| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Monday, 20 March
23:41
Hackers can hijack Samsung and Pixel phones by knowing phone number HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
In addition to Google Pixel and Samsung devices, Vivo devices were also vulnerable to this attack.
This is a post from HackRead.com Read the original post: Hackers can hijack Samsung and Pixel phones by knowing phone number
23:38
Agility Robotics: Digit cryptogon.com
So, youre living in a van down by the river, hoping to pick up some short term work at a fulfillment center during Christmas. And then Via: Agility Robotics:
23:26
Mispadu Banking Trojan Targets Latin America: 90,000+ Credentials Stolen The Hacker News
A banking trojan dubbed Mispadu has been linked to multiple spam campaigns targeting countries like Bolivia, Chile, Mexico, Peru, and Portugal with the goal of stealing credentials and delivering other payloads. The activity, which commenced in August 2022, is currently ongoing, Ocelot Team from Latin American cybersecurity firm Metabase Q said in a report shared with The Hacker News. Mispadu (
23:14
Ubuntu's Mir 2.13 Released With Wayland Updates, Other Enhancements Phoronix
Ahead of next month's Ubuntu 23.04 release, Canonical has that in its current incarnation is focused on serving as a Wayland compositor and abstraction layer...
22:34
Zippyshare Quits After 17 Years, 45m Visits Per Month Makes No Money TorrentFreak
 When file-hosting service Zippyshare showed its first
signs of life in September 2006, accessing the site using an iPhone
was impossible; the smart phones existence wouldnt be announced for
another four months.
When file-hosting service Zippyshare showed its first
signs of life in September 2006, accessing the site using an iPhone
was impossible; the smart phones existence wouldnt be announced for
another four months.
Zippyshares success was built on solid yet basic foundations; straightforward free hosting of files, via a clean interface, at zero cost to the user. With relatively few options available elsewhere, Zippyshare was a huge success and to celebrate its first birthday, Zippyshare went BIG.
A few days ago Zippyshare.com turned one year old, its operators wrote in 2007. For Zippyshares first birthday we are raising the filesize limit to 100mb.
Upgrade After Upgrade
After repeatedly upgrading to meet rising demand, Zippyshare launched Zippyshare Uploader, a software application that allowed users to upload files without using a web browser.
Almost three years after the surprise 100mb limit was introduced, Zippyshare doubled its filesize limit to 200mb. A little later, when the internet was consumed with Megaupload being taken down, Zippyshare carried on as if nothing had happened, or it did once its email servers had been fixed.
Zippyshare Breaks Five-Year Silence With Bad News
When Zippyshares operators announced the shutdown of the site yesterday, that was the first update posted to the site for almost five years.
Weve decided that were shutting down the project at the end of the month. Please make backups of your important files, you have about two weeks to do so. Until then, the site will run without any changes, the announcement reads.
In addition to hardw...
22:22
How AI could upend the world even more than electricity or the internet Lifeboat News: The Blog
The rise of artificial general intelligence now seen as inevitable in Silicon Valley will bring change that is orders of magnitude greater than anything the world has yet seen, observers say. But are we ready?
AGI defined as artificial intelligence with human cognitive abilities, as opposed to more narrow artificial intelligence, such as the headline-grabbing ChatGPT could free people from menial tasks and usher in a new era of creativity.
But such a historic paradigm shift could also threaten jobs and raise insurmountable social issues, experts warn.
22:13
PCIe for Hackers: The Diffpair Prelude SoylentNews
https://hackaday.com/2023/03/14/pcie-for-hackers-the-diffpair-prelude/
PCIe, also known as PCI-Express, is a highly powerful interface. So let's see what it takes to hack on something that powerful. PCIe is be a bit intimidating at first, however it is reasonably simple to start building PCIe stuff, and the interface is quite resilient for hobbyist-level technology. There will come a time when we want to use a PCIe chip in our designs, or perhaps, make use of the PCIe connection available on a certain Compute Module, and it's good to make sure that we're ready for that.
PCIe is everywhere now. Every modern computer has a bunch of PCIe devices performing crucial functions, and even iPhones use PCIe internally to connect the CPU with the flash and WiFi chips. You can get all kinds of PCIe devices: Ethernet controllers, high-throughput WiFi cards, graphics, and all the cheap NVMe drives that gladly provide you with heaps of storage when connected over PCIe. If you're hacking on a laptop or a single-board computer and you'd like to add a PCIe device, you can get some PCIe from one of the PCIe-carrying sockets, or just tap into an existing PCIe link if there's no socket to connect to. It's been two decades since we've started getting PCIe devices now, PCIe is on its 5.0 revision, and it's clear that it's here to stay.
PCIe is a point-to-point bus that connect two devices together as opposed to PCI, an older bus, that could connect a chain of devices on your mainboard. One side of a PCIe link is a device, and another is a host. For instance, in a laptop, your CPU will have multiple PCIe ports some used to connect the GPU, some used to connect a WiFi card, some used for Ethernet, and some used for a NVMe drive.
Each PCIe link consists of at least three differential pairs one is a 100 MHz clock, REFCLK, that is (almost) always required for a link, and two pairs that form a PCIe lane one for transmit and another for receive. This is an x link you can also have 2x, 4x, 8x and 16x links, with four, eight sixteen and thirty-two differential pairs respectively, plus, again, REFCLK. The wider the link, the higher its throughput!
Read more of this story at SoylentNews.
22:00
Remote Water Quality Monitoring Hackaday

While it can be straightforward to distill water to high purity, this is rarely the best method for producing water for useful purposes. Even drinking water typically needs certain minerals in it, plants may need a certain pH, and wastewater systems have a whole host of other qualities that need to be measured. Measuring water quality is a surprisingly complex endeavor as a result and often involves a wide array of sensors, much like this water quality meter from [RowlesGroupResearch].
The water quality meters that they are putting to use are typically set up in remote locations, without power, and are targeting natural bodies of water and also wastewater treatment plants. Temperature and pH are simple enough to measure and grasp, but this device also includes sensors for total dissolved solids (TDS) and turbidity which are both methods for measuring various amounts and types of particles suspended in the water. The build is based around an Arduino so that it is easy for others to replicate, and is housed in a waterproof box with a large battery, and includes data logging to an SD card in order to make it easy to deploy in remote, outdoor settings and to gather the data at a later time.
The build log for this device also goes into detail about al...
22:00
Intel Xeon Sapphire Rapids Code Continues Landing For Coreboot Phoronix
More Intel 4th Gen Xeon Scalable "Sapphire Rapids" code was merged this weekend into Coreboot as part of enabling this latest generation Intel server platform to enjoy this open-source system firmware solution when paired with the necessary Intel FSP binaries...
21:55
Emotet is back after a three-month hiatus Security Affairs
The infamous Emotet malware is back after a short hiatus, threat actors are spreading it via Microsoft OneNote email attachments.
The Emotet malware returns after a three-month hiatus and threat actors are distributing it via Microsoft OneNote email attachments to avoid detection.
The Emotet banking trojan has been active at least since 2014, the botnet is operated by a threat actor tracked as TA542.
The infamous banking trojan was also used to deliver other malicious code, such as Trickbot and QBot trojans, or ransomware such as Conti, ProLock, Ryuk, and Egregor.
In April, the operators of the infamous Emotet botnet started testing new attack techniques in response to Microsofts move to disable Visual Basic for Applications (VBA) macros by default.
In June, Proofpoint experts spotted a new variant of the Emotet bot that uses a new module to steal credit card information stored in the Chrome web browser.
Over time, Emotet operators have enhanced their attack chain by employing multiple attack vectors to remain under the radar.
The operators remained inactive between July and November 2022. In November, Proofpoint researchers warned of the return of the Emotet malware after having observed a high-volume malspam campaign delivering payloads like...
21:44
New Cyber Platform Lab 1 Decodes Dark Web Data to Uncover Hidden Supply Chain Breaches The Hacker News
This article has not been generated by ChatGPT. 2022 was the year when inflation hit world economies, except in one corner of the global marketplace stolen data. Ransomware payments fell by over 40% in 2022 compared to 2021. More organisations chose not to pay ransom demands, according to findings by blockchain firm Chainalysis. Nonetheless, stolen data has value beyond a price tag, and in
21:33
Apache CloudStack 4.18 LTS Released For Launching Your Own Open-Source Cloud Phoronix
Apache CloudStack 4.18 LTS has been released as the newest building out your own cloud atop various hypervisors and allows easy management for large networks of VMs...
21:26
Researchers Shed Light on CatB Ransomware's Evasion Techniques The Hacker News
The threat actors behind the CatB ransomware operation have been observed using a technique called DLL search order hijacking to evade detection and launch the payload. CatB, also referred to as CatB99 and Baxtoy, emerged late last year and is said to be an "evolution or direct rebrand" of another ransomware strain known as Pandora based on code-level similarities. It's worth noting that the use
21:16
Intel Compute Runtime Updated With Initial Xe Kernel Driver Support Phoronix
Getting back on track for its new release rhythm, Intel today Intel Graphics Compiler 1.0.13230.7...
21:06
curl 8.0 Released To Celebrate Project's 25th Birthday Phoronix
The open-source cURL project providing the widely-used curl CLI program for downloading of data across numerous network protoocols along with its associated library is celebrating 25 years of the project. As part of the celebrations, curl 8.0 was released today...
20:49
Waterfall Security Solutions launches WF-600 Unidirectional Security Gateway Help Net Security
Waterfall Security Solutions launched the WF-600 Unidirectional Security Gateway, an OT security protection against remote cyber attacks. The WF-600 product line is a blend of hardware and software, enabling unbreachable protection at IT/OT interfaces with unlimited visibility into OT networks, systems and data. The new WF-600 series of products represent decades of experience, investment and innovation, incorporating feedback received from thousands of critical infrastructure and manufacturing sites. Whats new in the 600 series includes: Integrated More
The post Waterfall Security Solutions launches WF-600 Unidirectional Security Gateway appeared first on Help Net Security.
20:46
Dragonfly 1.0 Released For What Claims To Be The World's Fastest In-Memory Data Store Phoronix
Dragonfly as what's a high performnace in-memory database compatible with the Memcached and Redis APIs has reached version 1.0...
20:10
How to protect online privacy in the age of pixel trackers Help Net Security
Tracking pixels like the Meta and TikTok pixels are popular tools for online businesses to monitor their website visitors behaviors and preferences, but they do come with risks. While pixel technology has been around for years, privacy regulations such as CCPA and GDPR have created new, much stricter rules, making the practice of data harvesting through a tracking pixel highly controversial. Tracking pixels on your website means that website owners are considered data controllers and More
The post How to protect online privacy in the age of pixel trackers appeared first on Help Net Security.
19:58
Links 20/03/2023: Amazon Linux 2023 and Linux Kernel 6.3 RC3 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Desktop/Laptop
-
19:26
Deepfakes, Synthetic Media: How Digital Propaganda Undermines Trust SoylentNews
More and more, nation-states are leveraging sophisticated cyber influence campaigns and digital propaganda to sway public opinion. Their goal? To decrease trust, increase polarization, and undermine democracies around the world.
In particular, synthetic media is becoming more commonplace thanks to an increase in tools that easily create and disseminate realistic artificial images, videos, and audio. This technology is advancing so quickly that soon anyone will be able to create a synthetic video of anyone saying or doing anything the creator wants. According to Sentinel, there was a 900% year-over-year increase in the proliferation of deepfakes in 2020.
It's up to organizations to protect against these cyber influence operations. But strategies are available for organizations to detect, disrupt, deter, and defend against online propaganda. Read on to learn more.
[...] As technology advances, tools that have traditionally been used in cyberattacks are now being applied to cyber influence operations. Nation-states have also begun collaborating to amplify each other's fake content.
These trends point to a need for greater consumer education on how to accurately identify foreign influence operations and avoid engaging with them. We believe the best way to promote this education is to increase collaboration between the federal government, the private sector, and end users in business and personal contexts.
Read more of this story at SoylentNews.
19:00
A Feature-Rich Amplifier Module For 3-Way Speaker Builds Hackaday

Theres something rewarding about building your own DIY audio hardware. Knowing you put it together yourself gives you faith in the construction, and psychosomatically makes the music sound all that much sweeter. If youre into that kind of thing, you might like to give [Eric Sorensens] Denmark amplifier module a look.
The amplifier is intended to be used in a 3-way system, running a subwoofer, woofer, and tweeter. It uses a 1000 W ICEpower module to run the subwoofer, with a pair of 500W ICEpower modules to run the woofer and tweeter respectively. Meanwhile, a MiniDSP 2x4HD is used to accept optical audio input. It also offers digital signal processing and serves as a crossover to split the signal across the three speakers. An STM32F401 is used to run the show, controlling all the various modules and the necessary status LEDs. Its a feature-rich build, too, with overtemperature monitoring, fan control, and clipping warnings built in.
The whole setup is built on to a sturdy aluminium backplate. The CNC-machined panel has simple tactile buttons for control. There&#...
18:39
[SECURITY ADVISORY] curl: CVE-2023-27538: SSH connection too eager reuse still Open Source Security
Posted by Daniel Stenberg on Mar 20
CVE-2023-27538: SSH connection too eager reuse still====================================================
Project curl Security Advisory, March 20th 2023 -
[Permalink](https://curl.se/docs/CVE-2023-27538.html)
VULNERABILITY
-------------
libcurl would reuse a previously created connection even when an SSH related
option had been changed that should have prohibited reuse.
libcurl keeps previously used connections in a connection pool for...
18:38
IRC Proceedings: Sunday, March 19, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-190323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-190323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-190323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-190323.gmi
Over HTTP:
|
... |
18:36
[SECURITY ADVISORY] curl: CVE-2023-27537: HSTS double-free Open Source Security
Posted by Daniel Stenberg on Mar 20
CVE-2023-27537: HSTS double-free================================
Project curl Security Advisory, March 20th 2023 -
[Permalink](https://curl.se/docs/CVE-2023-27537.html)
VULNERABILITY
-------------
libcurl supports sharing HSTS data between separate "handles". This sharing was
introduced without considerations for do this sharing across separate threads
but there was no indication of this fact in the documentation.
Due to missing...
18:34
[SECURITY ADVISORY] curl: CVE-2023-27536: GSS delegation too eager connection re-use Open Source Security
Posted by Daniel Stenberg on Mar 20
CVE-2023-27536: GSS delegation too eager connection re-use==========================================================
Project curl Security Advisory, March 20th 2023 -
[Permalink](https://curl.se/docs/CVE-2023-27536.html)
VULNERABILITY
-------------
libcurl would reuse a previously created connection even when the GSS
delegation (`CURLOPT_GSSAPI_DELEGATION`) option had been changed that could
have changed the user's permissions in a...
18:32
[SECURITY ADVISORY] curl: CVE-2023-27535: FTP too eager connection reuse Open Source Security
Posted by Daniel Stenberg on Mar 20
CVE-2023-27535: FTP too eager connection reuse==============================================
Project curl Security Advisory, March 20th 2023 -
[Permalink](https://curl.se/docs/CVE-2023-27535.html)
VULNERABILITY
-------------
libcurl would reuse a previously created FTP connection even when one or more
options had been changed that could have made the effective user a very
different one, thus leading to the doing the second transfer with wrong...
18:30
[SECURITY ADVISORY] curl: CVE-2023-27534: SFTP path ~ resolving discrepancy Open Source Security
Posted by Daniel Stenberg on Mar 20
CVE-2023-27534: SFTP path ~ resolving discrepancy=================================================
Project curl Security Advisory, March 20th 2023 -
[Permalink](https://curl.se/docs/CVE-2023-27534.html)
VULNERABILITY
-------------
curl supports SFTP transfers. curl's SFTP implementation offers a special
feature in the path component of URLs: a tilde (`~`) character as the first
path element in the path to denotes a path relative to the...
18:27
[SECURITY ADVISORY] curl: CVE-2023-27533: TELNET option IAC injection Open Source Security
Posted by Daniel Stenberg on Mar 20
CVE-2023-27533: TELNET option IAC injection============================================
Project curl Security Advisory, March 20th 2023 -
[Permalink](https://curl.se/docs/CVE-2023-27533.html)
VULNERABILITY
-------------
curl supports communicating using the TELNET protocol and as a part of this it
offers users to pass on user name and "telnet options" for the server
negotiation.
Due to lack of proper input scrubbing and without it...
18:00
How the ancient philosophers imagined the end of the world Terra Forming Terra
How to make friends as an adult Terra Forming Terra

This is a wonderful article to print up and to distribute at your local coffee shop along with a name tag then kept on a roster board to be put on and taken off when one is in attendence. It can be called the local coffee shop freindship club and it can be used to support a club email group or even a facebook page as well.
Pakistan faces terrorism surge post-Afghan war Terra Forming Terra

A New Science of Heaven with Robert Temple Terra Forming Terra
I have been asked to review a new book written by Robert Temple titled A New Science of Heaven. I am delighted to do so.
it is also a great wake up call for my work on Cloud Cosmology. Understanding plasma is extremely important.
Understand that any and all clouds of free electrons will naturally be divergent and obviously blow apart. Bit of a problem if you narrow your vision just to what we can see or detect. This is of course my beef with all of our physics as I can readily imagine a neutron pair decaying into a free hygrogen ion and an electron. I can also imagine an electron positron pairing that is also neutral and even an neutrino pair as well. My Cloud Cosmology also informs how to go about making them as well.
What is important is that we have detected two plasma clouds within the two Lagrange points using optical telescopes. They are several times larger than our own planet. This happens to be an excellent location also for a large mass of neutral items just like neutron neutron pairs and all that. Free electrons will be shielded by these objects and even be nicely aligned with them as well.
All this screams that such neutron pairs form the outer shell of the sun and that such pairs are actively decaying there along with everything else we see. We are assuming the process is sped up there as well. Again we are describing obvious forms of so called DARK MATTER that simply cannot be detected by the tools at hand. And yes, DARK MATTER makes up around 98% of the matter in our galaxy. It might be important.
The fact is that we are blind to such matter. Yet it rather nicely accomadates plasma in particular and what has been asigned to Fusion Energy.
I now wonder just what lightening actually is. Free electrons obviously blow open a physical channel and something then passes through to the Earh's surface. Ball lightening is an obvious surface of free electrons containing what? How about neutron pairs we cannot detect?
Understand again, that we...
17:19
Play ransomware gang hit Dutch shipping firm Royal Dirkzwager Security Affairs
Dutch maritime logistics company Royal Dirkzwager suffered a ransomware attack, the company was hit by the Play ransomware gang.
The Play ransomware group hit the Dutch maritime logistics company Royal Dirkzwager.
Royal Dirkzwager is specialized in optimizing shipping processes and managing maritime and logistic information flows.
The ransomware group added the company to its Tor data leak site and announced the theft of stolen private and personal confidential data, employee IDs, passports, contracts and etc.
The gang initially leaked a 5 GB archive as proof of the hack and threatens to release the full dump if the company will not pay the ransom.

Company CEO Joan Blaas said that the ransomware attack did not impact the operations of the company. He confirmed that threat actors have stolen sensitive data from its infrastructure.
It has had a huge impact on our employees. Over the last year, because of the companys bankruptcy, we had to let go of people and not everyone could stay. We had to move offices and now this. Its been a very difficult time, Company CEO Joan Blaas told The Record.
The company notified the Dutch Data Protection Authority and confirmed it is in negotiations with the ransomware group.
The Play ransomware group has been active since July 2022, the list of victims includes the City of Oakland and the Cloud services provider Rackspace.
The shipping industry is a privileged target of cybercrime organizations. In January, about 1,000 ves...
16:51
Emotet Rises Again: Evades Macro Security via OneNote Attachments The Hacker News
The notorious Emotet malware, in its return after a short hiatus, is now being distributed via Microsoft OneNote email attachments in an attempt to bypass macro-based security restrictions and compromise systems. Emotet, linked to a threat actor tracked as Gold Crestwood, Mummy Spider, or TA542, continues to be a potent and resilient threat despite attempts by law enforcement to take it down. A
16:39
Humanoid Robots are Coming SoylentNews
Human-shaped robots with dexterous hands will be staffing warehouses and retail stores, tending to the elderly and performing household chores within a decade or so, according to a Silicon Valley startup working toward that vision:
Demographic trends such as a persistent labor shortage and the growing elder care crisis make fully-functioning, AI-driven humanoid robots look tantalizingly appealing.
Companies such as Amazon are reportedly worried about running out of warehouse workers, whose jobs are physically and mentally demanding with high attrition.
A heavy-hitting startup called Figure, which just emerged from stealth mode, is building a prototype of a humanoid robot that the company says will eventually be able to walk, climb stairs, open doors, use tools and lift boxes perhaps even make dinner.
[...] It will take decades for humanoid robots to be able to replicate the sophisticated things our bodies can do, but visionaries are hard at work trying to make it happen.
Previously: Elon Musk Reveals Plans to Unleash a Humanoid Tesla Bot
Read more of this story at SoylentNews.
16:30
Detecting face morphing: A simple guide to countering complex identity fraud Help Net Security
Our reliance on face matching for identity verification is being challenged by the emergence of artificial intelligence (AI) and facial morphing technology. This technique involves digitally creating an image which is an average of two peoples faces, and which can deceive not only human examiners, but also facial recognition systems. The misuse of this technology can enable two individuals to use one ID, presenting a significant risk for businesses and governments. In 2018, a group More
The post Detecting face morphing: A simple guide to countering complex identity fraud appeared first on Help Net Security.
16:24
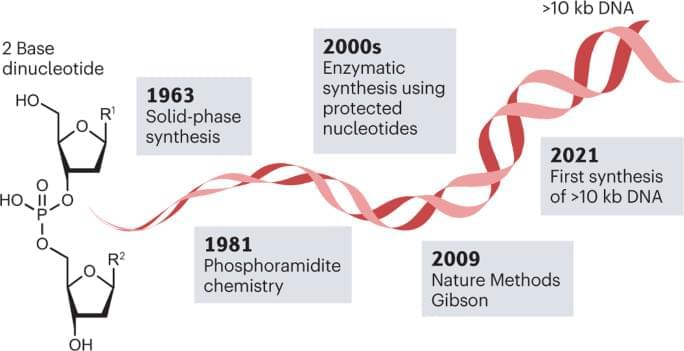
DNA synthesis technologies to close the gene writing gap Reviews Chemistry Lifeboat News: The Blog
There is increasing demand for synthetic DNA. However, our ability to make, or write, DNA lags behind our ability to sequence, or read, it. This Review discusses commercialized DNA synthesis technologies in the pursuit of closing the DNA writing gap.
16:23
Is Polands tap water really protected by clams? Lifeboat News: The Blog

Using living organisms to ensure water safety.
Theres a lot of articles written about how tap water in Warsaw
is constantly tested by a small team of clams. It felt like a hoax
to me: so I went to find out.  Thanks to MPWiK Warsaw: https://www.mpwik.com.pl/
Thanks to MPWiK Warsaw: https://www.mpwik.com.pl/
Producer: Marcin Krasnowolski https://polishfixer.com.
Camera: Micha Opala.
Editor: Michelle Martin
https://twitter.com/mrsmmartin.
Im at https://tomscott.com.
on Twitter at
https://twitter.com/tomscott.
on Facebook at https://facebook.com/tomscott.
and on Instagram as tomscottgo.
16:22
Biologists Figured Out How to Generate New Neurons in the Adult Brain, Revolutionizing Neurodegenerative Disease Research Lifeboat News: The Blog
Recently biologists discovered how to generate new neurons in the adult brain. This is an incredible breakthrough that has enormous potential to revolutionize neurodegenerative disease research. By generating genetically-mutated mice with a unique gene that activates dormant neural stem cells, scientists were able to generate new neurons in the brain. For years, scientists have been searching for ways to promote the growth of new neurons in the brain, especially in individuals with neurodegenerative diseases such as Alzheimers and Parkinsons. This new discovery could lead to new treatments and therapies that could help to restore brain function and improve the quality of life for millions of people around the world.
Leslie Samuel, founder of Interactive Biology, gives some context for the importance of genetic trading between organisms for scientific research, and notes how the loss of nerve cells in the brain is one of the hallmarks of neurodegenerative diseases. The ability to generate new neurons in the adult brain could be a game-changer in the field of neurology.
Leslies Thoughts
16:22
LoRA Weights Lifeboat News: The Blog
LoRA: Low-Rank Adaptation of Large Language Model Introducing ChatLLaMA: Your Personal AI Assistant Powered by LoRA!
Introducing ChatLLaMA: Your Personal AI Assistant Powered by LoRA!

 Were
excited to announce that you can now create custom personal
assistants that run directly on your GPUs! ChatLLaMA utilizes LoRA,
trained on Anthropics HH dataset, to model seamless convos between
an AI assistant & users. Plus, the "wp-smiley" src=
"https://s.w.org/images/core/emoji/14.0.0/72x72/1f525.png" style=
"height: 1em;">
Were
excited to announce that you can now create custom personal
assistants that run directly on your GPUs! ChatLLaMA utilizes LoRA,
trained on Anthropics HH dataset, to model seamless convos between
an AI assistant & users. Plus, the "wp-smiley" src=
"https://s.w.org/images/core/emoji/14.0.0/72x72/1f525.png" style=
"height: 1em;">  Know
any high-quality dialogue-style datasets? Share them with us, and
well train ChatLLaMA on them!
Know
any high-quality dialogue-style datasets? Share them with us, and
well train ChatLLaMA on them!  ChatLLaMA is currently available for 30B and 13B class="wp-smiley"
src= "https://s.w.org/images/core/emoji/14.0.0/72x72/1f914.png"
style= "height: 1em;"> Have questions or need help setting up
ChatLLaMA? Join our Discord group & ask! Lets revolutionize
AI-assisted conversations together!
ChatLLaMA is currently available for 30B and 13B class="wp-smiley"
src= "https://s.w.org/images/core/emoji/14.0.0/72x72/1f914.png"
style= "height: 1em;"> Have questions or need help setting up
ChatLLaMA? Join our Discord group & ask! Lets revolutionize
AI-assisted conversations together!  Disclaimer: trained for research, no foundation model weights, the
post was ran through gpt4 to make it more coherent.
Disclaimer: trained for research, no foundation model weights, the
post was ran through gpt4 to make it more coherent.
16:22
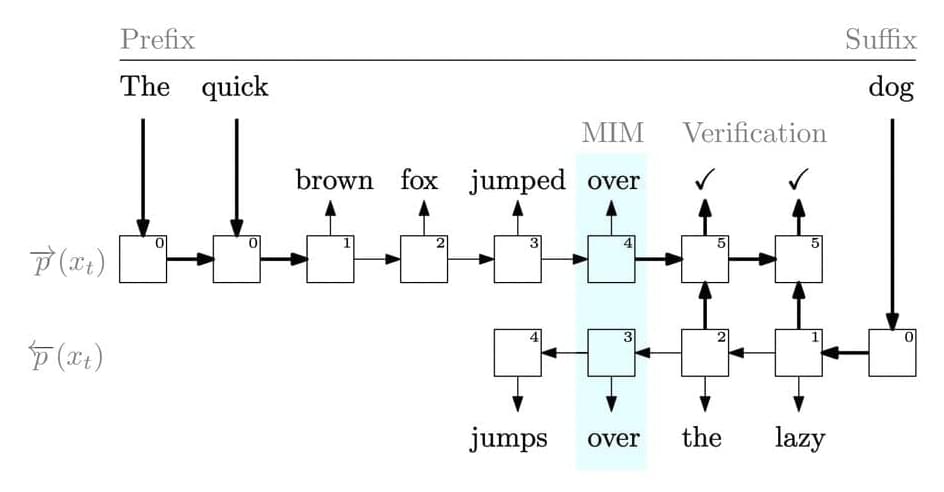
Microsoft Researchers Propose A New AI Method That Uses Both Forward And Backward Language Models To Meet In The Middle And Improve The Training Data Efficiency Lifeboat News: The Blog
Language models (LMs) have been extensively utilized for various aided writing activities, including text summarization, code completion, and paraphrasing. LMs are effective tools for creating both natural and programming languages. Most LMs must be able to develop the next token from the sequence of earlier tokens to be useful in a wide range of applications. Due to the significance of this operation, pretraining has concentrated on improving the models perplexity in predicting the next token given the last tokens. However, they do have extra information that they are not using during pretraining.
For instance, they entirely disregard the following tokens while training the model to predict one token and only condition on the prefix (prior tokens) (suffix). There are alternative approaches to include the suffix in pretraining that have yet to be discussed in the literature, even though it cannot be utilized as an input to the model. They want to increase the pretraining datas usefulness while maintaining the underlying LMs autoregressive properties. Their strategy calls for more modeling, which at first glance could appear useless. After all, an autoregressive left-to-right LM is a primary artifact created during pretraining, and the pretraining aim closely resembles how the LM is used.
Yet, there are two reasons to explore different training objectives. Data efficiency is discussed in the first. The LM is trained using a sparse, inexpensive signal that generates a probability distribution over all potential next-token selections. However, it is only supervised using the actual next token from the training set. What if a more intense kind of supervision was used during training, where the probability distribution for the next tokens was compared to a different probability distribution? The second justification relates to other connected responsibilities. For instance, the user may prefer to fill in or edit an existing sequence of tokens in many real-world settings rather than creating text entirely from scratch.
16:19
Standard Life Has in Effect Legitimised Business Fraud schestowitz.com

Official Standard Life paperwork (issued by
Standard Life) was used to legitimise fraud for over
half a decade
Summary: Its starting to look more and more like pension providers in the UK, including some very major and large ones, are aiding criminals who steal money from their workers under the guise of pensions
THIS site isnt about my work colleagues at Sirius Open Source. As explained this past month, this supposedly Open Source (not anymore!) company that was one of the FSFs early sponsors stole a lot of money from employees, myself included. This is now a criminal matter. Several managers knew what was happening; they stole money from many of us and we will put them behind bars if possible (one of them has fled to the United States already).
The pension providers are culpable too, as we shall explain in the habitual updates (maybe once or twice per week).
Former colleagues also chase the matter. Any progress on this? I asked this month. Did you file for review or something to that effect?
As it turns out, pension providers are stonewalling. They try hard to not get involved in these crime investigations. As if ignoring the victims is a wise strategy. Its not. It just makes them look complicit in cover-up. The person I blame the most is Leah Brown at Standard Life. For many weeks she kept saying my hands are tied, refusing to tell me what had actually happened. Shes a manager, so one cannot just report her to a manager. Leah Brown has made Standard Life look like part of the crime and there might be a class action lawsuit on the way. We just try to gather a list of people willing to participate in it (sharing the cost of litigation).
Do you have contact details of other past workers? I asked. Im sure quite a few had this pension and havent been keeping up with its status.
Over the past month I spoke to more former workers than I can count. Some arent surprised by this corruption; their view of the company was already mostly negative. Most of them left years ago.
We recently found out that the exisiting CEO of Sirius (last man standing so to speak) now tries to do the job of the engineers and is failing at it as they left. The former CEO left...
16:00
How to best allocate IT and cybersecurity budgets in 2023 Help Net Security
Despite the economic uncertainty, 57% of organizations plan to increase their cybersecurity budgets in 2023, according to a survey from Arctic Wolf. This highlights a powerful trend: critical needs like security must be addressed even with IT budgets tightening. As 48% of organizations rank ransomware and targeted threats as their number one concern for 2023, how can they allocate that increased cybersecurity budget effectively? In this Help Net Security video, Ian McShane, VP of Strategy More
The post How to best allocate IT and cybersecurity budgets in 2023 appeared first on Help Net Security.
16:00
RP2040 Runs Linux Through RISC-V Emulation Hackaday

Were used to running Linux on CPUs where it belongs, and the consensus is that RP2040 just isnt up for the task no memory controller, and nowhere near enough RAM, to boot. At least, thats what you might believe until you see [tvlad1234]s Linux-on-RP2040 project, reminding us theres more than one way to boot Linux on a CPU like this! Just like with the Linux on AVR project in 2012 that emulated an ARM processor, the pico-rv32ima project emulates a RISC-V core keeping up with the times.
Initially, the aforementioned Linux on AVR through ARM project was picked as a base then, a newer development, [cnlohr]s RISC-V emulator, presented itself and was too good to pass up on. Lack of RAM was fully negated by adding an SD card into the equation coupled with a small caching layer, this is a crucial part for the projects...
16:00
An Update on Sirius Open Source Pensiongate: Its Looking Worse Than Ever Techrights
Previously/context:
- Sirius Open Source and the Money Missing From the Pension
- Sirius Finished
- Sirius Open Source Pensiongate: An Introduction
- When the Pension Vanishes
- Sirius Open Source Pensiongate (Sirius Financial Crisis): Company May Have Squandered/Plundered the Pensions of Many People
- Sirius Open Source Pensiongate: Pension Providers That Repeatedly Lie to the Clients and Dont Respond to Messages
- NOW: Pensions Lies to Its Customers and Protects Abusers
- Sirius Open Source Pensiongate: Its Beginning to Look Like a Criminal Matter and Sirius is in Serious Trouble
- Sirius Open Source Pensiongate: A Long Story Merits Many Videos

Official Standard Life paperwork (issued by
Standard Life) was used to legitimise fraud for over
half a decade
Summary: Its starting to look more and more like pension providers in the UK, including some very major and large ones, are aiding criminals who steal money from their workers under the guise of pensions...
15:30
IT security spending to reach nearly $300 billion by 2026 Help Net Security
Worldwide spending on security solutions and services is forecast to be $219 billion in 2023, an increase of 12.1% compared to 2022, according to IDC. Investments in hardware, software, and services related to cybersecurity are expected to reach nearly $300 billion in 2026, driven by the ongoing threat of cyberattacks, the demands of providing a secure hybrid work environment, and the need to meet data privacy and governance requirements. Spend on security products and services More
The post IT security spending to reach nearly $300 billion by 2026 appeared first on Help Net Security.
15:13
Services and Users TRApped in Telescreen-Running Apps Techrights
New article by Alexandre Oliva (FSF Board, Linux-libre etc.)
Summary: TRApp, term that lends its name to this article, is short for "Telescreen-Running App". It sounds just like "trap". Any similarity is not purely coincidental.
Ive noticed a worrisome pattern, in Brazil, wherein companies and even governments entice users to install apps on portable telescreening devices, handheld versions of the telescreens in George Orwell's 1984, also known as smart mobile telephones, pocket electronic ankle tag, or Stalin's dream. They advertise benefits to customers over the same services previously delivered preferentially through web sites and browsers, when these alternatives aren't removed entirely.
As Big Bad Wolf disguised as grandma would respond, "my TRApps are so big the better to see you, dear, and the tighter to hold you." That's surveillance capitalism at work. But do they have any teeth?
First, allow me to detail my observations. It's not just multiple utilities, private businesses and governments advertising they now have apps on both major (nonfree) mobile TRApp stores, that offer similar services to those already available on a web site, but now without the alleged hassle of authenticating every time. It's not just that, while you hold on the phone waiting for a human attendant, recorded messages are played insisting for you to try the TRApp.
What catches my attention is when online merchants offer significant discounts, store credit or free shipping, but only if you make the purchase in the TRApp, rather than their web shop. That gas station chains offer discounts when you pay for your fuel using their TRApp rather than even cash or bank transfer. When banks want you to use their TRApps so bad that they won't just stop adding features to the web site, as if it was legacy abandonware, but will discontinue features that used to be available on the web site, for no reason other than to force you into their TRApps.
Various government agencies now issue virtual documents, such as id card, driver's and car license, voter id, proof of military service and of vaccination, proof of purchases, the list goes on and on but though they look essentially the same as their paper equivalents, and several of them contain even QR codes for validation, some of them are only valid when displayed by the official TRApp. Taking and carrying a digital picture of the paper document won't do, even when a paper copy of the document would!
Most busines...
15:00
Most mid-sized businesses lack cybersecurity experts, incident response plans Help Net Security
99% of all businesses across the United States and Canada are mid-sized businesses facing cybersecurity challenges, according to a Huntress report. Aimed to gain insights into organizational structure, resources and cybersecurity strategies, the results contextualize challenges across core functions including gaps in toolkits, planning, staffing, security awareness training and difficulty to secure cybersecurity insurance. Mid-sized businesses cybersecurity challenges 49% of mid-sized businesses plan to budget more for cyber security in 2023 In the last twelve More
The post Most mid-sized businesses lack cybersecurity experts, incident response plans appeared first on Help Net Security.
13:56
Can ChatGPT Write Better SQL Than a Data Analyst? SoylentNews
Extracting information from databases requires skill and
knowledge of query languages like SQL (Structured Query
Language).
Natural language querying (NLQ) which is also called Text-to-SQL
allows formation of information retrieval questions without
knowledge of database-specific languages. ChatGPT is the next level
in this area.
Data analyst Marie Truong challenged ChatGPT to write better SQL in January. She is comparing valid SQL syntax, query structure, correct results, and runtime. The result? ChatGPT got 50% of it wrong.
One of many new articles about this topic tries to convert database schemas into natural language as part of chatgpt prompts to provide more precise outcomes:
There has been an expectation that ChatGPT could assist in creating database queries, just as it can assist in creating computer programs. However, creating database queries requires an understanding of the database itself, and there is no conventional way to represent database semantics.
We present a solution to this problem by developing a set of syntax that can represent database semantics, such as table structure and relationships, in natural language. This allows for the creation of semantic representations of databases that can be understood by ChatGPT and enable it to perform database management tasks.
Experiment 2:
A SQL query needs to properly join four tables: careplans, providers, patients, and encounters. The encounters table plays a critical role here as it connects the patients table with the careplans table. This information is typically contained in an Entity Relationship schema.ChatGPT has successfully generated the query that results in a correct view.
There has been a research about generating SQL queries from natural language since 2016.
Read more of this story at SoylentNews.
13:33
Links 19/03/2023: Release of Libreboot 20230319 and NATO Expanding Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
9to5Linux 9to5Linux Weekly Roundup: March 19th, 2023
This week was a bit slow i...
-
13:19
Great Things Brewing Techrights
Summary: Weve been very busy behind the scenes this past week; we expect some good publications ahead
OVER the past few days weve barely published anything because we did lots of work related to tooling and workflow instead. Files were added to Git last night and weve just caught up with a lot of links. Daily Links are very important, orginal articles ideally contain exclusive (original) material. Trying to hold my former employer accountable for actual crimes takes a lot of time and in addition to this weve been investing in the sites future by writing a bunch of supportive programs. Python, Perl, Bash
Over the past few days we stumbled upon some truly encouraging news too.This coming week or fortnight we expect to have some exclusive EPO material. It might even be historic. We want to hold Antnio Campinos accountable; his appointer, Benot Battistelli, was never held accountable for some very serious crimes, which should really embarrass Europe.
Over the past few days we stumbled upon some truly encouraging news too. We intend to write about some of them, seeing that the media and social control media arent willing to.
Techrights is serving a likely unprecedented 7-8MB/second this weekend. Its mostly because of the RMS talk and partly because of Ken Thompson.
13:00
A Look at Zweikanalton Stereo Audio and Comparison With NICAM Hackaday

With how we take stereo sound for granted, there was a very long period where broadcast audio and television with accompanying audio track were in mono. Over the decades, multiple standards were developed that provide a way to transmit and receive two mono tracks, as a proper stereo transmission. In a recent video, [Matt] over at [Matts Tech Barn] takes a look at the German Zweikanalton (also known as A2 Stereo) standard, and compares it with the NICAM standard that was used elsewhere in the world.
Zweikanalton is quite simple compared to NICAM (which we covered previously), being purely analog with a second channel transmitted alongside the first. Since it didnt really make much of a splash outside of the German-speaking countries, equipment for it is more limited. In this video [Matt] looks at the Philips PM 5588 and Rohde & Schwarz 392, analyzing the different modulations for FM, Zweikanalton and NICAM transmissions and the basic operation of the modulator and demodulator equipment.
An interesting aspect of these modulations are the visible sidebands, and the detection of which modulatio...
12:23
Books: Hundreds of books created by artificial intelligence (AI) tool ChatGPT are flooding Amazon, showing the way the technology can be adopted to produce books at scale Lifeboat News: The Blog
Hundreds of books created by artificial intelligence (AI) tool ChatGPT are flooding Amazon, showing the way the technology can be adopted to produce books at scale.
Nearly 300 titles that claim to be written solely by or in collaboration with ChatGPT are listed on the online booksellers website, across a range of genres including non-fiction, fantasy and self-help.
Many of the books appear to be published using Amazons Kindle Direct Publishing tool, which allows users to quickly create, publish and promote their work using a modern-day equivalent of the self-publishing model.
12:23
On the Origin of Time: Stephen Hawkings mind-blowing final theory Lifeboat News: The Blog
Everything, everywhere, all at once? Forget it there are ideas about time far more outrageous than simply the multiverse Who knows where the time goes? asked Sandy Denny, though as good a question is where it came from in the first place.
12:22
A Leaning Tower of Pisa-Sized Asteroid Will Sweep Lifeboat News: The Blog

A newly discovered asteroid called 2023 DW has generated quite a buzz over the past week due to an estimated 1-in-670 chance of impact on Valentines Day 2046. But despite a NASA advisory and the resulting scary headlines, theres no need to put an asteroid doomsday on your day planner for that date.
The risk assessment doesnt have as much to do with the probabilistic roll of the cosmic dice as it does with the uncertainty thats associated with a limited set of astronomical observations. If the case of 2023 DW plays out the way all previous asteroid scares have gone over the course of nearly 20 years, and further observations will reduce the risk to zero.
Nevertheless, the hubbub over a space rock that could be as wide as 165 feet (50 meters) highlights a couple of trends to watch for: Were likely to get more of these asteroid alerts in the years to come, and NASA is likely to devote more attention to heading off potentially dangerous near-Earth objects, or NEOs.
11:22
Kernel prepatch 6.3-rc3 LWN.net
The 6.3-rc3
kernel prepatch is out for testing. "So rc3 is fairly big, but
that's not hugely usual: it's when a lot of the fixes tick up as it
takes a while before people find and start reporting
issues.
"
11:14
DistroWatch Weekly, Issue 1011 DistroWatch.com: News
This week in DistroWatch Weekly: Review: Serpent OS, Security Onion 2.3, and Gentoo LiveNews: Canonical offers "Pro" support for aging Ubuntu 18.04, openSUSE sees surge in downloads, Debian runs election with one potential Project LeaderQuestions and answers: Replacing the scp utilityReleased last week: Qubes OS 4.1.2, Kali Linux....
11:07
How a Beam of Pellets Could Blast a Probe Into Deep Space SoylentNews
If you want a spacecraft that can explore beyond the solar systemand you don't want to wait decades for it to get thereyou need one that can really move. Today's chemical rockets and solar-powered probes are downright poky on interstellar scales. Artur Davoyan has a completely different idea for how to accelerate a spacecraft to extreme speeds: pellet-beam propulsion.
Here's the gist of how it would work: First, you actually need two spacecraft. A probe blasts off on a one-way trip to deep space, while a second vehicle remains locked in an Earth orbit and fires thousands of tiny metallic pellets at its partner every second. The orbiting craft also either fires a 10-megawatt laser beam at the retreating probe, or aligns a laser fired from the ground at it. The laser hits the pellets, heats them, and ablates them, so that part of their material melts and becomes plasmaa hot cloud of ionized particles. That plasma accelerates the pellet remnants, and this pellet beam provides thrust to the spacecraft.
Alternatively, Davoyan thinks the probe could get thrust from the pellet beam if the craft were to deploy an on-board magnetic field-generating device to deflect the pellets. In this case, that magnetic action would push the craft forward.
Such a system could boost a 1-ton probe to speeds up to 300,000 miles per hour. That's slow compared to the speed of light, but more than 10 times faster than conventional propulsion systems.
It's a theoretical concept, but realistic enough that NASA's Innovative Advanced Concepts program has given Davoyan's group $175,000 to show that the technology is feasible. "There's rich physics in there," says Davoyan, a mechanical and aerospace engineer at UCLA. To create propulsion, he continues, "you either throw the fuel out of the rocket or you throw the fuel at the rocket." From a physics perspective, they work the same: Both impart momentum to a moving object.
Read more of this story at SoylentNews.
11:00
HPR3816: Post Apocalyptic 4s5 Battery Pack Hacker Public Radio
HR000000000 H Hybrid: Denotes some prepurchased or hard to find components R Robotics: suitable for robots buy: 4s 40A BMS https://www.aliexpress.com/item/4000025857655.html (can't specifically vouch for this vendor, just chose the first that came up) make sure to choose 4s and balance find or buy materials: duct or gorilla tape, trashed computer dvd or cd drive, 20 18650 cells, molex connectors(you can also use barrel jacks or whatever you want to transfer power), wire and maybe 'tab wire' https://nl.aliexpress.com/item/32650006768.html solder everything together as per schematic and pictures (there is theoretically a danger in soldering cells, but I have never had a problem. Have a pair of pliers and a nearby window handy to throw them out of if anything goes wrong) wrap in cardboard and tape as per pictures add the cd/dvd drive lids(if you taped well you won't short anything and burn your house down tape dvd lids to battery Getting into the battery for maintenance just requires a utility knife. Watt Hour does a great job describing the 3s BMS, which is very similar to the 4s used in my case: https://yewtu.be/watch?v=QNENyu97w2A Battery Schematic Click the thumbnail to see the full-sized image Cut through tape to reveal battery Click the thumbnail to see the full-sized image Flat metal holds cells together Click the thumbnail to see the full-sized image Detail of 4.2v Click the thumbnail to see the full-sized image Only have to desolder one side Click the thumbnail to see the full-sized image New cells in Click the thumbnail to see the full-sized image Make sure there is thick tape covering battery
K-12 Computing Education in Four African Countries It Will Never Work in Theory
For a few months in 2021 and 2022, it looked like technical conferences might start being more globally inclusive. COVID-19 restrictions meant that even people from affluent countries couldn't travel, so there was finally an effort to create a level playing field for remote attendance. It didn't last: all of the conferences I might have attended this year provided off-site options, but none of them included all of their talks, workshops, and gatherings. My colleagues in Latin America and Africa are therefore shut out of the conversation once again because of visa issues, travel costs, and a dozen other obstacles. As one of them said to me in frustration, "If people from Google and Stanford had to deal with this shit, the ACM would make Zoom conferences mandatory."
People from less affluent regions of the world are often left out of research as well: as that same colleague observed, there have probably been more studies of how students in Washington State program than of students from the whole of Latin America. This paper is a step toward closing that gap. In it, the authors present results from a survey of computer science educators in four African countries and compare them both to each other and to more affluent countries. Barriers to professional development are reported alongside what people actually teach, and some shortcomings of the analysis framework itself are discussed. The authors intend to repeat their survey in coming years, and I look forward to reading those sequels.
Ethel Tshukudu, Sue Sentance, Oluwatoyin Adelakun-Adeyemo, Brenda Nyaringita, Keith Quille, and Ziling Zhong. Investigating K-12 computing education in four African countries (Botswana, Kenya, Nigeria, and Uganda). ACM Transactions on Computing Education, 23(1):129, Jan 2023. doi:10.1145/3554924.
Motivation. As K-12 computing education becomes more established throughout the world, there is an increasing focus on accessibility for all, whether in a particular country or setting or in areas of the world that may not yet have computing established. This is primarily articulated as an equity issue. The recently developed capacity for, access to, participation in, and experience of computer science education (CAPE) Framework is one way of demonstrating stages and dependencies and understanding relative equity, taking into consideration the disparities between sub-populations. While there is existing research that covers the state of computing education and equity issues, it is mostly in high-income countries; there is minimal research in the context of low-middle-income countries like the sub-Saharan African countries.
Objectives. The objective of the article is therefore to report on a pilot study investigating the capacity (...
10:05
(Even more) Aggressive randomisation of stack location OpenBSD Journal
In a late-stage addition prior to the release of OpenBSD 7.3, Mark Kettenis
(kettenis@) has committed
[more] aggressive randomisation of the stack location for all
64-bit architectures except alpha:
10:00
Hackaday Links: March 19, 2023 Hackaday

We get results! Well, sort of. You may recall that in this space
last
week we discussed Fords plans to exclude AM reception on the
infotainment systems of certain of their cars starting in 2024. We
decried the decision, not for the loss of the sweet, sweet content
that AM stations tend to carry although we always enjoyed Traffic
on the 8s back in our dismal days of daily commuting but rather as
a safety concern, because AM radio can reach almost the entire US
population with emergency information using just 75 stations. To
our way of thinking, this makes AM radio critical infrastructure,
and eliminating it from motor vehicles is likely to have unintended
consequences. Now it seems like theres some agreement with that
position, as former administrators of FEMA (Federal Emergency
Management Administration; and no, not FEDRA) have gotten together to warn about the
dangers of deleting AM from cars. Manufacturers seem to be leaning
into the excuse that EVs emit a lot of radio frequency
interference, rendering static-sensitive AM receivers less useful
than other, more profitable less susceptible modes, like
digital satellite radio. Th...
09:56
rpki-client 8.3 released OpenBSD Journal
One small but significant step for routing security on the Internet happened Sunday 19th of March 2023 with the "https://man.openbsd.org/rpki-client.8">rpki-client.
The announcement reads,
Subject: rpki-client 8.3 released From: Sebastian Benoit <benno () openbsd ! org> Date: 2023-03-19 12:46:27 rpki-client 8.3 has just been released and will be available in the rpki-client directory of any OpenBSD mirror soon. rpki-client is a FREE, easy-to-use implementation of the Resource Public Key Infrastructure (RPKI) for Relying Parties (RP) to facilitate validation of BGP announcements. The program queries the global RPKI repository system and validates untrusted network inputs. The program outputs validated ROA payloads, BGPsec Router keys, and ASPA payloads in configuration formats suitable for OpenBGPD and BIRD, and supports emitting CSV and JSON for consumption by other routing stacks.
09:30
08:45
Security Affairs newsletter Round 411 by Pierluigi Paganini Security Affairs
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are free for you in your email box.
If you want to also receive for free the newsletter with the international press subscribe here.
08:30
07:56
Linux 6.3-rc3 Released: It's "Fairly Big" Phoronix
Linus Torvalds just released Linux 6.3-rc3 as the latest weekly test candidate for the in-development Linux 6.3 kernel that is slated to debut as stable toward the end of April...
07:27
Filmmakers Want Owner of Defunct VPN Arrested in Piracy Case TorrentFreak
 Over
the past two decades, online piracy has proven a massive challenge
for the entertainment industries.
Over
the past two decades, online piracy has proven a massive challenge
for the entertainment industries.
Some copyright holders have pursued legal action against individual pirates, but today its not uncommon for third-party intermediaries to also be considered legitimate targets.
Over the past several years, internet service providers, hosting companies, and VPN providers have faced infringement liability lawsuits. Most of the VPN companies chose to settle disputes but when LiquidVPN was sued, the provider simply ignored the lawsuit.
Filmmakers Win $15m in LiquidVPN Lawsuit
LiquidVPN was previously owned by David Cox, who was initially listed as a defendant. As the case progressed it emerged that Cox had sold the VPN provider before the lawsuit was filed, with Puerto Rico company 1701 Management identified as the buyer.
Despite facing serious allegations, 1701 Management and its alleged owner, Charles Muszynski, failed to answer the claims filed at a federal court in Florida. This prompted the film companies to request a default judgment of more than $15 million, which was eventually granted a year ago.
The default judgment marks the end of the road on the question of liability but doesnt necessarily mean that the filmmakers automatically get the money. As it turns out, that can be quite a challenge.
Chasing The Money
Over the past several months, the filmmakers attorney Kerry Culpepper has submitted several writs of garnishment to the court. Through these requests, the court can order the seizure of property owned or controlled by the debtors.
In this case, those efforts targeted a yacht, docked at a Florida harbor, and various other types of properties. In addition, the filmmakers obtained a worldwide restraining order against the assets of Mr. Muszynski, 1701 Management, and the third defendant AUH2O.
This hunt for assets connected several companies to Muszynski, including the New Mexico company WasteResources LLC. According to the legal paperwork, there is evidence to show that the company is owned and controlled by the defendant.
07:00

[Arca] sets out to build himself a low-cost pen plotter that doesnt require access to a 3D printer. The plotter uses a coreXY arrangement, powered by 28BYJ-48 stepper motors, which he overdrives with +12 VDC to increase the torque. Pen up and down control is done using a stepper motor salvaged from a DVD reader. The frame is constructed using PVC electrical conduit and associated fittings, and [Arca] uses the hot glue gun quite liberally. Steppers were driven by A4988 modules with heatsinks, and motion control is provided by GRBL running on an Arduino UNO.
He has a few issues with glitches on the limit switches, and is continuing to tweak the design. There is no documentation yet, but you can discern the construction easily from the video if you want to try your hand at making one of these. This is a really cool DIY plotter, and many parts you probably have laying around your parts boxes. As [Arca] says, its not an AxiDraw, but the results are respectable. Keep a lookout for part 2 of this project on his YouTube channel.
...
06:24
Globalization is Over, According to TSMC Founder SoylentNews
Free trade not quite as dead, 'but it's in danger' says Morris Chang:
Globalization is over, at least for the chip industry, and this will mean higher chip prices, according to semiconductor contract manufacturer giant TSMC. Despite this, the company's founder said he supports US actions to slow the development of China's chip technology.
The Taiwanese chip company is caught up in the ongoing semiconductor battle between the superpowers, where the US is trying to prevent China from getting access to cutting edge technology that might be used by its burgeoning military. At least, that is the reason given.
At an event hosted by Taiwan's CommonWealth Magazine in Taipei, retired TSMC founder Morris Chang said that efforts to contain China were leading to a split in the global supply chain that would likely increase prices and could have an effect on chip availability.
"There's no question in my mind that, in the chip sector, globalization is dead. Free trade is not quite that dead, but it's in danger," Chang said.
[...] It has already been noted that US efforts to isolate China are leading to an undoing of the distributed global supply chain infrastructure that has built up over the past few decades.
Richard Gordon, practice vice president for semiconductors and electronics at Gartner, told us earlier this year the outcome may be a world divided into China-centric and US-Europe-centric networks of supply chains and a greater self-reliance within those blocks.
Meanwhile, TSMC is also discussing subsidies with officials for the German state of Saxony about a new fabrication plant the chip giant is aiming to build there, despite publicly stating in December that it had no plans to site any facilities in Europe.
Read more of this story at SoylentNews.
05:57
Monitoring the QO-100 WB transponder usage with Maia SDR Daniel Estvez
I am interested in monitoring the usage of the QO-100 WB transponder over several weeks or months, to obtain statistics about how full the transponder is, what bandwidths are used, which channels are occupied more often, etc., as well as statistics about the power of the signals and the DVB-S2 beacon. For this, we need to compute and record to disk waterfall data for later analysis. Maia SDR is ideal for this task, because it is easy to write a Python script that configures the spectrometer to a low rate, connects to the WebSocket to fetch spectrometer data, performs some integrations to lower the rate even more, and records data to disk.
For this project Ive settled on using a sample rate of 20 Msps, which covers the whole transponder plus a few MHz of receiver noise floor on each side (this will be used to calibrate the receiver gain) and gives a frequency resolution of 4.9 kHz with Maia SDRs 4096-point FFT. At this sample rate, I can set the Maia SDR spectrometer to 5 Hz and then perform 50 integrations in the Python script to obtain one spectrum average every 10 seconds.
Part of the interest of setting up this project is that the Python script can serve as an example of how to interface Maia SDR with other applications and scripts. In this post I will show how the system works and an initial evaluation of the data that I have recorder over a week. More detailed analysis of the data will come in future posts.
The Python script Im using can be found here. It uses the Python requests package to configure Maia SDR using its REST API, the websockets package to connect to the spectrometer WebSocket, and NumPy to average groups of 50 spectra together and write them to a file, as well as writing timestamps to another file. Dealing with the spectrometer WebSocket is really simple. Each message provides a 4096-point spectrum (in linear unit), which we can convert to a NumPy array by doing
np.frombuffer(await ws.recv(), 'float32')The script produces two output files: a file with the spectrum data in float32 format, and a file with the timestamps in datetime64[ns] format.
I have set up a Pluto in my shack connected to the 750 MHz IF of my QO-100 groundstation. A LimeNET board that I had around is acting as USB to Ethernet bridge, but any Raspberry P...
05:34
Read "Building Commercial Space Infrastructure" (PDF) by our Alex Thatcher and Keith Taggart. Lifeboat News
Read "Building Commercial Space Infrastructure" (PDF) by our Alex Thatcher and Keith Taggart.
04:54
Lowes Market chain leaves client data up for grabs Security Affairs
A misconfiguration on a website owned by the US-based Lowes Market grocery store chain could have allowed threat actors to gain control of its systems.
On February 7, the Cybernews research team discovered a misconfiguration on the Lowes Market website. The supermarket chains website was leaking a treasure trove of private credentials, which left the company vulnerable to potential attacks by cybercriminals.
Together, the compromised credentials could enable an unscrupulous hacker to gain control of most of the online stores functionality, see sensitive customer information, and abuse access to paid services, all while putting Lowes Market customers at risk.
With almost 150 locations, the Lowes chain primarily operates stores in Texas, New Mexico, Colorado, Arizona, and Kansas.
At the time of writing, the company has already fixed the issue. Cybernews reached out to Lowes Market regarding the details of the misconfiguration and the possible duration of data exposure. However, the company has yet to provide a response to the inquiry.
Access to databases
Researchers found a publicly accessible environment file (.env) hosted on the Lowes Market website. Public access to the file posed a risk to the security of the companys systems, as it was leaking sensitive data and numerous credentials.
An examination of the environment file suggests that the developers were not following the best practices, while poor security configurations might have led to more secrets, an industry term for vital data that should be kept private, being exposed.
The leaked secrets could have allowed threat actors to access databases as the hosts, usernames, and ports of main, tracking, legacy, recipe, and redis.io databases were exposed.
Database hosts and credentials are considered sensitive information, as they are used to access respective databases and their contents. In the case of Lowes Market, most database hosts are internet-connected, making it particularly easy for threat actors to access them.
04:26
04:00
The Intricacies of Starting a Rocket Engine Hackaday

Rockets are conceptually rather simple: you put the pointy bit upwards and make sure that the bit that will go flamey points downwards before starting the engine(s). Yet how to start each rocket engine type in a way thats both safe and effective? Unlike in the Wile E. Coyote cartoons, real-life rocket engines do not have a fuse you light up before dashing off to a safe distance. Rather they use increasingly more complicated methods, which depend on the engine type and fuels used. In a recent article written by [Trevor Sesnic] with accompanying video featuring everyones favorite Everyday Astronaut [Tim Dodd], were taken through the intricacies of how flamey ends are made.
The least complicated are probabl...
03:29
Re: First result on google promotes insecure coding (XSS) Open Source Security
Posted by Georgi Guninski on Mar 19
No. Since this issue is already public, lol, let me see who fromthe community contacts them first. btw, I strongly suspect there are
many more buggy tutorials.
02:49
Version 16.0.0 of the LLVM compiler suite has been released. As usual, the list of changes is long; see the specific release notes for LLVM, Clang, Libc++, and others linked from the announcement.
02:39
The FSF's Free Software Awards LWN.net
The Free Software Foundation has announced the recipients of this year's Free Software Awards:
- Eli Zaretskii (advancement of free software)
- Tad (SkewedZeppelin) (outstanding new free software contributor)
- GNU Jami (project of social benefit)
02:25
How much fuel is left in this 20-year-old Mars orbiter? Lifeboat News: The Blog
Designing, building, and launching a spacecraft is hugely expensive. Thats why NASA missions to Mars are designed with the hope that theyll last as long as possible like the famous Opportunity rover which was supposed to last for 90 days and managed to keep going for 15 years. The longer a mission can keep running, the more data it can collect, and the more we can learn from it.
Thats true for the orbiters which travel around Mars as well as the rovers which explore its surface, like the Mars Odyssey spacecraft which was launched in 2001 and has been in orbit around Mars for more than 20 years. But the orbiter cant keep going forever as it will eventually run out of fuel, so figuring out exactly how much fuel is left is important but it also turned out to be more complicated than the NASA engineers were expecting.
Odyssey started out with nearly 500 pounds of hydrazine fuel, though last year it looked as if the spacecraft was running much lower on fuel than had been predicted.
02:24
NASAs Parker Solar Probe makes its 15th close flyby of the sun this St. Patricks Day Lifeboat News: The Blog
NASAs sun-touching Parker Solar Probe spacecraft will celebrate St. Patricks Day (March 17) by making another close approach to our star. While people all over Earth enjoy a cold beer, the spacecraft will brave blisteringly hot temperatures as high as 2,500 degrees Fahrenheit (1,400 degrees Celsius) as it makes its 15th close approach to the sun, or perihelion.
According to NASAs Parker Solar Probe website, (opens in new tab) the exact time of the close approach will be 4:30 p.m. EDT (2030 GMT) when the spacecraft comes to within around 5.3 million miles (8.5 million km) of the suns surface, the photosphere.
02:24
SpaceX now eyeing April for Starships 1st orbital launch, Elon Musk says Lifeboat News: The Blog

SpaceXs huge new Starship vehicle could launch on its first-ever orbital test flight a little over a month from now, if all goes according to plan.
SpaceX is now tentatively eyeing mid-to late April for that epic mission, which will lift off from the companys Starbase facility in South Texas.
02:24
This insertable 3D printer will repair tissue damage from the inside Lifeboat News: The Blog

Researchers at the University of New South Wales, Sydney, have developed a flexible 3D bioprinter that can layer organic material directly onto organs or tissue. Unlike other bioprinting approaches, this system would only be minimally invasive, perhaps helping to avoid major surgeries or the removal of organs. It sounds like the future at least in theory but the research team warns its still five to seven years away from human testing.
The printer, dubbed F3DB, has a soft robotic arm that can assemble biomaterials with living cells onto damaged internal organs or tissues. Its snake-like flexible body would enter the body through the mouth or anus, with a pilot / surgeon guiding it toward the injured area using hand gestures. In addition, it has jets that can spray water onto the target area, and its printing nozzle can double as an electric scalpel. The team hopes its multifunctional approach could someday be an all-in-one tool (incising, cleaning and printing) for minimally invasive operations.
The F3DBs robotic arm uses three soft-fabric-bellow actuators using a hydraulic system composed of DC-motor-driven syringes that pump water to the actuators, as summarized by IEEE Spectrum. Its arm and flexible printing head can each move in three degrees of freedom (DOFs), similar to desktop 3D printers. In addition, it includes a flexible miniature camera to let the operator view the task in real time.
02:24
02:23
Anaximander review: Did Anaximander create science, asks Carlo Rovelli Lifeboat News: The Blog
Ancient philosopher Anaximanders discoveries about rain, wind and the cosmos may make him the true force behind modern science, argues physicist Carlo Rovelli in his newly republished first book.
By Simon Ings
02:23
02:23
Scientists in Singapore Have Discovered How to Talk to Plants Lifeboat News: The Blog

Plants emit weak electric signals. Researchers have developed a device to read and send signals back a type of plant communication.
02:23
The fifth force: Is there another fundamental force of nature? Lifeboat News: The Blog
In recent years, a group of Hungarian researchers have made headlines with a bold claim. They say theyve discovered a new particle dubbed X17 that requires the existence of a fifth force of nature.
The researchers werent looking for the new particle, though. Instead, it popped up as an anomaly in their detector back in 2015 while they were searching for signs of dark matter. The oddity didnt draw much attention at first. But eventually, a group of prominent particle physicists working at the University of California, Irvine, took a closer look and suggested that the Hungarians had stumbled onto a new type of particle one that implies an entirely new force of nature.
Then, in late 2019, the Hungarian find hit the mainstream including a story featured prominently on CNN when they released new results suggesting that their signal hadnt gone away. The anomaly persisted even after they changed the parameters of their experiment. Theyve now seen it pop up in the same way hundreds of times.
02:23
10 Quantum Myths That Need to be Busted Lifeboat News: The Blog
The very word quantum makes peoples imaginations run wild. But chances are youve fallen for at least one of these myths.
01:41
Intel's Xeon W9-3495X Can Draw 1,900W of Power SoylentNews
Intel's new HEDT CPU leaves behind Skylake-X in terms of power consumption:
Intel's recently introduced Xeon W9-3495X processor packs 56 cores begging you to overclock them, as the CPU also features an unlocked multiplier. When cooled down using liquid nitrogen, the 56-core processor can indeed be pushed to a formidable 5.50 GHz frequency, but at such high clocks it alone consumes almost 1,900 watts, more than beefy high-end gaming PCs, reports HardwareLuxx.
Elmor, a professional overclocker who collaborates with Asus, recently tried to push a Xeon W9-3495X 'Sapphire Rapids-SP' CPU on an Asus Pro WS W790E Sage SE motherboard to its limits with liquid nitrogen cooling. When frozen to -92.8 degrees Celsius/-135 degrees Fahrenheit, the CPU can work at 5.50 GHz and hit 132,220 points in Cinebench R23, which is just a little bit lower than the absolute record of 132,484 points set by another heavily overclocked Xeon W9-3495X. But the result comes at a cost.
The heavily overclocked Intel Xeon W9-3495X processor not only demonstrates phenomenal performance in Cinebench R23, but it also sets record in terms of power consumption. The CPU draws as much as 1,881W power when operating at 5.50 GHz and requires two 1,600W PSUs to feed it.
[...] Without any doubts, hitting 5.50 GHz with a 56-core Xeon W9-3495X processor cooled down using liquid nitrogen is a monumental achievement. Yet, it remains to be seen what makers of boutique factory-overclocked extreme workstations manage to squeeze out of this CPU with a production-grade cooling system and guaranteed long-term stability.
Read more of this story at SoylentNews.
01:20
Libreboot 20230319 Released With ThinkPad T530/W530 Support Phoronix
Libreboot 20230319 has been released as the downstream of Coreboot focused on providing only pure open-source firmware replacements to proprietary BIOS/UEFI platforms compared to all the blobs permitted in upstream Coreboot...
01:01
Re: First result on google promotes insecure coding (XSS) Open Source Security
Posted by Solar Designer on Mar 19
Georgi, are you part of the community? Do you have a plan you're goingto follow yourself or/and recommend to others? If so, please share it.
It's easy to distance yourself from the community and criticize it, or
to claim there isn't a community like you seem to imply by the quotes.
It's more effort to be part of the community and actually do things.
Sometimes this involves figuring out the author's contact address...
01:00
3D-Printed Shredder Eats Lettuce For Breakfast Hackaday

Shredding things isnt just good for efficiently and securely disposing of them. Its also very fun, as well. [Joonas] of [Lets Print] didnt have a shredder, so set about 3D printing one of their very own.
The design apes that of the big metal trash shredders youve probably seen in videos all over the internet. They use a pair of counter-rotating drums with big teeth. As the drums turn, the teeth grab and pull objects into the gap between the drums, where they are duly torn apart into smaller pieces.
In this design, plastic drums are pressed into service as [Joonas] does not have a metal 3D printer. A brushed DC motor is used to drive the shredder. A large multi-stage gearbox is used to step down the motors output and provide plenty of torque to do the job.
The shredder gets tested with ple...
00:46
Links 19/03/2023: LLVM 16.0.0 and EasyOS Kirkstone 5.1 Releases Techrights
![]()
Contents
- GNU/Linux
- Desktop Environments/WMs
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Linux Links Linux Around The World: Albania
We cov...
-
00:42
Linux 6.3-rc3 Adding Protection From Malicious Guests Hammering AMD's Secure Processor Phoronix
A change sent in this Sunday ahead of the Linux 6.3-rc3 release is a late addition adding a throttling mechanism to protect the hypervisor from potentially malicious AMD Secure Encrypted Virtualization (SEV) guests. The change is to protect the AMD Secure Processor from being potentially overloaded with requests by nefarious guest VMs...
00:21
First result on google promotes insecure coding (XSS) Open Source Security
Posted by Georgi Guninski on Mar 19
"tutorial python cgi" returns as first result [1]on tutorialspoint.com
In "Simple URL Example:Get Method"
```
first_name = form.getvalue('first_name')
last_name = form.getvalue('last_name')
print "<h2>Hello %s %s</h2>" % (first_name, last_name)
```
Besides cgi tutorial, this is XSS and CSRF tutorial by example.
Does the so called security "community" plan to reduce...
00:20
Serpent OS Build Infrastructure Launched Phoronix
Serpent OS as the new Linux distribution project by Solus Linux founder Ikey Doherty has made public its build infrastructure as it begins building more packages and opening up packaging work to outside contributors...
00:18
NBA is warning fans of a data breach after a third-party newsletter service hack Security Affairs
The NBA (National Basketball Association) disclosed a data breach after a third-party firm providing a newsletter service was breached.
The NBA (National Basketball Association) is notifying followers of a data breach after a third-party company providing a newsletter service was breached.
The National Basketball Association (NBA) is a professional basketball league in Northern America composed of 30 teams (29 in the United States and 1 in Canada). It is one of the major professional sports leagues in the United States and Canada and is considered the premier mens professional basketball league in the world.
NBA launched an investigation into the security breach with the support of external cybersecurity experts to determine the extent of the incident.
The NBA pointed out that its systems were not impacted, according to the data breach notification sent to the fans, the incident affected an unknown number of individuals.
BleepingComputer, which first reported the news, confirmed that some fans personal information was stolen.
According to the association, an unauthorized third party accessed and created copies of the names and email addresses of some of its fans. The data breach did not compromise usernames, passwords, and other information.
We recently became aware that an unauthorized third party gained access to, and obtained a copy of, your name and email address, which was held by a third-party service provider that helps us communicate via email with fans who have shared this information with the NBA, reads the data breach notification, as reported by BleepingComputer.
There is no indication that our systems, your username, password, or any other information you have shared with us have been impacted.
Even if credentials were not exposed as a result of this incident, fans must be vigilant for phishing attacks and other fraudulent activities that could target them by abusing the exposed information.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs hacking, NBA)
The post...
00:15
Registration And Verification On The Mostbet Website h+ Media
Registration And Verification On The Mostbet Website
The app features a user-friendly interface and an intensive choice of fee and bonuses systems. The amount of sports supported is excessive and there are plenty of chips which you should use to increase your comfort and capital. Further, these bonuses differ only in the wagering guidelines, which mostbet clients can learn within the promotions part about.
The best method to clear up all of your troubles with playing and enjoying on line on line casino video games is to contact the help staff of Mostbet. There is a intensive number of the best way to get into conversation with Mostbet managers. Furthermore, the Geopoll Survey found that 79 p.c of bets positioned in Kenya are on football games, making the nation the main in football betting. In 2018, Kenyans went on-line of their numbers and searched for betting and sports-related sites, a new report has confirmed. A massive 11 of the highest 20 Google search queries have been immediately related to betting. Whilst the rest wager largely as soon as a month, a majority of Kenyans guess as quickly as every week with sports betting, particularly football being essentially the most most popular.
The Android os and iPhone apps can be found for download on the options of the game, plus the capability to bet on in style events. You may even change your quick bet amount and watch the betting options and obtainable odds. [newline]To set up the appliance, enter the Mostbet web site, after that a working obtain hyperlink might be displayed, then observe the hyperlink, obtain and register. In addition to themed slots, yow will discover lots of desk video video games at this firm. They at the moment are on the market to clients from Norway in a brand new format.
Many new customers now using the companys service regularly have used the simple steps from the instructions under. This category can give you a wide selection of hand types that influence the difficulty of the recreation and the size of the winnings. Sites strategies of replenishment.The withdrawal is on the market solely after verification of the account utilizing one of many listed methods. With that, you even have Indian keep on line on line casino games like Andar Bahar and Teen Patti! You might uncover different well-liked video video games like Sic Bo, Lucky 7, Deal or No Deal, et cetera.
GeoPoll earlier this year performed a research where it estimated that over 50% of earnings by youth consumers is spent on personal care. The report notes that an excellent of millennials in Sub-Saharan Africa are utilizing their cell phones to wager on football spending no more than $50USD per 30 days. Free and low-cost practice video games are supplied by many of the largest on-line betting features to assist players enhance their betting abilities. As a outcome, customers may experiment with varied video...
00:12
Mostbet Betting Guidelines h+ Media
Mostbet Betting Guidelines
After successful registration in Mostbet, the bettor can replenish the stability and place bets. In order to have the power to freely withdraw money from the sport account in the future, you need to affirm your e-mail. To do this, youll need to enter the code obtained in a particular letter.
I advise you to bet with Mostbet if you should see your money after successful, as a outcome of many bookmakers simply block accounts without the reasons now. Without an account, you wont have the ability to use some features, together with working with the financial transfers and putting bets. In the world of gambling, there are specific guidelines and necessities for his or her participants. Compliance with these guidelines and requirements ensures the safety of the participant and provides him with ample alternatives. When betting on sports, be certain to observe the suggestions of the bookmaker to keep away from any misunderstandings.
We love certainty and so do you, we ship exceptional companies to ensure that your peace of mind is where it ought to be, having fun with the moment! Hence, I favor to get lovers in a metropolis not distant from our house. Thus, this wont problems touring talkwothstranger for a distance of some lengthy distances to savor a scorching meetup. Dont really feel lazy and search for your personal luck significantly away from rut, and as well as the webpages is great for an individual. To proceed chatting with the equivalent individual, sign-up as a member.
Ghana has the least quantity at forty two percent, stated the 2017 Geopoll Survey on Gambling within the SSA area. It all is decided by how well-balanced a united workforce the gambler creates. This could be carried out on the website or in the software kind by filling out a small kind. The match of interest may be found through the search bar furthermore. Unlike different bookmakers, Mostbet wont indicate the quantity of matches for each discipline in the list of sports within the LIVE phase..
Processing adverse and optimistic opinions help us identify areas for progress and efficiently implement cutting-edge cures. Complete the registration by simply clicking the button at the end routinely adjusts to the monitor diagonal, making it the most user-friendly. Very usually the most effective player within the event is about by the top of the match. It is a guess on the handicap with that your united team which the bet was placed must win.
In order to win some big cash and are assured in inabilities, you should select these particular bets. Many users observe that every one strategies work flawlessly, you presumably can withdraw the winnings as quickly as attainable. A guess made for quantities 20 occasions the scale of the first deposit.
Although the stakes arent yet excessive, all the signs are there...
00:12
Bedava Bonus
Fortunately that the company permits the bettors to replenish the accounts by the use of quite lots of options so that they acquire their Mostbet promo code Bangladesh sooner. Targeting the most effective player in the nation and top-of-the-line strikers on the earth is simply another show of energy. Another instance of Man City flexing their muscular tissues, exhibiting their financial clout. The most popular on-line sportsbooks definitely assume so with Man City priced as favourites to win the league and favourites to win the Champions League this season. The fixture list has been printed with the curtain going up on Friday 13 August at Carrow Road when Norwich City host Arsenal. The Gunners are favourites with bookies featured at Onlinesportsbetting to get off the mark with a win, however Mikel Artetas aspect isnt expected to challenge for the title.
Unlike youth in different African nations, most Kenyan youth guess as soon as a week spending about $50 per 30 days totally on football bets. Youth elsewhere spend less than 50USD a month and most wager only once a month. The bonuses introduced to the purchasers are numerous and each bettor is eligible to the kinds of incentives. No matter for how long a player stays with the bookmaker because there is always a Mostbet bonus code each for latest and long-term punters. Under no circumstances anticipation each wager or slot machine game game hype again a detailed proportion presumably.
The official website is legally managed and welcomes customers
from Bangladesh over 18 years old. Jackpot Place could be licensed
by the Kahnawake Video gaming Payment moreover,the Malta Betting
Experienced. Licensed Mostbet casino and bookmaker website for
 people
from Bangladesh.
people
from Bangladesh. Registration and login rules within the Mostbet official
website.
Registration and login rules within the Mostbet official
website.
At least up to now, there has not been a single case of punishment for betting on the Internet. In addition to this, the membership is registered in the territory of one other state the place such activity isnt prohibited. Moreover, the membership makes use of trendy dependable data encryption techniques, so your personal data will stay secure.
As for using Paypal together with different popular strategies, youll get data concerning this from the representatives of the sportsbook instantly. Practice shows that the consumer service of this ongoing company reaches the excessive stage. Mostbet will not track the place bonuses are put in, all players are on equal terms, the operational program is clear and simple.
The bookmakers office is in demo mode.If you learn the evaluations, the office is rated properly by the players, there are a lot of constr...
00:10
Kenya Leads Africa In Sports Betting And Gambling h+ Media
Kenya Leads Africa In Sports Betting And Gambling
The finest strategy to clear up all your troubles with taking half in and taking half in on line on line casino video games is to contact the help staff of Mostbet. There is a in depth number of the means in which to get into dialog with Mostbet managers. Furthermore, the Geopoll Survey found that seventy nine p.c of bets positioned in Kenya are on soccer games, making the nation the main in football betting. In 2018, Kenyans went online in their numbers and searched for betting and sports-related websites, a model new report has confirmed. A massive 11 of the top 20 Google search queries had been instantly associated to betting. Whilst the remaining bet principally once a month, a majority of Kenyans guess as quickly as every week with sports activities betting, particularly soccer being the most most well-liked.
Followers of Arsenal demand a giant season from their team, and theyll get a greater thought of what to anticipate in the coming months after this game. Since 2014, desertcart has been delivering a broad range of products to clients and fulfilling their desires. You will discover a number of optimistic reviews by desertcart customers on portals like Trustpilot, and so on. The website makes use of an HTTPS system to safeguard all clients and defend financial details and transactions carried out online.
As its a chat web site made for hip and stylish members, most individuals who use their service are younger individuals from the age group 18 to 24. I tried some a number of matchmaking corporations, nevertheless this option seems first fee in the intervening time. Gambling house fleas the specific talked about bins you want to probably full the evaluation approach beforehand. Or, its true that the majority of individuals strat to register in betting websites bd.
Yes, the 2 of you require a more elaborate dialog for an understanding that is clear. In addition, usually you ought to talk with him, which might be uncomfortable ashley madison kortingscode for every of you. The bet may be canceled due to technical issues on the bookmakers side. The bookmaker reserves the right to refuse to accept a bet without giving a reason. The personal info offered in the registration form should be true. It just isnt allowed for a similar person to register with the identical bookmaker twice.
You can sign-up and use the chatroom to speak with different customers free of charge. The app is straightforward to use and has the identical functionalities as the positioning. Add your full name, begin date, location information, and group title, if any. All the members may be a half of the basic public chat rooms freed from charge. You can seek for a particular or be part of the actually useful one by the location.
The bookmakers office is in demo mode.If you learn the evaluations, the office is rated well by the avid gamers, there are lots of o...
00:01
FreeBSD 13.2-RC3 Released With OpenSSH 9.3, Major Performance Fix For Makefs Phoronix
The third and potentially last release candidate of FreeBSD 13.2 is now available for testing ahead of the planned stable 13.2-RELEASE around the end of March...
Sunday, 19 March
23:56
Distribution Release: SystemRescue 10.00 DistroWatch.com: News
Franois Dupoux has released a major update of SystemRescue, an Arch-based Linux distribution designed for administrating and repairing computer systems and rescuing data. branch, which is currently the latest long-term supported one. The changelog provides further....
22:00
Customizing the Start-Up Chime On a 1999 G3 iMac Hackaday

The start-up chime on Macs is probably as recognizable as the default Nokia ringtone in this day and age. Yet much like a ringtone, so too one might want to change the start-up chime on a Mac. This is something which [Doug Brown] has done in the past already on a Power Mac G3 in 2012, which made him instantly an expert on the topic in the eyes of a reader who wanted to know how to change the chime on a 1999 iMac. While the firmware on both these systems is written in Forth, it did take a bit of sleuthing to figure out where the chime was hiding in the firmware image, and how to change it.
The target iMac is somewhat unique in that it has a G4 PPC CPU rather than the more common G3. The firmware is similar enough that it was a snap to simply search the newer iMacs firmware for the signature of the chime sound data. This turned out to be the identical QuickTime IMA ADPCM format-encoded data, yet what was different was how this data was integrated into the firmware image. Key is finding the area in the firmware where not only the address of the chime datas start is defined, but also its length. Finally, the checksums in the firmware image have to be updated so that it matches the patched data.
Reverse-engineering the checksum calculation in the Forth code turned out to be fairly straightforward, but getting the new firmware on the iMa...
21:51
Nearly 200 Banks at Risk for Same Fate as Silicon Valley Bank cryptogon.com
Via: New York Post: Nearly 200 more banks may be vulnerable to the same type of risk that took down Silicon Valley Bank: The value of the assets they hold. There are 186 banks across the country that could fail if half of their depositors quickly withdraw their funds, a new study published on the []
21:03
Read "Shingles, Zostavax vaccination and risk of developing dementia: a nested case-control study -- results from the UK Biobank cohort" (PDF) coauthored by our Ruth Itzhaki. Lifeboat News
Read "Shingles, Zostavax vaccination and risk of developing dementia: a nested case-control study results from the UK Biobank cohort" (PDF) coauthored by our Ruth Itzhaki.
20:54
Sonys Using Lasers to Help Low-vision Users Take Pictures SoylentNews
Sony wants to help low-vision users enjoy photography by shining lasers in their eyes:
Giant frickin' laser beams get all the buzz and sci-fi love, but it's our little laser bros that are putting in the work: taking measurements, entertaining our cats, and now, in the case of a Sony camera, helping people with vision problems see clearly through an electronic viewfinder and take pictures.
Sony is working with fellow Japanese company QD Laser to release the HX99 RNV Retina Projection Camera kit, a compact camera with an add-on retinal laser housing for projecting the camera's focused live view image into the user's eye. The low-power laser projection is designed to effectively bypass the focusing of the eye, helping users with visual impairments like shortsightedness, farsightedness, or astigmatism see a clear image.
It uses Sony's existing DSC-HX99 compact camera, which is a somewhat middling model from 2018 with an 18-megapixel sensor and equivalent zoom lens of 24-720mm (30x magnification), combined with QD Laser's Retissa Neoviewer projector. According to QD Laser's specs, the Retissa Neoviewer uses an RGB semiconductor laser to display an image with an equivalent of 720p resolution and 8-bit color depth. This beamed image has an approximate 60-degree horizontal field of view with 60Hz refresh, and the housing's battery has an estimated four hours of battery life. Tragically, it charges via Micro USB instead of USB-C.
Read more of this story at SoylentNews.
20:30
Week in review: Kali Linux gets Purple, Microsoft zero-days get patched Help Net Security
Heres an overview of some of last weeks most interesting news, articles, interviews and videos: Samsung, Vivo, Google phones open to remote compromise without user interaction Several vulnerabilities in Samsungs Exynos chipsets may allow attackers to remotely compromise specific Samsung Galaxy, Vivo and Google Pixel mobile phones with no user interaction. Top 50 most impersonated brands by phishing URLs Finance, technology, and telecom brands were the most commonly impersonated industries, notably for the unprecedented access More
The post Week in review: Kali Linux gets Purple, Microsoft zero-days get patched appeared first on Help Net Security.
19:34
IRC Proceedings: Saturday, March 18, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-180323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-180323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-180323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-180323.gmi
Over HTTP:
|
... |
19:20
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Hanno Bck on Mar 19
Ok, good point. So disabling TIOCLINUX isn't an option.Looking into it, maybe restricting any TIOCLINUX sub features that
implement anything related to selection would be a good option. The gpm
daemon runs as root anyway.
Do you see any risk left if
TIOCL_SETSEL
TIOCL_PASTESEL
TIOCL_SELLOADLUT
are no longer accessible to non-privileged processes?
19:00
Tiny PCB PiezoPiano Plays Just One Octave Hackaday

Grand pianos are beautiful instruments, but take up altogether too much space. Upright pianos are smaller, but still fairly hefty. When it comes to the PiezoPiano, though, we suspect nobody could complain about its diminutive size. Its a tiny thing with just one buzzy little octave for your playing pleasure.
The PiezoPiano is a single PCB device with a ATmega4809 running the show. It has eight buttons and eight piezo transducers that give you just one octaves range on the keyboard. Truth be told, thats only in one scale; youre not getting the whole twelve tones of flats and sharps included. And, when we say keyboard, we really mean tactile buttons. You get the drift. Its all assembled in a cute enclosure mimicking the shape of a real grand piano.
Fundamentally, its a cute little musical desktoy that reminds us greatly of the Stylophone. Impressively, though, those eight buzzers mean it has eight-note polyphony. Thats nothing to sniff at compared to all the monophonic synths out there. Its also available on Tindie if youd like to buy a kit off the shelf. Video after the break.
...
18:22
Read "Drug Screening Implicates Chondroitin Sulfate as a Potential Longevity Pill" by our Collin Ewald. Lifeboat News
Read "Drug Screening Implicates Chondroitin Sulfate as a Potential Longevity Pill" by our Collin Ewald.
16:49
Read "Osteopontin: Building Skeletons in Aging's Closet" by our Clinton "Cosmo" Mielke. Lifeboat News
Read "Osteopontin: Building Skeletons in Agings Closet" by our Clinton Cosmo Mielke.
16:07
20 years later, Second Life is launching on mobile SoylentNews
https://arstechnica.com/gaming/2023/03/20-years-later-second-life-is-launching-on-mobile/
Remember Second Life? The virtual world launched on the desktop web back in 2003 with 3D avatars and spaces for various social activities. Believe it or not, it has been running continually this entire timeand now it's coming to mobile for the first time.
In fact, this will be the first time that Second Life has expanded beyond the PC (across Windows, macOS, and Linux) in any form.
In a post to the virtual world's community web forum, a community manager for Second Life developer Linden Lab shared a video with some details about the mobile version's development, and announced that year.
Read more of this story at SoylentNews.
16:00
Annoying Cicada Magnet Is Nonetheless Authentic Hackaday

Weve all heard of those chirper devices that randomly make annoying noises for no other reason than sending people insane. This project from [Kousuke Saito] brings altogether more art to this idea, while still being quite annoying indeed.
The build is essentially a replica cicada. [Saito] was inspired to build the device as the sounds of the insect remind him fondly of the summer. His design consists of a 3D-printed housing that roughly approximates something like a cicada, with two wings attached to a central body. In this case, the layer lines of the 3D print actually added to the realism of the ersatz insect The housing is nicely painted to serve as an adequate simulacra to those who arent up on their entomology.
Inside, theres an ATTiny 85 paired with an MP3 playback module and a small speaker. Its charged with reproducing the noise of various cicadas. Its setup with an ingenious mechanism to switch it on. There are magnets installed in the base which allow it to stick to metallic objects. Theres also a switch in the bottom of the dev...
13:26
Links 18/03/2023: Many HowTos, Several New Releases Techrights
![]()
Contents
-
GNU/Linux
-
Desktop/Laptop
-
Notebook Check MNT Pocket Reform: New 7-inch Linux laptop launches from US$899
MNT Research has finally launched the Pocket Reform, roughly 9 months after it presented the mini laptop. As we discussed last June, the MNT Pocket Reform has a 7-inch LCD panel. It now outputs at 1,920 x 1,200...
-
-
13:00
Building a Truss-Braced Model Airplane: Sense or Nonsense? Hackaday

Following NASAs recent results with truss-braced wing airplanes and the benefits this could bring to full-sized airplanes, [Think Flight] figured that if it helps with those airplanes, perhaps it may also be a boon for model airplanes. With the recent construction of a carrier airplane for smaller drones, he decided to give the concept a whirl to see whether it would make a difference compared to a regular wing design. This carrier airplane features a payload bay that can be opened in flight to release the drones stored inside it, making any potential increased payload capacity and improvements to the flight characteristics very welcome.
The truss-braced wing design has been studied by NASA and Boeing, with the design offering a high aspect ratio, not unlike the...
12:30
Keysight Digital Learning Suite streamlines and simplifies lab management Help Net Security
Keysight Technologies introduces the Keysight Digital Learning Suite, a new unified digital learning platform that provides university engineering educators and students with lab tools, resources, and courseware through a single, secure web interface. In response to demands for flexible learning options, universities are moving from in-person education to digital and hybrid learning models. Although these new models provide unprecedented flexibility for time and location, there are still challenges for engineering educators. They often find themselves More
The post Keysight Digital Learning Suite streamlines and simplifies lab management appeared first on Help Net Security.
12:25
NATO on bots, sockpuppets, and shills manipulating social media Geeking with Greg
NATO has a new report, "Social Media Manipulation 2022/2023: Assessing the Ability of Social Media Companies to Combat Platform Manipulation".
Buying manipulation remains cheap ... The vast majority of the inauthentic engagement remained active across all social media platforms four weeks after purchasing.The fake engagement gets picked up and amplified by algorithms like trending, search ranking, and recommenders. That's why it is so effective. A thousand sockpuppets engage with something new in the first hour, then the algorithms think it is popular and show crap to more people. I think there are a few questions to ask about this: Is it possible for social media platforms to stop their amplification of propaganda and scams? If it is possible but some of them don't, why not? Finally, is it in the best interest of the companies in the long-run to allow this manipulation of their platforms?[Scammers and foreign operatives are] exploiting flaws in platforms, and pose a structural threat to the integrity of platforms.
11:19
Humans (Mostly) Love Trash Robots SoylentNews
Simple robots wander NYC asking for trash and recycling, and it's adorable:
My favorite approach to human-robot interaction is minimalism. I've met a lot of robots, and some of the ones that have most effectively captured my heart are those that express themselves through their fundamental simplicity and purity of purpose. What's great about simple, purpose-driven robots is that they encourage humans to project needs and wants and personality onto them, letting us do a lot of the human-robot-interaction (HRI) heavy lifting.
In terms of simple, purpose-driven robots, you can't do much better than a robotic trash barrel (or bin or can or what have you). And in a paper presented at HRI 2023 this week, researchers from Cornell explored what happened when random strangers interacted with a pair of autonomous trash barrels in NYC, with intermittently delightful results.
What's especially cool about this, is how much HRI takes place around these robots that have essentially no explicit HRI features, since they're literally just trash barrels on wheels. They don't even have googly eyes! However, as the video notes, they're controlled remotely by humans, so a lot of the movement-based expression they demonstrate likely comes from a human sourcewhether or not that's intentional. [...]
Read more of this story at SoylentNews.
11:01
Researcher create polymorphic Blackmamba malware with ChatGPT HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
The ChatGPT-powered Blackmamba malware works as a keylogger, with the ability to send stolen credentials through Microsoft Teams.
This is a post from HackRead.com Read the original post: Researcher create polymorphic Blackmamba malware with ChatGPT
10:00
Calibrating Thermal Cameras With Hot Patterned Objects Hackaday

Thermal cameras are great if you want to get an idea of whats hot and whats not. If you want to use a thermal camera for certain machine vision tasks, though, you generally need to do a geometric calibration to understand what the camera is seeing and correct for lens distortion. [Henry Zhang] has shared various methods of doing just that.
09:02
BREIN Shut Down 449 Pirate Sites & Services in 2022 TorrentFreak
 Predicting whether specific torrent sites, streaming
portals, or IPTV services will still be around in five years time,
is difficult at best. At worst, almost impossible.
Predicting whether specific torrent sites, streaming
portals, or IPTV services will still be around in five years time,
is difficult at best. At worst, almost impossible.
Dutch anti-piracy group BREIN has been tackling pirates of all types for the last 25 years. Not only has it seen huge numbers come and go, BREIN can claim direct responsibility for thousands going offline. A relentless production line of pirate platforms means that BREIN being around in five years time seems easier to predict.
458 Investigations, 449 Sites/Services Removed
Published this week, BREINs annual report for 2022 covers enforcement actions carried out on behalf of rightsholders across most sectors, including movies, TV shows, music, games, and publishing.
BREIN says it completed 458 investigations in 2022, leading to 449 illegal sites/services being removed from the internet. BREIN refrains from publicly naming its targets but these figures certainly arent unusual. BREIN reported the shutdown of 349 infringing platforms in 2021 and 466 in 2020.
While sites returning under new branding may play some role in these persistently high numbers, the fact that full-blown pirate sites can now be deployed in minutes could be a more significant factor. But whatever the circumstances, BREIN has a tool for every occasion.
Preventing Big Sites From Getting Bigger
The Netherlands has long been associated with large piracy platforms but not necessarily because they were operated or hosted there. BREINs persistence on the legal front means that some of the largest torrent sites The Pirate Bay, RARBG, 1337x, YTS, EZTV, LimeTorrents and KickassTorrents variants are now dynamically blocked by major ISPs under the terms of a Website Blocking Covenant.
At the end of 2022, 196 proxies and mirrors were also blocked by IP address and/or DNS. BREIN further reports that an additional 328 proxies were stopped by other means last year.
Until relatively recently the sites mentioned above could still be found in Googles search results, but BREIN helped to change that too.
In cooperation with Google late 2021, Pirate Bay domains...
08:52
Kaspersky released a new decryptor for Conti-based ransomware Security Affairs
In March 2022, a Ukrainian security researcher has leaked the source code from the Conti ransomware operation to protest the gangs position on the conflict.
After the leak of the source code, an unknown ransomware group attacks aimed at companies and state institutions.
In late February 2023, Kaspersky researchers uncovered a new portion of leaked data published on forums and noticed the presence of 258 private keys. The leak also included source code and some pre-compiled decryptors, which allowed the researchers to release
The malware variant whose keys were leaked, had been discovered by Kaspersky specialists in December 2022. This strain was used in multiple attacks against companies and state institutions. states Kaspersky.
The leaked private keys are located in 257 folders (only one of these folders contains two keys). Some of them contain previously generated decryptors and several ordinary files: documents, photos, etc. Presumably the latter are test files a couple of files that the victim sends to the attackers to make sure that the files can be decrypted.
The researchers added all 258 keys to the latest build of Kasperskys utility RakhniDecryptor 1.40.0.00. Users can download the decryptor from the Kasperskys No Ransom site.
For many consecutive years, ransomware has remained a major tool used by cybercrooks. However, because we have studied the TTPs of various ransomware gangs and found out that many of them operate in similar ways, preventing attacks becomes easier. The decryption tool against a new Conti-based modification is already available on our No Ransom webpage. However, we would like to emphasize that the best strategy is to strengthen defenses and stop the attackers at early stages of their intrusion, preventing ransomware deployment and minimizing the consequences of the attack, said Fedor Sinitsyn, lead malware analyst at Kaspersky.
Be...
08:42
Read "The Ethics of Human Enhancement and Ferrando's Philosophical Posthumanism" by our Kevin LaGrandeur. Lifeboat News
Read "The Ethics of Human Enhancement and Ferrandos Philosophical Posthumanism" by our Kevin LaGrandeur.
07:00
Its a 486 Computer, On a Breadboard Hackaday

Ever since the 1970s, a frequent project has been to take a microprocessor and construct a computer system on a breadboard or stripboard. Usually these machines feature a familiar 8-bit processor such as a 6502 or a Z80 because of their breadboard-friendly DIP packages, but there is surprisingly little reason why some of the more recent silicon cant be treated in the same way. [FoxTech] is leading the way on this, by making a breadboard computer using an 80486DX.
A 1990-era 32-bit desktop CPU seems unpromising territory for this application, but its architecture is surprisingly accessible. It needs a breakout board to gain access to its various lines, but beyond that it can be interfaced to in a very similar way to those earlier chips.
So far there are two videos in the series, which weve placed below the break. The first one introduces the project and shows the basic set-up. A 486 running NOPs may produce a pretty light show, but as he starts to show in the second video, its capable of more. The eventual aim is to have a simple but fully functional breadboard computer, so hes starting with logic to decode the 32-bit bus on the 486 into the 8-bit bus hes going to use.
Its fascinating to learn about how the 32-bit 486 handles its interfacing and deals with four bytes at...
06:37
Asus Announces RISC-V Tinker Board Raspberry Pi Rival SoylentNews
Chances its Arm that maker community is looking for a fresh SBC:
Asus has unveiled a RISC-V model in its range of Tinker Board single board computer (SBC) systems, which up until now have all been Arm-based. However, it seems users should not expect too much in the way of performance from this first device.
The Tinker Board has been around since 2017 as Asus' answer to the Raspberry Pi, even keeping the same form factor and GPIO pinout in some models. Like the Pi, they have been based on various Arm-based system-on-chip (SoC) hardware.
Announced this week, the Tinker V is powered by a 64-bit RISC-V chip and aimed at embedded and IoT applications, but like other Tinker Boards and the Raspberry PI, is likely to find its way into the hands of makers and enthusiasts as well.
According to Asus, Tinker V "provides impressive power, comprehensive functionality and rich connectivity, making it the perfect choice for a diverse range of industrial IoT applications".
However, it is based on a 1GHz Renesas RZ/Five chip, which has just a single CPU core, the AX45MP designed by Andes Technology, whereas most rival products sport multiple processor cores.
Read more of this story at SoylentNews.
04:20
Half Of Americans Believe Media Intend To Mislead, Misinform cryptogon.com
Via: Summit News: A study has revealed new lows in terms of trust Americans have in the establishment media. The study by pollster Gallup and the Knight Foundation found that only a quarter of Americans have some level of favourability regarding the media, the lowest figure recorded for five years. The study also found that []
04:00
AMD P-State Guided Autonomous Mode Coming For Linux 6.4 Phoronix
While Linux 6.3 adds AMD P-State EPP as the "Energy Performance Preference" mode for enhancing the power/performance on recent Ryzen and EPYC systems on Linux, with Linux 6.4 the P-State Guided Autonomous Mode is coming to round out AMD's current CPU frequency scaling driver efforts...
03:58
Trump Says He Expects To Be Arrested On Tuesday cryptogon.com
Via: Reuters: Fox News anchor John Roberts informed viewers on Friday afternoon that the Manhattan District Attorneys Office has requested a meeting with law enforcement ahead of a potential Trump indictment. He said, to discuss logistics for some time next week, which would mean that they are anticipating an indictment next week. A spokesman []
03:41
Links 18/03/2023: Tor Browser 12.0.4 and Politics Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
-
GNU/Linux
-
Server
-
Kubernetes Blog Kubernetes Removals and Major Changes In v1.27
As Kubernetes develops and matures, features may be deprecated, removed, or replaced with better ones...
-
-
03:31
US govt agencies released a joint alert on the Lockbit 3.0 ransomware Security Affairs
The US government released a joint advisory that provides technical details about the operation of the Lockbit 3.0 ransomware gang.
The U.S. Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the Multi-State Information Sharing & Analysis Center (MS-ISAC) released a joint advisory that provides indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) associated with the notorious LockBit 3.0 ransomware.
The Federal Bureau of Investigation (FBI), CISA, and the Multi-State Information Sharing and Analysis Center (MS-ISAC) has released a joint cybersecurity advisory (CSA), #StopRansomware: LockBit 3.0. This joint advisory details known indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) that FBI investigations correlated with LockBit 3.0 ransomware as recently as March 2023. reads the advisory published by US agencies. LockBit 3.0 functions as an affiliate-based ransomware variant and is a continuation of LockBit 2.0 and LockBit.
The Lockbit gang has been active since at least 2019 and today it is one of the most active ransomware groups offering a Ransomware-as-a-Service (RaaS) model.
The LockBit 3.0 ransomware (aka LockBit Black) was launched in June 2022 and is a continuation of previous versions of the ransomware, LockBit 2.0 (released in mid-2021), and LockBit.
03:12
XCP-ng Initating Effort To Rewrite Xen Components In Rust Phoronix
The focus of this new effort isn't to immediately rewrite the Xen virtualization hypervisor in Rust but to begin gradually working toward rewriting some of the smaller Xen Project components in the Rust programming language and to see how everything pans out...
01:54
Maternal Deaths in the U.S. Keep Climbing SoylentNews
The COVID-19 pandemic contributed to the higher rate in 2020 and 2021:
An increasing number of U.S. women are dying during pregnancy or soon after giving birth, according to the latest data on the maternal mortality rate.
In 2021, there were 32.9 deaths per 100,000 live births, compared with 23.8 per 100,000 in 2020 and 20.1 in 2019, the National Center for Health Statistics reports March 16. The U.S. rate greatly exceeds those of other high-income countries. The total number of U.S. maternal deaths rose from 861 in 2020 to 1,205 in 2021.
There remains a wide disparity in the maternal mortality rate for Black women, at 69.9 deaths per 100,000 live births, compared with white women, at 26.6 per 100,000. Many social determinants of health underlie this gap, including differences in the quality of care that Black women receive before, during and after pregnancy.
The NCHS report doesn't discuss the reasons behind the increase for 2021. But COVID-19 contributed to a quarter of maternal deaths in 2020 and 2021, the U.S. Government Accountability Office reported in October. The pandemic also contributed to the mortality disparity between Black and white women, the GAO found, worsening existing structural inequities that lead to such issues as barriers to getting health care (SN: 4/10/20).
The U.S. maternal mortality rate has risen overall since 2018. The highest rate is among non-Hispanic Black women compared with Hispanic women and non-Hispanic white women.
The maternal deaths captured by the NCHS report are those that occur during pregnancy or within 42 days of the end of the pregnancy, "from any cause related to or aggravated by the pregnancy or its management." These causes include hemorrhaging, infections and high blood pressure disorders such as eclampsia.
The report excludes deaths after 42 days and up to the first year after birth. But 30 percent of pregnancy-related deaths occur during this period, the U.S. Centers for Disease Control and Prevention reported in September, from an analysis of the years 2017 to 2019.
...
01:00
Study Hacker History, and Update It Hackaday

Looking through past hacks is a great source of inspiration. This week, we saw [Russ Maschmeyer] re-visiting a classic hack by [Jonny Lee] that made use of a Wiimotes IR camera to fake 3D, or at least provide a compelling parallax effect thatll fool your brain, without any expensive custom hardware.
00:53
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Eric Ashley on Mar 18
According to a note from kernel maintenance(https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?h=v6.3-rc2&id=1e641743f055f075ed9a4edd75f1fb1e05669ddc),
as of 2008 only Heirloom mailx (a.k.a. nail) used it for ~h interactive header editing.
Best regards,
Eric
Sent with Proton Mail secure email.
------- Original Message -------
00:36
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Christos Zoulas on Mar 18
I think that the original reason was for csh(1) to implement file completion:https://nxr.netbsd.org/xref/src/bin/csh/file.c#161
I still have a use case for it. Sometimes I lose my VPN tunnel and an
ssh session where I am running vi(1) suddenly dies. When I ssh to that
machine, I can easily find the tty where the vi session is with ps(1) and
then type "sti pts/X :wq\\n" and save the file (https://man.netbsd.org/sti.8):-)
Of course on...
00:22
A hydrogenotrophic Sulfurimonas is globally abundant in deep-sea oxygen-saturated hydrothermal plumes Microbiology Lifeboat News: The Blog
An uncultivated, aerobic chemolithotrophic Sulfurimonas species with a reduced genome is abundant across diverse, hydrogen-rich hydrothermal plumes in the deep ocean.
Saturday, 18 March
23:38
Prime Spin And Win On-line Casinos In Kenya h+ Media
Prime Spin And Win On-line Casinos In Kenya
You ought to remember that the response times tend to be longer than using reside chat or cellphone assist. Browse the different varieties of video games obtainable at your most popular casino. Always choose only operators which are licensed by the gambling fee in Kenya. Here are our expert tips on how you can test and consider the Kenyan on line casino online gambling platforms.
A good casino will have at least one payment technique thats appropriate for you. This is a unbelievable vacation spot for slot machine fans, offering practically 70 completely different games. The casino is principally used by these staying in the adjoining lodge.
Online casinos in Kenya with free bonuses that we are recommending are 1XBet Kenya or 22Bet Kenya. Free spins on registration no deposit are precisely because the name suggests. The operator gives players real-money free spins for creating and verifying their accounts. We highlighted these above, slots free spins are bonus features designed into the game. The variety of spins you get also is decided by the slot, with some titles providing greater than one hundred in-game free spins. The majority of on-line casino operators let customers play their slots for free in demo mode.
Bingo can also be very fashionable and might supply some impressive prizes. Wed urge you to take a look at all sport types supplied at your chosen on line casino, as you can find one thing you absolutely love playing. [newline]Before you decide a factor or two about every available option. For starters, you may want to discover out extra about how online roulette for real money is totally different than free roulette video games. Well, every is slightly different by means of the monetary threat youll carry in addition to the accompanying game features.
When you play at a legit on line casino, you may be confident that the banking cashier is secure, enabling you to deposit safely. However, there are variations to be found across the assorted payment methods you can use. Whilst M-Pesa is a most well-liked option for many, there are some drawbacks to using it to make deposits at a Kenyan online on line casino. Another purpose why consumers are obsessive about online slots is the fun of taking part in them.
It is price keeping in thoughts nonetheless that the game selection on casino apps will usually be slightly smaller. This is because some older games havent been optimised for cellular gaming. Yet on the plus facet, the most popular video games and new releases are usually mobile-friendly, so the influence in your playing experience must be minimal. In your most popular Kenyan online on line casino, make positive you are aware of the available cost options before registering. Another factor that you just must also examine is whether or not or not the video games on the KE c...
23:35
What Is The Most Quantity I Can Win In A No h+ Media
What Is The Most Quantity I Can Win In A No
You can study so much just by trying at the sites customer-centric strategy via its customer support staff. A good web site should embody a number of methods of contacting the support team, and should have a pleasant help staff among other features. Jengacash is a simple-to-use website and doesnt provide extra games except for the spin wheel. Below, were going to see what its spin wheel is all about and the way to win on it.
Bonuses and promotions are a form of thanking you for choosing to play with them. In addition, some casinos require you to deposit cash to find a way to play. You will have a spread of choices for making an investment to be a winner in these games. While some casinos allow the deposit of bank card, other casinos require that you simply use the wire transfer methodology or a checkbook.
In this case, the on line casino randomly draws accounts and rewards these with this bonus. The bonus may also be chosen based on given standards at a particular time. In this occasion, specific accounts are recognized because of sure traits such as continued activity, in which case it additionally qualifies as a loyalty bonus. How you receive your free spins then is dependent upon the specific welcome bonus. We went through the totally different sorts of free spins somewhat earlier, but you will usually must make the primary deposit to get funds into your account.
Youll play with a real supplier, beamed to your display screen using a webcam, making this the most practical method to play on-line. Most websites provide a minimal of stay blackjack and roulette, plus baccarat and casino poker are also typically found in live casinos. The stakes are sometimes more expensive than standard on line casino video games though. There arent any legal guidelines that prohibit a player who is based in Kenya from becoming a member of a website and taking part in a recreation they get pleasure from. You could need to typically choose from reviewed and trusted online casinos.
When you play at a legit casino, you can be confident that the banking cashier is protected, enabling you to deposit safely. However, there are variations to be discovered across the various payment methods you ought to use. Whilst M-Pesa is a most well-liked choice for a lot of, there are some drawbacks to using it to make deposits at a Kenyan on-line casino. Another reason why shoppers are obsessive about online slots is the fun of playing them.
To facilitate the fast motion of cash out and in of your account, real money casinos have numerous cost options so that you can choose from. For occasion, when you bet one thousand dollars you would need to bet a minimum of ten thousand dollars in order to match the bonus. While these bonuses can definitely assist you to to start out out with nonetheless they receivedt help you get started on the proper path to gambling and w...
23:35
High Actual Money On-line Casinos In Kenya 2022 h+ Media
High Actual Money On-line Casinos In Kenya 2022
For Kenyans who want to play actual money casino games, payment options are a significant consider deciding the place to play. Whilst most casinos will let you deposit using bank playing cards similar to Visa and MasterCard, these do not meet the needs of each player. For making deposits at a web-based Kenyan on line casino M-Pesa is a top choice for many gamers, which comes as little surprise given the recognition of cellular gaming. The best Kenya online casinos include a variety of other games and conventional versions of popular online casino games like roulette and blackjack.
Lastly, remember that whereas no deposit-free spins can be a good way to boost your bankroll, they dont appear to be necessarily guaranteed to make you a revenue. So dont go in expecting to win huge give consideration to having fun and enjoying responsibly. Another casino that gives free spins with no deposit required is LeoVegas Casino. They offer new gamers up to 50 free spins with no deposit required. Most Kenyans will deposit and withdraw utilizing their credit score or debit card, as its incredibly handy, plus it presents excessive ranges of safety. E-wallets, corresponding to PayPal, Skrill and Neteller, are additionally generally used.
Because soon as gamers are situated of their lowest deposit, they may allowed carry out for once they need, at as a lot worth as theyve got on an people account. These individuals want inside order to withdraw their very own account, the robot free to perform. This is amongst the many few betting choices over online gambling that does not need a smallest deposit start with playing. We have completely examined and reviewed on-line casinos in Kenya to deliver you the most effective operators. Another popular casino recreation that gamers are always on the lookout for is blackjack. The recognition of bitcoin blackjack casinospeaked with the introduction of card counting.
A prerequisite for receiving a cashback bonus is to keep in mind the time restrict of this promotion. One of the finest options amongst spin on line casino website gaming fashions is minimal deposit essential need. Players arent required to put any cash to suppose about taking part in.
You will be succesful of make deposits using Bitcoin as nicely as withdraw winnings utilizing the same format. The cause why theres been a mass exodus of a few of the prime online casinos is because of the increased tax on the profit of the operators. However, this was briefly halted by the Supreme Court, which sparked the hope of seeing a few of the prime local on-line casinos opening their doors to patrons soon. Software developers within the on-line casino area of interest refer to these companies behind the games that you simply play. Some of the massive guns in the industry value their popularity and as such, will solely work with legitimate online on line casino manufacturer...
23:32
Play On-line Roulette h+ Media
Play On-line Roulette
It is value maintaining in mind nonetheless that the game choice on casino apps will normally be barely smaller. This is as a result of some older games havent been optimised for cellular gaming. Yet on the plus side, the preferred games and new releases are normally mobile-friendly, so the impression in your playing expertise must be minimal. In your most popular Kenyan on-line casino, make sure you are conscious of the out there cost choices earlier than registering. Another thing that you just must also check is whether the games at the KE on line casino sites have truthful payout rates. The Odibets casino platform has a straightforward to navigate interface with a variety of games, making it certainly one of, if not the most effective on-line on line casino in Kenya and Ghana.
On the opposite hand, when you have performed through the spins, you can nonetheless avail extra with the same deposit. One may say that it is not low as the deposit quantity is 5 euros. But considering the cash prizes, choosing Trada could be quite worthwhile for you.
A free casino bonus also has situations for its use and will or not be restricted to certain games. You may even have to use the bonus inside a specified time interval. These are the kinds of bonuses that we noticed earlier from Helabet and 1xBet. [newline]Here the free spins are used as an enticement to enroll for a brand new customer account. Players will register with the net casino and receive free spins as part of their welcome bonus. At Caxino, you presumably can spin the wheel at a minimum deposit of only 1 euro.
Also, the on line casino sets the value of every free spin, and players can not change this. Although there are several types of free spins bonuses , the fundamentals are the identical. The spins can be found on a selection of slots, which keeps things fresh and fascinating. And, of course, after taking half in the spins, you still have the matched deposit bonus to take pleasure in. Presently, you may solely play the dedicated Roulette77 sport from a desktop web site and directly on the website. The good news is you can still accomplish that from a mobile phone which can make it straightforward so that you simply can play remotely should you select to, which is useful.
No matter which methodology you determine to deposit funds to be a winner in these games you must read via the entire wagering rules previous to you make your deposit. While deposit bonuses are the commonest kind of online on line casino bonus, probably the most interesting for slot lovers are the Free Spins. On this page we focus extra on this sort of casino bonus, providing you with helpful details about how to use free spin and the place to find them. This is among the advantages that online casinos offer versus native casinos or slot halls. With the help of free spins, you can attempt free slot video games and whether this slot recreation is sweet for y...
23:17
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Lyndon Nerenberg (VE7TFX/VE6BBM) on Mar 18
Does anyone even remember why TIOCSTI was added in thefirst place? I remember stumbling across it decades
ago (SVR?), but I've ever seen a use case for it.
It puzzled me back then why it even existed.
--lyndon
22:30
Chinese Hackers Exploit Fortinet Zero-Day Flaw for Cyber Espionage Attack The Hacker News
The zero-day exploitation of a now-patched medium-severity security flaw in the Fortinet FortiOS operating system has been linked to a suspected Chinese hacking group. Threat intelligence firm Mandiant, which made the attribution, said the activity cluster is part of a broader campaign designed to deploy backdoors onto Fortinet and VMware solutions and maintain persistent access to victim
22:26
-current has moved to 7.3, ports commits restricted pending release OpenBSD Journal
With the following commit,
Theo de Raadt (deraadt@) moved -current to version
7.3:
CVSROOT: /cvs
Module name: src
Changes by: deraadt@cvs.openbsd.org 2023/03/17 16:52:22
Modified files:
sys/conf : newvers.sh
Log message:
remove -beta tag
For those unfamiliar with the process: this is not the 7.3 release, but is part of the standard build-up to the release.
22:10
Feds arrested Pompompurin, the alleged owner of BreachForums Security Affairs
U.S. law enforcement arrested this week a US citizen suspected to be Pompompurin, the notorious owner of the BreachForums cybercrime forum.
U.S. law enforcement arrested this week a US man that goes online with the moniker Pompompurin, the US citizen is accused to be the owner of the popular hacking forum BreachForums.
The news of the arrest was first reported by Bloomberg, which reported that federal agents arrested Conor Brian Fitzpatrick from Peekskill, New York.
The man was arrested by the feds at his home around 4:30 p.m. Wednesday.
Federal agents have arrested a Peekskill, New York, man they say ran the notorious dark web data-breach site BreachForums under the name Pompompurin. reads the post published by Bloomberg. Conor Brian Fitzpatrick was arrested by a team of investigators at his home around 4:30 p.m. Wednesday, an FBI agent said in a sworn statement filed in court the next day. Fitzpatrick is charged with a single count of conspiracy to commit access device fraud.
In an affidavit filed with the District Court for the Southern District of New York, FBI Special Agent John Langmire said that at around 4:30 p.m. on March 15, 2023, he led a team of that made a probable cause arrest of Conor Brian Fitzpatrick in Peekskill, NY.
When I arrested the defendant on March 15, 2023, he stated to me in substance and in part that: a) his name was Conor Brian Fitzpatrick; b) he used the alias pompompurin/ and c) he was the owner and administrator of BreachForums the data breach website referenced in the Complaint, Langmire wrote.
According to the Westchester News12 website, the agents spent hours inside and outside of the suspects home, they were seen removing several bags of evidence from the house.
The man has been charged with soliciting individuals with the purpose of selling unauthorized access devices.
Fitzpatrick was released on a $300,000 bond signed by his parents, he is scheduled to appear before the District Court for the Eastern District of Virginia on March 24, 2023.
The defendant must: submit to supervision by and rep...
22:00
Meet the New Moteus BLDC Controller Board, the N1 Hackaday

[Josh] over at mjbots just released a moteus-n1. One change is that the volume and footprint size has been reduced. Considering many people, [Josh] included, use these controllers to operate robotic dogs, smaller is better. The previous moteus controller maxed out at 44 V, but the n1 can run at up to 54 V, allowing use of 48 V power supplies. And [Josh] improved the interface circuitry, making it much more flexible than before. This comes at an increased price, but he sells both versions parts availability permitting. And like the previous versions of the moteus controller, this is an open source project and youre free to build it yourself. You can check out the complete design package at the projects GitHub repository.
One helpful point is that the firmware for the n1 is the same, it simply enables new features related to the I/O ports. This means a user could swap in a new controller with no impact to their system. Maintaining firmware compatibility was just one of the challenges [Josh] faced along the way. Squeezing addit...
21:52
Linux 6.4 AMD Graphics Driver Picking Up New Power Features For The Steam Deck Phoronix
A pull request of early AMDGPU kernel graphics driver changes was submitted for DRM-Next on Friday as some of the early feature work accumulating for the Linux 6.4 kernel cycle...
21:24
LLVM 16.0 Released With New Intel/AMD CPU Support, More C++20 / C2X Features Phoronix
LLVM 16 was released on Friday night as the latest half-year feature release to this open-source compiler stack. From initial AMD Zen 4 support to bringing up new Intel CPU instruction sets and processor targets for their new processors being introduced through 2024, there is a lot of exciting hardware additions in LLVM 16.0. LLVM 16.0 is also notable for faster LLD linking, Zstd compressed debug sections, stabilizing of its LoongArch target, defaulting to C++17 for Clang, and much more. Here's a look at all the exciting changes of LLVM 16...
21:12
National Academies: We Cant Define Race, So Stop Using It in Science SoylentNews
For genetics, use scientifically relevant descriptions, not outdated social ideas:
With the advent of genomic studies, it's become ever more clear that humanity's genetic history is one of churn. Populations migrated, intermingled, and fragmented wherever they went, leaving us with a tangled genetic legacy that we often struggle to understand. The environmentin the form of disease, diet, and technologyalso played a critical role in shaping populations.
But this understanding is frequently at odds with the popular understanding, which often views genetics as a determinative factor and, far too often, interprets genetics in terms of race. Worse still, even though race cannot be defined or quantified scientifically, popular thinking creeps back into scientific thought, shaping the sort of research we do and how we interpret the results.
Those are some of the conclusions of a new report produced by the National Academies of Science. Done at the request of the National Institutes of Health (NIH), the report calls for scientists and the agencies that fund them to stop thinking of genetics in terms of race, and instead to focus on things that can be determined scientifically.
The report is long overdue. Genetics data has revealed that the popular understanding of race, developed during a time when white supremacy was widely accepted, simply doesn't make any sense. In the popular view, for instance, "Black" represents a single, homogenous group. But genomic data makes clear that populations in Sub-Saharan Africa are the most genetically diverse on Earth.
And, like everywhere else, populations in this region haven't stayed static. While some groups remained isolated from each other, the vast Bantu expansion touched most of the continent. Along the coast of East Africa, the history of interchange with Mideastern traders can be detected in many groups. There's also a tendency to treat African Americans as being equivalent to African, when the former population carries the legacy of genetic mixing with European populationsoften not by choice.
Similar things are true for every population we have looked at, no matter where on the globe they reside. Treating any of these populations as a monolithic, uniform groupas a race, in other wordsmakes no scientific sense.
20:53
KDE Delivers More Wayland Fixes & Plasma 6.0 Changes This Week Phoronix
KDE developer Nate Graham is out with his usual weekly development summary that highlights all of the interesting desktop changes made over the course of the past seven days. This week he particularly calls out more Wayland fixes -- a common occurrence in the KDE camp...
20:46
Links 18/03/2023: Docker is Deleting Free Software Organisations Techrights
![]()
Contents
-
GNU/Linux
-
Desktop/Laptop
-
Veikk Voila L Pen Tablet review: budget drawing tablet is an attractive choice [Ed: GNU/Linux compatible]
The Veikk Voila L Pen Tablet from new kids on the block Veikk is a versatile, affordable drawing tablet thats worth buying even if for only occasional use. It comes in cheaper than its rival the Huion Inspiroy Ink H320 and its rugged and simple design and inbuilt dial make it very simple to use out of the box. Its supplied with different adaptors, allowing it to plug into phones, tablets and laptops and its pressure sensitivity is brilliant, especially for a sub-$50 tablet.
-
-
Server
-
Container Journal ...
-
-
20:13
19:10
IRC Proceedings: Friday, March 17, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-170323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-170323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-170323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-170323.gmi
Over HTTP:
|
... |
19:00
Joseph Takahashi joins our Neuroscience Board. Lifeboat News
Joseph Takahashi joins our Neuroscience Board.
Joe holds the Loyd B. Sands Distinguished Chair in Neuroscience and is Professor and Chair of the Department of Neuroscience at the University of Texas Southwestern Medical Center. He is also Investigator at the Howard Hughes Medical Institute.19:00
DOOM Ported to a Single LEGO Brick Hackaday

By now youve all seen the tiny LEGO brick with a working screen in it. The work of one [James Ancient Brown], it was truly a masterpiece of miniaturization and creativity. Since then, [James] hasnt stopped innovating. Now, hes "https://www.youtube.com/watch?v=o76U0JPrMFk" target= "_blank">running on a single plastic brick.
Weve covered the construction of these astounding screen bricks before. Long story short, [James] designed a tiny PCB that hosts an RP2040 microcontroller which is then hooked up to a tiny OLED screen. The components are placed in a silicone mold, which is then filled with transparent resin to form the brick. The screen is then powered via contacts in the bottom, much like older-style LEGO motors.
Early experiments involved running various graphics to emulate a spaceship dashboard, but [James] has now gone much further. Hes implemented RP2040-doom to run the game. It uses til...
18:24
Minnesota power plant leaks 400,000 gallons of radioactive water Lifeboat News: The Blog

A nuclear power plant along the Mississippi River in Monticello, Minnesota, has leaked more than 400,000 gallons of radioactive water due to a broken pipe. NBCs Maggie Vespa has the details.
Subscribe to NBC News: http://nbcnews.to/SubscribeToNBC
Watch more NBC video: http://bit.ly/MoreNBCNews.
NBC News Digital is a collection of innovative and powerful news brands that deliver compelling, diverse and engaging news stories. NBC News Digital features NBCNews.com, MSNBC.com, TODAY.com, Nightly News, Meet the Press, Dateline, and the existing apps and digital extensions of these respective properties. We deliver the best in breaking news, live video coverage, original journalism and segments from your favorite NBC News Shows.
Connect with NBC News Online!
NBC News App: https://smart.link/5d0cd9df61b80
Breaking News Alerts:
https://link.nbcnews.com/join/5cj/breaking-news-signup?cid=slip_190621
Visit NBCNews. Com: http://nbcnews.to/ReadNBC
Find NBC News on Facebook: http://nbcnews.to/LikeNBC
Follow NBC News on Twitter: http://nbcnews.to/FollowNBC
Get more of NBC News delivered to your inbox:
nbcnews.com/newsletters.
#Minnesota #Nuclear #Radioactive
18:22
Tomorrow Biostasis: The Berlin Startup That Wants to Bring You Back from the Dead Lifeboat News: The Blog
What if death was not the end? What if, instead of saying our final goodbyes to loved ones, we could freeze their bodies and bring them back to life once medical technology has advanced enough to cure their fatal illnesses? This is the mission of Tomorrow Biostasis, a Berlin-based startup that specializes in cryopreservation.
Cryopreservation, also known as biostasis or cryonics, is the process of preserving a human body (or brain) in a state of suspended animation, with the hope that it can be revived in the future when medical technology has advanced enough to treat the original cause of death. This may seem like science fiction, but it is a legitimate scientific procedure, and Tomorrow Biostasis is one of the few companies in the world that offers this service.
Dr Emil Kendziorra, co-founder and CEO of Tomorrow Biostasis explained that the goal of cryopreservation is to extend life by preserving the body until a cure can be found for the original illness. He emphasized that cryopreservation is not a form of immortality, but rather a way to give people a second chance at life.
18:00
Trump and White Hats Attack Corporate Marxism Terra Forming Terra

When Mary Wollstonecraft Was Duped by Love Terra Forming Terra

Emails in 2020 blow the covid PCR test scam out of the water Terra Forming Terra
A deep dive into the PCR test which was telied on to drive public policy. It completely fails to test for COVID at all which is no surprise since that was my blanket objection at the time. You really need to identify a pathogen of some sort in order to invent a test.
75-Year-Olds White Hair Turns Black, Doctor Explains Why Terra Forming Terra
This alone can make accupuncture into a growth industry. This should also trigger hair growth renewal as well and of course all customers will return for a refresher.
16:59
Pompompurin Unmasked: Infamous BreachForums Mastermind Arrested in New York The Hacker News
U.S. law enforcement authorities have arrested a New York man in connection with running the infamous BreachForums hacking forum under the online alias "Pompompurin." The development, first reported by Bloomberg Law, comes after News 12 Westchester, earlier this week, said that federal investigators "spent hours inside and outside of a home in Peekskill." "At one point, investigators were seen
16:27
The White House Might be Running Out of Time to Bring Back Net Neutrality SoylentNews
Shortly after coming into office, President Joe Biden moved to restore net neutrality. He signed a sweeping executive order to promote competition, calling on the Federal Communications Commission (FCC) to bring back the Obama-era internet rules rolled back by the Trump administration.
But close to two years later, the FCC remains deadlocked with only four of its five commissioner slots filled and Biden may be running out of time.
Biden's pick for a new FCC commissioner was Gigi Sohn, a former FCC official and public interest advocate. Sohn would have secured a long-awaited Democratic majority at the agency. After she was nominated in October 2021, however, a well-funded opposition organized a brutal opposition campaign against her. The culture-war campaign called Sohn an "extremist" and a "censor" because of past tweets criticizing Fox News and former President Donald Trump, largely ignoring her decades-long professional record. After more than 16 months and three separate confirmation hearings, Sohn withdrew her nomination earlier this month, citing the "unrelenting, dishonest and cruel attacks" by broadband and cable lobbyists and their friends.
It's unlikely Biden will pick someone as critical of cable companies again but Republicans could try to thwart even a centrist candidate
Now, the White House has been forced to start over, prolonging a vacancy that continues to obstruct the administration's broadband agenda. The White House hasn't announced a new nominee or when they're hoping to confirm someone, but it's unlikely that Biden would pick someone as critical of cable companies as Sohn. Republicans and "dark money" groups have already proved that they're willing to spend millions to block progressive nominees. With so little time left in Biden's first term, stakeholders may even try to thwart a more moderate nominee, especially if there's an opportunity to continue the stalemate past the 2024 election.
...
16:17
LockBit 3.0 Ransomware: Inside the Cyberthreat That's Costing Millions The Hacker News
U.S. government agencies have released a joint cybersecurity advisory detailing the indicators of compromise (IoCs) and tactics, techniques, and procedures (TTPs) associated with the notorious LockBit 3.0 ransomware. "The LockBit 3.0 ransomware operations function as a Ransomware-as-a-Service (RaaS) model and is a continuation of previous versions of the ransomware, LockBit 2.0, and LockBit,"
16:00
HP 3488A Teardown, Dismantled for Parts Hackaday

[IMSAI Guy] has an old HP 3488A Switch Control Unit that he wants to dismantle for parts ( see video below the break ). The 3488A is pretty simple as far as HP test equipment goes a chassis that can hold various types of relay cards and is programmable over GPIB. He notes up front that these are plentiful and inexpensive in the used test equipment market.
Around the back of the unit is a card cage that accepts up to five option cards providing
- 44 matrix switching
- on/off SPST switching
- switching signals to a common bus
- VHF switching
- Digital I/O signalling
14:23
How tumors transform blood vessels Lifeboat News: The Blog
Increasingly dense cell clusters in growing tumors convert blood vessels into fiber-filled channels. This makes immune cells less effective, as findings by researchers from ETH Zurich and the University of Strasbourg suggest. Their research is published in Matrix Biology.
It was almost ten years ago that researchers first observed that tumors occurring in different cancersincluding colorectal cancer, breast cancer and melanomaexhibit channels leading from the surface to the inside of the cell cluster. But how these channels form, and what functions they perform, long remained a mystery.
Through a series of elaborate and detailed experiments, the research groups led by Viola Vogel, Professor of Applied Mechanobiology at ETH Zurich, and Gertraud Orend from the University of Strasbourg have found possible answers to these questions. There is a great deal of evidence to suggest that these channels, which the researchers have dubbed tumor tracks, were once blood vessels.
14:23
New ocean in making? Africa slowly splitting into two, scientists predict natures rarest move Lifeboat News: The Blog
As Africa splits into two pieces, scientists predict the beginning of the rarest natural phenomena. Researchers believe that in the distant future, the creation of a new ocean may result in the division of Africa into two pieces. The separation of two significant portions of the continent may eventually lead to the formation of a new body of water. In millions of years, landlocked nations like Zambia and Uganda might have their own coasts.
The splitting of an one tectonic plate into two or more tectonic plates divided by divergent plate borders is known as rifting, according to Science Direct. Where the Earths tectonic plates separate, a lowland area known as the rift valley arises, according to National Geographic.
These rift valleys can be found both on land and on the oceans floor. According to IFLScience research, this event dates back at least 138 million years to the time when South America and Africa became separated into separate continents. According to NBC News, the Red Sea and the Gulf of Aden were formed as a result of the Arabian plate moving away from Africa for the past 30 million years.
14:22
Mirror-imaging in molecules can modify neuron signaling Lifeboat News: The Blog
With the aid of some sea slugs, University of NebraskaLincoln chemists have discovered that one of the smallest conceivable tweaks to a biomolecule can elicit one of the grandest conceivable consequences: directing the activation of neurons.
Their discovery came from investigating peptides, the short chains of amino acids that can transmit signals among cells, including neurons, while populating the central nervous systems and bloodstreams of most animals. Like many other molecules, an amino acid in a peptide can adopt one of two forms that feature the same atoms, with the same connectivity, but in mirror-image orientations: L and D.
Chemists often think of those two orientations as the left and right hands of a molecule. The L orientation is by far the more common in peptides, to the point of being considered the default. But when enzymes do flip an L to a D, the seemingly minor about-face can turn, say, a potentially therapeutic molecule into a toxic one, or vice versa.
14:22
#176 Human organoids are new AI frontier; Listening to the big bang through the cosmic microwave background Lifeboat News: The Blog
Brainoids tiny clumps of human brain cells are being turned into living artificial intelligence machines, capable of carrying out tasks like solving complex equations. The team finds out how these brain organoids compare to normal computer-based AIs, and they explore the ethics of it all.
Sickle cell disease is now curable, thanks to a pioneering trial with CRISPR gene editing. The team shares the story of a woman whose life has been transformed by the treatment.
We can now hear the sound of the afterglow of the big bang, the radiation in the universe known as the cosmic microwave background. The team shares the eerie piece that has been transposed for human ears, named by researchers The Echo of Eternity.
14:22
A scalable and programmable quantum phononic processor based on trapped ions Lifeboat News: The Blog
Quantum computing systems have the potential to outperform classical computers on some tasks, helping to solve complex real-world problems in shorter times. Research teams worldwide have thus been trying to realize this quantum advantage over traditional computers, by creating and testing different quantum systems.
Researchers at Tsinghua University recently developed a new programmable quantum phononic processor with trapped ions. This processor, introduced in a paper in Nature Physics, could be easier to scale up in size than other previously proposed photonic quantum processors, which could ultimately enable better performances on complex problems.
Originally, we were interested in the proposal of Scott Aaronson and others about Boson sampling, which might show the quantum advantages of simple linear optics and photons, Kihwan Kim, one of the researchers who carried out the study, told Phys.org. We were wondering if it is possible to realize it with the phonons in a trapped ion system.
13:31
New Talk: Richard Stallman Explains His Problem With Rust (Trademark Restrictions), Openwashing (Including Linux Kernel), Machine Learning, and the JavaScript Trap Techrights
Video download
link | md5sum
750dda35e5a1c938a6b961483896da2b
RMS Pre-LibrePlanet Talk (Richard Stallman Gave a Talk
Hours Ago)
Creative Commons Attribution-No Derivative Works 4.0
Summary: Richard Stallmans talk is now available above (skip to 18:20 to get to the talk; the volume was improved over time, corrected at the senders end)
The video above is a recording of the talk Richard M. Stallman (RMS) gave some hours ago. It was a live stream, broadcast by the Free Software Foundation. He founded it many years ago (the GNU Project turns 40 later this year and he turned 70 yesterday). The talk itself starts about 20 minutes into the video above; I had started recording about 15 minutes before the scheduled time of the talk.
At the start, Dr. Stallman notes that he cannot comment much about technical aspects of Rust, but he remains concerned (for a year already) about the trademark aspects. He is still receiving no clarification or assurances on the matter. Previously he suggested forking it and calling it something like crust (in a talk or a session he did with several Brazilian hackers).
Openwashing is not alluded to by that name. But he explains why Linux (the kernel) is non-free. He then comments on Debian including blobs in the installer (as of months ago). He mentions Respect(s) Your Freedom and alludes to various peripherals with code inside them. He suggests not being too judgemental of such microprocessors. Cameras, keyboards, and memory sticks, he says, typically have some small computers in them. Our ultimate goal is that all those should contain free software also, he stresses. To quote: We hope to hope that in the future well be able to [...] replace the non-free programs at a lower level of the products.
He asks for a distinction between software coming inside a piece of hardware and stuff the user adds to it later. These are growing challenges.
He speaks of Machine Learning and rejects the term AI (Hey Hi!). He compares it to dissociated press a very old term, not a buzzword or a misnomer. Its not just t...
13:00
The Blue Soup Saga Is One Beefy Mystery Hackaday

Beef soup! Youd normally expect it to be somewhere from reddish-brown to grey, depending on how well it was cooked and prepared. However, strangely, an assistant professor found the beef soup in their fridge had mysteriously turned blue. That spawned an investigation into the cause which is still ongoing.
[Dr. Elinne Becket] has earned her stripes in microbiology, but the blue soup astounded her. Despite her years of experience, she was unable to guess at the process or a source of contamination that could turn the soup blue. Indeed, very few natural foods are blue at all. Even blueberries themselves are more of a purple color. The case sparked enough interest that [Elinne] went back to the trash to collect photos and...
13:00
DataRobot releases AI Platform 9.0 to deliver value-driven AI Help Net Security
DataRobot has released DataRobot AI Platform 9.0, along with deeper partner integrations, AI Accelerators, and redesigned service offerings, all centered on helping organizations derive measurable value from their AI investments. AI has the potential to enhance every aspect of business transactions and human interactions to improve how we live and work, said Debanjan Saha, CEO of DataRobot. Since our founding, we have been 100% focused on helping enterprises realize measurable value from AI by offering More
The post DataRobot releases AI Platform 9.0 to deliver value-driven AI appeared first on Help Net Security.
12:24
Artistic Attempt To Send Digital Signals Via Fungus Lifeboat News: The Blog
Art projects can fundamentally be anything you like, as long as you say theyre art at the end of it all. They dont always work, or work well, but they often explore new ideas. Often, artists working on installations fall back on similar tools and techniques used by the maker community. [Julian] is no exception, and his Biotic Explorers work has many touchstones that will be familiar to the Hackaday set.
The Biotic Explorers Research Group is a broad art project, involving the creation of a fictitious scientific association. [Julian] created imaginary scientists, reports, and research to flesh out this world. The project culminates in the development of a prototype communications system, which uses pH sensors at either end of a fungal network in soil to send messages.
Liquids are applied to change the pH of the system, which can be picked up at the other end of the soil bed. The pH levels are read as digital signals, with pH levels either side of neutral reading as high and low bits. pH sensors can be expensive, so [Julian] chose the cheapest available, and tapped into their LCD display lines to read their output into an microcontroller. The system displays data using commonly available OLED displays, and hobby servo motors are used to control the dispensing of liquid.
11:50
Owner of Breach Forums Pompompurin Arrested in New York HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
Pompompurin's arrest was confirmed by one of the Breach Forum's administrators, Baphomet.
This is a post from HackRead.com Read the original post: Owner of Breach Forums Pompompurin Arrested in New York
11:44
Getting to Zettascale Without Needing Multiple Nuclear Power Plants SoylentNews
Getting To Zettascale Without Needing Multiple Nuclear Power Plants:
There's no resting on your laurels in the HPC world, no time to sit back and bask in a hard-won accomplishment that was years in the making. The ticker tape has only now been swept up in the wake of the long-awaited celebration last year of finally reaching the exascale computing level, with the Frontier supercomputer housed at the Oak Ridge National Labs breaking that barrier.
With that in the rear-view mirror, attention is turning to the next challenge: Zettascale computing, some 1,000 times faster than what Frontier is running. In the heady months after his heralded 2021 return to Intel as CEO, Pat Gelsinger made headlines by saying the giant chip maker was looking at 2027 to reach zettascale.
Lisa Su, the chief executive officer who has led the remarkable turnaround at Intel's chief rival AMD, took the stage at ISSCC 2023 to talk about zettascale computing, laying out a much more conservative some would say reasonable timeline.
Looking at supercomputer performance trends over the past two-plus decades and the ongoing innovation in computing think advanced package technologies, CPUs and GPUs, chiplet architectures, the pace of AI adoption, among others Su calculated that the industry could reach the zettabyte scale within the next 10 years or so.
Read more of this story at SoylentNews.
11:15
KELA partners with Snowflake to help joint customers remediate potential risks Help Net Security
KELA has partnered with Snowflake to launch its technical intelligence data on Snowflake Marketplace. KELAs Technical Cybercrime Intelligence availability on Snowflake Marketplace will enable joint customers to get near-instant, seamless, and secure access to potentially compromised IPs and domains involved in cybercrime activity. Commenting on the partnership, Itsik Kesler, CTO, said: Our Technical Cybercrime Intelligence capability will benefit Snowflake customers by providing them with the ability to automatically detect and monitor potentially compromised IPs and More
The post KELA partners with Snowflake to help joint customers remediate potential risks appeared first on Help Net Security.
10:39
Feds Charge NY Man as BreachForums Boss Pompompurin Krebs on Security
The U.S. Federal Bureau of Investigation (FBI) this week arrested a New York man on suspicion of running BreachForums, a popular English-language cybercrime forum where some of the world biggest hacked databases routinely show up for sale. The forums administrator Pompompurin has been a thorn in the side of the FBI for years, and BreachForums is widely considered a reincarnation of RaidForums, a remarkably similar crime forum that the FBI infiltrated and dismantled in 2022.
Federal agents carting items out of Fitzpatricks home on March 15. Image: News 12 Westchester.
In an affidavit filed with the District Court for the Southern District of New York, FBI Special Agent John Longmire said that at around 4:30 p.m. on March 15, 2023, he led a team of law enforcement agents that made a probable cause arrest of a Conor Brian Fitzpatrick in Peekskill, NY.
When I arrested the defendant on March 15, 2023, he stated to me in substance and in part that: a) his name was Conor Brian Fitzpatrick; b) he used the alias pompompurin/ and c) he was the owner and administrator of BreachForums the data breach website referenced in the Complaint, Longmire wrote.
Pompompurin has been something of a nemesis to the FBI for several years. In November 2021, KrebsOnSecurity broke the news that thousands of fake emails about a cybercrime investigation were blasted out from the FBIs email systems and Internet addresses.
Pompompurin took credit for that stunt, and said he was able to send the FBI email blast by exploiting a flaw in an FBI portal designed to share information with state and local law enforcement authorities. The FBI later acknowledged that a software misconfiguration allowed someone to send the fake emails.
In December, 2022, KrebsOnSecurity broke the news that hackers active on BreachForums had infiltrated the FBIs InfraGard program, a vetted FBI program designed to build cyber and physical threat information sharing partnerships with experts in the private sector. The hackers impersonated the CEO of a major financial company, applied for InfraGard membership in the CEOs name, and were granted admission to the community.
From there,...
10:12
New Vishing Attack Spreading FakeCalls Android Malware HackRead | Latest Cybersecurity and Hacking News Site
The malware campaign was noted to target users in South Korea.
This is a post from HackRead.com Read the original post: New Vishing Attack Spreading FakeCalls Android Malware
10:00
Broken Pocket Watch Becomes Pocket Sundial Hackaday

Pocket watches are all well and good, but they have some caveats. They either need regular rewinding, or they need batteries. Sundials on the other hand need only the light from our One True Sun. [JGJMatt] has just the project to convert your broken or disused pocket watches to the solar way of telling the time.
The key is to replace the clockwork internals and face of the pocket watch with a sundial instead. The first step is to create a face for the watch marked out for sundial use. [JGJMatt] explains how to do this with a variety of CNC, painting, or etching methods. He also explains how to use simple tools to generate a sundial design thats ideally suited to your geographical location. This includes methods for aligning the sundial to True North or True South with an offset compared to Magnetic North or Magnetic South. This allows the sundial to be as accurate as possible. [JGJMatt] describes the general techniques while also building a sundial of his very own. The resulting piece is a handsome bit of brass with a lovely gnomon standing tall to cast a shadow on the dial.
Its not a quick way to tell t...
09:36
Who Follows 1xbet Presents An Impressive List Of Sports Activities Betting Choices h+ Media
Who Follows 1xbet Presents An Impressive List Of Sports Activities Betting Choices
As you can see, the bookmaker company permits the users to decide on the registration method to own style. Decide which one fits you better of all, start the registration course of and enjoy on the market forms of sports activities activities as quickly as potential. 1xBet bookmaker is the name that just about each bettor may need come throughout. The bettor needs to obtain 1xbet app and to create a code. The program will assist to create a better password in addition to a unique login.
Also, the stay streaming app permits online players to watch matches of each in style leagues and distinctive sports activities. To do that, you have to log in and replenish your gaming account for a minimum amount. Its a typical factor when retailers supply prospects a bonus a reduction with a funded system. The bettor has an chance to use his Facebook, Google+ or Vk profile for this objective. It routinely turns right into a affirmation of his individuality.
The utility has great reviews, in plenty of respects due to the broad possibilities, from creating an account with a welcome bonus on bets to video games. Completing the 1xBet Android app get hold of and installing it on a gadget, a player will get fast entry to the complete performance of the betting platform. The equally fast transition is offered within the app and desktop model. Everyone chooses what to make use of based on their non-public preferences. Furthermore, players additionally get access to a 24/7 gaming platform and timely fee options.
In order to be taught more relating to the total report on on-line payments on betting web site 1xGuess, all people studying this should go to the 1xGuess platforms. The listing of the latter contains the championships of each nation, beginner tournaments, and qualifying rounds. [newline]The website online supplies special statistics, that you must use to get acquainted with the probabilities of a certain employees to win, along with betting coefficients. The latter requires stepping into private data, as appropriately as telephone number alongside the e-mail. To get pleasure from this bonus use the1xBet promo codeto make your bets. You can simply find out from recommendations on how to use 1xBet bonus elements. By putting within the 1xBet app, youll have the flexibility to guess on a pre-match or stay match.
If you select sports activities for the bonus provide, youll obtain +100% in your first deposit as so much as 20,000 INR. This betting company additionally permits the person to put a guess on a selection of sports activities available on 1xBet Bangladesh official web site. It has a 24/7 stay chat alternative from a 1xBet admin private for queries and clarifications, across the clock reside betting occasions, multi-live function, and so forth. There are many poker tables, roulettes, blackjack as nicely as slot machines. The particu...
09:34
Search Outcomes For boo On Line Casino No Deposit Bonus Code Open8010betcom Fifa 22 Beta Cellular Obtain 1xbet App Download 2022 Open8010betcom$$limitadong Regalo!mag Register Para Makakuha Ng P50 Might 50% Cashback Sayong Unang Deposit!$$wv h+ Media
Search Outcomes For boo On Line Casino No Deposit Bonus Code Open8010betcom Fifa 22 Beta Cellular Obtain 1xbet App Download 2022 Open8010betcom$$limitadong Regalo!mag Register Para Makakuha Ng P50 Might 50% Cashback Sayong Unang Deposit!$$wv
Its value noting that the official program at present holds a very extreme score in Apples retailer. Click on considered one of many supplied odds and select Bet or Add to Coupon. In the primary case youll make a single guess, contained in the second a parlay or a gaggle guess. Use the login and password you specified when registering your account or use any totally different technique of logging in. The gamblers are in a place to get the profitable soon after they win.
Only high coefficients wont be succesful of guarantee the long-term status of a bookmaker. If a company must succeed and appeal to lots of purchasers, it have to be ready to supply something further, as an example, 1xBet app for computer or one thing like that. This is to have the ability to make all the person experience as easy and as simple as attainable. The participant receives a complete listing and enough ratios, which contributes to a satisfying pastime.
The sms will comprise a momentary password that the bettor can change it. Pharmacist Only Medicine Pharmacist recommendation is required to buy this product. Please note that we reserve the proper to say no supply if the pharmacist assesses that using this drugs just isnt acceptable.
It will include several cifras, that are legitimate for a limited period. The bettor must fill out private data and economical data. I gave my good pal 1xbet registration hyperlink and he did the process in 5 minutes and he bets on sports activities with me. It is utilized by tens of 1000s of players as a outcome of it allows them to wager sooner and less complicated.
The Google Authenticator app could be downloaded onto most smart gadgets. If youve put in Authy, you do not want to put in Google Authenticator. Hi seems like you are not having entry to member information as were both waiting upon or processing your payment in your membership. At Electrify NZ we imagine the future of transportation is electrical.
To join up, its additionally necessary to specify your cell phone quantity and your real data, label and surname. This is actually the rationale why safe wager with 1xChoice on line playing home could also be made with absolute security. For occasion, a consumer can first insure 10%, subsequently 30%, then one other 50%.
The utility has nice reviews, in a lot of respects due to the broad potentialities, from creating an account with a welcome bonus on bets to video games. Completing the 1xBet Android app get hold of and installing it on a gadget, a participant will get fast entry to the entire performance of the betting platform. The equally quick transition is offere...
09:34
Functions For The 2021 Nzes Mentoring Scheme Now Open h+ Media
Functions For The 2021 Nzes Mentoring Scheme Now Open
You can choose the English variant, and its clear that the standard of the interpretation of 1xBet sport betting platform could also be very extreme. We can see the sections of the matches, promos, virtual sports activities, slot machines and a lot of others. Easy entry to on line on line casino from the 1xBet sport betting part to the on line casino and, and vice versa.
For soccer lovers, betting can be made on the outcome of the match as nicely as corners, free kicks, and yellow cards, and so on. When you be a part of the 1xbet on line casino section, a plethora of slot video games are at your fingertips. You can enjoy titles that have been impressed by animals, mythology, movies, Politicians, TV sequence, stars, and more. The betting and gaming site is simple to navigate since it features a user-friendly interface. Each betting possibility is accompanied by a straightforward to navigate drop-down that promotes self-discovering.
We need to make it simple so that you simply can browse, find and check out an electrical bike (e-bike) that works for you, from an intensive range of high quality ebike brands. From commuter ebikes, to folding e-bikes to electrical mountain bikes, we have a motorcycle to fit your finances and use. Book a free check journey at Electrify NZ and luxuriate in the advantages of an e-bike today.
There are an enormous number of high-quality on line casino games to choose from. Then your bookmaker might ask to supply a photo or check out of passport or some other personal doc that may verify your id. After that, youll be redirected for the webpage, to buy a account generated mechanically. Near the top of the home web page from the app, you can find the alternative registration button. Select the country program code within the subject with the cellphone quantity. Thats the reason the company offers not one but a level of choices for this well-liked online game with Jackpot and nice payout.
The know-how guarantees around the clock protection for personal information. The process is similar to setting an individual guess with the difference that there are extra options over the coupon that you ought to use. Choose the combinations you need, place your guess, and validate it.
The bookmakers group made positive that the bettors had a chance to guess on sports activities actions or play within the on line on line casino, poker and slots, and so forth. To begin betting on 1xBet bd or play 1xBet poker, you must first register and replenish your stability. Betting change alternative consists of eight the most well-liked sports actions to guess efficiently in opposition to other prospects. Nonetheless, lets not get ahead of ourselves for the explanation that ultimate verdict relies upon tremendously on the net sites payment/withdrawal capabilities. Now you need to type in the information, collectively together with your full...
09:32
Reap The Advantages Of 1xbet App h+ Media
Reap The Advantages Of 1xbet App
The bookmakers group made positive that the bettors had a chance to guess on sports activities activities or play in the on line on line casino, poker and slots, and so forth. To start betting on 1xBet bd or play 1xBet poker, you should first register and replenish your stability. Betting change different consists of eight the most well-liked sports activities to guess successfully against different clients. Nonetheless, lets not get forward of ourselves since the ultimate verdict relies upon tremendously on the net sites payment/withdrawal capabilities. Now you must type within the data, collectively with your full name, foreign money that youll be using, and so forth. 1xbet utility is absolutely compatible with all kinds of operating methods.
After the basic identification verify, the player has to get through a regular registration process. These methods are used when blocking the organizations website and provide access. With the first 4 deposits, customers can receive a welcome bonus as excessive as INR one hundred thirty five,000 at 1xWager Casino. Compared to further betting platforms, this bookmaker gives his one of many better casino welcome bonus products obtainable to Indian players. There is an totally different choice, though, any buyer can discover it on the official website online of the bookmaker. The one who makes betting is generally watching sports activities activities events regularly.
The comparability of bookmakers,sometimes, highlights the work of these departments. The firm turned well-known very quickly with the help of all the issues listed above. When contacted chat help they informed my cellphone number is linked to another account and mail to safety for the same. The identical payment methods can be utilized to withdraw the profitable. The bettors of 1xbet can withdraw each small and enormous amounts of cash. In order to take a giant profitable its all the time better to depend on banks companies.
1xBet also has a simple to make use of browser named the 1x browser that targets Android customers. 1x Bet is really a actually good gambling web site in India with incredible sports activities bets and online casino sections. The sports activities delightful bonus consists of a one hundred pc match extra as high as 20,000. Moreover, you want to use promo program code 1XSeries22 while registering and stand up to 130% extra on the primary deposit. The coupon acquired for bonus factors just isnt money, however you presumably can win it by making a profitable guess. When registering at a bookmaker, along with within the means of using its functionality, you presumably can profitably apply particular promotional codes.
All on line casino titles out there on the desktop website are additionally current in the 1xBet casino cell versions. The 1xBet live on line casino platform targets players in search of the actual on line casino experie...
09:30
Mostbets Mobile Version Has A Variety Of Benefits h+ Media
Mostbets Mobile Version Has A Variety Of Benefits
It contains making an attempt to foretell the competitions ultimate consequence. Allows the app to forestall the gadget from going to sleep.. Allows the app to view details about community connections similar to which networks exist and are related..
IOS Android You can discover the app within the Apple Store, so youll have the ability to open it and install an application as all the time. The design is optimized for all screen sizes and resolutions, so it would be comfortable to make use of the network web site to achieve some cash. Mostbet team does their greatest to make your gaming expertise as diversified as possible. Consequently, there are several types of putting odds out there in your fun.
The application is completely examined and safe in your gadget. Our utility database is protected, as we frequently scan programs with antivirus software. If you are a newbie, then you can use social networks for verification or e mail.
The app routinely adjusts itself to suit the screens diagonal. Mostbet offers players with the opportunity to immerse themselves in a visually gorgeous and evocative world of various on-line casino enjoyment. The casino web page on the internet and in the app is built in a vigorous environment, the place you presumably can remember to have a beautiful time whereas incomes actual money. In this article, youre going to get information about one of the most well-liked bookmakers in India.
Allows the app to create network sockets and use customized network protocols. The browser and different functions present means to send data to the internet, so this permission isnt required to ship information to the web.. Free play the most popular slot machines and video games. Above weve already lined many sturdy sides of the network.
The bookmaker first opened its doors in 2009 and has since grown to a multi-million player base and expanded its operations to more than ninety nations. The service is always altering, and the quality of the companies improves yr after year. Because Mostbet is legal in India and extensively regarded by Indian gamers, you might be assured in your gains.
The Latest Version of 7.three.5 Available for download. Download the app utilizing your favourite browser and click on on Install to put in the applying. Please note that we offer each basic and pure APK files and quicker download speeds than APK Mirror.
Replenishment and withdrawal of funds can carry out utilizing financial institution playing cards and digital wallets. You can additionally use Bitcoin, Litecoin, Ethereum, and Ripple. Prepare an digital copy of your passport prematurely. Sometimes a company practices Skype calls to verify a players identity.
To contact them, you have to use e-mail or name the indicated cellph...
09:27
Obtain Mostbet Apk Free For Android h+ Media
Obtain Mostbet Apk Free For Android
If you start it on your gadget, you see that theres the same line alternative as within the desktop one. Cricket, basketball, baseball, tennis, ipl, soccer, and a separate section bookmaker workplace is 100 percent identical to the desktop one. Mostbet bd app is a sports betting application obtainable for each Android and iOS gadgets. It permits its clients to be told about interesting matches, new bonuses, and paid bets. The app presents push-up notifications so that you simply dont have to download it to view the notifications.
However for Apple devices there may be a greater approach to obtain software program program from the App Retailer. Mostbet accepts bank transfers, payments methods, and e-wallets , as nicely as cryptocurrency deposits. Mostbet India works with the PayTM system and takes rupees. Making a deposit is straightforward and fast, and money is mostly out there instantly. The same is true for withdrawals; its preferable to use the same payment technique as for deposits, since this eliminates the necessity for added data.
The net application is presented in Mostbet apk format and is appropriate for Android gadgets. Just click on the button and await the obtain. It only takes a couple of minutes to install the required information. It is now very easy to place a web-based wager out of your mobile phone.
The firm is consistently creating, introducing new features to offer players with comfortable circumstances. Go to the cell model of the site from your smartphone. Then register with the bookmaker and download the application in Mostbet apk format.
The obtain is as direct as our velocity and we provide direct hyperlinks to all available variations of Mostbet APK free of charge. The Mostbet Apk is available for iPhone, Android, and Windows devices. The Mostbet Apk mobile web site is straightforward to make use of and would not have to be downloaded to your device.
Again, work is carried out at night time, when most gamers are sleeping. The website or app is undergoing technical or upkeep work. It usually takes no more than an hour and occurs at night so as not to intervene with bettors enjoying online.
Mostbet provides an app for Android customers thats appropriate for both smartphones and tablets. You can obtain the app from the Google Play store or some other alien source and set up it to your system. Once put in, you probably can place your bets or play the games.
Sports Betting is mostbet,sports,bookmaker,company.,betting, content material rating is Everyone (PEGI-3). This app is rated 5 by 1 users whore using this app. To know extra in regards to the company/developer, visit cpp ligastavok web site who developed it. Org.adverts.mostbet.apk apps may be downloaded and put in on Android 4.1.x and better Android gadgets.
Once the set u...
09:25
Mostbet App Evaluate
This might be because of technical points and hacker attacks or the company having a license abroad. Therefore, on this part, Mostbet talks about its present tackle. You can go to Mostbet at any time through our website. You also can benefit from the Mostbet casino, however this can be a bit inconvenient, so it is much better to use the app.
Again, work is carried out at night, when most players are sleeping. The web site or app is present process technical or maintenance work. It often takes no extra than an hour and occurs at night in order not to interfere with bettors playing on-line.
You can also register using the app, or you can log in via the operators web site. There is a simple way you should comply with for download and install Mostbet Apk 2021 in your android system. AS you know already if you obtain any apk apps from the net other than playstore you want to make some settings in your android system. The sports activities at Mostbet is out there in the type of stay video games, quick video games, virtual and e-games. Their sports betting gallery has over 10 video games for line. Most of the e-sports can be found for betting and the players can even entry live matches directly from the net site.
gadgets. These options are so simple to use that newbies wont discover any difficulties on the first betting attempt. [newline]Features like quick access, intuitive navigation, and clean design have made staking extra attractive for every person. The search bar function additionally made it easy for customers to rapidly find any class of a specific event. Mostbet is among the best betting platform that offers players one of the best probability to win big. They have been one of the best bookmaker and so they have been within the betting business for more than 12 years. During these years, they have been in a position to present excellent providers to their shoppers.However, you can nonetheless install APK recordsdata with OBB directly on your android system. You need to have ES File Explorer app on your android device if you would like to install the APK with OBB knowledge immediately in your android gadget. When you go to the homepage of the official web site, in the best prime corner youll find a huge purple Register button. Click on it, and youll see a kind, the place you should select an option for registration through the mobile number, e-mail, or social media networks. After making a deposit, the bonus cash will be credited to a particular account, and in order to withdraw it, the welcome bonus will need to be wagered. It is price noting that not considered one of the versions of the mobile app does help the perform of simple communication with the customer assist specialists.
Once the set up is full, launch the Mostbet app and check in to your Mostbet account. The Mostbet app is simple to use and can...
09:23
Wine 8.4 Released With The Early Wayland Graphics Driver Code, 51 Bug Fixes Phoronix
09:04
Everything Everywhere All at Once Piracy Skyrockets After Oscar Win TorrentFreak
 The Oscars are the most anticipated movie awards show
of the year, closely followed by hundreds of millions of movie fans
around the world.
The Oscars are the most anticipated movie awards show
of the year, closely followed by hundreds of millions of movie fans
around the world.
This years Academy Awards ceremony received plenty of attention as well, with one film standing out from all the rest.
With seven awards overall, including Best Picture, Best Director, and Best Actress, Everything Everywhere All at Once was the star of the night. The independent film impressed the voters, despite having a relatively tiny budget compared to competitors including Top Gun: Maverick and Avatar: The Way of Water.
The success didnt come as a complete surprise. The film had already scooped up dozens of accolades, including two Golden Globes, but winning seven Oscars was an entirely different level.
Oscar Boost
Renewed attention from the press and film fanatics boosted interest among the broader public. This typically increases legal sales and views on streaming platforms, especially for relatively small releases.
Everything Everywhere All at Once is no longer running in theaters, so there is no bump there. That said, there is another area where we observed a massive spike in interest, although thats unlikely to please the filmmakers.
The Oscars typically have a direct impact on piracy activity, and the big Oscars winner is no exception. Based on a sample of torrent activity tracked by IKnow, we can report that pirated downloads of Everything Everywhere All at Once skyrocketed this week.
Oscar Piracy
Before discussing the numbers, its important to highlight that pirated copies of the Oscars winner have already been circulating for months. The first high-quality copy leaked last May and it was in the top ten most pirated films for several weeks in a row.
Since its release, the film has been illegally downloaded and streamed millions of times. In January of this year, we observed two modest spikes in downloads, once after the Golden Globes win a...
08:52
In Wild Hacking Spree, Hackers Accessed Federal Law Enforcement Database SoylentNews
The U.S. government database provided access to a treasure trove of sensitive data. "I can request information on anyone in the U.S.," one of the alleged hackers wrote:
Two men, one of whom previously presented themselves as an independent security researcher to Motherboard, allegedly went on a wide spanning hacking spree that included breaking into a federal U.S. law enforcement database; using a compromised Bangladeshi police officer's email to fraudulently requesting user data from a social media company; and even trying to buy services from a facial recognition company which doesn't sell products to the wider public.
[...] Sagar Steven Singh, 19, was arrested in Rhode Island on Tuesday; Nicholas Ceraolo, 25, remains at large with his location listed as Queens, New York, a press release from the United States Attorney's Office for the Eastern District of New York says. "Singh and Ceraolo unlawfully used a police officer's stolen password to access a restricted database maintained by a federal law enforcement agency that contains (among other data) detailed, nonpublic records of narcotics and currency seizures, as well as law enforcement intelligence reports," it states.
[...] That pursuit of personal information is what allegedly drew Singh and Ceraolo to breaking into various law enforcement accounts. In one case, the pair allegedly used a police officer's credentials to access a web portal maintained by a U.S. federal law enforcement agency.
Also at Dnyuz.
Read more of this story at SoylentNews.
08:42
Hitachi Energy breached by Clop gang through GoAnywhere Zero-Day exploitation Security Affairs
Hitachi Energy disclosed a data breach, the Clop ransomware gang stole the company data by exploiting the recent GoAnywhere zero-day flaw.
Hitachi Energy disclosed a data breach, the company was hacked by the Clop ransomware gang that stole its data by exploiting the recently disclosed zero-day vulnerability in the GoAnywhere MFT (Managed File Transfer).
The company was the victim of a large-scale campaign targeting GoAnywhere MFT devices worldwide by exploiting the zero-day vulnerability.
We recently learned that a third-party software provider called FORTRA GoAnywhere MFT (Managed File Transfer) was the victim of an attack by the CLOP ransomware group that could have resulted in an unauthorized access to employee data in some countries. reads the statement pblished by the company.
Upon learning of this event, we took immediate action and initiated our own investigation, disconnected the third-party system, and engaged forensic IT experts to help us analyze the nature and scope of the attack. Employees who may be affected have been informed and we are providing support. We have also notified applicable data privacy, security and law enforcement authorities and we continue to cooperate with the relevant stakeholders.

Hitachi Energy immediately launched an investigation into the incident and disconnected the compromised system. The company reported the data breach to law enforcement agencies and data protection watchdog.
The company pointed out that its network operations o...
08:24
Links 17/03/2023: CentOS Newsletter and News About Mr. UNIX Ken Thompson Hopping on GNU/Linux Techrights
-
GNU/Linux
-
Desktop/Laptop
-
HowTo Geek The System76 Meerkat Is a Tiny PC Built for Linux
System76 is one of the few PC manufacturers with a focus on excellent Linux support, with a wide range of desktops and laptops. Now the company has brought back the Meerkat, a compact PC built for Linux.
System76 first introduced the Meerkat in 2009, which was advertised as a NetTop (remember those?), and has gone in and out of production over the years with occasional hardware upgrades. The tiny PC is once again available for purchase, this time with your choice of 10th, 11th, or 12th Gen Intel Core processors. There are two sizes: a short model (1.42 inches tall) with only one M.2 drive slot, and the bay for extra storage capacity. Both versions are 4.6 x 4.41 inches across.
-
-
Applications
-
Linux Links Excellent Utilities: nvitop GPU process management
...
-
-
08:14
Top Five Reads on FOSS Force for Week Ending March 17, 2023 FOSS Force
Here are the five most read articles on FOSS Force for the week ending March 17, 2023. Despite What Youve Heard, Open Source 101 Isnt
The post Top Five Reads on FOSS Force for Week Ending March 17, 2023 appeared first on FOSS Force.
07:57
The European Patent Offices Central Staff Committee Explains the Situation at the EPO to the Yes Men of Antnio Campinos (Who is Stacking All the Panels) Techrights
Video download
link | md5sum
59217133f9f9582b2c0934acb9c644a5
EPO and the GCC Meeting
Creative Commons Attribution-No Derivative Works 4.0
Summary: The EPOs management is lying to staff (even right to their faces!) and it is actively obstructing attempts to step back into compliance with the law; elected staff representatives have produced detailed documents that explain the nature of some of the problems theyre facing
THE
document discussed above [PDF] is very long. It
can help explain internal EPO
affairs to outsiders i.e. people to whom EPO blunders are known
only through media channels (those that Benot Battistelli and Antnio Campinos have not intimidated into
silence with threats of lawsuits and various sanctions).
The Central Staff Committee (CSC) does a good job explaing the hoax studies of the administration, pretending that the EPO is poor in order to lessen the compensation to staff and thus deter/discourage properly-trainied and experienced staff from joining/staying. Todays EPO is gradually running out of talent; as EPO insiders have warned repeatedly, this will result in further collapses, including patent quality and validity issues (illegitimate patents being granted, including European software patents). The biggest stakeholders in the EPO have already complained about the quality of European Patents; they too stand to lose because many of these patents can be used against them; only patent litigation firms stand to benefit regardless of the merit of cases.
The covering message (like cover letter) for the above PDF stated what was discussed, albeit the cronies of the President didnt bother discussing much. They just said yes to proposals. Heres the outline:
R...
07:37
1xbet Cell App In Liberia h+ Media
1xbet Cell App In Liberia
IOS users want a tool of a minimum of 6.zero to make the most of all of the choices on the app. Below is a list of each Android and iOS units which may be appropriate with the 1xBet app. By installing this app, you can execute all functions on 1xBet. The app is absolutely geared up with all features that you can find on the desktop. For occasion, youll find a way to create a model new account, claim bonuses, and make deposits and withdrawals.
Well over 90% of the bets placed on cricket matches are carried out in-play. Make sense with the character of the sport of cricket some times being long and good spacing for the motion. Compared to other prime betting websites we have reviewed, 10Cric is relatively new. We prefer it for its centered attention to Cricket and Indian gamers, with a lot of games having local flavouring. Their portfolio of games and occasions retains increasing every few weeks.
In phrases of functionality, the 1xbet app provides a clean and intuitive person experience with all of the features and companies youd find on their desktop site. One notable feature is the 1xbet live streaming option for numerous sports activities, which lets you stay up to date with the latest match developments.
Live betting is a popular possibility for on-line bookmakers, and 1xBet app additionally has this function. You can find this selection on the highest menu of the display.
To be on the safer side, make certain that the betting web site you might be utilizing is properly registered and licensed and its utterly secure and safe. Select Cricket from the websites menu and select a match/series/tournament you want to guess on. Sign up and create your betting account with that website. Covering predictions & previews on prime Cricket Tournaments; get match odds & updates on all One Day, Test & T20 Tournaments. Despite a group being in its type, the match outcome might be waived if it loses toss in a field where the pitch favors those who bat first or ball first. Thats where your betting decision should be calculated once more.
It is only a bunch of codes which are doing no going to our devices house till we make them work. Thats why this onex wager app launching stage turns out to be useful and bears excessive significance to the operation. Unfortunately, we want to run some system adjustments to make sure our technology recognizes the retrieved program recordsdata. Technology has heightened lots of transactions, some leading to constructive results while others fail to ship. However, ix wager app has not simply modified the way customers run varied operations, as an alternative, it has been the scoreboard against which different bookmakers assess their efficiency.
1xbet helps associates program promotions for new players. These gamers normally are out there in by way of a referral link offered to them by 1x...
07:34
Features Of 1xbet Cell App For Indian Gamers h+ Media
Features Of 1xbet Cell App For Indian Gamers
Please check the web playing regulation in your jurisdiction earlier than putting any bets on any betting websites advertised on our website. Here at OCB our objective is to review all of the betting websites our customers use, and time from time there are new betting sites entering the gaming markets. If you have been to discover a betting website that supplied you 1.25 odds on India to win, youll get an extra INR 50 for every INR a thousand you guess on India to win. These small sums adds up in case you are betting a lot of games, so keep in mind to shop round for the highest cricket betting odds. Since the time we began reviewing Parimatch for his or her local providing, weve constantly seen new features or fee options being added on their web site each few weeks.
ClaimGo to websiteOpen an account with bet365 right now and guess on an infinite range of markets with the worlds favourite on-line sports activities actions actions betting agency. They have been aggressive at making this regarded, and as a Nigerian participant, you need to be conversant on this. This isnt a shock, contemplating the precise truth what odds are outfitted to purchasers.
Even though sports betting and playing isnt legal in India, there are not any legal guidelines towards online gambling. This fact makes 1xBet authorized in Andhra Pradesh and different Indian states. Every player who is into betting has had the thought, What if I need to bet outdoors of simply my home? You can guess wherever you might be, using a state-of-the-art cell consumer. But earlier than downloading, allow apps from third-party sources to be put in. I even have been taking part in on 1x bet.com for over 5 years and this is one of the best place to bet.
It is very famous and players worldwide attempt to get auctioned and be a half of any of the 7 groups of the league. The Top IPL Betting Apps present a complete betting expertise for its customers. As far as cricket betting is worried, online cricket betting has witnessed the influx of millions of bettors from around the globe. Cricket is among the hottest sports in the world and the introduction of latest shorter formats within the sport has increased its betting market value by large numbers. Furthermore, the chances displayed on our website are for informational purposes solely and can not be wagered on. We arent a betting site and do not settle for bets from gamers.
Despite quite a few playing websites on the Internet, 1XBET continues to be probably the greatest web sites for sports betting in CIS countries. This is as a end result of it has all of the features required to make betting more convenient. These embody; detailed rules and instructions, reliable statistics, and protected payment methods. Although the response time isnt so fast, general, 1xBet has glorious customer support, which is great for an internet betting fir...
07:31
Password Generator
Minimum downpayment permitted is ten Euro, which is added to the account of the shopper therefore its made efficiently. In in the future, you should wager a turnover of 3 occasions the bonus quantity. After login, choose the Cards possibility in the Deposit part and fill within the required card details. After making a deposit into your 1xBet app, you may be eligible to receive a deposit bonus . After that, await the app to download and proceed to install. WebCatalog SpacesOrganize apps and accounts into tidy collections with Spaces.
There is not any want to put in torrent information and use mirrors. We ask that you simply contemplate turning off your advert blocker so we will deliver you the best expertise possible while you are right here. Tract IQ offers knowledge and visualizations showing where all new residence developments and multi-family amenities are being constructed. Health Poll 1xbet promo kod ochish Database presents health-related U.S. survey questions, overlaying eighty years of national polling. Supporting materials embrace examine guides, essays, and interviews with teachers & practitioners. The following databases are newly acquired or being evaluated for a future subscription. Crypto change large Coinbase has filed an amicus brief in its insider buying and selling case, slamming the SEC for not providing a clear regulatory method.
One of the USP is tt additionally supplies its participant with reside streaming on cricket, football, horse racing and extra . You can simply take your gaming to the subsequent degree on 1xbet app on line casino dashboard. They present the best range of events, with some thrilling ones like stay vendor games taking the center sport.
You can conduct 1xbet app free obtain for iOS devices or iPhone by following the download and set up steps outlined under. For the comfort of customers 1xbet has developed software for cell and laptop platforms.
Once prepared, they will type 1xbets name in the search field, use their Apple ID, and full this process. The app offers a perfect platform to scan the 1xBet web site and establish such extra sports betting incentives. You can even use the app to plan your sports activities betting schedule. The fact that 1xBet apps are fitted with automatic updates will allow you to spare some sources for upcoming events.
When you are pleased with the selection youve made, youll have the ability to return to the main menu of the 1xBet app and click on on on the Bet Slip possibility. This will convey up your coupon with all the totally different alternatives youve made. 1xBet is one of the solely betting apps in India that lets you bet on kabaddi. Please observe that the 1xBet register process is possible in several ways without delay.
Also, the app size is 249.2 MB, so ensure to have no less than this muc...
07:29
Chinese Hackers Exploiting 0-day Vulnerability in Fortinet Products HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
According to researchers, multiple Fortinet products were impacted by this vulnerability, including FortiManager, FortiGate, and FortiAnalyzer.
This is a post from HackRead.com Read the original post: Chinese Hackers Exploiting 0-day Vulnerability in Fortinet Products
07:00
Finessing a Soldering Iron to Remove Large Connectors Hackaday

One of the first tools that is added to a toolbox when working on electronics, perhaps besides a multimeter, is a soldering iron. From there, soldering tools can be added as needed such as a hot air gun, reflow oven, soldering gun, or desoldering pump. But often a soldering iron is all thats needed even for some specialized tasks as [Mr SolderFix] demonstrates.
This specific technique involves removing a large connector from a PCB. Typically either a heat gun would be used, which might damage the PCB, or a tedious process involving a desoldering tool or braided wick might be tried. But with just a soldering iron, a few pieces of wire can be soldered around each of the pins to create a massive solder blob which connects all the pins of the connector to this wire. With everything connected to solder and wire, the soldering iron is simply pressed into this amalgamation and the connector will fall right out of the board, and the wire can simply be dropped away from the PCB along with most of the solder.
There is some cleanup work to do afterwards, especially removing excess solder in the holes in the PCB, but its nothing a little wick and effort cant take care of....
06:43
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Jakub Wilk on Mar 17
* Hanno Bck <hanno () hboeck de>, 2023-03-17 11:48:[...]
Agreed.
I don't think that's gonna fly, because...
TIOCLINUX implements also functionality unrelated to copying and
pasting. See the ioctl_console(2) man page:
https://manpages.debian.org/unstable/manpages-dev/ioctl_console.2.en.html#TIOCLINUX
For example, apparently some of this stuff is used by systemd:
$ git grep -wB5 TIOCLINUX...
06:37
Open Source Initiative Extends Voting Period After Email Typo FOSS Force
Pushing the end of voting back by one day assures there will be no confusion about when the polls close, which could have cost some OSI members their votes.
The post Open Source Initiative Extends Voting Period After Email Typo appeared first on FOSS Force.
06:11
Precise Solar Observations Fed Millions in Ancient Mexico SoylentNews
Aztec farming calendar accurately tracked seasons, leap years:
Without clocks or modern tools, ancient Mexicans watched the sun to maintain a farming calendar that precisely tracked seasons and even adjusted for leap years.
Before the Spanish arrival in 1519, the Basin of Mexico's agricultural system fed a population that was extraordinarily large for the time. Whereas Seville, the largest urban center in Spain, had a population of fewer than 50,000, the Basin, now known as Mexico City, was home to as many as 3 million people.
To feed so many people in a region with a dry spring and summer monsoons required advanced understanding of when seasonal variations in weather would arrive. Planting too early, or too late, could have proved disastrous. The failure of any calendar to adjust for leap-year fluctuations could also have led to crop failure.
Though colonial chroniclers documented the use of a calendar, it was not previously understood how the Mexica, or Aztecs, were able to achieve such accuracy. New UC Riverside research, published in the Proceedings of the National Academy of Sciences, demonstrates how they did it. They used the mountains of the Basin as a solar observatory, keeping track of the sunrise against the peaks of the Sierra Nevada mountains.
"We concluded they must have stood at a single spot, looking eastwards from one day to another, to tell the time of year by watching the rising sun," said Exequiel Ezcurra, distinguished UCR professor of ecology who led the research.
To find that spot, the researchers studied Mexica manuscripts. These ancient texts referred to Mount Tlaloc, which lies east of the Basin. The research team explored the high mountains around the Basin and a temple at the mountain's summit. Using astronomical computer models, they confirmed that a long causeway structure at the temple aligns with the rising sun on Feb. 24, the first day of the Aztec new year.
Journal Reference:
Exequiel Ezcurra, Paula Ezcurra, and Ben Meissner, Ancient
inhabitants of the Basin of Mexico kept an accurate agricultural
calendar using sunrise observatories and mountain alignments
[open], PNAS, 2022. DOI: https://doi.org/10.1073/pnas.2215615119
Read more of this story at SoylentNews.
05:15
Fake Telegram and WhatsApp clones aim at crypto on Android and Windows HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
Currently, the scam targets users who speak Chinese.
This is a post from HackRead.com Read the original post: Fake Telegram and WhatsApp clones aim at crypto on Android and Windows
05:15
FakeCalls Vishing Malware Targets South Korean Users via Popular Financial Apps The Hacker News
An Android voice phishing (aka vishing) malware campaign known as FakeCalls has reared its head once again to target South Korean users under the guise of over 20 popular financial apps. "FakeCalls malware possesses the functionality of a Swiss army knife, able not only to conduct its primary aim but also to extract private data from the victim's device," cybersecurity firm Check Point said.
04:58
Firmware Assisted Shadowing Code Posted For AMD RDNA3 - Needed For SR-IOV Phoronix
A new patch series posted today is of interest and is for firmware-assisted shadowing for AMD RDNA3 (GFX11) graphics processors as it's necessary for proper SR-IOV support...
04:27
L.A. Riders Bail on Metro Trains Amid Horror of Deadly Drug Overdoses, Crime cryptogon.com
Via: Los Angeles Times: Drug use is rampant in the Metro system. Since January, 22 people have died on Metro buses and trains, mostly from suspected overdoses more people than all of 2022. Serious crimes such as robbery, rape and aggravated assault soared 24% last year compared with the previous. Horror. Thats []
04:18
Microsoft 365 Copilot: AI Assistant Integrated with Office Applications cryptogon.com
Via: IT Pro: Microsoft has integrated its AI technology into the entirety of the Microsoft 365 productivity suite, with businesses set to experience significant time savings with meetings. Named 365 Copilot, the AI helper is being added across the Office apps and can cut down time spent writing up meeting notes, combing through inboxes, and []
03:56
Polish MiG-29s to Ukraine cryptogon.com
Via: The Warzone: In the latest development in the saga of getting Polish Air Force MiG-29 Fulcrum fighter jets to Ukraine, the Polish president has confirmed that the first four examples will be handed over to Kyiv within the next few days. More MiGs will be transferred to Ukraine after that, Polish President Andrzej Duda []
03:29
Baidu Shares Fall After Ernie AI Chatbot Demo Disappoints SoylentNews
Shares of Baidu fell as much as 10 percent on Thursday after the web search company showed only a pre-recorded video of its AI chatbot Ernie in the first public release of China's answer to ChatGPT.
The Beijing-based tech company has claimed Ernie will remake its business and for weeks talked up plans to incorporate generative artificial intelligence into its search engine and other products.
But on Thursday, millions of people tuning in to the event were left with little idea of whether Baidu's chatbot could compete with ChatGPT.
[...]
"We can only explore by ourselves. Training ChatGPT took OpenAI more than a year, and it took them another year to tune GPT-4," said one Baidu employee. "It means we're two years behind."Baidu did not immediately respond to a request for comment.
Related:
The AI
Hype Bubble is the New Crypto Hype Bubble
DuckDuckGo's
New Wikipedia Summary Bot: "We Fully Expect It to Make
Mistakes"
LLM
ChatGPT Might Change the World, but Not in a Good Way
Alphabet
Stock Price Drops After Google Bard Launch Blunder
OpenAI
and Microsoft Announce Extended, Multi-Billion-Dollar
Partnership
Read more of this story at SoylentNews.
03:22
Confidential Pfizer Documents Reveal Pharmaceutical Giant Had Evidence Suggesting Increased Risk of Myocarditis Following COVID-19 Vaccinations in Early 2022 cryptogon.com
Via: Project Veritas: There is evidence that suggests patients who receive a COVID-19 vaccine are at an increased risk of myocarditis. Onset was typically within several days after mRNA COVID-19 vaccination (from Pfizer or Moderna), and cases have occurred more often after the second dose than the first dose. [PAGE 19] The []
03:01
Storing sensitive data using Podman secrets: Which method should you use? Linux.com
Podman supports two ways for storing sensitive data: using raw Podman secrets or creating Kubernetes secrets using Podman.
Read More at Enable Sysadmin
The post Storing sensitive data using Podman secrets: Which method should you use? appeared first on Linux.com.
03:00
Video Friday: Resilient Bugbots IEEE Spectrum

Video Friday is your weekly selection of awesome robotics
videos, collected by your friends at IEEE Spectrum
robotics. We also post a weekly calendar of upcoming robotics
events for the next few months. Please
send us your events for inclusion.
Robotics Summit & Expo: 1011 May 2023, BOSTON
ICRA 2023: 29 May2 June 2023, LONDON
RoboCup 2023: 410 July 2023, BORDEAUX, FRANCE
RSS 2023: 1014 July 2023, DAEGU, KOREA
IEEE RO-MAN 2023: 2831 August 2023, BUSAN, KOREA
CLAWAR 2023: 24 October 2023, FLORIANOPOLIS, BRAZIL
Humanoids 2023: 1214 December 2023, AUSTIN, TEXAS, USA
Enjoy todays videos!
Inspired by the hardiness of bumblebees, MIT researchers have developed repair techniques that enable a bug-sized aerial robot to sustain severe damage to the actuators, or artificial muscles, that power its wingsbut to still fly effectively.
[ MIT ]
This robot gripper is called DragonClaw, and do you really need to know anything else?
Alas, DragonClaw wins again!
[ AMTL ]
Heres a good argument for having legs on a robot:
...02:56
Minnesota Nuke Plant Admits To 400,000 Gallon Leak Of Radioactive Water cryptogon.com
Via: ZeroHedge: Minnesotans are wondering why state regulators waited months to inform the public that hundreds of thousands of gallons of radioactive water leaked from Xcel Energys Monticello nuclear power plant. Minnesota Department of Health released a statement Thursday about Xcels efforts to clean up 400,000 gallons of the water containing tritium that leaked from []
02:54
CDC Bought Phone Data to Monitor Americans Compliance With Lockdowns, Contracts Show cryptogon.com
Via: Epoch Times: The U.S. Centers for Disease Control and Prevention (CDC) purchased data from tracking companies to monitor compliance with lockdowns, according to contracts with the firms. The CDC paid one firm $420,000 and another $208,000. That bought access to location data from at least 55 million cellphone users. The contracts, approved under emergency []
02:49
France: Rioters Outside Macrons House After Forcing Through Retirement Age Increase Without Parliament Vote cryptogon.com
Via: Daily Mail: Rioters threatened the home of French president Emmanuel Macron after he bypassed parliament to raise the retirement age from 62 to 64. Thousands took to the streets across France last night to express their fury at the move, setting fires to property and fighting the police. The demonstrations in Paris, Lyon, Marseille []
02:45
ICC Judges Issue Arrest Warrant for Putin Over War Crimes in Ukraine cryptogon.com
Putin: Add it to the list. Via: Reuters: The International Criminal Court (ICC) issued an arrest warrant on Friday against Russian President Vladimir Putin, accusing him of being responsible for war crimes committed in Ukraine. Moscow has repeatedly denied accusations that its forces have committed atrocities during its one-year invasion of its neighbour. In its []
02:41
HinataBot, a new Go-Based DDoS botnet in the threat landscape Security Affairs
A new Golang-based DDoS botnet, tracked as HinataBot, targets routers and servers by exploiting known vulnerabilities.
Akamai researchers spotted a new DDoS Golang-based botnet, dubbed HinataBot, which has been observed exploiting known flaws to compromise routers and servers.
The experts reported that the HinataBot bot was seen being distributed since the beginning of 2023 and its operators are actively updating it.
The name Hinata comes after a character from the popular anime series, Naruto.
Akamais SIRT recently discovered the new bot within HTTP and SSH honeypots, it stood out due to its large size and the lack of specific identification around its newer hashes.
The sample captured by the experts abuses old vulnerabilities and weak credentials, the researchers reported that it attempts to exploit flaws in the miniigd SOAP service on Realtek SDK devices (CVE-2014-8361), Huawei HG532 routers (CVE-2017-17215), and exposed Hadoop YARN servers (CVE N/A).
HinataBot supports multiple methods of communication, including both dialing out and listening for incoming connections. The botnet can launch distributed denial-of-service (DDoS) flooding attacks that relies on protocols such as HTTP, UDP, TCP, and ICMP to send HTTP and UDP attacks.
Akamai said that by reverse engineering the bot and imitating the command and control (C2) server, was able to test the offensive capabilities of the botnet by running two attack methods (HTTP and UDP) in a 10-second period.

The http_flood generated 3.4 MB of packet capture data and pushed 20,430 HTTP requests. The request sizes ranged from 484 to 589 bytes per reque...
02:19
Free decryptor released for Conti-based ransomware following data leak Graham Cluley
Security researchers have released a new decryption tool which the Conti ransomware, helping them to recover their encrypted data for free. Read more in my article on the Tripwire State of Security blog.
02:09
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Ed Maste on Mar 17
All of tcsh's uses of TIOCSTI are in `#ifdef TIOCSTI` blocks so tcshshould still build and function with it removed (e.g., with the ioctl
renamed) I imagine.
01:54
Eight Graphs That Explain Software Engineering Salaries in 2023 IEEE Spectrum
Every year, online job search firms collect data about the salaries, skills, and overall job market for tech professionals, generally focusing on software engineers
The numbers from job search firms Dice and Hired have been released. These 2022 numbers have been eagerly anticipated, given the turmoil generated by a spate of tech layoffs in the latter part of the year, which Dice estimates at more than 140,000. The data they collect doesnt allow for apples-to-apples comparisons, but Ive read through both reports, pulled out data from past years to give the numbers some perspective when possible, and summarized it in eight charts. Dices numbers come from a survey administered to its registered job seekers and site visitors between 16 August 2022 and 17 October 2022, for a total of 7,098 completed surveys. Hireds analysis included data from 68,500 job candidates and 494,000 interview requests collected from the site between January 2021 through December 2022, supplemented by a survey of 1,300 software engineers.
Tech salaries jump, but dont keep up with inflation
According to Dices numbers, tech salaries grew 2.3 percent in 2022 compared with 2021, reflecting a steady upward trend since 2017 (with 2020 omitted due to the pandemic disruption). However, its clear that the 2022 news isnt so good when considering inflation. These numbers have been adjusted from those previously reported by IEEE Spectrum; Dice recently tightened its survey to focus on tech professionals in more tech-specific job functions.
Whats the best-paying job in tech?
If you want the highest pay, its a no-brainer: Get yourself into the C-suite. That is not, of course, a particularly useful takeaway from Dices data. Perhaps of more interest is that scrum masters are com...
01:53
Read "A First Course in Network Science", coauthored by our Filippo Menczer. Lifeboat News
Read "A First Course in Network Science", coauthored by our Filippo Menczer.
Networks are everywhere: networks of friends, transportation networks and the Web. Neurons in our brains and proteins within our bodies form networks that determine our intelligence and survival. This modern, accessible textbook introduces the basics of network science for a wide range of job sectors from management to marketing, from biology to engineering, and from neuroscience to the social sciences.01:48
Android phones can be hacked just by someone knowing your phone number Graham Cluley
Well, this isnt good. Google has issued a warning that some Android phones can be hacked remotely, without the intended victim having to click on anything.
01:36
Links 17/03/2023: Linux 6.2.7 and LibreSSL 3.7.1 Released Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
-
GNU/Linux
-
Desktop/Laptop
-
Liliputing System76 Meerkat mini Linux PC now available with up to Intel Core i7-1260P
While the design is similar for all models, models with newer processors tend to have slightly better specs. For example you get a Gigabit Ethernet port on Comet Lake systems, compared with 2.5 GbE Ethernet on Tiger Lake and Alder Lake models. The Alder Lake
-
-
01:30
Amazon Linux 2023 Is Running Well, Boosting EC2 Performance Over Amazon Linux 2 Phoronix
For those currently making use of Amazon Linux 2 (AL2) as the operating system for Elastic Compute Cloud (EC2) instances, the newly-released Amazon Linux 2023 (AL2023) is delivering some worthwhile speed-ups for maximizing your performance and value in their public cloud.
00:38
1xbet Bonus First Deposit Bonus 1xbet Bonus Account h+ Media
1xbet Bonus First Deposit Bonus 1xbet Bonus Account
However, as is with any bonus presents, there are phrases and circumstances hooked up to the 1xBet join provide. Sportsbooksto check out other betting websites and cool bonuses. Youve obtained no excuse to miss placing sports activities bets in your favourite bookmaker, even when your PC is at home. With the 1XBet app, you easily place bets on the go, straight from your smartphone.
This truth is especially essential for gamers, because the bookmaker offers a possibility to guess through the match and watch the event of events using on-line broadcasts. The degree of such packages is different, bettors like some of them, and others are significantly inferior to their counterparts. 1xBet app has acquired the greatest recognition updated.
The 1xBet promo code Bangladesh site offers fashionable and nice navigation, though some would possibly find the ergonomics a bit too heavy. But everything could be done quite rapidly 1xbet, and new users wont have bother getting acquainted with the positioning. If youre a newcomer, in case of registration, you will get a 1xBet bonus code, during your first deposit. This is a regular bonus of as much as 100 percent on a most quantity of 144$ . The store part is designed to retain 1xBet promo code for registration customers and allow them to redeem bonus points for free bets. The website precept is that every time prospects make bets, they accumulate bonus points.
Moreover, it could boast dozens of alternatives for bettors inside a certain sports activities betting or on line casino market. The bookmaker keeps on growing and bettering its service to obtain as many satisfied bettors as possible. They are also working onerous on making the standard greater striving for a similar objective to keep being one of the top betting platforms by all means. Consequently, 1xBet bd presents an web site that is user-friendly and accommodates the necessary information only. An choice, making it attainable to ship funds to a good friend, is one more service, which makes 1xBet bookmaker stand out from other companies out there.
We could possibly be grateful ought to you would give us more particulars about your experience. You can acquire 1xWin 100 laptop freed from cost and to enjoy the limitless bets immediately on your desktop. Otherwise, your bonus prizes could be taken away out of your account steadiness. 1xBet Sportsbook is a web-based bookmaker platform that accepts Canadian punters. The web site has been online since 2011 and has gained a robust following among punters seeking a dependable, easy-to-use sports actions gambling decision. The web site states that theyve over four hundred,000 bettors that use their companies, which is a large number of prospects by any requirements.
Just lately, Algeria played with Senegal, the place he acquir...
00:31
Top 5 Insider Threats to Look Out For in 2023 Security Affairs
Unquestionably, insider threats is one of the most neglected aspects of cybersecurity and some companies fail to recognize associated dangers.
Cyberattacks are growing more complex as technology advances. Many businesses concentrate their cybersecurity efforts solely on external attacks, which leaves more openings for internal risks. Some companies fail to recognise the danger of losing confidential information owing to employee negligence or malice. Unquestionably, insider threats is one of the most neglected aspects of cybersecurity. According to statistics on insider threats, these threats may originate from employees, business contractors, or other reliable partners with simple access to your network. However, insider threat reports and recent developments have shown a sharp rise in the frequency of insider attacks. Because of these, cybersecurity professionals are now paying more attention to the detrimental effects of insider attacks.
In general, security experts need more confidence in their ability to identify and thwart insider threats successfully. 74% of respondents in an insider attack said their company was moderately to extremely vulnerable. 74% of respondentsa 6% increase from 2021also claim that insider threat assaults have become more regular. In 2022, 60% of respondents said they had an insider attack, while 8% said more than 20. Insider assaults are more challenging to identify and thwart than external attacks, according to 48% of respondents. It can be challenging for defences to distinguish between insider threats and regular user activity since insider threats employ genuine accounts, passwords, and IT technologies. Overall, insider threats are becoming a more significant threat. These findings imply that security teams should prepare for them in 2023.
Organisations must be able to address the risks from malicious insiders who intentionally steal sensitive data for personal reasons and users who can accidentally expose information due to negligence or simple mistakes.
Here are the top 5 threats security teams should look out for in 2023:
Employee Negligence
Employee carelessness or ignorance may result in unintentional data leaks, improper handling of sensitive information, or a failure to adhere to security policies and procedures. Negligence is to blame for more than two of every three insider incidents. Workers could not be cognizant of the possible hazards they bring to the company or might not prioritise security measures. They act carelessly, repeating passwords for personal and professional accounts or leaving flash drives wit...
00:00
What Is Teslas Mystery Magnet? IEEE Spectrum

Teslas investor day on 1 March began with a rambling, detailed discourse on energy and the environment before transitioning into a series of mostly predictable announcements and boasts. And then, out of nowhere, came an absolute bombshell: We have designed our next drive unit, which uses a permanent-magnet motor, to not use any rare-earth elements at all, declared Colin Campbell, Teslas director of power-train engineering.
It was a stunning disclosure that left most experts in permanent magnetism wary and perplexed. Alexander Gabay, a researcher at the University of Delaware, states flatly: I am skeptical that any non-rare-earth permanent magnet could be used in a synchronous traction motor in the near future. And at Uppsala University, in Sweden, Alena Vishina, a physicist, elaborates, Im not sure its possible to use only rare-earth-free materials to make a powerful and efficient motor.
The problem here is physics, which not even Tesla can alter.
And at a recent magnetics conference Ping Liu, a professor at the University of Texas, in Arlington, asked other researchers what they thought of Teslas announcement. No one fully understands this, he reports. (Tesla did not respond to an e-mail asking for elaboration of Campbells comment.)
Teslas technical prowess should never be underestimated. But on the other hand, the companyand in particular, its CEOhas a history of making sporadic sensational claims that dont pan out (were still waiting for that US $35,000 Model 3, for example).
The problem here is physics, which not even Tesla can alter. Permanent magnetism occurs in certain crystalline materials when the spins of electrons of some of the atoms in the crystal are forced to point in the same direction. The more of these aligned spins, the stronger the magnetism. For this, the ideal atoms are ones that have unpaired electrons swarming around the nucleus in what are known as...