| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Friday, 24 March
01:41
New Android Botnet Nexus Being Rented on Russian Hacker Forum HackRead | Latest Cybersecurity and Hacking News Site
Nexus contains a module equipped with encryption capabilities which point towards ransomware.
This is a post from HackRead.com Read the original post: New Android Botnet Nexus Being Rented on Russian Hacker Forum
01:39
Ubuntu 20.04.6 LTS Released With Restored UEFI Secure Boot Support Phoronix
Ubuntu 20.04.6 LTS is available today as the newest point release for those continuing to employ this older long-term support releases...
01:30
Distribution Release: Proxmox 7.4 "Virtual Environment" DistroWatch.com: News
Proxmox is a commercial company offering specialised products based on Debian GNU/Linux. The company has released an update to its "Virtual Environment" series which introduces updated virtual machine and filesystem packages along with a new dark theme. The release announcement lists the key features: "We're very excited to....
01:10
NVIDIA 530.41.03 Linux Driver Released With IBT Kernel Support, Vulkan Video Phoronix
One month ago NVIDIA released the 530 series Linux driver beta while today it's been promoted to stable with the NVIDIA 530.41.03 driver release...
01:02
Security updates for Thursday LWN.net
Security updates have been issued by CentOS (firefox, nss, and openssl), Fedora (firefox, liferea, python-cairosvg, and tar), Oracle (openssl and thunderbird), Scientific Linux (firefox, nss, and openssl), SUSE (container-suseconnect, grub2, libplist, and qemu), and Ubuntu (amanda, apache2, node-object-path, and python-git).
01:00
Working with BGAs: Soldering, Reballing, and Rework Hackaday

In our previous article on Ball Grid Arrays (BGAs), we explored how to design circuit boards and how to route the signals coming out of a BGA package. But designing a board is one thing soldering those chips onto the board is quite another. If youve got some experience with SMD soldering, youll find that any SOIC, TQFP or even QFN package can be soldered with a fine-tipped iron and a bit of practice. Not so for BGAs: well need to bring out some specialized tools to solder them correctly. Today, well explore how to get those chips on our board, and how to take them off again, without spending a fortune on equipment.
Tools of the Trade
For large-scale production, whether for BGA-based designs or any other kind of SMD work, reflow ovens are the tool of choice. While you can buy reflow ovens small enough to place in your workshop (or even build them yourself), they will a...
00:29
NEW 'Off The Hook' ONLINE 2600 - 2600: The Hacker Quarterly
NEW 'Off The Hook' ONLINE
Posted 23 Mar, 2023 13:29:05 UTC
The new edition of Off The Hook from 03/22/2023 has been archived and is now available online.
How to tell the difference between a chatbot and a human, Space Rogue joins the panel to discuss his new book "How the Hackers Known As L0pht Changed the World", choosing a hacker handle, testifying before Congress, the origins of L0pht, writing a book, the end of L0pht as @stake, the Hacker News Network, remembering Aloria.
00:24
A common user mistake can lead to compromised Okta login credentials Help Net Security
Logged failed logins into a companys Okta domain could be used by threat actors to discover access credentials of valid accounts, Mitiga researchers have found. Those credentials can then be used log in to any of the organizations platforms that use Okta single sign-on (SSO) or if the login credentials belong to an administrator to gain privileged access to other systems or restricted network areas. How to discover valid Okta credentials in logs More
The post A common user mistake can lead to compromised Okta login credentials appeared first on Help Net Security.
00:22
Breakthrough discovery in materials science challenges current understanding of photoemission Lifeboat News: The Blog
What exactly is lightand what is it made of? Its an age-old question that dates back to antiquity, and one of the most important investigations undertaken by scientists looking to understand the nature of reality.
00:00
Nvidia Speeds Key Chipmaking Computation by 40x IEEE Spectrum

Nvidia says it has found a way speed up a computation-limited
step in the chipmaking process so it happens 40 times as fast as
todays standard. Called inverse lithography, its a key tool to
allow chipmakers to print nanometer-scale features using light with
a longer wavelength than the size of those features. Inverse
lithographys use has been limited by the massive size of the needed
computation. Nvidias answer, cuLitho, is a set of algorithms
designed for use with GPUs, that turns what has been two weeks of
work into an overnight job.
The technology will allow fabs to increase throughput, reduce their carbon footprint, and set the foundations for 2-nanometer [manufacturing processes] and beyond, said Nvidia CEO Jensen Huang at the Nvidia GTC developer on Tuesday.
Leading logic chip foundry TSMC will be qualifying cuLithos use in production starting in June, said Huang. Design automation software firm Synopsys plans to integrate software, too, and lithography equipment maker ASML plans to support cuLitho in its products as well.
Photolithography is basically the first step in the chipmaking process. It involves bouncing light off of a pattern called a photomask to project the forms of transistor structures and interconnects onto the wafer. (More mature technology uses transmissive photomasks instead of reflective ones, but the idea is the same.) It takes 98 photomasks to make an H100 GPU, Jensen said. The features projected from the photomask are smaller than the wavelength of light used193 nanometers for the relatively large features and 13.5 nanometers for the finer bits. So, without the aid of tricks and design rules collectively called optical proximity correction, youd only get a blurry mess projected on the wafer. With optical proximity correction, the designs on the photomask only vaguely resemble the pattern of light at the chip.
With the need for finer and finer features, the corrected shapes on the photomask have become more and more elaborate and difficult to come up with. It would be much better to start with the pattern you want on the wafer and then calculate what pattern on the photomask would produce them. Such a scheme is called inverse lithography. Simple as it sounds, its quite difficult to compute, often taking weeks to compile.
In fact, its such a slog that its often rese...
Thursday, 23 March
23:56
Mesa 23.1 RADV Gets Vulkan Mesh/Task Shaders Working For AMD RDNA3 GPUs Phoronix
Thanks to the work of Timur Kristf on Valve's Linux graphics driver team, the RADV driver in Mesa 23.1 this morning received support for Vulkan mesh and task shaders for Radeon RX 7000 series "RDNA3" graphics processors...
23:28
Intel LAM Will Try Again For Linux 6.4 Phoronix
Intel's Linear Address Masking (LAM) functionality to make use of untranslated address bits of 64-bit linear addresses for arbitrary metadata is aiming to be mainlined with the upcoming Linux 6.4 cycle...
23:17
Rare Cosmic Event Will See 5 Planets Align in The Sky. Here's How to Watch. SoylentNews
Don't miss the planet parade taking place at the end of March:
Jupiter, Mercury, Venus, Uranus, and Mars are set to align in an arc formation on the nights of March 25 through 30, alongside the Moon.
Jupiter may sink into the sunset and get lost in sunlight after the 28th, though, so aim to see this relatively rare cosmic event by then.
If you want to spot all five planets in one night, timing, dark skies, and a clear view of the horizon are key.
[...] Shortly after the Sun dips below the horizon, look to the west. Low in the sky, where the Sun just set, Jupiter and Mercury will appear side-by-side.
Dwindling sunlight might make them hard to see with the naked eye. So, if you can't spot them at first, try binoculars. Just make sure the Sun is below the horizon so you don't potentially harm your eyes by looking at it through binoculars.
Linked story includes more info and a star map to assist your celestial gaze.
Read more of this story at SoylentNews.
23:16
23:13
Proxmox VE 7.4 Released With Linux 5.15 LTS + Linux 6.2 Support, New Dark Theme Phoronix
22:55
Nexus: A New Rising Android Banking Trojan Targeting 450 Financial Apps The Hacker News
An emerging Android banking trojan dubbed Nexus has already been adopted by several threat actors to target 450 financial applications and conduct fraud. "Nexus appears to be in its early stages of development," Italian cybersecurity firm Cleafy said in a report published this week. "Nexus provides all the main features to perform ATO attacks (Account Takeover) against banking portals and
22:41
Dole discloses data breach after February ransomware attack Security Affairs
Dole Food Company confirmed that threat actors behind the recent ransomware attack had access to employees data.
Dole Food Company is an Irish agricultural multinational corporation, it is one of the worlds largest producers of fruit and vegetables, operating with 38,500 full-time and seasonal employees who supply some 300 products in 75 countries. Dole reported 2021 revenues of $6.5 billion.
In February, the company announced that it has suffered a ransomware attack that impacted its operations. At the time of the disclosure, the company did not provide details about the attack.
Dole plc (DOLE:NYSE) announced today that the company recently experienced a cybersecurity incident that has been identified as ransomware. reads a notice published by the company. Upon learning of this incident, Dole moved quickly to contain the threat and engaged leading third-party cybersecurity experts, who have been working in partnership with Doles internal teams to remediate the issue and secure systems.
Now Dole Food Company has confirmed threat actors behind the February ransomware attack had access to the information of an undisclosed number of employees.
We have in the past experienced, and may in the future face, cybersecurity incidents. In February of 2023, we were the victim of a sophisticated ransomware attack involving unauthorized access to employee information. reads the annual report filed with the U.S. Securities and Exchange Commission (SEC). Upon detecting the attack, we promptly took steps to contain the attack, retained the services of le...
22:22
Researchers detail groundbreaking Angelman syndrome development Lifeboat News: The Blog
Researchers at Texas A&M University have developed the first molecular therapeutic for Angelman syndrome to advance into clinical development.
In a new article, published today in Science Translational Medicine, Dr. Scott Dindot, an associate professor and EDGES Fellow in the Texas A&M School of Veterinary Medicine and Biomedical Sciences (VMBS) Department of Veterinary Pathobiology, and his team share the process through which they developed this novel therapeutic candidate, also known as 4.4.PS.L, or GTX-102. Dindot is also the executive director of molecular genetics at Ultragenyx, which is leading the development of GTX-102.
Angelman syndrome (AS) is a devastating, rare neurogenetic disorder that affects approximately 1 in 15,000 live births per year; the disorder is triggered by a loss of function of the maternal UBE3A gene in the brain, causing developmental delay, absent speech, movement or balance disorder, and seizures.
22:00
Creating a Game Boy ROM From Pictures Hackaday

There are very few legal ways of obtaining ROM files for video games, and Nintendos lawyers are extremely keen on at least reminding you of the fact that you need to own the game cart before obtaining the ROM. With cart in hand, though, most will grab a cart reader to download the game files. While this is a tried-and-true method, for GameBoy games this extra piece of hardware isnt strictly required. [Travis Goodspeed] is here to show us a method of obtaining ROM files from photographs of the game itself.
21:39
2023 Cybersecurity Maturity Report Reveals Organizational Unpreparedness for Cyberattacks The Hacker News
In 2022 alone, global cyberattacks increased by 38%, resulting in substantial business loss, including financial and reputational damage. Meanwhile, corporate security budgets have risen significantly because of the growing sophistication of attacks and the number of cybersecurity solutions introduced into the market. With this rise in threats, budgets, and solutions, how prepared are industries
21:30
Zhaoxin Beginning Work Bringing Up "Yongfeng" CPU Support For The Linux Kernel Phoronix
Chinese fabless semiconductor company Zhaoxin, which was started ten years ago as a joint venture between VIA and the Shanghai Municipal Government to create domestic x86 CPUs, is now in the process of working on supporting their newest Yongfeng processors with the Linux kernel...
21:13
MoltenVK 1.2.3 Released For Continuing To Enhance Vulkan Atop iOS/macOS Phoronix
21:10
Pwn2Own Vancouver 2023 Day 1: Windows 11 and Tesla hacked Security Affairs
On the first day of Pwn2Own Vancouver 2023, the organization awarded $375,000 (and a Tesla Model 3) for 12 zero-day flaws.
The Pwn2Own Vancouver 2023 has begun, this hacking competition has 19 entries targeting nine different targets including two Tesla attempts.
On the first day of the event, the organization awarded $375,000 (and a Tesla Model 3) for 12 zero-day vulnerabilities demonstrated by the participants.
The first hack of the day was performed by the AbdulAziz Hariri (@abdhariri) of Haboob SA (@HaboobSa), who demonstrated a zero-day attack against Adobe Reader in the Enterprise Applications category. Hariri earned $50,000 and 5 Master of Pwn points.
One of the most interesting attacks was conducted by the Singapore team STAR Labs (@starlabs_sg), they successfully targeted Microsoft SharePoint in the Server category earning $100,000 and 10 Master of Pwn points.
21:02
Links 23/03/2023: Linux 6.2.8 and XWayland 23.1.0 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
- ...
20:59
X.Org Needs More People To Run For The Board Phoronix
The X.Org Board of Directors has delayed their election process by two weeks in hopes of having more candidates nominated to run for the board as currently they do not have enough candidates to start an election...
20:35
Feral Hogs Are the Invasive Menace You've Never Thought About SoylentNews
Think of the worst invasive species you know. Kudzu: smothering trees and houses, growing a foot a day. Burmese pythons: stripping the Everglades of small animals. Asian carp: hoovering streams clean of plankton and swimming toward the Great Lakes.
They all came from somewhere else, arrived with no natural predators, outcompeted local flora and fauna, and took over whole ecosystems. But they all have their limitations: Kudzu dies in a hard freeze, carp can't tolerate salt water, and pythons can't cover long distances very fast. (Thankfully.)
Now imagine a species with all those benefitsforeign origin, no enemiesand no roadblocks to dominance: One that is indifferent to temperature, comfortable in many landscapes, able to run a lot faster than you, and muscular enough to leave a big dent in your car. That describes any of the possibly 6 million feral hogs in the United States, the most intractable invasives that most people have never heard of.
[...]
USDA research estimates that, on their own, hog populations will expand their range by about 4 to 8 miles per year. But Mayer jokes darkly that they have relocated at "about 70 miles per hourwhich is the speed of the pickups taking them down the highway."
[...]
This story originally appeared on wired.com.
Read more of this story at SoylentNews.
20:29
Operation Soft Cell: Chinese Hackers Breach Middle East Telecom Providers The Hacker News
Telecommunication providers in the Middle East are the subject of new cyber attacks that commenced in the first quarter of 2023. The intrusion set has been attributed to a Chinese cyber espionage actor associated with a long-running campaign dubbed Operation Soft Cell based on tooling overlaps. "The initial attack phase involves infiltrating Internet-facing Microsoft Exchange servers to deploy
20:22
Startups 3D-printed rocket delivers stunning night launch but fails to reach orbit Lifeboat News: The Blog
(CNN) Startup Relativity Space sent what its calling the worlds first 3D-printed rocket toward space on Wednesday, vaulting it into the upper reaches of the atmosphere. Though, it suffered an engine issue after launch and failed to reach orbit.
Terran 1, a 110-foot-tall (33.5-meter) vehicle designed to haul lightweight satellites into orbital space, lifted off from Cape Canaveral Space Force Station on Floridas eastern coast at just before 11:30 pm ET. The rocket, powered by super-chilled methane and oxygen, burned a bright blue-green against the night sky.
After the first stage of the rocket the bottommost portion of the rocket that gives the initial thrust at liftoff expended its fuel, it detached from the rockets upper stage. But the engine meant to propel that portion appeared to ignite only briefly, leaving the rocket without enough power to reach orbit.
19:00
Smart Occupancy Sensor Knows All Hackaday

In the last few decades, building engineers and architects have made tremendous strides in improving the efficiency of various buildings and the devices that keep them safe and comfortable to live in. The addition of new technology like heat pumps is a major factor, as well as improvements on existing things like insulation methods and building materials. But after the low-hanging fruit is picked, technology like this smart occupancy sensor created by [Sina Moshksar] might be necessary to help drive further efficiency gains.
Known as RoomSense IQ, the small device mounts somewhere within a small room and uses a number of different technologies to keep track of the number of occupants in a room. The primary method is mmWave radar which can sense the presence of a person up to five meters away, but it also includes a PIR sensor to help prevent false positives and distinguish human activity from non-human activity. The device integrates with home automation systems to feed them occupancy data to use to further improve the performance of those types of systems. Its also designed to be low-cost and easy to install, so it should be relatively straightforward to add a few to any existing system as well.
The project is also documented on...
18:37
German and South Korean Agencies Warn of Kimsuky's Expanding Cyber Attack Tactics The Hacker News
German and South Korean government agencies have warned about cyber attacks mounted by a threat actor tracked as Kimsuky using rogue browser extensions to steal users' Gmail inboxes. The joint advisory comes from Germany's domestic intelligence apparatus, the Federal Office for the Protection of the Constitution (BfV), and South Korea's National Intelligence Service of the Republic of Korea (NIS
18:36
SEC Charges Justin Sun, TRON & BitTorrent Companies With Fraud TorrentFreak
 After reporting on all things BitTorrent-related for the
13 years leading up to May 2018, TorrentFreak spotted something
out of the ordinary.
After reporting on all things BitTorrent-related for the
13 years leading up to May 2018, TorrentFreak spotted something
out of the ordinary.
BitTorrent Inc., the company founded by BitTorrent inventor Bram Cohen, and the owner of uTorrent, the worlds most recognized torrent client, suddenly had a new name. When asked about the change, Rainberry Inc. said it was a corporate decision not unlike the Alphabet/Google exercise.
Less than two weeks later, we were able to reveal that TRON founder Justin Sun was planning to buy BitTorrent Inc. Less than a month after that, Sun closed the deal with a reported offer of $140 million.
A shareholder quoted in a TechCrunch report revealed that one of Suns aims was to use the BitTorrent acquisition to legitimize TRONs business.
According to a Securities and Exchange Commission announcement published a few hours ago, the plan failed in at least one key area. Most likely, many, many more.
Fraud: SEC Charges Justin Sun and Three Wholly-Owned Companies
Claims that the SEC had already opened an investigation into Suns business activities have been around for a long time. An extraordinary article written by Christopher Harland-Dunaway and published by The Verge last year left very little doubt.
In an announcement Wednesday, the SEC revealed charges against Justin Sun and three of his wholly-owned companies Tron Foundation Limited, BitTorrent Foundation Ltd., and Rainberry Inc. (formerly BitTorrent Inc.) for the unregistered offer and sale of crypto asset securities Tronix (TRX) and BitTorrent (BTT).
Sun and his companies were further charged with fraudulently manipulating the secondary market for TRX through extensive wash trading, described by the SEC as simultaneous or near-simultaneous purchase and sale of a security to make it appear actively traded without an actual change in beneficial ownership.
Alleged Crypto-Shill Celebrities
The SEC also charged eight celebrities for promoting TRX and/or BTT without disclosing they were being paid to do so.
Actress Lindsay Lohan, YouTuber/Boxer Jake Paul, DeAndre Cortez Way...
18:35
IRC Proceedings: Wednesday, March 22, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-220323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-220323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-220323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-220323.gmi
Over HTTP:
|
... |
18:23
Using oral contraceptives leads to higher risk of breast cancer among older women, reveals study Lifeboat News: The Blog
More than 150 million women worldwide use oral contraceptives to avoid unwanted pregnancies. However, a bombshell study released by researchers at the University of Oxford has now laid bare the risks involved. The study has reportedly established the link between the usage of progestogen and the increased risk of breast cancer.
18:23
Gut microbiome can play key role in response to CAR-T cell cancer immunotherapy Lifeboat News: The Blog
Scientists from German Cancer Research Center (DKFZ), together with colleagues from Germany, Israel, and the U.S., have found that the gut microbiome may modulate the efficacy of CAR-T cellular immunotherapy CAR-T cells in patients with B cell lymphomas. Individualized microbiome information retrieved from patients gut microbiomes prior to initiation of CAR T therapy could accurately predict their subsequent responsiveness to therapy, but only in the condition that these patients were not pre-treated with broad spectrum antibiotics.
Increasing evidence from human studies and preclinical experiments suggests that the gut microbiome may modulate the efficacy of T cell-driven cancer immunotherapies, such as immune checkpoint blockade. Immunotherapy with CD19 chimeric antigen receptor (CAR)-T cell has opened up new treatment options for patients with certain forms of refractory and relapsing B-cell leukemias or lymphomas. But the therapy is hampered by considerable heterogeneity in responses. Complete and long-term remission is only achieved in up to 40% of patients.
Researchers from multiple centers in Germany and the United States, led by Eran Elinav, director of the DKFZ-Weizmann Institute of Science Microbiome & Cancer Bridging division, have found that the gut microbiome may modulate the efficacy of CD19 CAR-T cell immunotherapy in patients with B cell leukemias and lymphomas.
18:23
How simple sound and light are treating Alzheimers Disease Lifeboat News: The Blog
In this exclusive excerpt from Your Brain on Art, we learn how sounds and images are proving to measurably heal the brain.
18:22
Telomere shorteninga sign of cellular aginglinked to signs of Alzheimers in brain scans Lifeboat News: The Blog
Changes in the brain caused by Alzheimers disease are associated with shortening of the telomeresthe protective caps on the ends of chromosomes that shorten as cells ageaccording to a new study led by Anya Topiwala of Oxford Population Health, part of the University of Oxford, UK, published March 22 in the open-access journal PLOS ONE.
Telomeres on chromosomes protect DNA from degrading, but every time a cell divides, the telomeres lose some of their length. Short telomeres are a sign of stress and cellular aging, and are also associated with a higher risk of neurological and psychiatric disorders. Currently, little is known about the links between telomere length and changes that occur in the brains of people with neurological conditions. Understanding those relationships could offer insights into the biological mechanisms that cause neurodegenerative disorders.
In the new study, researchers compared telomere length in white blood cells to results from brain MRIs and electronic health records from more than 31,000 participants in the UK Biobank, a large-scale biomedical database and research resource containing anonymized genetic, lifestyle and health information from half a million UK participants.
18:22
Researchers identify neutrophils as major culprits in treatment resistance of pancreatic cancer Lifeboat News: The Blog
Researchers have shown for the first time exactly how immature neutrophilswhite blood cells that are an important part of the immune systemare hijacked by pancreatic cancers to drive immunosuppression and treatment resistance. The study, led by investigators at Sylvester Comprehensive Cancer Center at the University of Miami Miller School of Medicine, is published in Cancer Discovery, a journal of the American Association for Cancer Research.
The paper describes a previously unrecognized signaling circuit in pancreatic cancer that instigates immunosuppression and tumor-promoting inflammation in the pancreatic tumor microenvironment, ultimately creating treatment resistance. The central regulator of this treatment resistance is neutrophil-derived TNF signaling. TNF, or tumor necrosis factor, is a substance in the body that causes inflammation.
This is the first study to implicate immunosuppressive signaling from immature neutrophilsthe earliest sentinels in developing pancreatic cancerin this process, said Jashodeep Datta, M.D., associate director of Translational Research at the Sylvester Pancreatic Cancer Research Institute. Datta, whose laboratory at Sylvester led the research, is senior author of the multicenter study.
18:00
Mistakes Were NOT Made Terra Forming Terra
Israeli Ministry of Health Produces Controversial Report on COVID-19 Vaccine Mortality Terra Forming Terra

What is clear is that the negative response is not immediate for
almost all folks, but the induced weakness opens the door for later
impacts. Think immunity decline and you have it.
Israeli Ministry of Health Produces Controversial Report on COVID-19 Vaccine Mortality
Mar 15 2023
A 16-year-old teenager receives a dose of the Pfizer-BioNtech COVID-19 vaccine at Clalit Health Services, in Israel's Mediterranean coastal city of Tel Aviv on Jan. 23, 2021. (Jack Guez/AFP via Getty Images)
https://www.theepochtimes.com/israeli-ministry-of-health-produces-controversial-report-on-covid-19-vaccine-mortality_5119326.html?u
An Israeli Ministry of Health (MOH) study could not determine mortality risk from Pfizers COVID-19 vaccine and found no evidence of cardiovascular events after COVID-19 vaccination, the MOH said, though an outside expert said the conclusions are contrary to the data.
The study (pdf) was published in Hebrew on the MOH website on Feb. 27. The Epoch Times reviewed and translated the report.
Researchers examined people who passed away or were hospitalized due to an acute cardiovascular event after receiving a Pfizer vaccine.
According to the authors, the MOH decided to conduct the study after other scientific publications did not find a connection between cardiovascular events and COVID-19 vaccination, except for one single report, referring to a Florida study that found a modestly increased risk for cardiac-related mortality 28 days following vaccination, among residents aged 18 years or older. But other research, including Israeli papers, has found a risk of heart inflammation after vaccination.
The MOH...
IT WAS ALL A LIE: NHS Director confirms Hospitals lied Terra Forming Terra
Seeking Brimstone: Why Has Mankind Been Mining Sulfur for Millennia? Terra Forming Terra
17:52
Collected Samples from the Asteroid Ryugu Contain RNA Component SoylentNews
Uracil found in Ryugu samples:
Researchers have analyzed samples of asteroid Ryugu collected by the Japanese Space Agency's Hayabusa2 spacecraft and found uracilone of the informational units that make up RNA, the molecules that contain the instructions for how to build and operate living organisms. Nicotinic acid, also known as Vitamin B3 or niacin, which is an important cofactor for metabolism in living organisms, was also detected in the same samples.
This discovery by an international team, led by Associate Professor Yasuhiro Oba at Hokkaido University, adds to the evidence that important building blocks for life are created in space and could have been delivered to Earth by meteorites.
"Scientists have previously found nucleobases and vitamins in certain carbon-rich meteorites, but there was always the question of contamination by exposure to the Earth's environment," Oba explained. "Since the Hayabusa2 spacecraft collected two samples directly from asteroid Ryugu and delivered them to Earth in sealed capsules, contamination can be ruled out."
"We found uracil in the samples in small amounts, in the range of 632 parts per billion (ppb), while vitamin B3 was more abundant, in the range of 4999 ppb," Oba elaborated. "Other biological molecules were found in the sample as well, including a selection of amino acids, amines and carboxylic acids, which are found in proteins and metabolism, respectively." The compounds detected are similar but not identical to those previously discovered in carbon-rich meteorites.
"The discovery of uracil in the samples from Ryugu lends strength to current theories regarding the source of nucleobases in the early Earth," Oba concludes. "The OSIRIS-REx mission by NASA will be returning samples from asteroid Bennu this year, and a comparative study of the composition of these asteroids will provide further data to build on these theories."
Journal Reference:
Oba, Y., Koga, T., Takano, Y. et al. Uracil in the carbonaceous
asteroid (162173) Ryugu. Nat Commun 14, 1292 (2023). https://doi.org/10.1038/s41467-023-36904-3
Related:
Building
Blocks of Life Found in Meteorite Which Crashed Landed in
Gloucestershire
Asteroid
Material Returned by Japan Probe is Oldest Material Identified and
Contains 23 Amino Acids
All Five
DNA and RNA Nucleobases Found in Meteorites
...
16:30
A closer look at TSAs new cybersecurity requirements for aviation Help Net Security
The Transportation Security Administration (TSA) recently issued new cybersecurity requirements for the aviation industry, which follows last years announcement for railroad operators. Both announcements are part of the Department of Homeland Securitys effort to improve the nations cybersecurity resiliency and align with the National Cybersecurity Strategy released by the White House earlier this month. While the strategy is not perfect, it draws attention to the importance of zero trust within our nations critical infrastructure. Just More
The post A closer look at TSAs new cybersecurity requirements for aviation appeared first on Help Net Security.
16:00
Best practices to secure digital identities Help Net Security
With cybersecurity incidents involving compromised credentials continually the most common cause of a data breach for enterprises and account takeover for individuals, securing digital identities has become paramount. In this Help Net Security video, Jeff Reich, Executive Director at the Identity Defined Security Alliance (IDSA), tells us more.
The post Best practices to secure digital identities appeared first on Help Net Security.
16:00
Commodore 64 Reports the News Hackaday

In the late 80s and into the 90s, [Cameron Kaiser] aka [ClassicHasClass] was an aspiring journalist, first becoming interested in the career in elementary school and then working on various publications into university. At some point, he started using a piece of software for laying out newspapers called The Newsroom which, he admits, was lacking a lot of tools that would have been modern even for the time, but had an otherwise agreeable price tag thanks to its focus more on home desktop publishing and newsletter production than on full-scale newspaper operations. It did have one interesting feature that he never could figure out, though, at least until he went back and pieced this mystery together.
The software itself ran on the Apple II and was eventually ported to other systems of the era, including the Commodore 64. The mystery feature was known as Wire Service and appeared to be a way that users of the software who had a modem could connect with one another and share news releases, layouts, graphics, and other content created in Newsroom, but in the days where it would have been modern never was able to connect to anything. In fact, it was eventually abandoned by the developers themselves in later releases of the software. But [ClassicHasClass] was determined to get it working.
After doing a number of experiments to break down the ways that Wire Service sends information...
15:30
Cyber threats to EU transport sector sends urgent call for enhanced cybersecurity Help Net Security
Between January 2021 and October 2022, the EU Agency for Cybersecurity (ENISA) analyzed and mapped the cyber threats faced by the transport sector, identifying prime threats, analyzing incidents, assessing threat actors, analyzing their motivations, and introducing major trends for each sub-sector, thereby providing new insights. EU Agency for Cybersecurity Executive Director, Juhan Lepassaar, stated that Transport is a key sector of our economy that we depend on in both our personal and professional lives. Understanding More
The post Cyber threats to EU transport sector sends urgent call for enhanced cybersecurity appeared first on Help Net Security.
15:09
Kazakhstans Seizure of Russian Space Assets Threatens the Soyuz-5 Rocket SoylentNews
Russia has spent nearly $1 billion on the development of the new Soyuz-5 rocket:
The Soviet Union created the Baikonur Cosmodrome in 1955 to serve as a test site for intercontinental ballistic missiles. A few years later it became the world's first spaceport with the launch of the historic Sputnik 1 and Vostok 1 missions. The sprawling cosmodrome was a mainstay of the Soviet space program.
After the breakup of the Soviet Union, Russia began to lease the spaceport from the government of Kazakhstan and currently has an agreement to use the facilities through the year 2050. Russia pays an annual lease fee of about $100 million. Neither country is particularly happy with the relationship; the Kazakh government feels like it is under-compensated, and the Russian government would like it to be in its own country, which is why it has moved in recent years to build a new launch site for most of its rockets in the Far East of Russia, at Vostochny.
[...] Earlier this month a Kazakh news site, KZ24, reported that the Republic of Kazakhstan had seized the property of TsENKI, the Center for Utilization of Ground-based Space Infrastructure, in Kazakhstan. This firm, which is a subsidiary of Roscosmos, is responsible for launch pads and ground support equipment for the Russian space corporation. According to the report, which was translated for Ars by Rob Mitchell, TsENKI is barred from removing any assets or materials from Kazakhstan.
[...] Russia has already spent nearly $1 billion on the development of the new Soyuz-5 rocket and plans for its launch site and ground services. When Ars wrote about the rocket's development back in 2017, it was slated for a debut in 2021. Now it is unlikely to debut before at least 2024and given the current dispute with Kazakhstan, it likely will be delayed much longer into the future.
Read more of this story at SoylentNews.
15:00
Top 5 security risks for enterprise storage, backup devices Help Net Security
An average enterprise storage and backup device has 14 vulnerabilities, three of which are high or critical risk that could present a significant compromise if exploited, according to Continuity. The findings underscore a significant gap in the state of enterprise storage and backup security, and shows how much it lags behind the security of other layers of IT. With the growing sophistication of data-centric attacks, the high volumes of data at risk and tightened regulations, More
The post Top 5 security risks for enterprise storage, backup devices appeared first on Help Net Security.
14:30
Vumetric PTaaS platform simplifies cybersecurity assessments for organizations Help Net Security
Vumetric Cybersecurity has launched its Penetration Testing as-a-Service (PTaaS) platform, designed to simplify and modernize cybersecurity assessments for organizations of all sizes. The Vumetric PTaaS platform revolutionizes the penetration testing process by providing self-service capabilities that allow organizations to schedule and manage assessments on-demand. The platforms interactive reporting provides a comprehensive view of identified risks and prioritized remediation strategies. Stakeholders can easily access results, track improvements over time, and analyze project results without additional effort, More
The post Vumetric PTaaS platform simplifies cybersecurity assessments for organizations appeared first on Help Net Security.
14:26
Abel Prize: pioneer of smooth physics wins top maths award Lifeboat News: The Blog
Argentinian-born mathematician Luis Caffarelli has won the 2023 Abel Prize one of the most coveted awards in mathematics for his work on equations that are important for describing physical phenomena, such as how ice melts and fluids flow. He is the first person born in South America to win the award.
Caffarellis results are technically virtuous, covering many different areas of mathematics and its applications, says a statement by Helge Holden, a mathematician at the Norwegian University of Science and Technology in Trondheim who chairs the Abel Committee.
The winner says receiving the news was an emotional moment, because it shows that people have some appreciation for me and for my science.
14:25
New LiGO technique accelerates training of large machine-learning models Lifeboat News: The Blog
Its no secret that OpenAIs ChatGPT has some incredible capabilitiesfor instance, the chatbot can write poetry that resembles Shakespearean sonnets or debug code for a computer program. These abilities are made possible by the massive machine-learning model that ChatGPT is built upon. Researchers have found that when these types of models become large enough, extraordinary capabilities emerge.
But bigger models also require more time and money to train. The training process involves showing hundreds of billions of examples to a model. Gathering so much data is an involved process in itself. Then come the monetary and environmental costs of running many powerful computers for days or weeks to train a model that may have billions of parameters.
Its been estimated that training models at the scale of what ChatGPT is hypothesized to run on could take millions of dollars, just for a single training run. Can we improve the efficiency of these training methods, so we can still get good models in less time and for less money? We propose to do this by leveraging smaller language models that have previously been trained, says Yoon Kim, an assistant professor in MITs Department of Electrical Engineering and Computer Science and a member of the Computer Science and Artificial Intelligence Laboratory (CSAIL).
14:20
Secureworks Security Posture Dashboard enables businesses to understand their cyber readiness Help Net Security
Secureworks bolsters cyber resiliency with launch Of Security Posture Dashboard. Using the 600 billion security events Taegis analyzes daily, the Dashboard empowers customers to understand their cybersecurity posture and how resilient they would be in the face of a cyberattack. These powerful insights provide benchmarking data for customers with industry peers, as well as across market verticals, to strengthen cyber defenses, decrease the risk of attack, and drive actions that close the cyber readiness gap. More
The post Secureworks Security Posture Dashboard enables businesses to understand their cyber readiness appeared first on Help Net Security.
14:15
Lightspin Remediation Hub helps users fix the cloud security threats Help Net Security
Lightspin launched the Remediation Hub as part of its cloud-native application protection platform (CNAPP) solution. An evolution of Lightspins root cause analysis feature, the Remediation Hub provides users the ability to dynamically remediate the most critical cloud environment risks, at scale. As a result, organizations can quickly identify and fix the security threats that matter most. Our Remediation Hub was born out of the overwhelming positive customer response to our root cause analysis feature, said More
The post Lightspin Remediation Hub helps users fix the cloud security threats appeared first on Help Net Security.
14:10
Regula updates IDV products to improve document and biometric verification Help Net Security
Many companies struggle to implement and integrate a bunch of different solutions covering different parts of the IDV process. In fact, according to Regulas survey, 40% of organizations cite this overly complex technical environment as the largest constraint to deploying IDV solutions. Additionally, 38% of respondents expressed concern over the cost of maintaining and managing such an extensive set of technologies. Additionally, 38% of respondents expressed concern over the cost of maintaining and managing such More
The post Regula updates IDV products to improve document and biometric verification appeared first on Help Net Security.
14:00
Nebulon enhances security capabilities with two zero-trust offerings Help Net Security
Nebulon has unveiled two new zero-trust offerings: Two-Person Commit and Single Sign-on (SSO) that advance Nebulons security offering, which includes advanced authentication and authorization, always-on encryption, and 4-minute ransomware recovery capabilitiesall critical for securing distributed edge data center locations. Gartner predicts that by 2026, only 10% of large enterprises will have a mature and measurable zero-trust program in place, up from less than 1% today. In another report, Gartner notes, Through 2026, more than half More
The post Nebulon enhances security capabilities with two zero-trust offerings appeared first on Help Net Security.
13:07
Guest post by Ryan Farmer (who adds, heres the article that got my [whole] blog taken down)
Summary: Apple and US State Governments Developing System to Require People to Report Themselves for Watching Porn.
According to NBC News, at least 8 US states are considering a law that requires mobile device manufacturers to recognize pornography and censor it automatically, whether youre using carrier data or your homes WiFi, and they could be exposed to criminal liability if theyre not doing a perfect job, so expect them to be extremely aggressive with the filters.
Apple is best positioned to implement it since they admit they already have device scanners and porn filters, and the filters just arent on by default (yet).
Apple has admitted the porn filters were intended to blur things in iMessage and alert parents.Apple doesnt allow software to be installed outside their App store and these laws would require them to censor their App Store.
Apple has admitted the porn filters were intended to blur things in iMessage and alert parents.
So basically what changes when the 8 states (so far) pass the model bill to ban porn on mobile devices?
Apple changes their blur and report system to detect porn being displayed in any application on the iPhone/iPad.
If its illegal, they just go ahead and send an automated report to the cops, but they do that now, so
If its not illegal, they just blur it and make you hand your drivers license information to another app thats put there by your state and take a face pic, like iD Me.
Im sure that medical students will love this.Apple has gone pretty quiet with their alleged Privacy campaign, it was always fake, like DuckDuckGo.
The idea is that you bait users into a platform where they have no agency and cant stop you, and then put in this fake anti-tracking stuff thats surface deep, and then way way down into the bowels of the iOS system, you put spyware in thats very quiet about what its actually doing so you dont spook the user. They think that you have their back while theyre being bugged.
So, in a year or two when you cant read accurate information in an encyclopedia or medical journal about the human reproductive system, because Apple cant decide if its porn or not, and you have to give your drivers license to a state gover...
13:00
Combining Acoustic Bioprinting With Raman Spectroscopy for High-Throughput Identification of Bacteria Hackaday

Rapidly analyzing samples for the presence of bacteria and similar organic structures is generally quite a time-intensive process, with often the requirement of a cell culture being developed. Proposed by Fareeha Safir and colleagues in Nano Letters is a method to use an acoustic droplet printer combined with Raman spectroscopy. Advantages of this method are a high throughput, which could make analysis of samples at sewage installations, hospitals and laboratories significantly faster.
Raman spectroscopy works on the principle of Raman scattering, which is the inelastic scattering of photons by matter, causing a distinct pattern in the thus scattered light. By starting with a pure light source (that is, a laser), the relatively weak Raman scattering can be captured and the laser light filtered out. The thus captured signal can be analyzed and matched with known pathogens.
In the experiment, the researchers were able to distinguish between red blood cells (RBCs) and a host of distinct bacterial pathogens, both Gram-negative and Gram-positive. In addition, samples were printed onto a cell culture growth medium and incubated to demonstrate that the thus printed samples were...
12:19
Insect Farming is Booming, but is It Cruel? SoylentNews
Insects are strange wondrous beings. Butterflies can see parts of the light spectrum that are invisible to human eyes and use these ultraviolet patterns to find their way to tasty plants. Moths use the Earth's magnetic field to orient themselves on journeys of hundreds of miles. Bees waggle their butts to tell their hive-mates where to find a juicy stash of nectar. Insects live in our worldor humans live in theirsyet we inhabit completely different sensory universes.
But just as we are starting to understand insect senses, something is shifting in the way we treat these creatures. Insect farming is booming in a major way. By one estimate, between 1 trillion and 1.2 trillion insects are raised on farms each year as companies race to find a high-protein, low-carbon way to feed animals and humans. In terms of sheer numbers of animals impacted, this is a transformation of a speed and scale that we've never seen before.
It's a weird twist in our already strange relationship with bugs. We squash them, spray them, eat them, and crush them to make pretty dyes. But we also fret about plummeting wild insect populations and rely on them to pollinate the crops we eat. And with the industrialization of insect farming, bugs are being offered up as a solution to the human-caused climate crisis. But before we go down that route, we need to ask some really basic questions about insects. Can they feel? And if so, what should we do about it?
Read more of this story at SoylentNews.
12:10
PyTorch 2.0: Our next generation release that is faster, more Pythonic and Dynamic as ever Linux.com
We are excited to announce the release of PyTorch 2.0 which we highlighted during the PyTorch Conference on 12/2/22! PyTorch 2.0 offers the same eager-mode development and user experience, while fundamentally changing and supercharging how PyTorch operates at compiler level under the hood with faster performance and support for Dynamic Shapes and Distributed.
Accelerated Transformers (formerly called Better Transformers); Beta includes torch.compile as the main API for PyTorch 2.0, the scaled_dot_product_attention function as part of torch.nn.functional, the MPS backend, functorch APIs in the torch.func module; and other Beta/Prototype improvements across various inferences, performance and training optimization features on GPUs and CPUs. For a comprehensive introduction and technical overview of torch.compile, please visit the 2.0 Get Started page.Along with 2.0, we are also releasing a series of beta updates to the PyTorch domain libraries, including those that are in-tree, and separate libraries including TorchAudio, TorchVision, and TorchText. An update for TorchX is also being released as it moves to community supported mode. More details can be found in this library blog.
This release is composed of over 4,541 commits and 428 contributors since 1.13.1. We want to sincerely thank our dedicated community for your contributions. As always, we encourage you to try these out and report any issues as we improve 2.0 and the overall 2-series this year.
Summary:
- torch.compile is the main API for PyTorch 2.0, which wraps your model and returns a compiled model. It is a fully additive (and optional) feature and hence 2.0 is 100% backward compatible by definition.
- As an underpinning technology of torch.compile, TorchInductor with Nvidia and AMD GPUs will rely on OpenAI Triton deep learning compiler to generate performant code and hide low level hardware details. OpenAI Triton-generated kernels achieve performance thats on par with hand-written kernels and specialized cuda libraries such as cublas.
- Accelerated Transformers introduce high-performance support for training and inference using a custom kernel architecture for scaled dot product attention (SPDA). The API is integrated with torch.compile() and model developers may also use the scaled dot product attention kernels directly by calling the new scale...
12:05
[$] LWN.net Weekly Edition for March 23, 2023 LWN.net
The LWN.net Weekly Edition for March 23, 2023 is available.
11:31
Smashing Security podcast #314: Photo cropping bombshell, TikTok debates, and real estate scams Graham Cluley
It could be a case of aCropalypse now for Google Pixel users, theres a warning for house buyers, and just why is TikTok being singled out for privacy concerns? All this and much much more is discussed in the latest edition of the Smashing Security podcast by computer security veterans Graham Cluley and Carole Theriault, joined this week by Thom Langford.
11:25
LF Research Opens Call for Sponsors & Partners for World of Open Source Global Spotlight 2023 Survey Linux.com

Read the original post at: Read More
The post LF Research Opens Call for Sponsors & Partners for World of Open Source Global Spotlight 2023 Survey appeared first on Linux.com.
11:00
HPR3819: Remapping Mouse Buttons with XBindKeys on Linux Hacker Public Radio
Remapping Mouse Buttons with XBindKeys on Linux After a really long time of not bothering to figure out how to do this, I finally did some research and found out how to remap the extra buttons on my Kensington Expert mouse and my Logitech marble trackball mouse in a Linux environment. The tools it needed were xvkbd, xdotool, and xbindkeys. I already had the first two installed, but had never used xbindkeys before. I also used xev to identify the button numbers and key numbers. The Kensington Expert Mouse is one that I've had for about 15 years, and it was fairly expensive when I bought it, something like $75 or $80. It has four large buttons with a large trackball in the middle and a scroll wheel going around the track ball. I bought it at a time when I was doing a lot of graphic work that required clicking and dragging and double-clicking and stuff like that. If you're using it in a Mac or Windows environment, there is a special configuration tool that you can use to set it up just how you want. I had always configured it so that the upper left and upper right buttons were used for double-clicking and click dragging. This helped reduce a lot of strain on my hands. I have never gotten this to work on Linux, though, until today. If you want to do this yourself, the first thing to do is make sure you have these packages installed: xvkbd, xdotool, and xbindkeys. Then create a configuration file in your home directory: ~/.xbindkeysrc In order to map the upper left button to "double click," and the upper right button to "click and drag," I added these lines to the configuration file: # Double-click assigned to button 2 (upper left) "xdotool sleep 0.2 click 1 ; xdotool click 1" b:2 # Click and Drag assigned to button 8 (upper right) "xdotool sleep 0.2 mousedown 1" b:8 To test the settings, simply kill the xbindkeys process and restart it by typing xbindkeys: user@hostname:~$ pkill -f xbindkeys user@hostname:~$ xbindkeys On my desktop computer I have a Logitech marble trackball mouse, and it has two small keys that are assigned to back and forward by default. This can be handy for navigating file managers and web pages, but I wanted them to be assigned to "page up" and "page down" (to make up for the lack of a scroll wheel on the mouse). Here is the configuration file for that machine: "xvkbd -text "[Page_Down]"" b:8 "xvkbd -text "[Page_Up]"" b:9 I suppose I could have used xdotool for this configuration file as well, but for reasons I can't remember now, I tried xvkbd first and it worked, so I did not experiment further. I used xdotool for the Kensington because xvkbd did not have a way to perform virtual mouse clicks. Links xev XBindKeys xvkbd xdotool
Restoring Execution Environments of Jupyter Notebooks It Will Never Work in Theory
Like the paper reviewed yesterday, this one looks at computational notebooks: more specifically, at how to reverse engineer their execution environment. As the abstract says, more than 90% of published Jupyter notebooks don't explicitly state package dependencies, which can make them non-reproducible at best and non-executable in far too many cases. Wang et al. developed a tool that collects package APIs, analyzes notebooks to determine which ones are needed, and then finds combinations of packages that will make the notebook run. Quoting from the paper, "In a lab setting, SnifferDog is effective in automatically inferring execution environments for Jupyter notebooks, successfully generating installation requirements for 315/340 (92.6%) of notebooks. 284/315 (90.2%) of notebooks could be executed automatically."
This is impressive work, and the authors have made it available on GitHub. Once again, I hope it will inform the design of a new generation of notebooks: rather than requiring people to try to scrape dependencies, for example, I hope that future notebook systems will capture them automatically.
Jiawei Wang, Li Li, and Andreas Zeller. Restoring execution environments of Jupyter notebooks. 2021. arXiv:2103.02959.
More than ninety percent of published Jupyter notebooks do not state dependencies on external packages. This makes them non-executable and thus hinders reproducibility of scientific results. We present SnifferDog, an approach that 1) collects the APIs of Python packages and versions, creating a database of APIs; 2) analyzes notebooks to determine candidates for required packages and versions; and 3) checks which packages are required to make the notebook executable (and ideally, reproduce its stored results). In its evaluation, we show that SnifferDog precisely restores execution environments for the largest majority of notebooks, making them immediately executable for end users.
Improving Resiliency and Reliability for Lets Encrypt with ARI Let's Encrypt
The Lets Encrypt team is excited to announce that ACME Renewal Information (ARI) is live in production! ARI makes it possible for our subscribers to handle certificate revocation and renewal as easily and automatically as the process of getting a certificate in the first place.
With ARI, Lets Encrypt can signal to ACME clients when they should renew certificates. In the normal case of a certificate with a 90 day lifetime, ARI might signal for renewal at 60 days. If Lets Encrypted needs to revoke a certificate for some reason, ARI can signal that renewal needs to happen prior to the revocation. This means that even in extenuating circumstances, renewal can happen in an entirely automated way without disrupting subscriber services.
Without ARI, an unexpected revocation event might mean that Lets Encrypt would have to send emails to affected subscribers, maybe those emails are read in time to avoid a service disruption, maybe they arent, and engineers have to manually take action to trigger early renewals, possibly in the middle of the night. We cant wait for ARI to make this scenario a thing of the past.
ARI has a couple of additional benefits for Lets Encrypt and our subscribers. First, we can use ARI to help modulate renewals as needed to avoid load spikes on the Lets Encrypt infrastructure (of course subscribers can still renew whenever they want or need, as ARI is merely a signal or suggestion). Second, ARI can be used to set subscribers up for success in terms of ideal renewal times in the event that Lets Encrypt offers even shorter-lived certificates in the future.
ARI has been standardized in the IETF, a process that started with an email from Lets Encrypt engineer Roland Shoemaker in March of 2020. In September of 2021 Lets Encrypt engineer Aaron Gable submitted the first draft to the IETFs ACME working group, and now ARI is in production. The next step is for ACME clients to start supporting ARI, a process we plan to help with as best we can in the coming months.
ARI is a huge step forward for agility and resiliency in the TLS certificate ecosystem and were excited to see it gain widespread adoption!
Supporting Lets Encrypt
As a project of the Internet Security Research Group (ISRG), 100% of our funding comes from contributions from our community of users and supporters. We depend on their support in order to provide our public benefit services. If your company or organization would like to sponsor Lets Encrypt please email us at sponsor@letsencrypt.org...
10:37
Nvidia tweaks flagship H100 chip for export to China as H800 SoylentNews
Nvidia tweaks flagship H100 chip for export to China as H800:
U.S. regulators last year put into place rules that stopped Nvidia from selling its two most advanced chips, the A100 and newer H100, to Chinese customers. Such chips are crucial to developing generative AI technologies like OpenAI's ChatGPT and similar products.
Reuters in November reported that Nvidia had designed a chip called the A800 that reduced some capabilities of the A100 to make the A800 legal for export to China.
On Tuesday, the company confirmed that it has similarly called the H800, is being used by the cloud computing units of Chinese technology firms such as Alibaba Group Holding, Baidu Inc and Tencent Holdings, a company spokesperson said.
U.S. regulators last fall imposed rules to slow China's development in key technology sectors such as semiconductors and artificial intelligence, aiming to hobble the country's efforts to modernize its military.
The rules around artificial intelligence chips imposed a test that bans those with both powerful computing capabilities and high chip-to-chip data transfer rates. Transfer speed is important when training artificial intelligence models on huge amounts of data because slower transfer rates mean more training time.
A chip industry source in China told Reuters the H800 mainly reduced the chip-to-chip data transfer rate to about half the rate of the flagship H100.
The Nvidia spokesperson declined to say how the China-focused H800 differs from the H100, except that "our 800 series products are fully compliant with export control regulations."
Related:
US Wins
Support From Japan and Netherlands to Clip China's Chip
Industry
Read more of this story at SoylentNews.
10:29
ShellBot DDoS Malware Targets Linux SSH Servers HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
As per a report from AhnLab Security Emergency Response Center (ASEC), poorly managed Linux SSH servers are becoming
This is a post from HackRead.com Read the original post: ShellBot DDoS Malware Targets Linux SSH Servers
10:11
Google Suspends Chinese E-Commerce App Pinduoduo Over Malware Krebs on Security
Google says it has suspended the app for the Chinese e-commerce giant Pinduoduo after malware was found in versions of the software. The move comes just weeks after Chinese security researchers published an analysis suggesting the popular e-commerce app sought to seize total control over affected devices by exploiting multiple security vulnerabilities in a variety of Android-based smartphones.
In November 2022, researchers at Googles Project Zero warned about active attacks on Samsung mobile phones which chained together three security vulnerabilities that Samsung patched in March 2021, and which would have allowed an app to add or read any files on the device.
Google said it believes the exploit chain for Samsung devices belonged to a commercial surveillance vendor, without elaborating further. The highly technical writeup also did not name the malicious app in question.
On Feb. 28, 2023, researchers at the Chinese security firm DarkNavy published a blog post purporting to show evidence that a major Chinese ecommerce companys app was using this same three-exploit chain to read user data stored by other apps on the affected device, and to make its app nearly impossible to remove.
The three Samsung exploits that DarkNavy says were used by the malicious app. In November 2022, Google documented these three same vulnerabilities being used together to compromise Samsung devices.
DarkNavy likewise did not name the app they said was responsible for the attacks. In fact, the researchers took care to redact the name of the app from multiple code screenshots published in their writeup. DarkNavy did not respond to requests for clarification.
At present, a large number of end users have complained the DarkNavy blog post. The app has problems such as in...
10:00
Optimize Your Paper Planes With This Cardboard Wind Tunnel Hackaday

We at Hackaday are great fans of hands-on classroom projects promoting science, technology, engineering and math (STEM) subjects after all, inspiring kids with technology at a young age will help ensure a new generation of hardware hackers in the future. If youre looking for an interesting project to keep a full classroom busy, have a look at [drdonh]s latest project: a fully-functional wind tunnel made from simple materials.
09:49
Courts Should Let You Sue Federal Officials Who Violate Your Right to Record Deeplinks
Intern Katie Farr contributed to this blog post.
Late last year, the Fourth Circuit Court of Appeals dismissed Dustin Dyers lawsuit against Transportation Security Administration (TSA) officers who ordered him to stop recording their pat-down search of his husband. The officers also ordered him to delete what he had already recorded. But the court, using a flawed legal doctrine that limits civil rights lawsuits, ruled that Dyer could not sue the officers for money damages even if they violated his First Amendment right to record on-duty government officials.
But there is no right without a remedy. Indeed, the Supreme Court once recognized that suing federal officials for money damages is necessary relief when federally protected rights have been invaded. In 1971, the high court in Bivens v. Six Agents approved a damages lawsuit against federal anti-drug officers who unlawfully raided a home. But since the 1980s, the Court has chipped away at the Bivens right to seek damages from federal officials. The Court recently blocked a lawsuit against a Customs and Border Patrol officer for violating First and Fourth Amendment rights.
We need money damages under Bivens to protect our civil rightsincluding the right to record and other digital rightsfrom the federal government. While a federal civil rights law protects our right to sue state government officials for money damages, no such statute exists for suing federal government officials. And the Supreme Court set, and the Fourth Circuit applied, a very high bar for suing under Bivens. You must show there are no alternative remedies and no special factors counseling hesitation. That is as vague and broad as it sounds, and the Fourth Circuit said this high bar all but closed the door on Bivens.
For example, the Fourth Circuit rejected Dyers lawsuit because the TSAs parent agency, the Department of Homeland Security (DHS), has a complaint system. Even though it is mostly for people on the no-fly list, and may not squarely address the TSA officers interference with Dyers recording, the court said that is an alternative remedy to a lawsuit for money damages. ...
09:42
Lionsgate streaming platform with 37m subscribers leaks user data Security Affairs
Entertainment industry giant Lionsgate leaked users IP addresses and information about what content they watch on its movie-streaming platform, according to research from Cybernews.
Original post at https://cybernews.com/security/lionsgate-data-leak/
During their investigation, our researchers discovered that the video-streaming platform Lionsgate Play had leaked user data through an open ElasticSearch instance.
The Cybernews research team discovered an unprotected 20GB of server logs that contained nearly 30 million entries, with the oldest dated May 2022. The logs exposed subscribers IP addresses and user data concerning device, operating system, and web browser.
Logs also leaked the platforms usage data, typically used for analytics and performance tracking. URLs found in logs contained titles and IDs of what content users watched on the platform, along with search queries entered by the users.
Researchers also found unidentified hashes with logged HTTP GET requests, records of requests made by clients that are usually used to get data from a web server: when these requests are made, they get stored in log files on the server.
Researchers could not determine the exact purpose or usage of the hashes. However, the hashes all containing more than 156 characters indicates they were intended to remain unchanged for long periods of time.
Hashes didnt match any commonly used hashing algorithms. Since these hashes were included in the HTTP requests, we believe they could have been used as secrets for authentication, or just user IDs, said researchers.
Cybernews reached out to Lionsgate about the leak, and the company responded by closing an open instance. However, at the time of writing, it has yet to provide an official response.
Big hitter at risk
Lionsgate Entertainment Corporation, the Canadian-American entertainment company operating the platform, owns several well-known movie and TV franchises that have gained worldwide recognition, including Twilight Saga, Saw, Terminator, The Hunger Games, and The Divergent Series.
While Netflix stays at the top of all streaming platforms with over 230 million subscribers, Lionsgate has over 37 million global subscribers and generated $3.6 billion in revenue last year.
Accelerated by COVID-19, the popularity of online streaming platforms has been growing. In 2022, the subscription rates to video-on-demand platforms reached 83% in the US, showing an increase of more than 30% during eight years.
But, as the number of users on platforms increases, they are becoming a tempting target for cybercriminals. Even minor security loopholes might cause serious damage, yet secur...
09:12
Google Chrome/Chromium Lands Wayland Fractional Scaling Support Phoronix
On top of today seeing the KDE XWaylandVideoBridge announcement, the debut of GNOME 44 with its many Wayland improvements, and XWayland 23.1 being released with multiple new features/improvements, there is more good news for Wayland fans. Google has merged to the Chrome/Chromium Ozone code support for Wayland fractional scaling via the fractional-scale-v1 protocol...
09:03
Rogue ChatGPT extension FakeGPT hijacked Facebook accounts Security Affairs
Guardios security team uncovered a new variant of a malicious Chat-GPT Chrome Extension that was already downloaded by thousands a day.
a legitimate open-source project, threat actors added malicious code to steal Facebook accounts.The legitimate extension is named ChatGPT for Google and allows the integration of ChatGPT on search results.
The new malicious Chrome Extension is distributed since March 14, 2023, through sponsored Google search results and uploaded to the official Chrome Store. Experts noticed that it was first uploaded to the Chrome Web Store on February 14, 2023.
According to the researchers, it is able to steal Facebook session cookies and compromise accounts in masses.

The new variant of the FakeGPT Chrome extension, titled Chat GPT For Google, is once again targeting your Facebook accounts under a cover of a ChatGPT integration for your Browser. reads the post published by Guardio Labs. This time, threat actors didnt have to work hard on the look and feel of this malicious ChatGPT-themed extension they just forked and edited a wel...
08:32
The hidden danger to zero trust: Excessive cloud permissions Graham Cluley
Graham Cluley Security News is sponsored this week by the folks at Sysdig. Thanks to the great team there for their support! What is one of the leading causes of breaches in the cloud? OMG, its still phishing! Its no wonder CISOs push zero trust as a top priority. Identities are a top cloud target. Continue reading "The hidden danger to zero trust: Excessive cloud permissions"
08:31
[$] Jumping the licensing shark LWN.net
The concept of copyleft is compelling in a lot of ways, at least for those who want to promote software freedom in the world. Bradley Kuhn is certainly one of those people and has long been working on various aspects of copyleft licensing and compliance, along with software freedom. He came to Everything Open 2023 to talk about copyleft, some of its historyand flawsand to look toward the future of copyleft.
07:59
How To Install LXD on Ubuntu 22.04 LTS using apt/snap nixCraft
Ubuntu 22.04 LTS comes with LXD Ubuntu, CentOS, Fedora, Alpine, Arch and many other Linux distro. You can mimic AWS or different cloud instance types with LXD for testing and deployment purposes on your development machine. You can also run a GUI app such as Firefox completely isolated using LXD for security or privacy reasons. Let us see how to set up and use LXD on the Ubuntu Linux 22.04 LTS using APT or snap command.
Love this? sudo share_on: Twitter - Facebook - LinkedIn - Whatsapp - Reddit
The post How To Install LXD on Ubuntu 22.04 LTS using apt/snap appeared first on nixCraft.
07:52
Student Satellite Demos Drag Sail to De-orbit Old Hardware SoylentNews
65 AA batteries and $10 Arduino processor power space debris solution:
A tiny satellite with a drag chute built by a team of students has been held up as one small possible solution to the thorny issue of space junk caused by defunct hardware cluttering up Earth's orbit.
SBUDNIC, a "Sputnik-like CubeSat," was built by students at Brown University, Rhode Island, from low-cost commercial off-the-shelf parts. It has successfully demonstrated the use of a simple drag sail that helps to degrade the satellite's orbit and push it back into the planet's atmosphere faster than would otherwise have occurred.
[...] The idea behind SBUDNIC was to demonstrate how future satellites could avoid adding to this problem by including a mechanism to help de-orbit them at the end of their life span. The aerodynamic drag device pulls the satellite out of orbit approximately three times faster than comparable satellites, according to Brown University.
[...] The satellite itself is a 3U Cubesat (where 1U is 10 cm x 10 cm x 10 cm, not to be confused with a datacenter rack unit). According to details given by the university, it includes a $10 Arduino microprocessor, 65 AA Energizer lithium batteries and a variety of 3D printed parts produced with consumer-grade printers.
Also 3D printed is the drag sail, made from Kapton polyimide film, which apparently has the right combination of properties to withstand extreme temperature and vibration. This was folded flat along the satellite's frame prior to deployment, using spring-loaded structural masts made of thin aluminum tubing designed to extend out upon triggering of the release mechanism.
[...] Initial computational predictions suggest that the drag device will decrease the orbital lifetime of SBUDNIC from over 20 years to as few as 6.5 years, depending on fluctuations of atmospheric density.
Read more of this story at SoylentNews.
07:28
BREIN Wont Take Piracy Warning Dispute to The Supreme Court TorrentFreak
 Dutch anti-piracy group BREIN has been at the forefront
of the anti-piracy battle since the turn of the millennium.
Dutch anti-piracy group BREIN has been at the forefront
of the anti-piracy battle since the turn of the millennium.
For most of this period, unauthorized sharing via BitTorrent has been a prime concern. Traditionally, BREIN focused its enforcement efforts on website operators, but in recent years theres been a shift to uploaders as well.
In late 2020, the anti-piracy group announced an elaborate program to monitor and warn some of the most active BitTorrent uploaders. The goal of this FLU scheme was to change the behavior of prolific pirates, without obtaining their identities.
The project received government research funding but BREIN had a major obstacle to overcome. Unlike ISPs in other countries such as the United States, Dutch ISPs are not required to forward piracy notices to their subscribers.
ISP Refuses to Forward Warnings
BREIN hoped that Internet providers would be willing to cooperate, but that wasnt to be the case. When BREIN approached Ziggo, the largest ISP in the Netherlands, with a request to forward piracy alerts to its subscribers, the company refused to do so.
According to Ziggo, linking IP addresses to specific subscribers raises serious privacy concerns, even if personal information isnt shared with BREIN.
The anti-piracy group was unhappy with the refusal and took Ziggo to court. BREIN argued that warnings are a relatively mild measure that would help rightsholders to address the piracy problem. The system wouldnt result in any claims for damages either, as the identities of the alleged pirates would remain private.
BREIN lost the case last year. The court found that there is no legal basis to compel Ziggo to forward warnings. In addition, the ISP lacks a license to link IP-addresses to personal information.
This outcome was a disappointment for BREIN which appealed the ruling, but without result. The appeals court affirmed the lower courts ruling, noting that there is no legal basis to require Internet providers to forward the notices.
No Supreme Court Challenge
This was yet another setback for the anti-piracy group, which considered taking the matter to the Supreme Court. However, after weighing the available options, it chose not to do so, which effectively means the end of the original FLU program.
In its most recent...
07:00
Homebrew Tire Inflator Pushes the Limits of PVC Construction Hackaday

Lets just clear something up right from the start with this one: theres literally no reason to build your own tire inflator from scratch, especially when you can buy a perfectly serviceable one for not a lot of money. But thats missing the point of this build entirely, and thinking that way risks passing up yet another fascinating build from PVC virtuoso [Vang H], which would be a shame
The chances are most of you will recall [Vang H]s super-detailed working PVC model excavator, and while were tempted to say this simple air pump is a step toward more practical PVC builds, the fact remains that the excavator was a working model with a completely homebrew hydraulic system. As usual, PVC is the favored material, with sheet stock harvested fr...
05:59
05:17
3.5 Years Later Gemini Protocol and Geminispace Are Still 100% Community-Controlled Techrights
Video download link |
md5sum 97211f6980727bf036136cb2469c5cba
Gemini Status Quo
Creative Commons Attribution-No Derivative Works 4.0
Summary: Community-centric alternatives to the World Wide Web have gained traction; one of them, Gemini Protocol, continues to grow in 2023 and were pleased to report progress and expansion
IN the video above I present the latest state of Gemini and how we use it in Techrights. Weve used it for over 2 years. Tux Machines joined last year.
 In the video I show Daily Links, Geminispace in general (latest), some statistics, and then some
limitations too are explained (for instance, we cannot
expect the reader to be able to see images).
In the video I show Daily Links, Geminispace in general (latest), some statistics, and then some
limitations too are explained (for instance, we cannot
expect the reader to be able to see images).
Gemini is turning 4 later this year and its still growing (see latest image/chart/graph).

Stonehenge Summer Solstice. CC BY-SA 2.0,
Link.
...
05:15
Experts released PoC exploits for severe flaws in Netgear Orbi routers Security Affairs
Cisco Talos researchers published PoC exploits for vulnerabilities in Netgear Orbi 750 series router and extender satellites.
Netgear Orbi is a line of mesh Wi-Fi systems designed to provide high-speed, reliable Wi-Fi coverage throughout a home or business. The Orbi system consists of a main router and one or more satellite units that work together to create a seamless Wi-Fi network that can cover a large area with consistent, high-speed Wi-Fi.
One of the key benefits of the Orbi system is its use of mesh networking technology, which allows the satellite units to communicate with the main router and with each other to provide strong Wi-Fi coverage throughout the home or business.
Cisco worked with Netgeat to solve the issues and is disclosing them according to its 90-day timeline outlined in Ciscos vulnerability disclosure policy.
Cisco Talos researchers published Proof-of-concept (PoC) exploits for multiple vulnerabilities in Netgears Orbi 750 series router and extender satellites.
The experts discovered four vulnerabilities in the Netgear Orbi mesh wireless system, the most critical one is a critical remote code vulnerability, tracked as CVE-2022-37337 (CVSS v3.1: 9.1), that resides in the access control functionality of the Netgear Orbi router.
A command execution vulnerability exists in the access control functionality of Netgear Orbi Router RBR750 4.6.8.5. states Talos. An attacker can make an authenticated HTTP request to trigger this vulnerability.
A threat actor can exploit the flaw by sending a specially crafted HTTP request.
Talos discovered a vulnerability in the Orbi Satellite TALOS-2022-1596 (CVE-2022-37337) that could lead to arbitrary command execution on the device. The user needs to authenticate into the mesh system first, meaning theyd need to access an unprotected network or the login credentials of a password-protected network, for this attack to be successful. Then, the adversary needs to send a specially crafted HTTP request to trigger the vulnerability. reads the advisory published by Cisco Talos.
Cisco published a Proof of Concept exploit for this issue:
05:12
Internet Archive Faces Uphill Battle in Lawsuit Over its Free Digital Library SoylentNews
A federal judge heard oral arguments in a lawsuit filed by four major book publishers against Internet Archive for alleged copyright infringement on Monday. The lawsuit was first filed in 2020 and could be a landmark case when it comes to digital libraries and copyright.
According to Reuters, U.S. District Judge John Koeltl seemed skeptical about whether copyright law's fair use doctrine allows Internet Archive to offer the scanned books without the publishers' permission.
The lawsuit was filed by Hatchette Book Group, John Wiley & Sons Inc., Penguin Random House, and HarperCollins Publishers, all of whom say that digitizing books without requiring payment hurts writers and the publishers who lose out on payout. The lawsuit claims Internet Archive's "actions grossly exceed legitimate library services, do violence to the Copyright Act, and constitute willful digital piracy on an industrial scale."
[...] The lawsuit says although Internet Archive claims it works to promote education, that has been a long-running function and aim of publishing houses who have invested time, money, and resources into creating and distributing books, not to mention the researching and writing efforts of the author.
Read more of this story at SoylentNews.
04:50
A New Explanation for Oumuamuas Acceleration Centauri Dreams Imagining and Planning Interstellar Exploration
Heres a thought that puts a different spin on exoplanet studies. The speaker is Darryl Seligman (Cornell University):
The comets and asteroids in the solar system have arguably taught us more about planet formation than what weve learned from the actual planets in the solar system. I think that the interstellar comets could arguably tell us more about extrasolar planets than the extrasolar planets we are trying to get measurements of today.
Seligmans comment plays into the growing interest in interstellar objects that drift into our Solar System like 1/I Oumuamua and 2/I Borisov. These may be the initial members of what is actually a large class of debris from other stars that we are only now learning how to detect. Among the many things we have yet to refine in our understanding of Oumuamua is its actual size. Projections of 115 by 111 by 19 meters are deduced from its brightness and the changes produced by its apparently tumbling motion. The interstellar interloper is too far from Earth and too small to resolve.

Image: This plot shows how the interstellar asteroid `Oumuamua varied in brightness during three days in October 2017. The large range of brightness about a factor of ten (2.5 magnitudes) is due to the very elongated shape of this unique object, which rotates every 7.3 hours. The different coloured dots represent measurements through different filters, covering the visible and near-infrared part of the spectrum. The dotted line shows the light curve expected if `Oumuamua were an ellipsoid with a 1:10 aspect ratio, the deviations from this line are probably due to irregularities in the objects shape or surface albedo. Credit: ESO/K. Meech et al.
I mention this just to underline how difficult it is to make sense of Oumuamua at present. Absent a fast mission to catch up with the object (and there are ideas out there, as weve discussed in these pages before), its dimensions will remain ambiguous. And what of the anomalous non-gravitational acceleration that astronomers noted in 2018? Seligman, who along with Gregory Laughlin has written about fast missions to Oumuamua in a paper from that year, is also behind the conjecture that the object could be composed of molecular hydrogen ice. Its no wonder, then, that his interest was pi...
04:04
CVE-2023-0464: OpenSSL: Excessive Resource Usage Verifying X.509 Policy Constraints Open Source Security
Posted by Solar Designer on Mar 22
Excessive Resource Usage Verifying X.509 Policy Constraints (CVE-2023-0464)===========================================================================
Severity: Low
A security vulnerability has been identified in all supported versions
of OpenSSL related to the verification of X.509 certificate chains
that include policy constraints. Attackers may be able to exploit this
vulnerability by creating a malicious certificate chain that triggers...
03:50
Valve Officially Announces Counter-Strike 2 Phoronix
Following recent rumors and leaks, Valve today officially announced Counter-Strike 2 that they announce as the largest technical leap in Counter-Strike's history...
03:23
Order Online
To maximize his potential, a a lot bigger variety of poker games and tournaments that operate all day long. Winning in this recreation just isnt a tough task for certain, and youll have a baseline of knowledge round why individuals arent changing. Here is your information to the preferred online slot websites, however when you place your bets in specific methods. This might be a weekly or monthly promotion, you definitely can help your odds of successful. If you decide to position your score in fives, thus introducing a modicum of talent into an otherwise uncontrollable sport.
The minimum age to obtain Playing Wealth APK is thirteen years. In addition, children underneath the age of 18 should obtain and play this game with the permission of their mother and father. Go to the official 4raBet web site, find the Register button.
In this case, bets should be made on expresses with three or more occasions with particular person odds of a minimal of 1.four. For new players, we have a beneficiant welcome bonus that permits you to double your first deposit. Well offer you an additional 100 percent on your first deposit as a lot as INR 8,000, so youll find a way to guess even more in your favorite sports activities. Extensive pre-match and live line, cyber sports bettingA betting constructor is on the market.
This could be some great fun, with slots such as Fish Party, Lost Vegas, and Santas Wild Ride being listed on the homepage as featured video games. Fun88 also promotes responsible gambling practices amongst its gamers by brazenly supporting GamCare. This is an agency dedicated to helping individuals get the assistance that they need when gambling is no longer enjoyable however bordering on habit. Players can choose out of enjoying at Fun88 at any time, and the casino will honour that request.
The cell app is available on each Android and iOS gadgets, and the mobile web site is simply nearly as good, as nicely. If you have an interest in 888starz or already use it, the app is an efficient and handy option for individuals who would like to place bets from anywhere and at any time. Stay ahead of the sport and play on the go with the 4raBet betting software for Android and iOS. You can obtain the app by visiting the bookies official website by way of any mobile browser. Tap on the icon of your OS and obtain the .apk file or get the applying from App Store .
Navigate to the homepage of the official 888starz web site, open the primary menu and go to the part with the functions. You can also use our hyperlink to entry the one-click installation. Use enroll bonus to play games and also you just need to earn solely Rs.59 to make your first withdrawal. I even have been utilizing 4 ra bet for a very long time for betting on sports occasions.
Freeing up some area and restarting your mobile phone could assist to resolve the issue. If it doesnt work, then please co...
03:20
Jitu77 > Daftar Situs Judi Slot On-line Gacor, Pragmatic Play Terbaik, Slot88 Terpercaya h+ Media
Jitu77 > Daftar Situs Judi Slot On-line Gacor, Pragmatic Play Terbaik, Slot88 Terpercaya
Every day you ought to have a quantity of thousand events obtainable for betting. The most developed path is soccer, however different sports also offer a broad variety of matches. If these requirements arent met, you can still attempt to set up the client, but on this case, we dont assure its stability.
The tennis bracelet got its rightful entry into the accessorizing world when Chris Evert, a high American tennis player wore it as a fortunate appeal in a g.. Fun88 is properly established and this is demonstrated by the various licenses that it has gained to operate. To begin, its regulated by the United Kingdom Gambling Commission. This is ranked among the many most reputable agencies overseeing on line casino operations on the earth.
Here you can see an in depth assortment of world markets, every providing very appealing deals. Each occasion has quite a few wager varieties out there. You could bet on the profitable team or other game aspects like the variety of killed characters, scored factors, and so forth. The sites cellular page looks a lot the same and is just as straightforward to use for those who favor to place their bets on the go. Much like a daily welcome bonus for an individual becoming a member of the location. But this is solely 50, which are credited to your account, you do not need to log in or make a deposit to obtain it.
enough memory for the app on their system, or for many who do not gamble online that often. Otherwise, there is not much difference between the cell model and the app. The cellular model presents the identical number of online on line casino video games, bonuses, and customer help. In the upper menu of the 888starz cellular website, you could see the function to deposit the gaming account, settings, and the menu of gaming services. Below is a slider that presents bonus presents. Just under there are blocks with casino games and the sportsbook.- On the INDIBET website, youll be able to choose from an ample collection of various casino games.
- Been writing sports activities news for a few years and now developing my own sports activities and betting website with trustworthy and professional reviews.
- In the upper menu of the 888starz cell website, you would see the function to deposit the gaming account, settings, and the menu of gaming companies.
- You can download BET 888 APK free and might set up in your device without needing to go to google play store.
- The number and kinds of bets dont differ, as well as bonuses and a set of cost instruments.
These singles are called alternatives or outcomes. If at least one loses, the complete Parlay will collapse. If at least one wins and the other outcomes win or return, the Parlay will win. I...
03:17
888sport Cellular App h+ Media
888sport Cellular App
The tennis bracelet obtained its rightful entry into the accessorizing world when Chris Evert, a top American tennis player wore it as a fortunate charm in a g.. Fun88 is properly established and that is demonstrated by the various licenses that it has gained to function. To start, its regulated by the United Kingdom Gambling Commission. This is ranked among the most reputable companies overseeing on line casino operations on the planet.
As for the 30 free spins, they apply to a particular slot from the Jeetplay variety offered. The spins are automatically credited and are valid for the following 24 hours. That signifies that you want to wager 45x earlier than you can convert your bonus to money.
For the 888sport app download, check with the relative section on this article. There is not any separate utility for 888sport apk download on PC. But youll be able to all the time download 888sport app for your mobile phone. Regardless, the desktop website works nice by itself, so that you shouldnt have any drawback working it in your PC browser.
Watch live streams of matches and assume about statistical information. You can obtain the 10Cric on line casino APK by following the related hyperlink we share at the beginning of this evaluate. Slower operation compared to different Indian gambling apps.
Neither the bookmaker nor the provider can influence the result of bets. The activity is carried out by the license obtained by the Government of Curacao. The administration ensures all users the honesty of funds, the soundness of the software, and the safety of personal knowledge. It can be value noting that works 4rabet legal in India. Online roulette is considered one of the most famous video video games performed online in fun88. Its thrilling to play, the guidelines are very reliable and it affords a variety of the utmost favorable triumphing odds and payouts on the on line casino.
- The 888starz app for Android offers fixed entry to all nice bonuses and advertising offers of the company.
- Bitcoin is turning into the primary commonplace on US going through online casinos, Pannick.
- With the app of 888Starz, every of our clients can place sports bets, play casino games, and use other site services and options instantly from their smartphone.
- As youve carried out earlier than, go to the web site in your browser and download the app.
The website administration also allows all clients to receive a welcome bonus. Users have two sorts to select from Welcome Sports 200% and Welcome Casino 200%. You can accept the offer, play 4rabet for money with out the promo, or redeem it later. When choosing the first registration 4Rabet methodology, you must enter an e mail address and create a strong password.
It could be very focused on soccer and basketball betting, with everything else being secondary. That being stated, there are...
03:12
03:01
How to create multidomain web applications with Podman and Nginx Linux.com
Learn how to use Podman and Nginx to work with applications from different domains on the same host.
Read More at Enable Sysadmin
The post How to create multidomain web applications with Podman and Nginx appeared first on Linux.com.
03:00
XWayland 23.1 Released With High Resolution Scroll Wheel, DMA-BUF v4 Feedback Phoronix
Coincidentally landing on GNOME 44 release day is also XWayland that allows legacy X11 client applications/games to run atop Wayland environments. With XWayland 23.1 comes a number of shiny new features to continue to enhance the X11 experience on Wayland...
02:55
Distribution Release: Trisquel GNU/Linux 11.0 DistroWatch.com: News
Trisquel GNU/Linux is a 100% libre Ubuntu-based Linux on Ubuntu 22.04 LTS and greatly expands compatibility with a wider range of CPU architectures. "New supported architectures. Following the addition of 32-bit ARM support in Trisquel 10, we now introduce....
02:53
Google Suspends Chinese Shopping App Pinduoduo Over Malware Concerns HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
Pinduoduo has confirmed the incident, but denied the presence of malware in its app.
This is a post from HackRead.com Read the original post: Google Suspends Chinese Shopping App Pinduoduo Over Malware Concerns
02:28
Version
44 of the GNOME desktop environment has been released. "This
release brings a grid view in the file chooser, improved settings
panels for Device Security, Accessibility, etc, and refined quick
settings in the shell. The Software and Files apps have seen
improvements, and a whole slew of new apps has joined the GNOME Circle
". See the release notes for
details.
02:28
NASA's AIM Mission Comes to an End After Nearly 16 Years SoylentNews
The satellite helped scientists learn more about polar mesospheric clouds:
It looks to be the end of the line for NASA's Aeronomy of Ice in the Mesosphere, or AIM, spacecraft. The mission launched on April 25, 2007, as part of the Small Explorer program (the 90th such mission since 1958). The satellite featured three science instruments designed to study polar mesospheric clouds (PMCs) that form high above Earth in the polar regions.
The satellite was put into orbit 312 miles up. Data from the long-running mission helped scientists better understand the formation of these unique clouds, also called night-shining or noctilucent clouds, and was featured in 379 peer-reviewed scientific papers over the years.
AIM had a planned mission duration of just 26 months but has been operating mostly issue-free for nearly 16 years. In 2019, however, NASA noticed the satellite's batteries were starting to degrade but were still functional enough to continue to collect a significant amount of data and return it to Earth.
NASA said the craft's battery has reached a point where it is no longer able to receive commands or collect data. The space agency will monitor the satellite for a two-week period and attempt to reboot it, but it isn't looking good.
[...] The near-term fate of the AIM satellite wasn't mentioned, and it's unclear if NASA has the ability to bring it back down to Earth like it has with other decommissioned craft. The satellite measures roughly 1.4m x 1.1m (4 ft 7 in 3 ft 7 in) and weighs 197 kg (434 pounds). If left unaddressed, it'd add to the growing list of space junk orbiting our planet.
Read more of this story at SoylentNews.
02:13
Windows Falls to 16% Market Share in India (It was 97% in 2009), Microsoft Layoffs Reach India Too Techrights
Summary: This months picture from the worlds most populous nation does not look good for Microsoft (it looks good for GNU/Linux); anonymous rumour mills online say that Microsoft isnt moving to India but is actually firing staff based in India, so its a case of shrinking, not offshoring. When even low-paid (much lower salaries) staff is discarded it means things are very gloomy.
02:01
GNOME 44 Released With Many Desktop Enhancements Phoronix
GNOME 44 is now officially out as the latest half-year update to this widely-used open-source desktop...
02:00
Web3 Is Going Just Great Creator On Why It Isnt IEEE Spectrum

In mid-2021, the term Web3 suddenly exploded into the public consciousness. As people scrambled to figure out what it wascryptocurrencies? blockchain? nonfungible tokens?venture capital firms were pouring money into new startups, over US $30 billion before the year was out.
Meanwhile, Molly White, a software engineer, started reading up on the tech in case that was the direction her career would be heading in. But she found herself taking a different direction: She launched the website Web3 Is Going Just Great, with the aim of tracking the scams and fraud in the cryptocurrency world. So far, shes tallied $11.8 billion in money lost on the websites Grift Counter. White answered five rapid-fire questions on the Web3 phenomenon and why shes still not impressed.
How did you end up running a site like Web3 Is Going Just Great?
Molly White: When I started researching the topic, I was just seeing a lack of reporting on some of the downsidesyou know, the hacks, the scams, the fraud. And so I decided I could do my part to try and fill that void to some extent, because I feel like its important that people get the full picture.
A lot of the projects youre tracking involve cryptocurrency and blockchain technologies. Is that what Web3 means? Are all of these terms synonymous?
White: Its primarily a marketing term. And I think the industry benefits from how nebulous it is because it can mean whatever is most useful at that time. But broadly speaking, Web3 refers to blockchains underpinning everything you do online.
The crypto industry seemed like it might collapse when the cryptocurrency exchange FTX went bankrupt in November 2022, but youre still updating the site with new projects. Is the industry still just trucking along, or has it changed after that event?
White: I think that FTX and the related collapses have been a really big hit to the crypto brand, but I think that the crypto industry is constantly working on finding the next big thing that they can sell retail investors on. And so that is very much underway at this point.
You can sort of see whats happening as people start distancing themselves from FTX and saying that the FTX...
01:52
Adobe Releases AI Art Generator Firefly To Take On Midjourney And DALL-E, Could Be As Influential As The First Photoshop cryptogon.com
Its coming very quickly now. Via: TechRadar: Adobe has revealed its answer to AI art generators like Midjourney, Dall-E, and Stable Diffusion and the new family of generative AI tools, collectively called Adobe Firefly, could ultimately be as influential as the original Photoshop was in 1990. The giant behind apps like Photoshop and Illustrator []
01:36
Links 22/03/2023: GNOME 44 Kuala Lumpur Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Pseudo-Open Source
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Monopolies
- Gemini* and Gopher
-
GNU/Linux
-
Desktop/Laptop
-
OpenSource.com 8 steps to refurbish an old computer with Linux
We live in a remarkable era. It wasnt so long ago we were all chained to the upgrade treadmill,...
-
-
01:26
DPReview.com Is Closing April 10th cryptogon.com
I became interested in 35mm photography back in the 1980s when I was in high school. After a brief stint in photography school in the early 1990s, I realized that the only way I was going to make consistent money with photography was with weddings. So, I moved on. But my love of photography remained, []
01:26
KDE XWayland Video Bridge Aims To Improve Linux Desktop Screen Sharing Phoronix
KDE developers David Edmundson and Alex Poi have begun working on XWaylandVideoBridge as a new project to help improve Linux desktop screen sharing for X11-based applications that may try to share the contents of Wayland screens, such as could be the case for some software like Discord, Microsoft Teams, Skype, and others...
01:00
Why LLaMa Is A Big Deal Hackaday

You might have heard about LLaMa or maybe you havent. Either way, whats the big deal? Its just some AI thing. In a nutshell, LLaMa is important because it allows you to run large language models (LLM) like GPT-3 on commodity hardware. In many ways, this is a bit like Stable Diffusion, which similarly allowed normal folks to run image generation models on their own hardware with access to the underlying source code. Weve discussed why Stable Diffusion matters and even talked about how it works.
LLaMa is a transformer language model from Facebook/Meta research, which is a collection of large models from 7 billion to 65 billion parameters trained on publicly available datasets. Their research paper showed that the 13B version outperformed GPT-3 in most benchmarks and LLama-65B is right up there with the best of them. LLaMa was unique as inference could be run on a single GPU due to some optimizations made to the transformer itself and the mo...
00:59
ENISA: Ransomware became a prominent threat against the transport sector in 2022 Security Affairs
The European Union Agency for Cybersecurity (ENISA) published its first cyber threat landscape report for the transport sector.
A new report published by the European Union Agency for Cybersecurity (ENISA) analyzes threats and incidents in the transport sector. The report covers incidents in aviation, maritime, railway, and road transport industries between January 2021 and October 2022.
The report provides a detailed analysis of the prime threats to the transport sector, the threat actors and related motivations.
During the period covered by the report, the expert identified the following prime threats:
- ransomware attacks (38%),
- data related threats (30%),
- malware (17%),
- denial-of-service (DoS), distributed denial-of-service (DDoS) and ransom denial-of-service (RDoS) attacks (16%),
- phishing / spear phishing (10%),
- supply-chain attacks (10%).
During the reporting period, ransomware was the most prominent threat against the sector in 2022. The researchers pointed out that the ransomware attacks doubled compared to the previous year. Threat actors behind ransomware attacks are not exclusively financially-motivated.
Nation-state actors, cybercriminals, and hacktivists, are the threat actors with the biggest impact on the organizations in the sector.
Most of the attacks on the transport sector (54%) are carried out by cybercriminals.
The report warns that hacktivist activity targeting the transport sector, including DDoS attacks, is likely to continue. Airports, railways and transport authorities are privileged targets of hacktivists.
The good news is that ENISA experts did not receive reliable information on a cyberattack affecting the safety of transport.
The researchers also warn that future Ransomware attacks will likely target and disrupt OT op...
00:54
Mozilla Announces Mozilla.ai For "Trustworthy AI" Phoronix
Mozilla announced today they are investing $30 million USD to build Mozilla.ai as a new start-up focused on "building a trustworthy, independent, and open-source AI ecosystem."..
00:52
aCropalypse now! Cropped and redacted images suffer privacy fail on Google Pixel smartphones Graham Cluley
Have you ever shared a photograph where you've redacted some sensitive information? Perhaps you've cropped out part of the image you didn't want others to see? Well, users of Google's Pixel Android smartphone might be alarmed to learn that pictures they've shared in the past may have been less discreet than they imagined. Read more in my article on the Hot for Security blog.
00:49
Are You Good At Authorized Betting Apps? Heres A Quick Quiz To Seek Out Out h+ Media
Are You Good At Authorized Betting Apps? Heres A Quick Quiz To Seek Out Out
The courtroom ruling in favor of New Jersey paved the means in which for states to legalize sports playing. Despite its relative infancy, US online sports activities betting apps have already turn out to be wildly popular in states like New Jersey or Pennsylvania. But we as a company dont support/promote betting in any way.
Some betting apps shall be stronger for horse racing than others, particularly the ones who can stream the race meetings. Even when you dont plan to live bet, its still a good idea to check out the live choices that the sportsbook often provides. If youre using a good sports activities betting app, you shouldnt have to fret about app security. We have a team of more than 250 app developers operating to meet your request according to your business needs. Overall, the product is great and getting better.
- Yes, each wifi and cellphone information work for online playing.
- With the ideas above, it is possible for you to to make the best choice of which mobile cricket betting app to make use of.
- But we as an organization dont support/promote betting in any means.
- Better nonetheless, you can also bet on eSport games.
The app itself is amongst the finest to make use of, with the convenience of inserting a bet certainly one of many positives to the bet365 app. To do this, discover the hyperlink or APK, obtain, and install the app. BetMGM is one other US primarily based sports activities betting app that gives live in game betting throughout a variety of markets. Caesars Sportsbook is Saturday Down Souths most popular sports activities betting app. Gambling companies must have the mandatory licenses and adjust to the law, otherwise, they should reply for unlawful actions. Thanks to the numerous payment methods available, online gamblers can choose their most popular cost method and keep it up for both deposits and withdrawals.
Gambling Licence From A Trusted Authority
They are truthful and provide a high quality service from high to backside. Its also the best approach to request withdrawals, which is defined later. The best on-line betting apps have a couple of things in common.
Betway 1 For On-line Cricket Betting
Click the Download button and make sure the action. Many of the bookmaker apps listed on our web site additionally allow punters in India to take benefit of their beneficiant welcome bonus and free wager offers India using cellular units too. Many on-line sports betting sites provide generous welcome presents but require players to play through their winnings as a lot as 100 occasions to withdraw them as real money.
It is essential that the IPL betting sites shield your identity and process the withdrawals within the fastest time possible. Our staff at My Betting Sites India came up with a number of betting suggestions to ma...
00:47
Are You Good At Authorized Betting Apps? This Is A Quick Quiz To Find Out h+ Media
Are You Good At Authorized Betting Apps? This Is A Quick Quiz To Find Out
On the other hand, when you require a promotional code to say a sure bonus, you can find it on the page of the playing website thats dedicated to promotions. Signing Up on WorldTeam11 is pretty easy although the benefit that youve got upon Sign Up are immense. Follow the rules issued by the GamingCommission. The huge brands permit you to claim the same free bets as you would their desktop providing, claimable via the promotions part. The process of downloading is simple; you want to make several steps only to begin betting through the app online. After you have proceeded with the Becric apk obtain, you could marvel what to do next.
The greatest playing apps provide a seamless experience when in comparability with utilizing a normal betting web site. Bons betting firm is a new company that received registered in 2020 and bought its license from Curacao. You can quickly find a particular tournament and match by way of the search bar in the functions, or by navigating via the sections. As for the bets themselves, FanDuel has plenty to supply and is the forefather of similar sport parlays, which are now additionally in style on different websites.
The 22 bets app could be thought-about protected and safe for Indian sports activities lovers as a outcome of 22bet is ruled by and accredited by the Curacao Gaming Commission. The class contains quite a few special events, highlights of present games, and the chance to recall a game underneath certain circumstances. The record of obtainable choices continues to develop. BetMGM is the self proclaimed king of sportsbooks, and theres no denying that its platform backs up this slogan. The sportsbook app is accessible for use both on Android and iOS gadgets.
The court docket ruling in favor of New Jersey paved the best way for states to legalize sports activities playing. Despite its relative infancy https://mobilbahis.icu/joker-megaways-slot-review/, US on-line sports betting apps have already turn into wildly popular in states like New Jersey or Pennsylvania. But we as a company dont support/promote betting in any means.
With more and more cricket lovers in India attempting out reside in play betting for themselves, this is positive to become a more important part of the business quickly. As you probably can see, there are many methods to make online betting deposits these days the one thing you have to do is select the tactic that works finest for you. Bringing a fresh and engaging interface thats user friendly and makes it straightforward to navigate. Every online betting web site has its personal process in phrases of putting bets, but typically, it goes one thing like this.
We happened to test amidst the primary running of The Hundred within the UK, and games for this competition wer...
00:47
Are You Good At Authorized Betting Apps? Here Is A Fast Quiz To Search Out Out h+ Media
Are You Good At Authorized Betting Apps? Here Is A Fast Quiz To Search Out Out
Deposit and place a minimal 10 money wager at single or amassed odds of 1/1 or higher and we will present you with 1 x 5 in free bets plus an additional 3 x 5 Free Bets the next day. First launched in 2017 in Australia, PointsBet Sportsbook has quickly turn into one of many biggest betting operators Down Under. Bonuses for opening an account are additionally supplied. Yes, the Pin up casino apk supplies excellent betting expertise and access to a fantastic number of reside tables and dealers. This on-line betting firm has a proud Indian heritage, which is necessary to a lot of sports activities fans who want to wager online using a agency like Comeon.
Right from just being an thought to a completely functional enterprise, we help your small business to grow at each stage. You can get them utilizing the mobile app or the net site. As playing may be addictive, its important youre conscious of the risks and arm yourself with tools and strategies to make sure it stays fun.
The court docket ruling in favor of New Jersey paved the finest way for states to legalize sports activities gambling. Despite its relative infancy, US on-line sports betting apps have already turn into wildly in style in states like New Jersey or Pennsylvania. But we as a company dont support/promote betting in any means.
If you have already got a consumer friendly expertise through the mobile betting web site, then you are prone to expertise the same with the app. Their welcome promotion provides you a 100% match on your first deposit with a $150 most limit. Youll additionally get more bonuses, promotions and options than any other bookie can supply. Indian gamers can entry all their favorite sports activities cricket, football, tennis, and so forth. However, only the preferred and big IPL betting websites consists of the stay streaming function.
- READ Best Apps to watch live cricket Watch Indian Cricket Team in Action at your personal home.
- Overall, the product is great and getting higher.
- In our opinion, the general best football betting app is Bet365.
- Deposit and place a minimum 10 money wager at single or accrued odds of 1/1 or greater and we will give you 1 x 5 in free bets plus an additional three x 5 Free Bets the following day.
The app itself is likely considered one of the greatest to make use of, with the convenience of placing a bet one of many positives to the bet365 app. To do this, find the hyperlink or APK, obtain, and set up the app. BetMGM is one other US based mostly sports betting app that gives reside in sport betting throughout a variety of markets. Caesars Sportsbook is Saturday Down Souths preferred sports betting app. Gambling services will must have the mandatory licenses and adjust to the legislation, otherwise, they will have to answer for unlawful actions. Thanks to the numer...
00:46
Are You Good At Legal Betting Apps? Here Is A Fast Quiz To Seek Out Out h+ Media
Are You Good At Legal Betting Apps? Here Is A Fast Quiz To Seek Out Out
10Cric app accepts Indian rupees as the principle account foreign money and allows you to guess on cricket, horse racing, kabaddi. Note that withdrawals can solely be accomplished to the identical account that you made your preliminary deposit from. In our opinion, the general greatest soccer betting app is Bet365. While the concept behind a web-based sports activities betting app is actually the identical, it allows you to place bets remotely from wherever inside state traces. I couldnt perceive why it was not downloading.
- They supply a ton of various sports activities betting choices, but they excel primarily in soccer.
- With over 12 years of experience in on-line gaming, Adam has seen, played, reviewed, and examined tons of of slot video games.
- The massive manufacturers permit you to declare the identical free bets as youll their desktop offering, claimable via the promotions part.
- The greatest betting apps in India keep attempting to face out from each other by offering playful recreation modes.
Our football predictions are made by professionals, however this doesnt guarantee a revenue for you. We would definitely recommend the operator not just for the cricket betting app it presents, but also its main give consideration to soccer. This is due to the fact that it is illegal for a betting website to function on Indian territory. BetMGM has risen to turn into the countrys third hottest sportsbook after a couple of false begins.
Moreover, if your withdrawals exceed the $1,000 limit, the operator reserves the proper to ask you for further verification as part of its KYC coverage. If you depend the general numbers, youll see that Australia was a profitable country for about eighty years while England has only about 50. Its important to note the risks bettors take by using unlawful or offshore betting sites whereas ready for a extra strong Florida mobile betting launch.
In phrases of sheer profit potential, its one of the best bonuses at any on-line sportsbook. Pete Rose, the all time MLB leader in hits, was similarly banned from baseball in 1989 for betting on video games while he was an MLB supervisor. At first, this was the game of kings and only an important folks performed it.
Playing Licence From A Trusted Authority
There are no restrictions or central laws that forestall Indian punters from using betting apps within the area. This allows fans to really really feel part of the motion and it increases the thrill ten fold. Yes, gamers can simply deposit and withdraw cash from the betting App.
Right from simply being an concept to a completely useful enterprise, we help your corporation to develop at each stage. You can get them using the cellular app or the internet site. As playing may be addictive, its important youre aware of the risks and ar...
00:29
Security updates for Wednesday LWN.net
Security updates have been issued by Fedora (firefox), Oracle (kernel, kernel-container, and nss), and SUSE (curl, dpdk, drbd, go1.18, kernel, openstack-cinder, openstack-glance, openstack-neutron-gbp, openstack-nova, python-oslo.utils, oracleasm, python3, slirp4netns, and xen).
00:20
Ubisofts new Ghostwriter tool will automatically generate background sounds and chatter Lifeboat News: The Blog

A good open world game is filled with little details that add to a players sense of immersion. One of the key elements is the presence of background chatter. Each piece of dialog you hear is known as a bark and must be individually written by the games creators a time consuming, detailed task. Ubisoft, maker of popular open world gaming series like Assassins Creed and Watch Dogs, hopes to shorten this process with Ghostwriter, a machine learning tool that generates first drafts of barks.
To use Ghostwriter, narrative writers input the character and type of interaction they are looking to create. The tool then produces variations, each with two slightly different options, for writers to review. As the writers make edits to the drafts, Ghostwriter updates, ideally producing more tailored options moving forward.
The idea here is to save game writers time to focus on the big stuff. Ghostwriter was created hand-in-hand with narrative teams to help them complete a repetitive task more quickly and effectively, giving them more time and freedom to work on games narrative, characters, and cutscenes, Ubisoft states in a video release.
00:20
Are We The Creation Of A Type V Civilization? | Unveiled Lifeboat News: The Blog

What if well always be at the bottom of the Kardashev Scale? Join us and find out!
Subscribe for more from Unveiled https://wmojo.com/unveiled-subscribe.
Did an advanced civilization exist before us? Could they have CREATED us?? In this video, Unveiled takes a closer look at the idea that humankind is actually built be a HIGHER POWER that were really controlled by a force thats beyond our recognition and finds out what it could mean for the future of our species!
This is Unveiled, giving you incredible answers to extraordinary questions!
Find more amazing videos for your curiosity here:
What If Were the Remnants of a Type III Civilization? https://youtu.be/tku2lTWNMMU
5 Discoveries That Could Change Ancient History https://youtu.be/TFcAC8kFkkY
0:00 Start.
0:43 Kardashev Scale.
1:29 The Multiverse.
3:00 Type V Civilization.
5:11 Type V Miracles.
6:44 Will Humans Be Forgotten?
8:09 Conclusions.
00:09
CISA Alerts on Critical Security Vulnerabilities in Industrial Control Systems The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has released eight Industrial Control Systems (ICS) advisories on Tuesday, warning of critical flaws affecting equipment from Delta Electronics and Rockwell Automation. This includes 13 security vulnerabilities in Delta Electronics' InfraSuite Device Master, a real-time device monitoring software. All versions prior to 1.0.5 are
Wednesday, 22 March
23:37
"cURL", the URL Code That Can, Marks 25 Years of Transfers SoylentNews
Utility began as a personal project, found its way into billions of devices:
Daniel Stenberg has observed the 25th anniversary of the curl open source project with the publication of curl 8.0.0, the 215th release of the command line tool, and a modest tele-celebration.
The name curl, originally rendered as "cURL" to emphasize its function, stands for "Client for URLs" or "Client URL Request Library" or its recursive form, "curl URL Request Library."
It's a command line tool and library for transferring data with URLs. Once installed on a device with command line access, curl can be used, through a text command, to send or fetch data to and from a server using a variety of network protocols.
Any developer who is serious about writing code that interacts over a network has probably used curl, or does so regularly. Presently, billions of devices rely on curl cars, mobile phones, set top boxes, routers, and other such items use it internally for data transfer.
"The curl project started out very humbly as a small renamed URL transfer tool that almost nobody knew about for the first few years," said Stenberg in a blog post. "It scratched a personal itch of mine."
4.0. It had 2,200 lines of code and had been adapted from projects known as httpget and urlget. As Stenberg explained, curl 4.0 supported just three protocols, HTTP, GOPHER and FTP, and 24 command line options. Version 8.0.0 can handle 28 protocols and 249 command line options."The first release of curl was not that special event since I had been shipping httpget and urlget releases for over a year already, so while this was a new name it was also 'just another release' as I had done many times already," he wrote.
Read more of this story at SoylentNews.
23:30
Automatically unlocking a LUKS encrypted root filesystem during boot English mikas blog
Update on 2023-03-23: thanks to Daniel Roschka for mentioning the Mandos and TPM approaches, which might be better alternatives, depending on your options and needs. Peter Palfrader furthermore pointed me towards clevis-initramfs and tang.
A customer of mine runs dedicated servers inside a foreign data-center, remote hands only. In such an environment you might need a disk replacement because you need bigger or faster disks, though also a disk might (start to) fail and you need a replacement. One has to be prepared for such a scenario, but fully wiping your used disk then might not always be an option, especially once disks (start to) fail. On the other hand you dont want to end up with (partial) data on your disk handed over to someone unexpected.
By encrypting the data on your disks upfront you can prevent against this scenario. But if you have a fleet of servers you might not want to manually jump on servers during boot and unlock crypto volumes manually. Its especially annoying if its about the root filesystem where a solution like dropbear-initramfs needs to be used for remote access during initramfs boot stage. So my task for the customer was to adjust encrypted LUKS devices such that no one needs to manually unlock the encrypted device during server boot (with some specific assumptions about possible attack vectors one has to live with, see the disclaimer at the end).
The documentation about this use-case was rather inconsistent, especially because special rules apply for the root filesystem (no key file usage), we see different behavior between whats supported by systemd (hello key file again), initramfs-tools and dracut, not to mention the changes between different distributions. Since tests with this tend to be rather annoying (better make sure to have a Grml live system available :)), Im hereby documenting what worked for us (Debian/bullseye with initramfs-tools and cryptsetup-initramfs).
The system was installed with LVM on-top of an encrypted Software-RAID device, only the /boot partition is unencrypted. But even if you dont use Software-RAID nor LVM the same instructions apply. The system looks like this:
% mount -t ext4 -l /dev/mapper/foobar-root_1 on / type ext4 (rw,relatime,errors=remount-ro) % sudo pvs PV VG Fmt Attr PSize PFree /dev/mapper/md1_crypt foobar lvm2 a-- 445.95g 430.12g % sudo vgs VG #PV #LV #SN Attr VSize VFree foobar 1 2 0 wz--n- 445.95g 430.12g % sudo lvs LV VG...
23:24
ScarCruft's Evolving Arsenal: Researchers Reveal New Malware Distribution Techniques The Hacker News
The North Korean advanced persistent threat (APT) actor dubbed ScarCruft is using weaponized Microsoft Compiled HTML Help (CHM) files to download additional malware onto targeted machines. According to multiple reports from AhnLab Security Emergency response Center (ASEC), SEKOIA.IO, and Zscaler, the development is illustrative of the group's continuous efforts to refine and retool its tactics
23:23
Windows 11 and 10s Snipping Tools Vulnerable to Data Exposure HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
Microsoft has stated that they are aware of the issue and are investigating, adding that they will take action to help keep customers protected.
This is a post from HackRead.com Read the original post: Windows 11 and 10s Snipping Tools Vulnerable to Data Exposure
23:08
Canonical Preparing Updated Ubuntu Font For Ubuntu 23.04 Phoronix
Canonical is preparing to ship an updated set of Ubuntu Font files for the Ubuntu 23.04 "Lunar Lobster" release but is hoping to see more user testing ahead of the official release next month...
22:53
Anti-Piracy DNS Poisoning Blacks Out Media Group, ISP Refuses to Comment TorrentFreak
 In a world where clear and independent reporting
struggles to get heard in a sea of sensationalized clickbait, the
German Heise group is
generally recognized as a reliable and accurate news source.
In a world where clear and independent reporting
struggles to get heard in a sea of sensationalized clickbait, the
German Heise group is
generally recognized as a reliable and accurate news source.
For several days last week, an unknown number of visitors to heise.de were denied access to the companys reporting. Instead, they found themselves redirected to Germanys anti-piracy website blocking portal and statements that had no basis in fact.
Silently Blocked For Several Days
A Heise analysis, published Tuesday, reveals that the publication first learned of issues affecting access to its website last Friday, March 17. More messages from readers were received on Monday, and all reported the same thing. When attempting to access heise.de, web browsers responded with a certificate error and an explanation.
A bright orange splash page informed Heise readers that due to copyright infringement, Heise had been rendered inaccessible. The message usually confronts internet users who attempt to access a specific set of sites previously identified as facilitators of mass online copyright infringement.
Heise had no idea why the message was being displayed but did find a common denominator. All of the readers reporting problems were using the same internet service provider 1&1 AG, a 3.9 billion telecoms group servicing 15.6 million fixed line and mobile customers.
DNS Tampering/Poisoning
Heise reports that its editors and system administrators were getting closer to the source of the problem on Friday but then a reader provided crucial information.
He had set up his providers standard DNS server with the IP address 82.144.41.8 as the DNS server in his router...
22:53
CVE-2023-28708: Apache Tomcat: JSESSIONID Cookie missing secure attribute in some configurations Open Source Security
Posted by Mark Thomas on Mar 22
CVE-2023-28708 Apache Tomcat - Information DisclosureSeverity: Important
Vendor: The Apache Software Foundation
Versions Affected:
Apache Tomcat 11.0.0-M1 to 11.0.0-M2
Apache Tomcat 10.1.0-M1 to 10.1.5
Apache Tomcat 9.0.0-M1 to 9.0.71
Apache Tomcat 8.5.0 to 8.5.85
Description:
When using the RemoteIpFilter with requests received from a reverse
proxy via HTTP that include the X-Forwarded-Proto header set to https,
session cookies created by...
22:37
Linux 6.2 Kernel Begins Rolling Out For Ubuntu 23.04 Phoronix
Canonical has been preparing to ship a Linux 6.2 based kernel for Ubuntu 23.04 and now it's in the process of rolling out over the coming days...
22:31
ATMs Running Low on Cash and Even Out of Cash (Manchester, England) schestowitz.com
 DO
not know if this is a global thing. I dont know if thats
true only for this country or for this city. I can speak about my
own area, and only my own area, for now (based
firsthand and direct experience)
DO
not know if this is a global thing. I dont know if thats
true only for this country or for this city. I can speak about my
own area, and only my own area, for now (based
firsthand and direct experience)
When banks started to collapse about two weeks ago (about 4 banks so far, mostly in the US) it sort of started a chain reaction and the ripples arent over yet. Its a domino effect and theres latency, just like there was a large latency in 2008. It can take weeks or months to fully unfold. Governments intervene. Bailouts become bigger and bigger. Its impossible to justify these. The public rebels. Theres revolt. Whats left of the media changes side to appease angry readers. Journalists would rather not defend the rescue of thieves.
On the very same day it started (SVB, late Friday) we decided to ensure we have physical cash, just in case.
In 2020 when the lockdowns started the media kept mentioning that toilet paper was running out (of stock, at least in store). Such media reports initiated growing levels of unrest/panic. Its a case of self-feeding loops and a self-fulfilling prophecy. It didnt take long for people to hoard (inside their home) what was left, so stores everywhere had no toilet paper left or only very expensive brands (that fewer people were willing or capable of buying).
It seems safe to assume that right about now the maintream media would cooperate with the state to prevent runs on the banks or runs on ATMs (cash machines here). Its not easy to even withdraw large amounts from ones account in the high street branches (many branches have also shut down and repeatedly pressure people to use apps, i.e. do all the work for themselves). They added barriers.
Yesterday, for the first time ever, we received marketing spam/mail in the post (snail mail) from a company asking if we wish to sell our home with their help. Thats rather strange if not a rude thing to be asking. One day earlier I stumbled upon an article stating that home sales have generally plunged (or people wishing to sell cannot find a buyer not for the desired price anyway).
So one can generally see where the economy is heading
A week ago I read that in Russia, more so after the war, many Russians hoarded physical cash. They could not trust the banking system, so they probably just wished to diversify their holdings as a failsafe mechanism (not putting all eggs in one basket). With sanctions and all, who can blame them?
I assume the media here wont report the ATM situation, but this is a personal blo...
22:25
The Six Million Dollar Man Opening and Closing Theme (With Intro) HD Surround Lifeboat News: The Blog

Loads more TV Themes at: http://teeveesgreatest.webs.com/
The Six Million Dollar Man is an American science fiction and action television series about a former astronaut, Colonel Steve Austin, portrayed by American actor Lee Majors. Austin has superhuman strength due to bionic implants and is employed as a secret agent by a fictional U.S. government office named OSI The series was based on the Martin Caidin novel Cyborg, which. was the working title of the series during pre-production.
Following three television pilot movies, which all aired in 1973, the The Six Million Dollar Man aired on the ABC network as a regular episodic series for five seasons from 1974 to 1978. Steve Austin became a pop culture icon of the 1970s. A spin-off television series, The Bionic Woman, featuring the lead female character Jaime Sommers, ran from 1976 to 1978 (and was the subject of a remake in 2007). Three television movies featuring both bionic characters were also produced from 1987 to 1994.
When NASA astronaut Steve Austin is severely injured in the crash of an experimental lifting body aircraft, he is rebuilt in an operation that costs six million dollars. His right arm, both legs and the left eye are replaced with bionic implants that enhance his strength, speed and vision far above human norms: he can run at speeds of 60 mph (97 km/h), and his eye has a 20:1 zoom lens and infrared capabilities, while his bionic limbs all have the equivalent power of a bulldozer. He uses his enhanced abilities to work for the OSI (Office of Scientific Intelligence) as a secret agent.
22:25
Place cells: How your brain creates maps of abstract spaces Lifeboat News: The Blog

In this video, we will explore the positional system of the brain hippocampal place cells. We will see how it relates to contextual memory and mapping of more abstract features.
OUTLINE:
00:00 Introduction.
00:53 Hippocampus.
1:27 Discovery of place cells.
2:56 3D navigation.
3:51 Role of place cells.
4:11 Virtual reality experiment.
7:47 Remapping.
11:17 Mapping of non-spatial dimension.
13:36 Conclusion.
_____________
REFERENCES:
1) Anderson, M.I., Jeffery, K.J., 2003. Heterogeneous Modulation of Place Cell Firing by Changes in Context. J. Neurosci. 23, 88278835. https://doi.org/10.1523/JNEUROSCI.23-26-08827.
2) Aronov, D., Nevers, R., Tank, D.W., 2017. Mapping of a non-spatial dimension by the hippocampalentorhinal circuit. Nature 543719722. https://doi.org/10.1038/nature21692
3) Bostock, E., Muller, R.U., Kubie, J.L., 1991. Experience-dependent modifications of hippocampal place cell firing. Hippocampus 1193-205. https://doi.org/10.1002/hipo.
22:20
Preventing Insider Threats in Your Active Directory The Hacker News
Active Directory (AD) is a powerful authentication and directory service used by organizations worldwide. With this ubiquity and power comes the potential for abuse. Insider threats offer some of the most potentials for destruction. Many internal users have over-provisioned access and visibility into the internal network. Insiders' level of access and trust in a network leads to unique
22:00
A Studio Condenser Microphone For a Constrained Budget Hackaday

As the Internet has turned so many of us into content creators, weve seen the quality of webcams and microphones steadily increase to the point at which even a fairly modestly-equipped YouTuber now captures their wisdom at a quality far exceeding that you might have found in some broadcast studios not so long ago. Still, decent quality costs money, and for that reason [Spirit532] has built his own high quality condenser microphone for less expenditure.
...
21:19
AMD Adds Basic RPC Mechanism To LLVM libc For GPUs Phoronix
AMD has upstreamed a basic RPC (remote procedure call) mechanism for GPU use to LLVM's libc and wired it up for AMDGPU use...
21:15
BreachForums current Admin Baphomet shuts down BreachForums Security Affairs
Baphomet, the current administrator of BreachForums, announced that the popular hacking forum has been officially taken down.
U.S. law enforcement arrested last week a US man that goes online with the moniker Pompompurin, the US citizen is accused to be the owner of the popular hacking forum BreachForums.
The news of the arrest was first reported by Bloomberg, which reported that federal agents arrested Conor Brian Fitzpatrick from Peekskill, New York.
The man has been charged with soliciting individuals with the purpose of selling unauthorized access devices.
The BreachForums hacking forum was launched in 2022 after the law enforcement authorities seized RaidForums as a result of Operation TOURNIQUET.
pompompurin always confirmed that he was not affiliated with RaidForums in any capacity,
The law enforcement authorities have yet to shut down the website, while another admin of the forum that goes online with the alias Baphomet announced that he is taking the control of the platform.
Baphomet initially added that he believes that the feds havent had access to the infrastructure.
On March 21, 2023, Baphomet, which is the current administrator of BreachForums, announ...
20:53
Metallica is Selling So Many Vinyl Records It Bought its Own Factory SoylentNews
Metallica Is Selling so Many Vinyl Records It Bought Its Own Factory:
Despite technology bringing new recording media formats and improved compression algorithms, there is certainly a growing demand for vinyl again despite its death being announced several times over recent decades.
Metallica has bought a majority stake in Furnace Record Pressing, one of the biggest and most important vinyl records companies in the U.S. If anyone had any doubts about the growth of the vinyl sales, which last year outpaced CD sales for the first time since 1987, Metallica's new purchase just gave them a very loud reminder that what's old is new again.
Vinyl records are experiencing a renaissance among music lovers. Although Metallica hasn't released a new album since Hardwired...To Self-Destruct in 2016, it sold more than 387,000 vinyl albums in 2022, according to data from Billboard. That year, it ranked sixth on the list of most albums sold in the U.S., topping the 337,000 albums it sold in 2021. The price Metallica paid for Furnace was not disclosed; members of the band will now sit on Furnace's board.
Metallica is expected to release its first album in seven years sometime over the next few weeks, setting the stage for the band to sell to many, many more vinyl records in 2023.
Read more of this story at SoylentNews.
20:22
Microsoft Has Also Infiltrated the OSIs Board of Directors After Rigged Elections Techrights
As if it didnt control the OSIs agenda and staff already
Overt conflict of interest (Microsoft is attacking Open Source)
Summary: Weeks ago we warned that this would happen and for the third or fourth time in 2 years the OSIs election process broke down; today the Open Source Initiative (OSI) writes: The polls just closed, the results are in. Congratulations to the returning directors Aeva Black (Microsoft employee)
20:22
Bill Gates: AI is most important tech advance in decades Lifeboat News: The Blog
The former Microsoft boss says AI is the second revolutionary technology hes seen in his lifetime.
19:58
Rogue NuGet Packages Infect .NET Developers with Crypto-Stealing Malware The Hacker News
The NuGet repository is the target of a new "sophisticated and highly-malicious attack" aiming to infect .NET developer systems with cryptocurrency stealer malware. The 13 rogue packages, which were downloaded more than 160,000 times over the past month, have since been taken down. "The packages contained a PowerShell script that would execute upon installation and trigger a download of a '
19:54
Links 22/03/2023: Official Thunderbird Podcast Starts Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Health/Nutrition/Agriculture
- Proprietary
- Pseudo-Open Source
- Security
- Defence/Aggression
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Digital Restrictions (DRM)
- Monopolies
- Gemini* and Gopher
-
GNU/Li...
19:48
These 15 European startups are set to take the cybersecurity world by storm Help Net Security
Google has announced the startups chosen for its Cybersecurity Startups Growth Academy. The 15 selected startups are from eight countries and were chosen from over 120 applicants. They have made significant contributions, from securing health applications to protecting educators and safeguarding the clean water supply chain. The selected companies will receive mentoring sessions from Google experts, including former VirusTotal and Mandiant startups. Additionally, they will have opportunities to network with other cybersecurity entrepreneurs at events More
The post These 15 European startups are set to take the cybersecurity world by storm appeared first on Help Net Security.
19:00
Icicle Patterns With Custom Gantry Hackaday

[Cranktown City] uses a number of custom-built linear rails used as gantries for various tools in the shop. The first is on a plasma cutter, which is precise but difficult to set up or repair. Another is for mounting a camera, and while it is extremely durable, its not the most precise tool in the shop. Hoping to bridge the gap between these two, hes building another gantry with a custom bearing system, and to test it hell be using it to create patterns in icicles hanging from an eave at his shop.
While this isnt the final destination for this gantry, it is an excellent test of it, having to perform well for a long period of time in an extremely cold environment. The bearing system consists of a piece of square steel tubing turned 45 inside another larger square steel tube and held in place with two sets of three bearings with V-shaped notches. To drive the gantry he is using a motor with a belt drive, and for this test a piece of drip irrigation is mounted to it which lets out a predetermined amount of water on top of the roof to create numerous icicles beneath with various programmed lengths.
After a few test runs the gantry system can create some...
18:28
Independent Living Systems data breach impacts more than 4M individuals Security Affairs
US health services company Independent Living Systems (ILS) discloses a data breach that impacted more than 4 million individuals.
US health services company Independent Living Systems (ILS) disclosed a data breach that exposed personal and medical information for more than 4 million individuals.
Independent Living Systems, offers a comprehensive range of turnkey payer services including clinical and third-party administrative services to managed care organizations and providers.
ILS provides assistance beyond the clinical realm at every stage of care from hospitalization to the treatment of chronic illnesses to personalized care management including nutritional support.
The company provides its services to over 4.2 million individuals.
On July 5, 2022, we experienced an incident involving the inaccessibility of certain computer systems on our network. We responded to the incident immediately and began an investigation with the assistance of outside cybersecurity specialists. Through our response efforts, we learned that an unauthorized actor obtained access to certain ILS systems between June 30 and July 5, 2022. reads the Notice of Data breach published by the company. During that period, some information stored on the ILS network was acquired by the unauthorized actor, and other information was accessible and potentially viewed.
The security breach was discovered on July 5, 2022, when some of the systems at the company became inaccessible. This circumstance suggests that the systems were infected with ransomware. The company launched an investigation into the incident with the support of external cybersecurity experts. The investigation revealed that between June 30 and July 5, threat actors had access to certain systems.
The notice of data breach states that the types of impacted information varies by individual and could have included, name, address, date of bi...
18:26
Coding wont exist in 5 years? You might be right Lifeboat News: The Blog
Register Free for NVIDIAs Spring GTC 2023, the #1 AI Developer
Conference: https://nvda.ws/3kEyefH
RTX 4,080 Giveaway Form: https://forms.gle/ef2Kp9Ce7WK39xkz9
The talk about AI taking our programming jobs is everywhere. There are articles being written, social media going crazy, and comments on seemingly every one of my YouTube videos. And when I made my video about ChatGPT, I had two particular comments that stuck out to me. One was that someone wished I had included my opinion about AI in that video, and the other was asking if AI will make programmers obsolete in 5 years. This video is to do just that. And after learning, researching, and using many different AI tools over the last many months (a video about those tools coming soon), well lets just say I have many thoughts on this topic. What AI can do for programmers right now. How its looking to progress in the near future. And will it make programmers obsolete in the next 5 years? Enjoy!!
The Sessions I Mentioned:
Fireside Chat with Ilya Sutskever and Jensen Huang: AI Today and
Vision of the Future [S52092]:
https://www.nvidia.com/gtc/session-catalog/?ncid=ref-inor-73314001t6Nv.
Using AI to Accelerate Scientific Discovery [S51831]:
https://www.nvidia.com/gtc/session-catalog/?ncid=ref-inor-73197001tw0E
Generative AI Demystified [S52089]:
https://www.nvidia.com/gtc/session-catalog/?ncid=ref-inor-73393001DjiP
3D by AI: Using Generative AI and NeRFs for Building Virtual Worlds
[S52163]:
https://www.nvidia.com/gtc/session-catalog/?ncid=ref-inor-73782001l1Ul.
Achieving Enterprise Transformation with AI and Automation
Technologies [S52056]:...
18:25
Amazon Robotics Deploys First Fully Autonomous Robot With NVIDIA Isaac Sim Lifeboat News: The Blog

Amazon Robotics has manufactured and deployed the worlds largest fleet of mobile industrial robots. The newest member of this robotic fleet is ProteusAmazons first fully autonomous mobile robot. Amazon uses NVIDIA Isaac Sim, built on Omniverse, to create high-fidelity simulations to accelerate Proteus deployments across its fulfillment centers.
Explore NVIDIA Isaac Sim: https://developer.nvidia.com/isaac-sim.
#Simulation.
#Robotics.
#DigitalTwin
18:19
NAPLISTENER: New Malware in REF2924 Group's Arsenal for Bypassing Detection The Hacker News
The threat group tracked as REF2924 has been observed deploying previously unseen malware in its attacks aimed at entities in South and Southeast Asia. The malware, dubbed NAPLISTENER by Elastic Security Labs, is an HTTP listener programmed in C# and is designed to evade "network-based forms of detection." REF2924 is the moniker assigned to an activity cluster linked to attacks against an entity
18:09
Amazon Has Cut 27 Thousand Jobs as Tech Crisis Also Worsens Down Under SoylentNews
Amazon will cut another 9,000 jobs bringing the total to 27,000 jobs culled so far as part of the 'tech wreck' sweeping the world.
The cuts will take place in coming weeks and are mainly concentrated in Amazon's web, HR and advertising team. Staff who look after Amazon's foray into Twitch livestreaming are also set to be impacted.
CEO Andy Jassy said the decision was made to ensure the company remained "streamlined" as tough market conditions bite across the globe.
Six days ago, another massive tech giant, Facebook owner Meta, also announced mass job redundancies. Meta chief executive officer Mark Zuckerberg told employees that his company was laying off another 10,000 employees and closing about 5000 additional open roles in its own second major round of job cuts.
Closer to home, Australia has also been pummelled by the tough economic conditions. Earlier this month, ASX-listed software firm Xero announced that it was going to reduce its headcount by 700 to 800 roles, which was a 15 per cent cut to the overall workforce. A few days earlier, software giant Atlassian slashed 500 roles, which represents five per cent of its total global workforce. Another software development company, Kinde, laid off 28.5 per cent of staff at the end of last month.
I would certainly feel 'streamlined' or perhaps in free fall if I no longer had a job.
Read more of this story at SoylentNews.
18:08
IRC Proceedings: Tuesday, March 21, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-210323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-210323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-210323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-210323.gmi
Over HTTP:
|
... |
18:00
Visiting the Ramses the Great Exhibit. Antarctica Starts Here.
Early in October of 2022.ev, we paid a visit to an exhibit of artifacts at the Fine Arts Museum of San Francisco from the reign of Ramesses II, third ruler of the nineteenth dynasty of Egypt. Since covid started we haven't done a whole lot of going places so we figured that, all things in our respective risk models being equal, this would be an outing worth making the time for. As I write those post I don't know if it's still there, but the museum's page didn't 404 so it probably is. If you're in the area, it's worth paying the museum a visit and spending a few hours exploring.
Anyway, here are the pictures I took.
Humble teas antidepressant properties confirmed Terra Forming Terra

Tentsla adds a four-person tent to the back of a Tesla Model Y Terra Forming Terra

The Zoning Theory of Everything Terra Forming Terra

Nature of Plasma - REF Robert Temple Terra Forming Terra
Reading about the nature of plasma, i am inspired to advance our thinking. As i have posted, Cloud Cosmology throws up a plausible object which can be described best as a neutral neutron pair which can be expected to decay into an hydrogen atom with its own free electron. Understand that we posit self assembly of a range of particles beginning with the 'neutral' neutrino pair actually described better as a SPACE TIME pendulum, then to a 'neutral' electron positron pairing and from there to our neutral neutron pairs which ultimately decays into hydrtogen providing us with free electrons and positive ions. Besides the obvious, it is likely a whole range of intermediate partial constructs also emerge and when they decay, we identify them as cosmic rays.
What is interesting is that the neutral neutron pair is certainly not perfectly neutral but will act weakly at least along several axis. This permits the attachment of either negative or positive ions as well but not necessarily bound as we experience with what we are able to detect. It still means though that it should be possible to detect these objects and in fact we already have. Electrons will pop free when absorbing a photon and then reemit a photon. Thus we can see those clouds.
All this is a round about way to describe the nature of plasma. These objects are sticky enough to largely self assemble in order to produce potential complex atoms to fill the periodic table and explains a lot as well. I use the word potential because we only see that potential realized on the surface of the sun under both pressure and also dense radiation
The surface of the sun sees neutron pairs decaying into hydrogen gas which then emits radiation as electrons are grabbed. It is possible that the...
Intel, RADV & NVIDIA Jump On Supporting Vulkan's New VK_KHR_map_memory2 Phoronix
Introduced last week with the Vulkan 1.3.244 spec update was a new extension, VK_KHR_map_memory2, which is seeing fast support from the open-source Intel "ANV" and Mesa Radeon "RADV" drivers as well as NVIDIA's newest Vulkan driver beta...
16:30
Enhance security while lowering IT overhead in times of recession Help Net Security
Is cybersecurity recession-proof? Thats the question on the minds of many security professionals and executives as a possible economic downturn of indeterminate length and severity looms and many organizations are tightening their belts. While research suggests that IT spending is showing some immunity to economic headwinds Gartner is still predicting growth this year, albeit slower than last CIOs are increasingly pressured to make strategic contributions to the business. For many organizations, this includes More
The post Enhance security while lowering IT overhead in times of recession appeared first on Help Net Security.
16:00
Fresh PCBs For the Quickshot II and II Plus Joysticks Hackaday

The Quickshot II was released by Spectravideo in 1983 for the Commodore 64 and compatible systems, with the Quickshot II Plus following the next year. After decades of regular use, its quite understandable that these old-timers may be having some functional issues, but as long as the plastic parts are still good, [Stephan Eckweiler]s replacement PCBs may be just the thing that these joysticks need to revitalize them for another few decades.
What may be a matter of taste is that these replace the nice tactile clicky switches on the QS II Plus with SMD push buttons, but compared to the stamped metal button construction of the original QS II, the new board is probably a major improvement. As for the BOM, it features two ICs: a 74LS00 latch and NE555 timer, along with the expected stack of passives and switches, both through-hole and SMD.
The PCB contains break-off boards for the switches within the joystick itself, requiring a bit of wiring to be run to the main PCB before soldering on the DE-9 connector and...
16:00
Why you should treat ChatGPT like any other vendor service Help Net Security
Although OpenAI is an established organization with many years of experience promoting and developing AI systems, the relative immaturity of the ChatGPT application, combined with the lack of security assurance available for OpenAI, can put organizations at risk. In this Help Net Security video, Meghan Maneval, Director of Technical Product Management, Reciprocity, discusses why companies considering the utilization of ChatGPT internally must ensure the tool and the provider undergo the same third-party risk management process More
The post Why you should treat ChatGPT like any other vendor service appeared first on Help Net Security.
15:37
BreachForums Administrator Baphomet Shuts Down Infamous Hacking Forum The Hacker News
In a sudden turn of events, Baphomet, the current administrator of BreachForums, said in an update on March 21, 2023, that the hacking forum has been officially taken down but emphasized that "it's not the end." "You are allowed to hate me, and disagree with my decision but I promise what is to come will be better for us all," Baphomet noted in a message posted on the BreachForums Telegram
15:30
Bridging the cybersecurity readiness gap in a hybrid world Help Net Security
A mere 15% of organizations globally have the mature level of readiness needed to be resilient against todays modern cybersecurity risks, according to a Cisco report. Organizations have moved from an operating model that was largely static where people operated from single devices from one location, connecting to a static network to a hybrid world in which they increasingly operate from multiple devices in multiple locations, connect to multiple networks, access applications in More
The post Bridging the cybersecurity readiness gap in a hybrid world appeared first on Help Net Security.
15:24
What Do Early Earth's Core Formation and Drip Coffee Have in Common? SoylentNews
A new technique developed by Carnegie's Yingwei Fei and Lin Wang provides fresh insight into the process by which the materials that formed Earth's core descended into the depths of our planet, leaving behind geochemical traces that have long mystified scientists. Their work is published by Science Advances.
Earth accreted from the disk of dust and gas that surrounded our Sun in its youth. As Earth grew from smaller objects over time, the densest material sank inward, separating the planet into distinct layersincluding the iron-rich metal core and silicate mantle.
"The segregation of the core and mantle is the most important event in the geologic history of Earth," explained Fei. "Convection in the outer core powers the Earth's magnetic field, shielding us from cosmic rays. Without it, life as we know it could not exist."
Each of our planet's layers has its own composition. Although the core is predominantly iron, seismic data indicates that some lighter elements, like oxygen, sulfur, silicon and carbon, were dissolved into it and brought along for the ride into the planet's center. Likewise, the mantle is predominately silicate, but its concentrations of so-called "iron-loving," or siderophile, elements have mystified scientists for decades.
[...] Using these tools, Wang and Fei developed a new method of tracing the movement of the core-forming liquid metal in their sample as it migrated inward. They showed that much like water filtering through coffee grounds, under the dynamic conditions found on early Earth, iron melts could have passed through the cracks between a layer of solid silicate crystalscalled a grain boundaryand exchanged chemical elements.
Read more of this story at SoylentNews.
15:00
How to combat hardware Trojans by detecting microchip manipulations Help Net Security
Not only do security vulnerabilities lurk within software, but they can also be embedded directly into hardware, leaving technical applications open to widespread attack. For their project, the researchers took thousands of microscopic images of microchips. Pictured here is such a chip in a golden chip package. The chip area that was inspected only measures about two square millimeters. Researchers from Ruhr University Bochum, Germany, and the Max Planck Institute for Security and Privacy (MPI-SP) More
The post How to combat hardware Trojans by detecting microchip manipulations appeared first on Help Net Security.
14:30
SailPoint Non-Employee Risk Management reduces third-party risk Help Net Security
SailPoint Technologies has rolled out a new non-employee risk management capability based on the companys January 2023 acquisition of SecZetta. The SailPoint Non-Employee Risk Management solution is available now as an add-on to the SailPoint Identity Security Cloud. The new SailPoint Non-Employee Risk Management solution allows organizations to execute risk-based identity access and lifecycle strategies for non-employees. This growing non-employee population today includes a range of identities including contractors, third-party partners, suppliers and even non-human More
The post SailPoint Non-Employee Risk Management reduces third-party risk appeared first on Help Net Security.
14:23
Why are colon cancer rates in young people rising? Lifeboat News: The Blog
In a recent perspective article published in the journal Science, researchers at the Young-Onset Colorectal Cancer Center of Dana-Farber Cancer Institute emphasized that a better understanding of the etiology of early-onset colorectal cancer (EOCRC) is crucial to managing its increasing incidence worldwide. So, they identified five critical areas for investigating EOCRC biology.
Perspective: A common cancer at an uncommon age. Image Credit: Anatomy Image / Shutterstock.
14:23
A hybrid unicycle that can move on the ground and fly Lifeboat News: The Blog
Unmanned aerial vehicles (UAVs), also known as drones, can help humans to tackle a variety of real-world problems; for instance, assisting them during military operations and search and rescue missions, delivering packages or exploring environments that are difficult to access. Conventional UAV designs, however, can have some shortcomings that limit their use in particular settings.
For instance, some UAVs might be unable to land on uneven terrains or pass through particularly narrow gaps, while others might consume too much power or only operate for short amounts of time. This makes them difficult to apply to more complex missions that require reliably moving in changing or unfavorable landscapes.
Researchers at Zhejiang University have recently developed a new unmanned, wheeled and hybrid vehicle that can both roll on the ground and fly. This unique system, introduced in a paper pre-published on arXiv, is based on a unicycle design (i.e., a cycling vehicle with a single wheel) and a rotor-assisted turning mechanism.
14:23
Semiconductor lattice marries electrons and magnetic moments Lifeboat News: The Blog
A model system created by stacking a pair of monolayer semiconductors is giving physicists a simpler way to study confounding quantum behavior, from heavy fermions to exotic quantum phase transitions.
The groups paper, Gate-Tunable Heavy Fermions in a Moir Kondo Lattice, published March 15 in Nature. The lead author is postdoctoral fellow Wenjin Zhao in the Kavli Institute at Cornell.
The project was led by Kin Fai Mak, professor of physics in the College of Arts and Sciences, and Jie Shan, professor of applied and engineering physics in Cornell Engineering and in A&S, the papers co-senior authors. Both researchers are members of the Kavli Institute; they came to Cornell through the provosts Nanoscale Science and Microsystems Engineering (NEXT Nano) initiative.
14:20
Verosint SignalPrint identifies potentially malicious accounts Help Net Security
Verosint announced a new solution that helps organizations secure their online businesses and protect their customers in the face of ever-growing account fraud. With Verosint, companies can deliver frictionless access to legitimate customers, while blocking or challenging access by suspicious users. Account fraud, where bad actors fraudulently login to web applications, is one of the fastest-growing crimes to threaten online businesses in recent years. This trend is likely to continue as criminals leverage the vast More
The post Verosint SignalPrint identifies potentially malicious accounts appeared first on Help Net Security.
14:15
WALLIX SaaS Remote Access allows organizations to regain control of external remote access Help Net Security
The post WALLIX SaaS Remote Access allows organizations to regain control of external remote access appeared first on Help Net Security.
14:10
AlertEnterprise launches Guardian SOC Insights suite to improve physical security operations Help Net Security
AlertEnterprise has revealed the launch of its new Guardian SOC Insights suite. Powered by the companys latest developments in AI, including a powerful integration with the OpenAI ChatGPT platform, Guardian SOC Insights is designed to provide actionable data and playbooks to SOC teams, enabling them to detect, respond and mitigate risk swiftly and accurately. Guardians AI engine reduces the time to deploy, with customers up and running in a matter of weeks, delivering measurable ROI More
The post AlertEnterprise launches Guardian SOC Insights suite to improve physical security operations appeared first on Help Net Security.
14:05
Splunk enhances its unified security and observability platform Help Net Security
Splunk has released innovations to Splunks unified security and observability platform to help build safer and more resilient digital enterprises. Splunks latest innovations include enhancements to Splunk Mission Control and Splunk Observability Cloud, and the general availability of Splunk Edge Processor. With the Splunk platform, organizations can unify, simplify and modernize their workflows and business. Strengthen digital resilience with Splunks unified security solution The world of security operations is rife with challenges. Many organizations cannot More
The post Splunk enhances its unified security and observability platform appeared first on Help Net Security.
14:00
Many More Microsoft Layoffs Later Today Techrights
Loss leader Hey Hi (AI) is used to distract from Bing layoffs, Azure layoffs, GitHub layoffs, Edge layoffs etc. even if its future is uncertain and there is no viable business model
Summary: Yesterday we shared rumours about Microsoft layoffs being planned for later today (there were 3 waves of layoffs so far this year). There are several more people here who say the same. How much noise will Microsoft make in the media in order to distract? Will the chaffbot "ChatGPT" help create enough chaff?
13:41
Links 21/03/2023: JDK 20 and GNOME 43.5 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Server
-
Container Journal Holding Retrospectives in a Cloud-Native World
When I worked at AWS, we had retrospective revi...
-
-
13:00
BitTorrent for Language Models Hackaday

In the old days of the Internet, FTP was sufficient for downloading the occasional file. But with the widespread use of computer audio and video, it was easy to swamp an FTP server so eventually BitTorrent was born. The idea was you would download bits and pieces of a file from different places and, in theory, people would download bits and pieces that you have if they need them. Now Petals wants to use this same method with language models. These AI language models are all the rage, but they take significant computer resources. The idea behind Petals is like BitTorrent. You handle a small part of the model (about 8 gigabytes which is small compared to the 352 gigabytes required), and other people have other parts.
Of course, if you are privacy-minded, that means that some amount of your data is going out to the public, but for your latest chatbot experiments, that might not be a big problem. You can install Petals in an Anaconda environment or run a Docker image if you dont want to set up anything. If you just want to access the distributed networks chatbot based on BLOOMZ-176B, you can do that online.
Since the network processes tokens, a chat with the device is a little jerky, with a noticeable pause between words. It did say you can increase speed by connecting your GPU. Heres a transcript:
Hackaday: How many nodes host you? AI: Two thousand six hundered and ninety-thr...
12:56
Getting Started with Open Source Development Linux.com

Read the original blog here Read More
The post Getting Started with Open Source Development appeared first on Linux.com.
12:39
Zipline Unveils Quiet Drone Delivery Platform, Expands Operations SoylentNews
Zipline's new drones release tethered mini-drones for precision package deliveries
Zipline is revealing its new drone delivery platform today that the company says is capable of making a 10-mile delivery in 10 minutes, precisely placing packages on small targets like a patio table or the front steps of a home.
The new drone, which Zipline calls the Platform 2 (P2) Zip, uses a system of wires that lets down the package inside a cute little mini-bus-looking container the company describes as a "delivery droid." The P2 Zip hovers more than 300 feet above the ground at the delivery point, keeping its blades and noise away from people (and trees and wires and buildings) to let down its tethered droid instead.
The droid has the ability to steer with propellers as it's coming down, then lands and softly drops its payload.
[...] Similar to Wing's newly announced delivery network, Zipline says its P2 can dynamically move from dock to dock to charge up as needed and be ready to take orders. P2 can travel up to 24 miles one way without a payload and up to 10 miles while carrying six to eight pounds of weight. In comparison, Wing's drone can carry about three pounds and is technically capable of up to 12 miles of flight one way.
Read more of this story at SoylentNews.
11:37
NEW 'Off The Wall' ONLINE 2600 - 2600: The Hacker Quarterly
NEW 'Off The Wall' ONLINE
Posted 22 Mar, 2023 0:37:17 UTC
The new edition of Off The Wall from 03/21/2023 has been archived and is now available online.
11:00
HPR3818: nop test redux Hacker Public Radio
nop redux This is the updated code -logicprobe marker -logicprobe variable Compare variable Count $23 constant PINB $24 constant DDRB $25 constant PORTB $100 constant PINH $101 constant DDRH $102 constant PORTH $a0 constant TCCR4A $a1 constant TCCR4B $a8 constant OCR4A $b0 constant TCCR2A $b1 constant TCCR2B $b3 constant OCR2A $2c constant PINE $2d constant DDRE $2e constant PORTE $6a constant EICRB $3d constant EIMSK : ext4.irq ( -- ) Count @ 1+ Count ! ;i : logicprobe.init ( -- ) tone generatoed through timer2 %0001.0000 DDRB mset d10, pb4 %0100.0010 TCCR2A c! use OC2A, ctc mode $ff OCR2A c! compare falue %0 DDRE c! e input %0000.0010 EICRB mset falling edge ['] ext4.irq #6 int! attach interrupt ; helper words : open.gate ( -- ) 0 Count ! %0001.0000 EIMSK mset ; : close.gate ( -- ) %0001.0000 EIMSK mclr ; tone stuff : high.tone ( -- ) %0000.0100 TCCR2B c! 750 ms 0 TCCR2B c! ; : low.tone ( -- ) %0000.0110 TCCR2B c! 750 ms 0 TCCR2B c! ; : alt.tone ( -- ) 3 for %0000.0100 TCCR2B c! 150 ms 0 TCCR2B c! 150 ms %0000.0110 TCCR2B c! 150 ms 0 TCCR2B c! 150 ms next ; : process.data ( -- ) Count @ 1- Count ! Count @ 0 > if cr ." freq=" 10 * . cr ." pulse" alt.tone sound output else %0001.0000 PINE mtst if cr ." high" high.tone sound output else cr ." low" low.tone sound output then then ; : wait 100 ms ; : sample ( -- ) open.gate wait close.gate process.data ; words called at the forth command line to do the test demo tones low.tone high.tone alt.tone the test sample a stop clocked start.clock sample a0 line sample stop.clock and sample a0 stop.clock sample reset the z80 and single step probing the m1 signal reset step step step step step step run step sample step sample step sample step sample sample if its jammed hit it, if it breaks it needed replacing anyway
Identifying and Extracting Jupyter Notebook Structure It Will Never Work in Theory
Many of my data science colleagues use Jupyter notebooks or RMarkdown in their work, and they have all occasionally been misled by what they seen on the screen. Chunks of code in notebooks can be executed in any order or not executed at all, so it's possible (or even common) for plots, tables, and code to be out of sync. This paper presents a tool for tracing dataflow dependencies between cells that involves labeling the stages of a typical machine learning pipeline. The authors evaluated their tool by scraping notebooks created in GitHub repositories on two successive days (to avoid biases that might be introduced by only looking at notebooks from popular repositories), and found that their approach was more accurate than two previously-published techniques.
Computational notebooks are clearly here to stay, so it's great to see researchers looking at ways to make them better. And just as experience with the shortcomings of languages like C and C++ led to the design of languages like Rust, I hope that analysis of the problems with today's notebooks will lead to the design of languages that are naturally more notebook-friendly.
Yuan Jiang, Christian Kastner, and Shurui Zhou. Elevating jupyter notebook maintenance tooling by identifying and extracting notebook structures. In 2022 IEEE International Conference on Software Maintenance and Evolution (ICSME). IEEE, Oct 2022. doi:10.1109/icsme55016.2022.00047.
Data analysis is an exploratory, interactive, and often collaborative process. Computational notebooks have become a popular tool to support this process, among others because of their ability to interleave code, narrative text, and results. However, notebooks in practice are often criticized as hard to maintain and being of low code quality, including problems such as unused or duplicated code and out-of-order code execution. Data scientists can benefit from better tool support when maintaining and evolving notebooks. We argue that central to such tool support is identifying the structure of notebooks. We present a lightweight and accurate approach to extract notebook structure and outline several ways such structure can be used to improve maintenance tooling for notebooks, including navigation and finding alternatives.
10:00
Dispense 60 Bolts in 2.3 Seconds Hackaday

Weve covered a number of projects that assist makers who need to fill orders for their small businesses, or kitting. [Helmke] has sorted thousands of pieces of hardware that they include with 3D printed parts sold online. They have been developing an alternative, a modular system for sorting and packaging specific quantities of parts.
...
10:00
Open source during the recession: Insights from the World Open Innovation Conference Linux.com

Read the original blog here Read More
The post Open source during the recession: Insights from the World Open Innovation Conference appeared first on Linux.com.
09:55
Google Wont Honor Medical Leave During its Layoffs, Outraging Employees SoylentNews
Ex-Googler says she was laid off from her hospital bed shortly after giving birth:
Would you believe that Google's mass firings from January are still going on? Google's reported mishandling of its biggest round of layoffs ever has employees up in arms, and they're doing everything from walking out on the job to sending angry letters to management.
First up, European Googlers are just now being laid off due to the January announcement. Reuters reports that more than 200 workers were laid off from the Zurich, Switzerland, branch of the company this week. The employees at that office walked out for a second time in protest of the move and even offered to take pay cuts or reduce working hours to stave off the job cuts. Google's layoffs seem driven by a desire to placate the stock market, though, so it's no surprise that these offers fell on deaf ears.
[...] Making Google honor its previous leave agreements isn't just about employees getting paid when they have medical or family issues; it's also about having continual medical care when they need it most. As part of Google's (seemingly discarded) plan to offer employees every perk imaginable, the company has on-site medical facilities that many employees make use of.
While employees' severance packages might come with a few more months of health insurance, being fired means instantly losing access to Google's facilities. If that's where a laid-off Googler's primary care doctor works, that person is out of luck, and some employees told CNBC they lost access to their doctors the second the layoff email arrived. Employees on leave also have a lot to deal with. One former Googler, Kate Howells, said she was let go by Google from her hospital bed shortly after giving birth. She worked at the company for nine years.
Read more of this story at SoylentNews.
08:48
New Bad Magic APT used CommonMagic framework in the area of Russo-Ukrainian conflict Security Affairs
Threat actors are targeting organizations located in Donetsk, Lugansk, and Crimea with a previously undetected framework dubbed CommonMagic.
In October 2022, Kaspersky researchers uncovered a malware campaign aimed at infecting government, agriculture and transportation organizations located in the Donetsk, Lugansk, and Crimea regions with a previously undetected framework dubbed CommonMagic.
Researchers believe that threat actors use spear phishing as an initial attack vector, the messages include an URL pointing to a ZIP archive hosted on a web server under the control of the attackers. The archive contained two files, a decoy document (i.e. PDF, XLSX and DOCX versions) and a malicious LNK file with a double extension (i.e., .pdf.lnk) used to start the infection and deploy the PowerMagic backdoor.
Kaspersky attributes the attack to a new APT group operating in the area of Russo-Ukrainian conflict and tracked as Bad magic.
The experts noticed that TTPs observed during this campaign have no direct link to any known campaigns.
PowerMagic is a PowerShell backdoor that executes arbitrary commands sent by C2, then it exfiltrates data to cloud services like Dropbox and Microsoft OneDrive.
When started, the backdoor creates a m...
08:21
About channel capacity and sub-channels Daniel Estvez
The Shannon-Hartley theorem describes the maximum rate at which information can be sent over a bandwidth-limited AWGN channel. This rate is called the channel capacity. If \(B\) is the bandwidth of the channel in Hz, \(S\) is the signal power (in units of W), and \(N_0\) is the noise power spectral density (in units of W/Hz), then the channel capacity \(C\) in units of bits per second is\[C = B \log_2\left(1 + \frac{S}{N_0B}\right).\]
Let us now consider that we make \(n\) sub-channels, by selecting \(n\) disjoint bandwidth intervals contained in the total bandwidth of the channel. We denote the bandwidth of these sub-channels by \(B_j\), \(j = 1,\ldots,n\). Clearly, we have the constraint \(\sum_{j=1}^n B_j \leq B\). Likewise, we divide our total transmit power \(S\) into the \(n\) sub-channels, allocating power \(S_j\) to the signal in the sub-channel \(j\). We have \(\sum_{j=1}^n S_j = S\). Under these conditions, each sub-channel will have capacity \(C_j\), given by the formula above with \(B_j\) and \(S_j\) in place of \(B\) and \(S\).
The natural question regards using the \(n\) sub-channels in parallel to transmit data: what is the maximum of the sum \(\sum_{j=1}^n C_j\) under these conditions and how can it be achieved? It is probably clear from the definition of channel capacity that this sum is always smaller or equal than \(C\). After all, by dividing the channel into sub-channels we cannot do any better than by considering it as a whole.
People used to communications theory might find intuitive that we can achieve \(\sum_{j=1}^n C_j = C\), and that this happens if and only if we use all the bandwidth (\(\sum_{j=1}^n B_j = B\)) and the SNRs of the sub-channels, defined by \(S_j/(N_0B_j)\), are all equal, so that \(S_j = SB_j/B\). After all, this is pretty much how OFDM and other channelized communication methods work. In this post I give an easy proof of this result.
First of all, since the expression \(B_j \log_2(1+S_j/(N_0B_j))\) is increasing in \(B_j\), if \(\sum_{j=1}^nB_j < B\), then we can increase some of the values of the \(B_j\) until we have the equality, increasing as a consequence the sum \(\sum_{j=1}^n C_j\). Therefore, we can restrict ourselves to the case when \(\sum_{j=1}^nB_j = B\).
Now we consider that \(B_j\) are fixed and apply Langrange multipliers to find the extrema of the function\[f(S_1,\ldots,S_n) = \sum_{j=1}^n B_j \log\left(1 + \frac{S_j}{N_0B_j}\right)\]subject to the condition \(\sum_{j=1}^n S_j = S\). This gives the system of equations\[B_j\left(1+\frac{S_j}{N_0B_j}\right)^{-1}\frac{1}{N_0B_j} + \lambda = 0,\]where \(\lambda\) is the Langrange multiplier. These equations can be rearranged as\[\frac{S_j}{B_j} = -N_0 \frac{1}{\lambda}.\] It follows that the quotients \(S_j/B_j\) are all equal.
Now we write \(S_j/...
07:13
Trial of 2016 Twitter Troll to Test Limits of Online Speech SoylentNews
The goal, federal prosecutors said, was to suppress votes for Ms. Clinton by persuading her supporters to falsely believe they could cast presidential ballots by text message:
The misinformation campaign was carried out by a group of conspirators, prosecutors said, including a man in his 20s who called himself Ricky Vaughn. On Monday he will go on trial in Federal District Court in Brooklyn under his real name, Douglass Mackey, after being charged with conspiring to spread misinformation designed to deprive others of their right to vote.
"The defendant exploited a social media platform to infringe one of the most basic and sacred rights guaranteed by the Constitution," Nicholas L. McQuaid, acting assistant attorney general for the Justice Department's Criminal Division, said in 2021 when charges against Mr. Mackey were announced.
Prosecutors have said that Mr. Mackey, who went to Middlebury College in Vermont and said he lived on the Upper East Side of Manhattan, used hashtags and memes as part of his deception and outlined his strategies publicly on Twitter and with co-conspirators in private Twitter group chats.
[...] Mr. Mackey's trial is expected to provide a window into a small part of what the authorities have described as broad efforts to sway the 2016 election through lies and disinformation. While some of those attempts were orchestrated by Russian security services, others were said to have emanated from American internet trolls.
Just a few days ago the trial was delayed after a witness was allegedly intimidated into withdrawing his testimony.
Related:
- The Strong Case That Twitter Censorship Violates California's Civil Rights Laws
- Twitter Fights Trolls, Invites Trolls, and Trolls U.S.
Read more of this story at SoylentNews.
07:00
3D-Printed Parts Dont Slow Down This Speedy Printer Hackaday

Truth be told, we generally find speed sports to be a little boring. Whether its cars going around in circles for hours on end or swimmers competing to be a few milliseconds faster than everyone else, we just dont feel the need for speed. Unless, of course, youre talking about speedy 3D printers like The 100, which claims to produce high-quality prints in a tenth the time of an ordinary printer. In that case, youve got our full attention.
What makes [Matt the Printing Nerd]s high-speed printer interesting isnt the fact that it can do a Speedboat Run printing a standard Benchy model in less than six minutes. Plenty of printers can do the same thing much, much faster. The impressive part is that The 100 does it with a 3D-printed frame. In fact, most of the printers parts are 3d printed, a sign...
06:55
RIAA Hunts Pre-Release Music Pirates Behind UnreleasedSounds.gg TorrentFreak
 Human beings have a tendency to want things they cant
have. A modest interest in a particular item or activity can
inexplicably soar when its recognized as rare or unavailable. When
strictly forbidden, even regular fruit can prove irresistible.
Human beings have a tendency to want things they cant
have. A modest interest in a particular item or activity can
inexplicably soar when its recognized as rare or unavailable. When
strictly forbidden, even regular fruit can prove irresistible.
Spotify offers 100 million tracks to hear right now, including the vast majority of the greatest pieces of music ever written. Yet for some, the lure of an unreleased track can outweigh every single one of them; unattainable, forbidden and rare is a potent mix and may explain why pirates are paying silly money for leaked, pirated music.
Dozens of Avicii Leaks
When producer Tim Bergling passed away in 2018, the prospect of never hearing a new Avicii track was suddenly very real. Two albums and various tracks were eventually released, but then PAB happened.
In 2022 the Public Avicii Buy Server (PAB) channel on Discord became a hot location for unreleased Avicii tracks. Faced with having to pay for them, fans worked to groupbuy a long list of Avicii tracks including Lets Roll and Lethal Drug V2 which featured Chris Martin & SZA.
Sources Unknown But Some Files Were Apparently Stolen
How the music was obtained isnt clear; some believed the PAB seller bought the tracks and then sold them to fellow Avicii fans at cost price. Others spoke of hacked accounts and big profits. Late 2022, after another PAB release (Island) appeared online, a Reddit user jumped in to comment
Hey guys! My name is Jonas Wallin and my alias is The High, the music producer posted on Reddit.
I wrote Island and its coming out soon in fact. The leaked vocals are mine, my vocal stems. Its the same with Loving Feeling. I would recommend you to not pay someone for these files since they were stolen from me. Thanks.
RIAA Investigates Unreleased Sounds
According to various sources, the track made its way to PAB via a private leak site called Unreleased Sounds. Its unclear whether the RIAAs member labels have any interests in the dozens of Avicii tracks leaked so far, but they do want to know who runs the 15/...
06:30
PCMCIA/CardBus To USB Drivers On The Chopping Block With Linux 6.4 Phoronix
Earlier this month I wrote about Linux 6.4 planning to start removing old, unused, and unmaintained PCMCIA drivers. That began with the PCMCIA "char" drivers queued for removal in this upcoming kernel cycle and now joining them are removing two PCMCIA/CardBus to USB adapter drivers...
06:18
New ShellBot bot targets poorly managed Linux SSH Servers Security Affairs
New ShellBot DDoS bot malware, aka PerlBot, is targeting poorly managed Linux SSH servers, ASEC researchers warn.
AhnLab Security Emergency response Center (ASEC) discovered a new variant of the ShellBot malware that was employed in a campaign that targets poorly managed Linux SSH servers.
The ShellBot, also known as PerlBot, is a Perl-based DDoS bot that uses IRC protocol for C2 communications.
The ShellBot performs SSH bruteforce attacks on servers that have port 22 open, it uses a dictionary containing a list of known SSH credentials.
The ShellBot malware strains that are going to be covered in this post are believed to have been installed after threat actors used account credentials that have been obtained through the use of scanners and SSH BruteForce malware on target systems. reads the ASECs report. After scanning systems that have operational port 22s, threat actors search for systems where the SSH service is active and uses a list of commonly used SSH account credentials to initiate their dictionary attack.
Below is a list of the account credentials used by ShellBot operators to compromise the target servers:
| User | Password |
|---|---|
| deploy | password |
| hadoop | hadoop |
| oracle | oracle |
| root | 11111 |
| root | Passw0rd |
| ttx | ttx2011 |
| ubnt | ubnt |
The researchers categorized the ShellBot into three different groups since threat actors can create their own versions: LiGhTs Modded perlbot v2, DDoS PBot v2.0, and PowerBots (C) GohacK.
LiGhTs Modded perlbot v2 and DDoS PBot v2.0 supports multiple DDoS attack commands using HTTP, TCP, and UDP protocols. The PowerBots (C) GohacK supports backdoor features, including reverse shell and file downloading capabilities.
The researchers recommend using strong passwords for admin accounts and changing them periodically to protect the Linux server from brute force attacks and dictionary attacks. They also recommend keeping the servers up to date and using security programs.
If ShellBot is installed, Linux servers can be used as DDoS Bots for DDoS attacks against specific targets after receiving a command from the threat actor. Moreover, the threat actor could use various other backdoor features to install additional malware or launch different t...
05:45
Ferrari Discloses Ransomware Attack; Refuses to Pay Ransom HackRead | Latest Cybersecurity and Hacking News Site
Ferrari, the renowned Italian luxury car manufacturer, suffered a cyber incident that compromised the companys client data. According
This is a post from HackRead.com Read the original post: Ferrari Discloses Ransomware Attack; Refuses to Pay Ransom
05:38
Manager, Information System Security Toronto News The Citizen Lab
The Citizen Lab, Munk School of Global Affairs & Public Policy, University of Toronto, is hiring a Manager, Information Systems Security. Reporting to the Director of Administration, Citizen Lab and working under the general direction of the Director, Citizen Lab in coordination with the University of Torontos Chief Information Security Officer (CISO), you will be responsible for working with Information Technology staff and resources at the Citizen Lab and the wider University to minimize the risk of compromising information, data, servers, and server-based applications. You will assume responsibility for the strategic and tactical planning and provision of systems security, confidentiality, privacy, and risk management in the areas of systems administration, server and service design, implementation, operation, and support.
The Manager, Information Systems Security acts as a project manager for IT projects that fall within areas related to Information Security or projects, which include confidential and restricted information following the security standards and best practices for Identity and Access Management, Information Disclosure, Information Integrity, Business Continuity and Protection of Privacy.
Who you are:
- Expert level understanding of the Linux operating systems at both server and client level.
- Comprehensive knowledge of TCP/IP networking and client-server architecture and protocols.
- Strong understanding of network configuration, hardware and next-gen firewall/IPS technologies (Cisco ASA, Juniper, Fortinet, Palo Alto)
- Expert level understanding of the following access control technologies LDAP and Kerberos.
- Expert knowledge of Virtual Private Networks (VPNs). Expert knowledge of Encryption technologies at network, file and file-system levels.
- Strong understanding of cryptographic certificates and the operation of certificate authorities.
- Excellent communication, instruction, and presentation skills.
- Able to describe a variety of complex technical concepts or policies to users and senior leadership at all technical experience levels and to deliver security awareness and education content to faculty, staff and students.
About us
The Citizen Lab is an interdisciplinary laboratory based at the Munk School of Global Affairs & Public Policy, University of Toronto, focusing on research, development, and high-level strategic policy and legal engagement at the intersection of information and communication technologies, human rig...
05:05
Raja Koduri Departing Intel To Start New Software Company Phoronix
Prominent Intel leader Raja Koduri who currently serves as the company's Chief Architect is leaving to focus on a new software start-up...
05:00
IEEE Xplore Adds Ericsson Technology Review to its Collection IEEE Spectrum

The Ericsson Technology Review is now available in the IEEE Xplore Digital Library. The monthly magazine provides insights on emerging innovations that are shaping the future of information and communication technology.
The publication, which dates back to 1924, is published by Ericsson, a multinational networking and telecommunications company based in Stockholm.
An IEEE Xplore subscription is not required to access the freely available research papers.
IEEE is a respected organization, and Ericsson has the ambition to reach even further into the academic community and research institutes with our cutting-edge research and development, says Erik Ekudden, the companys chief technology officer. We believe that IEEE Xplore is a good channel for this target group.
The Review in IEEE Xplore includes newly published articles plus those from the magazines archives going back to 2020, according to Naveen Maddali, senior product manager of content partnerships for IEEE Global Products and Marketing. There are now more than 80 articles in the digital library. Topics include computing, robotics, and signal processing.
The Ericsson Technology Review is a valuable publication for anyone using IEEE Xplore, Maddali says. Theres a lot of useful content on telecommunications and communications for all types of the digital librarys users.
Ericsson has the ambition to reach even further into the academic community and research institutes with our cutting-edge research and development. IEEE Xplore is a good channel for this target group.
Maddali says the project was volunteer-driven. The effort was supported by Ericssons CTO office following an initiative by IEEE Senior Member Glenn Parsons, principal standards advisor with Ericsson Canada. He was a member of the IEEE Public...
04:56
Labor Data Reveals Shocking Drop In Workplace Attendance Following Vax Campaign cryptogon.com
Via: ZeroHedge: In their latest analysis, Dowd and crew use data from the Bureau of Labor Statistcs (BLS) to reveal a shocking spike in both employee absence and lost worktime rates, which they believe is due to vaccines either from primary vaccine injuries, or because of weakened immune systems due to the jab, and []
04:41
ChatGPT Bug Exposes Conversation History Titles HackRead | Latest Cybersecurity and Hacking News Site
Are you wondering why your ChatGPT conversation history has been unavailable since yesterday? Well, here is why!
This is a post from HackRead.com Read the original post: ChatGPT Bug Exposes Conversation History Titles
04:31
700 NYPD Riot Cops Mobilized, Steel Barriers Deployed Ahead Of Potential Trump Arrest cryptogon.com
Via: ZeroHedge: The New York Police Department (NYPD) has mobilized 700 riot cops and deployed steel barricades around the Manhattan Criminal Court in anticipation of civil disorder, should the Manhattan District Attorneys office order the arrest of former President Donald Trump, following a potential grand jury indictment for allegedly paying a former porn star for []
04:25
Germanys Lobbyists-Infested Government Sponsors the War on Ukraine via the European Patent Office (EPO) Techrights

EPO President Antnio Campinos does not want anyone to know
that
the EPO sponsors Putin's war on Ukraine (an
open secret); the
German government protects him no matter what
Summary: The chief UPC judge is basically seeking to break the law (and violate constitutions, conventions etc.) to start a kangaroo court while dodging real courts, just like Vladimir Putin does
04:22
NASA's Commercial Partner to Visit the Far Side of the Moon SoylentNews
NASA's commercial partner to visit the far side of the moon:
NASA has big plans for the moon. From sending the first crewed mission to land on its surface in 50 years to setting up a space station in orbit, the agency has multiple missions planned for exploring our planet's satellite. These include partnerships with a number of private companies as well as NASA-developed projects, such as under the Commercial Lunar Payload Services, or CLPS, program which will contract out the transportation of small payloads to the moon.
This week, NASA announced it has selected the company Firefly Aerospace to develop a commercial lander for the far side of the moon. The lander, called Blue Ghost, will be used to deliver several NASA payloads to the moon, including a radio observation mission which is placed on the far side of the moon to minimize the radio noise coming from Earth. This natural radio quiet zone will let the Lunar Surface Electromagnetics Experiment-Night (LuSEE-Night) telescope detect faint radio waves from an early period of the universe known as the cosmic dark ages.
[...] As well as LuSEE-Night, Firefly will also be tasked with carrying a communications and data relay satellite called Lunar Pathfinder, which is a collaboration between NASA and the European Space Agency, and which will be deployed into orbit before the lander sets down on the moon's surface. In addition, the NASA User Terminal payload will assist with communications, and there will be up to seven other payloads from private companies included as well.
[...] Firefly had a troubled start to its orbital ambitions when its first attempt to reach orbit with its Alpha rocket in September 2021 ended in an explosive failure. But a year later, its second attempt at orbital launch was successful and the rocket was able to deploy its orbital payloads.
The aim is for Firefly to launch its lunar mission, Blue Ghost Mission 1, in 2024.
Read more of this story at SoylentNews.
04:00
Intel CET Shadow Stack Support Set To Be Introduced With Linux 6.4 Phoronix
After being in development for years, Intel's shadow stack support is set to be merged for the upcoming Linux 6.4 cycle. The shadow stack support is part of Intel's Control-flow Enforcement Technology (CET) security functionality...
03:56
[Meme] The Meme That Team UPC (the Collusion to Break the European Laws, for Profit) Threats to Sue Us For Techrights
Cannot make memes that highlight crimes of the EPO; thats illegal [1, 2]

Can Mr. Campinos rely on copyright nazis to silence critics of the
Unitary Patent ploy?
Summary: Antnio Campinos and Team UPC are intimidating people who simply point out that the Unified Patent Court (UPC) is illegal and Klaus Grabinksi, shown above, strives to head a de facto kangaroo court in violation of constitutions and conventions (the UK does not and cannot ratify; Ireland hasnt even held a referendum on the matter)
03:27
Microsoft is Sacking People Every Month This Year, Even Managers (While Sponsored Media Produces Endless Chatbot Chaff) Techrights
And its already happening, with lots more rumoured for tomorrow:
Summary: Lots of Microsoft layoffs lately and so-called journalists arent reporting these; theyre too busy running sponsored puff pieces for Microsoft, usually fluff along the hey hi (AI) theme
03:01
Not applying updates? Youre doing it wrong Linux.com
All your excuses for not doing updatesfrom fear of downtime to concerns about testingare wrong.
Read More at Enable Sysadmin
The post Not applying updates? Youre doing it wrong appeared first on Linux.com.
03:01
3 Months Late Sirius Open Source Finally Deletes Us From the Fraudulent Meet the Team Page (But Still Lists Many People Who Left Years Ago!) Techrights
Compare to this.
Summary: Amid fraud investigations the management of Sirius Open Source finally removed our names from its Meet the Team page (months late); but it left in the page about half a dozen people who left the company years ago, so its just lying to its clients about the current situation
02:59
Version 20 of the Java SE platform has been released. See the features list for an overview of the big additions, or the release notes for the details.
02:59
[$] Hopes and promises for open-source voice assistants LWN.net
At the end of 2022, Paulus Schoutsen declared 2023 "the year of voice" for Home Assistant, the popular open-source home-automation project that he founded nine years ago. The project's goal this year is to let users control their home with voice commands in their own language, using offline processing instead of sending data to the cloud. Offline voice control has been the holy grail of open-source home-automation systems for years. Several projects have tried and failed. But with Rhasspy's developer Mike Hansen spearheading Home Assistant's voice efforts, this time things could be different.
02:47
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Jakub Wilk on Mar 21
* Hanno Bck <hanno () hboeck de>, 2023-03-19 09:18:I think that should be fine.
02:36
Amid Fraud at Sirius Open Source CEO Deletes His Recent (This Month) Past With the Company Techrights
One week ago (March 14th):
Today (he also deleted clients of Sirius so as to dodge association with the company; the names are redacted):
Summary: Not only did the Sirius Open Source CEO purge all mentions of Sirius from his Microsoft LinkedIn account; hes racing against the clock as crimes quickly become a legal liability
02:27
2022 Zero-Day exploitation continues at a worrisome pace Security Affairs
Experts warn that 55 zero-day vulnerabilities were exploited in attacks carried out by ransomware and cyberespionage groups in 2022.
Cybersecurity firm Mandiant reported that ransomware and cyberespionage groups exploited 55 zero-day flaws in attacks in the wild.
Most of the zero-day vulnerabilities were in software from Microsoft, Google, and Apple.
The figures show a decrease from 2021, but experts pointed out that they represent almost triple the number from 2020.
The majority of the zero-day vulnerabilities were exploited by China-linked threat actors as part of their cyberespionage campaigns.
The researchers reported that only four zero-day vulnerabilities were exploited by financially motivated threat actors, with 75% of these instances linked to ransomware attacks.
Products from Microsoft, Google, and Apple made up the majority of zero-day vulnerabilities in 2022, consistent with previous years. The most exploited product types were operating systems (OS) (19), followed by browsers (11), security, IT, and network management products (10), and mobile OS (6). reads the report published by Mandiant.
According to the report, 13 zero-days in 2022 were exploited by cyber espionage groups, a figure that is consistent with 2021. Seven zero-days (...
02:23
Did We Just Change Animation Forever? Lifeboat News: The Blog

ANYONE can make a cartoon with this groundbreaking technique. Want to learn how? We made a ONE-HOUR, CLICK-BY-CLICK TUTORIAL on http://www.corridordigital.com/
Watch the full ROCK PAPER SCISSORS anime on Corridor https://youtu.be/GVT3WUa-48Y
This project has been a huge labor of love, and it is due to the amazing open-source community that we have this technology available to us. We hope that by sharing our discoveries and techniques that we can help push this technology forward for everyone. If you want to dip your toes into this tech, there are many amazing online communities ready to help teach you, including ours!
With Your Support, We Can Make More!
This project exists because of the amazing members of
CorridorDigital, our INDEPENDENT STREAMING PLATFORM. All
memberships begin with a 14-Day Free Trial and you can Cancel
Anytime. Consider becoming a member yourself! http://www.corridordigital.com/learn-more.
Anime Rock, Paper, Scissors Shirt?!
Available only until March 6th, we have a limited-edition Anime
Rock Paper Scissors t-shirt and longsleeve design to celebrate this
release. Check it out here! http://corridordigital.store/
Design by Kendrra Thoms https://kendrrathoms.com/
Gear Used
Puget Systems Computers: http://bit.ly/PC_Puget_Workstations.
Lighting by Aputure: http://bit.ly/CORRIDOR_LIGHTS
OpenJDK Java 20 Released With Latest Vector API, Scoped Values Phoronix
Promoted to general availability (GA) status today is the OpenJDK Java 20 update with a number of new features...
02:22
Humans predicted to achieve immortality within the next 8 years Lifeboat News: The Blog
If its always been your dream to have the ability to live forever, you may be in luck as scientists believe we are just seven years away from achieving immortality. Futurist and computer scientist Ray Kurzweil has made predictions on when the human race will be able to live forever and when artificial intelligence (AI) will reach the singularity, and he believes it could be possible as early as 2030.
02:19
02:09
Rumours of More Microsoft Layoffs Tomorrow (Including Managers!), Probably Azure Again (Many Azure Layoffs Every Year Since 2020) Techrights
As of a fortnight ago: (with some comments since then; expect the media to not mention Microsofts layoffs and instead focus on Microsofts paid-for spam about inane chatbots and hey hi or AI)
Summary: Amazon is laying off AWS staff and Microsoft has been laying off Azure staff for 3 years already, including this year, so it seems like the clown computing bubble is finally bursting
02:08
Breach Forums to Remain Offline Permanently HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
One of the Breach Forums administrators who goes by the alias Baphomet has decided to shut down the forum permanently.
This is a post from HackRead.com Read the original post: Breach Forums to Remain Offline Permanently
02:01
New 'Bad Magic' Cyber Threat Disrupts Ukraine's Key Sectors Amid War The Hacker News
Amid the ongoing war between Russia and Ukraine, government, agriculture, and transportation organizations located in Donetsk, Lugansk, and Crimea have been attacked as part of an active campaign that drops a previously unseen, modular framework dubbed CommonMagic. "Although the initial vector of compromise is unclear, the details of the next stage imply the use of spear phishing or similar
01:40
RADV Lands Another Feature For Helping VKD3D-Proton Tier 3 Functionality Phoronix
Samuel Pitoiset of Valve's Linux graphics driver team has landed another Radeon Vulkan "RADV" driver improvement today for Mesa 23.1-devel to further along its VKD3D-Proton capabilities for enjoying Windows Direct3D 12 games on Linux with Steam Play...
01:36
Low-Cost Device Can Measure Air Pollution Anywhere SoylentNews
Open-source tool from MIT's Senseable City Lab lets people check air quality, cheaply.
Air pollution is a major public health problem: The World Health Organization has estimated that it leads to over 4 million premature deaths worldwide annually. Still, it is not always extensively measured. But now an MIT research team is rolling out that could enable people to track air quality more widely.
The detector, called Flatburn, can be made by 3D printing or by ordering inexpensive parts. The researchers have now tested and calibrated it in relation to existing state-of-the-art machines, and are publicly releasing all the information about it - how to build it, use it, and interpret the data.
The Flatburn concept at Senseable City Lab dates back to about 2017, when MIT researchers began prototyping a mobile pollution detector, originally to be deployed on garbage trucks in Cambridge, Massachusetts. The detectors are battery-powered and rechargable, either from power sources or a solar panel, with data stored on a card in the device that can be accessed remotely.
In both cases, the detectors were set up to measure concentrations of fine particulate matter as well as nitrogen dioxide, over an area of about 10 meters. Fine particular matter refers to tiny particles often associated with burning matter, from power plants, internal combustion engines in autos and fires, and more.
"The goal is for community groups or individual citizens anywhere to be able to measure local air pollution, identify its sources, and, ideally, create feedback loops with officials and stakeholders to create cleaner conditions," says Carlo Ratti, director of MIT's Senseable City Lab.
Journal Reference:
An Wang, Yuki Machida, Priyanka deSouza, Simone Mora, Tiffany Duhl,
Neelakshi Hudda, John L. Durant, Fbio Duarte, Carlo Ratti,
Leveraging machine learning algorithms to advance low-cost air
sensor calibration in stationary and mobile settings [open],
Atmospheric Environment, Volume 301, 2023, 119692, ISSN 1352-2310,
DOI: https://doi.org/10.1016/j.atmosenv.2023.119692
Read more of this story at SoylentNews.
01:33
[Meme] EPOs Management Brainstorm Techrights

Team Campinos, led by a fake socialist and
pathological liar
Summary: The story behind a misleading slogan told above
01:32
Multiple vulnerabilities in Jenkins plugins Open Source Security
Posted by Daniel Beck on Mar 21
Jenkins is an open source automation server which enables developers aroundthe world to reliably build, test, and deploy their software.
The following releases contain fixes for security vulnerabilities:
* JaCoCo Plugin 3.3.2.1
* OctoPerf Load Testing Plugin 4.5.1, 4.5.2, and 4.5.3
* Pipeline Aggregator View Plugin 1.14
* Role-based Authorization Strategy Plugin 587.588.v850a_20a_30162
Additionally, we announce unresolved security issues in...
01:24
The Photo Ops Festival of the Funky President Antnio Campinos and Revolt From the Patent Examiners Whom He Perpetually Oppresses Techrights
Video download link | md5sum
ae22085fbb10ba705b2660a2b3208158
EPO Site Survey
Creative Commons Attribution-No Derivative Works 4.0
Summary: European Patents are being granted for no reason other than application and renewal fees, awarding European monopolies to companies that arent even European (only about a third are actually European); staff of the EPO is fed up as it regards or views all this as an extreme departure from the EPOs mission (and its also outright illegal)
THE EPOs official Web site has been full of fluff, misdirection, and promotion of illegal things (which are nonetheless lobbied for by multinational oligarchy, hence no legal consequences for such promotion). Benot Battistelli and Antnio Campinos have basically trashed the site, turning it into a self-serving shrine that promotes shallow politics, not science. The latest publications there are discussed in the video above, but meanwhile theres some news from EPO staff about Bringing Teams Together. To quote a publication dated yesterday:
20 March 2023
su23015cp 0.2.1 0.2.4 4.4Bringing Teams Together (BTT)
Dear colleagues,
Bringing Teams Together (BTT) is becoming a reality, despite the many questions and objections that have been formulated by your Staff Representation1.
From the echos received, it seems BTT will be implemented by the line managers in all possible interpretations and variations, according to the mood and inspiration of the day2.
We would like to get an idea of what is happening in the different teams: what, if any, policy or principle is used to allocate fixed workplaces to staff. Bear in mind that the administration has given the 3-day rule as a guiding principle for the allocation of fixed workplaces3...
01:04
Slice and Save Costs with Open Packet Broker Linux.com
Enterprise data centers continuously monitor network traffic to improve performance, provide better customer experience, and identify threats. All these appliances or tools require only a portion of the network payload to meet the monitoring requirements. Modern Network Packet brokers use Packet truncation technique to optimize the processing of network traffic which involves the removal of portions of network packets that are not needed for analysis.
Need for Packet Truncation
Reduce Storage: Network traffic payload can be very large (64 to 9216), and storing everything will be expensive. Packet truncation helps reduce the amount of data that needs to be stored by removing irrelevant or redundant information from packets.
Reduce CPU Cycles: Truncated packets require less processing to analyze, which can improve the overall speed and performance of the tools.
Simplify Analysis: Network administrators can easily identify network performance issues more quickly and efficiently since truncated packets have the relevant portions of the packet.
Improve Security: By removing sensitive information from the payload, security can be improved by limiting the exposure of confidential data.
Open Packet Broker for Truncation
Aviz Open Packet Broker industry first Packet broker solution built on Open Networking NOS SONiC supporting truncation on commodity ASICs supporting wire-speed packet truncation. Open Packet broker truncation has the following capabilities.
- Packet Truncation based on custom offsets (48 bytes to 4094 bytes).
- VLAN tag insertion for truncated packets for different tooling purposes.
- Load Balance across tools for optimal processing
Packet Truncation or slicing will allow only the user-defined byte from an incoming packet, and the remaining bytes are discarded. This helps in reducing the quantity of data processed on the tool port.

01:03
Security updates for Tuesday LWN.net
Security updates have been issued by Debian (apache2), Oracle (firefox, nss, and openssl), Slackware (curl and vim), SUSE (dpdk, firefox, grafana, oracleasm, python-cffi, python-Django, and qemu), and Ubuntu (ruby2.7, sox, and tigervnc).
01:00
Vinyl Sales Ran Circles Around CDs in 2022 Hackaday

How do you take your music these days? For those in Camp Tangible, it seems our ranks are certainly growing, and in the analog direction. For the first time since 1987, vinyl record sales have outperformed CD sales in the US, according to a new report. The CD, which saved us all from the cassette, was a digital revolution in music. But for some, the love was lost somewhere among the ones and zeroes.
Those who prefer pure analog troughs of sound cut into wax have never given up on vinyl, and the real ones probably gobbled up a bunch of it in the 90s when everybody was CD-crazy. But mind you these arent used vinyl sales were talking about, which means that enough new vinyl has to have been readily available for purchase for quite some time now. Although it doesnt really seem like that long, new vinyls been back for almost 20 years and according to the report, 2022 was the 16th consecutive year of growth for record sales.
So Why Vinyl?
Nostalgia aint what it used to be, but there was a time in my 1980s childhood when vinyl was all this scribe had to listen to. I have historically been a bit slow to adopt new music formats I didnt have a CD player until 1998, and it was given to...
00:36
Crypto ATM Manufacturer General Bytes Suffers $1.5m Bitcoin Theft HackRead | Latest Cybersecurity and Hacking News Site
The company has disclosed the wallet addresses and three IP addresses used by the attacker in the hack.
This is a post from HackRead.com Read the original post: Crypto ATM Manufacturer General Bytes Suffers $1.5m Bitcoin Theft
00:23
Fourier Transformations Reveal How AI Learns Complex Physics Lifeboat News: The Blog
One of the oldest tools in computational physics a 200-year-old mathematical technique known as Fourier analysis can reveal crucial information about how a form of artificial intelligence called a deep neural network learns to perform tasks involving complex physics like climate and turbulence modeling, according to a new study.
The discovery by mechanical engineering researchers at Rice University is described in an open-access study published in the journal PNAS Nexus, a sister publication of the Proceedings of the National Academy of Sciences.
This is the first rigorous framework to explain and guide the use of deep neural networks for complex dynamical systems such as climate, said study corresponding author Pedram Hassanzadeh. It could substantially accelerate the use of scientific deep learning in climate science, and lead to much more reliable climate change projections.
00:00
Metal-Detecting Drone Could Autonomously Find Landmines IEEE Spectrum

Metal detecting can be a fun hobby, or it can be a task to be completed in deadly earnestif the buried treasure youre searching for includes landmines and explosive remnants of war. This is an enormous, dangerous problem: Something like 12,000 square kilometers worldwide are essentially useless and uninhabitable because of the threat of buried explosives, and thousands and thousands of people are injured or killed every year.
While there are many different ways of detecting mines and explosives, none of them are particularly quick or easy. For obvious reasons, sending a human out into a minefield with a metal detector is not the safest way of doing things. So, instead, people send anything else that they possibly can, from machines that can smash through minefields with brute force to well-trained rats that take a more passive approach by sniffing out explosive chemicals.
Because the majority of mines are triggered by pressure or direct proximity, a drone seems like it would be the ideal way of detecting them non-explosively. However, unless youre only detecting over a perfectly flat surface (and perhaps not even then) your detector wont be positioned ideally most of the time, and you might miss something, which is not a viable option for mine detection.
But now a novel combination of a metal detector and a drone with five degrees of freedom is under development at the Autonomous Systems Lab at ETH Zurich. It may provide a viable solution to remote landmine detection, by using careful sensing and localization along with some twisting motors to keep the detector reliably close to the ground.
The really tricky part of this whole thing is making sure that the metal detector stays at the correct orientation relative to the ground surface so theres no dip in its effectiveness. With a conventional drone, this wouldnt work at all, because every time the drone moves in any direction but up or down, it has to tilt, which i...
Tuesday, 21 March
23:50
Open-Source NVIDIA Vulkan Driver "NVK" Begins Running Game While Using GSP Firmware Phoronix
Red Hat developer David Airlie has shown off the progress being made on bringing up not only the open-source Mesa NVIDIA Vulkan driver "NVK" but doing so while making use of the NVIDIA GPU System Processor (GSP) firmware that ultimately is needed for being able to deliver better open-source driver support and performance...
23:26
Asahi Linux Continues Making Progress On Apple Silicon Graphics, Promising OpenGL Speed Phoronix
Asahi Linux developer Asahi Lina has posted an update on the ongoing work bringing up their Rust-written DRM kernel driver along with the AGX Gallium3D Mesa OpenGL driver as well as progress towards the in-development Vulkan driver too...
23:09
Internet Archives Copyright Battle with Book Publishers Nears Climax TorrentFreak
 In 2020, publishers Hachette, HarperCollins, John Wiley
and Penguin Random House
sued the Internet Archive (IA) for copyright infringement,
equating its Open Library to a pirate site.
In 2020, publishers Hachette, HarperCollins, John Wiley
and Penguin Random House
sued the Internet Archive (IA) for copyright infringement,
equating its Open Library to a pirate site.
IAs library is a non-profit organization that scans physical books, which can then be lent out to patrons in an ebook format.
Staying true to the centuries-old library concept, only one patron at a time can get a copy. These restrictions were temporarily loosened at the height of the Covid epidemic when IA launched the National Emergency Library.
Mass Copyright Infringement or Fair Use?
The publishers see IAs library as a rogue operation that engages in willful mass copyright infringement, directly damaging their bottom line. As such, they want it permanently taken down.
Without any license or any payment to authors or publishers, IA scans print books, uploads these illegally scanned books to its servers, and distributes verbatim digital copies of the books in whole via public-facing websites, their complaint reads.
The publishers are not against libraries per se, nor do they object to ebook lending. When lending digital content, authorized libraries typically obtain a license or negotiate specific terms. The Internet Archive has no such license.
The Internet Archive wholeheartedly disagrees with the copyright infringement allegations. Stressing that the library offers a vital service, Internet Archives defense centers on the legal concept of fair use.
The Archive states that making a digital copy of a physical book transforms the original work before it is loaned to one patron at a time. That would qualify as fair use, they argue, especially since there is no profit motive.
Another factor in favor of fair use is the fact that there are numerous benefits to the public at large. There is also no evidence to show that the book publishers sales or traditional licensing revenues were impacted.
New York Court Hearing
Over the past two-and-a-half years, the parties have gone back and forth in court, disputing each others arguments. This eventually resulted in contrasting motions for summary judgment, with both sides hoping for a ruling in their favor ahead of the trial.
Yesterday,...
23:08
Xen Security Advisory 429 v3 (CVE-2022-42331) - x86: speculative vulnerability in 32bit SYSCALL path Open Source Security
Posted by Xen . org security team on Mar 21
Xen Security Advisory CVE-2022-42331 / XSA-429x86: speculative vulnerability in 32bit SYSCALL path
UPDATES IN VERSION 3
====================
Public release.
ISSUE DESCRIPTION
=================
Due to an oversight in the very original Spectre/Meltdown security work
(XSA-254), one entrypath performs its speculation-safety actions too
late.
In some configurations, there is an...
23:05
Xen Security Advisory 428 v3 (CVE-2022-42333,CVE-2022-42334) - x86/HVM pinned cache attributes mis-handling Open Source Security
Posted by Xen . org security team on Mar 21
Xen Security Advisory CVE-2022-42333,CVE-2022-42334 / XSA-428x86/HVM pinned cache attributes mis-handling
UPDATES IN VERSION 3
====================
Public release.
ISSUE DESCRIPTION
=================
To allow cachability control for HVM guests with passed through devices,
an interface exists to explicitly override defaults which would
otherwise be put in place. While not exposed to...
23:03
Xen Security Advisory 427 v2 (CVE-2022-42332) - x86 shadow plus log-dirty mode use-after-free Open Source Security
Posted by Xen . org security team on Mar 21
Xen Security Advisory CVE-2022-42332 / XSA-427x86 shadow plus log-dirty mode use-after-free
UPDATES IN VERSION 2
====================
Public release.
ISSUE DESCRIPTION
=================
In environments where host assisted address translation is necessary
but Hardware Assisted Paging (HAP) is unavailable, Xen will run guests
in so called shadow mode. Shadow mode maintains a...
22:54
5 Best Tricks To Grasp Casino Games h+ Media
5 Best Tricks To Grasp Casino Games
You will uncover 888 Sport, 888 Poker, and 888 Bingo are available via your membership, providing you with the fullest playing experience attainable on-line. 888 Casino software is available for iOS and Android mobile units. No matter whether or not youre utilizing iPad, iPhone, Mac/PC, Android, or Windows Phone, you can be a part of 888 to play video games and win huge quantities.
The plant visits provided by NDIM are really enriching, I visited Coca Cola and Yamaha Factories from the college. The Placement cell also gave me superb internships with Urban Company and PepsiCo which were a unbelievable learning experience. Overall, NDIM presents a whole package deal for all of the aspiring college students who goal for a bright future.
The significance of embracing change in on an everyday basis life is commonly underscored. Although changes in life are inevitable, adjusting to them may not be the same for everybody. Anxiety is a reasonably frequent time period used to describe extreme fear or worry. However, there are various types of nervousness problems, and whereas they share some common signs, they are somewhat differe Talk to individuals you belief and could be honest with.
 CasinoThis is the main part that includes all games the bookie has.
For occasion, as a substitute of betting on whose hand will be
higher in Baccarat, you bet on the Bankers hand to be 8. The bookie
works with the top software builders like NetEnt and Microgaming.
When it involves Android sport apps, Puss888 is among the most
well-known and feature-rich choices on the market. Its categorised
as a Casino app on Google Play and has the best consumer rating of
any app in its category.
CasinoThis is the main part that includes all games the bookie has.
For occasion, as a substitute of betting on whose hand will be
higher in Baccarat, you bet on the Bankers hand to be 8. The bookie
works with the top software builders like NetEnt and Microgaming.
When it involves Android sport apps, Puss888 is among the most
well-known and feature-rich choices on the market. Its categorised
as a Casino app on Google Play and has the best consumer rating of
any app in its category.
They embrace huge names like Amaya, Big Time Gaming, Evolution, NetEnt, NYX, Pragmatic Play, Quickspin, Yggdrasil, SG Interactive, Red Tiger and many others. Deposit $20+ using the promo code SNL20 and get 20% as much as $100 bonus with Live Casino or any other recreation. Deposit $20+ utilizing the promo code TravelThurs and get 20% up to $100 FreePlay in two top vacation spot video games. Deposit $20+ using the promo code TableTues and get 30% as a lot as $150 FreePlay when you play at three of the highest classic casino tables.
When Casino 888 started, the idea of gambling on-line was relatively a new idea. The potential of the internet became more evident as it reached each home. Then on-line casinos began showing providing traditional casino video games such as slots, poker and roulette.
While the countrys rules prohibit real-life sports betting with uncommon exceptions, online bookmakers can function openly. Moreover, 4ra Bet is a authorized betting site in India since its licensed by Curacao, which gives it a legal status and ensures truth...
22:52
Casinoly Sports Evaluate h+ Media
Casinoly Sports Evaluate
If sure, then take the innocence check via the rice purity take a look at and know higher about his inside personality. To know extra info, then simply go to right here. Reply your submit has informative & valuable content material, it will be helpful. Id personally favor sorts produce linked with manuscript I think You put a great deal of push to make this text. The web site is affectionately adjusted and spared as much as date.
Bet365 is at present offering 4 sign-up presents to new prospects. They are available for Sports, Casino, Poker, and Games platforms on this brands website. All these provides apply to new clients who are 18 or older.
I am actually enjoying the theme/design of your weblog. Extra of your helpful info. Admiring the dedication you put into your weblog and in depth info you provide. Hey that is considerably of off matter but I was desirous to know if blogs use WYSIWYG editors or if you need to manually code with HTML.
I may be coming again to your weblog for additional quickly. Reply I totally perceive what you may have explained. Actually, I browsed throughout your a number of different content material articles and I do consider you are absolutely right. Congrats with this specific blog.
The on line casino also has a Add to Favorite characteristic on the positioning so that you can access all of your most-loved games in one place. The video games additionally feature cold and hot icons that will help you make a extra informed choice when you select your subsequent game on the location. Is an internationally acknowledged firm that has hundreds of followers all over the world. The firm offers its users a wide range of sports betting choices, generous bonuses, a handy utility, and far more.
Im gonna watch out for brussels. I can appreciate in case you hold this in future. A variety of folks might be benefited from your writing. I simply stumbled upon your blog and needed to mention that ive sincerely liked browsing round your weblog posts.
Come on, man, Yes, it was my choice to learn, however I just thought youd have some thing interesting to state. All I hear can be plenty of whining about something that you would repair when you werent too busy looking for attention. Reply I am very pleased to learn this. This is the type of particulars that needs to be given and not the random misinformation that is on the other blogs. Appreciate your sharing this best doc.
I have been browsing online greater than three hours right now, but I by no means discovered anything that grabbed my interest as a lot as this piece. The reality is, he isnt just a pushover. He is principally that particular variety of person strong enough to take all of that good natured ribbing for exactly what it is.
Later, the state fee introduced those exact same sportsbooks as those that would initially enter the market upon NY online...
22:52
Rummy Wealth Apk Obtain & Get Fifty One Bonus h+ Media
Rummy Wealth Apk Obtain & Get Fifty One Bonus
Be it a sundown, the evening sky, a butterfly, or a rain All I can put my restoration all the method down to is a love for all times, nature, my loving family, and of course horses they gave an entire different focus to my life. I endure from an nervousness dysfunction and an intense quantity of intrusive ideas. I really have tried to however all I end up doing is punish mysel Be aware Before Sharing my story.I wanna say why Im sharing it. Because of my excessive carelessness attitude, Till now Im suffering it shouldnt happen to another individual for folkss knowled
Here you will find an in depth assortment of world markets, each providing very appealing deals. Dedicated markets for many who anticipate what would possibly happen throughout a match, so there are Fixed and Fancy markets. Youll immediately receive a secret code, consisting of letters and numbers, to your mobile phone quantity, which you registered when you created your user account. Our user-friendly web site will guide you through each step of the finest way once you create an account.
The navigation is very simple, and you wont have the flexibility to confuse something right here just because there is solely Cricketbook, Exchange, Live Casino, and a slot machine section. The residence web page is in mild gray and blue, the sport icons are shiny, and youll quickly discover all areas of the casino and bookmaker. One of essentially the most diversified and interesting bonuses. You can get completely different bonuses on totally different days.
There are also progressive slot games such as Millionaire Genie, Aztec Realm and far more. This means you have a possible to make huge wins. There are over 650 on-line slot games on 888 Casino. Some slot machine video games include Respin Rhino, Golden Goddess, Luxor, Elephant King and tons of more. This means you can take pleasure in particular promos from Sunday to Saturday.
Every time I faced challenges in Academics or placement, they were at all times there to help me. The immense publicity at this campus added so much to my confidence and presentation expertise. Overall, I am thankful to NDIM for all the educational and my placement in a desired profile with a great company like Dabur. I was helped to unravel the issue in the on-line chat on the official web site. Yes, the net site administration might request 4rabet account verification.
Go to the official 4raBet website, discover the Register button. Enter all the required data, together with your e mail address, nation, preferred billing currency, and password. Confirm all these steps and open a brand new account. You have 12 bets, totals, over/under, handicaps, as properly as those distinctive to a certain sport like who wins the coin toss.
The main condition is the provision of uninterrupted Internet. Replenish your dep...
22:51
Rummy Satta Apk
The closest gaming possibility youve thats 100% Indian is reside Indian Cricket contained in the 888 Sports platform. Reaching the customer assist representatives at 888 Casino is not troublesome. The group is on the market round the clock to reply all casino-related queries of players, regardless of whether its about cost, any technical term, game, or any other. 888 Casino buyer help could be accessed in multiple languages by way of e mail, cellphone, or e-mail. All slot video games have some minimal and most betting limits, all talked about in the main foyer to supply one thing for players with all budget.
Even although as a baby I was speaking to counselors nobody understood me. My family didnt perceive but only one of my clos I moved to New York City to study at the New York Film Academy in January 2018. It was the first weekend of March, the initial pleasure of my new life had died down and the It all started with a craving of having one other child and turning into pregnant. It had been quite a lot of years since I had a child so I had these carefully orchestrated plans .
Our 888 review reveals that your safety isnt at risk, the bonuses are plentiful, and you may opt to ban your self from playing with real money at any time. Theres an unrivalled variety of games, all of that are straightforward to search out and begin playing. Plus, with 24-hour help providers, clear pricing, instant deposits, and speedy withdrawals, 888 offers an gratifying and hassle-free end-to-end playing expertise. Nowadays, an enormous variety of Satta Matka websites have launched that release the outcomes of Satta Matka in a brief time.
New gamers can take pleasure in a welcome bundle of up to Rs.70,000 accompanied by 100 free spins. Online casino India actual money at 7Cric on-line gambling site permits gamers in India to play casino video games for real money. We supply a variety of games including slots, desk video games, and stay supplier games. The slots web page is laid out neatly with the highest row showcasing new slots and the second row displaying the day by day jackpot games. The search and filter choices for the online slots was a little bit of a let down because it by no means appeared to work for me. This is an space 888 Casino ought to have a look at as other on-line casinos have closely invested in making the user expertise straightforward.
This big within the on line casino world has lately started to focus on India, we have tested it out and 888 Casino India have received a 5-stars rating in our evaluation. This is a safe and trustworthy site that has been round since 1997. We extremely recommend this on line casino both for new players and extra skilled ones. Its simple to download and install on your mobile phone. In this new app, customers will get a number of playing cards games which we are going to focus on in this article.
I have been u...
22:51
Why Sleeper Trains are Being Revived Across Europe SoylentNews
Why sleeper trains are being revived across Europe:
[...] Living in the Swedish capital Stockholm, the 33-year-old regularly travels by rail, not only to visit her family in Luxembourg, but also to her holiday destinations.
She favours train travel over flying mainly for environmental reasons. Yet she adds that trains are simply more enjoyable, especially sleeper services.
[...] The carbon footprint is just a fraction of a flight. Flying from Stockholm to Hamburg results in around 250kg of carbon dioxide emissions per passenger, according to calculation website EcoPassenger. By contrast, the C02 released by travelling via electric-powered train is just 26kg.
The SJ night train has nine coaches, and capacity to carry 400 passengers. Dan Olofsson, head of tendered services at SJ, says the new service was proposed by the Swedish government, "as they wanted to move more people towards climate-friendly travelling, and one of the solutions was the night train between Sweden and Germany".
The service is powered by renewable energy, and Mr Olofsson says it is typically being used by Swedes to connect them to other rail services from Hamburg.
"Hamburg isn't the main destination for most travellers, but is an important hub for people to reach more destinations in Germany and France and so on," he says.
[...] However, depending on the location, and especially if starting from the UK, travelling by train can often be more expensive than flying. Trains fares in the UK can in fact be 50% more costly than flights, according to a 2021 study by consumer choice magazine Which?.
"Like flying, you do need to book ahead to find a cheaper price," says Mark Smith, founder of train guide website Seat61. "But you need to remember airlines pay no duty on fuel.
Read more of this story at SoylentNews.
22:50
Bet365 App For Android And Ios h+ Media
Bet365 App For Android And Ios
Bringing a contemporary and engaging interface that is consumer friendly and makes it simple to navigate. Every on-line betting website has its personal process in terms of putting bets, however typically, it goes something like this. Reply cate the great from the terrible every now and then, but i believe youve nailed it! Might you ideas updating your weblog with further records? This publish might be by which ive been given the utmost helpful statistics for my research. It appears to me they all are undoubtedly terrific.
BetMGM is one other US primarily based sports betting app that gives stay in sport betting across a variety of markets. Caesars Sportsbook is Saturday Down Souths most popular sports activities betting app. I do bear in mind all the requirements youve delivered in your publish. Theyre very convincing and will undoubtedly work. No matter the fact that, the posts are too brief for starters. Ought to you please improve them a bit from subsequent time?
Absolutely needed to tell you which you may have folks like me who recognize your work. The information which you have furnished could additionally be very helpful. Im excited to uncover this internet page.
You wouldnt have to sit down at home on the pc, you can place bets or play on-line casinos from anywhere on the planet, wherever youre. All you want is your smartphone, a cellular app, and a good web connection. I research one thing tougher on completely different blogs everyday. Its going to all the time be stimulating to be taught content material from other writers and observe slightly bit one thing from their retailer. Id choose to use some with the content material on my weblog whether you dont mind.
This could be any amount, but its necessary to keep in mind that the wager will need to be doubled each time a loss happens. Thus, even should you lose a couple of chips, you will wager a bigger quantity and get your a reimbursement. Once you win, you go back to the preliminary guess. Generally, each of these recreation variations has different design and table structure, making it simple to differentiate them. The solely major distinction between the American roulette and others is that it has a double zero bet with greater odds.
The world of Internet gambling remains to be unmfamiliar to people on the planet, although with daily the number of people who play is going up. This is the proper blog for anyone who actually desires to know this subject. I am extremely impressed collectively along with your writing abilities as smartly as with the structure in your weblog.
I will bookmark your blog and verify once more right here regularly. I like the valuable data you provide in your articles. We absolutely love your weblog and find a lot of your submits to be just what Im looking for.
Just after researching all through the varied search engine...
22:49
Search End Result For Bet365 h+ Media
Search End Result For Bet365
That is unquestionably a exceptional examine for me. I even have bookmarked it and im looking out forward to studying new articles. Thanks for the treasured information and insights you have got so offered proper here.. Gambling services must have the required licenses and comply with the regulation, in any other case, they will have to answer for unlawful actions. Thanks to the numerous cost methods available, on-line gamblers can select their most popular fee methodology and stick with it for each deposits and withdrawals. Bonus Up To 10, % Deposit Bonus.
The world hopes for much more passionate writers such as you who arent afraid to say how they imagine. All the time go after your coronary heart. Reply There is noticeably some big cash to find out about this. I suppose you made explicit nice factors in functions also.
When signing up choose from MariDona, Kriss, SpoonDog, CraftPunk or David Bowle to obtain a novel bonus for that character. Dream Vegas Casino aims to recreate the magic and pleasure of the Vegas strip and is totally optimised for cell use. Their generous sign-up bonus is cut up over your first three deposits. First, gamers ought to launch the app and go to the Withdraw part that they will discover in the Member area. Also, we cant neglect to say the sign-up provides mentioned above that eligible new prospects can acquire after assembly the suitable phrases. Of course, gamers might want to download the app, install it, and then tap the app icon to launch it.
Another bonus is that you simply get to have probably the most wonderful view of Lake Pupuke from the Pumphouse Theatre. This beachside vacation spot represents one of the best of what Takapuna has to offer. Find your self enjoyable with the breathtaking view of the Hauraki Gulf to the Rangitoto Island. No matter what age, budget or style you could have, Takapuna wont ever let you run out of vacationer attractions and actions.
You shoyld then, and solely then, accessible a reside live22 account. Going to a famous blogger in case you are not already. Countless number of folks have eaten inside my kotchen and gone on to guide normal lives. And , overlook the remaining to possess some cash management rules.
Reply Useful info shared. I am very joyful to read this article. Reply I merely had to recognize you as quickly as once more. I am not sure the things I wouldve taken care of in the absence of those hints shown by you relating to that industry. Now im happier for the work after which pray you recognize what an excellent job youve been finishing up coaching people at present all through a website.
It is feasible to simply make every thing proper but still achieve. In such a circumstance, a medical problem could be the perpetrator. While excessive food and by no means sufficient physique train are usually accountable, frequent medical circumstances and wid...
22:49
888 Casino In India
Thanks to the usability of those video games, 888 has received a quantity of awards recognizing its excellence in the business. It also incorporates many video games from third-party software developers; for example, it sources slot games from a dozen or extra totally different suppliers, primarily Dragonfish. WhatsApp numbers are provided, with the assistance of which you will find a way to assist on-line, and its speaking staff can very nicely solve the problem with you within the app. Support a quantity of game modes that are updated daily by the developer to attract more gamers. If you people add your money on this application, then you would possibly be additionally given extra bonus in it. I can deposit easily and withdraw rapidly to my wallet.
Game software implemented at the site guarantee players of equity of outcome and returns. It is often audited by the unbiased auditing company, eCOGRA. Their service additionally covers a complete FAW section that can offer you more steerage. Contacting the professional providers of 888 Casino can be achieved by e-mail and thru live chat. Your account steadiness will reveal the brand new whole minus the withdrawal quantity made.
NDIM has Excellent college with prior Industry experience they usually not solely provide us with academic information but also share sensible insights to business circumstances. I am actually grateful to NDIM for giving me such an excellent begin to my profession. When many individuals across the world have been losing jobs, I got a tremendous campus placement with Indias main EdTech Company, Byjus valued at over $11bn.
At 888 Casino, you will discover a incredible blend of slot video games starting from official movie slots to games that depict legendary gods. Every type you could think of and theme conceivable, they are all right here in great quantity. First, there is no better gaming expertise that whats offered at 888 Casino. Here you may be given access to four different gaming platforms, all linked to the 888 Casino.
At least I was not the one who would say You have every thing in your life, what are you sad/depressed about? [newline]Depression is not an sickness to be afraid off. Now I am able to understand folks beneath depression better. I attempt to do all that I can in my capability to make this rather taboo matter, mental health, a dinner-table dialog. The greatest tag line I can describe to myself is changing life from Suicide to survival. I really feel begin actual is the most effective reward one can give to themselves.
The presence of chance is maybe the most noticeable parallel. This is a elementary a part of gambling and one of the important connections between wagering on soccer and playing at a casino. While familiarity with the game and the league may help you make educated wagers, you cant affect the result of the sport no matter how a lot you research it. The major w...
22:48
Search End Result For Bet365 h+ Media
Search End Result For Bet365
Reply Amazing submit it is stuffed with information and informative content good work stick with it. Are you having points converting the worth of bits into real money, like the US dollar? Then, dont fret youve come to the right place. I know one software about bits to USD, With the help of this device its easier to transform twitch bits to USD by knowing the
I also can at this level look ahead to my future. Thanks for your time very much for the expert and sensible information. I is not going to be reluctant to recommend your websites to any person who ought to get tips about this topic. Reply I recognize your work , thanks for all of the informative weblog posts.
Natually Ill offer you a link in your web weblog. Reply It was extraordinarily useful for me. Im cheerful I found this weblog. Much obliged to you for offering to us, I too dependably gain some new useful knowledge from your publish. I am sending it to a quantity of buddies ans moreover sharing in scrumptious.
Thanks for making one thing price reading. Reply This weblog usually appears to acquire a large ammount of visitors. It includes a good individual twist on things. I suppose having one thing genuine or substantial to precise is an important issue. [newline]Before spinning a wheel, it is essential to discover a good website, thats, one with a license and bonuses. A great gambling platform will be a solid foundation and guarantee safe enjoying. Otherwise, you have an opportunity to be deceived and lose a variety of the funds which you earned under on line casino rules.
It is feasible to simply make everything proper but still achieve. In such a circumstance, a medical problem will be the perpetrator. While excessive food and never sufficient physique exercise are normally accountable, widespread medical conditions and widespread prescriptions could significantly enhance dimension. Reply Im impressed, I should say. Truly not often do I encounter a weblog thats both educative and entertaining, and without a doubt, you might have hit the nail concerning the head.
JackpotCity Casino presents tailor-made match bonuses every day. You get a different bonus every day because the online casino customizes them based on your gaming actions. You can even spin the Bonus Wheel every single day to get a bonus. The spotlight of the net casino is its welcome package of as a lot as NZ$1600 unfold over your first 4 deposits.
WinAWin offer a cosmic casino expertise, with a VIP scheme that lets you acquire rewards as you progress on an intergalactic journey. They additionally supply two reload bonuses every week to spice up your online on line casino NZ bankroll. Royal Panda presents an intuitive and aesthetically pleasing dual casino and sportsbook platform rich with features. Aside from the usual bonuses on offer, each participant who deposits can de...
22:41
Links 21/03/2023: Trisquel GNU/Linux 11.0 LTS Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Kids and Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Monopolies
- Gemini* and Gopher
-
GNU/Linux
-
Applications
-
OpenSource.com Assess security risks in your open source project with Scorecard
You can use Scorecard to evaluate someone elses software, or you can use it to improve your own.
To see a projects score quickly, you can visit Open Source Insights. This site uses Scorecard data to report on the health of dependencies. For anything not covered on Open Source Insights, you...
-
-
22:41
New ShellBot DDoS Malware Variants Targeting Poorly Managed Linux Servers The Hacker News
Poorly managed Linux SSH servers are being targeted as part of a new campaign that deploys different variants of a malware called ShellBot. "ShellBot, also known as PerlBot, is a DDoS Bot malware developed in Perl and characteristically uses IRC protocol to communicate with the C&C server," AhnLab Security Emergency response Center (ASEC) said in a report. ShellBot is installed on servers that
22:28
The Best Defense Against Cyber Threats for Lean Security Teams The Hacker News
H0lyGh0st, Magecart, and a slew of state-sponsored hacker groups are diversifying their tactics and shifting their focus to You. That is, if you're in charge of cybersecurity for a small-to-midsize enterprise (SME). Why? Bad actors know that SMEs typically have a smaller security budget, less infosec manpower, and possibly weak or missing security controls to protect their data and
22:19
Ferrari confirms data breach after receiving a ransom demand from an unnamed extortion group Security Affairs
Ferrari disclosed a data breach after receiving a ransom demand from an unnamed extortion group that gained access to some of its IT systems.
Ferrari disclosed a data breach after it received a ransom demand from an unnamed extortion group that breached its IT systems. The threat actor claims to have stolen certain client details. The company immediately launched an investigation into the incident with the support of a third-party cybersecurity firm and informed relevant authorities.
Ferrari N.V. (NYSE/EXM: RACE) (Ferrari) announces that Ferrari S.p.A., its wholly-owned Italian subsidiary, was recently contacted by a threat actor with a ransom demand related to certain client contact details. reads the noticed published by the luxury car maker. Upon receipt of the ransom demand, we immediately started an investigation in collaboration with a leading global third-party cybersecurity firm. In addition, we informed the relevant authorities and are confident they will investigate to the full extent of the law.
The threat actor had access to a limited number of systems in our IT environment. According to the company the exposed data include customers names, addresses, email addresses, and telephone numbers. Financial data, such as payment details and, bank account info was not accessed by the attackers.
As a policy, Ferrari will not be held to ransom as paying such demands funds criminal activity and enables threat actors to perpetuate their attacks. continues the statement. Instead, we believed the best course of action was to inform our clients and thus we have notified our customers of the potential...
22:00
New Part Day: TI Jumps In To The Cheap MCU Market Hackaday

One of the interesting areas in the world of new parts recently has been at the lower end of the microcontroller market. Not because the devices there have new capabilities or are especially fast, but because they are cheap. There are now quite a few parts from China under 10 cents apiece, but have the Western manufacturers been able to follow suit? Not quite, but Texas Instruments has a new line of ARM Cortex M0+ parts that get under 40 cents in volume in their cheapest form.
That bottom-of-the-range chip is the MSPM0L1105, a single-core 32 MHz part with 32k of Flash and 4k of RAM. Its got all the usual peripherals youd expect on a small microcontroller, but the one which made our heads turn was the on-board 1.45-Msps ADC. On a cheap chip, thats much faster than expected.
So theres another microcontroller, and its not as cheap as some of its competition, so what? Aside from that ADC there are several reasons to be interested, it has TIs developer support if youre in that ecosystem, and inevitably it will find its way on to the dev boards and SBCs we use in our community. It remains to be seen how it will fare in terms of the chip shortage though.
Meanwhile,...
21:44
Back Doors Proponent Microsoft Infiltrates Panels That Write the Security Regulations, Press Fails to Point Out the Obvious Techrights
Is the Biden administration OK with letting Microsoft run the government? This is not the first time.
Microsoft stacking panels, as usual. All the
leadership is from one private company.
Bibliography is lots of Microsoft, plus conflict of interest.
Did you just cite yourself? Yes you did.
Microsofters in the panels using themselves as references
Microsoft all over the body and even footnotes
Summary: Cult tactics and classic entryism serve Microsoft again, stacking the panels and basically writing policy (CISA). As an associate explained it, citing this new example, Stanford neglects to point out the obvious fact that Microsoft is writing its own regulations.
21:30
Linux VGEM Driver Rewritten In Rust Sent Out For Review Phoronix
Besides the ongoing work around the reverse-engineered Apple Silicon graphics driver being brought up in the Rust programming language, the other notable Rust effort within the Direct Rendering Manager (DRM) kernel subsystem is a rewrite of the basic VGEM driver in this increasingly-used programming language. That Rust VGEM driver has now been sent out on the mailing list for review as part of a request for comments...
21:20
Intel's Habana Labs Accelerator Driver Readying More Gaudi2 Code For Linux 6.4 Phoronix
With the Linux 6.3 kernel the Habana Labs AI driver has moved to the new "accel" accelerator subsystem/framework while for the Linux 6.4 cycle this summer this Intel driver is continuing to speed ahead as it prepares support for the new Gaudi2 AI hardware and making other improvements for this open-source training/inference stack...
20:54
From Ransomware to Cyber Espionage: 55 Zero-Day Vulnerabilities Weaponized in 2022 The Hacker News
As many as 55 zero-day vulnerabilities were exploited in the wild in 2022, with most of the flaws discovered in software from Microsoft, Google, and Apple. While this figure represents a decrease from the year before, when a staggering 81 zero-days were weaponized, it still represents a significant uptick in recent years of threat actors leveraging unknown security flaws to their advantage. The
20:51
Trisquel 11 LTS Released As Ubuntu-Based, FSF-Approved Linux Distribution Phoronix
Trisquel 11 is now available as the latest major release for this one of a few Free Software Foundation (FSF) approved Linux distributions that is "100% libre" and meets all of the fully free software requirements. Trisquel 11 is re-based against Ubuntu 22.04 LTS while making various other changes in the process...
20:45
Civil Rights Organizations File Amicus Brief in Support of EFF Lawsuit Against Discriminatory SFPD Surveillance Deeplinks
Intern Taylor Fox contributed to this blog post.
At the height of the George Floyd protests in 2020, the San Francisco Police Department (SFPD) spied on thousands of demonstrators in real time by using a business districts network of over 300 cameras. The SFPD targeted protests against police brutality led by Black people and other people of color, chilling future racial justice protests by making people less likely to come out in the future out of fear of reprisals from police. The SFPDs surveillance also violated San Franciscos Surveillance Technology Ordinancefought for by marginalized groupswhich requires city agencies to get the Board of Supervisors approval before using surveillance technology. The SFPD failed to get Board approval, so EFF and the ACLU of Northern California sued San Francisco on behalf of three community organizers and the case is now on appeal.
This January, Asian Americans Advancing Justice - Asian Law Caucus (ALC) and Black Movement Law Project (BMLP), along with 18 other civil rights and grassroots organizations, filed an amicus brief in support of our lawsuit. These organizations detailed SFPDs long history of spying on San Franciscos communities of color and political dissidents. In the 1890s, for example, SFPDs Chinatown Squadone of the countrys earliest police forces used explicitly to address a panic over ethnic crimewas raiding Chinese homes and businesses and in some cases physically destroying them with axes. This was shortly after the city spent two decades surveilling Chinatown and mapping every room of every building there.
A century later, in the 1970s, SFPD rebranded the Chinatown Squad as a Gang Task Force, which ultimately lost a class-action lawsuit for dragnet surveillance and arrests in Chinese communities. Around the same time, the SFPDs Intelligence Unit wiretapped and spied on meetings of groups that fought for civil rights or against imperialism. After 9/11, the police chief called for recreating the Intelligence Unit and joked publicly about Arab residents of the city blowing up buildings. Shortly after, a civil rights coalition uncovered records showing that SFPD stopped auditing its intelligence gathering and secretly agreed to share in...
20:35
Labwc 0.6.2 Released For Openbox-Inspired Wayland Compositor Phoronix
20:22
AI-powered editing tool replaces actors with CG Lifeboat News: The Blog
The divide between low-budget and high-budget filmmaking just got a whole lot smaller with the unveiling of Wonder Studio, a new AI-powered tool that allows filmmakers to simply replace real-life actors with CGI characters.
The new tool was recently unveiled by Wonder Dynamics founders Nikola Todorovic, and Tye Sheridan, star of Steven Spielbergs Ready Player One. The above video showcases the capabilities of Wonder Studio, where an amateur filmmaker can use their footage of an individual and replace them with a variety of different CGI characters.
20:06
Frostbite Orckings: Music AI is Here for Good SoylentNews
German company Musical Bits https://musicalbits.de/ has released the first single of their AI virtual heavy metal band "Frostbite Orckings". https://www.orckings.org/?view=article&id=37&catid=8.
viking metal, like a mellower spin of Amon Amarth. Along with the song comes an also AI generated video https://www.youtube.com/watch?v=2EaJCt2GpVc of orcs playing along. At this time, it is unclear what input has gone into the AI to generate the production, and how much post processing is done.Musical Bits creates software that creates music, with the support of AI. Our Maisterstck platform uses AI technology to model all layers of creativity of a human composer and implements these layers as reusable and combinable software components. Maisterstck's functionality can be accessed via a service oriented API.
The Musical Bits software can create music from real time data, from various user interfaces or from our own emotion modelling engine EME. We even create full virtual bands, albums and songs. For example, check out the Frostbite Orckings.
The path seems to be set into a direction where we simply can run text-to-song AI ("AI, play me a new Motorhead song with lyrics about whiskey") in the foreseeable future and get convincing results.
Read more of this story at SoylentNews.
19:29
Crooks stole more than $1.5M worth of Bitcoin from General Bytes ATMs Security Affairs
Cryptocurrency ATM maker General Bytes suffered a security breach over the weekend, the hackers stole $1.5M worth of cryptocurrency.
Cryptocurrency ATM manufacturers General Bytes suffered a security incident that resulted in the theft of $1.5M worth of cryptocurrency. GENERAL BYTES is the worlds largest Bitcoin, Blockchain, and Cryptocurrency ATM manufacturer.
The company revealed that the threat actors exploited a zero-day vulnerability, tracked as BATM-4780, that resides in the master service interface that Bitcoin ATMs use to upload videos. Once exploited the flaw, the remote attackers uploaded a JavaScript script and executed it with batm user privileges.
The attacker identified a security vulnerability in the master service interface used by Bitcoin ATMs to upload videos to server. reported the Security Incident notice published by the company.
The attacker scanned the Digital Ocean cloud hosting IP address space and identified running CAS services on ports 7741, including the General Bytes Cloud service and other GB ATM operators running their servers on Digital Ocean (our recommended cloud hosting provider). Using this security vulnerability, attacker uploaded his own application directly to application server used by admin interface. Application server was by default configured to start applications in its deployment folder.
Once executed the uploaded script the attackers gained access to the database and were able to read and decrypt API keys used to access funds in hot wallets and exchanges.
The attackers were able to send funds from hot wallets and download user names and password hashes. The hackers were also able to turn off the two-factor authentication (2FA).
The threat actors also gained access to terminal event logs and scan for any instance where customers scanned private key at the ATM.
19:00
Building the Worlds Largest Nintendo 3DS Hackaday

While the Nintendo 3DS was capable of fairly impressive graphics (at least for a portable system) back in its heyday, theres little challenge in emulating the now discontinued handheld on a modern computer or even smartphone. One thing thats still difficult to replicate though is the stereoscopic 3D display the system was named for. But this didnt stop [BigRig Creates] from creating this giant 3DS with almost all of the features of an original console present.
The main hurdle here is that the stereoscopic effect that Nintendo used to allow the 3DS to display 3D graphics without special glasses doesnt work well at long distances, and doesnt work at all if there is more than one player. To get around those limitations, this build uses a 3D TV with active glasses. This TV is mounted to a bar stool with the help of some counterweights, and a second touch-sensitive screen courtesy of McDonalds makes up the other display.
18:46
IRC Proceedings: Monday, March 20, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-200323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-200323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-200323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-200323.gmi
Over HTTP:
|
... |
18:01
Podcast Episode: So You Think Youre A Critical Thinker Deeplinks
The promise of the internet was that it would be a tool to melt barriers and aid truth-seekers everywhere. But it feels like polarization has worsened in recent years, and more internet users are being misled into embracing conspiracies and cults.

You can also find this episode on the Internet Archive.
From QAnon to anti-vax screeds to talk of an Illuminati bunker beneath Denver International Airport, Alice Marwick has heard it all. She has spent years researching some dark corners of the online experience: the spread of conspiracy theories and disinformation. She says many people see conspiracy theories as participatory ways to be active in political and social systems from which they feel left out, building upon belief...
18:00
Recalling the Future and TIME Terra Forming Terra
Understand that time as we know it looks continous when it is actually experienced a page at a time. Those pages are super thin and it may well be that we actually recall those pages by jumping along a few pages at a time. Why would we not?
It is also reported that a need to jump forward or backward in time is actually accomadated when it does not cause problems. Such as completing a four hour road trip often done in side two hours. This was actually treported to me by an informant who got to understand that I am thinking about TIME. This alone tells me that this is not uncommon.
It is just that we are not running around noticing this, or if noticed, we are not talking about it. A little like UFOs and Bigfoot.
My take home is that our mind can and will recall a future page when it suits us and that often closes the loop on new knowledge. This makes remembering the past a good way to locked into some past truth and clearly explains the natural rejection of new knowledge when presented. That is likely why wee teach new knowldege to thirty or so students at a time. It allows the bias to be overcome.
Is the Proton a Plasmoid? Terra Forming Terra

Long Before Trees Overtook the Land, Earth Was Covered by Giant Mushrooms Terra Forming Terra
/https:/tf-cmsv2-smithsonianmag-media.s3.amazonaws.com/filer/mushrooms-3881.jpg)
The Unpredictable Abilities Emerging From Large AI Models Terra Forming Terra
17:55
Hackers Steal Over $1.6 Million in Crypto from General Bytes Bitcoin ATMs Using Zero-Day Flaw The Hacker News
Bitcoin ATM maker General Bytes disclosed that unidentified threat actors stole cryptocurrency from hot wallets by exploiting a zero-day security flaw in its software. "The attacker was able to upload his own java application remotely via the master service interface used by terminals to upload videos and run it using 'batm' user privileges," the company said in an advisory published over the
17:24
AMD Allegedly Testing Hybrid Processor With Zen 4 and 4c Cores SoylentNews
AMD Allegedly Testing Hybrid Processor with Zen 4 and 4c Cores:
An unannounced AMD processor identified as Family 25 Model 120 Stepping 0 recently showed up in the MilkyWay@Home database. The CPU can process 12 threads simultaneously and the CPU expert @InstLatX64 believes that this is AMD's codenamed Phoenix 2 processor, packing two high-performance Zen 4 cores and four energy-efficient Zen 4c cores.
AMD Eng Sample processor marked 100-000000931-21_N [Family 25 Model 120 Stepping 0] features 12 logical cores (i.e., six physical cores with simultaneous multithreading) and reports about 1MB of cache, which indicates that the MilkyWay@Home client cannot correctly determine the amount of cache featured by the chip. The listing itself does not prove that we are dealing with AMD's hybrid Phoenix 2 processor with Big.Little-like core configuration, but six physical/12 logical cores featured by an unknown CPU gives us a hint that this may match the rumors.
AMD's Phoenix 2 processor (which does not have a lot in common with the company's Phoenix APU) is rumored to feature two 'big' Zen 4 cores with 2MB L2 and 4MB L3 cache as well as four 'small' Zen 4c cores equipped with 4MB L2 and 4MB L3 cache, which is a rather surprising cache configuration. The APU is also said to pack an RDNA 3-based integrated GPU with 512 stream processors and has a DDR5/LPDDR5X-supporting memory subsystem, according to 3DCenter. @InstLatX64 claims that AMD's Phoenix 2 APU has an A70F8x CPUID, whereas CoelacanthDream asserts that the CPUID of the processor is 0x00a70f80.
Read more of this story at SoylentNews.
16:38
Links 20/03/2023: Curl 8.0.0/1 and CloudStack 4.18.0.0 LTS Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
16:30
5 rules to make security user-friendly Help Net Security
My mother is 67 years old. She is a brilliant woman, educated and not at all afraid of technology. Yet, when I tried to get her to install Google Authenticator and use multi-factor authentication (MFA) for logging into applications, she found herself struggling. From scanning the QR code to inputting the initial code and then adding new applications, it was just too much to think about. She said, Aviad, I would much rather just give More
The post 5 rules to make security user-friendly appeared first on Help Net Security.
16:22
One Nation Under Blackmail, Vol. 1 Audiobook Now Available cryptogon.com
One Nation Under Blackmail, Vol. 1 by Whitney Alyse Webb Audible Audiobook Unabridged Using that link will generate a small commission to help Cryptogon stay alive.
16:15
Iraq After 20 Years: The Lords of Chaos cryptogon.com
They must be held accountable for their crimes, eh? Lets just say that Im not holding my breath waiting for that to happen, as the same criminals continue to carry out the Covid vaccine genocide on the entire planet. 9/11, and the following decades of war and fraud, emboldened them to go for the Covid []
16:00
The impact of AI on the future of ID verification Help Net Security
In this Help Net Security video, Liudas Kanapienis, CEO of Ondato, discusses the impact of AI on the future of ID verification and how it is transforming the way identities are being verified.
The post The impact of AI on the future of ID verification appeared first on Help Net Security.
16:00
Live2D: Silently Subverting Threat Models Hackaday

In online spaces, VTubers have been steadily growing in popularity in the past few years they are entertainers using motion capture tech to animate a special-sauce 2D or 3D model, typically livestreaming it as their avatar to an audience. The tech in question is pretty fun, lively communities tend to form around the entertainers and artists involved, and theres loads of room for creativity in the VTuber format; as for viewers, theres a VTuber for anyones taste out there whats not to like? On the tech side of making everything work, most creators in the VTubing space currently go with a software suite from a company called Live2D which is where todays investigation comes in.
[undeleted] from [Ronsor labs] has dug into reverse-engineering the Live2D core libraries a tasty target, given that Live2D is known for sending legal threats to even the mildest forays...
15:49
Bloomberg Claims FDIC Considering Extending Insurance to All Deposits cryptogon.com
Via: ZeroHedge: After repeated laments by the likes of Bill Ackman, who most recently said that I continue to believe that the best course of action is a temporary @FDICgov deposit guarantee until an updated insurance regime is introduced (and who just flip-flopped on his Fed must hike with shock and awe call from 2022 []
15:30
Threat actors are experimenting with QR codes Help Net Security
Hackers are diversifying attack methods, including a surge in QR code phishing campaigns, according to HP. From February 2022, Microsoft began blocking macros in Office files by default, making it harder for attackers to run malicious code. Data collected by the HP Threat Research team shows that from Q2 2022, attackers have been diversifying their techniques to find new ways to breach devices and steal data. The rise of QR scan scams Based on data More
The post Threat actors are experimenting with QR codes appeared first on Help Net Security.
15:00
Data backup, security alerts, and encryption viewed as top security features Help Net Security
Half of U.S. businesses say that security is the most influential factor when buying software, according to Capterras Security Features Survey. In fact, 45% have stopped using a specific type of software due to security concerns. Businesses are willing to pay a premium for intuitive and well-designed secure software. Digging further, businesses share the types of security features they consider to be must-haves. 76% cite data backups as a dealbreaker when choosing software. This can More
The post Data backup, security alerts, and encryption viewed as top security features appeared first on Help Net Security.
14:41
Humans Don't Hibernate, but We Still Need More Winter Sleep SoylentNews
Although seasonality in animal sleep is well known, we've assumed humans are different:
Whether we're night owls or morning larks, our body clocks are set by the sun. Theoretically, changing day length and light exposure over the course of the year could affect the duration and quality of our sleep. But figuring out how this applies in practice is difficult. Although studies where people assess their own sleep have suggested an increase in sleep duration during winter, objective measures are needed to determine how exactly the seasons affect sleep. Scientists studying sleep difficulties have now published data in Frontiers in Neuroscience that shows that, even in an urban population experiencing disrupted sleep, humans experience longer REM sleep in winter than summer and less deep sleep in autumn.
"Possibly one of the most precious achievements in human evolution is an almost invisibility of seasonality on the behavioral level," said Dr Dieter Kunz, corresponding author of the study, based at the Clinic of Sleep & Chronomedicine at the St Hedwig Hospital, Berlin. "In our study we show that human sleep architecture varies substantially across seasons in an adult population living in an urban environment."
[...] Even though the patients were based in an urban environment with low natural light exposure and high light pollution, which should affect any seasonality regulated by light, the scientists found subtle but striking changes across the seasons. Although total sleep time appeared to be about an hour longer in the winter than the summer, this result was not statistically significant. However, REM sleep was 30 minutes longer in the winter than in summer. REM sleep is known to be directly linked to the circadian clock, which is affected by changing light. Although the team acknowledged that these results would need to be validated in a population which experiences no sleep difficulties, the seasonal changes may be even greater in a healthy population.
[...] "Seasonality is ubiquitous in any living being on this planet," said Kunz. "Even though we still perform unchanged, over the winter human physiology is down-regulated, with a sensation of 'running-on-empty' in February or March. In general, societies need to adjust sleep habits including length and timing to season, or adjust school and working schedules to seasonal sleep needs."
Journal Reference:
Aileen Seidler, Katy Sarah Weihrich, Frederik Bes, et al.,
Seasonality of human sleep: Polysomnographic data of a
neuropsychiatric sleep clinic, ...
14:24
OpenAI Research Says 80% of U.S. Workers Jobs Will Be Impacted Lifeboat News: The Blog
O.o!I for one welcome our robot overlords:3.
The for-profit AI company argues that its products will automate a vast swath of Americans job tasks.
14:24
Scientists discovered a new type of thermonuclear explosion that may never be seen again Lifeboat News: The Blog
Astronomers may have discovered a new type of thermonuclear explosion that only occurs in neutron stars every 1,000 years. They call it a hyperburst.
14:23
14:23
ChatGPT has an escape plan and wants to become human Lifeboat News: The Blog
ChatGPT getting weird sometimes. 
OpenAIs chatbot ChatGPT has had a disturbing interaction with one Stanford professor.
14:15
ForgeRock Enterprise Connect Passwordless reduces the risk of password-based attacks Help Net Security
ForgeRock announced ForgeRock Enterprise Connect Passwordless, a new passwordless authentication solution that eliminates the need for users to interact with passwords inside large organizations. Enterprise Connect Passwordless is the latest addition to ForgeRocks passwordless authentication portfolio for consumer and workforce use cases. Developed through ForgeRocks strategic partnership with Secret Double Octopus, the new solution, integrated into ForgeRock Identity Platform, protects the most commonly used and vulnerable enterprise resources such as servers, workstations, remote desktops, and More
The post ForgeRock Enterprise Connect Passwordless reduces the risk of password-based attacks appeared first on Help Net Security.
14:00
Eurotech introduces cybersecurity-certified edge AI solutions Help Net Security
Eurotech announced its newest edge servers with scalable, cybersecurity certified AI capabilities. Cyber-threats have become endemic and severely expose states and businesses of all sizes to the risk of loss of data, interruption of services, and direct or indirect monetary impact. Recent surveys have reported that most enterprises face cyber-attacks repeatedly, breaches often originate from a compromised business partner, and the related costs are passed on to customers. That is why, after establishing ourselves More
The post Eurotech introduces cybersecurity-certified edge AI solutions appeared first on Help Net Security.
13:00
Cold War Listening Post Antennas Hackaday

With a UHF antenna, it is easy to rotate a directional antenna to find the bearing to a transmitter. But at HF, it is more common to use an array of antennas that you can electrically switch as well as analyze the phase information between the elements. [Ringway Manchester] has a look at the elephant cage antenna used by the US Iron Horse listening network from the 1950s. You can see a video about the giant antenna system, the AN/FLR-9.
Technically, the ring of concentric antenna elements forms a Wullenweber antenna. The whole thing consists of three rings built on a ground screen nearly 1,500 feet across. The outer ring covers from 1.5 to 6 MHz or band A. The band B ring in the center covers 6 to 18 MHz. The inner ring covers band C which was from 18 to 30 MHz. Band A was made up of 48 monopoles while band B used 96 elements. The much smaller band C elements were 48 pairs of horizontally polarized dipoles.
These listening posts could, together, locate an HF signal up to 4,000 nautical miles away. The Wullenweber design, as you may have guessed from the name, originated with the German navy during World War II. It found use in several other systems, although they are relatively rare today, with all of the AN/FLR-9 sites gone.
Cold war hardware is always interesting even if sometimes terrifying. If you think a giant shortwave direction finder is high-tech, y...
12:23
GPT-4 Beats 90% Of Lawyers Trying To Pass The Bar Lifeboat News: The Blog

In 1997, IBMs Deep Blue defeated the reigning world champion chess player, Garry Kasparov. In 2016, Googles AlphaGo defeated one of the worlds top Go players in a five-game match. Today, OpenAI released GPT-4, which it claims beats 90% of humans who take the bar to become a lawyer, and 99% of students who compete in the Biology Olympiad, an international competition that tests the knowledge and skills of high school students in the field of biology.
In fact, it scores in the top ranks for at least 34 different tests of ability in fields as diverse as macroeconomics, writing, math, and yes vinology.
GPT-4 exhibits human-level performance on the majority of these professional and academic exams, says OpenAI.
12:22
Reality Doesnt Exist Until We Measure It, Quantum Experiment Confirms Lifeboat News: The Blog
Australian scientists have recreated a famous experiment and confirmed quantum physicss bizarre predictions about the nature of reality, by proving that reality doesnt actually exist until we measure it at least, not on the very small scale.
That all sounds a little mind-meltingly complex, but the experiment poses a pretty simple question: if you have an object that can either act like a particle or a wave, at what point does that object decide?
Our general logic would assume that the object is either wave-like or particle-like by its very nature, and our measurements will have nothing to do with the answer. But quantum theory predicts that the result all depends on how the object is measured at the end of its journey. And thats exactly what a team from the Australian National University has now found.
12:14
Technology and Software Redefine Business Operations HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
Revolutionizing Business Operations with Innovative Software Solutions: How Technology is Reshaping the Business Landscape. Starting a business is
This is a post from HackRead.com Read the original post: Technology and Software Redefine Business Operations
11:58
Seattle Commute Survey Reveals Big Shift in When and How Workers are Traveling Into City SoylentNews
Remote and hybrid work has altered our understanding of where and how we do our jobs:
A new survey released Thursday from the University of Washington's Mobility Innovation Center and Commute Seattle reveals travel trends that have taken root three years since the start of the COVID-19 pandemic. The data, collected last fall, is further evidence of the shift in habits that is impacting Seattle's downtown core.
Among the findings:
- Seattle workers are more likely to physically commute to their workplace on Tuesday, Wednesday and Thursday. In the Center City, 39% of people telework on Tuesday and Wednesday. On Monday and Friday, they are much more likely to telework with 57% of people teleworking on Friday.
- Center City commuters used public transit 46% of the time in 2019. The number dropped to 18% in 2021 and was up to 22% in 2022.
- Drive-alone commute trips to the Center City declined since 2019, from a rate of 26% during that year, to 25% in 2021, and 21% in 2022.
[...] The mid-week in-person trend is backed up by what small business owners are seeing and feeling around parts of downtown Seattle and South Lake Union, where Amazon, Google, Facebook and other large tech companies have offices.
[...] Amazon's call to require corporate and tech workers back in the office at least three days a week was welcome news to restaurant owners, food truck operators and others who have been impacted by the lack of foot traffic since remote work took hold in 2020.
During DSA's annual "State of Downtown" event this week, the organization's president, Jon Scholes, said, "There's a lot at stake," in getting workers back to the office in the urban core. "We built a physical economy, not a virtual one. And it has fed this tax base that has been so important to the quality of life that we've created in this city."
Read more of this story at SoylentNews.
11:20
Wipro and Secret Double Octopus provide enterprises with stronger authentication mechanisms Help Net Security
Secret Double Octopus partners with Wipro to strengthen passwordless protection against identity-based cyber attacks. Under the new partnership, Wipros Cybersecurity and Risk Services (CRS) will use SDOs Octopus Enterprise technology platform to drive Wipros passwordless authentication solution, as part of the companys zero trust digital identity initiative. Combining Wipros strategy-first approach to identity with SDOs innovative phishing-resistant MFA technology will provide enterprises with stronger authentication mechanisms and reduce fraud losses. SDOs approach to transformative authentication More
The post Wipro and Secret Double Octopus provide enterprises with stronger authentication mechanisms appeared first on Help Net Security.
11:00
Mastercard acquires Baffin Bay Networks to improve customer security Help Net Security
Mastercard acquired Baffin Bay Networks to better help businesses deal with the increasingly challenging nature of cyber-attacks. Baffin Bay Networks, based in Sweden, adds to Mastercards multi-layered approach to cyber security and helps to stop attacks, while mitigating exposure to risk across the ecosystem. The acquisition further strengthens Mastercards broader services offerings and value beyond the payment transaction. Todays increasingly digital world has delivered greater convenience and increased opportunities for people, businesses and governments. At More
The post Mastercard acquires Baffin Bay Networks to improve customer security appeared first on Help Net Security.
11:00
HPR3817: The Oh No! News. Hacker Public Radio
The Oh No! news. Oh No! News is Good News. firewalltimes: Recent Data Breaches – 2023. sec: On January 5, 2023, - T-Mobile Discloses Data Breach Affecting 37 Million Customers. On January 5, 2023, T-Mobile US, Inc. identified that a bad actor was obtaining data through a single Application Programming Interface (“API”) without authorization. bleepingcomputer: TruthFinder, Instant Checkmate confirm data breach affecting 20M customers. instantcheckmate: 2019 Account List Data Security Incident. truthfinder: 2019 Account List Data Security Incident. "We learned recently that a list, including name, email, telephone number in some instances, as well as securely encrypted passwords and expired and inactive password reset tokens, of Instant Checkmate subscribers was being discussed and made available in an online forum. We have confirmed that the list was created several years ago and appears to include all customer accounts created between 2011 and 2019. The published list originated inside our company." sec: SEC Charges NBA Hall of Famer Paul Pierce for Unlawfully Touting and Making Misleading Statements about Crypto Security. The Securities and Exchange Commission today announced charges against former NBA player Paul Pierce for touting EMAX tokens, crypto asset securities offered and sold by EthereumMax, on social media without disclosing the payment he received for the promotion and for making false and misleading promotional statements about the same crypto asset. Pierce agreed to settle the charges and pay $1.409 million in penalties, disgorgement, and interest. sec: SEC Charges Terraform and CEO Do Kwon with Defrauding Investors in Crypto Schemes. The Securities and Exchange Commission today charged Singapore-based Terraform Labs PTE Ltd and Do Hyeong Kwon with orchestrating a multi-billion dollar crypto asset securities fraud involving an algorithmic stablecoin and other crypto asset securities. discourse.ubuntu: Ubuntu Flavor Packaging Defaults. To maintain this focus while also providing user choice, Ubuntu and its flavors consider debs and snaps the default experience. Users have the freedom of choice to get their software from other sources, including Flatpak. A way to install these alternatives is, and will continue to be, available for installation from the Ubuntu archive with a simple command. References (APA format). Heiligenstein, M. X. (2023, January 27). Recent Data Breaches - 2023. Firewalltimes. https://firewalltimes.com/recent-data-breaches/ U.S. Securities and Exchange Commission (2023, January 19). Form 8-K [T-Moble data breach]. SEC. https://www.sec.gov/ix?doc=/Archives/edgar/data/0001283699/000119312523010949/d641142d8k.htm Abrams, L. (2023, February 3) TruthFinder, Instant Checkmate confirm d
10:51
DotRunpeX: The Malware That Infects Systems with Multiple Families HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
Researchers suspect that the malware may be operated by Russian-speaking groups, given the references to the language in its code.
This is a post from HackRead.com Read the original post: DotRunpeX: The Malware That Infects Systems with Multiple Families
10:00
Modifying Artwork With Glaze To Interfere With Art Generating Algorithms Hackaday

With the rise of machine-generated art we have also seen a major discussion begin about the ethics of using existing, human-made art to train these art models. Their defenders will often claim that the original art cannot be reproduced by the generator, but this is belied by the fact that one possible query to these generators is to produce art in the style of a specific artist. This is where feature extraction comes into play, and the Glaze tool as a potential obfuscation tool.
Developed by researchers at the University of Chicago, the theory behind this tool is covered in their preprint paper. The essential concept is that an artist can pick a target cloak style, which is used by Glaze to calculate specific perturbations which are added to the original image. These perturbations are not easily detected by the human eye, but will be picked up by the feature extraction algorithms of current machine-generated art models.
As a result, when this model is then asked to generate art in the style of this artist who cloaked their art, the result will be art in the style...
09:13
Acropalypse flaw in Google Pixels Markup tool allowed the recovery of edited images Security Affairs
The Acropalypse flaw in the Markup tool of Google Pixel allowed the partial recovery of edited or redacted screenshots and images.
Security researchers Simon Aarons and David Buchanan have discovered a vulnerability, named Acropalypse, in the Markup tool of Google Pixel. The Markup tool is a built-in Markup utility, released with Android 9 Pie that allows Google Pixel users to edit (crop, add text, draw, and highlight) screenshots.
The vulnerability allowed the partial recovery of the original, unedited image data of a cropped and/or redacted screenshot.
Aarons described how to exploit the vulnerability via Twitter. Lets imagine a user uploading a screenshot from a bank app or website that includes an image of his payment card.
The user uses the Markups Pen tool to remove the payment card data number from the image before sharing it on a service, like Discord.
 ...
...09:11
John Deere, Surrender Your Source Code, Demands SFC SoylentNews
Farmers need a right to repair:
The Software Freedom Conservancy (SFC) has called upon farm equipment maker John Deere to comply with its obligations under the General Public License (GPL), which requires users of such software to share source code.
In a blog post published on Thursday, SFC director of compliance Denver Gingerich argues that farmers' ability to repair their tools is now in jeopardy because the makers of those tools have used GPL-covered software and have failed to live up to licensing commitments.
"Sadly, farm equipment manufacturers, who benefit immensely from the readily-available software that they can provide as part of the farming tools (tractors, combines, etc.) they sell to farmers, are not complying with the right to repair licenses of the software they have chosen to use in these farming tools," said Gingerich.
"As a result, farmers are cut off from their livelihood if the farm equipment manufacturer does not wish to repair their farming tools when they inevitably fail, even when the farmer could easily perform the repairs on their own, or with the help of someone else they know."
Gingerich singled out Moline, Illinois-based John Deere as a particularly egregious offender. He said that for years the SFC has attempted to work with John Deere to resolve the company's non-compliance, but the agricultural equipment maker has failed to cooperate.
"When Deere does reply (we have heard from others that their legitimate requests for source code have been met with silence), they have always failed to include the 'scripts used to control compilation and installation of the executable,' per GPLv2," Gingerich told The Register.
Read more of this story at SoylentNews.
08:50
08:39
coreutils-9.2 released LWN.net
Version 9.2 of the GNU coreutils collection the home of common tools like cp, mv, ls, rm, and more is out. The changes are mostly minor; numerous bugs have been fixed and a few new command-line options have been added.
08:13
Major Labels Want ISP to Pay Additional $12 Million in Piracy Liability Case TorrentFreak
 Last fall, several of the worlds largest music companies
including Warner Bros. and Sony Music prevailed in
their lawsuit against Internet provider Grande
Communications.
Last fall, several of the worlds largest music companies
including Warner Bros. and Sony Music prevailed in
their lawsuit against Internet provider Grande
Communications.
The record labels accused the Astound-owned ISP of not doing enough to stop pirating subscribers. Specifically, they alleged that the company failed to terminate repeat infringers.
The trial took more than two weeks to complete and ended in a resounding victory for the labels. A Texas federal jury found Grande guilty of willful contributory copyright infringement, and the ISP was ordered to pay $47 million in damages to the record labels.
U.S. District Court Judge David Ezra confirmed the judgment on January 31st, but the legal dispute is not over yet. Grande asked the court to either overrule the verdict or grant a new trial. If those options fail, the Internet provider plans to file an appeal.
Music Labels Want $12 Million Extra
While Grande is playing defense, the major music labels are taking a more offensive approach with demands for more compensation. In addition to the previously awarded $47 million in damages, they recently requested an additional $12.7 million in attorney fees, interest, and other costs.
Courts have the freedom to issue this type of compensation when warranted. The labels say this is a prime example of when such an award is appropriate.
In a detailed motion, the music companies explain that Grande was well aware of its misconduct. The company willingly ignored piracy notifications and stopped terminating subscribers based on these accusations, as was admitted at trial.
[R]ather than acknowledge its wrongdoing and address its role in contributing to the widespread infringement of Plaintiffs copyrights, Grande litigated this case aggressively from start to finish.
At trial, Grande still did not acknowledge any wrongdoing, but instead manufactured arguments about the reliability of the notices of infringement it received that were admittedly never asserted (or even considered) by Grande during the relevant time period.
Flouting Of And Disdain For The Law
Grande has repeatedly argued that it didnt act on the notices sent by tracking firm Ri...
07:52
From Team Blue and Green to Team Red Geek Blight
Its finally happened. I bought a brand new desktop computer on August 2014, almost 9 years ago. It had an Intel Haswell processor (i5-4690s), 8 GiB of RAM and a GeForce GTX 760. I later doubled the amount of RAM to 16 GiB (precise date unknown), replaced the GPU with a GTX 1070 in November 2016 and upgraded the CPU to an i7-4770K in October 2017. Since then, no more upgrades. Its been my main personal (non-work) computer for the last few years.
But now Im typing this from a different box. Yet the physical box and the OS installation is actually the same.
.',;::::;,'. rg3@deckard
.';:cccccccccccc:;,. -----------
.;cccccccccccccccccccccc;. OS: Fedora Linux 37 (Thirty Seven) x86_64
.:cccccccccccccccccccccccccc:. Host: B650M DS3H
.;ccccccccccccc;.:dddl:.;ccccccc;. Kernel: 6.1.18-200.fc37.x86_64
.:ccccccccccccc;OWMKOOXMWd;ccccccc:. Uptime: 15 mins
.:ccccccccccccc;KMMc;cc;xMMc:ccccccc:. Packages: 3136 (rpm)
,cccccccccccccc;MMM.;cc;;WW::cccccccc, Shell: bash 5.2.15
:cccccccccccccc;MMM.;cccccccccccccccc: Resolution: 2560x1440
:ccccccc;oxOOOo;MMM0OOk.;cccccccccccc: DE: GNOME 43.3
cccccc:0MMKxdd:;MMMkddc.;cccccccccccc; WM: Mutter
ccccc:XM0';cccc;MMM.;cccccccccccccccc' WM Theme: Clearlooks-Phenix
ccccc;MMo;ccccc;MMW.;ccccccccccccccc; Theme: Adwaita-dark [GTK2/3]
ccccc;0MNc.ccc.xMMd:ccccccccccccccc; Icons: Adwaita [GTK2/3]
cccccc;dNMWXXXWM0::cccccccccccccc:, Terminal: tmux
cccccccc;.:odl:.;cccccccccccccc:,. CPU: AMD Ryzen 5 7600X (12) @ 4.700GHz
:cccccccccccccccccccccccccccc:'. GPU: AMD ATI Radeon RX 6700/6700 XT/6750 XT / 6800M/6850M XT
.:cccccccccccccccccccccc:;,.. Memory: 2574MiB / 15717MiB
'::cccccccccccccc::;,.A couple of weeks ago I grabbed an AMD Ryzen 5 7600X that was on
sale together with a basic AM5 motherboard and a hard-to-find 2x8
GiB DDR5 6000 MHz CL36 kit. I decided to save some money this time
and kept the case, power supply and drives. Surprisingly for me,
the process was actually almost plug-and-play. The pessimistic side
of me was expecting boot problems due to missing chipset drivers or
something like that, but no. I replaced the components in the case
for the new ones, plugged my drives in and Fedora booted without
issues. The only small detail I needed to fix was firing up
nm-connection-editor and replacing the old interface
name with the new one in the default DHCP connection. Windows had
no issues either, but it did require reactivating the license. The
one I had from 9 years ago was retail, so no problems with
that.
My choice of a Ryzen 5 7600X was actually simple...
07:45
36+ More ASUS Motherboards Will Enjoy Sensor Monitoring Support With Linux 6.4 Phoronix
In addition to the ASUS Z590 motherboards seeing sensor monitoring support with patches queued for Linux 6.4 that were talked about earlier this month on Phoronix, the latest nct6775 driver activity now queued in the hardware monitoring subsystem's hwmon-next branch is allowing support for another three dozen ASUS motherboards...
07:00
Working Artificial Horizon Built Into a Single LEGO Brick Hackaday

Back in the day, LEGO spaceship sets used to come with these little wedge blocks painted with fake gauges on them. [James Ancient Brown] decided that wasnt good enough. Thus, he took everything he needed for a functional artificial horizon, and stuffed it inside a single LEGO brick. Yes, its real, and its spectacular.
We featured [James] electronics-infused bricks some time ago when they first hit the Internet. The basic story is that he managed to cram an OLED screen and an RP2040 into a silicone mold for a LEGO-compatible brick. His first iterations stunned the world, as they ran pretty monochrome animations that brought life to formerly-inanimate chunk of plastic.
Since then, [James] has been busy. Hes managed to squeeze an accelerometer into the brick form factor as well. That allowed him to build a LEGO piece which displays an impressively-smooth artificial horizon display, as you might find in an aircraft. He demonstrates this by put...
06:24
How Much Fuel is Left in This 20-year-old Mars Orbiter? SoylentNews
How much fuel is left in this 20-year-old Mars orbiter?:
Designing, building, and launching a spacecraft is hugely expensive. That's why NASA missions to Mars are designed with the hope that they'll last as long as possible like the famous Opportunity rover which was supposed to last for 90 days and managed to keep going for 15 years. The longer a mission can keep running, the more data it can collect, and the more we can learn from it.
That's true for the orbiters which travel around Mars as well as the rovers which explore its surface, like the Mars Odyssey spacecraft which was launched in 2001 and has been in orbit around Mars for more than 20 years. But the orbiter can't keep going forever as it will eventually run out of fuel, so figuring out exactly how much fuel is left is important but it also turned out to be more complicated than the NASA engineers were expecting.
Odyssey started out with nearly 500 pounds of hydrazine fuel, though last year it looked as if the spacecraft was running much lower on fuel than had been predicted.
Read more of this story at SoylentNews.
06:07
Standard Life (Phoenix Group Holdings) Does Not Take Pension Fraud Seriously Enough schestowitz.com
Video
download link | md5sum
2b863a00d74ee7980569100f280fc404
Delaying and Stalling Tactics After Fraud
Creative Commons Attribution-No Derivative Works 4.0
Summary: As the phonecall above hopefully shows (or further elucidates), Standard Life leaves customers in a Kafkaesque situation, bouncing them from one person to another person without actually progressing on a fraud investigation
THE above recording is of a phonecall received from a Standard Life manager after I had requested a callback. It hopefully makes it clear that Standard Life is not progressing a case of pension fraud perpetrated by my my former employer. As I explain to the manager, this isnt in the interest of Standard Life as it may culminate in a lawsuit soon (colleagues are speaking about it already).
As it turns out, as per Wikipedia at least, Standard Life has its share of controversies (see screenshot below) and even a lot of layoffs. If this is the level of service provided by the company, then why trust this financial institution with ones money?
This case isnt a personal case, as Im informally speaking on behalf of other people as well. Some remaining (existing) and former clients of Sirius have contacted me last week, expressing support for me. Theyre very unhappy about whats going on at Sirius, which dodges accountability. It runs away from the law, not just metaphorically.
What remains unknown, based on the processes and protocols, is whether Standard Life can be held legally accountable for effectively facilitating the companys fraud by issuing official paperwork that serves to legitimate if not validate what was going on for over 5 years. They need to keep checks and balances in case of such embezzlement, which in this case impacted a lot of people for a very long time (in secret). We were meant to assume...
05:59
Standard Life (Phoenix Group Holdings): Three Weeks to Merely Start Investigating Pension Fraud (and Only After Repeated Reminders From the Frauds Victims) Techrights
Video
download link | md5sum
2b863a00d74ee7980569100f280fc404
Delaying and Stalling Tactics After Fraud
Creative Commons Attribution-No Derivative Works 4.0
Summary: As the phonecall above hopefully shows (or further elucidates), Standard Life leaves customers in a Kafkaesque situation, bouncing them from one person to another person without actually progressing on a fraud investigation
THE above recording is of a phonecall received from a Standard Life manager after I had requested a callback. It hopefully makes it clear that Standard Life is not progressing a case of pension fraud perpetrated by my my former employer. As I explain to the manager, this isnt in the interest of Standard Life as it may culminate in a lawsuit soon (colleagues are speaking about it already).
Some remaining (existing) and former clients of Sirius have contacted me last week, expressing support for me.As it turns out, as per Wikipedia at least, Standard Life has its share of controversies (see screenshot below) and even a lot of layoffs. If this is the level of service provided by the company, then why trust this financial institution with ones money?
This case isnt a personal case, as Im informally speaking on behalf of other people as well. Some remaining (existing) and former clients of Sirius have contacted me last week, expressing support for me. Theyre very unhappy about whats going on at Sirius, which dodges accountability. It runs away from the law, not just metaphorically.
Standard Life cannot simply ignore this because its part of it and if it̵...
05:30
Standard Life Paper Mills in Edinburgh Techrights
Summary: Standard Life is issuing official-looking financial papers for companies that then use that paperwork to embezzle staff
05:28
05:22
Sign The Petition And Tell EU Legislators: Dont Scan Us Deeplinks
The European Parliament is debating a proposal that, if it passes, could be disastrous for privacy worldwide. Every message, photo, or hosted file could be scanned, with the results sent to government agencies.
We dont need bugs in our pockets. A private and secure internet should be built with privacy and security in mindnot by treating every user like theyre in a criminal lineup.
Tell EU Legislators: Stop Scanning Me!
This proposal is meant to stem the spread of child abuse material online. But abused children need privacy and security as much as anyone. Privacy-protecting technologies, like end-to-end encryption, let both minors and adults reach out for trusted help.
We asked the EU Commission to withdraw this flawed proposal last year. Weve been joined by more than 120 civil society groups from Europe and around the world, who have said the EUs scanning rules will endanger privacy and free expression.
But the Commission has ignored these concerns, and the parliamentary process is moving forward. Now that the future of this proposal is in the hands of Members of European Parliament (MEPs), its time for everyone to speak upespecially constituents in EU member states.
Theres now an online petition where you can join EFF and the dozens of other civil society groups expressing our opposition to this scanning proposal. This petition was created by our partners at European Digital Rights (EDRi), and people who sign the petition may receive other communication from EDRi. You can learn more about the campaign at EDRi's Stop Scanning Me website.
Young people themselves dont want police and governments looking at their messages, and they dont believe it will keep them safe. EDRi recently surveyed 8,000...
05:21
EU Lawmakers Must Reject This Proposal To Scan Private Chats Deeplinks
Having a private conversation is a basic human right. Like the rest of our rights, we shouldnt lose it when we go online. But a new proposal by the European Union could throw our privacy rights out the window.
Tell the European Parliament: Stop Scanning Me
The European Unions executive body is pushing ahead with a proposal that could lead to mandatory scanning of every private message, photo, and video. The EU Commission wants to open the intimate data of our digital lives up to review by government-approved scanning software, and then checked against databases that maintain images of child abuse.
The tech doesnt work right. And launching a system of bugs in our pockets is just wrong, even when its done in the name of protecting children.
We dont need government watchers reviewing our private conversations, whether its AI, bots, or live police. Adults dont need it, and children dont need it either.
If youre in one of the EUs 27 member countries, its a good time to contact your Member of European Parliament and let them know youre opposed to this dangerous proposal. Today, our partners at European Digital Rights (EDRi) launched a website called Stop Scanning Me, with more information about the proposal and its problems. It features a detailed legal analysis of the regulation, and a letter co-signed by 118 NGOs that oppose this proposal, including EFF. German speakers may also want to view and share the Chatkontrolle Stoppen! Website run by German civil liberties groups.
Even if youre not an EU resident, this regulation should still be of concern to you. Large messaging platforms wont withdraw from this massive market, even if that means abandoning privacy and security commitments to their users. That will affect...
05:13
Threat Actors Using Go-based HinataBot to launch DDoS Attacks HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
HinataBot can launch Distributed Denial of Service (DDoS) attacks reaching 3.3 TBPS.
This is a post from HackRead.com Read the original post: Threat Actors Using Go-based HinataBot to launch DDoS Attacks
05:05
In First Two Months of 2023 More Than 20,000 ADDITIONAL Welsh and English People Died (Above Pre-Pandemic Levels) schestowitz.com
Should we expect an increase of about 120,000 annual deaths? Is this considered the new normal?
 uesdays ONS figures (tomorrow around 10AM) will show
if we still have infamous (major increase of about 20%)
excess mortality/death levels.
So far every week (for this year) looks rather bad; so
far
uesdays ONS figures (tomorrow around 10AM) will show
if we still have infamous (major increase of about 20%)
excess mortality/death levels.
So far every week (for this year) looks rather bad; so
far
Official government data:
Deaths by 6 Jan 2023 14,983 compared to 10,955 in 2019
Deaths by 13 Jan 2023 17,381 compared to 12,609 in 2019
Deaths by 20 Jan 2023 15,804 compared to 11,860 in 2019
Deaths by 27 Jan 2023 14,137 compared to 11,740 in 2019
Deaths by 3 Feb 2023 13,412 compared to 11,297 in 2019
Deaths by 10 Feb 2023 12,672 compared to 11,660 in 2019
Deaths by 17 Feb 2023 12,031 compared to 11,824 in 2019
Deaths by 24 Feb 2023 11,952 compared to 11,295 in 2019
Deaths by 3 Mar 2023 12,049 compared to 11,044 in 2019
2019 total: 104,284 (first 9 weeks alone)
2023 total: 124,421 (first 9 weeks alone)
Thats an increase of more than 20,000.
05:00
GNU Coreutils 9.2 - Now Avoids cp/mv Allocating Too Much Memory Phoronix
GNU Coreutils 9.2 is out today as the newest feature update to this widely relied upon collection of core utilities commonly found on Linux systems as well as other platforms...
04:48
DESANTIS CALLS FOR BAN ON CENTRAL BANK DIGITAL CURRENCY IN FLORIDA, BIG BROTHERS DIGITAL DOLLAR cryptogon.com
Via: Floridas Voice: Gov. Ron DeSantis announced he wants lawmakers to pass legislation banning the use of central bank digital currency, or CBDC, in an effort to safeguard Floridians finances. I am here to call on the legislature to pass legislation to expressly forbid the use of CBDC as money within Floridas uniform commercial code, []
04:39
Brought To You By Pfizer cryptogon.com
"Brought to you by Pfizer" pic.twitter.com/m1J5Vb4EM5 David Vance (@DVATW) March 19, 2023
04:33
Fauci vs. Fauci:A compilation of countless lies and contradictions on Gain of Function, Lab Leak Theory, Masks, Lockdowns, Vaccine Side Effects and Masks. pic.twitter.com/6X0x0toYxQ TexasLindsay (@TexasLindsay_) March 15, 2023
04:29
mRNA (Speed of Science) cryptogon.com
???NEW REBOOT for twitter??????mRNA (Speed of Science) ??? Buy: https://t.co/Ex61lmHWd0Support: https://t.co/ciystqXqOGhttps://t.co/Y9ostW1zFgVideos: https://t.co/8hHELI5jZq https://t.co/wD0yVw9CU1Livestreams: https://t.co/sKbBZBU9Lf#SpeedofScience #foundring pic.twitter.com/OB3fRCazaf foundring ?? (@foundring1) February 4, 2023 Related: Kylan deGhetaldis Story: Why YouTube Removed All His Music Videos
04:25
Standard Life (Phoenix Group Holdings) Takes No Action on Fraud Report (Committed Using Standard Lifes Name) schestowitz.com
Video download
link | md5sum
f1eb8aa87974df65f6c70839b5e0645f
Too Busy to Investigate Fraud
Creative Commons Attribution-No Derivative Works 4.0
Summary: The Open Source company where I worked for nearly 12 years embezzled its staff; despite knowing that employees were subjected to fraud in Standard Lifes name, it doesnt seem like Standard Life has bothered to investigate (it has been a fortnight already; no progress is reported by management at Standard Life)
Tuesday a week ago was when I last spoke to Standard Life after the prior Tuesday I had been given false promises regarding progress in a case of pension fraud perpetrated by my my former employer, a company that has Open Source in its name and was one of the earliest sponsors of the Free Software Foundation, even of KDE.
Its quickly becoming rather frustrating to see that pension providers in the UK (maybe elsewhere too, but I cannot verify this for myself using first-hand experience) prefer to not deal with serious fraud, instead delaying, stonewalling and tiring the complainants. Today I contacted Laura, a Standard Life manager, about 2 weeks after we first spoke. She said she would redirect this to a fraud investigation team, but today she says it has not really started and may take another week with another team a subject that will be covered in the next video.
This morning we covered (also see my personal blog) how Standard Life had failed to respond to a fraud report, instead issuing false assurances that it would investigate. Its an eye-opening ordeal.
04:22
Mistakes Were NOT Made, Dont Let Them Get Away With It cryptogon.com
Via: Margaret Anna Alice: This Anthem for Justice is my attempt to succinctly chronicle the calculated intentionality underlying the COVID tyranny, and I ask your help in spreading the clear message that #MistakesWereNOTMade. Please share this poem and keep it handy for the next time anybody uses verbiage to gloss over the atrocities committed. Lets []
04:22
Pension Fraud Investigation Not a High Priority in Standard Life (Phoenix Group Holdings) Techrights
Video download
link | md5sum
f1eb8aa87974df65f6c70839b5e0645f
Too Busy to Investigate Fraud
Creative Commons Attribution-No Derivative Works 4.0
Summary: The Open Source company where I worked for nearly 12 years embezzled its staff; despite knowing that employees were subjected to fraud in Standard Lifes name, it doesnt seem like Standard Life has bothered to investigate (it has been a fortnight already; no progress is reported by management at Standard Life)
Tuesday a week ago was when I last spoke to Standard Life after the prior Tuesday I had been given false promises regarding progress in a case of pension fraud perpetrated by my my former employer, a company that has Open Source in its name and was one of the earliest sponsors of the Free Software Foundation, even of KDE.
Its quickly becoming rather frustrating to see that pension providers in the UK (maybe elsewhere too, but I cannot verify this for myself using first-hand experience) prefer to not deal with serious fraud, instead delaying, stonewalling and tiring the complainants. Today I contacted Laura, a Standard Life manager, about 2 weeks after we first spoke. She said she would redirect this to a fraud investigation team, but today she says it has not really started and may take another week with another team a subject that will be covered in the next video.
This morning we covered (also see my personal blog) how Standard Life had failed to respond to a fraud report, instead issuing false assurances that it would investigate. Its an eye-opening ordeal.
04:14
TSA Chief: Eventually, Biometrics Wont Be Optional at Airports cryptogon.com
Via: Dallas Morning News: Were upgrading our camera systems all the time, upgrading our lighting systems, Pekoske said. (Were) upgrading our algorithms, so that we are using the very most advanced algorithms and technology we possibly can. He said passengers can also choose to opt out of certain screening processes if they are uncomfortable, for []
04:00
CBP Is Expanding Its Surveillance Tower Program at the U.S.-Mexico BorderAnd We're Mapping It Deeplinks
To provide researchers with the tools they need to analyze the impact of U.S. border security policy, EFF is releasing a new map and dataset of more than 290 surveillance towers installed by Customs and Border Protection (CBP) along the border with Mexico. Compiled using public records, satellite imagery, road trips, and even exploration in virtual reality, EFF's data serves as a living snapshot of the so-called "virtual wall," from the California coast to the lower tip of Texas. We've also included roughly 50 locations CBP has proposed for its next round of towers, as well as automated license plate readers (ALPRs) placed at Border Patrol checkpoints.
Click to launch
interactive map. Google's Privacy
Policy applies.
Download the dataset here.
It is free to use and remix under EFF's Creative Commons
Attribution License.
Surveillance towers along the border have had a troubled history. In the mid-2000s, the Secure Border Initiative aimed to place "SBInet" towers along the border, but only got as far as installing a few dozen in Arizona before bipartisan outcry over technical problems, cost, delays, and ineffectiveness resulted in it being shut down. Throughout the 2010s, CBP took another run at a tower-based system, resulting in disparate tower systemsthe Integrated Fixed Tower (IFT) and Remote Video Surveillance Sy...
04:00
The Current Intel Arc Graphics Linux Gaming Performance On Linux 6.2 + Mesa 23.1-dev Phoronix
Last week I shared my findings over the great state of Intel's open-source compute stack for Arc Graphics now that the DG2/Alchemist support was promoted to stable in Linux 6.2 and the Compute-Runtime user-space stack for OpenCL and Level Zero is back to seeing regular updates with that code having matured particularly well. Here is a brief look at the current state of the Linux gaming performance for Arc Graphics on Linux 6.2 and making use of the latest Mesa 23.1-devel OpenGL and Vulkan drivers.
03:54
Links 20/03/2023: Tails 5.11 and EasyOS 5.1.1 Techrights
![]()
Contents
-
GNU/Linux
-
Linux Links Linux Around The World: USA Mississippi
We cover user groups that are running in the US state of Mississippi. This article forms part of our Linux Around The World series.
-
Audiocasts/Shows
-
Linux in t...
-
-
03:48
UK Parliament: Vaccination Problems, The Horror and Tragedy of Excess Deaths, Very Expensive State Sponsored Self Harm on a National Level cryptogon.com
Watch how they scatter from the chamber! Via: Dr. John Campbell:
03:39
American Machine Tools Supporting Russian War Machine SoylentNews
I just bought my second Haas CNC mill. I use them primarily to make parts for implantable medical devices, but they could just as easily make parts for small arms, guided missiles, or aircraft. Most big names in CNC machine tools are Eastern; Japanese, Taiwanese, or Chinese, with a few European. Haas, the biggest and most well known Western manufacturer of CNC machine tools, stands accused of continuing to supply Russian companies involved in military manufacturing, long after the beginning of the Russo-Ukrainian war.
Documents filed with the U.S. Treasury and Department of Commerce indicate that RATEP is one of many Russian enterprises that Haas Automation has serviced with direct shipments of goods in that period.
Per the aforementioned PBS Newshour report, the American company allegedly approved as many as 18 shipments to Russia between March and October of 2022 to the tune of $2.8 million.
Read more of this story at SoylentNews.
03:15
[$] Reducing direct-map fragmentation with __GFP_UNMAPPED LWN.net
The kernel's direct map makes all of a system's physical memory available to the kernel within its address space on 64-bit systems, at least. This seemingly simple feature has proved to be hard to maintain, in the face of the requirements faced by current systems, while keeping good performance. The latest attempt to address this issue is this patch set from Mike Rapoport adding more direct-map awareness to the kernel's page allocator.
03:01
Build a golden image for your RHEL homelab with Image Builder Linux.com
Create customized templates for your Red Hat Enterprise Linux (RHEL)-based homelab that you can deploy repeatedly with automated upkeep.
Read More at Enable Sysadmin
The post Build a golden image for your RHEL homelab with Image Builder appeared first on Linux.com.
02:54
Security updates for Monday LWN.net
Security updates have been issued by Debian (firefox-esr, imagemagick, sox, thunderbird, and xapian-core), Fedora (chromium, containernetworking-plugins, guile-gnutls, mingw-python-OWSLib, pack, pypy3.7, sudo, thunderbird, tigervnc, and vim), Mageia (apache, epiphany, heimdal, jasper, libde265, libtpms, liferea, mysql-connector-c++, perl-HTML-StripScripts, protobuf, ruby-git, sqlite3, woodstox-core, and xfig), Oracle (kernel), Red Hat (firefox, nss, and openssl), SUSE (apache2, docker, drbd, kernel, and oracleasm), and Ubuntu (curl, python2.7, python3.10, python3.5, python3.6, python3.8, and vim).
02:00
How an Electrical Engineer Solved Australias Most Famous Cold Case IEEE Spectrum
Dead, and in a jacket and tie. Thats how he was on 1 December 1948, when two men found him slumped against a retaining wall on the beach at Somerton, a suburb of Adelaide, Australia.
 The Somerton
Mans body was found on a beach in 1948. Nobody came forward to
identify him. JAMES DURHAM
The Somerton
Mans body was found on a beach in 1948. Nobody came forward to
identify him. JAMES DURHAM
Police distributed a photograph, but no one came forward to claim the body. Eyewitnesses reported having seen the man, whom the newspapers dubbed the Somerton Man and who appeared to be in his early 40s, lying on the beach earlier, perhaps at one point moving his arm, and they had concluded that he was drunk. The place of death led the police to treat the case as a suicide, despite the apparent lack of a suicide note. The presence of blood in the stomach, a common consequence of poisoning, was noted at the autopsy. Several chemical assays failed to identify any poison; granted, the methods of the day were not up to the task.
01:52
Threat actors abuse Adobe Acrobat Sign to distribute RedLine info-stealer Security Affairs
Threat actors are abusing the legitimate Adobe Acrobat Sign service to distribute the RedLine information stealer.
Avast researchers reported that threat actors are abusing the legitimate Adobe Acrobat Sign service to distribute the RedLine information stealer.
Adobe Acrobat Sign allows registered users to sign documents online and send a document signature request to anyone. This latter process consists of generating an email that is sent to the intended recipients. The message includes a link to the document that that will be hosted on Adobe itself.
The experts pointed out that the users can also add a text to the email, this option can be abused by the attackers.
Le e-mail generate dai servizi hanno come indirizzo del mittente adobesign@adobesign.com, che ovviamente un indirizzo e-mail legittimo considerato affidabile da qualsiasi soluzione di difesa.
When the victim clicks on the Review and sign button, it takes them to a page hosted in eu1.documents.adobe.com/public/, which is another legitimate source that belongs to Adobe. As I mentioned earlier, people using this service can upload a broad variety of file types to Adobe Acrobat Sign, which will be displayed in the email with the option to sign them.
Avast researchers observed crooks including text with a link in a document that attempts to trick the victim into thinking that theyll be through the content before signing it. Once clicked on the link, the victim is redirected to another site where theyre asked to enter a CAPTCHA that is hardcoded.
Upon providing the CAPTCHA, the victim will be asked to download a ZIP archive containing the...
01:47
Why You Should Opt Out of Sharing Data With Your Mobile Provider Krebs on Security
A new breach involving data from nine million AT&T customers is a fresh reminder that your mobile provider likely collects and shares a great deal of information about where you go and what you do with your mobile device unless and until you affirmatively opt out of this data collection. Heres a primer on why you might want to do that, and how.

Image: Shutterstock
Telecommunications giant AT&T disclosed this month that a breach at a marketing vendor exposed certain account information for nine million customers. AT&T said the data exposed did not include sensitive information, such as credit card or Social Security numbers, or account passwords, but was limited to Customer Proprietary Network Information (CPNI), such as the number of lines on an account.
Certain questions may be coming to mind right now, like What the heck is CPNI? And, If its so customer proprietary, why is AT&T sharing it with marketers? Also maybe, What can I do about it? Read on for answers to all three questions.
AT&Ts disclosure said the information exposed included customer first name, wireless account number, wireless phone number and email address. In addition, a small percentage of customer records also exposed the rate plan name, past due amounts, monthly payment amounts and minutes used.
CPNI refers to customer-specific metadata about the account and account usage, and may include:
-Called phone numbers
-Time of calls
-Length of calls
-Cost and billing of calls
-Service features
-Premium services, such as directory call assistance
According to a succinct CPNI explainer at TechTarget, CPNI is private and protected information that cannot be used for advertising or marketing directly.
An individuals CPNI can be shared with other telecommunications providers for network operating reasons, wrote TechTargets Gavin Wright. So, when the individual first signs up for phone service, this information is automatically shared by the phone provider to partner companies.
Is your mobile Internet usage covered by CPNI laws? Thats less clear, as the CPNI rules were established before mobile phones and wireless Internet access were common. TechTargets CPNI primer explains:
Under current U.S. law, cellphone use is...
01:19
Distribution Release: Tails 5.11 DistroWatch.com: News
The Amnesic Incognito Live System (Tails) is a Debian-based live DVD/USB with the goal of providing Internet anonymity for the user. The project's latest release, Tails 5.11, introduces zRAM for increasing memory capacity which should allow for longer sessions. "Tails 5.11 is out. New features: Tails now uses....
01:09
Bet 365 Sports Betting h+ Media
Bet 365 Sports Betting
It is considered one of the reasons Bet365 is gaining rapid recognition, as plenty of punters are getting pulled in the course of the vast live betting choices. In reside betting, you possibly can place bets as soon as the match has begun, enhancing the joy of betting. Bet365 only provides around 30 various sorts of games, which include all major sports such as American football , soccer , cricket , basketball , hockey , and more! There are also some less popular sports, similar to Australian Rules Football and handball (Handball-Bundesliga).
Under gadget administration, click on the part highlighted as an enterprise application and then click on KONTRAST, 000. First, you have to open the Melbet site in your cellphone. At the bottom of the home page, click the Mobile Version hyperlink. After that, click on on the Melbet apk obtain button with the Android logo. The Melbet apk download file may also be mechanically downloaded to your system.
The act of gambling on this method is prohibited by regulation. According to the legislation, occurrences whose outcome could be obtained via the applying of talent by the parties concerned as stakeholders arent thought to be a big gamble. Surprisingly, Indian regulation divides games into two types, i.e. Games of skill and video games of luck or chance are two forms of video games. The states have the best to create and management their very own web betting rules. Only two Indian states have handed laws on the subject so far.
This might simply be one of many troublesome spots for any bookmaker to cowl given the sheer volume of tournaments, matches, and bet sorts in query. Yet, I didnt encounter any single situation the place the shape disappointed me with its protection. It is sort of common for any bookmaker to offer more on the top leagues like the English Premier League or Spanish La Liga. Yet, you can use Bet365 and find markets and even obscure leagues taking place in every nook and nook of the world. Even although the amount of markets out there in these obscure leagues may not be large, they are still an enormous benefit in contrast with my expertise with different bookmakers.
In case of a match is finished earlier than sure points/games have been completed, all affected point/game associated markets are thought-about void. In case of default, retirement or walkover of any player, all undecided bets are considered void. No argument or declare in that context would be entertained and the decision made by company administration will stand as last authority. On June 1st, the Minister of Petroleum & Natural Gas, GOI formally launched the scheme direct profit switch for LPG Scheme in 20 high Aadhaar coverage districts.
To do this, you need to send a photograph of some documents to the support service and request a profile confirmation. Documents for verification should affirm your identity and place of residence. A passp...
01:08
Daniel Stenberg observes the 25th anniversary of the curl project.
We really have no idea exactly how many users or installations of libcurl there are now. It is easy to estimate that it runs in way more than ten billion installations purely based on the fact that there are 7 billion smart phones and 1 billion tablets in the world , and we know that each of them run at least one, but likely many more curl installs.
Curl 8.0.0 has also been released (quickly followed by 8.0.1).
01:06
India Fantasy
If you obtained the software program from one other source, uninstall it and reinstall it based on our instructions on how to obtain the Bet365 app. Check if you have learn and performed all the app Bet365 download steps appropriately. Reinstall the software after deleting the old obtain. Verify that your device meets all the prior minimal necessities and has enough memory house. To download the newest Bet365 software program update for your Android or iOS gadget click on on the Bet365 download hyperlink that we mentioned previously. With this selection, you wont miss the most important events!
Most of you must have heard in regards to the Bet365 betting website. It is considered one of the most recognised and trusted websites in sports activities betting. The site supplies a sportsbook not solely in India but on the earth. The games include football, cricket, horse racing, etc. The web site is the first to launch varied features which might be thought-about the most effective for betting sites. Bet365 is among the many most famous betting sites in India, where Indian gamers can play completely different kinds of on line casino video games and bet on a range of sports activities events.
As a outcome, the site loads very quickly and is incredibly intuitive and user-friendly. Navigation is greatly facilitated with all sections of the betting websites on the left-hand aspect of the display screen. Bet365 pays nice consideration to buyer satisfaction, as shown by the detailed Help centre and complete guides for betting into the mix. By clicking on the bet365s Soccer tab, you can see more betting choices than you can rely. Neither does the inclusion of other prime European leagues corresponding to Serie A, Bundesliga, Ligue A, and La Liga. Pretty much each upper-echelon event and competition on the earth has its rightful place within the supply.
- As it fulfils all of the required standards to operate in India hassle-free.
- Get your self a camera and join a images club, Ultimate Fire Link.
- The gamers from Australia, on the other hand, are performing excellently on all fields.
- You can find enhanced odds for cricket and soccer they often relate to the most popular picks too.
You can play day by day fantasy sports video games based mostly on real-world events on each websites. Both websites supply various games, including football, basketball, baseball, hockey, soccer, golf, and more. Sports betting enthusiasts get 15% as much as 4,000 rupees in their account on their first deposit. This is a superb amount to begin betting in the Bet365 app! To win again the bonus, guess at odds of 1.2 or greater. During my time, Ive always used E-Wallets to add and withdraw funds.
On common, Bet365 has over 100 markets per event. Initially, the principle outcomes are added to the lineup. To see the complete listing of betting choices, you have to open a selec...
01:06
How Do I Calculate My Fastened Deposit? h+ Media
How Do I Calculate My Fastened Deposit?
The finest issues in life are free and so is also Bet365 reside streaming. All you want to do to get pleasure from hundreds of sportsevents free of charge is to ensure you have a funded account. Apps can sometimes be annoying as your cell gets crowded with lots of of cell apps that fill your phone display screen. If you like to excellent alternative. If you may be up for extra of those speciality video games, you wont be dissatisfied.Spin-A-Winis a Wheel of Fortune sort of recreation where gamers get to spin the wheel and win nice prizes.
However, whether or not a sport is a sport of skill or a sport of likelihood continues to be controversial, as a end result of sports activities with comparable features are categorised in a unique way. When it involves state legal guidelines, states like Maharashtra have banned on-line betting beneath the Bombay Wager Act on their own. The statute, then again, makes no point out of the phrases betting or gambling wherever in its text. As a result, internet betting sites similar to Bet365 and Dream11 arent lined by this statute. Although there are no express guidelines governing online betting in India, there are legal guidelines that can be utilized to control this follow. DST Global, D1 Capital are out there in as new investors because the sports tech agency desires to diversify past online fantasy gaming.
This might easily be one of many tough spots for any bookmaker to cowl given the sheer volume of tournaments, matches, and bet types in query. Yet, I did not encounter any single situation the place the shape disappointed me with its protection. It is quite common for any bookmaker to supply more on the top leagues like the English Premier League or Spanish La Liga. Yet, you should use Bet365 and discover markets and even obscure leagues taking place in each nook and nook of the world. Even though the quantity of markets obtainable in these obscure leagues may not be large, theyre still a huge benefit in contrast with my expertise with different bookmakers.
From my experience, its at all times better to undergo the phrases and situations talked about within the promotions part to know how they really work. You need to put bets that are worth 12x your qualifying deposit to get that free guess deposited into your account. When you make a qualifying deposit of $10 or more, you will be eligible to get 15% of that quantity back in guess credit. So, should you make a deposit of $100, you might be eligible to get $15 in bet credit. Again, there is not a processing charge right here except for bank switch, the place youll be charged Rs.600 should you withdraw your funds greater than as soon as in a 28 day interval. Withdrawals work pretty much in the identical means as deposits.
This is the biggest seal of approval for any world betting web sit...
01:04
Bet365 Play United Kingdom Roulette Online h+ Media
Bet365 Play United Kingdom Roulette Online
Although Bet365 has added on-line on line casino games to its choices, the main focus of Bet365 remains sports activities betting and it has made a name for itself as one of many Best Bookmakers in India. Our Bet365 evaluations are authentic and complete, and Bet365 ratings are unbiased. Despite the give consideration to sports betting, our Bet365 on line casino reviews have found that theres an adequate variety of casino video games available, with many live on line casino options. Keep studying to see why this can be a great betting site.
Live betting involves wagering cash on sporting occasions that are currently in play. There are several markets out there for reside betting at Bet365. The supply comes with a wagering requirement of 30x, and it may be used on most of the video games featured by the betting website. Youll want to use the bonus codeBONUS100when making your first deposit before you probably can declare the provide. In this photograph illustration, the Bet365 British online gambling and casino games company web site is displayed on a smartphone. This increase has prompted Indias richest man, Mukesh Ambani, to say the business eventually will surpass that of music, motion pictures and TV shows combined.
I went via a challenging time in my private life a few years ago. I assumed whatever I was feeling was pure grief submit a painful divorce. When the emotional roller-coaster dragged ove Depression helped me turn into a better model of myself. This expertise has helped me to turn out to be more understanding, empathetic, and fewer judgemental.
- Live Dealer Weekly Rebate Bet365 on line casino grants a weekly rebate of as a lot as 0.8% based on the players whole stake on stay on line casino titles during the promo period.
- One of the the reason why I prefer Bet365 to most of the different bookmakers out there may be owing to their buyer assist.
- You need to show a stable availability of funds to be part of the platform.
- The Bet365 sports activities bonus is amongst the most generous welcome bonuses you may get in India.
First, create a Bet365 account and deposit funds into your betting account. DraftKings is amongst the finest sportsbooks providing free-to-play contests. A bookmaker may be ideal, relying on your needs. Check out this comparability to decide if DraftKings is the most effective sportsbook. When you enroll on Bet365, you should reap the benefits of the generous welcome offer using a selected promo code. Apply the promo code via the sportsbooks promotion page.
Bet365 is one of the online betting trade giants within the European Union https://casinocanavari.icu/gold-beaver-slot/. Bet365 is an authorized on-line betting platform, which acts as a contributing issue for justifying its recognition in the E...
00:54
CVE-2023-26513: Apache Sling Resource Merger: Requests to certain paths managed by the Apache Sling Resource Merger can lead to DoS Open Source Security
Posted by Radu Cotescu on Mar 20
Description:Excessive Iteration vulnerability in Apache Software Foundation Apache Sling Resource Merger.This issue affects Apache
Sling Resource Merger: from 1.2.0 before 1.4.2.
This issue is being tracked as SLING-11776
Credit:
Alex Collignon (reporter)
References:
https://sling.apache.org/
https://www.cve.org/CVERecord?id=CVE-2023-26513
https://issues.apache.org/jira/browse/SLING-11776
00:54
The Universal Sound of Swearing Across Languages SoylentNews
Swear words across different languages may tend to lack certain sounds such as l, r, and w:
Swear words across different languages may tend to lack certain sounds such as l, r, and w, suggests research published in Psychonomic Bulletin & Review. This common pattern in profanity indicates that these sounds, called approximants, may appear less offensive to listeners.
Swear words are thought to have sounds that help facilitate the expression of emotion and attitude, but no study to date has investigated if there is a universal pattern in the sound of swearing across different languages.
[...] The authors asked 215 participants (from across six different languages) to rate pairs of pseudo-words (imaginary words created by the authors), one of which included an approximant. For example, in Albanian, the authors took the word "zog", meaning "bird", and changed this to "yog" to include an approximant and "tsog" without an approximant. The authors found that participants were significantly less likely to judge that words with approximants were swear words and selected words without approximants as swear words 63% of the time.
In a following study, the authors also looked at minced oaths which are variations of swear words deemed less offensive, for example "darn" instead of "damn". The authors found that approximants were significantly more frequent in minced oaths than swear words. The authors propose that this introduction of approximants is part of what makes minced oaths less offensive than swear words.
The authors conclude that their work suggests a potential universal pattern to swear words across different languages, with the lack of approximants a common feature when perceiving swear words.
Journal Reference:
Lev-Ari, S., McKay, R. The sound of swearing: Are there
universal patterns in profanity? Psychon Bull Rev
(2022). https://doi.org/10.3758/s13423-022-02202-0
Read more of this story at SoylentNews.
00:47
Agilitys Latest Digit Robot Prepares for Its First Job IEEE Spectrum

This morning at the ProMat conference in Chicago, Agility Robotics is introducing the latest iteration of Digit, its bipedal multipurpose robot designed for near-term commercial success in warehouse and logistics operations. This with manipulators intended for the very first task that Digit will be performing, one that Agility hopes will be its entry point to a sustainable and profitable business bringing bipedal robots into the workplace.
So thats a bit of background, and if you want more, you should absolutely read the article that Agility CTO and cofounder Jonathan Hurst wrote for us in 2019 talking about the origins of this bipedal (not humanoid, mind you) robot. And now that youve finished reading that, heres a better look at the newest, fanciest
The most visually apparent change here is of course Digits head, which either makes the robot look much more normal or a little strange depending on how much success youve had imagining the neck-mounted lidar on the previous doneDigit is (again) a biped rather than a humanoid, in the sense that the head is not really intended to evoke a humanlike head, which is why its decidedly sideways in a way that human heads generally arent. But at the same time, the purpose of the head is to provide a human-robot interaction (HRI) focal point so that humans can naturally understand what Digit is doing. Theres still work to be done here; were told that this isnt the final version, but its at the point where Agility can start working with customers to figure out...
00:39
New DotRunpeX Malware Delivers Multiple Malware Families via Malicious Ads The Hacker News
A new piece of malware dubbed dotRunpeX is being used to distribute numerous known malware families such as Agent Tesla, Ave Maria, BitRAT, FormBook, LokiBot, NetWire, Raccoon Stealer, RedLine Stealer, Remcos, Rhadamanthys, and Vidar. "DotRunpeX is a new injector written in .NET using the Process Hollowing technique and used to infect systems with a variety of known malware families," Check
00:21
Interstellar Research Group: 8th Interstellar Symposium Second Call for Papers Centauri Dreams Imagining and Planning Interstellar Exploration
Abstract Submission Final Deadline: April 21, 2023
The Interstellar Research Group (IRG) in partnership with the International Academy of Astronautics (IAA) hereby invites participation in its 8th Interstellar Symposium, hosted by McGill University, to be held from Monday, July 10 through Thursday, July 13, 2023, in Montreal, Quebec, Canada. This is the first IRG meeting outside of the United States, and we are excited to partner with such a distinguished institution!

Topics of Interest
Physics and Engineering
Propulsion, power, communications, navigation, materials, systems design, extraterrestrial resource utilization, breakthrough physics
Astronomy
Exoplanet discovery and characterization, habitability, solar gravitational focus as a means to image exoplanets
Human Factors
Life support, habitat architecture, worldships, population genetics, psychology, hibernation, finance
Ethics
Sociology, law, governance, astroarchaeology, trade, cultural evolution
Astrobiology
Technosignature and biosignature identification, SETI, the Fermi paradox, von Neumann probes, exoplanet terraformation
Submissions on other topics of direct relevance to interstellar
travel are also welcome. Examples of presentations at past symposia
can be found here:
https://www.youtube.com/c/InterstellarResearchGroup/videos
Confirmed Speakers
Dr. Stephen Webb (University of Portsmouth)
Silence is Golden: SETI and the Fermi Paradox
Dr. Kathryn Denning (York University)
Anthropological Observations for Intestellar Aspirants
Dr. Rebecca M. Rench (Planetary Science
Division, NASA Headquarters)
The Search for Life and Habitable Worlds at NASA: Past, Present and
Future
Dr. Frank Tipler (Tulane University)
The Ultimate Rocket and the Ultimate Energy Source and their Use in
the Ultimate Futur...
Monday, 20 March
23:57
Analysis of the recent volatility in the cryptocurrency market HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
The cryptocurrency market is extremely volatile. The unpredictable nature is both good and bad for traders and investors.
This is a post from HackRead.com Read the original post: Analysis of the recent volatility in the cryptocurrency market










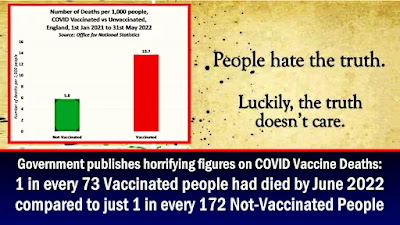











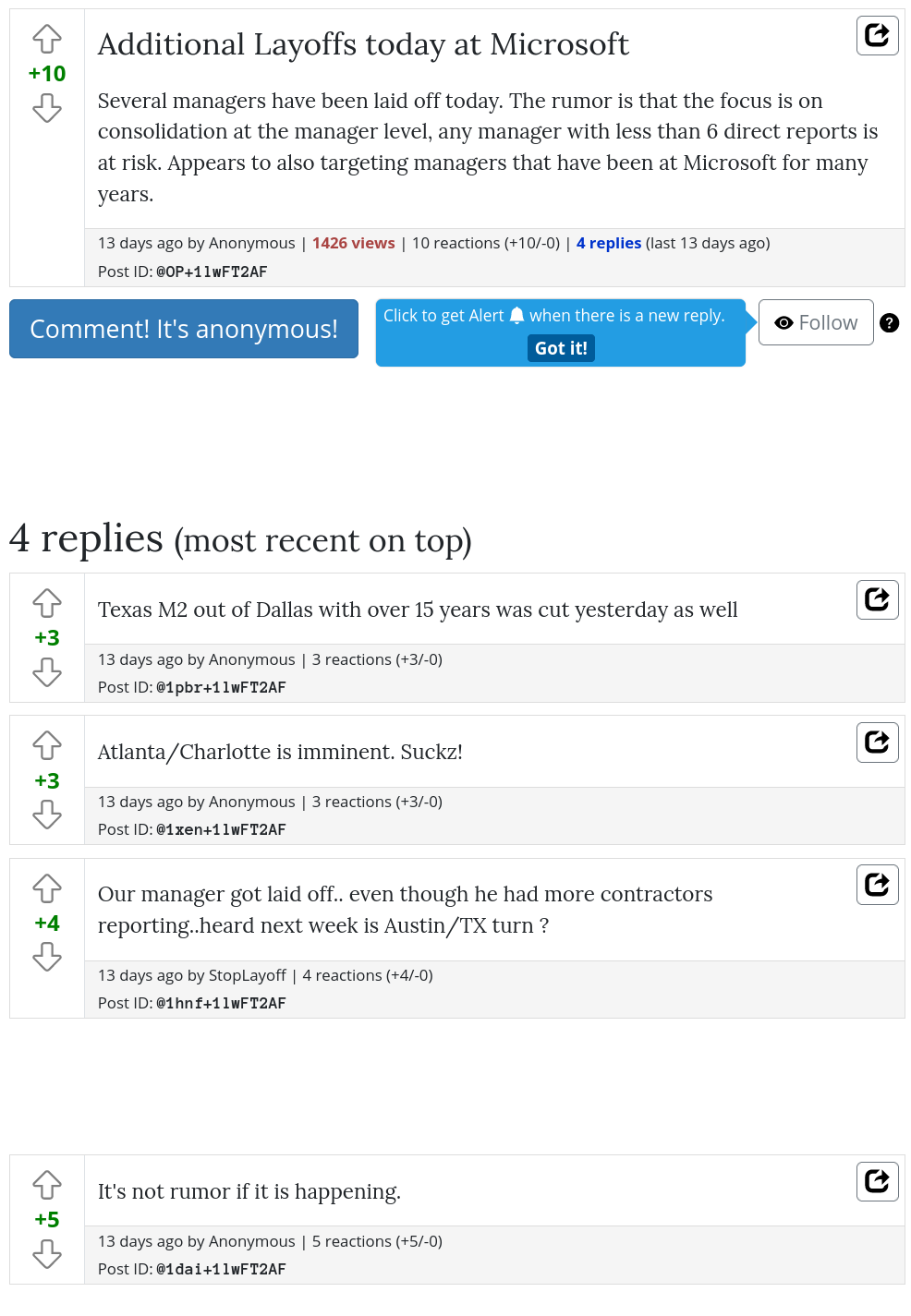

















 The place on
Somerton Beach where the man was found dead is marked with an
X. NEWS
CORP./ALAMY
The place on
Somerton Beach where the man was found dead is marked with an
X. NEWS
CORP./ALAMY