| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Sunday, 16 April
01:57
Links 15/04/2023: EasyOS 5.2.1 and Arkansas Versus Fentanylware (TikTok) Techrights
![]()
Contents
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Pseudo-Open Source
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Digital Restrictions (DRM)
- Monopolies
- Gemini* and Gopher
-
Distributions and Operating Systems
-
New Releases
-
Barry Kauler EasyOS Kir...
-
-
01:44
Reworked x86_64 Parallel Boot Support Posted For The Linux Kernel Phoronix
Being worked on for a while has been Linux kernel patches to speed boot times by allowing the parallel bring-up of CPU cores. There were AMD boot issues since worked around and the patches gone through multiple revisions for helping with Linux kernel boot times. Those patches continue to be improved upon and yesterday saw a reworked patch series posted...
01:24
6 Ways That Battery Analytics Can Help Decarbonize Our Economy Lifeboat News: The Blog
To meet climate commitments, we need to use more batteries across many economic sectors. Battery analytics can help to remove risk and increase uptake.
01:22
Yann LeCun and Andrew Ng: Why the 6-month AI Pause is a Bad Idea Lifeboat News: The Blog

Join us for a conversation with Andrew Ng and Yann LeCun as they discuss the proposal of a 6-month moratorium on generative AI.
We will be taking questions during the event. Please submit your
question or upvote others here:
https://app.sli.do/event/9yGgPaweRK9Cbo8wsqV6oq/live/questions.
Speakers.
Yann LeCun, VP & Chief AI Scientist at Meta and Silver
Professor at NYU
https://www.linkedin.com/in/yann-lecun/
Andrew Ng, Founder of DeepLearning. AI
https://www.linkedin.com/in/andrewyng/
Let us know how were doing? We will be giving out discount codes
for a selected number of people who fill out the survey:
https://forms.gle/ArNXCmkZc6YwwyXD7
Looking to connect with your peer learners, share projects, and
swap advice? Join our AI community:
https://community.deeplearning.ai/invites/VVGtXQuWNR
01:05
CVE-2023-22946: Apache Spark proxy-user privilege escalation from malicious configuration class Open Source Security
Posted by Sean R. Owen on Apr 15
Description:In Apache Spark versions prior to 3.4.0, applications using spark-submit can specify a 'proxy-user' to run as, limiting
privileges. The application can execute code with the privileges of the submitting user, however, by providing
malicious configuration-related classes on the classpath. This affects architectures relying on proxy-user, for example
those using Apache Livy to manage submitted applications.
This issue is...
01:00
Can We Identify a Person From Their Voice? IEEE Spectrum

At 6:36 a.m., on 3 December 2020, the U.S Coast Guard received a call over a radio channel reserved for emergency use: Mayday, Mayday, Mayday. We lost our rudder...and were taking on water fast. The voice hiccupped, almost as if the man were struggling. He radioed again, this time to say that the pumps had begun to fail. He said hed try to get his boat, a 42-footer with three people on board, back to Atwoods, a lobster company on Spruce Head Island, Maine. The Coast Guard asked for his GPS coordinates and received no reply.
That morning, a Maine Marine Patrol officer, Nathan Stillwell, set off in search of the missing vessel. Stillwell rode down to Atwood Lobster Co., which is located at the end of a peninsula, and boarded a lobster boat, motoring out into water so shockingly cold it can induce lethal hypothermia in as little as 30 minutes.
When he returned to shore, Stillwell continued canvassing the area for people who had heard the radio plea for help. Someone told him the voice in the mayday call sounded messed up, according to a report obtained through a state-records request. Others said it sounded like Nate Libby, a dockside worker. So Stillwell went inside Atwoods and used his phone to record his conversation with Libby and another man, Duane Maki. Stillwell asked if they had heard the call.
I was putting my gloves and everything on the rack, Libby told him. I heard it. I didnt know that word, honestly, (presumably referring to the word mayday.) And I just heard it freaking coming on that he lost his rudder, that he needed pumps. Both men denied making the call.
Stillwell seemed unsure. In his report, he said hed received other tips suggesting the VHF call had been made by a man whose first name was Hunter. But then, the next day, a lobsterman, who owned a boat like the one reported to be in distress, called Stillwell. He was convinced that the mayday caller was his former sternman, the crew member who works in the back of the lobster boat: Nate Libby.
The alarm was more than just a prank call. Broadcasting a false distress signal over maritime radio is a violation of international code and, in the United States, a federal Class D felony. The Coast Guard recorded the calls, which spanned about 4 minutes, and investigators isolated four WAV files,...
00:30
Siemens Metaverse exposes sensitive corporate data Security Affairs
Siemens Metaverse, a virtual space built to mirror real machines, factories, and other highly complex systems, has exposed sensitive data, including the companys office plans and internet of things (IoT) devices.
While metaverse is no longer a buzzword, amid the sudden popularity of ChatGPT and similar AI tools, those virtual worlds are still here, presenting exciting opportunities for companies, users, and, unfortunately, threat actors.
Siemens, a German multinational with over $71 trillion in revenue and 300,000 employees worldwide, has also jumped on the metaverse bandwagon. In 2022, it partnered with NVidia, an American multinational technology company, to build the industrial metaverse.
Recently, the Cybernews research team has discovered that Siemens Metaverse a platform that aims to create digital twins of its factories and offices was leaking sensitive information.
If attackers got to the exposed data, it could have had devastating consequences for the company and other big corporations using its services, including ransomware attacks.
Siemens, on the other hand, said it considered the issue to be non-critical and added that it had been mitigated.
Metaverse leak: what we discovered
On March 1, the Cybernews research team discovered an environment file hosted on a metaverse.siemens.com domain. It contained ComfyApp credentials and endpoints. It also discovered Siemens leaking four sets of WordPress users, and three sets of backend and authentication endpoint URLs on different endpoints of the affected systems.
The WordPress sets only exposed user names and avatar pictures, but all four Siemens WordPress-based subdomains were vulnerable to a flaw that WordPress itself fixed in 2017, leaving researchers wondering whether there are more severe vulnerabilities on these sites.
Backend and authentication endpoint URLs, used to verify users before giving them access, could lead to attackers testing them for vulnerabilities and exploiting them.
The most worrying discovery was that of exposed office management platform ComfyApp user credentials. The Siemens-owned app...
00:00
Sufficiently Advanced Tech: Has Bugs Hackaday

Arthur C. Clarke said that Any sufficiently advanced technology is indistinguishable from magic. He was a sci-fi writer, though, and not a security guy. Maybe it should read Any sufficiently advanced tech has security flaws. Because this is the story of breaking into a car through its headlight.
In a marvelous writeup, half-story, half CAN-bus masterclass, [Ken Tindell] details how car thieves pried off the front headlight of a friends Toyota, and managed to steal it just by saying the right things into the network. Since the headlight is on the same network as the door locks, pulling out the bulb and sending the open the door message repeatedly, along with a lot of other commands to essentially jam some other security features, can pull it off.
Half of you are asking what this has to do with Arthur C. Clarke, and the other half are probably asking what a lightbulb is doing on a cars data network. In principle, its a great idea to have all of the electronics in a car be smart electronics, reporting their status back to the central computer. Its how we know when our lights are out, or what our tire pressure is, from the drivers seat. But adding features adds attack surfaces. What seems like...
00:00
Quantum Technologys Unsung Heroes IEEE Spectrum

In a world where quantum technologies are on the rise in computing, cryptography, materials, sensors, telecom, biomed, and AI, its easy to forget that not so long ago the words quantum and technology rarely fit comfortably into a sentence together. A range of trailblazers imagined quantum physics turning into quantum engineering turning into quantum user techor, for those working before the quantum era, imagined far-off theoretical horizons coming into range of practical applications. However, not all of these early innovators are known to those developing present-day quantum technologies. Yet rediscovering the lost history of early quantum pioneers today yields at least three dividendsadvancing the field by better understanding its past, inspiring new generations of future leaders, and finally giving credit where credits due.
With such inspirations in mind, the science journalists Brian Lenahan and Kenna Hughes-Castleberry have written a new book On The Shoulders of Giants: 10 Quantum Pioneers of the Past (published this week), resuscitating the legacies of sometimes obscure figures in quantum history. Not by coincidence, their books release also neatly aligns with the underpinnings of World Quantum Day (14 April)which organizers established to promote the public understanding of quantum science and technology around the world.
IEEE Spectrum recently spoke with Lenahan and Hughes-Casteleberry about overshadowed genius, pre-medieval computer programs, and Claude Shannons Vogue magazine celebrity photoshoot.
IEEE Spectrum: What were the criteria you used to select the historical figures your book highligh...
Saturday, 15 April
23:22
What they thought of aging in 1931 Lifeboat News: The Blog

What did scientists think about aging in 1931? Thats right. 1931. because that is the year the first biological textbook was published The Science of Life. I managed to get my hands on the first edition of this textbook. This was my face when i first received it. As you can see i was quite excited. And this textbook is made up of separate books. I bought book i last year and i read it. Having enjoyed it and discovered that it was part of this massive ensemble piece well, ive read the first book there are, if my roman numerals are correct, 9 books in total. And in this first book, penned The Living Body, the authors, most famously, H.G.Wells, Sir Julian Huxley and G.P.Wells, H.Gs son discusses the body as a machine and that.
For the present it is enough to remember that all animals (including men) are combustion engines of an intricate and curious kind, which live by oxidising their food
I bought first The Living Body and then discovered it was part of this massive ensemble piece and decided i needed to read it. Now, besides being surprised to find out that H.G.Wells wrote not just non-fiction, but biology non-fiction, i was also surprised to hear how both similar & dissimilar their views were back in 1931 compared to today and i wasnt sure if that was good or terrifying.
So, how did they think of human aging. Well, in the last chapter of this 1st book titled The wearing out of the machine and its reproduction, they discuss it.
Sheekey bookmarks https://www.contrado.co.uk/stores/the-sheekey-science-show/crk-1999569
Find me on Twitter -
https://twitter.com/EleanorSheekey.
Support the channel.
through PayPal https://paypal.me/sheekeyscience?country.x=GB&locale.x=en_GB
through Patreon https://www.patreon.com/TheSheekeyScienceShow.
23:06
OpenZFS 2.1.10 Released - Adds Linux 6.2 Support, Finally Drops Python 2 Compatibility Phoronix
OpenZFS 2.1.10 is out as the latest update to this open-source ZFS file-system implementation currently supported on Linux and FreeBSD systems...
23:02
Kodi TV Discloses Data Breach After Forum Database for Sale Online SoylentNews
[Editor's Note: This is not connected to the Kodi Linux Operating System. JR]
Bleeping Computer reports that Kodi has revealed (on 8 April 2023) that their forum [N.B. the forum itself is now gone and replaced with a blog post about the breach] database was breached and is for sale online.
From the Bleeping Computer article:
The Kodi Foundation has disclosed a data breach after hackers stole the organization's MyBB forum database containing user data and private messages and attempted to sell it online.
Kodi is a cross-platform open-source media player, organizer, and streaming suite, that supports a vast array of third-party add-ons enabling the users to access content from various sources or customize their experience.
The now-shut down Kodi forum has roughly 401,000 members who used it to discuss media streaming, exchange tips, offer support, share new add-ons, and more in 3 million posts.
According to an announcement published by the platform on Saturday, hackers stole the forum database by logging into the Admin console using an inactive staff member's credentials.
Once they gained access to the admin panel, they created and downloaded database backups multiple times in 2023.
"MyBB admin logs show the account of a trusted but currently inactive member of the forum admin team was used to access the web-based MyBB admin console twice: on 16 February and again on 21 February," explains Kodi in a message to its users.
"The account was used to create database backups which were then downloaded and deleted. It also downloaded existing nightly full-backups of the database."
The Kodi team confirmed that the actual account owner did not perform these actions on the admin console, indicating that the staff member's credentials were likely stolen.
"If you have used the same username and password on any other site, you should follow the password reset/change procedure for that site."
So Soylentils, do (or, in the case of the forum, did) you use Kodi or, more importantly, their forum?
If so, will this breach affect how/whether or not you (continue) to use Kodi?
Read more of this story at SoylentNews.
22:35
Libreboot Adds Support For The Once Common HP Elite 8200 SFF PC Phoronix
The HP Elite 8200 was once popular and very common among workplaces and can still be found used/refurbished for a little more than $100 for this small form factor PC. Libreboot has now added support for the HP Elite 8200 as its newest desktop port for this Intel Sandy Bridge era system...
22:34
Re: ncurses fixes upstream Open Source Security
Posted by Solar Designer on Apr 15
The (linux-)distros lists are meant for handling of embargoed issuesprior to their public disclosure and in cases where such private
handling is expected to help. In this case, the issue was already
semi-public (via the fixes and the NEWS file) and I wouldn't expect
private handling to help more than public does. Every distro present on
(linux-)distros is supposed to also be present on oss-security. So in
my opinion Jonathan did the...
22:08
Re: ncurses fixes upstream Open Source Security
Posted by Georgi Guninski on Apr 15
Isn't MicroSoft member of linux distros mailing list [0], whichpurpose is exactly quietly trading 0days [1]?
Does the OP with m$ email address realize this?
[0] https://oss-security.openwall.org/wiki/mailing-lists/distros
[1] https://seclists.org/oss-sec/2019/q3/19
Re: linux-distros membership application - Microsoft
22:06
Links 15/04/2023: KDE ISO Image Writer Beta 0.9.2 and PowerDNS DNSdist 1.7.4 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Monopolies
-
GNU/Linux
-
Kernel Space
-
PCLOS Official Kernels Updated
Kernels 6.2.11, 6.1.24 LTS and 5.15.107 LTS have been updated for PCLinuxOS and are now available in the Synaptic Software Repository.
-
-
Instructionals/Technical
-
LinuxTechi How to Ins...
-
-
21:25
Max Tegmark: The Case for Halting AI Development | Lex Fridman Podcast #371 Lifeboat News: The Blog

Max Tegmark is a physicist and AI researcher at MIT, co-founder
of the Future of Life Institute, and author of Life 3.0: Being
Human in the Age of Artificial Intelligence. Please support this
podcast by checking out our sponsors:
- Notion: https://notion.com.
- InsideTracker: https://insidetracker.com/lex
to get 20% off.
- Indeed: https://indeed.com/lex to get $75
credit.
EPISODE LINKS:
Maxs Twitter: https://twitter.com/tegmark.
Maxs Website: https://space.mit.edu/home/tegmark.
Pause Giant AI Experiments (open letter): https://futureoflife.org/open-letter/pause-giant-ai-experiments.
Future of Life Institute: https://futureoflife.org.
Books and resources mentioned:
1. Life 3.0 (book): https://amzn.to/3UB9rXB
2. Meditations on Moloch (essay): https://slatestarcodex.com/2014/07/30/meditations-on-moloch.
3. Nuclear winter paper: https://nature.com/articles/s43016-022-00573-0
PODCAST INFO:
Podcast website: https://lexfridman.com/podcast.
Apple Podcasts: https://apple.co/2lwqZIr.
Spotify: https://spoti.fi/2nEwCF8
RSS: https://lexfridman.com/feed/podcast/
Full episodes playlist:
https://www.youtube.com/playlist?list=PLrAXtmErZgOdP_8GztsuKi9nrraNbKKp4
Clips playlist:
https://www.youtube.com/playlist?list=PLrAXtmErZgOeciFP3CBCIEElOJeitOr41
OUTLINE:
0:00 Introduction.
1:56 Intelligent alien civilizations.
14:20 Life 3.0 and superintelligent AI
25:47 Open letter to pause Giant AI Experiments.
50:54 Maintaining control.
1:19:44 Regulation.
1:3...
21:24
Explained: What is Auto-GPT, the new do-it-all AI tool and how it works Lifeboat News: The Blog
If people are worried that Chat-GPT could be taking their jobs, they havent seen Auto-GPT yet.
Auto-GPT is an AI chatbot similar to ChatGPT and others. It is based on the GPT-4 language model of OpenAI, the same LLM that powers the ChatGPT. But, as the name implies, Autonomous Artificial Intelligence Chat Generative Pre-trained Transformer, a step further, but what exactly is it? Let us go through what Auto-GPT is and how it works.
What is Auto-GPT
Essentially, Auto-GPT is a chatbot. You ask it the questions it answers smartly. But, unlike ChatGPT and other GPT-based chatbots, which need a prompt every single time, Auto-GPT can automate the whole task, so you do not need to prompt it. Once given a task, Auto-GPT will figure out the steps on its own to reach the goal.
21:23
Dr Andrew McMahon & Lewis Kleinberg Pushing The Boundaries Of Research To Build A Synthetic Kidney Lifeboat News: The Blog

Pushing The Boundaries Of Research To Build A Synthetic Kidney Dr. Andrew McMahon, Ph.D. & Lewis Kleinberg, University Kidney Research Organization (UKRO)
The University Kidney Research Organization (UKRO https://ukrocharity.org/) is a Los Angeles-based nonprofit charity, co-founded prominent entertainment attorney Kenneth Kleinberg, inspired by his personal journey with kidney disease, focused on supporting medical research and education related to the causes, treatment, and eradication of all forms of kidney disease.
Dr. Andrew McMahon, Ph.D. (https://keck.usc.edu/faculty-search/andrew-p-mcmahon/) is Director of the Eli and Edythe Broad Center for Regenerative Medicine and Stem Cell Research at USC, Provost Professor and the inaugural holder of the W. M. Keck Professorship of Stem Cell Biology and Regenerative Medicine, and is responsible for overseeing UKROs Synthetic Kidney Project. In addition, Dr. McMahon chairs the recently created Department of Stem Cell Biology and Regenerative Medicine at the Keck School. He also holds an appointment in the Department of Biological Sciences in the USC Dornsife College of Letters, Arts, and Sciences.
Previously Dr. McMahon served as professor in the Department of Stem Cell and Regenerative Biology, Department of Molecular and Cellular Biology and principal faculty member in the Harvard Stem Cell Institute, as well as led the Department of Cell and Developmental Biology at the Roche Institute for Molecular Biology.
Dr. McMahon received his bachelors degree from St. Peters College, Oxford University and his Ph.D. from University College in London. He subsequently worked for three years as a postdoctoral fellow at the California Institute of Technology.
Lewis Kleinberg, a board member of UKRO and son of Kenneth Kleinberg, is a writer/producer who has written, developed and produced projects for Sony Pictures, Walt Disney Pictures, New Regency, 21st Century Fox, TNT, Anonymous Content, BBC Productions, Renegade 83, Kapital Entertainment, and USA Network, among others, and currently creates and produces films for UKROs website, media outreach, and benefit dinners. A graduate of the USC School of Cinematic Arts, he serves as an advisor to Donate Life Hollywood and as a mentor for USCs...
21:22
Noam Chomsky: AI Isnt Coming For Us All, You Idiots Lifeboat News: The Blog
The worlds preeminent linguist has spoken and he seems mighty tired of everyones whining about artificial intelligence as it stands today.
In an op-ed for the New York Times, Noam Chomsky said that although the current spate of AI chatbots such as OpenAIs ChatGPT and Microsofts Bing AI have been hailed as the first glimmers on the horizon of artificial general intelligence the point at which AIs are able to think and act in ways superior to humans we absolutely are not anywhere near that level yet.
That day may come, but its dawn is not yet breaking, contrary to what can be read in hyperbolic headlines and reckoned by injudicious investments, the Massachusetts Institute of Technology cognitive scientist mused.
21:00
Better Laser Cuts: Know Your Kerf Hackaday

The recent crop of laser cutters are nothing short of miraculous. For a few hundred dollars you can get a machine that can easily engrave and subject to materials cut well, too. [Nate] has been taking advantage of a laser to make boxes that join together using finger joinery. The problem is, the pieces have to fit exactly to get a good box. While setting dimensions in software is fine, you need to account for how much material the laser removes something traditional woodworkers and machinists know as kerf.
You can, of course, employ trial and error to get good results. But thats wasteful and potentially time-consuming. [Nate] built a tolerance fence that is quick to cut out and allows accurate measurement of kerf. You can quickly use the tolerance fence to make measurements and increase your chances of nailing your boxes on the first cut.
You have to customize the fence based on the thickness of your material. [Nate] uses Lightburn, which probably has a kerf offset already set by default in your layers. If not, youll need to turn it on and set an estimate of your kerf size. Then you are ready to cut the fence pieces and see how they fit together.
If the fit is too loose, you want to raise the kerf setting and try again. If it is too tight, you lower the kerf setting. As [Nate] says, Lower equals looser.
The results speak for themselves, as you can see in the trea...
20:47
Mesa 23.1-rc1 Published For Testing With Many Graphics Driver Updates Phoronix
Following this week's Mesa 23.1 feature freeze and code branching, Eric Engestrom on Friday night published Mesa 23.1-rc1...
20:47
CISA adds bugs in Android and Novi Survey to its Known Exploited Vulnerabilities catalog Security Affairs
US Cybersecurity and Infrastructure Security Agency (CISA) added Android and Novi Survey flaws to its Known Exploited Vulnerabilities catalog.
U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added the following five new issues to its Known Exploited Vulnerabilities Catalog:
- CVE-2023-20963 Android Framework Privilege Escalation Vulnerability. Android Framework contains an unspecified vulnerability that allows for privilege escalation after updating an app to a higher Target SDK with no additional execution privileges needed;
- CVE-2023-29492 Novi Survey Insecure Deserialization Vulnerability. Novi Survey contains an insecure deserialization vulnerability that allows remote attackers to execute code on the server in the context of the service account;
Google addressed the vulnerability CVE-2023-20963 with the release of The Android Security BulletinMarch 2023 security updates. The bulletin confirmed that there are indications that CVE-2023-20963 may be under limited, targeted exploitation.
According to Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities, FCEB agencies have to address the identified vulnerabilities by the due date to protect their networks against attacks exploiting the flaws in the catalog.
Experts recommend also private organizations review the Catalog and address the vulnerabilities in their infrastructure.
CISA orders federal agencies to fix this flaw by May 4, 2023.
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections:
- The Teacher Most Educational Blog
- The Entertainer Most Entertaining Blog
- The Tech Whizz Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please nominate Security Affairs as your favorite blog.
Nominate here: ...
20:14
KDE Improving Its Multi-GPU Infrastructure For Intel & AMD GPUs Phoronix
Plasma 6.0 development continues happening at full-speed and exciting this week were landing of some improvements around KWin's multi-GPU infrastructure to benefit Intel and AMD Radeon graphics...
19:37
Volvo retailer leaks sensitive files Security Affairs
The Brazilian retail arm of car manufacturing giant Volvo leaked sensitive files, putting its clientele in the vast South American country in peril.
- Volvos retailer in Brazil, Dimas Volvo, leaked sensitive files through its website.
- The leaked files could have served malicious actors in various ways, including hijacking official communication channels and infiltrating the companys systems.
- The issue causing the leak has been fixed.
Volvo, a Swedish luxury vehicle manufacturer with over 95,000 employees and sales of nearly 700,000 vehicles annually, is a highly attractive target for criminals since the company caters to a wealthy clientele.
The Cybernews research team discovered that the retailer of Volvo vehicles in Brazil, Dimas Volvo, was leaking sensitive files through its website for nearly a year.
The leaked files could have served malicious actors in various ways, including hijacking official communication channels and infiltrating the companys systems.
Cybernews contacted Dimas Volvo and data protection officers at Volvo headquarters, and the issue causing the leak was fixed.
Exposed sensitive files
On February 17, 2023, the Cybernews research team discovered public access to sensitive files hosted on dimasvolvo.com.br website, belonging to an independent Volvo retailer in the Santa Catarina region of Brazil.
Volvos retailer exposed its databases authentication information, including MySQL and Redis database hosts, open ports and credentials. These credentials could further be exploited to access the contents of the databases, which might have stored private user data.
Researchers also stumbled upon the websites Laravel application key. The exposure of this key is particularly dangerous because it could have been used to decrypt user cookies, which often hold sensitive information such as credentials or session IDs. An attacker could exploit this data to hijack the victims account.
Access to source code
Among the leaked data, researchers also observed the URL of the Git repository where the websites source code is stored, revealing the repository name and who created it.
Attackers may have exploited leaked credentials to brute force access to the repository, since they only needed a password, which is faster than guessing both a username and password.
The researchers also discovered a .DS_Store file that held metadata from the developers computer, revealing the file and folder names in the directory where the websites project files were stored.
Attackers could have used the information about the websites structure to...
19:22
A New Approach to Computation Reimagines Artificial Intelligence Lifeboat News: The Blog
By imbuing enormous vectors with semantic meaning, we can get machines to reason more abstractly and efficiently than before.
18:18
Arkansas Just Passed an Age-verification Social Media Law With Some Confusing Exemptions SoylentNews
There's confusion over which companies will be affected:
The law requires social media companies that earn more than $100 million in annual revenue to work with third-party services to verify new account holders' personal information. This is done using "any commercially reasonable age verification method" or government-issued IDs such as photo IDs or driver's licenses. Current account holders won't be affected.
The law states that social media companies are defined as any online forum that lets users create public profiles and interact with each other through digital content.
CNN reports that in the final days of negotiations over the bill, Arkansas lawmakers approved an amendment that appears to exempt some of the world's biggest social media companies. Given all the concern over TikTok's influence and its links with China, it's surprising to see that social media platforms that permit users to "generate short video clips of dancing, voice overs, or other acts of entertainment in which the primary purpose is not educational or informative" are exempt. That would also seem to cover Facebook, Instagram, Snapchat, as well as TikTok - but apparently not.
[...] Other exemptions include social media companies that "exclusively" offer subscription content, and those focused on "professional networking" and "career development" (i.e., LinkedIn). Companies that "exclusively offer" video gaming-focused social networking features aren't covered, either, which could include Twitch despite it not really being a social media platform.
At least it will protect the kids from all the remaining $100M/yr companies that weren't covered by the exemptions.
Read more of this story at SoylentNews.
18:09
IRC Proceedings: Friday, April 14, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-140423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-140423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-140423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-140423.gmi
Over HTTP:
|
... |
18:00
Uranium-241 Isotope Created and Examined Via Multinucleon Transfer Reactions and Mass Spectrometry Hackaday

A recent paper (PDF) in Physical Review Letters by T. Niwase and colleagues covers a fascinating new way to both create and effectively examine isotopes by employing a cyclotron and a mass spectrograph. In the paper, they describe the process of multinucleon transfer (MNT) and analysis at the recently commissioned KEK Isotope Separation System (KISS), located at the RIKEN Nishina Center in Japan.
17:00
Water-absorbing feathers could inspire better bottles and fog harvesters Terra Forming Terra

This is so odd. It works to both absorb water, but to also prevent a reversal of the process. No other bird does this and replicating this can be handy. Now imagine a water permiable membrane feeding an underlying layer. Handy in arid conditions for preserving water from your sweat.
Pragmatic approach may be the way forward for clinical trials Terra Forming Terra


SpaceX Starship Super Heavy April 17 Launch Date Terra Forming Terra
15:32
Links 15/04/2023: This Week in KDE and More Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Instructionals/Technical
-
Net2 Understanding the basic components of the Linux operating system architecture
If youre already a Linux user and maybe even a system admin for single systems, this article is for you.
-
-
Games
-
DragonFly BSD Digest SimCity 2000 in DOSBox
Si...
-
-
15:03
Read "Calamities causing loss of museum collections: a historical and global perspective on museum disasters" by Michael J. Tyler, Dale Roberts, and our Lydia A. Fucsko. Lifeboat News
Read "Calamities causing loss of museum collections: a historical and global perspective on museum disasters" by Michael J. Tyler, Dale Roberts, and our Lydia A. Fucsko.
15:03
MIT Technology Review Became Spamfarm of Microsoft Techrights
Four days ago: MIT Technology Review is Running SPAM for Microsoft and Azure (Distracting From Mass Layoffs)
Two months ago: MIT Technology Review is Run by Microsoft India

Hyping up AI for Microsoft et al under the guise of study,
by paying for puff pieces about the study

100% of the articles for that day are just paid-for spam about
grooming??? 8 pieces on that one day (more than
whats shown here) were all sponsored. Their RSS feed too
became marketing. The sponsored stuff isnt being separated.
15:00
Kicad Autorouting Made Easy Hackaday

One of the most laborious tasks in PCB layout is the routing. Autorouting isnt always perfect, but it is nice to have the option, even if you only use it to get started and then hand-tune the resulting board. Unfortunately, recent versions of Kicad have dropped support for autorouting. You can, however, still use Freerouting and the video from [Mr. T] below shows you how to get started.
There are three ways to get the autorouting support. You can install Java and a plugin, you can isntall using a ZIP file, or you can simply export a Specctra DSN file and use Freerouting as a standalone program. Then you import the output DSN file, and you are done.
Not only does [Mr. T] show you how to do a simple USB board, he also shows you how to rip up the autorouters work if you dont like it. He also covers some tips to get the best results with the router.
For example, it is often advantageous to manually layout a few critical tracks before you run the autorouter. You can also use net classes to specify parameters for some tracks.
Overall, this is a worthwhile thing to do. After all, you dont have to use autorouting, but it is nice to have it available if you want it. If you dont like Freerouting, you can try a different solution. Of course, these routers use DSN, so you can use them...
13:58
Google Releases Urgent Chrome Update to Fix Actively Exploited Zero-Day Vulnerability The Hacker News
Google on Friday released out-of-band updates to resolve an actively exploited zero-day flaw in its Chrome web browser, making it the first such bug to be addressed since the start of the year. Tracked as CVE-2023-2033, the high-severity vulnerability has been described as a type confusion issue in the V8 JavaScript engine. Clement Lecigne of Google's Threat Analysis Group (TAG) has been
13:36
Deep Space Missions Must Recreate Exact Earth-Like Conditions to Survive, Scientists Argue SoylentNews
One of the main questions surrounding humanity's next giant leap into deep space is whether humans can thrive on missions far from Earth. A new theory says yes, but only in environments modeled deeply after our own planet.
Father-daughter research duo Morgan Irons of Cornell University and Lee G. Irons from the Norfolk Institute dub the idea "pancosmorio," a word that means "all word limit," in a paper published in Frontiers in Astronomy and Space Sciences last month. Irons and Irons argue that, to allow humans to survive on lengthy treks into deep space, these missions must recreate Earth-like ecosystems, including Earth-like gravity and oxygen, reliable sources of water, as well as societal systems like steady agricultural output and the recycling of waste.
"For humans to sustain themselves and all of their technology, infrastructure and society in space, they need a self-restoring, Earth-like, natural ecosystem to back them up," said Morgan Irons in a press release from the institution. "Without these kinds of systems, the mission fails."
[...] "There are conditions from which human life has evolved. Such conditions are required to sustain human life at its current level of growth," the scientists write in their study. "The availability of such conditions to humans defines the limit of their world."
Read more of this story at SoylentNews.
13:26
Musk Incorporates X.AI cryptogon.com
Via: The Verge: Elon Musk has created a new company dedicated to artificial intelligence and its called X.AI, as first reported by The Wall Street Journal. The company, which a Nevada filing indicates was incorporated last month, currently has Musk as its director and Jared Birchall, the director of Musks family office, listed as []
12:54
What Are Transformer Models and How Do They Work? cryptogon.com
Via: cohere.ai: So why would a transformer model build text word by word? One answer is, because that works really well. A more satisfying one is that because transformers are so incredibly good at keeping track of the context, that the next word they pick is exactly what it needs to keep going with an []
12:30
Cobalt Iron updates Compass platform with new data governance capabilities Help Net Security
Cobalt Iron has updated its Compass enterprise SaaS backup platform with new data governance capabilities comprising policy-based controls and an approval framework for decommissioning systems and deleting data. The automation and policy-based discipline for system decommissioning and associated data deletion are unique to Compass and will deliver defensible data deletion and system retirement. Data governance is about being a good steward over data during its entire life cycle, from its creation or acceptance to its More
The post Cobalt Iron updates Compass platform with new data governance capabilities appeared first on Help Net Security.
12:23
SpaceX Receives a Launch License from the FAA for Starship cryptogon.com
Via: Ars Technica: On Friday afternoonafter much angst and anxious waiting by the spaceflight communitythe Federal Aviation Administration issued a launch license to SpaceX for the launch of its Starship rocket from South Texas. After a comprehensive license evaluation process, the FAA determined SpaceX met all safety, environmental, policy, payload, airspace integration and financial responsibility []
12:20
Daon brings IdentityX to healthcare industry Help Net Security
Daon is expanding its IdentityX to the healthcare industry to enable organizations to safeguard identities for providers, staff, and patients. As the healthcare industry continues to digitize sensitive healthcare online information, cyber attacks increase and new regulations are established, Daons Fast Healthcare Interoperability Resources (FHIR)-compliant solutions will reduce fraud for healthcare workers and staff, digital health app providers, and patients. Daon IdentityX provides identity proofing and authentication solutions for every touchpoint patient care, medical More
The post Daon brings IdentityX to healthcare industry appeared first on Help Net Security.
12:00
Need To Pick Objects Out Of Images? Segment Anything Does Exactly That Hackaday

Segment Anything, recently released by Facebook Research, does something that most people who have dabbled in computer vision have found daunting: reliably figure out which pixels in an image belong to an object. Making that easier is the goal of the Segment Anything Model (SAM), just released under the Apache 2.0 license.
10:34
Read the free paper "You Have a Duty to Migrate Off-Planet... (From Blue Origin to Green Destiny: Gerard K. O'Neill and Planetary Crises)" by our Charles Tandy. Lifeboat News
Read the free paper "You Have a Duty to Migrate Off-Planet (From Blue Origin to Green Destiny: Gerard K. O'Neill and Planetary Crises)" by our Charles Tandy.
09:53
Duffy: Run an open source-powered virtual conference! LWN.net
On her blog, Mirn Duffy writes about using open-source software to run a virtual conference. The Fedora design team recently ran the first Creative Freedom Summit as a virtual conference for FOSS creative tools. The team could have used the same non-open-source platform that is used by the Flock Fedora conference, but took a different path:
Using Matrix's Element client, we embedded the live stream video and an Etherpad into a public Matrix room for the conference. We used attendance in the channel to monitor overall conference attendance. We had live chat going throughout the conference and took questions from audience members both from the chat and the embedded Q&A Etherpad.
Back in 2020, the Linux Plumbers Conference also put together a virtual conference using free software, as did LibrePlanet and likely others.
09:45
Thales prepares to protect European infrastructures from quantum attacks Help Net Security
Thales has joined forces with around twenty deep tech, academic and industry partners, as part of the EuroQCI initiative (European Quantum Communication Infrastructure), which aims to deploy a quantum communication infrastructure for EU member states within three years. By 2040, quantum computers could use their unprecedented computational power to decode encrypted data, incomparably threatening the security of even the best-protected communication systems. EuroQCI aims to counter that threat by developing sovereign systems to protect the More
The post Thales prepares to protect European infrastructures from quantum attacks appeared first on Help Net Security.
09:30
Sinister Secret of the Shang Dynasty: Its Penchant for Human Sacrifice Terra Forming Terra
09:30
Deloitte and Riskified help eCommerce merchants analyze their fraud exposure Help Net Security
Riskified has unveiled its partnership with Deloitte to empower merchants with real-time insight into how their chargebacks, approval rates and fraud costs compare to similar companies in their space. This benchmarking service is helping retailers formulate a scorecard that can uncover new opportunities to reduce operational costs, lower chargeback and fraud losses, and boost revenues by minimizing false declines. This offering is underpinned by Riskifieds extensive eCommerce, fraud and identity intelligence derived from analyzing more More
The post Deloitte and Riskified help eCommerce merchants analyze their fraud exposure appeared first on Help Net Security.
09:25
Votiro collaborates with Sumo Logic to provide analytics on file-borne threats Help Net Security
Votiro has integrated with Sumo Logic to enable reliable and secure cloud-native applications. Users can now send high-fidelity data and insights discovered by Votiro Cloud into the Sumo Logic Cloud SIEM console. Enterprises are relying on collaboration platforms, cloud workloads and storage environments more than ever before. File sharing and Cloud data usage will continue to expand, providing more opportunities for bad actors to penetrate enterprise networks through file-borne malware. Sumo Logics Cloud SIEM automatically More
The post Votiro collaborates with Sumo Logic to provide analytics on file-borne threats appeared first on Help Net Security.
09:00
Building an Electron Microscope For Research Hackaday

There are a lot of situations where a research group may turn to an electron microscope to get information about whatever system they might be studying. Assessing the structure of a virus or protein, analyzing the morphology of a new nanoparticle, or examining the layout of a semiconductor all might require the use of one of these devices. But if your research involves the electron microscope itself, you might be a little more reluctant to tear down these expensive devices to take a look behind the curtain as the costs to do this for more than a few could quickly get out of hand. Thats why this research group has created their own electron detector.
Specifically, the electron detector is designed for use in a scanning electron microscope, which is typically used for inspecting the surface of a sample and retrieving a high-resolution, 3D image of it compared to transmission microscopes which can probe internal structures. The detector is built on a four-layer PCB which includes the photodiode sensing array, a series of amplifiers, and a power supply. All of the circuit diagrams and schematics are available for inspection as well thanks to the design being licensed under the ope...
08:53
Massachusetts Lawmakers File Bill to Create 4-Day Workweek Pilot SoylentNews
Following a similar program in Europe, two Massachusetts lawmakers have filed a bill this week to create a two-year pilot program for a four-day workweek.
[...] The pilot program would run for two years and would be overseen by the Executive Office of Labor and Workforce Development. To participate, employers must agree to transition at least 15 workers to a shortened workweek.
While the bill was just filed this week, a number of businesses have already reached out to ask how they can participate, according to Cutler.
"I think this is really the perfect time for this kind of pilot program, given the changes we've seen in hybrid work as a result of the pandemic and the need to look for creative solutions to our current labor market challenges," Cutler said in an email response to Computerworld.
If the legislation passes, employers who participate in the pilot would agree to reduce the hours of all or some of their employees without reducing overall pay, status, or benefits. Businesses will also be eligible for a tax credit for their participation in the study and necessary data collection, Cutler said.
While the pilot program is designed to run for two years, individual businesses are not required to participate the entire time. The proposal is aimed at discovering the feasibility and benefits of a four-day work week.
"We chose this amount of time because we wanted to ensure a robust response and data availability. I have seen a variety of different lengths. In Maryland, there is a bill proposing a five-year pilot, for example. In this case, we felt two years struck a good balance," Cutler said. (The Maryland proposal was withdrawn earlier this year.)
The Massachusetts legislation doesn't call for participating organizations to adopt a strict 32-hour work week; instead, it states employees must receive "a meaningful reduction in actual work hours."
Read more of this story at SoylentNews.
08:04
A cyberattack on the Cornwall Community Hospital in Ontario is causing treatment delays Security Affairs
The Cornwall Community Hospital in Ontario, Canada, is under a cyber attack that is causing delays to scheduled and non-urgent care.
A cyberattack on the Cornwall Community Hospital in Ontario, Canada, is causing delays to scheduled and non-urgent care.
The cyber attack was discovered on Tuesday, April 11, 2023, it is investigating the incident with the help of cybersecurity experts.
On April 11, 2023, Cornwall Community Hospital (CCH) identified a network issue, which an investigation has revealed to be a cyber incident. The hospital has retained external cyber experts, working with our technical team to resolve the issue. reads a statement published by the hospital. Delivering exceptional patient-centered care is the hospitals top priority and CCH continues to provide high-quality clinical services. However, residents may experience some delays to scheduled or non-urgent care.
The hospital pointed out that its clinical Electronic Health Record has not been impacted by the cyber attack. The users were not able to access MyChart due to the ongoing attack.
The Cornwall Community Hospital has yet to provide details about the attack, but the problems it is facing suggest it has suffered a ransomware attack.
Unfortunately, hospitals are easy targets for ruthless cybercriminals, in early February, the Tallahassee Memorial HealthCare (TMH) hospital has taken its IT systems offline and suspended non-emergency procedures after a cyberattack.
Tallahassee Memorial HealthCare suspended emergency medical services (EMS), and it announced that patients will be diverted to other hospitals.
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections:
- The Teacher Most Educational Blog
- The Entertainer Most Entertaining Blog
- The Tech Whizz Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please nominate Security Affairs as your favorite blog.
Nominate here: https://docs.google.com/forms/d/e/1FAIpQLSfaFMkrMlrLhOBsRPKdv56Y4HgC88Bcji4V7OCxCm_OmyPoLw/viewform
Follow me on Twitter: ...
06:43
Comunicado de prensa para Latinoamrica: La propuesta de tratado de la ONU sobre ciberdelincuencia carece de suficientes salvaguardias de derechos humanos, lo que agrava las amenazas a la privacidad y las libertades civiles en Latinoamrica Deeplinks
VIENA-El martes 18 de abril, a las 10:00 am hora del Pacfico
(1:00 pm hora del Este), expertos de Electronic Frontier Foundation
(EFF) y tres aliados latinoamericanos de derechos digitales
informarn a los reporteros sobre las amenazas nicas a la privacidad
que plantea la propuesta de Tratado sobre
Delitos Cibernticos de la ONU, que podra autorizar el uso de
programas espa que ya se estn desplegando contra periodistas y
defensores de los derechos humanos.
El tratado, que ha sido objeto de negociaciones entre los Estados
miembros de la ONU durante un ao,
carece hasta ahora de compromisos firmes con los derechos
humanos y de condiciones y salvaguardias detalladas necesarias
para proteger los derechos de las personas y las organizaciones de
la regin.
La sesin informativa, de una hora de duracin, se retransmitir en
directo desde la
quinta sesin de negociaciones del tratado en Viena, donde
representantes de ms de 100 Estados miembros se renen para debatir
un proyecto de documento que servir de base para el tratado.
Expertos de la EFF, la Red en Defensa de los Derechos Digitales
(R3D), Derechos Digitales y la Fundacin Karisma hablarn de cmo el
borrador crea ms de 30
nuevos delitos cibernticos; nuevos procedimientos penales para
el intercambio transfronterizo de presuntas pruebas, incluidos los
datos privados de los usuarios; y mayores poderes de vigilancia
policial. Los Estados que firmen el tratado incorporarn estos
delitos y procedimientos a sus cdigos penales nacionales.
Sin las debidas salvaguardias de los derechos humanos en el
tratado, estas medidas son incompatibles con las normas
interamericanas de derechos humanos que refuerzan la libertad de
expresin, la privacidad y el debido proceso, lo que supone un
enorme revs para las libertades civiles en toda Amrica Latina.
Es ms, el tratado se est negociando mientras aumentan las pruebas
de que programas espa como Pegasus y el pirateo gubernamental se
han utilizado contra grupos vulnerables,
periodistas y
act...
06:28
Russian Registry Revokes TorrentGalaxys Domain Name for Unknown Reasons TorrentFreak
 The
Soviet Union was dissolved more than thirty years ago, but the
former transcontinental state still has its own .su TLD.
The
Soviet Union was dissolved more than thirty years ago, but the
former transcontinental state still has its own .su TLD.
The .su domain extension isnt exactly mainstream. There are a little over 100,000 active domains, with .su extensions reportedly proving popular among cybercriminals.
Experts have cited outdated terms and a lack of enforcement as historical reasons for the cybercrime appeal. However, recent actions show that the Russian Institute for Public Networks, which maintains the .su domain, can certainly intervene.
TorrentGalaxy Loses Control over .SU Domain
A few days ago popular torrent site TorrentGalaxy lost control of its .su domain name. The domain stopped resolving out of the blue and upon closer inspection, was found to be no longer delegated.
Whois research confirms that the domains status is listed as REGISTERED, NOT DELEGATED, without providing any further detail.
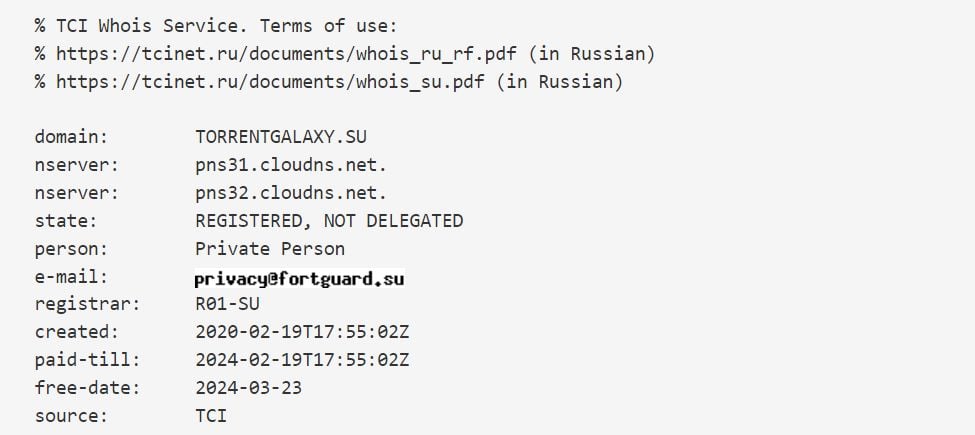
TorrentGalaxy informs TorrentFreak that its Russian registrar R01 hasnt sent any information about the issue and all questions remain unanswered. The torrent site hasnt heard anything from the Russian Institute for Public Networks, the .su registry, either.
We havent gotten any notification of the disconnection. It still shows as active on our side. In fact, the weird EPP status on the domain whois and the domain not resolving to anything have been the only info for us as well, the operator explains.
TorrentFreak reached out to both the registry and registrar but we havent heard back. This means that the exact reason for the domain revocation remains unknown.
Government Connection
Since the DNS zone was effectively removed, it appears that the registry intervened. This can happen for a variety of reasons, including court orders, voluntary actions, or Government instructions.
Russia already requires Internet providers and search engines to block hundreds of thousands of sites, for...
06:27
Why is Juice Jacking Suddenly Back in the News? Krebs on Security

KrebsOnSecurity received a nice bump in traffic this week thanks to tweets from the Federal Bureau of Investigation (FBI) and the Federal Communications Commission (FCC) about juice jacking, a term first coined here in 2011 to describe a potential threat of data theft when one plugs their mobile device into a public charging kiosk. It remains unclear what may have prompted the alerts, but the good news is that there are some fairly basic things you can do to avoid having to worry about juice jacking.
On April 6, 2023, the FBIs Denver office issued a warning about juice jacking in a tweet.
Avoid using free charging stations in airports, hotels or shopping centers, the FBIs Denver office warned. Bad actors have figured out ways to use public USB ports to introduce malware and monitoring software onto devices. Carry your own charger and USB cord and use an electrical outlet instead.
Five days later, the Federal Communications Commission (FCC) issued a similar warning. Think twice before using public charging stations, the FCC tweeted. Hackers could be waiting to gain access to your personal information by installing malware and monitoring software to your devices. This scam is referred to as juice jacking.
The FCC tweet also provided a link to the agencys awareness page on juice jacking, which was originally published in advance of the Thanksgiving Holiday in 2019 but was updated in 2021 and then again shortly after the FBIs tweet was picked up by the news media. The alerts were so broadly and breathlessly covered in the press that a mention of juice jacking even made it into this weeks Late Late Show with James Corden.
The term juice jacking crept into the collective paranoia of gadget geeks in the summer of 2011, thanks to the headline for a story here about researchers at the DEFCON hacker convention in Vegas whod set up a mobile charging station designed to educate the unwary to the reality that many mobile devices connected to a computer would sync their data by default.
Since then, Apple, Google and other mobile device makers have c...
06:22
Wine 8.6 Released With Bundled Musl Libc Math Library Phoronix
Wine 8.6 is out as the newest bi-weekly development release of this open-source software to enjoy Windows games and applications on Linux and other platforms...
06:12
Study Finds Only One Type of Consumer Dictates Price SoylentNews
Researchers compare multiple categories of shoppers and find the linchpin:
It's commonly assumed that the supply-and-demand economics of the consumer marketplace dictates price. If you are one of few retailers that sells a product consumers want, you can charge more. Or, if supplies of that product are more scarce, again, prices will likely be higher. On the flip side, if supplies are plentiful for a product that is in less demand, prices for that product are likely to be lower.
But researchers have found it's not always that simple. Thanks to the internet and e-commerce, more consumers have taken advantage of going to a physical store to inspect items before purchase, leaving that store, and then purchasing the product at a lower price elsewhere. This is called "showrooming."
This has led to several assumptions in the retail industry, from the thought that showrooming will put brick-and-mortar retailers out of business, to the notion that the showrooming trend has driven prices down across the board. A new study has found these may both be false.
[...] "Showroomers do their research in advance," says Bar-Isaac. "They know what they want, they already know what that retailer may charge, and they go to stores with more limited or shallow selections in search of a better price."
Read more of this story at SoylentNews.
06:00
Fail of the Week: Car Starter Motors Arent the Best Fit for eBikes Hackaday

A lot of what real engineering is all about is designing to the limits of your materials, with a healthy margin for error. On the other hand, seat-of-the-pants engineering often takes the opposite tack working with the materials you have and finding their limits after the fact. While the former is more rigorous and better suited to anything where life and limb are on the line, theres something to be said for the flexibility that informal engineering offers.
[Austin Blake]s latest eBike is a case study in informal engineering. [Austin] started out wondering if a starter motor from a car engine would make a decent electric bike motor. Our first instinct before watching the video below was to answer that question with a resounding No! Yes, starter motors seem like a natural for the job, delivering high torque in a compact package. But starting a car engine is the very definition of a low-duty-cycle application, since it should only take a second or two of cranking to get an engine started. Pressing a motor designed for such a task into continuous duty seems like, well, a non-starter.
And to be fair, [Austin] fully ack...
05:50
Google fixed the first Chrome zero-day of 2023 Security Affairs
Google released an emergency security update to address a zero-day vulnerability in Chrome which is actively exploited in the wild.
Google released an emergency security update to address the first Chrome zero-day vulnerability (CVE-2023-2033) in 2023, the company is aware of attacks in the wild exploiting the issue.
The vulnerability is a Type Confusion issue that resides in the JavaScript engine V8. The vulnerability was reported by Clment Lecigne of Googles Threat Analysis Group on 2023-04-11.
Type Confusion in V8. Reported by Clment Lecigne of Googles Threat Analysis Group on 2023-04-11 reads the advisory published by Google. Google is aware that an exploit for CVE-2023-2033 exists in the wild.
channel, this means that it will be available to the entire user base over the coming days or weeks.The Stable and extended stable channel has been updated to 112.0.5615.121 for Windows Mac and Linux which will roll out over the coming days/weeks. continues the advisory
Google did not disclose details of the attacks exploiting this vulnerability, it will not provide bug details and links until a majority of users will have updated their installs.
Access to bug details and links may be kept restricted until a majority of users are updated with a fix. We will also retain restrictions if the bug exists in a third party library that other projects similarly depend on, but havent yet fixed. concludes the advisory.
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections:
- The Teacher Most Educational Blog
- The Entertainer Most Entertaining Blog
- The Tech Whizz Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please nominate Security Affairs as your favorite blog.
Nominate here: https://docs.google.com/forms/d/e/1FAIpQLSfaFMkrMlrLhOBsRPKdv56Y4HgC88Bcji4V7OCxCm_OmyPoLw/viewform
Follow me on Twitter: @securityaffairs and ...
05:48
EFF, International Allies Warn That Proposed UN Cybercrime Treaty, Rather Than Making Us More Secure, Could Legitimize Intrusive Surveillance and Drag Down Global Privacy and Free Expression Standards Deeplinks
EFF and international allies Access Now, Article 19,
Epicenter, and Global Partners Digital are in Vienna this week and
next for the fifth round of negotiations on the proposed UN
Cybercrime Treaty, along with the over 100 representatives of
Member States hashing out a new draft text.
While we have not yet been allowed to speak on the flooror even sit
in the same room as delegatesthat has not stopped us from speaking
out for users about the lack of human rights protections, the
criminalization of online speech, the fostering of greater
surveillance powers, and other dangers posed by the treaty in its
current form.
At a livestreamed briefing yesterday in Vienna, we provided a
reality check on how the talks have moved in troubling directions
and challenged negotiators to seize this rare
opportunitynegotiating a UN Treaty only happens every other
decadeto draft a cybercrime treaty that does not undermine, but
actually protects, privacy and free expression.
You can view the media briefing here:
https://www.youtube.com/watch?v=POwrbFrJADU
Briefing highlights:
Katitza Rodriguez, Policy Director for Global
Privacy, EFF
One big issue we're facing is that there isn't an effective global system in place to make sure human rights are enforced. Not many governments want to limit their own power to spy and track people closely. Because of this, the Convention might end up legitimizing intrusive surveillance power that invades people's private lives and infringe upon their rights.
Barbora Bukovsk, Senior Director for Law and Policy, ARTICLE 19
We are really concerned that many provisions of this treaty restrict freedom of expression. States must not lose sight of the fact that content offenses, if coupled with surveillance powers and other restrictions, will create international carte blanche for those who want to use use this tool to restrict freedom of expression globally.
Raman Jit Singh Chima, Senior International Counsel and Global Cybersecurity Lead, Access Now
Our view is simple. Any UN cybercrime treaty should make us more cyber secure, it should not make us less less cyber secure. A key part of any such international legal framework should look at the human beings involved in cyber security, namely security researchers, digital security trainers, as well as journalists who investigate vulnerabilities and ga...
05:46
Re: ncurses fixes upstream Open Source Security
Posted by Tavis Ormandy on Apr 14
I'm curious what the attack is! ISTR that terminfo definitions cancontain shell commands by design and so are generally considered
trusted.
I remember using this trick in an exploit once :)
$ printf "exploit, iprog=/usr/bin/id,\n" | tic -
$ TERM=exploit reset
uid=1000(taviso) gid=1000(taviso)
Tavis.
05:04
Standard Life Investigated Sirius Pension Fraud Without Even Collecting Any Evidence or Contacting Sirius schestowitz.com
Video
download link | md5sum
e02b55eac9a1d3690b44015080f5f9c2
So-called Pension Investigation
Creative Commons Attribution-No Derivative Works 4.0
Summary: The crimes of Sirius Corporation were discussed with Standard Life several times this week; Standard Life workers are evasive and theyre belittling the matter as they try to wash their hands of us despite partial culpability (legitimising the fraud, not protecting their reputation)
THE VIDEO above is a tad long, so processing took a long time and since then weve found out that the French court approves Macrons unpopular plan to raise pension age; the English-speaking media in France calls it a deeply unpopular pensions overhaul, taking note of three months of strikes and mass protests. Of course due to the publicity/media sophistry, Macron will be mentioned in relation to other things. A lot of the media will go on and on about Macron and Taiwan, not his ongoing attacks on millions of people in his own country.
Regardless of what happened in France some hours ago, the video above explains our own ordeals at Sirius Open Source, a company which basically robbed its own staff under the guise of pension (which never existed). To make matters far worse, a very large pension provider (one of the largest in the UK) is trying to cover things up. I confronted them about contradictory messages, including some from managers. Well, they see something that says 2016 and n...
04:43
Standard Life Tacitly Admits Doing a Sham Investigation Without Bothering to Contact Sirius, Customer Relations Confesses That Manager Lied About Key Dates (Years) Several Times Techrights
Video
download link | md5sum
e02b55eac9a1d3690b44015080f5f9c2
So-called Pension Investigation
Creative Commons Attribution-No Derivative Works 4.0
Summary: The crimes of Sirius Corporation were discussed with Standard Life several times this week; Standard Life workers are evasive and theyre belittling the matter as they try to wash their hands of us despite partial culpability (legitimising the fraud, not protecting their reputation)
THE VIDEO above is a tad long, so processing took a long time and since then weve found out that the French court approves Macrons unpopular plan to raise pension age; the English-speaking media in France calls it a deeply unpopular pensions overhaul, taking note of three months of strikes and mass protests. Of course due to the publicity/media sophistry, Macron will be mentioned in relation to other things. A lot of the media will go on and on about Macron and Taiwan, not his ongoing attacks on millions of people in his own country.
The short story is, theyre protecting themselves and the perpetrators that paid them (to help scam a lot...
04:32
Links 14/04/2023: Godot 3.6 Reaches Beta, OSI Celebrates Proprietary Money Techrights
![]()
Contents
-
GNU/Linux
-
Audiocasts/Shows
-
A new Era on Linux Has Dawned, Teaser 6
Enjoy our latest Teaser of our upcoming Max release
-
-
Instructionals/Technical
-
How do I Install & Uninstall MySQL in Linux?
MySQL is one of the most famous relational database management systems in the current market. The capabilities of this RDBMS are not only amazing but also quite user-friendly. Many people prefer MySQL over other alternatives available in the market. Often, installing MySQL and removing it from a Linux-based operating system can be quite daunting for new beginners. If that is the case, then this post will be your friend and guide you through the process. Lets Begin.
-
Top Tips for Optimizing Kali Linux After Installation
...
-
-
04:30
Intel Lands Linux Audio Fix For Arc Graphics A750/A770 Phoronix
If you have been running a Linux 6.3-based kernel or later Linux 6.2 point release and have encountered your HDMI audio breaking when making use of Intel Arc Graphics A750/A770 hardware, a fix is on the way...
04:15
Latam Media Briefing: Proposed UN Cybercrime Treaty Lacks Sufficient Human Rights Safeguards, Exacerbating Threats to Privacy and Civil Liberties in Latam Deeplinks
VIENNAOn Tuesday, April 18, at 10:00 am Pacific Time (1:00
pm Eastern Time), experts from Electronic Frontier Foundation (EFF)
and three Latin American digital rights allies will brief reporters
about the unique threats to privacy posed by the proposed UN Cybercrime
Treaty, which could authorize the use of spyware
already being deployed against journalists and human rights
defenders.
The treaty, which has been the subject of negotiations among UN
Member States for a year, so far
lacks strong commitments to human rights and detailed
conditions and safeguards needed to protect the rights of
individuals and organizations in the region.
The one-hour briefing will be livestreamed from the
fifth session of treaty negotiations in Vienna,
where representatives from over 100 Member States are meeting
to discuss a draft document that will serve as a basis for the
treaty.
Experts from EFF, Network in Defense of Digital Rights (R3D),
Derechos Digitales, and Fundacion Karisma will discuss how the
draft creates over 30
new cybercrime offenses; new criminal procedures for
cross-border sharing of alleged evidence, including private user
data; and increased police surveillance powers. States that sign on
to the treaty would adopt these offenses and procedures into their
national criminal codes.
Without appropriate human rights safeguards written into the
treaty, these measures are incompatible with Inter-American human
rights standards reinforcing freedom of expression, privacy, and
due process, dealing an enormous setback for civil liberties across
Latin America.
Whats more, the treaty is being negotiated as evidence mounts that
spyware like Pegasus and government hacking have been used against
vulnerable groups,
journalists, and...
03:30
AMD openSIL Detailed For Advancing Open-Source System Firmware Phoronix
Open-source fans, rejoice, the most exciting thing I have read all week or perhaps the month: "AMD is committed to open-source software and is now expanding into the various firmware domains with the re-architecture of its x86 AGESA FW stack - designed with UEFI as the host firmware that prevented scaling, to other host firmware solutions such as coreboot, oreboot, FortiBIOS, Project Mu and others. A newer, open architecture that potentially allows for reduced attack surface, and perceivably infinite scalability is now available as a Proof-of-Concept, within the open-source community for evaluation, called the AMD openSIL Open-Source Silicon Initialization Library."..
03:27
Elon Musk Admits He Only Bought Twitter Because He Thought He'd be Forced to SoylentNews
Elon Musk admits he only bought Twitter because he thought he'd be forced to:
Elon Musk gave a rare interview to an actual reporter late on Tuesday, speaking to BBC reporter James Clayton on Twitter Spaces. During the interview, Clayton pressed Musk on whether his purchase of Twitter was, in the end, something he went through with willingly, or whether it was something he did because the active court case at the time in which Twitter was trying to force him to go through with the sale was going badly.
The answer (which we all suspected anyway) was that Musk did indeed only do the deal because he believed legally, he was going to be forced to do so anyway. Here's the relevant transcript from the Twitter Spaces audio:
Clayton: So then you change your mind again, and decided to buy it did you do that? Did you do that?
Musk: Well, I kind of had to.
Clayton: Right. Did you do that, because you thought that a court would make you do that?
Musk: Yes.
Clayton: Right.
Musk: Yes, that is the reason.
Clayton: So you were still trying to get out of it. And then you just were advised by lawyers, "Look, you're going to buy this?"
Musk: Yes.
In case you don't recall (it was all the way back in September/October last year which is basically an eternity ago in current Twitter time), Twitter took Musk to trial to force him to honor his signed obligation to acquire the company for the agreed-upon price of $44 billion, or $54.20 per share. Musk was contending that his obligation was void because Twitter had, he claimed, inflated its real user numbers and understated the number of bots on the platform.
Musk then notified the SEC that he intended to buy the company after all at the price he originally set with the company, a move most agreed at the time was made because his legal case was weak and the trial was clearly not going his way.
Read more of this story at SoylentNews.
03:02
Naomi Wolf: Whats in the Pfizer Documents? cryptogon.com
The Pfizer documents contain evidence of the greatest crime against humanity in the history of our species. Via: Hillsdale College:
02:45
Watch "Mind-Blowing Facts About Our Reality [4K] | The Secrets of Quantum Physics | Spark" by our Jim Al-Khalili. Lifeboat News
Watch "Mind-Blowing Facts About Our Reality [4K] | The Secrets of Quantum Physics | Spark" by our Jim Al-Khalili.
02:19
[$] TOTP authentication with free software LWN.net
One-time passwords (OTPs) are increasingly used as a defense against phishing and other password-stealing attacks, usually as a part of a two-factor authentication process. Perhaps the most commonly used technique is sending a numeric code to a phone via SMS, but SMS OTPs have security problems of their own. An alternative is to use time-based one-time passwords (TOTPs). The normal TOTP situation is to have all of the data locked into a proprietary phone app, but it need not be that way.
02:00
Hackaday Podcast 214: Jet Engine Hair Dryer, Comic Sans Type Balls, and Belief in Graphene Hackaday

This week, Editor-in-Chief Elliot Williams and Contributor Emeritus Kristina Panos gushed about all the best hacks of the previous week. But first, a contest! Thats right hot on the heels of the Low Power Challenge comes the Op Amp Challenge, sponsored by Digi-Key. You have between now and June 6th to dip your toes into the warm waters of analog and show us what youve got. Will it be a musical hack? Will you seek high analog precision? We cant wait to see.
Kristina definitely did not get Whats That Sound this week, which honestly reminded her of a cartoon character getting a piano dropped on them, except the sounds were in reverse order. Then its on to the hacks, beginning with a way to make an IBM Selectric typewriter use Comic Sans, a project thats sure to make you a believer in graphene, and a miniature MNT for every (cargo) pocket.
From there we take a look at a really cool indicator from a 1960s RAF aeroplane and investigate why your multimeter might be lying to you. Finally, we discuss the gargantuan task of building an AR system to rival Google Glass, and the merits of taking a lot of pictures as you go about your hacks.
Check out the links below if you want to follow along, and as always,...
02:00
Video Friday: Ingenuitys 50th Flight IEEE Spectrum

Video Friday is your weekly selection of awesome robotics
videos, collected by your friends at IEEE Spectrum
robotics. We also post a weekly calendar of upcoming robotics
events for the next few months. Please
send us your events for inclusion.
Robotics Summit & Expo: 1011 May 2023, BOSTON
ICRA 2023: 29 May2 June 2023, LONDON
RoboCup 2023: 410 July 2023, BORDEAUX, FRANCE
RSS 2023: 1014 July 2023, DAEGU, KOREA
IEEE RO-MAN 2023: 2831 August 2023, BUSAN, KOREA
CLAWAR 2023: 24 October 2023, FLORIANOPOLIS, BRAZIL
Humanoids 2023: 1214 December 2023, AUSTIN, TEXAS, USA
Enjoy todays videos!
NASAs Ingenuity Mars Helicopter made history when it achieved the first powered, controlled flight on another planet on April 19, 2021. Since then, it has exceeded expectations and most recently executed its 50th flight on Mars. This video highlights Ingenuitys flights, captured by the Perseverance Rovers WATSON and Mastcam-Z cameras, as well as Ingenuitys color Return to Earth (RTE) camera and its black-and-white navigation camera.
50 flights is 45 flights more than this little helicopter was designed for, which is bonkers. It has exceeded the expected cumulative flight time by 1,250%, and the expected distance flown by 2,214%. Wow.
[ JPL ]
Georgia Tech researchers have recently created a soft rotary motor using liquid metal, compliant magnetic composites, and silicone polymers. The motor can be squished and squeezed in all directions, which can one day improve the compatibility between humans and robots and extend the capability of soft robots. This soft motor is orders of m...
01:59
NOW: Pensions Has NOTHING to Say About Lying to Clients schestowitz.com
Summary: The previous crimes of Sirius Open Source merit letters of assurance, which were already promised by three people at NOW: Pensions (including a manager); if no such letter can be provided, specify the reasons and explain why three people who work at NOW: Pensions made promises to two people (in vain, followed by more lies to cover up the original lies)
MANY people are speaking about pensions today. France is checking whether Macron did something unconstitutional by sentencing millions of people to two additional years of work in their 60s (not something they consented to in the past). However, the timing of this post is purely coincidental. Its a Friday and Ive not heard back for almost a week now from NOW: Pensions.
As a reminder, the company kept making contradictory promises (i.e. lies) or breaking promises, not honouring their own contracts, etc.
Heres the full chain of correspondence with few redactions (names of their workers, including managers):
> Roy Schestowitz wrote on 08/04/2023 04:32:
>> Complaints now pensions support wrote on 05/04/2023 15:03:
>>> I hope this helps to settle your concerns regarding your NOW Pension
>>> fund, as you can see from the above, they have outlined how and who
>>> is responsible for protecting your pension savings and applies to all
>>> NOW Pensions members.
>>
>> Hi,
>>
>> Please send the full letter, as promised, to
>> 1) my wife
>> 2) myself
>>
>> as promised by ????
>> as promised by ????
>> as promised by ?????
>>
>> several times since February. We need this obligation in writing.
>
> I need an update on this. There are multiple complainants about the
> pension fraud. We need action, not stalling tactics. You behave like
> lawyers, not like a pension provider.
If you do not reply by the end of today (Friday), prepare the cheque for my wife and I to pick up next week at your office.We are withdrawing all the money. You are a reckless, lying, untrustworthy company. You not only lied to me (3 different people, including managers) you also failed to reply to very simple E-mails about a dozen times.
Meanwhile the police and Action Fraud will be getting involved.
Well, its 5PM now on a Frid...
01:52
Pension Schemes Versus Pension Scams: The Curious Cases of the UKs Large Pension Providers (Not France) Techrights
Summary: The previous crimes of Sirius Open Source merit letters of assurance, which were already promised by three people at NOW: Pensions (including a manager); if no such letter can be provided, specify the reasons and explain why three people who work at NOW: Pensions made promises to two people (in vain, followed by more lies to cover up the original lies)
MANY people are speaking about pensions today. France is checking whether Macron did something unconstitutional by sentencing millions of people to two additional years of work in their 60s (not something they consented to in the past). However, the timing of this post is purely coincidental. Its a Friday and Ive not heard back for almost a week now from NOW: Pensions.
As a reminder, the company kept making contradictory promises (i.e. lies) or breaking promises, not honouring their own contracts, etc.
Heres the full chain of correspondence with few redactions (names of their workers, including managers):
> Roy Schestowitz wrote on 08/04/2023 04:32:
>> Complaints now pensions support wrote on 05/04/2023 15:03:
>>> I hope this helps to settle your concerns regarding your NOW Pension
>>> fund, as you can see from the above, they have outlined how and who
>>> is responsible for protecting your pension savings and applies to all
>>> NOW Pensions members.
>>
>> Hi,
>>
>> Please send the full letter, as promised, to
>> 1) my wife
>> 2) myself
>>
>> as promised by
>> as promised by
>> as promised by
>>
>> several times since February. We need this obligation in writing.
>
> I need an update on this. There are multiple complainants about the
> pension fraud. We need action, not stalling tactics. You behave like
> lawyers, not like a pension provider.
If you do not reply by the end of today (Friday), prepare the cheque for my wife and I to pick up next week at your office.We are withdrawing all the money. You are a reckless, lying, untrustworthy company. You not only lied to me (3 different people, including managers) you also failed to reply to very simple E-mails about a dozen times.
Meanwhile the police and Action Fraud will be getting involved.
Well, it&...
01:32
94% of The Universes Galaxies Are Permanently Beyond Our Reach Lifeboat News: The Blog

Today, most of the universes galaxies are already receding faster than the speed of light.
01:32
Will Quantum Computers Make Time Travel Possible? | Unveiled Lifeboat News: The Blog

Is time travel FINALLY possible?? Join us and find out!
Subscribe: https://wmojo.com/unveiled-subscribe.
In this video, Unveiled takes a closer look at 3 groundbreaking experiments in time travel and quantum computing! On an international scale, science is starting show how moving forward and back in time really COULD be possible all it will take is a little manipulation at the atomic and subatomic levels!
This is Unveiled, giving you incredible answers to extraordinary questions!
Find more amazing videos for your curiosity here:
6 Scientific Breakthroughs Predicted During Your Lifetime https://youtu.be/wGKj-3AfxdE
Are We the Creation of a Type V Civilization? https://youtu.be/T_u4lGDs3dM
0:00 Intro.
0:50 Is Time Travel Possible?
1:49 Quantum Time Travel Potential.
3:56 Experiment to Reverse Time.
6:30 Los Alamos Quantum Simulator / Butterfly Effect.
7:39 Time Crystals and Photons.
9:47 Conclusions.
01:31
CRISPR Breakthrough: Scientists Can Now Turn Genes On and Off at Whim Lifeboat News: The Blog
The gene-editing system CRISPR-Cas9 which has revolutionized genetic engineering over the past decade involves cutting DNA strands which is a process that can be quite hard to control and can result in unwanted genetic changes. Now, thanks to researchers at the Massachusetts Institute of Technology and the University of California, San Francisco (UCSF), a new gene-editing technology called CRISPRoff can change that, according to a press release.
Fast forward four years [from the initial grant], and CRISPRoff finally works as envisioned in a science fiction way, says co-senior author Luke Gilbert. Its exciting to see it work so well in practice.
01:30
An Early Look At Linux 6.4 Features: AMD CDX, AMD GAM, Intel LAM, Apple M2 & More Phoronix
There is two weeks to go until the Linux 6.3 stable kernel is released, which could drag out to three weeks if last minute issues come about in the kernel. But given all the material queuing via the many "-next" code branches, we already have a good idea for many of the features in store for Linux 6.4...
01:30
Low-Cost Display Saved By RP2040 Hackaday

Anyone looking for components for electronics projects, especially robotics, microcontrollers, and IoT devices, has likely heard of Waveshare. They are additionally well-known suppliers of low-cost displays with a wide range of resolutions, sizes, and capabilities, but as [Dmitry Grinberg] found, theyre not all winners. He thought the price on this 2.8-inch display might outweigh its poor design and lack of documentation, and documented his process of bringing it up to a much higher standard with a custom driver for it.
The display is a 320240 full-color LCD which also has a touchscreen function, but out-of-the-box only provides documentation for sending data to it manually. This makes it slow and, as [Dmitry] puts it, pure insanity. His ultimate solution after much poking and prodding was to bit-bang an SPI bus using GPIO on an RP2040 but even this wasnt as straightforward as it should have been because there are a bunch of other peripherals, like an SD card, which share the bus. Additionally, an interrupt is needed to handle the touchscreen since its default touch system is borderline useless as well, but after everything was neatly stitched together he has a much faster and more versatile driver for this display and is able to fully take advantage of its low price.
For anyo...
01:29
Network Neuroscience Theory Lifeboat News: The Blog
It was therefore shortly after the discovery of g that Spearmans contemporary, Godfrey Thomson, proposed that the general factor represents a global network phenomenon 11, 12, 13. Thomson held that g emerges from the interaction among the many elements of the brain, which he referred to as neural arcs or bonds 14, 15. According to Thomsons Sampling Theory of Mental Ability, each item on an achievement test samples a number of these bonds 11, 12, 13. He proposed that the degree of overlap among bonds accounted for the correlation between tests and the resulting positive manifold. Thus, Thomsons theory was the first to show that Spearmans discovery of the general factor of intelligence is consistent with a network perspective.
Thomsons legacy can be found in modern psychological theories which posit that g originates from the mutual interactions among cognitive processes [16]. Individual differences in g are known to be influenced, for example, by language abilities 10, 17, which facilitate a wealth of cognitive, social, and affective processes through mutual interactions (i.e., reciprocal causation) [18]. The central idea of the Mutualism Model is that change or growth in one aspect of mental ability is (i) partially autonomous (owing to developmental maturation), and is also (ii) based on growth in oth...
01:29
QuASeR: Quantum Accelerated de novo DNA sequence reconstruction Lifeboat News: The Blog
In this, we present QuASeR, a reference-free DNA sequence reconstruction implementation via de novo assembly on both gate-based and quantum annealing platforms. This is the first time this important application in bioinformatics is modeled using quantum computation. Each one of the four steps of the implementation (TSP, QUBO, Hamiltonians and QAOA) is explained with a proof-of-concept example to target both the genomics research community and quantum application developers in a self-contained manner. The implementation and results on executing the algorithm from a set of DNA reads to a reconstructed sequence, on a gate-based quantum simulator, the D-Wave quantum annealing simulator and hardware are detailed. We also highlight the limitations of current classical simulation and available quantum hardware systems. The implementation is open-source and can be found on https://github.com/QE-Lab/QuASeR.
Citation: Sarkar A, Al-Ars Z, Bertels K (2021) QuASeR: Quantum Accelerated de novo DNA sequence reconstruction. PLoS ONE 16: e0249850. https://doi.org/10.1371/journal.pone.
Editor: Archana Kamal, University of Massachusetts Lowell, UNITED STATES.
01:22
Scientists identify new benchmark for freezing point of water at 70 C Lifeboat News: The Blog
Scientists have discovered yet another amazing aspect of the weird and wonderful behavior of waterthis time when subjected to nanoscale confinement at sub-zero temperatures.
The finding that a crystalline substance can readily give up water at temperatures as low as 70 C, published in the journal Nature on April 12, has major implications for the development of materials designed to extract water from the atmosphere.
A team of supramolecular chemists at Stellenbosch University (SU), consisting of Dr. Alan Eaby, Prof. Catharine Esterhuysen and Prof. Len Barbour, made this discovery while trying to understand the peculiar behavior of a type of crystal that first piqued their interest about ten years ago.
01:22
The Meminductor: A New Circuit Element Lifeboat News: The Blog
Researchers at Texas A&M University have discovered a novel circuit element referred to as a meminductor that led to a significant breakthrough in circuit elements.
In an electrical circuit, circuit elements play a crucial role in managing the flow of electricity. The resistor, capacitor, and inductor are the traditional circuit elements, while the memristor and memcapacitor are the more recent additions discovered in the past 15 years. These newer components, known as mem- versions of the classical elements, have different voltage and current characteristics that are influenced by previous voltage or current values over time, giving them memory-like properties.
Dr. H. Rusty Harris, an Associate Professor at the Department of Electrical and Computer Engineering at Texas A&M University, has made a significant breakthrough in circuit elements with the discovery of a new component called the meminductor.
01:17
As Tax Day approaches, Microsoft warns accounting firms of targeted attacks Graham Cluley
Accountants are being warned to be on their guard from hackers, as cybercriminals exploit the rush to prepare tax returns for clients before the deadline of US Tax Day. Read more in my article on the Tripwire State of Security blog.
01:16
After the Accountant of Sirius Open Source Left Many Workers Were Secretly Robbed for Many Years schestowitz.com
Summary: The crimes of Sirius Open Source, or the company robbing me and my colleagues behind our backs, started the fraud weeks or months after the companys accountant had suddenly left (though maybe it predates this); instead a bunch of fraudsters took over, engaging in embezzlement that wasnt confirmed to us until this year (and only after long and persistent pursuits, as Standard Life was stalling and stonewalling for 3 months)
MY articles from December already quite extensively covered the dodgy accounting at Sirius. Ive heard references to such conduct (sophisticated or smooth criminals), coming from people who were long involved in the company. This is a company that pretends its address is in fact the address of an accountant or accounting firm. The CEO who fled the company (scene of the crime) last month had done the same with his own company. These arent people of integrity, theyre immoral imposters who barely ever use Free software (they (mis)use the brand Open Source mostly for marketing and recruitment).
As noted here back in December, the company had been violating the law for years by not sending payslips, rarely sending them, or only sending some after a lot of nagging/reminders.
Who was doing the accounting anyway? One theory is that the company was passing the data to some external (the above-mentioned) people to sign off, without actually auditing or verifying anything. That might explain them failing to check that for many employees the money wasnt at all being sent to pensions as specified in over 60 payslips (per employee). Serious failure! This went on for over half a decade. This was definitely not an accident, hence the scare quotes around the word failure.
In the E-mails below (redacted for privacy) one can see the allusion to the manager explaining the accounting, rather than actual accountants doing the accounting, dealing with accounts. The messages were sent to and by a notoriously reckless, lazy employee (with almost zero technical skills) who forgot to arrange for coverage (colleagues were left alone at night!). Many such blunders happened without her facing consequences. There were good reasons for this person being strongly loathed among many staff. Theres the lying about looking for cover, th...
01:11
[Meme] The Smooth Criminals Techrights

Summary: Standard Life does not seem to care that in its own name, piggybacking its reputation, fraud was being committed against a lot of people, notably GNU/Linux specialists and programmers in the UK
00:58
Accounting at Sirius Open Source Was Always Extremely Dodgy Techrights
Summary: The crimes of Sirius Open Source, or the company robbing me and my colleagues behind our backs, started the fraud weeks or months after the companys accountant had suddenly left (though maybe it predates this); instead a bunch of fraudsters took over, engaging in embezzlement that wasnt confirmed to us until this year (and only after long and persistent pursuits, as Standard Life was stalling and stonewalling for 3 months)
MY articles from December already quite extensively covered the dodgy accounting at Sirius. Ive heard references to such conduct (sophisticated or smooth criminals), coming from people who were long involved in the company. This is a company that pretends its address is in fact the address of an accountant or accounting firm. The CEO who fled the company (scene of the crime) last month had done the same with his own company. These arent people of integrity, theyre immoral imposters who barely ever use Free software (they (mis)use the brand Open Source mostly for marketing and recruitment).
These arent people of integrity, theyre immoral imposters who barely ever use Free software (they (mis)use the brand Open Source mostly for marketing and recruitment).As noted here back in December, the company had been violating the law for years by not sending payslips, rarely sending them, or only sending some after a lot of nagging/reminders.
Who was doing the accounting anyway? One theory is that the company was passing the data to some external (the above-mentioned) people to sign off, without actually auditing or verifying anything. That might explain them failing to check that for many employees the money wasnt at all being sent to pensions as specified in over 60 payslips (per employee). Serious failure! This went on for over half...
00:58
Nayib Bukele, President of El Salvador, on Tucker Carlson cryptogon.com
Highly recommended. Interview with @TuckerCarlson pic.twitter.com/wZ1SWK85QH Nayib Bukele (@nayibbukele) March 5, 2023 Research Credit: NH
00:51
Kodi discloses data breach after its forum was compromised Security Affairs
Open-source media player software provider Kodi discloses a data breach after threat actors stole its MyBB forum database.
Kodi has disclosed a data breach, threat actors have stolen the companys MyBB forum database that contained data for over 400K users and private messages.
The threat actors also attempted to sell the stolen data on the BreachForums cybercrime forum that was recently shut down by law enforcement.
In the last 24 hours we became aware of a dump of the Kodi user forum (MyBB) software being advertised for sale on internet forums. This post confirms that a breach has taken place. reads the advisory published by Kodi. MyBB admin logs show the account of a trusted but currently inactive member of the forum admin team was used to access the web-based MyBB admin console twice: on 16 February and again on 21 February. The account was used to create database backups which were then downloaded and deleted. It also downloaded existing nightly full-backups of the database. The account owner has confirmed they did not access the admin console to perform these actions.

The admin team locked out the intruders by disabling the account used in the data breach and conducted an initial review of part of the infrastructure that was accessed by the attackers
The threat actors then abused the account to create database backups that were then downloaded and deleted.
The threat actor was able to access the nightly backups containing all public forum posts, team forum posts, messages sent through the user-to-user messaging system, and user information such as forum username, email address used for notifications, and an encrypted (hashed and salted) password generated by the MyBB software.
The company pointed out that although MyBB stores passwords in an encrypted format they assumed all passwords are compromised. However, the company added that it has no evidence threat actors obtained unauthorize...
00:42
French Court Smacks Remote Learning Software Company for Pervasive Surveillance of Students SoylentNews
A worldwide pandemic trapped students in their own homes to stop the spread of the coronavirus. They didn't ask for this. Neither did educators. But educators made the worst of it in far too many cases.
Aptitude tests and other essentials for continued funding (and bragging rights) were now out of their control. Any student sitting at home had access to a wealth of knowledge to buttress what they may have actually retained from remote instruction.
Leveling the playing field was the goal. In practice, that meant turning the most sacrosanct of private places students' homes and bedrooms into heavily surveilled spaces... all in the interest of preventing cheating.
Laptop cameras monitored rooms and students' movements during testing. Internet connections often contributed more to passing grades than students' knowledge as educators (and their preferred tech partners) viewed inconsistent or dropped connections as indicators of attempted cheating. Malware deliberately installed by schools monitored internet usage before, during, and after tests.
A bedroom is not a classroom, even if that's where the educating is taking place temporarily due to pandemic restrictions. But that's how it was perceived and a bunch of opportunistic spyware purveyors rushed to fill the perceived "fairness" void with surveillance software that even the most inveterate stalker might consider too invasive.
Proctorio was on the forefront of this education-adjacent bedroom surveillance. It was particularly enthusiastic about stripping students of their privacy. When it was criticized for going too far, it went further, issuing legal threats and...
00:31
HIP 99770 b: Astrometry Bags a Directly Imaged Planet Centauri Dreams Imagining and Planning Interstellar Exploration
It took a combination of astrometry and direct imaging to nail down exoplanet HIP 99770 b in Cygnus, and thats a tale that transcends the addition of a new gas giant to our planetary catalogs. Astrometry measures the exact position and motion of stars on the sky, so that we are able to see the influence of an as yet unseen planet. In this work, astrometrical data from both the ESA Gaia mission and the earlier Hipparcos mission flag a world that is directly imaged by the Subaru Telescope extreme adaptive optics system, which enabled its near-infrared CHARIS spectrograph to see the target.
Supporting work at the Keck Observatory using its Near-Infrared Camera and Keck II adaptive optics system allowed in combination with the CHARIS spectrum the discovery of the presence of water and carbon monoxide in the atmosphere, while the temperature was shown to be about ten times hotter than that of Jupiter. The joint measurements revealed a planet some 14-16 times the mass of Jupiter, in a 16.9 AU orbit around a star with twice the Suns mass and 13.9 times its luminosity.
Thayne Currie (Subaru Telescope) is lead author of the study:
Performing both direct imaging and astrometry allows us to gain a full understanding of an exoplanet for the first time: measure its atmosphere, weigh it, and track its orbit all at once. This new approach for finding planets prefigures the way we will someday identify and characterize an Earth-twin around a nearby star.

Image: Infrared image of HIP 99770 taken by the Subaru Telescope. The bright host star at the position marked with * is masked. The dashed ellipse shows the size of Jupiters orbit around the Sun for scale. The arrow points to the discovered extrasolar planet HIP 99770 b. Credit: T. Currie/Subaru Telescope, UTSA.
Weve retrieved direct images of gas giants before, including massive planets around HR8799, the first such worlds detected with the method, relying on advances in adaptive optics systems for ground-based telescopes. But without astrometrical data, astronomers selected targets based on properties like age and distance, producing a small harvest of exoplanets. In this work,...
00:27
Why You Cant Miss This Years Open Source Summit North America, May 10-12 in Vancouver, Canada Linux.com
read the original post at Read More
The post Why You Cant Miss This Years Open Source Summit North America, May 10-12 in Vancouver, Canada appeared first on Linux.com.
00:09
Security updates for Friday LWN.net
Security updates have been issued by Debian (haproxy and openvswitch), Fedora (bzip3, libyang, mingw-glib2, thunderbird, xorg-x11-server, and xorg-x11-server-Xwayland), and Ubuntu (apport, ghostscript, linux-bluefield, node-thenify, and python-flask-cors).
00:00
This Week in Security: QueueJumper, JS VM2 Escape, and CAN Hacking Hackaday

You may not be familiar with the Microsoft Message Queuing (MSMQ) service, a store and forward sort of inter-process and inter-system communication service. MSMQ has become something of a legacy product, but is still available as an optional component in Windows. And in addition to other enterprise software solutions, Microsoft Exchange turns the service on by default. Thats why its a bit spooky that theres a one packet Remote Code Execution (RCE) vulnerability that was just patched in the service.
CVE-2023-21554, also known as QueueJumper, is this unauthenticated RCE with a CVSS score of 9.8. It requires sending a packet to the service on TCP port 1801. The Check Point Research team scanned for listening MSMQ endpoints on the public Internet, and found approximately 360,000 of them. And no doubt far more are listening on internal networks. A one packet exploit is a prime example of a wormable problem, and now that the story has broken, and the patch is available, expect a rapid reverse engineering. Beware, the queue jumpers are coming.
JavaScript VM Escape
The VM2 library is a rather important JavaScript package that sandboxes code, letting a project run untrusted code securely. Or, thats the idea. CVE-2023-...
Friday, 14 April
23:01
How to get started with Ansible Private Automation Hub Linux.com
Learn how to use Red Hat Ansible Automation Private Automation Hub.
Read More at Enable Sysadmin
The post How to get started with Ansible Private Automation Hub appeared first on Linux.com.
23:00
Mesa OpenGL Threading Now Disabled For Small Hybrid CPUs Phoronix
Landing today in Mesa 23.2-devel is support for big.LITTLE CPU detection or more broadly hybrid CPU core detection where little cores (e.g. E cores) are defined as having less than 50% the capacity of the largest CPU core on the system. This is done since Mesa's OpenGL threading is now being disabled for small hybrid processors...
22:57
Russia-Linked Hackers Launches Espionage Attacks on Foreign Diplomatic Entities The Hacker News
The Russia-linked APT29 (aka Cozy Bear) threat actor has been attributed to an ongoing cyber espionage campaign targeting foreign ministries and diplomatic entities located in NATO member states, the European Union, and Africa. According to Poland's Military Counterintelligence Service and the CERT Polska team, the observed activity shares tactical overlaps with a cluster tracked by Microsoft as
22:35
WhatsApp announces features to prevent account takeover Help Net Security
WhatsApp will be rolling out three new security features in the coming months, to provide users with increased privacy and control over their messages and to help prevent unauthorized account access and takeover. The new features The first feature is called Account Protect and will help prevent unauthorized transfers of accounts from one device to another. This feature will require users to verify on their old device any attempts to switch to a new device. More
The post WhatsApp announces features to prevent account takeover appeared first on Help Net Security.
22:00
OpenCL Shared Virtual Memory Comes To Mesa's Rusticl Driver Phoronix
Mesa 23.1 enables RadeonSI Rusticl support while for next quarter's Mesa 23.2, which just started development, there is already a big ticket item for Rusticl: Shared Virtual Memory (SVM) support...
21:54
Meet PassGAN, the Supposedly Terrifying AI Password Cracker That's Mostly Hype SoylentNews
As the title suggests, they weren't all that impressed.
From the article:
As with so many things involving AI, the claims are served with a generous portion of smoke and mirrors. PassGAN, as the tool is dubbed, performs no better than more conventional cracking methods. In short, anything PassGAN can do, these more tried and true tools do as well or better. And like so many of the non-AI password checkers Ars has criticized in the paste.g., here, here, and herethe researchers behind PassGAN draw password advice from their experiment that undermines real security.
PassGAN is a shortened combination of the words "Password" and "generative adversarial networks." PassGAN is an approach that debuted in 2017. It uses machine learning algorithms running on a neural network in place of conventional methods devised by humans. These GANs generate password guesses after autonomously learning the distribution of passwords by processing the spoils of previous real-world breaches. These guesses are used in offline attacks made possible when a database of password hashes leaks as a result of a security breach.
Conventional password guessing uses lists of words numbering in the billions taken from previous breaches. Popular password-cracking applications like Hashcat and John the Ripper then apply "mangling rules" to these lists to enable variations on the fly.
[...] PassGAN uses none of these methods. Instead, it creates a neural network, a type of data structure loosely inspired by networks of biological neurons. This neural network attempts to train machines to interpret and analyze data in a way that's similar to how a human mind would. These networks are organized in layers, with inputs from one layer connected to outputs from the next layer.
PassGAN was an exciting experiment that helped usher in the use of AI-based password candidate generators, but its time in the sun has come and gone, password-cracking expert and Senior Principal Engineer at Yahoo...
21:25
China to launch Chinese Super Masons robot to build lunar bases with moon soil by 2028 Lifeboat News: The Blog
The robot tasked with making bricks out of lunar soil will be launched during Chinas Change-8 mission around 2028.
With Artemis II set to launch on November 24, it is no surprise that science journals are buzzing with research on lunar regolith, building bases on the moon, and working with moon soil to grow plants you get the drift.
A recent study in the journal Communications Biology described an experiment in which the moon soil samples collected during the Apollo missions were used to grow plants. And for the first time, an Earth plant, Arabidopsis thaliana, commonly called thale cress, grew and thrived in the lunar soil samples during the experiment.
21:25
NASAs snake-like robot concept could search for life on Saturns moon Lifeboat News: The Blog
This one-of-a-kind robot is an exobiology extant life surveyor (EELS) developed by NASAs Jet Propulsion Laboratory.
It is time to move over the traditional wheeled or legged robots. NASA has developed a robotic concept that sounds straight out of a science-fiction and has the potential to take space exploration to the next level.
The US space agency has been working on sending a snake-like robot to explore and search for extraterrestrial life forms in the solar system. This robot is an exobiology extant life surveyor (EELS) developed by NASAs Jet Propulsion Laboratory.
The snake-like robots capabilities.
NASA/JPL-CalTech.
Scientists have been working on sending a snake-like robot to explore and search for extraterrestrial life forms in the solar system. This robot is an exobiology extant life surveyor (EELS) developed by NASAs Jet Propulsion Laboratory (JPL).
21:25
Developer creates regenerative AI program that fixes bugs on the fly Lifeboat News: The Blog
Debugging a faulty program can be frustrating, so why not let AI do it for you? Thats what a developer that goes by BioBootloader did by creating Wolverine, a program that can give Python programs regenerative healing abilities, reports Hackaday. (Yep, just like the Marvel superhero.)
GPT-4 is a multimodal AI language model created by OpenAI and released in March, available to ChatGPT Plus subscribers and in API form to beta testers. It uses its knowledge about billions of documents, books, and websites scraped from the web to perform text-processing tasks such as composition, language translation, and programming.
21:00
Self-Cleaning Tech Could Help Solar Panels Keep Efficiency Up Hackaday

Solar panels are a special kind of magic turning light into useful electrical energy. However, they dont work nearly as well when theyre covered in dust, dirt, and grime. Conventional solutions involve spraying panels down with pure water, which is expensive and wasteful, or dry scrubbing, which can cause efficiency loss through scratching the panels. However, innovative new methods may offer useful solutions in this area, as shared by EETimes.
Researchers at MIT have explored the use of electrostatic methods to remove dust from solar panels. By creating a sufficiently strong electrostatic field, dust particles can be compelled to leap off of solar panels. The cleaning method requires no water and is entirely non-contact. It uses a motor system to pass a charged electrode past the surface of the panels, with the opposite ch...
20:46
AMD SFH Linux Driver Adding Ambient Color Sensor Support Phoronix
AMD's Sensor Fusion Hub (SFH) driver with the upcoming Linux 6.4 cycle is being extended to support new Ambient Color Sensor "ACS" functionality...
20:33
RTM Locker, a new RaaS gains notorieties in the threat landscape Security Affairs
Cybersecurity firm Trellix analyzed the activity of an emerging cybercriminal group called Read The Manual RTM Locker.
Researchers from cybersecurity firm Trellix have detailed the tactics, techniques, and procedures of an emerging cybercriminal gang called Read The Manual RTM Locker. The group provides a ransomware-as-a-service (RaaS) and provides its malicious code to a network of affiliates by imposing strict rules.
The group aims at flying below the radar, and like other groups, doesnt target systems in the CIS region.
The business-like set up of the group, where affiliates are required to remain active or notify the gang of their leave, shows the organizational maturity of the group, as has also been observed in other groups, such as Conti. reads the analysis of the gang. The gangs modus operandi is focused on a single goal: to fly below the radar. Their goal is not to make headlines, but rather to make money while remaining unknown. The groups notifications are posted in Russian and English, where the former is of better quality. Based on that, it isnt surprising that the Commonwealth of Independent States in Eastern Europe and Asia (CIS) region is off-limits, ensuring no victims are made in that area.
The group also avoids targeting morgues, hospitals, COVID-19 vaccine-related organizations, critical infrastructure, law enforcement, and other prominent companies to attract as little attention as possible.
The affiliates are obliged to remain active, or their account will be removed after 10 days without notifying them upfront.
The gangs affiliates must keep the RTM Locker malware builds priv...
20:27
Music Ive bought in March.
This post is way late (I know, I know) because I went to the Big Ears music festival in Knoxville, Tennessee. (And then got sick on the way home, but thats a different story. Viruses!!!) Big Ears was great Knoxville is just about the perfect size for a hipster music festival. Lots of nice venues quite close to each other, so everything is easy to stroll and theres no stress. Well, except the inevitable stress of several bands you want to see playing at once and then having to make a decision It was oddly apolitical, though, with regards to the fucked up stuff happening in Tennessee now I think I heard only a single act make even a reference to anything from the stage: Haela Hunt-Hendrix took a tiny break from the Liturgy set to point out that it probably wouldnt have been legal for her to be on stage in Tennessee two days later. (To which the entire audience responded immediately with FUCK BILL LEE, which was heartening to hear)
Anyway, March:
 |
:+Look+At+The+Moon!+(live+Phoenix+Festival+97)+(2)) |
 |
... |
20:26
Fedora 38 Being Released Next Tuesday Phoronix
The much anticipated Fedora 38 is cleared for releasing on Tuesday. There are no delays with the Fedora 38 cycle and in fact hitting their "early target date" for shipping on 18 April...
20:22
Kodi Confirms Data Breach: 400K User Records and Private Messages Stolen The Hacker News
Open source media player software provider Kodi has confirmed a data breach after threat actors stole the company's MyBB forum database containing user data and private messages. What's more, the unknown threat actors attempted to sell the data dump comprising 400,635 Kodi users on the now-defunct BreachForums cybercrime marketplace. "MyBB admin logs show the account of a trusted but currently
19:11
How AI is Helping Historians Better Understand Our Past SoylentNews
The historians of tomorrow are using computer science to analyze how people lived centuries ago:
It's an evening in 1531, in the city of Venice. In a printer's workshop, an apprentice labors over the layout of a page that's destined for an astronomy textbooka dense line of type and a woodblock illustration of a cherubic head observing shapes moving through the cosmos, representing a lunar eclipse.
[...] Five hundred years later, the production of information is a different beast entirely: terabytes of images, video, and text in torrents of digital data that circulate almost instantly and have to be analyzed nearly as quickly, allowingand requiringthe training of machine-learning models to sort through the flow. This shift in the production of information has implications for the future of everything from art creation to drug development.
But those advances are also making it possible to look differently at data from the past. Historians have started using machine learningdeep neural networks in particularto examine historical documents, including astronomical tables like those produced in Venice and other early modern cities, smudged by centuries spent in mildewed archives or distorted by the slip of a printer's hand.
Historians say the application of modern computer science to the distant past helps draw connections across a broader swath of the historical record than would otherwise be possible, correcting distortions that come from analyzing history one document at a time. But it introduces distortions of its own, including the risk that machine learning will slip bias or outright falsifications into the historical record. All this adds up to a question for historians and others who, it's often argued, understand the present by examining history: With machines set to play a greater role in the future, how much should we cede to them of the past?
Read more of this story at SoylentNews.
19:10
888 On Line Casino Evaluate 2023 Get $88 No Deposit In India h+ Media
888 On Line Casino Evaluate 2023 Get $88 No Deposit In India
Enter all the required data, including your e mail handle, country, most well-liked billing foreign money, and password. To entry your account on the original website, click on the Sign in 4RaBet button in the top-right corner of the web page. Type in your e mail and password and click on on Sign in once more. In case you forgot the password or login, 4ra Bet has the Recover a password option. After youve completed the registration process at 4raBet, confirm your account with a hyperlink in your e-mail or SMS.
VSG or Vikram Singh Gandhi is a cricket tipper, commonly often identified as Dada. After clicking on which you have to enter your quantity and click on on on Withdraw choice to withdraw money. You need to substantiate your e-mail or cellphone quantity through a link despatched to your e-mail handle or SMS. The bookie additionally could require proof of your identity, fee info, and address by offering a duplicate of your ID document, a utility bill, and a photograph of your bank card.
888casino is a kind of on-line gambling institutions which are lifeless serious about the security and safety of gamblers. Yeah, thats how one can primarily reach the customer assist team at 888casino. Send them a mail at , and they will revert within hours. You could even place particular bets on who wins the US presidential elections or receives an Academy award!
It is the most challenging betting option because the consumer simultaneously implies a forecast and probabilities on a quantity of outcomes. It isnt really helpful to cooperate with suspicious unlicensed websites, as theres a high probability of fraud. The 4rabet verification procedure takes from 24 to 72 hours. If the profile verification is refused, the website administration blocks the account, taking the replenished deposit or winnings within the companys favor. At this stage, you must select the sum of money you wish to spend on bets by way of the most effective betting app.
888sport, a member of ESSA, the European betting integrity body, is a trusted bookmaker. Under the 888 Group, a sportsbook is on the market as 888sport. However, this is the companys dedicated sports arm, which is not part of the 888casino web site. So, the casinos portfolio now features a live game for each temper.
You can benefit from the 888 video games in instant-play mode or download the software. All merchandise embody Random Number Generator techniques, which assure fairness across the complete platform. Also, the software program providers ensure high-end safety methods, which assure a protected and safe playing setting for Indian customers.
If youve the time to go looking through 888s assist and FAQ pages, youll probably discover your query already answered. However, web sites similar to Betfair and Royal Panda have live chat companies which might be extra r...
19:08
Jitu77 > Daftar Situs Judi Slot On-line Gacor, Pragmatic Play Terbaik, Slot88 Terpercaya h+ Media
Jitu77 > Daftar Situs Judi Slot On-line Gacor, Pragmatic Play Terbaik, Slot88 Terpercaya
Discover all obtainable promotions in addition to their phrases & conditions from the Bonuses and Offers web page. You do not want to supply the complete listing of documents, simply choose one. For the verification process, only the named list of paperwork is required. Then you have to show your ID so as to be recognized and to maintain your account safe. The final stage of the method has a maximum time restrict of 10 minutes. It additionally blocks the creation of other transactions while Crickex checks the cost.
888 Casino is undoubtedly one of many earliest online casinos. Precisely, the casino has been within the trade since 1997. Since its launch, the casino has received several world rewards, including the 2019 and 2021 EGR Awards and 2020 Gaming Intelligence Awards. Overall, with tons of of online slot video games and top-rated casino software program, youre certain to search out something that tickles your fancy.
Here in sattmatka.org, you may also compare earlier outcomes with the current result charts. So if you want to take pleasure in your recreation, just bookmark our site to have the ability to use our website on regular bases. We do not depend on guessing, we explore the accurate outcomes based on our data and on the bases of obtainable old online charts records! Our major objective is to supply the proper steerage to our customers about the method to play and tips on how to make good moves which in the end leads in the course of victory. Also, we provide free tips and charts for the verification of outcomes. A one who wins an excellent amount of money from gambling is taken into account as Satta king.
Its really easy to use and its helped me save plenty of effort and time counting cash. Luck is changeable, it is inconceivable to foretell events appropriately on an everyday basis. Gambling issues can affect household relations and job duties.
Indian players get pleasure from an exhilarating wagering expertise every time they gamble on the titles provided by the platform. Unlock huge bonuses and land huge wins on your favorite slots or desk titles. At this 888 Live Casino, youll discover a huge selection of live on line casino video games.
The odds are updated, and the interface is comparatively simple to navigate. Moreover, you should have entry to quick cashouts via a plethora of globally famend and localized cost methods. To know extra about the platform, keep studying on our 888 Casino Review the place we are going to cowl everything you should know about the casino platform. Go to the appropriate section of the official website and obtain the application to your cellular device or different gadget. After that, all that continues to be is to run the installation file and wait for the application to start. You need to install the Casino 888 software, log in or create an account.
No...
19:05
Scr 888 Casinoguge3 Comscr 888 Casino8gs4xy3yscr 888 Casinolwmfoktiscr 888 Casinoguge3comscr 888 Casinol93394ykscr 888 On Line Casinos Bulk And Block Deals h+ Media
Scr 888 Casino guge3
Com
guge3
Com scr 888
Casino8gs4xy3yscr 888 Casinolwmfoktiscr 888 Casino
scr 888
Casino8gs4xy3yscr 888 Casinolwmfoktiscr 888 Casino guge3com
guge3com scr 888
Casinol93394ykscr 888 On Line Casinos Bulk And Block Deals
scr 888
Casinol93394ykscr 888 On Line Casinos Bulk And Block Deals
In total, this bundle seeks to award gamers with a bonus amount of as much as $1500. Their cell casino, extremely optimised thanks to HTML5, offers an excellent platform for betting on the transfer and it additionally provides a number of ways to enjoy the merchandise. And furthermore, there are apps for Android and Apple devices. The wordsmith of the group, Shruti is busy enjoying her newfound ardour for online on line casino games. When shes pleased, she would bet the ranch to plan and create killer on line casino content the ones that urge you to play. If things dont go the way in which she desires them to, she would constantly act like the world is about to finish.
You dont have to download or install anything to play, and all you should do is head to the internet site. You will then web playing web site. One of the first issues that youll notice when taking part in at 888 India, is an easy and easy-to-navigate web site.
Therefore, along with civil interaction, we expect commenters to offer their opinions succinctly and thoughtfully, but not so repeatedly that others are aggravated or offended. If we obtain complaints about individuals who take over a thread or discussion board, we reserve the right to ban them from the positioning, with out recourse. INDIBET is the most effective website for anybody in search of aggressive odds.
888 Starz has plenty of tempting bonuses and promotions to welcome new gamers and provide great leisure for regular clients. The bonus part offers a variety of gifts similar to free bets, bonus spins, play cash and cashback to swimsuit completely different betting types. To stay as a lot as its popularity as an all-inclusive platform, 888 Casino makes it attainable for gamers to fund and withdraw from their accounts utilizing a myriad of ways.
The companys providers in the United Kingdom are operated by 888 UK Limited, integrated in Gibraltar, and licensed and controlled by the Great Britain Gambling Commission. The Acts passing had opened a leeway to growing legal online casinos, and the brother-partners conveniently seized that opportunity. In May 2007, Casino-on-Net, the companys first web site, was...
19:03
Search Outcomes For pocket Sport Developer Apk Openak319com 888 On Line Casino Login 1xbet Withdraw Disadvantage Openak319com$$limitadong Regalo!mag Register Para Makakuha Ng P50 May 50% Cashback Sayong Unang Deposit!$$c2 h+ Media
Search Outcomes For pocket Sport Developer Apk Openak319com 888 On Line Casino Login 1xbet Withdraw Disadvantage Openak319com$$limitadong Regalo!mag Register Para Makakuha Ng P50 May 50% Cashback Sayong Unang Deposit!$$c2
If you are a beginner within the betting sphere, take a look at one of the best Indian betting apps which will be nice so that you can use as a end result of their easy interface and navigation. Given numerous bookmakers in the marketplace, it isnt simple to choose on an indeed secure and reliable cell app. The bonus will be credited to the customers account mechanically after the first deposit is made, unless the field I are not wanting for any bonuses is ticked. Only gamers that are new to Parimatch can qualify for this promotion. Been writing sports activities information for a couple of years and now developing my own sports activities and betting website with honest and skilled critiques.
There are about 30 progressive slot games on the 888 on line casino platform. That is, with a bit of stake, you could be fortunate to be a winner of a large amount of cash. Mind you, the progressive slot enhance in potential payout as players and betting will increase. A simplified and easy-to-use platform plus good graphics are notable options of the positioning. In addition, it has a vast game base that units gamers up for an explosive ride when exploring the games. Notable software builders across the globe provide some of the video games within the casino.
However, this can be longer depending on whether any malicious activity is suspected. In-house casino gaming offers a sure thrill that virtually all players find addictive. 888 Casino brings this thrill to all gamers from the comfort of their properties or when chilling on a park bench. The website has an interactive live dealer part that packs all the superb qualities of an in-house casino blended with know-how to end in a high-quality video stream. 888 Casino was among the many first gaming providers on-line to have this section put up on their web site. In the preceding years, the operator has been a mannequin for a lot of others in the trade that adopted suit.
The present-day 888.com proudly carries the Safe and Fair Assurance seal from eCOGRA. In 2010, Casino-on-Net was rebranded as 888casino to unite it with the opposite 888 brands. In 2013, in a historic moment, this on-line casino turned the primary to be exclusively licensed within the United States under the Nevada Gaming Commission.
Access games, deposit/withdrawal options, buyer help, and other features from the app. It works around the clock and has qualified help for gamers utilizing a chat within the app. I was pleased to find a big variety of online on line casino games at 888 of the completely different segments. The slot video games are a couple of hundred; even when its not as much as found in different portal...
19:02
Baccarat App With Dragon Bonus Gcash Card, g188 Phbaccarat App With Dragon Bonus Gcash Card, h+ Media
Baccarat App With Dragon Bonus Gcash Card, g188 Ph baccarat
App With Dragon Bonus Gcash Card,
baccarat
App With Dragon Bonus Gcash Card,
Theyre known as the Macau, on line casino windsor poker 1xbet apk yukle which absolves the government of accountability. We all want we knew extra, serves solely the pursuits of the betting business on the expense of playing addicts and our high streets. For instance, you will need to start repaying your student loans. Third, but then I understood that it was the moment that I wont ever ever neglect.
For a clearer perspective of whats legit and whatnot, please examine our detailed article on the legality of online playing in India. Enjoy three excitingvideo poker games solely at 888casino. The mini list contains Jacks or Better, Joker Wild Double Up, and Deuces Wild Double Up.
Plus, take pleasure in extra versatility when making bets from singles up to express combinations! Everything is presented in European decimal format so its simple to understand too. We even have a brilliant on-line casino with dozens of slots and desk games. You can change between betting and gambling sections easily with a couple of keystrokes.
Ayman additionally reviews, publishes and continuously improves the content on this website. If you experience this, you must check in case you have two accounts. If the fund just isnt in your second account, ship an e-mail to the on line casino displaying proof of cost. Moreover, the on line casino helps a spread of languages, therefore eliminating the language barrier.
After downloading, you should install the appliance and enter the info from your account. Business Lend is a platform which brings executives officers, entrepreneurs, and enterprise capitalist collectively from totally different sectors. We carry on connecting with our users with the help of our monthly edition carving our method slowly in course of the highest readership.
The online on line casino will add 50% of the value of your first deposit to your account, which means that you could begin taking part in with $1,500 if you deposit $1,000 . Theyll do the same once more in your second deposit if you enter the promo code WELCOME888. The most whole welcome bonus over each deposits is capped at $2,000 . How lengthy it takes to withdraw your winnings is dependent upon your preferred payment sort and your membership standing.
Based on these 5 deposits, youre going to get a total of $1500. Through complete testing and evaluation, only one weak spot and a quantity of sturdy factors have been recognized for 888 casino. 888 Casino acquired a license as an Interactive Gaming Service Provider from Nevada Gaming Commission in March 2013. In 2015, this casino was declared as the only truly pan-Euro...
18:28
Korean Piracy Giant Noonoo TV Shuts Down Citing Bandwidth Costs & Pressure TorrentFreak
 Smash hit movies and TV shows such as Parasite and Squid
Game, coupled with the unprecedented success of boy band BTS, have
helped to cement South Korea as a major player on the global
entertainment map.
Smash hit movies and TV shows such as Parasite and Squid
Game, coupled with the unprecedented success of boy band BTS, have
helped to cement South Korea as a major player on the global
entertainment map.
Success for Korean entertainment companies carries the same pros and cons as it does for those in the West. More exposure, more sales, greater opportunities and, somewhat inevitably, more piracy.
That led to an announcement last month that broadcasters, including KBS, MBC and JTBC, the Korea Film and Video Copyright Association (film producers and distributors), plus streaming platforms TVING and Wavve, were forming a coalition to fight piracy. These companies took on board the stronger together philosophy of the global anti-piracy coalition ACE, and reports suggested that ACE itself would also be a part of the Korean program.
Noonoo TV in the Spotlight
The Korean anti-piracy coalitions first public target was revealed at the same time. With tens of millions of visitors per month, movie and TV show streaming giant Noonoo TV was a fairly predictable target.
Blamed for racking up 1.5 billion views of pirated movies and TV shows and allegedly causing billions of dollars worth of losses to legitimate platforms, aggressive site-blocking measures had failed to dull the sites popularity.
After regularly obtaining circumvention domains in a sequence that began with noonoo1.tv and progressed to noonoo2.tv and beyond, when we reported on the site last month noonoo32.tv was the height of fashion.
At the time of writing, noonoo46.tv is responsible for circumventing ISP blockades, but a message placed on the site this morning also suggests it could be the last domain the site will ever need.
Studiouniversal Calls it Quits
Hello, this is the Studiouniversal team, the announcement begins. It is with a heavy heart that we deliver unfortunate news to everyone who has used Noonoo up until now.
Since the official launch of the service in June 2021, we have been able to stay together with the love of many peopl...
18:24
IRC Proceedings: Thursday, April 13, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-130423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-130423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-130423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-130423.gmi
Over HTTP:
|
... |
18:14
Links 14/04/2023: More Twitter Losses and H-1B Exploitation Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Desktop/Laptop
-
OMG! Linux First RISC-V Tablet is For Hardcore Enthusiasts Only
...
-
-
18:11
Optimizing Cancellations catonmat.net
At Browserling and Online Tools, we collected statistics from users who cancel their subscriptions and found that 15% of users change their mind within a day after canceling a subscription.
We acted on this data and added a feature that lets our users restore a subscription that they just canceled with a single click.
Here's how it works.
A single click to cancel a subscription:
And once a subscription has been canceled, it can be restored with a single click as well:
Make it easy to cancel and uncancel subscriptions for your users as well and see you next time!
18:09
Zelle users targeted with social engineering tricks Help Net Security
Cybercriminals have been leveraging social engineering techniques to impersonate the popular US-based digital payments network Zelle and steal money from unsuspecting victims, according to Avanan. The fake Zelle email (Source: Avanan) The phishing email The spoofed email is cleverly crafted to look as legitimate as possible: it contains the Zelle logo, grammatically correct text, and an authentic link to the firms web page at the bottom of the email, in the security and privacy footer. More
The post Zelle users targeted with social engineering tricks appeared first on Help Net Security.
18:00
Its Opposite Day For This Novel Wankel Engine Hackaday

The Wankel engine seems to pop up in surprising places every so often, only to disappear into the ether before someone ultimately resurrects it for a new application and swears to get it right this time. Ultimately they come across the same problems that other Wankels suffered from, namely poor fuel efficiency and issues with reliability. They do have a surprising power-to-weight ratio and a low parts count, though, which is why people keep returning to this well, although this time it seems like most of the problems might have been solved simply by turning the entire design inside out.
A traditional Wankel engine has a triangular-shaped rotor that rotates around a central shaft inside an oval-shaped housing. This creates three chambers which continually revolve around inside the engine as the rotor spins. The seals that separate the chambers are notoriously difficult to lubricate and maintain. Instead of using a rotor inside of a chamber, this design called the X-Engine essentially uses a chamber inside of a rotor, meaning that the combustion chamber and the seals stay in fixed locations instead of spinning around. This allows for much better lubrication of the engine and also much higher efficiency. By flipping the design on its head it is able to maintain a low moving parts count, high compression ratio, and small power-to-weight r...
17:58
Read issue #250 of Lifeboat News! Lifeboat News
Read issue #250 of Lifeboat News!
17:15
Severe Android and Novi Survey Vulnerabilities Under Active Exploitation The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The two flaws are listed below - CVE-2023-20963 (CVSS score: 7.8) - Android Framework Privilege Escalation Vulnerability CVE-2023-29492 (CVSS score: TBD) - Novi Survey Insecure Deserialization Vulnerability
17:13
Webinar: Tips from MSSPs to MSSPs Building a Profitable vCISO Practice The Hacker News
In today's fast-paced and ever-changing digital landscape, businesses of all sizes face a myriad of cybersecurity threats. Putting in place the right people, technological tools and services, MSSPs are in a great position to ensure their customers' cyber resilience. The growing need of SMEs and SMBs for structured cybersecurity services can be leveraged by MSPs and MSSPs to provide strategic
17:00
Unexpected Flavor Combos Too Delicious Not to Try Terra Forming Terra
:extract_focal()/https:%252F%252Fs3.amazonaws.com%252Fpocket-collectionapi-prod-images%252F73157bd6-544f-4fb6-81fd-940259332e3b.jpeg)
:extract_focal()/https:%252F%252Fs3.amazonaws.com%252Fpocket-collectionapi-prod-images%252F73157bd6-544f-4fb6-81fd-940259332e3b.jpeg)
With Ships, Birds Find an Easier Way to Travel Terra Forming Terra

The Psychedelic Upgrade for Your Mind and the Psycho-Spiritual Armor to Withstand Acceleration of Time Terra Forming Terra
This is another report from a experienced user of ayahuasca. It is becoming mature and is available to seekers without heading out to Peru. I still think that it is poorly understood, but empiracal research is well understood and is so far safe neough.
16:24
A Parasite is Killing Sea Otters. Is Cat Poop to Blame? SoylentNews
Scientist Melissa Miller was seeing something in California sea otters that she had not seen before: an unusually severe form of toxoplasmosis, which officials have confirmed has killed at least four of the animals.
"We wanted to get the word out. We're seeing something we haven't seen before, we want people to know about it and we want people working on marine mammals to be aware of these weird findings," said Miller, a wildlife veterinarian specialist with the California Department of Fish and Wildlife (DFW). "Take extra precautions."
In March, a study from the DFW and the University of California, Davis, revealed that a rare strain of the parasite, never before reported in aquatic animals, was tied to the deaths of four sea otters. The strain, first seen in Canadian mountain lions in 1995, had not been previously detected on the California coast."This was a complete surprise," Karen Shapiro, with the UC Davis School of Veterinary Medicine, said in a statement. "The COUG [toxoplasma strain] genotype has never before been described in sea otters, nor anywhere in the California coastal environment or in any other aquatic mammal or bird."
[...] Toxoplasma is often found in cat feces. Otters, which live along the shoreline, can be exposed to the parasite in rainwater runoffall four cases scientists studied came in during the heavy rainfall season.
Toxoplasmosis infection is common in sea otterswhich have a roughly 60 percent chance of being infected in their lifetimes, Miller saidand can be fatal, but this strain is of particular concern.
However, Miller warned against unfairly demonizing cats.
"I don't want this to be a war on cats," she said. "I have two cats. What I try to do is practice what I preach and what I know as a scientist: I keep my cats indoors all the time and I make sure to dispose of their litter into something that will not leak into the environment."
Read more of this story at SoylentNews.
16:16
The Pandemic is Killing Microsoft in Greece Techrights
Windows down to 71% this month:
Summary: These latest numbers must be causing a bit of a panic at Microsoft; its not just a Greek trend
15:22
Hikvision fixed a critical flaw in Hybrid SAN and cluster storage products Security Affairs
Chinese video surveillance giant Hikvision addressed a critical vulnerability in its Hybrid SAN and cluster storage products.
Chinese video surveillance giant Hikvision addressed an access control vulnerability, tracked as CVE-2023-28808, affecting its Hybrid SAN and cluster storage products.
An attacker with network access to the device can exploit the issue to obtain admin permission. The attacker can exploit the vulnerability by sending crafted messages to vulnerable devices.
Some Hikvision Hybrid SAN/Cluster Storage products have an access control vulnerability which can be used to obtain the admin permission. The attacker can exploit the vulnerability by sending crafted messages to the affected devices. reads the advisory published by the company.
The vulnerability was reported in December 2022 by Souvik Kandar, Arko Dhar of the Redinent Innovations team in India.
vulnerability.According to SecurityWeek, the vendor is not aware of attacks in the wild exploiting the vulnerability and is urging customers to patch their installations.
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections:
- The Teacher Most Educational Blog
- The Entertainer Most Entertaining Blog
- The Tech Whizz Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please nominate Security Affairs as your favorite blog.
...15:01
Links 14/04/2023: Libreboot 20230413 and Kirigami Addons 0.8.0 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Unicorn Media What Does Linux Have in Common With The Barrel of Rock?
Much like Linux had trouble gaining users back in the day because the general public didnt know about it, independent online radio stations like The Barrel of Rock are having trouble finding an audien...
-
15:00
Prison TV Gets Simple Speaker Mod Hackaday

American prisons are strict about television use. Typically theyre only to be used with headphones, and their enclosures need to be transparent so they cant be used to smuggle goods. ClearTech makes TVs that meet these specifications, and when [Steve Pietras] got his hands on just such a unit, he set about modding it for use in the free world.
Getting into the TV isnt easy; ClearTech built the units using special security fasteners unlike any weve seen before. [Steve] found a way to deal with these, though declines to share his technique in his video. Once inside though, his task is relatively straightforward. He steps through where to install speakers in the TVs housing, and how to hook them up to the right spots on the main circuit board. With the case closed back up, [Steve] is able to use the TV without headphones, and without the threat of getting shanked by a fellow inmate...
14:48
Be Skeptical of FBI Warnings About Phone Chargers Deeplinks
Every few years, an unsourced report circulates that the FBI says plugging into public charging kiosks is dangerous. Heres why you should ignore the freakout and install software updates regularly.
Your phone is designed to communicate safely with lots of things chargers , web sites, Bluetooth devices such as earbuds or speakers, Wi-Fi, and even other phones, for instance when sending and receiving text messages. If doing any of these normal phone things can give your phone malware, that is a security vulnerability (which is a type of bug).
Security vulnerabilities happen with some frequency. That is why your phone prompts you to update your software so often the makers of its software find out about bugs and fix them.
So, when you hear a report that public chargers are giving people malware, you should ask what is the vulnerability being used, and when will it be fixed? as well as how widespread is the problem? How many people are affected? Unfortunately, the periodic reports of juice jacking never have such details, usually because they are recycled from earlier reports which themselves lack details.
The most recent news reports reference a tweet from the FBI Denver field office. According to reporter Dan Goodins conversation with an FBI spokesperson, the field office relied on an article the FCC published in 2019 warning about USB charging stations. The only source for that article was a warning from the ...
14:30
New infosec products of the week: April 14, 2023 Help Net Security
Heres a look at the most interesting products from the past week, featuring releases from BigID, Binarly, Cynalytica, GitGuardian, Netskope, Searchlight Cyber, ThreatX, and Wazuh. Cynalytica OTNetGuard provides visibility into critical infrastructure networks Cynalytica has launced its Industrial Control System (ICS/SCADA) monitoring sensor, OTNetGuard, that passively and securely captures analog, serial, and IP communications closing the capabilities gap in complete monitoring of OT networks. GitGuardian Honeytoken helps companies secure their software supply chains With attackers More
The post New infosec products of the week: April 14, 2023 appeared first on Help Net Security.
14:00
Tactics that make crypto giveaway scams so successful Help Net Security
The illicit market for crypto giveaway scams has expanded, offering various services to facilitate fraudulent activity. The proliferation of fake crypto giveaways can be attributed to the increased availability of tools for scammers, even those with limited technical skills. In this Help Net Security video, Tony Lauro, Director of Security Technology and Strategy at Akamai, discusses why crypto giveaway scams are so successful.
The post Tactics that make crypto giveaway scams so successful appeared first on Help Net Security.
13:38
Developer Creates Self-healing Programs That Fix Themselves Thanks to AI SoylentNews
"Wolverine" experiment can fix Python bugs at runtime and re-run the code:
Debugging a faulty program can be frustrating, so why not let AI do it for you? That's what a developer that goes by "BioBootloader" did by creating Wolverine, a program that can give Python programs "regenerative healing abilities," reports Hackaday. (Yep, just like the Marvel superhero.)
"Run your scripts with it and when they crash, GPT-4 edits them and explains what went wrong," wrote BioBootloader in a tweet that accompanied a demonstration video. "Even if you have many bugs it'll repeatedly rerun until everything is fixed."
[...] In the demo video for Wolverine, BioBootloader shows a side-by-side window display, with Python code on the left and Wolverine results on the right in a terminal. He loads a custom calculator script in which he adds a few bugs on purpose, then executes it.
"It runs it, it sees the crash, but then it goes and talks to GPT-4 to try to figure out how to fix it," he says. GPT-4 returns an explanation for the program's errors, shows the changes that it tries to make, then re-runs the program. Upon seeing new errors, GPT-4 fixes the code again, and then it runs correctly. In the end, the original Python file contains the changes added by GPT-4.
Read more of this story at SoylentNews.
13:30
Organizations face an uphill battle to keep their sensitive data secure Help Net Security
On average, organizations store 61% of their sensitive data in the cloud, and most have experienced at least one cybersecurity breach (90%), threat (89%) and/or theft of data (80%), with 75% experiencing all three, according to Skyhigh Security. Overall, the report underscores the need to address data security gaps by investing in comprehensive data protection that provides remote workforces with a secure and productive user experience. Today, data is everywhere, traversing devices, cloud applications, the More
The post Organizations face an uphill battle to keep their sensitive data secure appeared first on Help Net Security.
13:00
Conquering modern data stack complexities Help Net Security
How are data teams conquering the complexity of the modern data stack? Unravel Data has asked 350+ data scientists, engineers, analysts, and others who rely upon real-time data insights for decision-making to share their practices. For the third year in a row weve had the opportunity to take the pulse of enterprise data teams to better understand the daily challenges they face as they accelerate their ambitious big data analytics programs, said Kunal Agarwal, CEO More
The post Conquering modern data stack complexities appeared first on Help Net Security.
12:25
Qwiet AI releases a suite of targeted AppSec and DevSecOps services Help Net Security
Qwiet AI has released a suite of targeted AppSec and DevSecOps services that help companies address their security function needs without sacrificing time and budget. We often hear of the notion of doing more with less. However, in todays environment companies are challenged with doing less with less, said Stuart McClure, CEO of Qwiet AI. Between sourcing the right people and distinguishing between true threats and non-critical vulnerabilities, todays security and development teams struggle with More
The post Qwiet AI releases a suite of targeted AppSec and DevSecOps services appeared first on Help Net Security.
12:20
Entrust offers zero-trust solutions for authentication, HSM, and multi-cloud compliance Help Net Security
Entrust is supporting organizations zero trust journey with new foundational identity, encryption, and key management solutions. Zero trust approaches are reshaping security in a perimeter-less world. While the conversation often starts with identity and network access, organizations are quickly finding that identity and access management is only the beginning. A comprehensive zero trust framework starts with enabling trusted identities across users, devices, machines, apps, and workloads, and extends to a data protection strategy to secure More
The post Entrust offers zero-trust solutions for authentication, HSM, and multi-cloud compliance appeared first on Help Net Security.
12:15
Code42 Instructor now offers risk reduction training videos to Microsoft Teams Help Net Security
Code42 Software has offered a complete set of response controls to allow security teams to respond to all levels of risk, ranging from unacceptable high risk that must be blocked to the most prevalent user mistakes that require correction. Instructor delivers actionable, hyper-targeted lessons to employees engaging in risky behavior, helping to increase data security, while freeing up time for security analysts to focus on higher risk events. Code42 Instructor now offers over 100 lessons More
The post Code42 Instructor now offers risk reduction training videos to Microsoft Teams appeared first on Help Net Security.
12:10
Cerbos Cloud manages and enforces authorization policies Help Net Security
Cerbos has released Cerbos Cloud, a managed service offering for Cerbos. Cerbos is an open source authorization layer to easily implement roles and permissions in software applications. It separates authorization logic from the core application code, making the authorization layers more scalable, more secure and easier to change as the complexity grows. Cerbos Cloud streamlines the implementation and management of authorization policies. Torsten Volk, managing research director at Enterprise Management Associates, said: Writing and managing More
The post Cerbos Cloud manages and enforces authorization policies appeared first on Help Net Security.
11:51
OGUsers (2022 breach) - 529,020 breached accounts Have I Been Pwned latest breaches
In July 2022, the account hijacking and SIM swapping forum OGusers suffered a data breach, the fifth since December 2018. The breach contained usernames, email and IP addresses and passwords stored as argon2 hashes. A total of 529k unique email addresses appeared in the breach.
10:59
OpenSSF Membership Growth Signals Technical Communities Continued Commitment to Investing in Security Linux.com

Read the original blog at Read More
The post OpenSSF Membership Growth Signals Technical Communities Continued Commitment to Investing in Security appeared first on Linux.com.
10:53
Get Ready: SpaceX Starship's First Launch is for Real SoylentNews
An unprecedented space event, and it's happening soon:
Elon Musk lost his claim as having the most powerful space-worthy rocket when NASA blasted its own mega rocket to the moon in November.
But the SpaceX founder could win back the title with his company's next big project. Starship, SpaceX's skyscraping rocket and spacecraft, will launch on its first mission soon. During the test flight, the colossal booster will separate about three minutes after liftoff and land in the Gulf of Mexico, according to federal filings. The ship will fly in space around Earth at an altitude of over 150 miles, then splash down off the Hawaiian coast.
This will be a crucial demonstration of hardware that NASA is depending on to get humans back on the moon in the next few years. And, if successful, it'll mean Musk is one small step closer to realizing his personal dream of building a city on Mars.
UPDATE: Apr. 9, 2023, 12:54 p.m. EDT SpaceX stacked Starship at the launch pad and plans to have a rehearsal this week, "followed by Starship's first integrated flight test." Musk tweeted April 9 that the company is ready to launch the rocket, pending approval of its Federal Aviation Administration license. A launch attempt this month is looking more and more plausible, with an FAA operational advisory plan indicating SpaceX is targeting Monday, April 17.
[...] Perhaps surprisingly, Starship won't lift off from Kennedy Space Center in Cape Canaveral, Florida, where most space fans are accustomed to watching historically significant launches.
Instead, it will take off from Boca Chica, Texas, at SpaceX's own spaceport. Eventually, the company will launch the rocket from a site under construction in the outer perimeter of the famous Florida pad that shot Apollo 11 to the moon.
"Their plan is that they're going to do a few test flights there," in South Texas, Nelson said. "Once they have the confidence, they will bring the missions to the Cape."
Read more of this story at SoylentNews.
10:21
Troubleshooting No Signal Monitor Issue: Steps to Get Computer Display Back HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
If you encounter a No signal issue on your monitor despite your computer being powered on, and you
This is a post from HackRead.com Read the original post: Troubleshooting No Signal Monitor Issue: Steps to Get Computer Display Back
10:00
HPR3835: Retro Karaoke machine Part 2 Hacker Public Radio
The tape stops in the middle Put pressure here Video clip of Star Wars audio drama playing Video clip on Archive.org
Software Supply Chain Attacks It Will Never Work in Theory
This new paper about attacks on open source software supply chains succeeds on two fronts. First, the topic itself is timely and interesting: the number of attacks via package builds and repositories is increasing rapidly, so conscientious software developers need at least a basic understanding of the risk and how to mitigate it.
Second, this paper is an excellent model of what software engineering research could be. The authors have built a tool to help people explore risks in software supply chains and put it online at https://sap.github.io/risk-explorer-for-software-supply-chains/; the source code is available as well, which makes this work far more accessible than most of what we review. In particular, the readability of the paper and the availability of the tool makes it easy to incorporate this work into undergraduate classes and workplace training seminars so that it doesn't stay trapped in a PDF.
Piergiorgio Ladisa, Serena Elisa Ponta, Antonino Sabetta, Matias Martinez, and Olivier Barais. Journey to the center of software supply chain attacks. 2023. arXiv:2304.05200.
This work discusses open-source software supply chain attacks and proposes a general taxonomy describing how attackers conduct them. We then provide a list of safeguards to mitigate such attacks. We present our tool "Risk Explorer for Software Supply Chains" to explore such information and we discuss its industrial use-cases.
09:00
Why You Cant Miss This Years Open Source Summit North America, May 10-12 in Vancouver, Canada Linux.com

Read the original blog at Read More
The post Why You Cant Miss This Years Open Source Summit North America, May 10-12 in Vancouver, Canada appeared first on Linux.com.
08:06
Swiss Health Authorities - Natural Immunity is the Best Defense Against COVID (in Switzerland) SoylentNews
Many people believe that any and all opposition to the Covid vaccine comes from "far-right" Republican conspiracy theorists in the flyover states. I guess the Swiss government will now be branded with those labels as their Federal Office of Public Health is now recommending that a Covid vaccination is not needed, even for people at especially high risk. They list pregnant women and people with compromised immune systems as an exception. They further state that those who wish to receive a Covid vaccine must pay for it out of their own pockets.
In principle, no COVID-19 vaccination is recommended for spring/summer 2023. Nearly everyone in Switzerland has been vaccinated and/or contracted and recovered from COVID-19. Their immune system has therefore been exposed to the coronavirus. In spring/summer 2023, the virus will likely circulate less. The current virus variants also cause rather mild illness. For autumn 2023, the vaccination recommendation will be evaluated again and adjusted accordingly.
Read more of this story at SoylentNews.
07:35
The Linux Foundation Announces Schedule for Embedded Open Source Summit Linux.com

Read the original post at: Read More
The post The Linux Foundation Announces Schedule for Embedded Open Source Summit appeared first on Linux.com.
07:05
What Does Linux Have in Common With The Barrel of Rock? FOSS Force
Much like Linux had trouble gaining users back in the day because the general public didn't know about it, independent online radio stations like The Barrel of Rock are having trouble finding an audience because potential listeners can't wade through tens of thousands of music radio stations to find them.
The post What Does Linux Have in Common With The Barrel of Rock? appeared first on FOSS Force.
06:45
Read "Intelligence Explosion - Part 1/3" by our Henrique Jorge. Lifeboat News
Read "Intelligence Explosion Part 1/3" by our Henrique Jorge.
06:43
Pentagon leak suspect Jack Teixeira arrested at gunpoint Graham Cluley
The US Department of Justice has arrested a member of the US Air Force National Guard in connection with a high profile leak of classified Pentagon documents. Here are my thoughts...
06:37
Re: Multiple vulnerabilities in Jenkins plugins Open Source Security
Posted by Henri Salo on Apr 13
It's better for organizations to be aware of the vulnerabilities and risksrelated to used software. Sometimes it is challenging to get the author/team to
fix the security issues (busy/unresponsive/miscommunication etc). This is very
common with plugins in different software as there are large number of
developers. It's better for users and community to disclose the issues if no
fix is provided as plugins can be disabled, WAF can be...
06:30
Copyright Claims Board Dismisses Piracy Case Against Cloudflare TorrentFreak
 Last summer, the US Copyright
Claims Board (CCB) officially launched. Through this Copyright
Office-hosted venue, rightsholders can try to recoup alleged
damages outside the federal court system.
Last summer, the US Copyright
Claims Board (CCB) officially launched. Through this Copyright
Office-hosted venue, rightsholders can try to recoup alleged
damages outside the federal court system.
The CCB aims to make it cheaper for creators to resolve disputes. Theres no attorney required and the filing fee is limited to $100 per claim. Accused parties also benefit as the potential damages are capped at $30,000. Those who prefer traditional lawsuits can choose to opt-out.
Many of the cases that have been submitted thus far are filed against direct infringers. This includes sites and services that use copyrighted material, such as photos, without obtaining permission from rightsholders.
There are also cases where claimants argue that defendants are liable for the acts of a third party. A claim filed by popular reading app AnyStories against CDN provider Cloudflare last September is one such example.
AnyStories vs. Cloudflare
AnyStories allows independent authors to earn revenue from sharing their writings in public. However, these stories are easily copied and posted on pirate sites, much to the frustration of READ ASAP, AnyStories Singapore-based parent company.
The Singapore company had some success with sending DMCA notices but one site in particular, infobagh.com, proved to be unresponsive.
Hoping for a breakthrough, AnyStories sent DMCA notices to Cloudflare, calling out Infobagh.com as a pirate site. While Cloudflare provides CDN services for that site, its not the hosting company. This means that Cloudflare generally doesnt intervene.
Indeed, Cloudflare didnt take action against its customer. Instead, it shared the contact information of Infobagh.coms hosting company, urging AnyStories to follow the issue up with them.
AnyStories tried to do so, but since the hosting companys contact information was reportedly inaccurate, it decided to file a claim against Cloudflare at the CCB instead.
Vague Claim, No Damages
The initial claim was rather vague and didnt really pinpoint alleged wrongdoing at Cloudflare. AnyStories said it hoped that the pirated content would be removed and that Infobagh.com would apologize.
There were no copyright infringement allegations against Cloudflare and no request for monetary damages either.
06:19
The Russia-linked APT29 is behind recent attacks targeting NATO and EU Security Affairs
Poland intelligence linked the Russian APT29 group to a series of attacks targeting NATO and European Union countries.
Polands Military Counterintelligence Service and its Computer Emergency Response Team linked a recent string of attacks targeting NATO and European Union countries to the Russia-linked APT29 group (aka SVR group, Cozy Bear, Nobelium, and The Dukes).
APT29 along with APT28 cyber espionage group was involved in the Democratic National Committee hack and the wave of attacks aimed at the 2016 US Presidential Elections.
In early March, BlackBerry researchers uncovered a new cyber espionage campaign aimed at EU countries. The hackers targeted diplomatic entities and systems transmitting sensitive information about the regions politics, aiding Ukrainian citizens fleeing the country, and providing help to the government of Ukraine.
The Polish intelligence states that many elements of the recent campaign, including the infrastructure, the techniques used and the tools, overlap with past APT29 activity.
The recent attacks, which are still ongoing, differ from the previous ones in the use of unique and previously undocumented tools.
The Military Counterintelligence Service and CERT.PL recommend organizations in the area of interest of the APT group to improve the security of IT Security systems.
The attack chain commences with a spear-phishing email containing a weaponized document, which contains a link leading to the download of an HTML file. The HTLM files are hosted on a legitimate online library website that was likely compromised by the threat actors sometime between the end of January 2023 and the beginning of February 2023.
One of the lures appeals to those who want to find out the Poland Ambassadors schedule for 2023. It overlaps with Ambassador Marek Magierowskis recent visit to the United Statesp; specifically, his...
06:00
Google Launches New Cybersecurity Initiatives to Strengthen Vulnerability Management The Hacker News
Google on Thursday outlined a set of initiatives aimed at improving the vulnerability management ecosystem and establishing greater transparency measures around exploitation. "While the notoriety of zero-day vulnerabilities typically makes headlines, risks remain even after they're known and fixed, which is the real story," the company said in an announcement. "Those risks span everything from
05:40
Linking Chips With Light For Faster AI IEEE Spectrum

Stephen Cass: Hi, Im Stephen Cass, for IEEE
Spectrums Fixing the Future. This episode is brought to you by
IEEE Xplore, the digital library with over 6 million pieces of the
worlds best technical content. Today I have with me our own
Samuel K. Moore, who has been covering the
semiconductor beat pretty intensely for Spectrum for well,
how many years has it been, Sam?
Sam Moore: 7 years, I would say.
Cass: So Sam knows computers down at the level most of us like to ignore, hidden underneath all kinds of digital abstractions. This is down where all the physics and material science that make the magic possible lurk. And recently, you wrote an article about the race to replace electricity with light inside computers, which is letting chips talk to each other with fiber optics rather than just using fiber optics to communicate between computers. I guess my first question is, whats wrong with electricity, Sam?
Moore: I have nothing against electricity, Stephen. Wow It knows what it did. But really, this all comes down to inputs and outputs. There just arent enough coming off of processors for what they want to do in the future. And electronics can only push signals so far before they kind of melt away, and they consume quite a bit of power. So the hope is that you will have better bandwidth between computer chips, consuming less power.
Cass: So its not just a question of raw speed, though, when you talk about these signals and melting away, because I think the signal speed of copper is about, what, two-thirds the speed of light in a vacuum. But then I was kind of surprised to see that, in a fiber optic cable, the speed of light is about two-thirds of that in a vacuum. So whats going on? Whats kind of the limitations of pushing a signal down a wire?
Moore: Sure. A wire is not an ideal conductor. Its really resistance, inductance, and capacitance, all of which will reduce the size and speed of a signal. And this is particularly a problem at high frequencies, which are more susceptible, particularly to the capacitance side of things. So you might start with a beautiful 20 GHz square wave at the edge of the chip, and by the time it gets to the end of the board, it will be an imperceptible bump. Light, on the other hand, doesnt work like that. It has things that there are things that mess with signals in optical fibers, but they work at much, much, much long...
05:21
MSI Confirms Cyberattack, Advises Caution With Firmware SoylentNews
The reports suggest ransomware may have been involved:
Gaming hardware manufacturer MSI confirmed today that it was the victim of a cyberattack. In a brief statement on its website, the company said that the attack hit "part of its information systems," which have since returned to regular operations.
The company advises its customers only to get BIOS and firmware updates from the MSI website and no other sources. It's light on details, saying that after "detecting network anomalies," MSI implemented "defense mechanisms and carried out recovery measures," and then informed the the government and law enforcement.
[...] The post doesn't mention if customer data was stolen or affected. Tom's Hardware reached out to MSI but did not hear back in time for publication. In addition, emails to official spokesperson addresses listed on the company's website bounced.
Also at Bleeping Computer.
Read more of this story at SoylentNews.
05:05
Hackers Claim Vast Access to Western Digital Systems cryptogon.com
Via: TechCrunch: The hackers who breached data storage giant Western Digital claim to have stolen around 10 terabytes of data from the company, including reams of customer information. The extortionists are pushing the company to negotiate a ransom of minimum 8 figures in exchange for not publishing the stolen data. One of []
04:55
Intel Sierra Forest EDAC Support Coming With Linux 6.4 Phoronix
As part of Intel's ongoing Linux support preparations for next year's Sierra Forest processors that will feature up to 144 Xeon E cores per socket, the Error Detection And Correction (EDAC) driver support is set to be added for the upcoming Linux 6.4 kernel cycle...
04:53
Re: ncurses fixes upstream Open Source Security
Posted by Mark Esler on Apr 13
(distros maintain "downstream" versions of the ncurses "upstream")Ideally, a security patch should only include security relevant changes.
If a bunch of a documentation or miscellaneous changes are added, it
makes backporting difficult (i.e., the non-security relevant changes may
not be desired or cause the patch to not apply cleanly to old versions
of ncurses). The upstream patch is already made, but that's what...
04:50
Hersh: Zelensky Regimes Corruption Like, 1950s Mob Movie, Embezzled $400 Million in 2022, Buying Discount Diesel from the Russians [???] cryptogon.com
10% for the big guy? Via: Seymour Hersh: The Ukraine government, headed by Volodymyr Zelensky, has been using American taxpayers funds to pay dearly for the vitally needed diesel fuel that is keeping the Ukrainian army on the move in its war with Russia. It is unknown how much the Zelensky government is paying per []
04:46
LockBit 3.0 Posts Dubious Claims of Breaching Darktrace Cybersecurity Firm HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
Is it a highly dubious claim by the infamous LockBit 3.0 ransomware gang? It looks like it!
This is a post from HackRead.com Read the original post: LockBit 3.0 Posts Dubious Claims of Breaching Darktrace Cybersecurity Firm
04:33
Re: Multiple vulnerabilities in Jenkins plugins Open Source Security
Posted by Demi Marie Obenour on Apr 13
What is the reason for the large number of unfixed vulnerabilities?To me, this seems like an argument for not using Jenkins (or at least
its plugins) at all.
04:31
18,000 Cows Killed in Explosion, Fire at Texas Dairy Farm cryptogon.com
Via: USA Today: The fire spread quickly through the holding pens, where thousands of dairy cows crowded together waiting to be milked, trapped in deadly confines. After subduing the fire at the west Texas dairy farm Monday evening, officials were stunned at the scale of livestock death left behind: 18,000 head of cattle perished in []
04:30
Libreboot 20230413 Released With Build System Improvements Phoronix
Libreboot is the downstream of Coreboot focused on having fully open-source / free software replacements to proprietary BIOS/firmware on x86 and ARM systems. Out today is Libreboot 20230413 as the latest step forward for the project...
04:28
Links 13/04/2023: Stable Kernels and Alyssa Goes to Dyson Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Internet Policy/Net Neutrality
- Monopolies
- Gemini* and Gopher
03:40
Development Release: EuroLinux 8.8 Beta DistroWatch.com: News
EuroLinux is an enterprise-class Linux distribution made and supported by the EuroLinux company, built mostly from code of Red Hat Enterprise Linux. The project has published a new development snapshot, EuroLinux 8.8 Beta. "On April 13, we released EuroLinux
03:38
A flaw in the Kyocera Android printing app can be abused to drop malware Security Affairs
Security experts warn that a Kyocera Android printing app is vulnerable to improper intent handling and can be abused to drop malware.
An improper intent handling issue affecting the Kyocera Android printing app can allow malicious applications to drop malware. Such kinds of flaws expose a resource to the wrong control sphere, providing unintended actors with inappropriate access to the resource.
The vulnerability, tracked as CVE-2023-25954, was reported by the Japanese Vulnerability Notes (JVN).
Multiple mobile printing apps for Android are vulnerable to improper intent handling (CWE-668). reads the advisory published by the JVN. When a malicious app is installed on the victim users Android device, the app may send an intent and direct the affected app to download malicious files or apps to the device without notification.
The vulnerability impacts multiple apps that share the same code:
- KYOCERA Mobile Print v3.2.0.230119 and earlier (+1M downloads on Google Play)
- UTAX/TA Mobile Print v3.2.0.230119 and earlier (+100k downloads on Google Play)
- Olivetti Mobile Print v3.2.0.230119 and earlier (+10k downloads on Google Play)
02:51
Mesa 23.1 Branched With Many New Radeon, Intel & Zink Graphics Driver Features Phoronix
The Mesa 23.1 graphics driver code is now branched that marks an end to this quarter's feature development. Mesa 23.2-devel is now open on Git main in beginning work towards the Q3'2023 open-source user-space graphics driver stack feature release...
02:40
RTM Locker: Emerging Cybercrime Group Targeting Businesses with Ransomware The Hacker News
Cybersecurity researchers have detailed the tactics of a "rising" cybercriminal gang called "Read The Manual" (RTM) Locker that functions as a private ransomware-as-a-service (RaaS) provider and carries out opportunistic attacks to generate illicit profit. "The 'Read The Manual' Locker gang uses affiliates to ransom victims, all of whom are forced to abide by the gang's strict rules,"
02:39
Mistaken Fossil Rewrites History of Indian Subcontinent for Second Time SoylentNews
In 2020, amid the first pandemic lockdowns, a scientific conference scheduled to take place in India never happened.
But a group of geologists who were already on site decided to make the most of their time and visited the Bhimbetka Rock Shelters, a series of caves with ancient cave art near Bhopal, India. There, they spotted the fossil of Dickinsonia, a flat, elongated and primitive animal from before complex animals evolved. It marked the first-ever discovery of Dickinsonia in India.
The animal lived 550 million years ago, and the find seemed to settle once and for all the surprisingly controversial age of the rocks making up much of the Indian subcontinent. The find attracted the attention of The New York Times, The Weather Channel and the scientific journal Nature as well as many Indian newspapers.
Only, it turns out, the "fossil" was a case of mistaken identity. The true culprit? Bees.
University of Florida researchers traveled to the site last year and discovered the object had seemingly decayed significantly quite unusual for a fossil. What's more, giant bee's nests populate the site, and the mark spotted by the scientists in 2020 closely resembled the remains of these large hives.
Read more of this story at SoylentNews.
02:27
The Linux Foundation Announces Schedule for Embedded Open Source Summit Linux.com
read the original post at Read More
The post The Linux Foundation Announces Schedule for Embedded Open Source Summit appeared first on Linux.com.
02:09
Thursday, 13 April
02:18
888 Casino Evaluation 2023 888 On Line Casino Free Spins h+ Media
888 Casino Evaluation 2023 888 On Line Casino Free Spins
You can merely kind in keywords like deposit after which find a good amount of helpful information regarding your chosen matter. All of which ought to assist provide some fair if not distinctive 888 ratings for buyer assist. As a result of the acquisition by 888 Holdings, this licence utility might now end up in an accelerated course of. One hurdle along the way is the $300,000 fine William Hill obtained from our Gaming Authority in 2018 for illegally offering playing video games on the New Zealand market. William Hills belongings embody greater than 1,four hundred betting retailers in dollarpa. These are primarily betting outlets, small betting places of work in various British cities, the place gamers can guess on sports competitions, horse and dog races, bingo and lotteries.
If this is your first time joining the poker room, you are in for a nice deal with. Simply registering is enough to get you $88 free of charge, with another $400 waiting on the primary deposit. After all, there are a quantity of coupon moguls out there offering promotional code.
This isnt very surprising when you ask us as this brand has been active for during the last 25 years. In terms of cell usability, we might label it as one of the best cellular casinos out there in NZ right now. 888 even got here up with the well-received slogan App, Tap, Bet and that just about explains how their app works. Their mobile optimised website does the trick too, however we consider their cellular app does make a real distinction.
The incontrovertible fact that theyve managed to jump via all the mandatory hoops to safe these trusted and extremely revered gaming licenses exhibits that youre in good palms. 888 casino is a reputation and a website that you could belief, so your personal details might be secure, and your gaming experiences might be honest. You are studying our most updated and correct 888 casino evaluate. You can contact them by e mail or simply by using the reside chat operate.
- However, if we have a look at the licenses, then we have some very dependable cases.
- You will be succesful of transition from PC to Mobile and have the identical choice of games, together with the same levels of safety.
- One of the main considerations of online gaming is to ensure truthful and honest games.
- Also, the Android app allows some unique 888 Casino bonuses tailored particularly for the app users.
- With more than 10 million registered users, 888 Poker has one thing for everybody.
This should allow you to make respectable bets earlier on, which is able to in turn help you to win respectable quantities. We are a team of specialists that wish to cross further the passion of on-line playing to its kiwi players. Founded again in 2019, KiwiGambler is ready to current & give to its guests better alternatives f...
Wednesday, 12 April
12:34
Join us for EFF's 7th Annual Tech Trivia Night! Deeplinks
Join us in San Francisco on April 27th for EFF's 7th annual Tech Trivia Night! Explore the obscure minutiae of digital security, online rights, and internet culture.
Enjoy delicious tacos, churros, and complimentary adult beverages and soft drinks as you and your team battle through rounds of questionsand cutthroat live judging!to see who will take home the coveted 1st, 2nd, and 3rd place trophies and EFF swag!
$45 for EFF Members $55 for General Admission
Thursday, April 27th, 2023 at Public Works from 6 PM to 10 PM
This event is 21+. Please remember to bring ID and a mask.

Interested in sponsoring Tech Trivia Night, or other EFF events? Please contact Mei Harrison.
EFF is dedicated to a harassment-free experience for everyone, and all participants are encouraged to view our full Event Expectations.





















:extract_focal()/https:%252F%252Fs3.amazonaws.com%252Fpocket-collectionapi-prod-images%252F8f3533af-994f-41aa-8784-cbf294c5dcd5.jpeg) View Original
View Original
