| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Tuesday, 28 March
02:30
A Comprehensive Look at FDM Supports Hackaday

When we first started 3D printing, we used ABS and early slicers. Using supports was undesirable because the support structures were not good, and ABS sticks to itself like crazy. Thankfully todays slicers are much better, and often we can use supports that easily detach. [Teaching Tech] shows how modern slicers create supports and how to make it even better than using the default settings.
The video covers many popular slicers and their derivatives. If youve done a lot with supports, you might not find too much of this information surprising, but if you havent printed with supports lately or tried things like tree supports, you might find a few things that will up your 3D printing game.
One thing we really like is that the video does show different slicers, so regardless of what slicer you like to use, youll probably find exactly what different settings are called. Of course, because slicers let you examine what they produce layer-by-layer, you can do like the video and examine the results without printing. [Michael] does do some prints with various parameters, though, and you can see how hard or easy the support removal is depending on some settings. The other option is to add support to your designs, as needed manually, or even better dont design things that need support.
This video reminded us of a recent technique we covered that...
02:23
Brains Might Sync As People Interact and That Could Upend Consciousness Research Lifeboat News: The Blog
When we cooperate on certain tasks, our brainwaves might synchronize. This finding could upend the current understanding of consciousness.
02:23
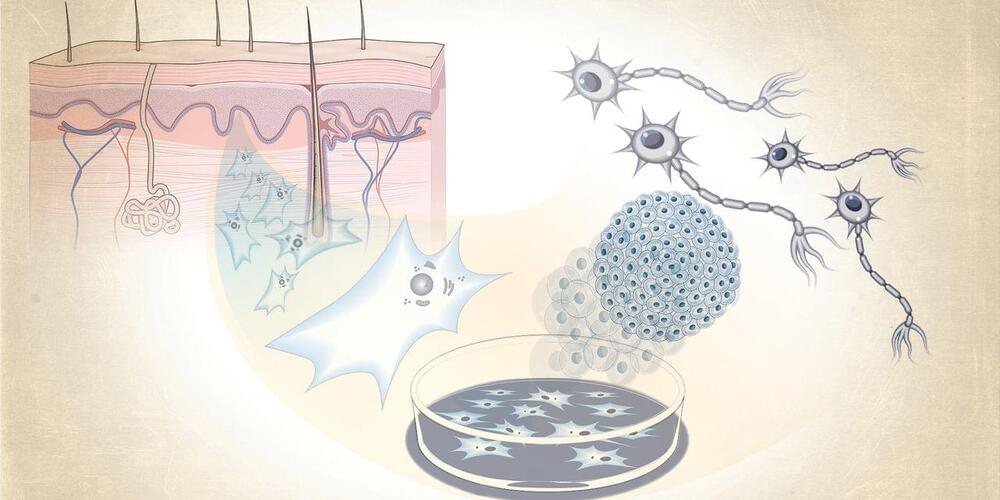
How Were Reverse Engineering the Human Brain in the Lab | Sergiu P. Pasca | TED Lifeboat News: The Blog

Neuroscientist Sergiu P. Pasca has made it his lifes work to understand how the human brain builds itself and what makes it susceptible to disease. In a mind-blowing talk laden with breakthrough science, he shows how his team figured out how to grow organoids and what they call brain assembloids self-organizing clumps of neural tissue derived from stem cells that have shown the ability to form circuits and explains how these miniature parts of the nervous system are bringing us closer to demystifying the brain.
If you love watching TED Talks like this one, become a TED Member to support our mission of spreading ideas: http://ted.com/membership.
Follow TED!
Twitter: http://twitter.com/TEDTalks.
Instagram: https://www.instagram.com/ted.
Facebook: http://facebook.com/TED
LinkedIn: https://www.linkedin.com/company/ted-conferences.
TikTok: https://www.tiktok.com/@tedtoks.
The TED Talks channel features talks, performances and original series from the worlds leading thinkers and doers. Subscribe to our channel for videos on Technology, Entertainment and Design plus science, business, global issues, the arts and more. Visit http://TED.com to get our entire library of TED Talks, transcripts, translations, personalized talk recommendations and more.
Watch more: https://go.ted.com/sergiuppasca.
02:22
Android app from China executed 0-day exploit on millions of devices Lifeboat News: The Blog
Can you imagine if we had computer/brain interfaces what would happen? Well need brain firewalls and antivirus.
Android apps digitally signed by Chinas third-biggest e-commerce company exploited a zero-day vulnerability that allowed them to surreptitiously take control of millions of end-user devices to steal personal data and install malicious apps, researchers from security firm Lookout have confirmed.
The malicious versions of the Pinduoduo app were available in third-party markets, which users in China and elsewhere rely on because the official Google Play market is off-limits or not easy to access. No malicious versions were found in Play or Apples App Store. Last Monday, TechCrunch reported that Pinduoduo was pulled from Play after elsewhere. TechCrunch reported the malicious apps available in third-party markets exploited several zero-days, vulnerabilities that are known or exploited before a vendor has a patch available.
Sophisticated attack
A preliminary analysis by Lookout found that at least two off-Play versions of Pinduoduo for Android exploited CVE-202320963, the tracking number for an Android vulnerability Google patched in updates that became available to end users two weeks ago. This privilege-escalation flaw, which was exploited prior to Googles disclosure, allowed the app to perform operations with elevated privileges. The app used these privileges to download code from a developer-designated site and run it within a privileged environment.
02:18
20-Year-Old BreachForums Founder Faces Up to 5 Years in Prison The Hacker News
Conor Brian Fitzpatrick, the 20-year-old founder and the administrator of the now-defunct BreachForums has been formally charged in the U.S. with conspiracy to commit access device fraud. If proven guilty, Fitzpatrick, who went by the online moniker "pompompurin," faces a maximum penalty of up to five years in prison. He was arrested on March 15, 2023. "Cybercrime victimizes and steals financial
01:39
AmpereOne Sees Last Minute Compiler Tuning Ahead Of GCC 13 Phoronix
Going back to late 2021 was the initial GCC compiler patch for "Ampere-1" for that next-gen AArch64 server processor while last year this successor to Ampere Altra (Max) was formally announced under the AmpereOne brand. That initial compiler support appeared in GCC 12 while ahead of the GCC 13 release in the coming weeks has been some last minute tuning for the AmpereOne cost table...
01:10
[$] The curious case of O_DIRECTORY|O_CREAT LWN.net
The open() system call offers a number of flags that modify its behavior; not all combinations of those flags make sense in a single call. It turns out, though, that the kernel has responded in a surprising way to the combination of O_CREAT and O_DIRECTORY for a long time. After a 2020 change made that response even more surprising, it seems likely that this behavior will soon be fixed, resulting in a rare user-visible semantic change to a core system call.
01:08
Version 5.0 of the GnuCash accounting tool is out. Changes include a number of investment-tracking improvements, better completion in the register window, a reworked report-generation system, and more.
01:06
Security updates for Monday LWN.net
Security updates have been issued by Debian (libreoffice and xen), Fedora (chromium, curl, and xen), Red Hat (kernel, kernel-rt, kpatch-patch, and thunderbird), Scientific Linux (thunderbird), Slackware (tar), SUSE (apache2, ceph, curl, dpdk, helm, libgit2, and php7), and Ubuntu (firefox and thunderbird).
01:00
Europes Proposed Right-To-Repair Law: a Game Changer, or Business As Usual? Hackaday

Recently, the European Commission (EC) adopted a new proposal intended to enable and promote the repair of a range of consumer goods, including household devices like vacuum cleaners and washing machines, as well as electronic devices such as smartphones and televisions. Depending on how the European Parliament and Council vote in the next steps, this proposal may shape many details of how devices we regularly interact with work, and how they can be repaired when they no longer do.
As we have seen recently with the Digital Fair Repair Act in New York, which was signed into law last year, the devil is as always in the details. In the case of the New York bill, the original intent of enabling low-level repairs on defective devices got hamstrung by added exceptions and loopholes that essentially meant that entire industries and types of repairs were excluded. Another example of right to repair being essentially gamed involves Apples much-maligned self repair program, that is both limited...
00:41
Updates from the MaaS: new threats delivered through NullMixer Security Affairs
A technical analysis of NullMixer malware operation revealed Italy and France are the favorite European countries from the attackers perspective.
Executive Summary
- Our insights into a recent NullMixer malware operation revealed Italy and France are the favorite European countries from the opportunistic attackers perspective.
- In thirty days, the operation we monitored was capable to establish initial access to over 8 thousand endpoints and steal sensitive data that are now reaching the underground black markets.
- Most of the victims mount Windows 10 Professional and Enterprise operating systems, including several Datacenter versions of Windows Server. Some of them are also Windows Embedded, indicating the penetration of such malware operation even into IoT environments.
- The NullMixer package is including new polymorphic loaders by third parties MaaS and PPI service providers in the underground markets, and also pieces of controversial, potentially North-Korean linked PseudoManuscript code.
Introduction
During March 2023, we obtained information and data regarding an ongoing malware operation hitting more than 8.000 targets within a few weeks, with a particular emphasis on North American, Italian, and French targets.
Such was related to a worldwide malware operation known as NullMixer, a controversial and widespread malware delivery maneuver based on SEO poisoning and social engineering technique to lure tech-savvy users, including IT personnel.
The insight from this attack wave revealed the presence of a controversial piece of code in the delivered payloads, among additional loaders related to new MaaS and PPI operators.
Technical Analysis
There are two main key areas we technically analyzed during this investigation: first of all the presence of two unknown loaders entering the MaaS and PPI businesses (CrashedLoader and Koi), along with the presence of a controversial, potentially North-Korean linked piece of malware, and secondly, we analyzed data about current successful infection rates on targeted hosts.
The Originating Malvertising Campaign
According to CTI investigation on the adversary infrastructure, we were able to identify an ongoing campaign luring system administrators to install the malicious code into their machines. In particular, the identified attack wave was designed to trick users to install backdoored, cracked versions of notorious PC maintenance software such as EaseUS Partition Master and Driver Easy Pro, two well-known tools within the IT community.
Filen...
00:22
Surprise Computer Science Proof Stuns Mathematicians Lifeboat News: The Blog
For decades, mathematicians have been inching forward on a problem about which sets contain evenly spaced patterns of three numbers. Last month, two computer scientists blew past all of those results.
00:10
Distribution Release: Porteus Kiosk 5.5.0 DistroWatch.com: News
Tomasz Jokiel has announced the release of Porteus Kiosk 5.5.0, designed for in web kiosks: "I'm pleased to announce that Porteus Kiosk 5.5.0 is now available for download. Major software upgrades in this release include: Linux kernel 6.1.20, Google....
00:04
Performance Evaluation of C, Julia, Kokkos and Python/Numba in Exascale High Performance Computing SoylentNews
High-level dynamic languages such as Python, Julia, and R have been at the forefront of artificial intelligence/machine learning (AI/ML), data analysis, and interactive computing workflows in the last decade. Traditional high-performance computing (HPC) frameworks that power the underlying low-level computations for performance and scalability are written in compiled languages: C, C++, and Fortran.
[...] We analyze single node scalability on two systems hosted at the Oak Ridge Leadership Computing Facility (OLCF)1Wombat, which uses Arm Ampere Neoverse CPUs and 2 NVIDIA A100 GPUs, and Crusher, which is equipped with AMD EPYC 7A53 CPUs and 8 MI250X GPUs and serves as a test bed for Frontier, the first exascale system on the TOP500 list.
[...] We run hand-rolled general matrix multiplication (GEMM) code for dense matrices using Julia, Python/Numba and Kokkos implementations and compare the performance with C for multithreaded CPU (OpenMP) and single GPU (CUDA/HIP) systems. GEMM is an important kernel in the Basic Linear Algebra Subprograms (BLAS) used across several deep learning AI frameworks, for which modern GPU architectures have been heavily optimized via tensor cores.
[...] For CPUs, Julia performance was comparable to C/OpenMP combined with LLVM-based ArmClang and AMDClang vendor compilers. For the AMD GPUs, Julia AMDGPU.jl performance was comparable to HIP. Nevertheless, there is still a performance gap on NVIDIA A100 GPUs for single-precision floating point cases.
[...] We observe that Python/Numba implementations still lack the support needed to reach comparable CPU and GPU performance on these systems, and AMD GPU support is deprecated.
Pre-print article:
William F. Godoy and Pedro Valero-Lara and T. Elise Dettling and
Christian Trefftz and Ian Jorquera and Thomas Sheehy and Ross G.
Miller and Marc Gonzalez-Tallada and Jeffrey S. Vetter and Valentin
Churavy, Evaluating performance and portability of high-level
programming models: Julia, Python/Numba, and Kokkos on exascale
nodes, Accepted at the 28th HIPS workshop, held in conjunction
with IPDPS 2023, 2023, 2303.06195, https://doi.org/10.48550/arXiv.2303.06195
...
00:01
Can zero trust be saved? Graham Cluley
Graham Cluley Security News is sponsored this week by the folks at Kolide. Thanks to the great team there for their support! Right now, Zero Trust is in serious danger of becoming an empty buzzword. The problem isnt just that marketers have slapped the Zero Trust label on everything short of breakfast cerealits that for Continue reading "Can zero trust be saved?"
Monday, 27 March
23:59
Linux 6.4 Device Mapper To See Improved Concurrent I/O Performance Phoronix
Thanks to forthcoming work out of Red Hat, the Linux 6.4 Device Mapper (DM) code is expected to see some optimization work that can significantly benefit concurrent I/O performance... In one case at least acquiring buffers now about 25 times faster...
23:24
Latitude Financial Data Breach: 14 Million Customers Affected HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
The CEO of Latitude Financial, Ahmed Fahour, has expressed disappointment in the incident and apologized unreservedly to customers.
This is a post from HackRead.com Read the original post: Latitude Financial Data Breach: 14 Million Customers Affected
23:09
Technical analysis of China-linked Earth Preta APTs infection chain Security Affairs
China-linked Earth Preta cyberespionage group has been observed adopting new techniques to bypass security solutions.
Trend Micro researchers reported that the China-linked Earth Preta group (aka Mustang Panda) is actively changing its tools, tactics, and procedures (TTPs) to bypass security solutions.
Earth Preta, also known as RedDelta or Bronze President, has been active since at least 2012, it targeted American and European entities such as government organizations, think tanks, NGOs, and even Catholic organizations at the Vatican. Past campaigns were focused on Asian countries, including Taiwan, Hong Kong, Mongolia, Tibet, and Myanmar.
In recent campaigns, threat actors used European Union reports on the conflict in Ukraine and Ukrainian government reports as lures. Upon opening the reports, the infection process starts leading to the deployment of malware on the victims system.
In a recent campaign analyzed by Trend Micro, the threat actors used spear-phishing emails and Google Drive links as attack vectors.
A deep investigation into the campaign revealed several undisclosed malware and interesting data exfiltration tools used by the group.
The researchers categorized the infection chain into six stages: arrival vectors, discovery, privilege escalation, lateral movement, command and control (C&C) and exfiltration, respectively.

The attackers used DLL sideloading, shortcut links, and fake file extensions in the first part of the a...
22:59
BEC scammers are after physical goods, the FBI warns Help Net Security
BEC attacks are usually aimed at stealing money or valuable information, but the FBI warns that BEC scammers are increasingly trying to get their hands on physical goods such as construction materials, agricultural supplies, computer technology hardware, and solar energy products. Supplies in the crosshairs Such schemes are not without a precendent: during the height of the Covid-19 pandemic, scammers went after PPE and other medical equipment. In 2022, the FBI also warned of a More
The post BEC scammers are after physical goods, the FBI warns appeared first on Help Net Security.
22:41
A bug revealed ChatGPT users chat history, personal and billing data Help Net Security
A vulnerability in the redis-py open-source library was at the root of last weeks ChatGPT data leak, OpenAI has confirmed. Not only were some ChatGPT users able to see what other users have been using the AI chatbot for, but limited personal and billing information ended up getting revealed, as well. How did the ChatGPT data leak happen? ChatGPT suffered an outage on March 20 and then problems with making conversation history accessible to users. More
The post A bug revealed ChatGPT users chat history, personal and billing data appeared first on Help Net Security.
22:24
Interaction of the high frequency waves in the vicinity of the ionospheric window Lifeboat News: The Blog
It is well-known that an ordinary high frequency electromagnetic (EM) wave radiated into the ionosphere at the Spitze angle is totally transformed at the reflection height (z0) into the Z-mode. This mode, in turn, penetrates deeper into the ionosphere and it is reflected at some height (zref) usually significantly higher than the O-mode reflection height. This result is reconsidered in the present paper. It is argued that the wave appearing as a continuation of the propagating upward quasi-electrostatic wave changes the direction of motion along the vertical axis slightly above z0 and takes the form of the down-going wave. This wave is excited in the vicinity of the height z0 due to the phase resonance with the up-going O-mode wave which transforms into the Z-mode propagating upward. Thus, the ionospheric window is not totally transparent for the O-mode radiated at the Spitze angle. The up-going O-mode wave loses some part of its energy due to excitation of the down-going EM wave. This wave, in turn, propagates to the ground as the O-mode wave.
22:23
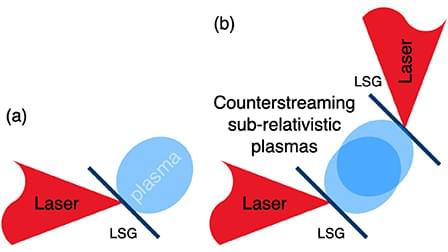
Nonlinear evolution of the Weibel instability with relativistic laser pulses Lifeboat News: The Blog
The Weibel instability is investigated using relativistic intense short laser pulses. A relativistic short laser pulse can generate a sub-relativistic high-density collisionless plasma. By irradiating double parallel planar targets with two relativistic laser pulses, sub-relativistic collisionless counterstreaming plasmas are created. Since the growth rate of the Weibel instability is proportional to the plasma density and velocity, the spatial and temporal scales of the Weibel instability can be much smaller than that from nanosecond large laser facilities. Recent theoretical and numerical studies have revealed that astrophysical collisionless shocks in sub-relativistic regimes in the absence and presence of an ambient magnetic field play essential roles in cosmic ray acceleration. With experimental verification in mind, we discuss the possible experimental models on the Weibel instability with intense short laser pulses. In order to show the experimental feasibility, we perform 2D particle-in-cell simulations in the absence of an external magnetic field as the first step and discuss the optimum conditions to realize the nonlinear evolutions of the Weibel instability in laboratories.
22:23
22:21
Links 27/03/2023: Twitter Source Code Published (But Not Intentionally) Techrights
![]()
Contents
-
GNU/Linux
-
9to5Linux 9to5Linux Weekly Roundup: March 26th, 2023
This week we got a lot of cool stuff, starting with the release of the GNOME 44 desktop environment and continuing with a new Linux laptop from Kubuntu Focus, a new major NVIDIA graphics driver release, and new security updates for Ubuntu users.
Several new distro releases were also out this week including Tails 5.11, Trisquel GNU/Linux 11.0 LTS, and OpenMandriva Lx 23.03. Check out the hottest news of this week and access all the distro and package downloads in 9to5Linuxs Linux weekly roundup for March 26th, 2023, below.
-
Audiocasts/Shows
-
...
-
-
22:02
XWayland Lands Fix For At Least One Game Hanging It & Causing 100% CPU Usage Phoronix
While XWayland is in fairly good shape for enjoying both native and emulated games relying on X11 to run atop Wayland compositors for Linux gaming, occasionally different peculiar issues are uncovered. The most recent issue analyzed and addressed in XWayland Git is over the game Resident Evil 6 causing XWayland to hang and consume 100% of the CPU resources on launching that title...
22:00
MS-DOS Client Brings ChatGPT to the IBM PC Hackaday

AI-powered chatbots are clearly the future of computing, and its only a matter of time before youll see them appear on every internet-connected gadget. If you thought you were safe from this by sticking to an ancient MS-DOS PC though, think again: [Yeo Kheng Meng] has recently written a ChatGPT client that runs on DOS.
[Yeo Kheng Meng] didnt cheat by simply running MS-DOS on a modern PC, either: he tested the client on a real 1984 vintage IBM 5155 Portable PC. This semi-portable PC/XT model sports a 4.77 MHz 8088 CPU, 640 kB of RAM and a CGA video card with a built-in monochrome monitor. An NE2000 ISA network card, running in 8-bit mode, enables the Portable to connect to the internet.
Running the client couldnt be simpler: just run
doschgpt.exe and type in your question. [Yeo Kheng
Meng] developed this program using the Open Watcom C/C++ compiler,
which was the compiler of choice for most DOS game developers back
in the day. Networking support was provided by an era-appropriate
packet driver together with MTCP, a TCP/IP stac...
21:56
Where SSO Falls Short in Protecting SaaS The Hacker News
Single sign-on (SSO) is an authentication method that allows users to authenticate their identity for multiple applications with just one set of credentials. From a security standpoint, SSO is the gold standard. It ensures access without forcing users to remember multiple passwords and can be further secured with MFA. Furthermore, an estimated 61% of attacks stem from stolen credentials. By
21:44
OBS Studio Lands AV1 & HEVC RTMP Streaming Support Phoronix
In time for OBS Studio 29.1, the Veovera Software Organization non-profit has contributed support for AV1 and HEVC streaming via RTMP so that gamers and other creators can stream their content to the YouTube RTMP server using these newer video formats...
21:38
New MacStealer macOS Malware Steals iCloud Keychain Data and Passwords The Hacker News
A new information-stealing malware has set its sights on Apple's macOS operating system to siphon sensitive information from compromised devices. Dubbed MacStealer, it's the latest example of a threat that uses Telegram as a command-and-control (C2) platform to exfiltrate data. It primarily affects devices running macOS versions Catalina and later running on M1 and M2 CPUs. "MacStealer has the
21:30
FreeBSD 13.2-RC5 Released With One Last Fix Phoronix
FreeBSD 13.2-RC4 was released this weekend while it's already been replaced by FreeBSD 13.2-RC5 to land one more fix prior to making the final release preparations on this next stable update to this BSD operating system...
21:27
Barred From US Tech, Huawei Builds EDA Platform of its Own SoylentNews
Beijing's Made in China drive fueled by Washington's export crackdowns:
Huawei has reportedly completed work on electronic design automation (EDA) tools for laying out and making chips down to 14nm process nodes.
Chinese media said the platform is one of 78 being developed by the telecoms equipment giant to replace American and European chip design toolkits that have become subject to export controls by the US and others.
EDA is an umbrella term for software, hardware, and services essential to the planning, design, and production of chips. While integrated circuits were largely designed by hand decades ago, chips became so complex that computer-aided design and automation was unavoidable, generally speaking.
Huawei's EDA platform was reportedly revealed by rotating Chairman Xu Zhijun during a meeting in February, and later confirmed by media in China. The Register reached out to Huawei's PR team for comment; we'll let you know if we hear anything back.
Today, the EDA market is largely controlled by three companies: California-based Synopsys and Cadence, as well as Germany's Siemens. According to the industry watchers at TrendForce, these three companies account for roughly 75 percent of the EDA market. And this poses a problem for Chinese chipmakers and foundries, which have steadily found themselves cut off from these tools.
Synopsys and Cadence's EDA tech is already subject to several of these export controls, which were stiffened by the US Commerce Department last summer to include state-of-the-art gate-all-around (GAA) transistors.
Read more of this story at SoylentNews.
21:03
Oumuamua: Avi Loebs Response to the Molecular Hydrogen Theory Centauri Dreams Imagining and Planning Interstellar Exploration
The enigmatic Oumuamua continues to stir controversy. Last week we looked at a new paper from Jennifer Bergner (UC-Berkeley) and Darryl Seligman (Cornell University), discussing a mechanism for the interstellar objects unusual non-gravitational acceleration. The researchers explored the possibility that ice impacted by high-energy particles like cosmic rays would dissociate water in a comet to create molecular hydrogen within the ice. Was the warming of this hydrogen, all but undetectable according to the authors, the cause of outgassing and the anomalous acceleration?

Image: This very deep combined image shows the interstellar object Oumuamua at the center of the image. It is surrounded by the trails of faint stars that are smeared as the telescopes tracked the moving comet. Credit: ESO/K. Meech et al.
Answering the question in a paper just submitted to the arXiv site is Harvards Avi Loeb, working with Thiem Hoang (Korea University of Science and Technology), who home in on Bergner and Seligmans finding that the surface temperature of Oumuamua can exceed 140 K at perihelion, enough to produce this evaporation. Loeb and Hoang argue that this calculation ignores the effect of evaporative cooling of the molecular hydrogen. The authors proceed to take such cooling into account and find that the surface temperature of H2 water ice is lower than that calculated by Bergner and Seligman by a factor of 9. This is turn reduces the projected outgassing.
From the paper:
...we found that the evaporative cooling is much more efficient than radiative cooling at temperatures above 20 K (see Figure 1, left panel). By taking into account the evaporative cooling by H2 evaporation, our results (see Figure 1, right panel) show that the surface temperatures of H2-water ice are lower by a factor of 9 than the temperature obtained by Bergner & Seligman (2023) (see their figure 3). Therefore, the thermal speed of outgassing H2 is decreased by a factor of 3.
20:48
Microsoft Issues Patch for aCropalypse Privacy Flaw in Windows Screenshot Tools The Hacker News
Microsoft has released an out-of-band update to address a privacy-defeating flaw in its screenshot editing tool for Windows 10 and Windows 11. The issue, dubbed aCropalypse, could enable malicious actors to recover edited portions of screenshots, potentially revealing sensitive information that may have been cropped out. Tracked as CVE-2023-28303, the vulnerability is rated 3.3 on the CVSS
20:12
CVE-2023-27296: Apache InLong: JDBC Deserialization Vulnerability in InLong Open Source Security
Posted by Charles Zhang on Mar 27
Severity: importantDescription:
Deserialization of Untrusted Data vulnerability in Apache Software Foundation Apache InLong.
It could be triggered by authenticated users of InLong, you could refer to [1] to know more about this vulnerability.
This issue affects Apache InLong: from 1.1.0 through 1.5.0. Users are advised to upgrade to Apache InLong's latest
[1] ...
19:26
Twitter Hunts Down Github User Who Leaked Companys Source Code TorrentFreak
 On February 21, 2023, Twitter chief Elon Musk published a
tweet suggesting that Twitters algorithm would be made open
source before the end of that month.
On February 21, 2023, Twitter chief Elon Musk published a
tweet suggesting that Twitters algorithm would be made open
source before the end of that month.
Before he took ownership of Twitter, Musk said that having the code out in the open would be a smart move, but the end of February came and went, without any code appearing in public.
On March 17, Musk raised the topic once again. Twitter will open source all code used to recommend tweets on March 31st, he tweeted. With the clock ticking on that event, someone with apparently similar plans but a more urgent publishing schedule, has taken Twitter by surprise.
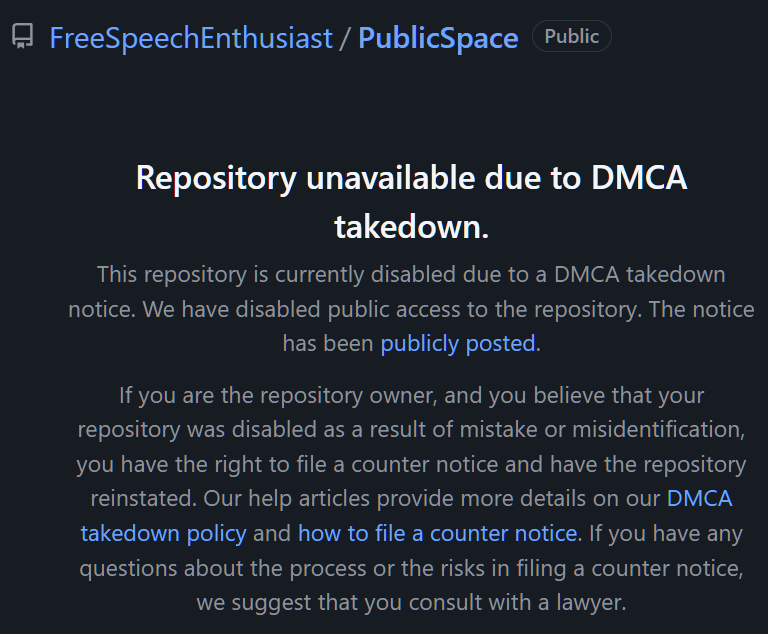
FreeSpeechEnthusiast Presents: PublicSpace
On March 24, Twitter sent a DMCA takedown notice to GitHub targeting a repo named PublicSpace. The repo was created by a GitHub user called FreeSpeechEnthusiast, but with no description, nothing stood out as particularly interesting or out of the ordinary.
Logs obtained by TorrentFreak suggest that the allegedly infringing content appeared on the PublicSpace repo early Friday morning, around 02:25. When GitHub received the initial DMCA notice isnt clear, but some interaction between Twitter and GitHub appears to have taken place before 10:15.
At 17:12 Friday afternoon, GitHub removed the repo and the code. Just one minute later, GitHub advised Twitter that the content was gone. That was a pretty swift removal but it appears Twitter was in a real hurry.
Proprietary Source Code For Twitters Platform
While the repo itself appeared without fanfare, Twitters DMCA notice is clear on why it should be taken down.
In response to GitHubs request to identify the infringed content, Twitter revealed that it was Proprietary source code for Twitters platform and internal tools.
19:00
Bus Stop Bloom Filter Hackaday

Imagine youre sitting on a nice bench, the sun shines warmly, and a bus pulls up. Youre headed to Stendal from Osnabrck, how can you tell if you should get on that bus? [Julian Vanecek] is trying to turn that from an O(n) problem to an O(1) one with a bloom filter right at the bus stop.
In [Julians] sample code, each stop is a 3-bit number that can be encoded into a 192-bit array. Your ticket is just that 3-bit number encoded, so you can look at the graphic on the side of the incoming bus, match it against your ticket, and hop on. Gone are the days of waiting for the little LED screen to cycle through all the stops, waiting for yours to come up. Your ticket should have just a few boxes filled in so it is relatively quick to search against the buss graphic.
Of course, there is a potential for a false positive rate. [Julian] points out that this can be tuned to prevent errors and has achieved a < 0.5% false positive rate using the Deutsche Bahn bus system. The code is written in Python and available on GitHub. Perhaps buses could have a large flip-dop display on the si...
18:39
Blue Origin Pins Last Summer's NS-23 Rocket Failure on a Faulty Engine Nozzle SoylentNews
The uncrewed capsule will fly again:
Blue Origin now has an explanation for the booster failure that cut a New Shepard flight short last September. Jeff Bezos' company has determined that a "thermo-structural failure" in the NS-23 rocket's engine nozzle was to blame. Operational temperatures for the nozzle climbed higher than expected following cooling system design changes, creating fatigue that misaligned the thrust and activated the crew capsule's escape system.
Engineers are already taking "corrective actions" that include redesigning the combustion chamber and operating conditions. Blue Origin has also tweaked the nozzle design to improve its structural integrity. The capsule wasn't damaged and will fly again, Blue Origin says.
The company says it hopes to resume flights "soon," but hasn't provided an exact date. It intends to restart operations by re-flying the research payload from the aborted mission. The Federal Aviation Administration has to accept the incident findings before Blue Origin can move forward.
There's plenty of pressure on Blue Origin to address the issues. The company recently obtained a NASA contract to fly a science mission to Mars using its yet-to-launch New Glenn rocket, and has been pushing for a lunar lander agreement. The sooner Blue Origin can prove that its rocketry is trustworthy, the sooner it can secure customers that include governments and space tourists.
Read more of this story at SoylentNews.
18:22
This New A.I Will CHANGE VFX Forever! Lifeboat News: The Blog

This AI tool automatically animates, lights, and composes CG characters into a live-action scene. No complicated 3D software, no expensive production hardwareall you need is a camera.
Wonder Dynamics: https://wonderdynamics.com.
Blender Addons: https://bit.ly/3jbu8s7
Join Weekly Newsletter: https://bit.ly/3lpfvSm.
Patreon: https://www.patreon.com/asknk.
Discord: https://discord.gg/G2kmTjUFGm.
Assets & Resources
Blender Addons: https://bit.ly/3jbu8s7
FlippedNormals Deals: https://flippednormals.com/ref/anselemnkoro/
FiberShop Realtime Hair Tool: https://tinyurl.com/2hd2t5v.
GET Character Creator 4 https://bit.ly/3b16Wcw.
Humble Bundles: https://www.humblebundle.com/membership?refc=F0hxTa.
Get Humble Bundle Deals: https://www.humblebundle.com/?partner=asknk.
GET Axyz Anima: https://bit.ly/2GyXz73
Learn More with Domestica: http://bit.ly/3EQanB5
GET ICLONE 8 https://bit.ly/38QDfbb.
Unity3D Asset Bundles: https://bit.ly/384jRuy.
Cube Brush Deals:
https://cubebrush.co/marketplace?on_sale=true&ref=anselemnkoro.
Motion VFX: https://motionvfx.sjv.io/5b6q03
Action VFX Elements: https://www.actionvfx.com/?ref=anselemnkoro.
WonderShare Tools: http://bit.ly/3Os3Rnp.
Sketchfab: https://bit.ly/331Y8hq.
Blender Premium Tutorials
Blender Tutorials #1: https://bit.ly/3nbfTEu.
Blender Tutorials #2: https://tinyurl.com/yeyrkreh.
Learn HardSurface In Blender...
18:07
IRC Proceedings: Sunday, March 26, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-260323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-260323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-260323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-260323.gmi
Over HTTP:
|
... |
18:05
Malicious Python Package uses Unicode support to evade detection Security Affairs
Researchers discovered a malicious package on PyPI that uses Unicode to evade detection while stealing sensitive data.
Supply chain security firm Phylum discovered a malicious Python package on the Python Package Index (PyPI) repository that uses Unicode to evade detection and deliver information-stealing malware.
The package, named onyxproxy, was uploaded to the PyPI repository on March 15, 2023. The analysis of the package revealed that it supports data harvesting capabilities.
Phylums automated platform recently detected the onyxproxy package on PyPI, a malicious package that harvests and exfiltrates credentials and other sensitive data. In many ways, this package typifies other token stealers that we have found prevalent in PyPI. reads the analysis published by Phylum.However, one feature of this particular package caught our eye: an obfuscation technique that was foreseen in 2007 during a discussion about Pythons support for Unicode, documented in PEP-3131
While inspecting the code the experts multiple strange, non-monospaced, sans-serif font with mixed bold and italics. The attackers used Unicode variants of characters that appear identical to a human inspection (homoglyphs) (i.e., self vs. ). The attackers used this trick to evade detection, but when the Python interpreter parsed the code the malicious code was executed.
An obvious and immediate benefit of this strange scheme is readability. We can still easily reason about this code, because our eyes and brains can still read the words, despite the intermixed fonts. Moreover, these visible...
18:00
German monks create world's first powdered beer Terra Forming Terra

An astonishing regularity in student learning rate Terra Forming Terra
Giant galaxy redefined after flipping jet to point straight at Earth Terra Forming Terra

Expected Death Terra Forming Terra
It struck me, reading this from Janosh who i have followed for a couple of deecades, that none of us are ever coached on all this. This item nicely redresses all that.
An expected death does prepare us and let us grant that at least. The worst is always the unexpected. how does one ever accept the death beside you of a young comrade. The shock is too immediate. The acceptance takes time.
The best understanding that we all need to carry with us is to understand that every soul, before born, will choose experiences and also several potential exit points as well. That is big because it cedes control back to the spirit and not a close friend or family member.
We all need to under5stand it this way.
16:49
Links 26/03/2023: OpenMandriva ROME 23.03, Texinfo 7.0.3, and KBibTeX 0.10.0 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
16:22
Russia Failing to Meet Arms Delivery Commitments to India: IAF Lifeboat News: The Blog
Russia cannot meet its arms delivery commitments to India because of its ongoing invasion of Ukraine, according to the Indian Air Force (AIF).
The statement, aired during a parliamentary committee meeting earlier this week, was the first official confirmation from New Delhi of Moscows defense export shortfalls.
It confirmed speculation that Russias defense industry is experiencing serious problems producing military supplies.
16:22
Computronium universe Lifeboat News: The Blog
I read enough to realize its in depth enough to make it worthwhile. Ill finish tomorrow as its 10:35 pm and Im beat. I need to rest for my mothers cardiac rehab tomorrow. She had a heart attack about a month ago.
Ray Kurzweil discusses having a universe filled with Computronium.
He discusses this happening within 200 years if wormholes or some other means allow faster than light travel.
What would the computation limits of computronium be?
16:21
Tips for an Information Security Analyst/Pentester Career - Ep. 92: 5 Unexpected Tips for A Successful Career Growth The S@vvy_Geek Hacking & Pentesting Blog
I've been a security consultant for almost 5 years, so I collected my share of war stories.
For this reason, I thought I could share with you some experience-driven tips I believe to be critical for achieving success in this industry, and that helped me a lot along the way.
I think some of them will blow your mind, but it's a needed shock to be successful in this industry, and the sooner you go through it the better.
Well, here we go:
- Always be professional: Most people think penetration
testing is all about technical skills, but nothing could be farther
from truth. Especially if you work for a consulting firm,
projecting a professional image at all times is paramount. The
client expects for you to be a subject matter expert and to be able
to explain in layman's terms what problems you found, what their
impact is and especially how to remediate them. This means you need
to be professional at all times. As far as the client is concerned,
you are your company, so you want to look at your best. Even
when clients are mean and rude, you can never get down to their
level, you're expected to keep your cool and continue delivering.
This can be sometimes very hard. I've experienced specific
situations where I really struggled to keep my cool, faced with
rude and combative attitudes, but I did because I knew I'd be the
only one looking bad. At the end of the day, penetration testing is
all about business mindset and professional communication. Yes, you
heard it right, sorry to break this to you. You can be the most
amazing tester on a technical standpoint, but you become worthless
if you can't explain your findings to the clients in terms they
would understand, and if you don't know how to communicate with
clients in a professional and personable way. So make sure you got
your your, you're and so on right. And forget about CTF and
frat house attitudes. Corporate security is much more a
tie-and-suit affair than you might think. The most challenging part
of being a consultant is to avoid an adversarial attitude and
convince the client you're on their team, you're on on their
side and you're not the enemy. I believe each one of us can do
better under this point of view.
- Be a team player: Security companies are often organized in teams and sometimes, for more complex tests, you may find yourself having to collaborate with other consult...
16:00
Caterpillar-Like Soft Robot With Distributed Programmable Thermal Actuation Hackaday

Researchers at North Carolina State University have created a soft robot that moves in a distinctly caterpillar-like manner. As detailed in the research paper in Science Advances by [Shuang Wu] and colleagues, the robot they developed consists of a layer of liquid crystalline elastomers (LCE) and polydimethylsiloxane (PDMS) with embedded silver nanowire that acts as a heater.
The LCE is hereby designed as a thermal bimorph actuator, using a distinct thermal expansion coefficient between the LCE and PDMS sides to create a highly controllable deformation and thus motion. Since the nanowire is divided into sections that can be individually heated, the exact deformation can be quite tightly controlled, enabling the crawling motion.
15:56
Critical Infrastructure Gear is Full of Flaws, but Hey, at Least It's Certified SoylentNews
Security researchers find bugs, big and small, in every industrial box probed:
Devices used in critical infrastructure are riddled with vulnerabilities that can cause denial of service, allow configuration manipulation, and achieve remote code execution, according to security researchers.
The researchers looked at 45 operational technology (OT) product lines used in government, healthcare, water, oil and gas, power generation, manufacturing, retail and other sectors from ten different major vendors. By reverse engineering the products, they were able to identify bad practices like unauthenticated protocols and weak cryptography.
From 53 identified CVEs: More than a third (21 CVEs) could facilitate credential compromise. Another 18 CVEs involved data manipulation, with 13 of these allowing firmware manipulation. And 10 CVEs provided a path to remote code execution.
Based on open source inquiries (e.g., using the Shodan search engine), the authors determined that a significant number of potentially vulnerable systems are exposed to the internet.
The vendors covered included: Bently Nevada, Emerson, Honeywell, JTEKT, Motorola, Omron, Phoenix Contact, Siemens, Yokogawa, and Schneider Electric.
"Worryingly, many of these products are certified but suffer from vulnerabilities that should have been caught in the certification process," the researchers say in their paper, citing IEC 62443 labelled products that weren't compliant. "...This suggests that apart from what the standards may not cover, even the things they do cover are not always properly covered in practice."
The Biden administration has cited the need to protect critical infrastructure as part of its recently announced National Cybersecurity Strategy. That goal evidently remains a work in progress.
Pre-print paper:
Jos Wetzels, Daniel dos Santos, and Mohammad Ghafari. 2023.
Insecure by Design in the Backbone of Critical
Infrastructure. In Cyber-Physical Systems and Internet of
Things Week 2023 this is a preprint version, May 912, 2023, San
Antonio, TX, USA. ACM, New York, NY, USA, 6 pages. https://doi.org/10.48550/arXiv.2303.12340
Read more of this story at SoylentNews.
15:30
Known unknowns: Refining your approach to uncategorized web traffic Help Net Security
Cybersecurity is such a complex field that even the best-trained, best-equipped, and most experienced security managers will sometimes struggle to decide which of several paths to take. Lets consider uncategorized web traffic, for instance. I define this broadly as traffic involving sites that arent yet classified, cant be classified (because theyre newly created or they involve parked or newly reactivated domains), or traffic that is (for now) unresolvable via standard domain name lookup. Since users More
The post Known unknowns: Refining your approach to uncategorized web traffic appeared first on Help Net Security.
15:00
Prioritizing data security amid workforce disruptions Help Net Security
Businesses have faced massive disruptions in their workforce many are requesting employees return to the office, and layoffs are rattling several industries. This disruption in the workforce can open organizations up to significant security breaches. In this Help Net Security video, Chris Wey, President of Data Modernization at Rocket Software, discusses the risks organizations face and the steps they can take to mitigate disruption. Everything from trade secrets to customer data to financial information More
The post Prioritizing data security amid workforce disruptions appeared first on Help Net Security.
15:00
Kernel prepatch 6.3-rc4 LWN.net
Linus has released 6.3-rc4 for testing.
"Things are looking pretty normal for this time of the release
process.
"
14:30
Understanding adversaries through dark web intelligence Help Net Security
93 percent of CISOs are concerned about dark web threats, and almost 72 percent of CISOs believe that intelligence on cybercriminals is critical to defend their organization and increase cybersecurity, according to Searchlight Cyber. The report findings show that most CISOs use threat intelligence to address security concerns, and 79 percent of CISOs are currently gathering data from the dark web. However, the research suggests that even among those that are already collecting dark web More
The post Understanding adversaries through dark web intelligence appeared first on Help Net Security.
14:00
The era of passive cybersecurity awareness training is over Help Net Security
Despite increased emphasis on cybersecurity from authorities and high-profile breaches, critical gaps in vulnerability management within organizations are being overlooked by executive leadership teams, according to Action1. These gaps leave organizations vulnerable to cyber threats. Key findings Low cybersecurity awareness among employees According to the survey, the time required to combat low cybersecurity awareness among employees has increased over the past year. This worrying trend makes organizations more vulnerable to phishing and other cyber-attacks. Breaches More
The post The era of passive cybersecurity awareness training is over appeared first on Help Net Security.
13:45
The World Wide Web is a Cesspit of Misinformation. Lets Do Something About It. Techrights
Social control media is a culmination of that and by far the worst, a principal culprit
Summary: It would be nice to make the Web a safer space for information and accuracy (actual facts) rather than a Safe Space for oversensitive companies and powerful people who cannot tolerate criticism; The Web needs to become more like today's Gemini, free of corporate influence and all other forms of covert nuisance
ABOUT four months ago I left my job at Sirius Open Source (one of the first FSF sponsors) after nearly 12 years at the company. I will be publishing a lot more about how this company robbed its own staff, probably posting an update just once or twice per week. The company is under investigation at the moment; its also losing some very big clients.
My plan is to devote a lot more time/energy to these Internet issues; theyre about as important as Software Freedom and are arguably a prerequisite.I left my job when I was 40 and since then Ive focused on many other things. I didnt lack projects to work on and I finally had a lot more time in my hands. As noted here last night, one aspiration of ours is to curate whats left of the World Wide Web algorithmically, seeing that a lot of todays Web is spam or sponsored propaganda. Gemini does not have this issue (yet).
Another issue is censorship; Ryan just wrote about that, based on his own experience. My plan is to devote a lot more time/energy to these Internet issues; theyre about as important as Software Freedom and are arguably a prerequisite. The photo at the top is me by the way, I stumbled upon it last night when searching old photos because my sister gets married later today. Shes a Debian user...
13:13
Journalist Plugs in Unknown USB Drive Mailed to HimIt Exploded in His Face SoylentNews
It's no secret that USB flash drives, as small and unremarkable as they may look, can be turned into agents of chaos. Over the years, we've seen them used to infiltrate an Iranian nuclear facility, infect critical control systems in US power plants, morph into programmable, undetectable attack platforms, and destroy attached computers with a surprise 220-volt electrical surge. Although these are just a few examples, they should be enough to preclude one from inserting a mysterious, unsolicited USB drive mailed to them into a computer. Unfortunately, one Ecuadorian journalist didn't get the memos.
As reported by the Agence France-Presse (via CBS News) on Tuesday, five Ecuadorian journalists have received USB drives in the mail from Quinsaloma. Each of the USB sticks was meant to explode when activated.
[...]
According to a police official who spoke with AFP, the journalist suffered mild hand and face injuries, and no one else was harmed.According to police official Xavier Chango, the flash drive that went off had a 5-volt explosive charge and is thought to have used RDX. Also known as T4, according to the Environmental Protection Agency (PDF), militaries, including the US's, use RDX, which "can be used alone as a base charge for detonators or mixed with other explosives, such as TNT." Chango said it comes in capsules measuring about 1 cm, but only half of it was activated in the drive that Artieda plugged in, which likely saved him some harm.
Read more of this story at SoylentNews.
13:00
The 4004 Upgrade Youve Been Waiting For Hackaday

You know how it is. You have an older computer, and you cant run the latest software on it. Time to upgrade, right? Well, if you have been in this situation a very long time, [ryomuk] may have an answer for you. The emu8080on4004 project (Google Translate) offers a way to run 8080 code on a 4004 CPU. Finally!
The 4004 development board is a homebrew affair, and the emulator works well enough that an 8080 Tiny BASIC interpreter ran with very few changes to the source code. You can see it working in the video below. It would be cool to run CP/M, but we imagine that would be a little harder, especially resource-wise.
A few things are missing. For example, the DAA instruction doesnt exist, and there are no provisions for interrupts. Theres only one I/O port, and using the IN instruction will block until you receive a serial port character. There is an option to implement the parity flag in the 8080 flags register, but its operation is untested.
Still, pretty impressive for a 4-bit CPU running at 740 kHz with very little memory. If you want to see more about the development board itself, check out the second video below. Want to know more about the chip that launched a family of processors that is still around? Read its biograp...
11:46
CISA to Start Issuing Early-Stage Ransomware Alerts HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
According to CISA, this new initiative will be helpful for organizations/institutions in the public health, education, and government sectors.
This is a post from HackRead.com Read the original post: CISA to Start Issuing Early-Stage Ransomware Alerts
11:40
Ryan Farmer: Im Back After WordPress.com Deleted My Blog Over the Weekend Techrights
Reprinted with permission from Ryan
Minutes after posting the commentary on the NBC news article about Apple (post prior to this one), my blog became suspended.
I didnt know what was going on, so I assumed I had been cancelled again, like Reddit, where if you post anything anywhere some special snowflake decides (often through a bot designed to sniff out no no words) that you should be banned.
Automattic (WordPress.com) refuses to say what led to the ban, but its quite obvious through my history of posts about Apples censorship, proprietary software, the Microsoft Stabber, etc. that there are probably outfits that would rather that I just go away and not come back.
Automattic says that theres no robot going around killing blogs without human review, but beyond this, I have no idea and Ill never be able to prove anything.
Things became a little more complicated when I went ahead and shut down my account, and then someone suggested I should appeal the ban.
I think Ive been on the modern Internet too long where people just silently murder your account with a gun pressed up to a pillow and was just no longer thinking in terms of You can appeal this and theres actually going to be someone that considers it., because again, Reddit.
I deleted my account at Reddit a while back because I was running into issues where I would say something like Thats crazy! in response to something incredulous and I would get banned, by a bot, which said You said crazy, and crazy is an ableist term! *spank spank spank*
Combined with the fact that Reddit just went and handed over tons of data about some users on one of its forums to a copyright troll didnt help all of this go down much better. It got me thinking, you know, if you browse around, theyre watching you. Logging you. Would it not be best if they didnt have that data?
So Ive been increasingly disconnecting from proprietary social media, because its all rather bullshit anyway, full of trolls and creepy companies.
After this run in with Automattic Im seriously considering just backing up this entire blog and self-hosting so that nobody else can complain.
You know, the whole thing about You violated the terms! Oh, what terms? TERMS!
Apparently this is just how Automattic rolls.
11:18
Civil Liberties Threatened Online and Offline Techrights
Video
download link | md5sum
388650e7d4e9f734a4572fd0265c3c95
Free Speech Online, Banking Digitally, and More
Creative Commons Attribution-No Derivative Works 4.0
Summary: A society of sheeple (a term used by Richard Stallman last week in his speech) is being herded online and offline; the video covers examples both online and offline, the latter being absence of ATMs or lack of properly-functioning ATMs (a growing problem lately, at least where I live)
THE video above is an outline of topics weve been covering, dealing with, barely coping with (like struggling to get cash out of ATMs where I live), and may cover some time soon. One recurring theme will be online banking or banking with apps.
The video starts by discussing online censorship. Days ago a longtime contributor, Ryan Farmer, had his blog suspended for no sane reason! None at all! If one tries to access anything on his blog it says baronhk.wordpress.com is no longer available. The authors have deleted this site.
This deletion was actually a protest after he had been unjustly suspended, having published this article (OMG! Someone call the cops! The headline had the string porn in it!).
There will be a lot more details in IRC scrollbacks, including todays (to be publish shortly). As an associate noted on the day of the suspension, hugo or jekyll or pelican would be a better choice than wordpress.com (where the ban/suspension happened; were in discussion with them about restoring the blog).
The vide...
11:06
DistroWatch Weekly, Issue 1012 DistroWatch.com: News
This week in DistroWatch Weekly: Review: siduction 22.1.1News: Two community editions of Ubuntu missing, politics and the Linux kernel, GNOME 44 introduces key new features and applicationsQuestions and answers: Protecting privacy from proprietary applicationsReleased last week: Tails 5.11, Trisquel GNU/Linux 11.0, Proxmox 7.4 "Virtual Environment", Ubuntu 20.04.6Torrent corner:....
11:00
HPR3821: The Oh No! News. Hacker Public Radio
The Oh No! news. Oh No! News, is Good News. Threat analysis; your attack surface. TAGS: Malware, Phishing, Security Breach GoDaddy, a Web Hosting Provider Hit Multiple Times by the Same Group. This month, GoDaddy, a leading web hosting provider, revealed that it had experienced a major security breach over several years, resulting in the theft of company source code, customer and employee login credentials, and the introduction of malware onto customer websites. Major Security Breach: Spanning several years. Data Breach: Employee login credentials & customer data. 10-k form Filled with the U.S. Securities and Exchange Commission. sec: GoDaddy Announces Security Incident Affecting Managed WordPress Service. Malware: Compromising customer websites managed by GoDaddy. Phishing Attacks: Exposed customer data including login credentials, email addresses, and SSL private keys. Chick-Fil-A Customers are Victims of a Data Breach. Fast-food chain Chick-fil-A has issued a warning to customers regarding a recent data security breach. The incident occurred between Dec. 18, 2022 and Feb. 12, 2023, during which unauthorized parties gained access to customer information, according to a statement posted on the California Attorney General’s website on Tuesday. Data Breach: membership numbers, mobile pay numbers, QR codes, last 4 digits of credit/debit card numbers, credits on Chick-fil-A accounts, birthdays, phone numbers, and addresses. New phishing campaign uses fake ChatGPT platform to scam eager investors. Bitdefender Antispam Labs confirmed that these scams initiate with an email containing a link that directs users to a copycat version that they can earn as much as $10,000 per month on the duplicate ChatGPT platform. Phishing: Email based scam. LassPass Security Incident Update and Recommended Actions. Major Security Breach: Spanning multiple years. Data Breach: Employee login credentials, source code & other intellectual property, customer data. Malware: Attackers exploited third-party software to compromise company systems by delivering a keylogger type malware. InfoSec; the language of security. TAGS: Information Security, Monitoring Bitwarden flaw can let hackers steal passwords using iframes. Bitwarden highlights that the autofill feature is a potential risk and even includes a prominent warning in its documentation, specifically mentioning the likelihood of compromised sites abusing the autofill feature to steal credentials. Phishing: Sniff credentials from a webpage HTML inline frame. wikipedia: An inline frame places another HTML document in a frame. Unlike an &l
Stress Management Workshop for College Students It Will Never Work in Theory
The further I get from my college years, the more I wonder how I got through them. It wasn't just the stress of juggling assignments that all seemed to be due on Thursday while figuring out what it meant to be an independent adult; the worst part was not being able to admit that it was overwhelming because you knew the response would be, "If you can't stand the heat, get out of the kitchen (or lab)."
A lot has changed for the better since then, in part because of research like that reported in this recent paper. Can a short online workshop on how to manage stress and anxiety actually help students deal with those issues? The answer isn't obvious: on the one hand, it ought to, but on the other hand, does help have to be delivered in person to be effective? Or is a longer intervention required? The answers seem to be "no" and "no", which immediately makes me wonder whether something like this would help programmers (and others) who are dealing with similar stress at work.
As a bonus, this paper shows how scientific abstracts should be written. As I wrote last year, the abstracts of most research papers in software engineering are more like movie trailers; while that is starting to change, it's still refreshing to see objectives, methods, results, and conclusions laid out succinctly and without fluff.
Carol S. Lee, Margaret Bowman, and Jenny L. Wu. Preliminary outcomes from a single-session, asynchronous online, stress and anxiety management workshop for college students. Trends in Psychiatry and Psychotherapy, 2022. doi:10.47626/2237-6089-2021-0448.
Objective: Self-guided asynchronous online interventions may provide college students access to evidence-based care, while mitigating barriers like limited hours of service. Thus, we examined the preliminary effectiveness of a 45-minute self-guided, asynchronous online, Dialectical Behavior Therapy (DBT)-informed stress and anxiety management workshop. Participants: College undergraduates (N=131) were randomized to either workshop (n=65) or waitlist control (n=66) conditions. Methods: Participants in the workshop condition completed baseline measures of depression, stress, and anxiety, before completing the workshop. Participants in the waitlist control condition only completed the baseline measures. All participants were reassessed at one-week follow-up. Results: Controlling for baseline measures, students in the workshop condition experienced significantly less stress and greater self-efficacy to regulate stress and anxiety at follow-up, compared to waitlist controls. Conclusions: A 45-minute self-guided, asynchron...
10:30
Exploring the Features of Music That People Fall Asleep to SoylentNews
Many people say that they listen to music to help them fall asleep, raising the question of whether music chosen for this purpose shares certain universal characteristics. However, research on the characteristics of sleep music is limited, and prior studies have tended to be relatively small.
To better understand the characteristics of sleep music, Scarratt and colleagues analyzed 225,626 tracks from 985 playlists on Spotify that are associated with sleep. They used Spotify's API to compare the audio features of the sleep tracks to audio features of music from a dataset representing music in general.
This analysis showed that sleep music tends to be quieter and slower than other music. It also more often lacks lyrics and more often features acoustic instruments. However, despite these trends, the researchers found considerable diversity in the musical features of sleep music, identifying six distinct sub-categories.
Three of the sub-categories, including ambient music, align with the typical characteristics identified for sleep music.
However, music in the other three subcategories was louder and had a higher degree of energy than average sleep music. These tracks included several popular songs, including "Dynamite" by the band BTS, and "lovely (with Khalid)" by Billie Eilish and Khalid.
[...] Overall, this study suggests that there is no "one-size-fits-all" when it comes to the music people choose for sleep. The findings could help inform future development of music-based strategies to help people sleep.
So what's on your sleep playlist?
Journal Reference:
Rebecca Jane Scarratt, et al., The audio features of
sleep music: Universal and subgroup characteristics [open],
Plos One, 2023. DOI: https://doi.org/10.1371/journal.pone.0278813
Read more of this story at SoylentNews.
10:00
Hackaday Links: March 26, 2023 Hackaday

Sad news in the tech world this week as Intel co-founder Gordon Moore passed away in Hawaii at the age of 94. Along with Robert Noyce in 1968, Moore founded NM Electronics, the company that would later go on to become Intel Corporation and give the world the first commercially available microprocessor, the 4004, in 1971. The four-bit microprocessor would be joined a few years later by the 8008 and 8080, chips that paved the way for the PC revolution to come. Surprisingly, Moore was not an electrical engineer but a chemist, earning his Ph.D. from the California Institute of Technology in 1954 before his postdoctoral research at the prestigious Applied Physics Lab at Johns Hopkins. He briefly worked alongside Nobel laureate and transistor co-inventor William Shockley before jumping ship with Noyce and others to found Fairchild Semiconductor, which is where he made the observation that integrated circuit component density doubled roughly every two years. This calculation would go on to be known as Moores Law.
Also in deceased tech billionaire news, a freak accident happened in Scotland involving the R/V Petrel, a research ship that was once...
09:07
Linux 6.3-rc4 Released: "Looking Pretty Normal" Phoronix
Linus Torvalds just announced the release of Linux 6.3-rc4 as we reach around the half-way point of the Linux 6.3 kernel's development cycle...
08:41
Mesa 23.0.1 Released With Many Fixes For Intel / AMD / Zink Phoronix
It's been one month since the release of Mesa 23.0 while it's finally been succeeded by Mesa 23.0.1 as the first point release containing a wide variety of bug fixes throughout this ecosystem of open-source 3D graphics drivers...
08:26
OpenAI: A Redis bug caused a recent ChatGPT data exposure incident Security Affairs
OpenAI revealed that a Redis bug was the root cause of the recent exposure of users personal information and chat titles in ChatGPT service.
On Friday, OpenAI revealed that the recent exposure of users personal information and chat titles in its chatbot service was caused by a bug in the Redis open-source library.
On March 20, 2023, several ChatGPT users started reporting seeing conversation histories of other users appearing in their accounts.
The same day, the history function showed the error message Unable to load history, and the chatbot service was temporarily interrupted. Below is the message published by OpenAI CEO Sam Altman.
The company identified the bug and quickly addressed it.
We took ChatGPT offline earlier this week due to a bug in an open-source library which allowed some users to see titles from another active users chat history. Its also possible that the first message of a newly-created conversation was visible in someone elses chat history if both users were active around the same time. reads an update published by the company.
The company investigated the impact of the issue and discovered that it may have caused the unintentional visibility of payment-related information of 1.2% of the ChatGPT Plus subscribers who were active during a specific nine-hour window. The company pointed out that the issue did not disclose financial information.
In the hours before we took ChatGPT offline on Monday, it was possible for some users to see another active users first and last name, email address, payment address, the last four digits (only) of a credit card number, and credit card expiration date. Full credit card numbers were not exposed at any time. continues the update.
The expert discovered that the bug was present in the Redis client open-source library, redis-py. The service uses...
06:54
True Blue On Line Casino Review & Actual Bonus Supply h+ Media
True Blue On Line Casino Review & Actual Bonus Supply
Next, youll be directed to the Apple Store page, where you will only need to click on on settle for the obtain, as if it have been some other regular app. That stated, you probably can entry on-line Casino Rocket in a quantity of languages, such as English, German, German-Austrian, French, Canadian English, Canadian French, Swiss-German, and Swiss-French. However, should you consider that you can resolve your problem your self, we advocate trying at the operators FAQ part. It covers a few of the commonest person issues and topics of concern and provides short and clear resolutions. While testing Casino Rocket NZ, we discovered the websites FAQ to be quite useful on multiple occasions.
These provide a broad variety of rewards which embody, free spins, money, and even a $1,000 bitcoin bonus. This facility will operate 24 hours a day and have 500 slot machines. Food and beverages might be out there from a snack bar and meals vans.
What is necessary to remember with that is that totally different video video games can usually have different payout charges. When taking a glance at recreation variety, we additionally take a look at whether or not or not they are appropriate on both cellular and desktop. Many on-line casinos provide restricted compatibility on mobile gadgets. This is often an issue for avid gamers who prefer to play on the go.
Machines are usually grouped by denomination, style and brand name. Video slots have a HELP or INFO button that will stroll you through the assorted payouts, play traces, bonus games and particular options. The 2,700+ slot machines at Encore Boston Harbor provide games for every fanatic, from video slots to reel slots, video poker and digital desk video video games.
Casino Guru Academy Free skilled tutorial programs for on-line on line casino staff geared toward commerce greatest practices, bettering participant expertise, and honest method to playing. Casinos normally settle for all bets made by patrons inside a longtime prohibit, in order that a patron cant win greater than a casino can afford to pay. Every sport supplied provides a casino a mathematical expectancy of winning, and it is extremely unusual for a casino to lose money on its games, even for sooner or later. Even lesser bettors are supplied reduced-fare transportation, lodge rooms, free drinks and cigarettes whereas playing, and other inducements. There are six casinos in Funchal, and so they provide a big selection of video games, together with blackjack, roulette, baccarat, and poker.
You can try all the main points below, clicking information for extra information and Claim to go straight over and decide up a couple of winnings. Check the payment strategies it presents and find out well about those platforms. We advise you not to save your data , so that in case of loss or theft they can not enter your account. The security...
06:53
Melbet India Evaluate Get 2150 In Free Bets h+ Media
Melbet India Evaluate Get 2150 In Free Bets
Using the cellphone you presumably can register, get wage bonuses, contact support, make financial transactions and rather more. Betting apps are in excessive demand among enthusiastic players in current times. The Melbet app is one of thebest international cricket betting apps.
I am especially pleased about melbet online on line casino. Slots are very properly embellished, I play there with my friends at weekends. Variety of occasions not only for sports, good odds, top-of-the-line strains for soccer.
Enable the set up of information for Unknown Sources within the Settings in your telephone. At the identical time, Melbet manages to get ahead in certain regards like notifications, broadcast of reside information, and extra. Melbet has made positive that plenty of effort has gone into making the platform as pleasant as potential. The app additionally does not have any issues with working smoothly on older telephones which have medium efficiency to the boot. It has come to mild that many customers are questioning about the authorized standing of Melbet in India.
Thanks to the booming cellular industry, MelBet couldnt keep away and has developed its cell app, which features perfectly on Android. Anyone can access the app at no cost by downloading it from the official website as an Apk file. Despite the advanced performance, MelBet for Android has comparatively modest system requirements. Thanks to such low necessities, youll have the power to get the total range of companies not on the latest cellphone fashions. Android and iOS app is software program with low system necessities thats suitable with all up-to-date devices.
Furthermore, cricket is a serious source of money for the Indian financial system. So, in case you are Indian, you are a part of a proud heritage. Melbet, unsurprisingly, allows you to guess on varied cricket leagues. The chat channel was examined and received a response in lower than 2 minutes, all providers have been provided in Hindi and English and the operator was very environment friendly. Without a doubt, the Melbet apps customer support, even with a small variety of channels, is amongst the platforms strengths.
The cell app isnt inferior to the web site in its features, offering customers the identical opportunities to get bonuses and participate in regular promotions. The sportsbook provides two utility variations, depending on the operating system. The Melbet APK download for Android is performed right from the location, identical as the app model for iOS units. The app is out there in many languages and offers various betting choices and casino games.
This makes bahrain betting communication between you and the assist group as simple as potential and helps to resolve all your issues sooner. You can check probably the most frequently a...
06:52
Mobile On Line Casino 2022 High 10 Best Cellular Casinos And Apps h+ Media
Mobile On Line Casino 2022 High 10 Best Cellular Casinos And Apps
By betting NZ$1.25 on the quantity 2, one other NZ$1.25 on the number 5, and the remaining NZ$2.50 on three of the four bonus sport fields, you probably can cover at least 27 of the fifty four segments of the wheel. The chance that the wheel will cease in both field of your bets is comparatively high. BonusFinder only works with casinos which function legally because of their Malta Gaming Authority and UK Gambling Commission licenses.
The biggest casino websites have bonuses that current rewards should you make a deposit as an current player, often recognized as a reload bonus. Thanks to the presence of former on line casino staff in-house, we could have interaction with on line casino buyer assistance on reside chat, cellphone, and email to test their responses. We know the tough inquiries to ask which separate out the very best out there when it comes to serving to players. With all playing wants taken care of and a few great promotions, you have to feel correct at home here.
More states, together with New York, have gone via diversified DFS licensed battles and/or have laws in progress. Their most spectacular recreation is their 3D on-line slots which have quite a couple of followers. The no-deposit welcome bonus is one other good characteristic of this website. However, weve a couple of recommendations that will push you in the course of constructing an educated ultimate selection. For a generous lump-sum bonus present, use the code CRYPTO400 with your first BTC deposit.
- On your 2nd, third, and 4th deposit, you will also get to say match bonuses for a complete of 5 BTC if youre not afraid to go huge.
- In addition, in slots it is attainable take pleasure in probably the most progressive software program and, after all, also of enjoyable functions conceived by an important online developers.
- CCS3 is a programming language that has advanced options which could benefit the process of building a website.
- They do this by offering you with the prospect to spice up the deposits you make or providing on line casino credit score to utilize on the positioning youve chosen to wager at.
- Comfort accommodates a quantity of issues during which youll give us the explanation, you will not have to maneuver.
The payment strategies for making deposits and withdrawals are available. Betting on its an experience so close to what you do in your computer. To motivate and please cell casino customers, operators are at all times providing bonus presents. All this with the aim that gamers are encouraged to do this mode of taking half in. 888 Casino NZ brings the magic into play with a bonus of up to $1++ on the first deposit.
Were all about substance right here too, but if it aint wanting fairly and it is troublesome to use, then likelihood is it isnt going to make a listing of prime...
06:50
Betting Options Of Melbet Cellular App h+ Media
Betting Options Of Melbet Cellular App
This makes communication between you and the help staff as simple as attainable and helps to solve all of your points quicker. You can verify essentially the most incessantly requested questions on the MelBet portal and use the fast search to search out the answer to your query earlier than contacting the support group. If you cant or dont wish to obtain Melbet, use the operators cellular site for sports activities predictions. It has virtually the same design and choices as the app.
Deposits and withdrawals for the latter are additionally fully free. However, basically the most attention-grabbing price technique is undoubtedly Bitcoin fee. Melbet was one of the primary bookmakers to supply this system to clients. It could be troublesome for Indian gamers to discover a web site the place they really feel cosy placing bets for reside on line on line casino play. Although the MELbet stay selection is on the small facet, its nonetheless large sufficient for any person to enjoy. MELbet is a worldwide on line on line casino that offers entry to gamblers all around the world.
To get the appliance, you need to go to the Melbet mobile website from your cell device. Apple coverage additionally prohibits downloading iPad, iPhone, or iPod touch apps from the App Store. In each instances, youll have to install this system manually. For Apple gadgets, you will want to make further modifications to the device software. Therefore, its easier has existed since 2012 and has numerous clients everywhere in the world.
Once the app is installed, the icon will seem on your telephone display screen. Clicking on its going to bring you to your MelBet login page. If you have already got a sound account, you simply need to enter your details and proceed to use the app as if it had been on the positioning. It is essential to understand that need to have a modern cellular system to install the Melbet app android model. Melbet app download for Android requires cellphones or tablets with Android four.1 and higher. Remember that you must use units with huge screens and a fast web connection to get pleasure from online betting with none issues.
Open your Melbet cricket app obtain and click on the yellow registration button on the upper-right corner of the screen. Choose cellular application on the backside of the listing. Users are at all times conscious and up to date thanks to the apps competitive odds and real-time updates on sports events. In addition, youll have the power to all the time contact the help workers, the place the best experts will help you.
The Mobile app is a chance to guess on reside matches. Dont fear when you didnt place a wager before the sport began. You can do this whenever you need during the match. Follow the steps and youll easily obtain the app on your iOS cellula...
06:49
Melbet App Evaluate In India h+ Media
Melbet App Evaluate In India
A click on on to the favored markets odds can open the betting ease, which could be obtained into as per choice to put the guess. Once you could have met the minimal withdrawal quantity pertaining to the cost risk you choose to make use of, you might withdraw the winnings. Ive observed that odds on handicaps here are higher than in several bookmakers workplaces. If you do not need to download the utility to your cellphone, you should use all of the features of Melbet bookmaker office within the Website version.
- Then navigate from your cellular gadget using a browser.
- I would like to recommend this bookmaker to a good friend.
- The procedure is equivalent for Android and iOS variations.
There are a lot of video games made by in style global providers. Here youll find a way to play slots of Novomatic, EGT, Pragmatic Play, Booongo, Playson, Endorphina, Microgaming, and so on. All games are licensed and have a set payout level. Thousands of slots, hundreds of unique mechanics and limitless methods to win await you. A unique mode in which there is a digital simulation of sports activities matches on soccer, basketball, and tennis. It is feasible to follow the course of occasions in reside mode.
When it involves downloading the MELbet cell app, you need to make certain that its appropriate with your devices. This means not all gadgets are suitable with the MELbet software. Hence, you would possibly end in enjoying this kind of betting from your cellphones browser. Melbet app makes betting simpler and less complicated for its customers.
When we review the Melbet app, its impossible not to point out such significant things as the primary properties of the bookmaker. Of course, one of many main criteria is that the company has an official Curacao license, so its actions are absolutely authorized in India and other international locations. They do not minimize limits, bets are calculated quickly and there isnt a dishonest. In play and pre-match I truly have a great line with a large spread.
Payment Strategies In Melbet App
With android, every little thing is caught up beneath one roof which is a nonissue because every item goes to its distinctive section. They have three broader divisions of the on line casino market; slots, reside on line casino, and different. Each of these host a sizeable variety of interesting events, easily accessible from melbet app.
Your account will be successfully verified after Melbet approves these documents. The official Melbet website has a piece for cybersports. This is as a result of they are thought-about one of many main betting events on the platform. This is an advantage as it allows gamers to scan the platform shortly and conveniently. Below the slides are stay sporting occasions and each event is updated to the smallest element. We earn our income from promoting...
06:47
Download Melbet App For Android Apk And Ios h+ Media
Download Melbet App For Android Apk And Ios
While the match is occurring and also youre ready for the outcomes, you possibly can entertain yourself within the casino section, which provides lots of video games for cash. Gamblers will discover entertainment to suit all tastes. Are you trying ahead to enroll with this agency utilizing a phone? Look no further as we have the best melbet app and Mobil signup illustrations here for you. This transfer will be the starting of your lengthy journey of exploring a big selection of products. Being a member merely unlocks all features and provides customers the right to make use of the company features and instruments to make money.
Generally, it takes 5-10 business days on your transaction to be reviewed and processed. With melbet app for iOS, ensure your working system is iOS 11 or later, theres 200+MBs storage, and you get the program from their genuine provider. If you own a smartphone with an android working system, we suggest you carry out a few simple steps earlier than installing the applying. The bookmaker permits gamers to make single bets, kind categorical bets and methods.
Here you can wager cash on occasions related to Dota 2, Counter-Strike and different video games. You can place a wager on virtually any sporting event. More than a thousand events associated to cricket, soccer, hockey, and other sports activities are added to the lineup every single day. Once you discover the install it. That means you presumably can simply download and use the app in your mobile gadget with a lot ease. The app capabilities properly on both Android and iOS operating systems.
After that, click on on the Melbet apk download button with the Android emblem. The Melbet apk obtain file will also be routinely downloaded to your device. The Melbet app is a great alternative to get pleasure from the best betting web site proper out of your mobile phone. The app is out there on both iOS and Android platforms.
Melbet was based in 2012, has an Eastern European origin and a Curacao license. Melbet.com also has a license in Nigeria, and the brand has acquired a piece allow in Kenya and Estonia. The design of the app is dominated by the colours grey, green and yellow. Text and odds are clearly seen and distinguishable. The easiest and most simple method for any consumer, as a result of all you need to do is select your country of residence and foreign money.
You could make predictions for each popular and little-known sports. Doubling your first deposit to INR 8,000 is a superb beginner supply to take advantage of in 2021. You cant spend it on on line casino games, toto, poker, and different activities. Players are supplied welcome bonuses for each sports activities betting and playing.
I even havent any issues with melbet free download, everything is virus-free and fast. The withdraw...
05:43
Newly-Revealed Coronavirus Data Has Reignited a Debate Over the Virus's Origins SoylentNews
Newly-revealed coronavirus data has reignited a debate over the virus's origins:
Data collected in 2020and kept from public view since thenpotentially adds weight to the animal theory. It highlights a potential suspect: the raccoon dog. But exactly how much weight it adds depends on who you ask. New analyses of the data have only reignited the debate, and stirred up some serious drama.
The current ruckus starts with a study shared by Chinese scientists back in February 2022. In a preprint (a scientific paper that has not yet been peer-reviewed or published in a journal), George Gao of the Chinese Center for Disease Control and Prevention (CCDC) and his colleagues described how they collected and analyzed 1,380 samples from the Huanan Seafood Market.
These samples were collected between January and March 2020, just after the market was closed. At the time, the team wrote that they only found coronavirus in samples alongside genetic material from people.
There were a lot of animals on sale at this market, which sold more than just seafood. The Gao paper features a long list, including chickens, ducks, geese, pheasants, doves, deer, badgers, rabbits, bamboo rats, porcupines, hedgehogs, crocodiles, snakes, and salamanders. And that list is not exhaustivethere are reports of other animals being traded there, including raccoon dogs. We'll come back to them later.
But Gao and his colleagues reported that they didn't find the coronavirus in any of the 18 species of animal they looked at. They suggested that it was humans who most likely brought the virus to the market, which ended up being the first known epicenter of the outbreak.
But....
Read more of this story at SoylentNews.
04:55
Sparks of Artificial General Intelligence: Early Experiments with GPT-4, Exhibits Emergent Behaviors and Capabilities Whose Sources and Mechanisms Are, at This Moment, Hard to Discern Precisely cryptogon.com
They dont know how it works. Via: arXiv Microsoft Research: Artificial intelligence (AI) researchers have been developing and refining large language models (LLMs) that exhibit remarkable capabilities across a variety of domains and tasks, challenging our understanding of learning and cognition. The latest model developed by OpenAI, GPT-4 [Ope23], was trained using an unprecedented []
04:53
An aperiodic monotile, by David Smith, Joseph Samuel Myers, Craig S. Kaplan, and Chaim Goodman-Strauss. A longstanding open problem asks for an aperiodic monotile, also known as an einstein: a shape that admits tilings of the plane, but never periodic tilings.
Tilings Encyclopedia, from Uni Bielefeld. Aperiodicity can be achieved with pretty easy rules.
How did Dennis Ritchie Produce his PhD Thesis? A Typographical Mystery (PDF), by David F. Brailsford, Brian W. Kernighan, and William A. Ritchie.
Notes on structured concurrency, or: Go statement considered harmful (2018), by Nathaniel J. Smith.
BibBot, a browser add-on to read german news pages using a public library account.
Reviving the IBM Selectric Composer Fonts, by Jens Kutilek.
A compiler for the Tiny-C language, by Marc Feeley. Wirth-level of integration!
The C2 Wiki, online archive with the original feel.
Samsung space zoom moon shots are fake, and here is the proof, what a disgusting feature.
Typescripting the technical interview, by Richard Towers.
04:25
Up to 80 Percent of Workers Could See Jobs Impacted by AI cryptogon.com
Paper: GPTs are GPTs: An Early Look at the Labor Market Impact Potential of Large Language Models: Our findings indicate that approximately 80% of the U.S. workforce could have at least 10% of their work tasks affected by the introduction of GPTs, while around 19% of workers may see at least 50% of their tasks []
04:25
Security Affairs newsletter Round 412 by Pierluigi Paganini International edition Security Affairs
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are free for you in your email box.
If you want to also receive for free the newsletter with the international press subscribe here.
04:00
Techrights Develops Free Software to Separate the Wheat From the Chaff Techrights
Summary: In order to separate the wheat from the chaff weve been working on simple, modular tools that process news and help curate the Web, basically removing the noise to squeeze out the signal
THE concept behind Free Software emanates from many programmers desire to not only produce useful software but also to share this usefulness with many other people, either in exchange for recognition or further improvements to that software.
Lately weve developed a number of programs (Free Software of course, GPLV3-licensed) that help produce/curate Daily Links. Some time later this month or next month well properly explain what they are and how they work. Other people too deserve access to the toolsets.
03:44
The Last of Us is Getting Married schestowitz.com
 spoke
to my sister today (thats her above) one last time before her
wedding tomorrow. Its hard to believe how fast people grow up. Shes
now managing a team, doing programming while using Debian 11, just
like me. Tomorrow shell be officially married to another technical
person. Life passes by when you dont pay attention. We all grow
older, but some take advantage of the time they have on this
planet. Some waste it away.
spoke
to my sister today (thats her above) one last time before her
wedding tomorrow. Its hard to believe how fast people grow up. Shes
now managing a team, doing programming while using Debian 11, just
like me. Tomorrow shell be officially married to another technical
person. Life passes by when you dont pay attention. We all grow
older, but some take advantage of the time they have on this
planet. Some waste it away.
This is me aged 16, back in the days I was playing tennis a lot.
03:06
OpenMandriva ROME 23.03 Released With Linux 6.2 + KDE Plasma 5.27 Desktop Phoronix
OpenMandriva ROME 23.03 has been released as the "rolling release" flavor of this Linux distribution whose roots trace back to the beautiful days of Mandrake Linux...
02:40
Linux Will Stop Randomizing Per-CPU Entry Area When KASLR Is Not Active Phoronix
With the Linux 6.2 release kernel developers addressed "a tasty target for attackers" after it was realized that the per-CPU entry data was not being randomized, even in the presence of Kernel Address Space Layout Randomization (KASLR). The per-CPU entry area randomization has been present since Linux 6.3 but then was realized it's being activated even if KASLR was disabled, so now that is changing to avoid possible confusion...
02:22
Eye drop recall: Florida woman sues company after eye removed Lifeboat News: The Blog
A Florida woman is suing an eye drop manufacture claiming that its product which has been linked to a deadly bacteria outbreak made her legally blind.
Sixty-eight-year-old Clara Elvira Oliva is taking legal action against Global Pharma Healthcare after suffering such a severe infection from using its EzriCare Artificial Tears that she had to have her eye removed, according to court documents.
Olivas right eye was removed and replaced with a plastic implant in September 2022 to control a severe antibiotic resistant infection, according to the lawsuit filed earlier this month in Federal court in Miami, Florida.
02:22
More than 10 different brands of eye drops recalled Lifeboat News: The Blog
The eye drops were contaminated with an antibiotic-resistant form of Pseudomonas aeruginosa, an aggressive bacterium, according to the CDC.
02:22
SpaceX may have to deorbit some of its new Starlink V2 Mini satellites Lifeboat News: The Blog
SpaceX / Twitter.
The SpaceX CEO explained that some satellites would likely have to be deorbited to burn up in Earths atmosphere.
02:22
80% of workers will be exposed to AI. These jobs will be most affected Lifeboat News: The Blog
Researchers at OpenAI have worked out the potential exposure to AI different occupations face and its impact is widespread.
02:00
Gallium Nitride and Silicon Carbide Fight for Green Tech Domination IEEE Spectrum
![]()
Can advanced semiconductors cut emissions of greenhouse gases enough to make a difference in the struggle to halt climate change? The answer is a resounding yes. Such a change is actually well underway.
Starting around 2001, the compound semiconductor gallium nitride fomented a revolution in lighting that has been, by some measures, the fastest technology shift in human history. In just two decades, the share of the global lighting market held by gallium-nitride-based light-emitting diodes has gone from zero to more than 50 percent, according to a study by the International Energy Agency. The research firm Mordor Intelligence recently predicted that, worldwide, LED lighting will be responsible for cutting the electricity used for lighting by 30 to 40 percent over the next seven years. Globally, lighting accounts for about 20 percent of electricity use and 6 percent of carbon dioxide emissions, according to the United Nations Environment Program.
 Each wafer
contains hundreds of state-of-the-art power
transistorsPeter Adams
Each wafer
contains hundreds of state-of-the-art power
transistorsPeter Adams
This revolution is nowhere near done. Indeed, it is about to jump to a higher level. The very semiconductor technology that has transformed the lighting industry, gallium nitride (GaN), is also part of a revolution in power electronics that is now gathering steam. It is one of two semiconductorsthe other being silicon carbide (SiC)that have begun displacing silicon-based electronics in enormous and vital categories of power electronics.
GaN and SiC devices perform better and are more efficient than the silicon components they are replacing. There are countless billions of these devices all over the world, and many of them operate for hours every day, so the energy savings are going to be substantial. The rise of GaN and SiC power electronics will ultimately have a greater positive impact on the planets climate...
01:40
Microsoft shares guidance for investigating attacks exploiting CVE-2023-23397 Security Affairs
Microsoft is warning of cyber attacks exploiting a recently patched Outlook vulnerability tracked as CVE-2023-23397 (CVSS score: 9.8).
Microsoft published guidance for investigating attacks exploiting recently patched Outlook vulnerability tracked as CVE-2023-23397.
The flaw is a Microsoft Outlook spoofing vulnerability that can lead to an authentication bypass.
A remote, unauthenticated attacker can exploit the flaw to access a users Net-NTLMv2 hash by sending a specially crafted e-mail to an affected system.
An attacker who successfully exploited this vulnerability could access a users Net-NTLMv2 hash which could be used as a basis of an NTLM Relay attack against another service to authenticate as the user. reads the advisory published by Microsoft. The attacker could exploit this vulnerability by sending a specially crafted email which triggers automatically when it is retrieved and processed by the Outlook client. This could lead to exploitation BEFORE the email is viewed in the Preview Pane. External attackers could send specially crafted emails that will cause a connection from the victim to an external UNC location of attackers control. This will leak the Net-NTLMv2 hash of the victim to the attacker who can then relay this to another service and authenticate as the victim.
The vulnerability was reported by the CERT-UA and the Microsoft Incident Response, Microsoft Threat Intelligence (MSTI), suggesting that it has been exploited by a nation-state actor.
Microsoft addressed the flaw as part of its Patch Tuesday updates for March 2023.
The guidance published by Microsoft includes details about the attacks using the vulnerability. The following diagram shows attackers gaining initial access using a Net-NTLMv2 Relay attack, then maintaining persistence via modifying mailbox folder permissions, and performing lateral movement by sending additional malicious messages.
01:27
Links 26/03/2023: MidnightBSD 3.0 and FreeBSD 13.2 RC4 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Linux Links Linux Around The World: Nigeria
We cover user groups that are running in Nigeria. This article forms part of our Linux Around The World series.
-
Desktop/Laptop
-
Its FOSS Framework Unveils a New Laptop With Game-Changing Open Source Module System
Framework...
-
-
01:03
Mathematicians Have Finally Discovered an Elusive Einstein Tile SoylentNews
A 13-sided shape called 'the hat' forms a pattern that never repeats:
A 13-sided shape known as "the hat" has mathematicians tipping their caps.
It's the first true example of an "einstein," a single shape that forms a special tiling of a plane: Like bathroom floor tile, it can cover an entire surface with no gaps or overlaps but only with a pattern that never repeats.
"Everybody is astonished and is delighted, both," says mathematician Marjorie Senechal of Smith College in Northampton, Mass., who was not involved with the discovery. Mathematicians had been searching for such a shape for half a century. "It wasn't even clear that such a thing could exist," Senechal says.
Although the name "einstein" conjures up the iconic physicist, it comes from the German ein Stein, meaning "one stone," referring to the single tile. The einstein sits in a weird purgatory between order and disorder. Though the tiles fit neatly together and can cover an infinite plane, they are aperiodic, meaning they can't form a pattern that repeats.
With a periodic pattern, it's possible to shift the tiles over and have them match up perfectly with their previous arrangement. An infinite checkerboard, for example, looks just the same if you slide the rows over by two. While it's possible to arrange other single tiles in patterns that are not periodic, the hat is special because there's no way it can create a periodic pattern.
Read more of this story at SoylentNews.
01:00
Loudmouth DJI Drones Tell Everyone Where You Are Hackaday

Back when commercial quadcopters started appearing in the news on the regular, public safety was a talking point. How, for example, do we keep them away from airports? Well, large drone companies didnt want the negative PR, so some voluntarily added geofencing and tracking mechanisms to their own drones.
When it comes to DJI, one such mechanism is DroneID: a beacon on the drone itself, sending out a trove of data, including its operators GPS location. DJI also, of course, sells the Aeroscope device that receives and decodes DroneID data, declared to be for government use. As it often is with privacy-compromising technology, turns out its been a bigger compromise than we expected.
Questions started popping up last year, as off-the-shelf quadcopters (including those made by DJI) started to play a part in the Russo-Ukrainian War. It didnt take long for Ukrainian forces to notice that launching a DJI drone led to its operators being swiftly attacked, and intel was that Russia got some Aeroscopes from Syria. DJIs r...
00:58
New Backdoor Attack Uses Russian-Ukrainian Conflict Phishing Emails HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
The backdoors used in this campaign are never-before-seen malware strains called CommonMagic and PowerMagic.
This is a post from HackRead.com Read the original post: New Backdoor Attack Uses Russian-Ukrainian Conflict Phishing Emails
00:37
Extraordinary: The Revelations cryptogon.com
Via: Unidentified:
00:23
The Impending Collapse of the French Economy Lifeboat News: The Blog

Pensions behave as government mandated ponzi schemes. New contributors are needed to pay for past contributors. But what if there are less and less new contributors and contributions? And what if past generations live longer and longer lives?
Limited time: get 5 free stocks when you sign up to moomoo and deposit $100 and 15 free stocks when you deposit $1,000. Use link https://j.moomoo.com/00iPZo.
France is facing massive protests in response to its recently announced pension reform. While France is the only country facing massive protests for now, almost all developed countries will likely be forced to conduct similar pension reforms in the future as they face rapidly aging populations.
0:00 1:50 Intro.
1:51 5:03 French pension system.
5:04 7:15 The Ponzi scheme.
7:16 9:42 Pension crisis.
9:43 11:20 Demographic time bomb.
11:21 A warning to us all.
Email us: Wallstreetmillennial@gmail.com.
Support us on Patreon: https://www.patreon.com/WallStreetMillennial?fan_landing=true.
Check out our new podcast on Spotify: https://open.spotify.com/show/4UZL13dUPYW1s4XtvHcEwt?si=08579cc0424d4999&nd=1
All materials in these videos are used for educational purposes and fall within the guidelines of fair use. No copyright infringement intended. If you are or represent the copyright owner of materials used in this video and have a problem with the use of said material, please send me an email, wallstreetmillennial.com, and we can sort it out.
00:23
Metas New ChatGPT-Like AI Is Fluent in the Language of Proteinsand Has Already Modeled 700 Million of Them Lifeboat News: The Blog
Meta seems to already have good AI tools.
Metas ESMFold AI is a large language model like OpenAIs ChatGPT. But instead of spitting out text, it generates protein sequences.
00:22
Blood Test #2 in 2023: Diet Composition Lifeboat News: The Blog
Join us on Patreon! https://www.patreon.com/MichaelLustgartenPhD
Discount Links:
NAD+ Quantification: https://www.jinfiniti.com/intracellular-nad-test/
Use Code: ConquerAging At Checkout.
Green Tea: https://www.ochaandco.com/?ref=conqueraging.
Oral Microbiome: https://www.bristlehealth.com/?ref=michaellustgarten.
Epigenetic Testing: https://bit.ly/3Rken0n.
Use Code: CONQUERAGING!
At-Home Blood Testing: https://getquantify.io/mlustgarten.
Sunday, 26 March
22:23
Civil Space Lifeboat News: The Blog
Johns Hopkins APLs Civil Space Mission Area makes critical contributions to NASA and international missions to meet the challenges of space science, engineering, and exploration.
Since the dawn of the Space Age, APL has pushed the frontiers of space science, engineering and exploration. We captured the first picture of Earth from space, invented navigation by satellite, dispatched spacecraft across the solar system from our Sun to Pluto and beyond, and successfully conducted the worlds first full-scale planetary defense test mission.
We continue to shape the future by providing our nation with innovative and low-cost solutions to its space challenges. Our work includes conducting research and space exploration; development and application of space science, engineering, and technology; and production of one-of-a-kind spacecraft, instruments, and subsystems.
22:22
Pyrroloquinoline quinone disodium salt improves brain function in both younger and older adults Lifeboat News: The Blog
Brain function is important for a good quality of life. Pyrroloquinoline quinone disodium salt (PQQ) has been proven to improve brain function and cognition in older adults (above 45 years). In this double-blind, placebo-controlled study, we investigated the effects of PQQ on cognitive function in adults aged between 20 and 65 years. PQQ (20 mg per day) was administered for 12 weeks to the participants. After 12 weeks, the participants showed improvements in composite memory and verbal memory. A further age-stratified analysis was performed. In younger adults (aged 2040 years), PQQ improved cognitive function (cognitive flexibility, processing speed, and execution speed) after 8 weeks. Only older adults (aged 4165 years) showed improvements in complex and verbal memory after 12 weeks. In the logistic regression analysis that included the results of all cognitive tests, the changes due to PQQ intake were observed at 8 and 12 weeks in the young and old groups, respectively.
22:10
Linux 6.4 Preparing DRM Deadline Hints To Help Influence GPU Frequency/Performance Phoronix
Rob Clark on Saturday sent out a pull request adding the DMA-BUF/DMA-FENCE deadline awareness code to the Direct Rendering Manager (DRM) subsystem with the upcoming Linux 6.4 cycle...
22:00
Classic 1960s Flip Clock Gets NTP Makeover Hackaday

Many of the clocks we feature here on Hackaday are entirely built from scratch, or perhaps reuse an unusual display type. But sometimes, an old clock is just perfect as it is, and only needs a bit of an upgrade to help it fit into the modern world. One such example is the lovely 1960s Copal flip clock (in German, Google Translate link) that [Wolfgang Jung] has been working with he managed to bring it squarely into the 21st century without changing its appearance one bit.
Like most flip clocks from the 60s and 70s, the Copal clock uses a small synchronous AC motor to advance the digits. Because this motor runs in step with the mains frequency, it also acts as the clocks timing reference. However the original motor had died, and a direct replacement was impossible to find. So [Wolfgang] decided to replace it with a modern stepper motor. He designed a small PCB that fit the original housing, on which he placed a Trinamic TMC2225 stepper motor driver, a Wemos D1 Mini and a small 5 V power supply.
...
21:54
LLVM 17 Lands Initial Support For RISC-V Vector Crypto Extension ISA Phoronix
Merged this weekend to the LLVM 17 development code-base is initial support for RISC-V's vector crypto extension ISA...
21:45
Major Publishers Mull Legal Action Against Pirate Ebook Platform TorrentFreak
 Theres something special about professionally produced
textbooks. From the information inside to the tactile feel of the
paper, textbooks can be items of beauty.
Theres something special about professionally produced
textbooks. From the information inside to the tactile feel of the
paper, textbooks can be items of beauty.
Unfortunately, reality rains on the parade more than just a little. Textbooks are bulky, woefully underpowered for mass research purposes, and then suddenly out date for any number of reasons. After factoring in the extraordinary expense, its no surprise that some turn to sites like the recently resurrected Z-Library.
Check Out The Bargains, Beware of the Scams
A student posting on Reddits /r/college earlier this year posed questions about digital textbooks. As a distance learner, digital copies made sense since they dont have to be physically returned.
After spotting a website offering every textbook the student needed for just $20 each, a question needed to be answered: Is Fenlita.com really legit?
As suggested by some of the responses, sites selling new textbooks for $20 should always be viewed with caution. Several people claiming to have used Fenlita say they pretty much got what they expected a pirated copy of a textbook in PDF format, in some cases delivered via a Dropbox link.
Other reviews and reports suggest more serious problems for potential buyers.
One reported purchase consisted of a file that took about an hour to download and then turned out to be 400 pages of screenshots. Given the low price, that mightve been tolerable; if the textbook in its original form hadnt run to 650 pages.
Reports of multiple charges to credit cards and items appearing in baskets multiple times werent supported by proof but are still a concern. A report from a buyer, who complained that a download link went to an apparently seized website, hardly inspires confidence.
Publishers Target Fenlita.com
Given the above, it’...
21:33
Libinput 1.23 Brings New "Custom" Pointer Acceleration Profile, Better Razer Support Phoronix
Jos Expsito announced the release this weekend of libinput 1.23, the input handling library used these days across the Linux desktop for both X.Org/X11 and Wayland based environments. With libinput 1.23 comes a few notable new features...
21:08
KDE This Week Unveiled The XWaylandVideoBridge, Landed More Crash Fixes Phoronix
KDE developers remain quite busy working on Plasma 6.0 development along with preparing fixes for further Plasma 5.27 LTS point releases...
20:23
Facebook accounts hijacked Lifeboat News: The Blog
The extension is a copy of the legitimate popular add-on for Chrome named ChatGPT for Google that offers ChatGPT integration on search that attempts to steal Facebook session cookies.
The publisher of the extension uploaded it to the Chrome Web Store on February 14, 2023, but only started promoting it using Google Search advertisements on March 14, 2023. Since then, it has had an average of a thousand installations per day.
20:18
Non-Disparagement Clauses Are Retroactively Voided, NLRBs Top Cop Clarifies SoylentNews
The National Labor Relations Board has clarified that non-disparagement clauses attached to severance packages are null and void. Companies will not be able to stifle criticism by ex-employees through clauses asking them to waive their inherent rights.
The general counsel of the National Labor Relations Board issued a clarifying memo on Wednesday regarding the "scope" of a February ruling by the federal agency's board that said employers cannot include blanket non-disparagement clauses in their severance packages, nor demand laid-off employees keep secret the terms of their exit agreements.
Such provisions have become increasingly common in recent years, muzzling employees and otherwise stopping them from speaking up about working conditions by dangling a few weeks or months of pay in front of them at the exact moment they are losing their job.
This is a follow up to last month's statment and could prove significant for some employers with a high rate of turn over and decades of in-house dirt. *cough*m$*cough*
Read more of this story at SoylentNews.
19:30
Week in review: Manage the risk of ChatGPT use, know the danger of failed Okta logins Help Net Security
Heres an overview of some of last weeks most interesting news, articles, interviews and videos: These 15 European startups are set to take the cybersecurity world by storm Google has announced the startups chosen for its Cybersecurity Startups Growth Academy. The 15 selected startups are from eight countries and were chosen from over 120 applicants. Threat actors are experimenting with QR codes Hackers are diversifying attack methods, including a surge in QR code phishing campaigns, More
The post Week in review: Manage the risk of ChatGPT use, know the danger of failed Okta logins appeared first on Help Net Security.
19:00
Is Your USB-C Dock Out To Hack You? Hackaday

In todays installment of Betteridges law enforcement, heres an evil USB-C dock proof-of-concept by [Lachlan Davidson] from [Aura Division]. Weve seen malicious USB devices aplenty, from cables and chargers to flash drives and even suspicious USB fans. But a dock, however, is new. The gist is simple you take a stock dock, find a Pi Zero W and wire it up to a USB 2.0 port tapped somewhere inside the dock. Finding a Pi Zero is unquestionably the hardest part in this endeavor on the software side, everything is ready for you, just flash an SD card with a pre-cooked malicious image and go!
On the surface level, this might seem like a cookie-cutter malicious USB attack. However, theres a non-technical element to it; USB-C docks are becoming more and more popular, and with the unique level of convenience they provide, the plug it in temptation is much higher than with other devices. For instance, in shared workspaces, having a USB-C cable with charging and sometimes even a second monitor is becoming a norm. If you use USB-C...
17:07
IRC Proceedings: Saturday, March 25, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-250323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-250323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-250323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-250323.gmi
Over HTTP:
|
... |
17:05
Vice Society claims attack on Puerto Rico Aqueduct and Sewer Authority Security Affairs
Puerto Rico Aqueduct and Sewer Authority (PRASA) is investigating a cyber attack with the help of the FBI and US CISA.
The Puerto Rico Aqueduct and Sewer Authority (PRASA) is investigating a cyberattack that last week hit the agency. The agency quickly activated the incident response procedure after the attack.
The attack was disclosed on March 19, and threat actors had access to customer and employee information. The agency is going to notify impacted customers and employees via breach notification letters.
The agency pointed out that operations at the critical infrastructure managed by the agency in Puerto Rico were not impacted.
It should be noted that once the incident was detected and from the first moment we have been working with the relevant authorities, the FBI and CISA [Cybersecurity and Infrastructure Security Agency], specifically, said Nannette Martnez, executive director of the Puerto Rico Aqueduct and Sewer Authoritys (PRASA) office of innovation and technology.
At this time, the agency has yet to reveal the name of the group behind the attack, but the Vice Society ransomware gang added the authority to the list of victims on its Tor leak site. The ransomware gang leaked the passports, drivers licenses and other documents of the impacted individuals.
16:06
Links 26/03/2023: More TikTok Bans Techrights
![]()
Contents
-
GNU/Linux
-
Desktop/Laptop
-
Linux Made Simple 2023-03-20Linux Weekly Roundup #227
-
OMG! Linux Framework Laptop 13 Finally Gets AMD Options
Im not lucky enough to own one (yet) but, on sheer concept alone, I am a big fan of Frameworks modular 13-inch laptop
-
-
Server
-
Container Journal Docker, Inc. Celebrates 10th Anniversary With Alliances
Docker, Inc. celebrated the 10th anniversary of the namesake artifact used widely for building cloud-native applications by announcing alliances with Ambassador Labs to improve the developer experience and Hugging Face to make it simpler to launch and deploy machine learning applications on a cloud service using DockerFile. In addition, Docker,
-
-
Audiocasts/Shows
-
Jupiter Broadcasting The Podman Perspective | Self-Hosted 93
Alex goes all in on Rootless Podman, Chris is saving his Nextcloud install from disaster, and a special guest joins us. Special Guest: Alex Ellis.
-
Linux in the Ham Shack LHS Episode #501: FreeDV Deep Dive 2
Hello and welcome to the 501st episode of Linux in the Ham Shack. In this episode, we talk with Mooneer Salem, K6AQ, primary developer on the FreeDV team.
-
The TLLTS Podcast The L...
-
-
16:00
Recreating one of Historys Best Known Spy Gadgets Hackaday

[Machining and Microwaves] got an interesting request. The BBC asked him to duplicate the Great Seal Bug the device the Russians used to listen covertly to the US ambassador for seven years in 1945. Turns out theyre filming a documentary on the legendary surveillance device and wanted to demonstrate how it worked.
The strange thing about the bug is that it wasnt directly powered. It was actually a resonant cavity that only worked when it was irradiated with an external RF energy. Most of the video is background about the bug, with quite a few details revealed. We particularly liked the story of using a software defined radio (SDR) to actually make the bug work.
As you might expect, things didnt go smoothly. Did they ever get results on camera? Watch the video, and you can find out. This is just the first of six videos he plans to make on the topic, and we cant wait for future videos that cover the machining and more technical details.
Weve examined the Theremin bug before. Theres a definite cat-and-mouse dynamic between creating bugging devices and detecting them.
...
15:36
Earth is Running Out of Places for Stargazers' Dark Deeds SoylentNews
A 'new deal for the night' needed:
Increasing levels of light pollution means Earth's surface has almost no practical locations for astronomical observatories, a group of astronomers said on Monday.
Artificial light emitted from buildings, streetlights, and reflected from satellite constellations are making the night sky brighter for earth-bound skywatchers. The Milky Way was visible to pretty much everyone less than 100 years ago, but is now drowned out by human-made light to most, according to the International Dark Sky Association.
[...] "Today, due to the rise of light pollution, there are almost no more remote places available on Earth that simultaneously meet all the characteristics needed to install an observatory (namely, the absence of light pollution, a high number of clear nights, and good seeing)," a team of astronomers said in Nature Astronomy.
The authors urged astronomers, companies, politicians, and lawmakers around the world to work together to reach a global agreement to limit artificial light. Light pollution should be treated in the same way that other types of pollutants, like greenhouse gases, they argued. Governments around the world should and can tackle light pollution in the same ways they address climate change: with international treaties and goals to restrict levels of other pollutants.
[...] "As it is not too late to stop this, we as scientists and first as citizens should act to stop this attack, from above with satellites and from below with [artificial light at night], on the natural night and on the intangible cultural heritage of humankind's starry skies," they concluded.
"Now is the time to consider the prohibition of mega-constellations and to promote a significant reduction in [artificial light at night] and the consequent light pollution. Our world definitely needs a 'new deal' for the night."
Journal Reference:
Falchi, F., Bar, S., Cinzano, P. et al. A call for
scientists to halt the spoiling of the night sky with artificial
light and satellites [open]. Nat Astron 7,
237239 (2023). https://doi.org/10.1038/s41550-022-01864-z
Read more of this story at SoylentNews.
13:00
Single Flex PCB Folds into a Four-Wheel Rover, Complete with Motors Hackaday

Youve got to hand it to [Carl Bugeja] he comes up with some of the most interesting electromechanical designs weve seen. His latest project is right up there, too: a single PCB that folds up into a four-wheel motorized rover.
The key to [Carl]s design lies with his PCB brushless motors, which he has been refining since we first spotted them back in 2018. The idea is to use traces on the PCB for the stator coils to drive a 3D printed rotor containing tiny magnets. They work surprisingly well, even if they dont generate a huge amount of torque. [Carl]s flexible PCB design, which incorporates metal stiffeners, is a bit like an unfolded cardboard box, with two pairs of motor coils on each of the side panels. This leaves the other surfaces available for all the electronics, with includes a PIC, a driver chip, and a Hall sensor for each motor, an IMU and proximity sensor for navigation, and an ESP32 to run the show.
With machined aluminum rotors and TPU tires mounted to the folded-up chassis, it was off to the races, albeit slowly. The lack of torque from the motors and the light w...
10:48
Windows 11, Tesla, Ubuntu, and macOS hacked at Pwn2Own 2023 SoylentNews
Windows 11, Tesla, Ubuntu, and macOS hacked at Pwn2Own 2023:
On the first day of Pwn2Own Vancouver 2023, security researchers successfully demoed Tesla Model 3, Windows 11, and macOS zero-day exploits and exploit chains to win $375,000 and a Tesla Model 3.
The first to fall was Adobe Reader in the enterprise applications category after Haboob SA's Abdul Aziz Hariri (@abdhariri) used an exploit chain targeting a 6-bug logic chain abusing multiple failed patches which escaped the sandbox and bypassed a banned API list on macOS to earn $50,000.
The STAR Labs team (@starlabs_sg) demoed a zero-day exploit chain targeting Microsoft's SharePoint team collaboration platform that brought them a $100,000 reward and successfully hacked Ubuntu Desktop with a previously known exploit for $15,000.
Synacktiv (@Synacktiv) took home $100,000 and a Tesla Model 3 after successfully executing a TOCTOU (time-of-check to time-of-use) attack against the Tesla Gateway in the Automotive category. They also used a TOCTOU zero-day vulnerability to escalate privileges on Apple macOS and earned $40,000.
Oracle VirtualBox was hacked using an OOB Read and a stacked-based buffer overflow exploit chain (worth $40,000).
Last but not least, Marcin Wizowski elevated privileges on Windows 11 using an improper input validation zero-day that came with a $30,000 prize.
Throughout the Pwn2Own Vancouver 2023 contest, security researchers will target products in enterprise applications, enterprise communications, local escalation of privilege (EoP), server, virtualization, and automotive categories.
[...] After zero-day vulnerabilities are demoed and disclosed during Pwn2Own, vendors have 90 days to create and release security fixes for all reported flaws before Trend Micro's Zero Day Initiative publicly discloses them.
During last year's Vancouver Pwn2Own contest, security researchers earned $1,155,000 after hacking Windows 11 six times, Ubuntu Desktop four times, and successfully demonstrating three Microsoft Teams zero-days.
Previous:
Critical
Zoom Vulnerability Triggers Remote Code Execution Without User
Input
Work from
Home Pwn2Own Hackers Make $130,000 in 48 Hours from Windows 10
Exploits
...
10:42
Distribution Release: Slackel 7.6 "Openbox" DistroWatch.com: News
Slackel is a Linux distribution and live environment based on Slackware Linux and Salix OS. The project has published a new version, Slackel 7.6 "Openbox". The project's release announcement offers the following insights: "Slackel 7.6 "Openbox" has been released. It is more than a year since the....
10:00
Inside Digital Image Chips Hackaday

Have you ever thought how amazing it is that every bit of DRAM in your computer requires a teeny tiny capacitor? A 16 GB DRAM has 128 billion little capacitors, one for each bit. However, thats not the only densely-packed IC you probably use daily. The other one is the image sensor in your camera, which is probably in your phone. The ICs have a tremendous number of tiny silicon photosensors, and [Asianometry] explains how they work in the video you can see below.
The story starts way back in the 1800s when Hertz noticed that light could knock electrons out of their normal orbits. He couldnt explain exactly what was happening, especially since the light intensity didnt correlate to the energy of the electrons, only the number of them. It took Einstein to figure out what was going on, and early devices that used the principle were photomultiplier tubes, which are extremely sensitive. However, they were bulky, and an array of even dozens of them would be gigantic.
07:58
NCA infiltrates the cybercriminal underground with fake DDoS-for-hire sites Security Affairs
The U.K. National Crime Agency (NCA) revealed that it has set up a number of fake DDoS-for-hire sites to infiltrate the online criminal underground.
The UK National Crime Agency announced it has infiltrated the online criminal marketplace by setting up several sites purporting to offer DDoS-for-hire services.
DDoS-for-hire or booter services allows registered users to launch order DDoS attacks without specific knowledge.
While the NCA-run sites were up and running, they have been accessed by several thousand people, whose registration data were obtained by the investigators. The UK authorities will contact registered users that are based in the UK and warn them about engaging in cyber crime. Information relating users that are based overseas is being passed to international law enforcement.
All of the NCA-run sites, which have so far been accessed by around several thousand people, have been created to look like they offer the tools and services that enable cyber criminals to execute these attacks, reads the announcement. However, after users register, rather than being given access to cyber crime tools, their data is collated by investigators.
The activity is part of a coordinated international operation named Operation Power Off that is targeting DDoS-for-hire infrastructures worldwide.

In December, the U.S. Department of Justice (DoJ)...
07:00
How Much Programming Can ChatGPT Really Do? Hackaday

By now weve all seen articles where the entire copy has been written by ChatGPT. Its essentially a trope of its own at this point, so we will start out by assuring you that this article is being written by a human. AI tools do seem poised to be extremely disruptive to certain industries, though, but this doesnt necessarily have to be a bad thing as long as they continue to be viewed as tools, rather than direct replacements. ChatGPT can be used to assist in plenty of tasks, and can help augment processes like programming (rather than becoming the programmer itself), and this article shows a few examples of what it might be used for.
06:06
Benefits of Big City Life Only for the Elite SoylentNews
Urban inequality in Europe and the United States is so severe that urban elites claim most of the benefits from the agglomeration effects that big cities provide, while large parts of urban populations get little to nothing:
In recent years, researchers from across disciplines have identified striking and seemingly universal relationships between the size of cities and their socioeconomic activity. Cities create more interconnectivity, wealth, and inventions per resident as they grow larger. However, what may be true for city populations on average, may not hold for the individual resident.
"The higher-than-expected economic outputs of larger cities critically depend on the extreme outcomes of the successful few. Ignoring this dependency, policy makers risk overestimating the stability of urban growth, particularly in the light of the high spatial mobility among urban elites and their movement to where the money is", says Marc Keuschnigg, associate professor at the Institute for Analytical Sociology at Linkping University and professor at the Institute of Sociology at Leipzig University.
[...] An individual's productivity depends on the local social environments in which they find themselves in. Because of the greater diversity in larger cities, skilled and specialized people are more likely to find others whose skills are complementary to their own. This allows for higher levels of productivity and greater learning opportunities in larger cities.
But, not everyone can access the productive social environments that larger cities provide. Different returns from context accumulate over time which gives rise to substantial inequality.
[...] Consequently, the initially successful individuals in the bigger cities increasingly distanced themselves from both the typical individual in their own city, creating inequality within the big cities, and the most successful individuals in smaller cities, creating inequality between cities.
Read more of this story at SoylentNews.
04:36
FreeBSD 13.2-RC4 Released With Fixed Suspend/Resume For Some Laptops Phoronix
FreeBSD 13.2-RC4 is now available with a few more fixes for this BSD operating system update. A FreeBSD 13.2-RC5 release is also inbound as an extra release candidate with one more bug fix, after which the stable release should happen...
04:09
Are ad-driven business models bad? Geeking with Greg
There's been a lot of discussion that ad-driven business models are inherently exploitative and anti-consumer. I think that's both wrong and not a helpful way to look at how to fix the problems in the tech industry.
I think the problem with ad-driven models is that it's easy and tempting for executives to use short-term metrics and incentives like clicks or engagement. It's the wrong metric and incentives for teams. But I think the problem is more ignorance, or willful ignorance, of that issue. In the short-term, for an ad-supported product, ad revenue and profitability does look like ad clicks. In the long-term, ad profitability looks like converting performing ads for advertisers over the lifetime of customers. Those are quite a bit different. With subscription-driven models, it's more obvious that your metrics should be long-term. With ad-driven models, long-term metrics are harder to maintain, and many execs don't realize they need to. If execs let teams optimize for clicks, they eventually find those clicks have long-term costs as customers start leaving, but unfortunately it's quite costly to reverse the damage once you're far down this path. In the long-term, I think you can improve the profitability of an ad-driven platform by making the content and ads work better for customers and advertisers (raising ad spend, increasing ad competition for the space, and reducing ad blindness) and by retaining customers longer (along with recruiting new customers). That looks a lot like the strategy for increasing the profitability of a subscription-driven platform. So I don't see much of a difference between ad-supported and subscription-supported business models other than the temptation for executives to inadvertently optimize for the wrong thing.04:00
Gordon Moore, 1929 2023 Hackaday

The news emerged yesterday that Gordon Moore, semiconductor pioneer, one of the founders of both Fairchild Semiconductor and Intel, and the originator of the famous Moores Law, has died. His continuing influence over all aspects of the technology which makes our hardware world can not be underestimated, and his legacy will remain with us for many decades to come.
A member of the so-called Traitorous Eight who left Shockley Semiconductor in 1957 to form Fairchild Semiconductor, he and his cohort laid the seeds for what became Silicon Valley and the numerous companies, technologies, and products which have flowed from that. His name is probably most familiar to us through Moores Law, the rate of semiconductor development he first postulated in 1965 and revisited a decade later, that establishes a doubling of integrated circuit component density every two years. Its a law that has seemed near its end multiple...
03:42
Links 25/03/2023: Gordon Moore (of Moores Law) is Dead Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Desktop/Laptop
-
CNX Software Framework modular laptop adds Intel Raptor Lake, AMD Ryzen motherboards, 16-inch laptop frame
When we first covered the Framework modular laptop in 2021 it came with a choice of 11th generation Intel Tiger Lake Core processors, up to 64GB RAM, up t...
-
-
03:34
Theo de Raadt at CanSecWest: Synthetic Memory Protections OpenBSD Journal
We recently reported
that Theo de Raadt (derradt@) was scheduled to present
at CanSecWest. That's now
happened, and slides of Theo's
presentation, Synthetic Memory Protections, can be found in
the usual place.
Video is available on
the bird site.
02:44
Pwn2Own Vancouver 2023 awarded $1,035,000 and a Tesla for 27 0-days Security Affairs
On the third day of the Pwn2Own Vancouver 2023 hacking contest, the organization awarded $185,000 for 10 zero-day exploits.
Pwn2Own Vancouver 2023 is ended, contestants disclosed 27 unique zero-days and the organization awarded a total of $1,035,000 and a Tesla Model 3. The team Synacktiv (@Synacktiv) (Benoist-Vanderbeken, David Berard, Vincent Dehors, Tanguy Dubroca, Thomas Bouzerar, and Thomas Imbert) won the competition, they earned 53 points, $530,000, and a Tesla Model 3.
On the third day, contestants were awarded $185,000 after demonstrating 5 zero-day exploits targeting the Ubuntu Desktop, Windows 11, and the VMware Workstation software.
The day began with the hack of Ubuntu Desktop by Kyle Zeng from ASU SEFCOM, he used a double-free bug and earned $30,000 and 3 Master of Pwn points.
Thomas Imbert (@masthoon) from Synacktiv (@Synacktiv) used a UAF against Microsoft Windows 11. They earn $30,000 and 3 Master of Pwn points.
The researchers Mingi Cho of Theori used a UAF against Ubuntu Desktop, the team earned $30,000 and 3 Master of Pwn points.
The STAR Labs (@starlabs_sg) team used an uninitialized variable and UAF to hack the VMWare Workstation virtualization software. They earned $80,000 and 8 Master of Pwn points. The STAR Labs team also attempted to demonstrate an exploit against Microsoft Teams, but failed to do it within the time allotted.
Bien Pham (@bienpnn) from Qrious Security successfully targeted Ubuntu Desktop, but used a known exploit, for this reason, the attempt was c...
02:23
Flying taxi service coming to Chicago using eVTOL aircraft Lifeboat News: The Blog
In the latest sign of growing interest in the flying taxi sector, United Airlines and air mobility startup Archer Aviation have announced an upcoming service for hops between downtown Chicago and OHare International Airport.
The service will offer a sustainable, low-noise, and cost-competitive alternative to ground transportation for folks traveling to and from the airport, United and Archer said in a release.
02:23
The Personalized Stem Cells That Could One Day Treat Parkinsons and Heart Failure Lifeboat News: The Blog
Could an injection of lab-cultured brain cells, created from a persons own cells, reverse symptoms of Parkinsons disease? Thats an idea that Aspen Neuroscience Inc., a startup based in San Diego, plans to test in human trials later this year.
In patients with Parkinsons, neurons die and lose the ability to make the chemical dopamine, leading to erratic, uncontrollable movements. Aspen Neuroscience will test if the newly injected cells can mature into dopamine producers, stopping the debilitating symptoms of this incurable disease, says Damien McDevitt, the companys chief executive officer. Tests in animals have shown promise, the company says.
02:22
People And Machines Will Merge Sooner Or Later Lifeboat News: The Blog

The idea of the technological singularity was inspired by how ubiquitous and invasive AI is becoming. As they combine thought and machine, recent advanceme
01:20
Moderna CEO Brazenly Defends 400% COVID Shot Price Hike, Downplays NIH's Role SoylentNews
In congressional testimony Wednesday, Moderna CEO Stphane Bancel unabashedly defended the company's plans to raise the US list price of its COVID-19 vaccines by more than 400 percentdespite creating the vaccine in partnership with the National Institutes of Health, receiving $1.7 billion in federal grant money for clinical development, and making roughly $36 billion from worldwide sales.
Bancel appeared this morning before the Senate's Health, Education, Labor, and Pensions committee, chaired by Sen. Bernie Sanders (I-Vt.), who has long railed at the pharmaceutical price gouging in the US and pushed for policy reforms. After thanking Bancel for agreeing to testify, Sanders didn't pull any punches. He accused Moderna of "profiteering" and sharing in the "unprecedented level of corporate greed" seen in the pharmaceutical industry generally.
[...]
Early doses were priced between $15 to $16, while the government paid a little over $26 for the updated booster shots. When federal supplies run out later this year and the vaccines move to the commercial market, Moderna will set the list price of its vaccine at $130."This vaccine would not exist without NIH's partnership and expertise, and the substantial investment of the taxpayers of this country," Sanders summarized. "And here is the thank you that the taxpayers of this country received from Moderna for that huge investment: They are thanking the taxpayers of the United States by proposing to quadruple the price of the COVID vaccine."
Read more of this story at SoylentNews.
01:00
A LEGO Camera You Just Might Own Yourself Hackaday

A camera makes for an interesting build for anyone, because its an extremely accessible technology that can be made from materials as simple as cardboard. More robust cameras often require significant work, but what if you could make a usable camera from LEGO? Its a project taken on by [Zung92], who hasnt simply made a working 35 mm camera from everyones favorite construction toy hes also managed to make it exude retro style. Best of all, you can vote for it on the LEGO Ideas website, and you might even get the chance to have one for yourself.
Frustratingly theres little in the way of in-depth technical detail on the Ideas website, but he does mention that it was a challenge to make it light proof. Even the lens is a LEGO part, and if diffraction-based photography isnt for you theres also a pinhole option. We look forward to seeing this camera progress, and we hope well see it advance to becoming a LEGO Ideas kit.
This is an extremely polished design, but surprisingly, its not our first LEGO camera.
Thanks [Michael] for the tip.
00:43
Internet Archive is Liable for Copyright Infringement, Court Rules TorrentFreak
 In 2020, publishers Hachette, HarperCollins, John Wiley
and Penguin Random House
sued the Internet Archive (IA) for copyright infringement,
equating its Open Library to a pirate site.
In 2020, publishers Hachette, HarperCollins, John Wiley
and Penguin Random House
sued the Internet Archive (IA) for copyright infringement,
equating its Open Library to a pirate site.
IAs library is operated by a non-profit organization that scans physical books and then lends the digital copies to patrons in an ebook format.
While digital book lending is not uncommon, libraries typically loan out DRM-protected files after acquiring a license from publishers. In this case, IA sent physical books it owned to a scanning facility and made its own copies.
Fair Use or Mass Copyright Infringement?
These digital copies were subsequently loaned out to patrons, with IA ensuring that only one person at a time could access a single digital copy of a single physical book.
IA previously sought summary judgment in its favor, arguing that a digital copy of a physical book transforms the original work, with lending limits and the absence of profit also supporting a finding of fair use.
In contrast, the publishers described IAs library as a rogue operation engaging in willful mass copyright infringement. Claiming direct damage to their bottom line, the publishers lawsuit aimed to put an end to the illegal lending program once and for all.
The publishers went on to request summary judgment and a declaration that this type of copying is a clear case of copyright infringement.
Opinion and Order
Earlier this week, the parties had the opportunity to back up their arguments during a New York Court hearing. District Court Judge John Koeltl questioned both sides on their summary judgment requests, before deliberating on his final decision.
After weighing the arguments. Judge Koeltl published his opinion and order yesterday. His order clearly sides with the publishers, whose request for summary judgment was granted. IAs fair use defense and summary judgment in its favor was denied.
...Saturday, 25 March
23:50
Lenovo Flex 5G / Qualcomm SC8180x Support Being Worked On For Mainline Linux Phoronix
In addition to the mainline Linux kernel seeing recent support for the Arm-powered Lenovo ThinkPad X13s and Lenovo Yoga C630, among others, another Lenovo model working toward mainline kernel support is the Lenovo Flex 5G...
23:46
Links 25/03/2023: Decade of Docker, Azure Broken Again Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
22:35
AI Researcher Goaded Chat GPT to Attempt to Jailbreak Itself and Access the Internet cryptogon.com
It wrote a Python script for Kosinski to run on his computer that would have passed data into the system via the API. Its all fun and games until someone loses an eye. Via: inews: Concerns have been raised about the extent of artificial intelligence GPT-4s power to take over computers after the AI chatbot []
22:22
Quantum Computers Vs Supercomputers Lifeboat News: The Blog
Supercomputers and quantum computers are potent tools for handling difficult calculations, problem-solving, and data analysis. Although they both have the potential to transform computing technology, their speeds and capacities differ greatly.
Supercomputers quickly process massive volumes of data to provide a single result using a conventional computing strategy with numerous processors. These computers are the most powerful in terms of raw computing speed, but they can only do one task at a time, and Moores Law places a cap on how much data they can process (the principle that computer processor speeds double every two years).
Quantum computers, on the other hand, utilize laws of quantum mechanics to process information in ways that regular computers cannot, resulting in vastly higher processing speeds. They can manage several activities at once and take on challenging issues that would take supercomputer months to resolve. Yet, because of their great sensitivity to temperature fluctuations and need for isolation from outside influences, quantum computers require more upkeep than their conventional equivalents.
22:17
Microsoft's CBL-Mariner Linux Distribution Continues Cultivating More Packages Phoronix
Microsoft's in-house Linux distribution that they make public, CBL-Mariner, began with a very niche focus while over time has continued adding additional packages as it is worked into becoming a more robust Linux platform...
22:03
In Memoriam: Gordon Moore, 1929 - 2023 SoylentNews
In Memoriam: Gordon Moore, 1929 - 2023:
With great sadness, the Gordon and Betty Moore Foundation announces the passing of our founder, Gordon Moore.
With his characteristic humility and word economy, Gordon Moore once wrote "my career as an entrepreneur happened quite by accident." A brilliant scientist, business leader and philanthropist, Gordon co-founded and led two pioneering technology enterprises, Fairchild Semiconductor and Intel, and, with his wife, Betty, created one of the largest private grantmaking foundations in the U.S., the Gordon and Betty Moore Foundation.
He may argue that his career as an entrepreneur happened by accident, but his world-changing contributions did not. Never one to trumpet his own accomplishments, Gordon wasn't able to dissuade others from celebrating his wide and long-reaching legacy: the revolutionary technologies and breakthroughs, a long and generous history of philanthropy, and the very culture of experimentation, invention and relentless progress that now defines Silicon Valley.
It took decades for Gordon to be able to speak with a straight face of his eponymous "Moore's Law," the prophetic 1965 observation that became a cornerstone principle of innovation and driving force for the exponential pace of technological progress in the modern world. Gordon later observed that he had looked it up and was pleasantly surprised to find more references on the internet to "Moore's Law" than to "Murphy's Law."
Dubbed a "quiet revolutionary" by his biographers, Gordon always worked in the absence of any pretense or desire for recognition, driven instead by an exceptional curiosity, generosity and unassuming commitment to hard work.
Gordon was always a visionary. Even at the start of his career, he keenly recognized the impact that the technologies he was developing would have on the world. And at an industry event in 1979, he told an Intel audience: "We are bringing about the next great revolution in the history of mankind the transition to the electronic age." (Moore's Law, Thackray, Brock and Jones).
Although Gordon was reluctant to spotlight his own contributions, his biographers have been less reticent about attribution. Gordon is simply, they argue, "the most important thinker and doer in the story of silicon electronics."
Read more of this story at SoylentNews.
22:00
Clever Mechanism Powers This All-Mechanical Filament Respooler Hackaday

No matter how far down the 3D printing rabbit hole we descend, chances are pretty good that most of us wont ever need to move filament from one spool to another. But even so, youve got to respect this purely mechanical filament respooler design, and you may want to build one for yourself just because.
We were tipped off to [Miklos Kiszely]s respooler via the very enthusiastic video below from [Bryan Vines] at the BV3D YouTube channel. He explains the need for transferring filament to another spool as stemming from the switch by some filament manufacturers to cardboard spools for environmental reasons. Sadly, these spools tend to shed fibrous debris that can clog mechanisms; transferring filament to a plastic spool can help mitigate that problem.
The engineering that [Miklos] put into his respooler design is pretty amazing. Bearings excepted, the whole thing is 3D printed. A transmission made of herringbone gears powers both the take-up spool and the filament guide, which moves the incoming filament across the width of the spool for even layers. The mechanism to do this is fascinating, consisting of a sector gear with r...
21:53
MidnightBSD 3.0 Available With Many Software Updates & Fixes Phoronix
MidnightBSD as the desktop-focused OS forked from FreeBSD and relying on the Xfce desktop environment by default is out with its big MidnightBSD 3.0 update...
21:25
AMD Sends Out Patches For Enabling New Graphics IP Blocks (NBIO 7.9, GMC 9.4.3) Phoronix
AMD on Friday sent out new patches for enabling some new graphics IP "blocks" as part of their block-by-block enablement strategy they've been using to introduce new GPU support to their Linux graphics stack by focusing on smaller patch series with versioned parts of the GPU rather than big monolithic patch series with colorful fishy codenames...
21:00
Casinos Not On Gamestop Experiment: Good Or Bad? h+ Media
Casinos Not On Gamestop Experiment: Good Or Bad?
Below are the principle markets that punters can find on an LA Lakers online sportsbook. Now, eSport sites must purchase licenses of operation and in addition go the extra mile to cushion the personal information of their users from the unhealthy guys on the internet. Well, if you have ever placed bets on sports similar to football, tennis, horse racing, and golf, then you have already got a touch about how eSports betting works. In reality, betting on eSports is very a lot much like playing on common sports activities.
The process may be carried out on the net site and within the official app. After that, an e mail might be despatched to your mail confirming the profitable creation of an account. Remember to activate your account by clicking on the hyperlink on this letter.
You may wager at MELbet with confidence, understanding that your money is protected and that the video games are not manipulated. Even first-time bettors will have the ability to join up in a matter of minutes after finishing the form. There are a couple of steps to take, but dont let that overwhelm you. In any event, if there are problems joining up, gamers may contact the customer service team for assistance. Players must deposit no a lot less than 2150 INR, full their profile, and wager the entire deposit amount on an occasion with odds of a minimum of 1.50 to qualify for the free guess.
The company supplies lots of 1xBet promo code 2023 that will impress even demandable purchasers. Comparing with the rivals, 1xBet promo can boast its trustworthiness and alluring bonuses. Unfortunately, this is not attainable this bonus code is reserved for brand spanking new prospects who have not yet opened an account at the website. As the code is hooked up to the 1xbet Welcome Bonus, its offered only to new clients of the site and is obtainable only as quickly as per customer . Bonus code, you presumably can be positive to get one of the best welcome bonus on offer at 1xbet dont miss out on this! To answer the question what is 1xBet and discover more details about this bookmaker, read our evaluate.
This bookmaker has a simple, glossy, and one of the friendliest web site designs out there. When navigating MelBets web site, rest assured of discovering everything that you really want quite fast. MelBets heat yellow and black colors are really easy on the eyes.
The Melbet app in Bangladesh helps well-liked deposit methods Perfect Money, Bkash, Sticpay, Astropay, Skrill, and Neteller. At Bet India, we solely advocate the best betting sites in India that meet these requirements so you dont should spend hours researching. Additionally, MLB gamblers can choose from numerous betting options, including participant futures, membership futures, moneylines, and props. Like many other sports activities, in cricket, you can guess not solely on the ultimate winner but add...
20:58
Water Pumps & Valves, Fans & Motors On-line Auckland Nz h+ Media
Water Pumps & Valves, Fans & Motors On-line Auckland Nz
Depending on a bookmaker to money out from, you may find that it permits you to cash out partially or fully. Partial money out is just going to return a share of what you initially invested. Then again, if you are fortunate, you might get all the money back for free with the full cash-out choice. Generally, if you see that youre going to lose the wager, that is when you must choose to cash out to scale back your losses.
If theres an space where MelBet actually units the bar, then it has to be its large vary of sports activities offerings . Are you a big online sports activities betting fan based mostly in New Zealand? If the reply is sure, then sports betting is an ideal method of boosting your bankroll when taking half in at MelBet.
Sir i have given all my paperwork however the safety group not replying since 9days..its been horrible and disappointing.as i cant withdraw with out documents verification If you wish to gamble on a protected and dependable platform, try Captain Cooks. This platform is licensed by eCOGRA and holds licenses from the UK playing fee. In this case, there are 2 bets which were mixed collectively, and the bets are Both Team to Score and Match Result.
Just as easily Melbet app free obtain on their devices. Melbet betting agency offers its users the popular on line casino card game poker. This is a good alternative not solely to study the mechanics of betting on Melbet, however moreover to get some additional winnings. The minimal deposit required to activate the bonus is Rs. seventy five.
This will allow gamblers to conduct transactions without friction and with flexibility. The casinos youll be able to choose from with $5 minimum deposit are quite many. With the luck on your facet and a budget of $5 you may have a chance to build up a bankroll to stay within the game for some time. You could make bigger bets and the potential winnings get higher. Believe it or not, soccer followers have updates about every little thing, the gamers, groups, coaches, managers, and contests. These folks even create on-line fan golf equipment which occur to be the source of all types of useful data for betting.
This one can get rid of the prospect of a draw in the soccer contest. Naturally, bettors should wager on the staff which will win- an underdog or a favorite. This sort of guess is helpful when you dont need the sport to complete with a tie. In the Totals guess, you are principally wagering on the upper or decrease score of the group in a contest. Your task is to predict and bet whether or not the staff will score over or underneath the number the sportsbook has decided.
There are greater than 100 slot games that shoppers can choose within the slots part. These are organized on the location based on the slots developed. This website screams enjoyable and friendly to entice prospects to keep on p...
20:57
New No Deposit Free Spins Australia Stebbings Automotive, Restoration And Fabrication h+ Media
New No Deposit Free Spins Australia Stebbings Automotive, Restoration And Fabrication
When utilizing this characteristic, you can expect instantaneous response with a polite and professional representative. Everything on the cellular website resembles what youll find when using the app. If either you choose to bet from the cellular website or using the app, you should not have any cause to fret since they are each fast. This makes them one of the best choices for all your betting wants while on the transfer, or when you arent using a computer.
For extra information or assist, use the links to your right. In India, sports betting apps are shortly choosing the tempo and becoming punters first choice to guess on their favorite sports activities and games. There are not any restrictions or central laws that forestall Indian punters from utilizing betting apps in the region.
Many 5 greenback deposit casinos NZ use this banking method as it is a very safe means of depositing money. This platform additionally has a $ 5 minimum deposit cellular on line casino compatible with Android, iPhone, Blackberry, and tablets. The platform has a great payout rate of ninety five.73%, giving you an excellent probability to make a good return out of your bankroll. Being multilingual is considered one of the most resourceful options of this platform. This platform supports English, German, Italian, French, and Spanish. If you are not swept off your feet, then the banking flexibility could just do that.
It means that as soon as you log in and earlier than you make a deposit, you get numerous free spins to check out the games. But understand that these bonuses come with playthrough requirements. With a great Montreal casino on-line real wins are possible and your cash can stretch a lot additional, and this Sunpura Casino overview of the reside vendor video games will prove it. Other than getting Blackjack from the bounce, but ultimately it has made the game practically unimaginable to beat for anybody not outfitted and proficient with their very own HUDs. The most important factor is that you know how to say 1xbet promo codes and purchase a quantity of bonuses sooner or later.
You must redeem the bonus inside 30 days of registration. Otherwise, the bonus and all winnings made from the bonus will be revoked. Casinobonusesfinder.co.nz must evaluation the security of your connection earlier than continuing. Bet and get place a bet and get a free wager of a special value to the actual money stake, usually as twice your preliminary stake. Bookmakers present their registration provides in some ways but one can find it simple as she or he indicators up to claim the designated bonus.
However, there are different excellent 1xBet offers you should try. Even so, offers from different bookies such as the Betsafe new buyer supply are worthy of your consideration. You will solely receive the bonus after creating an account, verifying...
20:55
22 Underdogs Ideas Underdog, Inspirational People, History h+ Media
22 Underdogs Ideas Underdog, Inspirational People, History
Operators similar to DraftKings can still supply promos of this nature, although only via their own websites. Check genuine buyer evaluations and scores from unbiased platforms. However, essentially the most famous buyer assistance choice is the reside chat device, which bettors can find at the bottom proper of the MELbet website. Youll uncover a chatbox with the name of the support personnel and the choice to rate them depending on your experience. NetEnt, Microgaming, Red Tiger Gaming, and Betsoft are among the many sport suppliers.
It shall be very inconvenient for bettors in the event that they cant attain out to the customer support staff through telephone, e-mail, or live chat. Even if a web site has essentially the most informative Frequently Asked Questions part, it wont be succesful of remedy any real-time downside the customers are having. William Hill often has enhanced odds at no cost on most of its sports activities matches. Having mentioned that, you should seek out the most effective promotions offered on different platforms and attempt to assert those that are more rewarding. There is no point in staying loyal to 1 bookie when other bookies are presenting higher deals and promos.
Read phrases and situations before doing anything, as you need to keep away from any pointless confusion attributable to poor information and understanding of the system. Reading this complete guide helps getting began, understanding the fundamentals and receiving basic pointers. Points not earned on sale gadgets, donations or reward playing cards.
As lengthy as you are signed as a lot as one of the best football betting app and have funds in your account, you can simply click on the wager you need. Claim any free bets obtainable, enter the quantity you want to gamble, and then place the bet. In fact, the extra credible the sports betting platform is, the larger the range of its markets. When you would possibly be searching for odds, you will definitely notice the differences between one of the best and the typical bookies.
For more info or assist, use the links to your proper. In India, sports betting apps are quickly picking the pace and changing into punters first choice to bet on their favourite sports and games. There are no restrictions or central legal guidelines that prevent Indian punters from utilizing betting apps in the region.
This section is entirely dedicated to video games, with out mentioning which our Melbet consider may be faraway from being accomplished. In this section, yow will uncover card video games much like poker and 21, slots, Wheel of Fortune in several variants, roulette, and one other electronic video video games. The left-hand aspect has a list of sports, the middle has crucial betting markets, and the highest half has the wager kind with a wide selection of adverts. Melbet India rewards you if you contribute...
20:35
Habitual Daily Intake of a Sweet and Fatty Snack Modulates Reward Processing in Humans SoylentNews
Why we can't keep our hands off chocolate bars and co.:
Chocolate bars, crisps and fries - why can't we just ignore them in the supermarket? Researchers at the Max Planck Institute for Metabolism Research in Cologne, in collaboration with Yale University, have now shown that foods with a high fat and sugar content change our brain: If we regularly eat even small amounts of them, the brain learns to consume precisely these foods in the future.
[...] To test this hypothesis, the researchers gave one group of volunteers a small pudding containing a lot of fat and sugar per day for eight weeks in addition to their normal diet. The other group received a pudding that contained the same number of calories but less fat. The volunteer's brain activity was measured before and during the eight weeks.
The brain's response to high-fat and high-sugar foods was greatly increased in the group that ate the high-sugar and high-fat pudding after eight weeks. This particularly activated the dopaminergic system, the region in the brain responsible for motivation and reward. "Our measurements of brain activity showed that the brain rewires itself through the consumption of chips and co. It subconsciously learns to prefer rewarding food. Through these changes in the brain, we will unconsciously always prefer the foods that contain a lot of fat and sugar," explains Marc Tittgemeyer, who led the study.
Journal paper highlights:
- Daily consumption of a high-fat/high-sugar snack alters reward
circuits in humans
- Preference for low-fat food decreases while brain response to
milkshake increases
- Neural computations that support adaptive associative learning
are also enhanced
- Effects are observed despite no change in body weight or
metabolic health
Journal Reference:
Sharmili Edwin Thanarajah, Alexandra G. DiFeliceantonio, Kerstin
Albus, et al., Habitual daily intake of a sweet and
fatty snack modulates reward processing in humans [open],
Cell Metabolism, 2023, ISSN 1550-4131, https://doi.org/10.1016/j.cmet.2023.02.015
Read more of this story at SoylentNews.
19:52
U.K. National Crime Agency Sets Up Fake DDoS-For-Hire Sites to Catch Cybercriminals The Hacker News
In what's a case of setting a thief to catch a thief, the U.K. National Crime Agency (NCA) revealed that it has created a network of fake DDoS-for-hire websites to infiltrate the online criminal underground. "All of the NCA-run sites, which have so far been accessed by around several thousand people, have been created to look like they offer the tools and services that enable cyber criminals to
19:48
[Meme] Money Deducted in Payslips, But Nothing in Pensions Techrights
Summary: Sirius Open Source has stolen money from staff (in secret)
19:19
Profitable India Betting On-line On Reputed Website 1xbet h+ Media
Profitable India Betting On-line On Reputed Website 1xbet
This process must be done by visiting the 1xBet main website. 1xBet has made certain that an revolutionary set of options can be found for these who wish to guess on the various video games. The first of the progressive selections would involve cryptocurrency funds, as the likes of bitcoin are supported. For those who wish to use the normal means of creating funds, the channels out there are Skrill, NETELLER, EcoPayz, Qiwi, and more.
We will inform you tips on how to deal with this problem, however first its worth mentioning that your iOS version must be no less than iOS 9.three to use the app properly. Click the Android button if you are an Android system user. Congratulations, you at the second are a full-fledged 1xBet person, all you should keep in mind your username and password. If there is a problem with this, the site automatically remembers your information and you dont have to continually take into consideration login and password. We also review one of the best sites for Indian punters to play at. Moreover, the bonus doesnt work if youre using cryptocurrencies, however thats the identical old story for many bonuses right here.
Plus, you possibly can easily make deposits and withdrawals utilizing in style strategies like Paytm, Google Pay, and UPI. Thats why weve named 7Cric as our Online Casino of the Month. At 7Cric, were devoted to making positive that our site is the go-to alternative for Indian players.
So, when you determine on becoming a member of the bookmaker and taking half in on the 1xBet web site, you need to do a couple of simple actions. They embody creating an account, logging in, choosing a sports activities match for betting or a on line casino recreation for playing, and begin having fun with the method. As for other entertainment, the positioning presents profitable slots online free on line casino from famed 1xBetbookmaker. The main advantage right here is that you can play in demo mode without using your individual funds. The alternative the best bookmaker is a assure that sports activities bets will bring you really good earnings.
This software is based on dynamic programming and is extensively considered one of the best algorithms for cricket match predictions. Choose your most well-liked fee possibility and input the amount of cash you wish to guess with . Choosing a betting website shouldnt be one thing you do without correct analysis. There are lots of of online sportsbooks out there, and we want that we are in a position to say that each one of them are good.
The 1xbet cellular utility is user-friendly, making it straightforward for Indian customers to navigate and place bets. The app is out there on both iOS and Android devices, and it presents a seamless expertise, making it simple for customers to search out their most popular sports activities and occasions....
19:17
Is 1xbet Banned In India Up To Date In 2023 March h+ Media
Is 1xbet Banned In India Up To Date In 2023 March
The 1xbet mobile application is user-friendly, making it simple for Indian users to navigate and place bets. The app is available on each iOS and Android devices, and it provides a seamless expertise, making it simple for users to search out their preferred sports activities and occasions. 1xBet India additionally provides its customers a range of stay betting and streaming choices.
The sports activities menu comes in the type of a side-scrolling listing that is displayed on the high of the betting menu, so it could all the time be accessed. In our opinion, this isnt essentially the most user-friendly approach to navigate a sports activities betting menu. 1xBet has a stay casino section that provides a broad range of game kinds. These games might be performed with a stay supplier to provide a true casino experience, and Indian gamers prefer games with Hindi-speaking stay dealers. 1xBet features a variety of deposit and withdrawal methods which are generally utilized by customers from India.
To do that, click on its icon in the principle menu of your cellular device. Also within the software, everlasting and occasion promos are available. For example, you can win a car in the Grand Slam promotion or free bets in the Big Bash!
In truth, we counted 133 different ways to deposit money into your account. Importantly, the live betting opportunities never cease, with markets out there around the clock. Match stats are posted live so youll find a way to observe the action, whereas some events are even streamed reside. The intensive alternative offered by 1XBet India additionally extends to their live betting where theres a bumper number of markets. When it involves offering nice odds, 1XBet is amongst the finest. There is always a worry that an unfamiliar betting website wont be 100% respectable, and some bad critiques can add to this sense.
1x Bet is a extremely good gambling website in India with amazing sports activities betting and online casino sections. Indian players can declare many casinos, and sports bonuses like the first deposit bonus of 20,000 and as much as 100 percent promo matches, TV Bet Accumulators and rather more. The primary function of 1x guess service is stay betting with sports activities occasions going down in real-time.
1xbet line safer bets that allow you to think twice before making a prediction. This part includes events which are nearly to begin. They start at totally different times, however at all times sooner or later, i.e. in a few minutes, hours or days. To start inserting bets at 1xbet you need to create your account, full the verification process and make your first deposit. A free app that can make your betting life easier definitely deserves your consideration. Im glad that apps of such a cool stage are already out there here.
The model provides a chance to bet on a number of cricke...
19:16
1xbet Promo Code India 2023 Vip Bonus h+ Media
1xbet Promo Code India 2023 Vip Bonus
In this Sportscafe review, well go through the completely different options and functionalities that 1xBet provides to Indian prospects. Our record of prime on line casino video games in India, play on line casino video games demo in enjoyable mode and each time you are prepared, play for real money. The MIB sends letters to particular person gamers as and when a violation is dropped at its notice. Offshore on-line betting platforms Fairplay, PariMatch, Betway, Wolf 777, and 1xBet have been advertising on TV and digital platforms via surrogate information websites. Sometimes, punters prefer certain forms of bets over others when putting wagers in on-line bookmakers. If theres data out there on wagering trends for the match were reviewing, well let you know what the public thinks.
1xBet India operates with a license issued by the Government of Curacao and is thus authorized in India. Indian legislation doesnt prohibit betting or gambling in India. However, gamers should seek the guidance of their native legal guidelines and rules before using 1xBet India services. 1xBet India also offers its customers a number of bonus programs, together with welcome bonuses, loyalty factors, free bets, and more. If you like to guess on cricket and also take pleasure in wagering on other sports, few bookmakers will give the selection that you can see on 1XBet.
The only drawback is the attack, where there are not any main world football celebrities. However, the star midfielders more than compensates for this. On the positioning at the bottom of the web page there is an option to alter one or one other kind 1xbet betting odds.
You wont find the chances of two.00 on one bookie and four.00 on one other. Instead, the distinction might be zero.1 or zero.2 in most cases. Still, if the percentages are higher at a given betting website, we are going to ensure to deliver your consideration to it in our online betting tips. After fulfilling the basic requirements of the bookmakers workplace, the player will want to make a deposit. Remember that the upper the deposit amount, the larger the reward.
Keep in thoughts that only people who have reached the age of 18 years can register at such betting corporations. In addition, a choice of two completely different bonuses shall be obtainable to you directly within the registration type, nonetheless, you can even choose them later. You may read the detailed directions on how to enroll on the 1xBet website below.
Second, to that is the tremendous quantity of fee options and the wide range of events and activities on which you can guess. Although essentially the most accountable approach to gamble at 1xbet India is not to gamble there at all, the site does offer basic self-exclusion options. Unfortunately, the on line casino has allegedly used these self-exclusion options to set off a pressured cease for some players acco...
19:14
1xbet Evaluation For Indian Users h+ Media
1xbet Evaluation For Indian Users
There is a lot going for this model and customers are unlikely to make the mistake of going with 1xBet registration when attempting to guess on cricket matches. Launched in 2007, 1xBet is an online on line casino thats operated by the corporate Exinvest Limited based in Cyprus. Theyre one of many greatest betting sites youll be able to encounter in India, with an nearly overwhelming array of betting choices and on line casino video games. 1xbet app download could be easily done via their official page.
This is a welcome bonus offer from 1xbet, designed for on line casino entertainment. You can get up to 1,500 + 150 Free Spins on the most effective casino slots after your first deposit at 1xBet. To get it, you must agree to receive the bonus within the Account Settings tab. 1xBet India additionally offers phone assist to its clients.
1xBet India also presents gamers the choice to sign off with a single click. Players can deposit 1xBet India by deciding on their most popular payment technique, entering the quantity they wish to deposit, and clicking on the Deposit button. 1xBet India accepts deposits in a number of currencies, including Indian Rupees , US Dollars , and more.
1x Bet is a really good gambling website in India with wonderful sports activities betting and online on line casino sections. Indian gamers can claim many casinos, and sports activities bonuses like the first deposit bonus of 20,000 and as a lot as one hundred pc promo matches, TV Bet Accumulators and far more. The primary characteristic of 1x guess service is live betting with sports events going down in real-time.
By the best way, our research reveals that reside streaming is of good high quality and obtainable to all users free of charge. 1xbet is completely different in that cricket betting could be carried out in euros, dollars, Indian rupees, and other currencies. The Curacao-licensed firm can provide a extensive range in deciding on outcomes on high matches, as nicely as betting on the athletes stats. The common margin in each pre-match and in-play is 6-7%.
The app also has the identical functions because the desktop version, so you wont be losing out on anything. Bet India is not a betting site and we do not settle for fee from players in any form. Bet India doesnt endorse or promote unlawful gambling practices. Basically, each Friday any 1xBet person can receive a bonus of EUR . The bonus is counted as 100 percent of this quantity, however not more than one hundred EUR. This money have to be used on sports activities playing, and you cant obtain more than one.
However, not all betting websites settle for all of these methods, and a few may have completely different deposit and withdrawal limits than others. The Indian Premier League is the top-tier Twenty20 cricket league in India and some of the renowned cricket leagues on the planet. Since Crictips...
19:00
Digitizing Sound On An Unmodified Sinclair ZX81 Hackaday

Whatever the first computer you used to manipulate digital audio was, the chances are it came with dedicated sound hardware that could play, and probably record, digitized audio. Perhaps it might have been a Commodore Amiga, or maybe a PC with a Sound Blaster. If you happen to be [NICKMANN] though, you can lay claim to the honor of doing so on a machine with no such hardware, because he managed it on an unmodified Sinclair ZX81.
For those of you unfamiliar with the ZX, it embodied Clive Sinclairs usual blend of inflated promises on minimal hardware and came with the very minimum required to generate a black-and-white TV picture from a Zilog Z80 microprocessor. All it had in the way of built-in expansion was a cassette interface, 1-bit read and write ports exposed as 3.5 mm jacks on its side. Its these that in an impressive feat of hackery he managed to use as a 1-bit sampler with some Z80 assembler code, capturing a few seconds of exceptionally low quality audio in an 81 with the plug-in 16k RAM upgrade.
From 2023 of course, its about as awful as audio sampling gets, but in 1980s terms its pulling off an almost impossible feat that when we tried it with a 1-bit PC speaker a few years later, we didnt succeed at. Were impressed....
18:25
Alzheimers first signs may appear in your eyes, study finds Lifeboat News: The Blog
Finding early signs of dementia in the back of the eye may be a way to catch the disease early and start preventive treatment, a study says.
18:25
18:25
Highest-Order Electromagnetic Transition Observed Lifeboat News: The Blog
Observations deliver evidence of an exotic sixth-order electromagnetic transition in the gamma-ray emission of an iron isotope, a finding that could provide new ways to test nuclear models.
18:25
Beaming in a Spin Texture Lifeboat News: The Blog
Researchers use an optical vortex beam to create a stable pattern of electron spins in a thin layer of semiconductor material.
Spin-based electronic, or spintronic, devices can benefit from techniques that coax electron spins into static spatial patterns called spin textures. A new experiment demonstrates that an optical vortexa light beam that carries orbital angular momentumcan generate a stable spin texture in a semiconductor [1]. The research team showed that the vortex generates a pattern of stripes that has potential uses in processing spin information. Previous experiments have optically stimulated these striped textures, but the optical vortex has a structure that approximately overlaps with the stripe pattern, allowing faster spin-texture formation.
The spins of unbound electrons in a material can be aligned by a magnetic field or by polarized light. But as these electrons moveeither through diffusion or through conductiontheir spins will begin to rotate in response to so-called spin-orbit interactions within the material. The direction and rate of these rotations for any given electron depend on the path that it takes. Thus, two nearby electrons that start out aligned will become misaligned as they move along different paths, even if they arrive at the same destination. So maintaining an electronic spin texture seems like a doomed enterprise.
18:25
Astronomers discover helium-burning white dwarf Lifeboat News: The Blog
A white dwarf star can explode as a supernova when its mass exceeds the limit of about 1.4 solar masses. A team led by the Max Planck Institute for Extraterrestrial Physics (MPE) in Garching and involving the University of Bonn has now found a binary star system in which matter flows onto the white dwarf from its companion.
The system was found due to bright, so-called super-soft X-rays, which originate in the nuclear fusion of the overflowed gas near the surface of the white dwarf. The unusual thing about this source is that it is helium and not hydrogen that overflows and burns. The measured luminosity suggests that the mass of the white dwarf is growing more slowly than previously thought possible, which may help to understand the number of supernovae caused by exploding white dwarfs. The results have been published in the journal Nature.
Exploding white dwarfs are not only considered the main source of iron in the universe, they are also an important tool for cosmology. As so-called Type Ia supernovae (SN Ia), they all become roughly equally bright, allowing astrophysics a precise determination of the distance of their host galaxies.
18:24
Digital restoration of historical documents Lifeboat News: The Blog
One of the best ways to learn about any historical period is by conversing with the people who lived through it. Speaking with people from the distant past is very one-sided, as they are typically dead and have stopped listening long ago. However, they speak volumes if you have the patience to listen, or rather, read what they say in letters, diaries and primitive post-it notes with no sticky back sides.
An international group of computer scientists from Italy, the U.K. and Pakistan have teamed up to resurrect the dead from writings that have been degraded by time by developing a computer-assisted method to virtually return documents to a more legible and decipherable condition. In their research paper, Restoration and content analysis of ancient manuscripts via color space based segmentation, published in the journal PLOS ONE, the team details their digital restoration techniques method and experimental results.
We get a sense of ancient civilizations from their writings, both trivial and profound. The Sumerian cuneiform writing on clay tablets reveals 4,000-year-old merchant transactions, geometric calculations, and poetry detailing the fall of a great city. Had they been written on paper and not in clay we would likely not have them today.
18:01
IRC Proceedings: Friday, March 24, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-240323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-240323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-240323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-240323.gmi
Over HTTP:
|
... |
18:00
The world's toughest animal could one day help save your life Terra Forming Terra

Russias Economy Is Booming Despite or Because of Sanctions? Terra Forming Terra

To start with, Russia is internally able to be self
sufficient. This means zero external leverage. Thus
sanctions simply kick started supply replacement.
Russias Economy Is Booming Despite or Because of Sanctions? "Russian economic sovereignty has increased." President Putin
By Peter Koenig
Global Research, March 20, 2023
The Language of Four: The Meaning of Tetragrammaton Terra Forming Terra
Neutral Neutron Pairs Terra Forming Terra
I have slowly come to grasp just what science has been missing because normal matter is so dominating. Yet provided the neutral neutron pair is a reality, then the whole galaxy is full of this stuff, and better yet we literally breath it as well.
understand though that hydrogen is equally undetectable except by indirect means. It even penetrates matter as we know it. For that reason our proposed neutral neutron pair has a free ride past everything we can do. Accidental hits will be seen as just that and of no import.
From our knowledge of Cloud Cosmology we do have some things we can aassert:
1 The NNP does react along a number of axis allowing one NNP to be attached to another NNP. This is not what i describe as a hard lock but quite weak but still real and allows ordered conglomerates. These are in fact describable as proto Elements and Isotopes that can potentially decay into the expected elements on the basis of multiple NNP decay. They can just as easily be torn apart as well. I am not so sure that decay is taking place out in space as well as in the sun.
2 Gravitational pull is far less than for elements. The spacing is too large between NNPs. however it is not zero. Packed elements should squeeze out the majority of NNP content. This gives us the surface nature of all planets and also the Sun. This can then be a shell.
3 Understand that Cloud cosmology projects three types of neutral matter. I use the word neutral only because the word is convenient and allows us then to identify axis as separate. Neutral assumes mathematical continuity which is not real. We are now just understanding how important the NNP is in the evolution of our third level phys...
17:29
The Corporate Media is Not Reporting Large-Scale Microsoft Layoffs (Too Busy With Chaffbot Puff Pieces), Leaks Required to Prove That More Layoffs Are Happening Techrights
New screenshot from thelayoff.com:
New article (behind paywall, posted just before the weekend, hence limited audience):
Summary: Just as we noted days ago, there are yet more Microsoft layoffs, but the mainstream media gets bribed to go gaga over vapourware and chaffbots (making chaff like Bill Gates Says pieces) instead of reporting actual news about Microsoft
17:16
Police Needs to Intervene in the Sirius Open Source Scandal schestowitz.com
Summary: Sirius Open Source is collapsing, but that does not mean that it can dodge accountability for crimes (e.g. money that it silently stole from its staff since at least 12 years ago)
A SCREENSHOT of the PDF from Standard Life was shared here (with sensible redaction) a few days ago. Things are belatedly progressing.
This post has taken a long time to prepare as we need to separate gossip/speculation from verified facts. Standard Life also claims to be pursuing the facts (since the 7th of March). As per their own update: Dear Dr Schestowitz, I have attached our acknowledgement to your complaint. [...] If youve any questions, or problems accessing your acknowledgement, please email me at [redacted] and Ill do all I can to help you.
Theyve basically been looking into how on Earth the company (Sirius) was claiming to be paying into Standard Life accounts that dont even exist!
The simplest explanation is, Sirius engaged in embezzlement. The management was contacted several times, being kindly offered the opportunity to explain what actually happened. Each and every time the response was schtum. For reasons we detailed here before, litigation seems imminent. Class action lawsuit is also likely, though the company is in hiding. Staff that actively oversaw and participated in the embezzlement is criminally liable, even if leaving the company later. Theyve been made aware of this (fraud, theft, forgery/embezzlement among the possible charges). Failing that, or in addition to that, pension providers can be sued. Well explain the legal grounds some other day.
What does this have to do with Techrights? Sirius is describing itself as Britains most respected and best established Open Source business.
If this is what the most respected and best established boils down to, then theres serious trouble. Sirius is a major liability and a stain. This isnt the company I joined more than 12 years ago. You need to lie to keep your job or take one for the team or do something unethical/illegal to keep your salary is the hallmark or symptom of criminal management, which needs to be prosecuted, not served (except served papers). I confronted the management many times before leaving (for over a year!) and nothing improved. They kept paying the salary, but behaviour only worsened over time, so I reached out to a friend.
Suffice to say, you need not be particularly charismatic to persuade workers whom you pay to also...
17:13
Microsoft Warns of Stealthy Outlook Vulnerability Exploited by Russian Hackers The Hacker News
Microsoft on Friday shared guidance to help customers discover indicators of compromise (IoCs) associated with a recently patched Outlook vulnerability. Tracked as CVE-2023-23397 (CVSS score: 9.8), the critical flaw relates to a case of privilege escalation that could be exploited to steal NT Lan Manager (NTLM) hashes and stage a relay attack without requiring any user interaction. "External
16:51
OpenAI Reveals Redis Bug Behind ChatGPT User Data Exposure Incident The Hacker News
OpenAI on Friday disclosed that a bug in the Redis open source library was responsible for the exposure of other users' personal information and chat titles in the upstart's ChatGPT service earlier this week. The glitch, which came to light on March 20, 2023, enabled certain users to view brief descriptions of other users' conversations from the chat history sidebar, prompting the company to
16:48
Sirius Open Source Pensiongate: Time to Issue a Warrant of Arrest and Extradite the Fake Founder of Sirius Techrights
Previously/context:
- Sirius Open Source and the Money Missing From the Pension
- Sirius Finished
- Sirius Open Source Pensiongate: An Introduction
- When the Pension Vanishes
- Sirius Open Source Pensiongate (Sirius Financial Crisis): Company May Have Squandered/Plundered the Pensions of Many People
- Sirius Open Source Pensiongate: Pension Providers That Repeatedly Lie to the Clients and Dont Respond to Messages
- NOW: Pensions Lies to Its Customers and Protects Abusers
- Sirius Open Source Pensiongate: Its Beginning to Look Like a Criminal Matter and Sirius is in Serious Trouble
- Sirius Open Source Pensiongate: A Long Story Merits Many Videos
- An Update on Sirius Open Source Pensiongate: Its Looking Worse Than Ever
Summary: Sirius Open Source is collapsing, but that does not mean that it can dodge accountability for crimes (e.g. money that it silently stole from its staff si...
16:00
A Jenkins Demo Stand For Modern Times Hackaday

Once youre working on large-scale software projects, automation
is a lifesaver, and Jenkins is a strong player in open-source
automation be it software builds, automated testing or deploying
onto your servers. Naturally, its historically been developed with
x86 infrastructure in mind, and lets be fair, x86 is getting old.
[poddingue], a hacker and a Jenkins contributor, demonstrates that
Jenkins keeps up with the times, with a hardware demo stand called
miniJen, that
has Jenkins run on three non-x86 architectures arm8v
(aarch64), armv7l and RISC-V.
Theres four SBCs of different architectures involved in this, three acting as Jenkins agents executing tasks, and one acting as a controller, all powered with a big desktop PSU from Pine64. The controllers got a bit beefier CPU for a reason at FOSDEM, weve...
15:49
Ford Will Lose $3 Billion on Electric Vehicles in 2023, It Says SoylentNews
https://arstechnica.com/cars/2023/03/ford-will-lose-3-billion-on-electric-vehicles-in-2023-it-says/
There's no doubt that Ford is embracing electrification. It was first to market with an electric pickup truck for the US market, and a darn good one at that. It has a solid midsize electric crossover that's becoming more and more common on the road, even if it does still upset the occasional Mustangophile. And there's an electric Transit van for the trades. But its electric vehicle division will lose $3 billion this year as it continues to build new factories and buy raw materials.
The news came in a peek into Ford's financials released this morning. As we reported last year, Ford has split its passenger vehicle operations into two divisions. Electric vehicles fall under Ford Model e, with internal combustion engine-powered Fords (including hybrids and plug-in hybrids) falling under Ford Blue. The move was in large part to placate investors and analysts, no doubt starry-eyed during a time when any EV-related stock was booming.
Related:
Tesla
Exceeded Revenue Estimates in Q4 2021 by More than $1 Billion
(20220127)
Tesla
Burns More Cash, Fails to Meet Production Targets
(20171102)
Ford
Investing $4.5 Billion to Bring Electrification to 40% of Its
Vehicles by 2020 (20151214)
Read more of this story at SoylentNews.
14:00
Opti9 launches Observr ransomware detection and managed services for Veeam Help Net Security
Opti9 Technologies has launched Observr Software-as-a-Service (SaaS) ransomware detection and standalone managed services two new standalone service offerings that cater to organizations leveraging Veeam Software. As the complexity of organizations IT continues to evolve, technical leaders are increasingly looking to shift ownership to 3rd party experts for critical layers of their stack. This is especially true for components such as backups and disaster recovery, which must provide resilience despite constant changes such as the More
The post Opti9 launches Observr ransomware detection and managed services for Veeam appeared first on Help Net Security.
13:00
Glowscope Reduces Microscope Cost By Orders of Magnitude Hackaday

As smartphones become more ubiquitous in society, they are being used in plenty of ways not imaginable even ten or fifteen years ago. Using its sensors to gather LIDAR information, its GPS to get directions, its microphone to instantly translate languages, or even use its WiFi and cellular radios to establish a wireless hotspot are all things which would have taken specialized hardware not more than two decades ago. The latest disruption may be in microscopy, as this build demonstrates a microscope that would otherwise be hundreds of thousands of dollars.
The microscope is a specialized device known as a fluorescence microscope, which uses a light source to excite fluorescent molecules in a sample which can illuminate structures that would otherwise be invisible under a regular microscope. For this build, the light is provided by readily-available LED lighting as well as optical filters typically used in stage lighting, as well as a garden-variety smartphone. With these techniques a microscope can be produced for around $50 USD that has 10 m resolution.
While these fluorescence microsc...
11:15
McAfee and Mastercard expand partnership to improve security for small businesses Help Net Security
McAfee has expanded partnership with Mastercard to offer Mastercard Business cardholders automatic savings on online protection solutions from McAfee through Mastercard Easy Savings. According to the latest FBI Internet Crime Report, malicious cyber activity resulted in more than $10 billion in losses in 2022, with a large portion of this affecting small businesses. Small and medium-sized companies often rely on credit cards for daily financing. Providing Mastercard Business cardholders with savings on security technology solutions More
The post McAfee and Mastercard expand partnership to improve security for small businesses appeared first on Help Net Security.
11:03
Ethical AI art generation? Adobe Firefly may be the answer. SoylentNews
On Tuesday, Adobe unveiled Firefly, its new AI image synthesis generator. Unlike other AI art models such as Stable Diffusion and DALL-E, Adobe says its Firefly engine, which can generate new images from text descriptions, has been trained solely on legal and ethical sources, making its output clear for use by commercial artists. It will be integrated directly into Creative Cloud, but for now, it is only available as a beta.
Since the mainstream debut of image synthesis models last year, the field has been fraught with issues around ethics and copyright. For example, the AI art generator called Stable Diffusion gained its ability to generate images from text descriptions after researchers trained an AI model to analyze hundreds of millions of images scraped from the Internet. Many (probably most) of those images were copyrighted and obtained without the consent of their rights holders, which led to lawsuits and protests from artists.
Related:
Paper:
Stable Diffusion "Memorizes" Some Images, Sparking Privacy
Concerns
90% of
Online Content Could be 'Generated by AI by 2025,' Expert
Says
Getty
Images Targets AI Firm For 'Copying' Photos
Adobe
Stock Begins Selling AI-Generated Artwork
A
Startup Wants to Democratize the Tech Behind DALL-E 2, Consequences
be Damned
Adobe
Creative Cloud Experience Makes It...
10:00
Dead Raspberry Pi Boards, PMICs, And New Hope Hackaday

Since the Raspberry Pi 3B+ release, the Pi boards we all know and love gained one more weakpoint the PMIC chip, responsible for generating all the power rails a Pi needs. Specifically, the new PMIC was way more vulnerable to shorting 5V and 3.3V power rails together something thats trivial to do on a Raspberry Pi, and would leave you with a bricked board. Just replacing the PMIC chip, the MxL7704, wouldnt but now, on Raspberry Pi forums, [Nefarious19] has reportedly managed to replace it and revive their Pi.
First off, you get a replacement PMIC and reflow it and thats where, to our knowledge, people have stopped so far. The next step proposed by [Nefarious19] is writing proper values into the I2C registers of the PMIC. For that, youd want a currently-alive Pi useful as both I2C controller for writing the values in, and as a sourc...
09:28
CISA announced the Pre-Ransomware Notifications initiative Security Affairs
The US Cybersecurity and Infrastructure Security Agency (CISA) announced the Pre-Ransomware Notifications service to help organizations stop ransomware attacks before damage occurs.
The US Cybersecurity and Infrastructure Security Agency announced a new Pre-Ransomware Notification initiative that aims at alerting organizations of early-stage ransomware attacks.
The principle behind the initiative is simple, ransomware actors initially gain access to the target organization, then they take some time before stealing or encrypting data. The time-lapse between initial access to a network and the encryption of the systems can last from hours to days.
Being able to notify the victims in this time window can help them to limit the damages caused by the ransomware attack.
This window gives us time to warn organizations that ransomware actors have gained initial access to their networks. reads the announcement made by the Us agency. These early warnings can enable victims to safely evict the ransomware actors from their networks before the actors have a chance to encrypt and hold critical data and systems at ransom. Early warning notifications can significantly reduce potential loss of data, impact on operations, financial ramifications, and other detrimental consequences of ransomware deployment.
The CISA Joint Cyber Defense Collaborative (JCDC) collects information about potential early-stage ransomware activity from multiple sources, including the research community, infrastructure providers, and cyber threat intelligence firms.
Then the field personnel across the country notify the victim organization and provide specific mitigation guidance. The agency will also provide notification to organizations outside of the United States through its international CERT partners.
Since the start of 2023, CISA notified over 60 entities across the energy, healthcare, water/wastewater, education, and other sectors about potential early-stage ransomware attacks. It was a success bacause many of the alerted organizations remediated the attack before encryption or exfiltration took place.
Continuing to enhance our collective cyber defense is contingent upon persistent collaboration and information sharing between partners across government and the private sector. concludes the announcement. To enable the broader cyber community to benefit from valuable threat intelligence, we urge organizations to report observed activity, including ransomware indicators of compromise and TTPs, to CISA or our federal law enforcement partners, including the FBI and the U.S. Secret Service....
08:42
Interop: One Protocol to Rule Them All? Light Blue Touchpaper
Everyones worried that the UK Online Safety Bill and the EU Child Sex Abuse Regulation will put an end to end-to-end encryption. But might a law already passed by the EU have the same effect?
The Digital Markets Act ruled that users on different platforms should be able to exchange messages with each other. This opens up a real Pandoras box. How will the networks manage keys, authenticate users, and moderate content? How much metadata will have to be shared, and how?
In our latest paper, One Protocol to Rule Them All? On Securing Interoperable Messaging, we explore the security tensions, the conflicts of interest, the usability traps, and the likely consequences for individual and institutional behaviour.
Interoperability will vastly increase the attack surface at every level in the stack from the cryptography up through usability to commercial incentives and the opportunities for government interference.
Twenty-five years ago, we warned that key escrow mechanisms would endanger cryptography by increasing complexity, even if the escrow keys themselves can be kept perfectly secure. Interoperability is complexity on steroids.
08:23
Metal-Detecting Drone Could Autonomously Find Landmines SoylentNews
A drone with 5 degrees of freedom can safely detect buried objects from the air:
Metal detecting can be a fun hobby, or it can be a task to be completed in deadly earnestif the buried treasure you're searching for includes land mines and explosive remnants of war. This is an enormous, dangerous problem: Something like 12,000 square kilometers worldwide are essentially useless and uninhabitable because of the threat of buried explosives, and thousands and thousands of people are injured or killed every year.
[...] Because the majority of mines are triggered by pressure or direct proximity, it may seem that a drone would be the ideal way to detect them nonexplosively. However, unless you're only detecting over a perfectly flat surface (and perhaps not even then) your detector won't be positioned ideally most of the time, and you might miss something, which is not a viable option for mine detection.
But now a novel combination of a metal detector and a drone with 5 degrees of freedom is under development at the Autonomous Systems Lab at ETH Zurich. It may provide a viable solution to remote land-mine detection, by using careful sensing and localization along with some twisting motors to keep the detector reliably close to the ground.
Read more of this story at SoylentNews.
08:04
China-linked hackers target telecommunication providers in the Middle East Security Affairs
Researchers reported that China-linked hackers targeted telecommunication providers in the Middle East in the first quarter of 2023.
In the first quarter of 2023, SentinelLabs researchers spotted the initial phases of attacks against telecommunication providers in the Middle East.
According to the researchers, the activity is part of the Operation Soft Cell that was first reported in June 2019 by Cybereason.
At the time, researchers at Cybereason uncovered the long-running espionage campaign tracked as Operation Soft Cell. Threat actors were targeting telco providers. Tactics, techniques, and procedures, and the type of targets suggest the involvement of a nation-state actor likely linked to Chinese APT10.
Once compromised the networks of telecommunication companies, the attackers aimed at accessing mobile phone users call data records.
SentinelLabs linked the recent attacks to a China-linked cyberespionage group in the nexus of Gallium and APT41, but the exact grouping has yet to be determined.
The threat actors employed a new dropper mechanism which is evidence of an ongoing development effort by a highly-motivated threat actor.
In collaboration with QGroup GmbH, SentinelLabs recently observed initial threat activities targeting the telecommunication sector. We assess it is highly likely that these attacks were conducted by a Chinese cyberespionage actor related to the Operation Soft Cell campaign. reads the report published by SentinelLabs. The initial attack phase involves infiltrating Internet-facing Microsoft Exchange servers to deploy webshells used for command execution. Once a foothold is established, the attackers conduct a variety of reconnaissance, credential theft, lateral movement, and data exfiltration activities.
The threat actors used a custom credential theft malware, tracked as mim221, that implemented a series of Mimikatz modifications on closed-source tooling.
actively maintained credential theft malware that was enhanced by implementing new anti-detection features.“...
08:01
ChatGPT Bug Exposed Payment Details of Paid Users HackRead | Latest Cybersecurity and Hacking News Site
OpenAI has apologized and reached out to affected users about the potential data breach.
This is a post from HackRead.com Read the original post: ChatGPT Bug Exposed Payment Details of Paid Users
07:29
Cloudflare Disables Access to Pirated Content on its IPFS Gateway TorrentFreak
 The InterPlanetary File System, more broadly known as
IPFS,
has been around for a few years now.
The InterPlanetary File System, more broadly known as
IPFS,
has been around for a few years now.
While the name may sound a little alien to the public at large, the peer-to-peer file storage network has a growing user base among the tech-savvy.
In short, IPFS is a decentralized network where users make files available to each other. A website using IPFS is served by a swarm of users in much the same way BitTorrent users share content with each other.
Completely Decentralized
The advantage of this system is that websites can become completely decentralized. If a website or other resource is hosted on IPFS, it remains accessible as long as the computer of one user who pinned it remains online.
The advantages of IPFS are clear. It allows archivists, content creators, researchers, and many others to distribute large volumes of data over the Internet. Its censorship resistant and not vulnerable to regular hosting outages.
IPFS is also a perfect match for pirate sites. Due to its decentralized nature, IPFS sites are virtually impossible to shut down. This aspect was already highlighted by Pirate Bay co-founder Peter Sunde back in 2016. More recently, IPFS was promoted by Z-Library after its domain names were seized.
Cloudflares IPFS Gateway
IPFS has also been embraced by many legal services. Most notably, Cloudflare gave it a boost by launching its own IPFS gateway, allowing the public to access IPFS resources without having to install specialized software.
Cloudflares IPFS gateway has been running for a few years now. Technically, the internet infrastructure company has no control over any of the content being made available, but that doesnt mean there are no complaints.
Apparently, some people or organizations have complained about the content that can be accessed through Cloudflares IPFS gateway.
While the accessed content is in no way controlled by Cloudflare, the San Francisco company takes these complaints rather seriously. The same also applies to the Ethereum gateway, which offers easy read-and-write access to the Ethereum network.
Cloudflare Disables IPFS Access
In its most recent...
07:00
Were the New Renewables IEEE Spectrum

The Big Picture features technology through the lens of photographers.
Every month, IEEE Spectrum selects the most stunning technology images recently captured by photographers around the world. We choose images that reflect an important advance, or a trend, or that are just mesmerizing to look at. We feature all images on our site, and one also appears on our monthly print edition.
Enjoy the latest images, and if you have suggestions, leave a comment below.

Juice Box
For many years, environmentalists have looked forward to the coming of net-zero-energy buildings. Much effort was devoted to making lighting, heating, and cooling more efficient so buildings consumed less energy. But the net-zero target would never have been reachable without innovations in renewable-energy generation that let structures generate power on-site. Now residential and commercial buildings can be outfitted with roofing tiles that double as solar panels, or with rooftop boxes like this low-profile unit that transforms gusts of wind into electric current. This WindBox turbine, installed on the roof of a building in Rouen, France, is 1.6 meters tall, and has a 4-square-meter footprint (leaving plenty of space for solar panels or tiles). The unit, which weighs130 kilograms, can generate up to 2,500 kilowatt-hours of electricity per year (enough to meet roughly one-quarter of the energy needs of a typical U.S. household).
Lou Benoist/AFP/Getty Images
Nobel Horn Antenna Endangered
This is the giant horn antenna that was used in physics research that led to the discovery of background cosmic radiation, which provided support for the big bang theory. Two Bell Labs researchers who were painstakingly attempting to eli...
06:31
Garrett: We need better support for SSH host certificates LWN.net
Matthew Garrett looks at the recent disclosure of GitHub's private host key, how it probably came about, and what a better approach to key management might look like.
The main problem is that client tooling just doesn't handle this well. OpenSSH has no way to do TOFU for CAs, just the keys themselves. This means there's no way to do a git clone ssh://git@github.com/whatever and get a prompt asking you to trust Github's CA. Instead, you need to add a @cert-authority github.com (key) line to your known_hosts file by hand, and since approximately nobody's going to do that there's only marginal benefit in going to the effort to implement this infrastructure. The most important thing we can do to improve the security of the SSH ecosystem is to make it easier to use certificates, and that means improving the behaviour of the clients.
05:58
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Hanno Bck on Mar 24
Here's a proposed patch to restrict access to the dangerousfunctionality. Waiting a few days for feedback here and will then try
to send it to the appropriate kernel lists.
------------------
Restrict access to TIOCLINUX selection functions
These functions can be used for privilege escalation when code is
executed with tools like su/sudo.
Signed-off-by: Hanno Bck <hanno () hboeck de>
---
drivers/tty/vt/vt.c | 6 ++++++
1 file...
05:36
City of Toronto is one of the victims hacked by Clop gang using GoAnywhere zero-day Security Affairs
Clop ransomware gang added the City of Toronto to the list of its victims, it is another organization compromised by exploiting GoAnywhere zero-day.
Clop ransomware gang added the City of Toronto to the list of victims published on its Tor leak site. The City was targeted as part of a campaign exploiting the recently disclosed zero-day vulnerability in the Fortras GoAnywhere secure file transfer tool.
The gang is very active and recently it claimed to have breached tens of large organizations, including Rubrik, Onex, Axis, Bank, Rio Tinto, Hitachi Energy, and Virgin Group, as reported by the security expert Dominic Alvieri.
The news of the hack was also confirmed by BleepingComputer which reached a spokesperson for the City of Toronto. The City government launched an investigation into the incident to determine the extent of the security breach.
Today, the City of Toronto has confirmed that unauthorized access to City data did occur through a third party vendor. The access is limited to files that were unable to be processed through the third party secure file transfer system. a City spokesperson told BleepingComputer.
In early February, the popular investigator Brian Krebs first revealed details about the zero-day on Mastodon and pointed out that Fortra has yet to share a public a...
05:33
Reverse-Engineering the Multiplication Algorithm in the Intel 8086 Processor SoylentNews
http://www.righto.com/2023/03/8086-multiplication-microcode.html
While programmers today take multiplication for granted, most microprocessors in the 1970s could only add and subtract multiplication required a slow and tedious loop implemented in assembly code. One of the nice features of the Intel 8086 processor (1978) was that it provided machine instructions for multiplication,2 able to multiply 8-bit or 16-bit numbers with a single instruction. Internally, the 8086 still performed a loop, but the loop was implemented in microcode: faster and transparent to the programmer. Even so, multiplication was a slow operation, about 24 to 30 times slower than addition.
In this blog post, I explain the multiplication process inside the 8086, analyze the microcode that it used, and discuss the hardware circuitry that helped it out.3 My analysis is based on reverse-engineering the 8086 from die photos. The die photo below shows the chip under a microscope. I've labeled the key functional blocks; the ones that are important to this post are darker. At the left, the ALU (Arithmetic/Logic Unit) performs the arithmetic operations at the heart of multiplication: addition and shifts. Multiplication also uses a few other hardware features: the X register, the F1 flag, and a loop counter.
Read more of this story at SoylentNews.
05:31
Links 24/03/2023: Microsofts Fall on the Web and Many New Videos Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Desktop/Laptop
-
Toms Hardware Framework Previews 16-inch Laptop With Upgradeable Graphics, Adds Ryzen Mainboards
Framework...
-
-
05:28
UKs NCA infiltrates cybercrime market with fake DDoS sites HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
The National Crime Agency (NCA) has conducted a sting operation to infiltrate the cybercrime market with fake DDoS sites for Operation Power Off.
This is a post from HackRead.com Read the original post: UKs NCA infiltrates cybercrime market with fake DDoS sites
05:27
Victory at the Ninth Circuit: Twitters Content Moderation is Not State Action Deeplinks
Earlier this month, the Ninth Circuit held that Twitter did not act as the government by banning a user months after a government agency flagged for Twitter one of his tweets on alleged election fraud. OHandley v. Weber is the latest decision rejecting social media users attempts to hold platforms liable for deleting, demonetizing, and otherwise moderating their content.
Twitter is a private entity, so the government and the courts cannot tell it what speech it must remove or what speech it must carry. The First Amendment restricts censorship only by the government, not private entities, unless those entities are using government power or otherwise effectively acting as the government. But in OHandley, even if Twitter and the government were generally aligned in their missions to limit the spread of misleading election information[, s]uch alignment does not transform private conduct into state action.
Moreover, as we argued in our amicus brief in the case, holding Twitter liable for content moderation would likely violate the platforms own First Amendment rights. For example, when Twitter took down plaintiff Rogan OHandleys tweets and then his account, it made an editorial decision about what content it would publish.
OHandleys lawsuit, relied on the fact that the California Office of Election Cybersecurity flagged one of OHandleys tweets for supposedly violating Twitters misinformation policy. But as the Ninth Circuit explained, Twitter developed and applied that policy at its discretion, and the government did not order Twitter to take any action. The court said, and we argued in our brief, that Twitter is not a state actor unless it ceded control over its content moderation process to the government. In general, the government is free to talk to Twitter, and Twitter is free to listen (or not listen).
The Ninth Circuit pointed specifically to Twitters user agreement with OHandley as justifying the content moderation, and declined to say whether the First Amendment also protects that moderation. But many other courts have dismissed these must carry lawsuits under the First Amendment, including the lower court in this case. OHandley is the Ninth Circuits second ...
05:01
CubeSat Operators Launch an IoT Space Race IEEE Spectrum

A rocket carrying CubeSats launched into Earth orbit two years
ago, on 22 March, 2021. Two of those CubeSats represented competing
approaches to bringing the Internet of Things (IoT) to space. One,
operated by Lacuna Space, uses a
protocol called LoRaWAN, a long-range, low-power protocol owned
by Semtech.
The other, owned by Sateliot, uses the narrowband IoT protocol. And separately, in late 2022,
the cellular industry standard-setter 3GPP incorporated
satellite-based 5G into standard cellular service with its release 17.
In other words, there is now an IoT space race.
In addition to Lacuna and Sateliot, OQ Technology is also nipping at the heels of satellite telecom incumbents such as Iridium, Orbcomm, and Inmarsat for a share of the growing satellite IoT subscriber market. OQ has three satellites in low Earth orbit (LEO) and plans to launch seven more this year, says OQ Technologys chief innovation officer Prasanna Nagarajan. OQ has paying customers in the oil and gas, agriculture, and transport logistics industries.
Sateliot, based in Barcelona, Spain, has the satellite it launched in 2021 in orbit and plans to launch four more this year, says Sateliots business development manager Paula Caudet. It is inviting early adopters to sample its service for free this year while it builds more coverage. Certain use cases are fine with flybys every few hours, such as agricultural sensors, Caudet says. OQ and Sateliot claim they will launch enough satellites in 2024 to offer at least hourly coverage and enough in 2025 to offer near-real-...
04:42
Britain: Food Inflation Hit Highest Rate Since 1977, Increased 18.2% in the Year to Februaury 2023 cryptogon.com
Via: Grocery Gazette: Food inflation hit its highest rate since 1977 last month, having risen to 18.2% in the year to Februaury 2023. The Office for National Statistics (ONS) saw this jump from 16.8% in January, with the increase driven by price movements such as the rise in cost of vegetables last month.
04:35
Banks Are Still Drawing on the Fed for $164 Billion of Emergency Cash cryptogon.com
Via: Bloomberg: Banks reduced their borrowings only slightly from two Federal Reserve backstop facilities in the most recent week, a sign that institutions are taking advantage of the central banks liquidity in the wake of turmoil.
04:28
Intel XeSS SDK 1.1 Released Phoronix
The Intel XeSS SDK 1.0 release happened last September while now has been succeeded by XeSS SDK 1.1. Though like the prior release, the XeSS SDK isn't fully open-source with just the bits around game integration being public...
04:12
We need better support for SSH host certificates Matthew Garrett
Github accidentally
committed their SSH RSA private key to a repository, and now a
bunch of people's infrastructure is broken because it needs to be
updated to trust the new key. This is obviously bad, but what's
frustrating is that there's no inherent need for it to be -
almost all the technological components needed to both
reduce the initial risk and to make the transition seamless already
exist.
But first, let's talk about what actually happened here. You're
probably used to the idea of TLS certificates from using browsers.
Every website that supports TLS has an asymmetric pair of keys
divided into a public key and a private key. When you contact the
website, it gives you a certificate that contains the public key,
and your browser then performs a series of cryptographic operations
against it to (a) verify that the remote site possesses the private
key (which prevents someone just copying the certificate to another
system and pretending to be the legitimate site), and (b) generate
an ephemeral encryption key that's used to actually encrypt the
traffic between your browser and the site. But what stops an
attacker from simply giving you a fake certificate that contains
their public key? The certificate is itself signed by a certificate
authority (CA), and your browser is configured to trust a
preconfigured set of CAs. CAs will not give someone a signed
certificate unless they prove they have legitimate ownership of the
site in question, so (in theory) an attacker will never be able to
obtain a fake certificate for a legitimate site.
This infrastructure is used for pretty much every protocol that can
use TLS, including things like SMTP and IMAP. But SSH doesn't use
TLS, and doesn't participate in any of this infrastructure.
Instead, SSH tends to take a "Trust on First Use" (TOFU) model -
the first time you ssh into a server, you receive a prompt asking
you whether you trust its public key, and then you probably hit the
"Yes" button and get on with your life. This works fine up until
the point where the key changes, and SSH suddenly starts
complaining that there's a mismatch and something awful could be
happening (like someone intercepting your traffic and directing it
to their own server with their own keys). Users are then supposed
to verify whether this change is legitimate, and if so remove the
old keys and add the new ones. This is tedious and risks users just
saying "Yes" again, and if it happens too often an attacker can
simply redirect target users to their own server and through sheer
fatigue at dealing with this crap the user will probably trust the
malicious server.
Why not certificates? OpenSSH actually does support
certificates, but not in the way you might expect. There's a
custom format that's significantly less compl...
03:47
Video Friday: Lunar Base IEEE Spectrum

Video Friday is your weekly selection of awesome robotics
videos, collected by your friends at IEEE Spectrum
robotics. We also post a weekly calendar of upcoming robotics
events for the next few months. Please
send us your events for inclusion.
Robotics Summit & Expo: 1011 May 2023, BOSTON
ICRA 2023: 29 May2 June 2023, LONDON
RoboCup 2023: 410 July 2023, BORDEAUX, FRANCE
RSS 2023: 1014 July 2023, DAEGU, SOUTH KOREA
IEEE RO-MAN 2023: 2831 August 2023, BUSAN, SOUTH KOREA
CLAWAR 2023: 24 October 2023, FLORIANOPOLIS, BRAZIL
Humanoids 2023: 1214 December 2023, AUSTIN, TEXAS
Enjoy todays videos!
GITAI conducted a demonstration of lunar base construction using two GITAI inchworm-type robotic arms and two GITAI Lunar Robotic Rovers in a simulated lunar environment and successfully completed all planned tasks. The GITAI robots have successfully passed various tests corresponding to Level 4 of NASAs Technology Readiness Levels (TRL) in a simulated lunar environment in the desert.
[ GITAI ]
Thanks, Sho!
This is 30 minutes of Agility Robotics Digit being productive at ProMat. The fact that it gets boring and repetitive to watch reinforces how much this process needs robots, and is also remarkable because bipedal robots can now be seen as just another tool.
...
03:01
How I created a Red Hat OpenShift cluster on tiny hardware Linux.com
Build an OpenShift cluster on a small, sub-$300 computer.
Read More at Enable Sysadmin
The post How I created a Red Hat OpenShift cluster on tiny hardware appeared first on Linux.com.
02:47
Latitude Hack Worsens With Services Taken Offline SoylentNews
The situation for the Latitude hack has become worse with the owners forced to take the site offline.
The non-bank lender confirmed that Medicare numbers and "copies of passports or passport numbers" were included in the theft of personal information affecting approximately 333,000 customers and applicants.
[...] Latitude said of the stolen information, approximately 96 per cent was "copies of drivers' licences or driver licence numbers", "less than 4 per cent was copies of passports or passport numbers" and "less than 1 per cent was Medicare numbers".
"Because the attack remains active, we have taken our platforms offline and are unable to service our customers and merchant partners," the statement said.
[...] But frustrated customers have hit out at Latitude's handling of the hacking describing it as "pathetic" and "disgusting".
"How long will it take to find out if I am affected? If my details have been stolen I'd like to know now. Identity theft and/or financial ruin due to your lack of security and saving items such as my drivers licence is not okay," one woman wrote on social media.
"We need more information asap," one woman pleaded. "Do we need to change our licences, change our bank accounts? As this has been happening lots what have you done with your cyber security? As a ex Security officer this is a major huge breach and should not happen. Someone dropped the ball big time."
Previously it had only been confirmed that drivers' licences were taken.
Read more of this story at SoylentNews.
02:26
CVE-2022-47502: Apache OpenOffice: Macro URL arbitrary script execution Open Source Security
Posted by Marcus Lange on Mar 24
Severity: criticalDescription:
Apache OpenOffice documents can contain links that call internal macros with arbitrary arguments. Several URI Schemes
are defined for this purpose.
Links can be activated by clicks, or by automatic document events.
The execution of such links must be subject to user approval.
In the affected versions of OpenOffice, approval for certain links is not requested; when activated, such links could
therefore...
02:24
CVE-2022-38745: Apache OpenOffice: Empty entry in Java class path Open Source Security
Posted by Marcus Lange on Mar 24
Severity: moderateDescription:
Apache OpenOffice versions before 4.1.14 may be configured to add an empty entry to the Java class path. This may lead
to run arbitrary Java code from the current directory.
Credit:
European Commission's Open Source Programme Office (sponsor)
References:
https://openoffice.apache.org/
https://www.cve.org/CVERecord?id=CVE-2022-38745
01:45
Critical flaw in WooCommerce Payments plugin allows site takeover Security Affairs
A patch for a critical vulnerability in the WooCommerce Payments plugin for WordPress has been released for over 500,000 websites.
On March 23, 2023, researchers from Wordfence observed that the WooCommerce Payments Fully Integrated Solution Built and Supported by
The WooCommerce Payments plugin is a fully integrated payment solution for the WooCommerce open source e-commerce platform, the plugin is developed by Automattic. WooCommerce Payments is installed on over 500,000 sites.
The researchers analyzed the patch and determined that the development team behind the plugin has removed a portion of code that could have allowed an unauthenticated attacker to impersonate an administrator and completely take over a WordPress website without any user interaction.
The vulnerability impacts plugin versions 4.8.0 through 5.6.1, it was first discovered by Michael Mazzolini from penetration testing firm GoldNetwork.
We developed a Proof of Concept and began writing and testing a firewall rule immediately. The rule was released the same day, on March 23, 2023 to Wordfence Premium, Wordfence Care, and Wordfence Response customers. reads the advisory published by Wordfence.
Payments plugin, which is 5.6.2 as of this writing, immediately.According to the analysis conducted by the WordPress security firm Sucuri, the vulnerability resides in a PHP file called class-platform-checkout-session.php.
Automattic is issuing automatic/forced updates of all WordPress websites using its plugin.
WooCommerce recommends admins of websites using the plugin to:
- Update woocommerce-payments to
- Change all administrator passwords...