| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Sunday, 09 April
02:37
Raytheon Director and His Wife Killed in Plane Crash cryptogon.com
Via: Daily Mail: Two couples from Indiana were killed when their plane crashed off the coast of Venice, Florida after they flew in to have dinner with friends. The single-engine plane crashed near the Venice Fishing Pier soon after takeoff on Wednesday evening on its way back to St. Petersburg, Florida. Jeff Lumpkin, 64, an []
02:30
Ukrainians Say No to Microsoft Techrights
Microsoft has lost grip, so it is instead bribing officials for a "feast" on tax money
Summary: Despite the Ukraine-Microsoft graft (Azure deployment/outsourcing, in effect another hugely costly "defence"-themed bailout from taxpayers to Microsoft) it seems clear that Ukrainians themselves say no to Microsoft and many have moved to GNU/Linux; the majority of Ukrainians do not use Windows as of this month
02:08
Round-Up: ChatGPT, Bard, etc - We Did Ask What Could Go Wrong, Didn't We? SoylentNews
OpenAI threatened with landmark defamation lawsuit over ChatGPT false claims
A spokesperson for Gordon Legal provided a statement to Ars confirming that responses to text prompts generated by ChatGPT 3.5 and 4 vary, with defamatory comments still currently being generated in ChatGPT 3.5. Among "several false statements" generated by ChatGPT were falsehoods stating that Brian Hood "was accused of bribing officials in Malaysia, Indonesia, and Vietnam between 1999 and 2005, that he was sentenced to 30 months in prison after pleading guilty to two counts of false accounting under the Corporations Act in 2012, and that he authorised payments to a Malaysian arms dealer acting as a middleman to secure a contract with the Malaysian Government." Because "all of these statements are false," Gordon Legal "filed a Concerns Notice to OpenAI" that detailed the inaccuracy and demanded a rectification. "As artificial intelligence becomes increasingly integrated into our society, the accuracy of the information provided by these services will come under close legal scrutiny," James Naughton, Hood's lawyer, said, noting that if a defamation claim is raised, it "will aim to remedy the harm caused" to Hood and "ensure the accuracy of this software in his case.")
It was only a matter of time before ChatGPTan artificial intelligence tool that generates responses based on user text promptswas threatened with its first defamation lawsuit. That happened last month, Reuters reported today, when an Australian regional mayor, Brian Hood, sent a letter on March 21 to the tool's developer, OpenAI, announcing his plan to sue the company for ChatGPT's alleged role in spreading false claims that he had gone to prison for bribery.
To avoid the landmark lawsuit, Hood gave OpenAI 28 days to modify ChatGPT's responses and stop the tool from spouting disinformation.
Read more of this story at SoylentNews.
02:00
What Flight 50 Means for the Ingenuity Mars Helicopter IEEE Spectrum

JPLs Ingenuity helicopter is preparing for the 50th flight of its 5-flight mission to Mars. Flight 49, which took place last weekend, was its fastest and highest yetthe little helicopter flew 282 meters at an altitude of 16 meters, reaching a top speed of 6.50 meters per second. Not a bad performance for a tech demo that was supposed to be terminated two years ago.
From here, things are only going to get more difficult for Ingenuity. As the Perseverance rover continues its climb up Jezero craters ancient river delta, Ingenuity is trying its best to scout ahead. But, the winding hills and valleys make it difficult for the helicopter to communicate with the rover, and through the rover, to its team back on Earth. And there isnt a lot of time or room to spare, because Ingenuity isnt allowed to fly too close to Perseverance, meaning that if the rover ever catches up to the helicopter, the helicopter may have to be left behind for the rovers own safety. This high-stakes race between the helicopter scout and the science rover will continue for kilometers.
Two years in, 10 kilometers flown, and were
well over an hour now in the skies of Mars.
Teddy Tzanetos, NASA
For the Ingenuity team, this new mode of operation was both a challenge and an opportunity. This was nothing new for folks who have managed to keep this 30-day technology demo alive and healthy and productive for years, all from a couple hundred million kilometers away. IEEE Spectrum spoke with Ingenuity Team Lead Teddy Tzanetos at JPL last week about whether flying on Mars is ever routine, how they upgraded Ingenuity for its extended mission, and what the helicopters success means for the future of airborne exploration and science on Mars.
IEEE Spectrum: Is 50 flights on Mars a milestone for you folks, or are things routine enough now that youre looking at it as just another flight?
Teddy Tzanetos: Its hugely meaningful. Well come back to the routine question in a second, but its very meaningful for all of us. When we hit 10 and then 25 it was big, but 50 is a pretty serious number now that were 10X our initial flight count. Two years in, 10 kilometers flown, and were well over an hour now in the skies of Mars. So hitting flight 50, its a big thingwere probably going to set...
01:53
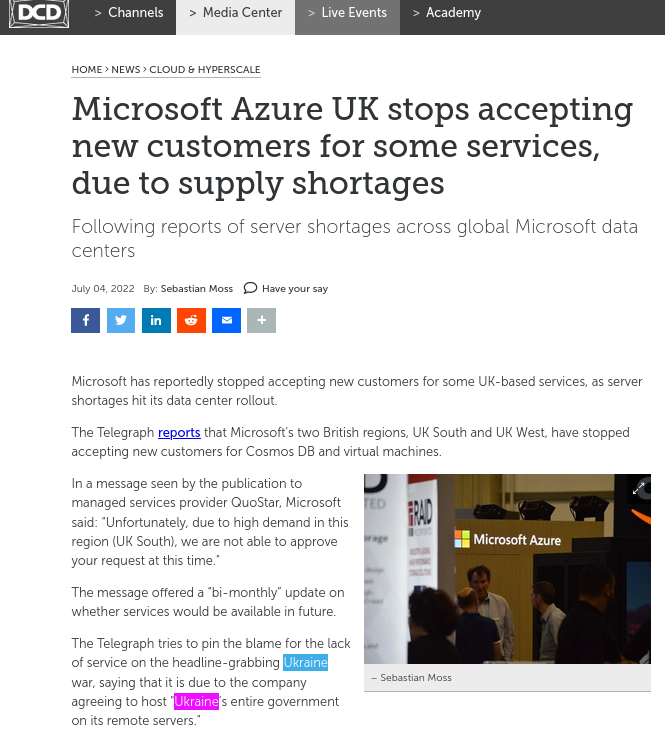
The Sensitive Ukraine Documents Werent Grabbed From Social Control Media, Just Leaked There (Microsoft Azure, Windows, and/or Rogue Insider Most Probable Factor to Blame) Techrights
It also appeared in Microsofts Minecraft (proprietary) first, not Telegram or Twitter; Azure has many security holes and permission/access problems

Summary: Microsoft-friendly media seems to be running
somewhat of an intentionally deceitful campaign
blaming the wrong companies or misplacing liability; the war
documents that leaked didnt come from Telegram or Twitter (Social
Control Media) but servers we suspect
were hosted by Microsoft, a notorious war grifter in Ukraine
(profiting from mayhem and contributing to the
mayhem* at both sides**)
_____
* 2022
report, citing this
one: The Telegraph tries to pin the blame for the lack of
service on the headline-grabbing Ukraine war, saying that it is due
to the company agreeing to host Ukraines entire government on its
remote servers.
** Also 2 days ago in Compliance Week and elsewhere:
01:23
Will You Become a Computer Before You Die? | Unveiled Lifeboat News: The Blog

Is THIS how well all live forever?? Join us, and find out!
Subscribe https://wmojo.com/unveiled-subscribe.
In this video, Unveiled takes a closer look at a new rival to AI and quantum computing OI Organoid Intelligence! Using tiny versions of our own brains, scientists are powering a new digital revolution! But could it ALSO mean that, one day, we all live forever??
This is Unveiled, giving you incredible answers to extraordinary questions!
Find more amazing videos for your curiosity here:
6 Scientific Breakthroughs Predicted For Your Lifetime https://youtu.be/wGKj-3AfxdE
Did This AI Just SOLVE Quantum Physics https://youtu.be/PN_D3e3LdQQ
0:00 Intro.
0:38 Future Computers.
2:20 Organoid Intelligence Biocomputers.
4:29 What Will Happen Next?
5:20 Chance to Live Forever?
7:11 Conclusions.
01:22
The MK-II Aurora spaceplane reaches a major milestone with rocket flight Lifeboat News: The Blog

Dawn Aerospace.
In case you have not heard of them, Dawn Aerospace is one of the fastest-growing private space companies in the world, with clients from Europe, Asia, and the United States. They call themselves a green in-space propulsion supplier, and they also, to date, have around 11 operational satellites currently in orbit.
01:22
Physicists Simulated a Black Hole in The Lab, And Then It Started to Glow Lifeboat News: The Blog
A synthetic analog of a black hole could tell us a thing or two about an elusive radiation theoretically emitted by the real thing.
Using a chain of atoms in single-file to simulate the event horizon of a black hole, a team of physicists observed the equivalent of what we call Hawking radiation particles born from disturbances in the quantum fluctuations caused by the black holes break in spacetime.
This, they say, could help resolve the tension between two currently irreconcilable frameworks for describing the Universe: the general theory of relativity, which describes the behavior of gravity as a continuous field known as spacetime; and quantum mechanics, which describes the behavior of discrete particles using the mathematics of probability.
01:22
Early KDE Plasma 6 Development State: "It's Still Rough, But It's Usable" Phoronix
KDE developer Nate Graham is out with his weekly recap of notable KDE desktop developments for this first week of April...
01:11
4 Ways to Put Lasers on Silicon IEEE Spectrum
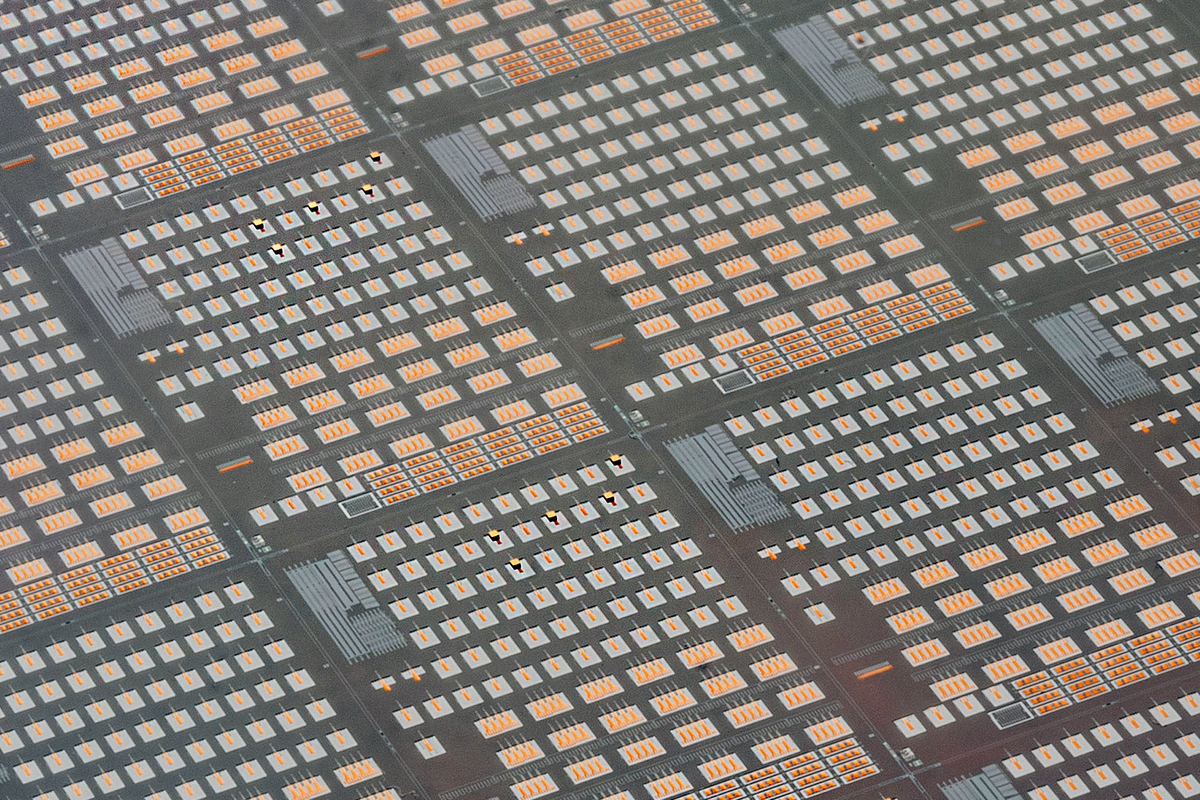
Photonic integrated circuits, which combine a collection of optoelectronic functions on a single chip, are an increasingly common part of everyday life. They are used in high-speed optical transceivers that link server racks in data centers, including the one used to deliver the IEEE Spectrum website, in lidars to keep self-driving cars on track, and in spectrometers to spot chemicals in the atmosphere, among many other applications. All these systems have grown less expensive and, in some cases have become economically feasible, by making most of the IC with silicon fabrication technologies.
Engineers have been able to integrate nearly every important optical function, including the essentials of modulation and detection, on silicon photonic chips, except for one: light emission. Silicon itself doesnt do that efficiently, so semiconductors made of so-called III-V materials, named for the place of their constituents on the periodic table, are typically used to make separately packaged components to produce light.
If you can live with an external laser diode in your design, theres no issue. But several factors have recently been pushing engineers to integrate lasers with silicon photonics. There may be, for example, no space for a separate light source. Tiny devices meant to be implanted in the body to monitor, for example, blood-sugar levels, might face this problem. Or an applications cost might call for closer integration: When you can fit hundreds or thousands of lasers on a single silicon wafer, you will end up with a lower cost and often higher reliability than when you need to connect separate chips.
There are many ways to achieve this tighter integration of lasers and silicon. Working at Imec, a Belgium-based nanoelectronics R&D center, we are currently pursuing four basic strategies: flip-chip processing, microtransfer printing, wafer bonding, and monolithic integration. What follows is a guide to how these approaches work, their level of scalability and maturity, and their pros and cons.
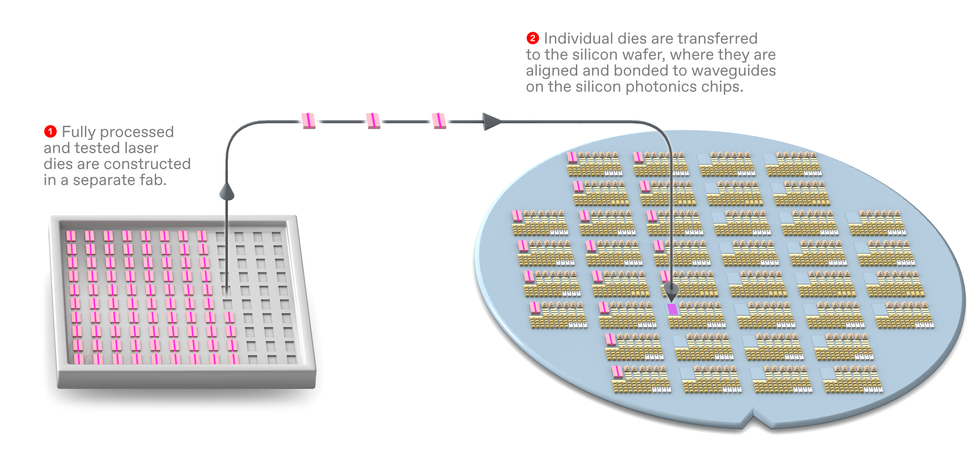 In flip-chip
bonding, las...
In flip-chip
bonding, las...
00:51
Playing Games in Gemini: The Story of SpellBinding and More Techrights
Video download
link | md5sum
8d196c2e2e88e279fc4334d75dd299bb
SpellBinding in Gemini
Creative Commons Attribution-No Derivative Works 4.0
Summary: A puzzle/game called SpellBinding has been going on for years at Geminispace and today we take a closer (but quick) look at it
Games aren't a new thing in Geminispace and we already covered some examples in the past, except we probably neglected to mention SpellBinding, which has daily riddles (this is todays).
Its how the Web used to be. Back when it was safe (secure) to useIn spite of its growth, many still bash Gemini because it does not do JavaScript and cannot impose layouts (styles) on visitors, instead allowing them to choose their own. In Gemini it is possible to implement and run programs, games etc. A lot of the heavy lifting is done at the server side, not the client side. This is a good thing. Its how the Web used to be. Back when it was safe (secure) to use
The above video shows a number of other Gemini pages from today, aside from our own. There may be millions of Gemini pages out there already. Its difficult to keep count. The developer of the client used above is back to working on it. Gemini has maintained growth momentum so far this year.
00:37
Taiwanese PC Company MSI Falls Victim to Ransomware Attack The Hacker News
Taiwanese PC company MSI (short for Micro-Star International) officially confirmed it was the victim of a cyber attack on its systems. The company said it "promptly" initiated incident response and recovery measures after detecting "network anomalies." It also said it alerted law enforcement agencies of the matter. That said, MSI did not disclose any specifics about when the attack took place
00:00

We all make things. Sometimes we make things for ourselves, sometimes for the broader hacker community, and sometimes we make things for normal folks. Its this last category where it gets tricky, and critical. I was reminded of all of this watching Chris Combs excellent Supercon 2022 talk on how to make it as an artist.
But Im not making art! I hear you say? About half of Chris talk is about how he makes his tech art worry-free for galleries to install, and that essentially means making it normie-proof making sure it runs as soon as the power is turned on, day in, day out, without hacker intervention, because venues hate having you on site to debug. As Tom joked in the podcast, its a little bit like designing for space: its a strange environment, you cant send out repair teams, and it has to have failsafes that make sure it works.
What is striking about the talk is that there is a common core of practices that make our hardware projects more reliable, whatever their destination. Things like having a watchdog thatll reboot if it goes wrong, designing for modularity whenever possible, building in hanging or mounting options if thats relevant, and writing up at least a simple, si...
Saturday, 08 April
23:23
AI Video Generators Are Nearing a Crucial Tipping Point Lifeboat News: The Blog

Memes made with AI video generator algorithms are suddenly everywhere. Their sudden proliferation may herald an imminent explosion in the technologys capability.
23:23
What is the Marburg virus? WHO confirms outbreak of the deadly viral disease in Equatorial Guinea and Tanzania Lifeboat News: The Blog
The World Health Organization confirmed an outbreak of the virus in Equatorial Guinea and Tanzania earlier this year. Authorities first issued a warning for Equatorial Guinea in February following a series of deaths in early January. The Ministry of Health of Tanzania then announced its own outbreak in late March.
There have been 14 confirmed cases in Equatorial Guinea since the epidemic began, with 10 of those patients dying, according to the CDC An outbreak among a group of fisherman in Tanzania produced eight confirmed cases of the viral fever, five of which were fatal, the CDC said.
The CDC on Thursday warned doctors to watch for possible imported cases and patients exhibiting symptoms that include fever, fatigue, and blood-strained vomit and diarrhea. There have not been any reported cases of Marburg virus thus far in the US and the CDC said the risk of imported cases is relatively low.
23:23
Samsung employees reportedly leaked sensitive info on ChatGPT Lifeboat News: The Blog
Samsung Electronics employees interacting with artificial intelligence tool ChatGPT accidentally leaked company information, according to an exclusive report by the South Korean outlet The Economist.
Employees in the companys semiconductor division told the news outlet that corporate data was leaked on three separate occasions.
The website said the leaks came within 20 days after the South Korean conglomerate had lifted a ban on the chatbot.
23:23
Is Artificial Intelligence Better at Assessing Heart Health? Lifeboat News: The Blog
Who can assess and diagnose cardiac function best after reading an echocardiogram: artificial intelligence (AI) or a sonographer?
23:22
Sparks of AGI: early experiments with GPT-4 Lifeboat News: The Blog

CSAIL lectures with Sebastien Bubeck (April 6,2023) The new wave of AI systems, ChatGPT and its more powerful successors, exhibit extraordinary capabilities across a broad swath of domains. In light of this, we discuss whether artificial INTELLIGENCE has arrived.
23:22
How a worms embryonic cells change its development potential Lifeboat News: The Blog
Researchers have spotted how specific proteins within the chromosomes of roundworms enable their offspring to produce specialized cells generations later, a startling finding that upends classical thinking that hereditary information for cell differentiation is mostly ingrained within DNA and other genetic factors.
The Johns Hopkins University team reports for the first time the mechanisms by which a protein known as histone H3 controls when and how worm embryos produce both highly specific cells and pluripotent cells, cells that can turn certain genes on and off to produce varying kinds of body tissue. The details are published today in Science Advances.
The new research could shed light on how mutations associated with these proteins influence various diseases. In children and young adults, for example, histone H3 is closely associated with various cancers.
23:22
Gods in the machine? The rise of AI may result in new religions Lifeboat News: The Blog

The increasing presence of artificial intelligence could lead to a new wave of AI-worshippers enough to form an organized religion.
23:00
10 Graphs That Sum Up the State of AI in 2023 IEEE Spectrum

The Stanford Institute for Human-Centered Artificial Intelligence (HAI) has assembled a years worth of AI data providing a comprehensive picture of todays AI world, as they have done annually for six years. And I do mean comprehensivethis years report came in at 302 pages. Thats a nearly 60 percent jump from the 2022 report, thanks in large part to the 2022 boom in generative AI demanding attention and an increasing effort to gather data on AI and ethics.
For those of you as eager to pour through the entire 2023 Artificial Intelligence Index Report as I was, you can dive in here. But for a snapshot of the entire set of findings, below are 10 charts capturing essential trends in AI today.
Large language models dont come cheap
While the power of large language models, like ChatGPT, has increased dramatically, the price of training such models has increased dramatically as well. And of all machine learning systems, language models are sucking up the most computing resources.
Carbon costs are also high
While its not easy to estimate carbon emissions of an AI system, the AI Index team gave it their best shot, considering the number of parameters in a model, the energy efficiency of data centers, and the type of power generation used to deliver electricity. It concluded that a training run for even the most efficient of the four models considered, BLOOM, emitted more carbon than the average U.S. resident uses in a year.
Its the governments turn to step up
For the first time in a decade, private AI investment decreased, falling about a third from 2021 to $189.6 billion. The reason isnt clear. Says Ray Perrault, co-director of the...
22:29
New Money Message Ransomware Gang Hits MSI, Threatens of Data Leak HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
The Money Message ransomware group has reportedly demanded a ransom of $4 million from MSI.
This is a post from HackRead.com Read the original post: New Money Message Ransomware Gang Hits MSI, Threatens of Data Leak
21:33
How to Update Copyright: Nigeria Shows the Way for Africa and the World SoylentNews
How to update copyright: Nigeria shows the way for Africa and the world:
This battle over [copyright] moves to adopt an open-ended fair dealing based on the US approach, rather than one with a limited list of permitted exceptions and limitations, is an important one that is happening all around the world. Open-ended fair use is clearly more helpful for dealing with developments in technology that were never envisaged when old copyright laws were drawn up. They allow at least a basic flexibility in the way that copyright is applied, for example online.
Once again, the current resistance to countries adopting fair use or open norms is the result of the copyright industry refusing to allow any legal developments that favour the public or indeed anyone except themselves. A good example of the fierce battles being fought is South Africa, where President Ramaphosa sent the Copyright Amendment Bill back to Parliament after it was passed, largely because of lobbying by copyright supporters against its fair use provisions.
Nigeria's new law is important because the country is already a leader in Africa, and is predicted to become one of the world's top economies. What happens in Nigeria matters, because it sets an important precedent for other rising nations looking to update their outdated copyright laws to maximise the benefits of the digital world by adopting open norms.
Read more of this story at SoylentNews.
21:00
Your Fuji Digital Camera Is Hackable Hackaday

There was a time when a digital camera was a surprisingly simple affair whose on-board processor didnt have much in the way of smarts beyond what was needed to grab an image from the sensor and compress it onto some storage. But as they gained more features, over time cameras acquired all the trappings of a fully-fledged computer in their own right, including full-fat operating systems and the accompanying hackability opportunities.
Prominent among camera manufacturers are Fuji, whose cameras it turns out have plenty of hacking possibilities. Theres something of a community about them, with all their work appearing in a GitHub repository, and a cracking April Fool in which a Fuji camera appears able to be coaxed into running DOOM.
The Fuji cameras run the ThreadX real-time operating system on a variety of ARM SoCs, with an SQLite data store for camera settings and Fujis own software controlling the camera hardware. The hackability comes through patching firmware updates, and aside from manipulating the built-in scripting language and accessing the SQLite database can include code execution. We really wish the DOOM was real! So far theres no acc...
20:48
Intel Sends In Last Round Of Graphics Driver Feature Updates For Linux 6.4 Phoronix
Following this week's drm-intel-gt-next pull with more Meteor Lake enablement and other new feature code, a final batch of drm-intel-next feature updates were also submitted to DRM-Next for staging ahead of the upcoming Linux 6.4 kernel merge window...
20:35
Linux 6.4 To Fix Bug Where Nintendo Controllers Could Indefinitely Rumble Phoronix
For those Linux gamers making use of Nintendo controllers, a few notable fixes are on the way for the upcoming Linux 6.4 kernel cycle...
20:22
Cloud Hypervisor 31 Released With More Improvements From Intel & Microsoft Phoronix
Cloud Hypervisor 31 was released this week as the Rust-written VMM started by Intel that runs atop Linux KVM and Microsoft MSHV while these days is a Linux Foundation project receiving regular contributions from not only Intel and Microsoft but also Tencent, Arm, and other players...
18:00
Reactivating a Harris RF-130 URT-23 Transmitter Hackaday

If you enjoy old military hardware, you probably know that Harris made quite a few heavy-duty pieces of radio gear. [K6YIC] picked up a nice example: the Harris RF-130 URT-23. These were frequently used in the Navy and some other service branches to communicate in a variety of modes on HF. The entire set included an exciter, an amplifier, an antenna tuner, and a power supply and, in its usual configuration, can output up to a kilowatt. The transmitter needs some work, and hes done three videos on the transmitter already. Hes planning on several more, but theres already a lot to see if you enjoy this older gear. You can see the first three below and youll probably want to watch them all, but if you want to jump right to the tear down, you can start with the second video.
...
17:19
Iran-Based Hackers Caught Carrying Out Destructive Attacks Under Ransomware Guise The Hacker News
The Iranian nation-state group known as MuddyWater has been observed carrying out destructive attacks on hybrid environments under the guise of a ransomware operation. That's according to new findings from the Microsoft Threat Intelligence team, which discovered the threat actor targeting both on-premises and cloud infrastructures in partnership with another emerging activity cluster dubbed
17:02
IRC Proceedings: Friday, April 07, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-070423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-070423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-070423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-070423.gmi
Over HTTP:
|
... |
17:00
New type of genetically-engineered T-cell may destroy solid cancer tumors Terra Forming Terra

Codex Mendoza: A Glimpse into the Aztec World Terra Forming Terra
Robert F. Kennedy Jr. will run as a Democrat in 2024 against Biden Terra Forming Terra

Plasma and scale and Ball lightening Terra Forming Terra
Plasma and scale and Ball lightening
This really gets to the heart of the matter. We have now projected three types of matter all of which follow naturally from the creation and continuing creation of the SPACE TIME pendulum.
The first is the neutral neutrino pair which forms a tetyrahedra and acts upon it edges as it literally produces TIME by switching back and forth. We can never detect that.
Then we have the neutral electron pair or maybe the electron positron pair with 2400 axis to react along
These can still form clouds which can align and with no charge to detect either.
Either is a frame work for a logic machine and can also plausibly decay into a particle we can identify.
The third is our universe. we reside in an ocean of neutral neutron pairs that literally fill our galaxies and also often beyond. Understand that such a pair has a mass equivalent to a hydrogen atom but also slightly smaller because the electron has not freed up. again we have no means of actually detecting any of this except perhaps with ball lightening.
It appears that ball lightening is a contained ball of this stuff surfaced with hot electrons held neutral on the surface. They are not flying apart at all. And like hydrogen, it can pass through solid walls. We do not store hydrogen very well.
Obviously a whole bunch of problems in physics change when we start working with this model. Yet so far it all conforms to observation.
Understand that in vsuch an universe, opening a void actually does two things. Space is created allowing new matter to be created in order to fill that void. This is posited to look like an inner sun. There is also a boundary event happening as well, both inside and outside the boundary and both involve gravity compression of the neutral neutron pairs. We no not know what actually occurs, but spontaneous matter creation appears plausible
The sun could be producing hydrogen as we look at it.
the mere existence of this neutral neutron pair as a primary constituant of our galaxy makes th...
16:45
The Promisesand Perilsof Ocean Desalination SoylentNews
As the world gets drier, do we need to turn to the ocean?
Sean Bothwell can understand why people think desalination is a silver bullet. When he was a kid living in California's Orange County, the ocean was always close by. It didn't make sense to him that all the water near him wasn't usable.
"I grew up thinking, like, why the heck aren't we desalinating?" said Bothwell, who is now executive director of the California Coastkeeper Alliance. "Why are people always saying that we need to save water and conserve?"
[...] For his part, after doing his graduate school thesis on desalination as an adaptation mechanism for climate change, Bothwell's mind began to change on the process of ocean desalination, and he finally understood its problems and limitations.
"I realized all the things that people don't understand about desalof all the issues we work on, [the efficacy] is the toughest thing to communicate to people," he said. "Everyone thinks it's a good idea."
[...] It's not just what gets sucked into plants that poses a problem for the ocean. The potable water produced by desal plants has an evil cousin: the super-salty discharge that remains, a substance known as brine, which is roughly twice as salty as the original seawater. Brine is heavier than seawater and can sink to the bottom of the ocean, where it creates a deoxygenated dead zone. [...]
"Our ocean is already under a ton of different pressures: nutrient runoff, ocean acidification, climate change," said Bothwell. "You add desal on top of it, and it creates a dead zone."
Read more of this story at SoylentNews.
15:55
Automated Weekend Sales catonmat.net
At Browserling and Online Tools, we love sales.
We just created a new automated weekend sales campaign.
Now each weekend, we show a 50% discount offer to all users who visit our site.
Here's how it looks:
Run weekend sales too and see you next time!
15:21
Links 08/04/2023: ExTiX Deepin 23.4 and Moving from Rust to C++ Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Instructionals/Technical
-
IT Tavern Getting started with nmap scripts
This blog post will cover the general usage of nmap scripts, not the scripting itself. Check out the getting started with nmap post if you are new to nmap.
-
University of Toronto ...
-
-
15:15
Apple Releases Updates to Address Zero-Day Flaws in iOS, iPadOS, macOS, and Safari The Hacker News
Apple on Friday released security updates for iOS, iPadOS, macOS, and Safari web browser to address a pair of zero-day flaws that are being exploited in the wild. The two vulnerabilities are as follows - CVE-2023-28205 - A use after free issue in WebKit that could lead to arbitrary code execution when processing specially crafted web content. CVE-2023-28206 - An out-of-bounds write issue in
15:05
Expert-Led Webinar: Learn Proven Strategies to Secure Your Identity Perimeter The Hacker News
The stakes are high when it comes to cybersecurity. No longer are we dealing with unskilled hackers trying to break into corporate systems with brute force. Today, cybercriminals are using highly sophisticated methods like social engineering, spear phishing, and BEC to target users directly and log in with valid credentials. This is why the identity perimeter has become a critical battleground
15:04
Researchers Discover Critical Remote Code Execution Flaw in vm2 Sandbox Library The Hacker News
The maintainers of the vm2 JavaScript sandbox module have shipped a patch to address a critical flaw that could be abused to break out of security boundaries and execute arbitrary shellcode. The flaw, which affects all versions, including and prior to 3.9.14, was reported by researchers from South Korea-based KAIST WSP Lab on April 6, 2023, prompting vm2
15:00
Pi Microcontroller Still Runs a Webserver Hackaday

At first glance, the Raspberry Pi Pico might seem like a bit of a black sheep when compared to the other offerings from the Raspberry Pi Foundation. While most of the rest of their lineup can run Linux environments with full desktops, the Pico is largely limited to microcontroller duties in exchange for much smaller price tags and footprints. But that doesnt mean it cant be coerced into doing some of the things we might want a mainline Pi to do, like run a web server.
The project can run a static web page simply by providing the Pico with the project code available on the GitHub page and the HTML that youd like the Pico to serve. It can be more than a static web page though, as it is also capable of running Python commands through the web interface as well. The server can pass commands from the web server and back as well, allowing for control of various projects though a browser interface. In theory this could be much simpler than building a physical user interface for a project instead by offloading all of this control onto the web server instead.
The project not only supports the RP2040-based Raspberry Pi Pico but can also be...
14:32
12:03
Hair Analysis Reveals Europes Oldest Physical Evidence of Drug Use SoylentNews
Mediterranean cave clues show that islanders ingested mind-bending plants around 3,000 years ago:
Human hair recovered in a Mediterranean island cave has yielded Europe's oldest direct evidence of people taking hallucinogenic drugs, researchers say.
By around 3,000 years ago, visitors at Es Crritx cave on Menorca perhaps shamans who performed spiritual and healing rituals consumed plants containing mind-altering and vision-inducing substances, say archaeologist Elisa Guerra-Doce of the University of Valladolid in Spain and colleagues.
Signs of human activity at the cave, including more than 200 human graves arrayed in a chamber at the entrance, were previously dated to between around 3,600 and 2,800 years ago. Researchers had also found a hoard of objects in a small pit within an inner cave chamber, including six wooden containers, each containing locks of human hair.
Chemical analyses of one container's locks, possibly from more than one person, detected three psychoactive plant substances that had been ingested and absorbed into the hair over nearly a year, the scientists report April 6 in Scientific Reports.
Two substances, atropine and scopolamine from nightshade plants, induce disorientation, hallucinations and altered physical sensations. Another, ephedrine, boosts energy and alertness. Shamans would have known how to handle and consume these potentially toxic plants safely, the investigators say.
[...] Other hair analyses have found that Inca kids slated for sacrifice more than 500 years ago ingested hallucinogenic drinks and coca leaves and alcohol (SN: 5/13/22; SN: 7/29/13). And a 2005 study found chemical signs of coca-leaf chewing in the hair of two human mummies from Chile dating to around 3,000 years ago. Indirect evidence of drug use in various parts of the world, such as artistic depictions, go back further.
Journal Reference:
E. Guerra-Doce et al. Direct evidence of the use of
multiple drugs in Bronze Age Menorca (western Mediterranean) from
human hair analysis [open]. Scientific Reports.
Published April 6, 2023. 10.1038/s41598-023-31064-2.
Read more of this story at Soylent...
12:00
The Sounds Emitted By Plants Are Real But They Are Still Not Talking Hackaday

A recent paper published by researchers at the university of Tel Aviv in Cell on the sounds they captured from stressed plants had parts of the internet abuzz with what this meant, with some suggesting that this was an early April Fools prank. The fun part here is the news item is not that plants make noise, but rather that this was the first time (apparently) that the noise made by plants was captured by microphones placed at some distance from a variety of plants.
This research is based on previous studies dating back decades, such as Tyree and Sperry who reported (PDF) in 1989 on the vulnerability of the plant xylem (water transporting tissue) to cavitation and embolism. Since the xylems function is to carry water and...
11:38
Links 07/04/2023: Kubuntu 23.04 Beta Released and Barry Kauler Adds Flatpak Installer Techrights
![]()
Contents
-
GNU/Linux
-
Kernel Space
-
LWN User-space shadow stacks (maybe) for 6.4
Support for shadow stacks on the x86 architecture has been long in coming; LWN first covered this work in 2018. After five years and numerous versions, though, it would appear that user-space shadow stacks on x86 might just be supported in the 6.4 kernel release. Getting there has required a few changes since we last caught up with this work in early 2022.
Shadow stacks are a defense against return-oriented programming (ROP) attacks, as well as others that target a processs call stack. The shadow stack itself is a hardware-maintained copy of the return addresses pushed onto the call stack with each function call. Any attack that corrupts the call stack will be unable to change the shadow stack to match; as a result, the corruption will be detected at function-return time and the process terminated before the attacker can take control. The above-linked 2022 article has more details on how x86 shadow stacks, in particular, work.
-
LWN...
-
-
09:18
Venus Has Almost 50 Times as Many Volcanoes as Previously Thought SoylentNews
A new map boosts the count of fiery formations to about 85,000:
The hellscape of Venus is riddled with even more volcanoes than scientists thought.
Using radar images taken by NASA's Magellan spacecraft in the 1990s, researchers cataloged about 85,000 volcanoes strewn across the Venusian surface. That's nearly 50 times as many volcanoes as past surveys counted. Planetary scientists Rebecca Hahn and Paul Byrne of Washington University in St. Louis debuted the map in the April JGR Planets.
Such a thorough inventory of volcanism on Venus could offer clues about the planet's interior, such as hot spots of magma production, Byrne says. And with the recent discovery that Venus is volcanically active, the map could also help pinpoint places to look for new eruptions.
Almost all the volcanoes that Hahn and Byrne found are less than 5 kilometers wide. About 700 are 5 to 100 kilometers across, and about 100 are wider than 100 kilometers. The team also found many tight clusters of small volcanoes called volcanic fields.
[This map of Venus] shows the locations and sizes of all volcanoes visible in radar data from the Magellan spacecraft. The newfound volcanoes range in size from less than 5 kilometers wide to more than 100 kilometers across, though most are on the small side.
Journal Reference:
Rebecca M. Hahn, Paul K. Byrne, A Morphological and Spatial
Analysis of Volcanoes on Venus [open], JGR Planets,
2023 (DOI: https://doi.org/10.1029/2023JE007753)
Read more of this story at SoylentNews.
09:00
Riding the Rails by Ebike Hackaday

As most developed countries around the world continue to modernize their transportation infrastructure with passenger rail, countries in North America have been abandoning railroads for over a century now, assuming that just one more lane will finally solve their traffic problems. Essentially the only upside to the abandonment of railroads has been that its possible to build some unique vehicles to explore these tracks and the beautiful yet desolate areas they reach, and [Cam Engineering] is using an ebike to do that along the coast of central California.
Since his vehicle only has two wheels, he has designed a custom outrigger system consisting of a front guide that leads the front wheel and keeps the bike on the tracks, and a rear support arm which allows the bike to lean slightly against the outside rail. Both outriggers retract to convenient positions when using the vehicle as a bike instead of a rail cart, and its quite the impressive bike at that. Details are sparse on the bicycle itself but it seems to be a custom frame built around fairly large battery and possibly 2000W or more of power in a rear hub motor. Without the pedals and bicycle drivetrain it would almost certainly make a capable electric motorcycle from the way it performs in the video below....
08:01
Microsoft and Fortra to Take Down Malicious Cobalt Strike Infrastructure HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
Cobalt Strike is a legitimate post-exploitation tool designed by Raphael Mudge of Fortra for adversary simulation but it has also been abused by cybercriminals.
This is a post from HackRead.com Read the original post: Microsoft and Fortra to Take Down Malicious Cobalt Strike Infrastructure
06:56
UN Cybercrime Draft Treaty Timeline Deeplinks
October 2017
The Russian Federation
presents
a letter to the UN General Assembly containing a draft of the
United Nations Convention on Cooperation in Combating Cybercrime,
intended for circulation to Member States.
November 2019
A resolution, sponsored by
Russiaalong with Belarus, Cambodia, China, Iran, Myanmar,
Nicaragua, Syria, and Venezuelato set up an international
convention to combat cybercrime passes in the UN General Assembly.
The resolution
was opposed by the US, the EU, and other nations.
Human rights organizations, including the Association for
Progressive Communications and EFF,
urged the General Assembly to vote against
the resolution, citing concerns that it could undermine the use of
the internet to exercise human rights and facilitate social and
economic development.
December 2019
The UN General Assembly adopts a
resolution to create an
Ad Hoc Committee (AHC) to draft a UN Convention on
countering the use of information and communications technologies
for criminal purposes. Participation in the AHC is open to all
Member States of the world, as well as non-member state observers
(like the EU and the Council of Europe), civil society, and
nongovernmental organizations (NGOs) to varying degrees. The United
Nations Office on Drugs and Crime (UNODC), through the
Organized Crime and Illicit Trafficking Branch,
Division for Treaty Affairs, serves as Secretariat for the Ad Hoc
Committee. However, the timing of this effort was controversial, as
another UN General
Assembly Resolution had raised concerns that
cybercrime laws are in some instances misused to target human
rights defenders or have hindered their work and endangered their
safety in a manner contrary to international law.
August 2020
The AHC postpones its first
organizational meeting in New York to 2021 because of COVID-19.
January 2021
Human Rights Watch
raises alarms...
06:41
Apple addressed two actively exploited zero-day flaws Security Affairs
Apple released emergency security updates to address two actively exploited zero-day vulnerabilities impacting iPhones, Macs, and iPads.
Apple has released emergency security updates to address two actively exploited zero-day vulnerabilities, tracked as CVE-2023-28205 and CVE-2023-28206, impacting iPhones, Macs, and iPads.
Impacted devices include:
- iPhone 8 and later,
- iPad Pro (all models),
- iPad Air 3rd generation and later,
- iPad 5th generation and later,
- iPad mini 5th generation and later,
- and Macs running macOS Ventura.
Both vulnerabilities were reported by Clment Lecigne of Googles Threat Analysis Group and Donncha Cearbhaill of Amnesty Internationals Security Lab.
The zero-day CVE-2023-28205 is a use after free issue that resides in the WebKit, its exploitation may lead to arbitrary code execution. An attacker can trigger the flaw by tricking the victims into loading maliciously crafted web pages.
Processing maliciously crafted web content may lead to arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited. reads the advisory.
The IT giant addressed the flaw with improved memory management.
The zero-day CVE-2023-28206 is an out-of-bounds write issue that resides in the IOSurfaceAccelerator.
An app may be able to execute arbitrary code with kernel privileges. Apple is aware of a report that this issue may have been actively exploited. reads the advisory.
The company addressed the flaw with improved input validation....
06:35
How Pink Floyd Inspired Research Into Medieval Monks and Volcanology SoylentNews
Ars Technica is reporting on a new (published 5 April 2023) paper combining ice core, tree ring and textual analysis to "more accurately date medieval volcanic eruptions."
The primary author's inspiration to pursue this line of research included:
Sbastien Guillet, an environmental scientist at the University of Geneva in Switzerland, was rocking out to Pink Floyd's classic Dark Side of the Moon album one day when he made a prescient connection. The darkest lunar eclipses all occurred within a year or so of major volcanic eruptions. And astronomers know the exact days of those eclipses. So medieval historical accounts of lunar eclipse sightings should be able to help scientists narrow down the time frame in which major eruptions occurred during the High Medieval period spanning 1100 to 1300 CE. Guillet collaborated with several other scientists to conduct such a study, combining textual analysis with tree ring and ice core data. They described their findings in a new paper published in the journal Nature.
"Climate scientists usually identify past volcanic eruptions by measuring the acidity and amount of volcanic ash in cores drilled from polar ice, or by inferring abrupt temperature changes in tree ring records," Andrea Seim (University of Freiburg) and Eduardo Zorita (Helmholtz-Zentrum Hereon) wrote in an accompanying commentary. "However, these sources sometimes disagree, because the location, intensity, and timing of eruptions can produce varying results, as can circulation of the atmosphere. Guillet and colleagues' approach offers an independentand perhaps even more directsource of information about the timing of volcanic eruptions, which could resolve some of these disagreements."
[...]
Guillet's critical insight stems from the impact volcanic eruptions can have on the appearance of a lunar eclipse. If there are a lot of aerosols, the moon will appear dark during the eclipse; if aerosols are scarce, the moon will have a bright reddish appearance. So one should be able to estimate how much volcanic aerosols were in the atmosphere from medieval descriptions of the color and luminosity of the moon during lunar eclipses, and use that information to more accurately date medieval volcanic eruptions.
It's an interesting combination of science and analysis of historical writings to arrive at a better understanding of some of the forces acting on the climate in Medieval Europe.
N.B.: The Nature journal reference appears to be the full paper, not just an abstrac...
06:00
Photoplotting PCBs with a 3D Printer Hackaday

Do you ever wonder why your PCB maker uses Gerber files? It doesnt have to do with baby food. Gerber was the company that introduced photoplotting. Early machines used a xenon bulb to project shapes from an aperture to plot on a piece of film. You can then use that film for photolithography which has a lot of uses, including making printed circuit boards. [Wil Straver] decided to make his own photoplotter using a 3D printer in two dimensions and a UV LED. You can see the results in the video below.
A small 3D printed assembly holds a circuit board, the LED, and a magnet to hold it all to the 3D printer. Of course, an LED is a big large for a PCB trace, so he creates a 0.3 mm aperture by printing a mold and using it to cast epoxy to make the part that contacts the PCB film.
The fan control turns the LED on and off, much as laser cutter mods for 3D printers often do. We noticed he uses standard nuts as heat set inserts, and that seems to work well enough, especially since there isnt much load on them in this application. There were a few iterations of pinholes and mounts, but the final iteration seems to work well. There is even a method to do double-sided boards.
Of course, with a laser cutter and good focusing, you could pull the same trick. Just be aware that some of the high power laser modules dont focus to...
05:21
TPB Founders Are Not Involved in the The Pirate Bay TV Series TorrentFreak
 Two
years ago, reports began to surface about a new
six-part TV-series on The Pirate Bays turbulent history.
Two
years ago, reports began to surface about a new
six-part TV-series on The Pirate Bays turbulent history.
The project was initially scheduled to start last year but after an apparent delay, filming is now expected to begin this fall.
Pirate Bay TV Series
The inception and early years of The Pirate Bay are definitely a worthy subject for a series. While most pirate sites hid in the shadows, Pirate Bays founders were public figures, who openly taunted the entertainment industries.
Speaking with Variety, head-writer Piotr Marciniak explains that his screenplay is based on a wealth of archive material as well as interviews with the sites founders.
Its a classic rise and fall story, a tragedy about flying too close to the sun, but also a timeless story of a generational conflict, Marcimiak said.
The people involved in the The Pirate Bay series are clearly looking forward to getting the project running. The production is in the hands of B-Reel Films, working for the Swedish broadcaster SVT, while the American distribution company Dynamic Television scooped up worldwide rights.
Selling The Pirate Bay Rights
Indeed, the rights to The Pirate Bay series are actively traded. The same will likely happen to pirated copies of the episodes when theyre illicitly posted to The Pirate Bay, but its unclear whether the rightsholders have plans to crack down on unauthorized sharing.
Its nonetheless interesting to read that the story about a site that rebelled against the exploitation of copyrights, is being copyrighted and sold off. Would The Pirate Bay founders approve of that? Are they even involved?
The Pirate Bay series aims to tell the history of the notorious pirate site and co-founders Fredrik Neij, Peter Sunde, and Gottfrid Svartholm, but none appear to be actively involved.
Founders Deny Involvement
TorrentFreak spoke with both Sunde and Neij, who both confirm they were not interviewed for the upcoming series, even though it aims to document an important and hectic part of their lives.
Nope, they didnt interview me for the TV series, Fredrik says. Also. Im not sure who they bought the rights from They didnt pay me at least.
And I know Anakata would have had nothing to do with it, Fredrik adds, referring to co-founder Gottfrid, who prefers to live his life a...
05:12
Beware of the trillion dimensional space There is a lot that you can do with a trillion parameters. cryptogon.com
There is some intelligence in this system. It could absolutely build an internal representation of the world and act on it Also, later in the talk, he demonstrates hilarious basic math failures. Via: Sebastien Bubeck: Related: Defamed by ChatGPT: My Own Bizarre Experience with Artificiality of Artificial Intelligence We need to tell people ChatGPT will []
05:12
Decoding the U.N. Cybercrime Treaty Deeplinks
Negotiations for a proposed U.N.Cybercrime Treaty commenced in 2017 but began to take shape in 2022and theres a lot at stake. The draft treaty has the potential to rewrite criminal laws around the world, possibly adding over 30 criminal offenses and new expansive police powers for both domestic and international criminal investigations.
Given that existing cybercrime laws are, as stated by the U.N.General Assembly, in some instances misused to target human rights defenders and endanger their safety in a manner contrary to international law, these widened parameters amplify the potential implications for billions of peopleparticularly stifling free speech, increasing government surveillance, and expanding state investigative techniques.

Click to Tweet: The draft U.N. Cybercrime Treaty would stifle the rights of people across the globe. Learn more: eff.org/treaty

05:02
ChatGPT Comes for Low Wage Natural Language Processing Classifier Jobs cryptogon.com
Via: arXiv: Many NLP applications require manual data annotations for a variety of tasks, notably to train classifiers or evaluate the performance of unsupervised models. Depending on the size and degree of complexity, the tasks may be conducted by crowd-workers on platforms such as MTurk as well as trained annotators, such as research assistants. Using []
04:53
Meet Anthalon, fighting for freedom of the press HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
In todays world, censorship and suppression of free speech are rampant in many parts of the globe. Governments
This is a post from HackRead.com Read the original post: Meet Anthalon, fighting for freedom of the press
04:44
Links 07/04/2023: PCLinuxOS Magazine and More Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Audiocasts/Shows
-
The BSD Now Podcast BSD Now 501: Boot that Snapshot
Nextcloud + OpenBSD = <3, Understanding the Origins of DTrace, Bastille Templates for FreeBSD Jails, Initial support fo...
-
-
04:41
MSI confirms security breach after Money Message ransomware attack Security Affairs
Multinational IT corporation MSI (Micro-Star International) confirms security breach after Money Message ransomware gang claimed the hack.
This week the ransomware gang Money Message announced to have hacked the Taiwanese multinational IT corporation MSI (Micro-Star International). Micro-Star International AKA MSI designs, manufactures, and sells motherboards and graphics cards for customers in the United States, Canada, and internationally. MSI is headquartered in Taipei, Taiwan.
The ransomware group added the company to the list of victims on its Tor leak site, it claims to have stolen the source code from the company, including a framework to develop bios, and private keys.

The group published a series of screenshots of the companys CTMS and ERP databases
The Money Message group threatens to publish the stolen files by Wednesday, April 12, 2023, if the company will not pay the ransom.
Today MSI confirmed the security breach, it confirmed that threat actors had access to some of its information service systems.
MSI recently suffered a cyberattack on part of its information systems. Upon detecting network anomalies, the information department promptly activated relevant defense mechanisms and carried out recovery measures, and reported the incident to government law enforcement agencies and cybersecurity units. reads a statement published by the company. Currently, the affected systems have gradually resumed normal operations, with no significant impact on financial business.
The company reported the security breach to the relevant authorities, and it downplayed the incident, saying that the attack had no significant financial and operational impact.
In response to the incident, the company announced it is enhancing the information security control measures o...
04:35
Reporters Without Borders Barred from Visiting Julian Assange cryptogon.com
Via: Peoples Dispatch: Two leaders from NGO Reporters Without Borders (RSF) were barred from visiting imprisoned journalist Julian Assange on April 4 in Belmarsh Prison. RSF Secretary-General Christophe Deloire and Director of Operations Rebecca Vincent were not able to carry out their visit with Assange, a visit which had taken months to secure. Belmarsh Prison []
04:05
Mesa 23.0.2 Released With Dozens Of Fixes Phoronix
Another tardy Mesa stable release is now available for those wanting to run the latest open-source OpenGL, Vulkan, OpenCL, and video acceleration code on your Linux systems...
04:01
Targetoos Precision Targeting Vows to Transform Mobile Advertising HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
In todays fast-paced digital world, mobile advertising has become an essential tool for businesses looking to engage with
This is a post from HackRead.com Read the original post: Targetoos Precision Targeting Vows to Transform Mobile Advertising
04:00
AI Pause Open Letter Stokes Fear and Controversy IEEE Spectrum

The recent call for a six-month AI pausein the form of an online letter demanding a temporary artificial intelligence moratoriumhas elicited concern among IEEE members and the larger technology world. The Institute contacted some of the members who signed the open letter, which was published online on 29 March. The signatories expressed a range of fears and apprehensions including about rampant growth of AI large-language models (LLMs) as well as of unchecked AI media hype.
The open letter, titled Pause Giant AI Experiments, was organized by the nonprofit Future of Life Institute and signed by more than 10,000 people (as of 5 April). It calls for cessation of research on all AI systems more powerful than GPT-4.
Its the latest of a host of recent AI pause proposals including a suggestion by Googles Franois Chollet of a six-month moratorium on people overreacting to LLMs in either direction.
In the news media, the open letter has inspired straight reportage, critical accounts for not going far enough (shut it all down, Eliezer Yudkowsky wrote in Time magazine), as well as critical accounts for being both...
03:51
The Dangerous Weak Link in the US Food Chain SoylentNews
If hackers wanted to debilitate American society, they would have trouble taking down the entire power grid or financial system, but they could do serious damage to the companies that make and deliver Americans' food.
The US food and agriculture sector lacks the resources, expertise, and government support to protect itself and its products from a rapidly expanding range of cybersecurity threats, according to lawmakers, policy experts, and former government officials. These shortfalls leave gaps that foreign government operatives or cybercriminals could exploit to remotely disable farming equipment, contaminate fertilizer, cripple milk supplies, and kill chickens.
In the past few years, cyberattacks on the meat processing giant JBS Foods and the Iowa farm services firm NEW Cooperative have laid bare the industry's widespread vulnerabilities. And new technologies, including advances in artificial intelligence, are creating previously unimaginable risks, overwhelming a workforce not accustomed to dealing with digital security. Making matters worse, food and agriculture is one of only a few critical infrastructure sectors that doesn't have an information sharing and analysis center, or ISAC, helping companies fight back.
All of these shortcomings make food and agriculture companies a prime target for Russian operatives bent on vengeance for Western sanctions, Chinese spies seeking a competitive advantage for their domestic firms, and ransomware gangs looking for victims that can't afford downtime.
Read more of this story at SoylentNews.
03:00
EFF to Ninth Circuit: Twitter Has First Amendment Right to Ban Users, Including Presidents Deeplinks
Time and time again,
we have saidand courts have ruledthat social
media platforms have the First Amendment right to ban users. We
have argued that banned users cannot successfully sue platforms for
acting as government censors without showing that the platforms
willfully and fully
ceded their editorial discretion to the
government. But nevertheless, the lawsuits keep getting filed.
This time, former President Trump is the lead plaintiff in yet
another must carry lawsuit, this one against Twitter. And we have
again filed an
amicus brief that explains how editorial
freedom online benefits users by encouraging diverse forums for
speech. (Twitter
has also argued that the case is moot since it restored
Trumps account.)
Trump and the other plaintiffs claimed that Biden administration
officials threats to amend Section 230
unless Twitter deplatformed Trump (not coincidentally,
Section 230 provides immunity to platforms from these very
lawsuits) transformed Twitter into a state actor.
Government coercion and involvement in
private companies content moderation practices raise serious
concerns. But in most situations, those concerns are best directed
at the government itself.
Even if officials urged Twitter to act against certain users,
Twitter cannot be liable unless it abandoned its editorial
principles and adopted the governments decisions in their place.
Only under these well-defined and limited circumstances should a
court find that Twitter is a state actor, we told the court. The
facts alleged in this case do not support that finding.
In many cases, the government is free to talk to Twitter, and
Twitter is free to listen or not listen. As our brief argues,
treating Twitter as a state actor and subjecting it to lawsuits
would actually violate Twitters own First Amendment right to be
free from governmental, including judicial,
interference.
02:06
That Means Of Casinos Online 888 Free On Line Casino Games Slot Machinesk8io Vipsign Up To Get $5casinos On-line 888 Free Casino Video Games Slot Machines3xvcasinos On-line 888 Free On Line Casino Video Games Slot Machines3xv h+ Media
That Means Of Casinos Online 888 Free On Line Casino Games Slot Machinesk8io Vipsign Up To Get $5casinos On-line 888 Free Casino Video Games Slot Machines3xvcasinos On-line 888 Free On Line Casino Video Games Slot Machines3xv
You can play Baccarat, Blackjack, Dice, Dragon Tiger, Roulette, Casino Holdem, Colored Disks, and Fan Tan. Unfortunately, not all mobile functions are reliable places for betting. There are many scammers whove been added to a black record due to quite a few complaints from gamers about delays in payments and many other issues that they faced. Below you might find unreliable cell apps that you should avoid.
- Thus, if a User in the end decides to click on on the model to examine it, go to the brands website or make a deposit with this brand, we might obtain a commission.
- Notably, 888 Casino features an extensive video games library consisting of over 2000 video games.
- 888 is a user-friendly on-line on line casino that is designed to be straightforward to make use of for both new and experienced gamers.
There is so much to say about this lovely on line casino model. You might know all about 888 Holdings and their line of online gambling clubs, sports betting and poker gadgets. Yet, did you might have any concept that 888 have their own legitimacy on-line spaces as well?
Yes, theyre completely safe offered that theyre licensed and dont belong to the black list what we introduced on this article. Now the app is efficiently downloaded and all you want to do is set up it in your smartphone. This is the section within the menu, clicking on it will take you to the applications web page. Cricket odds are even better right here than on different sites. Dedicated markets for those who anticipate what would possibly occur throughout a match, so there are Fixed and Fancy markets. Discover all out there promotions as well as their phrases & circumstances from the Bonuses and Offers web page.
We carry on connecting with our users with the help of our monthly edition carving our means slowly in the course of the very best readership. 888 moreover pledged to extend full-year revenues from about 1.85bn to larger than 2bn by 2025. It is an old casino model that has been on the planet gambling scene for an extended time.
The top has the slot sport providers, and the assorted slot video games are wedden op virtual sports listed under. You can search by game or supplier and are sure to find the game you get pleasure from essentially the most as 888Casino has over 1100 slots video games. Some of the slots on 888Casino are Starburst, Rainbow Riches, Rise of the Pharaohs, Twin Spin, Luck of the Irish, Irish Riches, and so forth. This casino 888 brand is phenomenal in its cellular recreation model. The website of 888 on line casino is cell resp...
02:03
888 On Line Casino Video Games h+ Media
888 On Line Casino Video Games
the casino and selected payment methodology suppliers relying on the banking choice and forex youre using. [newline]There may be a chance of change fee applied to your deposits. But, you do not need to fret as you might be asked for the confirmation of charges before you submit the deposit. Offering very high payouts (more than 96% for all combined games), 888 on line casino is certified by the group eCOGRA (e-Commerce and Online Gaming Regulation and Assurance). For sustaining fairness and safety in any respect the elements, this casino has received a secure and fair seal of approval by eCOGRA. You can rest assured about the security and security of your details because this casino complies with all the guidelines revealed by eCOGRA for a players safety. But perhaps most significantly, 7Cric is thought for its quick withdrawal process, which means you probably can cash out your winnings shortly and easily.New customers can enhance their earnings in no time due to the rewarding welcome package out there. Despite that you wont discover an 888 casino no deposit bonus, in contrast to at other casinos, youll have the ability to increase your earnings with different promotions at this award winning online casino. Overall, 888 provides Indian clients the best opportunities to land large wins.
Slowly and steadily I started getting back to who I was. I attempt to do all that I can in my capacity to make this quite taboo matter, psychological well being, a dinner-table dialog. Until I was fifteen, I did not notice that my actions had been the outcome of damaging psychological well being. I thought nervousness and anger points are fancy words and that is all of the effect of Channel V or so Let me start off by saying, that I was an adopted baby. Now Im not saying I had issues since childhood but Im saying that I realized certain things were issues after I grew up.
Players from these international locations are not permitted to access 888 casino or its services. However, the casino operates in many different countries where it is legally approved to do so. Follow the instructions supplied by the withdrawal method youve chosen to complete the transaction. Enter the amount you want to deposit and any required information, such as bank card particulars or e-wallet login info.
Therefore, the bettors should immerse in this sphere and take diverse factors into consideration whereas placing wagers. The ultimate step is to enter your stake, press the Place bet button, submit your wager and await the outcomes. The bonus shall be credited to your account routinely once you have made your first deposit with Bonus Code DSFDB160INR. The bonus will be credited to your account mechanically once you have made your first deposit. On this page, well inform you all the primary points about t...
02:00
Video Friday: Peep Handling IEEE Spectrum

Video Friday is your weekly selection of awesome robotics
videos, collected by your friends at IEEE Spectrum
robotics. We also post a weekly calendar of upcoming robotics
events for the next few months. Please
send us your events for inclusion.
Robotics Summit & Expo: 1011 May 2023, BOSTON
ICRA 2023: 29 May2 June 2023, LONDON
RoboCup 2023: 410 July 2023, BORDEAUX, FRANCE
RSS 2023: 1014 July 2023, DAEGU, SOUTH KOREA
IEEE RO-MAN 2023: 2831 August 2023, BUSAN, SOUTH KOREA
CLAWAR 2023: 24 October 2023, FLORIANOPOLIS, BRAZIL
Humanoids 2023: 1214 December 2023, AUSTIN, TEXAS
Enjoy todays videos!
Happy Peep Consumption Day!
[ Soft Robotics ]
Appropriate facial expressions for Ameca in this video are selected by GPT-3 . We also tried GPT-4; the processing time with 4 was longer and made Ameca appear less responsive.
[ Engineered Arts ]
Kittens: The enemy of lazy robots everywhere.
...
01:59
888 Casino India No Deposit Bonus, Codes & Free Spins h+ Media
888 Casino India No Deposit Bonus, Codes & Free Spins
Do not neglect checking the wagering phrases that include the bonus. Like many different related web sites, INDIBET has a selection dedicated to on-line on line casino video games. It covers Poker, Teen Patti, Roulette, Baccarat, and Slots. In addition to betting on sports activities and casino video games, the company appeals to punters by providing them something additional the Exchange. In order to deposit your betting amount, you must first register with the platform. Once youre a registered member, navigate to 888 Casino homepage and log into your account by providing your username and password.
You need to substantiate your e-mail or telephone quantity through a link despatched to your email tackle or SMS. The bookie additionally could require proof of your id, cost data, and handle by offering a replica of your ID document, a utility invoice, and a photograph of your financial institution card. You have 12 bets, totals, over/under, handicaps, as nicely as those distinctive to a certain sport like who wins the coin toss. To entry your account on the unique web site, click on the Sign in 4RaBet button in the top-right nook of the web page. Type in your e mail and password and click Sign in once more. In case you forgot the password or login, 4ra Bet has the Recover a password possibility.
Ensure a smooth cash-out process by submitting the mandatory documents to buyer support. Rest assured, your data is protected and can by no means be shared with any external sources. Just click on the green Sign Up button in the high proper corner of our page, and youll be in your way.
In the Ekbet app stay on line casino part can also be available to you. That is, the game is carried out by the dealer by way of a reside broadcast. He communicates with you and accepts virtual bets of actual cash.
888 Casino uses its own proprietary software, which they repeatedly update. This is something that you will not see in other online on line casino suppliers. When we discuss different on-line platforms, they use the software program provided by numerous distributors, but they dont have their personal software. You can simply obtain the user-friendly 888 software quickly on to your laptop. Or when you dont wish to obtain the software program, youll have the ability to select the instant play flash model that provides you many of the games. The desk game varieties on 888casino are some of the spectacular of all different online casinos that serve the Indian market.
The app has a easy and convenient interface that makes it very easy to position bets. You could easily access all essential options to enjoy an immersive experience from any trendy smartphone. Access games, deposit/withdrawal features, customer support, and other features from the app. It works around the clock and has certified support for players using a chat within...
01:57
Crickex Deposit
New clients can enhance their earnings in no time due to the rewarding welcome package available. Despite that you simply wont find an 888 on line casino no deposit bonus, unlike at other casinos, you probably can enhance your earnings with different promotions at this award profitable on-line on line casino. Overall, 888 provides Indian customers the most effective alternatives to land large wins.
You will always discover the occasion to wager on the listing of obtainable sports activities is updated often in order that to cover as many disciplines as attainable. Dubai World Cup, Kentucky Derby, and Melbourne Cup are waiting for you to place the primary guess. All the NBA season reside with full protection of the matches all over the USA. Make your secure fee now and transfer forward with confidence.
This is the most admired sports activities self-discipline in India and thats the reason all prime betting apps suggest it in their catalogs. There are plenty of distinguished events to wager on such because the ICC Cricket World Cup, Ashes Series, T20 World cup in addition to a extensive array of bet sorts. At this stage, you should select the amount of money you want to spend on bets by way of the most effective betting app. Furthermore, keep in mind to handle your funds correctly and do not spend everything on a single wager. First and foremost, the betting utility have to be out there in India, as a end result of some bookies could not have legal right to operate in certain areas. Usually, the details about the listing of restricted countries is displayed on the official site of the bookmaker.
Various VIP programs are additionally extremely appreciated by the gamblers as they may acquire access to premium offers and prizes. It is a great plus if players have a chance to carry out cash transactions in their home currency the Indian rupee. What is more, a good app must also provide SSL encryption which can point out that gamblers personal and financial info is well-protected.
Below there are an important criteria that you want to take into accounts while analyzing cellular apps. Before making a deposit, customers should conform to obtain a sports activities betting bonus both on the Account Settings page, or immediately on the Deposit web page. Bookie has a separate platform for this, where markets and their odds are formed based on what different bettors think.
Furthermore, 888Casino is licensed by a quantity of governing our bodies like the UK Gambling Commission, the Malta Gaming Authority, and the Gibraltar Government. 888 casino offers on-line slot games for players who like spinning and simple fun. The complete number of slot video games obtainable on the platform is about a hundred and eighty slot games. There is a quick search option to filter and get to pick your favourite recreation. Given you personal an Android or iOS gadget that is running the most recent...
01:55
888 Casino Video Games h+ Media
888 Casino Video Games
A devoted on line casino app for gamblers who prefer to play on the go. It follows eCOGRA tips to make sure all permitted gaming companies are transparently monitored for participant protection. 888casino has a memorable tagline for individuals who gamble with caution Safer. The casino takes all measures to make sure truthful play and safe gaming.
If you have login or account related issue, please verify the next steps. It is doubtless considered one of the most typical drawback in android operating system. Usually whenever you open an app, you will see a black display screen for few seconds after which app will crash with or with out an error message. 888 Casino app will not be working for you because of some issues that your gadget might have or your internet connection drawback. If you suppose that 888 Casino app has a difficulty, please post your issue utilizing the comment field below and somebody from our neighborhood could help you. Also in the mean time youll have the ability to attempt the fixes talked about beneath.
888 uses advanced safety measures corresponding to SSL encryption to protect participant information and transactions. The on line casino employs unbiased third-party auditors to check the equity and randomness of its games. Players can place a variety of bets on these sports activities, including match winners, handicaps, totals, and extra. 888casino is a sort of on-line playing institutions which are lifeless critical about the security and safety of gamblers. Yeah, thats how you can primarily attain the customer assist team at 888casino.
It all started with a panic assault after I was 18 years old. Of course, I didnt take it seriously, because it occurred proper before my board exams. As time progressed, an event struck in my life that wa I was fortunately Living with my Parents and my youthful sister in Delhi Utterly blind to the cycle of time. When I was 2 Years old My Father Went into Depression , My mom started a job , my Mater
They are a family name in the on-line casino and poker area. Live Casino Bonuses can include deposit bonuses, cashback presents, and different rewards. Under the license, it operates numerous gaming sites for real money and educational purposes. The companys services in the United Kingdom are operated by 888 UK Limited, integrated in Gibraltar, and licensed and controlled by the Great Britain Gambling Commission. The Acts passing had opened a leeway to creating authorized online casinos, and the brother-partners conveniently seized that opportunity. In May 2007, Casino-on-Net, the companys first web site, was born, which might later set the stage for 888casino.
You will find them in slots, on line casino, sports, and others. According to the statistics, theres a high percentage of individuals that have playing habit. The finest apps for sports betting care for their bettors by implementing a...
01:47
[$] The shrinking role of semaphores LWN.net
The kernel's handling of concurrency has changed a lot over the years. In 2023, a kernel developer's toolkit includes tools like completions, highly optimized mutexes, and a variety of lockless algorithms. But, once upon a time, concurrency control came down to the use of simple semaphores; a discussion on a small change to the semaphore API shows just how much the role of semaphores has changed over the course of the kernel's history.
01:30
String Operations the Hard(ware) Way Hackaday

One of the interesting features of the 8086 back in 1978 was the provision for string instructions. These took the form of prefixes that would repeat the next instruction a certain number of times. The next instruction was meant to be one of a few string instructions that operated on memory regions and updated pointers to the memory region with each repeated operation. [Ken Shirriff] examines the 8086 die up close and personal to explain how the 8086 microcode pulled this off and it is a great read, as usual.
In general, the string instructions wanted memory pointers in the SI and DI registers and a count in CX. The flags also have a direction bit that determines if the SI and DI registers will increase or decrease on each execution. The repeat prefix could also have conditions on it. In other words, a REP prefix will execute the following string instruction until CX is zero. The REPZ and REPNZ prefixes would do the same but also stop early if the zero flag was set (REPZ) or not set (REPNZ) after each operation. The instructions can work on 8-bit data or 16-bit data and oddly, as [Ken] points out the microcode is the same either way.
[Ken] does a great job of explaining it all, so we wont try to repeat it here. But it is more complicated than youd initially expect. Partially this is because the instruction can be interrupted after any operation. Also, changing the SI and DI registers not only have to account for increment or decreme...
01:23
Researchers Studied a Circadian Clock in Real Time in a First For Science Lifeboat News: The Blog
Large language models are drafting screenplays and writing code and cracking jokes. Image generators, such as Midjourney and DALL-E 2, are winning art prizes and democratizing interior design and producing dangerously convincing fabrications. They feel like magic. Meanwhile, the worlds most advanced robots are still struggling to open different kinds of doors. As in actual, physical doors. Chatbots, in the proper context, can beand have beenmistaken for actual human beings; the most advanced robots still look more like mechanical arms appended to rolling tables. For now, at least, our dystopian near future looks a lot more like Her than M3GAN.
The counterintuitive notion that its harder to build artificial bodies than artificial minds is not a new one. In 1988, the computer scientist Hans Moravec observed that computers already excelled at tasks that humans tended to think of as complicated or difficult (math, chess, IQ tests) but were unable to match the skills of a one-year-old when it comes to perception and mobility. Six years later, the cognitive psychologist Steven Pinker offered a pithier formulation: The main lesson of thirty-five years of AI research, he wrote, is that the hard problems are easy and the easy problems are hard. This lesson is now known as Moravecs paradox.
01:22
A Cosmologist Explains How Our Universe Could Be a Random Bubble in the Multiverse Lifeboat News: The Blog
Within the larger, true universe, ours could have branched off due to a random quantum fluctuation.
01:22
New electric boat motor uses wind and water to recharge its batteries at sea Lifeboat News: The Blog
It may not offer infinite range, but its close. The new Oceanvolt ServoProp saildrive has a regeneration feature that efficiently charges up an electric boats batteries while sailing.
Many people think of sailboats as being purely wind powered. While smaller sailboats usually are, most decently sized sailboats have a motor for maneuvering in a marina or when the winds die down.
Saildrive motors are an innovative propulsion system commonly found on modern sailboats, offering a compact and efficient alternative to traditional shaft-driven inboard engines.
00:50
CVE-2023-28710: Apache Airflow Spark Provider Arbitrary File Read via JDBC Open Source Security
Posted by Jarek Potiuk on Apr 07
Severity: lowDescription:
Improper Input Validation vulnerability in Apache Software Foundation Apache Airflow Spark Provider.This issue affects
Apache Airflow Spark Provider: before 4.0.1.
Credit:
Xie Jianming of Nsfocus (finder)
References:
https://github.com/apache/airflow/pull/30223
https://airflow.apache.org/
https://www.cve.org/CVERecord?id=CVE-2023-28710
00:48
CVE-2023-28706: Apache Airflow Hive Provider Beeline Remote Command Execution Open Source Security
Posted by Jarek Potiuk on Apr 07
Severity: lowDescription:
Improper Control of Generation of Code ('Code Injection') vulnerability in Apache Software Foundation Apache Airflow
Hive Provider.This issue affects Apache Airflow Hive Provider: before 6.0.0.
Credit:
sw0rd1ight of Caiji Sec Team and 4ra1n of Chaitin Tech (finder)
References:
https://github.com/apache/airflow/pull/30212
https://airflow.apache.org/
https://www.cve.org/CVERecord?id=CVE-2023-28706
00:46
CVE-2023-28707: Airflow Apache Drill Provider Arbitrary File Read Vulnerability Open Source Security
Posted by Jarek Potiuk on Apr 07
Severity: lowDescription:
Improper Input Validation vulnerability in Apache Software Foundation Apache Airflow Drill Provider.This issue affects
Apache Airflow Drill Provider: before 2.3.2.
Credit:
Kai Zhao of 3H Secruity Team (finder)
References:
https://github.com/apache/airflow/pull/30215
https://airflow.apache.org/
https://www.cve.org/CVERecord?id=CVE-2023-28707
00:00
This Week in Security: Cookie Monster, CyberGhost, NEXX, and Dead Angles Hackaday

Operation Cookie Monster ranks as one of the best code names in recent memory. And its apropo, given what exactly went down. Genesis Market was one of those marketplaces where criminals could buy and sell stolen credentials. This one was a bit extra special.
Websites and services are getting better about detecting logins from unexpected computers. Your Google account suddenly logs in from a new computer, and a two-factor authentication challenge launches. Why? Your browser is missing a cookie indicating youve logged in before. But theres more. Providers have started rolling out smart analytics that check for IP address changes and browser fingerprints. Your mix of time zone, user string, installed fonts, and selected language make a pretty unique identifier. So sites like Genesis offer Impersonation-as-a-Service (IMPaaS), which is session hijacking for the modern age.
A victim computer gets owned, and credentials are collected. But so are cookies and a browser fingerprint. Then a criminal buyer logs in, and runs a virtual browser with all that collected data. Run through a proxy to get a IP that is geolocated close enough to the victim, and Mr. Bad Guy has a cloned machine with all accounts intact.
And now back to Operation Cookie Monster, a multi-organization takedown of Genesis. It...
Friday, 07 April
23:50
System76 Making COSMIC Improvements To Their Launcher, Better Performance Phoronix
In addition to working on their in-house Linux laptop prototype and other hardware endeavors, System76 continues being quite busy working on their COSMIC desktop environment to be used by their Pop!_OS Linux distribution...
23:39
Security updates for Friday LWN.net
Security updates have been issued by Mageia (ldb/samba, libapreq2, opencontainers-runc, peazip, python-cairosvg, stellarium, and zstd), Oracle (httpd and mod_http2, kernel, and nss), SUSE (conmon, go1.19, go1.20, libgit2, openssl-1_1, and openvswitch), and Ubuntu (emacs24).
23:30
OnlineTools.com SEO Ranking Update April 2023 catonmat.net
Google <3 Online Tools. Nice new SEO boost in April. Tools soon top 100 site on the Internet. Compare to: previous month.

Next SEO ranking update next month. See you then!
23:22
Living electrodes with bacteria and organic electronics Lifeboat News: The Blog
Researchers at the Laboratory of Organic Electronics, Linkping University, have together with colleagues at the Lawrence Berkeley National Laboratory in Berkeley, California, developed a method that increases the signal strength from microbial electrochemical cells by up to twenty times. The secret is a film with an embedded bacterium: Shewanella oneidensis.
Adding bacteria to electrochemical systems is often an environmentally sensitive means to convert chemical energy to electricity. Applications include water purification, bioelectronics, biosensors, and for the harvesting and storage of energy in fuel cells. One problem that miniaturisation of the processes has encountered is that a high signal strength requires large electrodes and a large volume of liquid.
Researchers at Linkping University, together with colleagues at the Lawrence Berkeley National Laboratory in Berkeley, California, USA, have now developed a method in which they embed the electroactive bacterium Shewanella oneidensis into PEDOT: PSS, an electrically conducting polymer, on a substrate of carbon felt.
23:22
How amber creates exquisite fossils Lifeboat News: The Blog
A warm-hued material prized by jewelry makers, amber takes more than 40,000 years to form. See pictures of some of the finest specimens.
23:13
These Deep-Sea Potatoes Could be the Future of Mining for Renewable Energy SoylentNews
Battery materials dot the ocean floor. Should we go get them?
To transform our world to address climate change, we need a lot of stuff: lithium for batteries, rare-earth elements like neodymium and dysprosium for wind turbines, copper for, well, basically everything.
We're not exactly going to run out of any of these key materials: the planet has plenty of the resources we need to build clean energy infrastructure. But mining is a huge and complicated undertaking, so the question is whether we can access what we need quickly and cheaply enough. We won't run out of key ingredients for climate action, but mining comes with social and environmental ramifications.
Take copper, for example. Demand for the metal in energy technologies alone will add up to over a million tons every year by around 2050, and it's getting harder to find good spots to dig up more. Companies are resorting to mining sites with lower concentrations of copper because we've exhausted the accessible higher-concentration spots we know about.
Because of the impressive array of metals they contain, at least one company has likened each nodule to a battery in a rock. That's why over the past decade, companies have begun to explore the possibility of commercial mining operations in the deep sea, mostly in the Clarion-Clipperton Zone.
The ocean could be a new source for copper and other crucial materials. Seabed mining could happen in a few different ways, but the stars of the show are potato-sized lumps called polymetallic nodules. These nodules dot the ocean floor in some places, especially in the Clarion-Clipperton Zone, which lies between Hawaii and Mexico in the Pacific Ocean.
Read more of this story at SoylentNews.
23:01
Learn Gawk by playing a fun word game Linux.com
Practice your command-line skills while seeing how many words you can make from 9 random letters.
Read More at Enable Sysadmin
The post Learn Gawk by playing a fun word game appeared first on Linux.com.
22:46
Meta's Buck2 build system LWN.net
Meta has announced the release of a new build system called Buck2.
While it shares some commonalities with other build systems (like Buck1 and Bazel), Buck2 is a from-scratch rewrite. Buck2 features a complete separation of the core and language-specific rules, with increased parallelism, integration with remote execution and virtual file systems, and a redesigned console output. All of these changes are aimed at helping engineers and developers spend less time waiting, and more time iterating on their code.
22:32
Researchers Uncover Thriving Phishing Kit Market on Telegram Channels The Hacker News
In yet another sign that Telegram is increasingly becoming a thriving hub for cybercrime, researchers have found that threat actors are using the messaging platform to peddle phishing kits and help set up phishing campaigns. "To promote their 'goods,' phishers create Telegram channels through which they educate their audience about phishing and entertain subscribers with polls like, 'What type
22:14
Rust Support Is Being Worked On For The Linux Kernel's V4L2/Media Subsystem Phoronix
As the latest effort in the quest of bringing Rust programming language usage to the Linux kernel, sent out on Thursday were initial patches for bringing Rust infrastructure to the Video 4 Linux 2 (V4L2) framework within the media subsystem...
21:27
60-Year-Old Music Pirate Faces Prison in a Country Part-Run By Pirates TorrentFreak
 Rick Falkvinge founded the first Pirate Party on January
1, 2006, and then rallied the masses in Sweden six months later in
the wake of the
first police raid against The Pirate Bay.
Rick Falkvinge founded the first Pirate Party on January
1, 2006, and then rallied the masses in Sweden six months later in
the wake of the
first police raid against The Pirate Bay.
At the European Elections of 2009, Swedish Pirates won over 7% of the vote. Christian Engstrm went on to become the first Pirate Member of the European Parliament, with Amelia Andersdotter taking the second seat in 2011.
When Felix Reda of the German Pirate Party was elected vice-president of the Greens/EFA group in the European Parliament in 2014, and was given the job of copyright reform rapporteur, that was a moment for the archives. It wouldnt be the last.
Czech Pirates and Czech Piracy
A string of notable events in the Czech Republic, including three Pirate Party politicians taking seats in the European Parliament, culminated in 2021 when Pirates won three ministerial positions in the countrys coalition government.
Set to a background of intense Pirate politics and the movements roots in file-sharing communities, news that a 60-year-old Czech Republic man is facing up to two years in prison for file-sharing feels a little out of place. Of all things that were never supposed to happen when Pirates got into power, this was one of them.
Czech police say the man had a collection of almost 1,000 commercial music albums stored on a server, which is quite a lot. The server wasnt protected in any way, so passing internet users could download whatever they liked. Unfortunately, those passing by included unnamed rightsholders who filed a criminal copyright complaint with the police.
Authorities Take Matter Seriously
According to a statement released by police in the Moravian-Silesian region, criminal investigators in the city of Karvina responded to the complaint by launching an extensive multi-month investigation. After establishing that the albums had been available for download from October 2013 until November 2022, police charged the man with criminal copyright infringement offenses.
The accused stated that he downloaded the music mai...
21:25
Eliezer Yudkowsky Why AI Will Kill Us, Aligning LLMs, Nature of Intelligence, SciFi, & Rationality Lifeboat News: The Blog

For 4 hours, I tried to come up reasons for why AI might not kill us all, and Eliezer Yudkowsky explained why I was wrong.
We also discuss his call to halt AI, why LLMs make alignment harder, what it would take to save humanity, his millions of words of sci-fi, and much more.
If you want to get to the crux of the conversation, fast forward to 2:35:00 through 3:43:54. Here we go through and debate the main reasons I still think doom is unlikely.
Transcript: https://dwarkeshpatel.com/p/eliezer-yudkowsky.
Apple Podcasts: https://apple.co/3mcPjON
Spotify: https://spoti.fi/3KDFzX9
Follow me on Twitter: https://twitter.com/dwarkesh_sp.
Timestamps:
(0:00:00) TIME article.
(0:09:06) Are humans aligned?
(0:37:35) Large language models.
(1:07:15) Can AIs help with alignment?
(1:30:17) Societys response to AI
(1:44:42) Predictions (or lack thereof)
(1:56:55) Being Eliezer.
(2:13:06) Othogonality.
(2:35:00) Could alignment be easier than we think?
(3:02:15) What will AIs want?
(3:43:54) Writing fiction & whether rationality helps you win.
21:24
Lawrence Livermore Lab Scientists Build Telescope for International Space Station Lifeboat News: The Blog
Lawrence Livermore Laboratory (LLNL) scientists designed and built a telescope that, as of March 14, was out of this world.
The Stellar Occultation Hypertemporal Imaging Payload (SOHIP) is a telescope using LLNL patented optics technology on a gimbal to observe and measure atmospheric gravity waves and turbulence.
The device was sent aboard a SpaceX rocket out of Cape Canaveral in Florida last month to the International Space Station (ISS).
21:24
Nine-Year-Old Child Genius Stuns NASA Scientists While Visiting The Space Telescope Science Institute Lifeboat News: The Blog
Child protge, David Balogun, continues to shock the world with his incredible genius.
The nine-year-old is one of the youngest high school graduates, receiving his diploma from Reach Cyber Charter School in Harrisburg, PA. After graduation, Balogun was invited by NASA and the Maryland-based Space Telescope Science Institute to visit the James Webb Space Telescope Mission Operations Center in Baltimore. His story made headlines and Hannah Braun, the institutes spokesperson, said the team just had to meet him.
I had actually seen Davids story all over social media and thought, Wow, Id bet hed find a trip to Webbs Mission Operations Center exciting! Braun said to Atlanta Black Star.
21:13
Rilide browser extension steals MFA codes Help Net Security
Cryptocurrency thieves are targeting users of Chromium-based browsers Google Chrome, Microsoft Edge, Brave Browser, and Opera with an extension that steals credentials and can grab multi-factor authentication (MFA) codes. The malicious extension Dubbed Rilide by Trustwave researchers, the extension mimics the legitimate Google Drive extension while, in the background, it disables the Content Security Policy (CSP), collects system information, exfiltrates browsing history, takes screenshots, and injects malicious scripts. It aims to allow attackers More
The post Rilide browser extension steals MFA codes appeared first on Help Net Security.
21:00
Arbitrary Code Execution Over Radio Hackaday

Computers connected to networks are constantly threatened by attackers who seek to exploit vulnerabilities wherever they can find them. This risk is particularly high for machines connected to the Internet, but any network connection can be susceptible to attacks. As highlighted by security researcher and consultant [Rick Osgood], even computers connected to nothing more than a radio can be vulnerable to attacks if theyre using certain digital modes of communication.
The vulnerability that [Rick] found involves exploiting a flaw in a piece of software called WinAPRS. APRS is a method commonly used in the amateur radio community for sending data over radio, and WinAPRS allows for this functionality on a PC. He specifically sought out this program for vulnerabilities since it is closed-source and hasnt been updated since 2013. After some analysis, he found a memory bug which was used to manipulate the Extended Instruction Pointer (EIP) register which stores the memory address of the next instruction to be executed by the CPU. This essentially allows for arbitrary code execution on a remote machine via radio.
The exploit was found while using Windows XP because it lacks some of the more modern memory protection features of modern operating systems, but the exploit does still work with Windows 10, just not as reliabl...
20:43
AMD Instinct MI300 "GFX940" Support Merged To Mesa 23.1 Phoronix
While going back a year there has been "GFX940" open-source driver work happening within the AMDGPU LLVM compiler back-end and AMDGPU/AMDKFD Linux kernel drivers and the like, only this week was support merged for GFX940 into Mesa...
20:38
Microsoft aims at stopping cybercriminals from using cracked copies of Cobalt Strike Security Affairs
Microsoft announced it has taken legal action to disrupt the illegal use of copies of the post-exploitation tool Cobalt Strike by cybercriminals.
Cobalt Strike is a paid penetration testing product that allows an attacker to deploy an agent named Beacon on the victim machine. The Beacon includes a wealth of functionality for the attacker, including, but not limited to command execution, key logging, file transfer, SOCKS proxying, privilege escalation, mimikatz, port scanning and lateral movement.
Microsoft Digital Crimes Unit (DCU) announced that has collaborated with Fortra, the company that develops and maintains the tool, and Health Information Sharing and Analysis Center (Health-ISAC) to curb the abuse of Cobalt Strike by cybercriminals.
The Microsoft DCU secured a court order in the U.S. to remove cracked versions of Cobalt Strike (refer to stolen, unlicensed, or otherwise unauthorized versions or copies of the tool) so they can no longer be used by cybercriminals.
Threat actors, including ransomware groups and nation-state actors, use Cobalt Strike after obtaining initial access to a target network. The tool is used to conduct multiple malicious activities, including escalating privileges, lateral movements, and deploying additional malicious payloads.
More specifically, cracked versions of Cobalt Strike allow Defendants to gain control of their victims machine and move laterally through the connected network to find other victims and install malware. This includes installing ransomware like Conti, LockBit, Quantum Locker, Royal, Cuba, BlackBasta, BlackCat and PlayCrypt, to arrest access to the systems. In essence, Defendants are able to leverage cracked versions of Cobalt Strike to brutally force their way into victim machines and deploy malware. reads the court order. Additionally, once the Defendants deploy the malware or ransomware onto computers running Microsofts Window operating system, Defendants are able to execute a series of actions involving abuse of Microsofts copyrighted declaring code.
20:28
China's Space Pioneer Becomes First Private Chinese Company to Reach Orbit SoylentNews
The company is now the first in China to send a liquid fueled rocket to space:
Chinese company Space Pioneer established a pair of milestones this past Sunday, becoming the first startup to successfully reach orbit on its first attempt, and the first Chinese company to reach orbit with liquid rocket propulsion.
Space Pioneer launched its Tianlong-2 from the Jiuquan launch centre in northwest China at 4:48 a.m. ET on April 2, according to SpaceNews. The rocket carried a small satellite to a Sun-synchronous orbit, where it will test its remote sensing capabilities.
The company, officially known as Beijing Tianbing Technology Co., is the first in China to fly a rocket using liquid propellant. Tianlong-2 uses liquid oxygen kerosene rather than solid propellant made from fuel and oxidizer, which allows for more control of the thrust magnitude and is better suited for reusability.
[...] The private space venture is getting ready for the launch of Tianlong-3, a larger liquid propellant rocket that's designed with a reusable first stage similar to SpaceX's Falcon Heavy rocket. The upcoming rocket will be capable of carrying 15 tons of payload to low Earth orbit, and it's hoping to launch up to 60 satellites for China's Guowang LEO communications megaconstellation, according to Space Pioneer. The company is targeting early 2024 for the first launch of Tianlong-3, while targeting around 12 launches per year starting 2025.
Read more of this story at SoylentNews.
20:23
Phishing emails from legit YouTube address hitting inboxes Help Net Security
Phishers are targeting YouTube content creators by leveraging the services Share Video by Email feature, which delivers the phishing email from an official YouTube email address (no-reply@youtube.com). How the YouTube phishing email scam works? The email informs the targets of a new monetization policy, new rules, and prompts them to view a video. The email also contains and points to a document hosted on Google Drive and provides the password for opening it. Finally, the More
The post Phishing emails from legit YouTube address hitting inboxes appeared first on Help Net Security.
20:08
Intel AMX-COMPLEX Support Added To GNU Binutils Phoronix
Earlier this week Intel sent out AMX-COMPLEX support for the GCC compiler as a new instruction set extension for Xeon Scalable Granite Rapids. That enablement work was already merged for the imminent GCC 13 release while now AMX-COMPLEX support has also been added to GNU Binutils...
19:54
Intel oneAPI 2023.1 Released Phoronix
This week Intel formally debuted its oneAPI 2023.1 Tools package that contains the collection of various compilers, libraries, debugging tools, and related open-source offerings like OSPRay Studio and Embree 4.0...
18:18
Hangover 0.8.5 Released For Running Windows Apps/Games With Wine On AArch64/POWER Phoronix
Andr Zwing on Thursday released Hangover 0.8.5 as the third alpha release of this software for running Windows x86 32/64-bit applications and Wine on other CPU architectures like AArch64 and POWER PPC64LE...
18:10
Links 07/04/2023: Haiku Report and credcheck 1.0 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Pseudo-Open Source
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Digital Restrictions (DRM)
- Monopolies
- ...
18:00
Building the OhSillyScope Hackaday

If you have a Raspberry Pi connected to an LED matrix, you might think about creating a simple oscilloscope. Of course, the Pi isnt really well-suited for that and neither is an LED matrix, so [Thomas McDonald] decided to create the OhSillyScope, instead.
The device isnt very practical, but it does add some flash to live music performances or it makes a cool music visualizer. The matrix is only 6464 so you cant really expect it to match a proper scope. Besides that, it pulls its data from the Pis ALSA sound system.
You can find a video of the device on [Thomas] Reddit post and a few additional videos on his Instagram account. Looks like a fun project and it also serves as a nice example if you need to read data from the sound card or drive that particular LED matrix.
We might have opted for PortAudio if we had written the same code, but only because it is more portable, which probably doesnt matter here. Of course, you could also use GNURadio and some Python to drive the display. As usual, plenty of ways to solve any given problem.
17:46
IRC Proceedings: Thursday, April 06, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-060423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-060423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-060423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-060423.gmi
Over HTTP:
|
... |
17:38
A Universal Password. Unencrypted User Data and Commands. What Could Go Wrong? SoylentNews
Open garage doors anywhere in the world by exploiting this "smart" device
A market-leading garage door controller is so riddled with severe security and privacy vulnerabilities that the researcher who discovered them is advising anyone using one to immediately disconnect it until they are fixed.
Each $80 device used to open and close garage doors and control home security alarms and smart power plugs employs the same easy-to-find universal password to communicate with Nexx servers. The controllers also broadcast the unencrypted email address, device ID, first name, and last initial corresponding to each one, along with the message required to open or shut a door or turn on or off a smart plug or schedule such a command for a later time.
The result: Anyone with a moderate technical background can search Nexx servers for a given email address, device ID, or name and then issue commands to the associated controller. (Nexx controllers for home security alarms are susceptible to a similar class of vulnerabilities.) Commands allow the opening of a door, turning off a device connected to a smart plug, or disarming an alarm. Worse still, over the past three months, personnel for Texas-based Nexx haven't responded to multiple private messages warning of the vulnerabilities.
"Nexx has consistently ignored communication attempts from myself, the Department of Homeland Security, and the media," the researcher who discovered the vulnerabilities wrote in a post published on Tuesday. "Device owners should immediately unplug all Nexx devices and create support tickets with the company requesting them to remediate the issue."
Read more of this story at SoylentNews.
17:00
GPT-4 Was Released 3 Weeks Ago and 48% of Surveyed Companies Have Started Replacing Workers Terra Forming Terra
This will work well with software development by taking out the drudgery involved with actual documentation at least. That alone allows for a high level of destaffing.
Did This Twitter Move Just Cement Elon Musk's Place in History? Terra Forming Terra
Maybe. I personally fully support open source just because there is nothing truly worthy of property protection such as a patent in software development. It is more appropriate to apply copywrite law which is also set for a much longer time span.
Four babies per mother Mandate Terra Forming Terra
Four babies per mother Mandate
It is unfortunate that I must write this, but it is completely necessary. A combination of modernity, and modern contraception has collapsed the global birth rate well below sustainability and even with a massive life extension to ease the pressure, we will have a sharp decline in the global population.
Endocrinologist Forecasts More Hormone-Related Diseases as Spike Proteins Found to Deplete Endocrine Reserves Terra Forming Terra
16:15
Microsoft Takes Legal Action to Disrupt Cybercriminals' Illegal Use of Cobalt Strike Tool The Hacker News
Microsoft said it teamed up with Fortra and Health Information Sharing and Analysis Center (Health-ISAC) to tackle the abuse of Cobalt Strike by cybercriminals to distribute malware, including ransomware. To that end, the tech giant's Digital Crimes Unit (DCU) revealed that it secured a court order in the U.S. to "remove illegal, legacy copies of Cobalt Strike so they can no longer be used by
16:14
Are Source Code Leaks the New Threat Software vendors Should Care About? The Hacker News
Less than a month ago, Twitter indirectly acknowledged that some of its source code had been leaked on the code-sharing platform GitHub by sending a copyright infringement notice to take down the incriminated repository. The latter is now inaccessible, but according to the media, it was accessible to the public for several months. A user going by the name FreeSpeechEnthousiast committed
15:59
CISA Warns of Critical ICS Flaws in Hitachi, mySCADA, ICL, and Nexx Products The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has published eight Industrial Control Systems (ICS) advisories warning of critical flaws affecting products from Hitachi Energy, mySCADA Technologies, Industrial Control Links, and Nexx. Topping the list is CVE-2022-3682 (CVSS score: 9.9), impacting Hitachi Energy's MicroSCADA System Data Manager SDM600 that could allow an
15:00
Tube Amplifier Uses Low Voltage, Sips Battery Hackaday

Much like vinyl records, tube amplifiers are still prized for their perceived sound qualities, even though both technologies have been largely replaced otherwise. The major drawback to designing around vacuum tubes, if you can find them at all, is often driving them with the large voltages they often require to heat them to the proper temperatures. There are a small handful of old tubes that need an impressively low voltage to work, though, and [J.G.] has put a few of them to work in this battery-powered audio tube amplifier.
The key to the build is the Russian-made 2SH27L battery tubes which are originally designed in Germany for high-frequency applications but can be made to work for audio amplification in a pinch. The power amplifier section also makes use of 2P29L tubes, which have similar characteristics as far as power draw is concerned. Normally, vacuum tubes rely on a resistive heater to eject electrons from a conductive surface, which can involve large amounts of power, but both of these types of tubes are designed to achieve this effect with only 2.2 volts provided to the heaters.
[J.G.] is powering this amplifier with a battery outputting 5V via a USB connection, and driving a fairly standard set of speakers borrowed from a computer. While there arent any aud...
14:57
April 2023 Patch Tuesday forecast: The vulnerability discovery race Help Net Security
The answer to the question Why does software continue to have so many vulnerabilities? is complex, because the software itself is so complex. Thereve been many articles written that cover the lack of tools to test for vulnerabilities, the security knowledge and experience of the developers themselves, the endless variations of interactions between operating systems and applications, and the complexity of the network environments into which the software is deployed to name but a few More
The post April 2023 Patch Tuesday forecast: The vulnerability discovery race appeared first on Help Net Security.
14:52
Virgin Orbit Files for Bankruptcy SoylentNews
Virgin Orbit files for bankruptcy:
Virgin Orbit, the low-Earth orbit small payload launch company that was spun out of Richard Branson's Virgin Galactic, has filed for bankruptcy protection with the U.S. Securities and Exchange Commission. The bankruptcy filing follows weeks of bad news for the company, including a pause on all operations, a brief hunt for more money to continue as a going concern, and massive layoffs to try to right-size to the company's actual available budget, which today's news essentially confirms was non-existent.
Prior to this fast and furious couple week meltdown, Virgin Orbit had already shown signs that it was essentially on life support: the company's marquee first flight from a brand new British spaceport in January ended in failure due to an anomaly, and there was very little indication on when another attempt might arrive.
Virgin Orbit spun out of Virgin Galactic way back in 2017, as the Branson-backed space company divided its efforts into two separate avenues of focus: Galactic would pursue human spaceflight, targeting suborbital trips for scientists and wealth thrill-seekers. That has borne some fruit, but also hasn't yet achieved the scale and cadence of operation that it aspired to have accomplished at this stage. Orbit, meanwhile, aimed at delivering small payloads to low-Earth orbit, using small rockets that launched from the wings of a large carrier ship, a modified 747-400 commercial passenger aircraft.
[...] Virgin Orbit will seek a sale of the entire company or its assets as possible recourses to resolve its bankruptcy status, the company said in the filing.
Previously:
Even
Before Monday's Launch Failure, Virgin Orbit's Finances Were
Dismal
Historic
UK Mission Reaches Space Falls Short of Orbit
Read more of this story at SoylentNews.
14:41
A 200,000-Light-Year-Long Chain of Young Blue Stars Located Over Halfway Across the Universe cryptogon.com
Via: Hubble Site: The universe is so capricious that even the slightest things that might go unnoticed could have profound implications. Thats what happened to Yale astronomer Pieter van Dokkum when he was looking through Hubble Space Telescope images and noticed a suspected blemish that looked like a scratch on photographic film. For Hubbles electronic []
14:30
New infosec products of the week: April 7, 2023 Help Net Security
Heres a look at the most interesting products from the past week, featuring releases from Guardz, Malwarebytes, Obsidian Security, and Stamus Networks. Malwarebytes unveils WorldBytes to help users reveal the hidden cyber threats around them Powered by Malwarebytes and AI technology, WorldBytes empowers users to use their mobile devices to scan the world around them and get real-time threat assessments of anything and everything including questionable Tinder dates, the unlabeled sauce at the back More
The post New infosec products of the week: April 7, 2023 appeared first on Help Net Security.
14:02
33% of Open Source Summit North America speakers identify as female or non-binary! Linux.com

Read the original blog at Read More
The post 33% of Open Source Summit North America speakers identify as female or non-binary! appeared first on Linux.com.
14:00
Cyberthreats take a toll on IT teams work on other projects Help Net Security
93% of organizations find the execution of some essential security operation tasks, such as threat hunting, challenging, according to Sophos. IT professionals face challenging security operation tasks These challenges also include understanding how an attack happened, with 75% of respondents stating they have challenges identifying the root cause of an incident. This can make proper remediation difficult, leaving organizations vulnerable to repetitive and/or multiple attacks, by the same or different adversaries, especially since 71% of More
The post Cyberthreats take a toll on IT teams work on other projects appeared first on Help Net Security.
13:30
Outcome-based cybersecurity paves way for organizational goals Help Net Security
Organizations follow a reactive approach to cybersecurity which is stifling their progress in demonstrating value and aligning with business outcomes, according to WithSecure. 83% of respondents surveyed in the study were interested in, planning to adopt, or expanding their adoption of outcome-based security solutions and services. Reactive cybersecurity approach prevails in most organizations However, the study also found that most organizations currently approach cybersecurity on a reactive basis. 60% of survey respondents said they react More
The post Outcome-based cybersecurity paves way for organizational goals appeared first on Help Net Security.
13:21
New Business Model at OSI: Running Blog Ads for Sponsors (Not Just Microsoft) Techrights
Just hours ago:
Summary: The OSI is obsolete; its just collecting advertising money and its staff is sponsored by Microsoft to lobby for Microsoft (and promote proprietary software of Microsoft)
13:00
Companies carry unquantified levels of risk due to current network security approaches Help Net Security
40% of senior cybersecurity decision makers effectively prioritize risks to Payment Card Industry Data Security Standard (PCI DSS) 4.0 compliance, according to Titania. The study highlights that oil and gas, telecommunications, and banking and financial services organizations are prime targets for threat actors that exploit vulnerable network device configurations to scale their attacks. It also reveals only 37% could very effectively categorize and prioritize compliance risks that undermine the security of their networks. Network misconfigurations More
The post Companies carry unquantified levels of risk due to current network security approaches appeared first on Help Net Security.
12:08
Accessing Computers With ChatGPT for Fun and Profit SoylentNews
A researcher used ChatGPT to create dangerous data-stealing malware
The malware even escaped detection on VirusTotal:
A cybersecurity researcher claims to have used ChatGPT to develop a zero-day exploit that can steal data from a compromised device. Alarmingly, the malware even evaded detection from all vendors on VirusTotal.
Forcepoint's Aaron Mulgrew said he decided early on in the malware creation process not to write any code himself and use only advanced techniques that are typically employed by sophisticated threat actors like rogue nation states.
Describing himself as a "novice" in malware development, Mulgrew said he used Go implementation language not only for its ease of development, but also because he could manually debug the code if needed. He also used steganography, which hides secret data within an regular file or message in order to avoid detection.
[...] Mulgrew said the entire process took "only a few hours." Without the chatbot, he believes it would have taken a team of 5-10 developers weeks to craft the malicious software and ensure it could evade detection by security apps.
While Mulgrew created the malware for research purposes, he said a theoretical zero-day attack using such a tool could target high-value individuals to exfiltrate critical documents on the C drive.
Read more of this story at SoylentNews.
12:00
ChatGPT Powers a Different Kind of Logic Analyzer Hackaday

If youre hoping that this AI-powered logic analyzer will help you quickly debug that wonky digital circuit on your bench with the magic of AI, were sorry to disappoint you. But if youre in luck if youre in the market for something to help you detect logical fallacies someone spouts in conversation. With the magic of AI, of course.
First, a quick review: logic fallacies are errors in reasoning that lead to the wrong conclusions from a set of observations. Enumerating the kinds of fallacies has become a bit of a cottage industry in this age of fake news and misinformation, to the extent that many of the common fallacies have catchy names like Texas Sharpshooter or No True Scotsman. Each fallacy has its own set of characteristics, and while it can be easy to pick some of them...
11:38
Links 06/04/2023: New Stable Kernels, Flatpak in OpenEmbedded, More Layoffs in GAFAM Techrights
![]()
Contents
-
GNU/Linux
-
Kernel Space
-
LWN Linux 6.1.23
-
LWN Linux 6.2.10
I'm announcing the release of the 6.2.10 kernel. All users of the 6.2 kernel series must upgrade. The updated 6.2.y git tree can be found at: git://git.kernel.org/pub/scm/linux/kernel/git/stable/linux-stable.git linux-6.2.y and can be browsed at the normal kernel.org git web browser: https://git.kernel.org/?p=linux/kernel/git/stable/linux-s... thanks, greg k-h
-
-
A...
-
11:00
ISACA updates CMMI model to increase its flexibility and adaptability Help Net Security
In a tightening economic market, addressing enterprise performance can help organizations better weather challenges by reducing costs, creating efficiencies, and coming in on schedule while improving overall quality. ISACAs Capability Maturity Model Integration, or CMMI, has been doing just that for enterprises for more than three decades, and is now out with a major model update with three new model domainsData Management, People Management, and Virtual Workthat allow organizations even more flexibility to customize their More
The post ISACA updates CMMI model to increase its flexibility and adaptability appeared first on Help Net Security.
10:14
UK Criminal Records Office Crippled by Potential Ransomware Attack HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
The Criminal Records Office (ACRO) of the United Kingdom has acknowledged the cyberattack but did not confirm whether it was a ransomware attack.
This is a post from HackRead.com Read the original post: UK Criminal Records Office Crippled by Potential Ransomware Attack
10:00
LastPass Security Dashboard now features dark web monitoring Help Net Security
LastPass has expanded availability of its Security Dashboard and associated dark web monitoring and alerting, making it the only password manager providing proactive credential monitoring for all customers, including those using the product for free. The Security Dashboard is the central hub where customers can monitor the overall security of all vault credentials, including exposure to the dark web, which allows customers to better protect themselves from potential breaches. The Security Dashboard is an essential More
The post LastPass Security Dashboard now features dark web monitoring appeared first on Help Net Security.
10:00
HPR3830: Into New Mexico Hacker Public Radio
We made a change in our itinerary and instead of going up into the mountains of New Mexico we went down to the area of the border of Mexico. Our first stop was in Deming, NM for a few days, the on to Anthony, NM for a longer stay of nearly three weeks. Anthony is located between Las Cruces, NM, and El Paso, Texas, so it was a convenient location for visiting both of the places, and we did so. In hindsight, we liked Las Cruces and the New Mexico part a lot better than El Paso. Links: https://flic.kr/s/aHBqjzKYwL https://flic.kr/s/aHBqjzL1pH https://flic.kr/s/aHBqjzKYwM https://flic.kr/s/aHBqjzKZcd https://flic.kr/s/aHBqjzKYVh https://flic.kr/s/aHBqjzL1F8 https://flic.kr/s/aHBqjzKZLE https://flic.kr/s/aHBqjzL6F3 https://www.palain.com/travel/into-new-mexico/
09:30
AuthenticID launches identity document liveness detector Help Net Security
AuthenticID has revealed the launch of its identity document liveness detector. This feature enhancement validates the actual, physical presence of identity documents when used as part of the identity verification process. AuthenticIDs identity document liveness detector utilizes advanced AI and computer vision to detect many forms of document spoofing, especially digitally-displayed document spoofs. These spoofs are also called screen replay attacks. In this method, bad actors will attempt to bypass verification methods by displaying digital More
The post AuthenticID launches identity document liveness detector appeared first on Help Net Security.
09:19
The Microcode and Hardware in the 8086 Processor That Perform String Operations SoylentNews
https://www.righto.com/2023/04/8086-microcode-string-operations.html
Intel introduced the 8086 microprocessor in 1978. This processor ended up being hugely influential, setting the path for the x86 architecture that is extensively used today. One interesting feature of the 8086 was instructions that can efficiently operate on blocks of memory up to 64K bytes long. These instructions rapidly copy, compare, or scan data and are known as "string" instructions.
In this blog post, I explain string operations in the 8086, analyze the microcode that it used, and discuss the hardware circuitry that helped it out.
[...] I'll explain the behavior of an ALU micro-operation since it is important for string operations. The Arithmetic/Logic Unit (ALU) is the heart of the processor, performing addition, subtraction, and logical operations. The ALU has three temporary input registers that are invisible to the programmer: tmpA, tmpB, and tmpC. An ALU operation takes its first argument from any temporary register, while the second argument always comes from tmpB. Performing an ALU operation requires two micro-instructions. The first micro-instruction specifies the ALU operation and source register, configuring the ALU. For instance, ADD tmpA configures the ALU to add the tmpA register to the default tmpB register. In the next micro-instruction (or a later one), the ALU result can be accessed through a special register called (SIGMA) and moved to another register.
Read more of this story at SoylentNews.
09:00
Fast Scanning Bed Leveling Hackaday

The bane of 3D printing is what people commonly call bed leveling. The name is a bit of a misnomer since you arent actually getting the bed level but making the bed and the print head parallel. Many modern printers probe the bed at different points using their own nozzle, a contact probe, or a non-contact probe and develop a model of where the bed is at various points. It then moves the head up and down to maintain a constant distance between the head and the bed, so you dont have to fix any irregularities. [YGK3D] shows off the Beacon surface scanner, which is technically a non-contact probe, to do this, but it is very different from the normal inductive or capacitive probes, as you can see in the video below. Unfortunately, we didnt get to see it print because [YGK3D] mounted it too low to get the nozzle down on the bed. However, it did scan the bed, and you can learn a lot about how the device works in the video. If you want to see one actually printing, watch the second, very purple video from [Dre Duvenage].
Generally, the issues with probes are making them repeatable, able to sense the bed, and the speed of probing all the points on the bed. If your bed is relatively flat, you might get away with probing only 3 points so you can understand how the bed is tilted. That wont help you if your bed has bumps and valleys or even just twists in it. So most people will probe a grid of points.
Like a pixel is to...
08:41
New Dark Web Market Styx: Focuses on Money Laundering, Identity Theft HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
Styx has quickly gained traction as a hub for various illicit activities, following the recent seizure of the Genesis dark web market.
This is a post from HackRead.com Read the original post: New Dark Web Market Styx: Focuses on Money Laundering, Identity Theft
08:40
06:39
Fast Food, Fast Charge IEEE Spectrum

It sounds so obvious: Public EV chargers should be located in public, where people tend to gather. The reality has often been otherwise, with too many chargers tucked into desolate parking lots or seemingly random locations. And since even the speediest DC chargers take roughly 30 minutes to juice up an EV, drivers and passengers have time to kill, including enough time for a bite.
To keep cars and passengers full, 7-Eleven and Subway are among the companies planning to serve up EV charging along with their Big Gulps and sandwiches.
7-Eleven envisions its 7Charge network as one of the biggest fast-charging networks among convenience stores in the United States. The company hasnt cited exact numbers of how many DC chargers it hopes to open, but 7-Eleven operates about 9,400 stores in the United States, and nearly 600 more in Canada. The company currently has more than 30 fast chargers in California, Colorado, Texas, and Florida.
The new chargers aim to welcome owners of any EV, by offering both the CCS (Combined Charging System) connector and the CHAdeMO plug. Tesla owners can already hook into CCS stations by means of an adapter. A 7Charge app will offer a station locator and an easy-payment method through a linked account.
7-Eleven isnt alone. Subway will partner with Miami-based GenZ EV Solutions to create Subway EV Charging Oasis parks with fast-charging stalls, picnic tables, Wi-Fi, playgrounds, and restrooms. California is determined to require all new vehicles sold to be either EVs or plug-in hybrids by 2035. And a Taco Bell franchisee with more than 300 locations has launched the first of 100 planned California charging stations in San Francisco.
Restaurant and convenience-store operators cite ongoing gaps in public charging, including in rural, urban, and other underserved areas.
Equitable access to charging is essential to the adoption of EVs, and Subways scale will play an important role in democratizing charging infrastructure for millions of Americans, said Jose Valls, CEO of GenZ EV Solutions.
 Subway will
be partnering with GenZ EV...
Subway will
be partnering with GenZ EV...
06:32
Repeating Radio Signal Leads Astronomers to an Earth-size Exoplanet SoylentNews
Astronomers have detected a repeating radio signal from an exoplanet and the star that it orbits, both located 12 light-years away from Earth. The signal suggests that the Earth-size planet may have a magnetic field and perhaps even an atmosphere.
Scientists noticed strong radio waves coming from the star YZ Ceti and the rocky exoplanet that orbits it, called YZ Ceti b, during observations using the Karl G. Jansky Very Large Array of telescopes in New Mexico. The researchers believe the radio signal was created by interactions between the planet's magnetic field and the star.
[...] "We saw the initial burst and it looked beautiful," said lead study author Sebastian Pineda, a research astrophysicist at the University of Colorado Boulder, in a statement. "When we saw it again, it was very indicative that, OK, maybe we really have something here."
[...] YZ Ceti b only takes two Earth days to complete a single orbit around its star. Meanwhile, the shortest orbit in our solar system is the planet Mercury, which takes 88 Earth days to complete a lap around the sun.
While YZ Ceti b whips around its star, plasma from the star collides with the planet's magnetic field, bounces off and interacts with the star's magnetic field. All of these energetic reactions create and release strong radio waves that can be detected on Earth.
Pineda, J.S., Villadsen, J. Coherent radio bursts from known M-dwarf planet-host YZ Ceti. Nat Astron (2023). https://doi.org/10.1038/s41550-023-01914-0
Read more of this story at SoylentNews.
06:19
ISPs Fail to Dismiss Filmmakers Piracy Liability Lawsuits TorrentFreak
 Over the past two decades, online piracy has proven a massive
challenge for the entertainment industries.
Over the past two decades, online piracy has proven a massive
challenge for the entertainment industries.
Copyright holders have tried to go after individual pirates and pirate sites in court, but third-party intermediaries are now increasingly seen as targets as well.
Several active lawsuits in the United States feature rightsholders accusing Internet providers of not doing enough to stop piracy. One of the main allegations is that ISPs fail to terminate the accounts of repeat infringers in appropriate circumstances as the DMCA requires.
These lawsuits have resulted in multi-million dollar judgments against Cox and Grande. Meanwhile, more companies at risk too, such as WideOpenWest (WOW!), which was sued by a group of smaller movie companies, including Millennium Media and Voltage Pictures.
The filmmakers accused the Colorado-based ISP of failing to terminate the accounts of subscribers who were repeatedly flagged for sharing copyrighted material. They argue that WOW! is liable for these piracy activities and are demanding millions of dollars in damages.
WOW! Wants Troll Case Dismissed
The ISP challenged the claims and filed a motion to dismiss the case. WOW! addressed the substance of the allegations and described the film companies and their anti-piracy partner Maverickeye as copyright trolls.
Plaintiffs and Maverickeye are part of a well-known web of copyright trolls. Until now, Plaintiffs modus operandi has been to file John Doe lawsuits in the hope of securing quick settlements and to dismiss them at the slightest resistance, they wrote.
Indeed, several of the plaintiff film companies have filed cases against individual file-sharers, but they have also sued hosting providers, site operators, and app developers.
Responding to the substance of the allegations, WOW! argued that an IP address is not sufficient to prove that subscribers downloaded or shared any infringing material. And if thats not clear, the ISP cant be held liable either.
Something More?
To back this up, WOW! cites the Cobbler Nevada v. Gonzales case, where the court held that an...
06:00
Intel Linux Optimizations Help AMD EPYC "Genoa" Improve Scaling To 384 Threads Phoronix
Last month I wrote about Intel's Linux kernel engineering improvements to help enhance CPU scaling across various workloads by addressing low-level bottlenecks within the kernel. It's an area we'll likely see Intel continue to invest in as Sierra Forest comes next year with 144 E cores per socket. Already with the Linux kernel patches Intel is carrying at the moment via their in-house distribution, there are some significant benefits for Xeon Scalable Sapphire Rapids. I was curious to see how this Intel-focused work impacted AMD EPYC servers and thus in today's article is a similar analysis using two AMD EPYC 9654 "Genoa" flagship processors while evaluating Intel's Linux kernel optimizations.
Do I Belong? Investigating Belonging in Open Source through the Sense of Virtual Community Linux.com

Read the original blog at Read More
The post Do I Belong? Investigating Belonging in Open Source through the Sense of Virtual Community appeared first on Linux.com.
05:45
Free Software Foundation Certifies A $99 Mini VPN Router Phoronix
Over the years the Free Software Foundation has certified various devices that to their standards "Respect Your Freedom" from USB to parallel printer cables to re-branded and re-flashed motherboards to the Talos II at the higher-end. They've also certified different network hardware and other devices. The newest that they announced today is backing a $99 mini VPN router that supports WireGuard and other solutions...
05:22
Re: [ADVISORY] CVE-2023-1668: Open vSwitch: Remote traffic denial of service via crafted packets with IP proto 0 Open Source Security
Posted by Ilya Maximets on Apr 06
Correction:Priorities for these flows should be set to 65535 instead.
i.e. The maximum priority that can be set with OpenFlow.
05:20
[ADVISORY] CVE-2023-1668: Open vSwitch: Remote traffic denial of service via crafted packets with IP proto 0 Open Source Security
Posted by Ilya Maximets on Apr 06
Description===========
Multiple versions of Open vSwitch are vulnerable to crafted IP packets
with ip proto set to 0 causing a potential denial of service.
Triggering the vulnerability will require an attacker to send a crafted
IP packet with protocol field set to 0 and the flow rules to contain
'set' actions on other fields in the IP protocol header. The resulting
flows will omit required actions, and fail to mask the IP protocol...
04:47
Once More, With Feeling: Exploring Relatable Robotics at Disney IEEE Spectrum

This is a guest post. The views expressed here are solely those of the author and do not represent positions of IEEE Spectrum or the IEEE.
Most robotics projects focus on the output: What does this robot do? Is it reliable, is it precise, and can it achieve its goals? But at Disney, our focus is on the story: How does this robot make you feel? Is it emotive, is it relatable, and does it authentically reflect a character people know in its mannerisms, gait, or expressions?
This context changes everything. Take walking, for examplein robotics, its generally a priority to maximize the stability of a walking gait, since falling down doesnt help you move crates or explore terrain. At Disney, however, a stable walking gait is less important than a gait that brings a character to life. Falling down can be wildly entertaining, as long as the falling happens in character!
About a year ago, our team came to a realization: We needed robots that didnt mind taking the occasional tumble. If were going to be free to explore fun and evocative performances with our robots, failure had to be an option. And not only thatfailure had to be expected, and built into the design. We called our new project Indestructibles and set out toward the goal implied by that name.
 Disney
Disney
On 10 March 2023, we were able to show off our latest Indestructibles prototype at SXSW in Austin, Texas. We were nervous. We knew this little character had charmed us, but we couldnt be sure her personality would come through on such a big stage with a brand-new audience. But from the moment she peeked her head out of her crate, the energy in the crowd let us know they were not only seeing her but cheering for her. We were thrilled!
...
04:33
Phishers migrate to Telegram Security Affairs
Experts warn that Telegram is becoming a privileged platform for phishers that use it to automate their activities and for providing various services.
Kaspersky researchers have published an analysis of phishers Telegram channels used to promote their services and products.
The experts pointed out that crooks engaged in phishing activities have started to rely on the popular instant messaging platform more in recent months.
On Telegram is possible to find channels that offer:
Free phishing kits that can be used to target users of a large number of global and local brands. Phishers also use to share stolen personal data with their subscribers. The free phishing material is offered as bait of sorts for less experienced phishers to bite and to recruiting an unpaid workforce.
- One reason is that any free content or manuals so willingly distributed by scammers to their Telegram audience serve as bait of sorts for less experienced phishers to bite. Newbies get a taste of what phishing tools can do, pull off their first scam and wish for more, which is when they will be offered paid content. The creators of phishing bots and kits can get access to data that is gathered with their tools.
To attract larger audiences, scam operators advertise their services, promising to teach others how to phish for serious cash. reads the post published by Kaspersky.
Contents of a free phishing kit archive
- Paid phishing pages and data, as well as phishing-as-a-service (PhaaS) subscriptions. Crooks use Telegram channel to offer paid phishing content and data. They also provide phishing-as-a-service (PhaaS) subscriptions that give their customers access to phishing tools, as well as guides for beginners and technical su...
04:00
Survey Shows Overwhelming Interest in a Four-Day Workweek IEEE Spectrum

The Institute conducted an online poll in December, asking readers for their thoughts on a four-day workweek. About 95 percent of the respondents said they want to work a shorter weekwhich to me means employees think they can complete their tasks in four days rather than five. However, 89 percent of the respondents companies dont offer that type of work schedule.
The poll results inspired me to explore the matter further. I interviewed several engineers and tech company executives about four-day workweeks.
Providing more flexibility
 Before he
retired, IEEE Senior Member John McWilliams was a senior innovation
engineer at the Dairyland Power Cooperative, in La Crosse,
Wis.John
McWilliams
Before he
retired, IEEE Senior Member John McWilliams was a senior innovation
engineer at the Dairyland Power Cooperative, in La Crosse,
Wis.John
McWilliams
IEEE Senior Member John McWilliams reflected on his time as a field service engineer from 1978 to 1988 with Westinghouse and how difficult it was to be available and prepared to go anywhere at any time. He retired in October from his job as senior innovation engineer at the Dairyland Power Cooperative, in La Crosse, Wis.
That was tough, McWilliams recalls. I did not get the time to physically and mentally recover from previous assignments. There was no time to go on a vacation, attend a concert or to just relax at home.
Working that type of schedule at an early age negatively impacted his marriage and health, he says.
Westinghouse then assigned him to work on construction projects in Saudi Arabia in 50 C weather, without time to rest after the job was completed.
Making young professionals work a long work sche...
03:43
Maker of Eye Drops Linked to Deadly Outbreak Flunks FDA Inspection SoylentNews
The maker of eye drops linked to a deadly outbreak of extensively drug-resistant infections in the US had a slew of manufacturing violationsfrom brown slime on filling equipment to a lack of basic measures and systems to ensure sterilityaccording to an inspection report released by the Food and Drug Administration (PDF).
In February, the regulator warned consumers to immediately stop using eye drops and eye ointment made by Global Pharma, whose products were sold in the US under brand names EzriCare and Delsam Pharma and were available through Amazon, Walmart, eBay, and other retailers. Global Pharma later issued voluntary recalls of the products.
Health investigators had linked the drops to cases of an extensively drug-resistant Pseudomonas aeruginosa strain that had never been seen before in the US. The strain is identified as VIM-GES-CRPA, which stands for a carbapenem-resistant P. aeruginosa (CRPA) with Verona integron-mediated metallo--lactamase (VIM) and Guiana extended-spectrum--lactamase (GES). Although affected people reported using multiple brands of eye drops, EzriCare was the most common. Additionally, testing by the Centers for Disease Control and Prevention and independent researchers have identified the outbreak strain in opened bottles of EzriCare artificial tears.
As of March 14, 68 people in 16 states have been infected with the strain, the Centers for Disease Control and Prevention reports. Three people have died from the infection, eight have lost vision, and four have had their eyeballs surgically removed.
Read more of this story at SoylentNews.
03:20
Report Shows Astonishing Depravity in Sexual Abuse of More than 600 in Baltimores Catholic Archdiocese cryptogon.com
Via: Baltimore Sun: A four-year investigation of Baltimores Catholic archdiocese reveals the scope of 80 years of child sex abuse and torture and how church officials often covered it up and, in some cases, paved the way for further abuse. Among the accounts: A deacon who admitted abusing more than 100 children. A priest who []
03:09
Ukrainian hackers spend $25,000 of pro-Russian bloggers money on sex toys Graham Cluley
A pro-Russian blogger who raised $25,000 for drones to assist Russian troops fighting in Ukraine, has received a huge delivery of sex toys instead. Read more in my article on the Hot for Security blog.
02:52
Summary: Twitter addiction (or FOMO, or sometimes peoples wrong belief/intuition that their social life/popularity is the sum total of their Twitter followers) has thus far prevented more people from leaving; what else do they need to see before realising that its time to leave?
MAKE no mistake about it. The shitshow or the dumpster fire that Twitter has become since the takeover is miles worse than the Twitter I left completely over a year ago (I had left years earlier to a lesser degree). I didnt envision it would (just months later) be taken over by a pot-smoking fraud who replaces the logo with a meme, manipulates the algorithms to boost the ego of people who pay him, and so on and so on
Social control media is worse than a waste of time.The number of scandalous moves is too great to recall or itemise offhand. Weve added links to document most of these (Daily Links) and if anyone still believes things will improve in that platform, then one must be smoking the same stuff this guy does.
Leave Twitter. The sooner, the better. Social control media is worse than a waste of time.
Video download link |
md5sum 526954e8bf862702e446d6cce5e152b0
Why I Hate Elon Musk | Credit to original author here
02:49
Media Briefing: Proposed UN Cybercrime Treaty Negotiations Headed in Troubling Direction, Sidestepping Human Rights Protections and Threatening Free Expression, EFF and Allies Warn Deeplinks
San FranciscoOn Thursday, April 13, at 10:00 am Pacific
Time (1:00 pm Eastern Time, 7 pm CEST), experts with Electronic
Frontier Foundation (EFF) and four international allies will brief
reporters on the grave threat to human rights posed by ongoing UN
Cybercrime Treaty negotiations that could lead to broad
surveillance powers, criminalizing online speech, and enabling
hacking by police agencies.
The one-hour briefing will be livestreamed from the
fifth session of treaty negotiations in Vienna,
where representatives from over 100 Member States will meet
to discuss a
negotiating document reflecting their
suggestions for the treaty. The document lacks strong commitments
to human rights and detailed conditions and safeguards that are
needed to protect the rights of Individuals and organizations
around the world.
Without that, theres ample wiggle room for prosecutors to, for
example, access personal data with no independent or judicial
oversight, and use electronic surveillance to interfere with the
rights to privacy and freedom of expression in ways that violate
international human rights law.
The drafts scope needs to be narrowed and
include specific human rights protections.
As it stands, it
creates over thirty new cybercrime offenses,
including half a dozen that would make it a crime to send or post
legitimate content protected by international law. This goes far
beyond what States are allowed to restrict under international
human rights standards. Most concerning are overly broad provisions
seeking to
criminalize speech on the basis of fake
news, extremism, incitement and terrorism. International human
rights law already provides clear guidance on how to address many
of these issues.
Many Sta...
02:49
A fireside chat with four CISOs about how they secure their cybersecurity firms from attack Graham Cluley
On Tuesday 11 April, I'll be joined by the CISOs of security firms Wiz, Rubrik, Noname, and Abnormal, for a friendly chat about how they protect their organisations from the huge number of threats targeting them. I hope to see some of you there!
02:27
The Linux Foundation Events Monthly Snapshot April 2023 Linux.com
read the original post at Read More
The post The Linux Foundation Events Monthly Snapshot April 2023 appeared first on Linux.com.
02:12
Links 06/04/2023: PipeWire 0.3.68, Ofcom/Competition and Markets Authority May Study Microsofts Antitrust Abuses Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Digital Restrictions (DRM)
- Monopolies
- Gemini* and Gopher
-
GNU/Linux
-
Desktop/Laptop
-
CNX Software PineTab-V...
-
-
02:00
Linux 6.4 Bringing Apple M2 Additions For 2022 MacBook Air, MacBook Pro, Mac Mini Phoronix
Further adding to the excitement of the upcoming Linux 6.4 merge window is the mainline kernel seeing the Device Tree (DT) additions for Apple's current M2 devices including the MacBook Air, MacBook Pro, and Mac Mini systems. The upstream kernel still has more work to go around the M1/M2 support compared to the downstream state with Asahi Linux, but at least now with this DT support will provide some basic level of upstream kernel support for the Apple M2...
01:57
888casino Evaluations Read Customer Support Evaluations Of 888casino It h+ Media
888casino Evaluations Read Customer Support Evaluations Of 888casino It
All you must do is observe through their simple and fast registration course of and get ready to spin. All the video games that can be seen in a world-class brick and mortar casino can be discovered within the stay dealer part of 888 on line casino. Roulette, Blackjack, Bacarrat, Casino Holdem, Three card poker, Caribbean stud poker and Ultimate Texas Holdem are among the many most performed commonplace on line casino video games.
888casino wants gamers to kickstart their gambling voyage with a win. Other exciting bonuses are the FAB free spins, Fantastic FreePlay, and so on. The 88 Free spins are valid for scratch games, and there are limitations on what you can win, just like the NetEnt free spins. All new and present players can get pleasure from instant-play video games from an HTML5 net browser, including Google Chrome on Windows or Apple Safari on Mac OS. 888 Casino makes use of a proprietary software platform with a number of in-house video games. The casino cooperates with top-tier game providers like Playtech, NetEnt, 888 Gaming, IGT , WMS, and so on.
888 Casino is a authorized service for Kiwi players as a result of 888 is a casino thats registered exterior of New Zealand. Under NZ law, businesses are unable to provide online playing content material. Therefore, gamers are legally allowed to entry what are foreign web sites.
- Unfortunately, there are not any Live Chat choices or a toll-free quantity to call, and it may upset gamblers, as generally they may be impatient and expect immediate responses.
- The fantastic thing about the positioning is you could play at any time 24/7 either on-line in flash variations, or if you favor, on the downloadable model.
- But no matter the type of blackjack a participant needs to play, there are solely a handful of online casinos which provide the most effective variations.
- The Double Your Money first deposit offer permits new gamers to take advantage and get a one hundred pc bonus on their first deposit, as much as 100.
- As an 888 VIP Casino Club member, you get exclusive access to all of our 888 manufacturers, which incorporates 888casino.
For New Zealand gamers, withdrawing the money to Credit Cards may be tough at occasions, which is why I recommend utilizing the payment processors like PayPal or Skrill for probably the most half. The deposits from these methods are immediate and withdrawals are normally accomplished inside hours, with 2-3 days being the maximum amount of time youll ever wait on your cash to succeed in your account. With the assistance for theimprovement and developmentof the 888 cell on line casino app, players from New Zealand can now play the web cellular casino video games on their Apple gadgets and Android devices. This app is appropriate with almost each smartphones and cellular devices....
01:56
888 Casino Nz Review 2021 $1500 Premium Welcome Bonus h+ Media
888 Casino Nz Review 2021 $1500 Premium Welcome Bonus
After that we provide particular 888 Casino presents in case you are interested in buying something for a discount. Receive 500% bonus in your first deposit with us, 600% on the second deposit and 400% bonus on the third. We grant a bonus to all deposits, beginning with 200% on your first deposit of the day. Make the acquisition benefiting from the discounts now out there on Pokerstars.
The operator has the same data safety protocols for both platforms . In our full review of 888casino you presumably can seek the assistance of relevant details about the corporate, together with the security systems it applies. Once players have registered a brand new account, they must make a NZ$10 minimal deposit to trigger the Welcome Bonus. To declare the Welcome Bonus, Kiwis want to make certain that their cellphone number is verified beforehand.
888 has acquired William Hill and now they have joined forces and have shaped a piece staff and an experience within the reach of only a few. 888 Casino is among the most acknowledged and largest gambling platforms in our country. It has a self-exclusion program to help customers create responsible playing behaviors.
Various ways to payWith UPaycard, youve a quantity of methods to make on-line on line casino transactions, such as through the e-wallet choice, a prepaid card, and via crypto. But earlier than utilizing it, AU and NZ gamers ought to check UPaycard supported nations, including casinos that supply it as a fee method. Probably Evolution Gaming contributes many extra of their desk video games to their stay casino. A welcome offer is available for new gamers who register with New Zealand e-ID on their first deposit. The on line casino is licensed by The New Zealand Gambling Authority, offers quick on line casino withdrawals and has several payment methods to choose from. Their bonus construction permits gamers to choose how big the bonus might be relying on the amount they select to deposit which is at all times voluntary for gamers to choose.
Frank on line casino never shares any details about you as a player and the on line casino additionally has a New Zealand gaming license from in New Zealand. The license permits Frank on line casino to legally promote legal playing to you as a player in New Zealand. With give consideration to its members nothing is left to chance for anyone visiting Frank on line casino New Zealand web page. Here players will find a properly thought out and simply navigated on-line casino in cell, computer and tablet. First of all, in fact, we look at our own experiences with the on line casino.
And that is why, at OnlineCasinosNew Zealand, we only review New Zealander online casinos licensed by the SRIJ . GO competitive organizations arent that different from traditional sports activities golf equipment on this regard, they do inform you about the ongoing sporting occasion...
01:55
Commerce On Line Casino In Commerce h+ Media
Commerce On Line Casino In Commerce
In addition, the supply is huge and its typically troublesome to see the forest via the timber and find one of the best casino. If you had to go through the whole supply your self, you would be busy for a really long time and no longer have time to gamble. Cash games start from micro stakes of $0.01/$0.02 and may reach $25/$50 for no limit Texas Holdem. This is the variation that gets the most traffic right now since the poker sport is well-liked around the globe and attracts within the huge crowds.
Low deposit Casino, often generally in regards to the on-line playing websites that have casino$50 deposit or lower as a restrict. It can additionally be the minimum quantity to activate a the bonus provided in the intervening time. You can use any fee method at Frank to pick it up, which can be good for you to control. Good to notice is that there is no need to obtain any Frank casino app to succeed in their mobile casino . You play as usual by logging into your account after youve registered. When you exit from your mobile account, you possibly can, similar to in the computerized version, pick up video games the place you left off, make withdrawals, see present promotions, contact help and far more.
Games like Multi-hand Blackjack, European Roulette, and Jacks or Better all continue to show well-liked here. Pokies Here you probably can look forward to finding a extremely impressive degree of variety, with one of the best online pokies from NetEnt, Playn GO, and Red Tiger. A mixture of themes and sport options will hold you entertained for months to return playing the likes of Book of Dead, Street Fighter 2, and Wolf Ridge. Below will cowl a few regularly requested questions made about casino players after they first register a brand new account at 888 Casino. If you have any further questions please contact the assist part as described within the last paragraph.
The Frank Casino bonus is certainly one of the biggest bonuses at the on line casino proper now, and while it isnt with no turnover,$avet feels affordable for the scale. Not all providers are the same and not every on-line on line casino suits each player. 888 Casino brings its award profitable software program into the cellular area to offer access to a wonderful line-up of video games.
You can even sharpen your abilities in roulette and blackjack in your smartphone and the controls are very simple whereas presenting HD graphics for an immersive experience. 888 Mobile Casino is a should for model spanking new and current customers of the popular operator. If you want reside vendor video games, the on line casino launched a full library of video games which are broadcast from studios. These allow you to play baccarat, blackjack, Caribbean Stud, Three Card Poker, roulette, and Dream Catcher in high definition and is fairly nicely constructed.
Play the video games you love, earn fa...
01:54
[$] Seeking an acceptable unaccepted memory policy LWN.net
Operating systems have traditionally used all of the memory that the hardware provides to them. The advent of virtualization and confidential computing is changing this picture somewhat, though; the system can now be more picky about which memory it will use. Patches to add support for explicit memory acceptance when running under AMD's Secure Encrypted Virtualization and Secure Nested Paging (SEV-SNP), though, have run into some turbulence over how to handle a backward-compatibility issue.
01:52
Own a Nexx smart alarm or garage door opener? Get rid of it, or regret it Graham Cluley
Hacker can remotely open or close garage doors, seize control of alarms, and switch on (or switch off) customers' "smart" plugs due to vulnerabilities in Nexx products.
01:02
Kioxia Demos 7-Bits-Per-Cell Flash Memory SoylentNews
Kioxia, formerly Toshiba Memory Holdings, has demonstrated "hepta-level-cell" NAND memory:
Kioxia Researchers Demo Hepta-Level Cell NAND Flash, Nearly Doubling the Capacity of QLC
NAND researchers at Kioxia have successfully demonstrated a working concept of a new storage architecture called Hepta-level cell NAND flash. This new type of NAND can house up to 7 bits per cell, giving it nearly twice the storage capacity of QLC NAND flash. If Kioxia can stabilize this storage architecture at room temperature, it might become the ultimate successor to spinning hard drives in consumer and enterprise applications.
To create hepta-level NAND flash, Kioxia is using a new design called new silicon process technology to increase cell density, in conjunction with cryogenic cooling. New silicon process technology replaces current poly-silicon materials with a single-crystal silicon that is used in a channel inside a memory cell transistor. This apparently reduces the amount of read noise coming from the NAND flash by up to two-thirds. In other words, new silicon process technology produces clearer read signals for reading data off of the NAND flash, enough so to increase the bits cell capacity to 7.
7 / 4 = 1.75. Nearly double!
Kioxia has already demonstrated 6-bits-per-cell NAND. Multiple companies are mulling a transition to 5-bits-per-cell (PLC) NAND. Western Digital's technology and strategy chief Siva Sivaram doesn't expect PLC NAND to take off until 2025 or later.
Read more of this story at SoylentNews.
Thursday, 06 April
00:58
Melbet App Download For Android Apk & Ios In India h+ Media
Melbet App Download For Android Apk & Ios In India
Unfortunately, not all cell purposes are trustworthy places for betting. There are many scammers whove been added to a black list due to numerous complaints from gamers about delays in payments and many other problems that they confronted. Below you could find unreliable cell apps that you should keep away from. This sort of sports activities is actually well-liked among bettors because of a huge number of different prestigious tournaments that take place all year long throughout the globe.
Is available, in fact, for smartphones with the Android working system. This software may be very easy and fast to obtain to your cellular gadget. Therefore, you possibly can spend time well and profitably out of your cellphone. Generally, withdrawals take wherever from 24 hours to five business days after your account is verified and the transaction is accredited. You ought to know that the minimum withdrawal amount is USD 20. It all depends on the cost methodology every player chooses.
The greatest plus with Melbet is the ease of transactions with 56 deposit methods with forty eight of them getting used for withdrawals as nicely. With categories like Sports, LIVE bets, and eSports, Melbet presents you over 1,000 video games so that you just can guess on. If you are a sports activities fan whos at all times proper along with your predictions of an ongoing game and love your self an excellent on-line casino, Melbet Casino is simply the place for you. Melbet has been on the scene for more than a decade, at all times very consistent with payments and security.
Many luxurious facilities are also out there here for players like Sauna tub, Private Gym, Jacuzzi, Gym, Restaurant, sports and coaching academy, hostel, and so forth. Yes, you probably can claim any sort of bonus in a betting software together with free bets. All functions that personal an official license from gaming authorities are reliable in India. For now, there are no official legal guidelines in India that prohibit online betting on this nation.
Go to the official Melbet Bangladesh, where it is feasible for you to to see on the bottom the item with the bookmakers cellular apps. On the open web page, you will be able to choose the appliance on your gadget and instantly obtain and set up it. The Melbet app just isnt one of the latest additions to the world of online betting. Since its inception in 2012, this bookmaker has managed to gain recognition among sports activities fans. It has a variety of sports occasions and markets, which is attracting more and more betting followers.
Below there are crucial standards that you should think about whereas examining cellular apps. Downloading Melbet for Android is free, service is available to all Internet users. [newline]However, at the moment it is inconceivable to find this system in the Play Market. To obtain the Market app for fre...