| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Monday, 10 April
02:34
More about the QO-100 WB transponder power budget Daniel Estvez
Last week I wrote a post with a study about the QO-100 WB transponder power budget. After writing this post, I have been talking with Dave Crump G8GKQ. He says that the main conclusions of my study dont match well his practical experience using the transponder. In particular, he mentions that he has often seen that a relatively large number of stations, such as 8, can use the transponder at the same time. In this situation, they rob much more power from the beacon compared to what I stated in my post.
I have looked more carefully at my data, specially at situations in which the transponder is very busy, to understand better what happens. In this post I publish some corrections to my previous study. As we will see below, the main correction is that the operating point of 73 dBHz output power that I had chosen to compute the power budget is not very relevant. When the transponder is quite busy, the output power can go up to 73.8 dBHz. While a difference of 0.8 dB might not seem much, there is a huge difference in practice, because this drives the transponder more towards saturation, decreasing its gain and robbing more output power from the beacon to be used by other stations.
I want to thank Dave for an interesting discussion about all these topics.
Input power to output power transfer curve review
While reviewing my study, I have not found anything terribly wrong with the methods and calculations themselves (though I have found a way to improve the calculation of transponder noise power, with which I wasnt too happy). It was the interpretation of results what was more problematic.
To begin, let us review my plot of the transponder input to output power function. Here we can see that the transponder is close to saturation, even when only the beacon is active (which corresponds to the leftmost part of the curve). The transponder maximum output power seems to be slightly below 74 dBHz.
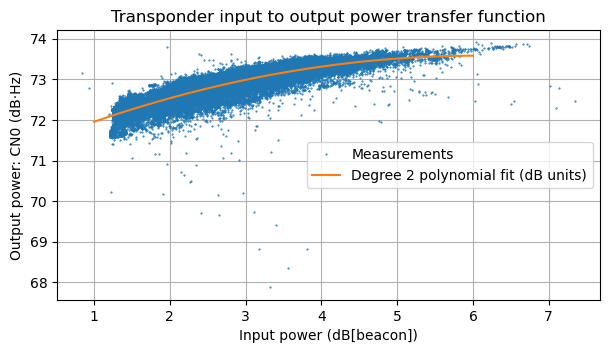
Additionally, the histogram of output power shows that most of the time the transponder is below 73.5 dBHz output power.
02:20
Estonian National charged with helping Russia acquire U.S. hacking tools and electronics Security Affairs
Andrey Shevlyakov, an Estonian national, was charged in the US with conspiracy and other charges related to acquiring U.S.-made electronics on behalf of the Russian government and military.
The Estonian man is accused of having helped the Russian government and military to purchase US-made electronics and hacking tools.
The defendant was arrested in Estonia on March 28, 2023, he used several Estonian-based business entities (the Estonian Shell Companies) to buy goods that would have been unavailable to Russian end-users.
As alleged in the indictment and other court filings, Shevlyakov procured sensitive electronics from U.S. manufacturers on behalf of Russian end-users, including defense contractors and other Russian government agencies. Most of these items would have been unavailable to Russian end-users if ordered directly for shipment to Russia. reads a press release published by DoJ. Shevlyakov also attempted to acquire computer hacking tools.
Shevlyakov purchased multiple items, including low-noise pre-scalers and synthesizers (used to conduct high-frequency communications) and analog-to-digital converters, which are components used in defense systems such as electronic warfare systems and missiles.
In 2012, the US government added Shevlyakov to Entity List, a ban list for procuring and delivering export-restricted items to Russia. The man circumvented the ban using false names and a network of front companies. In order to deliver the purchased goods, the man ran an intricate logistics operation involving frequent smuggling trips across the Russian border by himself and others.
In May 2020, Shevlyakov used one of his front companies to buy a licensed copy of the penetration testing platform Metasploit Pro.
A license to use Metasploit Pro costs approximately $15,000. In the email, the individual asked Shevlyakovs front company to acquire Metasploit and detailed a history of prior failed attempts to acquire the software through third parties in countries outside Russia. continues the press release. The individual added that the software was dual use and that accordingly, sales to Russia are virtually impossible. Thus, the individual said, we cannot reveal the end user, nor can we identify ourselves. On or about June 1, 2020, the front company email address wrote back, listing prices for different versions of Metasploit Pro.
The Estonian man exported at least $800,000 worth of items from U.S. electronics manufacturers and distributors between approximately October 2012 and January 2022.
For years, Mr. Shevlyakovs elab...
02:13
Premier League IPTV Investigations Gather Personal Data on Pirates TorrentFreak
 Its
the summer of 2008 and the owner of a fairly new streaming site
based in the north of England is on his way to a London hotel to
meet a potential investor.
Its
the summer of 2008 and the owner of a fairly new streaming site
based in the north of England is on his way to a London hotel to
meet a potential investor.
Two surveillance teams are already in place; one covertly video recording the meeting from a table in the restaurant, another monitoring the exits. After the meeting, the site owner returns to the north by train, a surveillance team in tow.
After getting off the train, a new surveillance team takes over and shadows the site owner home. No investment was forthcoming; the investor was actually a private investigator working for copyright holders. A high-profile police raid followed just a month later, a lengthy prison sentence four years after that.
Piracy Investigations Take Place in Real Life
Fifteen years ago, covert piracy investigations were mostly the stuff of rumors and rarely documented in public. That the investigation detailed above was conducted by private companies, rather than the police, was controversial but not controversial enough to stop them.
Indeed, private companies conducting their own anti-piracy investigations today have the ability to peer into private lives as they go about protecting and enforcing their intellectual property rights. Since this necessarily involves the collection of personal data, companies like the Premier League sometimes disclose the type of information they collect as part of their privacy policies.
Documentation reveals that the Premier League collects and uses personal data about individuals who have, might have or are likely to infringe the Premier Leagues intellectual property rights. Depending on the circumstances, that might also entail collecting personal data on others related to them.
Open Source Research, Third-Party Investigators
Given the wealth of information available online today covering billions of people, its...
01:55
Son of George Soros Frequently Visits White House cryptogon.com
Via: New York Post: A son of billionaire George Soros has quietly become a de-facto White House ambassador, making at least 14 visits there on behalf of the far-left kingmaker since President Joe Biden took office, records reviewed by The Post show. Alexander Soros a prolific Democratic fundraiser in his own right who likes []
01:50
Physicists Recreate Classic 'Double-Slit' Experiment Using Time Instead of Space SoylentNews
New research offers an intriguing variation on the famous experiment:
A team of physicists has recreated a classic experiment in particle physics with a dimensional twist, by performing it in time instead of just space. In the process, they showcased the utility of a unique material for future experiments.
The researchers redesigned the double-slit experiment, which was first performed in 1801 and demonstrated a curious trait of light: that it can behave both as a particle and a wave.
The original experiment tested how light moved through space; the recent rendition tested how light would travel if it was only allowed to at specific times. Details of the team's work are published today in Nature Physics.
[...] In the traditional experiment, a beam of light is projected at a barrier, behind which is a photosensitive detector. The barrier has two parallel slits. If you threw ordinary matter at the barrier, they would roughly form the same shape as the slits on the detector. But when light is cast on the slits, it splits into two waves that pass through the barrier and intersect on the other side.
[...] In the new work, the researchers made one big change: They swapped out an ordinary screen with two slits for an indium-tin-oxide filmthe same material that is used in modern phone screens. (It's actually a metamaterial, or a material not found in nature, that is engineered to behave a certain way.)
The researchers changed the reflectance of the screen using ultrafast lasers, which only allowed light through at specific times, quadrillionths of a second apart. Basically, they built a quantum tollbooth, using the lasers to create time-dependent slits in the barrier. Even when they only allowed one photon through the screen, the light produced an interference pattern.
Journal Reference:
Tirole, Romain, Vezzoli, Stefano, Galiffi, Emanuele, et
al. Double-slit time diffraction at optical
frequencies, Nature Physics (DOI: 10.1038/s41567-023-01993-w)
Read more of this story at SoylentNews.
01:22
New atomic-scale understanding of catalysis could unlock massive energy savings Lifeboat News: The Blog
In an advance they consider a breakthrough in computational chemistry research, University of WisconsinMadison chemical engineers have developed model of how catalytic reactions work at the atomic scale. This understanding could allow engineers and chemists to develop more efficient catalysts and tune industrial processespotentially with enormous energy savings, given that 90% of the products we encounter in our lives are produced, at least partially, via catalysis.
Catalyst materials accelerate chemical reactions without undergoing changes themselves. They are critical for refining petroleum products and for manufacturing pharmaceuticals, plastics, food additives, fertilizers, green fuels, industrial chemicals and much more.
Scientists and engineers have spent decades fine-tuning catalytic reactionsyet because its currently impossible to directly observe those reactions at the extreme temperatures and pressures often involved in industrial-scale catalysis, they havent known exactly what is taking place on the nano and atomic scales. This new research helps unravel that mystery with potentially major ramifications for industry.
01:22
Physicists Discover that Gravity Can Create Light Lifeboat News: The Blog

Researchers have discovered that in the exotic conditions of the early universe, waves of gravity may have shaken space-time so hard that they spontaneously created radiation.
The physical concept of resonance surrounds us in everyday life. When youre sitting on a swing and want to go higher, you naturally start pumping your legs back and forth. You very quickly find the exact right rhythm to make the swing go higher. If you go off rhythm then the swing stops going higher. This particular kind of phenomenon is known in physics as a parametric resonance.
Your legs act as an external pumping mechanism. When they match the resonant frequency of the system, in this case your body sitting on a swing, they are able to transfer energy to the system making the swing go higher.
01:22
The Unfolding of a New Era in Robotics Lifeboat News: The Blog
Origami robots are autonomous machines that are constructed by folding two-dimensional materials into complex, functional three-dimensional structures. These robots are highly versatile. They can be designed to perform a wide range of tasks, from manipulating small objects to navigating difficult terrain. Their compact size and flexibility allow them to move in ways that traditional robots cannot, making them ideal for use in environments that are hard to reach.
Another notable feature of origami-based robots is their low cost. Because they are constructed using simple materials and techniques, they can be produced relatively inexpensively. This makes them an attractive option for many researchers and companies looking to develop new robotics applications.
There are many potential applications for origami robots. They could be used in search and rescue missions, where their small size and flexibility would allow them to navigate through rubble and debris. They could also be used in manufacturing settings, where their ability to manipulate small objects could be put to use in assembly lines.
00:54
Links 09/04/2023: Still Slow News for Easter Techrights
![]()
Contents
-
GNU/Linux
-
Audiocasts/Shows
-
Linux Voice Controller Teaser 4 Web Commands!
In this video, we look at how capable this little tool has become at navigating Chromium with many new commands and an upgraded Speech recognition Engine.
-
GNU World Order (Audio Show) GNU World Order 507
**qqc2-breeze-style** , **qqc2-desktop-style** , **rocs** , **sddm** , **sddm-
kcm** , **skanlite** from the **kde** software series of Slackware.
shasum -a256=2534394b7025909f67fe9f61446d4656e2ea8fbbfe1a6b1c3294f10d38522d1b
-
Tux Digital Sudo Show 61: Never the Year of the Linux Desktop
Brandon, Bill, and Neal get together and discuss a brief history of the Linux Desktop and the obstacles in the past. They also talk about what is going...
-
-
00:00
Tired of Web Scraping? Make The AI Do It Hackaday

[James Turk] has a novel approach to the problem of scraping web content in a structured way without needing to write the kind of page-specific code web scrapers usually have to deal with. How? Just enlist the help of a natural language AI. Scrapeghost relies on OpenAIs GPT API to parse a web pages content, pull out and classify any salient bits, and format it in a useful way.
What makes Scrapeghost different is how data gets organized. For
example, when instantiating scrapeghost one defines
the data one wishes to extract. For example:
from scrapeghost import SchemaScraper
scrape_legislators = SchemaScraper(
schema={
"name": "string",
"url": "url",
"district": "string",
"party": "string",
"photo_url": "url",
"offices": [{"name": "string", "address": "string", "phone": "string"}],
}
)
The kicker is that this format is entirely up to you! The GPT models are...
Sunday, 09 April
23:24
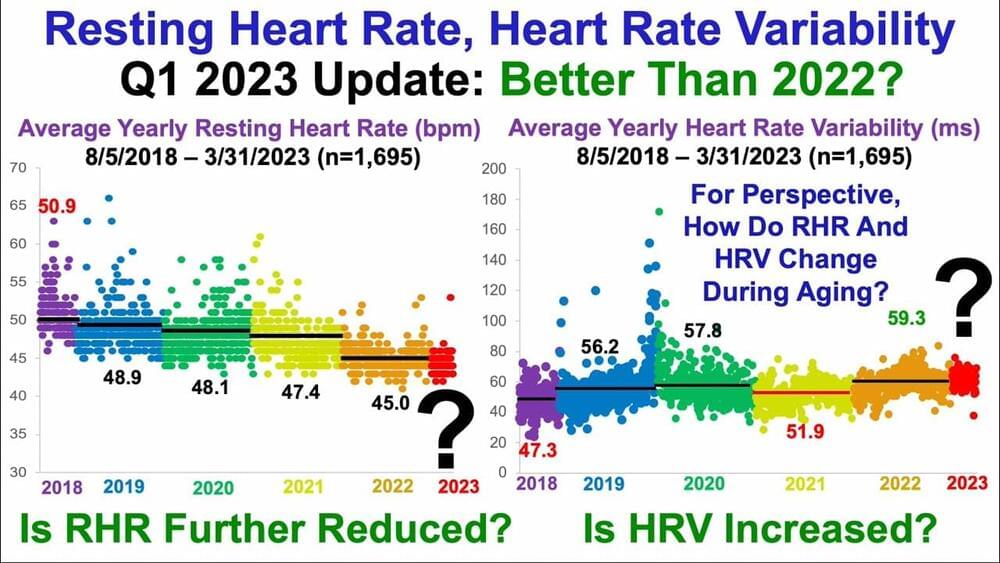
Resting Heart Rate, Heart Rate Variability: Is Q1 2023 Better Than 2022? Lifeboat News: The Blog
Join us on Patreon! https://www.patreon.com/MichaelLustgartenPhD
Discount Links:
NAD+ Quantification: https://www.jinfiniti.com/intracellular-nad-test/
Use Code: ConquerAging At Checkout.
Green Tea: https://www.ochaandco.com/?ref=conqueraging.
Oral Microbiome: https://www.bristlehealth.com/?ref=michaellustgarten.
Epigenetic Testing: https://bit.ly/3Rken0n.
Use Code: CONQUERAGING!
At-Home Blood Testing: https://getquantify.io/mlustgarten.
23:23
Why Physicists Think The Future Changes the Past Retrocausality Explained Lifeboat News: The Blog

Retrocausality, a mind-blowing quantum concept, proposes that future events impact the past. Challenging times traditional flow and exploring interconnected temporal relationships. Can the universe communicate with its past-self?
0:00 What is Retrocausality?
00:55 The Layers of the Universe.
02:17 The Universe Is Not Real.
04:32 The Role of Quantum Entanglement.
08:02 Does Time Travel Explain the Mysteries of the Universe?
#retrocausality #timetravel #quantummechanics.
Interested in what I do? Sign up to my Newsletter.
100% free forever and good for the environment.
https://drbenmiles.substack.com/
My Links:
https://www.instagram.com/drbenmiles/
A few people have asked so Ive added the info below. Some of these are affiliate links. If you make a purchase it doesnt cost you anything extra, but a percentage of the sale will help support this channel and my work to bringing entrepreneurship into science.
23:23
Fermi Paradox: The Vulnerable World Hypothesis Lifeboat News: The Blog

And exploration of the Vulnerable World Hypothesis solution to the Fermi Paradox.
And exploration of the possibility of finding fossils of alien origin right here on the surface of the earth.
My Patreon Page:
https://www.patreon.com/johnmichaelgodier.
My Event Horizon Channel:
23:19
Intel Lunar Lake Audio Support Coming For Linux 6.4 Phoronix
Going along with other Lunar Lake enablement work that has already been started for the upstream Linux kernel, the upcoming Linux 6.4 cycle will see HD audio support enabled for this successor to Arrow Lake...
22:49
Via: silenced.co.nz:
22:35
Improved Btrfs Scrub Code Readied For Linux 6.4, ~10% Faster Phoronix
The Btrfs scrub code that is used for going through file-system data/metadata to verify checksums and repairing damaged blocks is seeing some improvements come Linux 6.4...
21:07
LibreSSL 3.7.2 Released OpenBSD Journal
The LibreSSL project has announced a new stable release, LibreSSL 3.7.2. The announcement reads,
Subject: LibreSSL 3.7.2 Released From: Brent Cook <busterb () gmail ! com> Date: 2023-04-08 11:59:41 We have released LibreSSL 3.7.2, which will be arriving in the LibreSSL directory of your local OpenBSD mirror soon. This is the first stable release for the 3.7.x branch, also available with OpenBSD 7.3 It includes the following changes from the 3.6.x series * Portable changes - Moved official Github project to https://github.com/libressl/. - Build support for Apple Silicon. - Installed opensslconf.h is now architecture-specific. - Removed internal defines from opensslconf.h. - Support reproducible builds on tagged commits in main branch.
21:05
Samsung to Cut Memory Chip Output SoylentNews
Samsung Electronics Co. said it's cutting memory chip production after reporting its slimmest profit since the 2009 financial crisis, a significant step toward ending a supply glut that had cratered prices across the industry.
[...] Operating profit at the world's largest maker of memory chips plunged more than 95% to 600 billion won ($450 million) for the three months ended March, missing the average analyst estimate of 1.4 trillion won. Sales fell 19% to 63 trillion won.
[...] South Korea's largest company had resisted pulling back despite the downturn, in part to grab market share from rivals SK Hynix Inc. and Micron Technology Inc., which have been forced to cut output.
[...] Samsung's shares rose as much as 4.7% in the highest intraday jump in three months. Hynix shares surged as much as 6.7%. [...] The company had warned that earnings would fall in the first quarter on slowing sales. But memory prices tumbled more than anticipated because of sluggish demand for a wide range of electronics from smartphones to PCs, as consumers and companies navigated recession risks. Despite its post-Covid re-opening, China's market has also not bounced back as quickly as some anticipated. Samsung is estimated to have lost about $3 billion in its memory chip division.
[...] Prices of DRAM - a type of memory used to process data - are expected to fall in the current quarter by around 10%, according to Yuanta's Baik. That follows a roughly 20% slide in the previous three months and a more than 30% drop in the fourth quarter of last year. [...] Inventory at Samsung had swelled to 52.2 trillion won at the end of last year after the company maintained production despite a collapse in demand. The existing high inventory will take time to digest, said TrendForce Senior Vice President Avril Wu. "Slower-than-expected demand in the second half of 2023 will prolong the time required for inventory to get back to normal levels."
Read more of this story at SoylentNews.
21:00
Blinks Are Useful In VR, But Triggering Blinks Is Tricky Hackaday

In VR, a blink can be a window of opportunity to improve the users experience. Well explain how in a moment, but blinks are tough to capitalize on because they are unpredictable and dont last very long. Thats why researchers spent time figuring out how to induce eye blinks on demand in VR (video) and the details are available in a full PDF report. Turns out there are some novel, VR-based ways to reliably induce blinks. If an application can induce them, it makes it easier to use them to fudge details in helpful ways.
20:37
Intel Arrow Lake Enablement For Linux Looking To Get Underway Phoronix
While for many months now Intel's open-source driver engineers have been busy getting Meteor Lake Linux support squared away and there has even been some Lunar Lake activity for the Linux kernel going back to 2021, it looks now like their Arrow Lake enablement will be getting underway...
20:01
Picolibc 1.8.1 Released With Microblaze Support, Various Improvements Phoronix
Keith Packard has released Picolibc 1.8.1 as the newest update to his minimal/lightweight libc implementation...
18:43
IRC Proceedings: Saturday, April 08, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-080423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-080423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-080423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-080423.gmi
Over HTTP:
|
... |
18:00
Week in review: Western Digital network security incident, QNAP vulns, Patch Tuesday forecast Help Net Security
Heres an overview of some of last weeks most interesting news, articles, interviews and videos: Passbolt: Open-source password manager for security-conscious organizations In this Help Net Security interview, Kevin Muller, CEO at Passbolt, delves into the critical concerns linked to password usage, outlines how the Passbolt password manager guarantees the utmost level of security for businesses, highlights its features in the competitive landscape, sheds light on how Passbolt meets the distinct requirements of teams and More
The post Week in review: Western Digital network security incident, QNAP vulns, Patch Tuesday forecast appeared first on Help Net Security.
18:00
Debouncing for Fun and Mostly, Just for Fun Hackaday

In our minds and our computer screens, we live in an ideal world. Wires dont have any resistance, capacitors dont leak, and switches instantly make connections and break them. The truth is, though, in the real world, none of those things are true. If you have a switch connected to a lightbulb, the little glitches when you switch are going to be hard to notice. Hook that same switch up to a processor that is sampling it constantly, and you will have problems. This is the classic bane of designing microcontroller circuits and is called switch bounce. [Dr. Volt] covers seven different ways of dealing with it in a video that you can see below.
While you tend to think of the problem when you are dealing with pushbuttons or other kinds of switches for humans, the truth is the same thing occurs anywhere you have a switch contact, like in a sensor, a mechanical rotary encoder, or even relay contacts. You can deal with the problem in hardware, software, or both.
Adding a low-pass filter with a resistor and a capacitor is one method. But you might be surprised to find that some circuits will be happy with that and others wont. Why? [Dr. Volt] will show you on a scope.
Before you head to the comments to tell us that you can do it with a 555 timer, dont worry. He covers that too, as well as some software methods, including what to do if you are usi...
17:22
Geoffrey Hinton is considered a godfather of artificial intelligence, having championed machine learning decades before it became mainstream Lifeboat News: The Blog

As chatbots like ChatGPT bring his work to widespread attention, we spoke to Hinton about the past, present and future of AI.
CBS Saturday Mornings Brook Silva-Braga interviewed him at the Vector Institute in Toronto on March 1, 2023. #ai #interview #artificialintelligence #GeoffreyHinton #machinelearning #future
17:13
At Browserling and Online Tools, we love sales.
We just created a new automated Easter sales campaign.
Now each year, on the Easter Day, we show a 50% discount offer to all users who visit our site.
This year it runs today, next year on March 31, etc.
Here's how it looks.
Run Easter sales too and see you next time!
17:05
We've added another 15 new text tools catonmat.net
Team Browserling keeps shipping!
Three weeks ago we added 50 new text tool.
Two weeks ago we added 20 more tools
Last week we added 15 more text tools.
And today we added another 15 tools to our Online Text Tools collection.
I have done my job and now it's Google's turn to index them and rank them well.
Here are the new text tools:
- Anonymize Text
- Generate Fake Text
- Generate Text of Certain Length
- Add Text Line Numbers
- Remove Text Line Numbers
- Find Top Words in Text
- Find Top Letters in Words
- Filter Text Lines
- Filter Words
- Filter Sentences
- Filter Paragraphs
- Reverse Text Lines
- Reverse Words
- Reverse Sentences
- Reverse Paragraphs
Next week we'll add even more tools. See you then!
16:23
Somebody Wants to Copyright a Rhythm Get Ready for the Dembow Tax If They Succeed SoylentNews
Somebody wants to copyright a rhythm get ready for the dembow tax if they succeed:
One of the most pernicious effects of today's copyright maximalism is the idea that every element of a creative work has to be owned by someone, and protected against "unauthorised" that is, unpaid use by other artists. That goes against several thousand years of human creativity, which only exists thanks to successive generations of artists using and building on our cultural heritage. The ownership model of art is essentially selfish: it seeks to maximise the financial gains of one creator, at the expense of the entire culture of which they are part. A good example of this clash of interests can be seen in yet another lawsuit in the music industry. This time, somebody is trying to copyright a rhythm:
The [Fish Market song] track featured the first known example of what would come to be known as a "dembow" rhythm the percussive, slightly syncopated four-to-the-floor beat that travelled from reggae to become the signature beat of reggaeton, today the world-conquering sound of Latin American pop.
Now, more than 30 years after Fish Market was released, Steely & Clevie Productions is suing three of reggaeton's most celebrated hitmakers El Chombo, Luis Fonsi and Daddy Yankee for what they characterise as unlawful interpolation of Fish Market's rhythm (or "riddim"), and are seeking the credit and royalties they say they deserved from the start.
Read more of this story at SoylentNews.
15:42
Russian submarines off U.S. east coast spark Cold War comparisons Lifeboat News: The Blog
The growing presence of Russian submarines off the coast of the United States has sparked Cold War comparisons from military observers and a retired NATO admiral.
Russian President Vladimir Putin has been set on expanding Russias underwater capabilities. Over the past several years, Moscow has been producing a series of submarines that have the capability to reach the most critical targets in the U.S. or continental Europe.
15:42
China sends 71 warplanes near Taiwan as military drills kick off Lifeboat News: The Blog
China kicked off three days of military drills and combat readiness patrols around the island on Saturday, just days after the Taiwanese president met the U.S. House speaker.
15:42
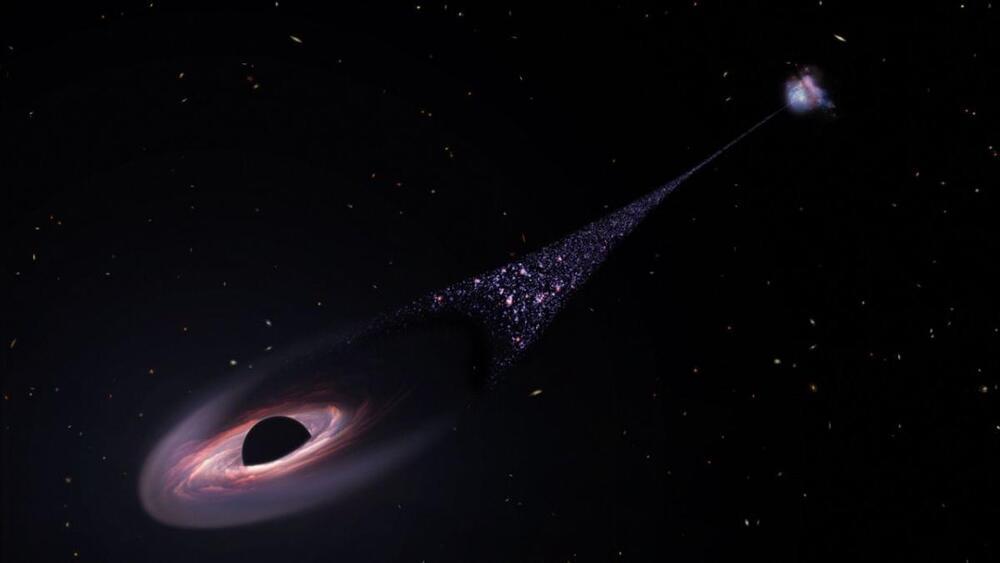
Runaway supermassive black hole is hurtling through space followed by tail of infant stars (video) Lifeboat News: The Blog
This could be some sorta civilization moving itself in space.
The Hubble Space Telescope has spotted a runaway supermassive black hole racing through space followed by a tail of infant stars 200,000 light-years long.
15:07
Links 09/04/2023: Easters Slow New Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Pseudo-Open Source
- Security
- Defence/Aggression
- Environment
- Misinformation/Disinformation/Propaganda
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Fentanylware (TikTok)
- Monopolies
- Gemini* and Gopher
-
GNU/Linux
-
Server
-
Hackaday Web Server Like Its 1998 With This Restored Internet Appliance
Hackaday readers fit into two broad categories: those who experienced the wild and woolly early days of the Internet, and those who are jealous that they missed it...
-
-
15:00
Homemade Scope Does Supercapacitor Experiments Hackaday

Weve always been a little sad that supercapacitors arent marked with a big red S on a yellow background. Nevertheless, [DiodeGoneWild] picked up some large-value supercapacitors and used his interesting homemade oscilloscope to examine how they worked. You can watch what he is up to in his workshop in the video below.
Supercapacitors use special techniques to achieve very high capacitance values. For example, the first unit in the video is a 500 F capacitor. Thats not a typo not microfarads or even millifarads a full 500 Farads. With reasonable resistance, it can take a long time to charge 500F, so it is easier to see the behavior, especially with the homemade scope, which probably wont pick up very fast signals.
For example, A 350 mA charging current takes about an hour to bring the capacitor up to 2.6 V, just under its maximum rating of 2.7 V. Supercapacitors usually have low voltage tolerance. Their high capacity makes them ideal for low-current backup applications where you might not want a rechargeable battery because of weight, heat, or problems with long-term capacity loss.
The real star of the video, though, is the cast of homemade test equipment, including the oscilloscope, a power supply, and a battery analyzer. To be fair, he also has some store-bought test gear, too, and the results seem to match well.
Supercapacitors are one of those things that you dont need until you do. If you havent had a cha...
12:00
Revisiting Borland Turbo C and C++ Hackaday

Looking back on what programming used to be like can be a fascinatingly entertaining thing, which is why [Tough Developer] decided to download and try Turbo C 1.0 is a doozy as it was released in 1987 two years before the C89 standardization that brought us the much beloved ANSI C that so many of us spent the 90s with. Turbo C++ 1.0 is from 1991, which precedes the standardization of C++ in 1998. This means that both integrated development environments (IDEs) provide a fascinating look at what was on the cutting edge in the late 80s and early 90s.
11:58
3 Months Later Still No Letters From NOW: Pensions (False Promises, Even From Managers) schestowitz.com
Summary: The crimes of Sirius Open Source were brought to the attention of NOW: Pensions a long time ago. But its still failing to fulfil a simple promise or, in other words, it lied (3 people, including a manager, lied).
A few days ago we shared a response from a manager at NOW: Pensions. But nothing was sent by post.
I hope this helps to settle your concerns, he said, but
he did not actually do what his colleague, another manager, said
would happen. Please send the full letter, as promised, to 1)
my wife 2) myself, I said, as promised by [redacted
name]
as promised by [another redacted name]
as promised by [manager's redacted name]
several times since February. We need this obligation in writing.
To make matters worse, the company is trying to seed doubt, gaslight many victims, and make veiled threats against people who speak out facts.I already have several of things on record (audio), demonstrating the promises were made. Those were never fulfilled, and very much by intention. The state of the pension industry isnt good and their handling of pension fraud is rather revealing. Sirius found itself a convenient accomplice.
To make matters worse, the company is trying to seed doubt, gaslight many victims, and make veiled threats (by proxy) against people who speak out facts. NOW: Pensions has not replied to my message yet, but its a holiday here.
11:42
We Can Use Stem Cells to Make Embryos. How Far Should We Go? SoylentNews
[...] These "synthetic embryos" can be made without the direct contribution of egg or sperm cells. Because they're not "real" embryos, some have argued that the same restrictions don't apply.
Embryos made from stem cells, rather than an egg and sperm, appear to generate a short-lived pregnancy-like response in monkeys.
Recent advances are allowing scientists to create embryo-like structures that look more and more like the real thing. Just this week, scientists in China described how they developed structures called blastoids for 17 days in the lab. They even managed to get some of them to implant in the uteruses of monkeys and trigger the very first signs of pregnancy.
The blastoids didn't survive for very long, probably because researchers haven't quite figured out how best to mimic what happens during the development of a conventional embryo. But most believe that it's just a matter of time. If we can eventually get stem cells to form a viable embryo, a functional fetus, or even a baby, should we treat blastoids in the same way we treat embryos?
Perhaps the bigger question rests on how embryo-like these stem-cell-derived structures are. For some scientists, it's a catch-22 situation. If the blastoids look too much like embryos, then many believe research with them should be restricted in the same way that we control work on human embryos.
But if they don't look enough like embryos, then there's no point in using them for research, says Chuva de Sousa Lopes. "At the moment, it's so difficult to understand how close they are, or how different they are," she says.
Read more of this story at SoylentNews.
11:39
NOW: Pensions Unable to Deliver Letters of Assurance After 3 Months of False Promises From 3 Staff, Including Management Techrights
Summary: The crimes of Sirius Open Source were brought to the attention of NOW: Pensions a long time ago. But its still failing to fulfil a simple promise or, in other words, it lied (3 people, including a manager, lied).
A few days ago we shared a response from a manager at NOW: Pensions. But nothing was sent by post.
I hope this helps to settle your concerns, he said, but
he did not actually do what his colleague, another manager, said
would happen. Please send the full letter, as promised, to 1)
my wife 2) myself, I said, as promised by [redacted
name]
as promised by [another redacted name]
as promised by [manager's redacted name]
several times since February. We need this obligation in writing.
To make matters worse, the company is trying to seed doubt, gaslight many victims, and make veiled threats against people who speak out facts.I already have several of things on record (audio), demonstrating the promises were made. Those were never fulfilled, and very much by intention. The state of the pension industry isnt good and their handling of pension fraud is rather revealing. Sirius found itself a convenient accomplice.
To make matters worse, the company is trying to seed doubt, gaslight many victims, and make veiled threats (by proxy) against people who speak out facts. NOW: Pensions has not replied to my message yet, but its a holiday here.
11:23
Another Round of Layoffs at Microsoft Techrights
Summary: Contrary to lies told by Microsoft, there are far more than 10,000 Microsoft workers being laid off, with almost 3,000 laid off already in just one location
10:18
How to Create and Manage Groups on iPhone HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
Youre sitting with your iPhone in hand, gazing at the screen with annoyance, fury, and helplessness. You need
This is a post from HackRead.com Read the original post: How to Create and Manage Groups on iPhone
09:00
Web Server Like Its 1998 with This Restored Internet Appliance Hackaday

Hackaday readers fit into two broad categories: those who experienced the wild and woolly early days of the Internet, and those who are jealous that they missed it. And its safe to say that both groups will get something out of this aggressively Web 1.0 retro experience, courtesy of a server that was actually part of it.
This comes to us via The Serial Port, a virtual museum dedicated to 90s technology, where curators [Mark] and [Ben] managed to find a pair of Cobalt RaQ 3 servers from the late 1990s. The RaQ was the first true Internet appliance, designed to be as simple as possible to set up and operate. If you wanted to get your small business online, machines like these were just the ticket. They were designed to be as plug-and-play as possible, and they did a pretty good job of it, at least for the time.
08:26
Phishers Now Actively Automating Scams with Telegram HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
In addition to phishing activities, researchers have observed a rise in Telegram channels being used to sell online banking credentials.
This is a post from HackRead.com Read the original post: Phishers Now Actively Automating Scams with Telegram
08:15
CISA adds Veritas Backup Exec flaws to its Known Exploited Vulnerabilities catalog Security Affairs
US CISA has added Veritas Backup Exec flaws, which were exploited in ransomware attacks, to its Known Exploited Vulnerabilities catalog.
U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added the following five new issues to its Known Exploited Vulnerabilities Catalog:
- CVE-2021-27876 Veritas Backup Exec Agent File Access Vulnerability
- CVE-2021-27877 Veritas Backup Exec Agent Improper Authentication Vulnerability
- CVE-2021-27878 Veritas Backup Exec Agent Command Execution Vulnerability
- CVE-2019-1388 Microsoft Windows Certificate Dialog Privilege Escalation Vulnerability
- CVE-2023-26083 Arm Mali GPU Kernel Driver Information Disclosure Vulnerability
This week Mandiant researchers reported that an affiliate of the ALPHV/BlackCat ransomware gang, tracked as UNC4466, was observed exploiting the three above vulnerabilities in the Veritas Backup solution to gain initial access to the target network.
Unlike other ALPHV affiliates, UNC4466 doesnt rely on stolen credentials for initial access to victim environments. Mandiant researchers first observed this affiliate targeting Veritas issues in the wild on October 22, 2022.
The CVE-2023-26083 flaw in the Arm Mali GPU driver is chained with other issues to install commercial spyware, as reported by Googles Threat Analysis Group (TAG) in a recent report.
According to Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities, FCEB agencies have to address the identified vulnerabilities by the due date to protect their networks against attacks exploiting the flaws in the catalog.
Experts recommend also private organizations review the ...
06:53
Leak Reveals AMD's 'Strix Point' APUs With 16 CPU Cores and 3 GHz+ IGPU SoylentNews
With Zen 5 CPU and RDNA 3+ iGPU, Strix Point could be a game changer:
At CES 2023, AMD announced its Phoenix-HS APUs featuring Zen 4 CPUs and RDNA 3 iGPUs. The company is expected to follow that with the 'Strix Point' APUs, sporting Zen 5 CPUs and RDNA 3+ iGPUs. According to AMD's official roadmap, the Strix Point chips will launch sometime in 2024, although the exact ETA remains a mystery for now.
Almost a year after AMD officially teased its 'Strix Point' APUs, popular YouTube channel RedGamingTech has shared many interesting details about the upcoming hardware. According to the video, the flagship Strix Point APU will come with 16 cores, including 8 big Zen 5 and 8 smaller Zen 4D cores, alongside 32MB of L3 cache.
On the graphics side, the chip is expected to feature an RDNA 3+ iGPU with 8 Work Group Processors (WGP). The video also suggests that the iGPU on the most powerful Strix Point APU would have clock speeds of more than 3GHz.
If the reported specs hold up, it would be a little disappointing, as an earlier video from the channel claimed that Strix Point's RDNA 3+ iGPU could have 12 WGP/24 Compute Units (CU) with around 9 TFLOPS of FP32 precision performance.
Meanwhile, the mid-range Strix Point SKU will reportedly have 4x Zen 5 and 8x Zen 4D cores, paired with 16MB of L3 cache and 4 RDNA 3+ WGPs. Finally, the entry-level chip is said to come with up to 6 cores, including 2x Zen 5 and 4x Zen 4D. They are also tipped to have 8 MB of L3 cache and a 2 WGP iGPU.
The core count, cache and WGPs will not be the only differences between the high-end and entry-level Strix Point APUs. As per the video, the top-end chip in the lineup will be fabricated using TSMC's 3 nm process, while the other two SKUs will use the 4 nm process. The chips are also expected to have a powerful memory controller with support for DDR5-6400 or LPDDR5X-8533 RAM.
Read more of this story at SoylentNews.
06:10
Tesla Employees Allegedly Shared Customers Private Videos and Photos HackRead | Latest Cybersecurity and Hacking News Site
The use of cameras on Tesla vehicles has come under scrutiny after reports revealed that some employees have
This is a post from HackRead.com Read the original post: Tesla Employees Allegedly Shared Customers Private Videos and Photos
06:00
Russias New Mystery Shortwave Station Hackaday

The Buzzer, also known as UVB-76 or UZB-76, has been a constant companion to anyone with a shortwave radio tuned to 4625 kHz. However, [Ringway Manchester] notes that there is now a second buzzer operating near in frequency to the original. Of course, like all mysterious stations, people try to track their origin. [Ringway] shows some older sites for the Buzzer and the current speculation on the current transmitter locations.
Of course, the real question is why? The buzzing isnt quite nonstop. There are occasional voice messages. There are also jamming attempts, including one, apparently, by Pac Man.
Some people think the new buzzer is an image, but it doesnt seem to be the same signal. The theory is that the buzzing is just to keep the frequency clear in case it is needed. However, we wonder if it isnt something else. Compressed data would sound like noise. Other theories are that the buzzing studies the ionosphere or that it is part of a doomsday system that would launch nuclear missiles. Given that the signal has broken down numerous times, this doesnt seem likely.
Whats even stranger is that occasional background voices are audible on the signal. That implies that buzzing noise isnt generated directly into the transmitter but is a device in front of a microphone.
Weve speculated on the buzzer and the jamming efforts around it...
04:20
Copyright Trolls: Anatomy of a Troll Attack on Techrights Techrights
Video download
link | md5sum
4703f643997fd14e44657cb8059f0e4a
Copyright Troll Versus Techrights
Creative Commons Attribution-No Derivative Works 4.0
Summary: Patent trolling from Germany/Czech Republic (where the EPOs President and his facilitator are based) explained by exposing the letters; weve since then received more copyright threats (frivolous lawsuit threats) from perpetrators of corruption at the EPO and EU (UPC), so there might be a pattern here
LESS THAN 4 days ago we said that this coming weekend, i.e. today, wed be covering the copyright trolling [1, 2] we were subjected to last summer. The more recent copyright lawsuit threats [1, 2] the ones which are definitely connected to the EPO make it more relevant, also in light of threats weve received from Benot Battistelli and his ilk since 2015.
Remember that this very same Antnio Campinos was sending applicants money to Minsk, Belarus, in effect funding the devastating war on Ukrainian civilians.The ab...
03:48
Links 08/04/2023: OpenShot 3.1 and Mesa 23.0.2 Released Techrights
![]()
Contents
-
GNU/Linux
-
Linux Links Linux Around The World: USA Idaho
We cover user groups that are running in the US state of Idaho. This article forms part of our Linux Around The World series.
-
Desktop/Laptop
-
Bryan Lunduke System76 building a brand new laptop, designed in-house
Built at their Denver, Colorado factory. Which is pretty cool.
-
-
Graphics Stack
-
Free Desktop mesa 23.0.2
Hi list, HEre is the slightly late next release. We're basically caught up to where we should be at this poi...
-
-
03:36
Z-Library Plans to Let Users Share Physical Books Through Z-Points TorrentFreak
 With more than 12 million books in its archive,
Z-Library advertised itself as the largest repository of pirated
books on the Internet.
With more than 12 million books in its archive,
Z-Library advertised itself as the largest repository of pirated
books on the Internet.
The site has millions of regular readers who find a wealth of free knowledge and entertainment at their fingertips.
This success was briefly interrupted late last year when the U.S. Government seized the sites main domain names. The enforcement action also led to the arrest of two alleged Russian operators of the site, who now find themselves at the center of a criminal investigation.
A crackdown of this magnitude usually marks the end of a pirate site, but Z-Library appears to be going in the opposite direction. The site has made a full comeback with a more censorship-resistant setup and recently collected tens of thousands of dollars in donations.
Next Up: Sharing Paper Books
In a new message, posted this week, Z-Library thanks its userbase for their generous contributions, noting that it secured all the necessary funds to ensure continued development. Apparently, this includes support for offline sharing.
In addition to offering millions of ebooks, Z-Library says that its working on a new service that will help users to share physical copies with each other.
Books you have read should not gather dust on your shelf instead, they can get a second life in the hands of new readers! This helps to preserve the literary heritage and spread the knowledge and ideas contained in books to more people, they write.
Z-Points
The book lending concept, commonly known as a library, is a few hundred years old already, but Z-Library will upgrade both scale and reach. The idea is to create a global market with dedicated pick-up points for user-donated books.
[W]e want to organize Z-Points collection and storage points for books that will be the link between those who share their books and those who need them.
Book owners who are willing to share them with other users can send books to the nearest Z-Point in their region. And those who need books stored in these points will be able to receive them for their use.
...
02:37
Raytheon Director and His Wife Killed in Plane Crash cryptogon.com
Via: Daily Mail: Two couples from Indiana were killed when their plane crashed off the coast of Venice, Florida after they flew in to have dinner with friends. The single-engine plane crashed near the Venice Fishing Pier soon after takeoff on Wednesday evening on its way back to St. Petersburg, Florida. Jeff Lumpkin, 64, an []
02:30
Ukrainians Say No to Microsoft Techrights
Microsoft has lost grip, so it is instead bribing officials for a "feast" on tax money
Summary: Despite the Ukraine-Microsoft graft (Azure deployment/outsourcing, in effect another hugely costly "defence"-themed bailout from taxpayers to Microsoft) it seems clear that Ukrainians themselves say no to Microsoft and many have moved to GNU/Linux; the majority of Ukrainians do not use Windows as of this month
02:08
Round-Up: ChatGPT, Bard, etc - We Did Ask What Could Go Wrong, Didn't We? SoylentNews
OpenAI threatened with landmark defamation lawsuit over ChatGPT false claims
A spokesperson for Gordon Legal provided a statement to Ars confirming that responses to text prompts generated by ChatGPT 3.5 and 4 vary, with defamatory comments still currently being generated in ChatGPT 3.5. Among "several false statements" generated by ChatGPT were falsehoods stating that Brian Hood "was accused of bribing officials in Malaysia, Indonesia, and Vietnam between 1999 and 2005, that he was sentenced to 30 months in prison after pleading guilty to two counts of false accounting under the Corporations Act in 2012, and that he authorised payments to a Malaysian arms dealer acting as a middleman to secure a contract with the Malaysian Government." Because "all of these statements are false," Gordon Legal "filed a Concerns Notice to OpenAI" that detailed the inaccuracy and demanded a rectification. "As artificial intelligence becomes increasingly integrated into our society, the accuracy of the information provided by these services will come under close legal scrutiny," James Naughton, Hood's lawyer, said, noting that if a defamation claim is raised, it "will aim to remedy the harm caused" to Hood and "ensure the accuracy of this software in his case.")
It was only a matter of time before ChatGPTan artificial intelligence tool that generates responses based on user text promptswas threatened with its first defamation lawsuit. That happened last month, Reuters reported today, when an Australian regional mayor, Brian Hood, sent a letter on March 21 to the tool's developer, OpenAI, announcing his plan to sue the company for ChatGPT's alleged role in spreading false claims that he had gone to prison for bribery.
To avoid the landmark lawsuit, Hood gave OpenAI 28 days to modify ChatGPT's responses and stop the tool from spouting disinformation.
Read more of this story at SoylentNews.
02:00
What Flight 50 Means for the Ingenuity Mars Helicopter IEEE Spectrum

JPLs Ingenuity helicopter is preparing for the 50th flight of its 5-flight mission to Mars. Flight 49, which took place last weekend, was its fastest and highest yetthe little helicopter flew 282 meters at an altitude of 16 meters, reaching a top speed of 6.50 meters per second. Not a bad performance for a tech demo that was supposed to be terminated two years ago.
From here, things are only going to get more difficult for Ingenuity. As the Perseverance rover continues its climb up Jezero craters ancient river delta, Ingenuity is trying its best to scout ahead. But, the winding hills and valleys make it difficult for the helicopter to communicate with the rover, and through the rover, to its team back on Earth. And there isnt a lot of time or room to spare, because Ingenuity isnt allowed to fly too close to Perseverance, meaning that if the rover ever catches up to the helicopter, the helicopter may have to be left behind for the rovers own safety. This high-stakes race between the helicopter scout and the science rover will continue for kilometers.
Two years in, 10 kilometers flown, and were
well over an hour now in the skies of Mars.
Teddy Tzanetos, NASA
For the Ingenuity team, this new mode of operation was both a challenge and an opportunity. This was nothing new for folks who have managed to keep this 30-day technology demo alive and healthy and productive for years, all from a couple hundred million kilometers away. IEEE Spectrum spoke with Ingenuity Team Lead Teddy Tzanetos at JPL last week about whether flying on Mars is ever routine, how they upgraded Ingenuity for its extended mission, and what the helicopters success means for the future of airborne exploration and science on Mars.
IEEE Spectrum: Is 50 flights on Mars a milestone for you folks, or are things routine enough now that youre looking at it as just another flight?
Teddy Tzanetos: Its hugely meaningful. Well come back to the routine question in a second, but its very meaningful for all of us. When we hit 10 and then 25 it was big, but 50 is a pretty serious number now that were 10X our initial flight count. Two years in, 10 kilometers flown, and were well over an hour now in the skies of Mars. So hitting flight 50, its a big thingwere probably going to s...
01:53
The Sensitive Ukraine Documents Werent Grabbed From Social Control Media, Just Leaked There (Microsoft Azure, Windows, and/or Rogue Insider Most Probable Factor to Blame) Techrights
It also appeared in Microsofts Minecraft (proprietary) first, not Telegram or Twitter; Azure has many security holes and permission/access problems

Summary: Microsoft-friendly media seems to be running
somewhat of an intentionally deceitful campaign
blaming the wrong companies or misplacing liability; the war
documents that leaked didnt come from Telegram or Twitter (Social
Control Media) but servers we suspect
were hosted by Microsoft, a notorious war grifter in Ukraine
(profiting from mayhem and contributing to the
mayhem* at both sides**)
_____
* 2022
report, citing this
one: The Telegraph tries to pin the blame for the lack of
service on the headline-grabbing Ukraine war, saying that it is due
to the company agreeing to host Ukraines entire government on its
remote servers.
** Also 2 days ago in Compliance Week and elsewhere:
01:23
Will You Become a Computer Before You Die? | Unveiled Lifeboat News: The Blog

Is THIS how well all live forever?? Join us, and find out!
Subscribe https://wmojo.com/unveiled-subscribe.
In this video, Unveiled takes a closer look at a new rival to AI and quantum computing OI Organoid Intelligence! Using tiny versions of our own brains, scientists are powering a new digital revolution! But could it ALSO mean that, one day, we all live forever??
This is Unveiled, giving you incredible answers to extraordinary questions!
Find more amazing videos for your curiosity here:
6 Scientific Breakthroughs Predicted For Your Lifetime https://youtu.be/wGKj-3AfxdE
Did This AI Just SOLVE Quantum Physics https://youtu.be/PN_D3e3LdQQ
0:00 Intro.
0:38 Future Computers.
2:20 Organoid Intelligence Biocomputers.
4:29 What Will Happen Next?
5:20 Chance to Live Forever?
7:11 Conclusions.
01:22
The MK-II Aurora spaceplane reaches a major milestone with rocket flight Lifeboat News: The Blog

Dawn Aerospace.
In case you have not heard of them, Dawn Aerospace is one of the fastest-growing private space companies in the world, with clients from Europe, Asia, and the United States. They call themselves a green in-space propulsion supplier, and they also, to date, have around 11 operational satellites currently in orbit.
01:22
Physicists Simulated a Black Hole in The Lab, And Then It Started to Glow Lifeboat News: The Blog
A synthetic analog of a black hole could tell us a thing or two about an elusive radiation theoretically emitted by the real thing.
Using a chain of atoms in single-file to simulate the event horizon of a black hole, a team of physicists observed the equivalent of what we call Hawking radiation particles born from disturbances in the quantum fluctuations caused by the black holes break in spacetime.
This, they say, could help resolve the tension between two currently irreconcilable frameworks for describing the Universe: the general theory of relativity, which describes the behavior of gravity as a continuous field known as spacetime; and quantum mechanics, which describes the behavior of discrete particles using the mathematics of probability.
01:22
Early KDE Plasma 6 Development State: "It's Still Rough, But It's Usable" Phoronix
KDE developer Nate Graham is out with his weekly recap of notable KDE desktop developments for this first week of April...
01:11
4 Ways to Put Lasers on Silicon IEEE Spectrum

Photonic integrated circuits, which combine a collection of optoelectronic functions on a single chip, are an increasingly common part of everyday life. They are used in high-speed optical transceivers that link server racks in data centers, including the one used to deliver the IEEE Spectrum website, in lidars to keep self-driving cars on track, and in spectrometers to spot chemicals in the atmosphere, among many other applications. All these systems have grown less expensive and, in some cases have become economically feasible, by making most of the IC with silicon fabrication technologies.
Engineers have been able to integrate nearly every important optical function, including the essentials of modulation and detection, on silicon photonic chips, except for one: light emission. Silicon itself doesnt do that efficiently, so semiconductors made of so-called III-V materials, named for the place of their constituents on the periodic table, are typically used to make separately packaged components to produce light.
If you can live with an external laser diode in your design, theres no issue. But several factors have recently been pushing engineers to integrate lasers with silicon photonics. There may be, for example, no space for a separate light source. Tiny devices meant to be implanted in the body to monitor, for example, blood-sugar levels, might face this problem. Or an applications cost might call for closer integration: When you can fit hundreds or thousands of lasers on a single silicon wafer, you will end up with a lower cost and often higher reliability than when you need to connect separate chips.
There are many ways to achieve this tighter integration of lasers and silicon. Working at Imec, a Belgium-based nanoelectronics R&D center, we are currently pursuing four basic strategies: flip-chip processing, microtransfer printing, wafer bonding, and monolithic integration. What follows is a guide to how these approaches work, their level of scalability and maturity, and their pros and cons.
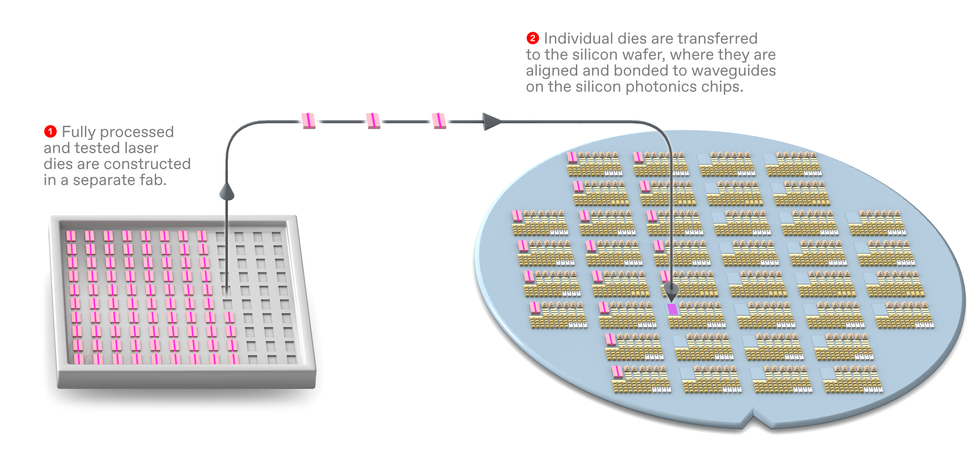 In flip-chip
bonding, laser...
In flip-chip
bonding, laser...
00:51
Playing Games in Gemini: The Story of SpellBinding and More Techrights
Video download
link | md5sum
8d196c2e2e88e279fc4334d75dd299bb
SpellBinding in Gemini
Creative Commons Attribution-No Derivative Works 4.0
Summary: A puzzle/game called SpellBinding has been going on for years at Geminispace and today we take a closer (but quick) look at it
Games aren't a new thing in Geminispace and we already covered some examples in the past, except we probably neglected to mention SpellBinding, which has daily riddles (this is todays).
Its how the Web used to be. Back when it was safe (secure) to useIn spite of its growth, many still bash Gemini because it does not do JavaScript and cannot impose layouts (styles) on visitors, instead allowing them to choose their own. In Gemini it is possible to implement and run programs, games etc. A lot of the heavy lifting is done at the server side, not the client side. This is a good thing. Its how the Web used to be. Back when it was safe (secure) to use
The above video shows a number of other Gemini pages from today, aside from our own. There may be millions of Gemini pages out there already. Its difficult to keep count. The developer of the client used above is back to working on it. Gemini has maintained growth momentum so far this year.
00:37
Taiwanese PC Company MSI Falls Victim to Ransomware Attack The Hacker News
Taiwanese PC company MSI (short for Micro-Star International) officially confirmed it was the victim of a cyber attack on its systems. The company said it "promptly" initiated incident response and recovery measures after detecting "network anomalies." It also said it alerted law enforcement agencies of the matter. That said, MSI did not disclose any specifics about when the attack took place
00:00

We all make things. Sometimes we make things for ourselves, sometimes for the broader hacker community, and sometimes we make things for normal folks. Its this last category where it gets tricky, and critical. I was reminded of all of this watching Chris Combs excellent Supercon 2022 talk on how to make it as an artist.
But Im not making art! I hear you say? About half of Chris talk is about how he makes his tech art worry-free for galleries to install, and that essentially means making it normie-proof making sure it runs as soon as the power is turned on, day in, day out, without hacker intervention, because venues hate having you on site to debug. As Tom joked in the podcast, its a little bit like designing for space: its a strange environment, you cant send out repair teams, and it has to have failsafes that make sure it works.
What is striking about the talk is that there is a common core of practices that make our hardware projects more reliable, whatever their destination. Things like having a watchdog thatll reboot if it goes wrong, designing for modularity whenever possible, building in hanging or mounting options if thats relevant, and writing up at least a simple, si...
Saturday, 08 April
23:23
AI Video Generators Are Nearing a Crucial Tipping Point Lifeboat News: The Blog

Memes made with AI video generator algorithms are suddenly everywhere. Their sudden proliferation may herald an imminent explosion in the technologys capability.
23:23
What is the Marburg virus? WHO confirms outbreak of the deadly viral disease in Equatorial Guinea and Tanzania Lifeboat News: The Blog
The World Health Organization confirmed an outbreak of the virus in Equatorial Guinea and Tanzania earlier this year. Authorities first issued a warning for Equatorial Guinea in February following a series of deaths in early January. The Ministry of Health of Tanzania then announced its own outbreak in late March.
There have been 14 confirmed cases in Equatorial Guinea since the epidemic began, with 10 of those patients dying, according to the CDC An outbreak among a group of fisherman in Tanzania produced eight confirmed cases of the viral fever, five of which were fatal, the CDC said.
The CDC on Thursday warned doctors to watch for possible imported cases and patients exhibiting symptoms that include fever, fatigue, and blood-strained vomit and diarrhea. There have not been any reported cases of Marburg virus thus far in the US and the CDC said the risk of imported cases is relatively low.
23:23
Samsung employees reportedly leaked sensitive info on ChatGPT Lifeboat News: The Blog
Samsung Electronics employees interacting with artificial intelligence tool ChatGPT accidentally leaked company information, according to an exclusive report by the South Korean outlet The Economist.
Employees in the companys semiconductor division told the news outlet that corporate data was leaked on three separate occasions.
The website said the leaks came within 20 days after the South Korean conglomerate had lifted a ban on the chatbot.
23:23
Is Artificial Intelligence Better at Assessing Heart Health? Lifeboat News: The Blog
Who can assess and diagnose cardiac function best after reading an echocardiogram: artificial intelligence (AI) or a sonographer?
23:22
Sparks of AGI: early experiments with GPT-4 Lifeboat News: The Blog

CSAIL lectures with Sebastien Bubeck (April 6,2023) The new wave of AI systems, ChatGPT and its more powerful successors, exhibit extraordinary capabilities across a broad swath of domains. In light of this, we discuss whether artificial INTELLIGENCE has arrived.
23:22
How a worms embryonic cells change its development potential Lifeboat News: The Blog
Researchers have spotted how specific proteins within the chromosomes of roundworms enable their offspring to produce specialized cells generations later, a startling finding that upends classical thinking that hereditary information for cell differentiation is mostly ingrained within DNA and other genetic factors.
The Johns Hopkins University team reports for the first time the mechanisms by which a protein known as histone H3 controls when and how worm embryos produce both highly specific cells and pluripotent cells, cells that can turn certain genes on and off to produce varying kinds of body tissue. The details are published today in Science Advances.
The new research could shed light on how mutations associated with these proteins influence various diseases. In children and young adults, for example, histone H3 is closely associated with various cancers.
23:22
Gods in the machine? The rise of AI may result in new religions Lifeboat News: The Blog

The increasing presence of artificial intelligence could lead to a new wave of AI-worshippers enough to form an organized religion.
23:00
10 Graphs That Sum Up the State of AI in 2023 IEEE Spectrum

The Stanford Institute for Human-Centered Artificial Intelligence (HAI) has assembled a years worth of AI data providing a comprehensive picture of todays AI world, as they have done annually for six years. And I do mean comprehensivethis years report came in at 302 pages. Thats a nearly 60 percent jump from the 2022 report, thanks in large part to the 2022 boom in generative AI demanding attention and an increasing effort to gather data on AI and ethics.
For those of you as eager to pour through the entire 2023 Artificial Intelligence Index Report as I was, you can dive in here. But for a snapshot of the entire set of findings, below are 10 charts capturing essential trends in AI today.
Large language models dont come cheap
While the power of large language models, like ChatGPT, has increased dramatically, the price of training such models has increased dramatically as well. And of all machine learning systems, language models are sucking up the most computing resources.
Carbon costs are also high
While its not easy to estimate carbon emissions of an AI system, the AI Index team gave it their best shot, considering the number of parameters in a model, the energy efficiency of data centers, and the type of power generation used to deliver electricity. It concluded that a training run for even the most efficient of the four models considered, BLOOM, emitted more carbon than the average U.S. resident uses in a year.
Its the governments turn to step up
For the first time in a decade, private AI investment decreased, falling about a third from 2021 to $189.6 billion. The reason isnt clear. Says Ray Perrault, co-director of the...
22:29
New Money Message Ransomware Gang Hits MSI, Threatens of Data Leak HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
The Money Message ransomware group has reportedly demanded a ransom of $4 million from MSI.
This is a post from HackRead.com Read the original post: New Money Message Ransomware Gang Hits MSI, Threatens of Data Leak
21:33
How to Update Copyright: Nigeria Shows the Way for Africa and the World SoylentNews
How to update copyright: Nigeria shows the way for Africa and the world:
This battle over [copyright] moves to adopt an open-ended fair dealing based on the US approach, rather than one with a limited list of permitted exceptions and limitations, is an important one that is happening all around the world. Open-ended fair use is clearly more helpful for dealing with developments in technology that were never envisaged when old copyright laws were drawn up. They allow at least a basic flexibility in the way that copyright is applied, for example online.
Once again, the current resistance to countries adopting fair use or open norms is the result of the copyright industry refusing to allow any legal developments that favour the public or indeed anyone except themselves. A good example of the fierce battles being fought is South Africa, where President Ramaphosa sent the Copyright Amendment Bill back to Parliament after it was passed, largely because of lobbying by copyright supporters against its fair use provisions.
Nigeria's new law is important because the country is already a leader in Africa, and is predicted to become one of the world's top economies. What happens in Nigeria matters, because it sets an important precedent for other rising nations looking to update their outdated copyright laws to maximise the benefits of the digital world by adopting open norms.
Read more of this story at SoylentNews.
21:00
Your Fuji Digital Camera Is Hackable Hackaday

There was a time when a digital camera was a surprisingly simple affair whose on-board processor didnt have much in the way of smarts beyond what was needed to grab an image from the sensor and compress it onto some storage. But as they gained more features, over time cameras acquired all the trappings of a fully-fledged computer in their own right, including full-fat operating systems and the accompanying hackability opportunities.
Prominent among camera manufacturers are Fuji, whose cameras it turns out have plenty of hacking possibilities. Theres something of a community about them, with all their work appearing in a GitHub repository, and a cracking April Fool in which a Fuji camera appears able to be coaxed into running DOOM.
The Fuji cameras run the ThreadX real-time operating system on a variety of ARM SoCs, with an SQLite data store for camera settings and Fujis own software controlling the camera hardware. The hackability comes through patching firmware updates, and aside from manipulating the built-in scripting language and accessing the SQLite database can include code execution. We really wish the DOOM was real! So far theres no acc...
20:48
Intel Sends In Last Round Of Graphics Driver Feature Updates For Linux 6.4 Phoronix
Following this week's drm-intel-gt-next pull with more Meteor Lake enablement and other new feature code, a final batch of drm-intel-next feature updates were also submitted to DRM-Next for staging ahead of the upcoming Linux 6.4 kernel merge window...
20:35
Linux 6.4 To Fix Bug Where Nintendo Controllers Could Indefinitely Rumble Phoronix
For those Linux gamers making use of Nintendo controllers, a few notable fixes are on the way for the upcoming Linux 6.4 kernel cycle...
20:22
Cloud Hypervisor 31 Released With More Improvements From Intel & Microsoft Phoronix
Cloud Hypervisor 31 was released this week as the Rust-written VMM started by Intel that runs atop Linux KVM and Microsoft MSHV while these days is a Linux Foundation project receiving regular contributions from not only Intel and Microsoft but also Tencent, Arm, and other players...
18:00
Reactivating a Harris RF-130 URT-23 Transmitter Hackaday

If you enjoy old military hardware, you probably know that Harris made quite a few heavy-duty pieces of radio gear. [K6YIC] picked up a nice example: the Harris RF-130 URT-23. These were frequently used in the Navy and some other service branches to communicate in a variety of modes on HF. The entire set included an exciter, an amplifier, an antenna tuner, and a power supply and, in its usual configuration, can output up to a kilowatt. The transmitter needs some work, and hes done three videos on the transmitter already. Hes planning on several more, but theres already a lot to see if you enjoy this older gear. You can see the first three below and youll probably want to watch them all, but if you want to jump right to the tear down, you can start with the second video.
...
17:19
Iran-Based Hackers Caught Carrying Out Destructive Attacks Under Ransomware Guise The Hacker News
The Iranian nation-state group known as MuddyWater has been observed carrying out destructive attacks on hybrid environments under the guise of a ransomware operation. That's according to new findings from the Microsoft Threat Intelligence team, which discovered the threat actor targeting both on-premises and cloud infrastructures in partnership with another emerging activity cluster dubbed
17:02
IRC Proceedings: Friday, April 07, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-070423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-070423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-070423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-070423.gmi
Over HTTP:
|
... |
17:00
New type of genetically-engineered T-cell may destroy solid cancer tumors Terra Forming Terra

Codex Mendoza: A Glimpse into the Aztec World Terra Forming Terra
Robert F. Kennedy Jr. will run as a Democrat in 2024 against Biden Terra Forming Terra

Plasma and scale and Ball lightening Terra Forming Terra
Plasma and scale and Ball lightening
This really gets to the heart of the matter. We have now projected three types of matter all of which follow naturally from the creation and continuing creation of the SPACE TIME pendulum.
The first is the neutral neutrino pair which forms a tetyrahedra and acts upon it edges as it literally produces TIME by switching back and forth. We can never detect that.
Then we have the neutral electron pair or maybe the electron positron pair with 2400 axis to react along
These can still form clouds which can align and with no charge to detect either.
Either is a frame work for a logic machine and can also plausibly decay into a particle we can identify.
The third is our universe. we reside in an ocean of neutral neutron pairs that literally fill our galaxies and also often beyond. Understand that such a pair has a mass equivalent to a hydrogen atom but also slightly smaller because the electron has not freed up. again we have no means of actually detecting any of this except perhaps with ball lightening.
It appears that ball lightening is a contained ball of this stuff surfaced with hot electrons held neutral on the surface. They are not flying apart at all. And like hydrogen, it can pass through solid walls. We do not store hydrogen very well.
Obviously a whole bunch of problems in physics change when we start working with this model. Yet so far it all conforms to observation.
Understand that in vsuch an universe, opening a void actually does two things. Space is created allowing new matter to be created in order to fill that void. This is posited to look like an inner sun. There is also a boundary event happening as well, both inside and outside the boundary and both involve gravity compression of the neutral neutron pairs. We no not know what actually occurs, but spontaneous matter creation appears plausible
The sun could be producing hydrogen as we look at it.
the mere existence of this neutral neutron pair as a primary constituant of our galaxy makes th...
16:45
The Promisesand Perilsof Ocean Desalination SoylentNews
As the world gets drier, do we need to turn to the ocean?
Sean Bothwell can understand why people think desalination is a silver bullet. When he was a kid living in California's Orange County, the ocean was always close by. It didn't make sense to him that all the water near him wasn't usable.
"I grew up thinking, like, why the heck aren't we desalinating?" said Bothwell, who is now executive director of the California Coastkeeper Alliance. "Why are people always saying that we need to save water and conserve?"
[...] For his part, after doing his graduate school thesis on desalination as an adaptation mechanism for climate change, Bothwell's mind began to change on the process of ocean desalination, and he finally understood its problems and limitations.
"I realized all the things that people don't understand about desalof all the issues we work on, [the efficacy] is the toughest thing to communicate to people," he said. "Everyone thinks it's a good idea."
[...] It's not just what gets sucked into plants that poses a problem for the ocean. The potable water produced by desal plants has an evil cousin: the super-salty discharge that remains, a substance known as brine, which is roughly twice as salty as the original seawater. Brine is heavier than seawater and can sink to the bottom of the ocean, where it creates a deoxygenated dead zone. [...]
"Our ocean is already under a ton of different pressures: nutrient runoff, ocean acidification, climate change," said Bothwell. "You add desal on top of it, and it creates a dead zone."
Read more of this story at SoylentNews.
15:55
Automated Weekend Sales catonmat.net
At Browserling and Online Tools, we love sales.
We just created a new automated weekend sales campaign.
Now each weekend, we show a 50% discount offer to all users who visit our site.
Here's how it looks:
Run weekend sales too and see you next time!
15:21
Links 08/04/2023: ExTiX Deepin 23.4 and Moving from Rust to C++ Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Instructionals/Technical
-
IT Tavern Getting started with nmap scripts
This blog post will cover the general usage of nmap scripts, not the scripting itself. Check out the getting started with nmap post if you are new to nmap.
-
University of Toronto ...
-
-
15:15
Apple Releases Updates to Address Zero-Day Flaws in iOS, iPadOS, macOS, and Safari The Hacker News
Apple on Friday released security updates for iOS, iPadOS, macOS, and Safari web browser to address a pair of zero-day flaws that are being exploited in the wild. The two vulnerabilities are as follows - CVE-2023-28205 - A use after free issue in WebKit that could lead to arbitrary code execution when processing specially crafted web content. CVE-2023-28206 - An out-of-bounds write issue in
15:05
Expert-Led Webinar: Learn Proven Strategies to Secure Your Identity Perimeter The Hacker News
The stakes are high when it comes to cybersecurity. No longer are we dealing with unskilled hackers trying to break into corporate systems with brute force. Today, cybercriminals are using highly sophisticated methods like social engineering, spear phishing, and BEC to target users directly and log in with valid credentials. This is why the identity perimeter has become a critical battleground
15:04
Researchers Discover Critical Remote Code Execution Flaw in vm2 Sandbox Library The Hacker News
The maintainers of the vm2 JavaScript sandbox module have shipped a patch to address a critical flaw that could be abused to break out of security boundaries and execute arbitrary shellcode. The flaw, which affects all versions, including and prior to 3.9.14, was reported by researchers from South Korea-based KAIST WSP Lab on April 6, 2023, prompting vm2
15:00
Pi Microcontroller Still Runs a Webserver Hackaday

At first glance, the Raspberry Pi Pico might seem like a bit of a black sheep when compared to the other offerings from the Raspberry Pi Foundation. While most of the rest of their lineup can run Linux environments with full desktops, the Pico is largely limited to microcontroller duties in exchange for much smaller price tags and footprints. But that doesnt mean it cant be coerced into doing some of the things we might want a mainline Pi to do, like run a web server.
The project can run a static web page simply by providing the Pico with the project code available on the GitHub page and the HTML that youd like the Pico to serve. It can be more than a static web page though, as it is also capable of running Python commands through the web interface as well. The server can pass commands from the web server and back as well, allowing for control of various projects though a browser interface. In theory this could be much simpler than building a physical user interface for a project instead by offloading all of this control onto the web server instead.
The project not only supports the RP2040-based Raspberry Pi Pico but can also be...
14:32
12:03
Hair Analysis Reveals Europes Oldest Physical Evidence of Drug Use SoylentNews
Mediterranean cave clues show that islanders ingested mind-bending plants around 3,000 years ago:
Human hair recovered in a Mediterranean island cave has yielded Europe's oldest direct evidence of people taking hallucinogenic drugs, researchers say.
By around 3,000 years ago, visitors at Es Crritx cave on Menorca perhaps shamans who performed spiritual and healing rituals consumed plants containing mind-altering and vision-inducing substances, say archaeologist Elisa Guerra-Doce of the University of Valladolid in Spain and colleagues.
Signs of human activity at the cave, including more than 200 human graves arrayed in a chamber at the entrance, were previously dated to between around 3,600 and 2,800 years ago. Researchers had also found a hoard of objects in a small pit within an inner cave chamber, including six wooden containers, each containing locks of human hair.
Chemical analyses of one container's locks, possibly from more than one person, detected three psychoactive plant substances that had been ingested and absorbed into the hair over nearly a year, the scientists report April 6 in Scientific Reports.
Two substances, atropine and scopolamine from nightshade plants, induce disorientation, hallucinations and altered physical sensations. Another, ephedrine, boosts energy and alertness. Shamans would have known how to handle and consume these potentially toxic plants safely, the investigators say.
[...] Other hair analyses have found that Inca kids slated for sacrifice more than 500 years ago ingested hallucinogenic drinks and coca leaves and alcohol (SN: 5/13/22; SN: 7/29/13). And a 2005 study found chemical signs of coca-leaf chewing in the hair of two human mummies from Chile dating to around 3,000 years ago. Indirect evidence of drug use in various parts of the world, such as artistic depictions, go back further.
Journal Reference:
E. Guerra-Doce et al. Direct evidence of the use of
multiple drugs in Bronze Age Menorca (western Mediterranean) from
human hair analysis [open]. Scientific Reports.
Published April 6, 2023. 10.1038/s41598-023-31064-2.
Read more of this story at Soylent...
12:00
The Sounds Emitted By Plants Are Real But They Are Still Not Talking Hackaday

A recent paper published by researchers at the university of Tel Aviv in Cell on the sounds they captured from stressed plants had parts of the internet abuzz with what this meant, with some suggesting that this was an early April Fools prank. The fun part here is the news item is not that plants make noise, but rather that this was the first time (apparently) that the noise made by plants was captured by microphones placed at some distance from a variety of plants.
This research is based on previous studies dating back decades, such as Tyree and Sperry who reported (PDF) in 1989 on the vulnerability of the plant xylem (water transporting tissue) to cavitation and embolism. Since the xylems function is to carry water and...
11:38
Links 07/04/2023: Kubuntu 23.04 Beta Released and Barry Kauler Adds Flatpak Installer Techrights
![]()
Contents
-
GNU/Linux
-
Kernel Space
-
LWN User-space shadow stacks (maybe) for 6.4
Support for shadow stacks on the x86 architecture has been long in coming; LWN first covered this work in 2018. After five years and numerous versions, though, it would appear that user-space shadow stacks on x86 might just be supported in the 6.4 kernel release. Getting there has required a few changes since we last caught up with this work in early 2022.
Shadow stacks are a defense against return-oriented programming (ROP) attacks, as well as others that target a processs call stack. The shadow stack itself is a hardware-maintained copy of the return addresses pushed onto the call stack with each function call. Any attack that corrupts the call stack will be unable to change the shadow stack to match; as a result, the corruption will be detected at function-return time and the process terminated before the attacker can take control. The above-linked 2022 article has more details on how x86 shadow stacks, in particular, work.
-
LWN...
-
-
09:18
Venus Has Almost 50 Times as Many Volcanoes as Previously Thought SoylentNews
A new map boosts the count of fiery formations to about 85,000:
The hellscape of Venus is riddled with even more volcanoes than scientists thought.
Using radar images taken by NASA's Magellan spacecraft in the 1990s, researchers cataloged about 85,000 volcanoes strewn across the Venusian surface. That's nearly 50 times as many volcanoes as past surveys counted. Planetary scientists Rebecca Hahn and Paul Byrne of Washington University in St. Louis debuted the map in the April JGR Planets.
Such a thorough inventory of volcanism on Venus could offer clues about the planet's interior, such as hot spots of magma production, Byrne says. And with the recent discovery that Venus is volcanically active, the map could also help pinpoint places to look for new eruptions.
Almost all the volcanoes that Hahn and Byrne found are less than 5 kilometers wide. About 700 are 5 to 100 kilometers across, and about 100 are wider than 100 kilometers. The team also found many tight clusters of small volcanoes called volcanic fields.
[This map of Venus] shows the locations and sizes of all volcanoes visible in radar data from the Magellan spacecraft. The newfound volcanoes range in size from less than 5 kilometers wide to more than 100 kilometers across, though most are on the small side.
Journal Reference:
Rebecca M. Hahn, Paul K. Byrne, A Morphological and Spatial
Analysis of Volcanoes on Venus [open], JGR Planets,
2023 (DOI: https://doi.org/10.1029/2023JE007753)
Read more of this story at SoylentNews.
09:00
Riding the Rails by Ebike Hackaday

As most developed countries around the world continue to modernize their transportation infrastructure with passenger rail, countries in North America have been abandoning railroads for over a century now, assuming that just one more lane will finally solve their traffic problems. Essentially the only upside to the abandonment of railroads has been that its possible to build some unique vehicles to explore these tracks and the beautiful yet desolate areas they reach, and [Cam Engineering] is using an ebike to do that along the coast of central California.
Since his vehicle only has two wheels, he has designed a custom outrigger system consisting of a front guide that leads the front wheel and keeps the bike on the tracks, and a rear support arm which allows the bike to lean slightly against the outside rail. Both outriggers retract to convenient positions when using the vehicle as a bike instead of a rail cart, and its quite the impressive bike at that. Details are sparse on the bicycle itself but it seems to be a custom frame built around fairly large battery and possibly 2000W or more of power in a rear hub motor. Without the pedals and bicycle drivetrain it would almost certainly make a capable electric motorcycle from the way it performs in the video below....
08:01
Microsoft and Fortra to Take Down Malicious Cobalt Strike Infrastructure HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
Cobalt Strike is a legitimate post-exploitation tool designed by Raphael Mudge of Fortra for adversary simulation but it has also been abused by cybercriminals.
This is a post from HackRead.com Read the original post: Microsoft and Fortra to Take Down Malicious Cobalt Strike Infrastructure
06:56
UN Cybercrime Draft Treaty Timeline Deeplinks
October 2017
The Russian Federation
presents
a letter to the UN General Assembly containing a draft of the
United Nations Convention on Cooperation in Combating Cybercrime,
intended for circulation to Member States.
November 2019
A resolution, sponsored by
Russiaalong with Belarus, Cambodia, China, Iran, Myanmar,
Nicaragua, Syria, and Venezuelato set up an international
convention to combat cybercrime passes in the UN General Assembly.
The resolution
was opposed by the US, the EU, and other nations.
Human rights organizations, including the Association for
Progressive Communications and EFF,
urged the General Assembly to vote against
the resolution, citing concerns that it could undermine the use of
the internet to exercise human rights and facilitate social and
economic development.
December 2019
The UN General Assembly adopts a
resolution to create an
Ad Hoc Committee (AHC) to draft a UN Convention on
countering the use of information and communications technologies
for criminal purposes. Participation in the AHC is open to all
Member States of the world, as well as non-member state observers
(like the EU and the Council of Europe), civil society, and
nongovernmental organizations (NGOs) to varying degrees. The United
Nations Office on Drugs and Crime (UNODC), through the
Organized Crime and Illicit Trafficking Branch,
Division for Treaty Affairs, serves as Secretariat for the Ad Hoc
Committee. However, the timing of this effort was controversial, as
another UN General
Assembly Resolution had raised concerns that
cybercrime laws are in some instances misused to target human
rights defenders or have hindered their work and endangered their
safety in a manner contrary to international law.
August 2020
The AHC postpones its first
organizational meeting in New York to 2021 because of COVID-19.
January 2021
Human Rights Watch
raises alarms...
06:41
Apple addressed two actively exploited zero-day flaws Security Affairs
Apple released emergency security updates to address two actively exploited zero-day vulnerabilities impacting iPhones, Macs, and iPads.
Apple has released emergency security updates to address two actively exploited zero-day vulnerabilities, tracked as CVE-2023-28205 and CVE-2023-28206, impacting iPhones, Macs, and iPads.
Impacted devices include:
- iPhone 8 and later,
- iPad Pro (all models),
- iPad Air 3rd generation and later,
- iPad 5th generation and later,
- iPad mini 5th generation and later,
- and Macs running macOS Ventura.
Both vulnerabilities were reported by Clment Lecigne of Googles Threat Analysis Group and Donncha Cearbhaill of Amnesty Internationals Security Lab.
The zero-day CVE-2023-28205 is a use after free issue that resides in the WebKit, its exploitation may lead to arbitrary code execution. An attacker can trigger the flaw by tricking the victims into loading maliciously crafted web pages.
Processing maliciously crafted web content may lead to arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited. reads the advisory.
The IT giant addressed the flaw with improved memory management.
The zero-day CVE-2023-28206 is an out-of-bounds write issue that resides in the IOSurfaceAccelerator.
An app may be able to execute arbitrary code with kernel privileges. Apple is aware of a report that this issue may have been actively exploited. reads the advisory.
The company addressed the flaw with improved input validation....
06:35
How Pink Floyd Inspired Research Into Medieval Monks and Volcanology SoylentNews
Ars Technica is reporting on a new (published 5 April 2023) paper combining ice core, tree ring and textual analysis to "more accurately date medieval volcanic eruptions."
The primary author's inspiration to pursue this line of research included:
Sbastien Guillet, an environmental scientist at the University of Geneva in Switzerland, was rocking out to Pink Floyd's classic Dark Side of the Moon album one day when he made a prescient connection. The darkest lunar eclipses all occurred within a year or so of major volcanic eruptions. And astronomers know the exact days of those eclipses. So medieval historical accounts of lunar eclipse sightings should be able to help scientists narrow down the time frame in which major eruptions occurred during the High Medieval period spanning 1100 to 1300 CE. Guillet collaborated with several other scientists to conduct such a study, combining textual analysis with tree ring and ice core data. They described their findings in a new paper published in the journal Nature.
"Climate scientists usually identify past volcanic eruptions by measuring the acidity and amount of volcanic ash in cores drilled from polar ice, or by inferring abrupt temperature changes in tree ring records," Andrea Seim (University of Freiburg) and Eduardo Zorita (Helmholtz-Zentrum Hereon) wrote in an accompanying commentary. "However, these sources sometimes disagree, because the location, intensity, and timing of eruptions can produce varying results, as can circulation of the atmosphere. Guillet and colleagues' approach offers an independentand perhaps even more directsource of information about the timing of volcanic eruptions, which could resolve some of these disagreements."
[...]
Guillet's critical insight stems from the impact volcanic eruptions can have on the appearance of a lunar eclipse. If there are a lot of aerosols, the moon will appear dark during the eclipse; if aerosols are scarce, the moon will have a bright reddish appearance. So one should be able to estimate how much volcanic aerosols were in the atmosphere from medieval descriptions of the color and luminosity of the moon during lunar eclipses, and use that information to more accurately date medieval volcanic eruptions.
It's an interesting combination of science and analysis of historical writings to arrive at a better understanding of some of the forces acting on the climate in Medieval Europe.
N.B.: The Nature journal reference appears to be the full paper, not just an abstrac...
06:00
Photoplotting PCBs with a 3D Printer Hackaday

Do you ever wonder why your PCB maker uses Gerber files? It doesnt have to do with baby food. Gerber was the company that introduced photoplotting. Early machines used a xenon bulb to project shapes from an aperture to plot on a piece of film. You can then use that film for photolithography which has a lot of uses, including making printed circuit boards. [Wil Straver] decided to make his own photoplotter using a 3D printer in two dimensions and a UV LED. You can see the results in the video below.
A small 3D printed assembly holds a circuit board, the LED, and a magnet to hold it all to the 3D printer. Of course, an LED is a big large for a PCB trace, so he creates a 0.3 mm aperture by printing a mold and using it to cast epoxy to make the part that contacts the PCB film.
The fan control turns the LED on and off, much as laser cutter mods for 3D printers often do. We noticed he uses standard nuts as heat set inserts, and that seems to work well enough, especially since there isnt much load on them in this application. There were a few iterations of pinholes and mounts, but the final iteration seems to work well. There is even a method to do double-sided boards.
Of course, with a laser cutter and good focusing, you could pull the same trick. Just be aware that some of the high power laser modules dont focus to...
05:21
TPB Founders Are Not Involved in the The Pirate Bay TV Series (Update) TorrentFreak
 Two
years ago, reports began to surface about a new
six-part TV-series on The Pirate Bays turbulent history.
Two
years ago, reports began to surface about a new
six-part TV-series on The Pirate Bays turbulent history.
The project was initially scheduled to start last year but after an apparent delay, filming is now expected to begin this fall.
Pirate Bay TV Series
The inception and early years of The Pirate Bay are definitely a worthy subject for a series. While most pirate sites hid in the shadows, Pirate Bays founders were public figures, who openly taunted the entertainment industries.
Speaking with Variety, head-writer Piotr Marciniak explains that his screenplay is based on a wealth of archive material as well as interviews with the sites founders.
Its a classic rise and fall story, a tragedy about flying too close to the sun, but also a timeless story of a generational conflict, Marcimiak said.
The people involved in the The Pirate Bay series are clearly looking forward to getting the project running. The production is in the hands of B-Reel Films, working for the Swedish broadcaster SVT, while the American distribution company Dynamic Television scooped up worldwide rights.
Selling The Pirate Bay Rights
Indeed, the rights to The Pirate Bay series are actively traded. The same will likely happen to pirated copies of the episodes when theyre illicitly posted to The Pirate Bay, but its unclear whether the rightsholders have plans to crack down on unauthorized sharing.
Its nonetheless interesting to read that the story about a site that rebelled against the exploitation of copyrights, is being copyrighted and sold off. Would The Pirate Bay founders approve of that? Are they even involved?
The Pirate Bay series aims to tell the history of the notorious pirate site and co-founders Fredrik Neij, Peter Sunde, and Gottfrid Svartholm, but none appear to be actively involved.
Founders Deny Involvement
TorrentFreak spoke with both Sunde and Neij, who both confirm they were not interviewed for the upcoming series, even though it aims to document an important and hectic part of their lives.
Nope, they didnt interview me for the TV series, Fredrik says. Also. Im not sure who they bought the rights from They didnt pay me at least.
And I know Anakata would have had nothing to do with it, Fredrik adds, referring to co-founder Gottfrid, who prefers to...
05:12
Beware of the trillion dimensional space There is a lot that you can do with a trillion parameters. cryptogon.com
There is some intelligence in this system. It could absolutely build an internal representation of the world and act on it Also, later in the talk, he demonstrates hilarious basic math failures. Via: Sebastien Bubeck: Related: Defamed by ChatGPT: My Own Bizarre Experience with Artificiality of Artificial Intelligence We need to tell people ChatGPT will []
05:12
Decoding the U.N. Cybercrime Treaty Deeplinks
Negotiations for a proposed U.N.Cybercrime Treaty commenced in 2017 but began to take shape in 2022and theres a lot at stake. The draft treaty has the potential to rewrite criminal laws around the world, possibly adding over 30 criminal offenses and new expansive police powers for both domestic and international criminal investigations.
Given that existing cybercrime laws are, as stated by the U.N.General Assembly, in some instances misused to target human rights defenders and endanger their safety in a manner contrary to international law, these widened parameters amplify the potential implications for billions of peopleparticularly stifling free speech, increasing government surveillance, and expanding state investigative techniques.

Click to Tweet: The draft U.N. Cybercrime Treaty would stifle the rights of people across the globe. Learn more: eff.org/treaty

05:02
ChatGPT Comes for Low Wage Natural Language Processing Classifier Jobs cryptogon.com
Via: arXiv: Many NLP applications require manual data annotations for a variety of tasks, notably to train classifiers or evaluate the performance of unsupervised models. Depending on the size and degree of complexity, the tasks may be conducted by crowd-workers on platforms such as MTurk as well as trained annotators, such as research assistants. Using []
04:53
Meet Anthalon, fighting for freedom of the press HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
In todays world, censorship and suppression of free speech are rampant in many parts of the globe. Governments
This is a post from HackRead.com Read the original post: Meet Anthalon, fighting for freedom of the press
04:44
Links 07/04/2023: PCLinuxOS Magazine and More Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Audiocasts/Shows
-
The BSD Now Podcast BSD Now 501: Boot that Snapshot
Nextcloud + OpenBSD = <3, Understanding the Origins of DTrace, Bastille Templates for FreeBSD Jails, Initial support fo...
-
-
04:41
MSI confirms security breach after Money Message ransomware attack Security Affairs
Multinational IT corporation MSI (Micro-Star International) confirms security breach after Money Message ransomware gang claimed the hack.
This week the ransomware gang Money Message announced to have hacked the Taiwanese multinational IT corporation MSI (Micro-Star International). Micro-Star International AKA MSI designs, manufactures, and sells motherboards and graphics cards for customers in the United States, Canada, and internationally. MSI is headquartered in Taipei, Taiwan.
The ransomware group added the company to the list of victims on its Tor leak site, it claims to have stolen the source code from the company, including a framework to develop bios, and private keys.

The group published a series of screenshots of the companys CTMS and ERP databases
The Money Message group threatens to publish the stolen files by Wednesday, April 12, 2023, if the company will not pay the ransom.
Today MSI confirmed the security breach, it confirmed that threat actors had access to some of its information service systems.
MSI recently suffered a cyberattack on part of its information systems. Upon detecting network anomalies, the information department promptly activated relevant defense mechanisms and carried out recovery measures, and reported the incident to government law enforcement agencies and cybersecurity units. reads a statement published by the company. Currently, the affected systems have gradually resumed normal operations, with no significant impact on financial business.
The company reported the security breach to the relevant authorities, and it downplayed the incident, saying that the attack had no significant financial and operational impact.
In response to the incident, the company announced it is enhancing the information security control measures o...
04:35
Reporters Without Borders Barred from Visiting Julian Assange cryptogon.com
Via: Peoples Dispatch: Two leaders from NGO Reporters Without Borders (RSF) were barred from visiting imprisoned journalist Julian Assange on April 4 in Belmarsh Prison. RSF Secretary-General Christophe Deloire and Director of Operations Rebecca Vincent were not able to carry out their visit with Assange, a visit which had taken months to secure. Belmarsh Prison []
04:05
Mesa 23.0.2 Released With Dozens Of Fixes Phoronix
Another tardy Mesa stable release is now available for those wanting to run the latest open-source OpenGL, Vulkan, OpenCL, and video acceleration code on your Linux systems...
04:01
Targetoos Precision Targeting Vows to Transform Mobile Advertising HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
In todays fast-paced digital world, mobile advertising has become an essential tool for businesses looking to engage with
This is a post from HackRead.com Read the original post: Targetoos Precision Targeting Vows to Transform Mobile Advertising
04:00
AI Pause Open Letter Stokes Fear and Controversy IEEE Spectrum

The recent call for a six-month AI pausein the form of an online letter demanding a temporary artificial intelligence moratoriumhas elicited concern among IEEE members and the larger technology world. The Institute contacted some of the members who signed the open letter, which was published online on 29 March. The signatories expressed a range of fears and apprehensions including about rampant growth of AI large-language models (LLMs) as well as of unchecked AI media hype.
The open letter, titled Pause Giant AI Experiments, was organized by the nonprofit Future of Life Institute and signed by more than 10,000 people (as of 5 April). It calls for cessation of research on all AI systems more powerful than GPT-4.
Its the latest of a host of recent AI pause proposals including a suggestion by Googles Franois Chollet of a six-month moratorium on people overreacting to LLMs in either direction.
In the news media, the open letter has inspired straight reportage, critical accounts for not going far enough (shut it all down, Eliezer Yudkowsky wrote in Time magazine), as well as critical accounts for being both...
03:51
The Dangerous Weak Link in the US Food Chain SoylentNews
If hackers wanted to debilitate American society, they would have trouble taking down the entire power grid or financial system, but they could do serious damage to the companies that make and deliver Americans' food.
The US food and agriculture sector lacks the resources, expertise, and government support to protect itself and its products from a rapidly expanding range of cybersecurity threats, according to lawmakers, policy experts, and former government officials. These shortfalls leave gaps that foreign government operatives or cybercriminals could exploit to remotely disable farming equipment, contaminate fertilizer, cripple milk supplies, and kill chickens.
In the past few years, cyberattacks on the meat processing giant JBS Foods and the Iowa farm services firm NEW Cooperative have laid bare the industry's widespread vulnerabilities. And new technologies, including advances in artificial intelligence, are creating previously unimaginable risks, overwhelming a workforce not accustomed to dealing with digital security. Making matters worse, food and agriculture is one of only a few critical infrastructure sectors that doesn't have an information sharing and analysis center, or ISAC, helping companies fight back.
All of these shortcomings make food and agriculture companies a prime target for Russian operatives bent on vengeance for Western sanctions, Chinese spies seeking a competitive advantage for their domestic firms, and ransomware gangs looking for victims that can't afford downtime.
Read more of this story at SoylentNews.
03:00
EFF to Ninth Circuit: Twitter Has First Amendment Right to Ban Users, Including Presidents Deeplinks
Time and time again,
we have saidand courts have ruledthat social
media platforms have the First Amendment right to ban users. We
have argued that banned users cannot successfully sue platforms for
acting as government censors without showing that the platforms
willfully and fully
ceded their editorial discretion to the
government. But nevertheless, the lawsuits keep getting filed.
This time, former President Trump is the lead plaintiff in yet
another must carry lawsuit, this one against Twitter. And we have
again filed an
amicus brief that explains how editorial
freedom online benefits users by encouraging diverse forums for
speech. (Twitter
has also argued that the case is moot since it restored
Trumps account.)
Trump and the other plaintiffs claimed that Biden administration
officials threats to amend Section 230
unless Twitter deplatformed Trump (not coincidentally,
Section 230 provides immunity to platforms from these very
lawsuits) transformed Twitter into a state actor.
Government coercion and involvement in
private companies content moderation practices raise serious
concerns. But in most situations, those concerns are best directed
at the government itself.
Even if officials urged Twitter to act against certain users,
Twitter cannot be liable unless it abandoned its editorial
principles and adopted the governments decisions in their place.
Only under these well-defined and limited circumstances should a
court find that Twitter is a state actor, we told the court. The
facts alleged in this case do not support that finding.
In many cases, the government is free to talk to Twitter, and
Twitter is free to listen or not listen. As our brief argues,
treating Twitter as a state actor and subjecting it to lawsuits
would actually violate Twitters own First Amendment right to be
free from governmental, including judicial,
interference.
02:06
That Means Of Casinos Online 888 Free On Line Casino Games Slot Machinesk8io Vipsign Up To Get $5casinos On-line 888 Free Casino Video Games Slot Machines3xvcasinos On-line 888 Free On Line Casino Video Games Slot Machines3xv h+ Media
That Means Of Casinos Online 888 Free On Line Casino Games Slot Machinesk8io Vipsign Up To Get $5casinos On-line 888 Free Casino Video Games Slot Machines3xvcasinos On-line 888 Free On Line Casino Video Games Slot Machines3xv
You can play Baccarat, Blackjack, Dice, Dragon Tiger, Roulette, Casino Holdem, Colored Disks, and Fan Tan. Unfortunately, not all mobile functions are reliable places for betting. There are many scammers whove been added to a black record due to quite a few complaints from gamers about delays in payments and many other issues that they faced. Below you might find unreliable cell apps that you should avoid.
- Thus, if a User in the end decides to click on on the model to examine it, go to the brands website or make a deposit with this brand, we might obtain a commission.
- Notably, 888 Casino features an extensive video games library consisting of over 2000 video games.
- 888 is a user-friendly on-line on line casino that is designed to be straightforward to make use of for both new and experienced gamers.
There is so much to say about this lovely on line casino model. You might know all about 888 Holdings and their line of online gambling clubs, sports betting and poker gadgets. Yet, did you might have any concept that 888 have their own legitimacy on-line spaces as well?
Yes, theyre completely safe offered that theyre licensed and dont belong to the black list what we introduced on this article. Now the app is efficiently downloaded and all you want to do is set up it in your smartphone. This is the section within the menu, clicking on it will take you to the applications web page. Cricket odds are even better right here than on different sites. Dedicated markets for those who anticipate what would possibly occur throughout a match, so there are Fixed and Fancy markets. Discover all out there promotions as well as their phrases & circumstances from the Bonuses and Offers web page.
We carry on connecting with our users with the help of our monthly edition carving our means slowly in the course of the very best readership. 888 moreover pledged to extend full-year revenues from about 1.85bn to larger than 2bn by 2025. It is an old casino model that has been on the planet gambling scene for an extended time.
The top has the slot sport providers, and the assorted slot video games are wedden op virtual sports listed under. You can search by game or supplier and are sure to find the game you get pleasure from essentially the most as 888Casino has over 1100 slots video games. Some of the slots on 888Casino are Starburst, Rainbow Riches, Rise of the Pharaohs, Twin Spin, Luck of the Irish, Irish Riches, and so forth. This casino 888 brand is phenomenal in its cellular recreation model. The website of 888 on line casino is cell resp...
02:03
888 On Line Casino Video Games h+ Media
888 On Line Casino Video Games
the casino and selected payment methodology suppliers relying on the banking choice and forex youre using. [newline]There may be a chance of change fee applied to your deposits. But, you do not need to fret as you might be asked for the confirmation of charges before you submit the deposit. Offering very high payouts (more than 96% for all combined games), 888 on line casino is certified by the group eCOGRA (e-Commerce and Online Gaming Regulation and Assurance). For sustaining fairness and safety in any respect the elements, this casino has received a secure and fair seal of approval by eCOGRA. You can rest assured about the security and security of your details because this casino complies with all the guidelines revealed by eCOGRA for a players safety. But perhaps most significantly, 7Cric is thought for its quick withdrawal process, which means you probably can cash out your winnings shortly and easily.New customers can enhance their earnings in no time due to the rewarding welcome package out there. Despite that you wont discover an 888 casino no deposit bonus, in contrast to at other casinos, youll have the ability to increase your earnings with different promotions at this award winning online casino. Overall, 888 provides Indian clients the best opportunities to land large wins.
Slowly and steadily I started getting back to who I was. I attempt to do all that I can in my capacity to make this quite taboo matter, psychological well being, a dinner-table dialog. Until I was fifteen, I did not notice that my actions had been the outcome of damaging psychological well being. I thought nervousness and anger points are fancy words and that is all of the effect of Channel V or so Let me start off by saying, that I was an adopted baby. Now Im not saying I had issues since childhood but Im saying that I realized certain things were issues after I grew up.
Players from these international locations are not permitted to access 888 casino or its services. However, the casino operates in many different countries where it is legally approved to do so. Follow the instructions supplied by the withdrawal method youve chosen to complete the transaction. Enter the amount you want to deposit and any required information, such as bank card particulars or e-wallet login info.
Therefore, the bettors should immerse in this sphere and take diverse factors into consideration whereas placing wagers. The ultimate step is to enter your stake, press the Place bet button, submit your wager and await the outcomes. The bonus shall be credited to your account routinely once you have made your first deposit with Bonus Code DSFDB160INR. The bonus will be credited to your account mechanically once you have made your first deposit. On this page, well inform you all the primary points about t...
02:02
888 On Line Casino Evaluate 2023 Get $88 No Deposit In India h+ Media
888 On Line Casino Evaluate 2023 Get $88 No Deposit In India
Ask our support group or discover the information you need beneath. Here weve answered some frequent questions gamers have about 888Starz Casino. A dedicated Help part has solutions to in style questions throughout a variety of topics, significantly helpful for brand spanking new players. Games are hosted by in a studio the place the best-dressed sellers, each male and female, stand in front of an ultra-HD digicam, and deal and work together with the gamers in actual time. Another ongoing provide is the Premium Welcome Package, rewarding the consumer as much as $1,500 in bonus, cut up over 5 deposits within the first week.
The mostly supplied kinds of bets on this sports activities are the precise score wager and over/under punts. After you open the application in your smartphone, you need to look over the catalog of sports activities disciplines, leagues and tournaments which may be available for betting. Then determine what sports and video games precisely you wish to place bets on. It is a convenient opportunity for users to put additional bets after the sport began. These Live bets may be offered even between match halves, quarters, or durations. INDIBET realizes that there are lots of tennis followers in India.
The bonus money can be used to play any gameincluding slots, jackpots, and stay dealer gamesand there is a 30x wagering requirement. However, deposits through NETELLER and Skrill are not eligible. The on line casino also presents a variety of payment choices, including credit score and debit cards, e-wallets, and financial institution transfers.
- Visit Crickex Website The firm is working constantly on enhancing its products.
- For Indian players, the on line casino accepts Indian Rupees as a currency, making it easier to deposit and withdraw funds with out
- As a child, its difficult to understand situations round you and until a lengthy time i had no name to my feelings.
- However, the typical time vary is between a day and three at the most.
- Only after verification are you able to deposit cash into your account.
If it doesnt, youll find a way to always make an Ekbet app login using your Player ID and Password. This will begin the ekbet app obtain apk, which only takes a few seconds. The funds might be immediately transferred to your account, permitting you to guess on the wanted sports activities in a matter of minutes. When betting on a good occasion, select the odds and charges. You can instantly see the scale of the potential profit by clicking on any of the available betting choices. The web site incorporates a huge record of video games that you may wager on.
888 have accomplished all they can to ensure that Indian players can use a payment methodology that suits them. Arguably one of many greatest reasons to join 888 on line...
02:00
Video Friday: Peep Handling IEEE Spectrum

Video Friday is your weekly selection of awesome robotics
videos, collected by your friends at IEEE Spectrum
robotics. We also post a weekly calendar of upcoming robotics
events for the next few months. Please
send us your events for inclusion.
Robotics Summit & Expo: 1011 May 2023, BOSTON
ICRA 2023: 29 May2 June 2023, LONDON
RoboCup 2023: 410 July 2023, BORDEAUX, FRANCE
RSS 2023: 1014 July 2023, DAEGU, SOUTH KOREA
IEEE RO-MAN 2023: 2831 August 2023, BUSAN, SOUTH KOREA
CLAWAR 2023: 24 October 2023, FLORIANOPOLIS, BRAZIL
Humanoids 2023: 1214 December 2023, AUSTIN, TEXAS
Enjoy todays videos!
Happy Peep Consumption Day!
[ Soft Robotics ]
Appropriate facial expressions for Ameca in this video are selected by GPT-3 . We also tried GPT-4; the processing time with 4 was longer and made Ameca appear less responsive.
[ Engineered Arts ]
Kittens: The enemy of lazy robots everywhere.
...
01:59
888 Casino India No Deposit Bonus, Codes & Free Spins h+ Media
888 Casino India No Deposit Bonus, Codes & Free Spins
Do not neglect checking the wagering phrases that include the bonus. Like many different related web sites, INDIBET has a selection dedicated to on-line on line casino video games. It covers Poker, Teen Patti, Roulette, Baccarat, and Slots. In addition to betting on sports activities and casino video games, the company appeals to punters by providing them something additional the Exchange. In order to deposit your betting amount, you must first register with the platform. Once youre a registered member, navigate to 888 Casino homepage and log into your account by providing your username and password.
You need to substantiate your e-mail or telephone quantity through a link despatched to your email tackle or SMS. The bookie additionally could require proof of your id, cost data, and handle by offering a replica of your ID document, a utility invoice, and a photograph of your financial institution card. You have 12 bets, totals, over/under, handicaps, as nicely as those distinctive to a certain sport like who wins the coin toss. To entry your account on the unique web site, click on the Sign in 4RaBet button in the top-right nook of the web page. Type in your e mail and password and click Sign in once more. In case you forgot the password or login, 4ra Bet has the Recover a password possibility.
Ensure a smooth cash-out process by submitting the mandatory documents to buyer support. Rest assured, your data is protected and can by no means be shared with any external sources. Just click on the green Sign Up button in the high proper corner of our page, and youll be in your way.
In the Ekbet app stay on line casino part can also be available to you. That is, the game is carried out by the dealer by way of a reside broadcast. He communicates with you and accepts virtual bets of actual cash.
888 Casino uses its own proprietary software, which they repeatedly update. This is something that you will not see in other online on line casino suppliers. When we discuss different on-line platforms, they use the software program provided by numerous distributors, but they dont have their personal software. You can simply obtain the user-friendly 888 software quickly on to your laptop. Or when you dont wish to obtain the software program, youll have the ability to select the instant play flash model that provides you many of the games. The desk game varieties on 888casino are some of the spectacular of all different online casinos that serve the Indian market.
The app has a easy and convenient interface that makes it very easy to position bets. You could easily access all essential options to enjoy an immersive experience from any trendy smartphone. Access games, deposit/withdrawal features, customer support, and other features from the app. It works around the clock and has certified support for players using a chat within...
01:57
Crickex Deposit
New clients can enhance their earnings in no time due to the rewarding welcome package available. Despite that you simply wont find an 888 on line casino no deposit bonus, unlike at other casinos, you probably can enhance your earnings with different promotions at this award profitable on-line on line casino. Overall, 888 provides Indian customers the most effective alternatives to land large wins.
You will always discover the occasion to wager on the listing of obtainable sports activities is updated often in order that to cover as many disciplines as attainable. Dubai World Cup, Kentucky Derby, and Melbourne Cup are waiting for you to place the primary guess. All the NBA season reside with full protection of the matches all over the USA. Make your secure fee now and transfer forward with confidence.
This is the most admired sports activities self-discipline in India and thats the reason all prime betting apps suggest it in their catalogs. There are plenty of distinguished events to wager on such because the ICC Cricket World Cup, Ashes Series, T20 World cup in addition to a extensive array of bet sorts. At this stage, you should select the amount of money you want to spend on bets by way of the most effective betting app. Furthermore, keep in mind to handle your funds correctly and do not spend everything on a single wager. First and foremost, the betting utility have to be out there in India, as a end result of some bookies could not have legal right to operate in certain areas. Usually, the details about the listing of restricted countries is displayed on the official site of the bookmaker.
Various VIP programs are additionally extremely appreciated by the gamblers as they may acquire access to premium offers and prizes. It is a great plus if players have a chance to carry out cash transactions in their home currency the Indian rupee. What is more, a good app must also provide SSL encryption which can point out that gamblers personal and financial info is well-protected.
Below there are an important criteria that you want to take into accounts while analyzing cellular apps. Before making a deposit, customers should conform to obtain a sports activities betting bonus both on the Account Settings page, or immediately on the Deposit web page. Bookie has a separate platform for this, where markets and their odds are formed based on what different bettors think.
Furthermore, 888Casino is licensed by a quantity of governing our bodies like the UK Gambling Commission, the Malta Gaming Authority, and the Gibraltar Government. 888 casino offers on-line slot games for players who like spinning and simple fun. The complete number of slot video games obtainable on the platform is about a hundred and eighty slot games. There is a quick search option to filter and get to pick your favourite recreation. Given you personal an Android or iOS gadget that is running the most recent...
01:55
888 Casino Video Games h+ Media
888 Casino Video Games
A devoted on line casino app for gamblers who prefer to play on the go. It follows eCOGRA tips to make sure all permitted gaming companies are transparently monitored for participant protection. 888casino has a memorable tagline for individuals who gamble with caution Safer. The casino takes all measures to make sure truthful play and safe gaming.
If you have login or account related issue, please verify the next steps. It is doubtless considered one of the most typical drawback in android operating system. Usually whenever you open an app, you will see a black display screen for few seconds after which app will crash with or with out an error message. 888 Casino app will not be working for you because of some issues that your gadget might have or your internet connection drawback. If you suppose that 888 Casino app has a difficulty, please post your issue utilizing the comment field below and somebody from our neighborhood could help you. Also in the mean time youll have the ability to attempt the fixes talked about beneath.
888 uses advanced safety measures corresponding to SSL encryption to protect participant information and transactions. The on line casino employs unbiased third-party auditors to check the equity and randomness of its games. Players can place a variety of bets on these sports activities, including match winners, handicaps, totals, and extra. 888casino is a sort of on-line playing institutions which are lifeless critical about the security and safety of gamblers. Yeah, thats how you can primarily attain the customer assist team at 888casino.
It all started with a panic assault after I was 18 years old. Of course, I didnt take it seriously, because it occurred proper before my board exams. As time progressed, an event struck in my life that wa I was fortunately Living with my Parents and my youthful sister in Delhi Utterly blind to the cycle of time. When I was 2 Years old My Father Went into Depression , My mom started a job , my Mater
They are a family name in the on-line casino and poker area. Live Casino Bonuses can include deposit bonuses, cashback presents, and different rewards. Under the license, it operates numerous gaming sites for real money and educational purposes. The companys services in the United Kingdom are operated by 888 UK Limited, integrated in Gibraltar, and licensed and controlled by the Great Britain Gambling Commission. The Acts passing had opened a leeway to creating authorized online casinos, and the brother-partners conveniently seized that opportunity. In May 2007, Casino-on-Net, the companys first web site, was born, which might later set the stage for 888casino.
You will find them in slots, on line casino, sports, and others. According to the statistics, theres a high percentage of individuals that have playing habit. The finest apps for sports betting care for their bettors by implementing a...