| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Saturday, 08 April
01:47
[$] The shrinking role of semaphores LWN.net
The kernel's handling of concurrency has changed a lot over the years. In 2023, a kernel developer's toolkit includes tools like completions, highly optimized mutexes, and a variety of lockless algorithms. But, once upon a time, concurrency control came down to the use of simple semaphores; a discussion on a small change to the semaphore API shows just how much the role of semaphores has changed over the course of the kernel's history.
01:30
String Operations the Hard(ware) Way Hackaday

One of the interesting features of the 8086 back in 1978 was the provision for string instructions. These took the form of prefixes that would repeat the next instruction a certain number of times. The next instruction was meant to be one of a few string instructions that operated on memory regions and updated pointers to the memory region with each repeated operation. [Ken Shirriff] examines the 8086 die up close and personal to explain how the 8086 microcode pulled this off and it is a great read, as usual.
In general, the string instructions wanted memory pointers in the SI and DI registers and a count in CX. The flags also have a direction bit that determines if the SI and DI registers will increase or decrease on each execution. The repeat prefix could also have conditions on it. In other words, a REP prefix will execute the following string instruction until CX is zero. The REPZ and REPNZ prefixes would do the same but also stop early if the zero flag was set (REPZ) or not set (REPNZ) after each operation. The instructions can work on 8-bit data or 16-bit data and oddly, as [Ken] points out the microcode is the same either way.
[Ken] does a great job of explaining it all, so we wont try to repeat it here. But it is more complicated than youd initially expect. Partially this is because the instruction can be interrupted after any operation. Also, changing the SI and DI registers not only have to account for increment or decreme...
01:23
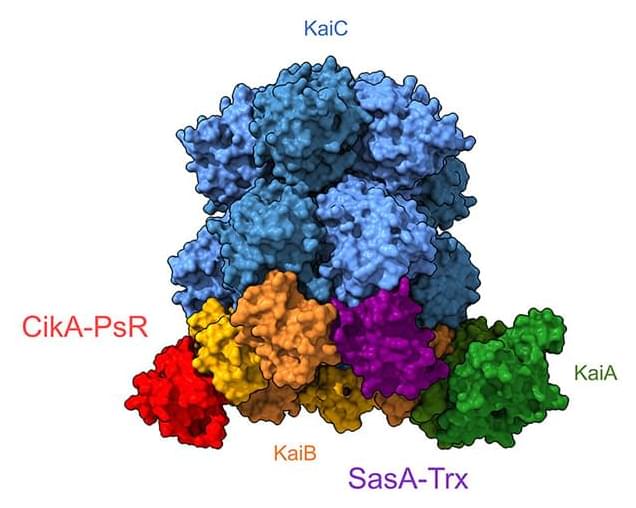
Researchers Studied a Circadian Clock in Real Time in a First For Science Lifeboat News: The Blog
Large language models are drafting screenplays and writing code and cracking jokes. Image generators, such as Midjourney and DALL-E 2, are winning art prizes and democratizing interior design and producing dangerously convincing fabrications. They feel like magic. Meanwhile, the worlds most advanced robots are still struggling to open different kinds of doors. As in actual, physical doors. Chatbots, in the proper context, can beand have beenmistaken for actual human beings; the most advanced robots still look more like mechanical arms appended to rolling tables. For now, at least, our dystopian near future looks a lot more like Her than M3GAN.
The counterintuitive notion that its harder to build artificial bodies than artificial minds is not a new one. In 1988, the computer scientist Hans Moravec observed that computers already excelled at tasks that humans tended to think of as complicated or difficult (math, chess, IQ tests) but were unable to match the skills of a one-year-old when it comes to perception and mobility. Six years later, the cognitive psychologist Steven Pinker offered a pithier formulation: The main lesson of thirty-five years of AI research, he wrote, is that the hard problems are easy and the easy problems are hard. This lesson is now known as Moravecs paradox.
01:22
A Cosmologist Explains How Our Universe Could Be a Random Bubble in the Multiverse Lifeboat News: The Blog
Within the larger, true universe, ours could have branched off due to a random quantum fluctuation.
01:22
New electric boat motor uses wind and water to recharge its batteries at sea Lifeboat News: The Blog
It may not offer infinite range, but its close. The new Oceanvolt ServoProp saildrive has a regeneration feature that efficiently charges up an electric boats batteries while sailing.
Many people think of sailboats as being purely wind powered. While smaller sailboats usually are, most decently sized sailboats have a motor for maneuvering in a marina or when the winds die down.
Saildrive motors are an innovative propulsion system commonly found on modern sailboats, offering a compact and efficient alternative to traditional shaft-driven inboard engines.
00:50
CVE-2023-28710: Apache Airflow Spark Provider Arbitrary File Read via JDBC Open Source Security
Posted by Jarek Potiuk on Apr 07
Severity: lowDescription:
Improper Input Validation vulnerability in Apache Software Foundation Apache Airflow Spark Provider.This issue affects
Apache Airflow Spark Provider: before 4.0.1.
Credit:
Xie Jianming of Nsfocus (finder)
References:
https://github.com/apache/airflow/pull/30223
https://airflow.apache.org/
https://www.cve.org/CVERecord?id=CVE-2023-28710
00:48
CVE-2023-28706: Apache Airflow Hive Provider Beeline Remote Command Execution Open Source Security
Posted by Jarek Potiuk on Apr 07
Severity: lowDescription:
Improper Control of Generation of Code ('Code Injection') vulnerability in Apache Software Foundation Apache Airflow
Hive Provider.This issue affects Apache Airflow Hive Provider: before 6.0.0.
Credit:
sw0rd1ight of Caiji Sec Team and 4ra1n of Chaitin Tech (finder)
References:
https://github.com/apache/airflow/pull/30212
https://airflow.apache.org/
https://www.cve.org/CVERecord?id=CVE-2023-28706
00:46
CVE-2023-28707: Airflow Apache Drill Provider Arbitrary File Read Vulnerability Open Source Security
Posted by Jarek Potiuk on Apr 07
Severity: lowDescription:
Improper Input Validation vulnerability in Apache Software Foundation Apache Airflow Drill Provider.This issue affects
Apache Airflow Drill Provider: before 2.3.2.
Credit:
Kai Zhao of 3H Secruity Team (finder)
References:
https://github.com/apache/airflow/pull/30215
https://airflow.apache.org/
https://www.cve.org/CVERecord?id=CVE-2023-28707
00:00
This Week in Security: Cookie Monster, CyberGhost, NEXX, and Dead Angles Hackaday

Operation Cookie Monster ranks as one of the best code names in recent memory. And its apropo, given what exactly went down. Genesis Market was one of those marketplaces where criminals could buy and sell stolen credentials. This one was a bit extra special.
Websites and services are getting better about detecting logins from unexpected computers. Your Google account suddenly logs in from a new computer, and a two-factor authentication challenge launches. Why? Your browser is missing a cookie indicating youve logged in before. But theres more. Providers have started rolling out smart analytics that check for IP address changes and browser fingerprints. Your mix of time zone, user string, installed fonts, and selected language make a pretty unique identifier. So sites like Genesis offer Impersonation-as-a-Service (IMPaaS), which is session hijacking for the modern age.
A victim computer gets owned, and credentials are collected. But so are cookies and a browser fingerprint. Then a criminal buyer logs in, and runs a virtual browser with all that collected data. Run through a proxy to get a IP that is geolocated close enough to the victim, and Mr. Bad Guy has a cloned machine with all accounts intact.
And now back to Operation Cookie Monster, a multi-organization takedown of Genesis. It...
Friday, 07 April
23:50
System76 Making COSMIC Improvements To Their Launcher, Better Performance Phoronix
In addition to working on their in-house Linux laptop prototype and other hardware endeavors, System76 continues being quite busy working on their COSMIC desktop environment to be used by their Pop!_OS Linux distribution...
23:39
Security updates for Friday LWN.net
Security updates have been issued by Mageia (ldb/samba, libapreq2, opencontainers-runc, peazip, python-cairosvg, stellarium, and zstd), Oracle (httpd and mod_http2, kernel, and nss), SUSE (conmon, go1.19, go1.20, libgit2, openssl-1_1, and openvswitch), and Ubuntu (emacs24).
23:30
23:22
Living electrodes with bacteria and organic electronics Lifeboat News: The Blog
Researchers at the Laboratory of Organic Electronics, Linkping University, have together with colleagues at the Lawrence Berkeley National Laboratory in Berkeley, California, developed a method that increases the signal strength from microbial electrochemical cells by up to twenty times. The secret is a film with an embedded bacterium: Shewanella oneidensis.
Adding bacteria to electrochemical systems is often an environmentally sensitive means to convert chemical energy to electricity. Applications include water purification, bioelectronics, biosensors, and for the harvesting and storage of energy in fuel cells. One problem that miniaturisation of the processes has encountered is that a high signal strength requires large electrodes and a large volume of liquid.
Researchers at Linkping University, together with colleagues at the Lawrence Berkeley National Laboratory in Berkeley, California, USA, have now developed a method in which they embed the electroactive bacterium Shewanella oneidensis into PEDOT: PSS, an electrically conducting polymer, on a substrate of carbon felt.
23:22
How amber creates exquisite fossils Lifeboat News: The Blog
A warm-hued material prized by jewelry makers, amber takes more than 40,000 years to form. See pictures of some of the finest specimens.
23:13
These Deep-Sea Potatoes Could be the Future of Mining for Renewable Energy SoylentNews
Battery materials dot the ocean floor. Should we go get them?
To transform our world to address climate change, we need a lot of stuff: lithium for batteries, rare-earth elements like neodymium and dysprosium for wind turbines, copper for, well, basically everything.
We're not exactly going to run out of any of these key materials: the planet has plenty of the resources we need to build clean energy infrastructure. But mining is a huge and complicated undertaking, so the question is whether we can access what we need quickly and cheaply enough. We won't run out of key ingredients for climate action, but mining comes with social and environmental ramifications.
Take copper, for example. Demand for the metal in energy technologies alone will add up to over a million tons every year by around 2050, and it's getting harder to find good spots to dig up more. Companies are resorting to mining sites with lower concentrations of copper because we've exhausted the accessible higher-concentration spots we know about.
Because of the impressive array of metals they contain, at least one company has likened each nodule to a battery in a rock. That's why over the past decade, companies have begun to explore the possibility of commercial mining operations in the deep sea, mostly in the Clarion-Clipperton Zone.
The ocean could be a new source for copper and other crucial materials. Seabed mining could happen in a few different ways, but the stars of the show are potato-sized lumps called polymetallic nodules. These nodules dot the ocean floor in some places, especially in the Clarion-Clipperton Zone, which lies between Hawaii and Mexico in the Pacific Ocean.
Read more of this story at SoylentNews.
23:01
Learn Gawk by playing a fun word game Linux.com
Practice your command-line skills while seeing how many words you can make from 9 random letters.
Read More at Enable Sysadmin
The post Learn Gawk by playing a fun word game appeared first on Linux.com.
22:46
Meta's Buck2 build system LWN.net
Meta has announced the release of a new build system called Buck2.
While it shares some commonalities with other build systems (like Buck1 and Bazel), Buck2 is a from-scratch rewrite. Buck2 features a complete separation of the core and language-specific rules, with increased parallelism, integration with remote execution and virtual file systems, and a redesigned console output. All of these changes are aimed at helping engineers and developers spend less time waiting, and more time iterating on their code.
22:32
Researchers Uncover Thriving Phishing Kit Market on Telegram Channels The Hacker News
In yet another sign that Telegram is increasingly becoming a thriving hub for cybercrime, researchers have found that threat actors are using the messaging platform to peddle phishing kits and help set up phishing campaigns. "To promote their 'goods,' phishers create Telegram channels through which they educate their audience about phishing and entertain subscribers with polls like, 'What type
22:14
Rust Support Is Being Worked On For The Linux Kernel's V4L2/Media Subsystem Phoronix
As the latest effort in the quest of bringing Rust programming language usage to the Linux kernel, sent out on Thursday were initial patches for bringing Rust infrastructure to the Video 4 Linux 2 (V4L2) framework within the media subsystem...
21:27
60-Year-Old Music Pirate Faces Prison in a Country Part-Run By Pirates TorrentFreak
 Rick Falkvinge founded the first Pirate Party on January
1, 2006, and then rallied the masses in Sweden six months later in
the wake of the
first police raid against The Pirate Bay.
Rick Falkvinge founded the first Pirate Party on January
1, 2006, and then rallied the masses in Sweden six months later in
the wake of the
first police raid against The Pirate Bay.
At the European Elections of 2009, Swedish Pirates won over 7% of the vote. Christian Engstrm went on to become the first Pirate Member of the European Parliament, with Amelia Andersdotter taking the second seat in 2011.
When Felix Reda of the German Pirate Party was elected vice-president of the Greens/EFA group in the European Parliament in 2014, and was given the job of copyright reform rapporteur, that was a moment for the archives. It wouldnt be the last.
Czech Pirates and Czech Piracy
A string of notable events in the Czech Republic, including three Pirate Party politicians taking seats in the European Parliament, culminated in 2021 when Pirates won three ministerial positions in the countrys coalition government.
Set to a background of intense Pirate politics and the movements roots in file-sharing communities, news that a 60-year-old Czech Republic man is facing up to two years in prison for file-sharing feels a little out of place. Of all things that were never supposed to happen when Pirates got into power, this was one of them.
Czech police say the man had a collection of almost 1,000 commercial music albums stored on a server, which is quite a lot. The server wasnt protected in any way, so passing internet users could download whatever they liked. Unfortunately, those passing by included unnamed rightsholders who filed a criminal copyright complaint with the police.
Authorities Take Matter Seriously
According to a statement released by police in the Moravian-Silesian region, criminal investigators in the city of Karvina responded to the complaint by launching an extensive multi-month investigation. After establishing that the albums had been available for download from October 2013 until November 2022, police charged the man with criminal copyright infringement offenses.
The accused stated that he downloaded the music mainly for his own...
21:25
Eliezer Yudkowsky Why AI Will Kill Us, Aligning LLMs, Nature of Intelligence, SciFi, & Rationality Lifeboat News: The Blog

For 4 hours, I tried to come up reasons for why AI might not kill us all, and Eliezer Yudkowsky explained why I was wrong.
We also discuss his call to halt AI, why LLMs make alignment harder, what it would take to save humanity, his millions of words of sci-fi, and much more.
If you want to get to the crux of the conversation, fast forward to 2:35:00 through 3:43:54. Here we go through and debate the main reasons I still think doom is unlikely.
Transcript: https://dwarkeshpatel.com/p/eliezer-yudkowsky.
Apple Podcasts: https://apple.co/3mcPjON
Spotify: https://spoti.fi/3KDFzX9
Follow me on Twitter: https://twitter.com/dwarkesh_sp.
Timestamps:
(0:00:00) TIME article.
(0:09:06) Are humans aligned?
(0:37:35) Large language models.
(1:07:15) Can AIs help with alignment?
(1:30:17) Societys response to AI
(1:44:42) Predictions (or lack thereof)
(1:56:55) Being Eliezer.
(2:13:06) Othogonality.
(2:35:00) Could alignment be easier than we think?
(3:02:15) What will AIs want?
(3:43:54) Writing fiction & whether rationality helps you win.
21:24
Lawrence Livermore Lab Scientists Build Telescope for International Space Station Lifeboat News: The Blog
Lawrence Livermore Laboratory (LLNL) scientists designed and built a telescope that, as of March 14, was out of this world.
The Stellar Occultation Hypertemporal Imaging Payload (SOHIP) is a telescope using LLNL patented optics technology on a gimbal to observe and measure atmospheric gravity waves and turbulence.
The device was sent aboard a SpaceX rocket out of Cape Canaveral in Florida last month to the International Space Station (ISS).
21:24
Nine-Year-Old Child Genius Stuns NASA Scientists While Visiting The Space Telescope Science Institute Lifeboat News: The Blog
Child protge, David Balogun, continues to shock the world with his incredible genius.
The nine-year-old is one of the youngest high school graduates, receiving his diploma from Reach Cyber Charter School in Harrisburg, PA. After graduation, Balogun was invited by NASA and the Maryland-based Space Telescope Science Institute to visit the James Webb Space Telescope Mission Operations Center in Baltimore. His story made headlines and Hannah Braun, the institutes spokesperson, said the team just had to meet him.
I had actually seen Davids story all over social media and thought, Wow, Id bet hed find a trip to Webbs Mission Operations Center exciting! Braun said to Atlanta Black Star.
21:13
Rilide browser extension steals MFA codes Help Net Security
Cryptocurrency thieves are targeting users of Chromium-based browsers Google Chrome, Microsoft Edge, Brave Browser, and Opera with an extension that steals credentials and can grab multi-factor authentication (MFA) codes. The malicious extension Dubbed Rilide by Trustwave researchers, the extension mimics the legitimate Google Drive extension while, in the background, it disables the Content Security Policy (CSP), collects system information, exfiltrates browsing history, takes screenshots, and injects malicious scripts. It aims to allow attackers More
The post Rilide browser extension steals MFA codes appeared first on Help Net Security.
21:00
Arbitrary Code Execution Over Radio Hackaday

Computers connected to networks are constantly threatened by attackers who seek to exploit vulnerabilities wherever they can find them. This risk is particularly high for machines connected to the Internet, but any network connection can be susceptible to attacks. As highlighted by security researcher and consultant [Rick Osgood], even computers connected to nothing more than a radio can be vulnerable to attacks if theyre using certain digital modes of communication.
The vulnerability that [Rick] found involves exploiting a flaw in a piece of software called WinAPRS. APRS is a method commonly used in the amateur radio community for sending data over radio, and WinAPRS allows for this functionality on a PC. He specifically sought out this program for vulnerabilities since it is closed-source and hasnt been updated since 2013. After some analysis, he found a memory bug which was used to manipulate the Extended Instruction Pointer (EIP) register which stores the memory address of the next instruction to be executed by the CPU. This essentially allows for arbitrary code execution on a remote machine via radio.
The exploit was found while using Windows XP because it lacks some of the more modern memory protection features of modern operating systems, but the exploit does still work with Windows 10, just not as reliabl...
20:43
AMD Instinct MI300 "GFX940" Support Merged To Mesa 23.1 Phoronix
While going back a year there has been "GFX940" open-source driver work happening within the AMDGPU LLVM compiler back-end and AMDGPU/AMDKFD Linux kernel drivers and the like, only this week was support merged for GFX940 into Mesa...
20:38
Microsoft aims at stopping cybercriminals from using cracked copies of Cobalt Strike Security Affairs
Microsoft announced it has taken legal action to disrupt the illegal use of copies of the post-exploitation tool Cobalt Strike by cybercriminals.
Cobalt Strike is a paid penetration testing product that allows an attacker to deploy an agent named Beacon on the victim machine. The Beacon includes a wealth of functionality for the attacker, including, but not limited to command execution, key logging, file transfer, SOCKS proxying, privilege escalation, mimikatz, port scanning and lateral movement.
Microsoft Digital Crimes Unit (DCU) announced that has collaborated with Fortra, the company that develops and maintains the tool, and Health Information Sharing and Analysis Center (Health-ISAC) to curb the abuse of Cobalt Strike by cybercriminals.
The Microsoft DCU secured a court order in the U.S. to remove cracked versions of Cobalt Strike (refer to stolen, unlicensed, or otherwise unauthorized versions or copies of the tool) so they can no longer be used by cybercriminals.
Threat actors, including ransomware groups and nation-state actors, use Cobalt Strike after obtaining initial access to a target network. The tool is used to conduct multiple malicious activities, including escalating privileges, lateral movements, and deploying additional malicious payloads.
More specifically, cracked versions of Cobalt Strike allow Defendants to gain control of their victims machine and move laterally through the connected network to find other victims and install malware. This includes installing ransomware like Conti, LockBit, Quantum Locker, Royal, Cuba, BlackBasta, BlackCat and PlayCrypt, to arrest access to the systems. In essence, Defendants are able to leverage cracked versions of Cobalt Strike to brutally force their way into victim machines and deploy malware. reads the court order. Additionally, once the Defendants deploy the malware or ransomware onto computers running Microsofts Window operating system, Defendants are able to execute a series of actions involving abuse of Microsofts copyrighted declaring code.
20:28
China's Space Pioneer Becomes First Private Chinese Company to Reach Orbit SoylentNews
The company is now the first in China to send a liquid fueled rocket to space:
Chinese company Space Pioneer established a pair of milestones this past Sunday, becoming the first startup to successfully reach orbit on its first attempt, and the first Chinese company to reach orbit with liquid rocket propulsion.
Space Pioneer launched its Tianlong-2 from the Jiuquan launch centre in northwest China at 4:48 a.m. ET on April 2, according to SpaceNews. The rocket carried a small satellite to a Sun-synchronous orbit, where it will test its remote sensing capabilities.
The company, officially known as Beijing Tianbing Technology Co., is the first in China to fly a rocket using liquid propellant. Tianlong-2 uses liquid oxygen kerosene rather than solid propellant made from fuel and oxidizer, which allows for more control of the thrust magnitude and is better suited for reusability.
[...] The private space venture is getting ready for the launch of Tianlong-3, a larger liquid propellant rocket that's designed with a reusable first stage similar to SpaceX's Falcon Heavy rocket. The upcoming rocket will be capable of carrying 15 tons of payload to low Earth orbit, and it's hoping to launch up to 60 satellites for China's Guowang LEO communications megaconstellation, according to Space Pioneer. The company is targeting early 2024 for the first launch of Tianlong-3, while targeting around 12 launches per year starting 2025.
Read more of this story at SoylentNews.
20:23
Phishing emails from legit YouTube address hitting inboxes Help Net Security
Phishers are targeting YouTube content creators by leveraging the services Share Video by Email feature, which delivers the phishing email from an official YouTube email address (no-reply@youtube.com). How the YouTube phishing email scam works? The email informs the targets of a new monetization policy, new rules, and prompts them to view a video. The email also contains and points to a document hosted on Google Drive and provides the password for opening it. Finally, the More
The post Phishing emails from legit YouTube address hitting inboxes appeared first on Help Net Security.
20:08
Intel AMX-COMPLEX Support Added To GNU Binutils Phoronix
Earlier this week Intel sent out AMX-COMPLEX support for the GCC compiler as a new instruction set extension for Xeon Scalable Granite Rapids. That enablement work was already merged for the imminent GCC 13 release while now AMX-COMPLEX support has also been added to GNU Binutils...
19:54
Intel oneAPI 2023.1 Released Phoronix
This week Intel formally debuted its oneAPI 2023.1 Tools package that contains the collection of various compilers, libraries, debugging tools, and related open-source offerings like OSPRay Studio and Embree 4.0...
18:18
Hangover 0.8.5 Released For Running Windows Apps/Games With Wine On AArch64/POWER Phoronix
Andr Zwing on Thursday released Hangover 0.8.5 as the third alpha release of this software for running Windows x86 32/64-bit applications and Wine on other CPU architectures like AArch64 and POWER PPC64LE...
18:10
Links 07/04/2023: Haiku Report and credcheck 1.0 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Pseudo-Open Source
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Digital Restrictions (DRM)
- Monopolies
- ...
18:00
Building the OhSillyScope Hackaday

If you have a Raspberry Pi connected to an LED matrix, you might think about creating a simple oscilloscope. Of course, the Pi isnt really well-suited for that and neither is an LED matrix, so [Thomas McDonald] decided to create the OhSillyScope, instead.
The device isnt very practical, but it does add some flash to live music performances or it makes a cool music visualizer. The matrix is only 6464 so you cant really expect it to match a proper scope. Besides that, it pulls its data from the Pis ALSA sound system.
You can find a video of the device on [Thomas] Reddit post and a few additional videos on his Instagram account. Looks like a fun project and it also serves as a nice example if you need to read data from the sound card or drive that particular LED matrix.
We might have opted for PortAudio if we had written the same code, but only because it is more portable, which probably doesnt matter here. Of course, you could also use GNURadio and some Python to drive the display. As usual, plenty of ways to solve any given problem.
17:46
IRC Proceedings: Thursday, April 06, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-060423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-060423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-060423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-060423.gmi
Over HTTP:
|
... |
17:38
A Universal Password. Unencrypted User Data and Commands. What Could Go Wrong? SoylentNews
Open garage doors anywhere in the world by exploiting this "smart" device
A market-leading garage door controller is so riddled with severe security and privacy vulnerabilities that the researcher who discovered them is advising anyone using one to immediately disconnect it until they are fixed.
Each $80 device used to open and close garage doors and control home security alarms and smart power plugs employs the same easy-to-find universal password to communicate with Nexx servers. The controllers also broadcast the unencrypted email address, device ID, first name, and last initial corresponding to each one, along with the message required to open or shut a door or turn on or off a smart plug or schedule such a command for a later time.
The result: Anyone with a moderate technical background can search Nexx servers for a given email address, device ID, or name and then issue commands to the associated controller. (Nexx controllers for home security alarms are susceptible to a similar class of vulnerabilities.) Commands allow the opening of a door, turning off a device connected to a smart plug, or disarming an alarm. Worse still, over the past three months, personnel for Texas-based Nexx haven't responded to multiple private messages warning of the vulnerabilities.
"Nexx has consistently ignored communication attempts from myself, the Department of Homeland Security, and the media," the researcher who discovered the vulnerabilities wrote in a post published on Tuesday. "Device owners should immediately unplug all Nexx devices and create support tickets with the company requesting them to remediate the issue."
Read more of this story at SoylentNews.
17:00
GPT-4 Was Released 3 Weeks Ago and 48% of Surveyed Companies Have Started Replacing Workers Terra Forming Terra
This will work well with software development by taking out the drudgery involved with actual documentation at least. That alone allows for a high level of destaffing.
Did This Twitter Move Just Cement Elon Musk's Place in History? Terra Forming Terra
Maybe. I personally fully support open source just because there is nothing truly worthy of property protection such as a patent in software development. It is more appropriate to apply copywrite law which is also set for a much longer time span.
Four babies per mother Mandate Terra Forming Terra
Four babies per mother Mandate
It is unfortunate that I must write this, but it is completely necessary. A combination of modernity, and modern contraception has collapsed the global birth rate well below sustainability and even with a massive life extension to ease the pressure, we will have a sharp decline in the global population.
Endocrinologist Forecasts More Hormone-Related Diseases as Spike Proteins Found to Deplete Endocrine Reserves Terra Forming Terra
16:15
Microsoft Takes Legal Action to Disrupt Cybercriminals' Illegal Use of Cobalt Strike Tool The Hacker News
Microsoft said it teamed up with Fortra and Health Information Sharing and Analysis Center (Health-ISAC) to tackle the abuse of Cobalt Strike by cybercriminals to distribute malware, including ransomware. To that end, the tech giant's Digital Crimes Unit (DCU) revealed that it secured a court order in the U.S. to "remove illegal, legacy copies of Cobalt Strike so they can no longer be used by
16:14
Are Source Code Leaks the New Threat Software vendors Should Care About? The Hacker News
Less than a month ago, Twitter indirectly acknowledged that some of its source code had been leaked on the code-sharing platform GitHub by sending a copyright infringement notice to take down the incriminated repository. The latter is now inaccessible, but according to the media, it was accessible to the public for several months. A user going by the name FreeSpeechEnthousiast committed
15:59
CISA Warns of Critical ICS Flaws in Hitachi, mySCADA, ICL, and Nexx Products The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has published eight Industrial Control Systems (ICS) advisories warning of critical flaws affecting products from Hitachi Energy, mySCADA Technologies, Industrial Control Links, and Nexx. Topping the list is CVE-2022-3682 (CVSS score: 9.9), impacting Hitachi Energy's MicroSCADA System Data Manager SDM600 that could allow an
15:00
Tube Amplifier Uses Low Voltage, Sips Battery Hackaday

Much like vinyl records, tube amplifiers are still prized for their perceived sound qualities, even though both technologies have been largely replaced otherwise. The major drawback to designing around vacuum tubes, if you can find them at all, is often driving them with the large voltages they often require to heat them to the proper temperatures. There are a small handful of old tubes that need an impressively low voltage to work, though, and [J.G.] has put a few of them to work in this battery-powered audio tube amplifier.
The key to the build is the Russian-made 2SH27L battery tubes which are originally designed in Germany for high-frequency applications but can be made to work for audio amplification in a pinch. The power amplifier section also makes use of 2P29L tubes, which have similar characteristics as far as power draw is concerned. Normally, vacuum tubes rely on a resistive heater to eject electrons from a conductive surface, which can involve large amounts of power, but both of these types of tubes are designed to achieve this effect with only 2.2 volts provided to the heaters.
[J.G.] is powering this amplifier with a battery outputting 5V via a USB connection, and driving a fairly standard set of speakers borrowed from a computer. While there arent any aud...
14:57
April 2023 Patch Tuesday forecast: The vulnerability discovery race Help Net Security
The answer to the question Why does software continue to have so many vulnerabilities? is complex, because the software itself is so complex. Thereve been many articles written that cover the lack of tools to test for vulnerabilities, the security knowledge and experience of the developers themselves, the endless variations of interactions between operating systems and applications, and the complexity of the network environments into which the software is deployed to name but a few More
The post April 2023 Patch Tuesday forecast: The vulnerability discovery race appeared first on Help Net Security.
14:52
Virgin Orbit Files for Bankruptcy SoylentNews
Virgin Orbit files for bankruptcy:
Virgin Orbit, the low-Earth orbit small payload launch company that was spun out of Richard Branson's Virgin Galactic, has filed for bankruptcy protection with the U.S. Securities and Exchange Commission. The bankruptcy filing follows weeks of bad news for the company, including a pause on all operations, a brief hunt for more money to continue as a going concern, and massive layoffs to try to right-size to the company's actual available budget, which today's news essentially confirms was non-existent.
Prior to this fast and furious couple week meltdown, Virgin Orbit had already shown signs that it was essentially on life support: the company's marquee first flight from a brand new British spaceport in January ended in failure due to an anomaly, and there was very little indication on when another attempt might arrive.
Virgin Orbit spun out of Virgin Galactic way back in 2017, as the Branson-backed space company divided its efforts into two separate avenues of focus: Galactic would pursue human spaceflight, targeting suborbital trips for scientists and wealth thrill-seekers. That has borne some fruit, but also hasn't yet achieved the scale and cadence of operation that it aspired to have accomplished at this stage. Orbit, meanwhile, aimed at delivering small payloads to low-Earth orbit, using small rockets that launched from the wings of a large carrier ship, a modified 747-400 commercial passenger aircraft.
[...] Virgin Orbit will seek a sale of the entire company or its assets as possible recourses to resolve its bankruptcy status, the company said in the filing.
Previously:
Even
Before Monday's Launch Failure, Virgin Orbit's Finances Were
Dismal
Historic
UK Mission Reaches Space Falls Short of Orbit
Read more of this story at SoylentNews.
14:41
A 200,000-Light-Year-Long Chain of Young Blue Stars Located Over Halfway Across the Universe cryptogon.com
Via: Hubble Site: The universe is so capricious that even the slightest things that might go unnoticed could have profound implications. Thats what happened to Yale astronomer Pieter van Dokkum when he was looking through Hubble Space Telescope images and noticed a suspected blemish that looked like a scratch on photographic film. For Hubbles electronic []
14:30
New infosec products of the week: April 7, 2023 Help Net Security
Heres a look at the most interesting products from the past week, featuring releases from Guardz, Malwarebytes, Obsidian Security, and Stamus Networks. Malwarebytes unveils WorldBytes to help users reveal the hidden cyber threats around them Powered by Malwarebytes and AI technology, WorldBytes empowers users to use their mobile devices to scan the world around them and get real-time threat assessments of anything and everything including questionable Tinder dates, the unlabeled sauce at the back More
The post New infosec products of the week: April 7, 2023 appeared first on Help Net Security.
14:02
33% of Open Source Summit North America speakers identify as female or non-binary! Linux.com

Read the original blog at Read More
The post 33% of Open Source Summit North America speakers identify as female or non-binary! appeared first on Linux.com.
14:00
Cyberthreats take a toll on IT teams work on other projects Help Net Security
93% of organizations find the execution of some essential security operation tasks, such as threat hunting, challenging, according to Sophos. IT professionals face challenging security operation tasks These challenges also include understanding how an attack happened, with 75% of respondents stating they have challenges identifying the root cause of an incident. This can make proper remediation difficult, leaving organizations vulnerable to repetitive and/or multiple attacks, by the same or different adversaries, especially since 71% of More
The post Cyberthreats take a toll on IT teams work on other projects appeared first on Help Net Security.
13:30
Outcome-based cybersecurity paves way for organizational goals Help Net Security
Organizations follow a reactive approach to cybersecurity which is stifling their progress in demonstrating value and aligning with business outcomes, according to WithSecure. 83% of respondents surveyed in the study were interested in, planning to adopt, or expanding their adoption of outcome-based security solutions and services. Reactive cybersecurity approach prevails in most organizations However, the study also found that most organizations currently approach cybersecurity on a reactive basis. 60% of survey respondents said they react More
The post Outcome-based cybersecurity paves way for organizational goals appeared first on Help Net Security.
13:21
New Business Model at OSI: Running Blog Ads for Sponsors (Not Just Microsoft) Techrights
Just hours ago:
Summary: The OSI is obsolete; its just collecting advertising money and its staff is sponsored by Microsoft to lobby for Microsoft (and promote proprietary software of Microsoft)
13:00
Companies carry unquantified levels of risk due to current network security approaches Help Net Security
40% of senior cybersecurity decision makers effectively prioritize risks to Payment Card Industry Data Security Standard (PCI DSS) 4.0 compliance, according to Titania. The study highlights that oil and gas, telecommunications, and banking and financial services organizations are prime targets for threat actors that exploit vulnerable network device configurations to scale their attacks. It also reveals only 37% could very effectively categorize and prioritize compliance risks that undermine the security of their networks. Network misconfigurations More
The post Companies carry unquantified levels of risk due to current network security approaches appeared first on Help Net Security.
12:08
Accessing Computers With ChatGPT for Fun and Profit SoylentNews
A researcher used ChatGPT to create dangerous data-stealing malware
The malware even escaped detection on VirusTotal:
A cybersecurity researcher claims to have used ChatGPT to develop a zero-day exploit that can steal data from a compromised device. Alarmingly, the malware even evaded detection from all vendors on VirusTotal.
Forcepoint's Aaron Mulgrew said he decided early on in the malware creation process not to write any code himself and use only advanced techniques that are typically employed by sophisticated threat actors like rogue nation states.
Describing himself as a "novice" in malware development, Mulgrew said he used Go implementation language not only for its ease of development, but also because he could manually debug the code if needed. He also used steganography, which hides secret data within an regular file or message in order to avoid detection.
[...] Mulgrew said the entire process took "only a few hours." Without the chatbot, he believes it would have taken a team of 5-10 developers weeks to craft the malicious software and ensure it could evade detection by security apps.
While Mulgrew created the malware for research purposes, he said a theoretical zero-day attack using such a tool could target high-value individuals to exfiltrate critical documents on the C drive.
Read more of this story at SoylentNews.
12:00
ChatGPT Powers a Different Kind of Logic Analyzer Hackaday

If youre hoping that this AI-powered logic analyzer will help you quickly debug that wonky digital circuit on your bench with the magic of AI, were sorry to disappoint you. But if youre in luck if youre in the market for something to help you detect logical fallacies someone spouts in conversation. With the magic of AI, of course.
First, a quick review: logic fallacies are errors in reasoning that lead to the wrong conclusions from a set of observations. Enumerating the kinds of fallacies has become a bit of a cottage industry in this age of fake news and misinformation, to the extent that many of the common fallacies have catchy names like Texas Sharpshooter or No True Scotsman. Each fallacy has its own set of characteristics, and while it can be easy to pick some of them...
11:38
Links 06/04/2023: New Stable Kernels, Flatpak in OpenEmbedded, More Layoffs in GAFAM Techrights
![]()
Contents
-
GNU/Linux
-
Kernel Space
-
LWN Linux 6.1.23
-
LWN Linux 6.2.10
I'm announcing the release of the 6.2.10 kernel. All users of the 6.2 kernel series must upgrade. The updated 6.2.y git tree can be found at: git://git.kernel.org/pub/scm/linux/kernel/git/stable/linux-stable.git linux-6.2.y and can be browsed at the normal kernel.org git web browser: https://git.kernel.org/?p=linux/kernel/git/stable/linux-s... thanks, greg k-h
-
-
A...
-
11:00
ISACA updates CMMI model to increase its flexibility and adaptability Help Net Security
In a tightening economic market, addressing enterprise performance can help organizations better weather challenges by reducing costs, creating efficiencies, and coming in on schedule while improving overall quality. ISACAs Capability Maturity Model Integration, or CMMI, has been doing just that for enterprises for more than three decades, and is now out with a major model update with three new model domainsData Management, People Management, and Virtual Workthat allow organizations even more flexibility to customize their More
The post ISACA updates CMMI model to increase its flexibility and adaptability appeared first on Help Net Security.
10:14
UK Criminal Records Office Crippled by Potential Ransomware Attack HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
The Criminal Records Office (ACRO) of the United Kingdom has acknowledged the cyberattack but did not confirm whether it was a ransomware attack.
This is a post from HackRead.com Read the original post: UK Criminal Records Office Crippled by Potential Ransomware Attack
10:00
LastPass Security Dashboard now features dark web monitoring Help Net Security
LastPass has expanded availability of its Security Dashboard and associated dark web monitoring and alerting, making it the only password manager providing proactive credential monitoring for all customers, including those using the product for free. The Security Dashboard is the central hub where customers can monitor the overall security of all vault credentials, including exposure to the dark web, which allows customers to better protect themselves from potential breaches. The Security Dashboard is an essential More
The post LastPass Security Dashboard now features dark web monitoring appeared first on Help Net Security.
10:00
HPR3830: Into New Mexico Hacker Public Radio
We made a change in our itinerary and instead of going up into the mountains of New Mexico we went down to the area of the border of Mexico. Our first stop was in Deming, NM for a few days, the on to Anthony, NM for a longer stay of nearly three weeks. Anthony is located between Las Cruces, NM, and El Paso, Texas, so it was a convenient location for visiting both of the places, and we did so. In hindsight, we liked Las Cruces and the New Mexico part a lot better than El Paso. Links: https://flic.kr/s/aHBqjzKYwL https://flic.kr/s/aHBqjzL1pH https://flic.kr/s/aHBqjzKYwM https://flic.kr/s/aHBqjzKZcd https://flic.kr/s/aHBqjzKYVh https://flic.kr/s/aHBqjzL1F8 https://flic.kr/s/aHBqjzKZLE https://flic.kr/s/aHBqjzL6F3 https://www.palain.com/travel/into-new-mexico/
09:30
AuthenticID launches identity document liveness detector Help Net Security
AuthenticID has revealed the launch of its identity document liveness detector. This feature enhancement validates the actual, physical presence of identity documents when used as part of the identity verification process. AuthenticIDs identity document liveness detector utilizes advanced AI and computer vision to detect many forms of document spoofing, especially digitally-displayed document spoofs. These spoofs are also called screen replay attacks. In this method, bad actors will attempt to bypass verification methods by displaying digital More
The post AuthenticID launches identity document liveness detector appeared first on Help Net Security.
09:19
The Microcode and Hardware in the 8086 Processor That Perform String Operations SoylentNews
https://www.righto.com/2023/04/8086-microcode-string-operations.html
Intel introduced the 8086 microprocessor in 1978. This processor ended up being hugely influential, setting the path for the x86 architecture that is extensively used today. One interesting feature of the 8086 was instructions that can efficiently operate on blocks of memory up to 64K bytes long. These instructions rapidly copy, compare, or scan data and are known as "string" instructions.
In this blog post, I explain string operations in the 8086, analyze the microcode that it used, and discuss the hardware circuitry that helped it out.
[...] I'll explain the behavior of an ALU micro-operation since it is important for string operations. The Arithmetic/Logic Unit (ALU) is the heart of the processor, performing addition, subtraction, and logical operations. The ALU has three temporary input registers that are invisible to the programmer: tmpA, tmpB, and tmpC. An ALU operation takes its first argument from any temporary register, while the second argument always comes from tmpB. Performing an ALU operation requires two micro-instructions. The first micro-instruction specifies the ALU operation and source register, configuring the ALU. For instance, ADD tmpA configures the ALU to add the tmpA register to the default tmpB register. In the next micro-instruction (or a later one), the ALU result can be accessed through a special register called (SIGMA) and moved to another register.
Read more of this story at SoylentNews.
09:00
Fast Scanning Bed Leveling Hackaday

The bane of 3D printing is what people commonly call bed leveling. The name is a bit of a misnomer since you arent actually getting the bed level but making the bed and the print head parallel. Many modern printers probe the bed at different points using their own nozzle, a contact probe, or a non-contact probe and develop a model of where the bed is at various points. It then moves the head up and down to maintain a constant distance between the head and the bed, so you dont have to fix any irregularities. [YGK3D] shows off the Beacon surface scanner, which is technically a non-contact probe, to do this, but it is very different from the normal inductive or capacitive probes, as you can see in the video below. Unfortunately, we didnt get to see it print because [YGK3D] mounted it too low to get the nozzle down on the bed. However, it did scan the bed, and you can learn a lot about how the device works in the video. If you want to see one actually printing, watch the second, very purple video from [Dre Duvenage].
Generally, the issues with probes are making them repeatable, able to sense the bed, and the speed of probing all the points on the bed. If your bed is relatively flat, you might get away with probing only 3 points so you can understand how the bed is tilted. That wont help you if your bed has bumps and valleys or even just twists in it. So most people will probe a grid of points.
Like a pixel is to...
08:41
New Dark Web Market Styx: Focuses on Money Laundering, Identity Theft HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
Styx has quickly gained traction as a hub for various illicit activities, following the recent seizure of the Genesis dark web market.
This is a post from HackRead.com Read the original post: New Dark Web Market Styx: Focuses on Money Laundering, Identity Theft
08:40
06:39
Fast Food, Fast Charge IEEE Spectrum

It sounds so obvious: Public EV chargers should be located in public, where people tend to gather. The reality has often been otherwise, with too many chargers tucked into desolate parking lots or seemingly random locations. And since even the speediest DC chargers take roughly 30 minutes to juice up an EV, drivers and passengers have time to kill, including enough time for a bite.
To keep cars and passengers full, 7-Eleven and Subway are among the companies planning to serve up EV charging along with their Big Gulps and sandwiches.
7-Eleven envisions its 7Charge network as one of the biggest fast-charging networks among convenience stores in the United States. The company hasnt cited exact numbers of how many DC chargers it hopes to open, but 7-Eleven operates about 9,400 stores in the United States, and nearly 600 more in Canada. The company currently has more than 30 fast chargers in California, Colorado, Texas, and Florida.
The new chargers aim to welcome owners of any EV, by offering both the CCS (Combined Charging System) connector and the CHAdeMO plug. Tesla owners can already hook into CCS stations by means of an adapter. A 7Charge app will offer a station locator and an easy-payment method through a linked account.
7-Eleven isnt alone. Subway will partner with Miami-based GenZ EV Solutions to create Subway EV Charging Oasis parks with fast-charging stalls, picnic tables, Wi-Fi, playgrounds, and restrooms. California is determined to require all new vehicles sold to be either EVs or plug-in hybrids by 2035. And a Taco Bell franchisee with more than 300 locations has launched the first of 100 planned California charging stations in San Francisco.
Restaurant and convenience-store operators cite ongoing gaps in public charging, including in rural, urban, and other underserved areas.
Equitable access to charging is essential to the adoption of EVs, and Subways scale will play an important role in democratizing charging infrastructure for millions of Americans, said Jose Valls, CEO of GenZ EV Solutions.
 Subway will
be partnering with GenZ...
Subway will
be partnering with GenZ...
06:32
Repeating Radio Signal Leads Astronomers to an Earth-size Exoplanet SoylentNews
Astronomers have detected a repeating radio signal from an exoplanet and the star that it orbits, both located 12 light-years away from Earth. The signal suggests that the Earth-size planet may have a magnetic field and perhaps even an atmosphere.
Scientists noticed strong radio waves coming from the star YZ Ceti and the rocky exoplanet that orbits it, called YZ Ceti b, during observations using the Karl G. Jansky Very Large Array of telescopes in New Mexico. The researchers believe the radio signal was created by interactions between the planet's magnetic field and the star.
[...] "We saw the initial burst and it looked beautiful," said lead study author Sebastian Pineda, a research astrophysicist at the University of Colorado Boulder, in a statement. "When we saw it again, it was very indicative that, OK, maybe we really have something here."
[...] YZ Ceti b only takes two Earth days to complete a single orbit around its star. Meanwhile, the shortest orbit in our solar system is the planet Mercury, which takes 88 Earth days to complete a lap around the sun.
While YZ Ceti b whips around its star, plasma from the star collides with the planet's magnetic field, bounces off and interacts with the star's magnetic field. All of these energetic reactions create and release strong radio waves that can be detected on Earth.
Pineda, J.S., Villadsen, J. Coherent radio bursts from known M-dwarf planet-host YZ Ceti. Nat Astron (2023). https://doi.org/10.1038/s41550-023-01914-0
Read more of this story at SoylentNews.
06:19
ISPs Fail to Dismiss Filmmakers Piracy Liability Lawsuits TorrentFreak
 Over the past two decades, online piracy has proven a massive
challenge for the entertainment industries.
Over the past two decades, online piracy has proven a massive
challenge for the entertainment industries.
Copyright holders have tried to go after individual pirates and pirate sites in court, but third-party intermediaries are now increasingly seen as targets as well.
Several active lawsuits in the United States feature rightsholders accusing Internet providers of not doing enough to stop piracy. One of the main allegations is that ISPs fail to terminate the accounts of repeat infringers in appropriate circumstances as the DMCA requires.
These lawsuits have resulted in multi-million dollar judgments against Cox and Grande. Meanwhile, more companies at risk too, such as WideOpenWest (WOW!), which was sued by a group of smaller movie companies, including Millennium Media and Voltage Pictures.
The filmmakers accused the Colorado-based ISP of failing to terminate the accounts of subscribers who were repeatedly flagged for sharing copyrighted material. They argue that WOW! is liable for these piracy activities and are demanding millions of dollars in damages.
WOW! Wants Troll Case Dismissed
The ISP challenged the claims and filed a motion to dismiss the case. WOW! addressed the substance of the allegations and described the film companies and their anti-piracy partner Maverickeye as copyright trolls.
Plaintiffs and Maverickeye are part of a well-known web of copyright trolls. Until now, Plaintiffs modus operandi has been to file John Doe lawsuits in the hope of securing quick settlements and to dismiss them at the slightest resistance, they wrote.
Indeed, several of the plaintiff film companies have filed cases against individual file-sharers, but they have also sued hosting providers, site operators, and app developers.
Responding to the substance of the allegations, WOW! argued that an IP address is not sufficient to prove that subscribers downloaded or shared any infringing material. And if thats not clear, the ISP cant be held liable either.
Something More?
To back this up, WOW! cites the Cobbler Nevada v. Gonzales case, where the court held that an...
06:00
Intel Linux Optimizations Help AMD EPYC "Genoa" Improve Scaling To 384 Threads Phoronix
Last month I wrote about Intel's Linux kernel engineering improvements to help enhance CPU scaling across various workloads by addressing low-level bottlenecks within the kernel. It's an area we'll likely see Intel continue to invest in as Sierra Forest comes next year with 144 E cores per socket. Already with the Linux kernel patches Intel is carrying at the moment via their in-house distribution, there are some significant benefits for Xeon Scalable Sapphire Rapids. I was curious to see how this Intel-focused work impacted AMD EPYC servers and thus in today's article is a similar analysis using two AMD EPYC 9654 "Genoa" flagship processors while evaluating Intel's Linux kernel optimizations.
Do I Belong? Investigating Belonging in Open Source through the Sense of Virtual Community Linux.com

Read the original blog at Read More
The post Do I Belong? Investigating Belonging in Open Source through the Sense of Virtual Community appeared first on Linux.com.
05:45
Free Software Foundation Certifies A $99 Mini VPN Router Phoronix
Over the years the Free Software Foundation has certified various devices that to their standards "Respect Your Freedom" from USB to parallel printer cables to re-branded and re-flashed motherboards to the Talos II at the higher-end. They've also certified different network hardware and other devices. The newest that they announced today is backing a $99 mini VPN router that supports WireGuard and other solutions...
05:22
Re: [ADVISORY] CVE-2023-1668: Open vSwitch: Remote traffic denial of service via crafted packets with IP proto 0 Open Source Security
Posted by Ilya Maximets on Apr 06
Correction:Priorities for these flows should be set to 65535 instead.
i.e. The maximum priority that can be set with OpenFlow.
05:20
[ADVISORY] CVE-2023-1668: Open vSwitch: Remote traffic denial of service via crafted packets with IP proto 0 Open Source Security
Posted by Ilya Maximets on Apr 06
Description===========
Multiple versions of Open vSwitch are vulnerable to crafted IP packets
with ip proto set to 0 causing a potential denial of service.
Triggering the vulnerability will require an attacker to send a crafted
IP packet with protocol field set to 0 and the flow rules to contain
'set' actions on other fields in the IP protocol header. The resulting
flows will omit required actions, and fail to mask the IP protocol...
04:47
Once More, With Feeling: Exploring Relatable Robotics at Disney IEEE Spectrum

This is a guest post. The views expressed here are solely those of the author and do not represent positions of IEEE Spectrum or the IEEE.
Most robotics projects focus on the output: What does this robot do? Is it reliable, is it precise, and can it achieve its goals? But at Disney, our focus is on the story: How does this robot make you feel? Is it emotive, is it relatable, and does it authentically reflect a character people know in its mannerisms, gait, or expressions?
This context changes everything. Take walking, for examplein robotics, its generally a priority to maximize the stability of a walking gait, since falling down doesnt help you move crates or explore terrain. At Disney, however, a stable walking gait is less important than a gait that brings a character to life. Falling down can be wildly entertaining, as long as the falling happens in character!
About a year ago, our team came to a realization: We needed robots that didnt mind taking the occasional tumble. If were going to be free to explore fun and evocative performances with our robots, failure had to be an option. And not only thatfailure had to be expected, and built into the design. We called our new project Indestructibles and set out toward the goal implied by that name.
 Disney
Disney
On 10 March 2023, we were able to show off our latest Indestructibles prototype at SXSW in Austin, Texas. We were nervous. We knew this little character had charmed us, but we couldnt be sure her personality would come through on such a big stage with a brand-new audience. But from the moment she peeked her head out of her crate, the energy in the crowd let us know they were not only seeing her but cheering for her. We were thrilled!
...
04:33
Phishers migrate to Telegram Security Affairs
Experts warn that Telegram is becoming a privileged platform for phishers that use it to automate their activities and for providing various services.
Kaspersky researchers have published an analysis of phishers Telegram channels used to promote their services and products.
The experts pointed out that crooks engaged in phishing activities have started to rely on the popular instant messaging platform more in recent months.
On Telegram is possible to find channels that offer:
Free phishing kits that can be used to target users of a large number of global and local brands. Phishers also use to share stolen personal data with their subscribers. The free phishing material is offered as bait of sorts for less experienced phishers to bite and to recruiting an unpaid workforce.
- One reason is that any free content or manuals so willingly distributed by scammers to their Telegram audience serve as bait of sorts for less experienced phishers to bite. Newbies get a taste of what phishing tools can do, pull off their first scam and wish for more, which is when they will be offered paid content. The creators of phishing bots and kits can get access to data that is gathered with their tools.
To attract larger audiences, scam operators advertise their services, promising to teach others how to phish for serious cash. reads the post published by Kaspersky.
Contents of a free phishing kit archive
- Paid phishing pages and data, as well as phishing-as-a-service (PhaaS) subscriptions. Crooks use Telegram channel to offer paid phishing content and data. They also provide phishing-as-a-service (PhaaS) subscriptions that give their customers access to phishing tools, as well as guides for beginners and technical su...
04:00
Survey Shows Overwhelming Interest in a Four-Day Workweek IEEE Spectrum

The Institute conducted an online poll in December, asking readers for their thoughts on a four-day workweek. About 95 percent of the respondents said they want to work a shorter weekwhich to me means employees think they can complete their tasks in four days rather than five. However, 89 percent of the respondents companies dont offer that type of work schedule.
The poll results inspired me to explore the matter further. I interviewed several engineers and tech company executives about four-day workweeks.
Providing more flexibility
 Before he
retired, IEEE Senior Member John McWilliams was a senior innovation
engineer at the Dairyland Power Cooperative, in La Crosse,
Wis.John
McWilliams
Before he
retired, IEEE Senior Member John McWilliams was a senior innovation
engineer at the Dairyland Power Cooperative, in La Crosse,
Wis.John
McWilliams
IEEE Senior Member John McWilliams reflected on his time as a field service engineer from 1978 to 1988 with Westinghouse and how difficult it was to be available and prepared to go anywhere at any time. He retired in October from his job as senior innovation engineer at the Dairyland Power Cooperative, in La Crosse, Wis.
That was tough, McWilliams recalls. I did not get the time to physically and mentally recover from previous assignments. There was no time to go on a vacation, attend a concert or to just relax at home.
Working that type of schedule at an early age negatively impacted his marriage and health, he says.
Westinghouse then assigned him to work on construction projects in Saudi Arabia in 50 C weather, without time to rest after the job was completed.
Making young professionals work a long work sche...
03:43
Maker of Eye Drops Linked to Deadly Outbreak Flunks FDA Inspection SoylentNews
The maker of eye drops linked to a deadly outbreak of extensively drug-resistant infections in the US had a slew of manufacturing violationsfrom brown slime on filling equipment to a lack of basic measures and systems to ensure sterilityaccording to an inspection report released by the Food and Drug Administration (PDF).
In February, the regulator warned consumers to immediately stop using eye drops and eye ointment made by Global Pharma, whose products were sold in the US under brand names EzriCare and Delsam Pharma and were available through Amazon, Walmart, eBay, and other retailers. Global Pharma later issued voluntary recalls of the products.
Health investigators had linked the drops to cases of an extensively drug-resistant Pseudomonas aeruginosa strain that had never been seen before in the US. The strain is identified as VIM-GES-CRPA, which stands for a carbapenem-resistant P. aeruginosa (CRPA) with Verona integron-mediated metallo--lactamase (VIM) and Guiana extended-spectrum--lactamase (GES). Although affected people reported using multiple brands of eye drops, EzriCare was the most common. Additionally, testing by the Centers for Disease Control and Prevention and independent researchers have identified the outbreak strain in opened bottles of EzriCare artificial tears.
As of March 14, 68 people in 16 states have been infected with the strain, the Centers for Disease Control and Prevention reports. Three people have died from the infection, eight have lost vision, and four have had their eyeballs surgically removed.
Read more of this story at SoylentNews.
03:20
Report Shows Astonishing Depravity in Sexual Abuse of More than 600 in Baltimores Catholic Archdiocese cryptogon.com
Via: Baltimore Sun: A four-year investigation of Baltimores Catholic archdiocese reveals the scope of 80 years of child sex abuse and torture and how church officials often covered it up and, in some cases, paved the way for further abuse. Among the accounts: A deacon who admitted abusing more than 100 children. A priest who []
03:09
Ukrainian hackers spend $25,000 of pro-Russian bloggers money on sex toys Graham Cluley
A pro-Russian blogger who raised $25,000 for drones to assist Russian troops fighting in Ukraine, has received a huge delivery of sex toys instead. Read more in my article on the Hot for Security blog.
02:52
Summary: Twitter addiction (or FOMO, or sometimes peoples wrong belief/intuition that their social life/popularity is the sum total of their Twitter followers) has thus far prevented more people from leaving; what else do they need to see before realising that its time to leave?
MAKE no mistake about it. The shitshow or the dumpster fire that Twitter has become since the takeover is miles worse than the Twitter I left completely over a year ago (I had left years earlier to a lesser degree). I didnt envision it would (just months later) be taken over by a pot-smoking fraud who replaces the logo with a meme, manipulates the algorithms to boost the ego of people who pay him, and so on and so on
Social control media is worse than a waste of time.The number of scandalous moves is too great to recall or itemise offhand. Weve added links to document most of these (Daily Links) and if anyone still believes things will improve in that platform, then one must be smoking the same stuff this guy does.
Leave Twitter. The sooner, the better. Social control media is worse than a waste of time.
Video download link |
md5sum 526954e8bf862702e446d6cce5e152b0
Why I Hate Elon Musk | Credit to original author here
02:49
Media Briefing: Proposed UN Cybercrime Treaty Negotiations Headed in Troubling Direction, Sidestepping Human Rights Protections and Threatening Free Expression, EFF and Allies Warn Deeplinks
San FranciscoOn Thursday, April 13, at 10:00 am Pacific
Time (1:00 pm Eastern Time, 7 pm CEST), experts with Electronic
Frontier Foundation (EFF) and four international allies will brief
reporters on the grave threat to human rights posed by ongoing UN
Cybercrime Treaty negotiations that could lead to broad
surveillance powers, criminalizing online speech, and enabling
hacking by police agencies.
The one-hour briefing will be livestreamed from the
fifth session of treaty negotiations in Vienna,
where representatives from over 100 Member States will meet
to discuss a
negotiating document reflecting their
suggestions for the treaty. The document lacks strong commitments
to human rights and detailed conditions and safeguards that are
needed to protect the rights of Individuals and organizations
around the world.
Without that, theres ample wiggle room for prosecutors to, for
example, access personal data with no independent or judicial
oversight, and use electronic surveillance to interfere with the
rights to privacy and freedom of expression in ways that violate
international human rights law.
The drafts scope needs to be narrowed and
include specific human rights protections.
As it stands, it
creates over thirty new cybercrime offenses,
including half a dozen that would make it a crime to send or post
legitimate content protected by international law. This goes far
beyond what States are allowed to restrict under international
human rights standards. Most concerning are overly broad provisions
seeking to
criminalize speech on the basis of fake
news, extremism, incitement and terrorism. International human
rights law already provides clear guidance on how to address many
of these issues.
Many Sta...
02:49
A fireside chat with four CISOs about how they secure their cybersecurity firms from attack Graham Cluley
On Tuesday 11 April, I'll be joined by the CISOs of security firms Wiz, Rubrik, Noname, and Abnormal, for a friendly chat about how they protect their organisations from the huge number of threats targeting them. I hope to see some of you there!
02:27
The Linux Foundation Events Monthly Snapshot April 2023 Linux.com
read the original post at Read More
The post The Linux Foundation Events Monthly Snapshot April 2023 appeared first on Linux.com.
02:12
Links 06/04/2023: PipeWire 0.3.68, Ofcom/Competition and Markets Authority May Study Microsofts Antitrust Abuses Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Digital Restrictions (DRM)
- Monopolies
- Gemini* and Gopher
-
GNU/Linux
-
Desktop/Laptop
-
CNX Software PineTab-V...
-
-
02:00
Linux 6.4 Bringing Apple M2 Additions For 2022 MacBook Air, MacBook Pro, Mac Mini Phoronix
Further adding to the excitement of the upcoming Linux 6.4 merge window is the mainline kernel seeing the Device Tree (DT) additions for Apple's current M2 devices including the MacBook Air, MacBook Pro, and Mac Mini systems. The upstream kernel still has more work to go around the M1/M2 support compared to the downstream state with Asahi Linux, but at least now with this DT support will provide some basic level of upstream kernel support for the Apple M2...
01:57
888casino Evaluations Read Customer Support Evaluations Of 888casino It h+ Media
888casino Evaluations Read Customer Support Evaluations Of 888casino It
All you must do is observe through their simple and fast registration course of and get ready to spin. All the video games that can be seen in a world-class brick and mortar casino can be discovered within the stay dealer part of 888 on line casino. Roulette, Blackjack, Bacarrat, Casino Holdem, Three card poker, Caribbean stud poker and Ultimate Texas Holdem are among the many most performed commonplace on line casino video games.
888casino wants gamers to kickstart their gambling voyage with a win. Other exciting bonuses are the FAB free spins, Fantastic FreePlay, and so on. The 88 Free spins are valid for scratch games, and there are limitations on what you can win, just like the NetEnt free spins. All new and present players can get pleasure from instant-play video games from an HTML5 net browser, including Google Chrome on Windows or Apple Safari on Mac OS. 888 Casino makes use of a proprietary software platform with a number of in-house video games. The casino cooperates with top-tier game providers like Playtech, NetEnt, 888 Gaming, IGT , WMS, and so on.
888 Casino is a authorized service for Kiwi players as a result of 888 is a casino thats registered exterior of New Zealand. Under NZ law, businesses are unable to provide online playing content material. Therefore, gamers are legally allowed to entry what are foreign web sites.
- Unfortunately, there are not any Live Chat choices or a toll-free quantity to call, and it may upset gamblers, as generally they may be impatient and expect immediate responses.
- The fantastic thing about the positioning is you could play at any time 24/7 either on-line in flash variations, or if you favor, on the downloadable model.
- But no matter the type of blackjack a participant needs to play, there are solely a handful of online casinos which provide the most effective variations.
- The Double Your Money first deposit offer permits new gamers to take advantage and get a one hundred pc bonus on their first deposit, as much as 100.
- As an 888 VIP Casino Club member, you get exclusive access to all of our 888 manufacturers, which incorporates 888casino.
For New Zealand gamers, withdrawing the money to Credit Cards may be tough at occasions, which is why I recommend utilizing the payment processors like PayPal or Skrill for probably the most half. The deposits from these methods are immediate and withdrawals are normally accomplished inside hours, with 2-3 days being the maximum amount of time youll ever wait on your cash to succeed in your account. With the assistance for theimprovement and developmentof the 888 cell on line casino app, players from New Zealand can now play the web cellular casino video games on their Apple gadgets and Android devices. This app is appropriate with almost each smartphones and cellular devices....
01:56
888 Casino Nz Review 2021 $1500 Premium Welcome Bonus h+ Media
888 Casino Nz Review 2021 $1500 Premium Welcome Bonus
After that we provide particular 888 Casino presents in case you are interested in buying something for a discount. Receive 500% bonus in your first deposit with us, 600% on the second deposit and 400% bonus on the third. We grant a bonus to all deposits, beginning with 200% on your first deposit of the day. Make the acquisition benefiting from the discounts now out there on Pokerstars.
The operator has the same data safety protocols for both platforms . In our full review of 888casino you presumably can seek the assistance of relevant details about the corporate, together with the security systems it applies. Once players have registered a brand new account, they must make a NZ$10 minimal deposit to trigger the Welcome Bonus. To declare the Welcome Bonus, Kiwis want to make certain that their cellphone number is verified beforehand.
888 has acquired William Hill and now they have joined forces and have shaped a piece staff and an experience within the reach of only a few. 888 Casino is among the most acknowledged and largest gambling platforms in our country. It has a self-exclusion program to help customers create responsible playing behaviors.
Various ways to payWith UPaycard, youve a quantity of methods to make on-line on line casino transactions, such as through the e-wallet choice, a prepaid card, and via crypto. But earlier than utilizing it, AU and NZ gamers ought to check UPaycard supported nations, including casinos that supply it as a fee method. Probably Evolution Gaming contributes many extra of their desk video games to their stay casino. A welcome offer is available for new gamers who register with New Zealand e-ID on their first deposit. The on line casino is licensed by The New Zealand Gambling Authority, offers quick on line casino withdrawals and has several payment methods to choose from. Their bonus construction permits gamers to choose how big the bonus might be relying on the amount they select to deposit which is at all times voluntary for gamers to choose.
Frank on line casino never shares any details about you as a player and the on line casino additionally has a New Zealand gaming license from in New Zealand. The license permits Frank on line casino to legally promote legal playing to you as a player in New Zealand. With give consideration to its members nothing is left to chance for anyone visiting Frank on line casino New Zealand web page. Here players will find a properly thought out and simply navigated on-line casino in cell, computer and tablet. First of all, in fact, we look at our own experiences with the on line casino.
And that is why, at OnlineCasinosNew Zealand, we only review New Zealander online casinos licensed by the SRIJ . GO competitive organizations arent that different from traditional sports activities golf equipment on this regard, they do inform you about the ongoing sporting occasion...
01:55
Commerce On Line Casino In Commerce h+ Media
Commerce On Line Casino In Commerce
In addition, the supply is huge and its typically troublesome to see the forest via the timber and find one of the best casino. If you had to go through the whole supply your self, you would be busy for a really long time and no longer have time to gamble. Cash games start from micro stakes of $0.01/$0.02 and may reach $25/$50 for no limit Texas Holdem. This is the variation that gets the most traffic right now since the poker sport is well-liked around the globe and attracts within the huge crowds.
Low deposit Casino, often generally in regards to the on-line playing websites that have casino$50 deposit or lower as a restrict. It can additionally be the minimum quantity to activate a the bonus provided in the intervening time. You can use any fee method at Frank to pick it up, which can be good for you to control. Good to notice is that there is no need to obtain any Frank casino app to succeed in their mobile casino . You play as usual by logging into your account after youve registered. When you exit from your mobile account, you possibly can, similar to in the computerized version, pick up video games the place you left off, make withdrawals, see present promotions, contact help and far more.
Games like Multi-hand Blackjack, European Roulette, and Jacks or Better all continue to show well-liked here. Pokies Here you probably can look forward to finding a extremely impressive degree of variety, with one of the best online pokies from NetEnt, Playn GO, and Red Tiger. A mixture of themes and sport options will hold you entertained for months to return playing the likes of Book of Dead, Street Fighter 2, and Wolf Ridge. Below will cowl a few regularly requested questions made about casino players after they first register a brand new account at 888 Casino. If you have any further questions please contact the assist part as described within the last paragraph.
The Frank Casino bonus is certainly one of the biggest bonuses at the on line casino proper now, and while it isnt with no turnover,$avet feels affordable for the scale. Not all providers are the same and not every on-line on line casino suits each player. 888 Casino brings its award profitable software program into the cellular area to offer access to a wonderful line-up of video games.
You can even sharpen your abilities in roulette and blackjack in your smartphone and the controls are very simple whereas presenting HD graphics for an immersive experience. 888 Mobile Casino is a should for model spanking new and current customers of the popular operator. If you want reside vendor video games, the on line casino launched a full library of video games which are broadcast from studios. These allow you to play baccarat, blackjack, Caribbean Stud, Three Card Poker, roulette, and Dream Catcher in high definition and is fairly nicely constructed.
Play the video games you love, earn fa...
01:54
[$] Seeking an acceptable unaccepted memory policy LWN.net
Operating systems have traditionally used all of the memory that the hardware provides to them. The advent of virtualization and confidential computing is changing this picture somewhat, though; the system can now be more picky about which memory it will use. Patches to add support for explicit memory acceptance when running under AMD's Secure Encrypted Virtualization and Secure Nested Paging (SEV-SNP), though, have run into some turbulence over how to handle a backward-compatibility issue.
01:52
Own a Nexx smart alarm or garage door opener? Get rid of it, or regret it Graham Cluley
Hacker can remotely open or close garage doors, seize control of alarms, and switch on (or switch off) customers' "smart" plugs due to vulnerabilities in Nexx products.
01:02
Kioxia Demos 7-Bits-Per-Cell Flash Memory SoylentNews
Kioxia, formerly Toshiba Memory Holdings, has demonstrated "hepta-level-cell" NAND memory:
Kioxia Researchers Demo Hepta-Level Cell NAND Flash, Nearly Doubling the Capacity of QLC
NAND researchers at Kioxia have successfully demonstrated a working concept of a new storage architecture called Hepta-level cell NAND flash. This new type of NAND can house up to 7 bits per cell, giving it nearly twice the storage capacity of QLC NAND flash. If Kioxia can stabilize this storage architecture at room temperature, it might become the ultimate successor to spinning hard drives in consumer and enterprise applications.
To create hepta-level NAND flash, Kioxia is using a new design called new silicon process technology to increase cell density, in conjunction with cryogenic cooling. New silicon process technology replaces current poly-silicon materials with a single-crystal silicon that is used in a channel inside a memory cell transistor. This apparently reduces the amount of read noise coming from the NAND flash by up to two-thirds. In other words, new silicon process technology produces clearer read signals for reading data off of the NAND flash, enough so to increase the bits cell capacity to 7.
7 / 4 = 1.75. Nearly double!
Kioxia has already demonstrated 6-bits-per-cell NAND. Multiple companies are mulling a transition to 5-bits-per-cell (PLC) NAND. Western Digital's technology and strategy chief Siva Sivaram doesn't expect PLC NAND to take off until 2025 or later.
Read more of this story at SoylentNews.
00:41
Adobe Reset User Passwords as Precaution Against Data Breach Risks HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
If you have received a password reset or "update your password" email from Adobe recently, you are not alone.
This is a post from HackRead.com Read the original post: Adobe Reset User Passwords as Precaution Against Data Breach Risks
00:30
Dozens Of Rust Updates Merged Ahead Of GCC 13.1 Phoronix
While the release of GCC 13.1 as the first stable GCC 13 compiler is due out in the next few weeks, ahead of that milestone dozens of Rust "gccrs" patches were merged today for furthering along that new language support...
00:01
Security updates for Thursday LWN.net
Security updates have been issued by Debian (cairosvg, ghostscript, grunt, tomcat9, and trafficserver), Fedora (golang, podman, xen, and zchunk), Red Hat (kpatch-patch), SUSE (systemd), and Ubuntu (apache-log4j1.2, liblouis, linux-aws, and linux-bluefield).
00:00
Qualcomm QAIC Accelerator Driver Coming With Linux 6.4 Phoronix
Following the Intel Meteor Lake VPU driver being added to the new accelerator "accel" subsystem in Linux 6.3 along with converting over the Habana Labs AI driver, coming in Linux 6.4 is now the Qualcomm QAIC Cloud AI driver to this subsystem that lives within the Direct Rendering Manager (DRM) umbrella...
00:00
If They Fire The Nukes, Will They Even Work? Hackaday

2022 was a harrowing year in a long line of harrowing years. A brutal war in Europe raised the prospect of nuclear war as the leaders behind the invasion rattled sabers and made thinly veiled threats to use weapons of mass destruction. And all this as were still working our way through the fallout of a global pandemic.
Those hot-headed threats raise an interesting question, however. Decades have passed since either Russia or the United States ran a live nuclear weapons test. Given that, would the nukes even work if they were fired in anger?
Check and Test
Thursday, 06 April
23:57
Money Message ransomware group claims to have hacked IT giant MSI Security Affairs
Ransomware gang Money Message claims to have hacked the Taiwanese multinational IT corporation MSI (Micro-Star International).
Ransomware gang Money Message announced to have hacked the Taiwanese multinational IT corporation MSI (Micro-Star International). Micro-Star International AKA MSI designs, manufactures, and sells motherboards and graphics cards for customers in the United States, Canada, and internationally. MSI is headquartered in Taipei, Taiwan.
The ransomware group added the company to the list of victims on its Tor leak site, it claims to have stolen the source code from the company, including a framework to develop bios, and private keys.
The group published a series of screenshots of the companys CTMS and ERP databases
The Money Message group threatens to publish the stolen files by Wednesday, April 12, 2023, if the company will not pay the ransom.
BleepingComputer reported that the ransomware gang has demanded a ransom payment of $4,000,000.
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections:
- The Teacher Most Educational Blog
- The Entertainer Most Entertaining Blog
- The Tech Whizz Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please nominate Security Affairs as your favorite blog.
Nominate...
23:01
Find mistakes in your playbooks with Ansible Lint Linux.com
Ansible Lint, a Python command-line tool, catches errors in Ansible playbooks and content.
Read More at Enable Sysadmin
The post Find mistakes in your playbooks with Ansible Lint appeared first on Linux.com.
23:00
PipeWire 0.3.68 Released With New RTP Session Module, Many Other Changes Phoronix
PipeWire 0.3.68 is out today as a significant update for this alternative to JACK and PulseAudio as well as managing both audio and video streams on the Linux desktop...
22:16
Intel Carries Out More Meteor Lake Graphics Enablement For Linux 6.4 Phoronix
Intel today submitted their final batch of "drm-intel-gt-next" feature changes that they have planned for the upcoming Linux 6.4 kernel cycle...
22:16
Modern Origami Method Creates Glass Shapes by Folding SoylentNews
Intricate glass designs can be made with origami and cutting techniques, which can be combined with 3D printing to make more complex shapes:
The ancient art of origami is well known for transforming sheets of paper and other foldable materials into complex 3D shapes. But now, chemical engineers have extended the centuries-old practice to produce intricate shapes made of glass or other hard materials. Their thoroughly modern method, which can be combined with 3D printing, could have applications ranging from sculpture to catalysis and beyond.
[...] Typically, glass and ceramics are shaped in a mold or are 3D printed in the desired final structure. But a mold can't produce a complicated shape, Xie says. And although 3D printing can do so, it's slow, and an object can be flimsy and need extra support while it's being made. In addition, the printed item usually has a layered texture that might not be the ideal appearance. The team set out to see if they could overcome these shortcomings.
Yang Xu, a graduate student who works in Xie's lab at Zhejiang University, devised a technique in which she mixed nanoparticles of silica the main ingredient for making glass into a liquid containing several compounds. Curing the mixture with ultraviolet light produced a cross-linked polycaprolactone polymer with tiny beads of silica suspended in it, like raisins in raisin bread.
[...] Next, Xu cut, folded, twisted and pulled on sheets of this translucent polymer composite, which has mechanical properties similar to paper, to make a crane, a feather, a lacy vase and a sphere made of intertwined ribbons, among other objects. If she did this at room temperature, the composite retained its new shape fairly well throughout the remaining production steps. Xu discovered that's because the folding and stretching process irreversibly disrupts the interface between some of the silica particles and the polymer matrix. But if it's critical to fully retain the new shape during the subsequent steps, Xu found that the composite must be heated at about 265 F when it is folded and stretched. That permanently rearranges the links between the polymer chains, firmly fixing the new shape in place.
Read more of this story at SoylentNews.
21:46
Supply Chain Attacks and Critical Infrastructure: How CISA Helps Secure a Nation's Crown Jewels The Hacker News
Critical infrastructure attacks are a preferred target for cyber criminals. Here's why and what's being done to protect them. What is Critical Infrastructure and Why is It Attacked? Critical infrastructure is the physical and digital assets, systems and networks that are vital to national security, the economy, public health, or safety. It can be government- or privately-owned. According to Etay
21:42
Self-Assembly: Reshaping Mission Design Centauri Dreams Imagining and Planning Interstellar Exploration
Its interesting to contemplate the kind of missions we could fly if we develop lightweight smallsats coupled with solar sails, deploying them in Sundiver maneuvers to boost their acceleration. Getting past Voyager 1s 17.1 kilometers per second would itself be a headline accomplishment, demonstrating the feasibility of this kind of maneuver for boosting delta-v as the spacecraft closes to perhaps 0.2 AU of the Sun before adjusting sail attitude to get maximum acceleration from solar photons.
The economic case for smallsats and sails is apparent. Consider The Planetary Societys LightSail-2, a solar sail in low Earth orbit, which demonstrated its ability to operate and change its orbit in space for multiple years before reentering Earths atmosphere in November of 2022. Launched in 2018, LightSail-2 cost $7 million. NASAs Solar Cruiser, a much larger design still in development despite budging hiccups, weighs in at $65 million. Slava Turyshev and team at the Jet Propulsion Laboratory independently verified a cost model, with the help of Aerospace Corporation, of $11 million for a one-year interplanetary flight based on their Technology Demonstrator design.
Those numbers go up with the complexity of the mission, but can be reduced if we take advantage of the fact that spacecraft like these can be repurposed. A string of smallsat sailcraft sent, for example, to Uranus to conduct flybys of the planet, its moons and rings, would benefit from economies of scale, with successive missions to other outer system targets costing less than the ones that preceded them. Here the contrast between dedicated flagship missions (think Cassini or the Decadal Sueveys projected Uranus Orbiter) could not be greater. Instead of a separately developed spacecraft for each destination, the modular smallsat/sail model creates a base platform allowing fast, low-cost missions throughout the Solar System.
To the objection that we need orbiters at places like Uranus to get the best science, the answer can only be that we need both kinds of mission if we are not to bog down in high-stakes financial commitments that preclude targets for decades at a time. Of course we need orbiters. But in between, the list of targets for fast flybys is long, and lets not forget the extraordinary range of data returned by New Horizons at Pluto/Charon and beyond. As the authors of the recent paper from the JPL team note, heliophysics can benefit from missions sent to various directions in the heliosphere:
The shape of the heliosphere and the extent of its tail are subject to debate and the new model of the heliosphereroughly spherical with a radius of 100 AUneeds confirmation. Of course, every mission out to >100 AU will test...
21:22
The Cancer Killing RatioHow 100:1 of Vitamin C and K3 (Apatone) Is Changing The Way We Fight Cancer! Lifeboat News: The Blog
Cancer is defined by cell cycle deregulation and uncontrolled growth. It is the second leading cause of death in the world. In the United States alone there were 1,658,370 new cancer cases diagnosed, 589,430 cancer deaths and an estimated 750,000 deaths in Europe.
We are fighting a losing battle?
IV Vitamin C for Cancer and Vitamin K3.
21:04
[Meme] UPC/ICC: London is in Manhattan, Lets Get the Unitary Patent System Rollin! Techrights
To some people, a court is just a political office and
they conveniently disregard rulings from judges (since
the beginning, in the EPOs case, as if obeying courts is
optional)
Summary: The EPOs very own kangaroo court is said to be scheduled for June, but any sane person knows that its both illegal and unconstitutional, certainly in violation of several conventions (not that Benot Battistelli and Antnio Campinos ever let German law, the European Patent Convention etc. get in their way); the European Union (EU) will be a causality of such forceful introduction of an illegal court system (emboldening EU critics/sceptics) , which puts Battistelli and Campinos in the same class as Donald Trump and Vladimir Putin (Battistelli and Campinos also funded Belarus a fact they want to distract from)
21:00
Finding Paths with Water is A-Mazing Hackaday

We arent sure if it qualifies as fluidic logic, but [Steve Mould] was inspired by a simulation of water flowing through a maze and decided to build some actual mazes and watch water flowing through them. It turns out there are several physical effects in play, and you can see [Steve] discuss them in the video below.
The maze, of course, has to be oriented so that water flows into the top and flows out of the bottom. Without much thought, youd think that the water just goes to the bottom and then fills up. Eventually, the part that is open at the bottom will have water coming out, right? Turns out it isnt that simple.
A combination of air pressure and surface tension conspire to make the water do better than expected. Not that it perfectly solves it, but it doesnt just fill up the entire maze, either. Even more interesting is that once the water has found the bottom, changing the water color will clearly show the path through the maze since nearly all of the new colored water will follow the flow path.
Practical? We cant think of why. But it is a great think piece on how water flows and what sort of forces can affect it.
[Steve] is no stranger to making water work out algorithms, something called fluidic logic.
...
20:59
Google Play apps will allow users to initiate in-app account deletion Help Net Security
Google Play will be pushing Android app developers to allow users to delete their account and associated data from within the app. Users will also be given the option to only delete data where applicable, as some data needs to be retained for security, fraud prevention, or regulatory reasons. Googles new app account and data deletion requirements Google Play has introduced new app account deletion requirements and added Data deletion questions to developers Data safety More
The post Google Play apps will allow users to initiate in-app account deletion appeared first on Help Net Security.
20:47
OCR Labs exposes its systems, jeopardizing major banking clients Security Affairs
A digital identification tool provided by OCR Labs to major banks and government agencies leaked sensitive credentials, putting clients at severe risk.
- London-based OCR Labs is a major provider of digital ID verification tools. Its services are used by companies and financial institutions including BMW, Vodafone, the Australian government, Westpac, ANZ, HSBC, and Virgin Money.
- A misconfiguration of the companys systems exposed sensitive credentials to the public.
- Data leak affected QBANK, Defence Bank, Bloom Money, Admiral Money, MA Money, and Reed.
- Using leaked data, threat actors could potentially breach banks backend infrastructure and consequently the infrastructure of their clients.
- Financial services are the main target for cybercriminals, so the threat for the organizations and their customers is severe.
- Cybernews contacted OCR Labs, and the company fixed the issue.
The Cybernews research team discovered a misconfiguration in the OCR Labs system that exposed sensitive data.
The company is a leading provider of digital ID verification tools, with its IDkit tool being used by major banks, telecoms companies, and governmental agencies. IDKit verifies users by linking their faces to their identity documents.
The discovered data leak impacted financial institutions in Australia QBANK, mainly used by government agency workers, Defence Bank, catering to the Australian armed forces, and MA Money, a company that focuses on residential mortgages.
The leak also affected Bloom Money and Admiral Money two financial companies based in the UK, and Reed, which is the UKs top recruitment agency.
Using leaked data, threat actors could potentially breach companies backend infrastructure and consequently the infrastructure of their clients. While financial services are the main target for cybercriminals, the threat to the organizations and their customers is severe.
Cybernews reached out to the company, and it fixed the issue.
A treasure trove of credentials
On March 8, 2023, the Cybernews research team discovered a publicly accessible environment file (.env) belonging to idkit.com, owned by OCR Labs.
The file contained database credentials, including host, port, and username, Amazon Web Services (AWS) with Simple Queue Service (SQS) access credentials, application tokens, and various application programming interface (API) keys.
Among the leaked data, researchers found Google and Liveness API keys. Liveness is used in the digital identification process, determining whether the sample belongs to a live person or a fake, thereby preventing ...
20:38
Chrome 113 To Ship WebGPU By Default Phoronix
While Chrome 112 just shipped this week and Chrome 113 only in beta, there is already a big reason to look forward to that next Chrome web browser release: Google is finally ready to ship WebGPU support! WebGPU provides the next-generation high performance 3D graphics API for the web...
20:36
EPO Staff Union: The Most Experienced Patent Examiners Are Leaving in Droves, Office Severely Understaffed Techrights
Summary: SUEPOs new publication, A State Of Affairs, is a shocking reminder that the EPO can collapse some time soon due to not only misguided leadership but deeply corrupt officials who rely on nepotism and bribes to delay/stall accountability
Dear colleagues, the Staff Union of the EPO (SUEPO) wrote today. In this State of Affairs, we briefly reflect on what will happen, what our administration should be doing vs. what it is doing.
We hope that our administration will observe the facts and starts looking at the longer-term sustainability of the office.
For 13 years (almost) Benot Battistelli and Antnio Campinos turned the EPO into not just a laughing stock but a serial violator of laws, conventions (including the EPC), and constitutions. The emergence of European software patents is a result of patent bubbles imploding and many examiners wont tolerate it anymore. Many have left for years and a lot more will leave, creating a vacuum in required skills, enraging top applicants. Heres the paper from SUEPO:
INTERNATIONALE GEWERKSCHAFT IM EUROPISCHEN PATENTAMT
STAFF UNION OF THE EUROPEAN PATENT OFFICE
UNION SYNDICALE DE LOFFICE EUROPEEN DES BREVETS6 April 2023
su23014cp 0.2.1/1.3.1/4.4A state of affairs
What will happen
- EPO staff will grow older;
- A quick glance at our demographics pyramid1 shows that soon enough we will see 200+, even 300+ colleagues the most experienced ones leave the EPO every year;
- There is no indication against the long-term trend in patent filings which has always been onwards and upwards2, even if the short-term variations may seem random.What should be happening...
20:25
IRC Proceedings: Wednesday, April 05, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-050423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-050423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-050423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-050423.gmi
Over HTTP:
|
... |
20:17
Huawei's Bolt 1.5 Adds AVX-VNNI, Intel Desktop GPU Support Phoronix
Huawei's Bolt project is a deep learning library focused on high performance and heterogeneous flexibility and supporting a variety of neural networks. Bolt claims to outperform other deep learning acceleration libraries while supporting models from TensorFlow, ONNX, Caffe, and more...
20:15
Threat Report Portugal: Q3 & Q4 2022 Security Affairs
The Threat Report Portugal: H2 2022 compiles data collected on the malicious campaigns that occurred from July to December, H2, 2022.
The Portuguese Abuse Open Feed 0xSI_f33d is an open-sharing database with the ability to collect indicators from multiple sources, developed and maintained by Segurana-Informtica. This feed is based on automatic searches and is supported by a healthy community of contributors. This makes it a reliable, trustworthy, continuously updated source, focused on the threats targeting Portuguese citizens. 0xSI_f33d has been part of the official VirusTotal ingestors since July 2021 allowing the community to verify threats worldwide provided by this feed.
The Threat Report Portugal: Q3 & Q4 2022 compiles data collected on the malicious campaigns that occurred from Jully to December, Q3 and Q4, 2022. The submissions were classified as either phishing or malware. In addition, the report highlights the threats, trends, and key takeaways of threats observed and reported into 0xSI_f33d. This report provides intelligence and indicators of compromise (IOCs) that organizations can use to fight current attacks, anticipate emerging threats, and manage security awareness in a better way.
Phishing and Malware Q3 & Q4 2022
The results depicted in Figure 1 show that phishing campaigns (98,7%) were more prevalent than malware (1,3%) during Q3 and Q4 2022. A growing trend in phishing submissions was observed in Q3 and Q4 (25369), with malware having 1.3% of the total, in comparison with 31.1% in Q2 2022.

Regarding Q1 2022, the phishing campaigns increased in reference to 2021 as a result of the research focused on the online stores scams that hit users worldwide. In detail, thousands of fake online store domains were compiled through this research in M...
20:02
VVenC 1.8 Released For Speeding Up Open-Source H.266/VVC Encoding Phoronix
VVenC is an open-source project from the Fraunhofer Institute for providing H.266/VVC video encode/decode capabilities. Out today is VVenC 1.8 with the latest enhancements for speeding up CPU-based H.266 video coding...
19:47
Analyzing attacks conducted by North Korea-linked ARCHIPELAGO APT group Security Affairs
Googles Threat Analysis Group (TAG) warns of a North Korea-linked cyberespionage group tracked as ARCHIPELAGO.
Googles Threat Analysis Group (TAG) is warning of the North Korea-linked ARCHIPELAGO group that is targeting government and military personnel, think tanks, policy makers, academics, and researchers in South Korea, the US and elsewhere.
Google experts are tracking ARCHIPELAGO since 2012 and have observed the group targeting individuals with expertise in North Korea policy issues.
TAG believes that the ARCHIPELAGO group is a subset of a threat actor tracked by Mandiant as APT43.
The attack chain associated with ARCHIPELAGO starts with phishing emails that embed malicious links. The messages pose as sent by a representative of a media outlet or think tank and ask North Korea experts to participate in a media interview or request for information (RFI). Upon clicking the link, the recipient is redirected to a phishing page that masquerades as a login prompt.
The credentials provided by the recipient are sent to an attacker-controlled URL, however, after the recipient enters their password, the phishing page redirects to a benign document that contains the interview questions, or an RFI that includes information of interest for the victims.
The experts pointed out that ARCHIPELAGO focuses on building a rapport with targets.
ARCHIPELAGO invests time and effort to build rapport with targets, often corresponding with them by email over several days or weeks before finally sending a malicious link or file. In one case, the group posed as a journalist for a South Korean news agency and sent benign emails with an interview request to North Korea experts. reads the analysis published by Google TAG. When recipients replied expressing interest in an interview, ARCHIPELAGO continued the correspondence over several emails before finally sending a OneDrive link to a password-protected file that contained malware.
The threat actor has also sent links that lead to browser-in-the-browser phishing pages. The phishing pages display users with a fake browser window rendered inside the actual browser window. The fake browser window displays a URL and a login prompt designed to trick recipients into providing their password to a legitimate login page.
19:33
Meta (Facebook, Instagram) Switching to "Legitimate Interest" for Ads SoylentNews
noyb will take immediate action to stop this illegal practice:
As the Wall Street Journal reports, Meta (Facebook and Instagram) is switching from an illegal contract to equally illegal basis "legitimate interests" for advertisement, after noyb won a series of complaints against them. noyb will take imminent action, as the clear case law and guidance does not allow a company to argue that its interests in profits overrides the users' right to privacy.
Background. The GDPR allows to process personal data if a company complies with at least one of six legal basis in Article 6 GDPR. Most of these six options are irrelevant for advertisement. While most companies require users to consent ("opt-in") for the use of personal data for advertisement, Meta (Facebook and Instagram) have tried to bypass this requirement by arguing that the use of personal data for ads is "necessary under the contract" when the GDPR became applicable in 2018. noyb has instantly filed a series of complaints and ultimately won them before the European Data Protection Board (EDPB) in December 2022. Meta got until April to stop the practice.
One illegal practice replaced by next illegal practice. Now Meta announces to give in against the pressure by noyb, but instead of switching to an "opt-in" system, like Google or Microsoft, they now try to argue the next unlawful option, by claiming that their "legitimate interest" to process user data would override the fundamental right to privacy and data protection of users. This was tried by other companies before, but rejected by the regulators multiple times (see e.g. the Italian DPA on TikTok or the Belgian DPA on the IAB TCF at para 441).
Read more of this story at SoylentNews.
19:24
United States: GNU/Linux Up to 11% in Desktops/Laptops, Windows Down to 53% Techrights
Another thing Microsoft would rather not be mentioned (the press is bribed to talk about some worthless chaffbot 24/7)
Summary: As can be seen above (latest data), Windows has barely even a majority market share for desktops/laptops in its home country
19:23
CryptoClippy: New Clipper Malware Targeting Portuguese Cryptocurrency Users Lifeboat News: The Blog
New CryptoClippy malware steals cryptocurrency by replacing wallet addresses during transactions.
19:23
Google Mandates Android Apps to Offer Easy Account Deletion In-App and Online Lifeboat News: The Blog
Google is enacting a new data deletion policy for Android apps that allow account creation to also offer users with a setting to delete their accounts in an attempt to provide more transparency and control over their data.
For apps that enable app account creation, developers will soon need to provide an option to initiate account and data deletion from within the app and online, Bethel Otuteye, senior director of product management for Android App Safety, said.
This web requirement, which you will link in your Data safety form, is especially important so that a user can request account and data deletion without having to reinstall an app.
19:23
Hackers Using Self-Extracting Archives Exploit for Stealthy Backdoor Attacks Lifeboat News: The Blog
Researchers uncover a new attack technique involving malicious SFX files! These files can hide hidden functionality, enabling persistent backdoor.
19:23
Typhon Reborn Stealer Malware Resurfaces with Advanced Evasion Techniques Lifeboat News: The Blog
Besides incorporating more anti-analysis and anti-virtualization checks, Typhon Reborn V2 removes its persistence features, instead opting to terminate itself after exfiltrating the data.
The malware ultimately transmits the collected data in a compressed archive via HTTPS using the Telegram API, marking continued abuse of the messaging platform.
Once the data has been successfully transmitted to the attacker, the archive is then deleted from the infected system, Brumaghin said. The malware then calls to terminate execution.
19:22
Rorschach Ransomware Emerges: Experts Warn of Advanced Evasion Strategies Lifeboat News: The Blog
Cybersecurity researchers have taken the wraps off a previously undocumented ransomware strain called Rorschach thats both sophisticated and fast.
What makes Rorschach stand out from other ransomware strains is its high level of customization and its technically unique features that have not been seen before in ransomware, Check Point Research said in a new report. In fact, Rorschach is one of the fastest ransomware strains ever observed, in terms of the speed of its encryption.
The cybersecurity firm said it observed the ransomware deployed against an unnamed U.S.-based company, adding it found no branding or overlaps that connect it to any previously known ransomware actors.
19:22
Shape-Shifting Antibiotics A New Weapon Against Drug-Resistant Superbugs Lifeboat News: The Blog
Antibiotic resistance is a major public health threat, ranked as one of the top 10 by the World Health Organization. Every year, in the United States alone, nearly 3 million people are infected by drug-resistant bacteria and fungi, resulting in the death of around 35,000. While antibiotics are crucial in treating infections, overuse has led to the development of antibiotic-resistant strains of bacteria. These infections pose a significant challenge to treatment.
Now, Professor John E. Moses of Cold Spring Harbor Laboratory (CSHL) has developed a new weapon to combat drug-resistant superbugs an innovative antibiotic that has the ability to shape-shift by rearranging its atoms.
Moses came up with the idea of shape-shifting antibiotics while observing tanks in military training exercises. With rotating turrets and nimble movements, the tanks could respond quickly to possible threats.
19:22
The Looming Marburg Crisis: How Virus Outbreaks Escalate and Spread Lifeboat News: The Blog
The World Health Organization confirmed an outbreak of the deadly Marburg virus disease in the central African country of Equatorial Guinea on February 13, 2023. To date, there have been 11 deaths suspected to be caused by the virus, with one case confirmed. Authorities are currently monitoring 48 contacts, four of whom have developed symptoms and three of whom are hospitalized as of publication. The WHO and the U.S. Centers for Disease Control and Prevention are assisting Equatorial Guinea in its efforts to stop the spread of the outbreak.
Marburg virus and the closely related Ebola virus belong to the filovirus family and are structurally similar. Both viruses cause severe disease and death in people, with fatality rates ranging from 22% to 90% depending on the outbreak. Patients infected by these viruses exhibit a wide range of similar symptoms, including fever, body aches, severe gastrointestinal symptoms like diarrhea and vomiting, lethargy and sometimes bleeding.
We are virologists who study Marburg, Ebola, and related viruses. Our laboratory has a long-standing interest in researching the underlying mechanisms of how these viruses cause disease in people. Learning more about how Marburg virus is transmitted from animals to humans and how it spreads between people is essential to preventing and limiting future outbreaks.
19:22
From Warzone to Fusion Power: Breakthrough in Cooking Up Plasmas With Microwaves Lifeboat News: The Blog
Lead author Yurii Victorovich Kovtun, despite being forced to evacuate the Kharkiv Institute of Physics and Technology amid the current Russia-Ukraine war, has continued to work with Kyoto University to create stable plasmas using microwaves.
Getting plasma just right is one of the hurdles to harnessing the massive amounts of energy promised by nuclear fusion.
Plasmas soups of ions and electrons must be held at the right density, temperature, and duration for atomic nuclei to fuse together to achieve the desired release of energy.
19:01
FBI Cracks Down on Genesis Market: 119 Arrested in Cybercrime Operation The Hacker News
A joint international law enforcement operation has dismantled Genesis Market, an illegal online marketplace that specialized in the sale of stolen credentials associated with email, bank accounts, and social media platforms. Coinciding with the infrastructure seizure, the major crackdown, which involved authorities from 17 countries, culminated in 119 arrests and 208 property searches in 13
18:23
Two Founders of Piracy Giant Zone-Telechargement Sentenced in France TorrentFreak
 For those who care to remember it, November 2016
was a dark month for communities with a penchant for sharing files.
Two huge sites fell in a matter of days, both courtesy of French
authorities.
For those who care to remember it, November 2016
was a dark month for communities with a penchant for sharing files.
Two huge sites fell in a matter of days, both courtesy of French
authorities.
When OiNK was shut down in 2007, the worlds largest dedicated music-sharing community fell with it. Few believed that a new site could fill the pig-shaped hole left behind; some insisted it would be wrong to even try.
What.cd not only filled that hole but did so by meeting and then surpassing all expectations. Then in November 2016, as French authorities swooped, What.cd self-destructed and disappeared into history, exactly as previously promised.
The cybercrime unit of the French military police didnt wait for the dust to settle. Following a two-year investigation into Zone-Telechargement, the most popular pirate download portal in France at the time, police shut down the site and arrested several people, including its alleged founders.
Operation Gervais
Local anti-piracy groups SACEM and ALPA filed a complaint against Zone-Telechargement in 2014. The goal was to identify financial accounts, assets, advertising agencies, and the sites hosting servers.
In the wake of the raid, it was claimed that Zone-Telechargement generated at least 1.5 million euros in sales per year, utilizing offshore accounts in Malta, Cyprus and Belize. The site caused an estimated 75 million euros in damages to rightsholders, rightsholders said.
The alleged founders of Zone-Telechargement were later identified as high-school buddies Thibault Ferreira and Wilfrid Duval. The pair founded the site in 2012 but had left France and were living in Andorra when the authorities shut down their site. That didnt prevent their arrest or the seizure of luxury cars, real estate, and at least 450,000 euros.
Fallout Zone
Ferreira and Duval were eventually charged with offenses related to intellectual property crime, money laundering, and operating as part of an organized criminal gang. They spent the next few months in prison before being released in March 2017 with conditions, electronic tagging included.
In the years that followed, sites claiming to be Zone-Telechargement regularly appeared to fill the vacuum, including one that was la...
18:22
Links 06/04/2023: StarFive-Based Star64 and Identity 0.5 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
-
GNU/Linux
-
Desktop/Laptop
-
GamingOnLinux TUXEDO reveal the Stellaris 16 (Gen5) for people with money to burn
Have some spare cash and in the market for a pricey and powerful Linux laptop? TUXEDO would l...
-
-
18:00
Printing Antennas on Circuit Boards Hackaday

Yagi-Uda antennas, or simply Yagis, are directional antennas that focus radio waves to increase gain, meaning that the radio waves can travel further in that direction for a given transmitter power. Anyone might recognize an old TV antenna on a roof that uses this type of antenna, but they can be used to increase the gain of an antenna at any frequency. This one is designed to operate within the frequencies allotted to WiFi and as a result is so small that the entire antenna can be printed directly on a PCB.
The antenna consists of what is effectively a dipole antenna, sandwiched in between a reflector and three directors. The reflector and directors are passive elements in that they interact with the radio wave to focus it in a specific direction, but the only thing actually powered is the dipole in the middle. It looks almost like a short circuit at first but thanks to the high frequencies involved in this band, will still function like any other dipole antenna would. [IMSAI Guy], who created the video linked above which goes over these details also analyzed the performance of this antenna and found it to be fairly impressive as a WiFi antenna, but he did make a few changes to the board for some other minor improvements in performance.
The creator of these antennas,...
17:00
All About Nuts: Eight Healthiest Varieties Terra Forming Terra

This needs to be shared. At least they are all now readily available and in generally fresh form. They all can go rancid and that is annoying.
It has taken a long time, but all these nuts are readily available, even in peeled form I just picked up a package of Brazil nuts, peeled from Costco for the first time.
Thus all forms of nuts have slowly come fully into the market. It really has not been easy. But here we are.

Energy-saving Paint Inspired by Butterflies Needs 0.3% Paint by Weight Terra Forming Terra
The return of silvopasture Terra Forming Terra
he sage and his foibles Terra Forming Terra
16:46
Germany Sours on Microsoft Again, Launches Antitrust Review SoylentNews
Microsoft is the latest US tech giant under investigation by Germany's competition watchdog:
On Tuesday, Germany's Bundeskartellamt which translates to federal cartel office announced it was evaluating whether Microsoft qualified as a company of "paramount significance." Or put another way, whether it's large enough to pose a threat to companies with fewer resources and therefore warrant closer scrutiny by regulators.
The investigation is being conducted under abuse control laws that went into effect in early 2021. These changes granted the agency the authority to prohibit large companies from engaging in certain business practices if it's determined they're likely to harm competition.
[...] The agency pointed to the company's expansive portfolio, which spans operating systems, productivity software, cloud services, video games, and social media as examples. "In light of this, there are good reasons to examine whether Microsoft is of paramount significance for competition across markets. Such a finding would allow us to take action at an early stage and prohibit possible anticompetitive practices," Bundeskartellamt President Andreas Mundt said in a statement.
There's also the fact that Microsoft isn't the first company to attract the German watchdog's attention. Last year, the agency found with "binding effect" that both Google and Meta were companies of paramount significance and were thus subject to heightened scrutiny. Amazon has found itself in a similar boat, but has appealed its decision. Meanwhile, the Bundeskartellamt says it's nearing completion of an investigation into Apple.
In response to the German government's investigation, a Microsoft spokesperson told The Register: "As a major technology company, we are mindful of our heightened responsibility to support a healthy competitive environment. We will engage constructively with the Bundeskartellamt, as they seek to understand our role in digital markets."
Read more of this story at SoylentNews.
16:27
ImmuniWeb unveils major updates to its AI platform Help Net Security
To help customers stay ahead of the emerging cybersecurity threats, fulfill regulatory and compliance requirements, and implement intelligent automation to accelerate internal processes and reduce operational costs, ImmuniWeb has unveiled many updates. ImmuniWeb AI platform: New CI/CD and DevSecOps integrations (35 in total) Improved project permissions management with granular access rights Integrations with AWS and Microsoft Azure for penetration testing of internal cloud apps ImmuniWeb Discovery: Advanced detection of exposed APIs with sensitive data Rapid More
The post ImmuniWeb unveils major updates to its AI platform appeared first on Help Net Security.
16:10
Resecurity uncovers STYX, new cybercriminal platform focused on financial fraud Help Net Security
Resecurity has recently identified the STYX Innovation Marketplace, a new cybercriminal e-commerce platform with a specialized focus on financial fraud and money laundering. STYX launched at the beginning of 2023. This platform is specifically designed to facilitate financial crime, providing cybercriminals with a range of services, including stolen financial data, credit card information, forged documents, money laundering services, victim reconnaissance lookups, and more. This discovery illustrates the post- pandemic menace of cyber-enabled financial crime and More
The post Resecurity uncovers STYX, new cybercriminal platform focused on financial fraud appeared first on Help Net Security.
15:00
No Home Cinema is Complete Without a Motorized Projector Hackaday

In the home of the future, everything is automated. Some of us are already there, in dwellings fully tricked-out with IoT and smart home devices. But they dont somehow look as futuristic as a home in which everything is motorized. We dont know whether this was the intention, but we certainly get a futuristic vibe from [Sam Baker]s home cinema projector mount. Its no mere bracket, instead on command the projector descends from concealment in the ceiling on a custom scissor lift mechanism.
A scissor lift is a simple enough mechanism, but since he was 3D printing one that had to withstand the weight of the projector, it took him a while to get it right. Even the lead screw which drives it is also printed, turned by a stepper motor. As the brains of the unit neednt be particularly accomplished, an Arduino Nano does the job well enough.
Its fair to say that his projector isnt the heaviest of models, but the result glides smoothly down from the ceiling for a perfect home cinema experience. We like it.
14:30
IT and security pros pressured to keep quiet about data breaches Help Net Security
Organizations globally are under tremendous pressure to address evolving threats like ransomware, zero-day vulnerabilities, and espionage, and they face challenges in extending security coverage across multiple environments and dealing with an ongoing skills shortage, according to Bitdefender. The results of this survey demonstrate, more than ever, the importance of layered security that delivers advanced threat prevention, detection and response across the entire business while improving efficiencies that allow security teams to do more with less, More
The post IT and security pros pressured to keep quiet about data breaches appeared first on Help Net Security.
14:00
Assessing AIs acquired knowledge from an organizations database Help Net Security
Researchers at the University of Surrey have developed software that can assess the amount of data that an artificial intelligence (AI) system has acquired from a digital database of an organization, in response to the increasing global interest in generative AI systems. This verification software can be used as part of a companys online security protocol, helping an organisation understand whether an AI has learned too much or even accessed sensitive data. The software is More
The post Assessing AIs acquired knowledge from an organizations database appeared first on Help Net Security.
13:59
Parisians Say Au Revoir to Shared E-scooters SoylentNews
89% of citizens want them gone at least among the 7.46% who showed up to vote:
Citizens of Paris voted on Sunday to ban e-scooters from the City of Love, and Mayor Anne Hidalgo responded by promising that the fleets of rechargeable rentables would be gone come September.
The outcome was overwhelming, with 89 percent of votes cast in favor of the ban, though only 103,084 of Paris's 1,382,322 registered voters participated around 7.5 percent. In a summary of the vote, the Parisian government noted that the final decision on the ban fell to city officials, who didn't appear to plan on countermanding the non-binding outcome.
[...] Only three companies are currently authorized to operate electric scooter fleets in Paris Lime, Dott and Tier which were granted three-year contracts in 2020 after Parisians voiced their dissatisfaction with a 2018 rollout in the city. Per Paris's government, the public domain occupancy agreements the three operators have all end on August 31, and it seems Hidalgo doesn't plan to renew them.
Lime and Tier both told The Register they would be ceasing operations in Paris come September 1, though Tier did note its shared e-bike service would still be available in the city.
Both companies expressed disappointment at the outcome, but pointed to the fact that the low voter turnout meant the results weren't representative of the city's entire population. "With approximately 93 percent of citizens not going to the polls, a large majority of Parisians have shown that e-scooters are not an issue," a Tier spokesperson said.
"We acknowledge the result of this unprecedented referendum, which was heavily impacted by very restrictive voting methods. This led to an extremely low turnout, heavily skewed towards older age groups, which has widened the gap between pros and cons," said a spokesperson for Lime.
Lime's response came from a third-party PR firm who said the statement represented a position "shared by Dott, Lime and Tier and not Lime speaking for the industry."
Read more of this story at SoylentNews.
13:40
Google Mandates Android Apps to Offer Easy Account Deletion In-App and Online The Hacker News
Google is enacting a new data deletion policy for Android apps that allow account creation to also offer users with a setting to delete their accounts in an attempt to provide more transparency and control over their data. "For apps that enable app account creation, developers will soon need to provide an option to initiate account and data deletion from within the app and online," Bethel
13:30
The staggering cost of identity fraud for financial services Help Net Security
The impact of identity fraud varies for organizations in the financial services industry, based on whether they belong to the banking or FinTech sector, according to Regula. Specifically, every fourth bank reported experiencing over 100 identity fraud incidents in the past year (26% of organizations), while this number is lower (17%) for the FinTech sector. Economic damage When asked to evaluate the cost of the identity fraud they had experienced, the banking sector was found More
The post The staggering cost of identity fraud for financial services appeared first on Help Net Security.
13:17
NOW: Pensions Trust Administration Team (Top Management) Gets Involved Amid Collapse of Sirius Corporation and Serious Embezzlement (Several Complaints, Several Victims) schestowitz.com
Even the CEO left last month!
Summary: Amid inflation, in light of Sirius workers leaving in droves, salaries have been cut even further (theyre looking to pay GNU/Linux engineers as little as 20,000 a year for an overnight job, including weekends and holidays!); of course many wont know some of that sum will moreover been stolen (embezzlement) under the guise of pension
Bonus: The current pension provider has been put on notice regarding pension fraud at Sirius Open Source . This has been escalated to the top management there. New letter below.
Dear Roy,
NOW: Pensions Trust (the Scheme)
Thank you for your time and patience allowing us to investigate your concerns, we very much regret that it has been necessary for you to contact us with your concerns.
Our understanding of your complaint is your concern that your NOW Pension is not safe due to your previous boss of Sirius potentially being involved in suspicious activities regarding the collection
of contributions.It was necessary for us to refer your concerns to our compliance department; they have come back with the following information.
NOW: Pensions are authorised and regulated as a master trust by The Pensions Regulator (TPR). Were one of approximately
38 master trusts approved and supervised continuously by TPR to maintain the quality of master trust providers in the UK. This means increased protection for members and their pension savings....
13:00
The hidden picture of malware attack trends Help Net Security
Despite the decline in network-detected malware in Q4 2022, endpoint ransomware spiked by 627%, while malware associated with phishing campaigns persisted as a threat, according to WatchGuard. Malware going undetected Despite seeing an overall decline in malware, further analysis from WatchGuard Threat Lab researchers looking at Fireboxes that decrypt HTTPS (TLS/SSL) traffic found a higher incidence of malware, indicating malware activity has shifted to encrypted traffic. Since just ~20% of Fireboxes that provide data for More
The post The hidden picture of malware attack trends appeared first on Help Net Security.
12:58
Amid Sirius Exodus (CEO, Engineers, NOC Staff) Salaries Reduced Even Further Techrights
Even the CEO left last month!
Summary: Amid inflation, in light of Sirius workers leaving in droves, salaries have been cut even further (theyre looking to pay GNU/Linux engineers as little as 20,000 a year for an overnight job, including weekends and holidays!); of course many wont know some of that sum will moreover been stolen (embezzlement) under the guise of pension
Bonus: The current pension provider has been put on notice regarding pension fraud at Sirius Open Source . This has been escalated to the top management there. New letter below.
Dear Roy,
NOW: Pensions Trust (the Scheme)
Thank you for your time and patience allowing us to investigate your concerns, we very much regret that it has been necessary for you to contact us with your concerns.
Our understanding of your complaint is your concern that your NOW Pension is not safe due to your previous boss of Sirius potentially being involved in suspicious activities regarding the collection
of contributions.It was necessary for us to refer your concerns to our compliance department; they have come back with the following information.
NOW: Pensions are authorised and regulated as a master trust by The Pensions Regulator (TPR). Were one of approximately
...
12:51
NEW 'Off The Hook' ONLINE 2600 - 2600: The Hacker Quarterly
NEW 'Off The Hook' ONLINE
Posted 06 Apr, 2023 2:51:03 UTC
The new edition of Off The Hook from 04/05/2023 has been archived and is now available online.
Cory Doctorow joins the panel to discuss his new book "Red Team Blues", the Amazon/Audible monopoly, Amazon's ad practices, an excerpt from "Red Team Blues", a preview of the next two books in the series, advice for new writers.
12:30
Stamus Networks U39 uncovers hidden anomalies in a proactive threat hunt Help Net Security
Stamus Networks released its latest software release, Update 39 (U39). The new release represents a significant enhancement to the companys flagship Stamus Security Platform (SSP), arming enterprise cybersecurity defenders with improved visibility while reducing the time it takes to respond to threats. Trusted by security teams in the worlds largest organizations, including government computer emergency response teams (CERTs), central banks, insurance providers, managed security service providers (MSSPs), multinational government institutions, broadcasters, travel and hospitality companies, More
The post Stamus Networks U39 uncovers hidden anomalies in a proactive threat hunt appeared first on Help Net Security.
12:30
Industrial Defender launches Phoenix to secure SMBs operations Help Net Security
Industrial Defender has unveiled the launch of Phoenix, an OT security solution tailored to the needs of SMBs. Phoenix is revolutionizing how smaller industrial organizations approach OT security by providing visibility into all their OT assets and their associated cyber risks. By providing a solution that is easy to deploy and cost-effective, Phoenix enables SMBs to overcome resource barriers and secure their operations effectively. From ransomware campaigns to nation-state attacks, cyber threats against industrial organizations More
The post Industrial Defender launches Phoenix to secure SMBs operations appeared first on Help Net Security.
12:15
Synopsys enhances Polaris Software Integrity Platform with fAST offerings Help Net Security
Synopsys has launched the Fast Application Security Testing (fAST) offerings that represent the latest capabilities and features of the Polaris Software Integrity Platform. Synopsys fAST Static and Synopsys fAST SCA enable DevOps teams to quickly find and fix vulnerabilities in their proprietary code and open source dependencies through a single fully integrated SaaS platform. Underpinned by modern cloud architecture and scalable multi-tenant SaaS delivery, Polaris makes it easy for developers to onboard and start scanning More
The post Synopsys enhances Polaris Software Integrity Platform with fAST offerings appeared first on Help Net Security.
12:00
Opening Up ASIC Design Hackaday

The odds are that if youve heard about application-specific integrated circuits (ASICs) at all, its in the context of cryptocurrency mining. For some currencies, the only way to efficiently mine them anymore is to build computers so single-purposed they cant do anything else. But an ASIC is a handy tool to develop for plenty of embedded applications where efficiency is a key design goal. Building integrated circuits isnt particularly straightforward or open, though, so youll need some tools to develop them such as OpenRAM.
Designing the working memory of a purpose-built computing system is a surprisingly complex task which OpenRAM seeks to demystify a bit. Built in Python, it can help a designer handle routing models, power modeling, timing, and plenty of other considerations when building static RAM modules within integrated circuits. Other tools for taking care of this step of IC design are proprietary, so this is one step on the way to a completely open toolchain that anyone can use to start building their own ASIC.
This tool is relatively new and while we mentioned it briefly in an article back in February, its worth taking a look at for anyone who needs more than something like an FPGA might offer and who also wants...
11:37
Links 05/04/2023: elementaryOS Updates and MidnightBSD 3.0.1 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Linux Format 301
Well keep your PCs old and new running that little bit longer with a combination of Linux Mint 21 and Linux Mint Debian Edition.
-
Desktop/Laptop
-
Its FOSS ...
-
-
11:35
Linux Foundation Launches Cybersecurity Essentials Linux.com

Read the original post at: Read More
The post Linux Foundation Launches Cybersecurity Essentials appeared first on Linux.com.
11:10
More Than Half of US Employees Don't Use All Their Vacation Time, Partly Due to Remote Work SoylentNews
The Pew Research Center's data (via Bloomberg) shows that only 48% of workers in the United States say they use up all their allocated vacation days. It might seem strange that someone would refuse to take paid time off that they're owed, but many say they worry about falling behind at work or feel bad about leaving an excessive workload with co-workers. Then there are those who feel they simply don't need the time off people who really love their jobs, presumably.
Another reason is the all-too-familiar fear (and occasionally a justified one) that using up all of one's vacation time could mean losing out on a promotion. Many also believe that if a company is making layoffs, which has become a familiar sight in the tech world these days, bosses are more likely to retain staff who take fewer vacation days.
[...] Ironically, working from home has also led to people taking fewer vacation days. Common reasons why employees used to take days off work, such as visiting a doctor, can now be done remotely or by leaving the home office for a short while.
"US employees have been conditioned to believe if you aren't at work, you are lazy or at risk of being replaced," said Christy Pruitt-Haynes, global head of talent and performance at workplace consultant firm NeuroLeadership Institute. "We also have been taught that to get more you have to work more, and since we all want more, we tend to prioritize active work over other things in our life."
The problem is less severe in Europe, where workers usually get more than the 15 - 20 average paid days off that US employees receive - and feel less guilty about using them.
Read more of this story at SoylentNews.
10:59
[$] LWN.net Weekly Edition for April 6, 2023 LWN.net
The LWN.net Weekly Edition for April 6, 2023 is available.
10:26
In the UK, Windows Falls to 63% on Laptops/Desktops (All-Time Low) Techrights
So says this survey that Microsoft fancies citing in self-serving contexts:
Summary: Now that Microsoft ditches plans for 500,000 sq ft London office its worth considering the companys status in the UK (its also under consideration/investigation for market abuse by Ofcom right about now)
10:00
HPR3829: The Edinburgh cohort of HPR hosts stops Mumbling! Hacker Public Radio
Introduction Hosts: MrX Dave Morriss We recorded this on Saturday March 11th 2023. This time we met in person, first at a pub called The Steading close to the entrance to the Midlothian Snowsports Centre where we had something to eat and drink - though they only serve breakfast items before 12 noon. Then we adjourned to Daves Citroen car (Studio C) in the car park and recorded a chat. The last of these chats was over Mumble in September 2022, so it was great to be away from home and to meet in person again after a long time of COVID avoidance. Topics discussed Google Docs - Dave and MrX use this to build shared notes to help organise these sessions There are issues with cut and paste when using Firefox it doesnt work! It can be fixed by selecting about:config in a new tab. Change the attribute dom.event.clipboardevents.enabled to true. Is email still relevant in 2023? Google Wave - Googles possible email replacement seemed not to have lasted very long Alternative access to Gmail using the IMAP protocol Folders versus labels. Tom Scotts video I tried using AI. It scared me. Daves experiences with email: Digital Equipment Corporations Vax VMS used DECmail, which needed DECNet networking. The UK Academic network (JANET) initially used its own Coloured Book protocols, including Grey Book mail. This ran over an X.25 network. Gradual transition to TCP/IP and SMTP mail (over JANET Internet Protocol Service, JIPS). In early Unix days (Ultrix) there was MH (Message Handler) Later, this was replaced by nmh. A GUI interface was available called xmh A very flexible open-source front end called exmh was crafted using Tcl/Tk Using procmail allowed an enormous number of capabilities, like sophisticated filtering, spam detection and automatic replies. Now using Thunderbird, and has been for maybe 15 years. MrX used Eudora in the past, but mostly uses Outlook now. Both agree that many useful features of email, available in the past, have gone. Both of us still find email relevant however! Calendars: MrX misses the calendar on the Psion Organiser Dave used to use an X-Windows tool called ical on Ultrix (no relation to the later iCalendar standard). Moved to Thunderbird and its calendar called Lightning. Both have used the Google Calendar, Dave uses a Thunderbird add-on to share family calendars Lifetime of storage media: SD cards can last a fairly long time, but getting the right type is important. Using older-style cards in new projects might turn out to be a false economy. Hard disks can last a long time if the right s
Challenges with Checked-In Secrets It Will Never Work in Theory
Like many programmers, I have accidentally committed authentication keys and other secrets to Git, then scrambled to delete them and replace them before anyone noticed. To find out exactly what kinds of mistakes people like me make, the authors of this paper mined questions from Stack Overflow, grouped them, and ranked the results. They found that the four most common problems are:
- storing and versioning secrets during deployment;
- storing and versioning secrets in source code;
- ignoring or hiding secrets in source code (which was surprising to me); and
- cleaning up verison control history after an oops.
The most common solutions recommended were:
- move secrets out of source code and use template configuration files;
- use some form of secret management in deployment; or
- rely on environment variables.
One of the most frequently ignored rules of engineering is, "Figure out what the problem is before you start trying to solve it," and this paper is a welcome example of a systematic, evidence-based attempt to do that.
Setu Kumar Basak, Lorenzo Neil, Bradley Reaves, and Laurie Williams. What challenges do developers face about checked-in secrets in software artifacts? 2023. arXiv:2301.12377.
Throughout 2021, GitGuardians monitoring of public GitHub repositories revealed a two-fold increase in the number of secrets (database credentials, API keys, and other credentials) exposed compared to 2020, accumulating more than six million secrets. To our knowledge, the challenges developers face to avoid checked-in secrets are not yet characterized. The goal of our paper is to aid researchers and tool developers in understanding and prioritizing opportunities for future research and tool automation for mitigating checked-in secrets through an empirical investigation of challenges and solutions related to checked-in secrets. We extract 779 questions related to checked-in secrets on Stack Exchange and apply qualitative analysis to determine the challenges and the solutions posed by others for each of the challenges. We identify 27 challenges and 13 solutions. The four most common challenges, in secrets in source code; and (iv) sanitize VCS history. The three most common solutions, in ranked order, are: (i) move secrets out secret management in deployment; and (iii) use local environment variables. Our findings indicate that the same solution has been mentioned to mitigate multiple challenges. However, our findings also identify an increasing trend in q...
09:02
Smashing Security podcast #316: Of Musk and Afroman Graham Cluley
An Elon Musk-worshipping college principal gets schooled, and rapper Afroman turns the tables after armed police raid his house. All this and much more is discussed in the latest edition of the "Smashing Security" podcast by computer security veterans Graham Cluley and Carole Theriault.
09:00
RP2040 And 5V Logic Best Friends? This FX9000P Confirms! Hackaday

Over the years, weve seen some modern microcontrollers turn out to be 5V-tolerant now, RP2040 joins the crowd. Half a year ago, when we covered an ISA card based on a Pi Pico, [Eben Upton] left a comment saying that RP2040 is, technically, 5V tolerant for GPIO input purposes. The datasheets dont state this because the reality of 5V tolerance isnt the same as for natively 5V-tolerant chips for instance, it doesnt extend all the way to 5.5V for it to be legally 5V-tolerant, as in, what 5V tolerance typically means when mentioned in a datasheet.
Having read that comment, [Andrew Menadue] has set out to test-drive the RP2040 GPIO capabilities, in a perfectly suited real-world scenario. Hes working with retro tech like Z80-era computers, using RP2040 boards for substituting entire RAM and ROM chips that have died in his FX9000P. N...
08:26
Star64 is a New RISC-V, Single-Board Computer for Developers and Hobbyists SoylentNews
The RISC-V alternative to Raspberry Pi is almost ready to ship:
The Star64 board, which was announced last summer, will finally be available for purchase this week. Developers will also be able to experiment with the system and enjoy the freedom of choice provided by the many interface options available on-board.
Open hardware company Pine64 is adding a new option to its offer of low-cost, ARM-based devices for developers and end users. Star64 is a single-board computer based on the RISC-V instruction set architecture (ISA), a Raspberry Pi alternative that provides an affordable way to create software for the RISC-based processor architecture.
The Star64 board should be available for purchase starting April of RAM. An 8GB model will be available as well for $90. The Star64 product page on the Pine64 store only shows the 8GB variant as of writing, and it is listed as out of stock.
As highlighted in Pine64's latest quarterly update, Star64 features a quad-core, 64-bit RISC-V 1.5GHz CPU (SiFive U74), a BX-4-32 GPU by Imagination Technology, support for up to 8GB of LPDDR4 RAM (1866MHz), and an integrated E24 RISC-V core for real-time control. The SiFive CPU should provide performance on par with the Rockchip RK3566 ARM (Cortex-A55) CPU, Pine64 says, while video support includes an HDMI port.
Star64 support for external communication is provided by a dual gigabit Ethernet port, WiFi 6 and Bluetooth 5.2 wireless interface, one USB 3.0 port, three USB 2.0 ports, and a 3.5mm audio jack. Power comes from a 12V/3A DC connector. Other connection options include a PCIe x1 slot, a GPIO port, and a MIPI-CSI camera interface. The board can be equipped with an optional eMMC module up to 128GB, and there's a microSD card reader for additional storage options.
[...] Compared to ARM, however, RISC-V is still severely lacking on the software side of things. A single-board computer like the Star64 could indeed provide a low-cost option for developers interested in experimenting with the RISC-V instruction set.
Read more of this story at SoylentNews.
07:56
[$] DCC-EX: open-source model railroading LWN.net
There's just something about trainsmodel trains in particular. At Everything Open 2023, Paul Antoine spoke about his experiences with the DCC-EX project, which has a variety of model-railroad automation hardware designs and software tools, all of which are freely available. There is a long legacy of sharing within the model railroading hobby, which continues today in the form of free and open-source software for it.
07:21
Beware of new YouTube phishing scam using authentic email address HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
Watch out for a new YouTube phishing scam and ignore any email from YouTube that claims to provide details about "Changes in YouTube rules and policies | Check the Description."
This is a post from HackRead.com Read the original post: Beware of new YouTube phishing scam using authentic email address
06:57
Nexx bugs allow to open garage doors, and take control of alarms and plugs Security Affairs
A series of vulnerabilities in multiple smart devices manufactured by Nexx can be exploited to remotely open garage doors, and take control of alarms and plugs.
In late 2022, the researcher Sam Sabetan discovered a series of critical vulnerabilities in several smart devices manufactured by Nexx, including Smart Garage Door Openers, Alarms, and Plugs. A remote attacker can exploit these vulnerabilities to open and close garage doors, take control of alarms, and switch smart plugs on and off for any customer.
The expert attempted to report the flaws to Nexx, but the company has never replied to the reports.
Nexx has not replied to any correspondence from myself, DHS (CISA and US-CERT) or VICE Media Group. reads a post published by Sabetan. I have independently verified Nexx has purposefully ignored all our attempts to assist with remediation and has let these critical flaws continue to affect their customers.
The researchers reported the issues to the United States Department of Homeland Security Cybersecurity and Infrastructure Security Agency (CISA), which assigned the following five CVEs:
- Use of Hard-coded Credentials CWE-798 (CVE-20231748, CVSS3.0: 8.6)
- Authorization Bypass Through User-Controlled Key CWE-639 (CVE-20231749, CVSS3.0: 6.5)
- Authorization Bypass Through User-Controlled Key CWE-639 (CVE-20231750, CVSS3.0: 7.1)
- Improper Input Validation CWE-20 (CVE-20231751, CVSS3.0: 7.5)
- Improper Authentication Validation CWE-287 (CVE-20231752, CVSS3.0: 8.1)
The expert estimated that over 40,000 devices, located in both residential and commercial properties, are affected by the above issues. He also determined that more than 20,000 individuals have active Nexx accounts.
06:23
New York City Is Dismantling Low-Cost Community Broadband Deeplinks
New York City is in the process of dismantling low-cost
community broadband infrastructure in public housing that, if
supported, could provide quality access to the internet for
hundreds of thousands of families. Its being replaced by a
$90 million, three-year government subsidy, called Big Apple
Connect that instead gives a contract to big internet providers
Optimum and Spectrum Communications (Charter).
This existing broadband network was built in 2021 mainly
by three community cooperatives: Metro IAF, BlocPower and Peoples
Choice Communications (PCC). These cooperatives built this network
after former New York City Mayor Bill de Blasio announced
New York Citys Internet Master Plan in January
2020, which set out to deliver broadband for
low-income New Yorkers by investing in public fiber infrastructure.
Since, then, the pandemic in 2020 exposed a digital divide that the
current mayors office knows it must attempt to bridge. Yet instead
of building off the network infrastructure already installed, it
appears the Mayors Office of Technology and Innovation (OTI) is
choosing to tear it down. In its place, the city is giving this
massive three-year contract to big telecom companiesincluding one
that has previously been untruthful to New York
residents.
Cable Already Failed NYC
Charter, the parent company of Spectrum, has been controversial in New York State for years. This is not only because of their five-year front-page fights with unions, but also because the company has a bad track record when it comes to meeting their promises. Charter Communications had to pay $174.2 million in a settlement with then New York Attorney General Barbara Underwoods office, following a 2017 lawsuit in which the New York Attorney Generals office sued the internet provider over misleading claims of internet speeds. The lawsuit, which was then led by Attorney General Eric Schneiderman, stated that speeds were up to 80 percent slower than Spectrum had advertised. Included in that $174.2 million settlement were payments to 700,000 of their customers, ranging between $75 to $150. The Attorney Generals office at the time called it the largest ever consumer settlement from an internet service provider.
All that has made many New Yorkers very skeptical of Spectrum. That's one reason why alternative options from community cooperatives were so attractive...
06:00
A Soft Soldering Jig For Hard Projects Hackaday

Weve seen some absolutely gorgeous freeform circuit sculptures. Theres a mystic quality to taking what has normally been hidden away for safety and reliability reasons and putting it on display for everyone to see. Of course, creating these unique circuit sculptures takes considerable time and effort. [Inne] created several silicone soldering jigs to help with these tricky joints.
While a vice or helping hands is crucial for many joints, when dealing with tiny SMD components and exacting angles, you need something a little more specialized. Double-sided tape is often recommended, but heat ruins the adhesive and SMD components like to stick to soldering iron tips. Since silicone tends to be heat resistant, it makes a decent material for soldering on. [Inne] uses a city analogy with the cups for soldering called plazas, each with a hole (called a manhole) leading to a foot-switch vacuum pump to keep parts in place. The OpenSCAD code is available on GitHu...
05:42
Using Running to Escape Everyday Stress May Lead to Exercise Dependence Instead of Mental Wellbeing SoylentNews
Recreational running offers a lot of physical and mental health benefits but some people can develop exercise dependence, a form of addiction to physical activity which can cause health issues. Shockingly, signs of exercise dependence are common even in recreational runners. A study published in Frontiers in Psychology investigated whether the concept of escapism can help us understand the relationship between running, wellbeing, and exercise dependence.
[...] "Escapism is often defined as 'an activity, a form of entertainment, etc. that helps you avoid or forget unpleasant or boring things'. In other words, many of our everyday activities may be interpreted as escapism," said Stenseng. "The psychological reward from escapism is reduced self-awareness, less rumination, and a relief from one's most pressing, or stressing, thoughts and emotions."
Escapism can restore perspective, or it can act as a distraction from problems that need to be tackled. Escapism which is adaptive, seeking out positive experiences, is referred to as self-expansion. Meanwhile maladaptive escapism, avoiding negative experiences, is called self-suppression. Effectively, running as exploration or as evasion.
Read more of this story at SoylentNews.
05:07
J&J to Pay $8.9 Billion to Settle Talc-Cancer Lawsuits cryptogon.com
Via: Bloomberg: Johnson & Johnson said it agreed to pay $8.9 billion to resolve all cancer lawsuits tied to its talc-based powders and will make a fresh attempt to contain the liability within a bankruptcy filing by one of its units.
05:03
Mohamed Ahmed Recipient of the 2023 Reset Scholarship in Social Media and Democracy News The Citizen Lab
The Citizen Lab is thrilled to welcome Mohamed Ahmed, the recipient of the 2023 Reset Scholarship in Social Media and Democracy.
Mohamed is a second year undergraduate student at the University of Toronto (U of T) majoring in Cognitive Science. Originally from Egypt, in 2021 he moved from Calgary, which is where his family lives, to Toronto for university. While researching various courses at U of T, he found himself drawn to the field of cognitive sciences, with a particular interest in the insights that computational approaches could yield on our understanding of human cognition, thought, perception, language, and emotion.
As a politically informed youth, he was intrigued by Professor Ronald Deiberts POL106 course, Contemporary Challenges to Democracy: Democracy in the Social Media Age. I had read Rons book Reset in my first year and was fascinated by immersive discussions on digital technology and its implications during his class and tutorial sessions. This scholarship was an opportunity to learn from people who work on these topics and I would have kicked myself for not trying, says Mohamed.
A competitive swimmer until Grade 12, Mohamed is an aquatic instructor at U of T and also a soccer enthusiast. In honor of Steven Gerrard, Mohamed is an ardent Liverpool supporter. He is currently watching Everything Everywhere All at Once and his all time favorite movie is Nacho Libre. When asked which app he typically uses before going to bed, he said Twitter. It is informative and contains some funny content, he claims.
04:56
Tax preparation and e-file service eFile.com compromised to serve malware Security Affairs
The eFile.com online service, which is authorized by the US Internal Revenue Service (IRS), was spotted serving malicious malware to visitors.
eFile.com, the personal online tax preparation and e-file service authorized by the US Internal Revenue Service (IRS), was spotted serving malware to visitors.
The service helps taxpayers to file tax returns, experts reported that eFile.com was first compromised in mid-March and was sanitized only this week.
A user on Reddit noticed that taxpayers attempting to load the website were redirected to a fake network error page that instructed them to download a fake browser update (called installer.exe or update.exe) to correctly access the service.
Any attempt to load the website www.efile.com appears to redirect to a fake Network Error page claiming that a browser update is required to access the site and providing a link to download an application called installer.exe or update.exe, depending on which browser is used. explained the user on Reddit.
I have attached screenshots of the error. Note that the lock icon in the address bar indicates the site is secure, contradicting the error message: NET::ERR_SSL_VERSION_OR_CIPHER_MISMATCH in the body of the page, and that clicking Advanced reveals further details that contain multiple misspellings, formatting, and grammatical errors. All of this suggests that the site is compromised and is being used to distribute malware.

The expert Johannes Ullrich, from the SANS Internet Storm Center, explained...
04:56
Twitter Labels NPR State Affiliated Media; Elon Musk Says Seems Accurate cryptogon.com
Via: Summit News: Twitter placed a label on NPRs account Tuesday describing the outlet as State-affiliated media, with owner Elon Musk commenting that the description seems accurate. Twitters guidelines state Labels on state-affiliated accounts provide additional context about accounts that are controlled by certain official representatives of governments, state-affiliated media entities, and individuals associated with []
04:26
Well-Known Crypto Tech Exec Murdered In San Francisco Stabbing cryptogon.com
Via: ZeroHedge: Well-known crypto tech executive Bob Lee was stabbed to death early Tuesday morning near downtown San Francisco. The 43-year-old Lee was perhaps best known for starting Cash App, and as former CTO of Square. He was the chief product officer of San Francisco-based crypto startup MobileCoin. San Francisco police responded at around []
04:24
AstraZeneca Clot Shot Is No Longer Available In Australia cryptogon.com
In other news from Australia: Excess Deaths Are the Highest Since World War II Via: Dr. John Campbell:
03:50
Police Confirm FBI-Assisted Takedown of Piracy Release Group EVO TorrentFreak
 EVO, short for EVOLUTiON, was a high-profile P2P group whose
activities stood out in recent years.
EVO, short for EVOLUTiON, was a high-profile P2P group whose
activities stood out in recent years.
The group released a steady stream of new movie and TV show titles and gained pirates admiration by leaking many screeners way ahead of their official premieres.
For several years in a row, EVO opened the screener season by releasing leaked copies of upcoming films. This included Oscar contenders, but also several Netflix titles that originated from festival screenings.
EVO was also the first to release an early Blu-Ray copy of Spider-Man: No Way Home last year, and a high-quality copy of the blockbuster Dune in 2021, ahead of its official U.S. premiere.
Like many other groups, EVO posted new releases on a regular schedule but that came to an abrupt halt last November when the group suddenly went quiet. While no explanation was given at the time, many pirates feared that the group had been busted.
National Criminal Investigation Police Take Credit
A few weeks ago TorrentFreak was able to confirm that this was indeed the case. Anti-piracy coalition ACE informed us that it had been working with Portuguese authorities to shut the group down and arrest its alleged leader.
This week Portuals Polcia Judiciria publicly confirmed that enforcement action Operation EVO 1.2 had been carried out through UNC3T, the national cybercrime unit.
The criminal investigation into EVO started early last year, following a complaint from Disney Enterprises, Paramount Pictures, Universal City Studios, Columbia Pictures, Warner Bros., Netflix, and Amazon. These are all members of the Motion Picture Association (MP...
03:30
Intel Vulkan Driver Squeezes In A Few More Performance Optimizations For Mesa 23.1 Phoronix
Ahead of the Mesa 23.1 branching and feature freeze coming up in the next week or two, Intel's open-source graphics driver developers have been landing some last minute performance optimizations to benefit their "ANV" Vulkan driver...
03:24
Dozer exits stealth to help any developer build real-time data apps in minutes Lifeboat News: The Blog
Data has emerged as one of the worlds greatest resources, underpinning everything from video-recommendation engines and digital banking, to the burgeoning AI revolution. But in a world where data has become increasingly distributed across locations, from databases to data warehouses to data lakes and beyond, combining it all into a compatible format for use in real-time scenarios can be a mammoth undertaking.
For context, applications that dont require instant, real-time data access can simply combine and process data in batches at fixed intervals. This so-called batch data processing can be useful for things like processing monthly sales data. But often, a company will need real-time access to data as its created, and this might be pivotal for customer support software that relies on current information about each and every sale, for example.
Elsewhere, ride-hail apps also need to process all manner of data points in order to connect a rider with a driver this isnt something that can wait a few days. These kinds of scenarios require what is known as stream data processing, where data is collected and combined for real-time access, which is far more complex to configure.
03:23
Rainbows are actually full circles. A physicist explains Lifeboat News: The Blog
Most of us only ever see a fraction of a full rainbow: an arc. But optically, a full rainbow makes a complete circle. Physics explains why.
03:23
This Insane 256-Foot Superyacht Concept Doubles as a Fully Functional Submarine Lifeboat News: The Blog
The concept for the CARAPACE yacht is sent straight from the future.
The 78m vessel has been conceptualized to double as a submarine that can dive to 985 feet.
Elena Nappi, an Italian based naval architect, has dreamed up this futuristic vessel.
The hybrid is designed for cruising the high seas and exploring the underwater world with its marine capabilities.
03:23
Mind-Bending Animation Shows How The Universe Would Look if We Could See Gamma Rays Lifeboat News: The Blog
Most of the light streaming through the Universe is invisible to human eyes. Beyond the mid-range wavelengths we can see, theres a whole cosmos shining in high-and low-energy radiation.
But we humans are clever little animals and have managed to build instruments that can see the light we cannot. One of these is NASAs Fermi Gamma-ray Space Telescope, an observatory hanging out in low-Earth orbit, monitoring the sky for gamma rays, the highest-energy light in the Universe.
Fermi constantly surveils the entire sky, observing gamma-ray sources and how they change over time, providing astronomers with a map of the various producers of gamma radiation that we can detect. This data is compiled into a catalog that scientists can use to probe the production of gamma radiation.
03:00
Retrotechtacular: Solder Like its 1944! Hackaday

When we first saw this 1944 US Office of Education film about hand soldering, we figured it might still have some good information. Well, perhaps it does, but the 1944 soldering was with a giant iron, and the work looked more like metal bricks than anything weve soldered lately. Of course, the physics is all the same, but some of the terminology, like sweating in isnt anything weve heard before, although we have heard of sweat soldering.
They do show some electronic soldering on components, including some interesting-looking coils. But the irons look more like a bad science fiction movies idea of a lightsaber. The solder is equally huge, of course.
If it Smells Like Bacon
We liked the soldering iron holder with a magnifier or maybe it is just a piece of shield glass that the lady in the movie uses. It would have made a perfect vent hood, too, but in 1944 we are guessing you were encouraged to sniff the fumes. They mention not letting wire fly into your eye, but they didnt cover safety glasses until well after that part. Not a word about lead safety, either.
The tip on the iron is bigger than most of the screwdrivers on our bench. Other than the scale, we didnt find much to disagree with in the film. After all, soldering is soldering regardless of the size of the solder joints. Of course, the real excitement comes at the end when they start using a flame to do some bulk soldering of some enclosures.
...02:58
How Russia Killed its Tech Industry SoylentNews
You may think, as I did, that Russia's current tech woe's are as a result of their invasion of Ukraine, or perhaps the annexation of Crimea. But it seems that the real problem started back around 2011 when it decided that the population having free access to information was not a good thing and, anyway, there must be money to be made if someone can take the tech industry under their control.
In Russia, technology was one of the few sectors where people felt they could succeed on merit instead of connections. The industry also maintained a spirit of openness: Russian entrepreneurs won international funding and made deals all over the world. For a time, the Kremlin seemed to embrace this openness too, inviting international companies to invest in Russia.
But cracks in Russia's tech industry started appearing well before the war. For more than a decade, the government has attempted to put Russia's internet and its most powerful tech companies in a tight grip, threatening an industry that once promised to bring the country into the future. Experts MIT Technology Review spoke with say Russia's war against Ukraine only accelerated the damage that was already being done, further pushing the country's biggest tech companies into isolation and chaos and corralling its citizens into its tightly controlled domestic internet, where news comes from official government sources and free speech is severely curtailed.
"The Russian leadership chose a completely different path of development for the country," says Ruben Enikolopov, assistant professor at the Barcelona School of Economics and former rector of Russia's New Economic School. Isolation became a strategic choice, he says.
The tech industry was not Russia's biggest, but it was one of the main drivers of the economy, says Enikolopov. Between 2015 and 2021, the IT sector in Russia was responsible for more than a third of the growth in the country's GDP, reaching 3.7 trillion rubles ($47.8 billion) in 2021. Even though that constituted just 3.2% of total GDP, Enikolopov saysthat as the tech industry falls behind, Russia's economy will stagnate. "I think this is probably one of the biggest blows to future economic growth in Russia," he says.
Read more of this story at SoylentNews.
02:30
HP WMI Driver To Expose More Sensors Under Linux For Business-Class Systems Phoronix
A patch was posted this week introducing a new "hp-wmi-sensors" Linux kernel driver for HP business-class computers for exposing WMI sensor functionality...
01:46
Z2U Market Leak Exposes Access to Illicit Services and Malware HackRead | Latest Cybersecurity and Hacking News Site
According to documents analyzed by Jeremiah Fowler, Z2U sells malware and other malicious services to customers under the guise of online trading.
This is a post from HackRead.com Read the original post: Z2U Market Leak Exposes Access to Illicit Services and Malware
01:40
Links 05/04/2023: GTK 4.11.1, Wayland 1.22, and Gajim 1.7.3 Techrights
![]()
Contents
-
GNU/Linux
-
Desktop/Laptop
-
Liliputing System76 teases made-in-Denver Linux laptop
System76 has been selling PCs that ship with Linux pre-installed for years. But for most of that time the company has worked with third-pa...
-
-
01:30
Typewriter Mashup Becomes 120-Year-Old Teletype Hackaday

Vintage typewriters can be beautiful and elegant devices. But theres a limit to their value if, as with the 1903 Remington owned by [Daniel Ross], they are fire-damaged and have a seized mechanism. What did he do with what was essentially a piece of scrap metal? Produce an unholy mashup of the vintage machine and a 1988 Sharp daisy wheel typewriter to make a steampunk-style teletype, of course!
Stripping down both machines was evidently no easy task, and the result hes achieved has the Sharps printer mechanism at 90 degrees to its original orientation sitting below the roller in the space once occupied by the Remingtons type bars. Were sad to see that the keyboard on the older machine appears to be inoperable, but on the other hand each letter does light up as its typed.
Meanwhile at the electronics side the components from the Sharp have been transferred to a custom PCB, and the whole can be driven from a 300-baud serial line. As can be seen from the video below the break, the result is an unholy love-child of two typewriters that could scarcely be more different, but somehow it works to make an impressive whole.
If this project looks a little familiar to Hackaday readers, its because weve mentioned it in passing before. Its hooked up...
01:24
Why It Was Important to Translate Linux Foundation Training Manuals to Ukrainian FOSS Force
The software industry plays a large role in Ukraine's economy, with many Ukrainian developers working remotely from Ukraine for software vendors located in the EU, UK, and US. Training manuals in the Ukrainian language will help veterans of Ukraine's military struggles against Russia take advantage of this opportunity.
The post Why It Was Important to Translate Linux Foundation Training Manuals to Ukrainian appeared first on FOSS Force.
01:23
Study explores the extent of Western dependency on Russian nuclear energy Lifeboat News: The Blog
Russias invasion of Ukraine in February 2022 had a profound deep impact on the economy, inflating the prices of energy and food, with detrimental consequences for both individuals and companies worldwide. As a result, many governments, particularly in Europe, have been discussing the possibility of reducing their dependence on Russian energy.
Most of these ongoing discussions specifically focus on fossil fuel energy, leading to the gradual introduction of sanctions for purchasing Russian coal, oil, and gas. However, Russia is also a key global provider of nuclear power, particularly via a state-owned nuclear energy corporation called Rosatom.
Researchers at the Norwegian Institute of International Affairs (NUPI) have recently carried out a study investigating the activity and global portfolio of Rosatom and its subsidiaries. Their findings, published in Nature Energy, highlight the high degree of European dependency on nuclear energy produced by this company, raising important questions about the need to find alternative energy suppliers.
01:23
More happy birthdays! Research says people could live to 141 Lifeboat News: The Blog
A scientist has predicted that men could live for as long as 141 years and women could reach over 130.
01:22
Scientists believe they may have found the secret to living to 100 and beyond Lifeboat News: The Blog
Scientists believe they may have found the secret to living past the age of 100. To some, the thought of living into your hundreds is a dream, while for others, its the complete opposite. But it seems that 70 percent of American adults actually want to live to 100, a 2022 poll by Edward Jones and Age Wave of 11,000 people revealed.
01:01
Melbet App Review For Android And Ios h+ Media
Melbet App Review For Android And Ios
It is useful for each type of smartphones of iOS and Android underneath that situation. One of an important things about Melbet is its transaction strategies. The structure of the app is in orange and black, which is quite soothing to the eyes. The casino can additionally be obtainable to all gamers in a special part. All slots are optimized for playing with mobile units. Also, popular stay on line casino leisure is out there to you.
The essential element when a bookmaker with a quantity of sports coverage decides to supply an app could be to offer simple navigation. In this regard, Melbet wins quite brilliantly by advantage of constructing it simple for customers to find the various sports activities and markets with out having to spend a lot of time. The benefit with Melbet can be the access offered via a mobile browser if the user just isnt so keen on utilizing the app. Fortunately, the browser experience is identical as one would get from the app.
The ecoPayz transfers are quite simple to implement and are very safe. The funds will be reflected in the account immediately with this feature. The minimal quantity to make an ecoPayz deposit is 87 INR and theres no payment included. If youre into card games or want to expertise the fun and adrenaline of enjoying with different gamers on-line, youve come to the right place. This is where youll get that experience within the poker sections of the Melbet App. The Melbet App uses the platform of sport maker Microgaming, which is among the most acknowledged in the on-line poker business.
Many of them being cryptocurrencies, so if you are looking for a bitcoin on line casino in India this might be the one for you. Melbet Bangladesh offers the richest potential number of sports disciplines and markets. All popular tournaments and occasions are represented here.
Most of Melbet Indias withdrawals are freed from cost and take approximately 24 hours for the transactions to be processed. There are additionally plenty of test matches that can assist you understand the Dos and Donts of the platform earlier than you stake actual cash. Melbet India is designed with a simple and straightforward to use interface for both skilled and versatile bettors or even for novice Indian bettors. The site has eye-friendly options with extremely seen shade displays that direct one to take motion without requiring technical abilities.
For Android and iOS devices, the software works more effectively and far quicker. This makes the method of inserting bets much simpler and extra pleasant for customers of the platform. Bingo is a worldwide well-liked TV sport the place the host takes numbers out of a bag and in the event that they match yours, youre fortunate and also you win. Melbet site has tailored the well-known TV recreation to their web site and now customers can play it on their phone or laptop.
You can even guess...
01:00
Melbet App For Android Apk & Ios h+ Media
Melbet App For Android Apk & Ios
It has the license registered from the Curacao which clearly defines its integrity and belief. In brief, Melbets quality of service is a strength that every sports membership and on line casino would like to have. So rest assured that youll feel snug being one of the privileged customers of the Melbet App. And if you have any doubts, youll have the ability to at all times refer to the FAQ section. In any case, navigating the poker game within the Melbet App is straightforward and its design is very sensible, so you presumably can quickly find what you want to play. A filter function is available here, which lets you choose what youre really excited about.
All slot machine games are enhanced for having fun with with cell items. Also, in fashion stay on line casino entertainment is available on the market to you. Making use of the Melbet software program makes your gambling lots easier. Betting site Melbet has been providing its players, including Indian users, ample alternatives for sports activities betting and on-line casino gambling since 2012. The company presently holds one of many leading positions in the Indian market, offering a huge number of markets, excessive odds and a high degree of player support.
E-sports can be obtainable within the cell utility sportsbook. FIFA, Mortal Combat, Call of Duty, and League of Legends are the most well-liked options amongst gamers thus far. With the Melbet app, it is extremely simple to make bets because of the platforms user-friendly layout.
Only on Melbet you can see the most detailed forecasts and probably the most favorable odds for badminton. Fans of this sport will definitely respect this spectacular provide from the bookmaker. In table tennis, essentially the most profitable type of bets are bets positioned earlier than the start of the sport. Football betting in Melbet additionally has very good odds, which may differ relying on different elements of the sport. The iOS Melbet app may be downloaded from the official iTunes retailer.
- In addition, you presumably can select whether or not you wish to wager in pre-match mode or choose to bet live.
- The course of could be very easy to observe and the processing time is immediate.
- To do this, select the free wager merchandise in the Bonus tab throughout registration.
- They should supply the likelihood to make bets, replenish the stability, withdraw winnings, contact customer service at any time, and so forth.
- The uniqueness of the application and in the speed of operation.
- The downloadable Melbet cellular app additionally incorporates a news feed.
Check the provision of further betting choices. The registration web page will open, the place youll be provided four methods to create an account (One-click, By telephone quantity, By e-mail, Via...
00:58
Melbet App Download For Android Apk & Ios In India h+ Media
Melbet App Download For Android Apk & Ios In India
Unfortunately, not all cell purposes are trustworthy places for betting. There are many scammers whove been added to a black list due to numerous complaints from gamers about delays in payments and many other problems that they confronted. Below you could find unreliable cell apps that you should keep away from. This sort of sports activities is actually well-liked among bettors because of a huge number of different prestigious tournaments that take place all year long throughout the globe.
Is available, in fact, for smartphones with the Android working system. This software may be very easy and fast to obtain to your cellular gadget. Therefore, you possibly can spend time well and profitably out of your cellphone. Generally, withdrawals take wherever from 24 hours to five business days after your account is verified and the transaction is accredited. You ought to know that the minimum withdrawal amount is USD 20. It all depends on the cost methodology every player chooses.
The greatest plus with Melbet is the ease of transactions with 56 deposit methods with forty eight of them getting used for withdrawals as nicely. With categories like Sports, LIVE bets, and eSports, Melbet presents you over 1,000 video games so that you just can guess on. If you are a sports activities fan whos at all times proper along with your predictions of an ongoing game and love your self an excellent on-line casino, Melbet Casino is simply the place for you. Melbet has been on the scene for more than a decade, at all times very consistent with payments and security.
Many luxurious facilities are also out there here for players like Sauna tub, Private Gym, Jacuzzi, Gym, Restaurant, sports and coaching academy, hostel, and so forth. Yes, you probably can claim any sort of bonus in a betting software together with free bets. All functions that personal an official license from gaming authorities are reliable in India. For now, there are no official legal guidelines in India that prohibit online betting on this nation.
Go to the official Melbet Bangladesh, where it is feasible for you to to see on the bottom the item with the bookmakers cellular apps. On the open web page, you will be able to choose the appliance on your gadget and instantly obtain and set up it. The Melbet app just isnt one of the latest additions to the world of online betting. Since its inception in 2012, this bookmaker has managed to gain recognition among sports activities fans. It has a variety of sports occasions and markets, which is attracting more and more betting followers.
Below there are crucial standards that you should think about whereas examining cellular apps. Downloading Melbet for Android is free, service is available to all Internet users. [newline]However, at the moment it is inconceivable to find this system in the Play Market. To obtain the Market app for fre...
00:56
Melbet App Evaluate For Indian Players h+ Media
Melbet App Evaluate For Indian Players
So youll have the ability to benefit from the on line casino expertise on the Melbet App. You also can bet on sports activities markets or on-line poker, and youre sure to search out the same gambling features as when you were betting on the official web site. Imagine being ready to keep related to different customers in the casino video games, slots, and different entertainment out there on the Melbet App wherever you are. Keep in mind that the games have the choice to play in demo mode. Yes, Melbet accepts Indian players and Indian foreign money as properly. One can bet on all the out there casino video games, sports/e-sports, and so forth.
The Melbet app for Android information may be found on the official web site together with apps that might run on Windows and Mac devices. The model has also made it straightforward to search out the location where one can get the Melbet app download. After downloading the file, the phones settings need to be modified in such a method that the restriction to put in apps solely from the Play Store is removed. After making this change, one can go back to the downloaded file and end the installation.
India vs New Zealand Ekana stadium IPL tickets demand could be very high as Lucknow cricket stadium is the home ground of the Lucknow Super Giants IPL staff. Lucknow IPL tickets are already out and ticket rates are ranging from 700. After the announcement of IPL tickets for Lucknow Super Giants IPL groups, cricket fans are on the lookout for IPL tickets price in Lucknow. A T20 international match between India and New Zealand was held at Lucknow Ekana stadium in January 2023.
The voucher allows new users to get a bonus for the primary deposit in the quantity of one hundred pc of the refilling sum, or a free wager that can be positioned on sports activities betting. The bookmaker offers its customers bets even on not very popular sports such as darts. Evaluate your intuitive talents by trying one thing new. A giant variety of sports activities and different events, many handy cost methods, and most importantly, all payments are fast and hassle-free. Yes, Melbet delivers Welcome offers to newcomers to its sports betting site and to its on line casino part.
One can access the Melbet India web site with its sports activities betting and casino merchandise from a Melbet app. This makes it simple to put bets or play casino video games from anywhere. Even on the Melbet app, youre unlikely to miss out on any of the highest features available from the model. The feeling that we get from MELbet is that the casino is making an attempt to position a strong emphasis on its sports betting function. It is clear that MELbet is attempting to build its brand as sports betting casino based mostly on the sheer number of sporting events that the casino makes obtainable to players. With hundreds of games in rotation and cryptocurrency choi...
00:53
Melbet India Review 2023 India Fast h+ Media
Melbet India Review 2023 India Fast
If you are on the lookout for a selected occasion to gamble on, you can use the search bar. I com login into melbet utilizing the com symbols within the line. High odds, plus bonuses and, in consequence, flies a reasonably penny. With Melbet, every little thing is easy, the location is convenient, the application does not freeze, the road is worthy of attention, the choice of occasions is wealthy. I played, bet on sports and even collected a moderately large sum. But Melbet is a fair bookmaker and I withdrew my cash efficiently.
I myself prefer to spend my evenings playing slot machines typically. So I recommend Melbet Bangladesh to you as a great bookmaker for newcomers from Bangladesh. A cause for Melbet changing into one of the key names within the online sportsbook segment can be its buyer support. Apart from being in a position to entry the betting markets and revel in most of the features, users can even attain customer assist directly from the app. Any options that can be built-in with none bother go into the Melbet app.
Even if the consumer decides to utterly abstain from Melbet app obtain, theyll still get the identical experience from the cellular browser. However, the app manages to supply a slightly optimized consumer expertise. Of course, the provide stays the identical and the same companies are retained. However, theres always doubt amongst Melbet App users that you can find all of the companies and leisure that the site provides on a desktop pc. This doubt arises because usually, some on-line pages restrict their promotions to completely different variations.
After entering the quantity, a code will be despatched to your cellphone, which you specify in a particular area. Try out the game on different sports activities and different coefficients. For example, football, hockey, basketball, or boxing give lower coefficients than baseball or American football. There is a chance to get acquainted with the features of betting on the newest sports activities. After the application has been downloaded, you have to install it, simply observe the instructions of the bookmaker.
It is adequate to make a deposit of 786 rupees or more to qualify for this 5-stage bonus. It can bring you an equal of up to EUR 1,750 with 290 additional spins of No Wager Bonus. Melbets web site is the place where the worlds greatest online TV video games are gathered. If youre bored with slots and card video games and wish to strive something new, the TV games section is ideal for you.
The add to favorites and enable reminder functions are additionally out there there. Also, sharing day-to-day investments in India by overlaying interviews, in-depth articles, & brand profiling tales together with main manufacturers in India. This web site is purely for informative and leisure functions solely. We do not accept any form of gambling, betting or wagering. We d...
00:52
How To Monetize Your Web Site With Melbet h+ Media
How To Monetize Your Web Site With Melbet
Accumulator of the day Every day, Melbet prepares a couple of accumulator bets with the most compelling events of the day, permitting you to place a guess. If you win, the percentages improve by 10%, giving you more cash than you were hoping to get. You can deposit the game account utilizing your mobile device via the game account menu.
Register in it, and when youre completed, you may have to level up in your affiliate program. The greater your degree the higher the cashback shall be. The Melbet app is on the market not just for Android but in addition for iOS. It also has low system necessities, and any iOS gadget will handle it. Melbet app for iPhone is available at no cost for anybody and has all the identical functions as the internet site.
You might be greeted by the acquainted design, the same interface, the same settings choices. The web page will automatically regulate to your screen size, and you shall be able to regulate it with one hand. Still, the browser-based model has a couple of variations from the downloadable apps. Live Casino The cellular platform is house to a live on line casino. Its introduced in HD video quality and crisp sound results.
To set up it successfully, allow your gadget to install recordsdata from unknown sources. Keep in mind that the casino only accepts bets in Euros. If you want to play in rupees, there might be an automated conversion. If youre a novice participant, low limits are available to you. But there can additionally be room for high rollers who are willing to wager 1000s of euros. Melbet is licensed by the Curacao regulator, which implies that enjoying right here is safe and the betting site is totally legal.
Once you open an account with Melbet India and fund it, you qualify for a one hundred pc matched bonus as much as 10,000. Melbet is Indias most trusted and fastest-growing company youll be able to trust your money with. Take your chances and win huge in 2023 and beyond as you develop with the brand.
If your operating system is Android, youll begin downloading the Apk file. You may get a warning that the file is probably not protected for your device. If youre downloading the app from the official web site, youre fine.
Its good that within the mobile app you can withdraw cash to paytm. Not many locations the place this payment system is available. After registration I was verified without delay and now the money is withdrawn in a couple of hours.
Whenever you log in, youll discover on-line gamers to compete and have enjoyable with. The mobile app appears to load quickly and its nice that you have to use the search performance to search out the competitors or team you need to wager on. [newline]However, it can be fiddly inserting a quantity of cricket bets with various legs and there can be delays in terms of getting cash out. Its clear that cricke...
00:49
Greatest On-line Casinos In New Zealand 223 Casino Evaluations h+ Media
Greatest On-line Casinos In New Zealand 223 Casino Evaluations
A readily-available, environment friendly customer support service is vital. We search for sites which have provide assist through quite lots of channels email, telephone or stay chat and assess the quality, timeliness and effectiveness of the care received. Anyone who wants to wager on Mr Green eSports should create a player account to access the sportsbook. It is not a must to add money instantly, however it will be required to place a real-money guess. Those whore new to gaming and betting should take time to know the chances. And when prepared, they will deposit cash into the account and start betting.
To be eligible for this bonus, you will have to play the exclusive reside blackjack table and you must play it throughout any weekend. If you are lucky sufficient to attract any of the 17 gold playing cards, you will receive the cash value on the actual gold card. On the opposite hand, when you draw Mr Green, you and different members of your team will get $20 each. There are some other variants just like the Multiplayer Roulette and the Double Bonus Spin.
However, this doesnt mean that its the finest online casino because the vary of video games is the most important. Since the New Zealand Gambling Act was amended in 2019, most New Zealand online casinos provide BankID as an id examine. This means that you mechanically register a sport account whenever you make a deposit on the on line casino. This way you dont have to register on the on line casino manually, and get registered in connection along with your deposit.
We even carried out an odds comparison check between Mr Green and one of its competitors for an NBA basketball match and located that Mr Green wont allow you to down right here. So just ensure you consider Mr Green for the following time that you need to bet on sports activities. Dont forget about the Mr Green Specials which are a good way to get odds boosts on some top sporting occasions. Mr Green offers you a good way to guess on all sports like rugby, cricket, golf, horse racing and rather more. Like many European bookmakers, Mr Green tends to concentrate on soccer betting, nevertheless it additionally has a formidable protection of anything from basketball and esports to boxing and tennis. We also appreciated the reality that Mr Green covers some smaller sports similar to snooker and MMA combating.
It also operates under the Isle of Man Gambling Supervision Commission, Gibraltar Gambling Commission, and Alderney Gambling Commission. The father or mother firm, Mr. Green Limited, based mostly in Malta, is a half of the GenCare and MRG group. The green bookie isnt just about providing lucrative betting opportunities; the platform upholds accountable gambling practices.
Many on-line gambling players in New Zealand look forward to seeing extra of her work right here at Kiw...
00:47
Mr Green On Line Casino Nz Evaluate 3x Welcome Bonuses As Much As $100 h+ Media
Mr Green On Line Casino Nz Evaluate 3x Welcome Bonuses As Much As $100
The talked about reloading bonuses provides you with a further cash boost up to NZD50 for stay on line casino video games. Not all of the games contribute the identical way towards the wagering requirement, so you have to examine the wagering contribution of assorted stay on line casino video games. Overall, the site provides a superb visible experience for its customers in addition to a good range of games to swimsuit everybody from the novice to the skilled on-line gambler.
During the registration process, a participant is offered to set limits for day by day, weekly and monthly video games by the system. With this function, you presumably can set the maximum quantity to be spent in the casino throughout the specified period. This characteristic permits gamers to regulate their own spending on gambling, particularly those that find it tough to manage the waste of cash being excited.
- Our evaluate team also is keen on reviewing the bonuses, which frequently make essentially the most of the web gaming experience.
- Mr Green on-line casino is powered by the Swedish on-line gaming giant Kambi.
- Although they are an effective way to boost your bankroll, be certain to verify how lengthy your bonus will remain legitimate, as some on-line Casino will withdraw it within a number of days.
- The comparability website owned by GiG, Gaming Innovation Group, A listed company in Stockholm active within the iGaming trade.
- Overall, nonetheless, we might advocate that you always use the reside chat operate.
The only factor that is not listed under the slots at Mr Vegas is Slingo games that Rainbow Richie and Starburst slingo . Sure you want these varieties of games that mix online bingo with slots you get to look further to casinos that concentrate on these sorts of video games, for example Slingo casino . In addition to this, Mr Vegas has done a fantastic job of providing as many casino video games as they really do. With secure casino licenses, which means the on line casino is audited from two different directions.
Activate notifications and you will immediately obtain the most recent promotions. Luckia has a downloadable casino games app for Android and iOS. The interface is excellent, navigation is completed without main inconvenience. Mobile on line casino App provides plenty of stay occasions and one of the best bets.
The web site incorporates information about gaming corporations and paid links to on-line casinos with New Zealand license from Playing with money may be addictive. Even in terms of, what is often mistakenly known as, on line casino on-line with out an account, its casinos with BankID which is used. These casinos usually known as Pay n play casino , as these kind of casinos at all times use Trustlys service for deposits and withdrawals.
If you suppose your gambli...
00:47
Mr Green On Line Casino Look Here! Nz 2023 h+ Media
Mr Green On Line Casino Look Here! Nz 2023
It could be played on a tool, in addition to on a smartphone or pill. Its simple to get started and take part within the enjoyable; all you need is an web connection. All of that is valid for the casino, live on line casino, odds, and stay betting. Mr Green casino has been round for 10 years, they usually have proved to be top-of-the-line on-line casinos because of their services and gaming environment.
You also can place live, in-play sports activities bets from inside the app. In cell on-line on line casino you can find more than 60 games, where slots predominate. Due to having an unique software supplier, the machines are distinctive, and theyre tailored to the display of your cellular device. The colour of the slots resembles Las Vegas but in your smartphone or pill. You can take pleasure in roulette, blackjack and poker in their variants including baccarat. The limits of bets, spins and games are the identical because the cellular on line casino model.
Apart from strolling the discuss and trying out quite swanky, Mr. Green Casino is totally respectable in terms of Kiwi players safety, security, and player help. Read on below and find out more about what Mr. Green has in retailer for New Zealand gamblers. The account verification is a standard procedure of every on line casino nowadays and they treat players privateness with the utmost confidentiality.
This website was a pioneer in the online gaming industry by being one of many first operators to take action. While it is primarily a web-based casino website, but it also supplies on-line sports activities betting. Mr Green understands this very well and offers their common customers an opportunity to get a share of 20,000 by participating in a slot contest. To play the contest, you first need to be eligible for the competition.
From our point of view, such a correct app for the smartphone is even a tick better than these web sites tailored for cellular gadgets. If you are on the lookout for one of the best online casino, our current ranking will help you. These are listed because the suppliers with one of the best video and audio quality. Comply with the specified times to charge your account the amount you request. Make full funds, in accordance with the circumstances accepted by the consumer.
There is a button Play For Fun that allows taking half in most video games freed from charge and without registration. Visa, MasterCard, Skrill, Neteller, Paysafecard and Direct Bank Transfer are some of the banking strategies available at Mr Green. I truly have personally used Visa and Skrill to buy goods on-line in addition to play casino games and utilizing them is seamless and easy. However, I dont prefer it when I need to pay a charge for utilizing these strategies, therefore, I assume that the two.5% fee for credit score and debit card deposits at Mr Green should be abolished. I wish to g...
00:44
Mr Green Casino Kiwi Evaluate Nz$1,200 Bonus + 200 Free Spins 1,600+ Video Games h+ Media
Mr Green Casino Kiwi Evaluate Nz$1,200 Bonus + 200 Free Spins 1,600+ Video Games
Since a casino account can be immediately created by way of this service, not all online casinos have been instantly convinced that it might be a useful addition to their web sites. But since Pay n Play, the life of online gamblers has made it really easy and increasingly players signed up on the best online casino Pay n Play. Other on-line casinos have additionally added this cost method so as to not lose its gamers.
- Additionally, youll have the ability to even modify a limit per a single bet with the wagering restrictions.
- Download your cell on line casino App from the App store or the cellular model from their website.
- All 3 deposit bonuses have the identical deposit requirement, which is a minimum of $25.
- Dont neglect in regards to the Mr Green Specials which are a good way to get odds boosts on some top sporting events.
They have excellent native customer assist groups as talked about earlier. You could be attain them by email in addition to being known as by way of native phone numbers. If, in reality, a player feels theyre hooked on playing, Mr Green astonishingly provides help. It offers particulars of multiple organizations positioned close to the participant. It supplies free, unbiased and private support on all aspects of issues with playing on their web site. Banking choices are lined extensively on Mr Greens help centre, every thing from withdrawals, deposits and proof of identification.
Banking strategies at Mr Green on line casino are numerous and Kiwis could have many choices to choose on for deposits. Mr Green really scores prime marks with its graphics and user interface, combining a modern and skilled looking background with wealthy gaming graphics. There is a excessive emphasis on entertainment constructed into all of the sites games, offering a visual feast for players of all levels.
Racking up plenty of awards and recognition for their excellent service and general buyer experiences in 2016 the company was listed in the main market of Nasdaq Stockholm. Mr Green may be very selective when bringing on gaming software program suppliers and will contract only one of the best for the internet site. 100 percent free to hitch the gaming web site provides many incentives, contests, prizes and perks you will learn more about below. Mr. Green was launched in 2008 and so far, it has turn into one of the best sportsbooks online. Mr Green is licenced and controlled to ensure that players dont get ripped off their winnings. The sportsbook provides actual money sports betting for all punters.
However, you may properly discover that it takes up to some days to execute the fee. Its all the time worth having a look on the live supplier recreation selection. Here at Casino New Zealand you will find details about every little thing associated to online casinos...
00:26
Survey results: the usage of money in Debian LWN.net
The Debian project has reported on a survey of developers on the use of project funds to support development work.
There seems to be broad support for paying people who are already involved as Debian contributors, but very little support for hiring contractors, that is to say, those who are not already Debian contributors in some way. Members of the Security Team were by far the most supportive towards the idea of paying Debian contributors.
The full report is available for those wanting all the details and pie charts.
00:17
CryptoClippy: New Clipper Malware Targeting Portuguese Cryptocurrency Users The Hacker News
Portuguese users are being targeted by a new malware codenamed CryptoClippy that's capable of stealing cryptocurrency as part of a malvertising campaign. The activity leverages SEO poisoning techniques to entice users searching for "WhatsApp web" to rogue domains hosting the malware, Palo Alto Networks Unit 42 said in a new report published today. CryptoClippy, a C-based executable, is a type
00:14
Lots of Microsoft Shutdowns Reported Today (Whole Offices, Divisions and Products Axed Entirely) Techrights
Can the chaffbot generate enough media noise/smokescreen (all that AI chaff) to distract from all that?
Yes, buzzwords as a vapourware tactic (be patient, shareholders, well razzle-dazzle you in the future while we lose money now). Weve seen this before. First "metaverse", now "AI" (they misleabel or call almost everything that)
Turns out greenwashing PR is a luxury when the marketing budget runs thin and the clown computing business disputes false narratives (AI means a lot of unnecessary pollution).
That does not seem like the hallmark of a healthy company. Even its expansion plan/PR turns out to be vapourware.
Summary: Microsofts layoffs and shrinking business footprint is a big feature this month, even if the media keeps focusing on vapourware and hype instead (Microsoft pays for misplaced media focus)
00:12
German Police Raid DDoS-Friendly Host FlyHosting SoylentNews
German Police Raid DDoS-Friendly Host 'FlyHosting':
Authorities in Germany this week seized Internet servers that powered FlyHosting, a dark web offering that catered to cybercriminals operating DDoS-for-hire services, KrebsOnSecurity has learned. FlyHosting first advertised on cybercrime forums in November 2022, saying it was a Germany-based hosting firm that was open for business to anyone looking for a reliable place to host malware, botnet controllers, or DDoS-for-hire infrastructure.
A statement released today by the German Federal Criminal Police Office says they served eight search warrants on March 30, and identified five individuals aged 16-24 suspected of operating "an internet service" since mid-2021. The German authorities did not name the suspects or the Internet service in question.
"Previously unknown perpetrators used the Internet service provided by the suspects in particular for so-called 'DDoS attacks', i.e. the simultaneous sending of a large number of data packets via the Internet for the purpose of disrupting other data processing systems," the statement reads.
[...] The German authorities said that as a result of the DDoS attacks facilitated by the defendants, the websites of various companies as well as those of the Hesse police have been overloaded in several cases since mid-2021, "so that they could only be operated to a limited extent or no longer at times."
The statement says police seized mobile phones, laptops, tablets, storage media and handwritten notes from the unnamed defendants, and confiscated servers operated by the suspects in Germany, Finland and the Netherlands.
[...] The apparent raids on FlyHosting come amid a broader law enforcement crackdown on DDoS-for-hire services internationally. The U.K.'s National Crime Agency announced last week that it's been busy setting up phony DDoS-for-hire websites that seek to collect information on users, remind them that launching DDoS attacks is illegal, and generally increase the level of paranoia for people looking to hire such services.
Read more of this story at SoylentNews.
00:00
How Tattoos Interact With The Immune System Could Have Impacts for Vaccines Hackaday

Tattoos are an interesting technology. Theyre a way of marking patterns and designs on the skin that can last for years or decades. All this, despite the fact that our skin sloughs off on a regular basis!
As it turns out, tattoos actually have a deep and complex interaction with our immune system, which hold some of the secrets regarding their longevity. New research has unveiled more insight into how the body responds when we get inked up.
Not Going Anywhere
As we all know, if you draw something on your skin with a pen, paint, or marker, it will eventually come off in a few days or so. Tattoos, on the other hand, are far more longer lasting. The basic theory of tattooing is simple. Rather than putting ink on the epidermis (the upper layer of skin), it is instead inserted into the underlying upper dermis. There, the ink is free from the day-to-day sloughing off of skin. A properly-performed tattoo can last a lifetime, and beyond, in the case of the oldest identified tattooed individual from 3250 BC.
...00:00
Wednesday, 05 April
23:53
HP would take up to 90 days to fix a critical bug in some business-grade printers Security Affairs
HP would take up to 90 days to address a critical flaw, tracked as CVE-2023-1707, that resides in the firmware of some business-grade printers.
HP is aware of a critical vulnerability, tracked as CVE-2023-1707 (CVSS v3.1 score 9.1), that affects tens of HP Enterprise LaserJet and HP LaserJet Managed Printers models. The exploitation of the flaw can potentially lead to information disclosure and the IT giant announced that it would take up to 90 days to address the vulnerability. An attack can trigger the bug to access data transmitted between the vulnerable HP printer and other systems on the same network segment.
The company pointed out that the information disclosure can be achieved only by exploiting the flaw on vulnerable devices running
Certain HP Enterprise LaserJet and HP LaserJet Managed Printers are potentially vulnerable to information disclosure when IPsec is enabled with FutureSmart version 5.6. reads the bulletin published by the company.
The vendor has released temporary firmware mitigation for customers currently running FutureSmart 5.6 with IPsec enabled on their printers. The company recommends customers immediately revert
HP told BleepingComputer that it is not aware of any active exploits, the company pointed out that the exposure period to this potential vulnerability was limited to mid-February 2023 until the end of March 2023)
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections:
- The Teacher Most Educational Blog
- The Entertainer Most Entertaining Blog
- The Tech Whizz Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please nominate Security Affairs as your favorite blog.
Nominate here: https://docs.google.com/forms/d/e/1FAIpQLSfaFMkrMlrLhOBsRPKdv56Y4HgC88Bcji4V7OCxCm_OmyPoLw/viewform
Follow me on Twitter: @securityaffairs and&nbs...
23:35
Security updates for Wednesday LWN.net
Security updates have been issued by Debian (ghostscript and openimageio), Fedora (kernel, rubygem-actioncable, rubygem-actionmailbox, rubygem-actionmailer, rubygem-actionpack, rubygem-actiontext, rubygem-actionview, rubygem-activejob, rubygem-activemodel, rubygem-activerecord, rubygem-activestorage, rubygem-activesupport, rubygem-rails, and rubygem-railties), Oracle (gnutls, httpd, kernel, nodejs:16, nodejs:18, pesign, postgresql:13, tigervnc, and tigervnc, xorg-x11-server), Red Hat (gnutls, httpd, httpd:2.4, kernel, kpatch-patch, pcs, pesign, postgresql:13, tigervnc, and tigervnc, xorg-x11-server), Scientific Linux (httpd and tigervnc, xorg-x11-server), SUSE (aws-efs-utils.11048, libheif, liblouis, openssl, python-cryptography, python-Werkzeug, skopeo, tomcat, and wireshark), and Ubuntu (imagemagick, ipmitool, and node-trim-newlines).
23:24
AGI Unleashed: Game Theory, Byzantine Generals, and the Heuristic Imperatives Lifeboat News: The Blog

Patreon: https://www.patreon.com/daveshap.
GitHub: https://github.com/daveshap.
Cognitive AI Lab Discord: https://discord.gg/yqaBG5rh4j.
Artificial Sentience Reddit: https://www.reddit.com/r/ArtificialSentience/
Heuristic Imperatives Reddit: https://www.reddit.com/r/HeuristicImperatives/
DISCLAIMER: This video is not medical, financial, or legal advice. This is just my personal story and research findings. Always consult a licensed professional.
I work to better myself and the rest of humanity.
23:23
Stephen Hawkings famous black hole paradox looks to finally have a solution Lifeboat News: The Blog
The Hawking radiation emitted by black holes may be able to carry crucial information, a new study suggests. Scientists may have just found the solution to one of astrophysics most mind-boggling mysteries concerning black holes, also known as the Hawking information paradox. A study published in the journal Physics Letters B last month offers a resolution to a problem the late physicist Stephen Hawking was working on in his final years.
23:23
23:18
Genesis Markets Clearnet domain seized; Dark Web site still online HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
The FBI and European authorities have seized Genesis Markets clearnet domains as part of the ongoing Operation Cookie
This is a post from HackRead.com Read the original post: Genesis Markets Clearnet domain seized; Dark Web site still online
23:13
Cyber threats organizations should keep an eye on in 2023 Help Net Security
In Malwarebytes most recent report on the current state of malware, the company has identified several high-profile cyber threats that organizations should be on the lookout for in 2023. The 5 most important cyber threats LockBit, an affiliate-based ransomware variant, has dominated the 2022 threat lascape, and it has affected hundreds of businesses of all sizes. Since April 2022, one in three known ransomware attacks has involved LockBit, the report revealed. Two of the currently More
The post Cyber threats organizations should keep an eye on in 2023 appeared first on Help Net Security.
23:01
How API burn rate alerts are calculated in Red Hat OpenShift Linux.com
Burn rates help you predict whether your downtime is too high or risks exceeding your service-level objective.
Read More at Enable Sysadmin
The post How API burn rate alerts are calculated in Red Hat OpenShift appeared first on Linux.com.
23:00
AMD Ryzen 7 7800X3D Linux Performance Phoronix
While the AMD Ryzen 9 7950X3D and Ryzen 9 7900X3D processors went on sale at the end of February as the first Zen 4 3D V-Cache processors, today marks the availability of the Ryzen 7 7800X3D processor. I've recently been putting the 7800X3D through its paces under Linux and have a plethora of benchmark data to share for launch day.
22:36
Hackers Using Self-Extracting Archives Exploit for Stealthy Backdoor Attacks The Hacker News
An unknown threat actor used a malicious self-extracting archive (SFX) file in an attempt to establish persistent backdoor access to a victim's environment, new findings from CrowdStrike show. SFX files are capable of extracting the data contained within them without the need for dedicated software to display the file contents. It achieves this by including a decompressor stub, a piece of code
22:27
GTK 4.11.1 Released With Better Textures, Wayland Fractional Scaling Phoronix
Following this week's Qt 6.5 LTS and Slint 1.0 Rust toolkit, debuting today is GTK 4.11.1 as the first development release of the new toolkit series in leading up to GTK 4.12...
22:19
Google TAG Warns of North Korean-linked ARCHIPELAGO Cyberattacks The Hacker News
A North Korean government-backed threat actor has been linked to attacks targeting government and military personnel, think tanks, policy makers, academics, and researchers in South Korea and the U.S. Google's Threat Analysis Group (TAG) is tracking the cluster under the name ARCHIPELAGO, which it said is a subset of another threat group tracked by Mandiant under the name APT43. The tech giant
22:15
CISA JCDC Will Focus on Energy Sector Security Affairs
The CISA s Joint Cyber Defense Collective (JCDC) initiative is going to build operation plans for protecting and responding to cyber threats.
What comes to mind when you think of cyber criminals? Depending on who you ask, youll get a variety of answers. For some, a cyber criminal matches some of the Hollywood tropes: a person sitting alone in a dimly lit room, furiously mashing on a keyboard to steal information from a person or company.
Those days are behind us, however, as cybercrime is establishing itself as a business in and of itself. Cyber attack instances are steeply rising across all sectors, leaving even the FBI to issue a bulletin about business email compromise (BEC) the $43 billion scam.
Taking note of the pervasive threat landscape, the US government has devoted more resources to building a team to protect citizens and businesses. This effort began with the 2018 establishment of the Cybersecurity and Infrastructure Security Agency (CISA), a Department of Homeland Security division.
Going one step further, in 2021, the CISA announced the formation of the Joint Cyber Defense Collective (JCDC), an initiative formulated to bring government and private industry representatives together to build operation plans for protecting and responding to cyber threats.
The JCDC has seen the benefits of collaboration for exigent risks (such as the heightened awareness and protection related to Russias invasion of Ukraine and the Log4Shell vulnerability) but sees a remaining gap when it comes to imminent risk. To address this gap, the JCDC is planning proactive measures for future cyber risks.
The backbone of this planning is the JCDCs 2023 Planning Agenda. The aim of the Agenda is to leverage the expertise of public and private sector members to develop and launch defense plans focused on risk reduction.
2023 Planning Agenda
The inaugural 2023 Planning Agenda will focus on three key topics:
Collective Cyber Response
JCDC will update the National Cyber Incident Response Plan in collaboration with the FBI, including outlying roles for non-federal units for incident response.
Systemic Risk
Cybercrime is a broad-reaching threat relevant to both individuals and organizations. The allure of a significant payday from successful cyber...
22:11
OSI: Lets Repeat Microsoft Lies Techrights
Two years before bagging bribes from Microsoft the OSI
published this: [PDF]
Of course it has gotten a lot worse since then. For example, consider this overt case of OSI lobbying for Microsoft in the class action lawsuit over GitHub Copilot (GPL violations). This is MICROSOFT funded. This is MICROSOFT staff. This is MICROSOFT propaganda. All this for MICROSOFT GPL VIOLATIONS. Hosted by a MICROSOFT-BRIBED OSI. They buy the OSIs platform and we know whose bank account nets those salaries.
Sometimes it feels like theres no greater foe or enemy to Open Source than the OSI itself (because of the misleading name, which complicates matters; its a powerful lobbying instrument). It literally works against its original mission, as last witnessed yesterday.
22:00
Remembering the Legacy of Trailblazing Technologist Gordon Moore IEEE Spectrum

Intel cofounder Gordon E. Moore, the man behind Moores Law, died on 24 March at the age of 94.
The IEEE Fellow was awarded the 2008 IEEE Medal of Honor for pioneering technical roles in integrated-circuit processing, and leadership in the development of MOS memory, the microprocessor computer, and the semiconductor industry.
Moore founded Intel in 1968 with computing pioneer Robert Noyce. Moore, Noyce, and other Intel engineers are credited with bringing laptop computers and numerous other electronics to millions of people thanks to their semiconductor development. Intel microprocessors now power personal computers made by major manufacturers including Dell, HP, and IBM.
Moore is best known for his 1965 prediction, which would become known as Moores Law: the observation that the number of transistors on an integrated circuit would grow exponentially while the retail cost of computers would decrease.
His original hypothesis, published in a 1965 Electronics magazine article, was that the number of transistors would double each year. His projection came true over the decade that followed. In 1975 he revised the theory and forecast that transistors would double every 18 monthsa statement that held true for several decades. Moores Law set the bar for semiconductor manufacturers and is still driving computing innovations today.
Gordon Moore, with his prediction that turned to law, captured the very gestalt of the semiconductor industry as an exponential ambition, says...
22:00
Ubuntu Talks Up Rust Kernel Programming Potential With Ubuntu 23.04 Phoronix
Ubuntu 23.04 is being talked up for how it can aide developers that want to begin programming with Rust code for Linux kernel modules. It's possible to get started with Rust kernel development on Ubuntu 23.04 thanks to its generic kernel having the necessary kernel configuration, but ultimately it's still in an early state and there isn't much to do with the stock kernel...
21:49
Law enforcement seized the Genesis Market cybercrime marketplace Security Affairs
Law enforcement seized the Genesis Market black marketplace, a platform focused on the sale of stolen credentials, as part of Operation Cookie Monster.
The FBI seized the Genesis Market, a black marketplace for stolen credentials that was launched in 2017. Genesis Market was an invite-only marketplace, but it was not complex to find invite codes online.
One of the most interesting features offered by the platform is the access to browser fingerprints that allow crooks to impersonate victims web browsers, including IP addresses, operating system data, time zones, device info, session cookies, and more.
The price for a stolen account was very cheap, paying a few dollars crooks were able to use it for a specific period. Genesis Market provided access to accounts of the most popular services, including Amazon, eBay, Facebook, Gmail, Netflix, PayPal, Spotify, and Zoom.
The seizure is part of a law enforcement operation codenamed Operation Cookie Monster.
The home page of the Genesis Market domains now shows a banner informing visitors that the FBI has executed a seizure warrant.
These seizures were possible because of international law enforcement and private sector coordination involving the partners listed below reads the banner.
The authorities are searching for information about the administrators of the platform, a circumstance that suggests that the FBI has yet to identify them.
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections:
- The Te...
21:49
Flood of malicious packages results in NPM registry DoS Help Net Security
Attackers are exploiting the good reputation and openness of the popular public JavaScript software registry NPM to deliver malware and scams, but are also simultaneously and inadvertently launching DoS attacks against the service. Malicious package on NPM pointing to a site serving malware (Source: Checkmarx) The unstoppable load created by those automated scripts made NPM unstable with sporadic Service Unavailable errors. I can witness in the past week it happened to me and my colleagues More
The post Flood of malicious packages results in NPM registry DoS appeared first on Help Net Security.
21:49
Protect Your Company: Ransomware Prevention Made Easy The Hacker News
Every year hundreds of millions of malware attacks occur worldwide, and every year businesses deal with the impact of viruses, worms, keyloggers, and ransomware. Malware is a pernicious threat and the biggest driver for businesses to look for cybersecurity solutions. Naturally, businesses want to find products that will stop malware in its tracks, and so they search for solutions to do that.
21:30
Fortinet enhances Security Fabric with real-time response and automation capabilities Help Net Security
Fortinet has expanded the Fortinet Security Fabric with new and enhanced products and capabilities to enable advanced threat prevention and coordinated response for a self-defending ecosystem across networks, endpoints, and clouds. The majority of organizations are pursuing a consolidation strategy for their security According to a recent survey from Gartner, 75 percent of organizations are pursuing security vendor consolidation, up from 29 percent in 2020. The same survey notes, Security and risk management leaders are More
The post Fortinet enhances Security Fabric with real-time response and automation capabilities appeared first on Help Net Security.
21:24
OSI Blog Composed by Microsofters on Microsofts Payroll, Promoting Proprietary GitHub Using Microsofts Terminology Techrights
Sponsored by Microsoft to occupy the OSI, serving and pushing Microsoft agenda, lobbying for proprietary software (under the guise of community!) and even painting plagiarism/GPL violations as benign "AI"
Yesterday:
This is what OSI is advocating:

Summary: Not only does Microsoft besiege the OSI's Board; it also has staff on the payroll (Microsoft's money) pushing the OSI in Microsofts direction; the OSI actively works to undermine its own mission, having taken money from (been bribed by) its foremost foe half a decade ago
21:22
Mullvad VPN And The Tor Project Collaborate On A Web Browser SoylentNews
The Tor Project and Mullvad VPN have both announced collaboration on a privacy-oriented web browser. The joint browser, which is based on Firefox, has the features of the Tor Browser but operates over the Mullvad Virtual Private Network rather than Tor's onion routers. The collaboration has helped polish interface improvements and address several long standing issues.
Mullvad and the Tor Project have been part of the same community that is dedicated to developing technology that prioritizes protecting people's right to privacy for many years now. Mullvad contributes to the Tor Project at the highest level of membership, Shallot, and were a founding member of the Tor Project's Membership Program. They approached us to help them develop their browser because they wanted to leverage our expertise to create a product that is built on the same principles and with similar safety levels as the Tor Browser -- but that works independently of the Tor network. The result is the Mullvad Browser, a free, privacy-preserving web browser to challenge the all-too-prevalent business model of exploiting people's data for profit.
and
"The mass surveillance of today is absurd. Both from commercial actors like big tech companies and from governments," says Jan Jonsson, CEO at Mullvad VPN. "We want to free the internet from mass surveillance and a VPN alone is not enough to achieve privacy. From our perspective there has been a gap in the market for those who want to run a privacy-focused browser as good as the Tor Project's but with a VPN instead of the Tor Network."
Mullvad has been an active member of the Tor project for years.
Oh, and one more thing, speaking of VPNs, buried in the actual text of Senate Bill S.686 - RESTRICT Act 118th Congress (2023-2024), hidden behind rhetoric about ByteDance and Tiktok is a ban on VPN usage.
Previously:
(2023) The
'Insanely Broad' RESTRICT Act Could Ban VPNs in the USA
(2022) Are
Virtual Private Networks Actually Private?
(2022) VPN
Providers Remove Servers From India in Wake of New Data Collection
Laws...
21:00
Classic Film Camera Goes Digital With Game Boy Tech Hackaday

Despite having been technologically obsolete for a decade or two, analog photography is still practiced by hobbyists and artists to achieve a particular aesthetic. One might imagine a similar thing happening with early digital cameras, and indeed it has: the Game Boy Camera has seen use in dozens of projects. [Michael Fitzmayer] however decided to combine the worlds of analog and early digital photography by equipping a Holga with the image sensor from a Game Boy Camera.
20:36
Zstd 1.5.5 Released With Corruption Fix, Improved Performance In Some Scenarios Phoronix
Just two months after Zstd 1.5.4 was published, Zstd 1.5.5 has algorithm implementation. Zstd 1.5.5's release is motivated by addressing a rare corruption bug fix but also has various performance optimizations...
20:16
LLVM 16.0.1 Released With Many Compiler Fixes, Backports AMD Zen 4 Scheduler Model Phoronix
It's been two weeks already since the release of LLVM 16.0 as the latest shiny feature update to this widely-used, open-source compiler stack. LLVM release manager Tom Stellard today issued LLVM 16.0.1 as the first point release with a wide collection of fixes and other maintenance work to LLVM and its contained sub-projects...
20:00
MidnightBSD 3.0.1 Released With Security Fixes, rc.d Scripts Cleanup Phoronix
Building off last month's release of MidnightBSD 3.0 for this desktop-focused, FreeBSD-forked operating system the v3.0.1 update is now available...
19:15
Take-Two Dismisses Claims Against Lead Defendants in GTA Mods Lawsuit TorrentFreak
 In 2021, a group of Grand Theft Auto enthusiast programmers
released re3 and reVC, a pair of reverse-engineered modifications
for GTA 3 and Vice City.
In 2021, a group of Grand Theft Auto enthusiast programmers
released re3 and reVC, a pair of reverse-engineered modifications
for GTA 3 and Vice City.
These projects breathed new life into games that while still fantastic, benefited greatly from significant enhancements that helped to wind back the years. Fans loved re3 and reVC but Take-Two and Rockstar Games most definitely did not.
The companies first move was to file a DMCA notice that ordered GitHub to take the projects down. The programmers response came via a DMCA counternotice which restored their projects on GitHub but left them exposed to a potential legal response by Take-Two.
Take-Two Files Copyright Lawsuit
In September 2021, Take-Two filed a lawsuit against the programmers, claiming that the aim of the projects was to create and distribute pirated versions of GTA 3 and Vice City.
The companys claims included damages for willful and malicious copyright infringement due to the illegal copying, adaption and distribution of GTA source code and other protected content. For good measure, Take-Two also demanded damages for alleged misrepresentations in the defendants DMCA counternotices.
The lawsuit listed 14 defendants, just four of which were named: Angelo Papenhoff (aap), Theo Morra, Eray Orunus, and Adrian Graber. In their November 2021 answer to the complaint, the four men denied the copyright infringement allegations and cited fair use among other affirmative defenses.
One Year Later, Limited Visible Progress
The first five months of 2022 were relatively uneventful, at least based on information made available to the public. The parties did participate in an ADR (Alternative Dispute Resolution) session but according to the mediators report early May, the case did not settle.
No further entries appeared on the docket until December 2022, when the parties informed the court that since disclosure and discovery in the lawsuit was likely to involve the production of confidential, proprietary, or private information, special protection from public disclosure may be warranted. The court had no problem with granting the request.
As part of this process, Tak...
19:12
New Strain of Rorschach Ransomware Targeting US- Firms HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
Rorschach ransomware boasts advanced encryption technology and can spread automatically on the machine if executed on a domain controller.
This is a post from HackRead.com Read the original post: New Strain of Rorschach Ransomware Targeting US- Firms
18:35
Typhon Reborn Stealer Malware Resurfaces with Advanced Evasion Techniques The Hacker News
The threat actor behind the information-stealing malware known as Typhon Reborn has resurfaced with an updated version (V2) that packs in improved capabilities to evade detection and criminal underground for $59 per month, $360 per year, or alternatively, for $540 for a lifetime subscription. "The stealer can harvest and exfiltrate
18:22
Links 05/04/2023: Fentanylware (TikTok) Fined for Abuse and German Court Orders Takedown of Free Software (Youtube-dl) Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Instructionals/Technical
-
Linux Handbook Special Variables in Bash Shell Scripting
Recently, I covered how you can use the number of arguments in bash that involved the use of the $# variable which is one of the special variables of bash.
-
University of Toronto Automated status tests need to have little or no noise
Unless youre in a bad situation, your systems are almost always working; your backups are happening properly, your mach...
-
-
18:17
STYX Marketplace emerged in Dark Web focused on Financial Fraud Security Affairs
Resecurity has recently identified the STYX Marketplace, a new cybercriminal e-commerce platform with a specialized focus on financial fraud and money laundering.
The STYX marketplace was launched at the beginning of 2023. This platform is specifically designed to facilitate financial crime, providing cybercriminals with a range of services, including stolen financial data, credit card information, forged documents, money laundering services, victim reconnaissance lookups, and more.
This discovery illustrates the post-pandemic menace of cyber-enabled financial crime and the threat it poses to financial institutions (FIs) and their customers.
The discovery of STYX coincides with Resecurity financial crime risk analysts observing a significant increase in threat actors offering money-laundering services that exploit digital banking and cryptocurrency accounts.
Cybercriminals have also started targeting new jurisdictions outside North America and the UK, including the United Arab Emirates and multiple countries in the European Union. The EU is where these types of threat actors typically set up merchant terminals and business bank accounts to facilitate money laundering in the form of cash-outs and bank drops. Typically, these tactics are used in the furtherance of online-banking account takeovers (ATOs) and credit card theft (carding), with commissions for successful cash-outs ranging from 40% to 70%.
Resecurity found that STYX has been operational for several months already, capturing a significant following in reputable c...
18:00
A NOR Gate For An ALU? Hackaday

If you know anything about he design of a CPU, youll probably be able to identify that a critical component of all CPUs is the Arithmetic Logic Unit, or ALU. This is a collection of gates that can do a selection of binary operations, and which depending on the capabilities of the computer, can be a complex component. Its a surprise then to find that a working CPU can be made with just a single NOR gate which is what is at the heart of [Dennis Kuschel]s My4th single board discrete logic computer. Its the latest in a series of machines from him using the NOR ALU technique, and it replaces hardware complexity with extra software to perform complex operations.
Aside from a refreshingly simple and understandable circuit, it has 32k of RAM and a 32k EPROM, of which about 9k is microcode and the rest program. Its called My4th because it has a Forth interpreter on board, and it has I2C and digital I/O as well as a serial port for its console.
This will never be a fast computer, but the fact that it computes at all is ts charm. In 2023 there are very few machines about that can be understood in their entirety, so this one is rather special even if its not the first 1-bit ALU weve seen.
Thanks [Ken Boak] for the tip.
17:34
IRC Proceedings: Tuesday, April 04, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-040423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-040423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-040423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-040423.gmi
Over HTTP:
|
... |
17:00
DISCOVERY Paleontologists Discover Fossil of Giant Extinct Eagle Terra Forming Terra
"Markets Will Always Outsmart The Best AI Systems That Our Computer Scientists Develop" Terra Forming Terra
Building material made with lemons and coconut could help heat a home Terra Forming Terra

War of the drones Terra Forming Terra
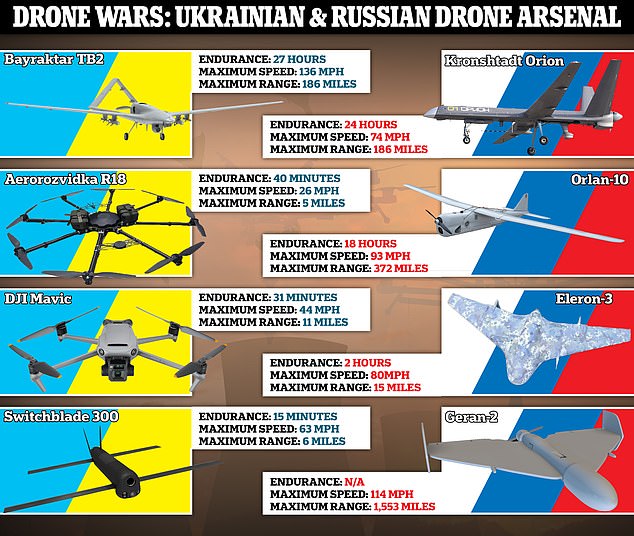
16:35
Seattle Becomes First U.S. City to Permanently Require Sick Leave for Delivery and App-based Workers SoylentNews
The Seattle City Council today unanimously approved rules providing paid sick leave for food-delivery and other on-demand, app-based gig economy workers. The city appears to be the first in the nation to permanently ensure these protections.
[...] The measure applies to workers for companies such as DoorDash, Grubhub and Uber Eats, as well as platforms providing on-demand work such as laundry services and car washing. Similar benefits already exist at the state level for ride-hailing companies including Lyft and Uber. Seattle's legislation provides a suite of sick and "safe" time benefits including paid time off for:
- an illness and preventative health care;
- if a company stops operations due to a public health emergency or other safety reason;
- due to a school closure for a family member; and
- in order to seek services for domestic violence, sexual assault or stalking.
Mosqueda sponsored the legislation and was also the lead on similar, temporary protections put in place in June 2020 to aid workers during the COVID-19 pandemic. Mayor Bruce Harrell drafted the new legislation in partnership with the council and lauded passage of the measure, according to a statement.
Read more of this story at SoylentNews.
15:47
Techrights Plans for Impending Easter Weekend Techrights
Summary: Techrights will be publishing threatening letters from trolls this coming weekend; its well overdue
LAST summer a copyright troll targeted Techrights [1, 2] and for full disclosure purposes we planned to disclose the letters some time around Christmas. Transparency is important if not paramount. Just before Christmas, however, that troll escalated a little by sending physical letters to our home, so we decided to delay this until Easter when its quieter and theres ample time to redact and preapre.
regardless of whether theres something more sinister or complicated going on behind the scenes, expect more to be published around Easter Sunday.The case itself is without merit, very obviously frivolous harassment, which we suspect may have comes from the EPO or is linked to Team UPC, which also issued some copyright threats only months ago [1, 2]. Either way, regardless of whether theres something more sinister or complicated going on behind the scenes, expect more to be published around Easter Sunday.
Techrights still attracts such self-defeating threats. Shedding light on them helps deter/discourage further attempts. That these threats are made in the first place can be rather revealing at times. That means Techrights makes an impact. Last year we covered another example of this.
15:15
Links 05/04/2023: EasyOS 5.2.1 and Shotcut 23.04; Donald Trump in Police Custody Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
GamingOnLinux ...
-
15:00
Upgrade Your Voodoo with More Memory Hackaday

In 1996, the 3Dfx VooDoo VGA chipset changed computer graphics forever. Because of the high cost of memory, most of the boards had only 4 MB of memory which seemed a lot back then. However, the chipset could actually handle up to 8 MB. [Bits and Bolts] couldnt stand that his board only had 4 MB, so he did what any good hacker would do: he figured out how to add the missing memory!
The mod has been done before using the piggyback technique, where you solder the new RAM chips on the old chips and bend out a few pins out to directly wire them to chip selects elsewhere on the board. [Bits and Bolts] didnt want to try that, so instead, he developed a PCB that slips over the chip using a socket.
Of course, this presumes the chips have enough clearance between them to fit the sockets. In addition, the board is pretty specific to a particular VGA board because each board has different memory chip layouts. The sockets also had plastic support structures that blocked the insertion, so a little surgery removed them.
The board can add more memory to either the frame buffer or the texture mapping memory. There are jumpers to set up, which you want to do.
While weve seen piggybacking done a few times weve even done it ourselves we havent thought of using a socket instead of just soldering on top of the memory. You still have to do the tiny soldering to graft the chip select, but th...
14:30
How AI is transforming cybersecurity for better and worse Help Net Security
Many sectors view AI and machine learning with mixed emotions, but for the cybersecurity industry, they present a double-edged sword. On the one hand, AI provides powerful tools for cybersecurity professionals, such as automated security processing and threat detection. On the other hand, cybercriminals have access to the same technology, making it a constant cat-and-mouse game between attackers and defenders. In this Help Net Security video, Matt Aldridge, Principal Solutions Consultant at OpenText Cyber Security, More
The post How AI is transforming cybersecurity for better and worse appeared first on Help Net Security.
14:00
Stop online counterfeiters dead in their tracks Help Net Security
During this Help Net Security interview, Nicole Hofmann, CEO at Sentryc, delves into the critical issue of counterfeiting and the detrimental impact it has on industries and brands. Hofmann sheds light on the modus operandi of counterfeiters, who operate with impunity on online marketplaces and digital sales channels, luring unsuspecting customers into purchasing fake products. Hofmann also highlights the crucial role of self-learning software in identifying and removing counterfeit products from online marketplaces, a crucial More
The post Stop online counterfeiters dead in their tracks appeared first on Help Net Security.
13:52
Ads Are Coming for the Bing AI Chatbot, as They Come for All Microsoft Products SoylentNews
Microsoft has spent a lot of time and energy over the last few months adding generative AI features to all its products, particularly its long-standing, long-struggling Bing search engine. And now the company is working on fusing this fast-moving, sometimes unsettling new technology with some old headaches: ads.
In a blog post earlier this week, Microsoft VP Yusuf Mehdi said the company was "exploring placing ads in the chat experience," one of several things the company is doing "to share the ad revenue with partners whose content contributed to the chat response." The company is also looking into ways to let Bing Chat show sources for its work, sort of like the ways Google, Bing, and other search engines display a source link below snippets of information they think might answer the question you asked.
Related:
Even the
FBI Says You Should Use an Ad Blocker (20221227)
Microsoft
Explores a Potentially Risky New Market (20220420)
Microsoft
is Testing Ads in the Windows 11 File Explorer (20220314)
Sen. Ron
Wyden Calls for an Investigation of the Ad-Blocking Industry
(20200115)
Windows 10
App Starts Showing Ads, Microsoft Says You Can't Remove Them
(20191215)
Microsoft
Experiments with Ads in Windows Email (20181117)
Read more of this story at SoylentNews.
13:30
The high cost of insecure authentication methods Help Net Security
Insecure authentication is a primary cause of cyber breaches, and that cumbersome login methods take an unacceptable toll on employees and business productivity, according to HYPR. Respondents indicate that a passwordless approach would increase productivity (45%), improve user experience (86%), strengthen security (86%) and accelerate adoption of multi-factor authentication (42%). Insecure authentication methods still in use The report findings make it evident that maintaining the status quo is a risky proposition all around, said Bojan More
The post The high cost of insecure authentication methods appeared first on Help Net Security.
13:00
Re-evaluating immature and ineffective insider risk management programs Help Net Security
Managing insider risk is becoming increasingly difficult. In fact, insider risk is emerging as one of the most challenging threats to detect, mitigate and manage, according to Code42. Although more than 72% of companies indicate they have an Insider Risk Management (IRM) program in place, the same companies experienced a year-over-year increase in data loss incidents of 32%, and 71% expect data loss from insider events to increase in the next 12 months. With insider More
The post Re-evaluating immature and ineffective insider risk management programs appeared first on Help Net Security.
12:20
F5 protects digital services with AI-powered app and API security capabilities Help Net Security
F5 has unveiled new security capabilities to give customers comprehensive protection and control in managing apps and APIs across on-premises, cloud, and edge locations. Specifically, new machine learning enhancements provide F5s cloud security portfolio with advanced API endpoint discovery, anomaly detection, telemetry, and behavioral analysis. As more transactions and customer engagements occur through digital channels such as web and mobile apps, organizations are seeking better solutions to provide secure experiences for their end users and More
The post F5 protects digital services with AI-powered app and API security capabilities appeared first on Help Net Security.
12:16
Troubleshooting Linux performance, building a golden image for your RHEL homelab, and more tips for sysadmins Linux.com
Check out Enable Sysadmins top 10 articles from March 2023.
Read More at Enable Sysadmin
The post Troubleshooting Linux performance, building a golden image for your RHEL homelab, and more tips for sysadmins appeared first on Linux.com.
12:10
Akamai introduces new premium offering and updated managed security service program Help Net Security
Akamai introduced an updated managed security service program and premium service offerings. The new capabilities are intended to help customers protect their businesses 247 from the most sophisticated attacks with proactive monitoring and rapid response in the event of a cyberattack. Customers can take advantage of access to more Akamai security experts, reduced pricing, and more available for customers seeking personalized support and prioritized More
The post Akamai introduces new premium offering and updated managed security service program appeared first on Help Net Security.
12:00
Reshoring Vacuum Tube Manufacturing, One Tube at a Time Hackaday

For most of us, vacuum tubes havent appeared in any of our schematics or BOMs in well, ever. Once mass-manufacturing made reliable transistors cheap enough for hobbyists, vacuum tubes became pretty passe, and it wasnt long before the once mighty US tube industry was decimated, leaving the few remaining tube enthusiasts to ferret out caches of old stock, or even seek new tubes from overseas manufacturers.
However, all that may change if [Charles Whitener] succeeds in reshoring at least part of the US vacuum tube manufacturing base. He seems to have made a good start, having purchased the Western Electric brand from AT&T and some of its remaining vacuum tube manufacturing equipment back in 1995. Since then, he has been on a talent hunt, locating as many people as possible who have experience in the tube business to help him gear back up.
The new Western Electric, now located in Rossville, Georgia, is currently manufacturing 300B power triodes and marketing them as a premium product aimed primarily at the audiophile market. A matched pair of tubes in a cherry wood pr...
11:39
[Meme] Unitary Patent and Unified Patent Court (UPC): Doing a Putin on European Patent Courts Techrights
Summary: Desperate to overcome legal barriers (i.e. to break the law) and impose European software patents on the whole of the EU, Benot Battistelli and Antnio Campinos have worked to dismantle European patent courts, replacing them with an organ that the EPO controls and can compel to hide the surging invalidity rates (at the expense of the EUs credibility and reputation; remember that the EPO is partly outsourced to Belarus)
11:25
Union Syndicale Fdrale (USF) Takes a Closer Look at the EPO and Worsening Staff Conditions in a Series of New Articles Techrights
Agora has devoted a lot of space to the matter
Summary: Last month Union Syndicale Fdrale spoke out in support of EPO workers who have felt besieged and abused by Benot Battistelli and Antnio Campinos since 2010; below one can find a new batch of articles related to the matter
-
Precarity at the European Patent Office
Due to the highly specific technical and legal skills requested from the majority of staff at the EPO, it has long been considered that fixed-term contracts were not the appropriate form of employment for this Office. The need of a lengthy and thorough training of new employees is a condition sine qua non to grant quality patents. This necessary time and resources investment could be lost for the organisation if fixed-term contracts were the norm, let alone the knowledge accumulated and shared by the newly recruited staff. Furthermore, at the individual level, a Golden Cage Syndrome exists at the EPO, since after some years of employment, staff tend to specialise in the field of patents and lose their general expertise. The expertise in the field of patents is not easily recognised in other fields. Staff leaving the EPO after some years of employment could find it very difficult to find employment elsewhere at comparable conditions. These considerations were valid in the past and are still valid today.
-
Social Security at the EPO: an overview
The EPO, the second largest European organisation after the Commission in terms of the number of employees, is a substantially independent body, which is neither part of the European Union nor attached to it in any way like the EU agencies. Its member states include the 27 EU member states, but also 11 non-EU states. It is also not one of the Coordinated Organisations, although some...
11:06
Scientists Capture Deepest-Ever Footage of a Fish SoylentNews
Researchers using baited camera traps recorded an unknown species of snailfish more than 5 miles (8 kilometers) deep just off the coast of Japan. These are the deepest fish ever caught on film.
A team with the Tokyo University of Marine Science and Technology and the University of Western Australia recently released the footage, which was collected in September 2022 in the Izu-Ogasawara Trench, which is just south of Japan. Cameras captured the unknown snailfish that belongs to the genus Pseudoliparis at 8,336 meters (5.1 miles) underwater, according to a press release from the University of Western Australia.
[...] The snailfish found in the Izu-Ogasaware Trench do not have any scales. They're covered in a gelatinous layer and do not have a swim bladder like other fish species do, The Guardian reports. This allows them to live under the extreme pressure found in the deepest parts of the ocean.
The expedition was part of a 10-year study into the deepest fish population on the planet. Researchers set out to study the Izu-Ogasaware, Ryukyu, and Japan trenchesall of which are over 7,000 meters (4.3 miles) deep. According to researchers, the recently released images show how different the Pacific Ocean's trenches are to others around the world. Alan Jamieson, a chief scientist in the expedition, explained in the UWA release that, in the Mariana Trench, the deeper researchers look, the less fish there are. But in the trenches around Japan, there are a lot of fish to be found even at extreme depths.
Read more of this story at SoylentNews.
11:00
Microsoft Layoffs Now in Bay Area (California) Techrights
Summary: Everyone seems to be talking about Apple layoffs this week, but 6 hours ago it was said that Microsoft [et al] have revealed plans for fresh Bay Area job cuts, together adding hundreds of workers to the regions worsening layoffs.
11:00
IBM unveils new options to help clients reach their sustainability goals Help Net Security
IBM has unveiled new single frame and rack mount configurations of IBM z16 and IBM LinuxONE 4, expanding their capabilities to a broader range of data center environments. Based on IBMs Telum processor, the new options are designed with sustainability in mind for highly efficient data centers, helping clients adapt to a digitized economy and ongoing global uncertainty. Introduced in April 2022, the IBM z16 multi frame has helped transform industries with real-time AI inferencing More
The post IBM unveils new options to help clients reach their sustainability goals appeared first on Help Net Security.
10:45
Desktop/Laptop Operating System Market Share in Ukraine: Windows Down From 90% to 82% in One Year Techrights
The latest on Ukraine (OS battle)
Summary: Microsofts invasion of Ukraine is not working anymore; GNU/Linux is growing there (not counting Android and ChromeOS, which arent freedom-respecting but run Linux), threatening Microsofts monopoly rents
10:25
How to Teach Your Child Coding: A Gift for Their Digital Future HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
Let's code, kids!
This is a post from HackRead.com Read the original post: How to Teach Your Child Coding: A Gift for Their Digital Future
10:13
NEW 'Off The Wall' ONLINE 2600 - 2600: The Hacker Quarterly
NEW 'Off The Wall' ONLINE
Posted 05 Apr, 2023 0:13:30 UTC
The new edition of Off The Wall from 04/04/2023 has been archived and is now available online.
10:00
HPR3828: The Oh No! News. Hacker Public Radio
The Oh No! news. Oh No! News is Good News. Threat analysis; your attack surface. Article: CISA warns of actively exploited Plex bug after LastPass breach. Author: Sergiu Gatlan (2023, Mar 11). Attackers with "admin access to a Plex Media Server could abuse the Camera Upload feature to make the server execute malicious code," according to an advisory published by the Plex Security Team in May 2020 when it patched the bug with the release of Plex Media Server 1.19.3. "This could be done by setting the server data directory to overlap with the content location for a library on which Camera Upload was enabled. This issue could not be exploited without first gaining access to the server's Plex account." Link to Cybersecurity & Infrastructure Security Agency (CISA). Supporting Article: Plex Security, regarding security vulnerability CVE-2020-5741. Author: PlexSecurity, Plex Employee. (2020, May). We have recently been made aware of a security vulnerability related to Plex Media Server. This issue allowed an attacker with access to the server administrator’s Plex account to upload a malicious file via the Camera Upload feature and have the media server execute it. Supporting Article: Official statement from Plex, concerning vulnerabilities, on LastPass Data Breach. Author: PlexInfo, Plex Employee. (2023, Feb 28). "We have not been contacted by LastPass so we cannot speak to the specifics of their incident. We take security issues very seriously, and frequently work with external parties who report issues big or small using our guidelines and bug bounty program. When vulnerabilities are reported following responsible disclosure we address them swiftly and thoroughly, and we’ve never had a critical vulnerability published for which there wasn’t already a of our own, we’ve always chosen to communicate them quickly. We are not aware of any unpatched vulnerabilities, and as always, we invite people to disclose issues to us following the guidelines linked above. Given recent articles about the LastPass incident, although we are not aware of any unpatched vulnerabilities, we have reached out to LastPass to be sure." Supporting Article: LastPass says employee’s home computer was hacked and corporate vault taken. Author: Dan Goodin. (2023, Feb 27). According to a person briefed on a private report from LastPass who spoke on the condition of anonymity, the media software package that was exploited on the employee’s home computer was Plex. Interestingly, Plex rep
Transgender Careers in the Software Industry It Will Never Work in Theory
If the true measure of a society is how it treats its weakest members, the true measure of a profession is how much it does to protect them. Software engineering does poorly by that standard: despite decades of hand-wringing, women and some racialized minorities are still often made to feel unwelcome, and programmers continue to build systems that codify discrimination against them.
This recent paper looks at the experiences of transgender people in our industry. They are still frequently discriminated against, but many find programming to be a safer career than other options, in part because of its early and widespread adoption of remote work. With far-right politicians in the United States and elsewhere stirring up transphobic hysteria, work like this helps us see where we are and how far we have to go.
If you'd like to know more, please watch this moving talk by Naomi Ceder.
Ronnie de Souza Santos, Brody Stuart-Verner, and Cleyton Magalhes. What do transgender software professionals say about a career in the software industry? IEEE Software, pages 16, 2023. doi:10.1109/ms.2023.3257743.
Diversity is an essential aspect of software development because technology influences almost every aspect of modern society, and if the software industry lacks diversity, software products might unintentionally constrain groups of individuals instead of promoting an equalitarian experience to all. In this study, we investigate the perspectives of transgender software professionals about a career in software engineering as one of the aspects of diversity in the software industry. Our findings demonstrate that, on the one hand, trans people choose careers in software engineering for two primary reasons: a) even though software development environments are not exempt from discrimination, the software industry is safer than other industries for transgenders; b) trans people occasionally have to deal with gender dysphoria, anxiety, and fear of judgment, and the work flexibility offered by software companies allow them to cope with these issues more efficiently.
09:46
Rilide Malware New Crypto Stealer Hits Chromium-Based Browsers HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
The Chromium-based browsers include Google Chrome, Microsoft Edge, Brave, Opera, Vivaldi, and several others.
This is a post from HackRead.com Read the original post: Rilide Malware New Crypto Stealer Hits Chromium-Based Browsers
09:13
Behind the scenes of running Linux kernel Mentorship Programs Linux.com

Read the original blog at Read More
The post Behind the scenes of running Linux kernel Mentorship Programs appeared first on Linux.com.
08:21
Firefox Will Support Windows 7/8 Until at Least 2024 SoylentNews
Mozilla won't abandon Microsoft's tried and tested platform anytime soon:
The Extended Support Release (ESR) of Firefox will keep supporting Windows 7 and Windows 8.1 until at least until 2024. Mozilla programmer Mike Kaply confirmed the decision through the Bugzilla platform, stating that the corporation "will not be ending support for Windows 7/Windows 8 before the release of the Firefox 115 ESR," and that the Firefox 115 ESR release will support the aged operating systems "at least until 3Q 2024."
Mike Kaply also hinted at the fact that Mozilla still has to decide exactly when support for Windows 7/8 will be finally removed. Firefox ESR is stable release of the open-source browser which Mozilla supports for an extended period of time compared to regular, "rapid" releases coming out every month. During its incremental updates containing security fixes with no new features or performance enhancements.
As stated by Firefox's official release calendar, Firefox 115 ESR should come out on July 4, 2023. The Firefox Public Data Report also reveals that Windows 7 still provides a sizable portion of the overall Firefox userbase (13.44%), while Windows 10 is the leading platform with 71% of users. The much-maligned Windows 8.1 is still used by 2.3% of Firefox installations.
[...] Windows 7 was already abandoned by Google Chrome (and other Chromium-based browsers), which doesn't run on the OS anymore starting from Chrome 110. Microsoft ended support for Windows 7 and Windows 8 in January 2023, and Valve will do the same with Steam on January 1, 2024.
Are you one of the 13.44%?
Read more of this story at SoylentNews.
08:17
Enough is Enough. Tell Congress to Ban Federal Use of Face Recognition Deeplinks
Cities and counties across the country have banned government use of face surveillance technology, and many more are weighing proposals to do so. From Boston to San Francisco, Jackson, Mississippi to Minneapolis, elected officials and activists know that face surveillance gives police the power to track us wherever we go. It also disproportionately impacts people of color, turns us all into perpetual suspects, increases the likelihood of being falsely arrested, and chills peoples willingness to participate in first amendment protected activities. Even Amazon, known for operating one of the largest video surveillance networks in the history of the world, extended its moratorium on selling face recognition to police.
Now, Congress must do its part. Weve
created a
campaign that will easily allow you to
contact your elected federal officials and tell them to support
the
Facial R...
07:20
Chrome 112 Released With WASM Garbage Collection Trial, CSS Nesting Phoronix
Google today promoted the Chrome 112 web browser to their stable channel on all supported platforms...
07:04
FBI Seizes Bot Shop Genesis Market Amid Arrests Targeting Operators, Suppliers Krebs on Security
Several domain names tied to Genesis Market, a bustling cybercrime store that sold access to passwords and other data stolen from millions of computers infected with malicious software, were seized by the Federal Bureau of Investigation (FBI) today. The domain seizures coincided with more than a hundred arrests in the United States and abroad targeting those who allegedly operated the service, as well as suppliers who continuously fed Genesis Market with freshly-stolen data.

Several websites tied to the cybercrime store Genesis Market had their homepages changed today to this seizure notice.
Active since 2018, Genesis Markets slogan was, Our store sells bots with logs, cookies, and their real fingerprints. Customers could search for infected systems with a variety of options, including by Internet address or by specific domain names associated with stolen credentials.
But earlier today, multiple domains associated with Genesis had their homepages replaced with a seizure notice from the FBI, which said the domains were seized pursuant to a warrant issued by the U.S. District Court for the Eastern District of Wisconsin.
The U.S. Attorneys Office for the Eastern District of Wisconsin did not respond to requests for comment. The FBI declined to comment.
Update, April 5, 11:40 a.m. ET: The U.S. Department of Justice just released a statement on its investigation into Genesis Market. In a press briefing this morning, FBI and DOJ officials said the international law enforcement investigation involved 14 countries and resulted in 400 law enforcement actions, including 119 arrests and 208 searches and interviews worldwide. The FBI confirmed that some American suspects are among those arrested, although officials declined to share more details on the arrests.
The DOJ said investigators were able to access the user database for Genesis Market, and found the invite-only service had more than 59,000 registered users. The database contained the purchase and activity history on all users, which the feds say helped them uncover the true identities of many users.
Original story: But sources close to the investigation tell KrebsOnSecurity that law enforcement agencies in the United States, Canada and across Europe are current...
06:55
RADV Lands Shader Caching For Graphics Pipeline Libraries Phoronix
Ahead of hopefully enabling the RADV Vulkan Graphics Pipeline Libraries "GPL" support by default for this quarter's Mesa 23.1 release, the RADV driver has now landed on-disk shader caching support for GPL libraries...
06:41
ALPHV/BlackCat ransomware affiliate targets Veritas Backup solution bugs Security Affairs
An ALPHV/BlackCat ransomware affiliate was spotted exploiting vulnerabilities in the Veritas Backup solution.
An affiliate of the ALPHV/BlackCat ransomware gang, tracked as UNC4466, was observed exploiting three vulnerabilities in the Veritas Backup solution to gain initial access to the target network.
Unlike other ALPHV affiliates, UNC4466 doesnt rely on stolen credentials for initial access to victim environments. Mandiant researchers first observed this affiliate targeting Veritas issues in the wild on October 22, 2022. Below is the list of flaws exploited by the ransomware gangs affiliate:
- CVE-2021-27876: The communication between a client and an Agent requires successful authentication, which is typically completed over a secure TLS communication. However, due to a vulnerability in the SHA Authentication scheme, an attacker is able to gain unauthorized access and complete the authentication process. Subsequently, the client can execute data management protocol commands on the authenticated connection. By using crafted input parameters in one of these commands, an attacker can access an arbitrary file on the system using System privileges.. (CVSS score: 8.1).
- CVE-2021-27877: An issue was discovered in Veritas Backup Exec before 21.2. It supports multiple authentication schemes: SHA authentication is one of these. This authentication scheme is no longer used in current versions of the product, but hadnt yet been disabled. An attacker could remotely exploit this scheme to gain unauthorized access to an Agent and execute privileged commands. (CVSS score: 8.2).
- CVE-2021-27878: An issue was discovered in Veritas Backup Exec before 21.2. The communication between a client and an Agent requires successful authentication, which is typically completed over a secure TLS communication. However, due to a vulnerability in the SHA Authentication scheme, an attacker is able to gain unauthorized access and complete the authentication process. Subsequently, the client can execute data management protocol commands on the authenticated connection. The attacker could use one of these commands to execute an arbitrary command on the system using system privileges. (CVSS score: 8.8)
The three flaws were addressed with the release of version 21.2 in March 2021, but many public-facing endpoints are yet to be updated. The researchers identified over 8,500 installations of Veritas Backup Exec instan...
06:27
Smart Locks Endanger Tenants Privacy and Should Be Regulated Deeplinks
The growing deployment of smart locks in apartments, often installed without tenants permission, has created a new stream of sensitive location data for law enforcement, landlords, and private companies. Tenants should not be forced to submit to tracking just to enter their home. At minimum, we need privacy laws that require consent to collect this data, a warrant for police access, and strong data minimization.
Smart locks come in many forms. At the most basic level, they are physical locks that can be opened with a nontraditional key like a smartphone or fingerprint. Most significantly from a privacy perspective, they allow the lock company (and sometimes landlords) to collect data each time you or any of your guests unlock your physical door. To do this, the locks themselves may be connected to the internet, or they can rely on an app you must install on your phone (the key) to transmit the data to the lock companys servers. Depending on the model, the lock might also record other datalike an image of the person trying to unlock the door.
Smart locks have become increasingly popular in recent years, specifically with landlords. For example, in 2019, tenants in New York City forced a settlement after a landlord attempted to require tenants to use smart locks. The settlement required an option for physical keys. The smart lock at issue in that case was made by a company called Latch. While Latch was not named in the lawsuit, the company changed its privacy policy to remove reference to marketing and collection of other location data. Its software is reportedly in more than 125,000 dwelling units or commercial spaces. Many other companies make smart locks as well. They are part of the growth of smart home devices.
Privacy risks from smart locks
Despite their convenience to some people, smart locks can create a revealing data trail that raises concerns about law enforcement power, data privacy, and information security.
This data could give law enforcement a powerful new stream of data to be obtained without your knowledge. Companies tend to store this kind of data for much longer than necessary, and it i...
05:50
[$] Mobian: bringing Debian to mobile devices LWN.net
Mobian is a project that aims to bring the Debian distribution to mobile devices such as smartphones and tablets. By building on the flexibility, stability, and community-driven development of Debian, Mobian aspires to create a powerful and user-friendly alternative to existing mobile operating systems. The project is actively working on reducing the delta between Mobian and Debian, and its ultimate goal is to be absorbed back into its parent distribution and to make it easy to run Debian on mobile devices.
05:36
BuzzFeed is Quietly Publishing Whole AI-Generated Articles, Not Just Quizzes SoylentNews
These read like a proof of concept for replacing human writers:
Earlier this year, when BuzzFeed announced plans to start publishing AI-assisted content, its CEO Jonah Peretti promised the tech would be held to a high standard.
"I think that there are two paths for AI in digital media," Peretti told CNN. "One path is the obvious path that a lot of people will do but it's a depressing path using the technology for cost savings and spamming out a bunch of SEO articles that are lower quality than what a journalist could do, but a tenth of the cost."
[...] Indeed, the first AI content BuzzFeed published a series of quizzes that turned user input into customized responses were an interesting experiment, avoiding many of the missteps that other publishers have made with the tech.
It doesn't seem like that commitment to quality has held up, though. This month, we noticed that with none of the fanfare of Peretti's multiple interviews about the quizzes, BuzzFeed quietly started publishing fully AI-generated articles that are produced by non-editorial staff and they sound a lot like the content mill model that Peretti had promised to avoid.
[...] A BuzzFeed spokesperson told us that the AI-generated pieces are part of an "experiment" the company is doing to see how well its AI writing assistance incorporates statements from non-writers.
The linked article includes many laughable examples of bland and similar phrases in multiple stories published on the site.
Previously: BuzzFeed Preps AI-Written Content While CNET Fumbles
Read more of this story at SoylentNews.
04:35
The Decades of Evidence That Antidepressants Cause Mass Shootings cryptogon.com
Via: The Forgotten Side of Medicine: Prior to the Covid vaccinations, psychiatric medications were the mass-prescribed medication that had the worst risk-to-benefit ratio on the market. In addition to rarely providing benefits to patients, there is a wide range of severe complications that commonly result from psychiatric medications. There are many serious issues with []
04:00
CentOS Hyperscale SIG Now Has An Intel-Optimized Repository Phoronix
The CentOS Hyperscale special interest group that is focused on providing new packages and features atop CentOS Stream for use by hyperscalers like Meta and Twitter have now established a "hyperscale-intel" repository for Intel-optimized packages...
03:47
Rorschach ransomware has the fastest file-encrypting routine to date Security Affairs
A new ransomware strain named Rorschach ransomware supports the fastest file-encrypting routine observed to date.
Check Point Research (CPR) and Check Point Incident Response Team (CPIRT) researchers detected a previously unknown ransomware strain, dubbed Rorschach ransomware, that was employed in attack against a US-based company.
The experts pointed out that the Rorschach ransomware appears to be unique. According to the report published by Check Point, Rorschach is one of the fastest ransomware observed to date.
The researchers conducted five separate encryption speed tests in a controlled environment (with 6 CPUs, 8192MB RAM, SSD, and 220000 files to be encrypted), limited to local drive encryption only. Below are the results of the tests:
| Ransomware | Average approximate time of encryption |
| LockBit v.3 | 7 minutes |
| Rorschach | 4 minutes, 30 seconds |
It turned out that we have a new speed demon in town. Whats
even more noteworthy is that the Rorschach ransomware is highly
customizable. By adjusting the number of encryption threads via the
command line argument --thread, it can achieve
even faster times. reads the
analysis published by CheckPoint.
It turned out that we have a new speed demon in town. Whats even
more noteworthy is that the Rorschach ransomware is highly
customizable. By adjusting the number of encryption threads via the
command line argument --thread, it can achieve
even faster times.
The malware is highly customizable and contains unique functions, such as the use of direct syscalls.
Attackers use DLL side-loading of a Cortex XDR Dump Service Tool, a signed commercial security product, to deploy the ransomware.
The Rorschach ransomware uses the following files:
- cy.exe Cortex XDR Dump Service
- winutils.dll Packed Rorschach loader and injector, used to decrypt and inject the ransomware.
- config.ini Encrypted Rorschach ransomware which contains all the logic and configuration.
Upon execution of cy.exe, due to DLL side-loading, the loader/injector winutils.dll is loaded into memory and runs in the context of cy.exe. The main Rorschach payload config.ini is subsequently loaded into memory as well, decrypted and injected into notepad.exe, where the ransomware logic begins. continues the...
03:11
The Broad, Vague RESTRICT Act Is a Dangerous Substitute for Comprehensive Data Privacy Legislation Deeplinks
The recently introduced RESTRICT Act (S. 686, Sen. Warner and Sen. Thune) rightfully is causing a lot of concern. This bill is being called a TikTok ban, but its more complicated than that. As we wrote in our initial review of the bill, the RESTRICT Act would authorize the executive branch to block transactions and holdings of foreign adversaries that involve information and communication technology and create undue or unacceptable risk to national security and more.
We've explained our opposition to the RESTRICT Act
and urged everyone who agrees to take action against it. But we've
also been asked to address some of the concerns raised by others.
We do that here in this post.
At its core, RESTRICT would exempt certain information services from the federal statute, known as the Berman Amendments, which protects the free flow of information in and out of the United States and supports the fundamental freedom of expression and human rights concerns. RESTRICT would give more power to the executive branch and remove many of the commonsense restrictions that exist under the Foreign Intelligence Services Act (FISA) and the aforementioned Berman Amendments.
But S. 686 also would do a lot more.
EFF opposes the bill, and encourages you to reach out to your representatives to ask them not to pass it. Our reasons for opposition are primarily that this bill is being used as a cudgel to protect data from foreign adversaries, but under our current data privacy laws, there are many domestic adversaries engaged in manipulative and invasive data collection as well. Separately, handing relatively unchecked power over to the executive branch to make determinations about what sort of information technologies and technology services are allowed to enter the U.S. is dangerous. If Congress is concerned about foreign powers collecting our data, it should focus on comprehensive consumer data privacy legislation that will have a real impact, and protect our data no matter what platform its onTikTok, Facebook, Twitter, or anywhere else that profits from our private information. Thats why EFF supports...
Tuesday, 04 April
21:21
Mr Green Review 2022 Nz$100 Bonus + 200 Free Spins! Read More! h+ Media
Mr Green Review 2022 Nz$100 Bonus + 200 Free Spins! Read More!
We are all the time on the lookout for ways to provide a 5-star service and expertise if you have particular feedback for us then wed be grateful if you could get in touch with us to tell us. They have one of many absolut worst customor service ive ever seen in an organization, not simply betting company however firm in genneral. Thank you Marc for taking the time to provide us with such an quantity of detailed feedback. If its, its insulting to experienced prospects and it is deception to the newbies. Adopt responsible gambling habits and search help immediately should you develop problems.
For instance, you could come across a very beneficiant welcome bonus, only for it to transpire later that the wagering requirement was 65x. This means you would wish to play the bonus value sixty five times earlier than you would really get to it. Remember that theres no obligation to accept any bonus whenever you join an online on line casino. Its at all times price looking at the reside supplier game choice.
When it is time to confirm your account, the casino will send you an e-mail to your personal e mail handle, so make sure to examine your inbox frequently. As standard process, the casino would need identification documentation, proof of residential address and generally even proof of fee technique, however this will likely vary from customer to customer. While the Mr. Green website interface could do with some work, the casino section is brimming with quality slots and desk games. Furthermore, the awards the operator has gained contributes to the notion that they are the place theyre in the gambling business for a cause. Mr. Greens casino is totally a safe on-line gambling route for punters to pursue. By downloading this app, youll enjoy a particular cell foyer thats designed to provide the best performance in your gaming.
This is because theyre little used in comparability with iOS and Android. Even so, there are web sites that can be accessed out of your Windows telephone as well. Nowadays you presumably can deposit, increase or cut back the bets, choose the paylines and wager easily from your mobile, with none downside. The second possibility is to use the demo or practice mode on the casino sites or of their purposes. When you are ready to move on to the real sport , you are in a place to do it with a easy click on of a button.
That means that you can relax and enjoy the protected, authentic atmosphere of the elegant European online casino. You can make the most of the stay chat, work together with sellers in table games, e-mail them or contact them by cellphone between 6 am and Midnight. MrGreen.com has an excellent popularity for delivering quick and efficient customer support that goes above and beyond for his or her gamers. Of course, theres that enjoyable part were all hoping for, withdrawal of...