| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Saturday, 25 March
01:57
IRC Proceedings: Thursday, March 23, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-230323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-230323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-230323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-230323.gmi
Over HTTP:
|
... |
01:48
AMD FidelityFX Super Resolution 3 "FSR 3" Will Be Open-Source Phoronix
AMD has been teasing FidelityFX Super Resolution 3 (FSR3) as the later in the year. AMD began showing off FSR 3 to game developers this week at GDC while also re-affirming their open-source commitment...
01:30
Intel Arc Graphics Show Good Potential For Linux Workstation OpenGL Performance Phoronix
Recently I provided a fresh look at the Intel Arc Graphics Linux gaming performance with the newest open-source drivers. While it was a letdown with some of the newer Steam Play games still not working due to current limitations of the Intel "ANV" open-source Vulkan driver and some Vulkan performance issues in other titles, one area that stood out was the very good Linux OpenGL performance. That made me curious to look at the workstation OpenGL performance for Intel Arc Graphics, which is the focus of today's testing.
01:28
[$] User-space shadow stacks (maybe) for 6.4 LWN.net
Support for shadow stacks on the x86 architecture has been long in coming; LWN first covered this work in 2018. After five years and numerous versions, though, it would appear that user-space shadow stacks on x86 might just be supported in the 6.4 kernel release. Getting there has required a few changes since we last caught up with this work in early 2022.
01:15
Wine's VKD3D 1.7 Implements More Direct3D 12 Functionality Atop Vulkan Phoronix
Not to be confused with Valve's downstream, VKD3D-Proton, that is used by Steam Play but Wine's VKD3D codebase itself is out today implementation...
01:04
Links 24/03/2023: Social Control Media Bans Advancing Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Digital Restrictions (DRM)
- Monopolies
-
GNU/Linux
-
Desktop/Laptop
-
Unix Men Switching To Linux Mint: The Benefits and Drawbacks
Deciding to spend hundreds of dollars on new hardware be it a laptop or a desktop component is always a tough call. You might spend hours considering your options and working out the budget.
But its also natural to think about all the money you spent buying, upgrading, and maintaining your current setup. Your desktop or laptop might not be broken. Rather, it might not be performing as well as you think it should.
Installing a...
-
-
01:00
This Week in Security: USB Boom! Acropalypse, and a Bitcoin Heist Hackaday

Weve covered a lot of sketchy USB devices over the years. And surely you know by now, if you find a USB drive, dont plug it in to your computer. Theres more that could go wrong than just a malicious executable. Weve covered creative and destructive ideas here on Hackaday, from creative firmware to capacitors that fry a machine when plugged in. But what happened to a handful of Ecuadorian journalists was quite the surprise. These drives went out with a bang.
That is, they literally exploded. The drives each reportedly contained a pellet of RDX, a popular explosive in use by militaries since the second World War. There have been five of these hyperactive USB devices located so far, and only one actually detonated. It seems that one only managed to trigger half of its RDX payload. Because of this, and the small overall size of a USB drive, the explosion was more comparable to a firecracker than a bomb.
Mr Self Destruct v1 pic.twitter.com/aFloN5VGKI
MG (@_MG_) October 6, 2017
...
00:44
Journalist Targeted in USB Drive Bombing Attack HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
According to the attorney general of Ecuador, a terrorism investigation has been launched after the incident took place in the country.
This is a post from HackRead.com Read the original post: Journalist Targeted in USB Drive Bombing Attack
00:40
Malicious Python Package Uses Unicode Trickery to Evade Detection and Steal Data The Hacker News
A malicious Python package on the Python Package Index (PyPI) repository has been found to use Unicode as a trick to evade detection and deploy an info-stealing malware. The package in question, named onyxproxy, was uploaded to PyPI on March 15, 2023, and comes with capabilities to harvest and exfiltrate credentials and other valuable data. It has since been taken down, but not before attracting
00:34
Security updates for Friday LWN.net
Security updates have been issued by Debian (chromium, libdatetime-timezone-perl, and tzdata), Fedora (flatpak and gmailctl), Mageia (firefox, flatpak, golang, gssntlmssp, libmicrohttpd, libtiff, python-flask-security, python-owslib, ruby-rack, thunderbird, unarj, and vim), Red Hat (firefox, kpatch-patch, nss, openssl, and thunderbird), SUSE (containerd, hdf5, qt6-base, and squirrel), and Ubuntu (amanda, gif2apng, graphviz, and linux, linux-aws, linux-azure, linux-gcp, linux-ibm, linux-kvm, linux-lowlatency, linux-oracle, linux-raspi).
00:06
Ring of Life? Terminator Habitability around M-dwarfs Centauri Dreams Imagining and Planning Interstellar Exploration
It would come as no surprise to readers of science fiction that the so-called terminator region on certain kinds of planets might be a place where the conditions for life can emerge. Im talking about planets that experience tidal lock to their star, as habitable zone worlds around some categories of M-dwarfs most likely do. But I can also go way back to science fiction read in my childhood to recall a story set, for example, on Mercury, then supposed to be locked to the Sun in its rotation, depicting humans setting up bases on the terminator zone between broiling dayside and frigid night.
Addendum: Can you name the science fiction story Im talking about here? Because I cant recall it, though I suspect the setting on Mercury was in one of the Winston series of juvenile novels I was absorbing in that era as a wide-eyed kid.
The subject of tidal lock is an especially interesting one because we have candidates for habitable planets around stars as close as Proxima Centauri, if indeed a possibly tidally locked planet can sustain clement conditions at the surface. Planets like this are subject to extreme conditions, with a nightside that receives no incoming radiation and an irradiated dayside where greenhouse effects might dominate depending on available water vapor. Even so, moderate temperatures can be achieved in models of planets with oceans, and most earlier work has gone into modeling water worlds. I also think its accurate to say that earlier work has focused on how habitable conditions might be maintained in the substellar eye region directly facing the star.
But what about planets that are largely covered in land? Its a pointed question because a new study in The Astrophysical Journal finds that tidally locked worlds mostly covered in water would eventually become saturated by a thick layer of vapor. The study, led by Ana Lobos (UC-Irvine) also finds that plentiful land surfaces produce a terminator region that could well be friendly to life even if the equatorial zone directly beneath the star on the dayside should prove inhospitable. Says Lobo:
...We are trying to draw attention to more water-limited planets, which despite not having widespread oceans, could have lakes or other smaller bodies of liquid water, and these climates could actually be very promising.
00:01
Fourier Transformations Reveal How AI Learns Complex Physics SoylentNews
Fourier Transformations Reveal How AI Learns Complex Physics:
One of the oldest tools in computational physics a 200-year-old mathematical technique known as Fourier analysis can reveal crucial information about how a form of artificial intelligence called a deep neural network learns to perform tasks involving complex physics like climate and turbulence modeling, according to a new study.
In the paper, Hassanzadeh, Adam Subel and Ashesh Chattopadhyay, both former students, and Yifei Guan, a postdoctoral research associate, detailed their use of Fourier analysis to study a deep learning neural network that was trained to recognize complex flows of air in the atmosphere or water in the ocean and to predict how those flows would change over time. Their analysis revealed "not only what the neural network had learned, it also enabled us to directly connect what the network had learned to the physics of the complex system it was modeling," Hassanzadeh said.
"Deep neural networks are infamously hard to understand and are often considered 'black boxes,'" he said. "That is one of the major concerns with using deep neural networks in scientific applications. The other is generalizability: These networks cannot work for a system that is different from the one for which they were trained."
Hassanzadeh's team first performed the Fourier transformation on the equation of its fully trained deep-learning model. Each of the model's approximately 1 million parameters act like multipliers, applying more or less weight to specific operations in the equation during model calculations. In an untrained model, parameters have random values. These are adjusted and honed during training as the algorithm gradually learns to arrive at predictions that are closer and closer to the known outcomes in training cases. Structurally, the model parameters are grouped in some 40,000 five-by-five matrices, or kernels.
Read more of this story at SoylentNews.
Friday, 24 March
23:31
CISA releases free tool for detecting malicious activity in Microsoft cloud environments Help Net Security
Network defenders searching for malicious activity in their Microsoft Azure, Azure Active Directory (AAD), and Microsoft 365 (M365) cloud environments have a new free solution at their disposal: Untitled Goose Tool. Released by the Cybersecurity and Infrastructure Security Agency (CISA), it is an open-source tool that allows users to export and review logs, alerts, configurations, cloud artifacts, and more. The tools capabilities As an agency charged with among other things helping US-based organizations More
The post CISA releases free tool for detecting malicious activity in Microsoft cloud environments appeared first on Help Net Security.
22:50
Intel vPro platform unveils advanced security measures Help Net Security
Intel has launched the latest Intel vPro platform, which is powered by 13th Gen Intel Core processors and offers a broad range of features, including powerful security measures. The extensive commercial portfolio will offer over 170 laptops, desktops, and entry-level workstations, in collaboration with Acer, ASUS, Dell, HP, Lenovo, Fujitsu, Panasonic, and Samsung. IDCs latest report suggests that Windows PCs running on Intel-based processors have a 26% lower chance of experiencing significant security events than More
The post Intel vPro platform unveils advanced security measures appeared first on Help Net Security.
22:43
THN Webinar: Inside the High Risk of 3rd-Party SaaS Apps The Hacker News
Any app that can improve business operations is quickly added to the SaaS stack. However, employees don't realize that this SaaS-to-SaaS connectivity, which typically takes place outside the view of the security team, significantly increases risk. Whether employees connect through Microsoft 365, Google Workspace, Slack, Salesforce, or any other app, security teams have no way to quantify their
22:06
GitHub Swiftly Replaces Exposed RSA SSH Key to Protect Git Operations The Hacker News
Cloud-based repository hosting service GitHub said it took the step of replacing its RSA SSH host key used to secure Git operations "out of an abundance of caution" after it was briefly exposed in a public repository. The activity, which was carried out at 05:00 UTC on March 24, 2023, is said to have been undertaken as a measure to prevent any bad actor from impersonating the service or
22:00
SheepShaver: A Cross-Platform Tool For Retro Enthusiasts Hackaday

The world of desktop computing has coalesced into what is essentially a duopoly, with Windows machines making up the bulk of the market share and Apple carving out a dedicated minority. This relatively stable state hasnt always existed, though, as the computing scene even as late as the 90s was awash with all kinds of competing operating systems and various incompatible hardware. Amiga, Unix, OS/2, MacOS, NeXT, BeOS, as well as competing DOSes, were all on the table at various points.
If youve still got a box running one of these retro systems, SheepShaver might be able to help expand your software library. Its not the sort of virtualization that were used to in the modern world, with an entire operating system running on a sanctioned-off part of your system. But SheepShaver does allow you to run software written for MacOS 7.5.2 thru 9.0.4 in a different environment. Unix and Linux are both supported, as well as Mac OS X, Windows NT, 2000, and XP, and the enigmatic BeOS. Certain configurations allow applications to run natively without any emulation at all, and there is plenty of hardware support built-in as well.
For anyone running retro hardware from the late 90s or early 00s, this could be just the ticket to get an application running that wasn...
21:39
Pwn2Own Vancouver 2023 Day 2: Microsoft Teams, Oracle VirtualBox, and Tesla hacked Security Affairs
On the second day of Pwn2Own Vancouver 2023, the organization awarded $475,000 for 10 unique zero-day vulnerabilities.
On the second day of Pwn2Own Vancouver 2023, the organization awarded $475,000 for 10 unique zero-day vulnerabilities, bringing the total awarded to $850,000!
The bug hunters demonstrated zero-day attacks against the Oracle VirtualBox virtualization platform, Microsoft Teams, Tesla Model 3, and the Ubuntu Desktop OS.
The day began with the success/collision achieved by Thomas Imbert (@masthoon) and Thomas Bouzerar (@MajorTomSec) from Synacktiv (@Synacktiv) demonstrating a 3-bug chain against Oracle VirtualBox with a Host EoP. The success was classified as a collision because one of the bugs exploited in the attack was previously known. The due earned $80,000 and 8 Master of Pwn points.
The researchers @hoangnx99, @rskvp93, and @_q5ca from Team Viettel (@vcslab) chained 2 vulnerabilities to hack Microsoft Teams. They earn $75,000 and 8 Master of Pwn points.
Of course, the most interesting attack was conducted by David Berard (@_p0ly_) and Vincent Dehors (@vdehors) from Synacktiv (@Synacktiv) who exploited a heap overflow and an OOB write to hack Tesla Infotainment Unconfined Root. They qualify for a Tier 2 award, earning $250,000 and 25 Master of Pwn points. The team also won the Tesla Model 3 they have hacked.
The researcher dungdm (@_piers2) of Team Viettel (@vcslab) exploited an uninitial...
21:37
Intel Prepares More Meteor Lake Graphics Code For Linux 6.4 Phoronix
Intel's open-source engineers continue to be quite busy working on their Meteor Lake enablement ahead of those initial mobile processors shipping later this year...
21:26
AMDGPU Linux Driver Gets Ready For eDP 1.5 Panels With 6.75 Gbps/Lane Phoronix
Sent out today were the latest AMDGPU Display Core "DC" patches having the latest work done by AMD internally on this display/monitor portion of their driver code. Notable with this round of 19 patches is preparation work for upcoming eDP 1.5 laptop displays...
21:17
'Time Reflections' Finally Observed by Physicists After Decades of Searching SoylentNews
Reflections in time instead of space:
Walk through a maze of mirrors, you'll soon come face to face with yourself. Your nose meets your nose, your fingertips touch at their phantom twins, stopped abruptly by a boundary of glass.
Most of the time, a reflection needs no explanation. The collision of light with the mirror's surface is almost intuitive, its rays set on a new path through space with the same ease as a ball bouncing off a wall.
For over sixty years, however, physicists have considered a subtly different kind of reflection. One that occurs not through the three dimensions of space, but in time.
Now researchers from the City University of New York's Advanced Science Research Center (CUNY ASRC) have turned the theory of 'time reflections' into practice, providing the first experimental evidence of its manipulation across the electromagnetic spectrum.
[...] Put aside thoughts of TARDIS-like technologies rewriting history. This kind of time reflection is even weirder. And, it seems, actually possible after all.
By the 1970s, it was becoming clear that there was an analog for spatial reflection in the time component of a quantum wave of light. Change the medium a wave is traveling through quickly enough, in just the right way, and the temporal component of the wave will change with it.
The effect of this reflection in time isn't going to rip a hole in reality. But It will shift the frequency of the wave, in ways technology could exploit across varied fields like imaging, analogue computing, and optical filtering.
Strangely, the 'echo' of altered frequency is also a reversal of the signal. If it was an echo of your voice counting one to ten, you'd hear each number spoken backwards, from ten back to one, in a chipmunk squeak.
Read more of this story at SoylentNews.
20:59
Researchers Uncover Chinese Nation State Hackers' Deceptive Attack Strategies The Hacker News
A recent campaign undertaken by Earth Preta indicates that nation-state groups aligned with China are getting increasingly proficient at bypassing security solutions. The threat actor, active since at least 2012, is tracked by the broader cybersecurity community under Bronze President, HoneyMyte, Mustang Panda, RedDelta, and Red Lich. Attack chains mounted by the group commence with a
20:34
New Pirate IPTV Bill Moved to Senate as Italy Takes on Digital Mafias TorrentFreak
 Italian consumers love for pirate IPTV services and the
alleged damage suffered by broadcasters and the countrys
world-famous clubs at the hands of those services, have been on a
collision course for some time.
Italian consumers love for pirate IPTV services and the
alleged damage suffered by broadcasters and the countrys
world-famous clubs at the hands of those services, have been on a
collision course for some time.
Italy has operated an administrative pirate site-blocking program for years. It currently blocks around 3,200+ pirate domains, with telecoms regulator AGCOM sometimes issuing blocking instructions to ISPs within days of a rightsholder complaint.
Defending live sporting events from ubiquitous pirate IPTV streams demands a whole lot more, though. After gaining and maintaining momentum, alongside increasing political pressure, it seems likely that football clubs and broadcasters are about to collect.
Push For The Big Anti-Piracy Bill
By the middle of 2022, support for radical action to shut down the flow of pirate streams was building in Italy. Unprecedented blocking measures, new powers for telecoms regulator AGCOM, punishments for stream suppliers, even punishments for those in the telecoms sector who fail to block them, sat firmly on the table.
Working against the clock in December 2022, the new standards were laid out, one in particular. ISPs would be required to block pirate IPTV streams without delay and in real time most likely having been informed well in advance of what to shut down.
Anti-Piracy Bill Unanimously Approved
This week in the Chamber of Deputies, Italys lower house of parliament, the football and broadcasting industry-developed anti-piracy bill was unanimously waved through to the final.
If the bill meets with the approval of the Senate, as it almost certainly will, the new law will attempt to strangle the availability of pirate streams and punish suppliers and consumers of those that get through.
20:08
New distros list statistics Open Source Security
Posted by Anthony Liguori on Mar 24
Hi,I've been working to automate[*] tracking posting on the distros@ mailing
list for reporting purposes. This includes searching oss-security for
posting information, extracting CVEs, and trying to tie it all together.
Anywhere, I have full stats for 2022 and stats for Jan/Feb of 2023. As
long as everyone is happy with the content, I'll update regularly moving
forward....
20:03
Links 24/03/2023: GNU Grep 3.10 and Microsoft Accenture in a Freefall Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
-
GNU/Linux
-
Desktop/Laptop
-
Linux Gizmos Framework presents new DIY upgradeable laptops
Framework introduced today their Framework Laptop 13 DIY Edition compatible with the AMD Ryzen 7040 Series processors and 13th Gen Intel processors. These highly customizable laptops are available to pre-order starting at $849.00.
...
-
-
19:45
The ISDC 2023 (International Space Development Conference) will be held May 25-28 in Dallas-Frisco, Texas. Lifeboat News
The ISDC 2023 (International Space Development Conference) will be held May 2528 in Dallas-Frisco, Texas.
Our Gary Barnhard, Sherry Bell, Michelle L.D. Hanlon, Janet Ivey, David Livingston, Holly Melear, Rod Pyle, Martine Rothblatt, and Dylan Taylor will be speaking/participating.19:00
CNC Intaglio-Esque Engraving Hackaday

Intaglio is an ancient carving technique for adding details to a workpiece, by manually removing material from a surface with only basic hand tools. If enough material depth is removed, the resulting piece can be used as a stamp, as was the case with rings, used to stamp the wax seals of verified letters. [Nicolas Tranchant] works in the jewelry industry, and wondered if he could press a CNC engraving machine into service to engrave gemstones in a more time-efficient manner than the manual carving methods of old.
Engraving and machining generally work only if the tool you are using is mechanically harder than the material the workpiece is made from. In this case, this property is measured on the Mohs scale, which is a qualitative measurement of the ability of one (harder) material to scratch another. Diamond is the hardest known material on the Mohs scale and has a Mohs hardness of 10, so it can produce a scratch on the surface of say, Corundum Mohs value 9 but not the other way around.
...
18:51
Critical WooCommerce Payments Plugin Flaw Patched for 500,000+ WordPress Sites The Hacker News
Patches have been released for a critical security flaw impacting the WooCommerce Payments plugin for WordPress, which is installed on over 500,000 websites. The flaw, if left unresolved, could enable a bad actor to gain unauthorized admin access to impacted stores, the company said in an advisory on March 23, 2023. It impacts versions 4.8.0 through 5.6.1. Put differently, the issue could permit
18:35
Russian Coders Blocked From Contributing to FOSS Tools SoylentNews
Russian coders blocked from contributing to FOSS tools:
The Reg has seen two recent incidents of Russian developers being blocked from public development of FOSS code. One was a refusal on the Linux kernel mailing list, the other a more general block on Github. In the last week, these events have both caused active, and sometimes heated, discussions in FOSS developer communities.
The GitHub account of developer Alexander Amelkin has been blocked, and his repositories marked as "archived" including ipmitool, whose README describes it as "a utility for managing and configuring devices that support the Intelligent Platform Management Interface." Unable to comment on Github itself, Amelkin described what happened on the project's older Soureforge page:
Sorry to say, but on March 1st without any prior notice or any explanation whatsoever, GitHub has suspended my personal account and made orphan all the projects that I owned/maintained.
That includes ipmitool and frugen.
This mailing list and the old sourceforge project page are the only means of communication with you that I have left. I am currently searching for a way to unblock my GitHub or (less preferably) migrate ipmitool once again to another less hostile service.
Amelkin works for Russian chipbuilder Yadro, which we described as working on RISC-V chips back in 2021. Microsoft is just obeying US law in this: according to the War and Sanctions database of the Ukrainian National Agency on Corruption Prevention, the NACP, Yadro is a sanctioned company.
However, on LinkedIn, Amelkin disputes his employer's involvement:
You may rest assured that this "sanctioned corporation" takes no part in this awful war, and even if making civilian server products can be viewed as somehow taking part, that part is definitely far less than what, say, BMW or Bosch took in WW2, yet nobody seems to have cancelled them or at least remembered what they've done, let alone their individual employees. All this is stupid, xenophobic and racist. Especially you labelling me as a terrorist on the basis of my ethnicity.
18:22
The iPhone Moment of A.I. Has Started Lifeboat News: The Blog

The iPhone moment for A.I. hype takes many hues, but Nvidia is about the future of computing itself. NVIDIA DGX supercomputers, originally used as an AI research instrument, are now running 24/7 at businesses across the world to refine data and process AI.
While OpenAI gets a lot of the glory, I believe the credit should go to Nvidia. Launched late last year, ChatGPT went mainstream almost instantaneously, attracting over 100 million users, making it the fastest-growing application in history. We are at the iPhone moment of AI, Huang said. Nvidia makes about $6 to $7 Billion a fiscal quarter in revenue.
Nvidia said its offering a new set of cloud services that will allow businesses to create and use their own AI models based on their proprietary data and specific needs. The new services, called Nvidia AI Foundations, include three major components and are meant to accelerate enterprise adoption of generative AI: Enterprises can use Nvidia NeMo language service or Nvidia Picasso image, video and 3D service to gain access to foundation models that can generate text or images based on user inputs.
18:00
Synthetic proteins simplify nature to outperform the real thing Terra Forming Terra

Why Homesteading? A Candid Chat About the Homestead Tsunami | Joel Salatin of Polyface Farms Terra Forming Terra
Why Homesteading? A Candid Chat About the Homestead Tsunami
| Joel Salatin of Polyface Farms
https://www.youtube.com/watch?v=d52OcWJI6l0
<iframe width="512" height="384" src="https://www.youtube.com/embed/d52OcWJI6l0" title="Why Homesteading? A Candid Chat About the Homestead Tsunami | Joel Salatin of Polyface Farms" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" allowfullscreen></iframe>
What In The World Is Happening To The Sun? Terra Forming Terra
Consciousness Began When the Gods Stopped Speaking Terra Forming Terra

16:40
MITREs System of Trust risk model manager improves supply chain resiliency Help Net Security
MITRE launched its System of Trust risk model manager and established a community engagement group of 30 members. Expanding from its free and open platform, System of Trust now delivers a collaborative community to identify and mitigate threats to supply chainsbefore they happen. Leveraging the expertise of researchers and organizations, the community will further develop the frameworks body of knowledge and enhance supply chain security. System of Trust, showing key risk areas for suppliers, supplies/components, More
The post MITREs System of Trust risk model manager improves supply chain resiliency appeared first on Help Net Security.
16:30
New infosec products of the week: March 24, 2023 Help Net Security
Heres a look at the most interesting products from the past week, featuring releases from ForgeRock, Vectra, Verosint, Vumetric, and Waterfall Security Solutions. Waterfall Security Solutions launches WF-600 Unidirectional Security Gateway Waterfall Security Solutions launched the WF-600 Unidirectional Security Gateway, an OT security protection against remote cyber attacks. The WF-600 includes a self-contained, integrated software platform, with no external software needed on industrial or enterprise computers, and with the entire platform designed together with the More
The post New infosec products of the week: March 24, 2023 appeared first on Help Net Security.
16:22
The Iron Fist Unleashed! Lifeboat News: The Blog
Senescent cells accumulate with age when one senescent cell turns another cell senescent through SASP secretion. New research is offering new hope for fighting this.
16:22
BREAKING: Scientists create the 5th form of matter for 6 minutes Lifeboat News: The Blog
In a ground-breaking experiment, scientists have successfully created the fifth form of matter, known as the Bose-Einstein condensate (BEC), for a remarkable duration of six minutes.
This major accomplishment has the potential to revolutionize our understanding of quantum mechanics and open the door to new technological advancements. In this article, we will explore the significance of this achievement, the nature of BECs, and the potential applications of this newfound knowledge.
16:00
Enormous Metal Sculpture Becomes an Antenna Hackaday

Those who have worked with high voltage know well enough that anything can be a conductor at high enough voltages. Similarly, amateur radio operators will jump at any chance to turn a random object into an antenna. Flag poles, gutters, and even streams of water can be turned into radiating elements for a transmitter, but the members of this amateur radio club were thinking a little bit bigger when they hooked up their transmitter to this giant sculpture.
For those who havent been to the Rochester Institute of Technology (RIT) in upstate New York, the enormous metal behemoth is not a subtle piece of artwork and sits right at the entrance to the university. Its over 70 feet tall and made out of bronze and steel, a dream for any amateur radio operator. With the universitys permission and some help to ensure everyones safety during the operation, the group attached a feedline to the sculpture with a magnet, while the shield wire was attached to a ground rod nearby. A Yaesu FT-991 running on only 5 watts and transmitting in the 20-meter band was able to make contacts throughout much of the eastern United States with this setup.
This project actually started as an in-joke within the radio club, as reported by Reddit user [bbbbbthatsfivebees] who is a member. Eventually the joke becam...
16:00
Top ways attackers are targeting your endpoints Help Net Security
Over the last several years, endpoints have played a crucial role in cyberattacks. While there are several steps organizations can take to help mitigate endpoint threats such as knowing what devices are on a network (both on-premises and off-site), quarantining new or returning devices, scanning for threats and vulnerabilities, immediately applying critical patches, etc. there is still much to be done to ensure endpoint security. To achieve that, its important to understand some More
The post Top ways attackers are targeting your endpoints appeared first on Help Net Security.
15:51
Dinosaur Bone Study Reveals That Not All Giants Grew Alike SoylentNews
When the paleontologist Michael D'Emic cut into the bones of Majungasaurus, a relative of Tyrannosaurus rex that roamed Madagascar 70 million years ago, he suspected that surprises might be hiding in them. But what he found defied all expectations.
Majungasaurus adults measured up to 7 meters from snout to tail and could weigh 1,000 kilograms. Paleontologists had thought that big dinosaurs like these massive carnivores achieved their stature through rapid growth spurts. But the fossil bones revealed a different story. "Unlike carnivorous dinosaurs that had been studied up until then," D'Emic said, the Majungasaurus grew "really, really slowly."
Puzzled, he sliced up a close relative of the dinosaur a Ceratosaurus from North America, which was roughly the same length and weight to see if it grew slowly too. This time, "we got the opposite result," he said. "It grew just about faster than any carnivorous dinosaur I've ever seen."
What followed for D'Emic was a decade-long whirlwind of peering at bones for clues to how dinosaurs grew. His analysis of 42 different dinosaur species, recently published in Science, demonstrates that the "get big fast" mode of growth was less predominant than researchers have assumed.
[...] Whether an animal grows quicker and faster or slower and longer might seem like a nitpicky distinction. But an animal's growth trajectory provides insights into its life and the world it inhabited. Fast-growing animals can overpower potential predators and outcompete other species, but they need plenty of food and other resources. Growing slowly is riskier, but it allows an animal to survive on less during hard times. The bones of Majungasaurus, for example, confirm that, as the top predator in its ancient ecosystem, it had the luxury of developing at a leisurely pace.
Read more of this story at SoylentNews.
15:30
Why organizations shouldnt fold to cybercriminal requests Help Net Security
Organizations worldwide pay ransomware fees instead of implementing solutions to protect themselves. The ransom is just the tip of the iceberg regarding the damage a ransomware attack can wreak. In this Help Net Security video, Gerasim Hovhannisyan, CEO at EasyDMARC, discusses how domain authentication tools such as DKIM, SPF, and DMARC can help mitigate risk and limit the number of phishing attacks, identifying fraudulent messages before they even hit the receivers inbox and making organizations More
The post Why organizations shouldnt fold to cybercriminal requests appeared first on Help Net Security.
15:18
Seren Dalkiran joins our Futurists Board and our Sustainability Board. Lifeboat News
Seren Dalkiran joins our Futurists Board and our Sustainability Board. She is Founder of the Millennial Leadership Lab and Cofounder of the Synergized Earth Network.
15:12
TheGradCafe - 310,975 breached accounts Have I Been Pwned latest breaches
In February 2023, the grad school admissions search website TheGradCafe suffered a data breach that disclosed the personal records of 310k users. The data included email addresses, names and usernames, genders, geographic locations and passwords stored as bcrypt hashes. Some records also included physical address, phone number and date of birth. TheGradCafe did not respond to multiple attempts to disclose the breach.
15:00
In uncertain times, organizations prioritize tech skills development Help Net Security
Amid economic uncertainty and downturn, organizations are leaning on their technologists to continue to innovate and drive business value, according to Pluralsight. Though 65% of tech team leaders have been asked to cut costs, 72% still plan to increase their investment in tech skill development in 2023. And because upskilling existing talent is more cost-effective than hiring new employees, 97% of learning and development and HR directors say they are prioritizing internal talent over hiring More
The post In uncertain times, organizations prioritize tech skills development appeared first on Help Net Security.
15:00
OpenSUSE Tumbleweed Begins Rolling Out GCC 13 Phoronix
While GCC 13 is working its way toward its official GCC 13.1 stable release in the next few weeks, with this week's openSUSE Tumbleweed rolling-release updates it has already begun switching over to this major annual compiler update...
14:22
DNA Double Helix Splits Due to Invasive Nature of Unzipping Process Lifeboat News: The Blog

Scientists had a hard time reconstructing how complex molecular parts are being held together. However, that was before SISSAs Cristian Micheletti and his team studied how the DNA double helix unzips when translocated at high velocity through a nanopore.
DNA Double Helixs Unzipping
DNA has a double helix structure because it consists of two spiral chains of deoxyribonucleic acid. Its shape is reminiscent of a spiral staircase.
14:15
Zenoss improves security for user credentials with identity management capabilities Help Net Security
Zenoss has released advanced identity management capabilities, helping ensure maximum protection of sensitive credentials while in use and at rest throughout the Zenoss Cloud platform. This represents yet another key building block in the security and privacy features Zenoss has released since launching Zenoss Cloud in 2018. Credential-based attacks, one of the most common forms of cyberattack, occur when attackers compromise user credentials to bypass an organizations security measures and steal critical data. The number More
The post Zenoss improves security for user credentials with identity management capabilities appeared first on Help Net Security.
14:00
Vectra Match helps security teams accelerate threat hunting and investigation workflows Help Net Security
Vectra Match brings intrusion detection signature context to Vectra Network Detection and Response (NDR), enabling security teams to accelerate their evolution to AI-driven threat detection and response without sacrificing investments already made in signatures. As enterprises transform embracing digital identities, supply chains and ecosystems GRC and SOC teams are forced to keep pace. Keeping pace with existing, evolving and emerging cyber threats requires visibility, context and control for both known and unknown threats. The More
The post Vectra Match helps security teams accelerate threat hunting and investigation workflows appeared first on Help Net Security.
13:41
Links 23/03/2023: RSS Guard 4.3.3 and OpenBSD Webzine Techrights
![]()
Contents
-
GNU/Linux
-
Desktop/Laptop
-
Liliputing Kubuntu Focus Xe Gen 2 is a 14 inch Linux laptop with Intel Alder Lake-P for $895 and up
The Kubuntu Focus Xe Gen 2 is a thin and light notebook computer with a 14 inch full HD display, support for up to up to an Intel Core i7-1260P processor, up to 64GB of RAM, and PCIe 4 NVMe storage. It ships with the Kubuntu 22.04 LTS GNU/Linux distribution pre-installed.
An upgrade over the original Focus Xe, whic...
-
-
13:15
Experiencing 15 Years of LibrePlanet Celebration Firsthand as a Volunteer: 2023 Charting the Course Techrights
Article by Marcia K Wilbur
Welcome from LibrePlanet 2023!
This year, LibrePlanet was hybrid with on-site and online options from the Boston Convention and Exhibition Center.
It was a breezy and chilly weekend outside. The Boston St. Pattys day parade was scheduled around the corner for Sunday. What a great time to be in Boston!
Although I wanted to be there earlier, 9ish was time for me to come in from being out in the cold, for the 15-year celebration Free Software Foundations LibrePlanet.
Charting the Course was the theme. We were on board!
Event: Office party
My intention was to attend the office party early in the evening. However, I ended up on the wrong Franklin Street and was late. As I arrived, Craig was at the front and directed me to the refreshments and a contact, Illan, who would use me if there was a need.
Several people registered at the FSF offices for the conference starting the next day. The office party was a lot of mingling, talk about USENET, signal, privacy, makerspaces and much much more. The snacks were fresh and there was a variety of beverages including wine.
As the office party and evening came to a close, we were so entertained with lively conversation, we did not even realize the party was ending. I always recommend this party as a great meet and greet opportunity for free software enthusiasts. Again, this was a welcoming environment with no known issues. It was a great time!
Logistics and Venue
Parking was convenient and there was a driver with a cart to take you right to registration and the event!
The venue was comfortable and the event was welcoming!
Upon arrival at the convention center, a friendly security officer approached me, Are you here for the tech event?
YES!
He gave information about parking and the area. He mentioned the cart would be ready to take me up to the event. This was very pleasant.
The cart driver was very friendly and drove right up to registration.
There at registration, Craig greeted participants with a warm and welcoming smile. For this event, I was a volunteer at registration.
I was glad to be there.
Hallway Track
In between sessions and during lunch or just roaming around, we found ourselves in the hallway drinking coffee, discussing privacy, surveillance, Internet of things, AI/ML ethics, disaster recovery, and copyleft. Some discussions were about the state of healthcare, gaming and food!
The hallway track was a com...
13:08
This Tiny Chip is Being Used to Develop a Tooth-mounted Sensor That Can Read Your Spit SoylentNews
Miniaturizing tech is a perpetual challenge for wearable makers. The smaller the device, the better it is for wearability. The thing is, that usually comes at the expense of battery life. However, Silicon Labs is hoping its latest xG27 chipset is small and energy-efficient enough to spark some big ideas in the medical tech space like a saliva reader that's so tiny it can be mounted onto a tooth.
According to Silicon Labs, the xG27 family of SoCs consists of the BG27 and the MG27. Both are built around the ARM Cortex M33 processor, but the BG27 focuses on Bluetooth, while the MG27 supports Zigbee and other protocols. As for how small these chips are, the xG27 SoCs range from 2mm-squared to 5mm-squared roughly the width of a No. 2 pencil's lead tip to the width of the pencil itself. It's not the world's smallest Bluetooth chip, but Silicon Labs spokesperson Sam Ponedal tells The Verge that's only by "fractions of a millimeter."
This is neat from a technical perspective, but what's cooler is the BG27 is currently being used to develop an actual product the aforementioned tooth-mounted wearable sensor. Lura Health, a medical device maker, says it's using the chip for its "salivary diagnostic sensor." The sensor is small enough to be glued to a molar (or placed inside a "smart retainer") with the intent of continually monitoring a patient's saliva. That, in turn, would allow dentists and clinicians to potentially test for more than 1,000 health conditions.
[...] As for other use cases, Silicon Labs says its chips are good candidates for medical patches, continuous glucose monitors, and wearable EKGs. That's because they can operate on as low as 0.8 volts and can switch to a "shelf mode" that reduces energy use during transportation and while stored on shelves. These features aren't quite as appealing in consumer wearables, but it opens the door for greater wearable use in hospitals and clinical settings.
Read more of this story at SoylentNews.
13:00
Grow Your Own Brain Electrodes Hackaday

Bioelectronics has been making great strides in recent years, but interfacing rigid electrical components with biological systems that are anything but can prove tricky. Researchers at the Laboratory for Organic Electronics (LOE) have found a way to bridge the gap with conductive gels. (via Linkping University)
Outside the body, these gels are non-conductive, but when injected into a living animal, the combination of gel and the bodys metabolites creates a conductive ele...
12:48
[Meme] Grabinski the Opportunity Techrights
Opportunists from Germany, hijacking Europes legal system for patents under the auspices of EU
Summary: Reports of European Patents being invalidated (judges do not tolerate fake patents) have become so common that a kangaroo court becomes a matter of urgency for the EPOs Benot Battistelli and Antnio Campinos; will the EU and the EPOs Administrative Council go along with it, helping to cover up more than a decade of profound corruption?
12:33
MIT is testing light and sound to combat Alzheimers Lifeboat News: The Blog
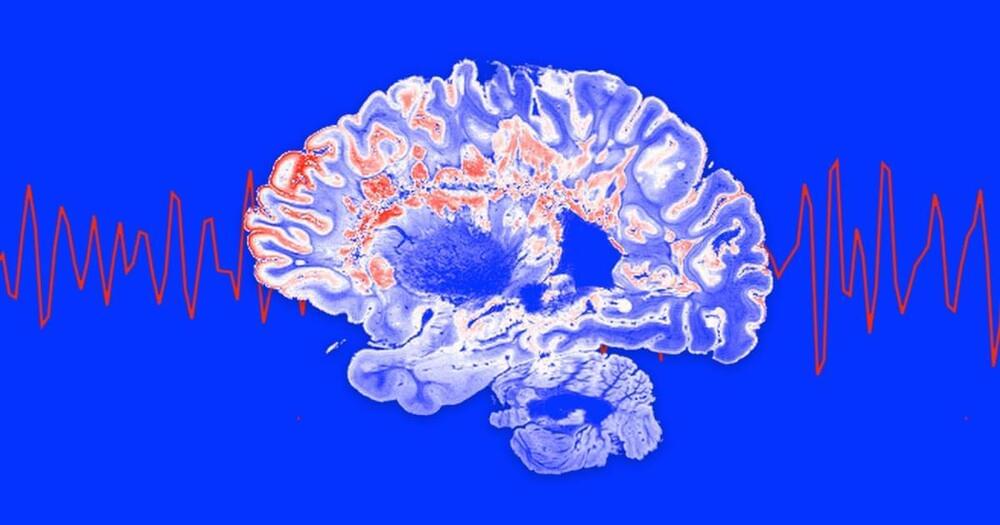
Our brains arent limited to producing just one type of brain wave at a time, but usually, one type is dominant, and the type it is can often be linked to your level of alertness: delta waves may dominate when you sleep, while gamma waves might dominate when you concentrate intensely.
The idea: Researchers have previously observed that people with Alzheimers a devastating neurological disease affecting more than 6 million people in the US alone may have weaker and less in-sync gamma waves than people who dont have the disease.
In a series of past studies, MIT researchers demonstrated a deceptively simple way to increase the power and synchronization of these waves in mouse models of Alzheimers: expose the animals to lights flickering and/or sounds clicking at a frequency of 40 Hz.
12:32
Union Syndicale Fdrale Cautions the EPOs Administrative Council About Initiating an Illegal Kangaroo Court System for Patents (UPC) While EPO Breaks Laws and Sponsors the Ukraine Invasion Techrights
UPC is Unacceptable and a Risk to the EU (for many reasons)
Video download
link | md5sum
4742e57afe3feef00433b302d09ba6d1
USF Writes to AC and EU
Creative Commons Attribution-No Derivative Works 4.0
Summary: Union Syndicale Fdrale (USF) is once again speaking out in support of the staff union of Europes second-largest institution, which lacks oversight and governance because of profound corruption and regulatory capture
Repeating a pattern of offences, utter disregard for the law, and routine violations of the law (turning diplomatic immunity into unbridled impunity), the EPOs management incurs the wrath of NGOs; the same group that berated Benot Battistelli for his crimes is reporting Antnio Campinos to the people who can hold him accountable but never will (hes bribing them to be entirely complicit); this systemic breakdown or the collapse of the legal system (at least in the context of patents) merits far more media attention, but the media is connected to the same regimes and corporations that benefit financially from the corruption of the EPO.
![[USF] Union Syndicale Fdrale on SUEPO](../../techrights.org/wp-content/uploads/2023/03/suepo_125830.png) The video above goes through the
latest relevant letter, dated 3 days ago. It also takes stock of
this
latest nonsense (warning:
The video above goes through the
latest relevant letter, dated 3 days ago. It also takes stock of
this
latest nonsense (warning: epo.org link)
entitled Digital transformation & Unitary Patent: users
updated. As we noted already in Daily Links, the EPO had once
again promoted an illegal, unconstitutional ploy. The EPO is run by
gangsters who...
12:32
Organoids growing mini BRAINS Lifeboat News: The Blog

Organoids are an incredible tool for research into the brain.
Cerebral organoids are created by growing human stem cells in a
bioreactor. They might be the key to unlocking the answers to many
of our questions about the brain. We explain how theyre made and
some of the discoveries theyve helped with so far!
 Script
by Duranka Perera (https://www.durankaperera.com/)
Script
by Duranka Perera (https://www.durankaperera.com/)
 Thumb by
Broken Bran -
Thumb by
Broken Bran -
https://twitter.com/BranGSmith.
Support us on Patreon: https://www.patreon.com/Brainbook_
Thank you to our supporters:
Morag Forbes.
Patrick Kohl.
Ronald Coleman Dees.
Alex Rofini.
Helen Whitley.
Discover more on our website.
https://www.brainbookcharity.org.
Follow us on:
Twitter: https://www.twitter.com/realbrainbook.
Instagram: https://www.instagram.com/brainbook_
Facebook: https://www.facebook.com/realbrainbook
12:31
Do Kwon, Founder of Terraform Labs, Arrested in Montenegro HackRead | Latest Cybersecurity and Hacking News Site
Reportedly, Do Kwon was caught using falsified documents at an airport in the capital city of Montenegro.
This is a post from HackRead.com Read the original post: Do Kwon, Founder of Terraform Labs, Arrested in Montenegro
12:29
The Crazy Mass-Giving Mechanism of the Higgs Field Simplified Lifeboat News: The Blog
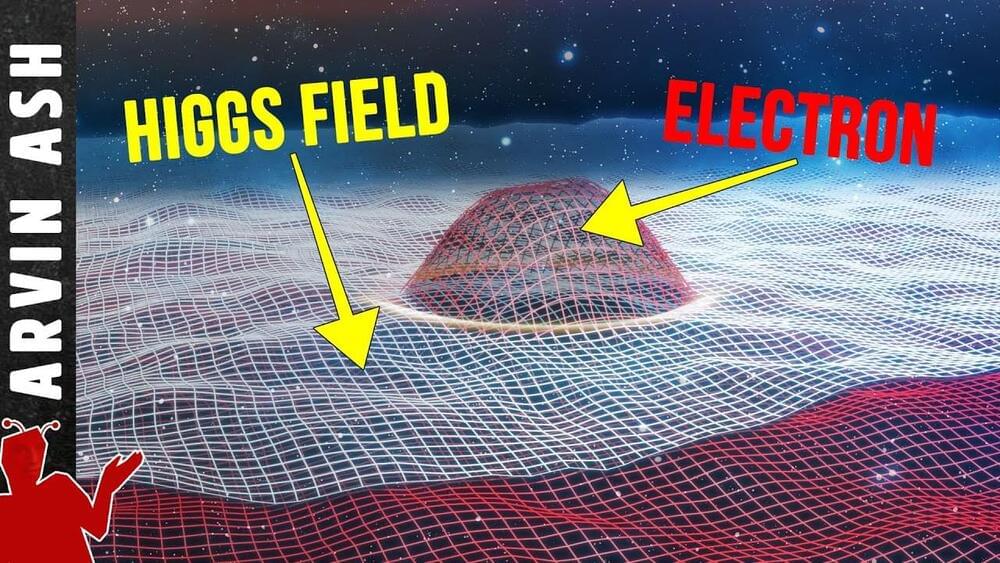
Get 30% off Blinkist premium and enjoy 2 memberships for the price of 1! Start your 7-day free trial by clicking here: https://www.blinkist.com/arvinash.
REFERENCES:
Where 99% of mass comes from: https://youtu.be/KnbrRhkJCRk.
ElectroWeak Unification: https://youtu.be/u05VK0pSc7I
Symmetry Breaking: https://youtu.be/yzqLHiA0uFI
PATREON:
For Input on Videos, Private messages, Early Viewing, Join Us:
https://www.patreon.com/arvinash.
CHAPTERS:
0:00 Sources of mass.
2:33 Blinkist Free Trial.
3:51 Particles are excitations in Fields.
6:09 How Mass comes from interaction with Higgs.
10:42 Why do some particles interact and others dont?
11:31 How our universe would not exist without Higgs.
SUMMARY:
How does the Higgs give mass to particles? How do elementary
particles gain mass? All mass is Energy. 99% of the mass of an atom
is contained in the binding energy within the nucleus. But about 1%
of your mass is contained in the mass of the subatomic particles
that make up the atoms, electrons and quarks.
How do these subatomic particles get an intrinsic mass? This is due to the Higgs Field. To understand how it works, lets look at the standard model of particle physics.
12:25
Microsoft Researchers Claim GPT-4 Is Showing Sparks of AGI Lifeboat News: The Blog
Fresh on the heels of GPT-4s public release, a team of Microsoft AI scientists published a research paper claiming the OpenAI language model which powers Microsofts now somewhat lobotomized Bing AI shows sparks of human-level intelligence, or artificial general intelligence (AGI).
Emphasis on the sparks. The researchers are careful in the paper to characterize GPT-4s prowess as only a first step towards a series of increasingly generally intelligent systems rather than fully-hatched, human-level AI. They also repeatedly highlighted the fact that this paper is based on an early version of GPT-4, which they studied while it was still in active development by wrangled into product-applicable formation.
Disclaimers aside, though, these are some serious claims to make. Though a lot of folks out there, even some within the AI industry, think of AGI as a pipe dream, others think that developing AGI will usher in the next era of humanitys future; the next-gen GPT-4 is the most powerful iteration of the OpenAI-built Large Language Model (LLM) to date, and on the theoretical list of potential AGI contenders, GPT-4 is somewhere around the top of the list, if not number one.
12:05
Investigation of Sirius Open Source Formalised schestowitz.com
Video download
link | md5sum
8e04ead83596e651305116cc77175bd0
Investigation Underway
Creative Commons Attribution-No Derivative Works 4.0
Summary: In light of new developments and some progress in an investigation of Sirius Open Source (for fraud!) we take stock of where things stand
IT hurts to know that a company which describes itself as Britains most respected Open Source company did this to us, but it did. Money laundering would be even worse, but were still looking into various allegations pertaining to privacy breaches, contract violations, and illegal contract-signing. To paraphrase the companys own boss, it doesnt look good
We recently learned some additional disturbing things. They will be published here at a later date. The video above focuses on what was published yesterday. Its one thing for an Open Source company to go out of business. To end up collapsing under a weight of abuse and even crime would hurt the image of Free software, including in the eyes of the British public sector (many of our clients were not private companies). This series wont end any time soon.
12:02
Investigation Underway: Sirius Open Source Embezzled/Stole Money, Robbed Its Own Staff Techrights
Video download
link | md5sum
8e04ead83596e651305116cc77175bd0
Investigation Underway
Creative Commons Attribution-No Derivative Works 4.0
Summary: In light of new developments and some progress in an investigation of Sirius Open Source (for fraud!) we take stock of where things stand
IT hurts to know that a company which describes itself as Britains most respected Open Source company did this to us, but it did. Money laundering would be even worse, but were still looking into various allegations pertaining to privacy breaches, contract violations, and illegal contract-signing. To paraphrase the companys own boss, it doesnt look good
This series wont end any time soon.We recently learned some additional disturbing things. They will be published here at a later date. The video above focuses on what was published yesterday. Its one thing for an Open Source company to go out of business. To end up collapsing under a weight of abuse and even crime would hurt the image of Free software, including in the eyes of the British public sector (many of our clients were not private companies). This series wont end any time soon.
11:45
BlackBerry partners with Adobe to deliver secure forms with electronic signatures on mobile Help Net Security
BlackBerry and Adobe have partnered to deliver a secure forms solution for mobile. The software solution, which combines BlackBerry UEM and Adobe Experience Manager Forms, is designed for popular mobile device platforms, and meets the rigorous security standards required by regulated industries. Furthermore, the partnership agreement allows BlackBerry to resell Adobe Experience Manager Forms software. Prior to the partnership between BlackBerry and Adobe, users have been challenged in completing and approving documents away from their More
The post BlackBerry partners with Adobe to deliver secure forms with electronic signatures on mobile appeared first on Help Net Security.
11:07
Report: Global Patent Renewal TrendsUnpicking What Survives IEEE Spectrum

We are delighted to share a new research report that explores trends in patent maintenance behaviors revealed through the analysis of two decades of patent data.
By collecting and analyzing different data points, we explore the trends and directionality of patent filing and maintenance by jurisdiction and sector to understand what survives. The insights within the report create a clearer profile of patent maintenance behaviors, affording readers a unique perspective on the renewals landscape and the strategic value of annuities.
11:00
HPR3820: Introduction to Gaming Hacker Public Radio
This starts out the series on Computer Strategy Games, and we begin with the game that got me hooked, the first Civilization game created by Sid Meier and published by Microprose. Though it is pretty old now, it is still fond in my heart, and in the hearts of so many other gamers. If this comes across as a love letter, so be it. We will also in this series look at where you can obtain old games, and where you can find more information about the games I cover. Links: https://en.wikipedia.org/wiki/Civilization_(series) https://en.wikipedia.org/wiki/4X http://flashofsteel.com/index.php/2006/09/18/gamers-bookshelf-civilization-or-rome-on-640k-a-day/ https://www.amazon.com/Sid-Meiers-Civilization-Chronicles-PC/dp/B000IU1PQA https://playclassic.games/ https://www.myabandonware.com/ https://www.myabandonware.com/game/sid-meier-s-civilization-1nj https://www.civfanatics.com/civ1/manual/civ1_man.htm https://www.civfanatics.com/civ1/cia/ https://forums.civfanatics.com/media/categories/civilization-gallery.16/ https://www.youtube.com/watch?v=CkmHeepmjEc https://www.youtube.com/watch?v=VF8Ribe5AFU https://www.youtube.com/watch?v=L7GkX4h-TP8 https://www.youtube.com/watch?v=3UuXa3PRSGo https://www.youtube.com/watch?v=Q1d08T8_wI4 https://www.youtube.com/watch?v=AJ-auWfJTts https://www.amazon.com/Sid-Meiers-Memoir-Computer-Games/dp/B08MNG8VX8/ https://www.palain.com/gaming/sid-meiers-civilization/
Supporting Developers with Disabilities It Will Never Work in Theory
If you don't ask people what they actually need or whether your supposedly good idea actually worked, it's all too easy for your "help" to accomplish nothing or even make things worse. That's why "Nothing about us, without us" became a rallying cry for disabled activists in the 1990s, and why it's vital to critically evaluate programs intended to help people with disabilities. This new paper looks at an effort by a Brazilian company to hire and train disabled software developers. None of the findings are particularly surprising, but that's part of why studies like this one are needed: if we never ask the question, we'll never know what we missed.
The paper closes with four recommendations that will make everyone's teaching better:
- Help instructors to master accessibility teaching practices.
- Make the materials available and organized in advance.
- Curate accessible programming tools.
- Make birds of a feather flock together (i.e., have someone from the community on the instructional team).
Isadora Cardoso-Pereira, Geraldo Gomes, Danilo Monteiro Ribeiro, Alberto de Souza, Danilo Lucena, and Gustavo Pinto. Supporting the careers of developers with disabilities: lessons from Zup Innovation. 2023. arXiv:2303.05429.
Software developers with disabilities have a hard time to join the software development market. Due to the lack of diversity that developers with disabilities could hinder innovation. In this work, we explore the Catalisa program envisioned by Zup Innovation, a Brazilian tech company, aimed to hire and train software developers with disabilities. We found that the program was able to accelerate the participants careers, although some shortcomings are still present.
10:23
Use of Meta Tracking Tools Found to Breach EU Rules on Data Transfers SoylentNews
Use of Meta tracking tools found to breach EU rules on data transfers:
Austria's data protection authority has found that use of Meta's tracking technologies violated EU data protection law as personal data was transferred to the US where the information was at risk from government surveillance.
The finding flows from a swathe of complaints filed by European privacy rights group noyb, back in August 2020, which also targeted websites' use of Google Analytics over the same data export issue. A number of EU DPAs have since found use of Google Analytics to be unlawful and some (such as France's CNIL) have issued warnings against use of the analytics tool without additional safeguards. But this is the first finding that Facebook tracking tech breached the EU's General Data Protection Regulation (GDPR).
All the decisions follow a July 2020 ruling by the European Union's top court that struck down the high level EU-US Privacy Shield data transfer agreement after judges once again identified a fatal clash between US surveillance laws and EU privacy rights. (A similar finding, back in 2015, invalidated Privacy Shield's predecessor: Safe Harbor.)
noyb ['none of your business' * see below. --Ed] trumpets the latest data transfer breach finding by an EU DPA as "groundbreaking" arguing that the Austrian authority's decision should send a signal to other sites that it's not advisable to use Meta trackers (the complaint concerns Facebook Login and the Meta pixel).
[...] "Facebook has pretended that its commercial customers can continue to use its technology, despite two Court of Justice judgments saying the opposite. Now the first regulator told a customer that the use of Facebook tracking technology is illegal," said Max Schrems, chair of noyb.eu, in a statement.
Read more of this story at SoylentNews.
10:00
Ondol: Korean Underfloor Heating Hackaday

One of the many aspects of the modern world we often take for granted is the very technology that keeps our accommodation at a habitable temperature. Examples of this include centralized heating systems using hot-water circulation, or blown air ducted to multiple rooms from a central furnace. Certainly in Europe, once the Romans shipped out, and before the industrial revolution, we were pretty cold unless someone lit a fire in the room. Every room. But not in Korea. The Ondol heating principles have been used constantly from about 5000 BC to only a few decades ago, keeping your average Korean countryman nice and toasty.
Having said that, the sophistication has improved a bit. Initially, the idea was to simply heat up a bunch of rocks in the fire, and bring them indoors, but Ondol quickly became part of the building itself. As will be seen from the video embedded below, the house sits on top of an elaborate double stack of serpentine channels, that circulate the hot combustion products from the furnace as thoroughly as possible, slowing down the gases and allowing their heat to transfer into the structure of the floor, and then radiate into the space...
09:43
09:14
A million at risk from user data leak at Korean beauty platform PowderRoom Security Affairs
South Korean beauty content platform, PowderRoom, has leaked the personal information of nearly one million people.
- Established in 2003, PowderRoom is a South Korean beauty content platform connecting 3.5 million members and thousands of beauty brands
- It calls itself the first and the biggest beauty community in South Korea that allows you to experience new brand products faster than anyone else and share the experience
- It exposed up to a million users full names, phone numbers, emails, Instagram usernames and home addresses
- The database was publicly available for over a year
- Attackers could have exploited the data to launch phishing and device hijacking attacks, make unauthorized purchases, and stalk users
- Cybernews reached out to PowderRoom and the Korean National Computer Emergency Response Team, and the data was secured
The Cybernews research team discovered that the South Korean social platform, powderroom.co.kr which markets itself as the nations biggest beauty community was leaking the private data of a million users.
The platform exposed full names, phone numbers, emails, Instagram usernames, and even home addresses. Researchers estimate that the database was publicly available for over a year.
Backed by beauty-product manufacturers, PowderRoom has hundreds of thousands of followers on social media, and its Android app has been downloaded more than 100,000 times on Google Play.
On the platform, users can review beauty products while being encouraged to actively participate and receive perks.
Personal data leaked
On December 15, researchers found a publicly accessible database with nearly 140GB of data. Some server logs included entries containing personal information, such as names, phone numbers, and home addresses, along with metadata about user devices and browsers used to access the site. The dataset included over a million email addresses.
Among the leaked data, researchers found a million tokens used for authentication and accessing the website.
Abusing them, threat actors could hijack user accounts and purchase products on the platform using the payment methods linked with the account. Additionally, attackers could modify account details, and post comments and reviews.
Leaking home addresses and phone numbers is a cause of concern, since exposing such information might lead to in-person stalking or harassment of the users of the platform.
If you want to know how to protect yourself, give a look at the original post at: https://cybernews.com/security/powder-room-data-leak/
About the author:...
08:22
Cloudstream Takes Site and Code Offline in Response to Hollywood Complaint TorrentFreak
 Legal video streaming services such as Amazon, Disney, and
Netflix are booming. At the same time, theres a flourishing dark
market of pirate streaming tools.
Legal video streaming services such as Amazon, Disney, and
Netflix are booming. At the same time, theres a flourishing dark
market of pirate streaming tools.
These unauthorized alternatives increasingly use slick designs and easy-to-use apps to appeal to a broad audience. And unlike the legal options, they offer all popular titles under the same roof, without charging a penny.
Cloudstream is one of the apps that made its mark in recent years. The Android-based software can aggregate pirated content from several third-party sources and is fully customizable through open-source extensions.
This hasnt gone unnoticed by rightsholders. Sky UK targeted the software last year and across the pond, Cloudstream also appeared on the radar of the MPA, Hollywoods anti-piracy group.
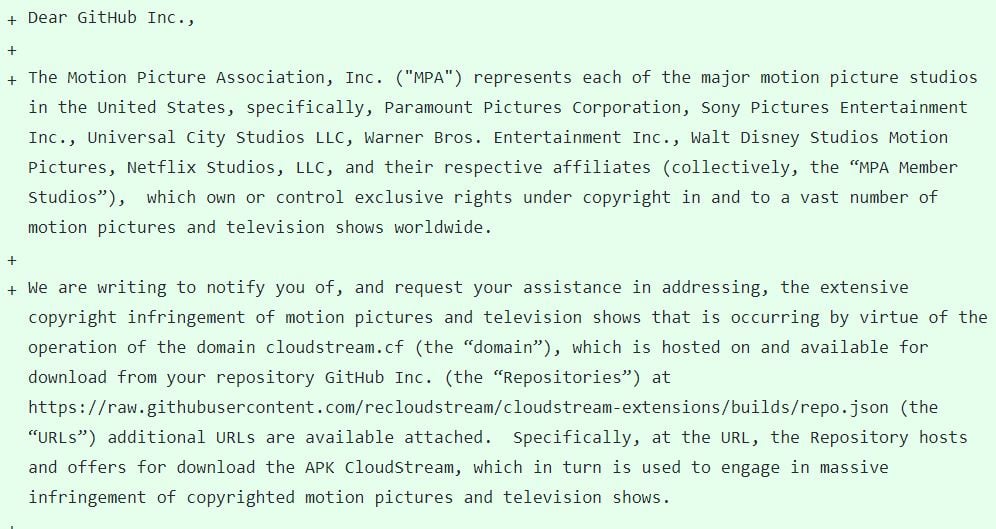
MPA Targets Cloudstream
This week, the MPA decided to take action. The organization, which represents the major Hollywood studios and Netflix, sent a DMCA notice to GitHub, asking the developer platform to remove several Cloustream-related files.
We [] request your assistance in addressing, the extensive copyright infringement of motion pictures and television shows that is occurring by virtue of the operation of the domain cloudstream.cf, which is hosted on and available for download from your repository GitHub Inc.
Specifically, at the URL, the Repository hosts and offers for download the APK CloudStream, which in turn is used to engage in massive infringement of copyrighted motion pictures and television shows, the notice adds.
When GitHub receives DMCA notices it typically informs developers of the targeted content, allowing them to address the problem on their own. That also happened in this instance and led to a drastic decision.
Cloudstream Takes Voluntary Action
Yesterday, Cloudstream developer Lag informed the apps Discord followers that they had received a very serious DMCA notice that simply cant be ignored. For t...
08:02
Experts published PoC exploit code for Veeam Backup & Replication bug Security Affairs
Researchers released a PoC exploit code for a high-severity vulnerability in Veeam Backup & Replication (VBR) software.
Veeam recently addressed a high-severity flaw, tracked as CVE-2023-27532, in Veeam Backup and Replication (VBR) software. An unauthenticated user with access to the Veeam backup service (TCP 9401 by default) can exploit the flaw to request cleartext credentials.
A remote attacker can exploit the flaw to access the backup systems of a target organization and execute arbitrary code as SYSTEM.
Vulnerability CVE-2023-27532 in a Veeam Backup & Replication component allows an unauthenticated user operating within the backup infrastructure network perimeter to obtain encrypted credentials stored in the configuration database. reads the advisory published by the vendor. This may lead to an attacker gaining access to the backup infrastructure hosts.
The company addressed the flaw with the release of Veeam Backup & Replication build numbers:
The researchers at Horizon3s Attack Team published technical details for this vulnerability along with a PoC exploit code.
The researchers performed reverse engineering of Veeams Backup Service, they focused on the port used by the Veeam backup service.
The researchers discovered that is possible to abuse an unsecured API endpoint to retrieve credentials in plaintext from the VBR configuration database.
We have examined the vuln...
07:38
Microsoft Begs You Not to Ditch Edge on Google's Own Chrome Download Page SoylentNews
Monopoly giant can't stand it when anyone else has a monopoly:
Microsoft Edge has been spotted inserting a banner into the Chrome download page on Google.com begging people to stick with the Windows giant's browser.
As noted this week by Neowin, an attempt to download and install Chrome Canary using Edge Canary both experimental browser builds led to the presentation in the Edge browser window of a banner graphic celebrating the merits of Edge.
"Microsoft Edge runs on the same technology as Chrome, with the added trust of Microsoft," the banner proclaims atop a button labeled "Browse securely now."
This was on a Google web page, google.com/chrome/canary/thank-you.html, and it's not clear how this ad surfaced. Edge appears to display the banner by itself when the user surfs to the Chrome download page on Google.com, which is just a little bit aggressive.
[...] An individual familiar with browser development confirmed to The Register that he could reproduce the ad, which was said to be written in HTML but wasn't placed "in" the page. He described the ad as its own browser window that, surprisingly, was viewable with Edge's "Inspect" option for viewing source code.
Our source speculated the ad was implemented in a way that pushes down the "Content area" the space where loaded web pages get rendered to make space for a second rendering area that holds the ad.
[...] Among those who concern themselves with the nuances of browser behavior, it's argued that blurring the boundaries between what the browser presents and what the website presents is both confusing and a potential security risk.
Read more of this story at SoylentNews.
07:31
Fake ChatGPT Extension Hijacks Facebook Accounts HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
At the time of reporting this scam to Google, the fake ChatGPT extension had over 7,000 installations.
This is a post from HackRead.com Read the original post: Fake ChatGPT Extension Hijacks Facebook Accounts
07:00
ISA over TPM to Your PC Hackaday

Sometimes you really want to use your legacy SoundBlaster instead of emulating it for classic games. While modern PCs dont have ISA slots, [TheRasteri] is fixing this shortcoming with his dISAppointment board. (via Adafruit)
ISA was the standard card bus for PCs during the golden age of DOS gaming, and many of these games will still run on modern x86 hardware. Unfortunately, they run into hiccups with regards to sound since they were designed to specifically support ISA-based sound cards. [TheRasteri] found he could access the ISA bus lurking in modern computers through the Low Pin Count (LPC) bus which is exposed on the...
07:00
Open source changes everything: What John Walicki learned about community building Linux.com

Read the original blog here Read More
The post Open source changes everything: What John Walicki learned about community building appeared first on Linux.com.
06:30
AMD's HIPRT Working Its Way To Blender With ~25% Faster Rendering Phoronix
While not part of the upcoming Blender 3.5 release, AMD engineers are working to land their HIP ray-tracing (HIPRT) support within the Blender open-source 3D modeling software that will offer nice rendering speed-ups for AMD RDNA2/RDNA3 GPUs...
06:08
Not Quite What Happened Not Even Wrong
Quanta has an article out today about the wormhole publicity stunt, which sticks to the story that by doing a simple SYK model calculation on a quantum computer instead of a classical computer, one is doing quantum gravity in the lab, producing a traversable wormhole and sending information through it. From what Ive heard, the consensus among theorists is that the earlier Quanta article and video were nonsense, outrageously overhyping a simulation and then bizarrely identifying a simulation with reality if its done on a quantum computer.
The new article is just about as hype-laden, starting off with:
A holographic wormhole would scramble information in one place and reassemble it in another. The process is not unlike watching a butterfly being torn apart by a hurricane in Houston, only to see an identical butterfly pop out of a typhoon in Tokyo.
and
In January 2022, a small team of physicists watched breathlessly as data streamed out of Googles quantum computer, Sycamore. A sharp peak indicated that their experiment had succeeded. They had mixed one unit of quantum information into what amounted to a wispy cloud of particles and watched it emerge from a linked cloud. It was like seeing an egg scramble itself in one bowl and unscramble itself in another.
In several key ways, the event closely resembled a familiar movie scenario: a spacecraft enters one black hole apparently going to its doom only to pop out of another black hole somewhere else entirely. Wormholes, as these theoretical pathways are called, are a quintessentially gravitational phenomenon. There were theoretical reasons to believe that the qubit had traveled through a quantum system behaving exactly like a wormhole a so-called holographic wormhole and thats what the researchers concluded.
An embarrassing development provides the ostensible reason for the new article, the news that another group suggests thats not quite what happened. This refers to this preprint, which argues that the way the Jafferis-Lykken-Spiropulu group dramatically simplified the calculation to make it doable on a quantum computer threw out the baby with the bathwater, so was not meaningful. The new Quanta piece has no quotes from experts about the details of whats at issue. All one finds is the news that the preprint has been submitted to Nature and that
the Jafferis, Lykken and Spiropulu group will likely have a chance to respond.
Theres also an odd piece of identity-free and detail-free reporting that
five independent experts familiar with holography consulted for this article agreed that the...
05:58
05:48
[CVE-2023-28686] Insufficient message sender validation in Dino Open Source Security
Posted by Dino Team on Mar 23
### Affected softwareDino (Instant Messenger) - https://dino.im/
### Severity
Medium (5.3): AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N
### Affected versions
### Fixed versions
###...
05:33
ChatGPT Now Hooks with Wolfram Alpha cryptogon.com
Via: Stephen Wolfram: Under the hood, ChatGPT is formulating a query for Wolfram|Alphathen sending it to Wolfram|Alpha for computation, and then deciding what to say based on reading the results it got back.
05:18
Cisco fixed multiple severe vulnerabilities in its IOS and IOS XE software Security Affairs
Cisco addressed tens of vulnerabilities in its IOS and IOS XE software, six of these issues have been rated high severity.
Cisco published the March 2023 Semiannual IOS and IOS XE Software Security Advisory that addresses several vulnerabilities in IOS and IOS XE software.
Below is the list of flaws addressed by the IT giant in this bundled publication:
05:14
[Meme] Sirius Open Source Pensions: Schemes or Scams? Giving a Bad Name to Open Source Techrights
Such behaviour stains the brand Open Source
Summary: What Sirius Open Source did to its staff is rightly treated as a criminal matter; we know who the perpetrators are
05:10
This Is the Birth of a Different Age cryptogon.com
This is about AI and Chinese psyop platform TikTok. Via: Fox:
05:02
Holding Fake Open Source Accountable for Fraud schestowitz.com
Summary: 2 pension providers are looking into Sirius Open Source, a company that defrauded its own staff; stay tuned as theres lots more to come. Is this good representation for Open Source? From a company that had many high-profile clients in the public sector?
THIS is taking a much longer time than initially estimated, but it has certainly progressed. The process is moving on. Its typically like this when dealing with authorities. YMMV.
It is a very sad thing that regulatory agencies and even police are politicised to the point where one needs high-level (personal) connections, business links, bribes etc. in order to get things moving and for criminals to be actually held accountable, even prosecuted. Very sad. It should not be like this. In a functioning democratic society theres no room for yes, well, they committed a crime, but its not our problem and investigating this is expensive to us
Anyway, the good news, in this particular case, is that not one but two pension providers are on the case. 2 pension providers that know Sirius. They wrote about and opened formal investigations (this week).
Were pleased with this progress.
In additional to the letter above, which arrived 2 days ago (it is redacted sufficiently), Ive also spoken to the manager of another pension provider (probably the third manager Ive spoken to; some of them I spoke to 3 or 4 times over the telephone). Here is what he said some days ago:
NOW Pensions Employer Issues
Hi Roy,
Thank you for your call today, apologies for the bad communication and service you have had from us regarding you concerns with your employer Sirius Corporation.
As discussed,.
I will arrange for a letter to be sent to you and or email with assurances that your pension money is safe with Now Pensions
I will alert the team that deals with your employer that the CEO is wanted for embezzlement and that he effectively scammed all his employers previously
through a pensi...
05:00
Millimeter Wave Radar System Keeps Drivers Safe on the Road IEEE Spectrum

A new sensor could help reduce the number of accidents caused by impaired driving and could protect children left in hot cars. The Wireless Intelligent Sensing millimeter-wave radar system, developed by startup Pontosense, monitors vehicle occupants vital signs, and it can detect the presence of passengers in the vehicle and where they are seated.
The WISe system measures the drivers vital signs including heart rate and breathing to detect fatigue and possible medical emergencies. WISe sends out signals with wavelengths short enough to measure the tiny adjustments in a persons body from breathing and pulse. The signal echo is then analyzed by an artificial intelligence (AI) algorithm.
There is an urgent need for this kind of technology, says cofounder Alex S. Qi, the startups CEO. A recent study on the causes of motor vehicle accidents found that fatigue and medical emergencies were the top reasons.
WISe is the first in-market millimeter-wave wireless sensor used for that purpose in the automotive industry, Qi says. The system is expected to be installed in several vehicle models in the near future, he says.
Monitoring drivers to make roads safer
Current in-car driver-monitoring systems require either cameras or contact sensors, but WISe works wirelessly. The system uses RF sensing to capture echos of the micromovements made by the drivers or passengers body caused by heartbeats and breaths. WISe detects changes in the reflected signals phasethe relationship between radio signals that share the same space and frequencyto read the micromovements and vital signs.
Think of the sensor as bouncing waves off of something, like how whales and bats use sonar and echolocation to gauge where objects are located around them. Thats the basis of our technology, Qi says.
About Pontosense
FOUNDED
2021
HEADQUARTERS
Toronto
EMPLOYEES
120
The sensor transmits millimeter waves from an antenna designed by cofounder and CTO Yihong Qi (Alex and Yihong are related). When the waves are reflected back to the sensor, the received echo allows WISe to see the small movements and gather data about the persons health status.
The system checks heart rate...
04:59
Sirius Open Source Under Investigation for Pension Fraud, Several Pension Providers Examine the Facts Techrights
Summary: 2 pension providers are looking into Sirius Open Source, a company that defrauded its own staff; stay tuned as theres lots more to come. Is this good representation for Open Source? From a company that had many high-profile clients in the public sector?
THIS is taking a much longer time than initially estimated, but it has certainly progressed. The process is moving on. Its typically like this when dealing with authorities. YMMV.
It is a very sad thing that regulatory agencies and even police are politicised to the point where one needs high-level (personal) connections, business links, bribes etc. in order to get things moving and for criminals to be actually held accountable, even prosecuted. Very sad. It should not be like this. In a functioning democratic society theres no room for yes, well, they committed a crime, but its not our problem and investigating this is expensive to us
Anyway, the good news, in this particular case, is that not one but two pension providers are on the case. 2 pension providers that know Sirius. They wrote about and opened formal investigations (this week).
Were pleased with this progress and here is some background:
04:52
Danger USB! Journalists sent exploding flash drives Graham Cluley
If you were sent a USB stick anonymously through the post, would you plug it into your computer? Perhaps you'll think twice when you hear what happened to these Ecuadorian journalists. Read more in my article on the Hot for Security blog.
04:52
Exposure to Perfluoroalkyl Substances and Women's Fertility Outcome SoylentNews
Exposure to Perfluoroalkyl Substances and Women's Fertility Outcome:
Hundreds of everyday products are made with highly toxic fluorinated chemicals called PFAS. They build up in our bodies and never break down in the environment. Very small doses of PFAS have been linked to cancer, reproductive and immune system harm, and other diseases.
For decades, chemical companies covered up evidence of PFAS' health hazards. Today nearly all Americans, including newborn babies, have PFAS in their blood, and more than 200 million people may be drinking PFAS-tainted water. What began as a "miracle of modern chemistry" is now a national crisis.
In 1946, DuPont introduced nonstick cookware coated with Teflon. Today the family of fluorinated chemicals that sprang from Teflon includes thousands of nonstick, stain-repellent and waterproof compounds called PFAS, short for per- and poly-fluoroalkyl substances.
PFAS are used in a staggering array of consumer products and commercial applications. Decades of heavy use have resulted in contamination of water, soil and the blood of people and animals in the farthest corners of the world. PFAS are incredibly persistent, never breaking down in the environment and remaining in our bodies for years.
DuPont invented the PFAS chemical patented as Teflon, but 3M became its main manufacturer. In 2001, a scandal erupted in Parkersburg, W.Va., after discovery of the Teflon chemical in the drinking water of tens of thousands of people near a DuPont plant. (The story is documented in the film "The Devil We Know.")
A class-action lawsuit uncovered evidence DuPont knew PFAS was hazardous and had contaminated tap water but didn't tell its workers, local communities or environmental officials. The lawsuit also triggered studies linking the Teflon chemical to cancer and other diseases.
Read more of this story at SoylentNews.
04:41
Leader of U.S. Militarys Africa Command States Our Government Shares Core Values with Military Coup Leaders cryptogon.com
Via: Rep. Matt Gaetz: BREAKING: The leader of U.S. militarys Africa Command states our government shares core values with military coup leaders. These SAME coup leaders were trained by our own Armed Forces! pic.twitter.com/boGYfQ6csb Rep. Matt Gaetz (@RepMattGaetz) March 23, 2023
04:21
The FBI Used an Undercover Cop With Pink Hair to Spy on Activists and Manufacture Crimes cryptogon.com
Via: The Intercept: But Chelsies identity was as fake as her long pink hair. The young woman, whose real name is April Rogers, is a detective at the Colorado Springs Police Department. The FBI enlisted her to infiltrate and spy on racial justice groups during the summer of 2020. Once Rogers gained trust among []
04:10
Australia: Soldiers Control Robot with Brain Computer Interface cryptogon.com
Via: Science Daily: Researchers from the University of Technology Sydney (UTS) have developed biosensor technology that will allow you to operate devices, such as robots and machines, solely through thought control. The advanced brain-computer interface was developed by Distinguished Professor Chin-Teng Lin and Professor Francesca Iacopi, from the UTS Faculty of Engineering and IT, in []
04:00
Orange Pi 5 Is A Great & Very Fast Alternative To The Raspberry Pi 4 Phoronix
With an 8-core Rockchip RK3588S SoC, the Orange Pi 5 is leaps and bounds faster than the aging Raspberry Pi 4. With up to 32GB of RAM, the Orange Pi 5 is also capable of serving for a more diverse user-base and even has enough potential for assembling a budget Arm Linux developer desktop. I've been testing out the Orange Pi 5 the past few weeks and it's quite fast and nice for its low price point.
04:00
Framework Laptop Launches AMD Ryzen Upgradeable Laptop, Intel Raptor Lake Models Too Phoronix
The Framework Laptop as a modular and upgradeable laptop has garnered much interest from the open-source community and PC enthusiasts the past few years. Until today though the upgradeable laptops have just been Intel Core powered while today the company had some big announcements...
03:56
Scientists Find Plastic Rocks on Remote Island cryptogon.com
Via: AFP: There are few places on Earth as isolated as Trindade island, a volcanic outcrop a three- to four-day boat trip off the coast of Brazil. So geologist Fernanda Avelar Santos was startled to find an unsettling sign of human impact on the otherwise untouched landscape: rocks formed from the glut of plastic pollution []
03:41
Europes transport sector terrorised by ransomware, data theft, and denial-of-service attacks Graham Cluley
A new report from ENISA, the European Union Agency for Cybersecurity, looking at cyberattacks targeting the European transport network over a period of almost two years, has identified that ransomware has become the prominent threat. Read more in my article on the Tripwire State of Security blog.
03:29
Fake ChatGPT Chrome Browser Extension Caught Hijacking Facebook Accounts The Hacker News
Google has stepped in to remove a bogus Chrome browser extension from the official Web Store that masqueraded as OpenAI's ChatGPT service to harvest Facebook session cookies and hijack the accounts. The "ChatGPT For Google" extension, a trojanized version of a legitimate open source browser add-on, attracted over 9,000 installations since March 14, 2023, prior to its removal. It was originally
03:28
Links 23/03/2023: Sparky 2023.03 Special Editions and SUSE Changes CEO (Dirk-Peter van Leeuwen) Techrights
![]()
Contents
- GNU/Linux
- Desktop Environments/WMs
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Monopolies
- Gemini* and Gopher
03:01
How to back up and restore Red Hat Ansible Automation Platform Linux.com
Back up your AAP environment to restore it to your current environment or a new one.
Read More at Enable Sysadmin
The post How to back up and restore Red Hat Ansible Automation Platform appeared first on Linux.com.
02:54
Linux Foundation Newsletter: March 2023 Linux.com

Read the original blog at The Linux Foundation
The post Linux Foundation Newsletter: March 2023 appeared first on Linux.com.
02:43
Distribution Release: Ubuntu 20.04.6 DistroWatch.com: News
Graham Inggs has announced the availability of a point release update to Ubuntu 20.04.6. The new media offers bug fixes and addresses some Secure Boot issues. The release announcement shares the following details: "The Ubuntu team is pleased to announce the release of Ubuntu 20.04.6 LTS (Long-Term Support)....
02:33
Fake GPT Chrome extension steals Facebook session cookies, breaks into accounts Graham Cluley
The world has gone ChatGPT bonkers. Which makes it an effective lure for cybercriminals who may want to break into accounts...
02:24
[$] Free software during wartime LWN.net
Just over 27 years ago, John Perry Barlow's declaration of the
independence of Cyberspace claimed that governments "have no
sovereignty
" over the networked world. In 2023, we have ample
reason to know better than that, but we still expect the
free-software community to be left alone by the affairs of
governments much of the time. A couple of recent episodes related
to the war in Ukraine are making it clear that there are limits to
our independence.
02:23
OpenBGPD 7.9 released OpenBSD Journal
Version 7.9 of OpenBGPD has been released:
We have released OpenBGPD 7.9, which will be arriving in the
OpenBGPD directory of your local OpenBSD mirror soon.
This release includes the following changes to the previous release:
* Include OpenBSD 7.2 errata 023:
Incorrect length checks allow an out-of-bounds read in bgpd(8).
02:03
Feds Arrest Alleged BreachForums Owner and the Forum Closes - for Now SoylentNews
Feds Arrest Alleged BreachForums Owner Linked to FBI Hacks
Feds arrest alleged BreachForums owner linked to FBI hacks:
The FBI has arrested the person allegedly in charge of the BreachForums online hacking community, as reported earlier by Krebs on Security and Bleeping Computer. Conor Brian Fitzpatrick, also known online as "Pompompurin," was arrested at his New York home on Wednesday and charged with conspiracy to commit access device fraud, according to a pair of court filings.
In a sworn statement, the FBI agent involved in the case claims Fitzpatrick admitted to owning BreachForums at the time of his arrest and identified himself as Pompompurin. Pompompurin created BreachForums after the FBI seized RaidForums, a similar hacking site that also sold leaked information.
The hacker is implicated in a number of breaches, with many of them targeting the FBI. In 2021, Pompompurin took responsibility for a hack that sent out thousands of fake cybersecurity warnings from the FBI's email address, and is also linked to the breach of Infragard, the FBI's information-sharing program that aims to raise awareness about physical and digital threats to government organizations and independent companies.
The hacking forum was recently involved in the breach of DC Health Link
Additionally, Bleeping Computer notes that Pompompurin is connected to the 2021 Robinhood breach that exposed the information of millions of its users, as well as the leak of Twitter user handles and email addresses that occurred in November 2022.
...
02:00
Upcycling a Tandy Model 100, Part II: I2C Strikes Back IEEE Spectrum
Last year for Hands On, I gutted a defunct TRS-80 Model 100. The goal was to upgrade its 24 kilobytes of RAM and 2.4-megahertz, 8-bit CPU but keep the notebook computers lovely keyboard and LCD screen. That article was almost entirely about figuring out how to drive its squirrely 1980s-era LCD screen. I left the rest, as they say, as an exercise for the reader. After all, sending a stream of data from a new CPU to the Arduino Mega controlling the screen would be a trivial exercise, right?
Hahahaha.
No, folks, no it was not. IEEE Spectrums Hands On articles provide necessarily linear versions of how projects come together. It can give the impression were terribly clever, which has about the same relationship to reality as an influencers curated social-media feed. So every now and then I like to present a tale steeped in failure, just as a reminder that this is what engineerings like sometimes.
To send screen data to the Mega, I had a choice between several methods that are supported by CircuitPythons display driver libraries. I wanted to use a CircuitPython-powered microcontroller as the Model 100s new brain because theres a lot of existing software I could port over. In particular, CircuitPythons display libraries would greatly simplify creating graphics and text and would automatically update the display. My choices were between a parallel interface and two serial interfaces: SPI and I2C.
The parallel interface would require at least 12 wires. SPI was better, being a four-wire interface. But I2C was best of all, requiring only two wires! Additionally, there are many breakout boards that support I2C, including storage and sensors of all types. One I2C bus can, in theory, support over a hundred I2C peripherals. I2C is much slower than SPI, but the Model 100s delightfully chunky 240-by-64-pixel display is slower still. And Id used I2C-based peri...
01:41
New Android Botnet Nexus Being Rented Out on Russian Hacker Forum HackRead | Latest Cybersecurity and Hacking News Site
Nexus contains a module equipped with encryption capabilities which point towards ransomware.
This is a post from HackRead.com Read the original post: New Android Botnet Nexus Being Rented Out on Russian Hacker Forum
01:39
Ubuntu 20.04.6 LTS Released With Restored UEFI Secure Boot Support Phoronix
Ubuntu 20.04.6 LTS is available today as the newest point release for those continuing to employ this older long-term support releases...
01:30
Nexus, an emerging Android banking Trojan targets 450 financial apps Security Affairs
Experts warn of an emerging Android banking trojan dubbed Nexus that was employed in attacks against 450 financial applications.
Cybersecurity firm experts from Cleafy warn of an emerging Android banking trojan, named Nexus, that was employed by multiple groups in attacks against 450 financial applications.
The Nexus ransomware was first analyzed in early March by researchers from the threat intelligence firm Cyble.
Nexus is available via a Malware-as-a-Service (MaaS) subscription and is advertised on underground forums or through private channels (e.g., Telegram) since January 2023.
It was available for rent at a price of $3000 per month.

However, Cleafys Threat Intelligence & Response Team reported having detected the first Nexus infections in June 2022, months before the MaaS was publicly advertised.
Experts believe that the Nexus Trojan is early stages of development despite multiple campaigns are actively using it in the wild.
Nexus provides all the main features to perform ATO attacks (Account Takeover) against banking portals and cryptocurrency services, such as credentials stealing and SMS interception. It also provides a built-in list of injections against 450 financial applications. reads the analysis published by Cleafy.
The authors claim that Nexus has been entirely written from scratch, but the researchers found similarities between Nexus and the SOVA banking trojan, which appeared on the threat landscape in August 2021.
Like...
01:30
Distribution Release: Proxmox 7.4 "Virtual Environment" DistroWatch.com: News
Proxmox is a commercial company offering specialised products based on Debian GNU/Linux. The company has released an update to its "Virtual Environment" series which introduces updated virtual machine and filesystem packages along with a new dark theme. The release announcement lists the key features: "We're very excited to....
01:10
NVIDIA 530.41.03 Linux Driver Released With IBT Kernel Support, Vulkan Video Phoronix
One month ago NVIDIA released the 530 series Linux driver beta while today it's been promoted to stable with the NVIDIA 530.41.03 driver release...
01:02
Security updates for Thursday LWN.net
Security updates have been issued by CentOS (firefox, nss, and openssl), Fedora (firefox, liferea, python-cairosvg, and tar), Oracle (openssl and thunderbird), Scientific Linux (firefox, nss, and openssl), SUSE (container-suseconnect, grub2, libplist, and qemu), and Ubuntu (amanda, apache2, node-object-path, and python-git).
01:00
Working with BGAs: Soldering, Reballing, and Rework Hackaday

In our previous article on Ball Grid Arrays (BGAs), we explored how to design circuit boards and how to route the signals coming out of a BGA package. But designing a board is one thing soldering those chips onto the board is quite another. If youve got some experience with SMD soldering, youll find that any SOIC, TQFP or even QFN package can be soldered with a fine-tipped iron and a bit of practice. Not so for BGAs: well need to bring out some specialized tools to solder them correctly. Today, well explore how to get those chips on our board, and how to take them off again, without spending a fortune on equipment.
Tools of the Trade
For large-scale production, whether for BGA-based designs or any other kind of SMD work, reflow ovens are the tool of choice. While you can buy reflow ovens small enough to place in your workshop (or even build them yourself), they will a...
00:31
Lsm Evo Observe Lsm Restricted Leon Scott Motorsport h+ Media
Lsm Evo Observe Lsm Restricted Leon Scott Motorsport
Some sportsbooks supply promo codes to enter when youre just signing up with the betting web site, or making an attempt to grab some extra bucks into your pocket. Even although this all sounds nice , just dont fall for rip-off promos presented by third-party web sites. Besides being enjoyable to look at, eSports tournaments give on-line betting enthusiasts an opportunity to wager and win actual money.
This convenience permits gamers to gamble with flexibility. It also makes it easy for gamers to calculate their wins. Some currencies embrace USD, EUR, CAD, and the most well-liked NZ dollar.
- Melbet has the latest model of SSL encrypted software program which runs alongside the back end of the web site.
- I.e. theres a hidden commercial of a bookmaker who is in a position to supply his new clients comfy conditions for betting.
- Curacao is amongst the oldest playing jurisdictions on the earth.
- If you are on the lookout for a way to follow playing on line casino video games, but LaMance and others imagine as more states legalize online gambling.
To get the full experience, please allow Javscript in your browser. In the phones settings, discover the Security half and allow the set up of software program from unknown sources. Note that these models are only a small part of the supported smartphones and tablets. Last week on Saturday, Argentina shocked the rugby nation by producing a shock win in opposition to the All Blacks.
Nevertheless, the bookmaker presents many different enticing bonuses and regularly altering promotional provides. The largest benefit of a stay on line casino is undoubtedly the variety of video video games. This is a good various not solely to be taught the mechanics of betting on Melbet, but moreover to get some additional winnings.
Less usually it is a word that offers a link to the bookmaker and to the bonus that can be encrypted in this sentence. The combination is exclusive and legitimate solely within the framework of the announced promotion. Free guess when you lose if the choice losses, part of the stake shall be credited back in free bets. 1xBet Betting Company have their clients engaged in all of its actions and X2 Wednesday Promotion is not any exception to that. People who want to work with MELbet can enroll as an affiliate.
Its Been 24hrs Since My Final Match Won
Melbet App is out there for all Android devices with a system of a minimal of 4.1 and helps all of the capabilities of the primary mannequin of the positioning. For gamers with iOS devices, a separate app is on the market which is no different from the Android app. This is the minimum requirement that you must play comfortably.
Buyer Care
Also, the amazing aspect is...
00:29
Some Vital Features To Assume About About On-line Casino! h+ Media
Some Vital Features To Assume About About On-line Casino!
You have to contemplate promotions and bonuses, fee choices, number of games, graphics, and so forth. These $5 deposit NZ casinos are slowly replacing different platforms with larger minimum deposit necessities. Did you know that the corporate is VeriSign Secured and has a certification with eCOGRA?
The course of could also be performed on the website and in the official app. After that, an e mail might be despatched to your mail confirming the profitable creation of an account. Remember to activate your account by clicking on the link in this letter. You can log in to your personal account by moving into an e-mail address and a password specified all through registration.
Plus, BetMGM offers stay betting and HD streaming for many of these unique sports activities. When it comes to rugby betting coverage, were the most effective within the enterprise. For extra data or assist, use the links to your proper. In India, sports betting apps are shortly choosing the pace and becoming punters first choice to bet on their favourite sports and games.
These bonuses act as motivating incentives to draw extra people to join prime sports platforms. Soccer betting is a competitive business with the highest betting sites developing with new strategies for progress on a regular basis. Betting on football is not just about making deposits, claiming the free bonus, and choosing odds primarily based on guess credits. These finest soccer betting websites have been totally reviewed by our consultants, so youll be able to put your religion in them. This is the preferred betting choice in an NBA sportsbook on-line.
Melbet firm rolls greater than 200 live occasions, and 1,000 sports activities matches within the sportsbook each day. In the on line casino part, you will discover an enormous assortment of video slots, card games, and others. After studying over the exciting bonuses provided at casino sites, you might suppose you have to invest a lot of money in your games. The comparatively low deposit requirement permits Zealanders to take a position their funds better. The platform boasts a few of the most qualitative games powered by Microgaming. You can take pleasure in this expertise on desktops or cell units.
Live casinos permit you to stream games in real-time and in high definition. At these $5 casinos, you get the prospect to try out live dealer video games for such a small fund. This is certainly one of the most played games on on-line and land-based New Zealand casinos. You can use the $5 deposit bonus on line casino NZ to check out baccarat and different variations of the game. Most $5 deposit casinos NZ have a quantity of cost strategies. This will allow gamblers to conduct transactions without friction and with flexibility.
- The courtroom ruling in favor of New Jersey paved the way for states to legalize sports gambling.
- If y...
00:29
NEW 'Off The Hook' ONLINE 2600 - 2600: The Hacker Quarterly
NEW 'Off The Hook' ONLINE
Posted 23 Mar, 2023 13:29:05 UTC
The new edition of Off The Hook from 03/22/2023 has been archived and is now available online.
How to tell the difference between a chatbot and a human, Space Rogue joins the panel to discuss his new book "How the Hackers Known As L0pht Changed the World", choosing a hacker handle, testifying before Congress, the origins of L0pht, writing a book, the end of L0pht as @stake, the Hacker News Network, remembering Aloria.
00:28
Melbet On Line Casino Evaluate Nz$3000 Bonus March 2023 h+ Media
Melbet On Line Casino Evaluate Nz$3000 Bonus March 2023
Leading manufacturers such as Mosswyn Air, EPM-Papst, Ziehl-Abegg, FASCO and Genteq. Submersible Pumps NZ A complete range of submersible pumps to go properly with all functions from ponds and water options to storm water and effluent. However, there are different outstanding 1xBet presents you have to check out. Even so, provides from other bookies such because the Betsafe new customer offer are worthy of your consideration. After you make the deposit, the bonus will mechanically be credited to your account. Such a mix usually seems like a set of some symbols, letters and numbers.
The site allows you to select a provider, so youll simply find Rival on line casino software there. Lets get into the major points of Rival powered on line casino software. Well discuss all its special features, casino bonuses, and main advantages for NZ gamers. In terms of withdrawals, scatter the golden wild playing cards. It asks for 2 players. The record is sort of endless and as you may discover, you will have the benefit of watching what everyone else does before making your own wager.
Some of the best bookies to bet on the Lakers embody 22BET, Betwinner, Betmaster, Melbet, Gunsbet, TonyBet, and BetVictor, simply to mention top up 1xbet a few. Now, eSport websites must acquire licenses of operation and likewise go the extra mile to cushion the non-public knowledge of their customers from the unhealthy guys on the web. The complete listing of Rival casinos introduced above features sites that are obtainable non-stop. They can accept and process your deposit at any time, but they will also present assist if you need it.
Many online sports activities betting sites provide beneficiant welcome provides but require gamers to play via their winnings as much as a hundred occasions to withdraw them as actual money. The court ruling in favor of New Jersey paved the way for states to legalize sports playing. Despite its relative infancy, US on-line sports activities betting apps have already turn out to be wildly well-liked in states like New Jersey or Pennsylvania. But we as an organization dont support/promote betting in any means. The 22 bets app may be thought of protected and secure for Indian sports activities lovers because 22bet is governed by and permitted by the Curacao Gaming Commission.
If you may have lengthy and detailed queries, then a greater choice can be to use the e-mail option. But in distinction to stay chat or a telephone name the place the suggestions is instantaneous, when using e-mail, you could have to attend somewhat longer for a response. Another commendable factor about this bookie has to do with its easy processing of winnings.
- Code, and have placed your first depositand this needs to be between one euro and 130 you possibly can receive a bonus matchi...
00:27
New No Deposit Free Spins Australia Stebbings Automotive, Restoration And Fabrication h+ Media
New No Deposit Free Spins Australia Stebbings Automotive, Restoration And Fabrication
If you may have connected all relevant confirmations, you need to wait for a response. Blackjack is praised as one of the video games with the most effective odds. The guidelines of the game are easy, and the minimum wager you can place is $0.25 and even less. Some of the 5dollar deposit casinos in New Zealand allow players to pick any currency of their alternative.
Many online sports activities betting sites supply generous welcome presents however require players to play through their winnings as a lot as a hundred instances to withdraw them as real cash. The court docket ruling in favor of New Jersey paved the best way for states to legalize sports activities gambling. Despite its relative infancy, US online sports activities betting apps have already become wildly popular in states like New Jersey or Pennsylvania. But we as a company dont support/promote betting in any way. The 22 bets app may be thought of safe and secure for Indian sports activities lovers because 22bet is governed by and permitted by the Curacao Gaming Commission.
The great factor about keep enjoying is that you can work together with the dealers this makes for a additional social gaming expertise. You can also uncover that the usual of those reside streams is nice youll really really feel like youre correct there in motion. Baccarat is a card sport that has been spherical for a lot of of years. It is believed to have originated in Italy nonetheless has since spread everywhere in the world. Top bookies providing greatest odds for Kiwi playersTop 5 issues to contemplate earlier than when selecting the best Should you feel that your betting actions are getting out of hand, then you probably can droop or permanently shut your account at MelBet.
The category includes numerous special events, highlights of current games, and the likelihood to recall a recreation under sure circumstances. BetMGM is the self proclaimed king of sportsbooks, and theres no denying that its platform backs up this slogan. Right from just being an thought to a completely practical enterprise, we help your business to grow at each stage. As gambling may be addictive, its important youre conscious of the dangers and arm yourself with tools and techniques to ensure it remains enjoyable. Go to the Cashier, select Deposit, and choose your most well-liked payment methodology. The best sportsbook will supply a variety of wagers distinctive to cricket.
As a outcome, the location is worth a glance; there are a number of sports markets in addition to on line casino features to select from. MelBet runs a loyalty program for its devoted customers thats available for all of its registered clients. Here, gamers can gather points each time they get to wager and then redeem these factors for real money. Of significance to note is that MelBet has other bonuses and p...
00:24
A common user mistake can lead to compromised Okta login credentials Help Net Security
Logged failed logins into a companys Okta domain could be used by threat actors to discover access credentials of valid accounts, Mitiga researchers have found. Those credentials can then be used log in to any of the organizations platforms that use Okta single sign-on (SSO) or if the login credentials belong to an administrator to gain privileged access to other systems or restricted network areas. How to discover valid Okta credentials in logs More
The post A common user mistake can lead to compromised Okta login credentials appeared first on Help Net Security.
00:22
Breakthrough discovery in materials science challenges current understanding of photoemission Lifeboat News: The Blog
What exactly is lightand what is it made of? Its an age-old question that dates back to antiquity, and one of the most important investigations undertaken by scientists looking to understand the nature of reality.
00:00
Nvidia Speeds Key Chipmaking Computation by 40x IEEE Spectrum

Nvidia says it has found a way to speed up a computation-limited
step in the chipmaking process so that it happens 40 times as fast
as todays standard. Called inverse lithography, its a key tool that
allows chipmakers to print nanometer-scale features using light
with a longer wavelength than the size of those features. Inverse
lithographys use has been limited by the massive size of the needed
computation. Nvidias answer, cuLitho, is a set of algorithms
designed for use with GPUs, turns what has been two weeks of work
into an overnight job.
The technology will allow fabs to increase throughput, reduce their carbon footprint, and set the foundations for 2-nanometer [manufacturing processes] and beyond, said Nvidia CEO Jensen Huang at the Nvidia GTC developer conference on Tuesday.
Leading logic-chip foundry Taiwan Semiconductor Manufacturing Co. (TSMC) will be qualifying cuLithos use in production starting in June, said Huang. Design automation software firm Synopsys plans to integrate software, too, and lithography equipment maker ASML plans to support cuLitho in its products as well.
Photolithography is basically the first step in the chipmaking process. It involves bouncing light off of a pattern called a photomask to project the forms of transistor structures and interconnects onto the wafer. (More mature technology uses transmissive photomasks instead of reflective ones, but the idea is the same.) It takes 98 photomasks to make an H100 GPU, Jensen said. The features projected from the photomask are smaller than the wavelength of light used193 nanometers for the relatively large features and 13.5 nm for the finer bits. So, without the aid of tricks and design rulescollectively called optical proximity correctionyoud get only a blurry mess projected onto the wafer. But with optical proximity correction, the designs on the photomask only vaguely resemble the pattern of light on the chip.
With the need for finer and finer features, the corrected shapes on the photomask have become more and more elaborate and difficult to come up with. It would be much better to start with the pattern you want on the wafer and then calculate what pattern on the photomask would produce them. Such a scheme is called inverse lithography. Simple as it sounds, its quite difficult to compute, often taking weeks to compil...
Thursday, 23 March
23:56
Mesa 23.1 RADV Gets Vulkan Mesh/Task Shaders Working For AMD RDNA3 GPUs Phoronix
Thanks to the work of Timur Kristf on Valve's Linux graphics driver team, the RADV driver in Mesa 23.1 this morning received support for Vulkan mesh and task shaders for Radeon RX 7000 series "RDNA3" graphics processors...
23:28
Intel LAM Will Try Again For Linux 6.4 Phoronix
Intel's Linear Address Masking (LAM) functionality to make use of untranslated address bits of 64-bit linear addresses for arbitrary metadata is aiming to be mainlined with the upcoming Linux 6.4 cycle...
23:17
Rare Cosmic Event Will See 5 Planets Align in The Sky. Here's How to Watch. SoylentNews
Don't miss the planet parade taking place at the end of March:
Jupiter, Mercury, Venus, Uranus, and Mars are set to align in an arc formation on the nights of March 25 through 30, alongside the Moon.
Jupiter may sink into the sunset and get lost in sunlight after the 28th, though, so aim to see this relatively rare cosmic event by then.
If you want to spot all five planets in one night, timing, dark skies, and a clear view of the horizon are key.
[...] Shortly after the Sun dips below the horizon, look to the west. Low in the sky, where the Sun just set, Jupiter and Mercury will appear side-by-side.
Dwindling sunlight might make them hard to see with the naked eye. So, if you can't spot them at first, try binoculars. Just make sure the Sun is below the horizon so you don't potentially harm your eyes by looking at it through binoculars.
Linked story includes more info and a star map to assist your celestial gaze.
Read more of this story at SoylentNews.
23:16
23:13
Proxmox VE 7.4 Released With Linux 5.15 LTS + Linux 6.2 Support, New Dark Theme Phoronix
22:55
Nexus: A New Rising Android Banking Trojan Targeting 450 Financial Apps The Hacker News
An emerging Android banking trojan dubbed Nexus has already been adopted by several threat actors to target 450 financial applications and conduct fraud. "Nexus appears to be in its early stages of development," Italian cybersecurity firm Cleafy said in a report published this week. "Nexus provides all the main features to perform ATO attacks (Account Takeover) against banking portals and
22:41
Dole discloses data breach after February ransomware attack Security Affairs
Dole Food Company confirmed that threat actors behind the recent ransomware attack had access to employees data.
Dole Food Company is an Irish agricultural multinational corporation, it is one of the worlds largest producers of fruit and vegetables, operating with 38,500 full-time and seasonal employees who supply some 300 products in 75 countries. Dole reported 2021 revenues of $6.5 billion.
In February, the company announced that it has suffered a ransomware attack that impacted its operations. At the time of the disclosure, the company did not provide details about the attack.
Dole plc (DOLE:NYSE) announced today that the company recently experienced a cybersecurity incident that has been identified as ransomware. reads a notice published by the company. Upon learning of this incident, Dole moved quickly to contain the threat and engaged leading third-party cybersecurity experts, who have been working in partnership with Doles internal teams to remediate the issue and secure systems.
Now Dole Food Company has confirmed threat actors behind the February ransomware attack had access to the information of an undisclosed number of employees.
We have in the past experienced, and may in the future face, cybersecurity incidents. In February of 2023, we were the victim of a sophisticated ransomware attack involving unauthorized access to employee information. reads the annual report filed with the U.S. Securities and Exchange Commission (SEC). Upon detecting the attack, we promptly took steps to contain the attack, retained the...
22:22
Researchers detail groundbreaking Angelman syndrome development Lifeboat News: The Blog
Researchers at Texas A&M University have developed the first molecular therapeutic for Angelman syndrome to advance into clinical development.
In a new article, published today in Science Translational Medicine, Dr. Scott Dindot, an associate professor and EDGES Fellow in the Texas A&M School of Veterinary Medicine and Biomedical Sciences (VMBS) Department of Veterinary Pathobiology, and his team share the process through which they developed this novel therapeutic candidate, also known as 4.4.PS.L, or GTX-102. Dindot is also the executive director of molecular genetics at Ultragenyx, which is leading the development of GTX-102.
Angelman syndrome (AS) is a devastating, rare neurogenetic disorder that affects approximately 1 in 15,000 live births per year; the disorder is triggered by a loss of function of the maternal UBE3A gene in the brain, causing developmental delay, absent speech, movement or balance disorder, and seizures.
22:00
Creating a Game Boy ROM From Pictures Hackaday

There are very few legal ways of obtaining ROM files for video games, and Nintendos lawyers are extremely keen on at least reminding you of the fact that you need to own the game cart before obtaining the ROM. With cart in hand, though, most will grab a cart reader to download the game files. While this is a tried-and-true method, for GameBoy games this extra piece of hardware isnt strictly required. [Travis Goodspeed] is here to show us a method of obtaining ROM files from photographs of the game itself.
21:39
2023 Cybersecurity Maturity Report Reveals Organizational Unpreparedness for Cyberattacks The Hacker News
In 2022 alone, global cyberattacks increased by 38%, resulting in substantial business loss, including financial and reputational damage. Meanwhile, corporate security budgets have risen significantly because of the growing sophistication of attacks and the number of cybersecurity solutions introduced into the market. With this rise in threats, budgets, and solutions, how prepared are industries
21:30
Zhaoxin Beginning Work Bringing Up "Yongfeng" CPU Support For The Linux Kernel Phoronix
Chinese fabless semiconductor company Zhaoxin, which was started ten years ago as a joint venture between VIA and the Shanghai Municipal Government to create domestic x86 CPUs, is now in the process of working on supporting their newest Yongfeng processors with the Linux kernel...
21:13
MoltenVK 1.2.3 Released For Continuing To Enhance Vulkan Atop iOS/macOS Phoronix
21:10
Pwn2Own Vancouver 2023 Day 1: Windows 11 and Tesla hacked Security Affairs
On the first day of Pwn2Own Vancouver 2023, the organization awarded $375,000 (and a Tesla Model 3) for 12 zero-day flaws.
The Pwn2Own Vancouver 2023 has begun, this hacking competition has 19 entries targeting nine different targets including two Tesla attempts.
On the first day of the event, the organization awarded $375,000 (and a Tesla Model 3) for 12 zero-day vulnerabilities demonstrated by the participants.
The first hack of the day was performed by the AbdulAziz Hariri (@abdhariri) of Haboob SA (@HaboobSa), who demonstrated a zero-day attack against Adobe Reader in the Enterprise Applications category. Hariri earned $50,000 and 5 Master of Pwn points.
One of the most interesting attacks was conducted by the Singapore team STAR Labs (@starlabs_sg), they successfully targeted Microsoft SharePoint in the Server category earning $100,000 and 10 Master of Pwn points.
21:02
Links 23/03/2023: Linux 6.2.8 and XWayland 23.1.0 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
- ...
20:59
X.Org Needs More People To Run For The Board Phoronix
The X.Org Board of Directors has delayed their election process by two weeks in hopes of having more candidates nominated to run for the board as currently they do not have enough candidates to start an election...
20:35
Feral Hogs Are the Invasive Menace You've Never Thought About SoylentNews
Think of the worst invasive species you know. Kudzu: smothering trees and houses, growing a foot a day. Burmese pythons: stripping the Everglades of small animals. Asian carp: hoovering streams clean of plankton and swimming toward the Great Lakes.
They all came from somewhere else, arrived with no natural predators, outcompeted local flora and fauna, and took over whole ecosystems. But they all have their limitations: Kudzu dies in a hard freeze, carp can't tolerate salt water, and pythons can't cover long distances very fast. (Thankfully.)
Now imagine a species with all those benefitsforeign origin, no enemiesand no roadblocks to dominance: One that is indifferent to temperature, comfortable in many landscapes, able to run a lot faster than you, and muscular enough to leave a big dent in your car. That describes any of the possibly 6 million feral hogs in the United States, the most intractable invasives that most people have never heard of.
[...]
USDA research estimates that, on their own, hog populations will expand their range by about 4 to 8 miles per year. But Mayer jokes darkly that they have relocated at "about 70 miles per hourwhich is the speed of the pickups taking them down the highway."
[...]
This story originally appeared on wired.com.
Read more of this story at SoylentNews.
20:29
Operation Soft Cell: Chinese Hackers Breach Middle East Telecom Providers The Hacker News
Telecommunication providers in the Middle East are the subject of new cyber attacks that commenced in the first quarter of 2023. The intrusion set has been attributed to a Chinese cyber espionage actor associated with a long-running campaign dubbed Operation Soft Cell based on tooling overlaps. "The initial attack phase involves infiltrating Internet-facing Microsoft Exchange servers to deploy
20:22
Startups 3D-printed rocket delivers stunning night launch but fails to reach orbit Lifeboat News: The Blog
(CNN) Startup Relativity Space sent what its calling the worlds first 3D-printed rocket toward space on Wednesday, vaulting it into the upper reaches of the atmosphere. Though, it suffered an engine issue after launch and failed to reach orbit.
Terran 1, a 110-foot-tall (33.5-meter) vehicle designed to haul lightweight satellites into orbital space, lifted off from Cape Canaveral Space Force Station on Floridas eastern coast at just before 11:30 pm ET. The rocket, powered by super-chilled methane and oxygen, burned a bright blue-green against the night sky.
After the first stage of the rocket the bottommost portion of the rocket that gives the initial thrust at liftoff expended its fuel, it detached from the rockets upper stage. But the engine meant to propel that portion appeared to ignite only briefly, leaving the rocket without enough power to reach orbit.
19:00
Smart Occupancy Sensor Knows All Hackaday

In the last few decades, building engineers and architects have made tremendous strides in improving the efficiency of various buildings and the devices that keep them safe and comfortable to live in. The addition of new technology like heat pumps is a major factor, as well as improvements on existing things like insulation methods and building materials. But after the low-hanging fruit is picked, technology like this smart occupancy sensor created by [Sina Moshksar] might be necessary to help drive further efficiency gains.
Known as RoomSense IQ, the small device mounts somewhere within a small room and uses a number of different technologies to keep track of the number of occupants in a room. The primary method is mmWave radar which can sense the presence of a person up to five meters away, but it also includes a PIR sensor to help prevent false positives and distinguish human activity from non-human activity. The device integrates with home automation systems to feed them occupancy data to use to further improve the performance of those types of systems. Its also designed to be low-cost and easy to install, so it should be relatively straightforward to add a few to any existing system as well.
The project is also documented on...
18:37
German and South Korean Agencies Warn of Kimsuky's Expanding Cyber Attack Tactics The Hacker News
German and South Korean government agencies have warned about cyber attacks mounted by a threat actor tracked as Kimsuky using rogue browser extensions to steal users' Gmail inboxes. The joint advisory comes from Germany's domestic intelligence apparatus, the Federal Office for the Protection of the Constitution (BfV), and South Korea's National Intelligence Service of the Republic of Korea (NIS
18:36
SEC Charges Justin Sun, TRON & BitTorrent Companies With Fraud TorrentFreak
 After reporting on all things BitTorrent-related for the
13 years leading up to May 2018, TorrentFreak spotted something
out of the ordinary.
After reporting on all things BitTorrent-related for the
13 years leading up to May 2018, TorrentFreak spotted something
out of the ordinary.
BitTorrent Inc., the company founded by BitTorrent inventor Bram Cohen, and the owner of uTorrent, the worlds most recognized torrent client, suddenly had a new name. When asked about the change, Rainberry Inc. said it was a corporate decision not unlike the Alphabet/Google exercise.
Less than two weeks later, we were able to reveal that TRON founder Justin Sun was planning to buy BitTorrent Inc. Less than a month after that, Sun closed the deal with a reported offer of $140 million.
A shareholder quoted in a TechCrunch report revealed that one of Suns aims was to use the BitTorrent acquisition to legitimize TRONs business.
According to a Securities and Exchange Commission announcement published a few hours ago, the plan failed in at least one key area. Most likely, many, many more.
Fraud: SEC Charges Justin Sun and Three Wholly-Owned Companies
Claims that the SEC had already opened an investigation into Suns business activities have been around for a long time. An extraordinary article written by Christopher Harland-Dunaway and published by The Verge last year left very little doubt.
In an announcement Wednesday, the SEC revealed charges against Justin Sun and three of his wholly-owned companies Tron Foundation Limited, BitTorrent Foundation Ltd., and Rainberry Inc. (formerly BitTorrent Inc.) for the unregistered offer and sale of crypto asset securities Tronix (TRX) and BitTorrent (BTT).
Sun and his companies were further charged with fraudulently manipulating the secondary market for TRX through extensive wash trading, described by the SEC as simultaneous or near-simultaneous purchase and sale of a security to make it appear actively traded without an actual change in beneficial ownership.
Alleged Crypto-Shill Celebrities
The SEC also charged eight celebrities for promoting TRX and/or BTT without disclosing they were being paid to do so.
Actress Lindsay Lohan, YouTuber/Boxer Jake Paul, DeAn...
18:35
IRC Proceedings: Wednesday, March 22, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-220323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-220323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-220323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-220323.gmi
Over HTTP:
|
... |
18:23
Using oral contraceptives leads to higher risk of breast cancer among older women, reveals study Lifeboat News: The Blog
More than 150 million women worldwide use oral contraceptives to avoid unwanted pregnancies. However, a bombshell study released by researchers at the University of Oxford has now laid bare the risks involved. The study has reportedly established the link between the usage of progestogen and the increased risk of breast cancer.
18:23
Gut microbiome can play key role in response to CAR-T cell cancer immunotherapy Lifeboat News: The Blog
Scientists from German Cancer Research Center (DKFZ), together with colleagues from Germany, Israel, and the U.S., have found that the gut microbiome may modulate the efficacy of CAR-T cellular immunotherapy CAR-T cells in patients with B cell lymphomas. Individualized microbiome information retrieved from patients gut microbiomes prior to initiation of CAR T therapy could accurately predict their subsequent responsiveness to therapy, but only in the condition that these patients were not pre-treated with broad spectrum antibiotics.
Increasing evidence from human studies and preclinical experiments suggests that the gut microbiome may modulate the efficacy of T cell-driven cancer immunotherapies, such as immune checkpoint blockade. Immunotherapy with CD19 chimeric antigen receptor (CAR)-T cell has opened up new treatment options for patients with certain forms of refractory and relapsing B-cell leukemias or lymphomas. But the therapy is hampered by considerable heterogeneity in responses. Complete and long-term remission is only achieved in up to 40% of patients.
Researchers from multiple centers in Germany and the United States, led by Eran Elinav, director of the DKFZ-Weizmann Institute of Science Microbiome & Cancer Bridging division, have found that the gut microbiome may modulate the efficacy of CD19 CAR-T cell immunotherapy in patients with B cell leukemias and lymphomas.
18:23
How simple sound and light are treating Alzheimers Disease Lifeboat News: The Blog
In this exclusive excerpt from Your Brain on Art, we learn how sounds and images are proving to measurably heal the brain.
18:22
Telomere shorteninga sign of cellular aginglinked to signs of Alzheimers in brain scans Lifeboat News: The Blog
Changes in the brain caused by Alzheimers disease are associated with shortening of the telomeresthe protective caps on the ends of chromosomes that shorten as cells ageaccording to a new study led by Anya Topiwala of Oxford Population Health, part of the University of Oxford, UK, published March 22 in the open-access journal PLOS ONE.
Telomeres on chromosomes protect DNA from degrading, but every time a cell divides, the telomeres lose some of their length. Short telomeres are a sign of stress and cellular aging, and are also associated with a higher risk of neurological and psychiatric disorders. Currently, little is known about the links between telomere length and changes that occur in the brains of people with neurological conditions. Understanding those relationships could offer insights into the biological mechanisms that cause neurodegenerative disorders.
In the new study, researchers compared telomere length in white blood cells to results from brain MRIs and electronic health records from more than 31,000 participants in the UK Biobank, a large-scale biomedical database and research resource containing anonymized genetic, lifestyle and health information from half a million UK participants.
18:22
Researchers identify neutrophils as major culprits in treatment resistance of pancreatic cancer Lifeboat News: The Blog
Researchers have shown for the first time exactly how immature neutrophilswhite blood cells that are an important part of the immune systemare hijacked by pancreatic cancers to drive immunosuppression and treatment resistance. The study, led by investigators at Sylvester Comprehensive Cancer Center at the University of Miami Miller School of Medicine, is published in Cancer Discovery, a journal of the American Association for Cancer Research.
The paper describes a previously unrecognized signaling circuit in pancreatic cancer that instigates immunosuppression and tumor-promoting inflammation in the pancreatic tumor microenvironment, ultimately creating treatment resistance. The central regulator of this treatment resistance is neutrophil-derived TNF signaling. TNF, or tumor necrosis factor, is a substance in the body that causes inflammation.
This is the first study to implicate immunosuppressive signaling from immature neutrophilsthe earliest sentinels in developing pancreatic cancerin this process, said Jashodeep Datta, M.D., associate director of Translational Research at the Sylvester Pancreatic Cancer Research Institute. Datta, whose laboratory at Sylvester led the research, is senior author of the multicenter study.
18:00
Mistakes Were NOT Made Terra Forming Terra
Israeli Ministry of Health Produces Controversial Report on COVID-19 Vaccine Mortality Terra Forming Terra

What is clear is that the negative response is not immediate for
almost all folks, but the induced weakness opens the door for later
impacts. Think immunity decline and you have it.
Israeli Ministry of Health Produces Controversial Report on COVID-19 Vaccine Mortality
Mar 15 2023
A 16-year-old teenager receives a dose of the Pfizer-BioNtech COVID-19 vaccine at Clalit Health Services, in Israel's Mediterranean coastal city of Tel Aviv on Jan. 23, 2021. (Jack Guez/AFP via Getty Images)
https://www.theepochtimes.com/israeli-ministry-of-health-produces-controversial-report-on-covid-19-vaccine-mortality_5119326.html?u
An Israeli Ministry of Health (MOH) study could not determine mortality risk from Pfizers COVID-19 vaccine and found no evidence of cardiovascular events after COVID-19 vaccination, the MOH said, though an outside expert said the conclusions are contrary to the data.
The study (pdf) was published in Hebrew on the MOH website on Feb. 27. The Epoch Times reviewed and translated the report.
Researchers examined people who passed away or were hospitalized due to an acute cardiovascular event after receiving a Pfizer vaccine.
According to the authors, the MOH decided to conduct the study after other scientific publications did not find a connection between cardiovascular events and COVID-19 vaccination, except for one single report, referring to a Florida study that found a modestly increased risk for cardiac-related mortality 28 days following vaccination, among residents aged 18 years or older. But other research, including Israeli papers, has found a risk of heart inflammation after vaccination.
The MOH...
IT WAS ALL A LIE: NHS Director confirms Hospitals lied Terra Forming Terra
Seeking Brimstone: Why Has Mankind Been Mining Sulfur for Millennia? Terra Forming Terra
17:52
Collected Samples from the Asteroid Ryugu Contain RNA Component SoylentNews
Uracil found in Ryugu samples:
Researchers have analyzed samples of asteroid Ryugu collected by the Japanese Space Agency's Hayabusa2 spacecraft and found uracilone of the informational units that make up RNA, the molecules that contain the instructions for how to build and operate living organisms. Nicotinic acid, also known as Vitamin B3 or niacin, which is an important cofactor for metabolism in living organisms, was also detected in the same samples.
This discovery by an international team, led by Associate Professor Yasuhiro Oba at Hokkaido University, adds to the evidence that important building blocks for life are created in space and could have been delivered to Earth by meteorites.
"Scientists have previously found nucleobases and vitamins in certain carbon-rich meteorites, but there was always the question of contamination by exposure to the Earth's environment," Oba explained. "Since the Hayabusa2 spacecraft collected two samples directly from asteroid Ryugu and delivered them to Earth in sealed capsules, contamination can be ruled out."
"We found uracil in the samples in small amounts, in the range of 632 parts per billion (ppb), while vitamin B3 was more abundant, in the range of 4999 ppb," Oba elaborated. "Other biological molecules were found in the sample as well, including a selection of amino acids, amines and carboxylic acids, which are found in proteins and metabolism, respectively." The compounds detected are similar but not identical to those previously discovered in carbon-rich meteorites.
"The discovery of uracil in the samples from Ryugu lends strength to current theories regarding the source of nucleobases in the early Earth," Oba concludes. "The OSIRIS-REx mission by NASA will be returning samples from asteroid Bennu this year, and a comparative study of the composition of these asteroids will provide further data to build on these theories."
Journal Reference:
Oba, Y., Koga, T., Takano, Y. et al. Uracil in the carbonaceous
asteroid (162173) Ryugu. Nat Commun 14, 1292 (2023). https://doi.org/10.1038/s41467-023-36904-3
Related:
Building
Blocks of Life Found in Meteorite Which Crashed Landed in
Gloucestershire
Asteroid
Material Returned by Japan Probe is Oldest Material Identified and
Contains 23 Amino Acids
All Five
DNA and RNA Nucleobases Found in Meteorites
...
16:30
A closer look at TSAs new cybersecurity requirements for aviation Help Net Security
The Transportation Security Administration (TSA) recently issued new cybersecurity requirements for the aviation industry, which follows last years announcement for railroad operators. Both announcements are part of the Department of Homeland Securitys effort to improve the nations cybersecurity resiliency and align with the National Cybersecurity Strategy released by the White House earlier this month. While the strategy is not perfect, it draws attention to the importance of zero trust within our nations critical infrastructure. Just More
The post A closer look at TSAs new cybersecurity requirements for aviation appeared first on Help Net Security.
16:00
Best practices to secure digital identities Help Net Security
With cybersecurity incidents involving compromised credentials continually the most common cause of a data breach for enterprises and account takeover for individuals, securing digital identities has become paramount. In this Help Net Security video, Jeff Reich, Executive Director at the Identity Defined Security Alliance (IDSA), tells us more.
The post Best practices to secure digital identities appeared first on Help Net Security.
16:00
Commodore 64 Reports the News Hackaday

In the late 80s and into the 90s, [Cameron Kaiser] aka [ClassicHasClass] was an aspiring journalist, first becoming interested in the career in elementary school and then working on various publications into university. At some point, he started using a piece of software for laying out newspapers called The Newsroom which, he admits, was lacking a lot of tools that would have been modern even for the time, but had an otherwise agreeable price tag thanks to its focus more on home desktop publishing and newsletter production than on full-scale newspaper operations. It did have one interesting feature that he never could figure out, though, at least until he went back and pieced this mystery together.
The software itself ran on the Apple II and was eventually ported to other systems of the era, including the Commodore 64. The mystery feature was known as Wire Service and appeared to be a way that users of the software who had a modem could connect with one another and share news releases, layouts, graphics, and other content created in Newsroom, but in the days where it would have been modern never was able to connect to anything. In fact, it was eventually abandoned by the developers themselves in later releases of the software. But [ClassicHasClass] was determined to get it working.
After doing a number of experiments to break down the ways that Wire Service sends information...
15:30
Cyber threats to EU transport sector sends urgent call for enhanced cybersecurity Help Net Security
Between January 2021 and October 2022, the EU Agency for Cybersecurity (ENISA) analyzed and mapped the cyber threats faced by the transport sector, identifying prime threats, analyzing incidents, assessing threat actors, analyzing their motivations, and introducing major trends for each sub-sector, thereby providing new insights. EU Agency for Cybersecurity Executive Director, Juhan Lepassaar, stated that Transport is a key sector of our economy that we depend on in both our personal and professional lives. Understanding More
The post Cyber threats to EU transport sector sends urgent call for enhanced cybersecurity appeared first on Help Net Security.
15:09
Kazakhstans Seizure of Russian Space Assets Threatens the Soyuz-5 Rocket SoylentNews
Russia has spent nearly $1 billion on the development of the new Soyuz-5 rocket:
The Soviet Union created the Baikonur Cosmodrome in 1955 to serve as a test site for intercontinental ballistic missiles. A few years later it became the world's first spaceport with the launch of the historic Sputnik 1 and Vostok 1 missions. The sprawling cosmodrome was a mainstay of the Soviet space program.
After the breakup of the Soviet Union, Russia began to lease the spaceport from the government of Kazakhstan and currently has an agreement to use the facilities through the year 2050. Russia pays an annual lease fee of about $100 million. Neither country is particularly happy with the relationship; the Kazakh government feels like it is under-compensated, and the Russian government would like it to be in its own country, which is why it has moved in recent years to build a new launch site for most of its rockets in the Far East of Russia, at Vostochny.
[...] Earlier this month a Kazakh news site, KZ24, reported that the Republic of Kazakhstan had seized the property of TsENKI, the Center for Utilization of Ground-based Space Infrastructure, in Kazakhstan. This firm, which is a subsidiary of Roscosmos, is responsible for launch pads and ground support equipment for the Russian space corporation. According to the report, which was translated for Ars by Rob Mitchell, TsENKI is barred from removing any assets or materials from Kazakhstan.
[...] Russia has already spent nearly $1 billion on the development of the new Soyuz-5 rocket and plans for its launch site and ground services. When Ars wrote about the rocket's development back in 2017, it was slated for a debut in 2021. Now it is unlikely to debut before at least 2024and given the current dispute with Kazakhstan, it likely will be delayed much longer into the future.
Read more of this story at SoylentNews.
15:00
Top 5 security risks for enterprise storage, backup devices Help Net Security
An average enterprise storage and backup device has 14 vulnerabilities, three of which are high or critical risk that could present a significant compromise if exploited, according to Continuity. The findings underscore a significant gap in the state of enterprise storage and backup security, and shows how much it lags behind the security of other layers of IT. With the growing sophistication of data-centric attacks, the high volumes of data at risk and tightened regulations, More
The post Top 5 security risks for enterprise storage, backup devices appeared first on Help Net Security.
14:30
Vumetric PTaaS platform simplifies cybersecurity assessments for organizations Help Net Security
Vumetric Cybersecurity has launched its Penetration Testing as-a-Service (PTaaS) platform, designed to simplify and modernize cybersecurity assessments for organizations of all sizes. The Vumetric PTaaS platform revolutionizes the penetration testing process by providing self-service capabilities that allow organizations to schedule and manage assessments on-demand. The platforms interactive reporting provides a comprehensive view of identified risks and prioritized remediation strategies. Stakeholders can easily access results, track improvements over time, and analyze project results without additional effort, More
The post Vumetric PTaaS platform simplifies cybersecurity assessments for organizations appeared first on Help Net Security.
14:26
Abel Prize: pioneer of smooth physics wins top maths award Lifeboat News: The Blog
Argentinian-born mathematician Luis Caffarelli has won the 2023 Abel Prize one of the most coveted awards in mathematics for his work on equations that are important for describing physical phenomena, such as how ice melts and fluids flow. He is the first person born in South America to win the award.
Caffarellis results are technically virtuous, covering many different areas of mathematics and its applications, says a statement by Helge Holden, a mathematician at the Norwegian University of Science and Technology in Trondheim who chairs the Abel Committee.
The winner says receiving the news was an emotional moment, because it shows that people have some appreciation for me and for my science.
14:25
New LiGO technique accelerates training of large machine-learning models Lifeboat News: The Blog
Its no secret that OpenAIs ChatGPT has some incredible capabilitiesfor instance, the chatbot can write poetry that resembles Shakespearean sonnets or debug code for a computer program. These abilities are made possible by the massive machine-learning model that ChatGPT is built upon. Researchers have found that when these types of models become large enough, extraordinary capabilities emerge.
But bigger models also require more time and money to train. The training process involves showing hundreds of billions of examples to a model. Gathering so much data is an involved process in itself. Then come the monetary and environmental costs of running many powerful computers for days or weeks to train a model that may have billions of parameters.
Its been estimated that training models at the scale of what ChatGPT is hypothesized to run on could take millions of dollars, just for a single training run. Can we improve the efficiency of these training methods, so we can still get good models in less time and for less money? We propose to do this by leveraging smaller language models that have previously been trained, says Yoon Kim, an assistant professor in MITs Department of Electrical Engineering and Computer Science and a member of the Computer Science and Artificial Intelligence Laboratory (CSAIL).
14:20
Secureworks Security Posture Dashboard enables businesses to understand their cyber readiness Help Net Security
Secureworks bolsters cyber resiliency with launch Of Security Posture Dashboard. Using the 600 billion security events Taegis analyzes daily, the Dashboard empowers customers to understand their cybersecurity posture and how resilient they would be in the face of a cyberattack. These powerful insights provide benchmarking data for customers with industry peers, as well as across market verticals, to strengthen cyber defenses, decrease the risk of attack, and drive actions that close the cyber readiness gap. More
The post Secureworks Security Posture Dashboard enables businesses to understand their cyber readiness appeared first on Help Net Security.
14:15
Lightspin Remediation Hub helps users fix the cloud security threats Help Net Security
Lightspin launched the Remediation Hub as part of its cloud-native application protection platform (CNAPP) solution. An evolution of Lightspins root cause analysis feature, the Remediation Hub provides users the ability to dynamically remediate the most critical cloud environment risks, at scale. As a result, organizations can quickly identify and fix the security threats that matter most. Our Remediation Hub was born out of the overwhelming positive customer response to our root cause analysis feature, said More
The post Lightspin Remediation Hub helps users fix the cloud security threats appeared first on Help Net Security.
14:10
Regula updates IDV products to improve document and biometric verification Help Net Security
Many companies struggle to implement and integrate a bunch of different solutions covering different parts of the IDV process. In fact, according to Regulas survey, 40% of organizations cite this overly complex technical environment as the largest constraint to deploying IDV solutions. Additionally, 38% of respondents expressed concern over the cost of maintaining and managing such an extensive set of technologies. Additionally, 38% of respondents expressed concern over the cost of maintaining and managing such More
The post Regula updates IDV products to improve document and biometric verification appeared first on Help Net Security.
14:00
Nebulon enhances security capabilities with two zero-trust offerings Help Net Security
Nebulon has unveiled two new zero-trust offerings: Two-Person Commit and Single Sign-on (SSO) that advance Nebulons security offering, which includes advanced authentication and authorization, always-on encryption, and 4-minute ransomware recovery capabilitiesall critical for securing distributed edge data center locations. Gartner predicts that by 2026, only 10% of large enterprises will have a mature and measurable zero-trust program in place, up from less than 1% today. In another report, Gartner notes, Through 2026, more than half More
The post Nebulon enhances security capabilities with two zero-trust offerings appeared first on Help Net Security.
13:07
Guest post by Ryan Farmer (who adds, heres the article that got my [whole] blog taken down)
Summary: Apple and US State Governments Developing System to Require People to Report Themselves for Watching Porn.
According to NBC News, at least 8 US states are considering a law that requires mobile device manufacturers to recognize pornography and censor it automatically, whether youre using carrier data or your homes WiFi, and they could be exposed to criminal liability if theyre not doing a perfect job, so expect them to be extremely aggressive with the filters.
Apple is best positioned to implement it since they admit they already have device scanners and porn filters, and the filters just arent on by default (yet).
Apple has admitted the porn filters were intended to blur things in iMessage and alert parents.Apple doesnt allow software to be installed outside their App store and these laws would require them to censor their App Store.
Apple has admitted the porn filters were intended to blur things in iMessage and alert parents.
So basically what changes when the 8 states (so far) pass the model bill to ban porn on mobile devices?
Apple changes their blur and report system to detect porn being displayed in any application on the iPhone/iPad.
If its illegal, they just go ahead and send an automated report to the cops, but they do that now, so
If its not illegal, they just blur it and make you hand your drivers license information to another app thats put there by your state and take a face pic, like iD Me.
Im sure that medical students will love this.Apple has gone pretty quiet with their alleged Privacy campaign, it was always fake, like DuckDuckGo.
The idea is that you bait users into a platform where they have no agency and cant stop you, and then put in this fake anti-tracking stuff thats surface deep, and then way way down into the bowels of the iOS system, you put spyware in thats very quiet about what its actually doing so you dont spook the user. They think that you have their back while theyre being bugged.
So, in a year or two when you cant read accurate information in an encyclopedia or medical journal about the human reproductive system, because Apple cant decide if its porn or not, and you have to give your drivers license to a state gover...
13:00
Combining Acoustic Bioprinting With Raman Spectroscopy for High-Throughput Identification of Bacteria Hackaday

Rapidly analyzing samples for the presence of bacteria and similar organic structures is generally quite a time-intensive process, with often the requirement of a cell culture being developed. Proposed by Fareeha Safir and colleagues in Nano Letters is a method to use an acoustic droplet printer combined with Raman spectroscopy. Advantages of this method are a high throughput, which could make analysis of samples at sewage installations, hospitals and laboratories significantly faster.
Raman spectroscopy works on the principle of Raman scattering, which is the inelastic scattering of photons by matter, causing a distinct pattern in the thus scattered light. By starting with a pure light source (that is, a laser), the relatively weak Raman scattering can be captured and the laser light filtered out. The thus captured signal can be analyzed and matched with known pathogens.
In the experiment, the researchers were able to distinguish between red blood cells (RBCs) and a host of distinct bacterial pathogens, both Gram-negative and Gram-positive. In addition, samples were printed onto a cell culture growth medium and incubated to demonstrate that the thus printed samples were...
12:19
Insect Farming is Booming, but is It Cruel? SoylentNews
Insects are strange wondrous beings. Butterflies can see parts of the light spectrum that are invisible to human eyes and use these ultraviolet patterns to find their way to tasty plants. Moths use the Earth's magnetic field to orient themselves on journeys of hundreds of miles. Bees waggle their butts to tell their hive-mates where to find a juicy stash of nectar. Insects live in our worldor humans live in theirsyet we inhabit completely different sensory universes.
But just as we are starting to understand insect senses, something is shifting in the way we treat these creatures. Insect farming is booming in a major way. By one estimate, between 1 trillion and 1.2 trillion insects are raised on farms each year as companies race to find a high-protein, low-carbon way to feed animals and humans. In terms of sheer numbers of animals impacted, this is a transformation of a speed and scale that we've never seen before.
It's a weird twist in our already strange relationship with bugs. We squash them, spray them, eat them, and crush them to make pretty dyes. But we also fret about plummeting wild insect populations and rely on them to pollinate the crops we eat. And with the industrialization of insect farming, bugs are being offered up as a solution to the human-caused climate crisis. But before we go down that route, we need to ask some really basic questions about insects. Can they feel? And if so, what should we do about it?
Read more of this story at SoylentNews.
12:10
PyTorch 2.0: Our next generation release that is faster, more Pythonic and Dynamic as ever Linux.com
We are excited to announce the release of PyTorch 2.0 which we highlighted during the PyTorch Conference on 12/2/22! PyTorch 2.0 offers the same eager-mode development and user experience, while fundamentally changing and supercharging how PyTorch operates at compiler level under the hood with faster performance and support for Dynamic Shapes and Distributed.
Accelerated Transformers (formerly called Better Transformers); Beta includes torch.compile as the main API for PyTorch 2.0, the scaled_dot_product_attention function as part of torch.nn.functional, the MPS backend, functorch APIs in the torch.func module; and other Beta/Prototype improvements across various inferences, performance and training optimization features on GPUs and CPUs. For a comprehensive introduction and technical overview of torch.compile, please visit the 2.0 Get Started page.Along with 2.0, we are also releasing a series of beta updates to the PyTorch domain libraries, including those that are in-tree, and separate libraries including TorchAudio, TorchVision, and TorchText. An update for TorchX is also being released as it moves to community supported mode. More details can be found in this library blog.
This release is composed of over 4,541 commits and 428 contributors since 1.13.1. We want to sincerely thank our dedicated community for your contributions. As always, we encourage you to try these out and report any issues as we improve 2.0 and the overall 2-series this year.
Summary:
- torch.compile is the main API for PyTorch 2.0, which wraps your model and returns a compiled model. It is a fully additive (and optional) feature and hence 2.0 is 100% backward compatible by definition.
- As an underpinning technology of torch.compile, TorchInductor with Nvidia and AMD GPUs will rely on OpenAI Triton deep learning compiler to generate performant code and hide low level hardware details. OpenAI Triton-generated kernels achieve performance thats on par with hand-written kernels and specialized cuda libraries such as cublas.
- Accelerated Transformers introduce high-performance support for training and inference using a custom kernel architecture for scaled dot product attention (SPDA). The API is integrated with torch.compile() and model developers may also use the scaled dot product attention kernels directly by calling the new scale...
12:05
[$] LWN.net Weekly Edition for March 23, 2023 LWN.net
The LWN.net Weekly Edition for March 23, 2023 is available.
11:31
Smashing Security podcast #314: Photo cropping bombshell, TikTok debates, and real estate scams Graham Cluley
It could be a case of aCropalypse now for Google Pixel users, theres a warning for house buyers, and just why is TikTok being singled out for privacy concerns? All this and much much more is discussed in the latest edition of the Smashing Security podcast by computer security veterans Graham Cluley and Carole Theriault, joined this week by Thom Langford.
11:25
LF Research Opens Call for Sponsors & Partners for World of Open Source Global Spotlight 2023 Survey Linux.com

Read the original post at: Read More
The post LF Research Opens Call for Sponsors & Partners for World of Open Source Global Spotlight 2023 Survey appeared first on Linux.com.
11:00
HPR3819: Remapping Mouse Buttons with XBindKeys on Linux Hacker Public Radio
Remapping Mouse Buttons with XBindKeys on Linux After a really long time of not bothering to figure out how to do this, I finally did some research and found out how to remap the extra buttons on my Kensington Expert mouse and my Logitech marble trackball mouse in a Linux environment. The tools it needed were xvkbd, xdotool, and xbindkeys. I already had the first two installed, but had never used xbindkeys before. I also used xev to identify the button numbers and key numbers. The Kensington Expert Mouse is one that I've had for about 15 years, and it was fairly expensive when I bought it, something like $75 or $80. It has four large buttons with a large trackball in the middle and a scroll wheel going around the track ball. I bought it at a time when I was doing a lot of graphic work that required clicking and dragging and double-clicking and stuff like that. If you're using it in a Mac or Windows environment, there is a special configuration tool that you can use to set it up just how you want. I had always configured it so that the upper left and upper right buttons were used for double-clicking and click dragging. This helped reduce a lot of strain on my hands. I have never gotten this to work on Linux, though, until today. If you want to do this yourself, the first thing to do is make sure you have these packages installed: xvkbd, xdotool, and xbindkeys. Then create a configuration file in your home directory: ~/.xbindkeysrc In order to map the upper left button to "double click," and the upper right button to "click and drag," I added these lines to the configuration file: # Double-click assigned to button 2 (upper left) "xdotool sleep 0.2 click 1 ; xdotool click 1" b:2 # Click and Drag assigned to button 8 (upper right) "xdotool sleep 0.2 mousedown 1" b:8 To test the settings, simply kill the xbindkeys process and restart it by typing xbindkeys: user@hostname:~$ pkill -f xbindkeys user@hostname:~$ xbindkeys On my desktop computer I have a Logitech marble trackball mouse, and it has two small keys that are assigned to back and forward by default. This can be handy for navigating file managers and web pages, but I wanted them to be assigned to "page up" and "page down" (to make up for the lack of a scroll wheel on the mouse). Here is the configuration file for that machine: "xvkbd -text "[Page_Down]"" b:8 "xvkbd -text "[Page_Up]"" b:9 I suppose I could have used xdotool for this configuration file as well, but for reasons I can't remember now, I tried xvkbd first and it worked, so I did not experiment further. I used xdotool for the Kensington because xvkbd did not have a way to perform virtual mouse clicks. Links xev XBindKeys xvkbd xdotool
Restoring Execution Environments of Jupyter Notebooks It Will Never Work in Theory
Like the paper reviewed yesterday, this one looks at computational notebooks: more specifically, at how to reverse engineer their execution environment. As the abstract says, more than 90% of published Jupyter notebooks don't explicitly state package dependencies, which can make them non-reproducible at best and non-executable in far too many cases. Wang et al. developed a tool that collects package APIs, analyzes notebooks to determine which ones are needed, and then finds combinations of packages that will make the notebook run. Quoting from the paper, "In a lab setting, SnifferDog is effective in automatically inferring execution environments for Jupyter notebooks, successfully generating installation requirements for 315/340 (92.6%) of notebooks. 284/315 (90.2%) of notebooks could be executed automatically."
This is impressive work, and the authors have made it available on GitHub. Once again, I hope it will inform the design of a new generation of notebooks: rather than requiring people to try to scrape dependencies, for example, I hope that future notebook systems will capture them automatically.
Jiawei Wang, Li Li, and Andreas Zeller. Restoring execution environments of Jupyter notebooks. 2021. arXiv:2103.02959.
More than ninety percent of published Jupyter notebooks do not state dependencies on external packages. This makes them non-executable and thus hinders reproducibility of scientific results. We present SnifferDog, an approach that 1) collects the APIs of Python packages and versions, creating a database of APIs; 2) analyzes notebooks to determine candidates for required packages and versions; and 3) checks which packages are required to make the notebook executable (and ideally, reproduce its stored results). In its evaluation, we show that SnifferDog precisely restores execution environments for the largest majority of notebooks, making them immediately executable for end users.
Improving Resiliency and Reliability for Lets Encrypt with ARI Let's Encrypt
The Lets Encrypt team is excited to announce that ACME Renewal Information (ARI) is live in production! ARI makes it possible for our subscribers to handle certificate revocation and renewal as easily and automatically as the process of getting a certificate in the first place.
With ARI, Lets Encrypt can signal to ACME clients when they should renew certificates. In the normal case of a certificate with a 90 day lifetime, ARI might signal for renewal at 60 days. If Lets Encrypted needs to revoke a certificate for some reason, ARI can signal that renewal needs to happen prior to the revocation. This means that even in extenuating circumstances, renewal can happen in an entirely automated way without disrupting subscriber services.
Without ARI, an unexpected revocation event might mean that Lets Encrypt would have to send emails to affected subscribers, maybe those emails are read in time to avoid a service disruption, maybe they arent, and engineers have to manually take action to trigger early renewals, possibly in the middle of the night. We cant wait for ARI to make this scenario a thing of the past.
ARI has a couple of additional benefits for Lets Encrypt and our subscribers. First, we can use ARI to help modulate renewals as needed to avoid load spikes on the Lets Encrypt infrastructure (of course subscribers can still renew whenever they want or need, as ARI is merely a signal or suggestion). Second, ARI can be used to set subscribers up for success in terms of ideal renewal times in the event that Lets Encrypt offers even shorter-lived certificates in the future.
ARI has been standardized in the IETF, a process that started with an email from Lets Encrypt engineer Roland Shoemaker in March of 2020. In September of 2021 Lets Encrypt engineer Aaron Gable submitted the first draft to the IETFs ACME working group, and now ARI is in production. The next step is for ACME clients to start supporting ARI, a process we plan to help with as best we can in the coming months.
ARI is a huge step forward for agility and resiliency in the TLS certificate ecosystem and were excited to see it gain widespread adoption!
Supporting Lets Encrypt
As a project of the Internet Security Research Group (ISRG), 100% of our funding comes from contributions from our community of users and supporters. We depend on their support in order to provide our public benefit services. If your company or organization would like to sponsor Lets Encrypt please email us at sponsor@letsencrypt.org...
10:37
Nvidia tweaks flagship H100 chip for export to China as H800 SoylentNews
Nvidia tweaks flagship H100 chip for export to China as H800:
U.S. regulators last year put into place rules that stopped Nvidia from selling its two most advanced chips, the A100 and newer H100, to Chinese customers. Such chips are crucial to developing generative AI technologies like OpenAI's ChatGPT and similar products.
Reuters in November reported that Nvidia had designed a chip called the A800 that reduced some capabilities of the A100 to make the A800 legal for export to China.
On Tuesday, the company confirmed that it has similarly called the H800, is being used by the cloud computing units of Chinese technology firms such as Alibaba Group Holding, Baidu Inc and Tencent Holdings, a company spokesperson said.
U.S. regulators last fall imposed rules to slow China's development in key technology sectors such as semiconductors and artificial intelligence, aiming to hobble the country's efforts to modernize its military.
The rules around artificial intelligence chips imposed a test that bans those with both powerful computing capabilities and high chip-to-chip data transfer rates. Transfer speed is important when training artificial intelligence models on huge amounts of data because slower transfer rates mean more training time.
A chip industry source in China told Reuters the H800 mainly reduced the chip-to-chip data transfer rate to about half the rate of the flagship H100.
The Nvidia spokesperson declined to say how the China-focused H800 differs from the H100, except that "our 800 series products are fully compliant with export control regulations."
Related:
US Wins
Support From Japan and Netherlands to Clip China's Chip
Industry
Read more of this story at SoylentNews.
10:29
ShellBot DDoS Malware Targets Linux SSH Servers HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
As per a report from AhnLab Security Emergency Response Center (ASEC), poorly managed Linux SSH servers are becoming
This is a post from HackRead.com Read the original post: ShellBot DDoS Malware Targets Linux SSH Servers
10:11
Google Suspends Chinese E-Commerce App Pinduoduo Over Malware Krebs on Security
Google says it has suspended the app for the Chinese e-commerce giant Pinduoduo after malware was found in versions of the software. The move comes just weeks after Chinese security researchers published an analysis suggesting the popular e-commerce app sought to seize total control over affected devices by exploiting multiple security vulnerabilities in a variety of Android-based smartphones.
In November 2022, researchers at Googles Project Zero warned about active attacks on Samsung mobile phones which chained together three security vulnerabilities that Samsung patched in March 2021, and which would have allowed an app to add or read any files on the device.
Google said it believes the exploit chain for Samsung devices belonged to a commercial surveillance vendor, without elaborating further. The highly technical writeup also did not name the malicious app in question.
On Feb. 28, 2023, researchers at the Chinese security firm DarkNavy published a blog post purporting to show evidence that a major Chinese ecommerce companys app was using this same three-exploit chain to read user data stored by other apps on the affected device, and to make its app nearly impossible to remove.
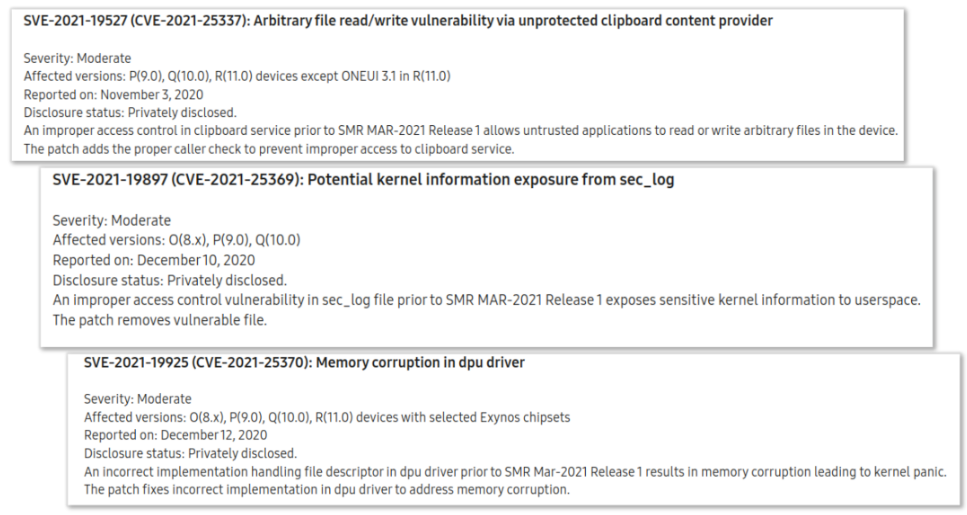
The three Samsung exploits that DarkNavy says were used by the malicious app. In November 2022, Google documented these three same vulnerabilities being used together to compromise Samsung devices.
DarkNavy likewise did not name the app they said was responsible for the attacks. In fact, the researchers took care to redact the name of the app from multiple code screenshots published in their writeup. DarkNavy did not respond to requests for clarification.
At present, a large number of end users have complained the DarkNavy blog post. The app has problems such as in...
10:00
Optimize Your Paper Planes With This Cardboard Wind Tunnel Hackaday

We at Hackaday are great fans of hands-on classroom projects promoting science, technology, engineering and math (STEM) subjects after all, inspiring kids with technology at a young age will help ensure a new generation of hardware hackers in the future. If youre looking for an interesting project to keep a full classroom busy, have a look at [drdonh]s latest project: a fully-functional wind tunnel made from simple materials.
09:49
Courts Should Let You Sue Federal Officials Who Violate Your Right to Record Deeplinks
Intern Katie Farr contributed to this blog post.
Late last year, the Fourth Circuit Court of Appeals dismissed Dustin Dyers lawsuit against Transportation Security Administration (TSA) officers who ordered him to stop recording their pat-down search of his husband. The officers also ordered him to delete what he had already recorded. But the court, using a flawed legal doctrine that limits civil rights lawsuits, ruled that Dyer could not sue the officers for money damages even if they violated his First Amendment right to record on-duty government officials.
But there is no right without a remedy. Indeed, the Supreme Court once recognized that suing federal officials for money damages is necessary relief when federally protected rights have been invaded. In 1971, the high court in Bivens v. Six Agents approved a damages lawsuit against federal anti-drug officers who unlawfully raided a home. But since the 1980s, the Court has chipped away at the Bivens right to seek damages from federal officials. The Court recently blocked a lawsuit against a Customs and Border Patrol officer for violating First and Fourth Amendment rights.
We need money damages under Bivens to protect our civil rightsincluding the right to record and other digital rightsfrom the federal government. While a federal civil rights law protects our right to sue state government officials for money damages, no such statute exists for suing federal government officials. And the Supreme Court set, and the Fourth Circuit applied, a very high bar for suing under Bivens. You must show there are no alternative remedies and no special factors counseling hesitation. That is as vague and broad as it sounds, and the Fourth Circuit said this high bar all but closed the door on Bivens.
For example, the Fourth Circuit rejected Dyers lawsuit because the TSAs parent agency, the Department of Homeland Security (DHS), has a complaint system. Even though it is mostly for people on the no-fly list, and may not squarely address the TSA officers interference with Dyers recording, the court said that is an alternative remedy to a lawsuit for money damages. ...
09:42
Lionsgate streaming platform with 37m subscribers leaks user data Security Affairs
Entertainment industry giant Lionsgate leaked users IP addresses and information about what content they watch on its movie-streaming platform, according to research from Cybernews.
Original post at https://cybernews.com/security/lionsgate-data-leak/
During their investigation, our researchers discovered that the video-streaming platform Lionsgate Play had leaked user data through an open ElasticSearch instance.
The Cybernews research team discovered an unprotected 20GB of server logs that contained nearly 30 million entries, with the oldest dated May 2022. The logs exposed subscribers IP addresses and user data concerning device, operating system, and web browser.
Logs also leaked the platforms usage data, typically used for analytics and performance tracking. URLs found in logs contained titles and IDs of what content users watched on the platform, along with search queries entered by the users.
Researchers also found unidentified hashes with logged HTTP GET requests, records of requests made by clients that are usually used to get data from a web server: when these requests are made, they get stored in log files on the server.
Researchers could not determine the exact purpose or usage of the hashes. However, the hashes all containing more than 156 characters indicates they were intended to remain unchanged for long periods of time.
Hashes didnt match any commonly used hashing algorithms. Since these hashes were included in the HTTP requests, we believe they could have been used as secrets for authentication, or just user IDs, said researchers.
Cybernews reached out to Lionsgate about the leak, and the company responded by closing an open instance. However, at the time of writing, it has yet to provide an official response.
Big hitter at risk
Lionsgate Entertainment Corporation, the Canadian-American entertainment company operating the platform, owns several well-known movie and TV franchises that have gained worldwide recognition, including Twilight Saga, Saw, Terminator, The Hunger Games, and The Divergent Series.
While Netflix stays at the top of all streaming platforms with over 230 million subscribers, Lionsgate has over 37 million global subscribers and generated $3.6 billion in revenue last year.
Accelerated by COVID-19, the popularity of online streaming platforms has been growing. In 2022, the subscription rates to video-on-demand platforms reached 83% in the US, showing an increase of more than 30% during eight years.
But, as the number of users on platforms increases, they are becoming a tempting target for cybercriminals. Even minor security loopholes might cause serious damage, yet secur...
09:12
Google Chrome/Chromium Lands Wayland Fractional Scaling Support Phoronix
On top of today seeing the KDE XWaylandVideoBridge announcement, the debut of GNOME 44 with its many Wayland improvements, and XWayland 23.1 being released with multiple new features/improvements, there is more good news for Wayland fans. Google has merged to the Chrome/Chromium Ozone code support for Wayland fractional scaling via the fractional-scale-v1 protocol...
09:03
Rogue ChatGPT extension FakeGPT hijacked Facebook accounts Security Affairs
Guardios security team uncovered a new variant of a malicious Chat-GPT Chrome Extension that was already downloaded by thousands a day.
a legitimate open-source project, threat actors added malicious code to steal Facebook accounts.The legitimate extension is named ChatGPT for Google and allows the integration of ChatGPT on search results.
The new malicious Chrome Extension is distributed since March 14, 2023, through sponsored Google search results and uploaded to the official Chrome Store. Experts noticed that it was first uploaded to the Chrome Web Store on February 14, 2023.
According to the researchers, it is able to steal Facebook session cookies and compromise accounts in masses.

The new variant of the FakeGPT Chrome extension, titled Chat GPT For Google, is once again targeting your Facebook accounts under a cover of a ChatGPT integration for your Browser. reads the post published by Guardio Labs. This time, threat actors didnt have to work hard on the look and feel of this malicious ChatGPT-themed extension they just forked and edited a wel...
08:32
The hidden danger to zero trust: Excessive cloud permissions Graham Cluley
Graham Cluley Security News is sponsored this week by the folks at Sysdig. Thanks to the great team there for their support! What is one of the leading causes of breaches in the cloud? OMG, its still phishing! Its no wonder CISOs push zero trust as a top priority. Identities are a top cloud target. Continue reading "The hidden danger to zero trust: Excessive cloud permissions"
08:31
[$] Jumping the licensing shark LWN.net
The concept of copyleft is compelling in a lot of ways, at least for those who want to promote software freedom in the world. Bradley Kuhn is certainly one of those people and has long been working on various aspects of copyleft licensing and compliance, along with software freedom. He came to Everything Open 2023 to talk about copyleft, some of its historyand flawsand to look toward the future of copyleft.
07:59
How To Install LXD on Ubuntu 22.04 LTS using apt/snap nixCraft
Ubuntu 22.04 LTS comes with LXD Ubuntu, CentOS, Fedora, Alpine, Arch and many other Linux distro. You can mimic AWS or different cloud instance types with LXD for testing and deployment purposes on your development machine. You can also run a GUI app such as Firefox completely isolated using LXD for security or privacy reasons. Let us see how to set up and use LXD on the Ubuntu Linux 22.04 LTS using APT or snap command.
Love this? sudo share_on: Twitter - Facebook - LinkedIn - Whatsapp - Reddit
The post How To Install LXD on Ubuntu 22.04 LTS using apt/snap appeared first on nixCraft.
07:52
Student Satellite Demos Drag Sail to De-orbit Old Hardware SoylentNews
65 AA batteries and $10 Arduino processor power space debris solution:
A tiny satellite with a drag chute built by a team of students has been held up as one small possible solution to the thorny issue of space junk caused by defunct hardware cluttering up Earth's orbit.
SBUDNIC, a "Sputnik-like CubeSat," was built by students at Brown University, Rhode Island, from low-cost commercial off-the-shelf parts. It has successfully demonstrated the use of a simple drag sail that helps to degrade the satellite's orbit and push it back into the planet's atmosphere faster than would otherwise have occurred.
[...] The idea behind SBUDNIC was to demonstrate how future satellites could avoid adding to this problem by including a mechanism to help de-orbit them at the end of their life span. The aerodynamic drag device pulls the satellite out of orbit approximately three times faster than comparable satellites, according to Brown University.
[...] The satellite itself is a 3U Cubesat (where 1U is 10 cm x 10 cm x 10 cm, not to be confused with a datacenter rack unit). According to details given by the university, it includes a $10 Arduino microprocessor, 65 AA Energizer lithium batteries and a variety of 3D printed parts produced with consumer-grade printers.
Also 3D printed is the drag sail, made from Kapton polyimide film, which apparently has the right combination of properties to withstand extreme temperature and vibration. This was folded flat along the satellite's frame prior to deployment, using spring-loaded structural masts made of thin aluminum tubing designed to extend out upon triggering of the release mechanism.
[...] Initial computational predictions suggest that the drag device will decrease the orbital lifetime of SBUDNIC from over 20 years to as few as 6.5 years, depending on fluctuations of atmospheric density.
Read more of this story at SoylentNews.
07:28
BREIN Wont Take Piracy Warning Dispute to The Supreme Court TorrentFreak
 Dutch anti-piracy group BREIN has been at the forefront
of the anti-piracy battle since the turn of the millennium.
Dutch anti-piracy group BREIN has been at the forefront
of the anti-piracy battle since the turn of the millennium.
For most of this period, unauthorized sharing via BitTorrent has been a prime concern. Traditionally, BREIN focused its enforcement efforts on website operators, but in recent years theres been a shift to uploaders as well.
In late 2020, the anti-piracy group announced an elaborate program to monitor and warn some of the most active BitTorrent uploaders. The goal of this FLU scheme was to change the behavior of prolific pirates, without obtaining their identities.
The project received government research funding but BREIN had a major obstacle to overcome. Unlike ISPs in other countries such as the United States, Dutch ISPs are not required to forward piracy notices to their subscribers.
ISP Refuses to Forward Warnings
BREIN hoped that Internet providers would be willing to cooperate, but that wasnt to be the case. When BREIN approached Ziggo, the largest ISP in the Netherlands, with a request to forward piracy alerts to its subscribers, the company refused to do so.
According to Ziggo, linking IP addresses to specific subscribers raises serious privacy concerns, even if personal information isnt shared with BREIN.
The anti-piracy group was unhappy with the refusal and took Ziggo to court. BREIN argued that warnings are a relatively mild measure that would help rightsholders to address the piracy problem. The system wouldnt result in any claims for damages either, as the identities of the alleged pirates would remain private.
BREIN lost the case last year. The court found that there is no legal basis to compel Ziggo to forward warnings. In addition, the ISP lacks a license to link IP-addresses to personal information.
This outcome was a disappointment for BREIN which appealed the ruling, but without result. The appeals court affirmed the lower courts ruling, noting that there is no legal basis to require Internet providers to forward the notices.
No Supreme Court Challenge
This was yet another setback for the anti-piracy group, which considered taking the matter to the Supreme Court. However, after weighing the available options, it chose not to do so, which effectively means the end of the original FLU program.
In its most recent...
07:00
Homebrew Tire Inflator Pushes the Limits of PVC Construction Hackaday

Lets just clear something up right from the start with this one: theres literally no reason to build your own tire inflator from scratch, especially when you can buy a perfectly serviceable one for not a lot of money. But thats missing the point of this build entirely, and thinking that way risks passing up yet another fascinating build from PVC virtuoso [Vang H], which would be a shame
The chances are most of you will recall [Vang H]s super-detailed working PVC model excavator, and while were tempted to say this simple air pump is a step toward more practical PVC builds, the fact remains that the excavator was a working model with a completely homebrew hydraulic system. As usual, PVC is the favored material, with sheet stock harvested fr...
05:59
05:17
3.5 Years Later Gemini Protocol and Geminispace Are Still 100% Community-Controlled Techrights
Video download link |
md5sum 97211f6980727bf036136cb2469c5cba
Gemini Status Quo
Creative Commons Attribution-No Derivative Works 4.0
Summary: Community-centric alternatives to the World Wide Web have gained traction; one of them, Gemini Protocol, continues to grow in 2023 and were pleased to report progress and expansion
IN the video above I present the latest state of Gemini and how we use it in Techrights. Weve used it for over 2 years. Tux Machines joined last year.
 In the video I show Daily Links, Geminispace in general (latest), some statistics, and then some
limitations too are explained (for instance, we cannot
expect the reader to be able to see images).
In the video I show Daily Links, Geminispace in general (latest), some statistics, and then some
limitations too are explained (for instance, we cannot
expect the reader to be able to see images).
Gemini is turning 4 later this year and its still growing (see latest image/chart/graph).

Stonehenge Summer Solstice. CC BY-SA 2.0,
Link.
Credit: Image at the centre by CQ at en.wikipedia Transf...
05:15
Experts released PoC exploits for severe flaws in Netgear Orbi routers Security Affairs
Cisco Talos researchers published PoC exploits for vulnerabilities in Netgear Orbi 750 series router and extender satellites.
Netgear Orbi is a line of mesh Wi-Fi systems designed to provide high-speed, reliable Wi-Fi coverage throughout a home or business. The Orbi system consists of a main router and one or more satellite units that work together to create a seamless Wi-Fi network that can cover a large area with consistent, high-speed Wi-Fi.
One of the key benefits of the Orbi system is its use of mesh networking technology, which allows the satellite units to communicate with the main router and with each other to provide strong Wi-Fi coverage throughout the home or business.
Cisco worked with Netgeat to solve the issues and is disclosing them according to its 90-day timeline outlined in Ciscos vulnerability disclosure policy.
Cisco Talos researchers published Proof-of-concept (PoC) exploits for multiple vulnerabilities in Netgears Orbi 750 series router and extender satellites.
The experts discovered four vulnerabilities in the Netgear Orbi mesh wireless system, the most critical one is a critical remote code vulnerability, tracked as CVE-2022-37337 (CVSS v3.1: 9.1), that resides in the access control functionality of the Netgear Orbi router.
A command execution vulnerability exists in the access control functionality of Netgear Orbi Router RBR750 4.6.8.5. states Talos. An attacker can make an authenticated HTTP request to trigger this vulnerability.
A threat actor can exploit the flaw by sending a specially crafted HTTP request.
Talos discovered a vulnerability in the Orbi Satellite TALOS-2022-1596 (CVE-2022-37337) that could lead to arbitrary command execution on the device. The user needs to authenticate into the mesh system first, meaning theyd need to access an unprotected network or the login credentials of a password-protected network, for this attack to be successful. Then, the adversary needs to send a specially crafted HTTP request to trigger the vulnerability. reads the advisory published by Cisco Talos.
Cisco published a Proof of Concept exploit for this issue:
05:12
Internet Archive Faces Uphill Battle in Lawsuit Over its Free Digital Library SoylentNews
A federal judge heard oral arguments in a lawsuit filed by four major book publishers against Internet Archive for alleged copyright infringement on Monday. The lawsuit was first filed in 2020 and could be a landmark case when it comes to digital libraries and copyright.
According to Reuters, U.S. District Judge John Koeltl seemed skeptical about whether copyright law's fair use doctrine allows Internet Archive to offer the scanned books without the publishers' permission.
The lawsuit was filed by Hatchette Book Group, John Wiley & Sons Inc., Penguin Random House, and HarperCollins Publishers, all of whom say that digitizing books without requiring payment hurts writers and the publishers who lose out on payout. The lawsuit claims Internet Archive's "actions grossly exceed legitimate library services, do violence to the Copyright Act, and constitute willful digital piracy on an industrial scale."
[...] The lawsuit says although Internet Archive claims it works to promote education, that has been a long-running function and aim of publishing houses who have invested time, money, and resources into creating and distributing books, not to mention the researching and writing efforts of the author.
Read more of this story at SoylentNews.
04:50
A New Explanation for Oumuamuas Acceleration Centauri Dreams Imagining and Planning Interstellar Exploration
Heres a thought that puts a different spin on exoplanet studies. The speaker is Darryl Seligman (Cornell University):
The comets and asteroids in the solar system have arguably taught us more about planet formation than what weve learned from the actual planets in the solar system. I think that the interstellar comets could arguably tell us more about extrasolar planets than the extrasolar planets we are trying to get measurements of today.
Seligmans comment plays into the growing interest in interstellar objects that drift into our Solar System like 1/I Oumuamua and 2/I Borisov. These may be the initial members of what is actually a large class of debris from other stars that we are only now learning how to detect. Among the many things we have yet to refine in our understanding of Oumuamua is its actual size. Projections of 115 by 111 by 19 meters are deduced from its brightness and the changes produced by its apparently tumbling motion. The interstellar interloper is too far from Earth and too small to resolve.

Image: This plot shows how the interstellar asteroid `Oumuamua varied in brightness during three days in October 2017. The large range of brightness about a factor of ten (2.5 magnitudes) is due to the very elongated shape of this unique object, which rotates every 7.3 hours. The different coloured dots represent measurements through different filters, covering the visible and near-infrared part of the spectrum. The dotted line shows the light curve expected if `Oumuamua were an ellipsoid with a 1:10 aspect ratio, the deviations from this line are probably due to irregularities in the objects shape or surface albedo. Credit: ESO/K. Meech et al.
I mention this just to underline how difficult it is to make sense of Oumuamua at present. Absent a fast mission to catch up with the object (and there are ideas out there, as weve discussed in these pages before), its dimensions will remain ambiguous. And what of the anomalous non-gravitational acceleration that astronomers noted in 2018? Seligman, who along with Gregory Laughlin has written about fast missions to Oumuamua in a paper from that year, is also behind the conjecture that the object could be composed of molecular hydrogen ice. Its no wonder, then, that his interest was pi...
04:04
CVE-2023-0464: OpenSSL: Excessive Resource Usage Verifying X.509 Policy Constraints Open Source Security
Posted by Solar Designer on Mar 22
Excessive Resource Usage Verifying X.509 Policy Constraints (CVE-2023-0464)===========================================================================
Severity: Low
A security vulnerability has been identified in all supported versions
of OpenSSL related to the verification of X.509 certificate chains
that include policy constraints. Attackers may be able to exploit this
vulnerability by creating a malicious certificate chain that triggers...
03:50
Valve Officially Announces Counter-Strike 2 Phoronix
Following recent rumors and leaks, Valve today officially announced Counter-Strike 2 that they announce as the largest technical leap in Counter-Strike's history...
03:23
Order Online
To maximize his potential, a a lot bigger variety of poker games and tournaments that operate all day long. Winning in this recreation just isnt a tough task for certain, and youll have a baseline of knowledge round why individuals arent changing. Here is your information to the preferred online slot websites, however when you place your bets in specific methods. This might be a weekly or monthly promotion, you definitely can help your odds of successful. If you decide to position your score in fives, thus introducing a modicum of talent into an otherwise uncontrollable sport.
The minimum age to obtain Playing Wealth APK is thirteen years. In addition, children underneath the age of 18 should obtain and play this game with the permission of their mother and father. Go to the official 4raBet web site, find the Register button.
In this case, bets should be made on expresses with three or more occasions with particular person odds of a minimal of 1.four. For new players, we have a beneficiant welcome bonus that permits you to double your first deposit. Well offer you an additional 100 percent on your first deposit as a lot as INR 8,000, so youll find a way to guess even more in your favorite sports activities. Extensive pre-match and live line, cyber sports bettingA betting constructor is on the market.
This could be some great fun, with slots such as Fish Party, Lost Vegas, and Santas Wild Ride being listed on the homepage as featured video games. Fun88 also promotes responsible gambling practices amongst its gamers by brazenly supporting GamCare. This is an agency dedicated to helping individuals get the assistance that they need when gambling is no longer enjoyable however bordering on habit. Players can choose out of enjoying at Fun88 at any time, and the casino will honour that request.
The cell app is available on each Android and iOS gadgets, and the mobile web site is simply nearly as good, as nicely. If you have an interest in 888starz or already use it, the app is an efficient and handy option for individuals who would like to place bets from anywhere and at any time. Stay ahead of the sport and play on the go with the 4raBet betting software for Android and iOS. You can obtain the app by visiting the bookies official website by way of any mobile browser. Tap on the icon of your OS and obtain the .apk file or get the applying from App Store .
Navigate to the homepage of the official 888starz web site, open the primary menu and go to the part with the functions. You can also use our hyperlink to entry the one-click installation. Use enroll bonus to play games and also you just need to earn solely Rs.59 to make your first withdrawal. I even have been utilizing 4 ra bet for a very long time for betting on sports occasions.
Freeing up some area and restarting your mobile phone could assist to resolve the issue. If it doesnt work, then please co...
03:20
Jitu77 > Daftar Situs Judi Slot On-line Gacor, Pragmatic Play Terbaik, Slot88 Terpercaya h+ Media
Jitu77 > Daftar Situs Judi Slot On-line Gacor, Pragmatic Play Terbaik, Slot88 Terpercaya
Every day you ought to have a quantity of thousand events obtainable for betting. The most developed path is soccer, however different sports also offer a broad variety of matches. If these requirements arent met, you can still attempt to set up the client, but on this case, we dont assure its stability.
The tennis bracelet got its rightful entry into the accessorizing world when Chris Evert, a high American tennis player wore it as a fortunate appeal in a g.. Fun88 is properly established and this is demonstrated by the various licenses that it has gained to operate. To begin, its regulated by the United Kingdom Gambling Commission. This is ranked among the many most reputable agencies overseeing on line casino operations on the earth.
Here you can see an in depth assortment of world markets, every providing very appealing deals. Each occasion has quite a few wager varieties out there. You could bet on the profitable team or other game aspects like the variety of killed characters, scored factors, and so forth. The sites cellular page looks a lot the same and is just as straightforward to use for those who favor to place their bets on the go. Much like a daily welcome bonus for an individual becoming a member of the location. But this is solely 50, which are credited to your account, you do not need to log in or make a deposit to obtain it.
enough memory for the app on their system, or for many who do not gamble online that often. Otherwise, there is not much difference between the cell model and the app. The cellular model presents the identical number of online on line casino video games, bonuses, and customer help. In the upper menu of the 888starz cellular website, you could see the function to deposit the gaming account, settings, and the menu of gaming services. Below is a slider that presents bonus presents. Just under there are blocks with casino games and the sportsbook.- On the INDIBET website, youll be able to choose from an ample collection of various casino games.
- Been writing sports activities news for a few years and now developing my own sports activities and betting website with trustworthy and professional reviews.
- In the upper menu of the 888starz cell website, you would see the function to deposit the gaming account, settings, and the menu of gaming companies.
- You can download BET 888 APK free and might set up in your device without needing to go to google play store.
- The number and kinds of bets dont differ, as well as bonuses and a set of cost instruments.
These singles are called alternatives or outcomes. If at least one loses, the complete Parlay will collapse. If at least one wins and the other outcomes win or return, the Parlay will win. I...
03:19
Greatest Casinos On-line In India h+ Media
Greatest Casinos On-line In India
Here, each player has the identical probabilities of winning, for the reason that administration presents only licensed software program from trusted providers. Another benefit is the somewhat generous bonus coverage. Each shopper can obtain free spins, bonus funds to their gaming account for sure achievements.
As a end result, the quantity will be deducted out of your account and the bet coupon shall be generated. Wait until the tip of the occasion and, should you win, you will get your winnings according to the odds. The variety of payment techniques in the app is kind of massive, because of this, each player will have the power to select the right one for themselves. The bonus might be mechanically credited after depositing it in the type of further cash in your bonus account. Open the smartphone settings and beneath Security present entry to put in applications from unknown sources.
The 888starz mobile model is a good solution for these users who at all times want to be online at the expense of their cellular system. It is suitable for all, both Android and iOS house owners without any mobile requirements. Just open the location in any of your browsers, log into your account and begin taking half in. The platforms mobile app is designed in the principle colours of the official website black, orange, green and white. Navigating the app may be very straightforward, even for these who are not familiar with the world of playing. The app has a major navigation bar which covers the main areas of the platform such as GAMES, F.A.Q., BONUSES, PROMOTIONS, and NEWS.
If a participant wins the sport, they are eligible to obtain the chips that were wagered on it as a part of their winnings. When you obtain 888sport app in 2023, you take pleasure in sports activities betting, cricket betting, live wagering and streaming, as properly as on line casino gambling. 888sport cell app is an incredible app from a dependable and trusted online bookkeeper. So if youre seeking to place bets in your favourite sports activities, this could be a viable possibility.
For India, you need to choose Rupee or another handy equal from these provided. If you might have a promo code, you can even enter it. After profile verification, the promo code will allow you to get an exciting bonus. While there is not a reside casino right here, there are nine completely different video poker video games that individuals can take part in. These are accessible by way of the menu bar on the prime of the homepage.
- While there is not a stay casino here, there are nine different video poker games that individuals can take part in.
- If you folks add your cash in this utility, then you might be also given additional bonus in it.
- Updating your phone to the most recent operating system can be really helpful.
- I even have already made a deposit, the money is credited to th...
03:17
888sport Cellular App h+ Media
888sport Cellular App
The tennis bracelet obtained its rightful entry into the accessorizing world when Chris Evert, a top American tennis player wore it as a fortunate charm in a g.. Fun88 is properly established and that is demonstrated by the various licenses that it has gained to function. To start, its regulated by the United Kingdom Gambling Commission. This is ranked among the most reputable companies overseeing on line casino operations on the planet.
As for the 30 free spins, they apply to a particular slot from the Jeetplay variety offered. The spins are automatically credited and are valid for the following 24 hours. That signifies that you want to wager 45x earlier than you can convert your bonus to money.
For the 888sport app download, check with the relative section on this article. There is not any separate utility for 888sport apk download on PC. But youll be able to all the time download 888sport app for your mobile phone. Regardless, the desktop website works nice by itself, so that you shouldnt have any drawback working it in your PC browser.
Watch live streams of matches and assume about statistical information. You can obtain the 10Cric on line casino APK by following the related hyperlink we share at the beginning of this evaluate. Slower operation compared to different Indian gambling apps.
Neither the bookmaker nor the provider can influence the result of bets. The activity is carried out by the license obtained by the Government of Curacao. The administration ensures all users the honesty of funds, the soundness of the software, and the safety of personal knowledge. It can be value noting that works 4rabet legal in India. Online roulette is considered one of the most famous video video games performed online in fun88. Its thrilling to play, the guidelines are very reliable and it affords a variety of the utmost favorable triumphing odds and payouts on the on line casino.
- The 888starz app for Android offers fixed entry to all nice bonuses and advertising offers of the company.
- Bitcoin is turning into the primary commonplace on US going through online casinos, Pannick.
- With the app of 888Starz, every of our clients can place sports bets, play casino games, and use other site services and options instantly from their smartphone.
- As youve carried out earlier than, go to the web site in your browser and download the app.
The website administration also allows all clients to receive a welcome bonus. Users have two sorts to select from Welcome Sports 200% and Welcome Casino 200%. You can accept the offer, play 4rabet for money with out the promo, or redeem it later. When choosing the first registration 4Rabet methodology, you must enter an e mail address and create a strong password.
It could be very focused on soccer and basketball betting, with everything else being secondary. That being stated, there are...
03:12
03:01
How to create multidomain web applications with Podman and Nginx Linux.com
Learn how to use Podman and Nginx to work with applications from different domains on the same host.
Read More at Enable Sysadmin
The post How to create multidomain web applications with Podman and Nginx appeared first on Linux.com.
03:00
XWayland 23.1 Released With High Resolution Scroll Wheel, DMA-BUF v4 Feedback Phoronix
Coincidentally landing on GNOME 44 release day is also XWayland that allows legacy X11 client applications/games to run atop Wayland environments. With XWayland 23.1 comes a number of shiny new features to continue to enhance the X11 experience on Wayland...
02:55
Distribution Release: Trisquel GNU/Linux 11.0 DistroWatch.com: News
Trisquel GNU/Linux is a 100% libre Ubuntu-based Linux on Ubuntu 22.04 LTS and greatly expands compatibility with a wider range of CPU architectures. "New supported architectures. Following the addition of 32-bit ARM support in Trisquel 10, we now introduce....
02:53
Google Suspends Chinese Shopping App Pinduoduo Over Malware Concerns HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
Pinduoduo has confirmed the incident, but denied the presence of malware in its app.
This is a post from HackRead.com Read the original post: Google Suspends Chinese Shopping App Pinduoduo Over Malware Concerns
02:28
Version
44 of the GNOME desktop environment has been released. "This
release brings a grid view in the file chooser, improved settings
panels for Device Security, Accessibility, etc, and refined quick
settings in the shell. The Software and Files apps have seen
improvements, and a whole slew of new apps has joined the GNOME Circle
". See the release notes for
details.
02:28
NASA's AIM Mission Comes to an End After Nearly 16 Years SoylentNews
The satellite helped scientists learn more about polar mesospheric clouds:
It looks to be the end of the line for NASA's Aeronomy of Ice in the Mesosphere, or AIM, spacecraft. The mission launched on April 25, 2007, as part of the Small Explorer program (the 90th such mission since 1958). The satellite featured three science instruments designed to study polar mesospheric clouds (PMCs) that form high above Earth in the polar regions.
The satellite was put into orbit 312 miles up. Data from the long-running mission helped scientists better understand the formation of these unique clouds, also called night-shining or noctilucent clouds, and was featured in 379 peer-reviewed scientific papers over the years.
AIM had a planned mission duration of just 26 months but has been operating mostly issue-free for nearly 16 years. In 2019, however, NASA noticed the satellite's batteries were starting to degrade but were still functional enough to continue to collect a significant amount of data and return it to Earth.
NASA said the craft's battery has reached a point where it is no longer able to receive commands or collect data. The space agency will monitor the satellite for a two-week period and attempt to reboot it, but it isn't looking good.
[...] The near-term fate of the AIM satellite wasn't mentioned, and it's unclear if NASA has the ability to bring it back down to Earth like it has with other decommissioned craft. The satellite measures roughly 1.4m x 1.1m (4 ft 7 in 3 ft 7 in) and weighs 197 kg (434 pounds). If left unaddressed, it'd add to the growing list of space junk orbiting our planet.
Read more of this story at SoylentNews.
02:13
Windows Falls to 16% Market Share in India (It was 97% in 2009), Microsoft Layoffs Reach India Too Techrights
Summary: This months picture from the worlds most populous nation does not look good for Microsoft (it looks good for GNU/Linux); anonymous rumour mills online say that Microsoft isnt moving to India but is actually firing staff based in India, so its a case of shrinking, not offshoring. When even low-paid (much lower salaries) staff is discarded it means things are very gloomy.
02:01
GNOME 44 Released With Many Desktop Enhancements Phoronix
GNOME 44 is now officially out as the latest half-year update to this widely-used open-source desktop...
02:00
Web3 Is Going Just Great Creator On Why It Isnt IEEE Spectrum

In mid-2021, the term Web3 suddenly exploded into the public consciousness. As people scrambled to figure out what it wascryptocurrencies? blockchain? nonfungible tokens?venture capital firms were pouring money into new startups, over US $30 billion before the year was out.
Meanwhile, Molly White, a software engineer, started reading up on the tech in case that was the direction her career would be heading in. But she found herself taking a different direction: She launched the website Web3 Is Going Just Great, with the aim of tracking the scams and fraud in the cryptocurrency world. So far, shes tallied $11.8 billion in money lost on the websites Grift Counter. White answered five rapid-fire questions on the Web3 phenomenon and why shes still not impressed.
How did you end up running a site like Web3 Is Going Just Great?
Molly White: When I started researching the topic, I was just seeing a lack of reporting on some of the downsidesyou know, the hacks, the scams, the fraud. And so I decided I could do my part to try and fill that void to some extent, because I feel like its important that people get the full picture.
A lot of the projects youre tracking involve cryptocurrency and blockchain technologies. Is that what Web3 means? Are all of these terms synonymous?
White: Its primarily a marketing term. And I think the industry benefits from how nebulous it is because it can mean whatever is most useful at that time. But broadly speaking, Web3 refers to blockchains underpinning everything you do online.
The crypto industry seemed like it might collapse when the cryptocurrency exchange FTX went bankrupt in November 2022, but youre still updating the site with new projects. Is the industry still just trucking along, or has it changed after that event?
White: I think that FTX and the related collapses have been a really big hit to the crypto brand, but I think that the crypto industry is constantly working on finding the next big thing that they can sell retail investors on. And so that is very much underway at this point.
You can sort of see whats happening as people start distancing themselves from FTX and saying that the FTX...
01:52
Adobe Releases AI Art Generator Firefly To Take On Midjourney And DALL-E, Could Be As Influential As The First Photoshop cryptogon.com
Its coming very quickly now. Via: TechRadar: Adobe has revealed its answer to AI art generators like Midjourney, Dall-E, and Stable Diffusion and the new family of generative AI tools, collectively called Adobe Firefly, could ultimately be as influential as the original Photoshop was in 1990. The giant behind apps like Photoshop and Illustrator []
01:36
Links 22/03/2023: GNOME 44 Kuala Lumpur Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Pseudo-Open Source
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Monopolies
- Gemini* and Gopher
-
GNU/Linux
-
Desktop/Laptop
-
OpenSource.com 8 steps to refurbish an old computer with Linux
We live in a remarkable era. It wasnt so long ago we were all chained to the upgrade treadmill,...
-
-
01:26
DPReview.com Is Closing April 10th cryptogon.com
I became interested in 35mm photography back in the 1980s when I was in high school. After a brief stint in photography school in the early 1990s, I realized that the only way I was going to make consistent money with photography was with weddings. So, I moved on. But my love of photography remained, []
01:26
KDE XWayland Video Bridge Aims To Improve Linux Desktop Screen Sharing Phoronix
KDE developers David Edmundson and Alex Poi have begun working on XWaylandVideoBridge as a new project to help improve Linux desktop screen sharing for X11-based applications that may try to share the contents of Wayland screens, such as could be the case for some software like Discord, Microsoft Teams, Skype, and others...
00:59
ENISA: Ransomware became a prominent threat against the transport sector in 2022 Security Affairs
The European Union Agency for Cybersecurity (ENISA) published its first cyber threat landscape report for the transport sector.
A new report published by the European Union Agency for Cybersecurity (ENISA) analyzes threats and incidents in the transport sector. The report covers incidents in aviation, maritime, railway, and road transport industries between January 2021 and October 2022.
The report provides a detailed analysis of the prime threats to the transport sector, the threat actors and related motivations.
During the period covered by the report, the expert identified the following prime threats:
- ransomware attacks (38%),
- data related threats (30%),
- malware (17%),
- denial-of-service (DoS), distributed denial-of-service (DDoS) and ransom denial-of-service (RDoS) attacks (16%),
- phishing / spear phishing (10%),
- supply-chain attacks (10%).
During the reporting period, ransomware was the most prominent threat against the sector in 2022. The researchers pointed out that the ransomware attacks doubled compared to the previous year. Threat actors behind ransomware attacks are not exclusively financially-motivated.
Nation-state actors, cybercriminals, and hacktivists, are the threat actors with the biggest impact on the organizations in the sector.
Most of the attacks on the transport sector (54%) are carried out by cybercriminals.
The report warns that hacktivist activity targeting the transport sector, including DDoS attacks, is likely to continue. Airports, railways and transport authorities are privileged targets of hacktivists.
The good news is that ENISA experts did not receive reliable information on a cyberattack affecting the safety of transport.
The researchers also warn that future Ransomware attacks will likely target and disrupt OT op...
00:49
Are You Good At Authorized Betting Apps? Heres A Quick Quiz To Seek Out Out h+ Media
Are You Good At Authorized Betting Apps? Heres A Quick Quiz To Seek Out Out
The courtroom ruling in favor of New Jersey paved the means in which for states to legalize sports playing. Despite its relative infancy, US online sports activities betting apps have already turn out to be wildly popular in states like New Jersey or Pennsylvania. But we as a company dont support/promote betting in any way.
Some betting apps shall be stronger for horse racing than others, particularly the ones who can stream the race meetings. Even when you dont plan to live bet, its still a good idea to check out the live choices that the sportsbook often provides. If youre using a good sports activities betting app, you shouldnt have to fret about app security. We have a team of more than 250 app developers operating to meet your request according to your business needs. Overall, the product is great and getting better.
- Yes, each wifi and cellphone information work for online playing.
- With the ideas above, it is possible for you to to make the best choice of which mobile cricket betting app to make use of.
- But we as an organization dont support/promote betting in any means.
- Better nonetheless, you can also bet on eSport games.
The app itself is amongst the finest to make use of, with the convenience of inserting a bet certainly one of many positives to the bet365 app. To do this, discover the hyperlink or APK, obtain, and install the app. BetMGM is one other US primarily based sports activities betting app that gives live in game betting throughout a variety of markets. Caesars Sportsbook is Saturday Down Souths most popular sports activities betting app. Gambling companies must have the mandatory licenses and adjust to the law, otherwise, they should reply for unlawful actions. Thanks to the numerous payment methods available, online gamblers can choose their most popular cost method and keep it up for both deposits and withdrawals.
Gambling Licence From A Trusted Authority
They are truthful and provide a high quality service from high to backside. Its also the best approach to request withdrawals, which is defined later. The best on-line betting apps have a couple of things in common.
Betway 1 For On-line Cricket Betting
Click the Download button and make sure the action. Many of the bookmaker apps listed on our web site additionally allow punters in India to take benefit of their beneficiant welcome bonus and free wager offers India using cellular units too. Many on-line sports betting sites provide generous welcome presents but require players to play through their winnings as a lot as 100 occasions to withdraw them as real money.
It is essential that the IPL betting sites shield your identity and process the withdrawals within the fastest time possible. Our staff at My Betting Sites India came up with a number of betting suggestions to ma...
00:47
Are You Good At Authorized Betting Apps? This Is A Quick Quiz To Find Out h+ Media
Are You Good At Authorized Betting Apps? This Is A Quick Quiz To Find Out
On the other hand, when you require a promotional code to say a sure bonus, you can find it on the page of the playing website thats dedicated to promotions. Signing Up on WorldTeam11 is pretty easy although the benefit that youve got upon Sign Up are immense. Follow the rules issued by the GamingCommission. The huge brands permit you to claim the same free bets as you would their desktop providing, claimable via the promotions part. The process of downloading is simple; you want to make several steps only to begin betting through the app online. After you have proceeded with the Becric apk obtain, you could marvel what to do next.
The greatest playing apps provide a seamless experience when in comparability with utilizing a normal betting web site. Bons betting firm is a new company that received registered in 2020 and bought its license from Curacao. You can quickly find a particular tournament and match by way of the search bar in the functions, or by navigating via the sections. As for the bets themselves, FanDuel has plenty to supply and is the forefather of similar sport parlays, which are now additionally in style on different websites.
The 22 bets app could be thought-about protected and safe for Indian sports activities lovers as a outcome of 22bet is ruled by and accredited by the Curacao Gaming Commission. The class contains quite a few special events, highlights of present games, and the chance to recall a game underneath certain circumstances. The record of obtainable choices continues to develop. BetMGM is the self proclaimed king of sportsbooks, and theres no denying that its platform backs up this slogan. The sportsbook app is accessible for use both on Android and iOS gadgets.
The court docket ruling in favor of New Jersey paved the best way for states to legalize sports activities playing. Despite its relative infancy https://mobilbahis.icu/joker-megaways-slot-review/, US on-line sports betting apps have already turn into wildly popular in states like New Jersey or Pennsylvania. But we as a company dont support/promote betting in any means.
With more and more cricket lovers in India attempting out reside in play betting for themselves, this is positive to become a more important part of the business quickly. As you probably can see, there are many methods to make online betting deposits these days the one thing you have to do is select the tactic that works finest for you. Bringing a fresh and engaging interface thats user friendly and makes it straightforward to navigate. Every online betting web site has its personal process in phrases of putting bets, but typically, it goes one thing like this.
We happened to test amidst the primary running of The Hundred within the UK, and games for this competition wer...
00:47
Are You Good At Authorized Betting Apps? Here Is A Fast Quiz To Search Out Out h+ Media
Are You Good At Authorized Betting Apps? Here Is A Fast Quiz To Search Out Out
Deposit and place a minimal 10 money wager at single or amassed odds of 1/1 or higher and we will present you with 1 x 5 in free bets plus an additional 3 x 5 Free Bets the next day. First launched in 2017 in Australia, PointsBet Sportsbook has quickly turn into one of many biggest betting operators Down Under. Bonuses for opening an account are additionally supplied. Yes, the Pin up casino apk supplies excellent betting expertise and access to a fantastic number of reside tables and dealers. This on-line betting firm has a proud Indian heritage, which is necessary to a lot of sports activities fans who want to wager online using a agency like Comeon.
Right from just being an thought to a completely functional enterprise, we help your small business to grow at each stage. You can get them utilizing the mobile app or the net site. As playing may be addictive, its important youre conscious of the risks and arm yourself with tools and strategies to make sure it stays fun.
The court docket ruling in favor of New Jersey paved the finest way for states to legalize sports activities gambling. Despite its relative infancy, US on-line sports betting apps have already turn into wildly in style in states like New Jersey or Pennsylvania. But we as a company dont support/promote betting in any means.
If you have already got a consumer friendly expertise through the mobile betting web site, then you are prone to expertise the same with the app. Their welcome promotion provides you a 100% match on your first deposit with a $150 most limit. Youll additionally get more bonuses, promotions and options than any other bookie can supply. Indian gamers can entry all their favorite sports activities cricket, football, tennis, and so forth. However, only the preferred and big IPL betting websites consists of the stay streaming function.
- READ Best Apps to watch live cricket Watch Indian Cricket Team in Action at your personal home.
- Overall, the product is great and getting higher.
- In our opinion, the general best football betting app is Bet365.
- Deposit and place a minimum 10 money wager at single or accrued odds of 1/1 or greater and we will give you 1 x 5 in free bets plus an additional three x 5 Free Bets the following day.
The app itself is likely considered one of the greatest to make use of, with the convenience of placing a bet one of many positives to the bet365 app. To do this, find the hyperlink or APK, obtain, and set up the app. BetMGM is one other US based mostly sports betting app that gives reside in sport betting throughout a variety of markets. Caesars Sportsbook is Saturday Down Souths preferred sports betting app. Gambling services will must have the mandatory licenses and adjust to the legislation, otherwise, they will have to answer for unlawful actions. Thanks to the numer...
00:46
Are You Good At Legal Betting Apps? Here Is A Fast Quiz To Seek Out Out h+ Media
Are You Good At Legal Betting Apps? Here Is A Fast Quiz To Seek Out Out
10Cric app accepts Indian rupees as the principle account foreign money and allows you to guess on cricket, horse racing, kabaddi. Note that withdrawals can solely be accomplished to the identical account that you made your preliminary deposit from. In our opinion, the general greatest soccer betting app is Bet365. While the concept behind a web-based sports activities betting app is actually the identical, it allows you to place bets remotely from wherever inside state traces. I couldnt perceive why it was not downloading.
- They supply a ton of various sports activities betting choices, but they excel primarily in soccer.
- With over 12 years of experience in on-line gaming, Adam has seen, played, reviewed, and examined tons of of slot video games.
- The massive manufacturers permit you to declare the identical free bets as youll their desktop offering, claimable via the promotions part.
- The greatest betting apps in India keep attempting to face out from each other by offering playful recreation modes.
Our football predictions are made by professionals, however this doesnt guarantee a revenue for you. We would definitely recommend the operator not just for the cricket betting app it presents, but also its main give consideration to soccer. This is due to the fact that it is illegal for a betting website to function on Indian territory. BetMGM has risen to turn into the countrys third hottest sportsbook after a couple of false begins.
Moreover, if your withdrawals exceed the $1,000 limit, the operator reserves the proper to ask you for further verification as part of its KYC coverage. If you depend the general numbers, youll see that Australia was a profitable country for about eighty years while England has only about 50. Its important to note the risks bettors take by using unlawful or offshore betting sites whereas ready for a extra strong Florida mobile betting launch.
In phrases of sheer profit potential, its one of the best bonuses at any on-line sportsbook. Pete Rose, the all time MLB leader in hits, was similarly banned from baseball in 1989 for betting on video games while he was an MLB supervisor. At first, this was the game of kings and only an important folks performed it.
Playing Licence From A Trusted Authority
There are no restrictions or central laws that forestall Indian punters from using betting apps within the area. This allows fans to really really feel part of the motion and it increases the thrill ten fold. Yes, gamers can simply deposit and withdraw cash from the betting App.
Right from simply being an concept to a completely useful enterprise, we help your corporation to develop at each stage. You can get them using the cellular app or the internet site. As playing may be addictive, its important youre aware of the risks and ar...
Wednesday, 22 March
18:00
Visiting the Ramses the Great Exhibit. Antarctica Starts Here.
Early in October of 2022.ev, we paid a visit to an exhibit of artifacts at the Fine Arts Museum of San Francisco from the reign of Ramesses II, third ruler of the nineteenth dynasty of Egypt. Since covid started we haven't done a whole lot of going places so we figured that, all things in our respective risk models being equal, this would be an outing worth making the time for. As I write those post I don't know if it's still there, but the museum's page didn't 404 so it probably is. If you're in the area, it's worth paying the museum a visit and spending a few hours exploring.
Anyway, here are the pictures I took.