carry on while lying to their clients
THE video above shows how in the company NOW: Pensions customer support staff is basically just a shield, making it virtually impossible to speak to people who can progress/resolve things. In a very Kafkaesque fashion they try to pass me from one person to another person without actually making any real progress. No apologies, no information, no reaction.
The recording above was made only after months of frustration and a waste of money, not just time.As it turns out this week, it can be more or less the same in the United States, so it seems like a global issue, a universal pattern.
The recording above was made only after months of frustration and a waste of money, not just time. NOW: Pensions lied to me repeatedly; they already have a history of misconduct and judging by the quality of their service (or disservice) they might go under again as they did before (until some other company bought them). As per British l...
06:29
US Marshals Service Data Sold on Russian Hacker Forum HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
The hacker is selling 350 GB worth of data for $150,000 supervised by the forums guarantor.
This is a post from HackRead.com Read the original post: US Marshals Service Data Sold on Russian Hacker Forum
06:13
Links 16/03/2023: War Escalations and More Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Desktop/Laptop
-
9to5Linux System76s Meerkat Mini Linux PC Now Ships with 12th Gen Intel Core i CPUs
Yes, System76 even sells a mini PC and the latest variant can be configured with 10th, 11th, or 12th Gen Intel Core i Series processors with up to 12 cores and 16 threads and up to Intel Iris Xe graphics on the 12th Gen Intel Core i7-1260P CPU, which also offers up to 4.7 GHz clock speeds.
Other 12th Gen Intel Core i Series processors include the Intel Core i3-1220P with 10 cores and 12 threads and up to 4.4 GHz clock speeds, as well as Intel Core i5-124...
-
-
05:58
Microsoft sheds light on a year of Russian hybrid warfare in Ukraine Security Affairs
Russia-linked threat actors targeted at least 17 European nations in 2023, and 74 countries since the start of the invasion of Ukraine.
Microsoft revealed that Russia-linked threat actors targeted at least 17 European nations between January and mid-February 2023. According to a report published by the IT giant, the state-sponsored hackers have targeted 74 countries since the start of the invasion of Ukraine. The cyber espionage operations aimed at government and defense-related organizations in Central and Eastern Europe and the Americas.
Between January and mid-February 2023, Microsoft threat intelligence analysts have found indications of Russian threat activity against organizations in at least 17 European nations, with the government sector the most targeted. reads the report published by Microsoft. While these actions are most likely intended to boost intelligence collection against organizations providing political and material support to Ukraine, they could also, if directed, inform destructive operations.
The report also states that the Russia-linked APT group IRIDIUM appears to be preparing for a renewed destructive campaign. The group could target Ukraine with destructive malware such as Foxblade and Caddywiper. The experts also reported that as of late 2022, the state actor may also have been testing additional malware with similar capabilities in destructive attacks on organizations outside Ukraine that serve key functions in Ukraines supply lines.
Sandworm (aka BlackEnergy and TeleBots) has been active since 2000, it operates under the control of Unit 74455 of the Russian GRUs Main Center for Special Technologies (GTsST).
The group is also the author of the NotPetya ransomware that hit hundreds of companies worldwide in June 2017, causing billions worth of damage.
In April, Sandworm targeted ene...
05:30
Robot Hand Looks and Acts Like the Real Thing Hackaday

Throughout history, visions of the future included human-looking robots. These days we have plenty of robots, but they dont look like people. They look like disembodied arms, cars, and over-sized hockey pucks concealing a vacuum cleaner. Of course theres still demand for humanoid robots like Commander Data, but there are many challenges: eyes, legs, skin, and hands. A company known as Clone may have the solution for that last item. The Clone Hand is the most human-level musculoskeletal hand in the world, according to the companys website.
The 0.75 kg hand and forearm offer 24 degrees of freedom and two hours of battery life. It sports 37 muscles and carbon fiber bones. The muscle fibers can cycle over 650,000 times. You can watch the hand in action in the video below.
There is a hydraulic pump that the company likens in size to a human heart. The hand can also sense for feedback purposes. If you want to build your own, youll have to figure it out yourself. The Clone Hand is proprietary, but it does show what is in the art of the possible. The company claims they cost under $3,000, but it isnt clear if thats their cost or a projected future retail price.
Of course, human hands arent always the perfect robot manipulator. But when you need a realistic hand, you really need it. We see a lot of...
05:24
You Can Now Run a GPT-3-Level AI Model on Your Laptop, Phone, and Raspberry Pi SoylentNews
...Things are moving at lightning speed in AI Land. On Friday, a software developer named Georgi Gerganov created a tool called "llama.cpp" that can run Meta's new GPT-3-class AI large language model, LLaMA, locally on a Mac laptop. Soon thereafter, people worked out how to run LLaMA on Windows as well. Then someone showed it running on a Pixel 6 phone, and next came a Raspberry Pi (albeit running very slowly).
If this keeps up, we may be looking at a pocket-sized ChatGPT competitor before we know it.
[...]
For example, here's a list of notable LLaMA-related events based on a timeline Willison laid out in a Hacker News comment:
- February 24, 2023: Meta AI announces LLaMA.
- March 2, 2023: Someone leaks the LLaMA models via BitTorrent.
- March 10, 2023: Georgi Gerganov creates llama.cpp, which can run on an M1 Mac.
- March 11, 2023: Artem Andreenko runs LLaMA 7B (slowly) on a Raspberry Pi 4, 4GB RAM, 10 sec/token.
- March 12, 2023: LLaMA 7B running on NPX, a node.js execution tool.
- March 13, 2023: Someone gets llama.cpp running on a Pixel 6 phone, also very slowly.
- March 13, 2023, 2023: Stanford releases Alpaca 7B, OpenAI's "text-davinci-003" but runs on much less powerful hardware.
05:00
Education Week Spotlights Programs for Students and Professionals IEEE Spectrum
![]()
As technology continues to evolve, STEM education is needed more than ever. With the vast technical expertise of its 400,000-plus members and volunteers, IEEE is a leader in engineering and technology education. Its technical societies and its councils, sections, and regional groups offer educational events and resources at every level to support technical professions and prepare the workforce of tomorrow.
IEEE offers many ways to support the educational needs of learners. For preuniversity students, the organization offers summer camps and other opportunities to explore science, technology, engineering, and mathematics careers. IEEEs continuing education courses allow professionals to stay up to date on technology, keep their skills sharp, and learn new things.
From 2 to 8 April, IEEE is highlighting resources available to students, educators, and technical professionals with IEEE Education Week. The annual celebration highlights educational opportunities provided by the worlds largest technical professional association and its many organizational units, societies, and councils.
Here are some of the events and resources available during this years Education Week.
Webinars
Climate Change: IEEEs Role in Bringing Technology Solutions to Meet the Challenge
3 April, noon to 1 p.m. EDT
IEEE President and CEO Saifur Rahman kicks off Education Week with a session on how the organization can serve as a vital connection between policymakers and the engineering and technology communities in bringing technological solutions to meet the universal challenge of climate change. Rahman plans to share how IEEE is committed to helping mitigate the effects of climate change through pragmatic and accessible technical solutions, as well as by providing engineers and technologists with a neutral space for discussion and action. The webinar also addresses the importance of educating the energy workforce.
3 April, 9 to 10 a.m. EDT
IEEE REACH (Raising Engineering Awareness through the Conduit of History) provides teachers with resources to help them explain the history of technology and the roles played by engineers. During this webinar, participants can learn how REACH can enhance the classroom experience.
...
04:30
Rivers Edge Rockabilly Automotive Present And Pinup Contest h+ Media
Rivers Edge Rockabilly Automotive Present And Pinup Contest
Copyright is held by the respective owners of all artwork. All different authentic works such as brand, mascot and articles are copyright Pin-ups & Cartoon Girls.com. An fascinating footnote to the Pop Art motion of the 1960s is the work of Mel Ramos, who mixed nude pin-ups with recognizable corporate images for a satiric mix of cheesecake and commercialism.
These dermatologist-recommended merchandise will give lips a luscious-looking temporary fullness. Your go-to poses will not reduce it on the earth of pinup. Pinup is all about curves, so arch your back, suck in your stomach and pop your booty, Dollface says.
Among the other well-known artists specializing in the field were Earle K. Bergey, Enoch Bolles, Gil Elvgren, George Petty, Rolf Armstrong, Zo Mozert, Duane Bryers and Art Frahm. Notable up to date pin-up artists include Olivia De Berardinis, identified for her pin-up artwork of Bettie Page and her items in Playboy. Sell customized creations to individuals who love your style.
Olivia also creates works based on the performances and photographs of Dita von Teese, one of todays foremost burlesque performers and fashions. Many of her work present women as powerful and confident, similar to how superheroes are depicted in comic books. Throughout history, there have also been feminine pinup artists. Zoe Mozert (American, 19041993) was one of the prime pinup artists during the mid20th century.
Pratically I get stuck on reboot conduct when pluging a TM1637 DIO and CLK to thos pins on TTGO-Micro32 based boards. Im a bit confused concerning the Input only pins as well. I did a board and used certainly one of them as an output, didnt work of course. In DOIT dev equipment GPIO21 and GPIO22 are utilized by I2C bus.
Prior to that, Duchamp and dadists explored the concept of what constitutes art. A painting of a pipe, a fountain made from a urinal and different works challenged the position an artist performed in relation to the world round themselves. In Europe during the 1800s, there have been actions to flee the excesses of the Baroque and Rococo periods and return to classical simplicity.
She was the image of idealized beauty within the early twentieth century. She was correct, selfconfident, and maintained an alluring gaze to the viewer. The Gibson Girl represented mischief in addition to liberation from tradition.
had the chops to have been one of the biggest pin-up artists in America, however presumably his lust for ample-sized ladies prevented that, admits the online gallery curator and Hilda collector, Les Toil. Although you could beforehand highlight a post in a Story and then pin that story to your profile, this new function makes that course of a lot easier and more easy. Its price noting that the brand new characteristic works equally to Twitters Pin to your profile...
04:29
Steam Deck Goes On Sale For Steam's Spring Sale Phoronix
Valve today started their first-ever Steam Spring Sale that runs through next week. In addition to sales on games, this is the first time Valve has offered the Steam Deck at a discounted price...
04:29
Twilek Pin
Prior to that, Duchamp and dadists explored the concept of what constitutes art. A portray of a pipe, a fountain produced from a urinal and other works challenged the role an artist performed in relation to the world around themselves. In Europe in the course of the 1800s, there have been actions to flee the excesses of the Baroque and Rococo periods and return to classical simplicity.
Instead, it drew lines from any level to any other point arbitrarily, sort of like an digital Etch-a-Sketch. Strictly Necessary Cookie should be enabled at all times so that we will save your preferences for cookie settings. Looking to partner with industry-leading brands? Gain entry to exclusive interviews with trade creatives, suppose pieces, development forecasts, guides and more. So much ink has been spilled into writing about Barbie, but nearly nothing has been written concerning the spaces during which she exists or the issues round her, Burrichter says.
The board puts the pins in the right state for flashing or boot mode. More info on the ESP32 Boot Mode Selection can be found here. Turning off your debit card is not a substitute for reporting your card lost or stolen. Contact us instantly if you imagine that unauthorized transactions have been made.
However, you can resolve which pins are UART, I2C, SPI, PWM, and so forth you just must assign them in the code. This is possible due to the ESP32 chips multiplexing feature. There are many questions on the means to use the ESP32 GPIOs. What pins do you have to keep away from using in your projects?
Talaski spoke to Insider about his work, which has since offered out, and he said he wished to combine his love for superheroes together with his love for classic pinup illustration. In current years, the singer has pushed the style boundaries and played around together with her beauty. After all, she isnt afraid to rock colourful hair or ultra-flashy fits on the pink carpet. Billie is the mastermind behind her magazine photoshoot, with British Vogue revealing she was impressed by a basic, old-timey pin-up look. Her sultry fashion, which was paying homage to pinup stars from the past, wasnt the only thing worth noting.
- But I assume all of the issues shes surrounded herself with are at all times a direct reflection of the issues that people will need and inspire to add each in each era.
- Working alongside other Pin-Up greats similar to Earl Moran, Zoe Mozert, and Rolf Armstrong, Elvgren created a minimal of twenty pinups a year.
- Orientalists might display nude alegorical figures in lush unique settings without reproach.
- The official roll out comes as Instagram confirmed to TechCrunch in April that it was testing the function.
Choosing a photographer to capture your recollections is no easy task it appears that evidently everyone is a photographe...
03:44
Amazon Linux 2023 released LWN.net
Amazon has released a new version of its vaguely Fedora-based, cloud-optimized distribution.
Lastand this policy is by far my favoriteAmazon Linux provides you with deterministic updates through versioned repositories, a flexible and consistent update Amazon Linux package repository, giving you control over how and when you absorb updates. By default, and in contrast with Amazon Linux 2, a dnf update command will not update your installed packages.
03:36
Amazon Linux 2023 Reaches GA, Built Atop Fedora Phoronix
03:36
Crypto exchange Fiatusdt leaked trove of users KYC data HackRead | Latest Cybersecurity and Hacking News Site
The database was exposed due to a misconfigured AWS S3 bucket.
This is a post from HackRead.com Read the original post: Crypto exchange Fiatusdt leaked trove of users KYC data
03:27
CVE-2023-24278 - Reflected XSS vulnerabilities in Squidex "/squid.svg" endpoint Open Source Security
Posted by Giannis Christodoulakos on Mar 16
Hello all,Squidex, a "headless" open source CMS framework was found to have two reflected XSS vulnerabilities in the "/squid.svg"
endpoint
affecting versions prior to 7.4.0. The vulnerabilities have been
CVE-2023-24278 was assigned to these vulnerabilities by MITRE.
The vulnerabilities affect both authenticated and unauthenticated users and allow for
malicious JavaScript...
03:26
SFC: John Deere's ongoing GPL violations: What's next LWN.net
The Software Freedom Conservancy calls out John Deere for failure to comply with the GPL and preventing farmers from repairing their own equipment.
This is a serious issue that goes far beyond one person wanting to fix their printer software, or install an alternative firmware on a luxury device. It has far-reaching implications for all farmers' livelihoods, for food security throughout the world, and for how we as a society choose to reward those who make our lives better, or stand in the way of empowering everyone to improve the world.
03:18
Pentagon Mobilized to Support Tech Startups After Bank Failure cryptogon.com
Via: Defense One: In the hours after Silicon Valley Bank collapsed on March 10, Pentagon officials who work directly with startups that develop national-security technologies grew increasingly concerned. Would startups that had money in the bank need to stop work? If that happened, would there be supply-chain disruptions? Would a company under financial stress put []
03:12
MQ-9 Sensor Video Showing Collision With Russian Su-27 Released cryptogon.com
Via: The Warzone: The U.S. Department of Defense has released a video showing part of the encounter between a U.S. Air Force MQ-9 Reaper and two Russian Su-27 Flanker fighter jets over the Black Sea on March 14 that resulted in the drone being lost. This seems to confirm that one of the Su-27s struck []
03:01
Create a libvirt network with Open vSwitch Linux.com
libvirts default Linux bridge imposes limitations with some advanced network features. Try using OVS to implement libvirt networks instead.
Read More at Enable Sysadmin
The post Create a libvirt network with Open vSwitch appeared first on Linux.com.
03:00
Linux 6.4 DRM To See New "imx25" Driver, 4K Support For Rockchip Display Driver Phoronix
Another set of drm-misc-next patches were submitted today for queuing in DRM-Next until the Linux 6.4 merge window kicks off this spring...
03:00
Humans (Mostly) Love Trash Robots IEEE Spectrum

My favorite approach to human-robot interaction is minimalism. Ive met a lot of robots, and some of the ones that have most effectively captured my heart are those that express themselves through their fundamental simplicity and purity of purpose. Whats great about simple, purpose-driven robots is that they encourage humans to project needs and wants and personality onto them, letting us do a lot of the human-robot-interaction (HRI) heavy lifting.
In terms of simple, purpose-driven robots, you cant do much better than a robotic trash barrel (or bin or can or what have you). And in a paper presented at HRI 2023 this week, researchers from Cornell explored what happened when random strangers interacted with a pair of autonomous trash barrels in NYC, with intermittently delightful results.
Whats especially cool about this, is how much HRI takes place around these robots that have essentially no explicit HRI features, since theyre literally just trash barrels on wheels. They dont even have googly eyes! However, as the video notes, theyre controlled remotely by humans, so a lot of the movement-based expression they demonstrate likely comes from a human sourcewhether or not thats intentional. These remote-controlled robots move much differently than an autonomous robot would. Folks who know how autonomous mobile robots work, expect such machines to perform slow, deliberate motions along smooth trajectories. But as an earlier paper on trash barrel robots describes, most people expect the opposite:
One peculiarity we discovered is that individuals appear to have a low confidence in autonomy, associating poor navigation and social mistakes with autonomy. In other words, people were more likely to think that the robot was computer controlled if they observed it getting stuck, bumping into obstacles, or ignoring peoples attempts to draw its attention.
We initially stumbled upon this perception when a less experienced robot driver was experimenting with the controls, actively moving the robot in strange patterns. An observer nearby asserted that the robot has to be autonomous. Its too erratic to be contro...
02:50
Polish intelligence dismantled a network of Russian spies Security Affairs
Polish intelligence dismantled a cell of Russian spies that gathered info on military equipment deliveries to Ukraine via the EU member.
Polish counter-intelligence has dismantled a cell of Russian spies that gathered information on the provisioning of military equipment to Ukraine via the EU member.
The ABW counter-intelligence agency has arrested nine people suspected of working for the Russian secret service, Polands Interior Minister Mariusz Kaminski told reporters. The suspects had been conducting espionage activities against Poland and preparing acts of sabotage on behalf of Russian intelligence services.
The suspects are foreigners from across Polands eastern border, Kaminski added.
Polish Defense Minister Mariusz Blaszczak also confirmed that the network has been dismantled by the countrys counter-intelligence.
Polish authorities charged six suspects with espionage and participation in an organized criminal group. The other three individuals arrested by the authorities were still being questioned. The member of the spy network received regular payment from the Russian secret services.
Kaminski also added that the cell was planning acts of sabotage to interfere with the delivery of military equipment and aid to Ukraine. The group was also involved in carrying out propaganda activity to destabilize Polish-Ukrainian relations as well as fomenting anti-NATO sentiment in Poland.
The suspects had also been preparing acts of sabotage meant to paralyze the delivery of military equipment, arms, and Ukraine aid, Kaminski declared.
The agents of the Polish Internal Security Agency ABW seized electronic equipment and GPS transmitters that once installed on trains carrying aid to Ukraine allowed Russian intelligence to track the shipments.
Local media, such as the Polish radio station RMF, reported that the spies installed hidden cameras on important railway routes and junctions, recording and transmitting data on traffic.
The Polish intelligence fears sabotage operations against railroads and critical infrastructure involved in the provisioning of military equipment to Ukraine.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs hacking, Polish intelligence)
The post...
02:37
Distribution Release: Murena 1.9 DistroWatch.com: News
The Murena project provides open source images for common smartphones, open source cloud-based storage, calendar, and backup solutions, and sells phones with /e/OS pre-installed. The project has announced the release of /e/OS 1.9 which includes several bug fixes, improvements, and security patches. "We are proud to deliver the....
02:34
Violence Was Widespread in Early Farming Society SoylentNews
Violence and warfare were widespread in many Neolithic communities across Northwest Europe:
Of the skeletal remains of more than 2300 early farmers from 180 sites dating from around 8000 4000 years ago to, more than one in ten displayed weapon injuries, bioarchaeologists found.
Contrary to the view that the Neolithic era was marked by peaceful cooperation, the team of international researchers say that in some regions the period from 6000BC to 2000BC may be a high point in conflict and violence with the destruction of entire communities.
The findings also suggest the rise of growing crops and herding animals as a way of life, replacing hunting and gathering, may have laid the foundations for formalised warfare.
[...] More than ten per cent showed damage potentially caused by frequent blows to the head by blunt instruments or stone axes. Several examples of penetrative injuries, thought to be from arrows, were also found.
Some of the injuries were linked to mass burials, which could suggest the destruction of entire communities, the researchers say.
Journal Reference:
Linda Fibiger, Torbjrn Ahlstrm, Christian Meyer, and Martin Smith,
Conflict, violence, and warfare among early farmers in
Northwestern Europe [open], PNAS, 2022. DOI: https://doi.org/10.1073/pnas.2209481119
Read more of this story at SoylentNews.
02:30
Chinese and Russian Hackers Using SILKLOADER Malware to Evade Detection The Hacker News
Threat activity clusters affiliated with the Chinese and Russian cybercriminal ecosystems have been observed using a new piece of malware that's designed to load Cobalt Strike onto infected machines. Dubbed SILKLOADER by Finnish cybersecurity company WithSecure, the malware leverages DLL side-loading techniques to deliver the commercial adversary simulation software. The development comes as
01:30
OpenSSH 9.3 has been released. It includes a couple of security fixes, as well as adding an option for hash-algorithm selection to ssh-keygen and an option that allows configuration checking without actually loading any private keys.
01:25
Civil Society Organizations Urge Ghanas Parliament to Reject Repressive Anti-LGBTQ+ Bill Deeplinks
With Ghana's 'Promotion of Proper Human Sexual Rights and Ghanaian Family Values Bill, 2021' set to undergo its second reading in the Ghanaian Parliament, EFF and other civil society partners are calling on the government of Ghana to immediately reject this draconian bill and commit instead to protecting the human rights of all people in Ghana.
As we've said before, this bill is not only an assault on the rights of LGBTQI+ people to exist, but it also represents a grave threat to freedom of expression. While Ghanaian law has long criminalized same-sex sexual activities, the new proposal goes much further by threatening up to five years in jail for publicly identifying as LGBTQ or "any other sexual or gender identity that is contrary to the binary categories of male and female."
The sentence increases if the offending person expresses their gender beyond or identifies outside of the so-called "binary gender." The bill also has a blanket prohibition on advocating for LGBTQI+ rights and explicitly assigns criminal penalties for speech posted online, and threatens online platformsspecifically naming Twitter and Meta products Facebook and Instagramwith criminal penalties if they do not restrict pro-LGBTQ content.
The letter continues:
As government officials, it is your duty to safeguard the accountability mechanisms that ensure Ghanas government adheres to its obligations to protect and promote human rights.
We therefore recommend that:
- The Committee on Constitutional, Legal and Parliamentary Affairs recommend that Parliament of Ghana reject the Promotion of Proper Human Sexual Rights and Ghanaian Family Values Bill, 2021 in its entirety.
- The Parliament of Ghana reject the Promotion of Proper Human Sexual Rights and Ghanaian Family Values Bill, 2021 in its entirety.
- The Attorney General revises his position on Clauses 12 and 13 of the bill, and recommends that the Parliament should reject the bill in its entirety.
- Members of Parl...
01:22
[$] Zero-copy I/O for ublk, three different ways LWN.net
The ublk subsystem enables the creation of user-space block drivers that communicate with the kernel using io_uring. Drivers implemented this way show some promise with regard to performance, but there is a bottleneck in the way: copying data between the kernel and the user-space driver's address space. It is thus not surprising that there is interest in implementing zero-copy I/O for ublk. The mailing lists have recently seen three different proposals for how this could be done.
01:02
Links 16/03/2023: OpenSSH 9.3 Released and WordPress 6.2 Release Candidate 2, Lapdock News Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Digital Restrictions (DRM)
- Monopolies
- Gemini* and Gopher
-
GNU/Linux
-
Applications
-
Ubuntubuzz SimulIDE The Free Electronic Workbench Software
...
-
-
01:00
The X Macro: A Historic Preprocessor Hack Hackaday

If we told you that a C preprocessor hack dated back to 1968,
youd be within your rights to remind us that C didnt exist in 1968.
However, assemblers with preprocessors did, and where there is a
preprocessor, there is an opportunity to do clever things. One of
those things is the so-called X macro, which saw a lot of use in
DEC System 10 code but probably dates back even earlier. You can
still use it today if you like, even though there are, of course,
other arguably better ways to get the same result. However, the
X macro can be very efficient, and you may well run
into it in some code, too.
Background
Preprocessing used to be a staple of programming. The idea is that code is manipulated purely at the text level before it is compiled. These days, languages with a preprocessor usually handle it as part of the compiler, but you can also use an external preprocessor like m4 for more sophisticated uses.
Modern languages tend to provide other ways to accomplish many of the tasks handled by the preprocessor. For example, if you have a constant you want to set at compile time, you could say:
int X = 32; y = X;
But then youve created a real variable along with the overhead that m...
00:39
Cryptojacking Group TeamTNT Suspected of Using Decoy Miner to Conceal Data Exfiltration The Hacker News
The cryptojacking group known as TeamTNT is suspected to be behind a previously undiscovered strain of malware used to mine Monero cryptocurrency on compromised systems. That's according to Cado Security, which found the sample after Sysdig detailed a sophisticated attack known as SCARLETEEL aimed at containerized environments to ultimately steal proprietary data and software. Specifically, the
00:21
Ohio, White Noise, and the Power of Words Over Things cryptogon.com
Via: Truthstream Media:
00:00
Linux Kernel Networking Driver Development Impacted By Russian Sanctions Phoronix
The US and western government sanctions around the Russian government and its defense industry/companies due to their war in Ukraine has caused interesting issues in the open-source world. A few days after ipmitool was archived/suspended on GitHub that turned out to be due to the current maintainer's affiliation with a Russian tech company, separately there is now a blocking of Linux kernel contributions from selected Russian developers...
Thursday, 16 March
23:55
AMDVLK 2023.Q1.3 Released With Various Fixes, TMZ For RDNA2 & Newer Phoronix
It's been nearly one month since AMDVLK 2023.Q1.2 as AMD's latest open-source Vulkan driver code drop while today it was replaced by AMDVLK 2023.Q1.3 as what will likely be their last Vulkan driver update for the quarter...
23:53
US Government Opens $2.5 Billion in Funding for Community EV Chargers SoylentNews
This includes hydrogen fuel stations:
[...] The Department of Transportation is now accepting applications for its $2.5 billion Charging and Fueling Infrastructure Discretionary Grant Program, which will hand out funds to cities, counties, regional governments and tribes to help deploy EV chargers, hydrogen fuel stations and other reduced-emissions systems near their residents.
Half of the program's funding will go to chargers and stations in "publicly accessible" places like parking facilities, parks and schools. The rest will install this equipment in "alternative fuel corridors" along highways to help with long-distance travel. The initial round of funding will make $700 million available, with the rest coming over the program's five-year span. Officials have to apply no later than May 30th.
The initiative is part of [a] broader campaign to build 500,000 charging stations by 2030, or about five times as many as there were in early 2022. The money, assigned as part of the Bipartisan Infrastructure Law, is meant to ensure charging access within 50 miles of someone's location in all 50 states, the District of Columbia and Puerto Rico. While the effort is intended to spur overall EV adoption, there's an added focus on underserved communities like some urban and rural areas.
A strong charging infrastructure is widely considered vital to successfully transitioning away from combustion engine cars. Existing stations can sometimes be crowded or unreliable, and don't always support the fast charging available with recent EVs.
Read more of this story at SoylentNews.
23:37
CVE-2023-24278 - Reflected XSS vulnerabilities in Squidex "/squid.svg" endpoint Open Source Security
Posted by Giannis Christodoulakos on Mar 16
Hello all,Squidex, a "headless" open source CMS framework was found to have two reflected XSS vulnerabilities in the "/squid.svg"
endpoint
affecting versions prior to 7.4.0. The vulnerabilities have been
CVE-2023-24278 was assigned to these vulnerabilities by MITRE.
The vulnerabilities affect both authenticated and unauthenticated users and allow for
malicious JavaScript...
22:56
Security updates for Thursday LWN.net
Security updates have been issued by Debian (firefox-esr and pcre2), Oracle (nss), Red Hat (kpatch-patch and nss), SUSE (java-11-openjdk, kernel, and python310), and Ubuntu (emacs24, ffmpeg, firefox, imagemagick, libphp-phpmailer, librecad, and openjpeg2).
22:22
Gaming company appoints AI bot as new CEO, sees record-breaking growth in stock market Lifeboat News: The Blog
Tang Yu, the AI CEO of the gaming company NetDragon Websoft, was assigned typical duties of the company that included reviewing high-level analytics, making leadership decisions, assessing risks, and fostering an efficient workplace. Tang Yu was the first CEO of a company that worked 24*7, without receiving compensation. The company said while appointing the AI chatbot as CEO that it will play a crucial role in the development of talents and ensuring a far and efficient workplace for all employees.
Tang Yus appointment highlights the Companys AI + management strategy and represents a major milestone of the Company towards being a Metaverse organization. Tang Yu will streamline process flow, enhance the quality of work tasks, and improve speed of execution. Tang Yu will also serve as a real-time data hub and analytical tool to support rational decision-making in daily operations, as well as to enable a more effective risk management system, NetDragon Websoft said in a blog post.
Interestingly, the AI bot helped the company in generating revenue. As per reports, the company outperformed the Hang Seng Index, which tracks the biggest companies listed in Hong Kong.
22:22
Worlds First Ethical Algorithm Lifeboat News: The Blog
This post is also available in:  (Hebrew)
(Hebrew)
Experts at the Technical University of Munich (TUM) have pioneered the worlds first ethical algorithm for autonomous vehicles, which could see autonomous driving become the norm globally.
The researchers ethical algorithm is significantly more advanced than its predecessors, as it fairly distributes levels of risks instead of operating on an either/or principle. The algorithm has been tested in 2,000 scenarios of critical conditions in various settings, such as streets in Europe, the US, and China. The innovation could improve the safety and uptake of autonomous vehicles worldwide.
22:22
A comprehensive circuit mapping study reveals many unexpected facts about the norepinephrine neurons in the brainstem Lifeboat News: The Blog
A small nucleus in the brainstem called locus coeruleus (literally the blue spot,) is the primary source of a major neuromodulator, norepinephrine (NE), an important mediator of the fight or flight response in animals. However, very little is known about the local connections of this small albeit critically important group of neurons. A recent pioneering study published in eLife from the laboratory of Dr. Xiaolong Jiang, investigator at the Jan and Dan Duncan Neurological Research Institute (Duncan NRI) at Texas Childrens Hospital and assistant professor at Baylor College of Medicine, now reveals the cellular composition and circuit organization of the locus coeruleus in adult mice.
In this study, we undertook the arduous task of mapping local connections of NE-producing neurons in the locus coeruleus, Dr. Jiang said. This is the first study of such an unprecedented magnitude and detail to be performed on the locus coeruleus, and in fact, on any monoamine neurotransmitter system. Our study has revealed that the neurons in the locus coeruleus have an unexpectedly rich cellular heterogeneity and local wiring logic.
Locus coeruleus (LC) is known to house the vast majority of norepinephrine-releasing neurons in the brain and regulates many fundamental brain functions including the fight and flight response, sleep/wake cycles, and attention control. Present in the pontine region of the brainstem, LC neurons sense any existential dangers or threats in our external environment and send signals to alert other brain regions of the impending danger.
22:00
Laser and Webcam Team Up for Micron-Resolution Flatness Measurements Hackaday

When you want to measure the length, breadth, or depth of an object, there are plenty of instruments for the job. You can start with a tape measure, move up to calipers if you need more precision, or maybe even a micrometer if its a really critical dimension. But what if you want to know how flat something is? Is there something other than a straightedge and an eyeball for assessing the flatness of a surface?
As it turns out, there is: a $15 webcam and a cheap laser level will do the job, along with some homebrew software and a little bit of patience. At least thats what [Bryan Howard] came up with to help him assess the flatness of the gantry he fabricated for a large CNC machine hes working on.
21:58
Multiple threat actors exploited Progress Telerik bug to breach U.S. federal agency Security Affairs
Multiple threat actors exploited a critical flaw in Progress Telerik to breach an unnamed US federal agency, said the US government.
A joint advisory issued by the Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), and Multi-State Information Sharing and Analysis Center (MS-ISAC) revealed that multiple threat actors, including a nation-state actor, exploited a critical vulnerability in Progress Telerik to breach an unnamed US federal agency.
The three-year-old vulnerability, tracked as CVE-2019-18935 (CVSS score: 9.8), is a .NET deserialization issue that resides in the Progress Telerik UI for ASP.NET AJAX. Exploitation can result in remote code execution.
CISA analysts determined that multiple cyber threat actors, including an Advanced Persistent Threat (APT) actor, exploited a .NET deserialization vulnerability in Progress Telerik user interface for ASP.NET AJAX. Exploitation of this vulnerability allowed malicious actors to successfully execute remote code on a federal civilian executive branch (FCEB) agencys Microsoft Internet Information Services (IIS) web server. reads the advisory. Actors were then able to upload malicious dynamic-link library (DLL) files (some masqueraded as portable network graphics [PNG] files) to the C:\Windows\Temp\ directory.
Threat actors exploited the vulnerability to execute arbitrary code on a Microsoft Internet Information Services (IIS) web server used by a federal civilian executive branch (FCEB) agency.
In 2020 and 2021, this flaw was included by the US National Security Agency (NSA) in the list of the top 25 vulnerabilities exploited by Chinese state-sponsored hacking groups in attacks in the wild.
The flaw was also used in the past by the NetWalker ransomware gang in its operations.
The joint alert recommends network defenders review the Malware Analysis Report, MAR-10413062-1.v1 Telerik Vulnerability in U.S. Government IIS Server, to reference CISAs analysis for the identified malicious files.
According to the MAR, CISA received 18 files for analysis from a forensic analysis engagement conducted at a Federal Civilian Executive Branch (FCEB)...
21:51
NVIDIA Improving wlroots For Better Dual-GPU Gaming Performance Phoronix
A NVIDIA engineer has opened up a merge request to improve the wlroots Wayland library so compositors based on it can enjoy better gaming performance for dual-GPU systems, namely around laptops sporting a discrete NVIDIA GPU but can help other GPU hardware/drivers too...
21:43
LibreSSL 3.7.1 Released OpenBSD Journal
With a
message to openbsd-announce and other lists, Brent
Cook (bcook@) announced the release of LibreSSL 3.7.1, with numerous
improvements.
The announcement reads,
Subject: LibreSSL 3.7.1 Released From: Brent Cook <busterb () gmail ! com> We have released LibreSSL 3.7.1, which will be arriving in the LibreSSL directory of your local OpenBSD mirror soon. This is the final development release for the 3.7.x branch, and we appreciate additional testing and feedback before the stable release coming soon with OpenBSD 7.3
21:19
Qualcomm Publishes Open-Source Compiler & User-Space For Their Cloud AI Accelerator Phoronix
Last month Qualcomm published updated patches for their Cloud AI 100 kernel driver to support this inference accelerator. The Qualcomm engineers said at the time that their user-space driver and associated compiler would be published shortly. That panned out and the user-space portion of this open-source AI inference stack was recently published...
21:08
NASA's Latest Request for Cash Includes Big Plans for a Deorbiting ISS 'Space Tug' SoylentNews
NASA is staying focused on the Artemis lunar program, its Moon to Mars objectives, and maintaining a presence in low Earth orbit as part of the agency's proposed budget for 2024. The space agency also has a new item on its annual wishlist: a space tug to deorbit the International Space Station (ISS) at the end of its life.
[...] NASA's proposed budget includes $180 million for developing a deorbit capability for the ISS by the end of 2030. Should the budget be approved, the space agendcy would call upon the private sector to come up with a space tug concept to lower the orbit of the ISS so that it can reenter and burn up through Earth's atmosphere. NASA had previously suggested using Russia's Progress cargo spacecraft to deorbit the ISS, and apparently that option is still on the table as well.
[...] Still, NASA's Artemis program sits at the top of the space agency's to-do list, snagging $8.1 billion from the budget (an increase from last year's $7.5 billion). The plan still stands for NASA to land humans on the Moon as early as 2025, and start on the construction of the Lunar Gateway, an outpost orbiting the Moon that will house astronauts and scientific research.
The budget request will allocate $2.5 billion towards the Space Launch System (SLS) rocket, which was used for the liftoff of the Artemis 1 mission in November 2022, "to focus on successful completion of Artemis 2, and make necessary preparations for Artemis 3 and 4, which includes the enhanced upper stage configuration and other upgrades," Schaus said during the call.
Read more of this story at SoylentNews.
21:00
Small Modular Reactors: Capital Funding, Financing & Economic Viability IEEE Spectrum

New nuclear looks different, which requires new types of financing. New investment and partnerships are seemingly occurring every day across the industry, including SK Groups $250million investment into Terrapower, and X-energys partnership with Dow Chemical.
What can be done to encourage financial investment and improve the economic viability and the ROI of SMRs? How does new nuclear differ, and how do we finance that?
Reuters Events latest report Capital Funding, Financing & Economic Viability of SMRs dives into the vehicles that will assist with advancing financing to support SMRs and advanced reactors deployment and commercialization. What to expect from the report:
- Expert insight into funding developments analysis of new types of funding for SMRs and advanced reactors, who they would help, and means to ensure financing. Deep dive into how utilities can help standardized deployment and licensing approaches
- Securing financing for new nuclear: Advancing financing is key for SMR commercialization. How can new forms of financing assist start-up companies who could move away from simply talking, and towards signing deals?
- We need to see operators signing deals - The CNSC has 10 vendors in pre-design review, 2 of whom propose to design a license for the model. SMRs should be more investable and easier for licensing, yet what are the blockers for operators putting pen to paper?
20:59
Qt 6.4.3 Released With 300+ Fixes Phoronix
Qt 6.4.3 is out today as the newest point release to this current stable series of the Qt6 tool-kit. This release is another big one with 300+ fixes in tow...
20:46
Authorities Shut Down ChipMixer Platform Tied to Crypto Laundering Scheme The Hacker News
A coalition of law enforcement agencies across Europe and the U.S. announced the takedown of ChipMixer, an unlicensed cryptocurrency mixer that began its operations in August 2017. "The ChipMixer software blocked the blockchain trail of the funds, making it attractive for cybercriminals looking to launder illegal proceeds from criminal activities such as drug trafficking, weapons trafficking,
20:43
Mold 1.11 High Performance Linker Released With Initial POWER10 Support Phoronix
20:22
Stunning room-temperature-superconductor claim is retracted Lifeboat News: The Blog
Retraction undermines the bold claim by physicists who said their material conducted electricity without resistance at 15 C.
20:22
Hornetsecurity VM Backup V9 protects users against ransomware threats Help Net Security
Hornetsecurity launched VM Backup V9 the newest version of its virtual machine (VM) backup, replication and recovery solution. This latest iteration offers ransomware protection leveraging immutable cloud storage on Wasabi and Amazon S3, with Microsoft Azure soon to follow. This new key feature enables customers to protect their backup data from ransomware by making their data tamper-proof for a defined period. A recent Hornetsecurity study revealed that 15% of ransomware attacks specifically targeted backups, More
The post Hornetsecurity VM Backup V9 protects users against ransomware threats appeared first on Help Net Security.
19:47
CISA adds Adobe ColdFusion bug to Known Exploited Vulnerabilities Catalog Security Affairs
US CISA added an actively exploited vulnerability in Adobe ColdFusion to its Known Exploited Vulnerabilities Catalog.
U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical vulnerability in Adobe ColdFusion, tracked as CVE-2023-26360 (CVSS score: 8.6), to its Known Exploited Vulnerabilities Catalog.
This week Adobe released security updates for ColdFusion versions2021 and2018 to resolve the critical flaw CVE-2023-26360 that was exploited in very limited attacks.
Adobe is aware that CVE-2023-26360 has been exploited in the wild in very limited attacks targeting Adobe ColdFusion. reads the advisory published by the company.
The vulnerability is an Improper Access Control that can allow a remote attacker to execute arbitrary code. The vulnerability could also lead toarbitrary file system read and memory leak.
According to Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities, FCEB agencies have to address the identified vulnerabilities by the due date to protect their networks against attacks exploiting the flaws in the catalog.
Experts recommend also private organizations review the Catalog and address the vulnerabilities in their infrastructure.
CISA orders federal agencies to fix this flaw by April 5, 2023.
The US Agency also added the following vulnerabilities to the catalog that must be addressed by April 4, 2023.
- CVE-2023-23397 Microsoft Office Outlook Privilege Escalation Vulnerability.
- CVE-2023-24880 Microsoft Windows SmartScreen Security Feature Bypass Vulnerability.
- CVE-2022-41328 Fortinet FortiOS Path Traversal Vulnerability.
Follow me on Twitter: @securityaffairs and...
19:46
After ACE Shuts Down Streamzz, Pirates Demand Refunds But Get Zebras Instead TorrentFreak
 As part of its relentless campaign to shut down as many
pirate sites as possible, on Wednesday the Alliance for Creativity
and Entertainment reported yet another big win.
As part of its relentless campaign to shut down as many
pirate sites as possible, on Wednesday the Alliance for Creativity
and Entertainment reported yet another big win.
The anti-piracy coalitions latest victim is Streamzz, a stream hosting platform that reportedly supplied over 75,000 movies and 15,000 TV episodes, which helped to fuel more than 60 pirate streaming sites.
ACE says that a third of the sites seven million monthly visits can be attributed to users in Germany, where Streamzz itself was based. Germany is also the home of ACE member Constantin Film, a film production and distribution company that worked with the coalition to take Streamzz down.
ACE Celebrates Win, Streamzz Infuriates Users
In an announcement Wednesday, ACE chief Jan van Voorn said that the closure of Streamzz shows that the coalition is capable of targeting pirates no matter where they exist in the chain of supply.
The shutdown of Streamzz is fresh proof that no one in the content piracy ecosystem whether theyre a streaming service, video streaming host or anything in between is above the law. We will target piracy services of various kinds in order to protect the global creative economy, he said.
Some users of Streamzz, meanwhile, have concerns about their own economies.
How it Started.
Streamzz (or simply Streamz) has been around since 2019, operating from several different domains. In a 2020 interview with Tarnkappe, one of the sites operators declined to comment on future successes leading to the sipping of cocktails on a tropical beach. We just let ourselves be surprised, he said.
On March 14, three of the sites domains streamz.vg, streamz.cc and streamz.tw had their records updated to reveal their new owner: Motion Picture Association, Inc. Domains still to be taken over currently deliver a message: We currently have server problems. Please understand.
19:30
Amazon Linux 2023: Create and execute cloud-based applications with enhanced security Help Net Security
AWS has been offering Amazon Linux, a cloud-optimized Linux distribution, since 2010. This distributions latest version is now available. Amazon Linux 2023 is provided at no additional charge. Standard Amazon EC2 and AWS charges apply for running EC2 instances and other services. This distribution includes full support for five years. By deploying your workloads on Amazon Linux 2023, you can enjoy three advantages: a robust security standard, a dependable lifecycle, and a uniform update process. More
The post Amazon Linux 2023: Create and execute cloud-based applications with enhanced security appeared first on Help Net Security.
19:17
Appian Protect safeguards sensitive and highly regulated data Help Net Security
Appian introduced Appian Protect, a new set of security offerings that delivers reliable data monitoring and end-to-end encryption for cloud and mobile applications. Appian Protect gives Appian customers increased control over their security posture, with top-tier encryption capabilities, 24x7x365 monitoring, defense-in-depth data protection, and a host of compliance accreditations. Appian is committed to providing the most trusted platform for complete process automation. Customers using Appian Protect receive all the powerful security features embedded in the More
The post Appian Protect safeguards sensitive and highly regulated data appeared first on Help Net Security.
19:00
Wooden ITX PC Case Smacks Of Sophistication Hackaday

Computer cases have come a long way from the ugly beige boxes of the early 2000s. Still, if it was going to sit on his desk, [MXC Builds] wanted something with a little more class. His custom Ironbark ITX PC seems to fit the aesthetic nicely.
The cases outer shell is ironbark wood cut at 45 degrees and joined for a beautiful waterfall edge (the wood grain seems to flow uninterrupted). The power supply was heavily modified to take a thinner but larger fan, and a new cover and intake grill were 3D printed. As there were no mounting holes on the bottom of the power supply, he printed a bracket with spring clips to hold the PSU securely. Next, he routed a PCI riser cable to the other side of the internal panel so the GPU could mount on the back. He cu...
18:26
NASA Reveals Prototype Spacesuit The First Woman On The Moon Will Wear Lifeboat News: The Blog
In the first public event presenting the Artemis III Lunar Space Suit, NASA revealed the prototype that will be worn by the first woman and person of color to go to the Moon. Made by Axiom Space, the next-gen spacesuit will eventually be white, but is currently on display with a black cover while they finalize the top layers final design.
The Axiom Extravehicular Mobility Unit, or AxEMU (fingers crossed this is the brief for the missions zero-gravity indicator plushie), got a grand reveal at Space Center Houstons Moon 2 Mars Festival. As a prototype, itll join a fleet of training suits sent to NASA later this year so that astronauts can begin preparing for the next crewed lunar landing, Artemis III, set to take place in 2025.
When that first woman steps down on the surface of the Moon on Artemis III, shes going to be wearing an Axiom Spacesuit, said associate administrator for NASA Bob Cabana at the reveal. Were going back to the Moon but were going to the South Pole this time. Why are we going there? Its challenging. .
18:25
The First Complete Brain Map of an Insect May Reveal Secrets for Better AI Lifeboat News: The Blog

Breakthroughs dont often happen in neuroscience, but we just had one. In a tour-de-force, an international team released the full brain connectivity map of the young fruit fly, described in a paper published last week in Science. Containing 3,016 neurons and 548,000 synapses, the mapcalled a connectomeis the most complex whole-brain wiring diagram to date.
Its a wow, said Dr. Shinya Yamamoto at Baylor College of Medicine, who was not involved in the work.
Why care about a fruit fly? Far from uninvited guests at the dinner table, Drosophila melanogaster is a neuroscience darling. Although its brain is smaller than a poppy seeda far cry from the 100 billion neurons that power human brainsthe flys neural system shares similar principles to those that underlie our own brains.
18:25
A Better Production Line for Atom Arrays Lifeboat News: The Blog
A new algorithm can organize hundreds of atoms into pristine patternsincluding a honeycomb lattice, a fractal called a Sierpiski triangle, and a lions head.
18:25
The Cosmos as a Colloid Lifeboat News: The Blog
A new methodology for analyzing the 3D distribution of galaxies borrows techniques from the study of colloids and other disordered materials.
18:25
The Impact of Ions on DNA Lifeboat News: The Blog
A study of the electron excitation response of DNA to proton radiation has elucidated mechanisms of damage incurred during proton radiotherapy.
Radiobiology studies on the effects of ionizing radiation on human health focus on the deoxyribonucleic acid (DNA) molecule as the primary target for deleterious outcomes. The interaction of ionizing radiation with tissue and organs can lead to localized energy deposition large enough to instigate double strand breaks in DNA, which can lead to mutations, chromosomal aberrations, and changes in gene expression. Understanding the mechanisms behind these interactions is critical for developing radiation therapies and improving radiation protection strategies. Christopher Shepard of the University of North Carolina at Chapel Hill and his colleagues now use powerful computer simulations to show exactly what part of the DNA molecule receives damaging levels of energy when exposed to charged-particle radiation (Fig. 1) [1]. Their findings could eventually help to minimize the long-term radiation effects from cancer treatments and human spaceflight.
The interaction of radiation with DNAs electronic structure is a complex process [2, 3]. The numerical models currently used in radiobiology and clinical radiotherapy do not capture the detailed dynamics of these interactions at the atomic level. Rather, these models use geometric cross-sections to predict whether a particle of radiation, such as a photon or an ion, crossing the cell volume will transfer sufficient energy to cause a break in one or both of the DNA strands [4 6]. The models do not describe the atomic-level interactions but simply provide the probability that some dose of radiation will cause a population of cells to lose their ability to reproduce.
18:25
The experimental observation of quantum avalanches in a many-body localized system Lifeboat News: The Blog
Strongly correlated systems are systems made of particles that strongly interact with one another, to such an extent that their individual behavior depends on the behavior of all other particles in the system. In states that are far from equilibrium, these systems can sometimes give rise to fascinating and unexpected physical phenomena, such as many-body localization.
Many-body localization occurs when a system made of interacting particles fails to reach thermal equilibrium even at high temperatures. In many-body localized systems, particles thus remain in a state of non-equilibrium for long periods of time, even when a lot of energy is flowing through them.
Theoretical predictions suggest that the instability of the many-body localized phase is caused by small thermal inclusions in the strongly interacting system that act as a bath. These inclusions prompt the delocalization of the entire system, through a mechanism that is known as avalanche propagation.
18:22
2B and 8 Years On, Still No Emergency Services Network SoylentNews
And not even a tentative date for a system go-live either:
By the end of this month, the UK Home Office will have spent just under 2 billion ($2.4 billion) on a new critical communications network for the country's police, fire and ambulance services with nothing to show for it, according to a report by the National Audit Office (NAO).
Even worse, the multi-year project has fallen further behind schedule and the Home Office cannot say when the replacement system will be operational, according to the spending watchdog.
The Emergency Services Network (ESN) program first kicked off in 2015 the idea being that it would fully replace the existing near-indestructible Airwave units and system, which uses the Terrestrial Trunked Radio (TETRA) network; would "cost less"; and would provide users with access to modern mobile data. ESN was supposed to move critical emergency services off of the tried and tested TETRA (which, among other things, you can access ubiquitously across the London Underground) and onto LTE radio comms with some obvious modifications and associated features like the push-to-talk ESN Direct.
[...] The UK's Competition and Markets Authority started a probe into the matter in 2021, with the PAC already noting in 2019 that Motorola's involvement in both the new and old contract had led "to perverse incentives" and put "the department in a weak negotiating position." Motorola has denied conflict of interest and said last year that "Airwave, over its life, is a much better deal for the UK taxpayer than the Home Office originally agreed."
[...] In January, eight years after the first proposals for a new system to replace the outdated Airwave platform were unveiled, the Home Office and Motorola Solutions agreed to end their work on the ESN contract in December 2023.
The Home Office, meanwhile, does not currently know when ESN will be ready or how much it will ultimately cost.
Read more of this story at SoylentNews.
18:12
What's Wrong with Manufacturing? The Hacker News
In last year's edition of the Security Navigator we noted that the Manufacturing Industry appeared to be totally over-represented in our dataset of Cyber Extortion victims. Neither the number of businesses nor their average revenue particularly stood out to explain this. Manufacturing was also the most represented Industry in our CyberSOC dataset contributing more Incidents than any other
18:01
IRC Proceedings: Wednesday, March 15, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-150323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-150323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-150323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-150323.gmi
Over HTTP:
|
... |
18:00
Superhuman artificial intelligence can improve human decision-making by increasing novelty Terra Forming Terra
Dr. Michael Salla: JP Mission to Ancient Artifacts and Civilizations Found in the Grand Canyon Terra Forming Terra
NY Times: Biden Administration Expected to Move Ahead on a Major Oil Project in Alaska Terra Forming Terra

17:34
Multiple Hacker Groups Exploit 3-Year-Old Vulnerability to Breach U.S. Federal Agency The Hacker News
Multiple threat actors, including a nation-state group, exploited a critical three-year-old security flaw in Progress Telerik to break into an unnamed federal entity in the U.S. The disclosure comes from a joint advisory issued by the Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), and Multi-State Information Sharing and Analysis Center (MS-ISAC).
17:23
Links 16/03/2023: OpenSSL 3.1 Released, 10,000 More Staff Cut in Facebook, and Windows Loses 10% in Speed Techrights
-
GNU/Linux
-
Applications
-
Linux Links Drop-in replacements for Core Utilities
The GNU Core Utilities or coreutils is a package of GNU software containing implementations for many of the basic tools, such as cat, ls, and rm, which are used on Unix-like operating systems.
-
-
Instructionals/Technical
-
Install Audacious 4.3 On Ubuntu / Linux Mint
In this article, well show you how to install Audacious 4.3 on Ubuntu or Linux Mint system, step by step.
Audacious is a free and open-source audio player for Linux and other Unix-like operating systems.
It is known for its lightweight, customizable, and user-friendly interface, making it a favorite among Linux users who prefer a simple and straightforward music player.
-
Linux Capable How to Install Bmon on Ubuntu 22.04 or 20.04
...
-
-
17:00
Cyber attribution: Vigilance or distraction? Help Net Security
Cyber attribution is a process by which security analysts collect evidence, build timelines and attempt to piece together evidence in the wake of a cyberattack to identify the responsible organization/individuals. Cyber threat attribution stems from the core psychology of a human being. Fritz Heider, who is considered to be the father of attribution theory, explained it as the way humans reconcile perceptions and observations in their quest for understanding. Attribution is not a problem limited More
The post Cyber attribution: Vigilance or distraction? appeared first on Help Net Security.
16:00
Raspberry Pi Adds Second Laptop Monitor Hackaday

If you have a cheap laptop and you realize you cant connect a second monitor to it, what do you do? Well, if you are [Pierre Couy], you grab a Raspberry Pi and put together a virtual screen solution.
Like all good projects, this one started with some goals and requirements:
- Low latency
- Redable text
- At least 10 frames per second
- Fast catch up if the remote screen falls behind
- Low-bitrate encoding; no hardware acceleration
- A DHCP server on the Pi to manage the network
- Power control for the attached monitor
Since Linux has such flexibility, it was possible to stitch the system together using existing components. The versatile ffmpeg handled the streaming. There was, however, a fair amount of troubleshooting necessary to track down some issues using Wireshark.
If you want to try something like this yourself, the files are on GitHub. Honestly, though, the best part of this project is seeing how the tools interact and the troubleshooting steps. For most laptops, this...
16:00
How two-step phishing attacks evade detection and what you can do about it Help Net Security
Phishing attacks have become increasingly prevalent and sophisticated, making it more difficult for individuals to protect themselves from these scams. In this Help Net Security video, Ofek Ronen, Software Engineer at Perception Point, discusses two-step phishing attacks, which are not only dangerous but also evasive, making them even more challenging to detect and avoid. Understanding the dangers of two-step phishing attacks and knowing what to look out for is critical in protecting yourself from falling More
The post How two-step phishing attacks evade detection and what you can do about it appeared first on Help Net Security.
15:47
CISA Issues Urgent Warning: Adobe ColdFusion Vulnerability Exploited in the Wild The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on March 15 added a security vulnerability impacting Adobe ColdFusion to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The critical flaw in question is CVE-2023-26360 (CVSS score: 8.6), which could be exploited by a threat actor to achieve arbitrary code execution. "Adobe ColdFusion
15:36
The AI Hype Bubble is the New Crypto Hype Bubble SoylentNews
Back in 2017 Long Island Ice Tea known for its undistinguished, barely drinkable sugar-water changed its name to "Long Blockchain Corp." Its shares surged to a peak of 400% over their pre-announcement price. The company announced no specific integrations with any kind of blockchain, nor has it made any such integrations since.
[...] The most remarkable thing about this incredibly stupid story is that LBCC wasn't the peak of the blockchain bubble rather, it was the start of blockchain's final pump-and-dump. By the standards of 2022's blockchain grifters, LBCC was small potatoes, a mere $138m sugar-water grift.
[...] They were amateurs. Their attempt to "make fetch happen" only succeeded for a brief instant. By contrast, the superpredators of the crypto bubble were able to make fetch happen over an improbably long timescale, deploying the most powerful reality distortion fields since Pets.com.
[...] Like any Ponzi scheme, crypto was a way to separate normies from their savings through the pretense that they were "investing" in a vast enterprise but the only real money ("fiat" in cryptospeak) in the system was the hardscrabble retirement savings of working people, which the bubble's energetic inflaters swapped for illiquid, worthless shitcoins.
We've stopped believing in the illusory billions. Sam Bankman-Fried is under house arrest. But the people who gave him money and the nimbler Ponzi artists who evaded arrest are looking for new scams to separate the marks from their money.
Take Morganstanley, who spent 2021 and 2022 hyping cryptocurrency as a massive growth opportunity:
Today, Morganstanley wants you to know that AI is a $6 trillion opportunity.
Read more of this story at SoylentNews.
15:30
Navigating the future of digital identity Help Net Security
1,450 global consumers experiences with passwordless authentication, hybrid identities, and ownership over personally identifiable information reveal that they want more convenience when it comes to identity credentials, according to Entrust. The pace of commerce and business is moving faster than ever before, and as a result, our lives are becoming more digital, said Jenn Markey, VP of Payments & Identity at Entrust. As organizations and governments bring more digital services online, its becoming clear that More
The post Navigating the future of digital identity appeared first on Help Net Security.
15:29
The Aftermath of Ola Binis Unanimous Acquittal by Ecuadorian Court Deeplinks
On January 31, the Swedish free software developer and computer security expert Ola Bini was declared innocent in a unanimous verdict by a three-judge tribunal in Ecuadorthe Court of Criminal Guarantees of Pichincha. After almost four years of a criminal prosecution plagued with irregularities, delays, and due process violations, his right to a fair trial has finally prevailed. EFF, Access Now, APC, Fundacin Karisma, and other digital and human rights groups that have been monitoring the case celebrate the ruling.
But more than a month after the ruling, we continue to see the pattern of delays surrounding the case again. The oral sentence stated in Januarys hearing has yet to be published in written form, and the precautionary measures against Bini remain in force. Despite his acquittal, the security expert still cant leave Ecuador, use his bank accounts, or get back any of several of his devices seized in 2019. In the meantime, the Prosecutors Office and Ecuador's National Telecommunications Corporation (CNT) have already shown their intention to appeal once they receive the formal notification of the sentence.
Bini himself has stressed the pioneering nature of the ruling. He said it was the first time an Ecuadorian court had analyzed the issue of access to a computer system and, more importantly, resisted setting a broad interpretation of unauthorized access that would seriously endanger the beneficial work of security researchers and the vital...
15:06
OpenSSH 9.3/9.3p1 released OpenBSD Journal
On , the release of version 9.3 of OpenSSH was announced:
15:00
Rushed cloud migrations result in escalating technical debt Help Net Security
While 93% of CIOs expect an increase in IT budgets for 2023, 83% of them are feeling pressured to stretch their budgets even further than before, with a focus on managing cloud costs more efficiently and addressing the growing issue of technical debt, according to SoftwareOne. The survey found that 72% of CIOs admit they are behind in their digital transformation because of this technical debt, which is of particular concern as 92% of CIOs More
The post Rushed cloud migrations result in escalating technical debt appeared first on Help Net Security.
14:45
Virtual patching: Cut time to patch from 250 days to Help Net Security
Unpatched vulnerabilities are responsible for 60% of all data breaches. The Department of Homeland Security has estimated that the proportion of breaches stemming from unpatched flaws may be as high as 85%. Timely patching is an important aspect of managing vulnerabilities but is not always achievable in every circumstance. Indusfaces State of Application Security 2022 report findings show that you could block complex attacks by using virtual patching through a WAF. Over 800 million attacks More
The post Virtual patching: Cut time to patch from 250 days to <1 day appeared first on Help Net Security.
13:40
Links 15/03/2023: Transmission 4.0.2 and Lots in Geminispace Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Hardware
- Health/Nutrition/Agriculture
- Linux Foundation
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Monopolies
- Gemini* and Gopher
-
GNU/Linux
-
Kernel Space
-
InfoWorld How eBPF unlocks cloud native innovation
Barbara Liskovthe brilliant Turing Award winner whose career inspired so much modern thinking around distributed computingwas fond of calling out the power of abstraction and it...
-
-
13:16
[$] LWN.net Weekly Edition for March 16, 2023 LWN.net
The LWN.net Weekly Edition for March 16, 2023 is available.
13:13
NEW 'Off The Hook' ONLINE 2600 - 2600: The Hacker Quarterly
NEW 'Off The Hook' ONLINE
Posted 16 Mar, 2023 2:13:51 UTC
The new edition of Off The Hook from 03/15/2023 has been archived and is now available online.
Alex is in London, testing the new studio setup, car manufacturers are phasing out AM radios, Volkswagen charges police to track stolen vehicle, some cars will be able to repossess themselves, Elon Musk says ChatGPT is too woke, Russia fines Wikipedia for misinformation, listener email.
13:00
Unconventional Computing Laboratory Grows Its Own Electronics Hackaday

While some might say were living in a cyberpunk future already, one technology thats conspicuously absent is wetware. The Unconventional Computing Laboratory is working to change that.
Previous work with slime molds has shown useful for spatial and network optimization, but mycelial networks add the feature of electrical spikes similar to those found in neurons, opening up the possibility of digital computing applications. While the work is still in its early stages, the researchers have already shown how to create logic gates with these fantastic fungi.
Long-term, lead researcher [Andrew Adamatzky] says, We can say Im planning to make a brain from mushrooms. That goal is quite awhile away, but using wetware to build low power, self-repairing fungi devices of lower complexity seems like it might not be too far away. We think this might b...
12:51
US Court Rules Uber and Lyft Workers are Contractors SoylentNews
The California appeals court found that a labour measure, known as Proposition 22, was largely constitutional.
Labour groups and some workers had opposed the measure, saying it robbed them of rights like sick leave.
The firms say the proposition protects other benefits such as flexibility.
The latest ruling overturns a decision made by a lower court in California in 2021, which found that Proposition 22 affected lawmakers' powers to set standards at the workplace.
The state of California and a group representing Uber, Lyft and other firms appealed against the decision.
Read more of this story at SoylentNews.
12:00
NETGEAR launches Nighthawk RS700 WiFi 7 router Help Net Security
With the rise of faster multi-gig internet speeds now available to more and more households, the growing number of connected devices per family and the ever-increasing growth of bandwidth hungry 4K/8K video streaming, HD Zoom calls, hybrid collaborative graphics-intensive work, highly interactive real-time gaming and AR/VR applications and experiences, WiFi continues to evolve to support faster speeds, lower latency and increased capacity. While WiFi 6E opened the 6GHz band as a superhighway for the latest, More
The post NETGEAR launches Nighthawk RS700 WiFi 7 router appeared first on Help Net Security.
11:26
Two US Citizens Charged for Hacking into DEA Portal in 2022 HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
Both suspects, Sagar Steven Singh and Nicholas Ceraolo, were reportedly members of a notorious cybercrime group, ViLE. Two
This is a post from HackRead.com Read the original post: Two US Citizens Charged for Hacking into DEA Portal in 2022
11:00
ReversingLabs adds secrets detection capabilities to SSCS platform Help Net Security
ReversingLabs has unveiled new secrets detection features within its Software Supply Chain Security (SSCS) platform. ReversingLabs improves secrets detection coverage by providing teams with the context and transparency needed to prioritize developers remediation efforts, reduce manual triage fatigue, and improve security controls that prevent secrets leaks. These new capabilities underscore ReversingLabs commitment to address growing software supply chain complexity and increasingly sophisticated threats. Our comprehensive solution enables teams to securely control the release of software More
The post ReversingLabs adds secrets detection capabilities to SSCS platform appeared first on Help Net Security.
11:00
Smashing Security podcast #313: Tesla twins and deepfake dramas Graham Cluley
The twisted tale of the two Teslas, and a deepfake sandwich. All this and more is discussed in the latest edition of the "Smashing Security" podcast by computer security veterans Graham Cluley and Carole Theriault.
11:00
HPR3814: 2022-2023 New Years Show Episode 3 Hacker Public Radio
Episode #3 wikipedia: The Drunkard's Walk: How Randomness Rules Our Lives. wikipedia: Lactose intolerance is a common condition caused by a decreased ability to digest lactose, a sugar found in dairy products. uncyclopedia: A tree hugging hippy is a hippy who hugs trees often found in Bezerkley, California. Many people think that there is much more to say about tree hugging hippies than just the fact that they hug trees, but reality is, that there is not really very much more to say about tree hugging hippies than that they hug trees. merriam-webster: A vegetarian is a person who does not eat meat : someone whose diet consists wholly of vegetables, fruits, grains, nuts, and sometimes eggs or dairy products. merriam-webster: A vegan is a strict vegetarian who consumes no food (such as meat, eggs, or dairy products) that comes from animals. wikipedia: Liberalism is a political and moral philosophy based on the rights of the individual, liberty, consent of the governed, political equality and equality before the law. Liberals espouse various views depending on their understanding of these principles. wikipedia: Conservatism is a cultural, social, and political philosophy that seeks to promote and to preserve traditional institutions, practices, and values. The central tenets of conservatism may vary in relation to the culture and civilization in which it appears. ssa: Social Security is committed to helping maintain the basic well-being and protection of the people we serve. We pay benefits to about 64 million people including retirees, children, widows, and widowers. From birth, to marriage, and into retirement, we are there to provide support throughout life's journey. wikipedia: In physiology, dehydration is a lack of total body water, with an accompanying disruption of metabolic processes. It occurs when free water loss exceeds free water intake, usually due to exercise, disease, or high environmental temperature. Mild dehydration can also be caused by immersion diuresis, which may increase risk of decompression sickness in divers. wikipedia: An emergency medical technician (EMT), also known as an ambulance technician, is a health professional that provides emergency medical services. EMTs are most commonly found working in ambulances. In English-speaking countries, paramedics are a separate profession that has additional educational requirements, qualifications, and scope of practice. wikipedia: Post-traumatic stress disorder (PTSD) is a mental and behavioral disorder that can develop because of exposure to a traumatic event, such as sexual assault, warfare, traffic collisions, child abuse, domestic violence, or other threats on a person's life. anxiety: Anxiety is the mind and body's reaction to stressful, dangerous, or unfamiliar situations. It's the sense of uneasiness, distress, or dread you feel before a significant event. alcoholism: Alcoholism is a condition that develops over time as someone continues to abuse alcohol. The result of al...
Self-Admitted Technical Debt It Will Never Work in Theory
The word "FIXME" appears 18 times in the source code of a small open source project I contribute to, and almost exactly the same number of times in the much larger code base I help develop in my job. Is that just a coincidence, or does it mean that I'm comfortable with a fixed amount of technical debt in any project regardless of size? Alternatively, does the lower density of "FIXME" comments at work imply that I'm less comfortable with technical debt on the job? All three explanations are plausible, and each one might be true under different circumstances.
The authors of this study found more similarities than differences between industry and open source when it comes to self-admitted technical debt. They also turned up a fourth possible explanation: that developers might be less comfortable admitting technical debt when it might affect their careers. Insights like this are why our profession needs empirical studies: not just to test ideas, but to suggest new ones.
Fiorella Zampetti, Gianmarco Fucci, Alexander Serebrenik, and Massimiliano Di Penta. Self-admitted technical debt practices: a comparison between industry and open-source. Empirical Software Engineering, Sep 2021. doi:10.1007/s10664-021-10031-3.
Self-admitted technical debt (SATD) consists of annotations, left by developers as comments in the source code or elsewhere, as a reminder about pieces of software manifesting technical debt (TD), i.e., "not being ready yet". While previous studies have investigated SATD management and its relationship with software quality, there is little understanding of the extent and circumstances to which developers admit TD. This paper reports the results of a study in which we asked developers from industry and open source about their practices in annotating source code and other artifacts for self-admitting TD. The study consists of two phases. First, we conducted 10 interviews to gather a first understanding of the phenomenon and to prepare a survey questionnaire. Then, we surveyed 52 industrial developers as well as 49 contributors to open-source projects. Results of the study show how the TD annotation practices, as well as the typical content of SATD comments, are very similar between open-source and industry. At the same time, our results highlight how, while open-source code is spread of comments admitting the need for improvements, SATD in industry may be dictated by organizational guidelines but, at the same time, implicitly discouraged by the fear of admitting responsibilities. Results also highlight the need for tools helping developers to achieve a better TD awareness.
10:28
Russia-linked APT29 abuses EU information exchange systems in recent attacks Security Affairs
Russia-linked APT29 group abused the legitimate information exchange systems used by European countries to target government entities.
Russia-linked APT29 (aka SVR group, Cozy Bear, Nobelium, and The Dukes) was spotted abusing the legitimate information exchange systems used by European countries in attacks aimed at governments.
In early March, BlackBerry researchers uncovered a new cyber espionage campaign aimed at EU countries. The hackers targeted diplomatic entities and systems transmitting sensitive information about the regions politics, aiding Ukrainian citizens fleeing the country, and providing help to the government of Ukraine.
The attack chain commences with a spear-phishing email containing a weaponized document, which contains a link leading to the download of an HTML file.
The HTLM files are hosted on a legitimate online library website that was likely compromised by the threat actors sometime between the end of January 2023 and the beginning of February 2023.
One of the lures appeals to those who want to find out the Poland Ambassadors schedule for 2023. It overlaps with Ambassador Marek Magierowskis recent visit to the United Statesp; specifically, his talk on February 2, where he discussed the war in Ukraine at the Catholic University of America Columbus School of Law, also known as the Catholic Law, which is based in Washington, DC. reads the analysis published by BlackBerry.
The APT29 group also abused multiple legitimate systems, including LegisWrite and eTrustEx, which are used by EU nations for exchanging info and data in a secure way.
10:20
Announce: OpenSSH 9.3 released Open Source Security
Posted by Damien Miller on Mar 15
OpenSSH 9.3 has just been released. It will be available from themirrors listed at https://www.openssh.com/ shortly.
OpenSSH is a 100% complete SSH protocol 2.0 implementation and
includes sftp client and server support.
Once again, we would like to thank the OpenSSH community for their
continued support of the project, especially those who contributed
code or patches, reported bugs, tested snapshots or donated to the
project. More information...
10:15
Minor stack-based buffer overflow in OpenBSD's libskey Open Source Security
Posted by Qualys Security Advisory on Mar 15
Hi all,(Posting this report here in case another project uses the same code.)
We discovered a minor stack-based buffer overflow in OpenBSD's libskey;
it was introduced in July 1997 by the following commit:
https://github.com/openbsd/src/commit/ea55ee16580e7b47c83712c5fd50615f8b1d26ad
and was fixed today by the following commit (thanks to OpenBSD for their
incredibly quick response!):...
10:08
Meta is Laying Off 10,000 More Employees SoylentNews
A tough time for big tech workers continues:
Founder and CEO Mark Zuckerberg announced Tuesday in a written statement that the tech giant would lay off 10,000 more workers, adding to the 11,000 people it laid off back in November. Additionally, around 5,000 open roles that hadn't been filled yet will be closed. In other words, it's a hiring freeze on top of a large number of layoffs.
Zuckerberg acknowledged the cuts in a blog post updating Meta's "Year of Efficiency."
This will be tough and there's no way around that. It will mean saying goodbye to talented and passionate colleagues who have been part of our success. They've dedicated themselves to our mission and I'm personally grateful for all their efforts. We will support people in the same ways we have before and treat everyone with the gratitude they deserve.
Amid the layoffs, Meta has also announced that it is stepping away from NFTs to focus on other projects.
According to TechCrunch, Meta's employee head-count came in at around 76,000 after November's layoffs. In the aftermath of this week's job cuts, that would bring the count down to around 66,000.
This is, unfortunately, just part of a wider trend in the world of big tech. Other tech firms of varying sizes like Lyft, Groupon, Vimeo, and Microsoft have all laid off workers in the last year due to broader economic difficulties.
Previously: Meta Employees Brace for Layoffs Ahead of Zuckerberg's Paternity Leave
Read more of this story at SoylentNews.
10:00

Just like the clock clock of old, theres something magical about a giant wall of smaller pieces working together to "https://www.youtube.com/watch?v=CAxm5W5Jioo" target= "_blank">E-Paper Wall 2.0 by [Aaron Christophel] is no exception as it has now upgraded from 2.9 to 7.4 screens.
On the 1.0 version, the bezels made it harder to make out the image. The larger screens still have bezels but the larger screen area makes it much easier to make out the image. 3D-printed clips hold the displays onto a plywood backer. We can marvel that e-ink price tags brought the price of e-ink down so that building a wall is still expensive but not eye-wateringly so. The 59 array likely uses a module sold on DigiKey for $47 each.
So aside from being willing to drop some money on a custom piece of...
09:28
PyTorch 2.0 Now Shipping With Better CPU & GPU Performance Phoronix
Following the PyTorch Foundation talking up PyTorch 2.0 since the end of last year, today marks the PyTorch 2.0 release officially shipping. PyTorch 2.0 has significant optimizations to "supercharge" it with better performance for both CPU and GPU modes of operation...
07:53
[$] Rules as code for more responsive governance LWN.net
Using rules as code to help bridge the gaps between policy creation, its implementation, and its, often unintended, effects on people was the subject of a talk by Pia Andrews on the first day of the inaugural Everything Open conference in Melbourne, Australia. She has long been exploring the space of open government, and her talk was a report on what she and others have been working on over the last seven years. Everything Open is the successor to the long-running, well-regarded linux.conf.au (LCA); Andrews (then Pia Waugh) gave the opening keynote at LCA 2017 in Hobart, Tasmania, and helped organize the 2007 event in Sydney.
07:47
Authorities Arrested Leaders of Prolific Piracy Release Group EVO TorrentFreak
 Every day millions of people download or stream
pirated movies, which are readily available online through hundreds
of dedicated sites.
Every day millions of people download or stream
pirated movies, which are readily available online through hundreds
of dedicated sites.
To the broader public, pirate sites and services are the gateways to a darker side of the entertainment world. In turn, however, these sites are heavily reliant on the crucial suppliers at the top of the piracy pyramid.
The Piracy Supply Chain
Broadly speaking, there are two supplier groups in this supply chain. On one side, The Scene, a conglomerate of often intertwined groups that release their content on private topsites. Rules and security are key in The Scene, but in 2020, a series of raids demonstrated that its not impenetrable.
In addition to Scene groups, there are also P2P groups. The latter operate more loosely and are generally connected to private sites, including torrent trackers where they publicly release pirated movies and TV shows.
Scene releases eventually appear on the wider internet through third parties, but P2P groups often upload their content straight to the public.
Unlike The Scene, P2P groups dont have to abide by a particular set of rules, but privacy is still a top priority. Release group members risk criminal prosecution and multi-year prison sentences should they be identified by anti-piracy groups or law enforcement agencies.
EVO The Leak Kings
EVO, short for EVOLUTiON, is a high-profile P2P group whose activities stood out in recent years. The group released a steady stream of new movie and TV show titles and gained pirates admiration by leaking many screeners way ahead of their official premieres.
For several years in a row, EVO opened the screener season by releasing leaked copies of upcoming films. This included Oscar contenders, but also several Netflix titles that originated from festival screenings.
EVO was also the first to release an early Blu-Ray copy of Spider-Man: No Way Home last year, and a high-quality copy of the blockbuster Dune in 2021, ahead of its off...
07:44
YoroTrooper APT group targets CIS countries and embassies Security Affairs
A new APT group, dubbed YoroTrooper, has been targeting government and energy organizations across Europe, experts warn.
Cisco Talos researchers uncovered a new cyber espionage group targeting CIS countries, embassies and EU health care agency since at least June 2022.
The APT group focuses on government or energy organizations in Azerbaijan, Tajikistan, Kyrgyzstan and other Commonwealth of Independent States (CIS). The experts reported that the group hacked accounts from at least two international organizations, a critical EU health care agency and the World Intellectual Property Organization (WIPO). Talos reported that the threat actor also likely targets other organizations across Europe and Turkish (Trkiye) government agencies.
Data stolen by the threat actors includes credentials from multiple applications, browser histories and cookies, system information and screenshots.
YoroTroopers arsenal includes Python-based, custom-built and open-source information stealers, such as the Stink stealer wrapped into executables via the Nuitka framework and PyInstaller. The group also employed commodity malware in its campaign, such as AveMaria/Warzone RAT, LodaRAT and Meterpreter.
The attack vectors are phishing emails with an attached archive containing two files, a shortcut file and a decoy PDF file.
The malicious LNK files acts as downloaders that uses mshta.exe to download and execute a remote HTA file on the infected endpoint.
The malicious HTA files employed in this campaign have seen a steady evolution with the latest variant downloading the next-stage payload: a malicious EXE-based dropper...
07:40
Khronos Developing SYCL SC For Safety-Critical C++ Heterogeneous Compute Phoronix
The SYCL single-source C++ based programming model has begun taking off with Intel investing in it heavily as part of their oneAPI / DPC++ compiler stack and a variety of different open-source projects bringing SYCL to the likes of AMD and NVIDIA GPUs, CPU-based OpenMP implementations, SYCL to Vulkan, and more for heterogeneous compute needs. The Khronos Group announced today they have begun working on SYCL SC as a safety-critical variant of this heterogeneous compute programming model...
07:35
Zipline Adds Rappelling Droid to Delivery Drones IEEE Spectrum

This morning, drone-delivery company Zipline announced a new drone-delivery system offering nearly silent, precise delivery thats intended to expand the companys capabilities into home delivery. This requires a much different approach from what Zipline has been doing for the past eight years. In order to make home deliveries that are quiet and precise, Zipline has developed a creative new combination of hybrid drones, droids, and all the supporting hardware necessary to make deliveries directly to your front porch.
We visited one of Ziplines distribution centers in Rwanda a few years ago to see how effective their system was at delivering blood across the countrys rugged terrain. To watch a delivery take place, we drove an hour over winding dirt roads to a rural hospital. Shortly after we arrived, a drone made the trip and delivered a package of blood in about 14 minutes. It was a compelling example of the value of drone delivery in situations where you have critical and time-sensitive goods in areas of low infrastructure, but the challenges of urban home delivery are something else entirely.
The way that Ziplines current generation of fixed-wing delivery drones work is by dropping boxes tethered to small parachutes while flying several tens of meters over an open delivery area. You need some obstacle-free space for this to work reliably (say, a handful of empty parking spaces or the equivalent), and its not a particularly gentle process, meaning that there are some constraints on what you can deliver and how its packaged. For hospitals and health centers, this is usually no problem. For your home, it very well may not be an option at all.
Ziplines new drones are much different. In a heavily produced online event featuring the Zipline team alongside Rwandan president Paul Kagame and company board member Bono, Zipline introduced P2, a new delivery system that combines a hybrid fixed-wing drone with a small tethered droid that can drop out of the belly of the drone to make precision deliveries.

Housed within the P2 Zip, the droid and whatever its carrying can travel at 112 kilometers per hour through all kinds of weather out to a service r...
07:27
Europe is Bracing for (Another) Devastating Drought SoylentNews
The drought in parts of France is so bad right now that some authorities have banned new home-building projectsfor the next four years. Despite a severe housing shortage in France, new homes just aren't worth the drain on water resources that construction, and eventual new residents, would cause, say nine communes in the south of the country.
It's just one of many signs that Europe is running dry. "What we are looking at is something like a multiyear drought," says Rohini Kumar of the Helmholtz Centre for Environmental Research in Germany. Unusually low rainfall and snowfall was recorded this winter not just in France but also in the UK, Ireland, Switzerland, and parts of Italy and Germany. The current predicament follows European droughts in 2018, 2019, 2020, and 2022.
Last summer, drought exacerbated by record temperatures around the continent was in the headlines. The subsequent dry winter has meant that many aquifersplaces underground that retain waterand surface reservoirs have not had a chance to recover. Now, summer beckons once again, and experts who spoke to WIRED are worried that a severe water shortage could threaten lives, industry, and biodiversity in a big way.
The European Drought Observatory tracks indicators of drought across the continent, including from satellite measurements, and suggests that vast regions are far drier than they should be. "Honestly, all over Central Europe, this issue, it's a widespread problem," says Carmelo Cammalleri at the Polytechnic University of Milan.
He estimates that reservoirs in France and northern Italy are about 40 to 50 percent lower than they should be. The longest river in Italy, the Po, is 60 percent below its normal levels. Not only that, there is roughly half the usual snow on the Alps than would be expected for this time of year. That's a huge problem, because much of Central Europe relies on meltwater from these famous mountains every spring. "The Alps are known as the water towers of Europe for a reason," says Cammalleri.
07:24
Microsoft has another go at closing security hole exploited by Magniber ransomware Graham Cluley
In its latest Patch Tuesday bundle of security fixes, Microsoft has patched a security flaw that was being used by the Magniber cybercrime gang to help them infect computers with ransomware. Read more in my article on the Hot for Security blog.
07:00
Spin Up To Speed With This Stroboscope Hackaday

A stroboscope is not the most common tool, and while they can be purchased fairly inexpensively from various online stores, they are straightforward enough tools that plenty of us could build our own mostly from parts laying around. The basic idea is to shine a flashing light on a spinning object, and when it appears stationary the stroboscope will indicate the rotational speed. There are a few specialty parts that might not be in everyones parts drawers, though, and [John] shows us the ins-and-outs of his own DIY stroboscope.
The effect relies on extremely precise timing, and as such the most important part of a build like this is making sure to get the LED circuitry correct so its duty cycle and frequency can be tightly controlled. [John] is using a PT4115E driver board for the LED, and is using it to power a 1W white LED which also includes its own heat sink and lens. The controls for the stroboscope are handled by an ATtiny1614 microcontroller which shows its pulse rate on a small screen. The user can control the rate the LED flashes with simple controls, and when the spinning object appears to come to a stop the only thing left to do is read this value off of the screen.
While it might seem like an overly niche tool, stroboscopes have plenty of day-to-day uses. Ol...
06:34
Despite What Youve Heard, Open Source 101 Isnt Just for Newbies FOSS Force
Although Open Source 101 (which will be held for the first time in Charlotte, North Carolina on Thursday March 23) targets those new to open source, veteran open sourcers can find benefits from attending, too.
The post Despite What Youve Heard, Open Source 101 Isnt Just for Newbies appeared first on FOSS Force.
05:16
Stellar Cyber Launches InterSTELLAR Partner Program for Open XDR Solutions HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
Stellar Cyber, the company that recently made headlines as one of the 10 Hot XDR Security Companies You
This is a post from HackRead.com Read the original post: Stellar Cyber Launches InterSTELLAR Partner Program for Open XDR Solutions
04:40
Cloud Computing is Driving a New Gig Economy in Tech SoylentNews
After being laid off, many people are starting their own businesses as cloud pros for hire:
The recent tech industry layoffs are driving a wave of what some are calling "solopreneurs" doing gig work or independent contracting. Think DoorDash or Uber Eats, but instead of delivering Thai food, people are delivering key cloud advisory services or even completed cloud-based systems ready for deployment.
This is driven by the anticipation that a slowing economy is likely to drive down tech sales. But also, a cloud skills shortage is occurring simultaneously. We're not preparing enough cloud professionals to keep up with demand, but, at the same time, tech companies are laying them off. Go figure.
This has been evolving for years as workers understand the value of the gig economy and may be looking for more independence and less employment reliance on the larger technology players. Many technology professionals are exploring more entrepreneurial options instead of opting for standard full-time jobs and cushy benefits with companies that can't guarantee a job for lifeand never could.
Indeed, 63% of tech workers report they have started their own company post-layoff, according to a recent survey of 1,000 professionals laid off in recent years. Most of these new ventures (83%) exist in the technology industry, especially cloud computing.
Read more of this story at SoylentNews.
04:15
DreamWorks' OpenMoonRay Renderer Code Published Phoronix
Last summer DreamWorks announced plans to open-source MoonRay, their production renderer used for films like The Bad Guys, Puss in Boots: The Last Wish, and other animated films. Today they have delivered on that exciting milestone with publishing the open-source code...
03:55
Australias Nuclear Submarine Program cryptogon.com
Madness. Via: The Diplomat: From around 2027, U.S. and U.K. nuclear submarines will undertake rotational deployments to Australia. In the 2030s, subject to U.S. Congressional approval, Australia will purchase three to five Virginia-class subs. The Biden administration and Australia itself are also making new investments in the United States submarine-building capacity. Lastly, beginning from the []
03:50
Snapdragon-Powered Acer Aspire 1 Laptop Nearing Mainline Linux Support Phoronix
While Lenovo's ThinkPad X13s has generated a fair amount of attention for being a Qualcomm Snapdragon SoC powered Arm laptop that supports running on the mainline Linux kernel, another option on the way is the Acer Aspire 1 that also makes use of a Qualcomm Soc...
03:47
Links 15/03/2023: Qubes OS 4.1.2, Mozilla Swallows Buzzwords Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
03:01
How to cache Ansible facts with MongoDB Linux.com
Ansibles flexibility and variety of fact caching plugins allow you to design the solutions that best fit your requirements.
Read More at Enable Sysadmin
The post How to cache Ansible facts with MongoDB appeared first on Linux.com.
03:00
Fedora Workstation 38 Is Shaping Up To Be Another Fantastic Release Phoronix
I've been playing around with the current development state of Fedora 38 the past few days on several test boxes. While only reaching Fedora 38 Beta this week, it already feels quite polished and stable. To sum it up quite simply, Fedora Workstation 38 is looking like it will be another fantastic release and continuing the modern Fedora Project trend of putting out a bleeding-edge Linux distribution yet production-ready and with far less blemishes compared to releases from years ago...
02:19
Microsoft Patch Tuesday, March 2023 Edition Krebs on Security
Microsoft on Tuesday released updates to quash at least 74 security bugs in its Windows operating systems and software. Two of those flaws are already being actively attacked, including an especially severe weakness in Microsoft Outlook that can be exploited without any user interaction.
The Outlook vulnerability (CVE-2023-23397) affects all versions of Microsoft Outlook from 2013 to the newest. Microsoft said it has seen evidence that attackers are exploiting this flaw, which can be done without any user interaction by sending a booby-trapped email that triggers automatically when retrieved by the email server before the email is even viewed in the Preview Pane.
While CVE-2023-23397 is labeled as an Elevation of Privilege vulnerability, that label doesnt accurately reflect its severity, said Kevin Breen, director of cyber threat research at Immersive Labs.
Known as an NTLM relay attack, it allows an attacker to get someones NTLM hash [Windows account password] and use it in an attack commonly referred to as Pass The Hash.
The vulnerability effectively lets the attacker authenticate as a trusted individual without having to know the persons password, Breen said. This is on par with an attacker having a valid password with access to an organizations systems.
Security firm Rapid7 points out that this bug affects self-hosted versions of Outlook like Microsoft 365 Apps for Enterprise, but Microsoft-hosted online services like Microsoft 365 are not vulnerable.
The other zero-day flaw being actively exploited in the wild CVE-2023-24880 is a Security Feature Bypass in Windows SmartScreen, part of Microsofts slate of endpoint protection tools.
Patch management vendor Action1 notes that the exploit for this bug is low in complexity and requires no special privileges. But it does require some user interaction,...
01:54
TikTok Now Offers a Feed Dedicated to Science and Tech SoylentNews
The STEM feed comes as TikTok faces increasing scrutiny:
TikTok has a large science community, and the social network wants everyone to know it on Pi Day (March 14). The company is launching a dedicated STEM (science, technology, engineering and math) feed that shows only these more educational videos. You may learn to code or discuss experiments without having to wade through TikTok's usual entertainment-focused content.
Not surprisingly, TikTok is taking steps to block misinformation in this new section. Curator Common Sense Networks will study content to make sure it's relevant to the STEM feed, while the fact-checkers at Poynter will gauge the accuracy. Any videos that don't pass both inspections won't reach the new feed.
Users in the US will start seeing the STEM feed in the "coming weeks," TikTok says. The social media giant has already been experimenting with a "Topic Feed" in some regions to court fans of gaming, sports and other common subjects. The science-oriented feed is considered an expansion of this initiative.
[...] Whether or not this helps with TikTok's survival in the US is another matter. Some politicians want to ban TikTok outright over fears it's a national security threat. Officials are concerned China may collect data about key Americans or spread propaganda.
See also: TikTok is Adding a Dedicated Feed for STEM Content
Read more of this story at SoylentNews.
01:38
CrowdStrike discovered the first-ever Dero cryptocurrency mining campaign Security Affairs
CrowdStrike researchers discovered the first-ever cryptocurrency mining campaign aimed at Dero mining since February 2023.
CrowdStrike has discovered the first-ever Dero cryptojacking campaign aimed at Kubernetes infrastructure. Dero is a general-purpose, private, and decentralized application platform that allows developers to deploy powerful and unstoppable applications. It claims to offer improved privacy, anonymity and higher monetary rewards compared to other cryptocurrencies.
The cryptojacking operation uncovered by CrowdStrike focuses on Kubernetes clusters with anonymous access enabled on a Kubernetes API and listening on non-standard ports exposed on the internet.
The campaign started in February 2023 and originated from three servers based in the U.S.
CrowdStrike has discovered the first-ever Dero cryptojacking operation targeting Kubernetes infrastructure. reads the analysis published by Crowdstrike. The novel Dero cryptojacking operation is found to be targeted by an existing Monero cryptojacking operation that was modified subsequently in February 2023. The modified Monero campaign kicks out the DaemonSets used for Dero cryptojacking in the Kubernetes cluster before taking it over.
Experts believe that the crypto-jacking operation is aimed at Dero, instead of Monero, because the former scheme offers larger rewards and provides the same or better anonymizing features, which is a perfect match for threat actors.
The attack chain commences with the attacker finding an Internet-facing vulnerable Kubernetes cluster. Once interacted with the Kubernetes API, the attacker deploys a Kubernetes DaemonSet (proxy-api) that deploys a malicious pod on each node of the Kubernetes cluster.
This helps attackers engage resources of all of the nodes at the same time to run a cryptojacking operation. The mining efforts by the pods are contributed back to a community pool, which distributes the reward (i.e., Dero coin) equally among its contributors through their digital wallet. continues the report.
00:48
Tell the UKs House of Lords: Protect End-to-End Encryption in the Online Safety Bill Deeplinks
Private communication is a basic, universal right. In the online world, the best tool we have to defend this right is end-to-end encryption.
End-to-end encryption ensures that governments, tech companies, social media platforms, and other groups cannot view or access our private messages, the pictures we share with family and friends, or our bank account details. This is a universal right, and one that is a particularly vital protection for the most vulnerable in societysuch as children or human rights defenders who rely on private messaging to do their jobs in hostile environments.
TELL the house of lords to protect encryption in the online safety bill
The UK Parliament is moving forward with its Online Safety Bill, which would undermine encryption. Clause 110 mandates that websites and apps must proactively prevent harmful content from appearing on messaging services. Thats going to lead to universal scanning of all user content, all the time. Its not compatible with encryption, or our right to privacy.
Over the past several years, UK government officials have expressed concerns that online services have not been doing enough to tackle illegal content, particularly child sexual abuse material (also called CSAM). At the same time, weve seen a number of proposals brought forward by governments that want to scan user-to-user communications for criminal content: the U.S. Congress tried to create backdoors to encryption through the EARN IT Act, and the EUs proposal to scan private chats could lead to the mandatory scanning of every private message, photo, and video. Government agencies also triedand failedto pressure Apple to propose a system of software scanners on every device, constantly checking for child abuse images and reporting back to authorities.
All of these proposals suffer from the incorrect belief that a backdoor or other workaround to read encrypted messages can be designed for use only in benevolent ways.
Unfortunately, this isn...