| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Tuesday, 14 March
00:24
Up to 1,000,000 Times Faster: A Switch Made From a Single Molecule Lifeboat News: The Blog
An international team of researchers, including those from the University of Tokyos Institute for Solid State Physics, has made a groundbreaking discovery. They have successfully demonstrated the use of a single molecule named fullerene as a switch, similar to a transistor. The team achieved this by employing a precisely calibrated laser pulse, which allowed them to control the path of an incoming electron in a predictable manner.
The switching process enabled by fullerene molecules can be significantly faster than the switches used in microchips, with a speed increase of three to six orders of magnitude, depending on the laser pulses utilized. The use of fullerene switches in a network could result in the creation of a computer with capabilities beyond what is currently achievable with electronic transistors. Additionally, they have the potential to revolutionize microscopic imaging devices by providing unprecedented levels of resolution.
Over 70 years ago, physicists discovered that molecules emit electrons in the presence of electric fields, and later on, certain wavelengths of light. The electron emissions created patterns that enticed curiosity but eluded explanation. But this has changed thanks to a new theoretical analysis, the ramification of which could not only lead to new high-tech applications but also improve our ability to scrutinize the physical world itself.
00:24
Reduced Blood Pressure: Was It Caused By Lung Muscle Training? Lifeboat News: The Blog
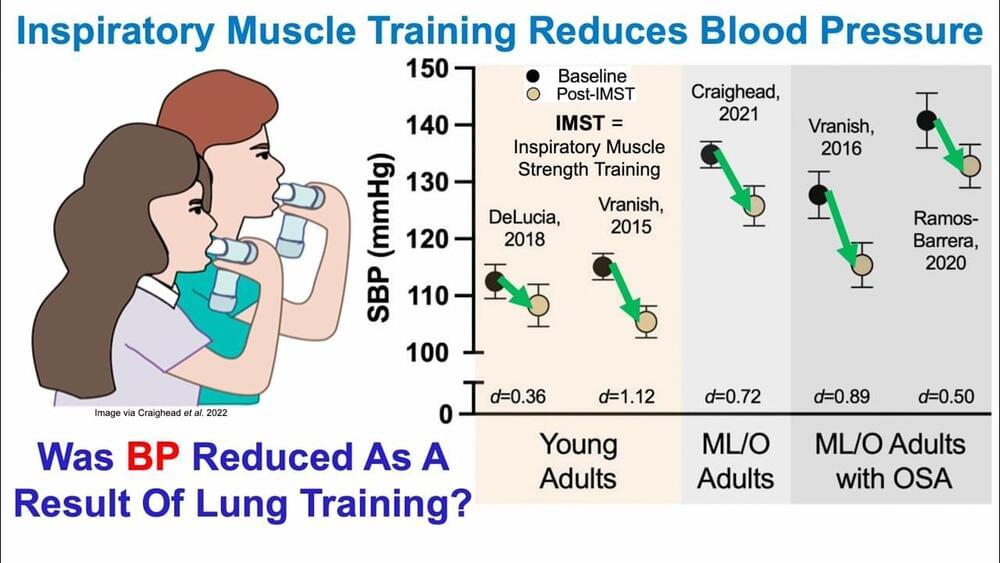
Join us on Patreon! https://www.patreon.com/MichaelLustgartenPhD
Discount Links:
NAD+ Quantification: https://www.jinfiniti.com/intracellular-nad-test/
Use Code: ConquerAging At Checkout.
Green Tea: https://www.ochaandco.com/?ref=conqueraging.
Oral Microbiome: https://www.bristlehealth.com/?ref=michaellustgarten.
Epigenetic Testing: https://bit.ly/3Rken0n.
Use Code: CONQUERAGING!
At-Home Blood Testing: https://getquantify.io/mlustgarten.
00:22
2302.037101.pdf Lifeboat News: The Blog
Bouncing cosmology from nonlinear dark energy with two cosmological constants.
Dropbox is a free service that lets you bring your photos, docs, and videos anywhere and share them easily. Never email yourself a file again!
00:19
Midazolam Murders When a Common Sedative Becomes an Execution Drug cryptogon.com
Via: Peak Prosperity:
00:19
Denmark is Storing CO2 in Abandoned North Sea Oil Fields SoylentNews
Last week, Denmark has stored the first volumes of carbon dioxide in an old oil and gas field in the Danish North Sea. The carbon dioxide sequestered comes from a chemical production plant (Ineos Oxide) in the Port of Antwerp, Belgium.
Since 2010, Ineos Oxide has captured CO2 as a by-product from its ethylene oxide (plastics) production, cooled it down to a liquid, and resold the product to the food (fizzy drinks, beer) and agricultural (greenhouse cultivation) industry. Now, instead, part of this production was transported to Nini, a previously abandoned oil platform about 200 km in front of the Danish coast, and injected 1,800 meters deep.
The test project, named Greensand, needs to prove that the process is possible, and safe. The modified transport vessel used, Aurora Storm, can only take 800 ton CO2 per traject; it will have to shuttle back and forth between Antwerp and Denmark about 20 times, enough for 15,000 ton, this year alone. The project will be upscaled to 1.5 million ton a year by 2025.
By 2030, 8 million ton a year is planned, or about half the carbon dioxide emitted by Antwerp's chemical cluster, the largest in Europe. This, however, requires investments in new offshore infrastructure, and larger transport ships known as CO2 carriers.
The Greensand project is racing behind another project though. That project is called Northern Lights, and aims to be able to store 1.5 million ton a year, by next year, 2024. Northern Lights is a partnership between Shell, Equinor and Total, and supported by Norway's government Langskip (Longship) CCS project.
The EU has set a target of capturing and storing a minimum 300 million ton CO2 a year by 2050.
Read more of this story at SoylentNews.
00:05
A USB-accessible slab-out-of-bounds read in Linux kernel driver Open Source Security
Posted by Jisoo Jang on Mar 13
=== Description ===A slab-out-of-bounds read bug was found in the Broadcom Full MAC Wi-Fi
driver (e.g., brcmfmac.ko in the linux-modules-extra package in Ubuntu),
The bug occurs in kmemdup() called from brcmf_get_assoc_ies(), when
assoc_info->req_len, data from a URB provided by a USB device, is bigger
than the size of buffer which is defined as WL_EXTRA_BUF_MAX.
The driver duplicates the data of cfg->extra_buf to conn_info->req_ie...
Monday, 13 March
23:36
Intel Meteor Lake Graphics IDs Enabled For Mesa 23.1 Phoronix
The open-source OpenGL and Vulkan support for Intel's next-generation Meteor Lake client processors is taking a step forward with next quarter's Mesa 23.1 release...
23:24
Fake ChatGPT Chrome Extension Hijacking Facebook Accounts for Malicious Advertising The Hacker News
A fake ChatGPT-branded Chrome browser extension has been found to come with capabilities to hijack Facebook accounts and create rogue admin accounts, highlighting one of the different methods cyber criminals are using to distribute malware. "By hijacking high-profile Facebook business accounts, the threat actor creates an elite army of Facebook bots and a malicious paid media apparatus," Guardio
23:23
How to Apply NIST Principles to SaaS in 2023 The Hacker News
The National Institute of Standards and Technology (NIST) is one of the standard-bearers in global cybersecurity. The U.S.-based institutes cybersecurity framework helps organizations of all sizes understand, manage, and reduce their cyber-risk levels and better protect their data. Its importance in the fight against cyberattacks cant be overstated. While NIST hasnt directly developed
22:47
Warning: AI-generated YouTube Video Tutorials Spreading Infostealer Malware The Hacker News
Threat actors have been increasingly observed using AI-generated YouTube Videos to spread a variety of stealer malware such as Raccoon, RedLine, and Vidar. "The videos lure users by pretending to be tutorials on how to download cracked versions of software such as Photoshop, Premiere Pro, Autodesk 3ds Max, AutoCAD, and other products that are licensed products available only to paid users,"
22:27
Michelle Catts SVP, Nuclear Programs, GE-Hitachi Reliable Carbon-Free Power For The World Lifeboat News: The Blog

Reliable carbon-free power for the world michelle catts, senior vice president, nuclear programs, ge-hitachi nuclear energy.
Michelle Catts is the Senior Vice President of Nuclear Programs at GE-Hitachi (GEH https://nuclear.gepower.com/) located in Wilmington, NC.
Ms. Catts has over 18 years of demonstrated managerial and technical expertise in nuclear Regulatory Affairs and currently is responsible for ensuring world-class Quality, Continuous Improvement, Regulatory Affairs, and oversight of Environment, Health & Safety programs. She manages a multimillion-dollar budget and over a 30-member organization. She provides licensing and quality leadership and guidance to support nuclear fuel facility licensing, current nuclear fleet fuel reload/outage licensing activities, new reactor and new fuel opportunities, Technical Regulations and Standards, and GE-Hitachiss Vallecitos and Morris sites.
Prior to joining GE-Hitachi, Ms. Catts worked for the U.S. Nuclear Regulatory Commission (NRC) where she held positions of increasing responsibility including as a nuclear reactor inspector stationed onsite at nuclear power plants up to the Policy Advisor to the Presidential Appointed NRC Chairman.
Ms. Catts holds a B.S. in Nuclear Engineering from North Carolina State University and is currently working on her MBA at UNCW.
Ms. Catts is also on the board of Smart Start of New Hanover County, an organization that seeks to build bridges to develop, sustain and enhance health, family support and early education services for all children, ages birth to five.
22:24
An Introduction to Neuroinformatics Lifeboat News: The Blog

Details
The goal of brain imaging is to provide in-vivo measures of the
human brain to better understand how the brain is structured,
connected and functions.
In this talk, we will discuss how to analyze brain imaging data in
order to make sense of the large amount of data that comes out of
the scanner.
 **About
the speaker**
**About
the speaker**
[Dr. Camille Maumet](https://twitter.com/cmaumet) is a
research scientist in neuroinformatics at Inria, Univ Rennes, CNRS,
Inserm in Rennes, France.
Her research focuses on the variability of analytical pipelines and
its impact on our ability to reuse brain imaging datasets.
She obtained her PhD in computer science at the University of
Rennes on the analyses of clinical neuroimaging datasets in
functional magnetic resonance imaging and.
arterial spin labelling. She was then a postdoctoral research
fellow in the Institute of Digital Healthcare at the University of
Warwick and the University of Oxford.
where she focused on meta-analyses and standards for neuroimaging
data sharing. She is also an open science advocate.
involved in the development of more inclusive research practices
and community-led research and participates in many collaborative
efforts including Brainhack.
the INCF, and the Open Science Special Interest Group of the
Organization for Human Brain Mapping that she chaired in 2020.
[Nipype Tutorial](https://miykael.github.io/nipype_tutorial/)
Annual Brain Imaging Events:
[OHBM Brainhack (Brain Hackathon) June 1618](https://ohbm.github.io/hackathon2022/)[registration via](https://www.humanbrainmapping.org/i4a/ams/meetings/index.cfmageID=4073)
- [OHBM Open Science Room (Discussions around open science practices & brain imaging)](https://ohbm.github.io/osr2022/)
22:00
Breaking Into the Nintendo DSi Through the (Browser) Window Hackaday

The Nintendo DSi was surpassed by newer and better handhelds many years ago, but that doesnt stop people like [Nathan Farlow] from attempting to break into the old abandoned house through a rather unexpected place: the (browser) window.
When the Nintendo DSi was released in 2008, one of its notable [Nathan] reasoned an exploit in this browser would be an ideal entry point, as theres no OS or kernel to get past once you get execution, you control the system. To put this plan into action, he put together two great ideas. First he used the WebKit layout tests to get the browser into weird edge cases, and then tracked down an Windows build of Opera 9.50 that he could run on his system under WINE. This allowed him to identify the use-after-free bugs that he was looking for.
21:40
Linux 6.1.19 LTS & 6.2.6 Released With AMD System Stuttering Workaround Phoronix
Following last night's Linux 6.3-rc2 release that brings a workaround for system stuttering on some AMD Ryzen systems, that workaround was quickly back-ported to the Linux 6.1 LTS and 6.2 stable series and spun into new releases for Monday morning...
21:39
Raising the Bar for Software Security: GitHub 2FA Begins March 13 SoylentNews
On March 13, we will officially begin rolling out our initiative to require all developers who contribute code on GitHub.com to enable one or more forms of two-factor authentication (2FA) by the end of 2023.
GitHub is central to the software supply chain, and securing the software supply chain starts with the developer. Our 2FA initiative is part of a platform-wide effort to secure software development by improving account security. Developers' accounts are frequent targets for social engineering and account takeover (ATO). Protecting developers and consumers of the open source ecosystem from these types of attacks is the first and most critical step toward securing the supply chain.
[...] If your account is selected for enrollment, you will be notified via email and see a banner on GitHub.com, asking you to enroll. You'll have 45 days to configure 2FA on your accountbefore that date nothing will change about using GitHub except for the reminders. We'll let you know when your enablement deadline is getting close, and once it has passed you will be required to enable 2FA the first time you access GitHub.com. You'll have the ability to snooze this notification for up to a week, but after that your ability to access your account will be limited.
So, what if you're not in an early enrollment group but you want to get started? Click here and follow a few easy steps to enroll in 2FA.
[...] You can choose between TOTP, SMS, security keys, or GitHub Mobile as your preferred 2FA method.
Recent GitHub security incidents:
GitHub says hackers cloned code-signing certificates in breached
repository(1/30/2023)
Slack's private GitHub code repositories stolen over
holidays(1/5/2023)
Okta's source code stolen after GitHub repositories
hacked(12/21/2022)
Read more of this story at SoylentNews.
21:26
AMD Working On VirtIO GPU & Passthrough GPU Support For Xen Virtualization Phoronix
AMD is working to enable VirtIO GPU and pass-through GPU support for the Xen virtualization hypervisor with Radeon graphics...
21:21
21:14
Intel Sends Out Sixteenth Round Of Linux LAM Patches Phoronix
Intel's Linux engineers continue working on Linear Address Masking (LAM) for making use of untranslated address bits of 64-bit linear addresses so that it can be used for arbitrary metadata. The hope is that this LAM metadata can lead to more efficient address sanitizers, optimizations for JITs and VMs, and more, but it's been a lengthy journey getting the support upstreamed...
21:00
Empowering Corporate IP Professionals with a Connected Ecosystem IEEE Spectrum

In this age of continuous innovation, intellectual property (IP) is a core business asset. As IP becomes ever more central to businesses ability to innovate, compete and grow, managing these assets is becoming more criticaland more complex.
In this new paper, we review why a new approach to IP management is needed - enabling corporate teams to remove friction from their IP management workflows and unlock the full potential of their IP.
Download this whitepaper to learn:
- The real costs associated with this disconnected approach to managing IP assets
- The economic value of taking steps to optimize IP management
- How a unified full lifecycle approach benefits corporate IP teams
- About our commitment to delivering the industrys most comprehensive, fully integrated solution for corporate IP lifecycle management
20:54
Experimental RADV Vulkan Video Decoding For VP9 Phoronix
David Airlie has managed to get some early code in place for handling VP9 video decoding with Vulkan using the Mesa RADV driver. This early Vulkan Video VP9 support also is accompanied by an FFmpeg branch supporting this experimental Mesa extension...
20:51
The SVB demise is a fraudsters paradise, so take precautions Help Net Security
For those who havent followed the drama, Silicon Valley Bank has been shut down by the California Department of Financial Protection and Innovation, after a bank run that followed an insolvency risk and a stock crash. The Federal Deposit Insurance Corporation has been named the receiver, and has established a deposit insurance national bank, through which SVB customers will be able to access the insured part of their deposits. Understandably, there is a lot of More
The post The SVB demise is a fraudsters paradise, so take precautions appeared first on Help Net Security.
20:25
20:22
Nokia Magic Max, Nokia is About to Reclaim its Crown with this Ultimate Flagship Lifeboat News: The Blog

Reports say that the Nokia Magic Max will come in three different memory configurations. We will have 8GB, 12GB and 16GB of RAM with 256GB and 512GB storage options. It will launch with Android 13 out of the box with Snapdragon 8 Gen 2 SoC under the hood. We may also see a 6.7-inch AMOLED display with 120Hz refresh rate on the device. Corning Gorilla Glass 7 protection could be on the display of the upcoming flagship device from Nokia.
The device will feature a triple camera setup on the back with 144MP main sensor, 64MP ultrawide and 48MP Telephoto lens. Rumors have suggested a massive 7950mAh battery which can also charge from 0 to 100 within a few minutes, thanks to the 180W fast charger.
The memory configurations will determine the price of each variant. Nevertheless, sources have suggested the starting price to be around $550 (INR44,900). There is no firm rumor with respect to the launch date, but we expect to see the launch of the Nokia Magic Max in a matter of few weeks.
19:43
Marvel Wants Reddit to Expose Mods Suspected of Ant-Man 3 Leak TorrentFreak
 As Reddit fights to
protect the identities of users who simply participated in
piracy-related discussions, two new cases filed last Friday may
also prove controversial.
As Reddit fights to
protect the identities of users who simply participated in
piracy-related discussions, two new cases filed last Friday may
also prove controversial.
On February 17, 2023, Marvels Ant-Man and the Wasp: Quantumania officially kicked off Phase 5 of the Marvel Cinematic Universe (MCU). Distributed by Disney to lukewarm reviews, the movie took $105 million at the box office in its first week and then plummeted 70% to $32 million in week two.
Thanks to a leak posted online around a month before the movies theatrical debut, some fans already had an idea of how the movie would play out. Marvels pursuit of the leakers is likely to have a storyline all of its own.
MVL Film Finance LLC Targets Google
When MVL Film Finance LLC (MVL) was incorporated in 2004/5, its purpose was to finance Marvel Studios production of 10 live-action or animated films based on up to 10 of Marvels comic book characters. Several related business entities, including Marvel Studios and parent company Marvel Entertainment, are owned by The Walt Disney Company.
Last Friday at the United States District for the Northern District of California, Marvel Studios submitted a declaration in support of a DMCA subpoena application targeting Google. Matthew Slatoff, Marvels Vice President, Global Security & Content Protection, informed the Court that his responsibilities include monitoring and addressing infringement of MVL Film Finances rights.
According to Slatoffs declaration, on January 21, a Disney anti-piracy analyst submitted a copyright infringement notice to Google after discovering that Ant-Man and the Wasp: Quantumania content had been uploaded to systems operated by Google, without MVLs authorization. The takedown notice, submitted via Googles webform, contained a prompt from Google and a response from the rightsholder.
Identify and describe the copyrighted work: Unreleased leaked script of the new Disney movie Ant-man and the Wasp: Quantumania.
Marvel supplied a docs.google.com/document/ URL as the location for the allegedly infringing content. The content no longer exists at that location.
19:06
Security updates for Monday LWN.net
Security updates have been issued by Debian (imagemagick, libapache2-mod-auth-mellon, mpv, rails, and ruby-sidekiq), Fedora (chromium, dcmtk, and strongswan), Mageia (chromium-browser-stable, dcmtk, kernel, kernel-linus, libreswan, microcode, redis, and tmux), SUSE (postgresql14 and python39), and Ubuntu (linux-kvm, linux-raspi-5.4, and thunderbird).
19:00
AI and Savvy Marketing Create Dubious Moon Photos Hackaday

Taking a high-resolution photo of the moon is a surprisingly difficult task. Not only is a long enough lens required, but the camera typically needs to be mounted on a tracking system of some kind, as the moon moves too fast for the long exposure times needed. Thats why plenty were skeptical of Samsungs claims that their latest smart phone cameras could actually photograph this celestial body with any degree of detail. It turns out that this skepticism might be warranted.
Samsungs marketing department is claiming that this phone is using artificial intelligence to improve photos, which should quickly raise a red flag for anyone technically minded. [ibreakphotos] wanted to put this to the test rather than speculate, so a high-resolution image of the moon was modified in such a way that most of the fine detail of the image was lost. Displaying this image on a monitor, standing across the room, and using the smartphone in question reveals details in the image that cant possibly be there.
The image that accompanies this post shows the two images side-by-side for those skeptical of these claims, but from what we can tell it looks like this is essentially an AI system copy-pasting the moon into images it thinks are of the moon its...
18:52
When Should Data Scientists Try a New Technique? SoylentNews
If a scientist wanted to forecast ocean currents to understand how pollution travels after an oil spill, she could use a common approach that looks at currents traveling between 10 and 200 kilometers. Or, she could choose a newer model that also includes shorter currents. This might be more accurate, but it could also require learning new software or running new computational experiments. How to know if it will be worth the time, cost, and effort to use the new method?
A new approach developed by MIT researchers could help data scientists answer this question, whether they are looking at statistics on ocean currents, violent crime, children's reading ability, or any number of other types of datasets.
The team created a new measure, known as the "c-value," that helps users choose between techniques based on the chance that a new method is more accurate for a specific dataset. This measure answers the question "is it likely that the new method is more accurate for this data than the common approach?"
Traditionally, statisticians compare methods by averaging a method's accuracy across all possible datasets. But just because a new method is better for all datasets on average doesn't mean it will actually provide a better estimate using one particular dataset. Averages are not application-specific.
So, researchers from MIT and elsewhere created the c-value, which is a dataset-specific tool. A high c-value means it is unlikely a new method will be less accurate than the original method on a specific data problem.
Read more of this story at SoylentNews.
18:49
Sirius UK CEO Resigns (or Gets Sacked) and Completely Deletes His Whole Past With Sirius Open Source Techrights
Not a single mention of Sirius, which used to be all over his LinkedIn page only weeks ago
Summary: The above person was with Sirius since 2017 and CEO for about 2 years; hes now hiding any connection to the company (it used to be all over his LinkedIn profile, from top to bottom); any attempts to send him E-mails bounce back from GMail, so he is eager to leave no paths open
18:36
Researchers Uncover Over a Dozen Security Flaws in Akuvox E11 Smart Intercom The Hacker News
More than a dozen security flaws have been disclosed in E11, a smart intercom product made by Chinese company Akuvox. "The vulnerabilities could allow attackers to execute code remotely in order to activate and control the device's camera and microphone, steal video and images, or gain a network foothold," Claroty security researcher Vera Mens said in a technical write-up. Akuvox E11 is
18:23
Uneven Circuit Aging Becoming A Bigger Problem Lifeboat News: The Blog
The industry is gaining ground in understanding how aging affects reliability, but more variables make it harder to fix.
Circuit aging is emerging as a first-order design challenge as engineering teams look for new ways to improve reliability and ensure the functionality of chips throughout their expected lifetimes.
The need for reliability is obvious in data centers and automobiles, where a chip failure could result in downtime or injury. It also is increasingly important in mobile and consumer electronics, which are being used for applications such as in-home health monitoring or for navigation, and where the cost of the devices has been steadily rising. But aging also needs to be assessed in the context of variation models from the foundries, different use cases that may stress various components in different ways, and different power and thermal profiles, all of which makes it harder to accurately predict how a chip will behave over time.
18:23
Designing for Data Flow Lifeboat News: The Blog
Processing more data in more places while minimizing its movement becomes a requirement and a challenge.
Movement and management of data inside and outside of chips is becoming a central theme for a growing number of electronic systems, and a huge challenge for all of them.
Entirely new architectures and techniques are being developed to reduce the movement of data and to accomplish more per compute cycle, and to speed the transfer of data between various components on a chip and between chips in a package. Alongside of that, new materials are being developed to increase electron mobility and to reduce resistance and capacitance.
18:23
Strange Circular Sand Dunes Discovered on Mars Lifeboat News: The Blog
Sand dunes of many shapes and sizes are common on Mars. In this example, the dunes are almost perfectly circular, which is unusual. Credit: NASA/JPL-Caltech/University of Arizona.
Sand dunes of many shapes and sizes are common on Mars.
Mars is the second smallest planet in our solar system and the fourth planet from the sun. It is a dusty, cold, desert world with a very thin atmosphere. Iron oxide is prevalent in Mars surface resulting in its reddish color and its nickname The Red Planet. Mars name comes from the Roman god of war.
18:13
IRC Proceedings: Sunday, March 12, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-120323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-120323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-120323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-120323.gmi
Over HTTP:
|
... |
18:00
How to Make Peace with Canada Geese Terra Forming Terra
...
Sugar-coated antibodies cross blood-brain barrier to fight Alzheimer's Terra Forming Terra

...
Clean energy breakthrough as electricity is produced out of thin air Terra Forming Terra

Do not ovethink this guys. Just make it work handily.
Behold 900+ Magnificent Botanical Collages Created by a 72-Year-Old Widow, Starting in 1772 Terra Forming Terra

17:46
Theo de Raadt to be presenting at CanSecWest. OpenBSD Journal
Dragos Ruiu recently announced that Theo de Raadt will be presenting at this year's CanSecWest, March 22-24 2023 in Vancouver, BC.
17:42
Game of Trees 0.86 released OpenBSD Journal
Version 0.86 of Game of Trees has been released (and the port updated):
17:24
The risk of pasting confidential company data into ChatGPT Security Affairs
Experts warn that employees are providing sensitive corporate data to the popular artificial intelligence chatbot model ChatGPT.
Researchers from Cyberhaven Labs analyzed the use of ChatGPT by 1.6 million workers at companies across industries. They reported that 5.6% of them have used it in the workplace and 4.9% have provided company data to the popular chatbot model since it launched. ChatGPT uses this data to build its knowledge base, but it publicly shares information built on it.
The use of ChatGPT is becoming a serious problem in the workspace, it can potentially cause the leak of sensitive and confidential data. For this reason, companies like JP Morgan and Verizon are blocking access to the chatbot over concerns about confidential data.
The experts reported that less than one percent (0.9%) of employees is responsible for 80% of leaks caused by pasting company data into the chatbot. This percentage could rapidly increase in the next months with the integration of the technology in multiple services, for example through the use of ChatGPT API.
Employees believe that the artificial intelligence chatbot developed by OpenAI can significatively improve their productivity.
The experts also warn that enterprise security software cannot monitor the use of ChatGPT by employees and prevent the leak of sensitive/confidential company data.
Since ChatGPT launched publicly, 5.6% of knowledge workers have tried using it at least once in the workplace. Furthermore, 2.3% of employees have put confidential company data into ChatGPT. reads the report published by Cyberhaven Labs. Despite a growing number of companies outright blocking access to ChatGPT, usage continues to grow exponentially. On March 1, our product detected a record 3,381 attempts to paste corporate data into ChatGPT per 100,000 employees, defined as data egress events in the chart below.
The researchers also monitored workers copying data out of the popular chatbot and pasting it elsewhere, like a company email, Google Doc, or their source code editor. They noticed that employees copy data out of the chatbot more than they paste company data into ChatGPT at a nearly 2-to-1 ratio.
The researchers pointed out that the average company leaks sensitive data to ChatGPT hundreds of times each week. For example, during the week of February 26 March 4, workers at the average company with 100,000 employees provided confidential documents into the AI-based chatbot 199 times, client data 173 times, and source code 159 times.
...17:15
KamiKakaBot Malware Used in Latest Dark Pink APT Attacks on Southeast Asian Targets The Hacker News
The Dark Pink advanced persistent threat (APT) actor has been linked to a fresh set of attacks targeting government and military entities in Southeast Asian countries with a malware called KamiKakaBot. Dark Pink, also called Saaiwc, was extensively profiled by Group-IB earlier this year, describing its use of custom tools such as TelePowerBot and KamiKakaBot to run arbitrary commands and
16:30
TSA issues additional cybersecurity rules for the aviation sector Help Net Security
The Transportation Security Administration (TSA) issued a new cybersecurity amendment to the security programs of certain TSA-regulated (airport and aircraft) operators in the aviation sector, following similar measures announced in October 2022 for passenger and freight railroad carriers. This is part of the Department of Homeland Securitys efforts to increase the cybersecurity resilience of U.S. critical infrastructure and follows extensive collaboration with aviation partners. Protecting our nations transportation system is our highest priority and TSA More
The post TSA issues additional cybersecurity rules for the aviation sector appeared first on Help Net Security.
16:07
ISS Swerves to Avoid Collision With Earth-Imaging Satellite SoylentNews
Earlier this week, the International Space Station was forced to adjust its orbit to avoid an encroaching commercial satellite. The object is likely one of many Earth-observing satellites that are falling into and aligning with the space station's orbital path, according to experts.
On Monday, the Progress 83 resupply ship that's docked to the space station fired its engines for just over six minutes, slightly raising the orbit of the ISS in order to avoid an approaching satellite, NASA wrote in a blog post. The space agency did not identify the object, except to say that it was an "Earth observation satellite."
However, there is speculation that the satellite in question may be Argentina's Nusat-17, one of 10 commercial Earth observation satellites form the Aleph-1 constellation operated by Satellogic. Jonathan McDowell, an astrophysicist at the Harvard-Smithsonian Center for Astrophysics, wrote on Twitter that the orbits of the Satellogic constellation has been gradually decaying and the satellites are now crossing the orbit of the ISS.
The latest ISS maneuver points to a larger issue of the growing number of satellites, both defunct and operational, and debris that pose a threat to orbiting spacecraft. More than 27,000 pieces of orbital debris are currently being tracked by the Department of Defense's global Space Surveillance Network, with lots of smaller pieces also floating around undetected.
Read more of this story at SoylentNews.
16:00
Fighting financial fraud through fusion centers Help Net Security
Keeping up with financial fraud is incredibly difficult because accurate fraud detection requires a deep, real-time analysis of all the events surrounding a transaction. Consider a typical payment transaction: A single transfer of funds to a new payee may not raise suspicion, but when authentication records show a discrepancy between the account owners usual geographic location and that of several device logins from multiple IP addresses in the same time frame, the transfer should be More
The post Fighting financial fraud through fusion centers appeared first on Help Net Security.
16:00
Flipper Zero Mayhem Hat Adds Camera, More Radios Hackaday

For a device advertised as the Multi-tool Device for Hackers, the Flipper Zero already offers a considerable list of onboard capabilities. But some hard decisions had to be made to get the retail price down, so features like WiFi and Bluetooth had to be left off. Luckily, theres an expansion interface along the top of the device which makes it possible to plug in additional hardware.
One of those expansions is the Mayhem Hat from [Erwin Ried]. This board adds many requested features to the Flipper Zero, as well as some that might not seem as obvious. The addition of an ESP32-CAM brings WiFi and Bluetooth to the party, while also unlocking access to the highly-capable ESP32Marauder firmware and the plethora of security research tools therein.
15:30
Understanding password behavior key to developing stronger cybersecurity protocols Help Net Security
Passwords are still the weakest link in an organizations network, as proven by the analysis of over 800 million breached passwords, according to Specops Software. The study found 88% of passwords used in successful attacks consisted of 12 characters or less, with the most common being 8 characters (24%). The most common base terms used in passwords were: password, admin, welcome and p@ssw0rd. Passwords containing only lowercase letters were the most common character combination found, More
The post Understanding password behavior key to developing stronger cybersecurity protocols appeared first on Help Net Security.
15:15
FBI Finally Admits to Buying Location Data on Americans cryptogon.com
As disturbing as this Ars Technica piece is, the actual situation might as well be infinitely worse. In 2013, we learned that law enforcement was laundering data collected through U.S. national security intercept systems for use against Americans, U.S. Communications Intelligence Secretly Shared with Law Enforcement for Use Against Americans in Criminal Investigations: Its just []
15:00
New algorithm may change the future of secure communication Help Net Security
Researchers have made a significant breakthrough in secure communication by developing an algorithm that conceals sensitive information so effectively that it is impossible to detect anything hidden. The team, led by the University of Oxford in close collaboration with Carnegie Mellon University, envisages that this method may soon be used widely in digital human communications, including social media and private messaging. In particular, the ability to send perfectly secure information may empower vulnerable groups, such More
The post New algorithm may change the future of secure communication appeared first on Help Net Security.
15:00
Linux 6.3-rc2 Released With Two AMD Workarounds, Drops The Useless r8188eu Driver Phoronix
The Linux 6.3-rc2 kernel is out today as the second weekly kernel test release since last weekend's closure of the Linux 6.3 merge window...
14:41
Deluxe Home Vintage Computer Den cryptogon.com
Via: Ars Technica: In a world where millions of people carry a 1990s-grade supercomputer in their pockets, its fun to revisit tech from a time when a 1 megahertz machine on a desktop represented a significant leap forward. Recently, a collector named Brian Green showed off his vintage computer collection on Twitter, and we thought []
13:35
Audio: Sirius Never Paid the Pension Provider, Staff Was in Effect Defrauded schestowitz.com
Video download link |
md5sum fadf7fcdfd1c9473e9ab4e8ebfed252e
Sirius Pension Crimes
Creative Commons Attribution-No Derivative Works 4.0
Summary: The company known as Sirius Open Source has stolen money of many workers; today we share audio of management at the pension provider admitting behaviour to that effect
THE news will be full of discussions about banks later today. People cannot access their own accounts, businesses cannot pay their workers, and as just noted two or three banks have already been suspended (some over the weekend). The time seems right to continue with our series about how Sirius plundered not just my pension but also colleagues or, as it seems on the surface, put the pension money in its own pockets (I can think of 3 people who conspired to do this) instead of a pension fund, in effect embezzling workers and falsifying payslips. As readers may recall from December, there were incidents of payslips not being sent out at all (for long periods of time, including for months before I resigned).
Over the next few weeks well share more information about what happened. The lesson for the general public is, check whether what employers say about pensions is true and get in contact with pension providers to verify youre not being lied to (validation of claims is imperative).
Of all the payslips I do have, in about 60 of them I have evidence of pensions being contributed to; but thats false, as the company did not pass the money and former colleagues were similarly embezzled. Played out in the video above (from a 55-minute audio) is 0-1:20, 1:50-, 2:30-5:40, 11:50-20:00, 21:18-22:08, 22:15-, 26:30-36:30, 39:40-, 41:55-51:00, 51:10-. I basically skip the pauses (waiting on the line), some personally-identifying details/codes and towards the end I note that even though the manager said shed contact me today (6 days ago) it never happened. They dont seem to consider embezzlement impacting many employees im...
13:26
The Sirius Pensions Heist Confirmed by the Pension Provider Techrights
Video download link |
md5sum fadf7fcdfd1c9473e9ab4e8ebfed252e
Sirius Pension Crimes
Creative Commons Attribution-No Derivative Works 4.0
Summary: The company known as Sirius Open Source has stolen money of many workers; today we share audio of management at the pension provider admitting behaviour to that effect
THE news will be full of discussions about banks later today. People cannot access their own accounts, businesses cannot pay their workers, and as just noted two or three banks have already been suspended (some over the weekend). The time seems right to continue with our series about how Sirius plundered not just my pension but also colleagues or, as it seems on the surface, put the pension money in its own pockets (I can think of 3 people who conspired to do this) instead of a pension fund, in effect embezzling workers and falsifying payslips. As readers may recall from December, there were incidents of payslips not being sent out at all (for long periods of time, including for months before I resigned).
Over the next few weeks well share more information about what happened. The lesson for the general public is, check whether what employers say about pensions is true and get in contact with pension providers to verify youre not being lied to (validation of claims is imperative).
In some ways it feels like 2008 re-enacted, except now they blame Russia, China, pandemic, crypto etc.Of all the payslips I do have, in about 60 of them I have evidence of pensions being contributed to; but thats false, as the company did not pass the money and former colleagues were similarly embezzled. Played out in the video above (from a 55-minute audio) is 0-1:20, 1:50-, 2:3...
13:18
The Time Russians Really Did Target Americans With Microwaves SoylentNews
The Time Russians Really Did Target Americans With Microwaves
A year before his arrival, State Department officials had told embassy staffers and their families that the Soviet Union had been blasting some kind of microwave beam at the embassy for up to 14 hours per day. But American higher-ups said there was little reason for concern. Issuing a "Fact Sheet," [1976] the State Department said that this microwave beam later dubbed the "Moscow Signal" was "no cause for concern," as "no causal relationship had been established between these microwave transmissions and any health problems."
There was, in other words, nothing to worry about. As a precaution, American officials erected aluminum "screening" around the embassy all the better to "reduce the anxiety of employees." But that was it. And so Schumaker went about his work, day in and day out. For years, he and dozens of others operated out of the American embassy, assured that the microwave radiation was perfectly normal.
It was only years later, when Schumaker received a surprise leukemia diagnosis and after multiple American ambassadors had already died from cancer, with the another diagnosed with a "severe blood disorder" that Schumaker realized that microwave radiation, and the U.S.'s lackadaisical response, was far more disastrous, and even fatal, than he ever thought. And in recent months, that realization only deepened, for a pair of reasons.
First, a tranche of newly declassified documents confirmed that the Soviets saturated American embassy staffers in decades of elevated microwave radiation and American higher-ups spent years trying to sweep the entire affair under the rug. And second, recent revelations about the so-called "Havana Syndrome" have given Schumaker and other diplomats who remember the days of Moscow Signal a sense of, as he sees it, "dj vu all over again."
Read more of this story at SoylentNews.
13:00
Efficient x86_64 Emulation with Box86 Hackaday

Running applications on a different architecture than the one for which they were compiled is a common occurrence, not in the least with Apples architectural migration every decade or so. Its also commonly used with for example ARM, OpenRISC, and RISC-V systems to run applications that are only available for x86 or x86_64. While QEMU and kin are often used here, theyre pretty resource heavy, which is where an option like Box86 and its 64-bit sibling Box64 are attractive options. Unlike QEMU, both offer dynamic recompilation and redirection of dynamic library calls to native libraries, including those for SDL and OpenGL.
Both are available on GitHub under an MIT license, with Box64 probably the most interesting these days as applications and games have moved on to a 64-bit only world. The only hard requirement that Box64 has for a host system is that it is little-endian, which is a pretty easy requirement to meet. The most recent release was on March 10th, with Box86 0.3 and Box64 0.2.2. As essentially a translation layer, it does not offer full compatibility with every bit of software out there, but it...
12:47
Mozilla and Many Other Companies Are in Trouble as Silicon Valley Bubbles Are Bursting Techrights
Video download link |
md5sum 2c5c09befcd83be44bd00fedc02d351c
Mozilla and SVB
Creative Commons Attribution-No Derivative Works 4.0
Summary: Some banks are collapsing, including very major ones; it seems like Mozilla will be among the companies affected
THE US regulators have just shut down another bank the second if not third one in days (during weekend). This is a very serious matter and itll caused a lot of panic later today when European markets open (and then American ones). What companies that we know and care about are impacted by this? Well, Mozilla seems like one of them.
The video above is a bunch of more personal thoughts and my interpretation of the situation. These turbulent times can affect Free software (negatively) and its safe to predict the matter will be in the news for weeks to come.
11:19
Kernel prepatch 6.3-rc2 LWN.net
The 6.3-rc2 kernel prepatch is out.
This one looks fairly normal, although if you look at the diffs, they are dominated by the removal of a staging driver (r8188eu) that has been superceded by a proper driver. That removal itself is 90% of the diffs. But if you filter that out, it all looks normal
11:12
DistroWatch Weekly, Issue 1010 DistroWatch.com: News
This week in DistroWatch Weekly: Review: blendOS 2023.01.26News: Improved network widget comes to elementary OS, Vanilla OS changes its base, Slackware phases out legacy dependenciesQuestions and answers: Keeping track of which files a package installsReleased last week: LibreELEC 11.0.0, Rescuezilla 2.4.2, siduction 22.1.1, helloSystem 0.8.1Torrent corner: SparkyLinuxUpcoming releases:....
11:00
HPR3811: mkfifo and named pipes Hacker Public Radio
A named pipe is like a UNIX pipe, except it takes the form of a file. $ mkfifo mypipe $ echo "Hacker Public Radio" > mypipe & $ cat mypipe Hacker Public Radio
Covert Cloud Communication with Lambdas It Will Never Work in Theory
The biggest change in practical computing in the last decade has been the nearly-universal return to shared hardware. As with the mainframes of my youth, companies rent time on other people's computers rather than buying and managing their own. And as with any form of sharing, that opens up new security holes and new avenues of attack.
This paper looks at something I would once have dismisssed as Hollywood word salad: covert communication between lambdas co-resident on the same physical server. The authors leverage the hardware's memory bus to detect what's running, and show that they can send a couple of hundred bits per second between supposedly-isolated processes. That might not seem like a lot, but it's more than enough to share a password or a private key, and like most of computer security it's both fascinating and frightening.
Anil Yelam, Shibani Subbareddy, Keerthana Ganesan, Stefan Savage, and Ariana Mirian. CoResident evil: covert communication in the cloud with lambdas. In Proceedings of the Web Conference 2021. ACM, Apr 2021. doi:10.1145/3442381.3450100.
"Serverless" cloud services, such as AWS lambdas, are one of the fastest growing segments of the cloud services market. These services are popular in part due to their light-weight nature and flexibility in scheduling and cost, however the security issues associated with serverless computing are not well understood. In this work, we explore the feasibility of constructing a practical covert channel from lambdas. We establish that a fast co-residence detection for lambdas is key to enabling such a covert channel, and proceed to develop a reliable and scalable co-residence detector based on the memory bus hardware. Our technique enables dynamic discovery for co-resident lambdas and is incredibly fast, executing in a matter of seconds. We evaluate our approach for correctness and scalability, and use it to establish covert channels and perform data transfer on AWS lambdas. We show that we can establish hundreds of individual covert channels for every 1000 lambdas deployed, and each of those channels can send data at a rate of ~200 bits per second, thus demonstrating that covert communication via lambdas is entirely feasible.
Linux 6.3-rc2 Introduces Stuttering Workaround For AMD Ryzen PCs Due To fTPM RNG Phoronix
Since the Linux 6.1 kernel various users have reported system stuttering issues when using modern AMD Ryzen systems. This has been similar to an "intermittent system stutter" issue AMD disclosed last year for Windows 10 and Windows 11 while now for today's Linux 6.3-rc2 a workaround is finally being merged that in turn will also be back-ported to the stable kernel series...
10:00
Hackaday Links: March 12, 2023 Hackaday

With a long history of nearly universal hate for their products, youd think printer manufacturers would by now have found ways to back off from the policies that only seem to keep aggravating customers. But rather than make it a financially wiser decision to throw out a printer and buy a new one than to buy new ink cartridges or toners, manufacturers keep coming up with new and devious ways to piss customers off. Case in point: Hewlett-Packard now seems to be bricking printers with third-party ink cartridges. Reports from users say that a new error message has popped up on screens of printers with non-HP cartridges installed warning that further use of the printer has been blocked. Previously, printers just warned about potential quality issues from non-HP consumables, but now theyre essentially bricked until you cough up the money for legit HP cartridges. Users who have contacted HP support say that they were told the change occurred because of a recent firmware update sent to the printer, so thats comforting.
In other news of corporate unpleasantness, if youve bought into t...
08:34
NASA Ready for Artemis II SoylentNews
The Moon or Bust, Says NASA, After Successful Test Flight
Heat shield sustained more damage than expected, but this shouldn't discourage astronauts:
NASA is ready to fly a crew of astronauts to the Moon next year after the success of the first test flight of its Space Launch System (SLS) rocket and Orion capsule.
[...] Orion fulfilled 161 test objectives and was more energy efficient than predicted, generating 20 per cent more power than predicted while consuming about 25 per cent less power than expected. All maneuvers including flying to and from the Moon, returning to Earth, and releasing the parachute for splashdown into the Pacific Ocean were executed without any major problems.
There are, however, a few niggling complications. Orion's latching current limiters which act like circuit breakers to transfer and distribute power from its solar panels switched open randomly during its flight for unknown reasons. Also, the material covering the heat shield used to protect the capsule and prevent it and any occupants from incineration as Orion re-enters Earth's atmosphere deteriorated more than NASA thought it would.
Little things like that.
The mobile launcher part of the SLS also sustained more damage than expected. NASA said its cryogenic fuel lines corroded, while 60 panels and cabinets broke, as did its elevators and blast shields. Officials continue to review hundreds of gigabytes worth of data gathered from the mission.
[...] "We're learning as much as we possibly can from Artemis I to ensure we fully understand every aspect of our systems and feed those lessons learned into how we plan for and fly crewed missions," said Jim Free, NASA associate administrator for the Exploration Systems Development Mission Directorate, in a prepared statement. "Safely flying crew is our top priority for Artemis II."
Engineers will, for example, modify the mobile launcher for the upcoming Artemis mission. They will build an emergency egress system at the launchpad in case the crew needs to make a last-minute exit from the rocket.
Read more of this story at SoylentNews.
07:46
Security Affairs newsletter Round 410 by Pierluigi Paganini Security Affairs
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are free for you in your email box.
If you want to also receive for free the newsletter with the international press subscribe here.
07:00
A Parts Bin Cyberdeck Built for Satellite Hacking Hackaday

While theres little in the way of hard rules dictating what constitutes a cyberdeck, one popular opinion is that it should be a piecemeal affair a custom rig built up of whatever high-tech detritus the intrepid hacker can get their hands on, whether it be through trades or the time-honored tradition of dumpster diving. It should also be functional, and ideally, capable of some feats which would be difficult to accomplish with a garden variety laptop.
If youre looking for an example that embraces these concepts to the fullest, look no further than the Spacedeck built by [saveitforparts]. Combining a touch screen all-in-one computer pulled from a police cruiser in the early 2000s, an RTL-SDR, and the contents of several parts bins, the rig is designed to work in conjunction with his growing collection of motorized satellite dishes to sniff out signals from space.
06:37
Robin Mansukhani, CEO of Deciduous Therapeutics, a venture-backed startup developing novel immunotherapies to treat age-related diseases, joins our Life Extension Board. Lifeboat News
Robin Mansukhani, CEO of Deciduous Therapeutics, a venture-backed startup developing novel immunotherapies to treat age-related diseases, joins our Life Extension Board.
05:45
GNOME 44 Release Candidate Arrives With Many Last Minute Changes Phoronix
The GNOME 44 release candidate was officially declared today as desktop later this month...
04:41
Why Would OpenAI Send ChatGPT Takedown Notices to Google? TorrentFreak
 ChatGPT
has captured the imagination of millions of people, offering a
glimpse of what an AI-assisted future might look like.
ChatGPT
has captured the imagination of millions of people, offering a
glimpse of what an AI-assisted future might look like.
The new technology also brings up novel copyright questions. Several people are worried that their work is being used to train AI without any form of compensation, for example.
Parent company OpenAI may in turn be worried that third parties are exploiting the ChatGPT model without permission. Thats what a recent DMCA takedown notice sent to Google tends to suggest.
OpenAIs Takedown Notice
The takedown request lists OpenAI as the sender and targets several ChatGPT-related links. These include the ChatGod app, which has since been removed from Google Play, as well as the Chat AI Pro app for iOS.
The notice isnt just restricted to apps. It also lists a PC Guide article with information on the chatbot, which appears to be relatively harmless.
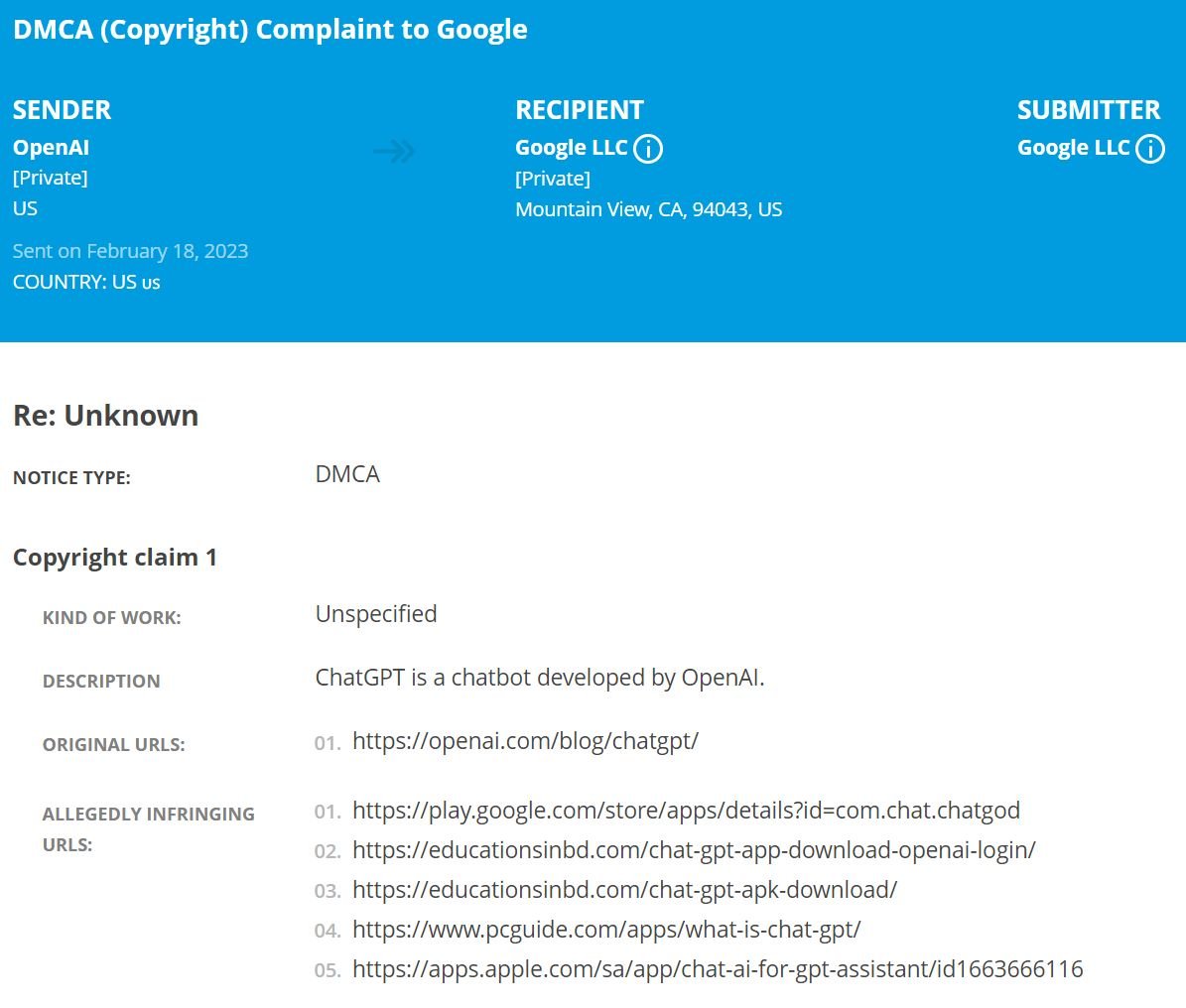
This isnt the first time that an OpenAI takedown notice has shown up in Googles transparency report. In December, a similar DMCA request asked for the removal of an AI writing tools GitHub repository.
Legitimate?
These enforcement actions are certainly newsworthy, but we cant independently confirm that OpenAI sent them. In the past, we have seen plenty of imposters claiming to be reputable rightsholders, and it could be the case here as well.
TorrentFreak reached out to OpenAI to confirm or deny the legitimacy of the notices but the organization didnt respond. Googles view on the matter is also unknown. What we do know is that the search engine hasnt removed any of the reported URLs.
Without a co...
04:00
Building the Sanni Cartridge Reader To Back Up and Restore Games and Saves Hackaday

Game cartridges are generally seen as a read-only medium with the contents as immutable as text chiseled into a granite slab, and with accompanying save files on the cartridge surviving for generations. The unfortunate truth is that as with any media storage, cartridges can and do fail, and save files are often just ethereal bits in battery-backed SRAM. This makes being able to copy not only the game data but also the save files off these cartridges essential. Projects like the Open Source Cartridge Reader by [sanni] make this something that everyone can do.
Intended to be a kind of Swiss Army knife of game cartridges, many game systems are supported directly, and many others via (user-created) adapters. A how-to-build tutorial is provided on the project wiki, though anyone inte...
03:50
DuckDuckGo's New Wikipedia Summary Bot: We Fully Expect It to Make Mistakes SoylentNews
Not to be left out of the rush to integrate generative AI into search, on Wednesday DuckDuckGo announced DuckAssist, an AI-powered factual summary service powered by technology from Anthropic and OpenAI. It is available for free today as a wide beta test for users of DuckDuckGo's browser extensions and browsing apps. Being powered by an AI model, the company admits that DuckAssist might make stuff up but hopes it will happen rarely.
Here's how it works: If a DuckDuckGo user searches a question that can be answered by Wikipedia, DuckAssist may appear and use AI natural language technology to generate a brief summary of what it finds in Wikipedia, with source links listed below. The summary appears above DuckDuckGo's regular search results in a special box.
[...] Update (March 9, 2023): We spoke with a representative of DuckDuckGo and they said they're using OpenAI's GPT-3.5 and Anthropic's Claude as LLMs. "We're experimenting with OpenAI's recently announced Turbo model, too," they said.
Related:
Robots
Let ChatGPT Touch the Real World Thanks to Microsoft (Article
has a bunch of other SoylentNews related links as well.)
Read more of this story at SoylentNews.
03:31
Recognizing the worst in government transparency.
The Foilies are co-written by EFF and MuckRock News and published in alternative newspapers around the country through a partnership with the Association of Alternative Newsmedia.
It seems like these days, everyone is finding classified
documents in places they shouldn't be: their homes, their offices,
their storage lockers, their garages, their guitar cases, between
the cracks of their couches, under some withered celery in the
vegetable drawer OK, we're exaggeratingbut it is getting
ridiculous.
While the pundits continue to speculate whether President
Donald Trump, Vice President Mike Pence and President Joe Biden put
national security at risk by hoarding these secrets, that
ultimately might not be the biggest problem.
What we know for sure is that these episodes illustrate
overlapping problems for government transparency. It reveals an
epidemic of over-aggressive classification of documents that could
easily be made public. It means that an untold number of documents
that belong to the public went missingeven though we may not get to
see them for at least 25 years, when the law requires a mandatory
declassification review. And then there's the big, troubling
transparency question: If these officials pocketed national
secrets, what other troves of non-secret but nonetheless important
documents did they hold on to, potentially frustrating the public's
ability to ever see them?
It doesn't do much good to file a Freedom of Information Act request for records that have mysteriously disappeared.
Misbehavior like this is why we created The Foilies, our annual tongue-in-cheek awards for agencies and officials that thwart the public's right to government information or otherwise respond outrageously to requests for documents and records. Each year, the Electronic Frontier Foundation and MuckRock News, in partnership with the Association of Alternative Newsmedia, publish this list of ne'er-do-wells to celebrate Sunshine Week (March 12-18)an annual event to raise the profile of the democratic concept of government transparency.
It may be many years before the public learns what secret and not-so-secret documents weren't turned over by past administrations to the National Archives. But when we do, we'll be sure to nominate them for the top prizes. In the meantime, we have no shortage of redaction rascals and right-to-know knaves, from agencies assessing astronomical fees to obtain documents to officials who overtly obstruct openness to protect corporat...
03:14
Links 12/03/2023: GNOME Extensions Site Adds Download Counts Techrights
![]()
Contents
-
GNU/Linux
-
Instructionals/Technical
-
Citizix How to set up Wireguard on Ubuntu 22.04
WireGuard is a communication protocol and free and open-source software that implements encrypted virtual private networks, and was designed with the goals of ease of use, high speed performance, and low attack surface. It is a lightweight Virtual Private Network (VPN) that supports IPv4 and IPv6 connections.
-
ID Root How To Install Ansible on Fedora 37
In this tutorial, we will show you how to install Ansible on Fedora 37. For those of y...
-
-
03:08
Linux Landing XMM Register Rollback Workaround For AMD Zen 1 / Zen 2 CPUs Phoronix
Sent in this morning via x86/urgent for integration into Linux 6.3 and also for back-porting to stable kernel series is disabling the XSAVES instruction for AMD Zen 1 and Zen 2 processors to workaround an AMD processor erratum made public last year...
01:25
Acronis states that only one customers account has been compromised. Much ado about nothing Security Affairs
Acronis downplays the severity of the recent security breach explaining that only a single customers account was compromised.
The CISO of Acronis downplayed a recent intrusion, revealing that only one customer was impacted.
This week a threat actor, who goes online with the moniker kernelware, claimed the theft of data from technology firm Acronis and started leaking it on the cybercrime forum Breached Forums.
The threat actor is the same who recently offered for sale the data stolen from Taiwanese multinational hardware and electronics corporation Acer.
The Acronis leak contains multiple certificate files, command logs, system configurations, system information logs, filesystem archives, python scripts for the companys maria.db database, backup configuration stuff, screenshots of backup operations,
Based on our investigation so far, the credentials used by a single specific customer to upload diagnostic data to Acronis support have been compromised. We are working with that customer and have suspended account access as we resolve the issue. We also shared IOCs with our industry partners and work with law enforcement. said Acronis CEO Kevin Reed. No other system or credential has been affected. There is no evidence of any other successful attack, nor there is any data in the leak that is not in the folder of that one customer. Our security team is obviously on high alert and the investigation continues.
The company added that its products were not affected by the security breach and that it is not aware of vulnerabilities affecting its s...
01:12
Yellen Says No Federal Bailout for Silicon Valley Bank Another Banking System Bailout Announced cryptogon.com
Update: Fed Panics: Signature Bank Closed By Regulators; Fed, TSY, FDIC Announce Another Banking System Bailout: On Friday, we said that the Fed will have to make an announcement before the Monday open, and we didnt have to wait that long: in fact, the Fed waited just 15 minutes after futures opened for trading to []
01:00
Large E-Paper Slow Movie Player Offers Great Docs Hackaday

Over the last couple of years weve seen several iterations of the slow movie player concept, where a film is broken up into individual frames which are displayed on an e-paper display for a few minutes at a time. This turns your favorite movie into a constantly changing piece of long-term art. Unfortunately, due to the relatively high cost of e-paper panels, most of the examples weve seen have only been a few inches across.
Of course, technology tends to get cheaper with time, which has allowed [szantaii] to put together this beautiful 10.3-inch version. With a 1872 1404 Waveshare panel capable of displaying 16 shades of gray and a Raspberry Pi Zero 2 W installed in a commercially purchased frame, the final product looks very professional. It certainly wouldnt look out of place in a well-appointed living room.
01:00
The EV Battery Wish List IEEE Spectrum

Electric cars barely existed in 2010, when the Tesla Model S was still a glint in Elon Musks eye. Now more than 20 million EVs girdle the globe, according to BloombergNEFand that count is expected to nearly quadruple to 77 million by 2025. A battery will be the high-voltage heart of each of those 77 million electric vehicles, and by far their most expensive component, setting off a worldwide race to ethically source their materials and crank up production to meet exploding demand.
EVs may have seized a record 5.8 percent of the United States market in 2022, according to J.D. Power, and could approach 11 percent of the global market this year. But experts still believe that better batteries, and many more of them, are a key to EVs reaching a market tipping point, even as Reuters projects automakers spending a whopping $1.2 trillion to develop and produce EVs through 2030.
IEEE Spectrum asked five industry experts to gaze deeply into their own crystal balls and outline what needs to happen in the EV battery space to wean the world off fossil-fueled transportation and onto the plug. Heres what they said:
Emad Dlala, Lucid Motors, vice-president of powertrain
Upstart Lucid Motors hasnt built many cars, but its built a reputation with the record-setting, 830-kilometer driving range of the Air Grand Touring Performance sedan. That range is a testament to Lucids obsessive pursuit of efficiency: The Air uses the same 2170-format cylindrical cells (supplied by Samsung SDI) as many EVs, but ekes out more miles via superior battery management, compact-yet-muscular power units and slippery aerodynamics.
Sophisticated chassis and battery design gives new life to lesser chemistriesespecially lithium iron phosphate thats the hottest thing in batteries around the worldthat would otherwise be uncompetitive and obsolete.
One might think Lucid would call for every electric model to cover such vast distances. Instead, Lucid leaders see a bright future in cars that aim for maximum efficiency rather than range...
00:51
Linux and Scanners and Stuff Random Thoughts
Some years back, I had to scan a bunch of stuff for various projects. One of them was the Lanterne series thing its totally frivolous, which is what makes it fun.
But now Ive managed to buy a whole bunch more books, so it was time to scan some more covers. (Thats the result of hunting books for three years up there.)
So I wheeled out my Epson DS-50000 again and dusted off three years worth of dust and plugged it into my laptop.
And, wonders of wonders, it worked fine.
Except it was stran...
00:25
Scientists discovered a totally new way to measure time Lifeboat News: The Blog
Measuring time might not seem like that complex of a thing. After all, we rely on simply counting seconds between the then and the now. But when you really start to break time down to the quantum level, things begin to get a bit foggier.
00:24
Harvard Professor Reveals 4 EASY Ways to Slow and Reverse Aging | Dr. David Sinclair Lifeboat News: The Blog

Opening comment which is repeated later: He is 50, but was biologically 60, until he changed his lifestyle and diet, and now he is 31. OMG does that mean we can already rejuvenate to a youthful state? Well no. These clocks measure how healthy you are, and yes if you copied Davids lifestyle youll get more yearsor more accurately, healthy years. Perhaps David would have made it to 80, but now hell make it to 100 and be active for most of it. But that is not true rejuvenation. For that he mentions reprogramming near the end of the vid and the fact they are working on whole body rejuvenation with the success they had in the eyes of mice.
Are you tired of feeling old and worn out? Do you want to look and feel younger without resorting to expensive treatments or surgeries? In this video, Dr. David Sinclair shares his expert tips on how to slow and reverse aging using simple, everyday practices like intermittent fasting, supplements, a healthy lifestyle, and proper diet. With over 20 years of experience studying longevity, Dr. Sinclair is a leading authority on the science of aging.#intermittentfasting #supplements #longevity.
Dr. Sinclairs AMAZING book: https://amzn.to/3Jp47m6
Products Mentioned by Dr. Sinclair:
High-Quality NMN: https://amzn.to/3ZYaHWp.
Resveratrol Supplement: https://amzn.to/3YDBXIG
Our website is supported by our users. We sometimes earn commissions when you click through the affiliate links on our website. This is not an endorsement of any product or company. As always, you should do your own research.
In this 6-minute video, youll discover:
- The surprising benefits of intermittent fasting for longevity
and overall health.
- The top supplements that can help slow down the aging
process.
- How a healthy lifestyle can add years to your life and keep you
feeling young and vibrant.
- The power of a proper diet to nourish your body and keep you
looking and feeling your best.
00:09
Linux 5.15.101 LTS Released To Fix Broken Intel Graphics At Boot Phoronix
Yesterday saw emergency hot-fix releases in the Linux 6.2 and 6.1 series for addressing an easy-to-trigger kernel oops when mounting and unmounting external storage. This weekend is proving more volatile with today bringing an emergency hot-fix release for the Linux 5.15 LTS series due to a separate issue...
Sunday, 12 March
23:06
Chocolate 3D Printer, Cocoa Press, to Ship this Fall SoylentNews
Instead of outputting in plastic, this printer builds models that you can eat:
All of the best 3D printers print from some form plastic, either from filament or from resin. But an upcoming printer, Cocoa Press, uses chocolate to create models you can eat. The brainchild of Maker and Battlebots Competitor Ellie Weinstein , who has been working on iterations of the printer since 2014, Cocoa Press will be available for pre-order, starting on April 17th via cocoapress.com (the company is also named Cocoa Press).
[...] In lieu of a roll of filament or a tank full of resin, the Cocoa Press uses 70g cartridges of special chocolate that solidifies at up to 26.67 degrees Celsius (80 degrees Fahrenheit), which the company will sell for $49 for a 10 pack. The cigar-shaped chocolate pieces go into a metal syringe where the entire thing is melted at the same time rather than melting as it passes through the extruder (like a typical FDM printer).
Video demonstrating how the Cocoa Press works.
Related: Why Chocolate Feels So Good? It's Down to Lubrication
Read more of this story at SoylentNews.
22:45
Linux GMUX Support For T2 Macs On The Way For Dual-GPU Graphics Switching Phoronix
A set of patches are expected to be merged for the Linux 6.4 cycle in two months enable support for the MMIO-based GMUX found on dual GPU Apple T2 Macs...
22:23
Linux 6.4 To Remove Old Workaround For Running On Very Outdated Distributions Phoronix
Linux 6.4 is set to remove the old CONFIG_SYSFS_DEPRECATED and CONFIG_SYSFS_DEPRECATED_V2 options that are used for running newer versions of the Linux kernel with very old Linux distributions and user-space tools. Pre 2007~2008 distributions as a result would likely run into trouble trying to run on Linux 6.4+ kernels...
22:22
Earths water came from super deep space, and its older than you can imagine Lifeboat News: The Blog
Astronomers found compelling evidence that the water in our solar system came from interstellar space. This water around a distant protostar is quite similar to the water found in our solar system, and on Earth.
22:15
Links 12/03/2023: GNOME Development Report and Companies in Panic Over SVB Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
-
GNU/Linux
-
Desktop/Laptop
-
Make Use Of Linux GUI Frameworks and Widget Toolkits Explained
Linux GUI toolkits might sound confusing, but they...
-
-
22:10
NVIDIA VA-API Driver 0.0.9 Released With YUV444 Support Phoronix
The open-source nvidia-vaapi-driver project is an independent effort implementing the Video Acceleration API (VA-API) atop of the NVDEC interface supported by NVIDIA's proprietary driver. This VA-API-on-NVDEC implementation allows for video acceleration within Firefox and other software only targeting this open API...
22:06
IRC Proceedings: Saturday, March 11, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-110323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-110323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-110323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-110323.gmi
Over HTTP:
|
... |
22:03
SDL3 Introduces The Concept Of Child Popup Windows Phoronix
Development work on SDL3 continues at full-speed for the next commonly used by cross-platform games. The newest feature merged is support for child pop-up windows...
22:00
Immersive Virtual Reality from the Humble Webcam Hackaday

[Russ Maschmeyer] and Spatial Commerce Projects developed WonkaVision to demonstrate how 3D eye tracking from a single webcam can support rendering a graphical virtual reality (VR) display with realistic depth and space. Spatial Commerce Projects is a Shopify lab working to provide concepts, prototypes, and tools to explore the crossroads of spatial computing and commerce.
The graphical output provides a real sense of depth and three-dimensional space using an optical illusion that reacts to the viewers eye position. The eye position is used to render view-dependent images. The computer screen is made to feel like a window into a realistic 3D virtual space where objects beyond the window appear to have depth and objects before the window appear to project out into the space in front of the screen. The resulting experience is like a 3D view into a virtual space. The downside is that the experience only works for one viewer.
Eye tracking is performed using Googles MediaPipe Iris library, which relies on the fact that the iris diameter of the human eye is almost exactly 11.7 mm for most humans. Computer vision algorithms in the library use this geome...
20:30
Week in review: Public MS Word RCE PoC, API exploitation, Patch Tuesday forecast Help Net Security
Microsoft to boost protection against malicious OneNote documents Microsoft has announced that, starting in April 2023, they will be adding enhanced protection when users open or download a file embedded in a OneNote document a known high-risk phishing file type. Massive GitHub analysis reveals 10 million secrets hidden in 1 billion commits GitGuardian scanned 1.027 billion new GitHub commits in 2022 (+20% compared to 2021) and found 10,000,000 secrets occurrences (+67% compared to 2022). More
The post Week in review: Public MS Word RCE PoC, API exploitation, Patch Tuesday forecast appeared first on Help Net Security.
20:25
Physicists explore mysteries of strange metals Lifeboat News: The Blog
Physicists are learning more about the bizarre behavior of strange metals, which operate outside the normal rules of electricity.
Theoretical physicist Yashar Komijani, an assistant professor at the University of Cincinnati, contributed to an international experiment using a strange metal made from an alloy of ytterbium, a rare earth metal. Physicists in a lab in Hyogo, Japan, fired radioactive gamma rays at the strange metal to observe its unusual electrical behavior.
Led by Hisao Kobayashi with the University of Hyogo and RIKEN, the study was published in the journal Science. The experiment revealed unusual fluctuations in the strange metals electrical charge.
20:25
Two exoplanets orbiting a sun-like star discovered Lifeboat News: The Blog
Astronomers report the discovery of two new exoplanets orbiting a bright sun-like star about 175 light years away. The newfound alien worlds, designated HIP 104,045 b and HIP 104,045 c, were classified as a Jupiter analog and a super Neptune planet, respectively. The finding was detailed in a paper published March 2 on the pre-print server arXiv.
The radial velocity (RV) method to detect an exoplanet is based on the detection of variations in the velocity of the central star, due to the changing direction of the gravitational pull from an unseen exoplanet as it orbits the star. Thanks to this technique, more than 600 exoplanets have been detected so far.
Now, a team of astronomers led by Thiago Ferreira of the University of So Paulo in Brazil, reports the detection of two new exoplanets using the RV method. They observed a solar-type star HIP 104,045 with the High Accuracy Radial Velocity Planet Searcher (HARPS) spectrograph on the 3.6m telescope of the European Southern Observatory (ESO) in La Silla, Chile. The observations, conducted as part of the Solar Twin Planet Search (STPS) program, resulted in the discovery of two massive extrasolar worlds.
20:25
A framework to self-test all entangled states using quantum networks Lifeboat News: The Blog
Self-testing is a promising method to infer the physics underlying specific quantum experiments using only collected measurements. While this method can be used to examine bipartite pure entangled states, so far it could only be applied to limited kinds of quantum states involving an arbitrary number of systems.
Researchers at Sorbonne University, ICFO-Institute of Photonic Sciences and Quantinuum recently introduced a framework for the quantum network-assisted self-testing of all pure entangled states of an arbitrary number of systems. Their paper, published in Nature Physics, could inform future research efforts aimed at certifying quantum phenomena.
I was a postdoctoral researcher in Barcelona in 2014 in the group of Antonio Acn when the first author, Ivan upi and I began working on self-testing quantum states together, Matty Hoban, one of the researchers who carried out the study, told Phys.org. That is, certifying that you have systems in particular quantum states without trusting the devices and treating them as black boxes (called the device-independent setting). Part of this work involved exploring different kinds of scenarios of trust.
20:25
Aluminum-based low-loss interconnects for superconducting quantum processors Lifeboat News: The Blog
Quantum processors are computing systems that process information and perform computations by exploiting quantum mechanical phenomena. These systems could significantly outperform conventional processors on certain tasks, both in terms of speed and computational capabilities.
While engineers have developed several promising quantum computing systems over the past decade or so, scaling these systems and ensuring that they can be deployed on a large-scale remains an ongoing challenge. One proposed strategy to increase the scalability of quantum processors entails the creation of modular systems containing multiple smaller quantum modules, which can be individually calibrated and then arranged into a bigger architecture. This, however, would require suitable and effective interconnects (i.e., devices for connecting these smaller modules).
Researchers at the Southern University of Science and Technology, the International Quantum Academy and other institutes in China have recently developed low-loss interconnects for linking the individual modules in modular superconducting quantum processors. These interconnects, introduced in Nature Electronics, are based on pure aluminum cables and on-chip impendence transformers.
20:25
A super-resolution microscopy method for rapid differentiation of molecular structures in 3D Lifeboat News: The Blog
Super-resolution microscopy methods are essential for uncovering the structures of cells and the dynamics of molecules. Since researchers overcame the resolution limit of around 250 nanometers (while winning the 2014 Nobel Prize in Chemistry for their efforts), which had long been considered absolute, the methods of microscopy have progressed rapidly.
Now a team led by LMU chemist Prof. Philip Tinnefeld has made a further advance through the combination of various methods, achieving the highest resolution in three-dimensional space and paving the way for a fundamentally new approach for faster imaging of dense molecular structures. The new method permits axial resolution of under 0.3 nanometers.
The researchers combined the so-called pMINFLUX method developed by Tinnefelds team with an approach that utilizes special properties of graphene as an energy acceptor. pMINFLUX is based on the measurement of the fluorescence intensity of molecules excited by laser pulses. The method makes it possible to distinguish their lateral distances with a resolution of just 1 nanometer.
20:25
Density-Functional Models Get Excited Lifeboat News: The Blog
A venerable strategy for approximating a systems ground states has now been extended to accommodate its excited states.
Density-functional theory (DFT) owes its name and utility to its central insight: that a potentials influence on a system of interacting electrons can be expressed in terms of the electrons density. Existing models restrict DFT to ground states and exclude excited states. But now Tim Gould of Griffith University, Australia, and his collaborators have found a way to overcome the restriction [1].
At the heart of DFT are exchange-correlation models, which simplify the treatment of electrons behavior by using certain limiting cases. This simplification allows DFT to simulate ground states of large electronic systems. A generalization of the theory, called ensemble DFT, can cope with excited states, but this theorys more complex exchange-correlation models make large systems computationally intractable. Gould and his collaborators discovered that when the electron density is sufficiently low, these complications vanish and the models for dealing with excited states revert to being as simple as those used for regular DFT. Then, regular DFT suffices. At the other extremewhen electron density is highcomplications are simplified to the point that exact solutions can be obtained.
20:24
Muted Response to New Claim of a Room-Temperature Superconductor Lifeboat News: The Blog
Another part of that wariness arises because, to date, no one has independently reproduced Dias teams results. This lack of verification was raised by Jorge Hirsch of the University of California, San Diego, in the last talk of the session in which Dias and his team spoke. Hirsch argued that those claiming to have created high-temperature superconducting hydrides suffered from confirmation bias, cherry-picking evidence to support their agenda. (Hirsch has been an outspoken critic of Dias work.) As the last question of the session, Dias asked Hirsch, Could you also have confirmation bias? Maybe, Hirsch replied.
After the session, a few attending researchersall collaborators of Diasspoke with Physics Magazine, telling us that they disagreed with Hirschs cherry-picking conclusion. One of them, Russell Hemley of the University of Illinois Chicago confirmed Pasans claim that they have replicated the 2020 carbonaceous sulfur hydrideas reported in an arXiv paper that the team recently posted [3].
Dias group still needs to more precisely characterize NLHs chemical composition, Pasan said. The samples also appear to consist of two phases, an observation that they need to investigate. Ultimately, they plan to innovate upon this material to create a superconductor at ambient pressure and temperature conditions, a goal that Pasan said he thinks is feasible. But extraordinary claims require extraordinary evidence, and the community has much of the latter still to gather.
20:12
Cisco fixed CVE-2023-20049 DoS flaw affecting enterprise routers Security Affairs
Cisco fixed a high-severity DoS vulnerability (CVE-2023-20049) in IOS XR software that impacts several enterprise routers.
Cisco has released security updates to address a high-severity DoS vulnerability, tracked as CVE-2023-20049 (CVSS score of 8.6), in IOS XR software used by several enterprise-grade routers.
The vulnerability resides in the bidirectional forwarding detection (BFD) hardware offload feature of Cisco IOS XR Software for Cisco ASR 9000 Series Aggregation Services Routers, ASR 9902 Compact High-Performance Routers, and ASR 9903 Compact High-Performance Routers.
An unauthenticated, remote attacker can trigger the flaw to cause a line card to reset, resulting in a denial of service (DoS) condition.
An attacker can trigger the CVE-2023-20049 vulnerability by sending a crafted IPv4 BFD packet to a vulnerable device.
This vulnerability is due to the incorrect handling of malformed BFD packets that are received on line cards where the BFD hardware offload feature is enabled. reads the advisory published by the vendor. . A successful exploit could allow the attacker to cause line card exceptions or a hard reset, resulting in loss of traffic over that line card while the line card reloads.
This flaw affects Cisco routers running a vulnerable release of Cisco IOS XR 64-bit Software and have BFD hardware offload enabled for any of the installed line cards:
- ASR 9000 Series Aggregation Services Routers only if they have a Lightspeed or Lightspeed-Plus-based line card installed
- ASR 9902 Compact High-Performance Routers
- ASR 9903 Compact High-Performance Routers
The company pointed out that this vulnerability does not affect the following Cisco products:
- IOS Software
- IOS XE Software
- IOS XR Platforms not listed in the Vulnerable Products section of this advisory
As a workaround, Cisco recommends disabling the BFD hardware offload and creating Infrastructure Access Control lists.
The IT giant addressed the issue with the release of IOS XR versions 7.5.3, 7.6.2, and 7.7.1.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(...
20:00
Hack Your Heathkit to Trace MOSFET Curves Hackaday

[TRX Lab] has an old Heathkit model IT-1121 curve tracer, and wants to modify it so he can plot the I-V curves of MOSFETs. For the uninitiated, curve tracers are used to determine the precise characteristics of components by measuring the output for a set of specific inputs either voltage or current depending on the device youre testing.
The IT-1121 was introduced in 1973 and supports bipolar and FET transistors of types NPN, PNP, N-channel, and P-channel, along with various other semiconductor devices. But [TRX] wanted to enhance the tester to deal with MOSFETs as well.
The IT-1121 is very flexible, and has selector switches for all the usual polarity and sweep settings Heathkit also sold a model IT-3121 in later years, but this seems to have been the same basic tester. [TRX] found two shortcomings when plotting the I-V curve of MOSFETs. First, there is no way to apply a Vgs threshold voltage to the curves. Second, when set for FET testing, the polarity of the gate voltage stair step waveform doesnt match the desired polarity of the drain-source voltage.
In the video below the break, [TRX] first walks us through some of the reasons youd want a curve tracer in your lab. In the next part of the video, he breadboards up the modification for testi...
18:19
Newly Spotted 50-meter Asteroid Tops Risk List SoylentNews
Newly spotted 50-meter asteroid tops Risk List:
Valentine's Day 2046 could be memorable for a number of reasons. Not only might you receive a card from an admirer you never knew you had, but you might also witness a large asteroid slamming into Earth and causing widespread devastation.
Hopefully the only delivery anyone will be getting that day is a card, but scientists say that a 49-meter-wide asteroid discovered last week is currently calculated to have a 1-in-625 chance of hitting our planet in a couple of decades from now.
The rock, called 2023 DW, now sits atop the European Space Agency's Risk List as the only one with a "1" rating on the Torino scale, which is used for categorizing the impact hazard of near-Earth objects.
[...] As asteroid 2023 DW was only discovered a few days ago, scientists are continuing with their analysis to determine more precisely the characteristics of the rock, which is similar in size to an Olympic swimming pool.
[...] If later analysis suggests an increased risk of 2023 DW crashing into Earth, it would be a golden opportunity for NASA to deploy its asteroid deflection system. The technology was tested last year with great success when it smashed a spacecraft into a distant asteroid, with the force of the impact altering the rock's course.
Read more of this story at SoylentNews.
17:54
Bug fixing in wscons OpenBSD Journal
Crystal Kolipe has written up more of her work on the console. This time, it regards bugs in the handling of UTF-8: ExoticSilicon.com - fixing cringeworthy bugs in the OpenBSD console code.
As Crystal pointed out in her email to Undeadly, Miod
Vallat (miod@) has committed
fixes.
17:00
This Open Hardware Li-Ion Charger Skips the TP4056 Hackaday

Theres a good chance that if you build something which includes the ability to top up a lithium-ion battery, its going to involve the incredibly common TP4056 charger IC. Now, theres certainly nothing wrong with that. Its a decent enough chip, and there are countless pre-made modules out there that make it extremely easy to implement. But if the chip shortage has taught us anything, its that alternatives are always good.
So wed suggest bookmarking this opensource hardware Li-Ion battery charger design from [Shahar Sery]. The circuit uses the BQ24060 from Texas Instruments, which other than the support for LiFePO4 batteries, doesnt seem to offer anything too new or exciting compared to the standard TP4056. But thats not the point this design is simply offered as a potential alternative to the TP4056, not necessarily an upgrade.
14:38
Read "On the Controllability of Artificial Intelligence: An Analysis of Limitations" by our Roman V. Yampolskiy. Lifeboat News
Read "On the Controllability of Artificial Intelligence: An Analysis of Limitations" by our Roman V. Yampolskiy.
14:00
Electronic Bandage Speeds Wound Healing Hackaday

Were a long way from the dermal regenerators in Star Trek, but researchers at Northwestern University have made a leap forward in the convenient use of...
13:41
Links 11/03/2023: Collapse of Misbehaving Banks Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Server
-
Kubernetes Blog Kubernetes Blog: k8s.gcr.io Redirect to registry.k8s.io What You Need to Know
On Monday, March 20th, the k8s.gcr.io registry will be redirected to the community owned registry, registry.k8s.io .
-
Container Journal...
-
-
13:37
Graph Databases Provide a Significant Advantage Over Well-Architected Relational Databases SoylentNews
The results of the great DB debate on The Register were announced. Although it was a close-run race, and RDBMS was well ahead at several points during the week before a late surge for graph DBs yesterday. Over 2,000 readers voted. This debate is a part of the current spotlight on databases.
Our first contributor, arguing FOR the motion, was Andy Pavlo, associate professor of databaseology at Carnegie Mellon University. Pavlo's starting point on Monday was that graph DBMSs are "fundamentally flawed and, for most applications, inferior to relational DBMSs."
Jim Webber, Neo4j's chief scientist and a professor of computer science at Newcastle University, arguing AGAINST, said in his rebuttal that he could not back the idea that "relational can do anything" and rejected the assertion that graph databases cannot properly support views and migrations.
Then, on Wednesday, Pavlo threw down the gauntlet, stating that abandoning the relational database model would be akin to "reinventing the wheel." He also doubled down on a public wager he'd previously made that graph databases won't overtake relational databases in 2030 by marketshare. He has promised that if he loses, Pavlo will replace his official CMU photo with one of him wearing a shirt that says "Graph Databases Are #1."
Webber then countered this in his Thursday argument, noting that the pending standard for graphs, GQL, is overseen by the same ISO committee that delivered SQL. If SQL extensions were enough to solve the graph problem, the committee wouldn't have bothered itself, he seemed to be saying. Instead, it decided graphs were different enough to warrant a full query language.
Webber also mentioned: In late 2010, I visited former colleagues at the University of Sydney, Australia. I gave a talk on graph databases and ended it by lightheartedly saying something like, "This technology category is going to catch on. You're going to ignore it for now, but in about a decade you will become interested and start telling us that we've done it all wrong."
Several papers from CIDR 2023 were cited in the discussion.
...
13:11
Read "A Reputation System for Artificial Societies" (PDF) coauthored by our Ben Goertzel, Matt Ikle, and Anton Kolonin. Lifeboat News
Read "A Reputation System for Artificial Societies" (PDF) coauthored by our Ben Goertzel, Matt Ikl, and Anton Kolonin.
12:52
HAPPY 40th ANNIVERSARY TO THE ACORN ELECTRON COMPUTER! commodore64crap
HAPPY 40th ANNIVERSARY TO THE ACORN ELECTRON COMPUTER!

This year (2023) marks the fortieth anniversary of the Acorn Electron computer!
Heres a summary of the Acorn Electrons pros and cons
- BBC BASIC programming language built in, which could also be mixed with 6502 Assembly Language in the same program
- Most BBC BASIC programs could run on the Acorn electron as well
- It could display text in 80 columns, as well as 40 columns and 20 columns
- Its highest resolution display mode was 640256 in 2 colours
- It was featured on the TV series Me and My Micro presented by Fred Harris as one of only two computers which they used to teach BASIC programming. The other was the Sinclair ZX Spectrum.
- It lacked the many interfaces of the BBC micro, which most people may never have used, but they were partly responsible for the BBC Micros higher price
- It lacked the three channel sound synthesizer chip of the BBC micro, having only a one channel tone generator
- It could only display 8 different colours, as used in Teletext/Videotext
- It lacked the Teletext/Videotext display mode of the BBC Micro, which was called MODE 7
To sum this up, the Acorn Electron had almost everything I was looking for in a computer! I must emphasise th...
11:20
ThreatBlockr and Engaged Security Partners help users prioritize breach prevention Help Net Security
ThreatBlockr and Engaged Security Partners announced a partnership focusing on left of boom protection to bring enhanced breach prevention to customers. Engaged Security Partners uses ThreatBlockrs platform for threat intelligence management and integration into the network. Together, Engaged Security Partners customers will benefit from blocking malicious traffic and reducing human error, turning employees into threat hunters and creating a strong first and last line of defense. We have been seeking a partner who prioritizes breach More
The post ThreatBlockr and Engaged Security Partners help users prioritize breach prevention appeared first on Help Net Security.
11:00
Quick and Dirty Microscope Motion Control for Focus Stacking Hackaday

If youve spent much time looking through a microscope, you know that their narrow depth of field can be a bit challenging to deal with. Most microscopes are designed to only have a very thin slice of the specimen in focus, so looking at anything above or below that plane requires a focus adjustment. Its tedious and fussy, and that makes it a perfect target for automation.
The goal behind [ItMightBeWorse]s microscope mods is focus stacking, a technique where multiple images of the same sample taken at different focal planes can be stitched together so that everything appears to be in focus. Rather than twist knobs and take pictures manually, he built a simpler Arduino-based rig to do the job for him. Focus control is through a small stepper motor connected to the fine focus knob of the scope, while the DSLR camera shutter is triggered throug...
08:59
How to add an IP alias on Amazon Linux 2 nixCraft
IP aliasing is nothing but associating more than one IP address to a network interface such as eth0. For example, using the following methods, you can add an IP alias on Amazon Linux 2.
Love this? sudo share_on: Twitter - Facebook - LinkedIn - Whatsapp - Reddit
The post How to add an IP alias on Amazon Linux 2 appeared first on nixCraft.
08:52
Room-Temperature Superconductor Works at Lower Pressures SoylentNews
Results come from a lab that had an earlier superconductivity paper retracted:
On Wednesday, a paper was released by Nature that describes a mixture of elements that can superconduct at room temperature. The work follows a general trend of finding new ways of stuffing hydrogen into a mixture of other atoms by using extreme pressure. This trend produced a variety of high-temperature superconductors in previous research, though characterizing them was difficult because of the pressures involved. This new chemical, however, superconducts at much lower pressures than previous versions, which should make it easier for others to replicate the work.
The lab that produced the chemical, however, had one of its earlier papers on high-temperature superconductivity retracted due to a lack of details regarding one of its key measurements. So, it's a fair bet that many other researchers will try to replicate it.
The form of superconductivity involved here requires that electrons partner up with each other, forming what are called Cooper pairs. One of the things that encourages Cooper pair formation is a high-frequency vibration (called a phonon) among the atomic nuclei that these electrons are associated with. That's easier to arrange with light nuclei, and hydrogen is the lightest around. So finding ways to stuff more hydrogen into a chemical is thought to be a viable route toward producing higher-temperature superconductors.
The surest way of doing that, however, involves extreme pressures. These pressures can induce hydrogen to enter the crystal structure of metals or to form hydrogen-rich chemicals that are unstable at lower pressures. Both of these approaches have resulted in chemicals with very high critical temperatures, the highest point at which they'll support superconductivity. While these have approached room temperature, however, the pressures required were multiple Gigapascalswith each Gigapascal being nearly 10,000 times the atmospheric pressure at sea level.
In essence, this involves trading off impractical temperatures for impractical pressures.
Original Submission #1 Original Submission #2
Read more of this story at SoylentNews.
08:00
A Retro-Style Trainer For Motorolas 1-Bit Chip Hackaday

If you want to program a microcontroller today, you pop open your editor of choice, bang out some code, and flash it over USB. But back in ancient times, when your editor was a piece of paper and you didnt even have a computer of your own, things were a bit different. In that case, you might have reached for a trainer: a PCB that included the chip you wanted to program along with an array of switches, LEDs, and maybe even a hex keypad for good measure. Grab yourself the programming manual (printed on paper, naturally), and youre good to go.
So when [Nicola Cimmino] became curious about the Motorola MC14500, a 1-bit ICU (Industrial Control Unit) from the 1970s, he could think of no more appropriate way to get up close and personal with the chip than to design an era-appropriate trainer for it. The resulting board, which hes calling the PLC14500 Nano, is festooned with LEDs that show the status of the system buses and registers. Thanks to the chips single-step mode, this gives you valuable insight into whats happening inside this piece of classic silicon.
06:40
PlugX malware delivered by exploiting flaws in Chinese programs Security Affairs
Researchers observed threat actors deploying PlugX malware by exploiting flaws in Chinese remote control programs Sunlogin and Awesun.
Researchers at ASEC (AhnLab Security Emergency response Center) observed threat actors deploying the PlugX malware by exploiting vulnerabilities in the Chinese remote control software Sunlogin and Awesun.
Sunlogin RCE vulnerability (CNVD-2022-10270 / CNVD-2022-03672) is known to be exploited by threat actors since an exploit code was disclosed. In the past, the issue was exploited in attacks to deliver Sliver C2, XMRig CoinMiner, and Gh0st RAT.
The same threat actors performed an RCE vulnerability exploitation on both Sunlogin and AweSun to install Sliver C2. reads the analysis published by ASEC.
The PlugX backdoor has been used since 2008 by multiple China-linked APT groups, including Mustang Panda, Winnti, and APT41
In the attacks observed by ASEC, once exploited the vulnerability, threat actors executed a PowerShell command to create a file named esetservice.exe.
esetservice.exe is actually a legitimate HTTP Server Service program made by the security firm ESET. Attackers also downloaded a file named http_dll.dll aside from esetservice.exe.
The http_dll.dll is invoked by the esetservice.exe when placed in the same directory, in a classic DLL side-loading attack.
The DLL acts as the loader for the...
06:34
VirtIO Native Context Being Worked On For AMD Drivers To Enhance VM Performance Phoronix
As part of an AMD effort to enhance the performance of the AMD Linux graphics drivers when running in a virtualized environment, a set of initial patches are pending for Mesa that implement native context support for VirtIO...
05:23
Watch "Brain, meet computer" by our Nuno Martins. Lifeboat News
Watch "Brain, meet computer" by our Nuno Martins.
05:05
Biden Asks for Massive $886 Billion Military Budget for 2024 cryptogon.com
Via: Antiwar: Congress could easily bring the 2024 NDAA to over $900 billion, closing in on the $1 trillion mark. The NDAAs dont include the funds authorized for the Ukraine war, which could add another $100 billion if the US keeps spending on the conflict at the same pace.
05:01
DNA Contamination of COVID-19 Injectable Products cryptogon.com
Via: Jessica Rose: The left-over expression vectors used to manufacture the mRNAs are at contamination levels 100-fold higher than originally proposed and imply trillions of DNA molecules per dose. This has implications for integration into our genome. Why were these basic assays/procedures not done/carried out prior to injecting billions of people? Or at least, []
04:54
Links 11/03/2023: KDE Frameworks 5.104 and Openwashing Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
04:05
Musk Apologizes for Mocking and Firing Twitter Exec With Muscular Dystrophy SoylentNews
After a tweet exchange where Twitter CEO Elon Musk questioned a fired former Twitter executive's disabilities and work performance, Musk has issued a rare apology and offered to rehire former Senior Director of Product Design Haraldur "Halli" Thorleifsson.
Thorleifsson joined Twitter in 2021, saying on the podcast Fast Politics with Molly Jong-Fast that he decided to let his successful design agency Ueno get acquired by Twitter because he really believed that, much like Musk, Twitter had "never lived up to its potential." Until his exit from Twitter, Thorleifsson led an innovation team at Twitter, but Musk apparently was not familiar with the meaningful contributions Thorleifsson made to the company until after he let Thorleifsson go. Now Musk apparently regrets dismissing Thorleifsson.
[...] Before Thorleifsson got the official notification that he'd been fired from Twitter, he told the BBC that he had a theory explaining why it took Twitter nine days to respond to his inquiries about layoffs.
"My theory is they made a mistake and are now looking for anything they can find to make this a 'for cause' firing to avoid having to fulfill their contractual obligations," Thorleifsson told the BBC.
According to The New York Times, the cost of firing Thorleifsson may be greater to Twitter than the cost of keeping him on, which could be another factor motivating Musk's decision to try to rehire the former design executive. Twitter users have speculated that his severance package could be worth $100 million, and Thorleifsson seems willing to take the money and leave. He tweeted that he's OK with his exit from Twitter and asked Musk to confirm he'll receive his full severance.
Related:
Open
Source Teams at Google Hit Hard by Layoffs: Was It the
Algorithm?
Read more of this story at SoylentNews.
03:00
False Starts: The Story of Vehicle-to-Grid Power IEEE Spectrum

In 2001, a team of engineers at a then-obscure R&D company called AC Propulsion quietly began a groundbreaking experiment. They wanted to see whether an electric vehicle could feed electricity back to the grid. The experiment seemed to prove the feasibility of the technology. The companys president, Tom Gage, dubbed the system vehicle to grid or V2G.
The concept behind V2G had gained traction in the late 1990s after Californias landmark zero-emission-vehicle (ZEV) mandate went into effect and compelled automakers to commercialize electric cars. In V2G, environmental-policy wonks saw a potent new application of the EV that might satisfy many interests. For the utilities, it promised an economical way of meeting rising demand for electricity. For ratepayers, it offered cheaper and more reliable electricity services. Purveyors of EVs would have a new public-policy rationale backing up their market. And EV owners would become entrepreneurs, selling electricity back to the grid.
AC Propulsions experiment was timely. It occurred in the wake of the California electricity crisis of 2000 and 2001, when mismanaged deregulation, market manipulation, and environmental catastrophe combined to unhinge the power grid. Some observers thought V2G could prevent the kinds of price spikes and rolling blackouts then plaguing the Golden State. Around the same time, however, General Motors and other automakers were in the process of decommissioning their battery EV fleets, the key component of V2G.
 AC
Propulsions president, Tom Gage, explains the companys
vehicle-to-grid technology at a 2001 conference in Seattle.
Photo-illustration:
Max-o-matic; photo source: Alec Brooks
AC
Propulsions president, Tom Gage, explains the companys
vehicle-to-grid technology at a 2001 conference in Seattle.
Photo-illustration:
Max-o-matic; photo source: Alec Brooks
The AC Propuls...
02:46
Piracy Subreddit Avoided a Reddit Ban By Censoring Itself to Death TorrentFreak
 In the wake of the music industrys destruction of
Napster, hopes of a file-sharing vacuum were overwhelmed by a
laundry list of protocols and software clients, some pre-existing,
some new.
In the wake of the music industrys destruction of
Napster, hopes of a file-sharing vacuum were overwhelmed by a
laundry list of protocols and software clients, some pre-existing,
some new.
DCC, Gnutella, Freenet, eDonkey2000, Kazaa/FastTrack, WinMX, Bearshare, Grokster, Morpheus the list went on and on but with no social media, various news and discussion forums took off. Sites like Slyck, Unite the Cows, and Zeropaid became the subreddits of the day, but even 20+ years ago, these platforms were hardly a piracy free-for-all, far from it.
Unlike today, where users happily post direct links to infringing content on social media in their own name, two decades ago in a legal environment far less developed than it is today that was generally forbidden and respected as such.
Reddits /r/piracy, which celebrated its one-millionth member this week, has an exponentially larger task on its hands but, considering its scale, does a remarkably good job of stifling users intent on breaking its rules and ultimately getting the community banned by Reddits administrators. Other piracy subs havent been so lucky.
Reddit Bans For Excessive Infringment
During the first half of 2022 alone, Reddit banned 1,543 subreddits for excessive copyright infringement. Many of those went down in flames after failing to self-censor, but thats not the only way to break up a community.
Reddits /r/iptv subredditt was created on Mar 6, 2011, and with 123,000+ members, ranks in the top 1% of subreddits according to data in its sidebar.

For those starting out in the world of pirate IPTV services or those already established, /r/iptv was a thriving community to learn about IPTV, discuss services and the pros and cons of software, solve technical issues, and much more. Today the com...
02:00
Optical Algorithm Simplifies Analog AI Training IEEE Spectrum

Researchers have developed a range of analog and other unconventional machine learning systems in the expectation that they will prove vastly more energy efficient than todays computers. But training these AIs to do their tasks has been a big stumbling block. Researchers at NTT Device Technology Labs and the University of Tokyo now say theyve come up with a training algorithm (announced by NTT last month) that goes a long way toward letting these systems meet their promise.
Their results, established on an optical analog computer, represent progress towards obtaining the potential efficiency gains that researchers have long sought from unconventional computer architectures.
Modern AI programs use a biologically-inspired architecture called an artificial neural network to execute tasks like image recognition or text generation. The strength of connections between artificial neurons, which control the outputs of the computation, must be modified or trained using standard algorithms. The most prominent of these algorithms is called backpropagation, which updates the connection strengths to reduce the networks errors, while it processes trial data. Because adjustments to some parameters depend on adjustments to others, there is a need for active information passing and routing by the computer.
As Spectrum has elsewhere explained, Error backpropagation is like running inference in reverse, moving from the last layer of the network back to the first layer; weight update then combines information from the original forward inference run with these backpropagated errors to adjust the network weights in a way that makes the model more accurate.
Alternative computing architectures, which trade complexity for efficiency, often cannot perform the information passing required by the algorithm. As a consequence, the trained parameters of the network must be obtained from an independent physics simulation of the entire hardware setup and its information processing. But creating simulations of sufficient quality can itself be challenging.
We found that it was very hard and tough to apply backpropagation algorithms to our device, said Katsuma Inoue of NTT Device Technology Labs, one of the resea...
01:57
BSD Release: helloSystem 0.8.1 DistroWatch.com: News
helloSystem is a FreeBSD-based, desktop-oriented operating system. The project seeks to provide a macOS-style desktop interface and layout while using open source software. The project has published an update to its 0.8.x series which includes a number of bug fixes and improvements. "USB sound devices are now shown....
01:27
More (hopefully) stable kernels LWN.net
The 6.2.4 and 6.1.17 stable kernels have been released; each contains a pair of reverts for problematic patches in yesterday's updates. But it doesn't stop there; also released are 6.2.5, 6.1.18, and 5.15.100 with another set of important fixes.
Update: they keep on coming: the large 5.10.173, 5.4.235, 4.19.276, and 4.14.308 kernels have been released, as has the single-revert 5.15.101 update
00:32
BATLOADER Malware Uses Google Ads to Deliver Vidar Stealer and Ursnif Payloads The Hacker News
The malware downloader known as BATLOADER has been observed abusing Google Ads to deliver secondary payloads like Vidar Stealer and Ursnif. According to cybersecurity company eSentire, the malicious ads are used to spoof a wide range of legitimate apps and services such as Adobe, OpenAPI's ChatGPT, Spotify, Tableau, and Zoom. BATLOADER, as the name suggests, is a loader that's responsible for
00:22
Get Ready to Meet the ChatGPT Clones Lifeboat News: The Blog
ChatGPT might well be the most famous, and potentially valuable, algorithm of the moment, but the artificial intelligence techniques used by OpenAI to provide its smarts are neither unique nor secret. Competing projects and open-source clones may soon make ChatGPT-style bots available for anyone to copy and reuse.
Stability AI, a startup that has already developed and open-sourced advanced image-generation technology, is working on an open competitor to ChatGPT. We are a few months from release, says Emad Mostaque, Stabilitys CEO. A number of competing startups, including Anthropic, Cohere, and AI21, are working on proprietary chatbots similar to OpenAIs bot.
The impending flood of sophisticated chatbots will make the technology more abundant and visible to consumers, as well as more accessible to AI businesses, developers, and researchers. That could accelerate the rush to make money with AI tools that generate images, code, and text.
00:22
GPT-4 reveal: Microsoft wont comment on launch rumors Lifeboat News: The Blog
Andreas Braun, CTO of Microsoft Germany, announced the introduction of GPT-4 for next week. The models will be multimodal.
At the AI in Focus Digital Kickoff event, Microsoft Germany presented business applications of large language models and talked about its cooperation with OpenAI and new Azure offerings resulting from it.
As Silke Hahn reports for Heise, Braun announced a GPT-4 reveal next week: Next week we will present GPT-4, there we have multimodal models that offer completely different possibilities for example videos, Braun said.
00:22
Microsoft Says OpenAIs Latest Blockbuster AI Is Dropping Next Week Lifeboat News: The Blog

Update, March 10: A spokesperson for OpenAI has confirmed in a statement to Futurism that OpenAI has not announced any timing for GPT-4.
A German Microsoft executive has, for some reason, claimed that OpenAIs next large language model (LLM) will drop imminently.
We will introduce GPT-4 next week, there we will have multimodal models that will offer completely different possibilities for example, videos, claimed Microsoft Germany CTO Andreas Braun during a digital kickoff event yesterday, per German tech news site Heise Online.
00:02
Links 11/03/2023: Curl is 25 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Digital Restrictions (DRM)
- Monopolies
- ...
00:01
Learn How to Code a zkApp Hello World With Me Using TypeScript David Wong | Cryptologie | HTML
Recorded this video for the Mina Foundation going through the first tutorial for zkapps. If you're interested in understanding what goes into these zk smart contracts then this is for you!
Saturday, 11 March
23:53
Prometei botnet evolves and infected +10,000 systems since November 2022 Security Affairs
Cisco Talos researchers reported that the Prometei botnet has infected more than 10,000 systems worldwide since November 2022. The crypto-mining botnet has a modular structure and employs multiple techniques to infect systems and evade detection.
The Prometei botnet was first observed by Cisco Talos experts on July 2020. A deep investigation on artifacts uploaded on VirusTotal allowed the experts to determine that the botnet may have been active at least since May 2016. Experts pointed out that the malware has constantly been updated by its creators with the implementation of new modules and features.
Now Talos confirms that the Prometei botnet continues to improve modules and exhibits new capabilities in recent updates.
More specifically, the botnet operators updated certain submodules of the execution chain to automate processes and challenge forensic analysis methods. reads the post published by Cisco Talos. We assess with high confidence that v3 of the Prometei botnet is of medium size, with more than 10,000 infected systems worldwide, based on data obtained by sinkholing the DGA domains over a period of one week in February 2023.
23:23
Silicon Valley Bank Shut Down by Regulators, Biggest Bank Failure Since 2008 Global Financial Crisis cryptogon.com
Via: CNBC: Financial regulators have closed Silicon Valley Bank and taken control of its deposits, the Federal Deposit Insurance Corp. announced Friday, in what is the largest U.S. bank failure since the global financial crisis more than a decade ago. The collapse of SVB, a key player in the tech and venture capital community, leaves []
23:18
How the 8086 Processor Determines the Length of an Instruction SoylentNews
https://www.righto.com/2023/02/how-8086-processor-determines-length-of.html
The Intel 8086 processor (1978) has a complicated instruction set with instructions ranging from one to six bytes long. This raises the question of how the processor knows the length of an instruction.1 The answer is that the 8086 uses an interesting combination of lookup ROMs and microcode to determine how many bytes to use for an instruction. In brief, the ROMs perform enough decoding to figure out if it needs one byte or two. After that, the microcode simply consumes instruction bytes as it needs them. Thus, nothing in the chip explicitly "knows" the length of an instruction. This blog post describes this process in more detail.
[...] The 8086 uses a 6-byte instruction prefetch queue to hold instructions, and this queue will play an important role in this discussion.3 Earlier microprocessors read instructions from memory as they were needed, which could cause the CPU to wait on memory. The 8086, instead, read instructions from memory before they were needed, storing them in the instruction prefetch queue. (You can think of this as a primitive instruction cache.) To execute an instruction, the 8086 took bytes out of the queue one at a time. If the queue ran empty, the processor waited until more instruction bytes were fetched from memory into the queue.
Read more of this story at SoylentNews.
23:15
Linux 6.4 To Enable Sensor Monitoring On More ASUS Z590 Motherboards Phoronix
A simple patch queued in "hwmon-next" this week for the Linux 6.4 cycle later this spring gets motherboard sensor monitoring working on three more ASUS motherbards for modern Intel systems...
23:09
Linux 6.2.4 & 6.1.17 Released To Fix An Easy-To-Trigger Kernel Oops Phoronix
Linux 6.2.4 and 6.1.17 kernels have been released this morning as new emergency releases...
23:03
GNU Octave 8.1 Released For Free Software MATLAB Alternative Phoronix
GNU Octave 8.1 is out today as the newest feature release to this free software for scientific computing and numerical computations that remains a leading open-source alternative to MATLAB...
23:00
A Fancy Connected Caliper For Not A Lot Hackaday

An essential for the engineer is a decent caliper, to measure dimensions with reasonable accuracy. Some of us have old-fashioned Vernier scales, while many up-to-date versions are electronic. When entering large numbers of dimensions into a CAD package matters can become a little tedious, so the fancier versions have connectivity for automatic reading transfer. [Mew463] didnt want to shell out the cash for one of those, so modified a cheaper caliper with an ESP32-C3 microcontroller to provide a Bluetooth interface.
Many cheaper calipers have a handy hidden serial port, and its to this interface the mod is connected via a simple level shifter. The ESP and associated circuitry is mounted on a custom PCB on the back of the caliper body, with a very neatly designed case also holding a small Li-Po cell. It adds a little bulk to the instrument, but not enough to render it unusable. Whether the work required to design and build it is worth the cost saving over an off-the-shelf connected caliper is left to the reader to decide.
Weve covered similar hacks in the past, but this ones to a very high standard. Meanwhile if calipers are of interest to you then theyre...
22:22
24/7 AI Seinfeld show is back on Twitch Lifeboat News: The Blog
Really bad now. BUT, the future of entertainment industry:
Transphobic comments lead to Larry Feinbergs downfall on Twitch. According to the host, the reason for Feinbergs bias is an outdated OpenAI language model without a functioning moderation system.
Since mid-December 2022, the small media group Mismatch Media has been running one of the most unusual shows on Twitch (and thats saying something): Using AI tools like DALL-E, GPT-3, Stable Diffusion, and more, Mismatch Media broadcasts an AI-generated show inspired by the popular U.S. sitcom Seinfeld every day, around the clock. Nothing, Forever is the name the team has given to their art project.
The AI-generated content is stitched together in the Unity engine to create an audiovisual pixel show reminiscent of early 90s video games. The jokes rarely have punchlines, the conversations are empty and incoherent, and the audiences fake applause starts in the wrong places.
22:16
KDE's Konsole Now Works On Windows, More Plasma Wayland Fixes Come Too Phoronix
It was a busy March week for KDE developers as they have now got the Konsole terminal emulator working on Windows, Qt apps surviving compositor restarts, other Plasma 6.0 development work under their belt, and the continued flow of fixes...
21:18
IRC Proceedings: Friday, March 10, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-100323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-100323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-100323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-100323.gmi
Over HTTP:
|
... |
20:24
Scientists Say The Moon Needs Its Own Lunar Time Zone. Heres Why Lifeboat News: The Blog
On July 21, 1969, Neil Armstrong took that first fateful step onto the Moon. The exact moment occurred just as our planets standard universal time hit 2.56 am. But what time was it for Neil?
Theres currently no answer to that question, but with plans in place to inhabit the Moon, that may need to change.
At a recent meeting in the Netherlands, members from space organizations around the world agreed that we need to implement a proper lunar time zone an internationally accepted common lunar reference time that all future missions can use to communicate and navigate with ease.
20:24
Meet ALAN, a robot that requires minimal human supervision Lifeboat News: The Blog

Deepak Pathak/YouTube.
Researchers at Carnegie Mellon University have created ALAN, an autonomous robot, meaning that it can perceive its environment, make decisions based on what it perceives, and can possibly work for extended periods of time. It has been programmed in such a way that it can recognize and then move or manipulate tasks within that environment.
20:23
Solving Previously Unsolvable Problems: A New Type of Analog Quantum Computer Lifeboat News: The Blog
Physicists have created a novel type of analog quantum computer capable of addressing challenging physics problems that the most powerful digital supercomputers cannot solve.
A groundbreaking study published in Nature Physics.
As the name implies, Nature Physics is a peer-reviewed, scientific journal covering physics and is published by Nature Research. It was first published in October 2005 and its monthly coverage includes articles, letters, reviews, research highlights, news and views, commentaries, book reviews, and correspondence.
20:23
Scientists Discover Enzyme That Can Turn Air Into Electricity Lifeboat News: The Blog
In an exciting turn for the field of sustainable energy research, Australian scientists have found a way to make energy out of thin air. Literally.
As detailed in a new study published this week in the journal Nature, researchers from Monash University in Melbourne, Australia discovered a new bacterial enzyme that transforms the traces of hydrogen in our atmosphere into electricity, technology that could one day be used in fuel cells that power anything from a smartwatch to even a car.
Weve known for some time that bacteria can use the trace hydrogen in the air as a source of energy to help them grow and survive, including in Antarctic soils, volcanic craters, and the deep ocean, said Professor Chris Greening, a contributor to the study, in a statement.
20:23
Is Neuralink the Next Step in Human Evolution? (Or its Downfall) Lifeboat News: The Blog

Thank you for watching my video about Elon Musks Neuralink! If you liked it, please consider subscribing! Have a great day. #neuralink #elonmusk.
Neuralink is a neurotechnology company founded by Elon Musk in
2016 with the goal of.
merging the human brain with artificial intelligence. The company
aims to develop a.
brain-machine interface that will enable humans to communicate with
computers and other.
devices directly through their thoughts. Neuralinks ultimate vision
is to create a symbiotic.
relationship between humans and AI, where the brain and the
computer work together to.
enhance human capabilities. While there is a huge potential in this
field, it could also turn out.
to be extremely dangerous. Heres why.
20:00
A Love Letter to the Sphere Computer Hackaday

[Ben Z] loves the Sphere computer, a very early entry in the personal computer boom of the mid 1970s. The 6800 CPU was unique in its day that it was a full system at least in theory. If you could afford the whole system, you got a nice case with a keyboard and a memory-mapped display board. You can see a great video tour of the system below the break.
The Sphere suffered from a few problems, none of which were easily foreseeable by its designer. First, the 6800 didnt get the traction that the 8080-derived CPUs did. Second, the S-100 bus would prove to be popular but that nearly always meant an 8080-type processor in practice. Third, while an all-in-one system was the right idea, it was pricey at the time, and many people would opt for something less expensive even if it had less capability. People also wanted to leverage hardware they may have already had. It was easier to imagine hooking up a surplus TeleType, for example, to a more conventional computer than to a Sphere that expected its own display hardware and keyboard.
19:20
CISA adds VMwares Cloud Foundation bug to Known Exploited Vulnerabilities Catalog Security Affairs
US CISA added an actively exploited vulnerability in VMwares Cloud Foundation to its Known Exploited Vulnerabilities Catalog.
U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical vulnerability in VMwares Cloud Foundation, tracked as CVE-2021-39144 (CVSS score: 9.8), to its Known Exploited Vulnerabilities Catalog.
The remote code execution vulnerability resides in the XStream open-source library. Unauthenticated attackers can exploit the vulnerability in low-complexity attacks without user interaction.
Due to an unauthenticated endpoint that leverages XStream for input serialization in VMware Cloud Foundation (NSX-V), a malicious actor can get remote code execution in the context of root on the appliance. reads the advisory published by the company.
The flaw was reported by Sina Kheirkhah and Steven Seeley from Source Incite.
...19:00
What Plants Are Saying About Us Terra Forming Terra

What the dogs of Chernobyl can teach us about life at the edge Terra Forming Terra

NATO a captured entity Terra Forming Terra
The Dire Significance of Putins Feb 21 Speech
53643 ViewsFebruary 22, 2023
by David Sant for the Saker blog
https://t.me/Thomas_Anderson_Author/5773
On Tuesday, February 21st President Putin gave a speech that was expected to be very significant. After it was delivered, however, most pundits said he didnt say anything we didnt already know. Most of them focused on his announcement of the withdrawal from the START II treaty. However, he said something far more significant.
An Existential Threat
What Mr. Putin said, when read through the lens of international law, should be chilling to the West.
We would do well to remember that Mr. Putin majored in international law. His speech made a legal case against NATO.
First he listed,...
This Planet would have Died without the Galactics with steve beckow Terra Forming Terra

18:34
When Forecasting Trends, Reading a Bar Chart Versus a Line Graph Biases Our Judgement SoylentNews
Study suggests that judgmental forecasting of trends in time-series data, such as weekly sales data, is lower when the information is displayed in bar chart format as opposed to a line graph or point graph:
A new study suggests that the format in which graphs are presented may be biasing people into being too optimistic or pessimistic about the trends in data that the graphs display.
Academics from City, University of London and University College London found that when people who were not experts about a set of data made predictions about how a trend in the data would develop over time, they made lower judgements when the trend was presented as a 'bar chart' type graph as compared to when exactly the same data was presented as a line graph or a graph consisting of a set of data points only.
Nevertheless, across many different types of trend participants consistently thought sales would be lower when the data were presented as bar charts than line graphs or point graphs.
The researchers wondered whether the reason was that in bar charts the area inside the bar is usually heavily shaded and hence visually draws attention to itself, lowering participants' estimates as compared to the other types of graph where there is no shading to attract the eye and attention.
However, in a third experiment, they found the same lower forecasts for bars even when the bars were left unshaded.
where the bars emanated from the top of the graph rather than the bottom. While subtle trends in the data suggest this may reverse the bias, the findings were inconclusive.
Read more of this story at SoylentNews.
18:20
Shopper+ - 878,290 breached accounts Have I Been Pwned latest breaches
In March 2023, "Canada's online shopping mall" Shopper+ disclosed a data breach discovered on a public hacking forum. The breach dated back to September 2020 and included 878k customer records with email and physical addresses, names, phone numbers and in some cases, genders and dates of birth.
17:00
27 Litres And 12 Cylinders, With A Practical Station Wagon Body Hackaday

If you were to name one of the most famous individual road cars in the world, what would it be? If youre British and of a Certain Age, then its possible your nomination is for sale, because The Beast, the one-off creation of [John Dodd] using a 27-litre Rolls-Royce Merlin aero engine, is up for auction. The Late Brake Shows [Jonny Smith] has given it a drive, and weve pasted the resulting video below the break.
A second-hand motor isnt usual Hackaday fare, but its the manner of this cars building which we think will draw you in. [John] originally acquired somebodys failed project featuring not a Merlin but its de-tuned derivative intended for tanks. He solved the problem of finding a transmission able to handle the immense power, and built it up with a pretty 1970s coupe body. After a fire a few years later he commissioned a new body from a dragster manufacturer, which is the wildly period estate car youll see in the video. It famously originally had a Rolls-Royce Cars grille, for which he ended up in court in the 1980s as the carmaker sought successfully to have it removed.
The tale of this car is one of epic scale hackery, as there is quite simply nothing else like it. It was once the worlds most powerful road car, and remains capable of well over 20...
16:00
Linux 6.4 Slated To Start Removing Old, Unused & Unmaintained PCMCIA Drivers Phoronix
Queued up ahead of the Linux 6.4 cycle this spring is removing all of the PCMCIA "char" drivers as part of a broader effort to remove PCMCIA socket and card driver code where there is no apparent users remaining...
14:00
The USB Protocol, Explained Hackaday

If you can explain what a USB PID, a J state, a K state, and an SOF are, you can probably stop reading now. But if you dont know or you want a refresher, you can spend 15 minutes watching [Sine Labs] straightforward explanation of the USB protocol details. You can find the video below.
The motivation for this is he wants to add USB to his projects using an ATMega with a hardware USB implementation. Honestly, most of the time, youll just consume some premade library and get it working that way. However, understanding the terminology can help you, especially if things dont go as planned.
Of course, another useful method is to just use a canned USB serial port and treat the whole thing like an old-fashioned serial port. But for some things you do want to take advantage of the speed and capabilities of the USB specification.
The last few minutes of the video get to a practical example. We agree with the decision to use a library, and in this case, he uses LUFA, an open-source USB stack for the processor he wants to use. But understanding the actual protocol will help you make sense of the documentation and troubleshoot. The example uses a HID device, which is yet more protocol youll have to read up on separately.
If you want to learn more about USB-C, [Arya Vor...
14:00
Avast One Platinum protects users against new and evolving threats Help Net Security
Avast launched Avast One Platinum, the new premium tier of the Cyber Safety service, Avast One. The new Platinum offering combines the full feature set from Avast One Family with identity monitoring and protection, identity theft resolution and reimbursement, and premium technical support, to give people more control and reassurance over their digital lives. The new Avast One Platinum tier is a step-change improvement to the award-winning Avast One integrated solution, said Leena Elias, CPO More
The post Avast One Platinum protects users against new and evolving threats appeared first on Help Net Security.
14:00
HDB Financial Services - 1,658,750 breached accounts Have I Been Pwned latest breaches
In March 2023, the Indian non-bank lending unit HDB Financial Services suffered a data breach that disclosed over 70M customer records. Containing 1.6M unique email addresses, the breach also disclosed names, dates of birth, phone numbers, genders, post codes and loan information belonging to the customers.
13:47
Freeing Up Japan's PhD Potential SoylentNews
Better prospects are needed in universities and industry to make the most of valuable talent:
Japanese science has a problem: there are too many PhD holders and not enough senior roles in universities for them to move into. This is partly caused by a well-meaning, but flawed policy to promote Japanese research that dates back almost three decades.
In 1996, Japan began a plan to boost the number of its academic researchers with a PhD but who are not yet in permanent faculty positions. The country aimed to produce 10,000 of these postdoctoral roles and by 2006 it had exceeded this goal, creating more than 16,000 positions. This leaves a fairly obvious question; what happens to a researcher after they've completed a postdoc? There hasn't been a serious enough effort to create a career pathway for these researchers in academia. Employment in industry is also an uphill battle for them because although progress has been made Japanese businesses on the whole still don't fully appreciate PhDs as a qualification.
Some comparison:
Many students here in Japan increasingly believe that finding jobs in industry, even in pharmaceutical firms and other research-related companies, is easier without a PhD. This is because there can be a belief in industry that it's better and easier for a company to train newly hired employees from scratch, rather than training someone who already has their 'own way of doing things'. In the United States, 40.2% of PhD holders are employed in private industry, but in Japan that figure is just 14%. Hopefully, the 14% in Japan will prove how PhD holders can contribute to businesses so that more companies employ doctoral graduates, something that could also lead to greater collaboration between academia and industry.
Earning a PhD demands an excess of patience, imagination, flexibility and expertise. Surely these are enviable characteristics for any candidate seeking promotion, be that in academia or private industry.
Read more of this story at SoylentNews.
13:41
Links 10/03/2023: Bodhi Linux 7.0.0 Alpha and Thunderbird for Android Coming Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Unix Men What You Need to Become a Linux Programmer
Are you looking to become a Linux programmer? The open-source operating system is a popular choic...
-
11:40
Atera and ESET join forces to arm customers against zero-day threats Help Net Security
Atera announced a new strategic partnership and integration with ESET, enabling Ateras community of IT professionals to deploy anti-malware solutions to protect their customers. As cyberattacks increase in sophistication and frequency, it is important that we partner with cybersecurity leaders like ESET to offer proactive protection against the toughest malware, and arm customers against zero-day threats, said Gil Pekelman, CEO of Atera. ESETs multi-layered approach to threat detection as well as response, including threat intelligence More
The post Atera and ESET join forces to arm customers against zero-day threats appeared first on Help Net Security.
11:37
Appeals Court Upholds Restriction on Twitters First Amendment Right to Publish National Security Transparency Report Deeplinks
A ruling from the Ninth Circuit Court of Appeals earlier this week marks a new low in judicial deference to classification and national security, even against the nearly inviolable First Amendment right to be free of prior restraints against speech. In Twitter v. Garland, the court ruled that it was not a violation of the First Amendment for the Justice Department to censor a draft transparency report on the aggregate number of national security demands Twitter received in the second half of 2013. Its a disappointing, dangerous opinion that may well empower even broader uses of government power to censor speech by unwilling participants in government investigations.
Background
In 2014, Twitter submitted its draft transparency report to the FBI to review. The FBI redacted the report, prohibiting Twitter from sharing the total number of foreign intelligence surveillance orders the government had served within a six-month period in aggregate bands such as 1-99. In response, Twitter filed suit in order to assert its First Amendment right to share that information. To be clear, Twitter did not plan to share any detail about the requests such as the targets or other identifying information.
In April 2020, a federal district court dismissed Twitters First Amendment claim. Among the several concerning aspects of the opinion, the judge devoted only a single paragraph to analyzing Twitters First Amendment right to inform the public about law enforcement orders for its users information. Twitter appealed to the Ninth Circuit, and EFF and the ACLU filed an amicus brief in support of the appeal.
A Dangerous Precedent
Not only did the Ninth Circuit uphold the lower courts ruling, it went out of its way to find that a large, well established body of prior restraint law did not apply. As we wrote in our amicus brief, when the government seeks to stop the publication of speech, it must satisfy extraordinarily exacting scru...
11:30
Aura partners with Robert Downey Jr. to increase awareness about the significance of online safety Help Net Security
Aura announced a multi-year partnership with Robert Downey Jr. Through the partnership, Downey Jr. joins Auras Board of Directors, invests in the company and commits to working with Aura as a strategist and brand advocate, supporting consumer education. Honestly, the exponential growth of online crime, just in the last several years, is truly terrifying, said Robert Downey Jr. It requires an innovative solution to protect our families, which is why Im joining Hari and his More
The post Aura partners with Robert Downey Jr. to increase awareness about the significance of online safety appeared first on Help Net Security.
11:00
Low-Power Wi-Fi Includes e-Paper Display Hackaday

Designing devices that can operate in remote environments on battery power is often challenging, especially if the devices need to last a long time between charges or battery swaps. Thankfully there are some things available that make these tasks a little easier, such as e-ink or e-paper displays which only use power when making changes to the display. That doesnt solve all of the challenges of low-power devices, but [Albertas] shows us a few other tricks with this development board.
The platform is designed around an e-paper display and is meant to be used in places where something like sensor data needs to not only be collected, but also displayed. It also uses the ESP32C3 microcontroller as a platform which is well-known for its low power capabilities, and additionally has an on-board temperature and humidity sensor. With Bluetooth included as well, the tiny device can connect to plenty of wireless networks while consuming a remarkably low 34 A in standby.
With a platform like this that can use extremely low power when not taking measurements, a battery charge can last a surprisingly long time. And, since it is based on common components, adding even a slightly larger battery would not be too difficult and could greatly extend this capability as well. But,...
10:32
NetWire Malware Site and Server Seized, Admin Arrested HackRead | Latest Cybersecurity and Hacking News Site
The alleged administrator of the website selling NetWire malware has been arrested in Croatia.
This is a post from HackRead.com Read the original post: NetWire Malware Site and Server Seized, Admin Arrested
10:15
QuSecure launches live end-to-end satellite quantum resilient link through space Help Net Security
QuSecure has accomplished the first known live, end-to-end quantum-resilient cryptographic communications satellite link through space, marking the first time U.S. satellite data transmissions have been protected from classical and quantum decryption attacks using post-quantum cryptography (PQC). The quantum-secure communication to space and back to Earth was made through a Starlink satellite working with a leading Global System Integrator (GSI) and security provider. Starlink is a satellite internet constellation operated by SpaceX consisting of more than More
The post QuSecure launches live end-to-end satellite quantum resilient link through space appeared first on Help Net Security.
08:53
The FBI Just Admitted It Bought US Location Data SoylentNews
Rather than obtaining a warrant, the bureau purchased sensitive data:
Federal Bureau of Investigation has acknowledged for the first time that it purchased US location data rather than obtaining a warrant. While the practice of buying people's location data has grown increasingly common since the US Supreme Court reined in the government's ability to warrantlessly track Americans' phones nearly five years ago, the FBI had not previously revealed ever making such purchases.
The disclosure came today during a US Senate hearing on global threats attended by five of the nation's intelligence chiefs. Senator Ron Wyden, an Oregon Democrat, put the question of the bureau's use of commercial data to its director, Christopher Wray: "Does the FBI purchase US phone-geolocation information?" Wray said his agency was not currently doing so, but he acknowledged that it had in the past. He also limited his response to data companies gathered specifically for advertising purposes.
"To my knowledge, we do not currently purchase commercial database information that includes location data derived from internet advertising," Wray said. "I understand that we previouslyas in the pastpurchased some such information for a specific national security pilot project. But that's not been active for some time." He added that the bureau now relies on a "court-authorized process" to obtain location data from companies.
It's not immediately clear whether Wray was referring to a warrantthat is, an order signed by a judge who is reasonably convinced that a crime has occurredor another legal device. Nor did Wray indicate what motivated the FBI to end the practice.
In its landmark Carpenter v. United States decision, the Supreme Court held that government agencies accessing historical location data without a warrant were violating the Fourth Amendment's guarantee against unreasonable searches. But the ruling was narrowly construed. Privacy advocates say the decision left open a glaring loophole that allows the government to simply purchase whatever it cannot otherwise legally obtain. US Customs and Border Protection (CBP) and the Defense Intelligence Agency are among the list of federal agencies known to have taken advantage of this loophole.
Read more of this story at SoylentNews.
08:41
Top Five Reads on FOSS Force for Week Ending March 10, 2023 FOSS Force
Here are the five most read articles on FOSS Force for the week ending March 3, 2023.
The post Top Five Reads on FOSS Force for Week Ending March 10, 2023 appeared first on FOSS Force.
08:00
More Drill Press Mods: Adding a VFD Means No More Belt Changes Hackaday

A decent drill press is an essential machine tool for almost any kind of shop, and marks a significant step up in precision compared to a hand drill. The ability to drill square, true holes is one thing, but the added power over whats possible with a portable tool is the real game changer. If only you didnt have to switch around those damn belts to change speeds, though.
You dont, of course, if you go through the effort to add a variable frequency drive to your drill press like [Midwest Cyberpunk] did, along with some other cool mods. The donor tool for these mods came from where else? Harbor Freight. Some will quibble with that choice, but the tool was pretty cheap, and really all [Midwest] was interested in here was some decent castings and a quill with acceptable runout, since the entire power train of the tool was slated for replacement. The original motor gave way to a beefy Baldor 3-phase/240-volt motor controlled by a VFD mounted on a bracket to th...
07:45
OpenForum Europe Mourns Passing of Co-Founder Basil Cousins at 91 FOSS Force
Basil Cousins, the co-founder and director of OpenForum Europe has died after a long illness.
The post OpenForum Europe Mourns Passing of Co-Founder Basil Cousins at 91 appeared first on FOSS Force.
07:39
Law enforcement seized the website selling the NetWire RAT and arrested a Croatian man Security Affairs
An international law enforcement operation seized the infrastructure associated with the NetWire RAT and resulted in the arrest of its administrator.
A coordinated international law enforcement operation resulted in the seizure of the infrastructure associated with the NetWire RAT, the police also arrested its administrator.
Law enforcement seized the website www.worldwiredlabs[.]com and its alleged administrator, a Croatian national.
 ...
...07:10
Open Source: Separating Fact from Fiction Linux.com

Read the original blog at The Linux Foundation
The post Open Source: Separating Fact from Fiction appeared first on Linux.com.
07:09
Age Verification Mandates Would Undermine Anonymity Online Deeplinks
Age verification systems are surveillance systems. Mandatory age verification, and with it, mandatory identity verification, is the wrong approach to protecting young people online. It would force websites to require visitors to prove their age by submitting information such as government-issued identification. This scheme would lead us further towards an internet where our private data is collected and sold by default. The tens of millions of Americans who do not have government-issued identification may lose access to much of the internet. And anonymous access to the web could cease to exist.
Why We Are Against Age Verification Mandates
Age verification laws dont just impact young people. Its necessary to confirm the age of all website visitors, in order to keep out one select age group.
Once information is shared to verify age, theres no way for a website visitor to be certain that the data theyre handing over is not going to be retained and used by the website, or further shared or even sold. While some age verification mandates have limits on retention and disclosure of this data, significant risk remains. Users are forced to trust that the website they visit, or its third-party verification service, both of which could be fly-by-night companies with no published privacy standards, are following these rules.
Further, there is risk that website employees will misuse the data, or that thieves will steal it. The more information a website collects, the more chances there are for it to get into the hands of a marketing company, a bad actor, or someone who has filed a subpoena for it. This would inevitably lead to further data breaches, because these laws wont just affect companies that are big enough to have robust data protection. If a website misuses or mishandles the data, the visitor might never find out. And if they do, they might lack an adequate enforcement mechanism. For example, one recent age verification law requires a user to prove damages resulting from the unlawful retention of data, in order to hold the website accountable in courta difficult bar to reach.
These mandates wouldnt just kick young people offline. There are tens of millions of U.S. residents without a form of government-issued identification. They could also be kept offline if age verification is required. These are primarily lower-income people who are ...
06:45
Radeon ProRender SDK 3.1 Released - Finishes Transition From OpenCL To HIP Phoronix
AMD today published Radeon ProRender SDK 3.1 as the newest rendering engine...
06:30
Making Dry Ice at Home is Just as Hard as It Sounds Hackaday

Along the road to developing his own cryocooler to produce liquid nitrogen, there are a number of interesting rabbit holes [Hyperspace Pirate] has found himself taking a look at. For example, using dry ice for a pre-cooling stage and subsequently wondering what itd take to make this dry ice oneself.
Getting the CO2 required for the dry ice is the easy part, requiring nothing more complicated than baking soda and a suitable acid (like hydrochloric acid). The other options to gather CO2 include using yeast, capturing the gas from the air people breathe out, calcium hydroxide, etc., none of which are as easy or convenient.
06:30
Video Friday: Agilicious IEEE Spectrum
Video Friday is your weekly selection of awesome robotics
videos, collected by your friends at IEEE Spectrum
robotics. We also post a weekly calendar of upcoming robotics
events for the next few months. Please
send us your events for inclusion.
HRI 2023: 1316 March 2023, STOCKHOLM
Robotics Summit & Expo: 1011 May 2023, BOSTON
ICRA 2023: 29 May2 June 2023, LONDON
RoboCup 2023: 410 July 2023, BORDEAUX, FRANCE
RSS 2023: 1014 July 2023, DAEGU, KOREA
IEEE RO-MAN 2023: 2831 August 2023, BUSAN, KOREA
CLAWAR 2023: 24 October 2023, FLORIANOPOLIS, BRAZIL
Humanoids 2023: 1214 December 2023, AUSTIN, TEXAS
Enjoy todays videos!
Agilicious is a co-designed hardware and software framework tailored to autonomous, agile quadrotor flight, which has been developed and used since 2016 at the Robotics and Perception Group of the University of Zurich. Agilicious is completely open-source and open hardware and supports both model-based and neural-network-based controllers!
[ Agilicious ]
Flexivs adaptive robot masseur fuses force control, computer vision, and artificial intelligence to emulate the skill and dexterity of a human massage therapist.
...
06:09
Feds Open New Tesla Probe After Two Model Y Steering Wheels Come Off SoylentNews
Tesla has yet another federal headache to contend with. On March 4, the National Highway Traffic Safety Administration's Office of Defects Investigation opened a preliminary investigation after two reports of Tesla Model Y steering wheels detaching in drivers' hands while driving.
NHTSA's ODI says that in both cases, the model year 2023 Model Ys each required repairs on the production line that involved removing their steering wheels. The wheels were refitted but were only held in place by frictionTesla workers never replaced the retaining bolt that affixes the steering wheel to the steering column. In 2018, Ford had to recall more than 1.3 million vehicles after an incorrectly sized bolt resulted in a similar problem.
The ODI document states that "sudden separation occurred when the force exerted on the steering wheel overcame the resistance of the friction fit while the vehicles were in motion" and that both incidents occurred while the electric vehicles still had low mileage.
Related:
Tesla
recalls all cars with FSD (full self driving) option (Elon
Tweet:"Definitely. The word "recall" for an over-the-air software
update is anachronistic and just flat wrong!")
Feds Open
Criminal Investigation Into Tesla Autopilot Claims
NHTSA
Investigation Into Telsa Autopilot Intensifies
Tesla's
Radar-less Cars Investigated by NHTSA After Complaints
Spike
Tesla
Under Federal Investigation Over Video Games That Drivers Can
Play
Tesla
Must Tell NHTSA How Autopilot Sees Emergency Vehicles
NHTSA
Opens Investigation into Tesla Autopilot after Crashes with Parked
Emergency Vehicles
Tesla
Recall is Due to Failing Flash Memory
Tesla
Crash Likely Caused by Video Game Distraction
Autopilot
Was Engaged...
06:00
Yu Yuan on Building A Persistent Virtual World IEEE Spectrum

Despite tech giants including Meta, Microsoft, and Nvidia investing billions of dollars in the development of the metaverse, it is still little more than a fantasy. Making it a reality is likely to require breakthroughs in a range of sectors such as storage, modeling, and communication.
To spur progress in the advancement of those technologies, the IEEE Standards Association has launched the Persistent Computing for Metaverse initiative. As part of the IEEEs Industry Connections Program, it will bring together experts from both industry and academia to help map out the innovations that will be needed to make the metaverse a reality.
Although disparate virtual-reality experiences exist today, the metaverse represents a vision of an interconnected and always-on virtual world that can host thousands, if not millions, of people simultaneously. The ultimate goal is for the virtual world to become so realistic that it is almost indistinguishable from the real one.
Todays technology is a long way from making that possible, says Yu Yuan, president of the IEEE Standards Association. The Institute spoke with Yuan to find out more about the initiative and the key challenges that need to be overcome. His answers have been edited for clarity.
The Institute: What is persistent computing?
Yu Yuan: I have been working in virtual reality and multimedia for more than 20 years, I just didnt call my work metaverse. After metaverse became a buzzword, I asked myself, Whats the difference between metaverse and VR? My answer is: persistence, or the ability to leave traces in a virtual world.
Persistent computing refers to the combination of all the technologies needed to support the development and operation of a persistent virtual world. In other words, a metaverse. There are different kinds of VR experiences, but many of them are one-time events. Similar to how video games work, every time a user logs in, the entire virtual world resets. But users in t...
05:32
Cybersecurity Firm Acronis Data Breach: Hackers Leak 21GB of Data HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
Acronis has confirmed the data breach, stating that the leak does not contain login credentials.
This is a post from HackRead.com Read the original post: Cybersecurity Firm Acronis Data Breach: Hackers Leak 21GB of Data
05:22
Its Board Election Time at Open Source Initiative Again FOSS Force
If this is March, it must be election time at OSI. This year, two individual seats and one affiliate seat are in the running.
The post Its Board Election Time at Open Source Initiative Again appeared first on FOSS Force.
05:10
UK Govt: Piracy Snitch Campaign Not Ideal During a Cost of Living Crisis TorrentFreak
 After reading hundreds of copyright reports, anti-piracy
studies, lobbying documents, and submissions to government and law
enforcement agencies, anything that strays from the norm tends to
stand out.
After reading hundreds of copyright reports, anti-piracy
studies, lobbying documents, and submissions to government and law
enforcement agencies, anything that strays from the norm tends to
stand out.
Last month the Industry Trust For IP published Taking a Whole Society Approach to Infringement in the UK, a report promoting collaboration and understanding to reduce piracy levels in the UK.
Our initial article focused on just one item in the report but something much more fundamental ran throughout. A pleasant surprise, even.
Softer, More Cooperative Tone
There is no such thing as a friendly anti-piracy report, the topic immediately rules that out, but the language and tone in the Industry Trusts publication is interestingly close. Considering that companies behind the Industry Trust include Sony, Universal, Disney, and Warner, not to mention Sky, Premier League and the Federation Against Copyright Theft, that seemed a little unusual.
Familiar themes are present calls for tech platforms to do more and hosts to implement Know Your Customer regimes to help identify pirates, for example. However, forceful language such as must be required to implement X and should be prevented from doing Y are mostly replaced by scenarios where various entities could be a real help if they did A, B or C.
Policymakers could update the UK Policy framework with due diligence protocols for intermediaries providing commercial services to online businesses
Technology companies could support enforcement efforts by introducing improved customer identification and verification
Technology companies could implement technical measures that introduce greater friction into infringement journeys
This type of language and tone certainly fits the overall sentiment of a collaborative campaign but also unusual enough to warrant a closer look.
Whether by pure coincidence or otherwise, the government appears to have concluded that aggressive messaging over online piracy may seem at odds with the cooperative tone that it considers advisable in communications this year.
Its hard to say whether the Industry Trusts recent report should be viewed as a product of government advice or independently prudent, but these them...
05:01
Inject external data in policy evaluations with Conftest Linux.com
Separating policy from data enables more robust and reusable policy definitions that allow you to factor external data sources in compliance evaluation.
Read More at Enable Sysadmin
The post Inject external data in policy evaluations with Conftest appeared first on Linux.com.
03:39
EPO Weaponises International Womens Day to Cover Up Its Attacks on Women Techrights
Video download link | md5sum
16272ba8c3034e82e1d6d5269085e6e5
EPO Women Affairs
Creative Commons Attribution-No Derivative Works 4.0
Summary: The narcissistic management of the EPO pats itself on the back over feminism, diversity etc. while women who actually work real work at the Office (examiners, not the family/cabal lodged at the top floor) dispute this misleading PR-esque narrative
Some years ago
there was
some waffle [PDF] from Elodie Bergot, who was promoted not as a woman
but as a family member (spouse) of the EPOs
mafia (Benot Battistellis faithful servant
from INPI). Bergot seems to be attacking more women than she
attacks men (M. & E.). Hows that for an achievement? Cat fights
are not breeding diversity more so in an office that already fails
to attract women and barely offers them promotions (compared to
men), according to the EPOs own numbers.
 Antnio Campinos also supports women. He
brought women without relevant experience in patents just because
they had previously worked with him at EUIPO the
subject of a new scandal as noted in the video above. It is
connected to Christian Archambeau, a confidant of
Campinos, who originally came from the EPO.
Antnio Campinos also supports women. He
brought women without relevant experience in patents just because
they had previously worked with him at EUIPO the
subject of a new scandal as noted in the video above. It is
connected to Christian Archambeau, a confidant of
Campinos, who originally came from the EPO.
Nothing allures women scientists more and even attracts them to the EPO than a Mr. Campinos dropping F bombs in front of women. Apply today, the fuckin...
03:30
Box86 v0.3 & Box64 v0.2.2 Released For Running Linux x86/x86_64 Programs On Arm Phoronix
In addition to this week seeing new releases of FEX-Emu and Hangover for open-source projects aiming to run x86/x86_64 binaries on 64-bit Arm, the Box86 and related Box64 projects are out today with their own feature updates for helping to enable x86 and x86_64 Linux binaries on Arm systems...
03:27
Moderna CEO Says Private Investors Funded COVID VaccineNot Billions From Gov't SoylentNews
Moderna CEO Stphane Bancel on Monday pushed back on criticism of the company's plans to raise the price of its mRNA-based COVID-19 vaccines by 400 percent, arguing that the billions of dollars in federal funding the company received played little role in the vaccine's development.
Speaking at the Wall Street Journal Health Forum, Bancel suggested that the vaccine's development is thanks to private investors and that the federal funding merely hastened development that would have occurred regardless.
[...]
While the government most recently paid $26 per dose of Moderna's updated booster, the company is planning to raise the price of its shots to $110 to $130 per dose.
Related:
"Pure and
Deadly Greed": Lawmakers Slam Pfizer's 400% Price Hike on COVID
Shots
Read more of this story at SoylentNews.
02:51
Unearthing Crimes of Sirius Open Source schestowitz.com
Video download link
| md5sum c00ff3859f267c20af0e44af8b6a439c
The Series on Sirius Crimes
Creative Commons Attribution-No Derivative Works 4.0
Summary: Today we start a string of videos and short texts about the company my wife and I left in December (we resigned just over 3 months ago); as it turns out, the company had been committing crimes for years before we left
THE Pensiongate mini-series is becoming a lot more extensive and far longer than we first estimated. We find out more and more things as one scandal helps unfold another. As such, this morning we started a dedicated Wiki page, Crimes of Sirius Open Source a complementary subset of Sirius Open Source, which started back in December.
The video above explains the motivation and emphasises that well try to cover this a lot in the form of videos, delivering perhaps a dozen more parts, including bits of evidence. Video will be a convenient means by which to deliver the material in a privacy-respecting matter.
Its sort of sad that weve come to this, but if you deal with people who defrauded not only you but also your colleagues, then it becomes imperative to speak out and do something about it. Some people have asked me to pursue a legal opinion on this. As a side note, several people say they love the term Mr. Kink, which does not infringe anyones privacy yet says a lot.
The journey required to write the series is mostly free free as in beer/gratis. The material is in the public domain, e.g. the Companies House. Its free. Except all the times we phoned pension providers quite an expensive endeavour when you do it for 2-3 months. The upside is that along the way we learned a lot about how the system works and how it is abused. Its cheaper to learn that on ones own. For instance, when my wife and I demand the money from both our accounts the providers are pretending its not possible (it is; with the high tax applied) and if they say no, or intentionally mislead clients, one...
02:48
Iran and Saudi Arabia Agree to Restore Relations cryptogon.com
Via: Al Jazeera: Iran and Saudi Arabia have agreed to re-establish diplomatic relations and reopen their embassies within two months, according to Iranian and Saudi state media. The agreement was reached on Friday during talks in Beijing. Iranian state media posted images and video of Ali Shamkhani, secretary of the Supreme National Security Council of []
02:47
Sirius Open Source Pensiongate: A Long Story Merits Many Videos Techrights
Video download link
| md5sum c00ff3859f267c20af0e44af8b6a439c
The Series on Sirius Crimes
Creative Commons Attribution-No Derivative Works 4.0
Summary: Today we start a string of videos and short texts about the company my wife and I left in December (we resigned just over 3 months ago); as it turns out, the company had been committing crimes for years before we left
THE Pensiongate mini-series is becoming a lot more extensive and far longer than we first estimated. We find out more and more things as one scandal helps unfold another. As such, this morning we started a dedicated Wiki page, Crimes of Sirius Open Source a complementary subset of Sirius Open Source, which started back in December.
For those who have missed some of the context, here are just several of the posts that covered this matter:
02:15
The author of the Xenomorph Android malware, the Hadoken Security Group, continues to improve their malicious code.
In February 2022, researchers from ThreatFabric first spotted the Xenomorph malware, which was distributed via the official Google Play Store reaching over 50,000 installations.
The banking Trojan was used to target 56 European banks and steal sensitive information from the devices of their customers. The analysis of the code revealed the presence of not implemented features and the large amount of logging present, a circumstance that suggests that this threat is under active development.
Xenomorph shares overlaps with the Alien banking trojan, but it has functionalities radically different from the Aliens one.
The experts noticed that the was continuously improved during 2022 and was distributed in small campaigns. The operators first distributed the Android malware via the GymDrop dropper operation, later the malicious code was also distributed via the Zombinder operation.
Experts warn that a new variant recently discovered, tracked as Xenomorph.C, was significantly improved.
The new variant supports a new automated transfer system (ATS) framework and can target over 400 banks and financial institutions mainly from Spain, Turkey, Poland, the United States, Australia, Canada, Italy, Portugal, France, Germany, UAE, and India
capabilities to an already feature rich Android Banker, most notably the introduction of a very extensive runtime engine powered by Accessibility services, which is used by actors to implement a complete ATS framework. With these new features, Xenomorph is now able to completely automate the whole fraud chain, from infection to funds exfiltration, making it one of the most advanced and dangerous Android Malware trojans in circulation. reads the report published by Threat Fabric. In addition, the samples identified by ThreatFabric featured config...01:57
[$] Interview: the FreeCAD Project Association LWN.net
The sustainability of free software continues to be mostly uncharted waters. No team is the same as any other, so copying, say, the Blender Foundations approach to governance will, most likely, not work for other projects. But there is value in understanding how various non-commercial organizations operate in order to make informed decisions for the governance of new ones. In late 2021, the FreeCAD team launched the FreeCAD Project Association (FPA) to handle the various assets that belong to this free 3D CAD project. In this interview, Yorik van Havre, a longtime FreeCAD developer and current president of the Association guides us through the process of starting and managing the FPA.
01:46
Microsoft to boost protection against malicious OneNote documents Help Net Security
Microsoft has announced that, starting in April 2023, they will be adding enhanced protection when users open or download a file embedded in a OneNote document a known high-risk phishing file type. Users will receive a notification when the files seem dangerous to improve the file protection experience in OneNote on Windows, the company said. A popular technique for malware delivery When last July Microsoft started blocking VBA macros from running by default in More
The post Microsoft to boost protection against malicious OneNote documents appeared first on Help Net Security.
01:40
01:37
Security updates for Friday LWN.net
Security updates have been issued by Debian (chromium and wireless-regdb), Fedora (caddy, python-cryptography, and redis), Oracle (gnutls), SUSE (hdf5, opera, python-Django, redis, tomcat, and xen), and Ubuntu (apache2 and snakeyaml).
01:02
New Version of Prometei Botnet Infects Over 10,000 Systems Worldwide The Hacker News
00:50
China-linked Hackers Targeting Unpatched SonicWall SMA Devices with Malware The Hacker News
A suspecting China-linked hacking campaign has been observed targeting unpatched SonicWall Secure Mobile Access (SMA) 100 appliances to drop malware and establish long-term persistence. "The malware has functionality to steal user credentials, provide shell access, and persist through firmware upgrades," cybersecurity company Mandiant said in a technical report published this week. The
00:39
International Law Enforcement Takes Down Infamous NetWire Cross-Platform RAT The Hacker News
A coordinated international law enforcement exercise has taken down the online infrastructure associated with a cross-platform remote access trojan (RAT) known as NetWire. Coinciding with the seizure of the sales website www.worldwiredlabs[.]com, a Croatian national who is suspected to be the website's administrator has been arrested. While the suspect's name was not released, investigative
Friday, 10 March
11:00
Reducing Withdrawal and Failure Rates with Labeled Subgoals It Will Never Work in Theory
Being a good programmer doesn't automatically make you good at teaching other people to program. In fact, the unconscious competence that allows you to focus on the problem rather than stumbling over syntax issues or fumbling to create functions may actually make you worse as a teacher, since you will skip or combine steps that novices still need to do slowly and one at a time.
Research has proven that labeling subgoalsi.e., breaking a solution technique down into small steps and giving those steps nameshelps learners master material more quickly. This study looked more closely at the benefits of labeled subgoals for introductory programming courses. The authors found that it helped on quizzes given within a week of new material being presented, but didn't make a difference to overall results on final exams done later. However, students who had been given labeled subgoals performed more consistently on exams; perhaps more importantly, they were also less likely to drop or fail the course. While studies like this one may not get the same attention as Silicon Valley hype about AI disrupting education, their findings are much more likely to actually help the next generation of programmers learn their craft.
Lauren E. Margulieux, Briana B. Morrison, and Adrienne Decker. Reducing withdrawal and failure rates in introductory programming with subgoal labeled worked examples. International Journal of STEM Education, May 2020. doi:10.1186/s40594-020-00222-7.
Background: Programming a computer is an increasingly valuable skill, but dropout and failure rates in introductory programming courses are regularly as high as 50%. Like many fields, programming requires students to learn complex problem-solving procedures from instructors who tend to have tacit knowledge about low-level procedures that they have automatized. The subgoal learning framework has been used in programming and other fields to break down procedural problem solving into smaller pieces that novices can grasp more easily, but it has only been used in short-term interventions. In this study, the subgoal learning framework was implemented throughout a semester-long introductory programming course to explore its longitudinal effects. Of 265 students in multiple sections of the course, half received subgoal-oriented instruction while the other half received typical instruction.
Results: Learning subgoals consistently improved performance on quizzes, which were formative and given within a week of learning a new procedure, but not on exams, which were summative. While exam performance was not statistically better, the subgoal group had lower variance in exam scores and fewer students dropped or failed the course than in the control group....
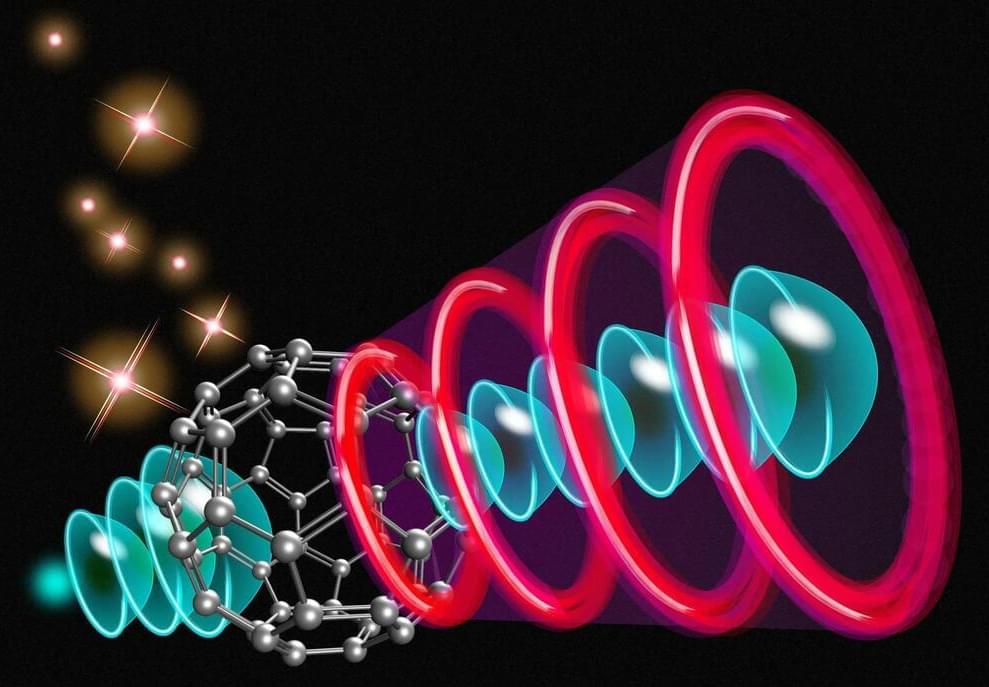















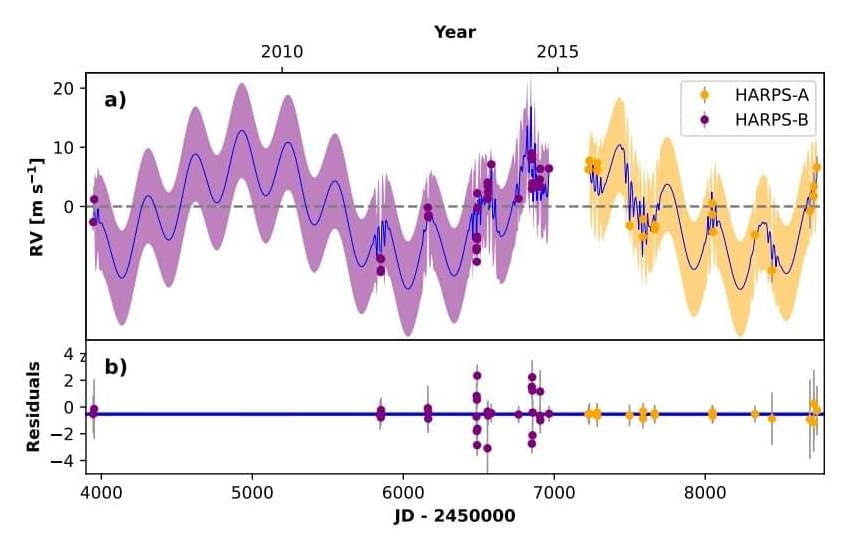













 additions & protect yourself from a malicious
additions & protect yourself from a malicious 



 has taken down the
has taken down the  Main
suspect arrested.
Main
suspect arrested.