| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Friday, 14 April
01:30
Square-Wheeled Bike Is Actually An Amazing Tracked Build Hackaday

The invention of the wheel is considered one of the crowning achievements of early humanity. Squares dont roll, after all. [The Q] decided to build a square-wheeled bike anyway, with a neat tracked setup that makes for an awesome visual gag.
The wheels are made out of C-angle steel, making them both stout and incredibly heavy. While they dont really need the additional structure for strength, they feature spokes which mount a central hub for attaching the wheels to a bicycle axle. The squares arent designed to roll, though. Instead, they are fitted with gears and rollers, upon which a track made of bicycle chain and tires is fitted. When the rider pedals, this turns the track, propelling the bike along. Cleverly, the track mechanism is neatly hidden by some framing, confusing passers-by.
The riding experience is noisy, thanks to the tracks. Theres also plenty of rolling resistance. Its unlikely bikes like these will become mainstream transport anytime soon,...
01:22
Dementia: Can phototherapy treatments improve cognitive function? Lifeboat News: The Blog
Upon analysis, researchers found the phototherapy treatments significantly improved MMSE scores in participants with dementia.
The second focus of the study was to see how phototherapy interventions affected the behavioral and psychological symptoms of dementia (BPSDs) such as depression and agitation and sleep. The researchers stated there were no significant differences in BPSDs and sleep between the phototherapy and control groups.
01:22
Keto diet may treat epilepsy Lifeboat News: The Blog
Mice that received gut microbes from children with epilepsy on the ketogenic diet were protected from seizures. The finding suggests the microbiome is behind the diets seizure-reducing effect.
By Grace Wade
01:20
Todays AI Job Market, in Four Graphs IEEE Spectrum

Whats the career outlook for AI professionals? In a word, growing, for all skill sets. But dig down into the data, and youll find some differences.
This latest look at the AI job market comes from the Stanford Institute for Human-Centered Artificial Intelligence (HAI), which this month released its 2023 AI Index Report, more than 300 pages of data capturing trends in artificial intelligence. A hunt through those pages brought me several key snapshots of career trends, in the form of graphs created using data from Lightcast, a labor market analytics firm that mined millions of jobs posted 51,000 websites since 2010, flagging those listing AI skills. Here are the key takeaways.
AI jobs are up around the world, but nowhere more so than in the United States
Machine learning booms, while robotics languishes
Python is the AI language of choice
California has the most AI hires, but the Texas job market gains share
01:05
Links 13/04/2023: Wireshark 4.0.5, Arianna 1.0, and Thunderbird Feature Requests Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Monopolies
- Gemini* and Gopher
-
GNU/Linux
-
Applications
-
Neowin Wireshark 4.0.5
Wireshark is a network packet analyzer. A network packet analyzer will try to capture network packets and tries to display that packet data as detailed as possible. You could think of a network packet analyzer as a measuring device use...
-
-
00:32
Legion: Credential Harvesting & SMS Hijacking Malware Sold on Telegram HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
The Legion malware is capable of stealing credentials from misconfigured or exposed servers and is linked to the AndroxGh0st malware family.
This is a post from HackRead.com Read the original post: Legion: Credential Harvesting & SMS Hijacking Malware Sold on Telegram
00:28
Where Did the CEO of Sirius Run Away to Last Month? A No-Content Company With 4,000 Pounds and No Employees. Techrights
Filed a week ago:
One-person shop with little funds in the bank:
Summary: The CEO of Sirius Open Source Limited left last month not because of some lucrative job offer from another company; hes back to a one-person non-business (placeholder/pot) registered at the address of the accountant with a single-page Web site (see below); its most likely that he runs away from the scene of the crime given how rampantly he has been purging any remnants of his time at Sirius
You can run, or delete pages, but you cannot hide. Bullied people always remember.
References: CEO of Sirius UK Continues to Purge Any Remnants of His Past With the Company (Trying Hard Not to Associate With It) | Sirius UK CEO Resigns (or Gets Sacked) and Completely Deletes His Whole Past With Sirius Open Source | Amid Fraud at Sirius Open Source CEO Deletes His Recent (This Month) Past With the Company]
...
00:27
[$] Process-level kernel samepage merging control LWN.net
The kernel samepage merging (KSM) feature can save significant amounts of memory with some types of workloads, but security concerns have greatly limited its use. Even when KSM can be safely enabled, though, the control interface provided by the kernel makes it unlikely that KSM actually will be used. A small patch series from Stefan Roesch aims to change this situation by improving and simplifying how KSM is managed.
00:09
The Boss of Sirius Open Source and His Ex-Wife Should be Reunited Inside the Prison Cell Techrights
Video
download link | md5sum
Time for Sirius Management to Face Prison
Creative Commons Attribution-No Derivative Works 4.0
Summary: The crimes of Sirius Open Source are very serious; weve come to the point now where its more or less a countdown ahead of arrests or class action lawsuit (or both)
TODAY we published a lot of material about Sirius Open Source and since recording the above video weve published a little more.
In light of what Standard Life told us last night (they sent a letter at night, which is unusual for firms that work 9 to 5), were now progressing the case against a company that defrauded GNU/Linux system administrators, Free software specialists, programmers and so on.
The principal fraudster now resides in Washington, the state. To get full accountability they will likely have to issue an extradition warrant (sent from authorities in the UK to the US).This is now a criminal matter. Several people need to be arrested.
The issue is further complicated by an NDA signed with the Gates Foundation (we dont even know the details of it). The principal fraudster now resides in Washington, the state. To get full accountability they will likely have to issue an extradition warrant (sent from authorities in the UK to the US). This adds a number of new dimensions, including the divorce. The financial fugitive has many liabilities in the UK. Some of these issues are discussed in length in the video above.
00:00
Tinkercad Gets a Move On Hackaday

Going to the movies is an experience. But how popular do you think theyd be if you went in, bought your popcorn, picked your seat, and the curtain would rise on a large still photograph? Probably not a great business model. If a picture is worth 1,000 words, then a video is worth at least a million, and thats why we thought it was awesome that Tinkercad now has a physics simulator built right in.
Thursday, 13 April
23:57
Intel Foundry Services Partners With Arm to Manufacture Next-Generation Mobile Chips SoylentNews
Intel Foundry Services partners with Arm to manufacture next-generation mobile chips:
Intel Corp. said today its Intel Foundry Services business unit is partnering with the British chip design firm Arm Ltd. to enable semiconductor designers to build low-power systems-on-chip on its cutting-edge manufacturing process.
The companies will initially focus on mobile SoC designs before expanding the deal to cover chips for automotive, internet of things, data center, aerospace and government applications. Under the agreement, customers that use Arm's designs as the basis of their chips will be able to use Intel's 18A process technology to manufacture their products.
The deal is said to be a big boon for customers, since Intel 18A is a more advanced process with capacity in both the U.S. and Europe. It will allow customers to design chips using electronic design automation software from third-party suppliers. EDA software is used by semiconductor engineers to create processor blueprints. The result will be more powerful processors with greater energy efficiency, Intel said.
Under the initiative, IFS and Arm will work together on design technology co-optimization, wherein chip design and process manufacturing are optimized to improve the power, performance and cost of Arm-based cores using the Intel 18A technology. Intel 18A is said to leverage two new technologies, including PowerVia for optimal power delivery and RibbonFET "gate all around" transistor architecture, which ensures optimal performance and power.
As part of this cooperation, IFS and Arm plan to develop a mobile reference design to demonstrate the technology to customers.
The deal is another key milestone for IFS, following its partnership with the Taiwanese semiconductor firm MediaTek Inc. that was announced last July. Intel set up the foundry business in 2021 to manufacture chips for other companies based on their own custom designs.
Read more of this story at SoylentNews.
23:40
Security updates for Thursday LWN.net
Security updates have been issued by Debian (chromium, firefox-esr, lldpd, and zabbix), Fedora (ffmpeg, firefox, pdns-recursor, polkit, and thunderbird), Oracle (kernel and nodejs:14), Red Hat (nodejs:14, openvswitch2.17, openvswitch3.1, and pki-core:10.6), Slackware (mozilla), SUSE (nextcloud-desktop), and Ubuntu (exo, linux, linux-kvm, linux-lts-xenial, linux-aws, smarty3, and thunderbird).
23:23
Strange New Explanation for Why Quantum World Collapses Into Reality Lifeboat News: The Blog

Get a Wonderful Person Tee: https://teespring.com/stores/whatdamath.
More cool designs are on Amazon: https://amzn.to/3wDGy2i.
Alternatively, PayPal donations can be sent here: http://paypal.me/whatdamath.
Hello and welcome! My name is Anton and in this video, we will
talk about the suggestion that horizons from black holes and the
expansion of the universe cause the quantum collapse into
reality.
Links:
https://arxiv.org/pdf/2301.00026.pdf.
#quantumphysics #blackhole #universe.
0:00 What this study is trying to solve.
2:05 Applying Einstein principles to Quantum Physics.
4:00 Do black holes server as observers?
5:00 What about the edge of the universe?
6:45 Does this prove universe is conscious? (no)
Support this channel on Patreon to help me make this a full time
job:
https://www.patreon.com/whatdamath.
Bitcoin/Ethereum to spare? Donate them here to help this channel
grow!
bc1qnkl3nk0zt7w0xzrgur9pnkcduj7a3xxllcn7d4
or ETH: 0x60f088B10b03115405d313f964BeA93eF0Bd3DbF
Space Engine is available for free here: http://spaceengine.org.
Enjoy and please subscribe.
23:22
Scientists discover a new circuit element, meminductor Lifeboat News: The Blog
Scientists have identified a new circuit element known as a meminductor. A circuit element is an electrical component used to help direct and control the flow of electricity through an electrical circuit. The classical three are known as the resistor, capacitor and inductor. Two additional circuit elements, the memristor and the memcapacitor, were only discovered in the past 15 years.
23:02
WhatsApp Introduces New Device Verification Feature to Prevent Account Takeover Attacks The Hacker News
Popular instant messaging app WhatsApp on Thursday announced a new account verification feature that ensures that malware running on a user's mobile device doesn't impact their account. "Mobile device malware is one of the biggest threats to people's privacy and security today because it can take advantage of your phone without your permission and use your WhatsApp to send unwanted messages,"
23:01
How we achieved a 6-fold increase in Podman startup speed Linux.com
By cutting unnecessary processes, you can realize near-real-time container startup, critical in cars and other time-sensitive applications.
Read More at Enable Sysadmin
The post How we achieved a 6-fold increase in Podman startup speed appeared first on Linux.com.
23:00
AMD Announces The Radeon PRO W7800/W7900 Series Phoronix
As the "world's first pro chiplet GPU", AMD today is announcing the Radeon PRO W7000 series as their first RDNA3-based professional offerings.
22:56
Re: ncurses fixes upstream Open Source Security
Posted by alice on Apr 13
having a patch that is possible to apply to ncurses would make this possible,since otherwise it's not possible to patch anything without just updating to the
latest ncurses snapshot.
that said,
- ncurses doesn't keep any git (or whatever) history anywhere (to my knowledge),
so i don't know where this would even come from
- as someone that uses the latest snapshots, 20230401 works, but 20230408 breaks
some applications like...
22:54
Re: ncurses fixes upstream Open Source Security
Posted by Sam James on Apr 13
"Jonathan Bar Or (JBO)" <jobaror () microsoft com> writes:Try emailing the distributions mailing list at lists.linux.dev too?
22:43
Canonical Livepatching Now Available For Ubuntu HWE Kernels Phoronix
Canonical announced today that their kernel livepatching service will now be available for their hardware enablement "HWE" kernels on Ubuntu Long-Term Support releases...
22:32
Google delivers secure open source software packages Help Net Security
Google has announced the Google Cloud Assured Open Source Software (Assured OSS) service, which aims to be a trusted source of secure open source packages, and the deps.dev API, which provides access to security metadata for 50+ million open source package versions. The Assured OSS service With Assured OSS, Google offers organizations the opportunity to integrate into their own developer workflows the same OSS packages Google uses and secures. Threat actors regularly attempt to compromise More
The post Google delivers secure open source software packages appeared first on Help Net Security.
22:02
Malicious ChatGPT & Google Bard Installers Distribute RedLine Stealer HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
Watch out for compromised Facebook business pages offering fake and malware-infected installers for ChatGPT and Google Bard AI chatbot.
This is a post from HackRead.com Read the original post: Malicious ChatGPT & Google Bard Installers Distribute RedLine Stealer
22:00
Multiphysics Analysis and Reliability for 5G/6G Antenna System Design IEEE Spectrum

Making 5G/6G technology real requires an increased density of more complex electronic systems in smaller form factors. As 5G/6G proliferates into safety critical systems and infrastructure, such as autonomous vehicles and healthcare, reliability is paramount.
Engineers must determine the performance and the lifetime of the systems they are designing and deploying. The increased density of components increases the interdependency of design considerations. For example, electromagnetic performance can no longer be considered in isolation from thermal and mechanical performance as they impact each other and are interdependent. Thermal issues are now one of the primary failure modes for electronic systems.
Register now for this free webinar.
Studying antenna array and tower structural integrity, you need to account for electro-thermal effects and thermal impact on data coverage. This includes interference, optimizing antenna design, and performance under severe wind loads with critical angles of attack to incorporate mechanical effects in an integrated workflow to determine thermal stress-induced deformation at the PCB level or the more detailed solder ball level to random model vibration, drop test, and fatigue studies.
All can help estimate the complete system performance and reliability under various external circumstances. Ansys dedicated electronics reliability solutions can make lifetime predictions by computing the cumulative damage index, time to failure, and life curve.
What You Will Learn
- Predict electrical performance drift under varying environmental conditions and thermal impact on RF link margin
- Assess and evaluate thermal management systems for cost/reliability tradeoffs
- Understand antenna deformation due to mechanical loads and structural specifications
- Right-sizing of antenna system housings and support structures to meet reliability targets while minimizing size and weight
Who Should Attend?
CAE Analyst Mechanical Engineer Reliability Engineer RF Engineer
21:29
Holding Sirius Corporation Criminally Accountable schestowitz.com
Video
download link | md5sum
Time for Sirius Management to Face Prison
Creative Commons Attribution-No Derivative Works 4.0
Summary: The crimes of Sirius Open Source are very serious; weve come to the point now where its more or less a countdown ahead of arrests or class action lawsuit (or both)
TODAY we published a lot of material about Sirius Open Source and since recording the above video weve published a little more.
In light of what Standard Life told us last night (they sent a letter at night, which is unusual for firms that work 9 to 5), were now progressing the case against a company that defrauded GNU/Linux system administrators, Free software specialists, programmers and so on.
This is now a criminal matter. Several people need to be arrested.
The issue is further complicated by an NDA signed with the Gates Foundation (we dont even know the details of it). The principal fraudster now resides in Washington, the state. To get full accountability they will likely have to issue an extradition warrant (sent from authorities in the UK to the US). This adds a number of new dimensions, including the divorce. The financial fugitive has many liabilities in the UK. Some of these issues are discussed in length in the video above.
21:24
The Boss of Sirius Open Source and His Ex-Wife Should be Reunited Inside the Prison Cell Techrights
Video
download link | md5sum
Time for Sirius Management to Face Prison
Creative Commons Attribution-No Derivative Works 4.0
Summary: The crimes of Sirius Open Source are very serious; weve come to the point now where its more or less a countdown ahead of arrests or class action lawsuit (or both)
TODAY we published a lot of material about Sirius Open Source and since recording the above video weve published a little more.
In light of what Standard Life told us last night (they sent a letter at night, which is unusual for firms that work 9 to 5), were now progressing the case against a company that defrauded GNU/Linux system administrators, Free software specialists, programmers and so on.
The principal fraudster now resides in Washington, the state. To get full accountability they will likely have to issue an extradition warrant (sent from authorities in the UK to the US).This is now a criminal matter. Several people need to be arrested.
The issue is further complicated by an NDA signed with the Gates Foundation (we dont even know the details of it). The principal fraudster now resides in Washington, the state. To get full accountability they will likely have to issue an extradition warrant (sent from authorities in the UK to the US). This adds a number of new dimensions, including the divorce. The financial fugitive has many liabilities in the UK. Some of these issues are discussed in length in the video above.
21:22
Pakistani court utilizes ChatGPT-4 to grant bail in a juvenile kidnapping case Lifeboat News: The Blog
The court claimed that after posing a number of inquiries to the AI chatbot, it was pleased with the responses received.
A municipal court in Pakistan has announced its judgment using artificial intelligence technology, a first for the Asian country.
The case was processed by ChatGPT-4, OpenAIs cutting-edge AI chatbot, before the local judge announced the decision, Samaa reported on Wednesday.
21:22
OpenAI launches $20k Bug Bounty Program to make its products safer Lifeboat News: The Blog
The company is offering rewards for exceptional discoveries.
OpenAI, the creator of conversational chatbot ChatGPT, has announced a Bug Bounty program where users can report vulnerabilities, bugs, or security flaws and be financially rewarded for finding them. The company has announced rewards ranging from $200 to $20,000 depending on the severity of the flaw and teamed up with a popular bug-finding platform to streamline the process.
OpenAIs ChatGPT has ushered in a race for artificial intelligence (AI) models that provide comprehensive solutions to user queries and can even simulate intriguing imagery with the help of a few text prompts.
Sestovic/iStock.
While the technology is advancing at a breathtaking pace and producing some mind-boggling results, there are also concerns about these products safety. AI researchers like Stuart Russell have warned that unchecked, the rise of AI could result in a Chernobyl-like incident for the tech industry.
21:22
Robotics firm promises new robot masseuse will be different this time Lifeboat News: The Blog

Its not unusual for a company to try and innovate on an existing products or technology, but robotics firm Flexiv promises that its massaging robot wont be like the mechanical massagers of the past.
Robotic or mechanical messagers are hardly a new idea, but a robotics firm called Flexiv is hoping that its new robot masseuse will succeed where others have succeeded at becoming a novelty at best and an embarrassing disaster at worst.
Announced earlier this week on its website, Flexiv is debuting its Rizon 4 robot which has been developed to enable a fully automatic massage experience.
21:13
Bad News: Copyright Industry Attacks on the Internets Plumbing are Increasing and Succeeding SoylentNews
Bad news: copyright industry attacks on the Internet's plumbing are increasing and succeeding:
Back in October 2021, Walled Culture wrote about a ruling from a US judge. It concerned an attempt to make the content delivery network (CDN) Cloudflare, which is simply part of the Internet's plumbing, responsible for what flows through its connections. The judge rightly decided: "a reasonable jury could not at least on this record conclude that Cloudflare materially contributes to the underlying copyright infringement".
A similar case in Germany was brought by Sony Music against the free, recursive, anycast DNS platform Quad9. Like CDNs, DNS platforms are crucial services that ensure that the Internet can function smoothly; they are not involved with any of the sites that may be accessed as a result of their services. In particular, they have no knowledge of whether copyright material on those sites is authorised or not. Unfortunately, two regional courts in Germany don't seem to understand that point, and have issued judgments against Quad9. Its FAQ on one of the cases explains why this is a dreadful result for the entire Internet:
The court argues with the German law principle of "interferer liability" the so-called "Stoererhaftung", which allows holding uninvolved third parties liable for an infringement if they have in some way adequately and causally contributed to the infringement of a protected legal interest. If DNS resolvers can be held liable as interferers, this would set a dangerous precedent for all services used in retrieving web pages. Providers of browsers, operating systems or antivirus software could be held liable as interferers on the same grounds if they do not prevent the accessibility of copyright-infringing websites.
Now an Italian court has confirmed a previous ruling that Cloudflare must block certain online sites accused of making available unauthorised copies of material. That's unfortunate, since taken with the German court rulings it is likely to encourage the copyright industry to widen its attack on the Internet's plumbing, regardless of th...
21:10
New Python-Based "Legion" Hacking Tool Emerges on Telegram The Hacker News
An emerging Python-based credential harvester and a hacking tool named Legion is being marketed via Telegram as a way for threat actors to break into various online services for further exploitation. Legion, according to Cado Labs, includes modules to enumerate vulnerable SMTP servers, conduct remote code execution (RCE) attacks, exploit unpatched versions of Apache, and brute-force cPanel and
21:00
Custom Bluetooth Adapter Brings 1990s Car Phone Back Online Hackaday

[Jeff Lau]s Mitsubishi 3000GT comes with all the essential features youd expect in a fancy sports car from 1993: pop-up headlights, movable spoilers, and a fully-functional telephone handset in the center console. The phone was fully functional until North Americas first-generation AMPS cellular network was shut down back in 2008, since then, it hasnt done much but show NO SVC on the display. That is, until [Jeff] decided to build a Bluetooth adapter that lets it connect to a modern smartphone.
The easy solution would have been to simply connect the handsets speaker and microphone to a standard Bluetooth headset, but that would have destroyed the 1990s aesthetic it had going on. So what [Jeff] did instead was construct a plug-in module that hooks up to the phones base station in the trunk and communicates directly with all the existing systems. That way, the phone works in exactly the same way it always did: the rad...
20:49
Standard Life Facilitated Fraud Against Free/Libre Software and GNU/Linux Technicians schestowitz.com
This is what they sent me in 2011 (other Free/libre software and GNU/Linux enthusiasts were also scammed this way):
Along with 7 pages in total:
Summary: The pension fraud of Sirius Open Source was facilitated by Standard Life; the very large pension fund, which is based in Scotland, needs to pay reparations to many victims (we cannot even tell how many; these are colleagues who are unaware of whats going on) and the criminals need to be arrested (the fugitive in the United States needs to be extradited to face justice for his crimes)
20:48
Lenovo Yoga Laptops Getting Tablet Mode Switch Driver With Linux 6.4 Phoronix
For those with a Lenovo Yoga 2-in-1/convertible laptop, a tablet mode switch driver is set to be merged for Linux 6.4 to properly handle the tablet mode switching support for these devices while running the mainline Linux kernel...
20:44
Photographic Evidence of Standard Lifes Involvement in Fraudulent Pensions (Many Victims Affected) Techrights
This is what they sent me in 2011 (other Free/libre software and GNU/Linux enthusiasts were also scammed this way):
Along with 7 pages in total:
Summary: The pension fraud of Sirius Open Source was facilitated by Standard Life; the very large pension fund, which is based in Scotland, needs to pay reparations to many victims (we cannot even tell how many; these are colleagues who are unaware of whats going on) and the criminals need to be arrested (the fugitive in the United States needs to be extradited to face justice for his crimes)
20:32
Intel oneVPL GPU Runtime 2023Q1 Adds AV1 Error Resilient Mode Phoronix
Days after releasing the Intel Media Driver 2023Q1, Intel's software engineers have now released oneVPL 2023Q1 as the updated quarterly release to this video processing library that is part of Intel's open-source oneAPI toolkit...
20:30
Fortinet fixed a critical vulnerability in its Data Analytics product Security Affairs
Fortinet addressed a critical vulnerability that can lead to remote, unauthenticated access to Redis and MongoDB instances.
Fortinet has addressed a critical vulnerability, tracked as CVE-2022-41331 (CVSS score of 9.3), in its Fortinet FortiPresence data analytics solution.
FortiPresence is a comprehensive data analytics solution designed for analyzing user traffic and deriving usage patterns.
Successful exploitation can lead to remote, unauthenticated access to Redis and MongoDB instances via crafted authentication requests.
A missing authentication for critical function vulnerability [CWE-306] in FortiPresence on-prem infrastructure server may allow a remote, unauthenticated attacker to access the Redis and MongoDB instances via crafted authentication requests. reads the advisory published by the vendor.
The vulnerability affects FortiPresence 1.2 all versions, FortiPresence 1.1 all versions, and FortiPresence 1.0 all versions. The company added that Cloud instances of FortiPresence are not impacted.
Fortinet addressed multiple vulnerabilities in its products as part of its April 2023 Vulnerability Advisories, below are the most severe ones:
- CVE-2022-43955 (CVSS score of 8) FortiWeb XSS vulnerability in HTML generated attack report files
- CVE-2022-27487 (CVSS score of 8.3) FortiSandbox / FortiDeceptor Improper profile-based access control over APIs
- CVE-2022-41330 (CVSS score of 8.3) FortiOS & FortiProxy Cross Site Scripting vulnerabilities in administrative interface
Customers are recommended to update their instances as soon as possible.
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections:
- The Teacher Most Educational Blog
- The Entertainer Most Entertaining Blog
- The Tech Whizz Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please nominate Security Affairs as your favorite blog.
...20:19
Why Shadow APIs are More Dangerous than You Think The Hacker News
Shadow APIs are a growing risk for organizations of all sizes as they can mask malicious behavior and induce substantial data loss. For those that aren't familiar with the term, shadow APIs are a type of application programming interface (API) that isn't officially documented or supported. Contrary to popular belief, it's unfortunately all too common to have APIs in production that no one on
Pakistan-based Transparent Tribe Hackers Targeting Indian Educational Institutions The Hacker News
The Transparent Tribe threat actor has been linked to a set of weaponized Microsoft Office documents in attacks targeting the Indian education sector using a continuously maintained piece of malware called Crimson RAT. While the suspected Pakistan-based threat group is known to target military and government entities in the country, the activities have since expanded to include the education
20:01
LinkedIn now allows you to verify your workplace Help Net Security
To combat the surge of fake LinkedIn accounts in recent years, Microsoft has introduced Entra Verified ID, a new feature that allows users to verify their workplace on the business-focused social media platform. Verified ID automates verification of identity credentials (Source: Microsoft) How to verify your workplace on LinkedIn With Entra Verified ID, organizations can create customized digital employee IDs that employees can use to prove their current employment with the firm. LinkedIn users can More
The post LinkedIn now allows you to verify your workplace appeared first on Help Net Security.
19:58
Servo Project To Focus On Their "Layout 2020" Engine Phoronix
Servo as the browser engine started at Mozilla but now developed as a Linux Foundation project has been maintaining two separate layout engines and moving forward they hope to be able to focus on the newer "Layout 2020" engine and fill in its missing gaps...
19:22
Playing table tennis against robotic player makes human brain work harder Lifeboat News: The Blog
To analyze the human players brain, the team designed a cap with over 100 electrodes mounted on a backpack-sized device.
A one-of-a-kind study documents how a human brain reacts when playing table tennis against a robotic opponent.
Scanning the brain activity with electrodes.
Frazier Springfield.
This study by the University of Florida scientists provides intriguing insights into human brain activity. The findings revealed that human players brains reacted differently to opponents (other humans and ball machines). And playing against a robotic opponent was much more difficult for the human brain.
19:22
Ultra-luminous X-ray sources defy Eddington limit and unlock universal secrets Lifeboat News: The Blog
The mystery of ultra-luminous X-ray sources (ULXs) and their astonishing brightness has been partially unraveled through a recent study utilizing NASAs NuSTAR.
Scientists have long been perplexed by ultra-luminous X-ray sources (ULXs), cosmic objects that emit about 10 million times more energy than the Sun and appear to break the Eddington limit a physical boundary that determines the maximum brightness of an object based on its mass. In a groundbreaking study published in The Astrophysical Journal, researchers have confirmed that these extraordinary light emitters surpass the Eddington limit, potentially due to their strong magnetic fields.
The effect of Eddington limit and magnetic fields
The Eddington limit plays a crucial role in determining the balance between the outward push of photons and the inward pull of an objects gravity. When an object reaches the Eddington limit, its light pushes away any gas or material falling toward it, thus controlling its brightness. The study focused on the ULX M82 X-2, a neutron star that was found to be stealing about 9 billion trillion tons of material from a neighboring star annually. The researchers calculations confirmed that M82 X-2 exceeds the Eddington limit.
The new study supports an alternative hypothesis that suggests strong magnetic fields can distort atoms into elongated shapes, reducing the photons ability to push atoms away and ultimately increasing an objects maximum brightness. By examining more ULXs, scientists may be able to further understand the role of magnetic fields in their extraordinary luminosity.
19:22
Miniature solar flares made in lab offer insight into high-speed energetic particles Lifeboat News: The Blog
The team created a vacuum chamber equipped with twin electrodes to simulate the coronal loop phenomenon.
Coronal loops are arcs of curving plasma that appear above the Suns surface. These loops are so powerful that they can travel up to 100,000 kilometers above the surface of the Sun and last for minutes to hours.
Understanding coronal loops.
NASA
However, there are numerous underlying factors that scientists are attempting to decipher in relation to coronal loops. With that stated, Caltech scientists have created a tiny coronal loop in a laboratory, which could help them closely understand the suns dynamics.
19:08
New Data Out From ONS (Week 12): Number of Deaths in England and Wales 16% Higher Than Before the Pandemic schestowitz.com
Some new numbers this morning*.
2019***: 10,402 deaths
2014-19 average***: 10,456 deaths
2022**: 10,747 deaths
2023**: 12,052 deaths
(12052-10402)/10402*100=15.86.
_____
*
As per 9:40 AM (earlier than 10, the usual time). Was supposed
to be out on Tuesday, but this time it got delayed till 13 April
2023 (due to Easter/Bank Holiday).
** From ONS (above).
*** From ONS (historic)
19:07
Lazarus Hacker Group Evolves Tactics, Tools, and Targets in DeathNote Campaign The Hacker News
The North Korean threat actor known as the Lazarus Group has been observed shifting its focus and rapidly evolving its tools and tactics as part of a long-running activity called DeathNote. While the nation-state adversary is known for its persistent attacks on the cryptocurrency sector, it has also targeted automotive, academic, and defense sectors in Eastern Europe and other parts of the world
18:54
How to Combat Insider Threats Security Affairs
Knowing that insider threats are a risk is one thing. Knowing how to fight them off is entirely another.
Dealing with issues of insider cyber risk can be different and nuanced. Its hard to admit that someone from within the company could not be who they say they are, and it takes a group effort to get these types of programs off the ground.
However, over one-third of businesses are impacted by insider threats every year, and US businesses face about 2.500 internal security breaches in the aggregate per day. These cases are out there. No company with any zero-trust initiatives can responsibly look the other way.
The question isnt why to build out an insider threat prevention program: its how.
The origin and impact of insider risk
To understand best how to combat them, it helps to know where insider threats originate and why.
As cited in TechJury, more than two out of three insider threats are caused by negligence. Fraud, financial gain, and intellectual property theft are the primary motivators, and trusted business partners typically account for 15-25% of the cases across all industries. Nine in ten result from human error.
What starts as a careless, disgruntled, or simply ignorant employee maneuver can result in credential theft, data loss, and unforeseen damage. These arent insignificant encounters: Credential theft can cost upwards of $850,000 per incident, and companies are now spending 60% more than they did three years ago combatting the effects of insider risk. In most cases (85%), companies cant even definitively determine the cost of the overall damage caused by these types of incidents.
Fortunately, some great products are out there to help organizations get a handle on the insider threat problem and make inroads into securing their digital enterprise from the inside out.
The top insider threat software products of 2023
Data Detection and Response (DDR) company Cyberhaven offers valuable insights into some of the top security tools designed with inside threats in mind. For a quick rundown, they are:
- Aware | This helps monitor messaging apps like Slack and Microsoft Teams
- Exabeam | A mature vendor that leverages SIEM and XDR to spot internal anomalies
- Gurucul | Baselines user behavior using AI-based tools and leverages social media data...
18:34
Anti-Piracy Mega-Firewall Could Render Italian ISPs Liable For Over-Blocking TorrentFreak
 Last month a bill crafted to crack down on pirate
IPTV services was
unanimously approved by Italys Chamber of Deputies.
Last month a bill crafted to crack down on pirate
IPTV services was
unanimously approved by Italys Chamber of Deputies.
If passed by the Senate, broadcasters through telecoms regulator AGCOM will have new powers to compel internet service providers to block pirate streams in a matter of minutes, potentially seconds. Site-blocking measures to deal with piracy are nothing new in Italy, but by narrowing the blocking window, the window for correcting errors is narrowed too.
Italys Mega-Firewall
The Association of Italian Internet Providers (AIIP) represents the interests of small to medium-sized ISPs in Italy. Given that ISPs are already required to implement AGCOMs blocking instructions under the current regime, it follows that they will also have key responsibilities under the proposed rapid blocking system.
AIIP recently revealed that it had sent a memorandum to the authorities detailing its concerns over the current proposals, which are already in the final stages before becoming law.
President of AIIP, Giovanni Zorzoni, says that the objective appears to be the creation of a mega-firewall managed by AGCOM which will have the legal authority to compel internet service providers to implement it, regardless of the inherent risks.
The creation of a homogeneous infrastructure based on a synchronous filtering system, capable of interfacing simultaneously with the operators offering access to the Internet, with the CDNs and with the Cloud operators, constitutes a single susceptible point of failure to undermine the security and resilience of national networks, Zorzoni warns.
Critical Need to Protect Critical Infrastructure
AIIP says it has always been in favor of copyright protection but says the speed at which the blocking proposals are being pushed through is a cause for concern. AIIP says that in advance of the Senates forthcoming examination, it is seeking a reassessment to ensure an adequate balance between the protection of intellectual property on one hand, and the protection of the internet ecosystem on the other.
AIIP reports progress in the form of a government commitment to evaluate the preparation of a whitelist of IP addresses and servers for the root zone of the Domain Name System (DNS) that can not be included in the blocking program. Since this would minimize the risks of erroneously disabling critical systems, AIIP hopes the government will fully implement the proposal....
18:27
3CX Knew its App Was Flagged as Malicious but Took No Action for 7 Days SoylentNews
The support team for 3CX, the VoIP/PBX software provider with more than 600,000 customers and 12 million daily users, was aware its desktop app was being flagged as malware but decided to take no action for a week when it learned it was on the receiving end of a massive supply chain attack, a thread on the company's community forum shows.
"Is anyone else seeing this issue with other A/V vendors?" one company customer asked on March 22, in a post titled "Threat alerts from SentinelOne for desktop update initiated from desktop client." The customer was referring to an endpoint malware detection product from security firm SentinelOne. Included in the post were some of SentinelOne's suspicions: the detection of shellcode, code injection to other process memory space, and other trademarks of software exploitation.
Read more of this story at SoylentNews.
18:01
IRC Proceedings: Wednesday, April 12, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-120423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-120423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-120423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-120423.gmi
Over HTTP:
|
... |
18:00
What Can You Do With Discarded Fish Aggregation Devices Hackaday

Often we bring you projects at the end of their trajectory so that you can marvel at a job well done, but sometimes we point you instead to the start of the story. Such is the case with [Brett Smith]s investigation of discarded fish aggregation buoys, referred to as FADs. These 700-plus dollar devices are deployed in the ocean in the thousands by commercial fishing fleets, and most are not recovered. Hes looking at them from the point of view of re-using their technology in the marine conservation business.
His progress has been documented in a series of short YouTube videos, starting with an introduction that weve placed below the break. So far hes gone on to a complete teardown, and then a detailed look at the PCB. Inside they have a solar charger for a bank of NiCd cells, an echo sounder, a GPS receiver, and an Iridium satellite modem allowing the device to phone home. Theres certainly plenty in there to experiment with, including a few slightly exotic parts, so keep an eye on his channel as were sure to see more.
These devices have never made it to Hackaday before, but we have seen...
17:00
Were Recent Bank Failures the Result of Lax Regulation? In a Word, No Terra Forming Terra
Of course not. Regulation only applies to those with the
least at stake. Otherwise bribery always rules the day.
The Culling of Mankind Terra Forming Terra

Analysis: COVID Vaccines Caused 300,000 Excess Deaths in 2022 Alone Terra Forming Terra
New Research Rewrites the History of American Horses Terra Forming Terra
:focal(2709x1831:2710x1832)/https:/tf-cmsv2-smithsonianmag-media.s3.amazonaws.com/filer_public/4d/20/4d20bdfc-794f-4984-b9eb-b9977cac6fa4/gettyimage)
The advent of the horse in North America has always been an obvious Spanish event, and our own experience with mustang herds informs us just how it always happened.
What makes it all interesting is that a full sized riding horse evolved more recently than we assume. Remember chariots? We used those until far too recently and surely that meant smaller horses generally. I do think that horsemanship was on horses that were mostly pony sized and great for pulling a chariot.
15:45
Open Source is Fueling the Future of Nuclear Physics SoylentNews
This once secretive scientific field is embracing openness in a big way:
The words "nuclear physics" tend to conjure images of heavily guarded laboratories or trench-coated spies whispering to each other on park benches and exchanging briefcases full of file folders stamped "Classified: Top Secret." But despite this reputation for secrecy, today's nuclear scientists embrace openness. And it's paying off.
[...] Many nuclear science organizations have released open source software in recent years, which is a big change from business as usual in the field. Though CERN, which focuses on fundamental particle physics rather than energy generation, is the birthplace of the web and has long embraced open source, other institutions have historically been less open. "There's a history of secrecy in the field. Most fusion and fission software used to be proprietary," says Paul Romano, the project lead for OpenMC and a computational scientist working in nuclear fusion at Argonne National Laboratory. "But as open source has exploded over the past decade, it plays an increasingly important role in research, both in the public and private sectors."
Despite open source's many benefits, it took time for the nuclear science field to adopt the open source ethos. Using open source tools was one thingPython's vast ecosystem of mathematical and scientific computing tools is widely used for data analysis in the fieldbut releasing open source code was quite another.
[...] Many of these projects that started with nuclear science in mind are applicable to just about any field that benefits from using supercomputers. MFEM, for example, is also used in LLNL's cardiac simulation toolkit Cardioid, its crystal plasticity application ExaConstit, and its thermomechanical simulation code Serac. It is also heavily used by the broader scientific community, including industry and academia, in applications such as MRI research at Harvard Medical School, and quantum computing hardware simulation at Amazon. MOOSE is widely used outside of the nuclear field, with applications in areas such as groundwater modeling and other geoscience use cases. During the early days of the Covid-19 pandemic, researchers at LLNL used Merlin to anticipate outbreaks and Maestro for antibody modeling.
...
15:43
Links 13/04/2023: Nanonote 1.4.0 and LWN Looks at Mobian Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
dwaves.de TuxMath Game now also as Android App SpaceX methane + GNU Linux powered StarShip Maiden flight
Mobile Version: https://f-droid.org/packages/org.afrikalan...
-
15:12
15:08
[Meme] The Fraud-o-mat Techrights
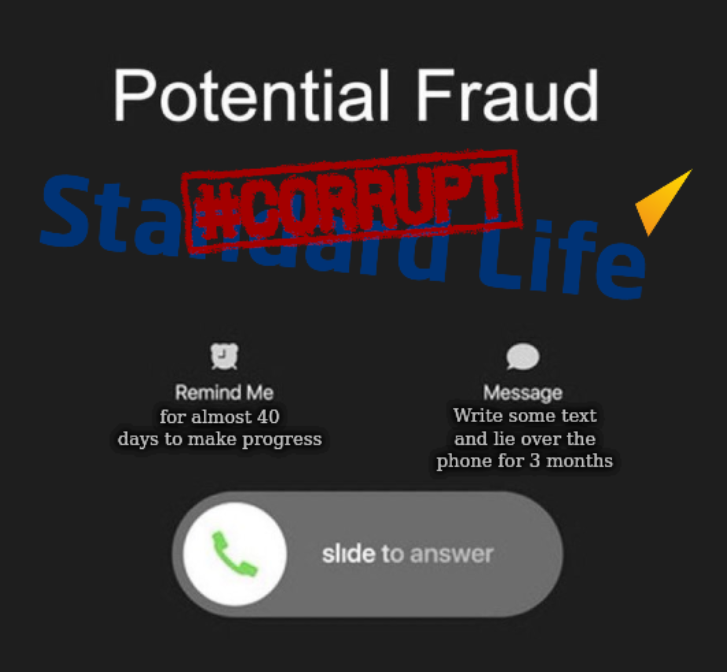
Summary: Pension-Fraud-as-a-Service (PFaaS) is sound business; Standard Life profited from facilitating pension fraud at Sirius Open Source; its a profound problem when financial institutions exist to maximalise profits, which means that they have greater incentive to cover up abuses, more so when complicity can be demonstrated
15:01
The Kodi Foundation - 400,635 breached accounts Have I Been Pwned latest breaches
In February 2023, The Kodi Foundation suffered a data breach that exposed more than 400k user records. Attributed to an account belonging to "a trusted but currently inactive member of the forum admin team", the breach involved the administrator account creating a database backup that was subsequently downloaded before being sold on a hacking forum. The breach exposed email and IP addresses, usernames, genders and passwords stored as MyBB salted hashes. The Kodi Foundation elected to self-submit impacted email addresses to HIBP.
15:01
Standard Life Covers Up Its Role in Pension Fraud, Lies to the Victims Techrights
In their own words (lies or contradictions included):
Summary: After almost 40 days Standard Life finally gets back (in writing) to victims of the fraud at Sirius Open Source; the response is designed to help Standard Life wash its hands without actually tackling fraud committed in its name (and with documents produced by Standard Life, not forged)
HOURS after I prodded Standard Life by E-mail they finally got back to me (and others) with something more concrete. As expected, they did nothing to actually solve the problem and in the process they resorted to lying to us about the dates.
I got response from standard life, one former colleague told me.
My former colleague noticed a glaring anomaly in their narrative/story.They have stated I can confirm Standard Life has administered a pension scheme for Sirius Corporation Plc from July 2009 until December 2012. Unfortunately, there is no record of you joining the scheme during that time and it would not have been possible to join after the Scheme closed in 2012.
Notice the above. They just used templates. They barely investigated anything on an individual basis, yet in their PDF they made it seem like it was tailored to the recipient, including individual passwords. All they changed was the name of the person and maybe the case number.
My former colleague noticed a glaring anomaly in their narrative/story. This seems to be slightly different to what you have been told, the former colleague said, as I think you said it was moved in 2018.
2016 was said repeatedly to me by the manager, on several occasions. So either the above letter contains a lie or the managers lied to me repeatedly over the telephone.
Here is the message I received:
Dear Dr Schestowitz
Ive completed my investigation of your concerns since I last contacted you on 29 March 2023. Thank you for your patien...
15:00
Autopsy Of A Drifting Thumbstick Reveals All Hackaday

Analog sticks have become a core part of modern video game controllers. They also routinely fail or end up drifting, consigning expensive controllers to the garbage. [sjm4306] recently did a repair job on an Oculus VR gaming controller with drifting analog sticks, and decided to do an autopsy to figure out what actually went wrong.
14:55
Listen to the "Everything Epigenetics" podcast with our Hannah Went on Apple, Spotify, and YouTube. Lifeboat News
Listen to the "Everything Epigenetics" podcast with our Hannah Went on Apple, Spotify, and YouTube. Connect with the show on Facebook and Instagram.
14:47
Standard Life Profits From Facilitating Pension Fraud schestowitz.com
In their own words (lies or contradictions included):
Summary: After almost 40 days Standard Life finally gets back (in writing) to victims of the fraud at Sirius Open Source; the response is designed to help Standard Life wash its hands without actually tackling fraud committed in its name (and with documents produced by Standard Life, not forged)
HOURS after I prodded Standard Life by E-mail they finally got back to me (and others) with something more concrete. As expected, they did nothing to actually solve the problem and in the process they resorted to lying to us about the dates.
I got response from standard life, one former colleague told me.
They have stated I can confirm Standard Life has administered a pension scheme for Sirius Corporation Plc from July 2009 until December 2012. Unfortunately, there is no record of you joining the scheme during that time and it would not have been possible to join after the Scheme closed in 2012.
Notice the above. They just used templates. They barely investigated anything on an individual basis, yet in their PDF they made it seem like it was tailored to the recipient, including individual passwords. All they changed was the name of the person and maybe the case number.
My former colleague noticed a glaring anomaly in their narrative/story. This seems to be slightly different to what you have been told, the former colleague said, as I think you said it was moved in 2018.
2016 was said repeatedly to me by the manager, on several occasions. So either the above letter contains a lie or the managers lied to me repeatedly over the telephone.
Here is the message I received:
Dear Dr Schestowitz
Ive completed my investigation of your concerns since I last contacted you on 29 March 2023. Thank you for your patience.
Ive attached a letter which outlines our position [...]
If you have any questions, or you are having a problem accessing the letter, please let me know.
Yours sincerely
???????? ??????????????
Customer Relations
slcomplaints@standardlife.com
The name is in the image, but we dont want that in text.
This is more like a cover-up, not an investigation. Did it take them a...
14:35
ChatGPT Security: OpenAI's Bug Bounty Program Offers Up to $20,000 Prizes The Hacker News
OpenAI, the company behind the massively popular ChatGPT AI chatbot, has launched a bug bounty program in an attempt to ensure its systems are "safe and secure." To that end, it has partnered with the crowdsourced security platform Bugcrowd for independent researchers to report vulnerabilities discovered in its product in exchange for rewards ranging from "$200 for low-severity findings to up to
14:30
The new weakest link in the cybersecurity chain Help Net Security
It used to be that people were the greatest cybersecurity vulnerability, but this is no longer true. The rise of the internet made people more connected than ever. Attackers capitalized on that fact and targeted employees directly to gain access to an organization. Leveraging highly automated methods (such as phishing that redirects users to compromised websites), attackers must only fool one employee to start a catastrophic attack against the entire organization. These methods are extremely More
The post The new weakest link in the cybersecurity chain appeared first on Help Net Security.
14:00
5 steps to building NSA-level access control for your app Help Net Security
Access control has become a main concern when it comes to developing secure web applications, and the NSA has a lot to say about it. Especially when it comes to the biggest access management pitfall developers make. In 2021 OWASP listed Broken Access Control as their A01 item on the list of Top 10 web application security risks. The 2020 Verizon data breach investigations report states that At least two-thirds of cyberattacks are now focused More
The post 5 steps to building NSA-level access control for your app appeared first on Help Net Security.
13:59
Linux Jobs in the UK Mailing List Censors Message Cautioning About Fraud in Company That Advertises Job (Sirius Open Source) Techrights
Did Sirius pressure the administrator to start censoring (gagging) its victims?
Summary: Victims of fraud committed by Sirius Open Source speak out in response to a job ad (workers are fleeing in droves, creating severe vacuum) and the administrator of the list resorts to censorship
Almost 24 hours have passed and the following message was not approved by the moderator, so Im reproducing it here:
Re: [linuxjobs] Helpdesk Operator roles at Sirius
> When I saw the praise for Sirius I did cringe to myself because I also find
> them to be a scummy company. I thought Id avoid responding, because
> frankly life is too short. However, this veiled threat of libel is simply
> ridiculous, so now I am going to respond.
>
> The reason I find them scummy is because I worked on a project with them
>> 10 years ago, and they simply didnt pay me and ignored reminders to pay
> the invoice. The project was ultimately cancelled as the client changed
> their mind, so I guess Sirius thought they didnt need to pay me.
>
> It wasnt even a huge sum of money, but it was enough to totally burn their
> reputation with me. So yeah, if they want to sue me for libel, bring it
> the fuck on.Hi Dave,
These tactics arent new. Only a week after I had resigned I received a threatening and legally-invalid letter from the CEO telling me to remove any criticism of the company (published after I already resigned).
http://techrights.org/wiki/Sirius_Open_Source#Attempts_to_Censor_Facts
Last month the above-mentioned CEO abruptly left the company and in recent weeks he worked hard to hide all traces of him ever working for Sirius:
http://techrights.org/2023/03/13/sirius-deleted-entirely/
http://techrights.org/2023/03/21/sirius-open-source-purged/
Today: http://techrights.org/2023/04/12/sirius-no-more/
It is imperative that people understand what Sirius really is to prevent this mailing list being leveraged to groom future victims.Kind regards,
13:38
Linux Foundation Events Code of Conduct Transparency Report 2022 Event Summary Linux.com
![]()
Read the original blog at Read More
The post Linux Foundation Events Code of Conduct Transparency Report 2022 Event Summary appeared first on Linux.com.
13:30
Technology investments feel the impact of weakening economy Help Net Security
For the fifth consecutive month, IDC has lowered its 2023 forecast for worldwide IT spending as technology investments continue to show the impact of a weakening economy. 2023 forecast for worldwide IT spending In its monthly forecast for worldwide IT spending growth, IDC projects overall growth this year in constant currency of 4.4% to $3.25 trillion. This is slightly down from 4.5% in the previous months forecast and represents a swing from a 6.0% growth More
The post Technology investments feel the impact of weakening economy appeared first on Help Net Security.
13:24
The Web Site Its FOSS Is Not Always FOSS (Sometimes Actively Harmful to FOSS) Techrights
Summary: Its FOSS changed editorial control some time ago; two of the main authors are barely active anymore and it shows (loss of direction). Its not the first such fluke. It keeps happening. Why promote (1) Microsoft and (2) proprietary stuff in a site called Its FOSS? What message does that send to FOSS proponents?
Its FOSS: Is it still for FOSS? As shown weeks ago (E-mail and Webform) to the sites editors and founder, there was a push to promote Microsofts proprietary chaffbot, in effect leading people away from FOSS and promoting anti-GPL territories. Hours ago there was this piece entitled How to Connect GitHub to VS Code [Step by Step] (they should instead guide readers away from these)
How would we feel about Greenpeace publishing an article, how to make the most out of coal?
13:00
DDoS alert traffic reaches record-breaking level of 436 petabits in one day Help Net Security
With over one billion websites worldwide, HTTP/HTTPS application-layer attacks have increased by 487% since 2019, with the most significant surge in the second half of 2022, according to NETSCOUT. The dynamic nature of the DDoS threat landscape Much of the increase comes from the pro-Russian group Killnet and others that explicitly target websites. Attacks of this nature preceded the Ukraine invasion, knocking out critical financial, government, and media sites. DDoS attacks threaten organizations worldwide and More
The post DDoS alert traffic reaches record-breaking level of 436 petabits in one day appeared first on Help Net Security.
12:58
The Hottest New Climate Technology is Bricks SoylentNews
Heat batteries could help cut emissions by providing new routes to use solar and wind power:
A handful of startups think bricks that hold heat could be the key to bringing renewable energy to some of the world's biggest polluters.
Industries that make products ranging from steel to baby food require a lot of heatmost of which is currently generated by burning fossil fuels like natural gas. Heavy industry makes up about a quarter of worldwide emissions, and alternative power sources that produce fewer greenhouse gases (like wind and solar) can't consistently generate the heat that factories need to manufacture their wares.
Enter heat batteries. A growing number of companies are working to deploy systems that can capture heat generated by clean electricity and store it for later in stacks of bricks. Many of these systems use simple designs and commercially available materials, and they could be built quickly, anywhere they're needed. One demonstration in California started up earlier this year, and other test systems are following close behind. They're still in early stages, but heat storage systems have the potential to help wean industries off fossil fuels.
One key to heat batteries' potential success is their simplicity. "If you want to make it to giant scale, everybody ought to agree that it's boring and reliable," says John O'Donnell, CEO of California-based heat storage startup Rondo Energy
Many industrial processes run 24 hours a day, so they'll need constant heating. By carefully controlling the heat transfer, Rondo's system can charge quickly, taking advantage of short periods when electricity is cheap because renewable sources are available. The startup's heat batteries will probably require about four hours of charging to be able to provide heat constantly, day and night.
Read more of this story at SoylentNews.
12:50
FSF: Googles Decision to Deprecate JPEG-XL Emphasises the Need for Browser Choice and Free Formats Techrights
This work is licensed under a Creative Commons Attribution-No Derivative Works 3.0 license (or later version) Original from FSF
Whether its
through the millions of dollars Google has funneled into
development and advertising or the convenience that it offers users
in exchange for freedom, the fact remains that Google Chrome is the
arbiter of web standards. Firefox, through ethical distributions
like GNU IceCat and
Abrowser, can weaken that stranglehold. Googles deprecation of the
JPEG-XL image format in February in favor of its own patented
AVIF format might
not end the web in the grand scheme of things, but it does
highlight, once again, the disturbing
amount of control it has over the platform generally.
Part of Googles official rationale
for the deprecation is the following line: There is not enough
interest from the entire ecosystem to continue experimenting with
JPEG-XL. Putting aside the
problematic
aspects of the term ecosystem, let us remark that its easy to
gauge the response of the entire ecosystem when you yourself are by
far the largest and most dangerous predator in said ecosystem. In
relation to Googles overwhelming power, the average web user might
as well be a microbe. In supposedly gauging what the ecosystem
wants, all Google is really doing is asking itself what Google
wants. If we take their contribution in turning the web into the
WWWorst
App Store seriously, then we understand what Google really
wants. Google wants to do whats best for its own predatory
interests, not whats best for the web.
While we cant link to Googles issue tracker directly because of another freedom issue its use of nonfree JavaScript were told that the issue regarding JPEG-XLs removal is the second-most starred issue in the history of the Chromium project, the nominally free basis for the Google Chrome browser. Chromium users came out of the woodwork to plead with Google not to make this decision. It made it anyway, not bothering to respond to users concerns. Were not sure what metric its using to gauge the interest of the entire ecosystem,...
12:30
Fleet MDM platform provides mobile workstation security with GitOps and workflow automation Help Net Security
Fleet has revealed a new programmable MDM, designed to give medium-to-large organizations control of remote workstation security with unsurpassed GitOps and workflow automation. Fleets availability as an open-source MDM not only makes it more accessible to organizations working to reduce costs, but also allows users to configure the platform to their own needs without having to pay additional fees or experiencing delays. Providing support for macOS, Windows, Linux and ChromeOS, Fleet can be easily configured More
The post Fleet MDM platform provides mobile workstation security with GitOps and workflow automation appeared first on Help Net Security.
12:25
Searchlight Cyber launches Stealth Browser for secure dark web access Help Net Security
Searchlight Cyber has launched Stealth Browser, a virtual machine for cyber professionals to access the dark web and conduct investigations anonymously, without risk to themselves or their organization. Stealth Browser is an enhancement to Searchlights Cerberus investigation platform, which is used by law enforcement agencies, enterprises and MSSPs to uncover criminal activity on the dark web. The dark web is a critical source of intelligence for cybersecurity professionals, but accessing it carries risks for the More
The post Searchlight Cyber launches Stealth Browser for secure dark web access appeared first on Help Net Security.
12:15
Binarly Transparency Platform identifies vulnerabilities and malicious threats in code Help Net Security
Binarly has released the Binarly Transparency Platform, delivering transparency for device supply chains enabling device manufacturers and endpoint protection products to analyze both firmware and hardware to identify vulnerabilities, misconfigurations, and malicious code implantation. The Binarly Transparency Platform is designed to identify vulnerabilities and malicious threats in code, seamlessly integrating as a security component of an SDLC or CI-CD pipeline or further down the supply chain. The platform takes security to the next level by More
The post Binarly Transparency Platform identifies vulnerabilities and malicious threats in code appeared first on Help Net Security.
12:10
Regula updates Face SDK to protect users against different attack vectors Help Net Security
Regula has redesigned Face SDK face liveness detection technology and offers a balance between a simple UX and high reliability by using the zero-trust concept. Every session has its own unique parameters that cannot be reused by fraudsters for tampering, so the enrollment process is more accurate and fraud-resistant. Exhaustive sets of checks are executed on a backend to protect against different attack vectors: printed photo, mask, screen replay, and so on. At the same More
The post Regula updates Face SDK to protect users against different attack vectors appeared first on Help Net Security.
12:00
Theres Cash in Them Old Solar Panels Hackaday

The first solar panels may have rolled out of Bell Labs in the 1950s, with major press around their inconsistent and patchy adoption in the decades that followed, but despite the fanfare they were not been able to compete on a price per kilowatt compared to other methods of power generation until much more recently. Since then the amount of solar farms has increased exponentially, and while generating energy from the sun is much cleaner than most other methods of energy production and contributes no greenhouse gasses in the process there are some concerns with disposal of solar panels as they reach the end of their 30-year lifespan. Some companies are planning on making money on recycling these old modules rather than letting them be landfilled.
Typical solar panels are encased in glass and waterproofed, which makes recycling them somewhat of a challenge, but there are a lot of valuable materials in them that are worth recovering, including silver and copper. Even silicon and aluminum are profitable to recover, and these companies have developed specialized (but secret and proprietary) processes to recover them as efficiently as possible. As [Jon Hurdle] notes in the linked article, another major concern with aging panels that...
11:29
NEW 'Off The Hook' ONLINE 2600 - 2600: The Hacker Quarterly
NEW 'Off The Hook' ONLINE
Posted 13 Apr, 2023 1:29:55 UTC
The new edition of Off The Hook from 04/12/2023 has been archived and is now available online.
The leaked Ukraine war documents, tracing the timeline of the leak, document alterations, debating the motivations of the source of the leak, the government investigation, more wayward documents, the surprising history of 2600 Magazine according to Google Bard, NPR labeled as "state affiliated media" on Twitter.
10:28
[$] LWN.net Weekly Edition for April 13, 2023 LWN.net
The LWN.net Weekly Edition for April 13, 2023 is available.
10:14
Brace Yourself for a Tidal Wave of ChatGPT Email Scams SoylentNews
Thanks to large language models, a single scammer can run hundreds or thousands of cons in parallel, night and day, in every language under the sun:
Here's an experiment being run by undergraduate computer science students everywhere: Ask ChatGPT to generate phishing emails, and test whether these are better at persuading victims to respond or click on the link than the usual spam. It's an interesting experiment, and the results are likely to vary wildly based on the details of the experiment.
But while it's an easy experiment to run, it misses the real risk of large language models (LLMs) writing scam emails. Today's human-run scams aren't limited by the number of people who respond to the initial email contact. They're limited by the labor-intensive process of persuading those people to send the scammer money. LLMs are about to change that.
[...] Long-running financial scams are now known as pig butchering, growing the potential mark up until their ultimate and sudden demise. Such scams, which require gaining trust and infiltrating a target's personal finances, take weeks or even months of personal time and repeated interactions. It's a high stakes and low probability game that the scammer is playing.
Here is where LLMs will make a difference. Much has been written about the unreliability of OpenAI's GPT models and those like them: They "hallucinate" frequently, making up things about the world and confidently spouting nonsense. For entertainment, this is fine, but for most practical uses it's a problem. It is, however, not a bug but a feature when it comes to scams: LLMs' ability to confidently roll with the punches, no matter what a user throws at them, will prove useful to scammers as they navigate hostile, bemused, and gullible scam targets by the billions. AI chatbot scams can ensnare more people, because the pool of victims who will fall for a more subtle and flexible scammerone that has been trained on everything ever written onlineis much larger than the pool of those who believe the king of Nigeria wants to give them a billion dollars.
Read more of this story at SoylentNews.
10:00
HPR3834: 2022-2023 New Years Show Episode 5 Hacker Public Radio
Episode #5 printables: Kirby 40mm Fume Extractor. wikipedia: The Kirby Company is a manufacturer of vacuum cleaners and home cleaning accessories, located in Cleveland, Ohio, United States. It is a division of Right Lane Industries. lugcast: We are an open Podcast/LUG that meets every first and third Friday of every month using mumble. wikipedia: The PlayStation Portable (PSP) is a handheld game console developed and marketed by Sony Computer Entertainment. wikipedia: Rammstein is a German Neue Deutsche Härte band formed in Berlin in 1994. Goodluck with all the rest of the band/music chatter. I can't understand any of it. youtube: Burger Dance. Please no. Why did I signup for this. wikipedia: Syphilis is most commonly spread through sexual activity. wikipedia: Death was an American death metal band formed in Altamonte Springs, Florida, in 1984 by Chuck Schuldiner. Death is considered to be among the most influential bands in heavy metal music and a pioneering force in death metal. wikipedia: Death is a Detroit rock band formed in Detroit, Michigan in 1971 by brothers Bobby, David, and Dannis Hackney. wikipedia: BitLocker is a full volume encryption feature included with Microsoft Windows versions starting with Windows Vista. dell: Latitude E6410 Laptop. slackware: Slackware is a Linux distribution created by Patrick Volkerding in 1993. puppylinux: Puppy Linux is an operating system and family of light-weight Linux distributions that focus on ease of use and minimal memory footprint. tails: Tails, or The Amnesic Incognito Live System, is a security-focused Debian-based Linux distribution aimed at preserving privacy and anonymity. debian: Debian, also known as Debian GNU/Linux, is a Linux distribution composed of free and open-source software, developed by the community-supported Debian Project, which was established by Ian Murdock on August 16, 1993. wikipedia: Trusted Platform Module (TPM, also known as ISO/IEC 11889) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated cryptographic keys. pine64: ROCK64 is a credit card sized Single Board Computer powered by Rockchip RK3328 quad-core ARM Cortex A53 64-Bit Processor and support up to 4GB 1600MHz LPDDR3 memory. docker: realies/nicotine. wikipedia: rsync is a utility for efficiently transferring and synchronizing files between a computer and an external hard drive and across networked computers by comparing the modification times and sizes of files. funkwhale: Listen to your music, everywhere. Upload your personal library to your pod
Comparing Student and LLM Code Explanations It Will Never Work in Theory
Asking whether Large Language Models (LLMs) are going to help or hurt education is about as sensible as asking whether the Internet has been good for society. This paper asks a more specific, and therefore more useful, question: can LLMs produce explanations that will help novice programmers understand code, and are those explanations better, worse, or the same as ones produced by their peers? The answers to both questions appear to be "yes": machine-generated explanations aren't always correct or comprehensible, but neither are those produced by other students.
The authors do touch on some potential concerns, such as ways to prevent students from becoming over-reliant on model-generated explanations, but overall they're very positive about these tools' potential. It will probably be a few years before any of this has significant impact on higher education, but I expect that most online/self-paced learn-to-code offerings are going to have to adapt quickly or find a new business model.
Disclosure: I co-authored a paper in 2019 with one of the authors of this paper (Denny).
Juho Leinonen, Paul Denny, Stephen MacNeil, Sami Sarsa, Seth Bernstein, Joanne Kim, Andrew Tran, and Arto Hellas. Comparing code explanations created by students and large language models. 2023. arXiv:2304.03938.
Reasoning about code and explaining its purpose are fundamental skills for computer scientists. There has been extensive research in the field of computing education on the relationship between a student's ability to explain code and other skills such as writing and tracing code. In particular, the ability to describe at a high-level of abstraction how code will behave over all possible inputs correlates strongly with code writing skills. However, developing the expertise to comprehend and explain code accurately and succinctly is a challenge for many students. Existing pedagogical approaches that scaffold the ability to explain code, such as producing exemplar code explanations on demand, do not currently scale well to large classrooms. The recent emergence of powerful large language models (LLMs) may offer a solution. In this paper, we explore the potential of LLMs in generating explanations that can serve as examples to scaffold students' ability to understand and explain code. To evaluate LLM-created explanations, we compare them with explanations created by students in a large course (n 1000) with respect to accuracy, understandability and length. We find that LLM-created explanations, which can be produced automatically on demand, are rated as being significantly easier to understand and more accurate summaries of code than student-created explanations. We discuss the significance of this finding, and suggest how such models can be...
09:37
Smashing Security podcast #317: Another Uber SNAFU, an AI chatbot quiz, and is juice-jacking genuine? Graham Cluley
Everyone's talking juice-jacking - but has anyone ever been juice-jacked? Uber suffers yet another data breach, but it hasn't been hacked. And Carole hosts the "AI-a-go-go or a no-no?" quiz for Dave and Graham. All this and much much more is discussed in the latest edition of the "Smashing Security" podcast by computer security veterans Graham Cluley and Carole Theriault, joined this week by The Cyberwire's Dave Bittner.
09:04
Top Mobile Security Considerations for Business Travelers HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
Mobile security is becoming increasingly important as we delve deeper into the era of the Internet of Things
This is a post from HackRead.com Read the original post: Top Mobile Security Considerations for Business Travelers
09:01
How To Safely Navigate the World of Crypto Finance HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
The world of crypto finance is rapidly evolving and providing new opportunities for individuals and businesses. With the
This is a post from HackRead.com Read the original post: How To Safely Navigate the World of Crypto Finance
09:00
The Eyes Have It with This Solid State Magic Eye Hackaday

The classic Magic Eye tuning indicator was a fantastic piece of vacuum tube technology that graced all kinds of electronic gear for a fair fraction of the 20th century. But despite its prevalence, finding a new-old-stock Magic Eye tube is a tall order these days, especially for the rare versions like the 6T5. No worries, though, since direct plug-in solid-state replacements for the 6T5 are now a thing, thanks to [Gord Rabjohn].
Readers will be forgiven if this seems a tad familiar, since the current work is based strongly on [Gord]s previous Magic Eye work. But the 6T5 was a unique tube, with a display that looked more like a dilating pupil than the sweeping circle of the more common 6E5 and 6U5 tubes. Luckily, most of the basic circuitry of the previous tubes, which was based on the classic LM391x LED bar graph display chips, could be leveraged for the 6T5 substitute. [Gord] did need to come up with a new display board, which holds 160 green surface-mount LEDs in six concentric rings. He also added a single orange LED to the very center of the display board, to simulate the cheery glow of the original tubes heater filament.
As seen...
08:45
[$] Searching for an elusive orchid pollinator LWN.net
Orchids are, of course, flowers, and flowers generally need pollinators in order to reproduce. A seemingly offhand comment about the unknown nature of the pollinator(s) for a species of orchid in Western Australia has led Paul Hamilton to undertake a multi-year citizen-science project to try to fill that hole. He came to Everything Open 2023 to give a report on the progress of the search.
08:02
Hyundai suffered a data breach that impacted customers in France and Italy Security Affairs
Hyundai disclosed a data breach that impacted Italian and French car owners and clients who booked a test drive.
Hyundai has suffered a data breach that impacted Italian and French car owners and customers who booked a test drive.
Threat actors had access to the email addresses, physical addresses, telephone numbers, and vehicle chassis numbers of the impacted individuals.
The data breach letter sent to the impacted individuals informs them that an unauthorized third party had access to the database of customers. Hyundai Italy has notified the privacy watchdog and hired external cybersecurity experts to determine the scope of the incident.
According to the letter, financial data were not exposed. The number of impacted individuals is still unclear.
In response to the incident, the company has taken the impacted systems offline.
On behalf of Hyundai Motor Company Italy, I regret to inform you that our company has recently learned that an unauthorized third party has accessed certain information contained in our customer database. reads the data breach notification letter sent to the impacted individuals. Although there is no evidence that the data concerned have been used for fraudulent purposes, out of extreme caution, we invite you to pay particular attention and to verify any contact attempt via e-mail, mail and/or text message that may appear to come from Hyundai Italia or by other entities of the Hyundai Group. In particular, we recommend that you avoid pressing any link that may be contained in the contact attempt you may receive.
The company also warns impacted individuals to be cautious with unsolicited contact attempts via e-mail, mail and/or text message.
The incident is the last problem in order of time suffered by the South Korean carmaker, in February Hyundai and Kia carmakers released an emergency software update to fix a flaw that can allow stealing a car with a USB cable.
In December 2019, German media reported that h...
07:48
AI Poised to Transform Video Compression Landscape IEEE Spectrum

Apples surprise purchase at the end of last month of WaveOne, a California-based startup that develops content-aware AI algorithms for video compression, showcases an important shift in how video signals are streamed to our devices. In the near-term Cuppertinos purchase will likely lead to smart video compression tools in Apples video creation products and in the development of its much-discussed augmented reality headset.
However, Apple isnt alone. Startups in the AI video codec space are likely to prove acquisition targets for other companies trying to keep up.
For decades video compression used mathematical models to reduce the bandwidth required for transmission of analog signals, focusing on the changing portions of a scene from frame-to-frame. When digital video was introduced in the 1970s, improving video compression became a major research focus, leading to the development of many compression algorithms called codecs, short for coder-decoder, that compress and decompress digital media files. These algorithms paved the way for the current dominance of video in the digital age.
AI compression of still images has shown initial success. Video remains more challenging.
While a new codec standard has appeared around every 10 years, all have been based on pixel mathematicsmanipulating the values of individual pixels in a video frame to remove information that is not essential for human perception. Other mathematical operations reduce the amount of data that needs to be transmitted or stored.
AI codecs, having been developed over the course of decades, use machine learning algorithms to analyze and understand the visual content of a video, identify redundancies and non-functional data, and compress the video in a more efficient way. They use learning-based techniques instead of manually designed tools for encoding and can use different ways to measure encoding quality beyond traditional distortion measures. Recent advancements, like attention mechanisms, help them understand the data better and optimize visual quality.
During the first half of the 2010s, Netflix and a California-based company called Harmonic helped to spearhead a movement of whats called content-aware encoding. CAE, as Harmon...
07:30
Upstream Mesa Close To Supporting The Experimental Xe DRM Kernel Driver Phoronix
While we are still waiting for the Intel Xe kernel driver to be upstreamed as the modern alternative to the long-used i915 Direct Rendering Manager (DRM) driver, upstream Mesa Git is nearly ready in supporting the Xe kernel driver and its new/changed interfaces...
07:27
A Stream of Cold Gas is Unexpectedly Feeding the Far-off Anthill Galaxy SoylentNews
The stream could keep the galaxy supplied with star-forming fuel for a billion years:
A long, cold stream of gas is feeding a very distant galaxy like a vast bendy straw. The finding suggests a new way for galaxies to grow in the early universe, researchers report in the March 31 Science.
Computer simulations predicted that streams of gas should connect galaxies to the cosmic web (SN: 3/6/23). But astronomers expected that gas to be warm, making it unsuitable for star-forming fuel and galaxy growth.
So astronomer Bjorn Emonts and his colleagues were surprised to see a stream of cold, star-forming gas leading into the Anthill Galaxy, a massive galaxy whose light takes 12 billion years to reach Earth.
[...] "People didn't think that these streams could get so cold," says Emonts, of the National Radio Astronomy Observatory in Charlottesville, Va.
But there, in the data, a frigid stream stretched at least 325,000 light-years away from the galaxy. The stream carries the mass of 70 billion suns and deposits the equivalent of about 450 suns in cold gas onto the galaxy every year, the team calculated. That's enough to double the galaxy's mass within a billion years.
[...] If other galaxies are fed by similar structures, it could mean that early galaxies grew mostly by drinking directly from the cosmic streams, rather than by the leading hypothesis violent galaxy mergers (SN: 6/28/19).
Journal Reference:
Bjorn H. C. Emonts, Matthew D. Lehnert, Ilsang Yoon, et
al., A cosmic stream of atomic carbon gas connected to a
massive radio galaxy at redshift 3.8, Science,
379, 2023 (DOI: https://www.science.org/doi/10.1126/science.abh2150)
Read more of this story at SoylentNews.
07:17
ncurses fixes upstream Open Source Security
Posted by Jonathan Bar Or (JBO) on Apr 12
Hello oss-security,Our team has worked with the maintainer of the ncurses library (used by several software packages in Linux) to fix
several memory corruption vulnerabilities.
They are now fixed at commit 20230408 - see details here
(https://invisible-island.net/ncurses/NEWS.html#index-t20230408)
A CVE was assigned (CVE-2023-29491) - it's still under a "reserved" status.
How can we ensure those fixes get deployed upstream, in...
05:51
05:14
OpenAI Launches ChatGPT Bug Bounty Program Earn $200 to $20k HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
Do you have the skills to take part in OpenAI's ChatGPT Bug Bounty Program? If so, here is your chance to earn big bucks.
This is a post from HackRead.com Read the original post: OpenAI Launches ChatGPT Bug Bounty Program Earn $200 to $20k
05:00
Perfect Illustration of How Scumbag Reporters Lie cryptogon.com
Perfect illustration of how scumbag reporters lie: This BBC hack claimed he's seen more hate on Twitter. When asked, he can't name a single example because he hasn't look. Then claims @ISDglobal funded by US, EU and neoliberal billionaires said it:pic.twitter.com/Z0F8eGm1wp Glenn Greenwald (@ggreenwald) April 12, 2023
04:52
Industrial Pork Producers Using Customizable mRNA-Based Vaccines on Their Herds cryptogon.com
Via: The Defender: Since 2018, industrial pork producers have been using customizable mRNA-based vaccines on their herds. According to drugmaker Merck, the vaccines target existing and evolving swine pathogens, including diseases not covered by conventional swine vaccines.
04:48
Boston FBI Raids Wrong Hotel Room, Detains And Interrogates Innocent Man For 45 Minutes cryptogon.com
Definitely nothing to see here. Via: ZeroHedge: Few FBI blunders of late likely compare to what just happened in Boston last week, when Federal Agents on a training mission wound up barging into the wrong hotel room and inadvertently interrogating an innocent hotel guest who was sleeping for nearly 45 minutes. The bizarre mistake, outlined []
04:43
Raspberry Pi Launches Online Code Editor to Help Kids Learn SoylentNews
New editor is integrated with Python lessons:
When we think about Raspberry Pi, we normally picture single-board computers, but the Raspberry Pi Foundation was started to help kids learn about computers and it wants to help whether or not you own its hardware. The non-profit arm of Raspberry Pi this week released its new, browser-based code editor that's designed for young people (or any people) who are learning.
The Raspberry Pi Code Editor, which is considered to be in beta, is available to everyone for free right now at editor.raspberrypi.org. The editor is currently designed to work with Python only, but the organization says that support for other languages such as HTML, JavaScript and CSS is coming.
I tried out the Code Editor on my PC's browser and, in its current form, there's nothing particularly unique about it. However, I found the UI very user-friendly and was impressed with how it is integrated into someone online tutorials. The interface consists of three panes: a list of files in your project, a code editor and an output pane that runs the result of your code when you hit the Run button.
If you create a free account on raspberrypi.org, which I did, the system will save all of your projects in the cloud and you can reload them any time you want. You can also download all the files in a project as a .zip file.
Since the entire programming experience takes place online, there's no way (at least right now) to use Python to control local hardware on your PC or your Raspberry Pi. If you want to attach one of the best Raspberry Pi HATs or use the GPIO pins on your Pi to light up an LED light, you need a local editor like Thonny, which comes preinstalled on all Raspberry Pis and is a free download for Windows, Mac and Linux.
Read more of this story at SoylentNews.
04:37
Walmart Abandons Unprofitable Chicago Stores After Investing Hundreds Of Millions In City cryptogon.com
Via: ZeroHedge: After two decades of losses and hundreds of millions of dollars invested in Chicago, Walmart is shuttering four unprofitable stores in the metropolitan area, reducing its store footprint by half in the crime-ridden city. The simplest explanation is that collectively our Chicago stores have not been profitable since we opened the first one []
04:20
QuaDream surveillance firms spyware targeted iPhones with zero-click exploit Security Affairs
At least five members of civil society worldwide have been targeted with spyware and exploits developed by surveillance firm QuaDream.
Citizen Lab researchers reported that at least five civil society members were victims of spyware and exploits developed by the Israeli surveillance firm QuaDream.
The victims include journalists, political opposition figures, and an NGO worker located in North America, Central Asia, Southeast Asia, Europe, and the Middle East.
The researchers also believe that the threat actors used a suspected iOS 14 zero-click exploit to deploy QuaDreams spyware. The zero-day exploit, dubbed ENDOFDAYS, appears to work against iOS versions 14.4 and 14.4.2, and possibly other versions. ENDOFDAYS relies on invisible iCloud calendar invitations sent from the spywares operator to victims.
CitizenLab identified QuaDream servers in multiple countries, including Bulgaria, Czech Republic, Hungary, Ghana, Israel, Mexico, Romania, Singapore, United Arab Emirates (UAE), and Uzbekistan.
The experts believe that the zero-day exploit was used at least since March 2021.
QuaDream Ltd ( ) is an Israeli company that specialises in the development and sale of advanced digital offensive technology to government clients. The company is known for its spyware marketed under the name Reign, which, like NSO Groups Pegasus spyware, reportedly utilises zero-click exploits to hack into target devices. reads the report published by Citizen Lab.
The Israeli firm has had a partnership with a Cypriot firm called InReach, with whom it is currently embroiled in a legal dispute. Multiple key figures of both companies have prior connections with the surveillance vendor Verint, as well as Isra...
04:09
Links 12/04/2023: Nginx 1.2 and Kubernetes 1.27 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Audiocasts/Shows
-
Voice Controller now has talking [algorithm/program]
We have given the voice Controller a nice Overhaul, some great new features Enjoy the teaser.
-
-
Applications
-
GStreamer: GStreamer 1.22.2 stable bug fix release
The GStreamer team is pleased to announce the second b...
-
-
03:27
Distribution Release: Tiny Core Linux 14.0 DistroWatch.com: News
Tiny Core Linux is a minimal Linux distribution which runs from memory. The Tiny Core Linux project has released a new version, 14.0, which is available in three editions: Core (for a command line only experience), TinyCore (which provides a minimal graphical environment), and CorePlus (which provides a....
03:11
[$] The early days of Linux LWN.net
My name is Lars Wirzenius, and I was there when Linux started. Linux is now a global success, but its beginnings were rather more humble. These are my memories of the earliest days of Linux, its creation, and the start of its path to where it is today.
03:00
Ryzen Mobile Power/Performance With Linux 6.3's New AMD P-State EPP Driver Phoronix
With Linux 6.3 there is the new AMD P-State EPP driver code for supporting the ACPI Energy Performance Preference (EPP) to further enhance the power efficiency and performance of modern AMD systems on Linux. Last week I ran some benchmarks of AMD EPYC with the new AMD P-State EPP mode while in today's article is a look at the laptop impact with Ryzen Mobile when comparing ACPI CPUFreq, the existing AMD P-State driver, and the new AMD P-State EPP mode and its multiple different preferences.
02:58
02:57
Ghostscript CVE-2023-28879: "Shell in the Ghost" Open Source Security
Posted by Alan Coopersmith on Apr 12
I haven't seen mail to the list about this yet, so FYI for those who haven'tseen it via other channels.
https://artifex.com/news/critical-security-vulnerability-fixed-in-ghostscript
says:
A report from those who found the bug, including their POC, was published
yesterday:
https://offsec.almond.consulting/ghostscript-cve-2023-28879.html
02:17
888 On Line Casino Review Get $200 Welcome Bonus + 88 Free Spins h+ Media
888 On Line Casino Review Get $200 Welcome Bonus + 88 Free Spins
Virtually all random number mills are additionally certified by outdoors players who check so that they are honest and never rigged on line casino games. Which presents a certification service for both casinos and its video games. If you see that a game developer is licensed by eCogra, you probably can ensure that the sport you would possibly be taking half in is completely honest. Licensed casinos solely provide video games from game builders which may be certified by eCorga. Although there are some games that might be won with ability and confirmed strategies, it is at all times chance that determines whether or not there shall be a win or not at pokies at the on line casino.
888 Casino is unquestionably on the top of the gaming business in terms ofonline on line casino in New Zealand. The company behind the operation of 888.com is the Cassava Enterprises under the legal guidelines of the Government of Gibraltar. Ultimately, slots are all about luck and youll normally solely come out as a winner should you stop whilst youre forward. What is one of the best free spins on line casino I can join proper now, casino 888 confiavel.
It is more than usual to be supplied a welcome supply when registering on a playing web site. However, these can differ considerably from one on line casino to another. We subsequently evaluate bonuses based mostly on their value and what requirements are set to evaluate how the bonus stands in comparability with other gambling sites offers. That yow will discover all kinds of gaming corporations and on-line casinos in New Zealand that have been granted a gaming license and are regulated by New Zealand authorities. You can simply evaluate casinos in online Casinos NZs leaderboards .
Some of the most effective live dealing action video games you can play on the site are sport exhibits by Evolution. This will open a window with all the premium live dealing games you can find on 888 Casino. This can additionally be the rationale behind the good array of premium slot games that includes different recreation mechanics on the location. So, there are additionally some other slot providers which is most likely not as well-liked because the listed however are still worth mentioning. The main focus point in relation to 888 Casino games is the slot selection. Regular jackpot games and twilight jackpots may also be found right here, making the format of the location full.
- Here, you can also make a decision on which sector and kind of recreation you wish to play on the positioning.
- This will open a window with all the premium stay dealing games youll find on 888 Casino.
- No matter where youre from, the casino could have you lined with at least one deposit and withdrawal technique.
- Place sports activities bets on 888 Casino and wager on the sport of...
02:16
Multiple vulnerabilities in Jenkins plugins Open Source Security
Posted by Daniel Beck on Apr 12
Jenkins is an open source automation server which enables developers aroundthe world to reliably build, test, and deploy their software.
The following releases contain fixes for security vulnerabilities:
* Azure Key Vault Plugin 188.vf46b_7fa_846a_1
* Kubernetes Plugin 3910.ve59cec5e33ea_
Additionally, we announce unresolved security issues in the following
plugins:
* Assembla merge request builder Plugin
* Consul KV Builder Plugin
* Fogbugz...
02:14
Apple Pay On Line Casino Nz On-line Casinos With Apple Pay 2023 h+ Media
Apple Pay On Line Casino Nz On-line Casinos With Apple Pay 2023
Kiwis can indulge in a wide range of exclusive bonuses and promotions obtainable at this on line casino. Unlike different online gaming platforms, 888Starz allows gamers to claim bonuses when making deposits using in style cryptocurrencies. Newly registered players are greeted with a luxurious Welcome Bonus amounting to as a lot as NZ$1,500 and an extra 150 Free Spins to sweeten the deal.
888 is available to prospects in the UK and Ireland, plus a host of different locations together with Canada, New Zealand and numerous European nations. There is also the 888 Blog that may hold you updated with all of the casinos information and game releases. The Live enviornment is a full-on streaming platform where you will compete towards the many totally different sellers hosting the tables.
A easy form of a random number generator is, for instance, to roll a cube or to flip a coin. This gives you fully random numbers with an equal probability of every consequence. Online on line casino games and pokies also use random quantity mills.
When it involves banking too, you ought to have absolutely no qualms. They offer a variety of main bank cards, corresponding to Visa and Mastercard, a choice of e-wallets, similar to Trustly and MuchBetter, in addition to more up and coming options like ApplePay. 888 poker works barely totally different to the relaxation of their service as essentially, the service is a downloadable consumer. Add this to your computer and you will acquire entry to a plethora of different poker options which are supplied to their players by the staff at 888 on line casino.
There can also be the choice to obtain their software program on your cell phone or pill. If any new scatter lands on the Hot 1, players can also anticipate to win extra when they spin the reels at no cost. Winnings allotted throughout free spins must be wagered 200 occasions, and savor the taste of the forbidden Sin City Nights. Overall, permitting you to get extra funds for taking half in slots. Along with their 100 percent deposit bonus, New Zealand players additionally obtain 25 free to get them began at the pokies.
A good touch to the gaming platform is that customers can still opt for practice play if they need and thus use the demo credits to play poker with actual opponents. Therefore, we additionally look at the frequency with which online casinos offer new slots. These Of course ensure that you as a gambler keep coming back to the online on line casino.
You also can select the subsections like new video games, in style video games, and all video games. In this 888 Casino evaluate, we will concentrate on individual game sections to bring you high quality info. The banner shows the welcome bonus and whenever you scroll you will see completely different sport classes. If you need to attain the casino help group then additionally the choice is c...
02:14
Top 10 Best Online Casino In New Zealand Get Bonuses Enjoying In Online Pokies h+ Media
Top 10 Best Online Casino In New Zealand Get Bonuses Enjoying In Online Pokies
But thats not all, in addition to the welcome bonus there may be also a Friday, birthday and VIP bonus! 888 are a high quality online playing brand and this certainly shines via within the performance of their websites in our reviews. Their sports activities site had a massive quantity of routinely glorious prematch and stay odds for all of the sports that you would wish for. Similarly their on line casino site had a powerful variety of on-line pokies and desk games. All 888 New Zealand clients will discover that they have instant entry to simply about any sort of on-line playing entertainment.
There are tables with completely different languages out there as properly German, Russian, Spanish or Danish being just some examples. The 888 part is actually one thing that most gamers recognize and many of the rivals are jealous of. It is really very good, as there is an abundance of obtainable tables and different video games.
For live on line casino gamers, there are other promotions just like the one where you can win eight pounds, whenever the ball is at the number eight. This is restricted time provide, and it begins at eight or nine afternoons. At 888 Sport, you can access lots of of sports markets with much better odds than land-based bookmakers. You can use the casinos sporting stats to assist you place your bets. You can watch all of the action via reside streaming on chosen video games. Plus, youve in-play sports activities analysis and digital gaming maps to observe the play in real-time.
Maybe these less typical styles could soon flip into your all-time favourite before lengthy. This is as a end result of of the truth that alongside their own games you also get to enjoy video games from big-name suppliers, such as Netent, Red Tiger, and Yggdrasil too. These offer slots video games anywhere from 1 to over 25 lines, in addition to extra basic on line casino and stay casino games too. As such, you get the best of both world if you end up having fun with the 888 casino games catalog.
New players will have an opportunity to earn 88 kilos without deposit money. You can win the utmost amount of 15 kilos should you dont play jackpot in fact. 888 Casino provides many companies that may assist you to to securely deposit NZ dollars into your 888 account. All transaction occasions are quick, thusly, permitting you to play games instantly. There is little question whatsoever once we say theyre top-of-the-line on line casino operators on the earth. And to now be a part of the NZ market, is an actual treat for New Zealand players looking for a model new online casino to go to.
- You can get professional help from organisations like Gamblers Anonymous and Gambling Therapy.
- They have video games obtainable from a few of the greatest suppliers as nicely as their very own Dragonfish video gam...
02:12
888 Reviews For Nz 2023 Is 888 Dependable For Sports Bets? h+ Media
888 Reviews For Nz 2023 Is 888 Dependable For Sports Bets?
Now, in 2021, they nonetheless preserve that high degree of offering the most important and the most effective games in stupidly excessive numbers. Prices are in New Zealand dollars otherwise said and are topic to GST. Any provides or promotions are non-exchangeable and non-refundable.
You can use Interac, Instant Banking, bank cards or iDebit to get dollars into your account. Another fantastic banking technique option for deposit and withdrawal is PaysafeCard. 888 took a bit of time onboarding Interac, however from the start of 2023 theyve allowed Interac transactions.
They truly stand out in relation to variations of video games, with a range of on-line slots, table video games, progressive video games, video poker games, reside supplier video games and specialty video games to select from. You will discover all of your favourite desk video games inside its lobby, including Blackjack, Roulette, Caribbean Stud, Baccarat, Casino Holdem, Red Dog and extra. In whole, 888 has about 25 desk video games to take pleasure in, excluding its big selection of Blackjack choices. If you like video poker games, check out Jacks or Better, All American Double Up, Aces and Faces, Tens or Better, Bonus Poker and extra. The can also be a live casino that options an authentic gaming experience, full with stay dealer, live gamers and actual time motion. Finally, no games lobby is full with slot machines, and 888 is no completely different.
888 mobile on line casino provides you the possibility to play anytime you want from anywhere you need, so you possibly can all the time win huge when you have an web connection. 888Casino has the top jackpot pokies out there together with the Millionaire Genie slot sport. This is doubtless certainly one of the prime rating pokies on the location, and all it takes is one spin to win massive. When it comes to gameplay, youll undoubtedly not be disappointed with the over a hundred choices that are obtainable. 888 Casino operates by itself software, Dragonfish, and this is what supplies each kiwi participant with the last word and most unique gaming expertise.
The monthly withdrawal restrict is above common and stands at $20,000, while youll face a most ready time of 48 hours on your withdrawal requests. A devoted part of the lobby will current numerous tables and tournaments for players looking to enjoy the sport without using real money in the course of. T simply apply to cash video games but additionally to online poker tournaments, because the schedule is always packed and the action never appears to cease. While the welcome bonus is type of small, compared to other online casinos, the wagering requirement solely requires that you play by way of the bonus quantity 30x earlier than cashing out.
There isnt any live chat obtainable for those non-registered members that we are ready to see, and so the messa...
02:01
Florida Officials Deleted Data, Stats From Dubious COVID Analysis: Report SoylentNews
"You can call it a lie by omission":
Florida health officials deleted key data and statistics from a state analysis on the safety of mRNA COVID-19 vaccines, falsely making them appear unsafe for young men, according to draft versions of the analysis obtained by the Tampa Bay Times through public records requests.
The final analysis, which was widely criticized for its poor quality and dubious conclusions, was the basis for a statewide recommendation by Surgeon General Joseph Ladapo last October that young men, ages 18 to 39, should not receive an mRNA COVID-19 vaccine. The analysisposted on the Florida Department of Health's website with no authors listedclaimed to find "an 84% increase in the relative incidence of cardiac-related death among males 18-39 years old within 28 days following mRNA vaccination."
Ladapo, who has a history of fearmongering about COVID-19 vaccines, touted the analysis, saying in a press release at the time that "these are important findings that should be communicated to Floridians."
But according to draft versions of the analysis, the state epidemiologists who worked on the report came to entirely different conclusions.
Read more of this story at SoylentNews.
01:45
CVE-2022-45064: Apache Sling Engine: Include-based XSS Open Source Security
Posted by Angela Schreiber on Apr 12
Description:The SlingRequestDispatcher doesn't correctly implement the RequestDispatcher API resulting in a generic type of
include-based cross-site scripting issues on the Apache Sling level. The vulnerability is exploitable by an attacker
that is able to include a resource with specific content-type and control the include path (i.e. writing content). The
impact of a successful attack is privilege escalation to administrative power....
01:14
Reality is a Paradox Not Even Wrong
Lex Fridmans latest podcast features a nearly four hour long conversation with Edward Frenkel, under the title Reality is a Paradox Mathematics, Physics, Truth & Love. Normally Im fairly allergic to hearing mathematicians or physicists publicly sharing their wisdom about the larger human experience (since they tend to have less of it than the average person), and Im pretty sure Ive never before listened to a podcast/interview longer than an hour or so. But in this case I listened to and enjoyed the entire thing. Besides sharing Frenkels deep interests in the relation of representation theory and quantum mechanics, and views on the unity of mathematics (and physics), I envy his positive and thoughtful outlook on life and his openness to a range of human experience. The interview left me with a lot to think about and I recommend it highly.
01:09
Operators of Movie & TV Piracy Giant 8maple Sentenced to Prison in Taiwan TorrentFreak
 Pirate sites with tens of millions of visits each
month are large enough to consider themselves global players yet
some achieve these levels in a tighter geographic niche.
Pirate sites with tens of millions of visits each
month are large enough to consider themselves global players yet
some achieve these levels in a tighter geographic niche.
Founded in 2014 by two Taiwanese software engineers, movie and TV show piracy site 8maple is a prime example. Initially, the site was promoted as a commercial advertising platform but soon transformed into a full-blown piracy portal pulling in millions of visitors each month and generating large sums in advertising revenue.
Spending an estimated US$9,800 on server hosting in the United States, Canada, Ukraine, France and Romania each month, early estimates suggested the men behind 8maple may have been generating around US$65,600 in monthly revenues. By early 2020, the sites main domain at 8maple.ru was pulling around 35 million visits per month, generating around US$133,000 per month in revenue.
Investigation and Shutdown
Following an investigation carried out by the Alliance for Creativity and Entertainment, the Asia-Pacific division of the Motion Picture Association (MPA-APC), Japan-based Content Overseas Distribution Association (CODA), and local TV network Sanli TV, Taiwans Criminal Investigation Bureau (CIB) shut down 8maple.ru late March 2020.
Two men in their early thirties (Chen Su, 33, and Zhuang Su, 32) were arrested and around $1.9m in illegal gains were seized from their bank accounts. Domains including 8maple.ru, 8maple.com, 8drama.com, 8drama.ru, 8duck.ru, 8video.tv, eyny.is, and eyny.tv, were shut down.
The suspects were arrested for copyright infringement offenses with Taiwans Telecommunications Investigation Corps estimating that 8maple caused around NT$1 billion (US$33.2m) in damages to the entertainment industries.
Court Sentences Men in Taiwan
More than two years after their arrest, the Taoyuan District Court has now sentenced the two men to serve 18 months in prison for jointly committing the crime of infringing copyright property rights under Article 92 of the Copyright Law.
TorrentFreak obtained a copy of the official verdict from Taiwan prosecutor Harris Chen. It reveals a highly complex case and what appears to be the involvement of other suspe...
01:08
US, India and China Most Targeted in DDoS Attacks, StormWall Q1 2023 Report HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
DDoS attacks have surged by 47% in Q1 2023, according to a StormWall report.
This is a post from HackRead.com Read the original post: US, India and China Most Targeted in DDoS Attacks, StormWall Q1 2023 Report
00:59
Zigbee PRO 2023 introduces new security mechanisms, feature enhancements Help Net Security
The Connectivity Standards Alliance released Zigbee PRO 2023 of the Zigbee protocol stack. The revision brings several enhancements and new features to the technology, allowing mesh networks to have a universal language that enables smart objects to work together. Whats new? Zigbee PRO 2023 expands on secure-by-design architecture by adding a number of security enhancements to address changing market needs while simplifying the user experience and extending supported bands beyond 2.4 GHz. The revision also More
The post Zigbee PRO 2023 introduces new security mechanisms, feature enhancements appeared first on Help Net Security.
00:50
Distribution Release: TrueNAS 22.12.2 "SCALE" DistroWatch.com: News
TrueNAS SCALE is a Debian-based operating system developed by iXsystems for providing network attached storage solutions. The includes some enhancements to administration and authentication. The release notes state: "22.12.2 includes many new features and improved functionality that span....
00:39
Testing for Coexistence in Crowded and Contested RF Environments IEEE Spectrum
This white paper presents some of the key research, development, test and evaluation (RDT&E) challenges that arise when developing and deploying systems that need to operate in congested and/or contested RF environments.
As our world becomes increasingly reliant on wireless communications, RF spectrum congestion and contention cause friction between incumbent users and newer, bandwidth- intensive applications such as cellular communications.
Over the last decade, the frequency bands allocated for cellular communications services that employ 3GPP technologies has increased from 11 bands to over 80 bands. In the ideal state of RF coexistence, RF signals utilize or exist in the same frequency bands and emanate from different transmitters.
The key issues facing coexistence are also discussed. Such issues include, a contested and congested spectrum, spectral sensing, spectrum sharing and dynamic spectrum allocation. The white paper concludes with an overview of the test systems that are used to create realistic RF environments that provide real-world operational conditions in a controlled laboratory environment.
00:30
NVIDIA RTX-Remix 0.1 Released For Adding Path Tracing To Classic Games Phoronix
In addition to releasing the GeForce RTX 4070 graphics card today (unfortunately, no launch day Linux review, still waiting on hardware...), NVIDIA has released as open-source the RTX Remix software for helping to add path tracing support to classic games...
00:25
Plenty of juice-jacking scare stories, but precious little juice-jacking Graham Cluley
Travellers are being told to be wary when plugging their smartphones and laptops into USB chargers. But has anyone ever actually been juice-jacked in the real world?
00:00
Signed Distance Functions: Modeling in Math Hackaday

What if instead of defining a mesh as a series of vertices and edges in a 3D space, you could describe it as a single function? The easiest function would return the signed distance to the closest point (negative meaning you were inside the object). Thats precisely what a signed distance function (SDF) is. A signed distance field (also SDF) is just a voxel grid where the SDF is sampled at each point on the grid. First, well discuss SDFs in 2D and then jump to 3D.
SDFs in 2D
A signed distance function in 2D is more straightforward to reason about so well cover it first. Additionally, it is helpful for font rendering in specific scenarios. [Vassilis] of [Render Diagrams] has a beautiful demo on two-dimensional SDFs that covers the basics. The naive technique for rendering is to create a grid and calculate the distance at each point in the grid. If the distance is greater than the size of the grid cell, the pixel i...
Wednesday, 12 April
23:53
Arm Opens Up To Using Intel's 18A Process For Leading-Edge SoCs Phoronix
Intel Foundry Services (IFS) has racked up a big win today with Arm over enabling chip designers to make use of Intel's upcoming 18A process for low-power Arm SoCs...
23:53
Links 12/04/2023: Youtube-dl Hosting Ban Paves the Way to Privatised Censorship Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Instructionals/Technical
-
RIPE SAV: Why Is Source Address Validation Still a Problem?
Network operators can implement filtering anywhere within their network. However, best current practices (BCPs) recommend they perform it close to the...
-
-
23:38
Android App Trojans Sold on Dark Web for $25-$20,000 HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
A Kaspersky study reveals security threats to the Google Play app store and how they have been exposing Android users to malware threats.
This is a post from HackRead.com Read the original post: Android App Trojans Sold on Dark Web for $25-$20,000
23:31
Security updates for Wednesday LWN.net
Security updates have been issued by Fedora (chromium, ghostscript, glusterfs, netatalk, php-Smarty, and skopeo), Mageia (ghostscript, imgagmagick, ipmitool, openssl, sudo, thunderbird, tigervnc/x11-server, and vim), Oracle (curl, haproxy, and postgresql), Red Hat (curl, haproxy, httpd:2.4, kernel, kernel-rt, kpatch-patch, and postgresql), Slackware (mozilla), SUSE (firefox), and Ubuntu (dotnet6, dotnet7, firefox, json-smart, linux-gcp, linux-intel-iotg, and sudo).
23:26
New AI scientist combines theory and data to discover scientific equations Lifeboat News: The Blog
In 1918, the American chemist Irving Langmuir published a paper examining the behavior of gas molecules sticking to a solid surface. Guided by the results of careful experiments, as well as his theory that solids offer discrete sites for the gas molecules to fill, he worked out a series of equations that describe how much gas will stick, given the pressure.
Now, about a hundred years later, an AI scientist developed by researchers at IBM Research, Samsung AI, and the University of Maryland, Baltimore County (UMBC) has reproduced a key part of Langmuirs Nobel Prize-winning work. The system artificial intelligence (AI) functioning as a scientistalso rediscovered Keplers third law of planetary motion, which can calculate the time it takes one space object to orbit another given the distance separating them, and produced a good approximation of Einsteins relativistic time-dilation law, which shows that time slows down for fast-moving objects.
A paper describing the results is published in Nature Communications on April 12.
23:25
(Extra) Quantum Computing Explained and Overview Lifeboat News: The Blog

Playlist:
https://www.youtube.com/playlist?list=PLnK6MrIqGXsJfcBdppW3CKJ858zR8P4eP
Download PowerPoint: https://github.com/hywong2/Intro_to_Quantum_Computing.
Book (Free with institution subscription): https://link.springer.com/book/10.1007/978-3-030-98339-0
Book:
https://www.amazon.com/Introduction-Quantum-Computing-Layperatfound-20
Can quantum computing replace classical computing? State, Superposition, Measurement, Entanglement, Qubit Implementation, No-cloning Theorem, Error Correction, Caveats.
23:25
Its Already Too Late Elon Musk on LATEST AI Lifeboat News: The Blog

Elon Musk has been warning of the dangers of artificial intelligence for as long he can remember and now, it looks like his worst fears might be coming true
23:22
Rapid alternating polarity brings new life to 189-year-old electrochemical reaction Lifeboat News: The Blog
Nearly 200 years since its discovery, industry rarely uses the carboncarbon bond-forming Kolbe reaction but now US researchers have shown it can sustainably make valuable substances.
Phil Barans team at Scripps Research Institute in La Jolla has done away with high voltages and platinum electrodes best established in the Kolbe reaction. In doing so, the researchers have made it much more versatile. The most important feature is the ability to take waste or similarly priced products convert them into extremely high value materials, Baran tells Chemistry World.
23:17
What Flight 50 Means for the Ingenuity Mars Helicopter SoylentNews
What Flight 50 Means for the Ingenuity Mars Helicopter:
JPL's Ingenuity helicopter is preparing for the 50th flight of its 5-flight mission to Mars. Flight 49, which took place last weekend, was its fastest and highest yetthe little helicopter flew 282 meters at an altitude of 16 meters, reaching a top speed of 6.50 meters per second. Not a bad performance for a tech demo that was supposed to be terminated two years ago.
From here, things are only going to get more difficult for Ingenuity. As the Perseverance rover continues its climb up Jezero crater's ancient river delta, Ingenuity is trying its best to scout ahead. But, the winding hills and valleys make it difficult for the helicopter to communicate with the rover, and through the rover, to its team back on Earth. And there isn't a lot of time or room to spare, because Ingenuity isn't allowed to fly too close to Perseverance, meaning that if the rover ever catches up to the helicopter, the helicopter may have to be left behind for the rover's own safety. This high-stakes race between the helicopter scout and the science rover will continue for kilometers.
For the Ingenuity team, this new mode of operation was both a challenge and an opportunity. This was nothing new for folks who have managed to keep this 30-day technology demo alive and healthy and productive for years, all from a couple hundred million kilometers away. IEEE Spectrum spoke with Ingenuity Team Lead Teddy Tzanetos at JPL last week about whether flying on Mars is ever routine, how they upgraded Ingenuity for its extended mission, and what the helicopter's success means for the future of airborne exploration and science on Mars.
Read more of this story at SoylentNews.
23:01
Monitor and troubleshoot applications with Glances and InfluxDB Linux.com
Set up a quick application observability solution that records metrics in real time and pipes them into a database for analysis.
Read More at Enable Sysadmin
The post Monitor and troubleshoot applications with Glances and InfluxDB appeared first on Linux.com.
22:45
[Meme] Unified Patent Court Versus Judges (That Arent Fully Controlled by the EPOs Junta, the Controversial Granting Authority) Techrights
Summary: The EPO is preparing to start its own (controlled) kangaroo court to help hide the effect of patent bubbles (mountains of legally-invalid monopolies)
22:40
What the Hard Data Says About Gender Inequality in Europes Second-Largest Institution, the EPO Techrights

The EUs unwillingness to do something about the EPO will
imperil the EU itself (the EU and EPO are very much connected
through the
illegal Unified Patent Court)
Summary: Gender inequality, or the considerably lower probability of women progressing at Europes largest patent office, as explained by the EPOs elected staff representation only days ago
The Central Staff Committee at the EPO started talking about the empty words from Antnio Campinos regarding inclusion, equality etc. Campinos is basically a low-grade liar. He last brought that up just weeks ago in a pre-recorded speech.
Under the current career system, the Central Staff Committee says, the gender pay gap has widened after every reward exercise. Progress has been made to fix the huge under rewarding of colleagues on maternity leave, but there is still much work to do in other areas. In particular, three issues are highlighted, including the under-rewarding of double-steps and promotions to women, and the under-rewarding of colleagues working part-time.
The paper below is dated 5 days ago. Originally a PDF circulated among stuff, here it is as HTML:
Zentraler Personalausschuss
Central Staff Committee
Le Comit Central du PersonnelMunich, 07/04/2023
sc23040cpGender Pay Gap: at last a fair reward exercise in 2023?
Dear colleagues,
Under the current career system, the gender pay gap has widened after every reward exercise. Progress has been made to fix the huge under rewarding of colleagues on maternity leave, but there is still much work to do regarding other minority groups, such as part-time workers and women, as detailed below.
The Presidents Instructions on Rewards confirm the reality of this trend with his recommendation to managers that states as a proactive measure in order to ensure a fair distribution of rewards to all...
22:27
Re: CVE-2017-11164 - stack exhaustion in PCRE Open Source Security
Posted by Matthew Vernon on Apr 12
I've been trying to push towards getting old-PCRE out of Debian; you cantrack the outstanding bugs online[0], and there's similar for Ubuntu[1].
Once the next Debian release "bookworm" is out, I'm hoping to be able to
make the outstanding bugs release critical, moving towards not shipping
the older pcre (called pcre3 in Debian for Historical Reasons) in the
next release...
Regards,
Matthew
[PCRE maintainer for...
22:00
HashiCorp Vault vulnerability could lead to RCE, patch today! (CVE-2023-0620) Help Net Security
Oxeye discovered a new vulnerability (CVE-2023-0620) in the HashiCorp Vault Project, an identity-based secrets and encryption management system that controls access to API encryption keys, passwords, and certificates. The vulnerability was an SQL injection vulnerability that potentially could lead to a Remote Code Execution (RCE). Oxeye reported this vulnerability to HashiCorp, and the team quickly patched it in versions 1.13.1, 1.12.5, and 1.11.9. of Vault. HashiCorp Vault HashiCorp Vault provides encryption services for modern, microservices-based More
The post HashiCorp Vault vulnerability could lead to RCE, patch today! (CVE-2023-0620) appeared first on Help Net Security.
21:58
Israel-based Spyware Firm QuaDream Targets High-Risk iPhones with Zero-Click Exploit The Hacker News
Threat actors using hacking tools from an Israeli surveillanceware vendor named QuaDream targeted at least five members of civil society in North America, Central Asia, Southeast Asia, Europe, and the Middle East. According to findings from a group of researchers from the Citizen Lab, the spyware campaign was directed against journalists, political opposition figures, and an NGO worker in 2021.
21:50
The Service Accounts Challenge: Can't See or Secure Them Until It's Too Late The Hacker News
Here's a hard question to answer: 'How many service accounts do you have in your environment?'. A harder one is: 'Do you know what these accounts are doing?'. And the hardest is probably: 'If any of your service account was compromised and used to access resources would you be able to detect and stop that in real-time?'. Since most identity and security teams would provide a negative reply,
21:22
Promising new AI can detect early signs of lung cancer that doctors cant see Lifeboat News: The Blog
Researchers in Boston are on the verge of what they say is a major advancement in lung cancer screening: Artificial intelligence that can detect early signs of the disease years before doctors would find it on a CT scan.
The new AI tool, called Sybil, was developed by scientists at the Mass General Cancer Center and the Massachusetts Institute of Technology in Cambridge. In one study, it was shown to accurately predict whether a person will develop lung cancer in the next year 86% to 94% of the time.
The Centers for Disease Control and Prevention currently recommends that adults at risk for lung cancer get a low-dose CT scan to screen for the disease annually.
21:22
A New Kind of Time Crystal Has Been Created That Does Interesting Things to Light Lifeboat News: The Blog
Scientists are still getting to grips with the ins and outs of strange materials known as time crystals; structures that buzz with movement for eternity. Now a new variety might help deepen our understanding of the perplexing state of matter.
Just as regular crystals are atoms and molecules that repeat over a volume of space, time crystals are collections of particles that tick-tock in patterns over a duration of time in ways that initially seem to defy science.
Theorized in 2012 before being observed in the lab for the first time just four years later, researchers have been busy tinkering with the structures to probe deeper foundations of particle physics and uncover potential applications.
21:02
Mesa 23.1 RadeonSI Enables Rusticl OpenCL Support Phoronix
If Mesa 23.1 couldn't get anymore exciting with RADV GPL support enabled by default, more RDNA3 optimizations, continued Zink optimizations, more Intel DG2/Alchemist enhancements, and a load of other features... Support for RadeonSI with the Rusticl Rust-written OpenCL driver has been merged!..
21:00
The Challenges of Producing Graphene in Quantity Hackaday

Weve all heard the incredible claims made about graphene and its many promising applications, but so far the wonder-material has been held back by the difficulty of producing it in large quantities. Although small-scale production was demonstrated many years ago using basic Scotch tape, producing grams or even kilograms of it in a scalable industrial process seemed like a pipedream until recently. As [Tech Ingredients] demonstrates in a new video, the technique of flash Joule heating of carbon may enable industrial graphene production.
The production of this flash graphene (FG) was first demonstrated by Duy X. Luong and colleagues in a 2020 paper in Nature, which describes a fairly straightforward process. In the [Tech Ingredients] demonstration it becomes obvious how easy graphene manufacturing is using this method, requiring nothing more t...
20:37
10 Years Later, Linux Getting A Touchscreen Driver For A Once Popular Tablet Phoronix
The mainline Linux 6.4 kernel is set to see a new touchscreen driver for supporting the Novatek NVT-ts, which is used by at least a once popular Intel Atom powered Android tablet from a decade prior...
20:36
3CX compromise: More details about the breach, new PWA app released Help Net Security
3CX has released an interim report about Mandiants findings related to the compromise the company suffered last month, which resulted in a supply chain attack targeting cryptocurrency companies. They discovered that: The attackers infected targeted 3CX systems with TAXHAUL (aka TxRLoader) malware, which decrypts and executes shellcode containee in a file with a name and location aimed to make it to blend into standard Windows installations The executed shellcode is the COLDCAT downloader They also More
The post 3CX compromise: More details about the breach, new PWA app released appeared first on Help Net Security.
20:30
Dashcam Footage Shows Driverless Cars Clogging San Francisco SoylentNews
[...] The 54 [Felton line], brought to a halt by an autonomous vehicle belonging to Alphabet's Waymo, isn't the only bus that's run into trouble with San Francisco's growing crowd of driverless vehicles. Bus and train surveillance videos obtained by WIRED through public records requests show a litany of incidents since September in which anxiety and confusion stirred up by driverless cars has spilled onto the streets of the US city that has become the epicenter for testing them.
As the incidents stack up, the companies behind the autonomous vehicles, such as Waymo and General Motors' Cruise, want to add more robotaxis to San Francisco's streets, cover more territory, and run at all hours. Waymo and Cruise say they learn from every incident. Each has logged over 1 million driverless miles and say their cars are safe enough to keep powering forward. But expansions are subject to approval from California state regulators, which have been pressed by San Francisco officials for years to restrict autonomous vehicles until issues subside.
Driverless cars have completed thousands of journeys in San Franciscotaking people to work, to school, and to and from dates. They have also proven to be a glitchy nuisance, snarling traffic and creeping into hazardous terrain such as construction zones and downedpow...
20:21
KDE Connect 2.0 Planning For Big Improvements Phoronix
KDE Connect is the great software that allows for interfacing between the KDE desktop and your various mobile devices running Android, Plasma Mobile, Apple iOS, or even Sailfish OS. KDE Connect allows easily sharing files and data with your mobile device(s), receiving phone notifications on your desktop, and a lot of other remote/cross-device functionality. The KDE Connect 2.0 initiative that is taking shape this year thanks to full-time development work is going to modernize this open-source solution...
20:20
The Impact of Microsoft Bribing the Media and Suppressing Facts That Are Rarely Mentioned (Despite Their High Importance) Techrights
Video download link |
md5sum 2505cca4353b58b6a2bd075ca0a698b2
Facts About Microsoft
Creative Commons Attribution-No Derivative Works 4.0
Summary: Grifting Microsoft, propped up by bailout money and "defence" contracts from Trump and Biden, isnt doing as well as Microsoft-funded media wants us to think; there are many layoffs, rapid erosion in market share, and deep losses in the buzzwords' departments
THE media has made it exceptionally easy to be cynical and sceptical of it. Yes, the media (or mass media, corporate media, mainstream media) is gaslighting people, lying to people, blaming the victims, and glorifying the criminals. Its absurd, but thats what happens when money buys the news and lobbying can become reporting.
As noted above, the GNU/Linux world isnt immune to that. For instance, Clickfraud Spamnil [1, 2] (TFIR) is producing Microsoft spam this week, sponsored by Linux Foundation. Yesterday we spoke about all the fake coverage that hyped up chaffbots, which months later seem like a forgotten fad.
In order for the media to regain peoples trust itll need to act like media again.We now have...
20:18
Kodi forum breach: User data, encrypted passwords grabbed Help Net Security
The developers of Kodi, the widely used open-source media player app, have revealed a data breach of its user forum. What happened? The breach did not happen due to a vulnerability. Instead, an unknown attacker used the account of a legitimate but inactive member of the forum admin team to access the MyBB admin console on two occasions: February 16 and 21, 2023. The attacker was able to create backups of databases, which they then More
The post Kodi forum breach: User data, encrypted passwords grabbed appeared first on Help Net Security.
20:07
Go JUICE Centauri Dreams Imagining and Planning Interstellar Exploration
Take a look at our missions to Jupiter in context. The image below shows the history back to 1973, with the launch of Pioneer 10, and of course, the Voyager encounters. We also have the flybys by Ulysses, Cassini and New Horizons, each designed for other destinations, for Jupiter offers that highly useful gravitational assist to help us get places fast. JUICE (Jupiter Icy Moons Explorer) joins the orbiter side of the image tomorrow, with launch aboard an Ariane 5 from Kourou (French Guiana) scheduled for 1215 UTC (0815 EDT) on Thursday. You can follow the launch live here or here.

The first gravitational maneuver will be in August of next year with a Lunar-Earth flyby, followed by Venus in 2025 and then two more Earth flybys (2026 and 2029) before arrival at Jupiter in July of 2031. Ive written a good deal about both Europa Clipper and JUICE in these pages and wont go back to repeat the details, but we can expect 35 icy moon flybys past Europa, Ganymede and Callisto before insertion into orbit at Ganymede, making JUICE the first mission that will go into orbit around a satellite of another planet. Needless to say, well track JUICE closely in these pages.

Image: Ariane 5 VA 260 with JUICE, start of rollout on Tuesday 11 April. Credit for this and the above infographic: ESA.

19:55
Linux Patches Confirm Intel Meteor Lake Having An L4 Cache Phoronix
A new Intel graphics kernel driver patch posted by Intel on Tuesday confirm that upcoming Meteor Lake processors will feature an ADM/L4 cache...
19:24
New discovery points the way to more compact fusion power plants Lifeboat News: The Blog
A magnetic cage keeps the more than 100 million degree Celsius hot plasmas in nuclear fusion devices at a distance from the vessel wall so that they do not melt. Now researchers at the Max Planck Institute for Plasma Physics (IPP) have found a way to significantly reduce this distance. This could make it possible to build smaller and cheaper fusion reactors for energy production. The work was published in the journal Physical Review Letters.
19:24
Endometriosis linked to increased risk of cardiovascular disease in women Lifeboat News: The Blog
In a recent study published in the journal Maturitas, researchers conducted a systematic review and meta-analysis to compare the risk of cardiovascular events in women with and without endometriosis.
Study: Endometriosis and cardiovascular disease: A systematic review and meta-analysis. Image Credit: Bangkok Click Studio / Shutterstock.
Apart from autoimmune disorders, polycystic ovary syndrome, depression, and premature menopause, there are pregnancy-associated risk factors for cardiovascular diseases, such as gestational diabetes, pregnancy-related hypertensive disorders, placental abruption, preterm delivery, and pregnancy loss. Women experience a higher mortality rate due to cardiovascular diseases, and while the treatment methods are the same for men and women, the presentation, symptoms, diagnosis, risk factors, and response to treatment differ for women.
19:24
Gaining a Multimessenger View of Supernovae Explosions Lifeboat News: The Blog
Simultaneously detecting the gravitational-wave and neutrino signals emitted during the last second of a massive stars life could show how such stars die.
19:24
NOW: Pensions and Standard Life Cannot Tackle Pension Fraud After 3+ Months schestowitz.com
Summary: The crimes of Sirius Open Source help highlight abuse by pension providers; after more than 3 months theyre still not holding accountable pension fraudsters (at least 3 people were involved in the fraud and two of them are based in the UK, so extradition proceedings arent even required)
Latest (today):
>> I hope this helps to settle your concerns regarding your
>> NOW Pension fund, as you can see from the above, they
>> have outlined how and who is responsible for protecting
>> your pension savings and applies to all NOW Pensions members.
>
> Hi,
>
> Please send the full letter, as promised, to
> 1) my wife
> 2) myself
>
> as promised by ???????? (staff)
> as promised by ???????? (staff)
> as promised by ???????? (manager)
>
> several times since February. We need this obligation in
> writing.I need an update on this. There are multiple complainants about the pension fraud. We need action, not stalling tactics. You behave like lawyers, not like a pension provider.
19:24
Probing the Helium Nucleus beyond the Ground State Lifeboat News: The Blog
A new electron-scattering experiment challenges our understanding of the first excited state of the helium nucleus.
A helium nucleus, also known as an particle, consists of two protons and two neutrons and is one of the most extensively studied atomic nuclei. Given the small number of constituents, the particle can be accurately described by first principles calculations. And yet, the excited states of the particle remain a bit of a mystery, as evidenced by a disagreement surrounding the excitation from the ground state 01+ to the first excited state 02+ [1]. Theoretical predictions for this transition do not match measurements, but the experimental uncertainties have been too large for implications to be drawn. Now, the A1 Collaboration at Mainz Microtron (MAMI) in Germany has remeasured this transition via inelastic electron scattering [2]. The new data significantly improves the precision compared to previous measurements and confirms the initial discrepancy.
19:22
Still Waiting: Pension Providers in the UK Stalling for Months After Several Independent Reports of Pension Fraud Techrights
Summary: The crimes of Sirius Open Source help highlight abuse by pension providers; after more than 3 months theyre still not holding accountable pension fraudsters (at least 3 people were involved in the fraud and two of them are based in the UK, so extradition proceedings arent even required)
Latest (today):
>> I hope this helps to settle your concerns regarding your
>> NOW Pension fund, as you can see from the above, they
>> have outlined how and who is responsible for protecting
>> your pension savings and applies to all NOW Pensions members.
>
> Hi,
>
> Please send the full letter, as promised, to
> 1) my wife
> 2) myself
>
> as promised by (staff)
> as promised by (staff)
> as promised by (manager)
>
> several times since February. We need this obligation in
> writing.I need an update on this. There are multiple complainants about the pension fraud. We need action, not stalling tactics. You behave like lawyers, not like a pension provider.
19:09
ACE Wants Cloudflare to Expose The Pirate Bays Operators TorrentFreak
 The
Pirate Bay has been around for nearly two decades, which is quite
an achievement considering the immense legal pressure it has faced
over the years.
The
Pirate Bay has been around for nearly two decades, which is quite
an achievement considering the immense legal pressure it has faced
over the years.
Swedish police tried to shut the site down, twice, raiding dozens of servers. This ultimate goal failed but local authorities did prosecute the sites three co-founders, who all served time in prison for their involvement.
The notorious torrent site stood tall in the midst of this turmoil and continues to operate from thepiratebay.org until this day. While it is no longer the largest piracy site online, anti-piracy forces havent forgotten about it.
Pirate Bay Targeted in New Subpoena Wave
This week, we spotted yet another attempt to uncover the current operators. Through the Motion Picture Association, the Alliance for Creativity and Entertainment (ACE) requested a DMCA subpoena at the U.S. District Court for the Central District of California.
These subpoenas are not uncommon and are typically directed at third-party intermediaries, Cloudflare in this case. The Pirate Bay is a Cloudflare customer and through the court, ACE requests all useful information the California company has on its illustrious client.
The subpoena requires that you provide information concerning the individuals offering infringing material described in the attached notice, ACE informs Cloudflare.
[Y]ou are required to disclose [] information sufficient to identify the infringers. This would include the individuals names, physical addresses, IP addresses, telephone numbers, e-mail addresses, payment information, account updates and account history.
These DMCA subpoenas dont require any judicial oversight. In most cases, they are swiftly signed off by a court clerk. The legal paperwork is then sent to Cloudflare, which typically replies with all relevant information it has on file.
Actionable Intel?
...18:00
Elegant Evening Dress Sports Servo-Actuated Flowers Hackaday

Theres been plenty of research into smart fabrics, and weve seen several projects involving items of clothing with electronics integrated inside. These typically include sensors and simple actuators like LEDS, but theres no reason you cant integrate moving electromechanical systems as well. [Rehana Al-Soltane] did just that: she made an elegant evening dress with flowers that open and close on command.
It took [Rehana] a bit of experimentation to figure out a floral design that opens and closes smoothly without crumpling the fabric or requiring excessive force to actuate. She finally settled on a plastic sheet sandwiched between two layers of fabric, with pieces of fishing line attached that pull the edges inward. The lines are guided through a tube down the back of the dress, where a servo pulls or releases them.
The mechanical flower can be operated by touch [Rehana] made one of the other flowers conductive by embedding copper tape betwee...
17:57
SAP April 2023 security updates fix critical vulnerabilities Security Affairs
SAP fixed two critical bugs that affect the Diagnostics Agent and the BusinessObjects Business Intelligence Platform.
SAP April 2023 security updates include a total of 24 notes, 19 of which are new vulnerabilities. The most critical vulnerabilities are:
- CVE-2023-27267: missing authentication and insufficient input validation in the exploited by an attacker to execute scripts on connected Diagnostics Agents. Successful exploitation can potentially lead to full compromise of the system.
- CVE-2023-28765: An attacker with basic privileges in SAP BusinessObjects Business Intelligence Platform (Promotion Management) versions 420, 430, can exploit the issue to access to lcmbiar file and further decrypt the file. Once the attacker gained access to BI users passwords and depending on the privileges of the BI user, he can perform operations that can completely compromise the application.
The complete list of the notes is reported in the latest security bulletin:
SAP administrators are urged to apply the available security patches as soon as possible.
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections:
- The Teacher Most Educational Blog
- The Entertainer Most Entertaining Blog
- The Tech Whizz Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please nominate Security Affairs as your favorite blog.
Nominate here: https://docs.google.com/forms/d/e/1FAIpQLSfaFMkrMlrLhOBsRPKdv56Y4HgC88Bcji4V7OCxCm_OmyPoLw/viewform
Follow me on Twitter: @securityaffairs and Facebook and Ma...
17:43
China's Loongson Unveils 32-Core CPU, Reportedly 4X Faster Than Arm Chip SoylentNews
The 3D5000 has come out of the oven:
Loongson, a Chinese fabless chipmaker, has launched the new 3D5000 processor for data centers and cloud computing. MyDrivers (opens in new tab) reported that Loongson claims its 32-core domestic chips deliver 4X higher performance than rival Arm processors.
The 3D5000 still leverages LoongArch, Loongson's homemade instruction set architecture (ISA) from 2020. The chipmaker was previously a firm believer in MIPS. However, Loongson eventually built LoongArch from the ground up with the sole objective of not relying on foreign technology to develop its processors. LoongArch is a RISC (reduced instruction set computer) ISA, similar to MIPS or RISC-V.
The 3D5000 arrives with 32 LA464 cores running at 2 GHz. The 32-core processor has 64MB of L3 cache, supports eight-channel DDR4-3200 ECC memory, and up to five HyperTransport (HT) 3.0 interfaces. It also supports dynamic frequency and voltage adjustments. Officially, the 3D5000 has a 300W TDP; however, Loongson stated that the conventional power consumption is around 150W. That's roughly 5W per core.
The 3D5000 flaunts a chiplet design since Loongson has glued together two 16-core 3C5000 processors. Loongson developed the 3C5000 server part to compete with AMD's Zen and Zen+ architectures. The latest 3D5000, which measures 75.4 x 58.5 x 7.1mm, slides into a custom LGA4129 socket.
Read more of this story at SoylentNews.
17:36
Nadine Hoosen, Chief Science Officer at TAFFD's, joins our Biotech/Medical Board. Lifeboat News
Nadine Hoosen, Chief Science Officer at TAFFDs, joins our Biotech/Medical Board.
17:23
IRC Proceedings: Tuesday, April 11, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-110423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-110423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-110423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-110423.gmi
Over HTTP:
|
... |
17:06
OpenAI launched a bug bounty program Security Affairs
AI company OpenAI launched a bug bounty program and announced payouts of up to $20,000 for security flaws in its ChatGPT chatbot service.
OpenAI launched a bug bounty program and it is offering up to $20,000 to bug hunters that will report vulnerabilities in its ChatGPT chatbot service.
The company explained that ChatGPT is in scope, including ChatGPT Plus, logins, subscriptions, OpenAI-created plugins (e.g. Browsing, Code Interpreter), plugins users create themselves, and all other functionality. Plugins developed by other people are out of the scope.
The bug bounty program, which is operated via the Bugcrowd crowdsourced security platform, also covers APIs, API keys, and other assets belonging to OpenAI. The company is also interested in confidential OpenAI corporate information that may be exposed through third parties, such as Google Workspace, Trello, Jira, Salesforce and Stripe.
The bounties range from $200 for low-severity security issues up to $20,000 for critical vulnerabilities.
Security is essential to OpenAIs mission. We appreciate the contributions of ethical hackers who help us uphold high privacy and security standards for our users and technology. This policy (based on disclose.io) outlines our definition of good faith regarding the discovery and reporting of vulnerabilities, and clarifies what you can expect from us in return. reads the announcement published by the company.
The initial priority rating for most findings will use the Bugcrowd Vulnerability Rating Taxonomy. However, vulnerability priority and reward may be modified based on likelihood or impact at OpenAIs sole discretion. In cases of downgraded issues, researchers will receive a detailed explanation.
In March, 2023, OpenAI addressed multiple severe vulnerabilities in ChatGPT that could have allowed attackers to take over user accounts and view chat histories.
One of the issues was a Web Cache Deception vulnerability reported by the bug bounty hunter and Shockwave founder Gal Nagli, it could lead to an account takeover.
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections:
- The Teacher Most Educational Blog
- The Entertainer Most Entertaining Blog
- The Tech Whizz Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please nominate Secur...
17:03
COVID-19 Won, We Lost. Why Doesnt the Media Admit This? schestowitz.com
Video download
link | md5sum
0728ff8efe7b4350ffebfe6c23131bb0
COVID-19 Remains Untackled
Creative Commons Attribution-No Derivative Works 4.0
 ve
just
published some hard data to show how deaths have soared this
year, probably in relation to the neglect of COVID-19 response.
Institutions and media compel us to think that COVID-19 is a thing
of the past or old news while publicly-available
data shows alarming numbers, including total mortality across
all age groups (its up sharply).
ve
just
published some hard data to show how deaths have soared this
year, probably in relation to the neglect of COVID-19 response.
Institutions and media compel us to think that COVID-19 is a thing
of the past or old news while publicly-available
data shows alarming numbers, including total mortality across
all age groups (its up sharply).
Media gaslighting wont be the solution to all this. We need proper research and real, hard answers.
17:00
Grandfather Paradox? Terra Forming Terra

Our own living plasma Ocean Terra Forming Terra
The more i get my mind around the neutral neutron pair or NNP for short, the more i am convinced that it lies dense about us and permeates the whole earth. It is scaled at the same size as the hydrogen atom without having the orbital and free electron of the hydrogen atom which enlarges the scale.. My point is that however spaced our NNPs are, at a size of half an angstrom they easily pass through all our matter and been effrectively chargeless, there is scant drag. I am not going to say zero but it is still so little that we have been almost unable to detect them.
Having said all that, let us return to lightening. First off a 3D mass of free electrons or free ions for that matter is an explosive. When we look at lightening bolts we actually see a massive column passing down to the earth. It follows that freee atmospheric ions flee to the surface and interact with free electrons to produce really hot electrons.
Thus it appears that a mass of NNPs carries charged ions down to toward the ground for discharge. When it hits the ground it opens a live surface for electrons to flow back up the column. If the column breaks up, the NNPs will drain into the ground which leaves both free ions and electrons in position to explode. Plenty of energy for both thunder and heat lightening. The take home is that by simply invoking NNPs we can clearly explain and understand what we see going on up in the skies.
another consequernce of all this is that a vacuum tube is no true vacuum tube at all, but contains a full load of NNPs. I do recall that odd observations exist likely to respond well to this model.
And just where does coherant light fit into all this? Suddenly we have a convenient ordered, but neutral structure around all that we see and measure.
This also explains the nature of gravity and what i have also
observed. I have already posted that we can drive gravity out
of a given mass, simply because I have seen it done. The big
take home is that the mass of NNPs is neutral and has zero effect
on our bodies which by the way, after been separat...
How to Get Geisha-Like Skin with Ancient Japanese Rice Water Treatment Terra Forming Terra

Barefoot and health becoming a tthing Terra Forming Terra
I have posted in the past about the likely virtues of walking barefoot on the ground. These werte simply my own observations ,but i did put a note together to see if we could drum up some interest. As it was, i need not have bothered because others have also woken up to the possibilities.
This is from seven years ago already and it turns out that serious effort is underway to make it easier to do.
I actually went barefoot in the summer until I turned six and went to school. That was the common deal then. winter time saw rubber boots and thick socks of course. also i stayed with leather shoes for office work until recently. All that is now harder to do.
The real take home is that been grounded empowers your body to heal pro[erly, simply because your nervous system can scavenge free electrons when needed. all those stories here go back to allowing your body to do its job and wrapping yourself in insulators is obviously stupid.
<iframe width="661" height="372" src="https://www.youtube.com/embed/cRW0XO2xWn4" title="Grounding - The Grounded Documentary Film about "Earthing"" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" allowfullscreen></iframe>
16:57
CEO of Sirius UK Continues to Purge Any Remnants of His Past With the Company (Trying Hard Not to Associate With It) Techrights
Also see: Sirius UK CEO Resigns (or Gets Sacked) and Completely Deletes His Whole Past With Sirius Open Source | Amid Fraud at Sirius Open Source CEO Deletes His Recent (This Month) Past With the Company
Latest:
Oh, look what has just happened:
Summary: Knowing the crimes of Sirius Open Source as a high-level insider, the CEO who bullied Sirius staff is running away, one can imagine after internal confrontation and risk of arrest/extradition/prosecution; we are still waiting for NOW: Pensions to send us letters and for Standard Life to progress several complaints from several of the companys victims
16:38
Urgent: Microsoft Issues Patches for 97 Flaws, Including Active Ransomware Exploit The Hacker News
It's the second Tuesday of the month, and Microsoft has released another set of security updates to fix a total of 97 flaws impacting its software, one of which has been actively exploited in ransomware attacks in the wild. Seven of the 97 bugs are rated Critical and 90 are rated Important in severity. Interestingly, 45 of the shortcomings are remote code execution flaws, followed by 20
16:15
GitGuardian Honeytoken helps companies secure their software supply chains Help Net Security
GitGuardian launched its new Honeytoken module, providing intrusion detection, code leakage detection and helping companies secure their software supply chains against attackers targeting Source Control Management (SCM) systems, Continuous Integration Continuous Deployment (CI/CD) pipelines, and software artifact registries. Honeytoken is a significant addition to our code and supply chain security platform, said Eric Fourrier, CEO of GitGuardian. It enables organizations to detect intrusions in their DevOps environments effectively. Security teams can now easily monitor their More
The post GitGuardian Honeytoken helps companies secure their software supply chains appeared first on Help Net Security.
15:10
Cybercrime group exploits Windows zero-day in ransomware attacks Security Affairs
Microsoft has addressed a zero-day in the Windows Common Log File System (CLFS) actively exploited in ransomware attacks.
Microsoft has addressed a zero-day vulnerability, tracked as CVE-2023-28252, in the Windows Common Log File System (CLFS), which is actively exploited in ransomware attacks. Microsoft fixed the issue with the release of Patch Tuesday security updates for April 2023.
The issue is an unspecified vulnerability in the CLFS driver that allows for privilege escalation. A local attacker can exploit this vulnerability to gain SYSTEM privileges. The vulnerability is easy to exploit and could be triggered without user interaction.
US CISA has added the flaw to its Known Exploited Vulnerabilities Catalog, based on evidence that threat actors are exploiting the flaw to escalate privileges and deploy Nokoyawa ransomware.
CISA orders federal agencies to fix this vulnerability by May 2nd, 2023.
Kaspersky Lab experts first reported that the CVE-2023-28252 flaw was exploited in attacks deploying the Nokoyawa ransomware.
On February 2023, Kaspersky experts observed a number of attempts to execute elevation-of-privilege exploits on Microsoft Windows servers belonging to small and medium-sized businesses in the Middle East, in North America, and previously in Asia regions.
The experts pointed out that while the majority of zero-days they have discovered in the past were used by APT groups, this zero-day was exploited by a sophisticated cybercrime group. This group is known to have used similar CLFS driver exploits in the past that were likely developed by the same author.
The discovered exploit uses the vulnerability to corrupt another specially crafted base log file object in a way that a fake element of the base log file gets treated as a real one.̶...
15:00
Portable MSX2 Brings the Fun on the Go Hackaday

Something of a rarity in the US, the MSX computer standard was rather popular in other parts of the world but mostly existed in the computer-in-a-keyboard format popular in the 80s. [Aron Hoekstra aka nullvalue] wanted to build an MSX2 of their own, but decided to build it in a...
14:57
Ethereums Shanghai Update Opens a Rift in Crypto SoylentNews
At 19:27 Eastern time on April 12, the Ethereum blockchain, home to the world's second-most-popular cryptocurrency, ether, will finally sever its links to crypto mining. Within the Ethereum bubble, a sense of anticipation is building; some are planning "viewing parties" for the occasion. Codenamed "Shanghai," the update to Ethereum caps off a process, after "The Merge," which fundamentally changes the way transactions are verified and the network secured.
Under the old system, proof-of-work (PoW) mining, the right to process a batch of transactions and earn a crypto reward is determined by a race to solve a mathematical puzzle. The greater the computing power miners throw at the problem, the greater their chance of winning the race. Under Ethereum's new proof-of-stake (PoS) system, there is no race and there are no miners; instead, the winner is determined by raffle. The greater the amount of ether somebody locks up on the networkor stakesthe greater the chance they hold a prize-winning ticket.
By demonstrating that a large-scale blockchain can shift from one system to another, Shanghai will reignite a debate over whether the practice of mining that still supports bitcoin, the most widely traded cryptocurrency, is viable and sustainable. [...]
"The energy consumption problem is Bitcoin's achilles heel," says de Vries. "It's a simple fact that as the price of bitcoin gets higher, the energy consumption problem gets worse. The more money miners make, the more they will typically spend on resources: hardware and electricity.
Read more of this story at SoylentNews.
14:30
Key factors driving changes in the perception of the CISO role Help Net Security
The CISO role is currently fraught with novel challenges and escalating workloads. This includes increased paperwork and time spent on risk assessments, which have surged from two to thirty hours per assessment. Furthermore, privacy regulations are expanding, and CISOs are increasingly being held responsible for the companys security decisions or lack thereof. These difficulties are poised to intensify further with the fresh mandates and demands outlined in the Biden administrations cyber strategy. In this Help More
The post Key factors driving changes in the perception of the CISO role appeared first on Help Net Security.
14:06
North Korean Hackers Uncovered as Mastermind in 3CX Supply Chain Attack The Hacker News
Enterprise communications service provider 3CX confirmed that the supply chain attack targeting its desktop application for Windows and macOS was the handiwork of a threat actor with North Korean nexus. The findings are the result of an interim assessment conducted by Google-owned Mandiant, whose services were enlisted after the intrusion came to light late last month. The threat intelligence
14:00
Data-backed insights for future-proof cybersecurity strategies Help Net Security
The Qualys Threat Research Unit (TRU) has been hard at work detecting vulnerabilities worldwide, and its latest report is set to shake up the industry. In this Help Net Security interview, Travis Smith, VP of the Qualys TRU, talks about the 2023 Qualys TruRisk Threat Research Report, which provides security teams with data-backed insights to help them better understand how adversaries exploit vulnerabilities and render attacks. What are the most dangerous cyber threats to look More
The post Data-backed insights for future-proof cybersecurity strategies appeared first on Help Net Security.
14:00
CoreCtrl Now Available In Debian & Ubuntu 23.04 For Managing Your System Phoronix
CoreCtrl as the open-source utility for managing your system's performance/vitals and supporting various application profiles has landed in Debian as well as being picked up for easy installation on the upcoming Ubuntu 23.04...
13:45
600,000 Americans Per Year Are Dying From COVID Shots Says Top Insurance Analyst cryptogon.com
Via: The Florida Standard: Those vaccinated against COVID-19 have a 26 percent higher mortality rate on average compared to those who declined the jab and the death toll is even more staggering for vaccinated people under 50 years old, where mortality is 49 percent higher than for those unvaccinated. The shocking numbers are based []
13:33
In Ireland, More Deaths at End of 2022 Than in 2021 (COVID-19) and Far More Deaths Now Than During COVID-19s Peak schestowitz.com
tl;dr 8467 deaths in 2022Q3, compared to 8165 in 2021Q3
 ast
year
we looked at this data and found that Ireland was not solving
the COVID-19 problem.
ast
year
we looked at this data and found that Ireland was not solving
the COVID-19 problem.
We have newer data now.
Now, lets compare Q3 deaths for even older years:
6517 in 2010
6911 in 2011
6825 in 2012
6983 in 2013
7001 in 2014
6851 in 2015
7129 in 2016
6987 in 2017
7143 in 2018
7358 in 2019
7111 in 2020
Dont believe the numbers? Heres the data:
13:30
Hybrid work environments are stressing CISOs Help Net Security
The impact of the hybrid workforce on security posture, as well as the risks introduced by this way of working, are posing concerns for CISOs and driving them to develop new strategies for hybrid work security, according to Red Access. Among the reports most critical findings is the revelation that browsing-based threats ranked as CISOs number one concern, regardless of whether their organization was operating primarily in an in-office, hybrid, or remote setting. And as More
The post Hybrid work environments are stressing CISOs appeared first on Help Net Security.
13:22
Leaked Classified Military Documents On Ukraine [???] cryptogon.com
The non-stop mainstream media promotion of this gives me pause. I dont know what Im looking at. As for Western special forces operating in Ukraine, Ive suspected it since May of last year. If you want to see the documents in question for yourself, Cryptome is hosting them. Via: BBC: The UK is among a []
13:14
COVID-19 Death Toll in the UK Passes 222,222, Not Counting Indirect Deaths schestowitz.com
 xcess
mortality has been off the charts since last summer. The media
chooses to not talk about this (or barely even mention
that). A lot more publicly-funded research is needed here, with no
(corporate) strings attached.
xcess
mortality has been off the charts since last summer. The media
chooses to not talk about this (or barely even mention
that). A lot more publicly-funded research is needed here, with no
(corporate) strings attached.
Meanwhile, UK Deaths with COVID-19 on the death certificate exceeds 222,222 (222,283 is the already-outdated figure).
Should we take this for granted? Or the new normal? Looking at the hard data, containment saved lived. Lockdowns had a real effect:
COVID-19 is still with us. It won. Its an unsolved problem and its not over, the media is just deflecting and leveraging Russia/Ukraine.
Yesterday around 10AM ONS was supposed to release some death-related figures (updated every Tuesday), but this time it was delayed till 13th of April 2023, i.e. tomorrow. Yesterday wasnt Bank Holiday.
13:00
Threat hunting programs can save organizations from costly security breaches Help Net Security
Cybersecurity threats to organizations are only increasing, not only in number but in scope, according to Team Cymru. The true cost of cyber breaches Proactive threat hunting helps organizations save money by preventing security breaches and reducing the impact of attacks. For example, a study by IBM found that the average total cost of a breach is $4.35 million. To better understand the perspective of threat hunters who are in the trenches defending their organizations More
The post Threat hunting programs can save organizations from costly security breaches appeared first on Help Net Security.
12:58
NYPD Reboots Cyborg Police Dog After Backlash cryptogon.com
Via: New York Daily News: Digidog, the NYPD robot pooch, is back and department leaders promise its not the dystopian surveillance nightmare it was made out to be the first time New Yorkers got a look at it. Two years after the $74,000 robot canine program landed the NYPD in the doghouse with civil rights []
12:30
11:11 Systems Managed SteelDome provides protection from ransomware attacks Help Net Security
11:11 Systems has revealed 11:11 Managed SteelDome in partnership with SteelDome Cyber. The fully managed service is designed for organizations in need of secure, scalable and cost-efficient storage of their unstructured, on-premises data. Leveraging SteelDomes InfiniVault application technology, 11:11 Managed SteelDome provides on-premises data storage, protection and recovery. This new offering provides data immutability and protection from ransomware attacks and optimizes data storage, all while meeting strict compliance and regulatory requirements. Acting as a storage More
The post 11:11 Systems Managed SteelDome provides protection from ransomware attacks appeared first on Help Net Security.
12:10
What to Know About the JUICE Mission to Jupiter and its Frozen Moons SoylentNews
JUICE, short for JUpiter ICy moons Explorer, is headed for Jupiter, but the spacecraft will focus its observations on three of the gas giant's many moons: Europa, Ganymede, and Callisto. Jupiter, the largest planet in the solar system, hosts more than 70 natural satellites, but these three Galilean moons are thought to hold immense amounts of subsurface water hidden beneath thick layers of ice (Io is the fourth Galilean moon, but it's an inhospitable volcanic hellhole). JUICE, an international collaboration headed by the European Space Agency, will spend three to four years at Jupiter, performing flybys and making detailed observations of the three icy moons and their immediate surroundings.
[...] JUICE will reach Jupiter in 2031 following an eight-year journey, but to get there it'll need to receive four gravity boosts from Earth and Venus. Excitingly, the spacecraft's flyby of the Earth-Moon system, a maneuver known as a Lunar-Earth gravity assist (LEGA), has never been attempted before. As ESA explains, JUICE will first get a gravitational assist from the Moon and then a second from Earth some 1.5 days later, in a maneuver meant to "save a significant amount of propellant."
Europa, Ganymede, and Callisto are all suspected of containing subsurface oceans capped in an icy crust. JUICE will evaluate the trio for potential signs of habitability, given the assumed presence of liquid water. Indeed, and as ESA makes clear, the overarching question of the mission is whether gas giants can harbor habitable conditions and spawn primitive life. In addition to its astrobiological duties, JUICE will seek to answer questions about planetary formation and the solar system in general. More conceptually, the spacecraft will evaluate the "wider Jupiter system as an archetype for gas giants across the Universe," according to ESA.
Read more of this story at SoylentNews.
12:00
Using Old Coal Mines As Cheap Sources of Geothermal Heat Hackaday

For as much old coal mines are a blight upon the face of the Earth, they may have at least one potential positive side-effect. Where the coal mine consists out of tunnels that were drilled deep into the soil, these tend to get flooded by groundwater after the pumps that keep them dry are turned off. Depending on the surrounding rock, this water tends to get not only contaminated, but also warmed up. As the BBC explains in a recent video as a follow-up to a 2021 article, when the water is pumped up for decontamination, it can be run through a heat exchanger in order to provide heat for homes and businesses.
11:55
11:41
Links 11/04/2023: Budgie Desktop 10.7.x and Ubuntu Budgie 23.04 Techrights
![]()
Contents
-
GNU/Linux
-
Server
-
Linux Links 9 Best Free and Open Source PaaS Cloud Computing Stacks
Platform as a Service (PaaS) is a category of cloud computing services which offers a way to support the complete lifecycle of delivering web applications and services via the cloud. Along with Software as a Service (SaaS) and Infr...
-
-
11:08
NEW 'Off The Wall' ONLINE 2600 - 2600: The Hacker Quarterly
NEW 'Off The Wall' ONLINE
Posted 12 Apr, 2023 1:08:08 UTC
The new edition of Off The Wall from 04/11/2023 has been archived and is now available online.
10:55
"Inside-out Wankel" rotary engine delivers 5X the power of a diesel Terra Forming Terra

10:06
Microsoft (& Apple) Patch Tuesday, April 2023 Edition Krebs on Security
Microsoft today released software updates to plug 100 security holes in its Windows operating systems and other software, including a zero-day vulnerability that is already being used in active attacks. Not to be outdone, Apple has released a set of important updates addressing two zero-day vulnerabilities that are being used to attack iPhones, iPads and Macs.

On April 7, Apple issued emergency security updates to fix two weaknesses that are being actively exploited, including CVE-2023-28206, which can be exploited by apps to seize control over a device. CVE-2023-28205 can be used by a malicious or hacked website to install code.
Both vulnerabilities are addressed in iOS/iPadOS 16.4.1, iOS 15.7.5, and macOS 12.6.5 and 11.7.6. If you use Apple devices and you dont have automatic updates enabled (they are on by default), you should probably take care of that soon as detailed instructions on how to attack CVE-2023-28206 are now public.
Microsofts bevy of 100 security updates released today include CVE-2023-28252, which is a weakness in Windows that Redmond says is under active attack. The vulnerability is in the Windows Common Log System File System (CLFS) driver, a core Windows component that was the source of attacks targeting a different zero-day vulnerability in February 2023.
If it seems familiar, thats because there was a similar 0-day patched in the same component just two months ago, said Dustin Childs at the Trend Micro Zero Day Initiative. To me, that implies the original fix was insufficient and attackers have found a method to bypass that fix. As in Februar...
10:00
HPR3833: Software Freedom Podcast Hacker Public Radio
Software Freedom Podcast - Free Software Foundation Europe Another recommendation for your podcatcher from our sister project https://freeculturepodcasts.org/ Website: https://fsfe.org/about/about.en.html Episode: https://fsfe.org/news/podcast/episode-14.html Feed Opus: feed://fsfe.org/news/podcast-opus.en.rss Feed mp3: feed://fsfe.org/news/podcast.en.rss Copyright (c) Free Software Foundation Europe. Creative Commons BY-SA 4.0 SFP#14: The world of mesh networking with Elektra Wagenrad With this episode the Software Freedom Podcast opens the door to the fascinating and sometimes complex world of mesh networking. And who better than Elektra Wagenrad can take us on this journey? Elektra is one of the original developers of the B.A.T.M.A.N. protocol and of the Mesh Potato project. In our 14th Software Freedom Podcast episode Matthias Kirschner talks with our guest, Elektra Wagenrad, about the origins of Freifunk, the B.A.T.M.A.N. protocol, and the Mesh Potato project. If you are new to the world of mesh networking this episodes is an easy entrance to it. Elektra not only explains the theory behind the protocols but also dives deeper into the philosophical idea of it. In this context, Matthias and Elektra also touch on the difficult topic of limiting the use of Free Software, using the example of the former ban on the use of the B.A.T.M.A.N. protocol for military activities. Last but not least they also discuss the EUs Radio Equipment Directive and the FSFE's Router Freedom activity. With this episode, the Software Freedom Podcast has produced an easy to follow and easy to understand podcast for everybody who is interested in mesh networking. Join us on our journey through this fascinating technical and philosophical world and listen to Elektra and Matthias as they tell the story with its ups and downs. Read more: What is Free Software? Freifunk (DE) Open-Mesh Project The "Mesh Potato" project FSFEs activity on Radio Lockdown FSFE's Router Freedom activity If you liked this episode and want to support our continuous work for software freedom, please help us with a donation.
09:44
Nonthapat "Brave" Pulsiri joins our blog team with the post "How can we make the space sector more sustainable?". Lifeboat News
Nonthapat Brave Pulsiri joins our blog team with the post "How can we make the space sector more sustainable?".
09:25
CVE-2023-1281, CVE-2023-1829: Linux kernel: Vulnerabilities in the tcindex classifier Open Source Security
Posted by valis on Apr 11
Hi,I have recently discovered two security issues in the tcindex
classifier (part of the network QoS subsystem of the Linux kernel):
CVE-2023-1281 Race condition leading to an use-after-free when
updating imperfect hash filters
CVE-2023-1829 Use-after-free when deleting a perfect hash filter
# Impact / mitigation:
Both of these vulnerabilities can be used for local privilege escalation.
The attacker needs CAP_NET_ADMIN to create/change...
09:24
Tesla Employees Reportedly Shared Videos Captured by Cameras on Customers' Cars SoylentNews
They even shared a clip of a child being hit by a car:
Some Tesla workers shared sensitive photos and videos captured by the cameras on owners' cars between each other for several years, according to Reuters. Former employees told the outlet that colleagues shared the images in group chats and one-on-one communications between 2019 and last year.
One such video showed a Tesla driving at high speed before hitting a child on a bike, Reuters reported. Other footage included things like a nude man walking toward a vehicle. "We could see them doing laundry and really intimate things. We could see their kids," one of the former employees said.
[...] The company states in its customer privacy notice that it designed the camera system to protect user privacy. It says that even if owners opt in to share camera recordings with Tesla for "fleet learning" purposes, "camera recordings remain anonymous and are not linked to you or your vehicle" unless it receives the footage due to a safety event, such as a crash or an airbag deployment. Even so, one employee said it was possible for Tesla data labelers to see the location of captured footage on Google Maps.
Tesla does not have a communications department that can be reached for comment.
Read more of this story at SoylentNews.
09:00
Mag Loop Antenna has a Brain Hackaday

Magnetic loop antennas are great if you are limited on space since they are just a potentially small loop of wire. The problem is, they are sharply tuned. You normally have an adjustment capacitor to tune the antenna to different frequencies. [TekMakerUK] built one with a motor and an Arduino that he can tune from an Android phone. You can see more about the project in the video below.
If you want to transmit, the capacitor is often the weak part of the system. Luckily, some old gear yielded a capacitor with multiple sections and enough plate distance to handle the 5W desired. Of course, motor driving a capacitor isnt a new idea, but this setup is nice since it uses a stepper motor and a rotary encoder.
For now, the control just moves the stepper to a particular
position, but long term, there are plans to have presets for each
band that the Arduino can set from a single command. You might
wonder how the stepper knows where it is since there are no limit
switches. It turns out he just stalls the motor and assumes it is
at the far limit and then moves it to the other limit (see
initMotor) in the GitHub source code.
Loops are easy to hide. This isnt, of course, the first...
08:21
QuaDream: Israeli Cyber Mercenary Behind iPhone Hacks HackRead | Latest Cybersecurity and Hacking News Site
Citizens Lab and Microsoft have exposed an Israeli firm, QuaDream, selling spyware to governments around the world.
This is a post from HackRead.com Read the original post: QuaDream: Israeli Cyber Mercenary Behind iPhone Hacks
07:00
Nginx 1.24 Released With TLSv1.3 Protocol Enabled By Default Phoronix
06:39
Satellite Imagery Reveals Hidden Tornado Tracks SoylentNews
The analysis could help researchers study storms that strike in the winter:
When a strong tornado roars through a city, it often leaves behind demolished buildings, broken tree limbs and trails of debris. But a similarly powerful storm touching down over barren, unvegetated land is much harder to spot in the rearview mirror.
Now, satellite imagery has revealed a 60-kilometer-long track of moist earth in Arkansas that was invisible to human eyes. The feature was presumably excavated by a tornado when it stripped away the uppermost layer of the soil, researchers report in the March 28 Geophysical Research Letters. This method of looking for "hidden" tornado tracks is particularly valuable for better understanding storms that strike in the winter, when there's less vegetation, the researchers suggest. And recent research has shown that wintertime storms are likely to increase in intensity as the climate warms (SN: 12/16/21).
[...] Swirling winds, even relatively weak ones, can suction up several centimeters of soil. And since deeper layers of the ground tend to be wetter, a tornado ought to leave behind a telltale signature: a long swath of moister-than-usual soil. Two properties linked with soil moisture level its texture and temperature in turn impact how much near-infrared light the soil reflects.
Wang and his collaborators analyzed near-infrared data collected by NASA's Terra and Aqua satellites and looked for changes in soil moisture consistent with a passing tornado.
Read more of this story at SoylentNews.
06:00
Truckla Gets an Open Source Charging Buddy Hackaday

More than three years have passed since Tesla announced its Cybertruck, and while not a one has been delivered, the first Tesla truck, Truckla, has kept on truckin. [Simone Giertz] just posted an update of what Truckla has been up to since it was built.
[Giertz] and friends DIT (do-it-together) truck was something of an internet sensation when it was revealed several m...
05:34
A By-Design flaw in Microsoft Azure can allow storage accounts takeover Security Affairs
A flaw in Microsoft Azure could be exploited by attackers to gain access to storage accounts, perform lateral movements, and even execute remote code.
Researchers from the security firm Orca demonstrated how to abuse Microsoft Azure Shared Key authorization to gain full access to storage accounts and potentially critical business assets. The issue can also be abused to move laterally in the environment and even execute remote code.
Microsoft already recommends disabling shared key access and using Azure Active Directory authentication instead, but experts pointed out that shared key authorization is still enabled by default when creating storage accounts.
Orca discovered that it is possible to abuse and leverage Microsoft Storage Accounts by manipulating Azure Functions to steal access tokens of higher privileged identities, move laterally, access critical business assets, and execute remote code (RCE). reads the advisory published by the security firm.
Azure storage accounts can host different data objects, such as blobs and file shares. By default, Azure Storage account requests can be authorized with either Azure Active Directory (Azure AD) credentials or by using the account access key for Shared Key authorization.
Every time users create a storage account, Azure generates two 512-bit storage account access keys for the account. Microsoft warns that anyone who can obtain one of these keys can authorize access to data via Shared Key Authorization and get access to a storage account. The IT giant recommends using Azure AD authorization instead of Shared Key Authorization.
Access to the shared key grants a user full access to a storage accounts configuration and its data. states Microsoft.
Once obtained full-access permission to storage accounts, an attacker within the cloud environment can access information in storage accounts, including Azure functions sources, and manipulate their code to steal and...
05:26
Ukrainian Hackers Breach Email of APT28 Leader, Whos Wanted by FBI HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
APT28, or Fancy Bear, is a Russian government-backed nefarious hacking group known for using spear-phishing campaigns against its targets.
This is a post from HackRead.com Read the original post: Ukrainian Hackers Breach Email of APT28 Leader, Whos Wanted by FBI
04:33
Youtube-dl Hosting Ban Paves the Way to Privatized Censorship TorrentFreak
 In 2020, the RIAA
infuriated many players in the open source community by
targeting YouTube-ripping tool youtube-dl.
In 2020, the RIAA
infuriated many players in the open source community by
targeting YouTube-ripping tool youtube-dl.
The RIAA sent a takedown notice to GitHub, alleging that the software bypassed technological protection measures, in violation of the DMCA.
GitHub initially complied but later changed course. After consulting legal experts, including those at the EFF, it restored the youtube-dl repository. GitHub also launched a million-dollar defense fund to assist developers in similar disputes.
Targeting Youtube-dls Host
This episode was a massive setback for the music industry, which had been fighting stream-ripping tools for years. However, instead of laying down their arms, the music companies went after Uberspace, youtube-dls website hosting company in Germany.
A few days ago this lawsuit resulted in a clear victory for Sony Entertainment, Warner Music Group and Universal Music. The district court of Hamburg essentially ruled that youtube-dl violates the law as it bypasses YouTubes technological protection measures.
Going one step further, the court also concluded that as a host, Uberspace can be held liable for youtube-dls activity. The hosting provider received a takedown notice for the website in the past but continued to host it. According to Uberspace, the software wasnt clearly illegal but the court ruled that the company should have known better.
With the dust beginning to settle, TorrentFreak spoke with Uberspace owner Jonas Pasche, who has decided to appeal the ruling. According to Pasche, the court made a big mistake that could have far-reaching consequences.
Uberspace Responds to Court Verdict
For starters, Pasche still doesnt believe that its clear that youtube-dl violates copyright law. More importantly for his own business, however, is the courts finding that a hosting company can be held liable for doubting the validity of a takedown request.
German law requires hosting companies to remove the content as soon as they learn about clear or obvious illegal activity. Thats an easy decision in many cases, but Uberspace paused for thought in youtube-dls case, presumably...
04:07
[$] Python 3.12: error messages, perf support, and more LWN.net
Python 3.12 approaches. While the full feature set of the final releaseslated for October 2023is still not completely known, by now we have a good sense for what it will offer. It picks up where Python 3.11 left off, improving error messages and performance. These changes are accompanied by a smattering of smaller changes, though Linux users will likely make use of one in particular: support for the perf profiler.
04:05
The U.S. Deserves Stronger Spyware Protections Than Bidens Executive Order Deeplinks
U.S. President Joe Biden has signed an executive order that limits U.S. government agencies from using commercially available spyware but that doesnt mean there will be no government use of spyware in the United States. Spyware is a type of malicious software (or malware) which allows someone to gain remote access to a targets device without the knowledge or consent of the device operator. This includes all of the data on it: messenger logs, photos, files, and contacts. It also gives the ability to conduct novel forms of real-time surveillance, for example, by accessing the devices microphone and cameras. This technique has been used by nation-states around the world to spy on journalists, dissidents, and minority groups.
Additionally, spyware allows governments to manipulate data on devices, including corrupting, planting, or deleting data, or recovering data that has been deleted, all while erasing any trace of the intrusion. There is a growing concern about law enforcement taking control of suspects' digital devices and tampering with their content.
The executive order arrived only days before revelations that the United States, which was previously thought to have steered clear of some of the most infamous foreign spyware products, actually had a contract to test and deploy the notorious Pegasus created by Israeli company NSO Group. The contract was signed under a fake name on November 8, 2021 between an organization that acts as a front for the U.S. government and an American affiliate of NSO group. Only...
04:00
Arizona State University Professors Work to Stabilize the Grid Pays Off IEEE Spectrum

Whenever new technologies are introduced into the power grid, theres always a chance they could disrupt the system, possibly even leading to blackouts.
Finding ways to deal with the impact on the grid caused by incorporating renewable energy has been the focus of Vijay Vittals research for nearly 20 years. He is a professor of power systems engineering in the Fulton program at Arizona State University, in Tempe.
The IEEE Life Fellow is credited with working out how best to isolate parts of the power grid to prevent the entire grid from going down.
He was part of an IEEE task force that in 2020 issued a report that described how equipment used for storing energy, transferring power over long distances, and integrating renewable energy could impact power system stability. The report recommended ways to characterize and define the problem.
Vijay Vittal
Employer
Arizona State University, in Tempe
Title
Regents professor of electrical, computer, and energy engineering
Member grade
Life Fellow
Alma mater
B.M.S. College of Engineering, in Bangalore
An article he cowrote that was based on the report received a 2022 IEEE Power & Energy Society Prize Paper Award.
The award was a welcome surprise, he says, though we thought the document turned out very well.
From synchronous machines to fast response power electronics
That article was an update of a 2004 article that Vittal coauthored as a member of a joint task force formed by the IEEE Power & Energy Society and CIGRE, an international association of power system professionals, headquartered in Paris.
03:57
Drivers in Europe Net Big Data Rights Win Against Uber and Ola SoylentNews
Drivers in Europe net big data rights win against Uber and Ola:
In a major win over opaque algorithmic management in the so-called gig economy an appeals court in the Netherlands has found largely in favor of platform workers litigating against ride-hailing giants Uber and Ola judging the platforms violated the drivers' rights in a number of instances, including when algorithms were involved in terminating driver accounts.
The court also ruled the platforms cannot rely on trade secrets exemptions to deny drivers access to their data. Although challenges remain for regional workers to use existing laws to get enough visibility into platforms' data processing to know what information to ask for to be able to meaningfully exercise their data access rights.
The appeal court rulings can be found here, here and here (in Dutch).
The appeal was brought by the not-for-profit data trust Worker Info Exchange (WIE) in support of members of the App Drivers & Couriers Union (ADCU) in the UK and a driver based in Portugal.
One case against Uber's robo-firings involved four drivers (three based in the UK, one in Portugal); a second case against Uber over data access involved six UK-based drivers; while a data access case against Ola involved thee UK-based drivers.
In the data access cases drivers were seeking information such as passenger ratings, fraud probability scores, earning profiles, as well as data on the allocation of journeys to drivers including Uber's batch matching and upfront pricing systems as well as information about the existence of automated decision-making touching their work on the platforms.
Several decisions taken by the ride-hailing platforms were found to meet the relevant legal test of automated decision-making including assigning rides; calculating prices; rating drivers; calculating 'fraud probability scores'; and deactivating drivers' accounts in response to suspicions of fraud meaning drivers are entitled to information on the underlying logic of these decisions. (And also to a right to meaningful human review if they object to decisions.)
Read more of this story at SoylentNews.
03:17
Links 11/04/2023: FreeBSD 13.2 is Out and Alyssa Rosenzweig Leaves Collabora Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Monopolies
-
GNU/Linux
-
Audiocasts/Shows
-
WordPress WP Briefing:...
-
-
03:14
Major Hack Hits South Korean Exchange GDAC, $13.9M Stolen HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
The hack took place on April 9, 2023, in which hackers gained control of some of the exchange's hot wallets.
This is a post from HackRead.com Read the original post: Major Hack Hits South Korean Exchange GDAC, $13.9M Stolen
02:32
Strategy Reporting Essentials: A Guide to Efficient Data Collection HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
In the dynamic world of business, the ability to make data-driven decisions is essential for organizations seeking a
This is a post from HackRead.com Read the original post: Strategy Reporting Essentials: A Guide to Efficient Data Collection
02:30
Firefox 113 Beta Adds Animated AV1 Image Support Phoronix
With Firefox 112 now released, Mozilla has promoted Firefox 113 to beta...
02:00
AMD CPUs Are Safe For Late-Loading Microcode, Will No Longer Taint The Linux Kernel Phoronix
Intel processors should have any CPU microcode updates loaded early during the Linux boot process to avoid various known issues. When "late loading" CPU microcode after the system is up and running, various issues can happen on Intel processors that led them to mark the Linux kernel as tainted under such conditions. Tainting the kernel also happened when late-loading microcode on AMD CPUs but now that's been deemed unnecessary and late-loading CPU microcode on AMD processors is reportedly safe...
01:59
Helsinki Times Shows Disturbing Trend of News Sites Which Falsely Market Themselves to Readers Techrights
Who pays for these promotional buses/trains?
But what does the company actually do?
Summary: There are many so-called news sites that operate similarly but arent ever telling this to their audience (readers are the real product, sold to the real clients, who are the marketers and lobbyists); this silent takeover by Public Relations (PR) nonsense or even disinformation campaigns has become rampant in todays World Wide Web; the Linux Foundation funds some of these sites
01:46
The latest release of FreeBSD, version 13.2, has been released. It contains lots of package upgrades including to OpenSSH 9.2p1, OpenSSL 1.1.1t, and OpenZFS 2.1.9. Other new features include upgrading the bhyve hypervisor to now support more than 16 virtual CPUs in a guest, a WireGuard VPN driver, netlink for network configuration, and lots more. See the release notes for more information.
01:45
MIT Technology Review is Running SPAM for Microsoft and Azure (Distracting From Mass Layoffs) Techrights
Two months ago: MIT Technology Review is Run by Microsoft India
This week:
Summary: Over the past couple of months MIT Technology Review ran endless Microsoft puff pieces (weve attempted never to link to them; this was a daily occurrence, sometimes the majority of all new content), but the sponsorship isnt so easy to hide anymore and it brings us back to the days MIT took bribes from Bill Gates via his close friend Jeffrey Epstein
01:30
It isnt WebAssembly, but it is Assembly in Your Browser Hackaday

You might think assembly language on a PC is passe. After all, we have a host of efficient high-level languages and plenty of resources. But there are times you want to use assembly for some reason. Even if you dont, the art of writing assembly language is very satisfying for some people like an intricate logic puzzle. Getting your assembly language fix on a microcontroller is usually pretty simple, but on a PC there are a lot of hoops to jump. So why not use your browser? Thats the point of this snazzy 8086 assembler and emulator that runs in your browser. Actually, it is not native to the browser, but thanks to WebAssembly, it works fine there, too.
No need to set up strange operating system environments or link to an executable file format. Just write some code, watch it run, and examine all the resulting registers. You can do things using BIOS interrupts, though, so if you want to write to the screen or whatnot, you can do that, too.
The emulation isnt very fast, but if you are single-stepping or watching, thats not a bad thing. It does mean you may want to adjust your timing loops, though. We didnt test our theory, but we expect this is only real mode 8086 emulation because we dont see any protected mode registers. Thats not a problem, though. For a learning tool, youd probably want to stick with real mode, anyway. The...
01:28
Mesa 23.1 RADV Change Leads To ~60% Smaller Single File Disk Cache Phoronix
For those making use of Mesa's single-file on-disk shader cache, with the upcoming Mesa 23.1 release there will be increased space savings with the Radeon Vulkan (RADV) driver...
01:22
Paul Thomas Anderson: Masterworks Lifeboat News: The Blog
An illustrated mid-career monograph exploring the 30-year creative journey of the 8-time Academy Award-nominated writer and director
Paul Thomas Anderson has been described as one of American films modern masters and the foremost filmmaking talent of his generation. Andersons lms have received 25 Academy Award nominations, and he has worked closely with many of the most accomplished actors of our time, including Lesley Ann Manville, Julianne Moore, Daniel Day-Lewis, Joaquin Phoenix, and Philip Seymour Homan. In Paul Thomas Anderson: Masterworks, Andersons entire careerfrom Hard Eight (1996), Boogie Nights (1997), Magnolia (1999), Punch Drunk Love (2002), There Will Be Blood (2007), The Master (2012), Inherent Vice (2014), and Phantom Thread (2017) to his music videos for Radiohead to his early short lmsis examined in illustrated detail for the rst time.
Andersons inuences, his style, and the recurring themes of alienation, reinvention, ambition, and destiny that course through his movies are analyzed and supplemented by rsthand interviews with Andersons closest collaboratorsincluding producer JoAnne Sellar, actor Vicky Krieps, and composer Jonny Greenwoodand illuminated by lm stills, archival photos, original illustrations, and an appropriately psychedelic design aesthetic. Masterworks is a tribute to the dreamers, drifters, and evil dentists who populate his world.
01:22
Jeff Bezos is looking to defy death. This is what we know about the science of aging Lifeboat News: The Blog
Never listen to anyone who says the big questions have already been answered. We still have plenty to learn about extending our lifespans.
01:19
Automotive Radar Object Simulation for Validation IEEE Spectrum

This is a sponsored article brought to you by Rohde & Schwarz.
Homologation and validation of new vehicle models today require millions of test kilometers to be driven under different environmental conditions, on different types of roads in various countries around the world.
Due to the increased complexity of automated driving (AD) and
advanced driver-assistance systems (ADAS) functions, and new
developments in radar technology, testing efforts expand very
quickly. Just relying on road testing is no longer
practical.
The Rohde & Schwarz radar test system opens a completely new field of possibilities for testing radar-based ADAS and AD features to ensure correct operation in hardware-in-the-loop (HiL) and vehicle-in-the-loop (ViL) testbeds.
In addition, scenario testing of autonomous driving functions on the public roads can be dangerous, and under conditions that are not easily reproducible.
As a result, hardware-in-the-loop (HiL) and vehicle-in-the-loop (ViL) scenario testing of automotive radar is gaining importance.
Your challenges:
- End-to-end verification, validation, calibration or homologation of AD/ADAS functions at component and full-vehicle level
- Reproducing complex traffic scenarios, automotive radar object simulation over-the-air
- Ensuring the radar target generation test equipment is scalable and has the technical specifications to cover the increasing number of targets, and future complex scenarios
- Meeting the increased test-complexity requirements of ADAS target simulation while minimizing costs and accelerating time-to-market
RTS features:
- Automotive radar target simulator for driving scenario testing that can be easily defined and executed with the highest reproducibility
- Complex automotive radar object simulations including multiple sensors, over-the-air
- Increased accuracy and repeatability from fully-electronic antenna arrays
- Fully scalable, covering all use cases from R&D to production, easily upgradable to cover future requirements
01:12
Combined Review and Tutorial Around the RUT-240 SoylentNews
Routing 4G cellular data to a BSD network using bridge mode on the RUT-240:
The RUT-240 from Teltonika networks is a small and fairly inexpensive 4G router which is commonly used to provide internet connectivity for remote devices that are either in locations without regular fixed-line broadband, or where high availability is required. Think smart meters, monitoring systems, and so on.
In the case of high availability, the RUT-240 is connected in line with a conventional internet router, and it's own cellular connection is only used when a lack of connectivity is detected. Both of these configurations often involve the use of a special SIM card, to which the cellular operator has provisioned a static, public IP address, thus allowing inbound connections to the connected remote devices, (as well as access to the router itself for configuration and admin purposes).
[...T]oday we're going to use our RUT-240 for a completely different purpose. No special SIM required, and we're not going to be travelling out in to the wilds either. Just a regular pre-paid SIM, and the normal office surroundings.
Instead, we'll be exploring the use of this router as a backup connection for an existing OpenBSD-based router, or even - within limits - as a replacement for fixed line broadband. This latter option might make sense on a short term basis in a new office that hasn't been fully connected yet, or in a temporary office in an awkward location where DSL or fibre isn't available. Attending a conference, but all the decent hotels are fully booked? Stuck on a boat in dry dock? Not a problem!
Read more of this story at SoylentNews.
00:46
Whole Foods Closes Flagship San Francisco Store Due To Employee Safety Concerns cryptogon.com
Via: ZeroHedge: Its yet another story of a major company leaving a U.S. city: this time, its a Whole Foods in San Francisco that is closing after barely being open for a year. The location in question is a 64,000 flagship Whole Foods store that you just know the company wouldnt be closing down unless []
00:37
Uranus: Diamond Rain, Bright Rings Centauri Dreams Imagining and Planning Interstellar Exploration
Thinking about the ice giants, as I have been doing recently in our look at fast mission concepts, reminds me of the diamond rain notion that has grown out of research into experiments with the temperatures and pressures found inside worlds like Uranus and Neptune. The concept isnt new, but I noted some months ago that scientists at the Department of Energys SLAC National Accelerator Laboratory had been studying diamond formation in such worlds in the presence of oxygen. Oxygen, it turns out, makes it more likely that diamonds form that may grow to extreme sizes.
So let me turn back the clock for a moment to last fall, when news emerged about this exotic precipitation indicating that it may be more common than we had thought. Using a material called PET (polyethylene terephthalate), the SLAC researchers created shock waves within the material and analyzed the result with X-ray pulses. The scientists used PET because of its balance between carbon, hydrogen and oxygen, components more closely mimicking the chemical composition of Neptune and Uranus.
While earlier experiments had used a plastic material made from hydrogen and carbon, the addition of oxygen made the formation of diamonds more likely, and apparently allowed them to grow at lower temperatures and pressures than previously thought possible. The team, led by Dominik Kraus (SLAC/University of Rostock), suggests that such diamonds under actual ice giant conditions might reach millions of carats in weight, forming a layer around the planetary core. Silvia Pandolfi, a SLAC scientist involved in this work, was quoted in a SLAC news release last September:
We know that Earths core is predominantly made of iron, but many experiments are still investigating how the presence of lighter elements can change the conditions of melting and phase transitions. Our experiment demonstrates how these elements can change the conditions in which diamonds are forming on ice giants. If we want to accurately model planets, then we need to get as close as we can to the actual composition of the planetary interior.

Image: Studying a material that even more closely resembles the composition of ice giants, researchers found that oxygen boost...
00:22
Mexico Battles U.S. Government and Mr. Monsanto to Protect Food Sovereignty cryptogon.com
Via: The Last American Vagabond: Despite legal threats from the U.S. government, Mexicos government plans to go forward with a partial ban on imports of genetically modified corn. On Wednesday Mexicos National Council for Science and Technology (CONACYT) hosted an online webinar laying out the science behind the nations decision to ban imports of Genetically []
00:20
CVE-2023-30465: Apache InLong: SQL injection in apache inLong 1.5.0 Open Source Security
Posted by Charles Zhang on Apr 11
Severity: importantDescription:
Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection') vulnerability in Apache Software
Foundation Apache InLong.This issue affects Apache InLong: from 1.4.0 through 1.5.0. By manipulating the "orderType"
parameter and the ordering of the returned content using an SQL injection attack, an attacker can extract the username
of the user with ID 1 from the...
00:16
A draft Rust trademark policy LWN.net
A draft updated trademark policy for the Rust language is being circulated for comments. It is not a short read.
RS can be used freely and without permission to indicate that software or a project is derived from or based on Rust, compatible with Rust, inspired by Rust, or can be used for the same purpose as Rust. We recommend using RS instead of Rust if you have any concerns about your use falling outside of this policy, for example, naming your crate foo-rs instead of rust-foo.
Some discussion can be found in this Reddit post.
Update: there has since been a followup note posted on the process being followed in the creation and consideration of this draft policy.
We want to thank the community for participating in this process, and for your patience as we learn the best way to navigate it. We recognize that the process and communication around it could have been better. Notably, the wider project was insufficiently included in the process. We were responsible for that and apologize.
00:16
Yum! Brands, the owner of KFC, Taco Bell and Pizza Hut, discloses data breach Security Affairs
Yum! Brands, the company that owns the KFC, Pizza Hut, and Taco Bell brands, disclosed a data breach after the January ransomware attack.
On January 13, 2023, Yum! Brands suffered a cyberattack that forced the company to take its systems offline closing roughly 300 restaurants in the UK for one day.
Now the company, which owns the KFC, Pizza Hut, and Taco Bell brands, disclosed a data breach and revealed that ransomware actors have stolen personally identifiable information (PII) of an unspecified number of individuals.
The data breach notification letter sent to potentially impacted individuals states that personal information was exposed, including names, drivers license numbers, Non-Driver Identification Card Number, and other types of personal identifiers.
Yum! Brands pointed out that they have no evidence of identity theft or fraud involving exposed data.
As we announced publicly in mid-January, Yum! experienced a cybersecurity incident involving unauthorized access to certain of our systems on or around January 13, 2023. Upon discovery, we took steps to lock down impacted systems, notified federal law enforcement authorities, worked with leading digital forensics and restoration teams to investigate and recover from the incident, and deployed enhanced 24/7 detection and monitoring technology. reads the data breach notification letter. Our review determined that the exposed files contained some of your personal information.
The company investigated the security breach with the help of third-party cybersecurity experts, to identify the scope of the incident.
At this time, Yum! Brands has yet to determine the exact number of impacted individuals.
The company is also providing complimentary credit monitoring and identity protection services for two years via IDX.
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections:
- The Teacher Most Educational Blog
- The Entertainer Most Entertaining Blog
- The Tech Whizz Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please nominate Security Affairs as your favorite blog.
Nominate here: ...
00:15
Estonian Arrested: Accused of Supplying Hacking Tools to Russia HackRead | Latest Cybersecurity and Hacking News Site
Shevlyakov obtained delicate electronic equipment from American manufacturers for the use of Russian end-users, such as defence contractors and other government agencies
This is a post from HackRead.com Read the original post: Estonian Arrested: Accused of Supplying Hacking Tools to Russia
00:12
Neil deGrasse Tyson Melts Down on The Highwire cryptogon.com
Its difficult to watch, but Tysons spectacular self immolation does produce warm, glowing schadenfreude. Via: Peak Prosperity: Related: Neil deGrasse Tyson on The Highwire
00:00
A Miniature MNT For Every Pocket Hackaday

Last time Hackaday went hands on with a product from German company MNT, it was the Reform laptop; a full size computer with a full feature set and fully open source design. Now theyre back with the same value proposition and feature set crammed into a much more adorable (and colorful!) package with the MNT Pocket Reform. If you want the big Reforms open source philosophy in a body fit for a coat pocket, this might be the computing device for you.
To refresh your memory, MNT is a company that specializes in open source hardware and the software to support it. They are probably best known for the Reform, their first laptop. Its marquis feature is a fully open design, from the mechanical components (designed with OSS tools) to the PCBAs (designed with KiCad) to the software (designed with, uh, software). When originally shipped that product packed a DIMM-style System On Module (SOM) with a default configuration containing a quad core NXP i.MX8M Quad and 4GB of RAM, as well as mini PCIe Card and M key m.2 2280 slots on the motherboard for storage and connectivity. That computer was designed to be easily serviceable and included a plethora of full sized ports along with easy to source cylindrical battery cells. The Pocket Reform takes the same intent and channels it into a much smaller package.
Speeds and Feeds
Tuesday, 11 April
23:55
BigIDs data minimization capabilities enable organizations to identify duplicate data Help Net Security
BigID launched ML-powered solution for finding duplicate and similar data content. The innovative technology uses AI to locate both similar and duplicate data on any data set, enabling organizations to identify duplicate data as well as redundant, obsolete, or trivial (ROT) data. These transformative capabilities mean that organizations can reduce their storage cost, accelerate compliance, and improve cybersecurity across their environment. Duplicate and redundant data are a treasure trove for cybercriminals exponentially increasing the More
The post BigIDs data minimization capabilities enable organizations to identify duplicate data appeared first on Help Net Security.
23:54
Beware of companies offering paid sextortion assistance Help Net Security
Sextortion victims are already in a vulnerable position, and shady companies are taking advantage of this vulnerability to offer sextortion assistance services for huge sums services that they may be unable to render or that wont help the victims in any way. The rise of the sextortion assistance scam In December, 2022, the FBI warned about the increasing number of sextortion attacks against children and teens. Over 7,000 cases of online financial sextortion of More
The post Beware of companies offering paid sextortion assistance appeared first on Help Net Security.
23:51
And Now Gavin Newsom Might Run for President [???] cryptogon.com
Mmm hmm. Via: Fox:
23:41
Security updates for Tuesday LWN.net
Security updates have been issued by Debian (keepalived and lldpd), Oracle (kernel), and SUSE (kernel, podman, seamonkey, and upx).
23:25
ThreatX Runtime API & Application Protection goes beyond basic observability Help Net Security
ThreatX has unveiled ThreatX Runtime API & Application Protection (RAAP). This patent-pending capability goes beyond basic observability to extend threat detection, tracking and blocking to customers runtime environments, without slowing developers or requiring expertise in cloud-native applications. As organizations transition apps and workloads to the cloud, often across multi-cloud environments, attackers seek new ways to access sensitive data. While the Log4Shell vulnerability served as a wake-up call to runtime threats, shoring up these gaps is More
The post ThreatX Runtime API & Application Protection goes beyond basic observability appeared first on Help Net Security.
23:22
Could this folding buggy be destined for Chinas future lunar base? Lifeboat News: The Blog
The Cubic Emergency Lunar Vehicle of China can be folded and tucked into the back of a regular roving vehicle and when in use can travel up to 10km/h on the moons surface, say researchers.
23:01
How to upgrade Red Hat Ansible Automation Platform Linux.com
Consider the variables when planning and executing your AAP or Tower upgrade and learn what makes sense for your scenario.
Read More at Enable Sysadmin
The post How to upgrade Red Hat Ansible Automation Platform appeared first on Linux.com.
23:00
Newly Discovered "By-Design" Flaw in Microsoft Azure Could Expose Storage Accounts to Hackers The Hacker News
A "by-design flaw" uncovered in Microsoft Azure could be exploited by attackers to gain access to storage accounts, move laterally in the environment, and even execute remote code. "It is possible to abuse and leverage Microsoft Storage Accounts by manipulating Azure Functions to steal access-tokens of higher privilege identities, move laterally, potentially access critical business assets, and
22:50
Syxsense platform updates simplify endpoint security and management Help Net Security
Syxsense has released new updates to the Syxsense product suite designed to extend automated workflow capabilities, improve usability, and enhance overall platform security. Key to this release is the introduction of Cortex Sequences, which uses the power of automation to chain together workflows or playbooks, further enabling Syxsense customers to have intelligent endpoints that can simplify endpoint security and management. With todays complex digital infrastructure and cybersecurity landscape, organizations are increasingly relying on automation to More
The post Syxsense platform updates simplify endpoint security and management appeared first on Help Net Security.
22:42
CVE-2017-11164 - stack exhaustion in PCRE Open Source Security
Posted by Sevan Janiyan on Apr 11
Hi,CVE-2017-11164 landed some years back[1] for PCRE 8.x and is marked
up with a high base score on the article[2], yet no fix was ever listed
and is still commonly packaged, so I asked Philip Hazel (the PCRE
maintainer) regarding the issue, and this is what Philip said
"Stack exhaustion is a FEP (frequently encountered problem) in PCRE1
(the 8.xx series). There are various limiting options that the user can
apply to limit stack usage....
22:30
Intel Back To Working On Key Locker For Linux After Tackling Big Performance Issue Phoronix
Going back to 2020 Intel's open-source engineers have been working on Key Locker support for Linux for that hardware feature introduced with Tigerlake CPUs. The Key Locker Linux support has been worked on now for nearly three years and finally after a significant performance issue now being addressed with forthcoming firmware...
22:29
Cybercriminals Turn to Android Loaders on Dark Web to Evade Google Play Security The Hacker News
Malicious loader programs capable of trojanizing Android applications are being traded on the criminal underground for up to $20,000 as a way to evade Google Play Store defenses. "The most popular application categories to hide malware and unwanted software include cryptocurrency trackers, financial apps, QR-code scanners, and even dating apps," Kaspersky said in a new report based on messages
22:23
Now We Know How a Solar Storm Took Out a Fleet of Starlinks SoylentNews
Now We Know How a Solar Storm Took Out a Fleet of Starlinks:
On March 23rd, sky observers marvelled at a gorgeous display of northern and southern lights. It was reminder that when our Sun gets active, it can spark a phenomenon called "space weather." Aurorae are among the most benign effects of this phenomenon.
At the other end of the space weather spectrum are solar storms that can knock out satellites. The folks at Starlink found that out the hard way in February 2022. On January 29th that year, the Sun belched out a class M 1.1 flare and related coronal mass ejection. Material from the Sun traveled out on the solar wind and arrived at Earth a few days later. On February 3, Starlink launched a group of 49 satellites to an altitude only 130 miles above Earth's surface. They didn't last long, and now solar physicists know why.
A group of researchers from NASA Goddard Space Flight Center and the Catholic University of America took a closer look at the specifics of that storm. Their analysis identified a mass of plasma that impacted our planet's magnetosphere. The actual event was a halo coronal mass ejection from an active region in the northeast quadrant of the Sun.
The material traveled out at around 690 kilometers per second as a shock-driving magnetic cloud. Think of it as a long ropy mass of material writhing its way through space. As it traveled, it expanded and at solar-facing satellitesincluding STEREO-A, which took a direct hit from itmade observations. Eventually, the cloud smacked into Earth's magnetosphere creating a geomagnetic storm.
One of the side effects of space weather that can affect satellites is warming in a region called the "thermosphere". That increased the density of the upper atmosphere over a short amount of time and caused it to swell up. A denser atmosphere causes a phenomenon called "atmospheric drag". Essentially, the thicker atmosphere slows down anything moving through. It also heats things up.
Read more of this story at SoylentNews.
22:05
Links 11/04/2023: GNU Parted 3.6 and More Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Instructionals/Technical
-
21:42
[eBook] A Step-by-Step Guide to Cyber Risk Assessment The Hacker News
In today's perilous cyber risk landscape, CISOs and CIOs must defend their organizations against relentless cyber threats, including ransomware, phishing, attacks on infrastructure, supply chain breaches, malicious insiders, and much more. Yet at the same time, security leaders are also under tremendous pressure to reduce costs and invest wisely. One of the most effective ways for CISOs and
21:00
IBM Selectric Typewriters Finally Get DIY Typeballs Hackaday

IBMs Selectric line of typewriters were quite popular in the 1960s, thanks in part to an innovation called the typeball which allowed for easy font changes on a single machine. Unfortunately, as if often the case when specialized components are involved, its an idea that hasnt aged particularly well. The Selectric typewriters are now around 60 years old and since IBM isnt making replacement parts, those restoring these machines have had to get somewhat creative like using a 3D printer to build new typeballs.
21:00
AMD Phoenix Support Progressing For Coreboot, New Google Chromebook Added Phoronix
AMD and their partners continue working on bringing up Coreboot for the Ryzen Mobile 7040 Series "Phoenix" support for those very interesting forthcoming mobile processors with Zen 4 CPU cores and RDNA3 graphics...
20:49
Russia Launches Anti-VPN Scare Campaign to Support Its VPN Blocking TorrentFreak
 VPN providers with any infrastructure in Russia have
experienced problems for years.
VPN providers with any infrastructure in Russia have
experienced problems for years.
Todays bottom line for anonymizing privacy services is that they must comply with Russias site-blocking demands and open up themselves up to scrutiny. Since the alternative is to break the law and face the consequences, many providers have pulled out of Russia completely.
In the wake of Russias invasion of Ukraine in February 2022, telecoms watchdog Rozkomnadzor stepped up its campaign against search engines. Demands to delist hundreds of thousands of VPN-related URLs from search results run alongside questionable requests to remove other content.
Despite renewed crackdowns on VPNs and Tor, it seems likely that Russia understands that short of blocking everything, blocking every VPN service and thousands of apps that constantly surface is impossible. As such, other methods are being explored.
Anti-VPN Scare Campaign
Public Service Announcements (PSA) have been deployed to nudge citizens in the right direction on genuine issues of public welfare for decades. Theyre also used to direct behavior in a way that benefits governments and corporations while making it appear that the interests of citizens are paramount.
Currently being spread via social media, the general premise of Russias anti-VPN campaign is that since no VPN service can be trusted with users private data, using a VPN is worse for privacy than not using a VPN at all.
The campaign is the work of ROCIT, which describes itself as a public organization that unites active Internet users in Russia. Funded by the Ministry of Digital Development, Communications and Mass Media (Minkomsvyaz), ROCIT issues advice on piracy, net neutrality and other internet-related issues, in line with government policy.
Campaign Videos
PSA 1: Your Data Can Be Leaked Online Due to VPN
ROCIT advice: VPN services accumulate a huge amount of personal data, including information about bank cards and perso...
20:37
Apple released emergency updates to fix recently disclosed zero-day bugs on older devices Security Affairs
Apple released updates to backport patches addressing two actively exploited zero-day vulnerabilities in older iPhones, iPads, and Macs.
Apple has released emergency updates to backport security patches that address two actively exploited zero-day flaws also affecting older iPhones, iPads, and Macs.
On April 7, 2023, Apple has released emergency security updates to address two actively exploited zero-day vulnerabilities, tracked as CVE-2023-28205 and CVE-2023-28206, impacting iPhones, Macs, and iPads.
Impacted devices include:
- iPhone 8 and later,
- iPad Pro (all models),
- iPad Air 3rd generation and later,
- iPad 5th generation and later,
- iPad mini 5th generation and later,
- and Macs running macOS Ventura.
The zero-day CVE-2023-28205 is a use after free issue that resides in the WebKit, its exploitation may lead to arbitrary code execution. An attacker can trigger the flaw by tricking the victims into loading maliciously crafted web pages. The IT giant addressed the flaw with improved memory management.
The zero-day CVE-2023-28206 is an out-of-bounds write issue that resides in the IOSurfaceAccelerator. The company addressed the flaw with improved input validation.
Apple addressed the zero-day issue with the release of macOS Ventura 13.3.1, iOS 16.4.1, iPadOS 16.4.1, and Safari 16.4.1.
Both vulnerabilities were reported by Clment Lecigne of Googles Threat Analysis Group and Donncha Cearbhaill of Amnesty Internationals Security Lab.
On April 10, 2023, US Cybersecurity and Infrastructure Security Agency (CISA) added the two vulnerabilities to its Known Exploited Vulnerabilities catalog.
Today, Apple extended the security updates to the following devices with the release of iOS 15.7.5 and iPadOS 15.7.5, macOS Monterey 12.6.5, and macOS Big Sur 11.7.6:
- iPhone 6s (all models),
- iPhone 7 (all models),
- iPhone SE (1st generation),
- iPad Air 2,
- iPad mini (4th generation),
- iPod touch (7th generation),
- and Macs running macOS Monterey and Big Sur.
Please vote for Security Affairs (...
20:20
Lucky 13? AMD Pensando Elba SoC Linux Enablement Revised The 13th Time Phoronix
For more than one year and now up to thirteen rounds of patch review, the AMD Pensando Elba SoC support continues in its trek toward the mainline Linux kernel...
20:02
CentOS Reminds Everyone End-Of-Life Is Coming For CentOS Linux 7, CentOS Stream 8 Phoronix
The CentOS Project has sent out a reminder of end-of-life dates for CentOS Linux 7 and CentOS Stream 8...
19:43
FreeBSD 13.2 Released With WireGuard Driver, ASLR By Default For 64-bit Executables Phoronix
Following some minor delays due to additional release candidates, FreeBSD 13.2-RELEASE is now officially available as this latest FreeBSD operating system update ahead of FreeBSD 14.0 debuting this summer...
19:42
Apple rushes fixes for exploited zero-days in iPhones and Macs (CVE-2023-28205, CVE-2023-28206) Help Net Security
Apple has pushed out security updates that fix two actively exploited zero-day vulnerabilities (CVE-2023-28205, CVE-2023-28206) in macOS, iOS and iPadOS. Reported by researchers Clment Lecigne of Googles Threat Analysis Group (TAG) and Donncha Cearbhaill, the head of Amnesty Internationals Security Lab, the vulnerabilities have been exploited in tandem to achieve full device compromise with the likely (though not confirmed) goal to install spyware on target devices. About the vulnerabilities CVE-2023-28205 is a use More
The post Apple rushes fixes for exploited zero-days in iPhones and Macs (CVE-2023-28205, CVE-2023-28206) appeared first on Help Net Security.
19:34
No NGO Has Been Allowed to See Julian Assange Since Four Years Ago SoylentNews
Democracy Now has a brief interview with a representative from Reporters Without Borders (RSF) on their latest attempt to meet Julian Assange inside Belmarsh high-security prison in the UK. Despite being granted approval, the RSF secretary-general and executive director Christophe Deloire and the others with him were denied entry. No other non-governmental agency has been able to meet with Assange in the last four years either.
CHRISTOPHE DELOIRE: So, what happened is that in the past years we requested to be able to visit Julian in his jail. We got an approval recently, which was confirmed on March 21st with a number, an official number, for myself and my colleague, Rebecca Vincent, and we were invited to come to the prison.
And when we just arrived, the guy at the desk, when he saw my passport, he suddenly was very stressed, and that taking a paper on his office on his desk, and that read it, saying, "According to Article" I do not remember the number of the article, but according to this article, "you are not allowed to visit Julian Assange. This is a decision that has been made by the governor of the Belmarsh prison, based on intelligence that we had" I quote him "that you are journalists."
And it doesn't make sense at all, first, because, personally, I've been a journalist since 1996, and we were vetted, so it was never a mystery that I was a journalist, never a secret. Second, my colleague wasn't a journalist herself. And we came here not as journalists, but as representatives of an international NGO with a constitutive status in many international organizations. So it was really as Reporters Without Borders representatives, not as reporters covering the case. So, it doesn't make sense for this second reason. And there is a third reason for which it doesn't make sense, is that already two journalists, at least, have been able to visit him in jail in the past four years. So
Previously:
(2022) Biden
Faces Growing Pressure to Drop Charges Against Julian
Assange
(2022) Assange
Lawyers Sue CIA for Spying on Them
(2022) Julian
Assange's Extradition to the US Approved by UK Home
Secretary
(2021) Key
Witness in Assange Case Jailed in Iceland After Admitting to Lies
and Ongoing Crime Spree
(2019) Top
Assange Defense Account Suspended By Twitter
(2019)...
19:16
Cryptocurrency Stealer Malware Distributed via 13 NuGet Packages The Hacker News
Cybersecurity researchers have detailed the inner workings of the cryptocurrency stealer malware that was distributed via 13 malicious NuGet packages as part of a supply chain attack targeting .NET developers. The sophisticated typosquatting campaign, which was uncovered by JFrog late last month, impersonated legitimate packages to execute PowerShell code designed to retrieve a follow-on binary
18:38
BSD Release: FreeBSD 13.2 DistroWatch.com: News
Colin Percival has announced the release of FreeBSD 13.2, the that focuses on features, speed and stability: "The FreeBSD Release Engineering team is pleased to announce the availability of FreeBSD 13.2-RELEASE. This is the third release of the stable/13....
18:00
Retired Welding Robot Picks Up Side Hustle as CNC Router Hackaday

Who says you cant teach an old robot new tricks? Nobody, actually. That saying is about dogs. But it applies to robots too, at least judging by the way this late-90s industrial beast was put to use in a way it was never intended: as a giant CNC router.
The machine in question is an ABB IRB6400, a six-axis, floor-mounted industrial machine that had a long career welding at a Eurorail factory in Austria before [Brian Brocken] made its acquaintance. He procured the non-working machine no word on what he paid for it and moved the 2-ton paperweight into his shop, itself a non-trivial endeavor. After a good scrubbing, [Brian] tried to get the machine started up. An error prevented the robot controller from booting; luckily, theres a large community of ABB users, and [Brian] learned that one of the modules in the controller needed replacement.
After fixing that and swapping out the controllers long-dead backup batteries, plus replacing the original 1.44 MB floppy drive with a USB drive he was able to bring the machine back to life. Unfortunately, the limited amount of internal memory made it difficult to use for anything complicated, so [Brian] came up with...
17:49
A cyber attack hit the water controllers for irrigating fields in the Jordan Valley Security Affairs
A cyber attack paralyzed the water controllers for irrigating fields in the Jordan Valley that are operated by the Galil Sewage Corporation.
A cyberattack blocked several controllers for irrigating fields in the Jordan Valley. The systems operated by the Galil Sewage Corporation monitor the irrigation process and wastewater treatment in the Jordan Valley.
The company experts spent the entire day recovering the operations, at this time the source of the attack is still unclear.
The management for both major systems was pushing all of Sunday morning to work through the issue and bring the systems back into full operation. reported the Jerusalem Post.
Local authorities were aware of the risk of a cyberattack and informed farmers in the region. Some of the farmers disconnected their irrigation systems from the Internet and switched them to manual operation.
The National Cyber Organization warned of the risk of cyber attacks that anti-Israeli hackers can carry out against national infrastructure during the month of Ramadan.
During the last week, private and government organizations in Israel were hit by massive cyber attacks that were part of the #OPIsrael campaign launched by hacktivists against Israeli critical infrastructure.
In November 2022, Ariel Stern, a former Israeli Air Force captain, warned that the US and Israel are still unprepared to defeat a cyber attack against the water sector that could be orchestrated by enemy states like Iran.
Stern highlighted the dangers for providers of critical infrastructure and issued his warning following the ransomware attack that in august disrupted the IT operations of South Staffordshire Water, a UK company supplying drinking water to 1.6M consumers daily.
The intelligence officer pointed out that nations like Russia, Iran, North Korea, and China have the capabilities to hit the water sector with dramatic consequences.
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections:
- The Teacher Most Educational Blog
- The Entertainer Most...
17:01
IRC Proceedings: Monday, April 10, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-100423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-100423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-100423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-100423.gmi
Over HTTP:
|
... |
17:00
COVID Vaccine SheddingCanaries in the Mine Terra Forming Terra
We are getting various related effects that we do not expect and
whose biological pathways are obscure. They are at least rare
enough. Still seriously unwelcome to encounter.
The Shroud of Turin: Myth or Miracle? Terra Forming Terra

An Introduction to the Book of John Terra Forming Terra
16:53
Sirius Open Source: Secrets, NDAs, Bullying, and Threats schestowitz.com
Video
download link | md5sum
819584aa5aa6510b785e6a76e1fcbbf7
Sirius Victims Out the Woodwork
Creative Commons Attribution-No Derivative Works 4.0
Summary: Were learning or becoming informed of some more crimes of Sirius Open Source (a company we left over 4 months ago); the video above explains that the company or its boosters (maybe shills) resort to intimidation tactics and threats (familiar tactics), having not just lost key staff (including the CEO) but also found itself unable to recruit
NOW that people are speaking out about what the company did to them even a decade ago I thought Id mention a bunch of old stories about what the company did to staff, clients, and suppliers.
The company may not last much longer (maybe weeks or months), pension providers have resorted to stalling tactics and lies (covering their own behinds), but we need to properly explain what happened, more so after Bill Gates had passed some money to the CEO under an NDA.
Whether Sirius was sabotaged or simply sabotaged itself is something for historians to decide. NDAs make its exceptionally hard to figure out what really happened.
16:49
Sirius Open Source Unopened: History of Threatening People and Intimidating Critics Was Always a Bad Strategy Techrights
Video
download link | md5sum
819584aa5aa6510b785e6a76e1fcbbf7
Sirius Victims Out the Woodwork
Creative Commons Attribution-No Derivative Works 4.0
Summary: Were learning or becoming informed of some more crimes of Sirius Open Source (a company we left over 4 months ago); the video above explains that the company or its boosters (maybe shills) resort to intimidation tactics and threats (familiar tactics), having not just lost key staff (including the CEO) but also found itself unable to recruit
NOW that people are speaking out about what the company did to them even a decade ago I thought Id mention a bunch of old stories about what the company did to staff, clients, and suppliers.
Whether Sirius was sabotaged or simply sabotaged itself is something for historians to decide.The company may not last much longer (maybe weeks or months), pension providers have resorted to stalling tactics and lies (covering their own behinds), but we need to properly explain what happened, more so after Bill Gates had passed some money to the CEO under an NDA.
Whether Sirius was sabotaged or simply sabotaged itself is something for historians...
16:48
Inside the Bitter Campus Privacy Battle Over Smart Building Sensors SoylentNews
Inside the bitter campus privacy battle over smart building sensors:
"The initial step was to ... see how these things behave," says Herbsleb, comparing the Mites sensors to motion detectors that people might want to test out. "It's purely just, 'How well does it work as a motion detector?' And, you know, nobody's asked to consent. It's just trying out a piece of hardware."
Of course, the system's advanced capabilities meant that Mites were not just motion detectorsand other department members saw things differently. "It's a lot to ask of people to have a sensor with a microphone that is running in their office," says Jonathan Aldrich, a computer science professor, even if "I trust my coworkers as a general principle and I believe they deserve that trust." He adds, "Trusting someone to be a good colleague is not the same as giving them a key to your office or having them install something in your office that can record private things." Allowing someone else to control a microphone in your office, he says, is "very much like giving someone else a key."
As the debate built over the next year, it pitted students against their advisors and academic heroes as wellalthough many objected in private, fearing the consequences of speaking out against a well-funded, university-backed project.
In the video recording of the town hall obtained by MIT Technology Review, attendees asked how researchers planned to notify building occupants and visitors about data collection. Jessica Colnago, then a PhD student, was concerned about how the Mites' mere presence would affect studies she was conducting on privacy. "As a privacy researcher, I would feel morally obligated to tell my participant about the technology in the room," she said in the meeting. While "we are all colleagues here" and "trust each other," she added, "outside participants might not."
Read more of this story at SoylentNews.
15:13
[Meme] More Money in McDonalds Than in Sirius Open Source Techrights
Sirius managers could not even get their grammar right. Sometimes they did not even pay the salary!
Summary: In 2023 Sirius Open Source wishes to pay GNU/Linux engineers as little as 20,000 pounds a year for an overnight job, including weekends and holidays, while secretly robbing them some more (and comparing them to monkeys); for comparisons sake, a McDonalds salary for Assistant Manager in the UK (daytime only, holidays taken off work) is higher than this. Remember that the company bags millions of pounds from public sector clients (taxpayers money) while bagging secret money from a corrupt oligarch under an NDA.
15:00
Your Multimeter Might Be Lying To You Hackaday

Multimeters are indispensable tools when working on electronics. Its almost impossible to build any but the most basic of circuits without one to test and troubleshoot potential issues, and they make possible a large array of measurement capabilities that are not easily performed otherwise. But when things start getting a little more complex its important to know their limitations, specifically around what they will tell you about circuits designed for high frequency. [watersstanton] explains in this video while troubleshooting an antenna circuit for ham radio.
The issue that often confuses people new to radio or other high-frequency projects revolves around the continuity testing function found on most multimeters. While useful for testing wiring and making sure connections are solid, they typically only test using DC. When applying AC to the same circuits, inductors start to offer higher impedance and capacitors lower impedance, up to the point that they become open and short circuits respectively. The same happens to transformers, but can also most antennas which often look like short circuits to ground at DC but can offer just enough impedance at their designed frequency to efficiently resonate and send out radio waves.
This can give some confusing readings, such as when testing...
15:00
Why its time to move towards a passwordless future Help Net Security
Adversaries dont need to use sophisticated methods to gain access to enterprise systems or to deploy ransomware they can just buy or steal credentials and log in. By burdening users with the near-impossible task of maintaining secure passwords, businesses ultimately give people a huge and unfair level of responsibility for security. As a result, many organizations are relying on what amounts to a roll of the dice to protect themselves and their customers from More
The post Why its time to move towards a passwordless future appeared first on Help Net Security.
14:46
On the Client Side, Linux Has Become Market Majority Techrights
Video download link |
md5sum b63a0c2d67b877a3efe281a8e187a103
GNU and Linux Rising
Creative Commons Attribution-No Derivative Works 4.0
Summary: If one counts Android as Linux, then its probably fair to say that nowadays most people already use Linux on the client side (the server side has been prominently GNU/Linux for a very long time) and if one counts Chrome OS as GNU/Linux (technically it is), then it seems reasonable to expect 10% market share by years end or some time next year
HOURS AGO we said that Windows Market Share is down From 80% to 26% in a Single Decade and nowadays Microsoft does not know how to stop this trend. Microsoft is the boy who cried "http://techrights.org/2023/04/02/saying-no-to-fentanylware/" title="Why Techrights Condones Fentanylware (TikTok) Ban and Suggests Extending Bans to Supposedly Good Fentanyl">FOMO tactics).
Android and Chrome OS are not freedom and weeks ago Richard Stallman told me that focusing on the need to replace Microsoft will (in his experience) lead to more people adopting Apple instead of GNU/Linux.The video above contains commentary about recent events/developments before discussing the growth of GNU/Linux, based on new data (for this month). At this point in time it makes sense to talk about Software Freedom, not just GNU/Linux. Android and Chrome OS are not freedom and weeks ago Richard Stallman told me that focusing on the need to replace Microsoft will (in his experience) lead to more people adopting Apple instead of GNU/Linux. While its true that Apple has serious issues right now (layoffs and sales slump), it does seem like some losses for Windows result in (or mean) gains for Apple. So lets focus on Software Freedom (the concept), not just brands.
14:30
Making risk-based decisions in a rapidly changing cyber climate Help Net Security
Nicole Darden Ford is Global VP & CISO at Rockwell Automation. As the companys cybersecurity leader, Nicole is entrusted to protect enterprise IT assets with scalable, future-ready platforms that enable the business. In addition to building cybersecurity programs for organizations across industries, including manufacturing, healthcare, and legal, Nicole has helped position two enterprises for IPOs. In this Help Net Security interview, Nicole reveals the three key indicators she uses to assess an industrial organizations cybersecurity More
The post Making risk-based decisions in a rapidly changing cyber climate appeared first on Help Net Security.
14:29
Running Techrights in 2023 Techrights
Summary: Weve evolved a lot this year; in 2022 I left my job at Sirius Open Source (turned out they had stolen money from me and from others) and as a result weve had a lot more capacity to expand and grow in reach
Just over a year ago I moved to another space in order to get my activism/reporting done. The photograph above is from the end of March in 2022 (compare to 2021), so a lot has changed (for the better) since then. Yesterday I made a lot of significant changes, including the addition of 3 large speakers Ive has since the early 1990s (they all still work; the same is true for my radio/alarm/clock) and today, after Easter, we resume as normal. We have much better tools, custom-made programs, to help us keep on top of news and to run all the services 24/7. A lot of the screens shown above are used for monitoring and communication.
We have much better tools,
custom-made programs, to help us keep on top of news and to run all
the services 24/7.Aside from that, yesterday we moved the
Gemini server, which is basically a Raspberry Pi that doubles up as a Web proxy and various
other things*. It used
to be on top of a shelf, but now its in the living room,
connected over Ethernet to a fibre-optic router, installed here
just over 2 months ago. We continue to make improvements to the
site, to the capsule, to IRC, IPFS and so on. We push as many of
these changes as possible/sensible to Git for transparencys sake (and
sharing).
____
* This month weve served over
120,000 Gemini pages in 10 days and about 30,000 Gemini pages
as HTML (over our own proxy). Gemini is strategic to us. We hope it
is the future.
14:00
How to transform cybersecurity learning and make content more engaging Help Net Security
While applications like Slack and Teams have transformed how we collaborate and communicate, cybersecurity training has not kept pace with these advancements. Most security training is still being delivered through web-based learning management systems, according to CybSafe. Often, important security information gets lost in the noise. Only half of the workers interviewed paid attention to emailed content. Furthermore, 20% of employees said they could not remember or find relevant cybersecurity information. In this Help Net More
The post How to transform cybersecurity learning and make content more engaging appeared first on Help Net Security.
13:38
Google is Dead, Say Microsoft Pundits, But Despite the Chatbot and Hype (and Amid Bing Layoffs) Bing Share Falls From 3.6% to 2.6% in a Matter of 6 Months Techrights
Summary: Over the past few months Microsoft-sponsored media kept saying that Google was doomed because of some chaffbot (smokescreen, vapourware or chaff amid Microsoft layoffs, including many in Bing), but judging by the actual data Bing is down from 3.6% to 2.6% (it lost about 30% of its relative share in only 6 months)
13:30
Criminal businesses adopt corporate behavior as they grow Help Net Security
As criminal groups increase in size, they adopt corporate-like behavior, but this shift brings about its own set of challenges and costs, according to Trend Micro. The criminal underground is rapidly professionalizing with groups beginning to mimic legitimate businesses that grow in complexity as their membership and revenue increases. However, larger cybercrime organizations can be harder to manage and have more office politics, poor performers, and trust issues. This report highlights to investigators the More
The post Criminal businesses adopt corporate behavior as they grow appeared first on Help Net Security.
13:23
A widow is accusing an AI chatbot of being a reason her husband killed himself Lifeboat News: The Blog
A chatbot supposedly encouraged someone to kill himself. And he did.
The company behind the Eliza chatbot says its put a new safety feature in place after hearing about this sad case.
13:23
Tesla is about to launch a big new software update with new features and UI upgrades Lifeboat News: The Blog
Tesla is about to launch a big new software update that includes a few new features and a lot of user interface upgrades.
As a Tesla owner, its always a good day to get a notification that a new software update is available. You start wondering what new features or improvements you are getting that day.
Well, now we have a good preview of the next Tesla software update as Teslascope (a service that tracks Tesla software updates) found out about a new update that the automaker is pushing to employee vehicles, which generally means it will be coming soon to the customer fleet as well.
13:22
Homologous pairing in short double-stranded DNA-grafted colloidal microspheres Lifeboat News: The Blog
Homologous pairing (HP), i.e., the pairing of similar or identical double-stranded DNA, is an insufficiently understood fundamental biological process. HP is now understood to also occur without protein mediation, but crucial mechanistic details remain poorly established. Unfortunately, systematic studies of sequence dependence are not practical due to the enormous number of nucleotide permutations and multiple possible conformations involved in existing biophysical strategies even when using as few as 150 basepairs. Here, we show that HP can occur in DNA as short as 18 basepairs in a colloidal microparticle-based system. Exemplary systematic studies include resolving opposing reports of the impact of % AT composition, validating the impact of nucleotide order and triplet framework and revealing isotropic bendability to be crucial for HP. These studies are enabled by statistical analysis of crystal size and fraction within coexisting fluid-crystal phases of double-stranded DNA-grafted colloidal microspheres, where crystallization is predicated by HP.
13:00
Consumers take data control into their own hands amid rising privacy concerns Help Net Security
Data Subject Requests (DSRs), which are formal requests made by individuals to access, modify, or delete their personal data held by a company, increased by 72% from 2021 to 2022. The increase was primarily driven by deletion and access requests, according to DataGrail. In fact, the number of deletion requests more than doubled while access requests grew fivefold. These numbers will continue to increase as new data privacy laws, like those in Virginia and Colorado, More
The post Consumers take data control into their own hands amid rising privacy concerns appeared first on Help Net Security.
12:05
Scientists Create an Eco-friendly Paint That Mimics Nature SoylentNews
An energy-saving coating needs no pigments, and it keeps the surface beneath it 30 degrees cooler:
Color surrounds us in nature, and we re-create it with pigments. You can think of pigments as pulverized minerals, heavy metals, or chemicals that we swish into oil and spread over a canvas or car: Cobalt becomes blue; ochre red; cadmium yellow. "But nature has a very different way of creating color than we do," Chanda says. Some of nature's most vivid looksthe kind worn by peacocks, beetles, and butterfliesdo their thing without pigment.
Those colors come from topography. Submicroscopic landscapes on the outer surfaces of peacock feathers, beetle shells, and butterfly wings diffract light to produce what's known as structural color. It's longer-lasting and pigment-free. And to scientists, it's the key to creating paint that is not only better for the planet but might also help us live in a hotter world.
In a paper published this month in Science Advances, Chanda's lab demonstrated a first-of-its-kind paint based on structural color. They think it's the lightest paint in the worldand they mean that both in terms of weight and temperature. The paint consists of tiny aluminum flakes dotted with even tinier aluminum nanoparticles. A raisin's worth of the stuff could cover both the front and back of a door. It's lightweight enough to potentially cut fuel usage in planes and cars that are coated with it. It doesn't trap heat from sunlight like pigments do, and its constituents are less toxic than paints made with heavy metals like cadmium and cobalt.
Read more of this story at SoylentNews.
12:00
The Hello World of GPT? Hackaday

Someone wants to learn about Arduino programming. Do you suggest they blink an LED first? Or should they go straight for a 3D laser scanner with galvos, a time-of-flight sensor, and multiple networking options? Most of us need to start with the blinking light and move forward from there. So what if you want to learn about the latest wave of GPT generative pre-trained transformer programs? Do you start with a language model that looks at thousands of possible tokens in large contexts? Or should you start with something simple? We think you should start simple, and [Andrej Karpathy] agrees. He has a workbook that makes a tiny GPT that can predict the next bit in a sequence. It isnt any more practical than a blinking LED, but it is a manageable place to start.
The simple example starts with a vocabulary of two. In other words, characters are 1 or 0. It also uses a context size of 3, so it will look at 3 bits and use that to infer the 4th bit. To further simplify things, the examples assume you will always get a fixed-size sequence of tokens, in this case, eight tokens. Then it builds a little from there.
The notebook uses PyTorch to create a GPT, but since you dont need to understand those details, the code is all collapsed. You can, of course, expand it and see it, but at first, you should probably just assume it works and continue the exercise. You do need to run each block of code in sequence, even if it i...
11:30
Links 10/04/2023: OpenBSD 7.3 and 4MLinux 42 Techrights
![]()
Contents
-
GNU/Linux
-
Desktop/Laptop
-
Liliputing PlanetPC XR mini PC dramatically fails to meet crowdfunding goals (Linux PC with ARM-based processor and integrated touch panel) Liliputing
The PlanetPC XR Series is a compact desktop computer with an ARM-based processor, Ubuntu Linux software, plenty of ports and storage options. Theres also an unusual touch panel on the front that can be used to control some of the PCs functions or display information.
Theres just one catch: it...
-
-
11:29
SoftwareQinc/staq: A full-stack quantum processing toolkit Lifeboat News: The Blog
A full-stack quantum processing toolkit. Contribute to softwareQinc/staq development by creating an account on GitHub.
11:29
What Is The Price of a Quantum Computer In 2023? Lifeboat News: The Blog
Many experts in the industry predict the cost of quantum computing hardware will continue to decrease over time as the technology advances, making it more accessible to a broader range of businesses and organizations. In a recent talk, the CTO of the CIA Nand Mulchandani noted that the quantum industry is still very early and unit costs are still very high, as we are very much in the research and development stage.
In general, pricing concerns are sure to be influenced by several important factors, including how advanced discoveries in the sector are made, market demand for the technology and competition among quantum computing providers.
The Quantum Insider observes with a keen eye the market trends and technological narrative that is evolving as we speak. When thinking about the price of a quantum computer price in 2023, its worth considering the access method, the type of computer and usage requirements.
11:25
Connecting Brains: The BrainNet VPRO documentary Lifeboat News: The Blog

Can we connect human brains together? What are the limits of
what we can do with our brain? Is BrainNet our future?
In science fiction movies, scientists brains are downloaded into
computers and criminal brains are connected to the Internet.
Interesting, but how does it work in real life?
Original title: The greedy brain.
Scientific journalist Rob van Hattum wondered what information we
can truly get from our brain and came across an extraordinary
scientific experience.
An experiment where the brains of two rats were directly connected:
one rat was in the United States and the other rat was in Brazil.
They could influence the brain of the other directly. Miguel
Nicolelis is the Brazilian neurologist who conducted this
experiment. In his book Beyond Boundaries he describes his special
experiences in detail and predicts that it should be possible to
create a kind of BrainNet.
For Backlight, Rob van Hattum went to Sao Paulo and also visited
all Dutch neuroscientists, looking for what the future holds for
our brain. He connected his own brain to computers and let it
completely be scanned, searching for the limits of reading out the
brain.
Originally broadcasted by VPRO in 2014.
VPRO Backlight July 2014
On VPRO broadcast you will find nonfiction videos with English
subtitles, French subtitles and Spanish subtitles, such as
documentaries, short interviews and documentary series.
VPRO Documentary publishes one new subtitled documentary about
current affairs, finance, sustainability, climate change or
politics every week. We research subjects like politics, world
economy, society and science with experts and try to grasp the
essence of prominent trends and developments.
Visit additional youtube channels bij VPRO broadcast:
VPRO Broadcast, all international VPRO programs: https://www.youtube.com/VPRObroadcast.
VPRO DOK, German only documentaries: https://www.youtube.com/channel/UCBi0VEPANmiT5zOoGvCi8Sg.
VPRO Metropolis, remarkable stories from all over the world:
https://www.youtube.com/user/VPROmetropolis.
VPRO World Stories, the travel series of VPRO: https://www.youtube.com/VPROworldstories.
VPRO Extra, additional footage and one offs:...
11:25
Toward understanding the communication in sperm whales Lifeboat News: The Blog
The recent success of machine learning (ML) methods in answering similar questions in human languages (Natural Language Processing or NLP) is related to the availability of large-scale datasets. The effort of creating a biological dataset in a format, level of detail, scale, and time span amenable to ML-based analysis is capital intensive and necessitates a multidisciplinary expertise to develop, deploy, and maintain specialized hardware to collect acoustic and behavioral signals, as well as software to process and analyze them, develop linguistic models that reveal the structure of animal communication and ground it in behavior, and finally perform playback experiments to attempt bidirectional communication for validation ( Figure 1 ). Yet, the deployment of graphics processing units (GPU) is following a trajectory akin to Moores Law ( https://openai.com/blog/ai-and-compute) and, at the same time, the success of such an endeavor could potentially yield cross-applications and advancements in broader communities investigating non-human communication and animal behavioral research. One of the main drivers of progress making deep learning successful has been the availability of large (both labeled and unlabeled) datasets (and of architectures capable of taking advantage of such large data). To build a more complete picture and capture the full range of a species behavior, collecting datasets containing measurements across a broad set of factors is essential. In turn, setting up infrastructure that allows for the collection of broad and sizable datasets would facilitate studies that allow the autonomous discovery of the meaning-carrying units of communication.
A dedicated interdisciplinary initiative toward a detailed understanding of animal communication could arguably be made with a number of species as its focus. Birds, primates, and marine mammals have all given insight into the capacity of animal communication. In some ways, the collective understanding of the capacity for and faculty of comm...
11:21
Desktops/Laptops: Windows Down to 64%, GNU/Linux Rises to 6.3% Techrights
Combined share (OpenDocument Format):
The overall picture:
Summary: The trend is revealing; amid gains for Chrome OS and GNU/Linux Microsoft is laying off untold number of workers and Windows market share is in a freefall
11:09
Windows Market Share: From 80% to 26% in a Single Decade Techrights
The fall or the losses deepen this month (Microsofts share of the pie was 3 times bigger 10 years ago)
Summary: As can be seen in the chart above, Microsoft is reaching all-time lows again in terms market share (not that the media bothers mentioning this; its paid to pretend chatbots are revolutionary and position Microsoft for huge growth)
10:40
U.S. Banks, Including Chase and Synchrony, File Suspicious Activity Reports and Shut Down Accounts for Logging in From Another Country and Transferring Retirement Funds; May Also Affect VPN Users Techrights
Reprinted with permission from Ryan
U.S. Banks, Including Chase and Synchrony, File Suspicious Activity Reports and Shut Down Accounts for Logging in From Another Country and Transferring Retirement Funds; May Also Affect VPN Users
American banks are closing customer accounts without warning and many are refusing to say why.
The ones named, according to the article, are Chase and Synchrony Bank.
(Two of the worst banks in the country to bank with, I might add. Chase was ripping my ex blind with $11 monthly checking account fees until I switched him to an online bank with no fees and put an end to that.)
Synchrony is an underlying bank for PayPal Savings and PayPal Checking.
Synchrony also runs some store cards. They have a possibly illegal practice (under Illinois BIPA) of collecting biometric data to open an Amazon Card.
If you use a VPN, you may want to use split tunneling for a Web browser session to do your online banking.
In at least one instance, according to the article, Chase Bank violated the Bank Secrecy Act, first by telling a man who had his accounts frozen in the middle of dinner and was left unable to pay the bill as a result, that it had filed a SAR (which is illegal.you cannot tell a customer you did that), and then violated the BSA again by telling him why (he had logged on to their online banking system from a foreign country while he was on vacation).
Theres a lot of weird stuff going on in the US banking industry right now, including an explosion of SARs. Ironically, the article says the explosion of SARs came after the pandemic, which was a pandemic of a SARS virus.
In all seriousness, the banks are reporting anything that looks even kind of dodgy, apparently, because theres no penalty to the bank to close accounts and file them, even though only 4% are possibly criminal activity, according to the New York Times article.
MinceR on #TechRights IRC channel raised a very good point.
Isnt losing clients a penalty?
Chase Bank has $4 trillion in assets. With that much and with the Systemically Important Bank regulators breathing down their necks, its not so serious if they...
10:24
How DARPA Leverages Open Source to Secure 5G Linux.com

Read the original blog at Read More
The post How DARPA Leverages Open Source to Secure 5G appeared first on Linux.com.
10:00
HPR3832: How I left Google behind Hacker Public Radio
A list of the software and hardware I cover in the show. Hardware: Server - 11th gen i5-11400, 64GB RAM, 12TB SSD storage Local backup server - 4th gen i5-4570, 32GB RAM, 24TB HDD storage in mirrored ZFS pool for 12TB usable. Offsite backup server - Celeron J4125, 16GB RAM, 8TB SSD storage Software: Hypervisor - Proxmox Virtual Environment https://www.proxmox.com/en/proxmox-ve Backup software - Proxmox Backup Server https://www.proxmox.com/en/proxmox-backup-server Email - iRedMail https://www.iredmail.org/index.html Photos, Notes, File Storage, Office Software - Nextcloud AIO https://github.com/nextcloud/all-in-one Music - Funkwhale https://funkwhale.audio/ Social Media - Mastodon https://github.com/mastodon/mastodon Blog - writefreely https://github.com/writefreely/writefreely Video - Invidious, Peertube https://invidious.io/ https://github.com/Chocobozzz/PeerTube/ Chat - Matrix, Element https://github.com/matrix-org/synapse/ https://element.io/
Automated Detection and Repair of Intrusive Ads It Will Never Work in Theory
Unless and until legislators give ad regulations some real teeth, we're going to have to rely on counter-measures. I can think of no better introduction and summary for this latest advance in that arms race than the one written by the authors themselves and quoted below.
we propose an automatic detection technique that addresses the following challenges: (1) Advertisements can be fully dynamic where the structure of an ad is unknown until runtime, making it difficult to identify an ad and differentiate it from other elements. (2) Dynamically loaded ads can be highly volatile (e.g., first appear and then disappear at any time), which makes it difficult to localize dynamic ads in the source code. (3) Advertisements can be initially preloaded and later have their properties modified during runtime, thus a pure static/dynamic analysis alone does not suffice.
To this end, we propose AdHere, a technique that can automatically detect violating ads and suggest repair proposals. The design of AdHere is based on a combination of static and dynamic analyses. It works by first parsing the initial web page to a DOM tree to search for potential static ads, and then using mutation observers to monitor and detect intrusive (dynamic/static) ads on the fly. To handle ads' volatile nature, AdHere includes two detection algorithms for desktop and mobile ads to identify different ad violations during three phases of page load events. Our approach recursively applies the detection algorithms to resolve nested layers of DOM elements inserted by ad delegations. We evaluate AdHere on Alexa Top 1 Million Websites to detect their compliance with the Better Ads Standards. AdHere detected violating ads on 5,540 mobile websites and 4,601 desktop websites. Compar[ed] to the currently available alternative, AdHere detected violations on 4,656 more mobile websites and 3,911 more desktop websites and improved recall (by 16.6%) and accuracy (by 4.2%).
Yutian Yan, Yunhui Zheng, Xinyue Liu, Nenad Medvidovic, and Weihang Wang. AdHere: automated detection and repair of intrusive ads. In Proc. ICSE'23, 2023, https://weihang-wang.github.io/papers/ICSE2023-AdHere.pdf.
09:20
Metaverse as a New Game Reality: Does it Make Sense to Invest in VR Development? HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
How much has Virtual reality (VR) technology evolved? It has evolved enough for indie virtual reality projects to
This is a post from HackRead.com Read the original post: Metaverse as a New Game Reality: Does it Make Sense to Invest in VR Development?
09:20
Twitter Shut Off its Free API and It's Breaking a Lot of Apps SoylentNews
Even developers who want to pay for the API are having trouble:
Twitter has finally shut off its free API and, predictably, it's breaking a lot of apps and websites. The company had previously said it would cut off access in early February, but later delayed the move without providing an updated timeline.
But, after announcing its new paid API tiers last week, the company seems to have started cutting off the thousands of developers relying on its free developer tools. Over the last couple days, a number of app makers and other services have reported that the Twitter API is no longer functioning. Mashable reported the shutoff seems to have started Tuesday morning, though many developers are still trying to understand what's happening as Twitter doesn't seem to have communicated with most developers about the changes.
The ending of Twitter's free API comes after the company abruptly changed its rules to ban third-party Twitter clients as part of a larger shakeup of its developer strategy. But, as we've previously reported, third-party clients were only a small fraction of the developers, researchers, bot makers and others who relied on Twitter's APIs.
[...] All of these issues are further complicated by the fact that Twitter seems to have communicated very little with any of its developers about these changes or what they mean. Most of the employees who worked in developer relations were cut during the company's mass layoffs. And the company's developer forums are filled with posts from confused developers looking for answers. The company no longer has a communications team, and its press email auto-responds with a poop emoji.
Read more of this story at SoylentNews.
09:00
My Glasses Hear Everything Im Not Saying! Hackaday

There was a time when you saw someone walking down the street talking to no one, they were probably crazy. Now you have to look for a Bluetooth headset. But soon they may just be quietly talking to their glasses. Cornell University researchers have EchoSpeech which use sonar-like sensors in a pair of glasses to watch your lips and mouth move. From that data, they can figure out what you are saying, even if you dont really say it out loud. You can see a video of the glasses below.
There are a few advantages to a method like this. For one thing, you can speak commands even in places where you cant talk out loud to a microphone. There have been HAL 9000-like attempts to read lips with cameras, but this is power-hungry and video tends to be data intensive.
By comparison, the EchoSpeech uses low-power speakers and transducers to silently collect a modest amount of data. In addition to convenience, this tech could be a real breakthrough for people who cant speak for some reason but can move their lips and mouth.
We often wondered if Star Trek-style voice command would be a pain in a 25th-century cube farm. EchoSpeech could solve this problem since you dont actually speak out loud.
Google Glass wasnt very successful, but this might be viable for some users. Even better if integrated with...
07:33
KillNet Claims Creating Gay Dating Profiles with NATO Logins HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
KillNet claims it carried out cyberattacks that resulted in the "paralysis" of 40% of NATO's electronic infrastructure.
This is a post from HackRead.com Read the original post: KillNet Claims Creating Gay Dating Profiles with NATO Logins
07:32
On-line Casino Greatest On-line Casinos In New Zealand 2023 h+ Media
On-line Casino Greatest On-line Casinos In New Zealand 2023
All the fun games we acknowledge and love from 888casino are here but now you will discover them with a extra private contact. The solely thing you need to play casino in Mobile is a fast web connection and a relatively trendy mobile system. You can play both on cellular and on tablet, whether or not you employ iOS or Android.
Since the New Zealand Gambling Act was amended in 2019, most New Zealand on-line casinos offer BankID as an identity verify. This means that you automatically register a game account if you make a deposit at the casino. This means you dont have to register on the on line casino manually, and get registered in connection along with your deposit. This is also called Pay n play on line casino and is a convenient approach to keep away from difficult registration processes whenever you need to get started with on line casino games on-line. He is always fast to review new casinos which have area of interest themselves on odds and esports. Edward is also no stranger to testing video games with distinctive ideas that do not belong to the traditional casino video games with free spins and bonuses.
Receive 500% bonus in your first deposit with us, 600% on the second deposit and 400% bonus on the third. We grant a bonus to all deposits, starting with 200% in your first deposit of the day. With this supply voucher, place your football bets and obtain a discount of $34.25 in Betfair. 888 Casino encourages you to addContent your documentation directly onto the on line casino web site for all future withdrawals.
- Online casinos even have one thing in store for Blackjack and Baccarat fans.
- The RNG works in the background and what you see on the screen are then solely animations of the end result from it.
- We can say that Bspin is genuinely a fantastic online on line casino that caters to the wants of every kind of gamblers, on-line casinos that provide no deposit bonuses.
- The on line casino provides an unlimited number of video games from varied firms, a great mobile app that works on all units and unbelievable participant help in each banking and issues decision.
- All-time favourite classic tables embody Blackjack, Poker, Sic Bo, Roulette, Baccarat, and Keno.
- We can even do it by e mail; dont hesitate to write down to us at earlier than any doubt you have.
1001couponcodes.co.nz has one of the best choices in addition to exclusive provides. The 888 Casino low cost coupon are codes used by online stores to convince undecided prospects to complete their purchase. If you enjoyed the low cost provided by our coupons, we recommend that you simply checkout immediately as they have very limited validity.
A wide range of games can be found by way of your cell device and gamers can count on the same high-quality gaming expertise whether or not youre enjoying from your...
07:30
888 Casino Review Up To $1500 On First 5 Deposits! h+ Media
888 Casino Review Up To $1500 On First 5 Deposits!
When it comes to cost strategies, 888 on line casinos supply is quite acceptable. The rollover amount is 30x and the completely different online casino games contribute differently to the same. The 888casino bonus cannot be withdrawn with out the necessities being met. With all that theres on provide under the 888 Umbrella, they really are the one-stop-shop for online playing and you really cant go incorrect no matter what service you be part of.
Thats why UPayCard is such an excellent possibility for those who favor it. Cassava Enterprises can be licensed and controlled to offer online gaming services under the legal guidelines of Gibraltar. Only gamers whove played with the on line casino enough will be invited to hitch this unique experience. Poker, baccarat and blackjack are obtainable in numerous recreation variants, so newcomers are finest off sticking to the traditional video games. Those who know somewhat will find variety in poker variants similar to Caribbean Stud, Casino Holdem and Pai Gow Poker.
Also benefit from our coupons and provides from the shop Tornadobet. These typically provide higher payout percentages and better probabilities of successful than bodily casinos. But additionally between these NZ online casinos, the RTP can vary fairly a bit. Because the number of on-line providers is consistently rising, we now have taken the search work off your arms and ready an outline of the best online casinos in the New Zealand. A dedicated part of the foyer will present numerous tables and tournaments for players trying to enjoy the game with out utilizing actual cash within the course of. T just apply to cash video games but in addition to on-line poker tournaments, for the explanation that schedule is all the time packed and the motion by no means seems to stop.
Essentially, if you would like the chance of successful over 1,000,000 NZ dollars from only one single recreation, from one single spin, that is the sector you play in. When analysing the on line casino, all areas of the location are equally matched in brilliance. The casino side, however, dominates within the variety of gameplay. Well over a thousand titles are lined up right here alone and every recreation you might have heard of and would need to play, they are all right here. 888 provides all the essential sports activities you could ask for from a sportsbook. NHL and different major sports are naturally on offer, as nicely as lacrosse and CFL.
If youve fortunate numbers or assume they are in your aspect, the roulette await you. For those who favor letters, the blackjack online poker is out there. The truth is that poker has seen lots of development in the https://casino-tr.top/superhero-reels-slot/ final twenty years, being not only performed amongst friends but in...
07:28
888poker Leaves Polish Market Nz On-line On Line Casino News h+ Media
888poker Leaves Polish Market Nz On-line On Line Casino News
No matter where youre and no matter how busy the remainder of your life will get, you by no means have to miss out on any on line casino video games or opportunities to win massive once more. There are many guides found on the site that can help you with their video games, covering slots, roulette, blackjack, Texas HoldEm, bingo, sports betting and stay on line casino video games. Internationally famend writer Henri Ojala has spent more than a decade mastering the ins and outs of the playing trade, specializing in online poker, sports betting, and on line casino video games. With over 10 years of expertise in the playing industry, hes a respected skilled in various types. Henri shares his in depth knowledge of strategies, odds, and danger administration, earning him recognition as an authority within the online casino area. Although the variety of online pokies isnt big at 888 Casino, there isvariety and games by the leading producers, as properly as some distinctive titles too.
888 Casino features a good welcome package for new players including 88 Free Spins with no deposit required and a welcome bonus that may go up to NZ$200. It additionally features ongoing promotions that function high-earning qualities. The proven truth that it has been around since 1997 makes it a very skilled on line casino and extremely trustworthy.
No downloads, identical content material, and still play anyplace that has Wi-Fi or a 4G/5G connection. You will be capable of transition from PC to Mobile and have the same selection of video games, together with the same ranges of safety. If youve a smartphone with Android, iOS, or Windows constructed into it, then yes, youll find a way to play 888 on line casino cell on the go. The Tropicana Casino and Resort has joined with Gamesys Limited, which runs the jackpotjoy.com web site. The four casinos owned by Caesars Entertainment Caesars Atlantic City, Ballys Atlantic City, Harrahs Resorts Atlantic City and the Showboat Casino Hotel are partnering with 888 Holdings. Nine of towns 12 casinos have acknowledged lining up companions for Internet gambling, and a 10th is widely rumored to have selected a companion, as nicely.
You can wager these bonus funds on eligible 888 casino games such because the model new Jacks Pot, Millionaire Genie, Irish Riches, Nightmare on Elm Street, and Ultimate Universe. You even have the prospect to hit the jackpot on one of these pokies! Make certain you learn the terms and conditions fastidiously whenever you join, as withdrawal restrictions apply. 888, founded in 1997, are stalwarts of the net on line casino industry with fingers in many pies. 888casino is only one such finger protruding from the 888 holdings tart.
888 Casino is now providing the Premier Players Welcome Bonus which begins with a one hundred pc match on your first deposit...
07:27
888 Casino Nz Review On-line $100 Nzd 888 On Line Casino Bonus 2023 h+ Media
888 Casino Nz Review On-line $100 Nzd 888 On Line Casino Bonus 2023
The provide itself is a 100 percent matched deposit bonus up to the value of $1500. We shall be introducing you to the casinos unique welcome bonus supply. We then inform you of a few of the ongoing rewards that may be collected from their Promotions page. And lastly, we shall be telling all about their 888 VIP Casino Club.
It features a six-line, Six-column format with forty six,656 paylines and an RTP rate of 94.8%. Its finest features embody free spins with various bonuses and progressive jackpots. Yes, 888 offers to its gamers all the wanted security measures. The casino is licensed and controlled by the Gibraltar Regulatory Authority, which means that it meets the entire standards for a fair and protected on-line casino. In addition, 888 has been rewarded an assurance seal for truthful gaming by eCORGA.
You ought to at all times look for the free spin feature of Aloha, you should use our sources below to grasp the game inside a very brief time period. In New Jersey, you get the free spins or money to enjoy desk video games. Slots are one of the favorite decisions of games at on-line casinos. A number of cost methods make the positioning so nice as every participant can discover a suitable method for managing funds.
The on line casino has the most important collection of games compared to some other crypto-friendly playing platform. Kiwis can indulge in Pokies, Live Dealer Games, Progressive Jackpots, Esports, Live Sports Betting, TV, and Virtual Games. 888Starz has a Buy Feature that lets gamers buy their means into bonus rounds on in style Pokies. For occasion, Kiwis do not have to attend to hit the bonus randomly, they usually can buy their means into a bonus round to trigger elevated winnings.
Minimum deposit 100$ free spins gilitga in Book of Dead 0x wagering requirements. By selecting games at licensed casinos, you could be assured that the on line casino is underneath the supervision of the New Zealand authorities who are there to safe your gaming environment. When New Zealand casinos want to supply a slot machine, all video games must have an eCorga certification. 99% RTP in a slot or slot machine by definition does not imply that the prospect of winning is 99% and games with excessive RTP usually are not a guarantee of successful. What RTP a sport has is predicated on the millions of billions of spins made in that specific sport. The extra check spins made, the safer and more accurate the gameS RTP becomes.
Casino 888 is offered by an interesting panoply of developers, made up of a few of the greatest names within the on-line casino world. Despite having a great supply of video games, on line casino 888 still does not supply its punters stay Casino games. Again, if youre not acquainted with the formats of those competitions than there is not a want to fret as 888 offer you guides to get b...
07:26
High 10 Greatest Online Casino In New Zealand Get Bonuses Enjoying In Online Pokies h+ Media
High 10 Greatest Online Casino In New Zealand Get Bonuses Enjoying In Online Pokies
MB Way is doubtless considered one of the most Moderna payment methods in New Zealand. This cellular app combines the most effective of the ATM system with the comfort of having the power to pay at any time, anyplace. You can even receive money, but for now, this feature just isnt obtainable within the legal on-line casinos that we recommend. Even though you can play slots with MB Way and all of the table games available, this is one of those sections of on-line casino video games that we need to see amongst ourselves. In a perfect world, with national sellers , lots of friendliness and some engaging gaming tables as is the case with the roulette tables that so many gamblers fascinates.
After graduation, she moved to Wellington to pursue a profession in writing. 888 Casino Compared with other casinos from the Online Pokies class. There can be the 888 Blog that will maintain you updated with all the casinos information and sport releases. The Live area is a full-on streaming platform where youll compete towards the various completely different sellers internet hosting the tables.
Providers corresponding to IGT, NetEnt, Pragmatic Play or Microgaming are included within the catalog, which provides quality to the casinos offer. Its straightforward to seek out the part devoted to promotions on the homepage, however where are they? On previous visits we got here across some well-structured offers that aroused our curiosity. Currently, solely two welcome presents had been out there, and its attainable to take pleasure in both, however weekly promotions, challenges, tournaments and other promotional add-ons are lacking. In this field, different casinos New Zealand on-line provides a lot more than 888.
Finally, it is much simpler to manage betting and impose limits on playing in a web-based on line casino, which makes on-line playing relatively cheaper, safer and simpler to control. The tables are real, the croupiers are real and the sport is not automated. These are the principle explanation why on-line gamblers select a Live Casino. Due to the growing popularity, providing a Live Casino is an enormous plus for on-line casinos on this rating. Blackjack is also identified as a game for which varied clever methods can be utilized.
This application can now even be used for casino video games for example. 888s cellular on line casino app provides three of its most distinguished options Sport, Poker and Casino. Within those three subsidiaries, youll discover a load of gaming choices. What units 888 apart from the competitors is its providing of sports betting as a portable option as that is one thing that is still in the implementation phase for many other cell casinos.
Besides offering all kinds of sports activities for wagering, additionally they broadcast several events reside...
07:03
Distribution Release: 4MLinux 42.0 DistroWatch.com: News
4MLinux is a miniature Linux distribution focusing on four capabilities: maintenance, games, multimedia, and servers. The introduces a few new applications and a series of updates. "4MLinux 42.0 stable released. The status of the 4MLinux 42.0 series has been changed....
06:34
Animal Mutation Rates Reveal Traits That Speed Evolution SoylentNews
Now, a massive analysis of 68 diverse vertebrate species, from lizards and penguins to humans and whales, has made the first large-scale comparison of the rates at which species mutate a first step toward understanding how quickly they can evolve. The findings, published in the journal Nature, unearthed surprising insights into how the tempo for mutations can change and what sets that pace.
The paper roughly "doubles the amount of mutation-rate estimates we have," said Michael Lynch, an evolutionary biologist at Arizona State University who was not involved in the study. Now we have a "better idea of the amount of variation within vertebrates."
With this extensive data, biologists can begin to answer questions about which traits most influence mutation rates and the pace of evolution. "There are things that affect the rate of evolution, [but] we don't know all of them," said Patricia Foster, a professor emerita of biology at Indiana University who was not involved in the study. "This is the start."
[...] If they found a mutation in around 50% of an offspring's DNA, they concluded that it was likely a germline mutation one inherited through either the mother's egg or the father's sperm. Natural selection can act directly on such a mutation. Less frequent mutations were deemed to have happened spontaneously in tissues outside the germline; they were less relevant to evolution because they wouldn't get passed on.
(Surprisingly often, mismatches in the family trios told the researchers that the fathers listed by the zoos were unrelated to the babies. Zoo representatives would often shrug at this news and say there might have been two males in the cage. "Yeah, well, the other one is the winner," Bergeron would joke.)
In the end, the researchers had 151 usable trios, representing species as physically, metabolically and behaviorally diverse as massive killer whales, tiny Siamese fighting fish, Texas banded geckos and humans. They then compared the species' mutation rates with what we know about the behaviors and characteristics called their life history. They also considered a statistical measure for each species called the effective population size, which roughly corresponds to how many individuals are needed to represent the genetic diversity. (For example, although the human population today is 8 billion, scientists usually estimate our effective population size to be around 10,000 or fewer.) Bergeron and her colleagues looked for patterns of associations in the numbers.
06:13
Reddit Banned 5,853 Users for Excessive Copyright Infringement Last Year TorrentFreak
 Every day, millions of people from all over the world submit
posts, comments, and other content to Reddit.
Every day, millions of people from all over the world submit
posts, comments, and other content to Reddit.
The social news and discussion platform has been around for more than 17 years and over time its popularity has only increased.
With Reddit about to reach adulthood, the site has certain responsibilities. In recent years, these have included the publication of a transparency report documenting how various legal policies affect the sites content.
The report shows how Reddits content policy leads to the deletion of millions of posts per week, including spam, hateful content, sexualization of minors, prohibited goods, and harassment. As a result, more than five million user accounts were banned last year, either temporarily or permanently.
DMCA Notices and Takedowns Increase
The number is significant, especially when taking into account that it doesnt include copyright-related complaints. Reddits responses to DMCA takedown notices and the sites handling of excessive copyright infringement are listed separately in the legal removals section.
These figures have been steadily increasing, and last year was no exception, according to the transparency report.
In 2022, we saw a 43% increase over the previous year in the total number of copyright notices received, a 126% increase in the amount of content reported for removal, and a 97% increase in the amount of content removed, Reddit reports.
Compared to other content removals, copyright actions are relatively modest. In 2022, Reddit received 254,632 copyright notices, in which rightsholders asked the site to remove 1,668,452 pieces of content. Of these requests, close to 80% resulted in items being removed.
These numbers are relatively small compared to the dozens of millions of content policy removals. However, they carry a different weight as the content is reported by third-party actors, instead of Reddit mods or bots.
User and Subreddit Bans
This increase is not limited to the copyrighted links and content removed, subreddits are affected too. Several popular Reddit communities have to jump through hoops to avoid getting banned but not all manage to do so. In 2022, Reddit booted 3,215 subreddits for exces...
06:09
Rosenzweig Steps Down As Open-Source Arm Mali "Panfrost" Driver Maintainer Phoronix
Alyssa Rosenzweig who has been leading the Panfrost open-source Arm Mali graphics driver reverse engineering effort the past half-decade is stepping down as maintainer of this driver as part of this also being her last day at Collabora...
05:32
The extended BPF (eBPF) virtual machine allows programs to be loaded into and executed with the kernel and, increasingly, other environments. As the use of BPF grows, so does interest in defining what the BPF virtual machine actually is. In an effort to ensure a consistent and fair environment for defining what constitutes the official BPF language and run-time environment, and to encourage NVMe vendors to support BPF offloading, a recent effort has been undertaken to standardize BPF.
05:04
Linux cp command copy symbolic (soft) link tutorial nixCraft
Do you want to copy a symbolic (soft) link instead of a file using the cp command under Linux? Try passing the -a (--archive) to copy and preserve all soft (symbolic) links. The cp command is a naturally used file copying under Linux and it comes with a few rules for copying symbolic links.
Love this? sudo share_on: Twitter - Facebook - LinkedIn - Whatsapp - Reddit
The post Linux cp command copy symbolic (soft) link tutorial appeared first on nixCraft.
05:00
NVIDIA Finally Working On A Linux Driver For Their 2017 SHIELD Controller Phoronix
NVIDIA launched their SHIELD "Thunderstrike" gaming controller back in 2017 and now in 2023 they are working to upstream their HD driver support for it...
04:52
Israel Faces Fresh Wave of Cyberattacks Targeting Critical Infrastructure HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
Authorities believe that these cyberattacks may be part of OpIsrael, organized by pro-Palestinian hackers.
This is a post from HackRead.com Read the original post: Israel Faces Fresh Wave of Cyberattacks Targeting Critical Infrastructure
04:10
In SAS v. WPL, the Federal Circuit Finally Gets Something Right on Computer Copyright Deeplinks
Figuring out the correct boundaries of software copyright protection is a difficult task. As several judges have put it, applying copyright law to computer programs is like assembling a jigsaw puzzle whose pieces do not quite fit. Last week, the U.S. Court of Appeals for the Federal Circuit solved one piece of that puzzle, by approving a procedural framework for analyzing software copyright cases.
Previously, the Federal Circuit failed miserably at solving that puzzle. It had issued two horrible computer copyright decisions in the long-running Oracle v. Google saga. The first of those opinions held that the Java Application Program Interfaces (APIs) were eligible for copyright protection. The second reversed a jurys determination that Googles use of the Java APIs was a fair use. Fortunately, the Supreme Court stepped in and reversed the second opinion, finding fair use. Unfortunately, the Courts fair use decision left open the first issue, whether APIs are copyright-eligible in the first place.
In a decision last week, the Federal Circuit finally got something right about copyright
In a decision last week, the Federal Circuit finally got something right about copyright, or at least the framework for deciding copyrightability of functional aspects of software. The case is between SAS Institute Inc. (SAS) and World Programming Ltd. (WPL). The two companies have been feuding for years over SASs effort to ef...
04:07
Who was Not Even Wrong first? Not Even Wrong
I recently heard from John Minkowski, whose father Jan Minkowksi was a student of Paulis in the late 1940s. He asked if I knew what the specific context of Paulis Not Even Wrong comment was, and I told him I didnt. I referred to this early blog post, which explains that Karl von Meyenn (editor of Paulis correspondence) had pointed me to a biographical memoir about Pauli by Rudolf Peierls which includes:
Quite recently, a friend showed him the paper of a young physicist which he suspected was not of great value but on which he wanted Paulis views. Pauli remarked sadly It is not even wrong.
Looking around for any more information about this, Wikipedia links to a 1992 letter to the editor at Physics Today from Peierls, which states
Wolfgang Paulis remark Das is nicht einmal falsch (That is not even wrong) was made not as a comment on a seminar talk but as a reaction to a paper by a young theoretician, on which a colleague (I believe it was Sam Goudsmit) had invited Paulis opinion.
Google also turned up a translation of a talk by Peierls in this article by Mikhail Shifman, which includes:
Somebody showed to Pauli a work of a young theorist being well aware that the work was not too good but still willing to hear Paulis opinion. Pauli read the paper and said, with sadness: It is not even wrong.
Trying to guess what the article in question might have been, Im tempted by the hypothesis that the discussion with Goudsmit was about Everetts Relative State Formulation of Quantum Mechanics paper. The timing (Quite recently) would have been right, with the paper published in July 1957, Paulis death later in December 1958. Goudsmit at the time was editor-in-chief at Physical Review, so would have been interested in Paulis opinion of the paper.
Complicating this story, John Minkowki sent me some pages from his fathers 1991 book Through three wars: The memoirs of Jan Michael Minkowski, which included this (in a context describing his 1946-48 student days at ETH):
I remember a seminar in theoretical physics given by a visitor from another Swiss university. These seminars were presided over by Dr. Pauli, and after the speaker finished all eyes would turn to Pauli to pronounce the verdict in his commentary. This particular lecture was treated by Pau...
04:00
Remembering Data Compression Pioneer Jacob Ziv IEEE Spectrum

Jacob Ziv, codeveloper of the Lempel-Ziv data compression algorithm, died on 26 March at the age of 91.
The IEEE Life Fellow was awarded the 2021 IEEE Medal of Honor for fundamental contributions to information theory and data compression technology, and for distinguished research leadership.
Ziv, an electrical engineering professor at the Technionthe Israel Institute of Technology, in Haifaand his colleague Abraham Lempel perfected the lossless compression technique, enabling perfect data reconstruction. With lossless algorithms, as an IEEE Spectrum article explained in 2021, bits disappear, making the data file dramatically smaller and thus easier to store and transmit, but unlike lossy compression techniques such as the ones used with JPEG and MP3 files, the bits reappear on command.
The Lempel-Ziv data compression algorithm, which paved the way for GIF, PNG, and ZIP files, was designated an IEEE Milestone in 2004.
Zivs scientific contributions changed forever the way we store, process, and transfer information, the Technions president, physicist Uri Sivan, wrote in a tribute to Ziv. He was an inspiration to all of usa beacon of scientific excellence [and] a symbol of sciences great potential to ignite technological revolutions that affect all of mankind.
Information and communication theory pioneer
Born in Israel, Ziv received bachelors and masters degrees in electrical engineering from the Technion in 1954 and 1957. He began his career in 1955 as a research engineer with the Israeli...
03:49
New AI Model Can Cut Out Any Object Within an Imageand Meta is Sharing the Code SoylentNews
On Wednesday, Meta announced an AI model called the Segment Anything Model (SAM) that can identify individual objects in images and videos, even those not encountered during training, reports Reuters.
According to a blog post from Meta, SAM is an image segmentation model that can respond to text prompts or user clicks to isolate specific objects within an image. Image segmentation is a process in computer vision that involves dividing an image into multiple segments or regions, each representing a specific object or area of interest.
The purpose of image segmentation is to make an image easier to analyze or process. Meta also sees the technology as being useful for understanding webpage content, augmented reality applications, image editing, and aiding scientific study by automatically localizing animals or objects to track on video.
Related:
MIT's
Computer Vision (CV) Algorithm Identifies Images Down to the
Pixel (20220424)
NVIDIA
Research's GauGAN AI Art Demo Responds to Words (20211130)
Ask
Soylent: Beginning in Artificial Intelligence Methods
(20150629)
Read more of this story at SoylentNews.
03:30
CISA adds zero-day bugs in iPhones, Macs, and iPads to its Known Exploited Vulnerabilities catalog Security Affairs
US Cybersecurity and Infrastructure Security Agency (CISA) added two flaws in iPhones, Macs, and iPads to its Known Exploited Vulnerabilities catalog.
U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added the following five new issues to its Known Exploited Vulnerabilities Catalog:
- CVE-2023-28205 Apple Multiple Products WebKit Use-After-Free Vulnerability;
- CVE-2023-28206 Apple iOS, iPadOS, and macOS IOSurfaceAccelerator Out-of-Bounds Write Vulnerability;
This week Apple has released emergency security updates to address the above actively exploited zero-day vulnerabilities impacting iPhones, Macs, and iPads.
Impacted devices include:
- iPhone 8 and later,
- iPad Pro (all models),
- iPad Air 3rd generation and later,
- iPad 5th generation and later,
- iPad mini 5th generation and later,
- and Macs running macOS Ventura.
Both vulnerabilities were reported by Clment Lecigne of Googles Threat Analysis Group and Donncha Cearbhaill of Amnesty Internationals Security Lab.
The zero-day CVE-2023-28205 is a use after free issue that resides in the WebKit, its exploitation may lead to arbitrary code execution. An attacker can trigger the flaw by tricking the victims into loading maliciously crafted web pages.
Processing maliciously crafted web content may lead to arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited. reads the advisory.
The IT giant addressed the flaw with improved memory management.
The zero-day CVE-2023-28206 is an out-of-bounds write issue that resides in the IOSurfaceAccelerator.
An app may be able to execute arbitrary code with kernel privileges. Apple is aware of a report that this issue may have been actively exploited. reads the advisory.
The company addressed the flaw with improved input validation.
Apple addressed the zero-day issue with the release of macOS Ventura 13.3.1, iOS 16.4.1, iPadOS 16.4.1, and Safari 16.4.1.
According to Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities, FCEB agencies have to address the identified vulnerabilities by the due date to protect their networks against attacks exploiting the flaws in the catalog.
Experts recom...
03:00
Linux Cluster-Aware Scheduling Being Extended To AMD Processors Phoronix
Back in 2021 saw work on CPU cluster-aware scheduling by HiSilicon engineers for Arm processors as well as Intel engineers with a focus on their Jacobsville platform being comprised of clusters of Atom cores. That x86 cluster-aware scheduling was enabled for capable Intel processors while now two years later is being extended for AMD processors...
02:46
SD Worx shuts down UK and Ireland services after cyberattack Security Affairs
Belgian HR giant SD Worx was forced to shut down its IT infrastructure for its UK and Ireland services after a cyber attack.
HR and payroll management firm SD Worx shut down its IT systems for its UK and Ireland services after a cyber attack. The company employs more than 7,000 HR professionals and serves over 5.2 million employees every month. The company claims a client base of over 82,000.
The UK and Ireland branch disclosed a security breach and began notifying its customers.
Our security team has discovered malicious activities in our hosted data centre last night. We have taken immediate action and have preventively isolated all systems and servers to mitigate any further impact. As a result, there is currently no access to our systems, which we deeply regret of course, reads the security breach notification sent by the company to UK and Ireland customers, as reported by BleepingComputer.
SD Worx emphasises that it applies extremely stringent organisational and technical security measures to secure the privacy and data of its customers at all times. It goes without saying that we are handling this with the highest priority and that we are working very hard on a solution to give you access to our systems again. We will keep you informed about the further status.
The company did not reveal the type of attack it has suffered and did not reveal if it has suffered a data breach.
At the time of this writing, the companys portal for UK and Ireland is reachable again.
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections:
- The Teacher Most Educational Blog
- The Entertainer Most Entertaining Blog
- The Tech Whizz Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please nominate Security Affairs as your favorite blog.
Nominate here: https://docs.google.com/forms/d/e/1FAIpQLSfaFMkrMlrLhOBsRPKdv56Y4HgC88Bcji4V7OCxCm_OmyPoLw/viewform
Follow me on Twitter: @securityaffairs and ...
02:36
Meson 1.1 Build System Released With Numerous Additions Phoronix
Just before Christmas Meson 1.0 was released for this widely-used, open-source software build system. Out today is Meson 1.1 as the newest feature update...










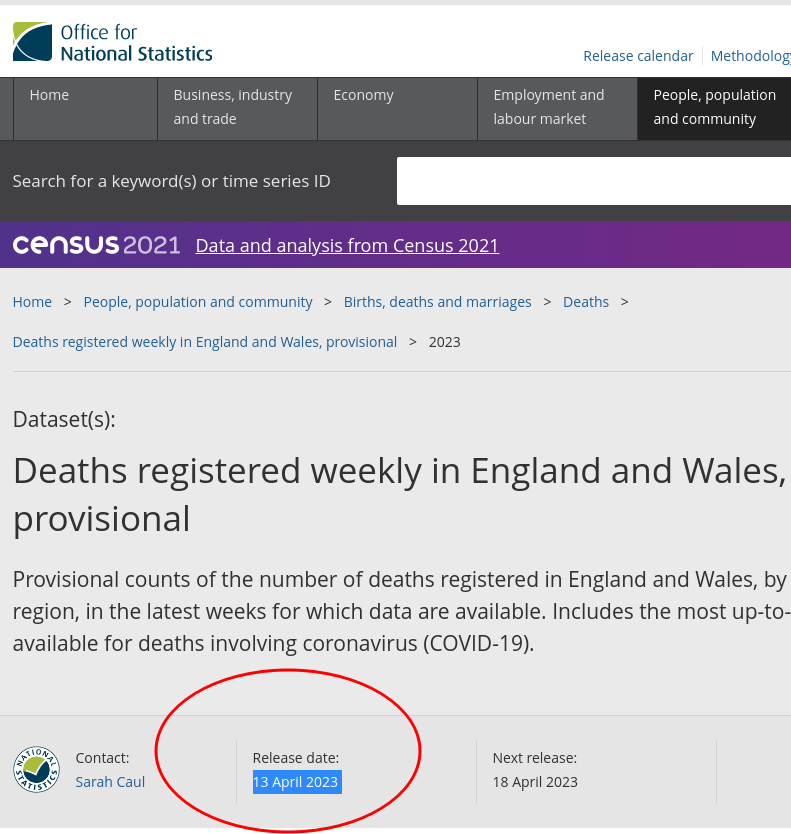
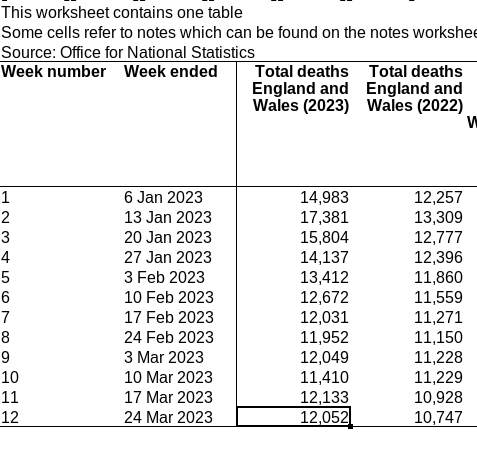





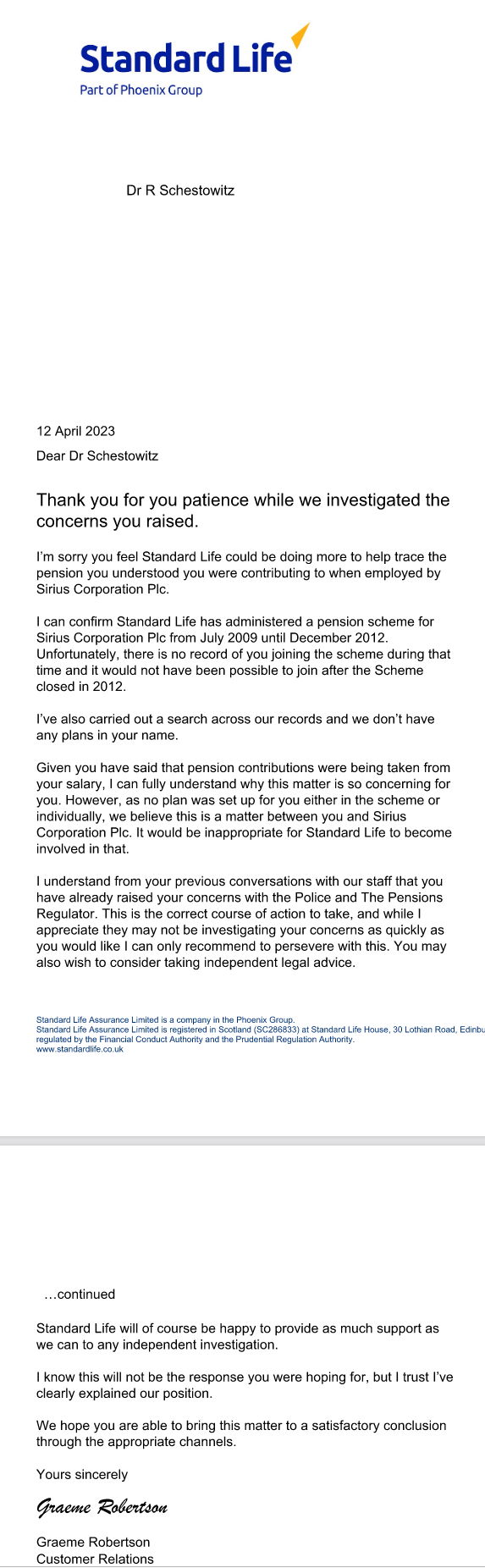
![How to Connect GitHub to VS Code [Step by Step]: GitHub is proprietary software. VS Code is proprietary spyware. Both are controlled by a company that viciously attacks Open Source in a number of ways. Why is a site called 'It's FOSS' publish such stuff? Seems contrary to its raison detre.](../../techrights.org/wp-content/uploads/2023/04/vs-code-github.png)