| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Wednesday, 15 March
02:03
ALPHV ransomware gang claims it has hacked Amazons Ring HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
ALPHV Ransomware group threatens to leak sensitive data stolen from amazon's ring security cameras unless demands are met.
This is a post from HackRead.com Read the original post: ALPHV ransomware gang claims it has hacked Amazons Ring
02:00
Development Release: Fedora 38 Beta DistroWatch.com: News
The Fedora project has published a beta snapshot of the distribution's upcoming Fedora 38 release. The new beta features GNOME 44, updtaed development tools, and strict compile flags to protect against common memory attacks. "Fedora 38 Workstation Beta includes GNOME 44. Its currently in beta, with a final....
01:45
ASUS Unveils The Tinker V As Their First RISC-V Board Phoronix
For over a half-decade ASUS has been selling the Thinker Board devices as their line of Raspberry Pi alternatives. To date the ASUS Tinker Board single board computers have all been Arm-based while now they have launched their first RISC-V board, the Tinker V...
01:12
SSD Reliability is Only Slightly Better Than HDD, Backblaze Says SoylentNews
SSD Reliability is Only Slightly Better Than HDD, Backblaze Says
A surprising outcome for the first SSD-based AFR report:
Backblaze is a California-based company dealing with cloud storage and data backup services. Every year, the organization provides some interesting reliability data about the large fleet of storage units employed in its five data centers around the world.
For the first time, Backblaze's latest report on storage drive reliability is focusing on Solid State Drives (SSD) rather than HDD units alone. The company started using SSDs in the fourth quarter of 2018, employing the NAND Flash-based units as boot drives rather than data-storing drives. Backblaze uses consumer-grade drives, providing Annualized Failure Rate (AFR) information about 13 different models from five different manufacturers.
The 2022 Drive States review is based on data recorded from 2,906 SSD boot units, Backblaze states, and it is essentially confirming what the company was saying in its 2022 mid-year report. SSDs are more reliable than HDDs, Backblaze says, as they show a lower AFR rate (0.98%) compared to HDDs (1.64%).
The fact that the difference in reliability level isn't exactly staggering (0.66% AFR) is rather surprising, however, as SSDs are essentially just moving electrons through memory chips while hard drives have to deal with a complex (and failure-prone) mechanism employing spinning platters and extremely sensitive read/write magnetic heads.
The reasons behind failing drives aren't known, as only an SSD manufacturer would have the equipment needed to make a reliable diagnose. For 2022, Backblaze says that seven of the 13 drive models had no failure at all. Six of those seven models had a limited number of "drive days" (less than 10,000), the company concedes, meaning that there is not enough data to make a reliable projection about their failure rates.
An interesting tidbit about Backblaze's report is that the company hasn't used a single SSD unit made by Samsung, which is a major player in the SSD consumer market. One possible explanation is that Samsung drives aren't cheap, and Backblaze is essentially using the cheapest drives they can buy in bulk quantities.
Read more of this story at SoylentNews.
01:08
Security updates for Tuesday LWN.net
Security updates have been issued by Debian (redis), Fedora (cairo, freetype, harfbuzz, and qt6-qtwebengine), Red Hat (kpatch-patch), SUSE (chromium, java-1_8_0-openj9, and nodejs18), and Ubuntu (chromium-browser, libxstream-java, php-twig, twig, protobuf, and python-werkzeug).
01:04
Software supply chain attacks are on the rise are you at risk? Graham Cluley
Graham Cluley Security News is sponsored this week by the folks at Sysdig. Thanks to the great team there for their support! Attacks targeting the software supply chain are on the rise and splashed across the news. SolarWinds raised awareness about the risk. More recent events, like the Federal Civilian Executive Branch (FCEB) agency breach, Continue reading "Software supply chain attacks are on the rise are you at risk?"
01:00
PCIe For Hackers: The Diffpair Prelude Hackaday

PCIe, also known as PCI-Express, is a highly powerful interface. So lets see what it takes to hack on something that powerful. PCIe is be a bit intimidating at first, however it is reasonably simple to start building PCIe stuff, and the interface is quite resilient for hobbyist-level technology. There will come a time when we want to use a PCIe chip in our designs, or perhaps, make use of the PCIe connection available on a certain Compute Module, and its good to make sure that were ready for that.
PCIe is everywhere now. Every modern computer has a bunch of PCIe devices performing crucial functions, and even iPhones use PCIe internally to connect the CPU with the flash and WiFi chips. You can get all kinds of PCIe devices: Ethernet controllers, high-throughput WiFi cards, graphics, and all the cheap NVMe drives that gladly provide you with heaps of storage when connected over PCIe. If youre hacking on a laptop or a single-board computer and youd like to add a PCIe device, you can get some PCIe from one of the PCIe-carrying sockets, or just tap into an existing PCIe link if theres no socket to connect to. Its been two decades since weve started getting PCIe devices now, PCIe is on its 5.0 revision, and its clear that its here to stay.
...
00:47
Oceanic Surprise: Pushing Europas Ice Centauri Dreams Imagining and Planning Interstellar Exploration
Getting Europa Clipper to its target to analyze the surface of Jupiters most interesting moon (in terms of possible life, at least) sets up a whole range of comparative studies. We have been mining data for many years from the Galileo mission and will soon be able at last! to compare its results to new images pulled in by Europa Clippers flybys. Out of this comes an interesting question recently addressed by a new paper in JGR Planets: Is Europas ice shell changing in position with time?
An answer here would establish whether we are dealing with a free-floating shell moving at a different rate than the salty ocean beneath. Computer modeling has previously suggested that the oceans effects on the shell may affect its movement, but this is evidently the first study that calculates the amount of drag involved in this scenario. Ocean flow may explain surface features Galileo revealed, with ridges and cracks as evidence of the stretching and straining effects of currents below.
Hamish Hay (University of Oxford) is lead author of the paper on this work, which was performed at the Jet Propulsion Laboratory during his postdoctoral tenure there. The study reveals a net torque on the ice shell from ocean currents moving as alternating east-west jets, sometimes spinning up the shell and at other times spinning it down as convection is altered by the evolution of the moons interior. Says Hay:
Before this, it was known through laboratory experiments and modeling that heating and cooling of Europas ocean may drive currents. Now our results highlight a coupling between the ocean and the rotation of the icy shell that was never previously considered.
Thus we are forced to reconsider some old assumptions, one of them being that the primary force acting on Europas surface is the gravitational pull of Jupiter. The paper calculates that an average jet speed of at least ~1 cm s-1 produces enough ice-ocean torque to be comparable to tidal torque. Calling these results a huge surprise, Europa Clipper project scientist Robert Pappalardo (JPL) notes that thinking about ocean circulation as the driver of surface cracks and ridges takes scientists in a new direction: [G]eologists dont usually think, Maybe its the ocean doing that.

Image: This view of Jupiter&#...
00:29
STALKER 2 hacker demands Ukrainian game developer reinstates Russian language support, or else Graham Cluley
A Ukrainian video game developer has revealed that a hacker has leaked development material stolen from the company's systems, and is threatening to release tens of gigabytes more if their unorthodox ransom demands are not met.
00:24
How Will The World End? Lifeboat News: The Blog
End of World Scenarios what are they? what is likely and what is not?
Posted on Big Think, direct link at.
Posted on Big Think.
00:23
Joel Greshock VP, Oncology, Data Science & Digital Health Janssen Research & Development Lifeboat News: The Blog

Driving Toward the Elimination of Cancer Joel Greshock VP, Oncology, Data Science & Digital Health, Janssen Pharmaceutical Companies of Johnson & Johnson.
Joel Greshock is VP, Oncology, Data Science & Digital Health, Janssen Research & Development (https://www.janssen.com/oncology/leadership-team). In this position, he is responsible for creating unique and actionable medical insights using large and increasingly available datasets. The focus of this research includes discovering novel therapeutic targets, identifying areas of unmet medical need, and enhancing clinical trial recruitment and execution.
Prior to joining Janssen R&D, Joel served as Vice President of Bioinformatics at Neon Therapeutics, Inc., where he built and managed the Data Sciences organization. At Neon, he was responsible for the design and deployment of personalized cancer therapies now under clinical evaluation.
Prior to joining Neon, Joel served as Head of Oncology Translational Informatics for Novartis, where he was responsible for the correlation of patient outcomes with molecular biomarkers, identification of mechanisms of clinical resistance and computational research for assets approaching or being evaluated in early phases of development.
Before joining Novartis, Joel assumed numerous roles for GlaxoSmithKline Oncology, which included Head of Bioinformatics. Earlier in his career, Joel was a Data Analyst at Abramson Family Cancer Research Institute at the University of Pennsylvania, where he built early generation microarray platforms and developed widely used predictive models for cancer predisposition mutations.
Joel holds a Bachelor of Science in Comprehensive Science and a Master of Science in Biology/Biostatistics, both from Villanova University. He also completed studies at the University of Pennsylvania and Temple University in Statistics and Computer Science.
00:22
An AI Learned to Play Atari 6,000 Times Faster Lifeboat News: The Blog

We dont learn by brute force repetition. AI shouldnt either.
Despite impressive progress, todays AI models are very inefficient learners, taking huge amounts of time and data to solve problems humans pick up almost instantaneously. A new approach could drastically speed things up by getting AI to read instruction manuals before attempting a challenge.
One of the most promising approaches to creating AI that can solve a diverse range of problems is reinforcement learning, which involves setting a goal and rewarding the AI for taking actions that work towards that goal. This is the approach behind most of the major breakthroughs in game-playing AI, such as DeepMinds AlphaGo.
As powerful as the technique is, it essentially relies on trial and error to find an effective strategy. This means these algorithms can spend the equivalent of several years blundering through video and board games until they hit on a winning formula.
Tuesday, 14 March
23:56
What You Need to Know to Create a Winning Hybrid Workplace HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
The global epidemic prompted enterprises to operationalize their businesses by switching to remote work. According to numerous surveys,
This is a post from HackRead.com Read the original post: What You Need to Know to Create a Winning Hybrid Workplace
23:55
Fedora 38 Beta Released With Many Exciting Updates Phoronix
The beta of Fedora 38 is out and on-time this morning for those wanting to test this latest major update to Fedora Linux...
23:02
GoBruteforcer: New Golang-Based Malware Breaches Web Servers Via Brute-Force Attacks The Hacker News
A new Golang-based malware dubbed GoBruteforcer has been found targeting web servers running phpMyAdmin, MySQL, FTP, and Postgres to corral the devices into a botnet. "GoBruteforcer chose a Classless Inter-Domain Routing (CIDR) block for scanning the network during the attack, and it targeted all IP addresses within that CIDR range," Palo Alto Networks Unit 42 researchers said. "The threat actor
22:52
The Prolificacy of LockBit Ransomware The Hacker News
Today, the LockBit ransomware is the most active and successful cybercrime organization in the world. Attributed to a Russian Threat Actor, LockBit has stepped out from the shadows of the Conti ransomware group, who were disbanded in early 2022. LockBit ransomware was first discovered in September 2019 and was previously known as ABCD ransomware because of the ".abcd virus" extension first
22:50
Advanced actor targets Fortinet FortiOS in attacks on govt entities Security Affairs
An unknown threat actor is targeting Government entities and large organizations by exploiting a security flaw in Fortinet FortiOS.
Fortinet researchers are warning of an advanced threat actor and is targeting governmental or government-related entities.
The unknown threat actor is exploiting a vulnerability in Fortinet FortiOS software, tracked as CVE-2022-41328, that may allow a privileged attacker to read and write arbitrary files via crafted CLI commands.
The CVE-2022-41328 vulnerability (CVSS score: 6.5) is a path traversal issue in FortiOS can can result in arbitrary code execution.
A improper limitation of a pathname to a restricted directory vulnerability (path traversal) [CWE-22] in FortiOS may allow a privileged attacker to read and write arbitrary files via crafted CLI commands. reads the advisory published by Fortinet.
The vulnerability impacts FortiOS versions 6.0, 6.2, 6.4.0 through 6.4.11, 7.0.0 through 7.0.9, and 7.2.0 through 7.2.3. The company addressed the vulnerability with the release of versions 6.4.12, 7.0.10, and 7.2.4 respectively.
Fortinet launched an investigation into the attacks after the FortiGate devices of one customer suddenly halted and failed to reboot. The devices halted displaying the following error message:
System enters error-mode due to FIPS error: Firmware Integrity self-test failed
The failure of the integrity test blocks the re-boot of the device to protect the integrity of the network.
The researchers discovered that the attackers modified the /sbin/init folder in the firmware image, they noticed the presence of a new file /bin/fgfm. The modification aims at providing a persistent access to the attacker.
The modification to /sbin/init ensures that /bin/fgfm, which may provide an attacker with persistent access and control, runs before proceeding with regular boot-up actions. reads the analysis published by Fortinet.
Upon executing the fgfm malware, it contacts a remote server (C2) and awaits for commands to execute.
The malicious code can perform various actions depending on the commands it receives from the C&C server, including exit program, exfiltrate data, download/write files, establish a remote shell.
The security firm pointed out that the exploit requires a deep understanding of FortiOS and the underlying hardware, a circumstance that suggests t...
22:43
CISA warns CI operators about vulnerabilities on their networks exploited by ransomware gangs Help Net Security
Organizations in critical infrastructure sectors whose information systems contain security vulnerabilities associated with ransomware attacks are being notified by the US Cybersecurity and Infrastructure Security Agency (CISA) and urged to implement a fix. A pilot program to strengthen critical infrastructure against ransomware CISA leverages multiple open-source and internal tools to research and detect vulnerabilities within U.S. critical infrastructure, the agency explained in the formal announcement of its Ransomware Vulnerability Warning Pilot (RVWP). CISA additionally leverages More
The post CISA warns CI operators about vulnerabilities on their networks exploited by ransomware gangs appeared first on Help Net Security.
22:43
Security issue in Hotspot elevate_perf_privileges.sh (CVE-2023-28144) Open Source Security
Posted by Matthias Gerstner on Mar 14
Hello list,this report is about a possible security vulnerability I found in the Hotspot
[1] project.
An openSUSE packager for hotspot requested a review of a Hotspot update to
and Polkit
authentication. During the review I found a vulnerability in the helper script
`elevate_perf_privileges.sh` that is likely not exploitable by default, but
could easily become a local root...
22:38
Re: sox: patches for old vulnerabilities Open Source Security
Posted by Helmut Grohne on Mar 14
The original fix for this issue would cause a regression. After applyingit, sox would be unable to decode WAV GSM files. This has been reported
as https://bugs.debian.org/1032082. I am attaching an updated patch that
fixes this regression. It is meant to replace the previous patch. The
updated patch includes a regression test case to avoid repeating the
mistake.
I see that most distributions (e.g. RedHat, SUSE, Gentoo, etc.) have not
picked up...
22:34
FBI reveals that more money is lost to investment fraud than ransomware and business email compromise combined Graham Cluley
The latest annual FBI report on the state of cybercrime has shown a massive increase in the amount of money stolen through investment scams. Read more in my article on the Hot for Security blog.
22:26
How We Navigate Through Crowds SoylentNews
Whether you are making your way through a crowded pedestrian zone or striving towards the goal in a team game, in both situations it is important to think not only about your own movements but also those of others. These navigation and orientation processes are carried out by brain cells that register our current position, where we are coming from, where we are moving towards and in which direction we are looking. Through their joint activity, they create a "map" of our surroundings. A special type of these cells are the so-called grid cells in the entorhinal cortex, a small brain region in the middle temporal lobe. They function like the brain's own GPS, because they not only represent our position in space, but can also put it in relation to other points in the same space.
[...] They found that the brain activity recorded while watching others was comparable to the activity of grid cells. In addition, the team was able to show that this activity was part of a larger network of brain regions that are associated with navigation processes. Interestingly, however, it turned out that the better a subject was at following the path of others, the less active this network was. "We interpret this as greater efficiency of the grid cells, which might make it less necessary to engage the larger brain network," Wagner explains.
The results of the study thus suggest that grid cells belong to a larger network of brain regions that, among other aspects, coordinates navigation processes. However, this network is particularly affected by ageing processes and especially by dementia. Wagner explains: "The function of grid cells decreases with age and dementia. As a result, people can no longer find their way around and their orientation is impaired." The group's further research is now dedicated to the question of whether grid cells are also involved in recognising other people - an aspect that is often impaired in advanced dementia.
Journal Reference:
Wagner, I.C., Graichen, L.P., Todorova, B. et al.
Entorhinal grid-like codes and time-locked network dynamics
track others navigating through space. Nat Commun
14, 231 (2023). https://doi.org/10.1038/s41467-023-35819-3
Read more of this story at SoylentNews.
22:25
The Future of VPNs Lifeboat News: The Blog
This post is also available in:  (Hebrew)
(Hebrew)
According to a report done by Surfshark VPN, out of the approximately 5 billion of internet users, over 1.6 billion of them (31% of users) use a VPN. Thats close to a fifth of the worlds population.
A VPN, or a Virtual Private Network, is a mechanism for creating a secure connection between a computing device and a computer network, or between two networks, using an insecure communication medium such as the public Internet. A VPN can extend a private network (one that disallows or restricts public access), enabling users to send and receive data across public networks as if their devices were directly connected to the private network.
22:24
6 Theories About What Lies Outside The Observable Universe! Lifeboat News: The Blog

For copyright contact: stienlemane2379(at)gmail.com.
Welcome to Futureunity, where we explore the fascinating world of science, technology, and the universe! From the inner workings of the human body to the outer reaches of space, we delve into the latest and most interesting discoveries that are shaping our world. Whether youre a science buff or just looking for some mind-blowing facts, weve got you covered. Join us as we uncover the mysteries of the world around us and discover new frontiers in the fields of science and technology. Get ready for a journey thats both educational and entertaining!
Disclaimer Fair Use:
1. The videos have no negative impact on the original works.
2. The videos we make are used for educational purposes.
3. The videos are transformative in nature.
4. We use only the audio component and tiny pieces of video
footage, only if its necessary.
Copyright Disclaimer under section 107 of the Copyright Act 1976,
allowance is made for fair use for purposes such as criticism,
comment, news reporting, teaching, scholarship, education, and
research. Fair use is a use permitted by copyright statutes that
might otherwise be infringing.
Disclaimer:
Our channel is based on facts, rumors & fiction.
22:23
A modal defense of strong AI Lifeboat News: The Blog
Dropbox is a free service that lets you bring your photos, docs, and videos anywhere and share them easily. Never email yourself a file again!
22:12
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Peter Bex on Mar 14
Indeed, the GitHub issue makes this clear as well (that's why Ispecifically mentioned opendoas and not doas in general).
It just shows that even for security-minded folks it's a big trap
to fall into.
This is the case *especially* when either
a) the developers are mainly working on OpenBSD
or
b) it's a port from OpenBSD
Because it isn't even an issue there. And you wouldn't expect an
OpenBSD-developer to include a PTY...
22:06
High Court Bans Singer From Hitting YouTube Rival With DMCA Notices TorrentFreak
 Having developed a highly automated system that attempts
to deal with huge and increasing instances of piracy, YouTube has
shown it can handle copyright complaints on an unprecedented
scale.
Having developed a highly automated system that attempts
to deal with huge and increasing instances of piracy, YouTube has
shown it can handle copyright complaints on an unprecedented
scale.
Whether the next stages of development will tackle widespread abuse of the takedown system remains to be seen but the High Court of Justice, via the Business and Property Court in Birmingham, UK, hopes to reduce the volume, if only by a little.
Two Can Play The Takedown Game
Those with both the time and the patience to read the judgment handed down last week in Moviebox Megastores International Ltd & Ors v Rahi & Ors will likely emerge from the other side with a) a headache and b) relief that relatively few copyright takedown abuse cases ever get near a courtroom.
The judgment references a trial related to three sets of proceedings that were consolidated by court order in 2021.
The Courts timeline of the dispute dates back to February 2017 when singer and claimed songwriter Mohammad Rahi emailed Kamraan Ahmed, a director of music publisher Moviebox Megastores International Limited. Rahi warned that if his music albums werent removed from Movieboxs YouTube channel and from iTunes, legal action would follow.
When Ahmed refused to remove the albums, Rahi responded by setting up his own YouTube channel, populated with music he claimed to own. A month after that, in April 2017, Rahi filed copyright claims at iTunes for four of his albums published by Moviebox, and six published on iTunes by the second claimant in the case, Oriental Star Agencies Ltd. All complaints were rejected.
In May 2017, Moviebox used YouTubes Content ID system to take all revenue generated by Rahi in respect of four albums hed uploaded to his newly-created YouTube channel. Two years later in October 2019, Rahi began filing applications at the Intellectual Property Office in Pakistan seeking copyright certificates for a number of songs, and a book in which several songs were written.
Game On: Laying the Foundations
The background to the dispute is an extraordinary maze of claims, counterclaims, and bitterness spread out over several years, during which documents were forensically examined and fingerprints subjected to professional scrutiny.
The Courts judgment, dated March 8, 2023, is concise yet still manages to weigh in at almost 54,000 words; our focus here will be on the YouTube takedown campaign and the subsequent fallout.
Rahis albums were legally obtained by one company and then transferred to another; both companies operated under Moviebox branding. It was alleged that two of Rahis co-defendants, Mr Quresh...
22:03
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Hanno Bck on Mar 14
Though some context is relevant here: doas is a tool from OpenBSD.According to the Linux kernel commit message [1] OpenBSD has fixed this
already 3 years ago by entirely removing TIOCSTI [2][3].
[1]
https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=83efeeeb3d04
[2] https://undeadly.org/cgi?action=article;sid=20170701132619
[3] https://marc.info/?l=openbsd-cvs&m=149870941319610
22:00
Three Way LED Bulb Gives Up Its Secrets Hackaday

Youve probably seen three-way bulbs. You know, the ones that can go dim or bright with each turn of a switch. [Brian Dipert] wondered how
Inside the LED, [Brian] found two rings of LEDs that took the place of the filaments. He was able to identify all the ICs and devices on the board except one, an MT7712S. If you can read Mandarin, we think this is the datasheet for it.
We werent sure what [Brian] would find inside. After all, you could just sense which contacts had voltage and dim the LEDs using PWM. It probably wouldnt take any less circuitry. LED lighting is everywhere these days, and maybe they don̵...
22:00
Vulkanised 2023 Vulkan Conference Slides/Videos Available Phoronix
Taking place last month in the most wonderful city of Munich, The Khronos Group hosted Vulkanised 2023 as their Vulkan Developers' Conference and Meetup. The slides and videos from the event are now available, including talks on Valve's RADV effort and more...
21:48
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Peter Bex on Mar 14
thisexact bug as well: https://github.com/Duncaen/OpenDoas/issues/106
Cheers,
Peter
21:45
AMD Launches The EPYC Embedded 9004 Series Phoronix
AMD is using Embedded World 2023 in Nrnberg to launch the EPYC Embedded 9004 series as their 4th Gen EPYC processors intended for telecommunications, edge computing, automation, and IoT applications...
21:38
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Jakub Wilk on Mar 14
* Hanno Bck <hanno () hboeck de>, 2023-03-14 09:51:I believe this is the post in question:
https://www.openwall.com/lists/oss-security/2017/06/03/9
Nice, but...
On Linux virtual terminals, it's possible to achieve pretty much the
same effect using TIOCLINUX, the ioctl used by gpm to implement
copy&pasting.
I've attached a minimal PoC. A more elaborate one is here:
https://github.com/jwilk/ttyjack
21:33
21:28
How Cloudflare Updates The BIOS & Firmware Across Thousands Of Servers Phoronix
For those wondering how Cloudflare keeps their thousands of servers around the world up-to-date for the latest BIOS and firmware, Cloudflare's engineering blog has put out an interesting post that outlines their process of handling system BIOS updates as well as various other firmware updates...
21:17
Ubuntu Core now compatible with the Arm SystemReady IR systems specification Help Net Security
Canonical announced its Ubuntu Core OS is now compatible with the Arm SystemReady IR system specification, enabling security best practices across connected devices. In addition, the OS has achieved the PSA Certified Level 1. Ubuntu Core is a minimal devices, IoT devices, and other similar applications. It is a lightweight and secure Linux-based operating system that is optimized for efficiency and performance. Arm SystemReady More
The post Ubuntu Core now compatible with the Arm SystemReady IR systems specification appeared first on Help Net Security.
21:11
Microsoft Warns of Large-Scale Use of Phishing Kits to Send Millions of Emails Daily The Hacker News
An open source adversary-in-the-middle (AiTM) phishing kit has found a number of takers in the cybercrime world for its ability to orchestrate attacks at scale. Microsoft Threat Intelligence is tracking the threat actor behind the development of the kit under its emerging moniker DEV-1101. An AiTM phishing attack typically involves a threat actor attempting to steal and intercept a target's
21:02
KDE KWin's Move Away From GBM Surfaces Phoronix
KDE developer Xaver Hugl has written a blog post how the KWin compositor's DRM back-end has been working to move itself off GBM surfaces (gbm_surfaces) to instead allocate buffers directly and import them into EGL. This ultimately should be a win for the KWin compositor once everything is complete...
19:52
TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Hanno Bck on Mar 14
Hi,This blogpost highlights TTY Pushback vulnerabilities enabled via the
TIOCSTI kernel functionality available in the Linux kernel:
https://www.errno.fr/TTYPushback.html
This has been discussed here previously:
https://www.openwall.com/lists/oss-security/2017/06/03/9
Though I think there are some noteworthy updates. In the 2017 post
solar designer mentioned that the Linux kernel developers have multiple
times rejected changes in the kernel....
19:42
Wildfire Smoke Eroded Ozone Layer by 10 Percent in 2020 SoylentNews
Wildfire Smoke Eroded Ozone Layer By 10 Percent In 2020: Study:
The havoc wreaked by wildfires isn't just on the ground. Researchers at MIT have found that wildfire smoke particles actively erode Earth's protective ozone layer, thus widening the gap we've been spending the last decade trying to close.
When something burns and produces smoke, those smoke particlesotherwise called wildfire aerosolcan drift into the stratosphere, where they hang out for a year or more. According to a study published Wednesday in the journal Nature, chemists and atmospheric scientists have found that suspended wildfire aerosol sparks chemical reactions that ultimately degrade the ozone layer, or the thin atmospheric layer responsible for shielding Earth from the Sun.
The newly-discovered chemical reaction increases hydrochloric acid's solubility. While hydrochloric acid is already present in the atmosphere, MIT found that larger hydrochloric acid quantities activate chlorine in the air and increase ozone loss rates when warmer temperatures strike. This spells danger for the storied hole in the ozone layer, which environmental activists, scientists, and policymakers have been fighting to shrink for several years.
[...] Thankfully, recent attempts to mitigate damage to the ozone layer have been quite successful. International treaties like the Montreal Protocol have helped phase out the use of ozone-depleting pollutants. The world's gradual adoption of electric vehicles might have also helped. The US National Oceanic and Atmospheric Administration even found that the Antarctic ozone hole was slightly smaller in 2022 than in 2021 and far smaller than in 2006 when its size peaked. That said, it's difficult to know right now whether these efforts are enough to compensate for the ozone damage caused by wildfire smoke.
Journal Reference:
Solomon, S., Stone, K., Yu, P. et al. Chlorine
activation and enhanced ozone depletion induced by wildfire
aerosol. Nature 615, 259264 (2023). https://doi.org/10.1038/s41586-022-05683-0
...
19:40
Re: A USB-accessible slab-out-of-bounds read in Linux kernel driver Open Source Security
Posted by Jisoo Jang on Mar 14
This bug was assigned CVE-2023-1380.Best,Jisoo
19:00
Classic Gaming With FPGA and ATX Hackaday

Playing classic games, whether they are games from the golden age of arcades or simply games from consoles that are long out of production, tends to exist on a spectrum. At one end is grabbing a games ROM file, finding an emulator, and kludging together some controls on a keyboard and mouse with your average PC. At the other is meticulously restoring classic hardware for the true feel of what the game would have felt like when it was new. Towards the latter end is emulating the hardware with an FPGA which the open-source MiSTer project attempts to do. This build, though, adds ATX capabilities for the retrocomputing platform.
The ATX standard was developed as a way to standardize motherboard mounting points in PC cases. This one uses the Mini-ITX version, allowing the MiSTer FPGA board to mount to a PCB which fits into a Mini-ITX case. All of the ports on the board appear where the I/O would normally be if this was a standard motherboard, but filling the otherwise empty space with blank PCB is where this project really shines. This allows the...
18:39
Dissecting the malicious arsenal of the Makop ransomware gang Security Affairs
Cyber security researcher Luca Mella analyzed the Makop ransomware employed in a recent intrusion.
Executive summary
- Insights from a recent intrusion authored by Makop ransomware operators show persistence capability through dedicated .NET tools.
- Makop toolkit includes both off-the-shelf tools and custom-developed ones, including tools from the Chinese underground ecosystem.
- Makop gang did not conduct any significative retooling since 2020, which is a clear indicator of their effectiveness even after three years and hundreds of successful compromises.
- The gang leverages exposed remote administration services and internet-facing vulnerabilities to gain and maintain access to victim networks.
Introduction
The Makop ransomware operators started their infamous criminal business in 2020 leveraging a new variant of the notorious Phobos ransomware. During the last years, the gang maintained a solid presence in the criminal underground even if they did not join the double extortion practice.
Their operations are based on the human operator ransomware practice where most of the intrusion is handled by hands-on keyboard criminals, even in the encryption stage.
Makop ransomware gang is classified as a tier-B ransomware actor, but despite this, they keep hitting companies in Europe and Italy. Technical details of the Makop ransomware encryption tool have been greatly deepened by the Lifars security team (link), so, in this article, I am going to focus on other parts of the Makop gang arsenal leveraged to conduct digital extortions.
Technical Details
Makop ransomware operator arsenal is a hybrid one: it contains both cust-developed tools and off-the-shelf software taken from public repositories. In particular, recent investigations were able to identify four of them: the ARestore escalation tool, the backdoor, and other publicly available toolkits such as Advanced_Port_Scanner and a particular popular Chinese hack tool.
Custom tools
After the initial access, Makop criminals are still using an old tool dated back to their first operations in cyberspace. The ARestore tool is .NET executable built in 2020 and partially obfuscated. Also, the compilation time in the PE header looks time stomped, but the metadata from the .NET assembly modules reveal a more plausible date matching the time scale of the Makop operations.
filename: ARestore.exe
md5: 7f86b67ac003eda9d2929c9317025013
18:32
IRC Proceedings: Monday, March 13, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-130323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-130323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-130323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-130323.gmi
Over HTTP:
|
... |
18:28
Immediate complete revascularization found to be as safe, effective as staged procedure in treating multi-vessel disease Lifeboat News: The Blog
In patients with multi-vessel heart disease who have had a heart attack, immediate treatment with stents in all diseased arteries was found to be as safe and effective at one year of follow-up as staged treatment, according to findings from the first large, randomized trial to address this question that is being presented at the American College of Cardiologys Annual Scientific Session Together With the World Congress of Cardiology. In staged treatment, the blocked artery that caused the heart attack is treated with a stent immediately and other partially blocked arteries are treated in a second procedure up to six weeks later. This study was simultaneously published online in The Lancet at the time of presentation.
About half of patients who have a heart attack have multi-vessel heart diseasethis means that in addition to having one completely blocked coronary artery that caused their heart attack, they have additional narrowed coronary arteries that are at risk of becoming blocked or unstable, leading to another heart attack. Clinicians refer to the blocked artery that causes a heart attack as the culprit lesion and to the other at-risk arteries as non-culprit lesions.
The purpose of the international, randomized BIOVASC trial was to compare outcomes for immediate and staged complete revascularization for patients with multi-vessel heart disease who have suffered a heart attack. The goal was not to determine which approach was superior but rather to establish whether immediate complete vascularization was not inferior to the staged approach, which needed to be answered first, said Roberto Diletti, MD, Ph.D., an interventional cardiologist at Erasmus Medical Center in Rotterdam, Netherlands, and lead author of the study.
18:27
Your brain is moving along the surface of the torus Lifeboat News: The Blog
Shortform link:
https://shortform.com/artem.
In this video we will explore a very interesting paper published in Nature in 2022, which describes the hidden torus in the neuronal activity of cells in the entorhinal cortex, known as grid cells.
Place cell video: https://www.youtube.com/watch?v=iV-EMA5g288&t=158s.
Neural manifolds video: https://www.youtube.com/watch?v=QHj9uVmwA_0
My name is Artem, Im a computational neuroscience student and
researcher.
Socials:
Twitter: https://twitter.com/ArtemKRSV
REFERENCES:
1. Gardner, R. J. et al. Toroidal topology of population activity
in grid cells. Nature 602123128 (2022).
2. Pisokas, I., Heinze, S. & Webb, B. The head direction
circuit of two insect species. eLife 9, e53985 (2020).
3. Shilnikov, A. L. & Maurer, A. P. The Art of Grid Fields:
Geometry of Neuronal Time. Front. Neural Circuits 10, (2016).
4. Moser, M.-B., Rowland, D. C. & Moser, E. I. Place Cells,
Grid Cells, and Memory. Cold Spring Harb Perspect Biol 7, a021808
(2015).
5. Lewis, M., Purdy, S., Ahmad, S. & Hawkins, J. Locations in
the Neocortex: A Theory of Sensorimotor Object Recognition Using
Cortical Grid Cells. http://biorxiv.org/lookup/doi/10.1101/436352
(2018) doi:10.1101/436352.
18:26
Logarithmic nature of the brain Lifeboat News: The Blog

Shortform link:
https://shortform.com/artem.
My name is Artem, Im a computational neuroscience student and researcher.
In this video we will talk about the fundamental role of lognormal distribution in neuroscience. First, we will derive it through Central Limit Theorem, and then explore how it support brain operations on many scales from cells to perception.
REFERENCES:
1. Buzski, G. & Mizuseki, K. The log-dynamic brain: how
skewed distributions affect network operations. Nat Rev Neurosci
15264278 (2014).
2. Ikegaya, Y. et al. Interpyramid Spike Transmission Stabilizes
the Sparseness of Recurrent Network Activity. Cerebral Cortex
23293304 (2013).
3. Loewenstein, Y., Kuras, A. & Rumpel, S. Multiplicative
Dynamics Underlie the Emergence of the Log-Normal Distribution of
Spine Sizes in the Neocortex In Vivo. Journal of Neuroscience 31,
94819488 (2011).
4. Morales-Gregorio, A., van Meegen, A. & van Albada, S. J.
Ubiquitous lognormal distribution of neuron densities across
mammalian cerebral cortex. http://biorxiv.org/lookup/doi/10.1101/2022.03.17.480842
(2022) doi:10.1101/2022.03.17.480842.
OUTLINE:
00:00 Introduction.
01:15 What is Normal distribution.
03:03 Central Limit Theorem.
04:23 Normality in biology.
05:46 Derivation of lognormal distribution.
10:20 Division of labour in the brain.
12:20 Generalizer and specialist neurons.
13:37 How lognormality arises.
15:19 Conclusion.
16:00 Shortform: sponsor message.
16:54 Outro.
18:24
1129890b-1.pdf Lifeboat News: The Blog
A hidden pattern a patternist philosophy of mind by Ben Goertzel.
Dropbox is a free service that lets you bring your photos, docs, and videos anywhere and share them easily. Never email yourself a file again!
18:00
Rolex Prices to Drop Further as Supply Surges Terra Forming Terra
:quality(70)/cloudfront-eu-central-1.images.arcpublishing.com/businessoffashion/76BKM47SP5CPPGZILXQUPWHF3E.jpg)
Naomi Wolf - Dear Conservatives, I Apologize Terra Forming Terra
Here we are, a full two years later seeing a key reporter do a full on recantation. I do not think that MSM can do this until their leaders have been formally removed with full disclosure.
Naoni can at least get on with salvaging her reputation somewhat. Who was she listening to?
Ontario MPP Leaves PC Caucus After Report Alleges He Funnelled CCP Money to Candidates Terra Forming Terra
Room-Temperature Superconductor Discovery Meets With Resistance Terra Forming Terra

17:39
10,000 Dutch Farmers Protest Governments Crippling Nitrogen Emissions Target in The Hague cryptogon.com
Famine is a common result of maniac big state policies. Via: ReMix: Thousands of Dutch farmers protested on Saturday against the governments policies to reduce nitrogen emissions, warning they will put farms out of business and affect food production. Hundreds of tractors from across the Netherlands could be seen driving to the event in The []
17:01
Fortinet FortiOS Flaw Exploited in Targeted Cyberattacks on Government Entities The Hacker News
Government entities and large organizations have been targeted by an unknown threat actor by exploiting a security flaw in Fortinet FortiOS software to result in data loss and OS and file corruption. "The complexity of the exploit suggests an advanced actor and that it is highly targeted at governmental or government-related targets," Fortinet researchers Guillaume Lovet and Alex Kong said in an
16:54
Microsoft Has Had THREE Waves of Layoffs in Less Than Three Months (Yes, Its Happening Again) While Media Obsesses Over HEY HI Vapourware Techrights
On February 11th we mentioned the second round of layoffs in 2023. Now this:
Even supposedly strategic areas are culled (including Bing, Azure), but media barely bothers to mention it. Today:
Summary: Third round of job cuts at Microsoft is reported today, but many wont notice because of ChatGPT fluff and lies (targeting shareholders, trying to make it seem like Microsoft is leading in some domain and has a future)
16:54
British Chipmaker Issues Warning About Inventory Glut SoylentNews
IQE says collapse in smartphone sales may wipe one-third off revenue in first half of 2023:
Plunging demand for semiconductors is taking an obvious toll on the chip sector, and Brit compound semiconductor wafer maker IQE is warning of a serious dent in sales.
In a trading update to investors, the London Stock Exchange listed business said it had seen an acceleration of de-stocking trends across the tech industry, "with weaker demand leading to inventory build-up throughout the supply chain."
"This reduction in customer orders and forecasts is expected to result in a decline of approximately 30 million in reported revenues for H1 2023," the Cardiff-based wafer manufacturer said.
It noted the patterns monitored by the Semiconductor Industry Association that reported an 18.5 percent tumble in shipments during calendar Q1.
[...] IQE makes wafers used for radio frequency and photonics applications in several smartphones, and was a major supplier to multiple chip companies who supplied Huawei, before the US government intervened to destroy Huawei's handset business. It is widening the portfolio to also include Power Electronics and Micro-LED tech used in VR headsets.
]...] The smartphone industry has shrunk for the past two years and great things aren't expected this year either. Likewise, the PC industry has also stumbled and isn't expected to bumble along in 2023. As such, the sales bonanza that chipmakers enjoyed in recent years is over for now.
Read more of this story at SoylentNews.
16:30
We cant wait for SBOMs to be demanded by regulation Help Net Security
Old ads can be startlingcigarette ads used to boast their health-giving properties, sugar-laden candy was once advertised as a dietary aid, and soft drinks were advertised as a milk alternative for babies. None of this would fly today, of course, thanks to regulations. Foods must be advertised more responsibly, and they must list their ingredients clearly on the packaging, especially allergens. Software bills of materials (SBOMs) are like ingredient lists for software. No software is More
The post We cant wait for SBOMs to be demanded by regulation appeared first on Help Net Security.
16:00
The Curious Etymology Of The Elements Hackaday

Its not often that the worlds of lexicography and technology collide, but in a video by the etymologist [RobWords] we may have found a rare example. In a fascinating 16-minute video he takes us through the origins of the names youll find in the periodic table. Heres a word video you dont have to be on the staff of a dictionary to appreciate!
Etymology is a fascinating study, in which the scholar must disentangle folk etymologies and mistaken homophones to find the true root of a word. Fortunately in the case of most elements they bear a name bestowed on them by the scientists who discovered them, so their etymologies are rarely in dispute.
The etymologies split neatly into categories, with among them such distinctions as Latin or Greek descriptions, places including the Swedish village of Ytterby which has more elements named after it than anywhere else, elements named for mythological figures, and those named for people.
He artfully skates over the distinction between aluminium and a curiously similar metal the Americans call aluminum, because etymologists are used to deflecting controversy when language differences colour, or even color, peoples emotions. Thank you,...
16:00
Product showcase: Permit.io Application-level permissions with a no-code UI Help Net Security
Managing user access in applications has always been a headache for any developer. Implementing policies and enforcing them can prove to be quite complex, and very time-consuming. Even if a homebrew authorization solution has been developed for an application, sooner or later, problems will arise with scaling the permission system. More roles will need to be created, and further resources and actions will need to be applied and thus, more developer time will be More
The post Product showcase: Permit.io Application-level permissions with a no-code UI appeared first on Help Net Security.
15:30
The rise of AI threats: Is your business prepared to face ChatGPT? Help Net Security
Skyhigh Security has seen firsthand how 33,000 enterprise users have accessed ChatGPT through corporate infrastructures. Almost 7 TB of data has been transacted with ChatGPT through corporate web and cloud assets between Nov 2022 Feb 2023. In this Help Net Security video, Rodman Ramezanian, Global Cloud Threat Lead at Skyhigh Security, discusses how ChatGPT can strengthen business defenses. Still, nasty actors can exploit it to carry out attacks more easily and effectively. Therefore, security More
The post The rise of AI threats: Is your business prepared to face ChatGPT? appeared first on Help Net Security.
15:00
Organizations need to re-examine their approach to BEC protection Help Net Security
BEC attacks are growing year over year and are projected to be twice as high as the threat of phishing in general, according to IRONSCALES and Osterman Research. 93% of organizations experienced one or more of the BEC attack variants in the previous 12 months, with 62% facing three or more attack variants. Moreover, 43.3% of respondents from large enterprises (10,000 employees) expect these BEC attacks to increase over the next 12 months. The report More
The post Organizations need to re-examine their approach to BEC protection appeared first on Help Net Security.
14:45
Security in the cloud with more automation Help Net Security
Hopefully, youve been working with the Center for Internet Security (CIS) on securing your cloud infrastructure for a while now. Initially, you might have used our CIS Benchmarks and other free resources to manually configure your operating systems in the public cloud. Now, you might be using the CIS Hardened Images, virtual machine (VM) images that are pre-hardened to the CIS Benchmarks recommendations. They are both designed to help you avoid misconfigurations and stay secure More
The post Security in the cloud with more automation appeared first on Help Net Security.
14:06
C++ is Still 100 Times Faster Than a Compiled Version of Python SoylentNews
The Register has a story about a Python compiler called Codon that turns Python code into native machine code without a runtime performance hit.:
Python is among the one of the most popular programming languages, yet it's generally not the first choice when speed is required.
"Typical speedups over Python are on the order of 10-100x or more, on a single thread," the Codon repo declares. "Codon's performance is typically on par with (and sometimes better than) that of C/C++."
"Unlike other performance-oriented Python implementations (such as PyPy or Numba), Codon is built from the ground up as a standalone system that compiles ahead-of-time to a static executable and is not tied to an existing Python runtime (e.g., CPython or RPython) for execution," the paper says. "As a result, Codon can achieve better performance and overcome runtime-specific issues such as the global interpreter lock."
C++ Weekly - Ep 366 - C++ vs Compiled Python (Codon) performs a benchmark by running the same algorithm in Python (Codon) 8.4 seconds and C++ which takes 0.09 seconds. The video also points out the following:
We need a python code that works with codon. It takes some porting. We have to give types. It is a lot like C++ in this regard.
Read more of this story at SoylentNews.
13:34
Links 13/03/2023: Firefox 111 and FreeBSD 13.2 RC2 Techrights
![]()
Contents
- GNU/Linux
- Graphics Stack
- Applications
- Instructionals/Technical
- Games
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
13:00
Building A Communications Grid with LoRaType Hackaday

Almost all of modern society is built around various infrastructure, whether thats for electricity, water and sewer, transportation, or even communication. These vast networks arent immune from failure though, and at least as far as communication goes, plenty will reach for a radio of some sort to communicate when Internet or phone services are lacking. It turns out that certain LoRa devices are excellent for local communication as well, and this system known as LoraType looks to create off-grid text-based communications networks wherever they might be needed.
The project is based around the ESP32 platform with an E22 LoRa module built-in to allow it to operate within its UHF bands. It also includes a USB-based battery charger for its small battery, an e-paper display module to display the text messages without consuming too much power, and a keyboard layout for quickly typing messages. The device firmware lets it be largely automated; it will seek out other devices on the local mesh network automatically and the user can immediately begin communicating with other devices on that network as soon as it connects.
There are a few other upsides of using a device like this. Since it doesnt require any existing communications infrastructure to function, it can be used wherever there are...
11:25
This Texas Bill Would Systematically Silence Anyone Who Dares to Talk About Abortion Pills Deeplinks
Texas State Representative Steve Toth recently introduced a bill that targets the most viable form of safe and effective abortion access todaymedication abortion.
House Bill (HB) 2690 seeks to prevent the sale and distribution of abortion pills like Mifepristone and misoprostol, but it doesnt stop there. By restricting access to certain information online, the bill seeks to prevent people from learning about abortion drugs, or even being aware of their existence. It would also systematically incentivize people and companies to silence anyone who wants to speak about abortion pills.
If passed, HB2690 would make it illegal to provide information on how to obtain an abortion-inducing drug. This includes stopping people from making or maintaining websites or creating and distributing applications on the topic.
On top of going after online speakers who create and post content, the bill also targets internet service providers (ISPs)companies like AT&T and Spectrum that provide access to the internet. HB 2690 would require ISPs to make every reasonable and technologically feasible effort to block Internet access to information or material intended to assist or facilitate efforts to obtain an elective abortion or an abortion-inducing drug.
In other words, Texas legislators not only want to make sure no one can start a discussion on these topics, they also want to make sure no one can find one. That creates glaring free-speech issues with this bill and, if passed, the consequences would be dire.
The bill is carefully designed to scare people into silence. First, HB 2690 encourages individuals to sue people or organizations that violate the proposed law. An interactive computer service can also be sued if it allows residents of [Texas] to access information or material that assists or facilitates efforts to obtain elective abortions or abortion-inducing drugs.
So, similar to Texas Senate Bill 8, the bill encourages anyone to file lawsuits against those who merely speak about or provide access to certain information. This is intended to, and will, chill free speech. The looming threat of litigation can be used to silence those who seek to give women truthful information about their reproductive optionspotentially putting their health or lives in danger.
Second, in a more novel approach, the legislation targets ISPs and incentivizes them to be overbroad in what they restrict. The bill encourages people to notify ISPs of abortion-related content and request th...
11:16
Scientists Call for a Global Treaty to Address Space Junk SoylentNews
What goes up must come down, and that includes all of the satellites, rocket stages, and junk that humans have launched into space. A group of scientists is sounding the alarm about how that growing cloud of debris orbiting Earth may cause us trouble in the future, and are championing a global approach to governing Earth's orbit.
In a letter published in Science today, the team of researchers says that there are 9,000 satellites currently in orbit, but that that number is projected to rise to 60,000 by 2030. All of these satellites are sources of orbital debris, whether the spacecraft themselves become junk when they are decommissioned or whether they become involved in an in-orbit crash resulting in a cascade of debris that will circle the planet.
Regardless, this group of researchers points to this boom in the space economy as a problem for the future of space safety and are calling for a legally-binding treaty to enforce the sustainability of Earth's orbitmuch the way 190 nations just vowed to protect the global oceans."
[...] Until a global initiative to reign in the issue of space debris is achieved, some space agencies are taking steps to tackle the problem. Last year, NASA announced it would be funding three projects from various universities to better understand orbital debris and sustainability in space. Likewise, ESA has approved ClearSpace's giant claw that will grab onto junk in orbit and send it into Earth's atmosphere to burn up to take care of pre-existing space debris. Meanwhile, The Drag Augmentation Deorbiting System, a 38-square-foot (3.5-square-meter) sail to increase a satellite's surface drag, could be a way to retire yet-to-be-launched satellites at the end of their lives.
Read more of this story at SoylentNews.
11:15
Adtran and Satelles offer new levels of security for synchronization network infrastructure Help Net Security
Adtran and Satelles collaboration will enable operators of critical infrastructure to safeguard their timing networks with Satellite Time and Location (STL) technology. By integrating Satelles STL into its Oscilloquartz network synchronization products, Adtran will provide an alternative to GNSS systems or a way to augment them with reliability and security. With the ability to deliver precise PNT service, even in GNSS-denied applications, STL offers a vital resource for mobile operators, power utility companies, government, scientific More
The post Adtran and Satelles offer new levels of security for synchronization network infrastructure appeared first on Help Net Security.
11:00
HPR3812: PeePaw's computer does nothing Hacker Public Radio
peepaws computer does nothing who's peepaw, whats the goal to build and understand the inner workings of an 8 bit computer and maybe one day pass it on to a grand kid this episode -nop test do a nop test, that is get the z80 up and running executing the nop instruction using the facilities of an arduino mega board running flash forth to do that, talk about pictures why? flash forth is interactive, without being such a big application itself. Happily runs on an atmega328 why the mega, oodles and oodles of io, so emulating hardware should be a snap use the microcontroller board to provide 5 volts, clock signal and data to get the z80 up and running use the logic probe to see if there is activity on the address bus wiring up hot glued solderless breadboard on to an arduino mega protoshield, white wire is the logicprobe input power and ground first clock, blue control lines int, nmi, wait busrq and reset orange wires data bus address lines go around the chip clockwise from the clock signal (blue wire) we'll be probing A0, next to the ground line 1.logicprobe.jpg 2.power.jpg 3.clock.jpg 4.control.signals.jpg 5.data.jpg 6.ready.to.probe.jpg z80-pinout.jpg 2560-pinout.jpg Click the thumbnail to see the full-sized image fixing some words, refactoring some words, defining new words fixed the data processing word to us the input on pin e4 (digital 2) not the output on pin h6 (digital 9) changed freq= some value to simply pulse, not interested in the specific frequency split clock and logic probe init words added some words to control the reset line reset and run added a word step that allows for single clock pulses the test, mega board plugged into laptop, seral terminal running spool up the logic probe spool up the microcontroller board setting up a port to provide data on the z80 data bus (rudimentary rom) add 5 volts initialize and start the clock probe the clock line probe a0 line a little more to see what else we can discern single step to reset probe m1 single step to reset add halt instruction probe halt line this is output captured from the tests run on the show. lines that begin with a back slash are comments used as narration ok<#,ram> is the forth interpreter reporting it has successfully processed the proceeding word(s), including comments pulse, high and low are output from the logicprobe, all other words are defined in the source text and the end of the notes E FlashForth 5 ATmega2560 13.06.2022 initialize the logic probe
Test Flakiness Across Programming Languages It Will Never Work in Theory
How are programming languages similar, and how do they differ? Most arguments about this are based on lists of language features, but another way to tackle the question is to ask how different languages behave in practice. This paper does that by looking at how flaky tests in C, Go, Java, JavaScript, and Python are similar and how they differ. The authors find that things like concurrency are hard everywhere, but other things (like resource management) vary from language to language. They also found that less than a dozen strategies for fixing flaky tests accounting for 85% of fixes, which suggests that explicitly teaching people bug-fixing and refactoring patterns for tests would be beneficial. Finally, they found that people either fix flaky tests right away or leave them broken for a long time, suggesting either that some tests are useful and some are not, or that some projects have a culture of clean coding and others don't with little middle ground.
Keila Costa, Ronivaldo Ferreira, Gustavo Pinto, Marcelo d'Amorim, and Breno Miranda. Test flakiness across programming languages. IEEE Transactions on Software Engineering, pages 114, 2022. doi:10.1109/tse.2022.3208864.
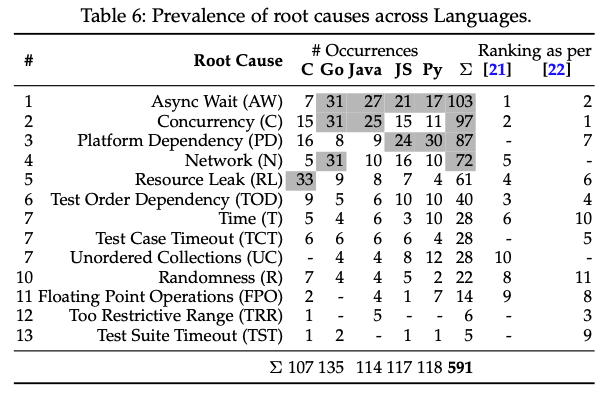
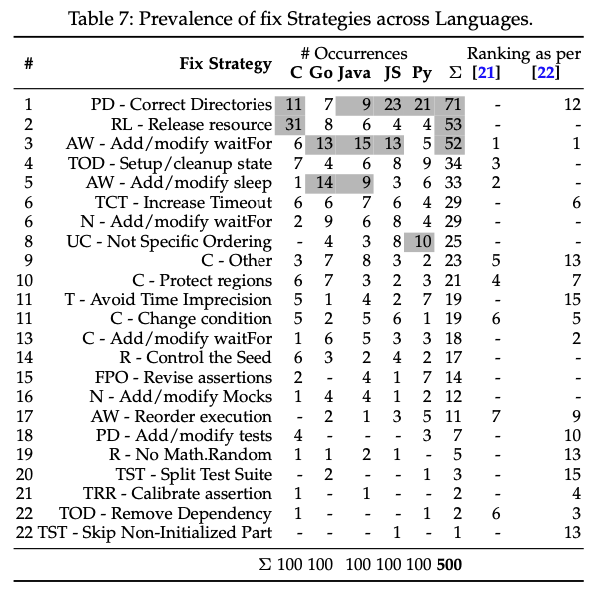
Regression Testing (RT) is a quality-assurance practice commonly adopted in the software industry to check if functionality remains intact after code changes. Test flakiness is a serious problem for RT. A test is said to be flaky when it non-deterministically passes or fails on a fixed environment. Prior work studied test flakiness primarily on Java programs. It is unclear, however, how problematic is test flakiness for software written in other programming languages. This paper reports on a study focusing on three central aspects of test flakiness: concentration, similarity, and cost. Considering concentration, our results show that, for any given programming language that we studied (C, Go, Java, JS, and Python), most issues could be explained by a small fraction of root causes (5/13 root causes cover 78.07% of the issues) and could be fixed by a relatively small fraction of fix strategies (10/23 fix strategies cover 85.20% of the issues). Considering similarity, although there were commonalities in root causes and fixes across languages (e.g., concurrency and async wait are common causes of flakiness in most languages), we also found important differences (e.g., flakiness due to improper release of resources are more common in C), suggesting that there is opportunity to fine tuning analysis tools. Consid...
New Research on What Drives Developer Productivity It Will Never Work in Theory
Cat Hicks (who spoke at our first two live events), Carol Lee (who's speaking next month), and their colleague Morgan Ramsey have released a new report: Developer Thriving: The Four Factors that Drive Software Developer Productivity Across Industries. It's important, insightful work, and I hope it will spark useful conversations among your team.
10:00
The Nixie Clock from Outer Space Hackaday

Nixie clocks are nothing new. But [CuriousMarc] has one with a unique pedigree: the Apollo Program. While restoring the Apollos Central Timing Equipment box, [Marc] decided to throw together a nixie-based clock. The avionics unit in question sent timing pulses and a mission elapsed time signal to the rest of the spacecraft. Oddly enough, while it had an internal oscillator, it was only used during failures. It normally synched to the guidance computers onboard clock.
There is a detailed explanation of the unit, along with some of the ancillary equipment and panels. Much of what the output from the unit is driving counters to display timers, although some of the clocks drive other pieces of equipment, like the telemetry commutator, which time stamps each telemetry frame.
[Marc] reminds us of an archeologist employing X-rays and other tools to examine the rare hardware. Some of the connectors are very strange these days, too, and require some custom boards. The nixie clock depends on an old HP counter. The counter had an output that sends the BCD digits visible on the display. [Marc] intercepted the connections there and allowed the connector to receive the digits instead of sending them.
The modification involved removing some buffer ICs and replacing them with sockets. If you plug the original ICs in, the counter works as before. If you plug in a special substitute board, you can use the counter as an externally-driven nixie display.
...09:49
Golang-Based Botnet GoBruteforcer targets web servers Security Affairs
A recently discovered Golang-based botnet, dubbed GoBruteforcer, is targeting web servers running FTP, MySQL, phpMyAdmin, and Postgres services
Researchers from Palo Alto Networks Unit 42 recently discovered a Golang-based botnet, tracked as GoBruteforcer, which is targeting web servers running FTP, MySQL, phpMyAdmin, and Postgres services.
In order to compromise a target system, the samples require special conditions on it, such as the use of specific arguments and targeted services already being installed (with weak passwords).
GoBruteforcer targets all IP addresses within a chosen Classless Inter-Domain Routing (CIDR) block, then attempt to compromise the identified servers with brute force attacks. The botnet uses a multiscan module to scan for the hosts inside a CIDR for its attack.
Once the multi-scan module has identified open ports for targeted services, it performs a brute-force attack against the server using a set of credentials.
The botnet targets x86, x64 and ARM processor architectures, experts noticed that it relies on an internet relay chat (IRC) bot on the victim server to communicate with the attackers server.
Once a host is found, GoBruteforcer tries to get access to the server via brute force. After achieving access, GoBruteforcer deploys an IRC bot containing the attackers URL. reads the analysis published by Palo Alto Networks. Later, GoBruteforcer also tries to query the victim system using a PHP web shell.
Unit 42 has yet to determine the initial vector of the GoBruteforcer and the PHP web shell campaign is s...
08:57
Distribution Release: Kali Linux 2023.1 DistroWatch.com: News
Kali Linux is a Debian-based distribution with a collection of security and forensics tools. The project's latest release, Kali Linux 2023.1, introduces a few new features, including defensive (purple) tools and Python virtual environments. "There are times where apt may not work for you, such as if there....
08:36
Nearly Every Person in Iraq is an Illegal Streaming Pirate, Sources Say TorrentFreak
 Piracy is a global phenomenon but the availability of
enforcement options varies from country to country.
Piracy is a global phenomenon but the availability of
enforcement options varies from country to country.
In Iraq, for example, tackling copyright infringement isnt seen as a priority or a new phenomenon.
When U.S. troops were still stationed in Iraq, rightsholders discovered that American soldiers were picking up the local habit. As a result, copyright notices were sent to US bases and United States Central Command was put on high alert.
At the end of 2021, the U.S. combat mission in Iraq officially ended, so thats no longer an issue. Iraq still faces plenty of internal issues, of course, but fighting piracy doesnt appear to be high on the agenda. Thats a concern for copyright holders.
Rightsholders Report Iraq to the USTR
Given Iraqs history, it is no surprise that the country has been repeatedly flagged by the U.S. Trade Representative. The USTR considers rightsholder input and other public signals when compiling its Special 301 Report, an annual list of countries that deserve extra attention due to intellectual property shortcomings that may hurt U.S. businesses.
The report doesnt lead directly to concrete action but is used as a leverage tool at the highest diplomatic levels to demand change. As such, recommendations are taken very seriously.
Ideally, strong statements and claims from rightsholders should be backed up by solid evidence. Thats not always needed for their positions to be cited in the USTR report but, more recently, the USTR has begun asking detailed follow-up questions. That has lead to some insightful results, also regarding Iraq.
90% Are Pirates?
Miramax and beIN, for example, stated in their submission that around 90% of the Iraqi population watches pirated live sports events and other media content. Thats a remarkable figure that we have never seen in any official reports, and it also triggered the USTR to ask how these estimates are formulated.

With roughly half of Iraq lacking a basic broadband connection, describing this section of society as online pirates is problematic. And since mor...
08:35
VW Says Sorry for Child Carjacking Fiasco, Makes Safety Service Free SoylentNews
Last month,
Volkswagen garnered plenty of bad publicity when it emerged
that the company's connected car service refused to help track a
stolen carwith a 2-year-old child still on boarduntil someone paid
to reactivate the service. Now, the automaker says it's very sorry
this happened, and it's making its connected vehicle emergency
service free to most model-year 2020-2023 Volkswagens.
[...]
Most MY2020 or newer VWs are able to use connected services, apart
from MY2020 Passats.
Some additional story details for the click-averse:
As Lake County deputies desperately tried to find a stolen Volkswagen with a toddler still inside, they reached out to Car-Net, a service that lets VW owners track their vehicles.
But the Car-Net trial period had ended, and a representative wanted $150 to restart the service and locate the SUV.
The detective pleaded, explaining the "extremely exigent circumstance," but the representative didn't budge, saying it was company policy, sheriff's office Deputy Chief Christopher Covelli said Friday.
"The detective had to work out getting a credit card number and then call the representative back to pay the $150 and at that time the representative provided the GPS location of the vehicle," Covelli said.
Read more of this story at SoylentNews.
07:43
CISA adds Plex Media Server bug, exploited in LastPass attack, to Known Exploited Vulnerabilities Catalog Security Affairs
US CISA added remote code execution vulnerability in Plex Media Server to its Known Exploited Vulnerabilities Catalog.
U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a remote code execution (RCE) vulnerability in the Plex Media Server, tracked as CVE-2020-5741 (CVSS score: 7.2), to its Known Exploited Vulnerabilities Catalog.
The three-year-old high-severity flaw is a deserialization of untrusted data in Plex Media Server on Windows, a remote, authenticated attacker can trigger it to execute arbitrary Python code.
This issue allowed an attacker with access to the server administrators Plex account to upload a malicious file via the Camera Upload feature and have the media server execute it. This could be done by setting the server data directory to overlap with the content location for a library on which Camera Upload was enabled. reads the advisory published by Plex. This issue could not be exploited without first gaining access to the servers Plex account.
The company addressed the vulnerability with the release of Plex Med...
07:10
CVE-2023-1032 - Linux kernel io_uring IORING_OP_SOCKET double free Open Source Security
Posted by Thadeu Lima de Souza Cascardo on Mar 13
A double-free vulnerability was found in the handling of IORING_OP_SOCKEToperation with io_uring on the Linux kernel.
It was fixed by commit:
649c15c7691e9b13cbe9bf6c65c365350e056067 ("net: avoid double iput when sock_alloc_file fails")
It has been assigned CVE-2023-1032.
It affects kernel versions starting with 5.19-rc1 and should affect any
backports including commits da214a475f8bd1d3e9e7a19ddfeb4d1617551bab ("net: add...
07:00
Low Power Challenge: LCD Solar Creatures Live on Sunlight, Sleep at Night Hackaday

With all those e-paper based projects doing the rounds these days, including in our Low Power Challenge, youd almost forget that monochrome LCDs were the original ultra-low-power display. Without them, we wouldnt have had watches, calculators and handheld games operating off button cell batteries or tiny solar panels back in the 80s and 90s. [Gabor] decided to build a set of gadgets with a 1990s LCD aesthetic, called LCD Solar Creatures. These cute little beasts live on nothing but solar power and provide some amusing animations on a classic seven-segment LCD screen.
The Creatures activity depends entirely on the amount of power thats available to them. If their supercapacitors dip below 3.3 V, their micros enter a deep sleep state and do nothing except briefly flash an LED every now and then as a sign of life. When light hits the solar panel, the supercaps are charged up and the Creatures come to life and display a few basic stats. Once the caps hit 4.1 V...
06:08
Kali Linux 2023.1 released and so is Kali Purple! Help Net Security
OffSec (formerly Offensive Security) has released Kali Linux digital forensics platform, and the release is accompanied by a big surprise: a technical preview of Kali Purple, a one stop shop for blue and purple teams. Kali Purple We are making defensive security accessible to everyone. No expensive licenses required, no need for commercial grade infrastructure, no writing code or compiling from source to make it More
The post Kali Linux 2023.1 released and so is Kali Purple! appeared first on Help Net Security.
06:00
Ubuntu 23.04 Preparing To Land Its Linux 6.2 Based Kernel Phoronix
The Ubuntu 23.04 "Lunar Lobster" development builds recently transitioned from Linux 5.19 as in use by Ubuntu 22.10/22.04.2 to a Linux 6.1 based kernel. This led some -- including myself -- to wonder if Canonical changed course and shifted to Linux 6.1 LTS instead of the Linux 6.2 kernel that has been out as stable since last month. Fortunately, that's not the case and Ubuntu 23.04 is preparing to soon land Linux 6.2 across all kernel flavors...
05:53
The Key to Healthier Employees Could be a Quieter or Louder Office Space SoylentNews
A new study suggests that too much or too little office noise has a negative effect on employee well-being. The sweet spot? About 50 decibels, comparable to moderate rain or birdsong.
Choosing to work in the murmur of a busy coffee shop rather than in an office with library-level silence might be healthier, according to a new study by researchers at the University of Arizona and University of Kansas.
The study finds perhaps unsurprisingly that loud noises at the office have a negative impact on employee well-being. But the study also suggests that complete silence is not conducive to a healthy workplace.
[...] "Everybody knows that loud noise is stressful, and, in fact, extremely loud noise is harmful to your ear," said study co-author Esther Sternberg, director of the UArizona Institute on Place, Wellbeing & Performance. "But what was new about this is that with even low levels of sound less than 50 decibels the stress response is higher."
[...] Humans' tendency to get distracted, Sternberg said, is a result of the brain's stress response to potential threats. Our brains are "difference detectors" that take note of sudden changes in sounds so we can decide to fight or flee, she said.
That may explain why low, steady sounds help mask distractions in the workplace, she added.
"People are always working in coffee shops those are not quiet spaces. But the reason you can concentrate there is because the sounds all merge to become background noise," Sternberg said. "It masks sound that might be distracting. If you hear a pin drop when it's very, very quiet, it will distract you from what you're doing."
Journal Reference:
Karthik Srinivasan, Faiz Currim, Casey M. Lindberg, et
al., Discovery of associative patterns between workplace
sound level and physiological wellbeing using wearable devices and
empirical Bayes modeling [open], npj Digital Medicine
(2023) 6:5 ; https://doi.org/10.1038/s41746-022-00727-1
Read more of this story at SoylentNews.
05:30
Version 2.40.0 of the Git source-code management system is out. Changes include a new --merge-base option for merges, a built-in implementation of bisection, Emacs support for git jump, a fair number of smallish user-interface tweaks, and a lot of bug fixes. See the announcement and this GitHub blog entry for the details.
05:10
Cat Toys, Toaster Bots, and Scolding Lamps IEEE Spectrum
The 2023 ACM/IEEE Human-Robot Interaction Conference (HRI) is taking place this week in Stockholm, with the theme of HRI for all. Its a good theme, promoting diversity and inclusion, but its also a good reminder that all robots have (or should have) some thought put into how they interact with humans. HRI isnt just for social robots. Even the most industrial of industrial robots, the lights-out manufacturing sorts of things that may never see a human while operating unless something is (or is about to be) very very wrong, still have to be set up and programmed by a human. And those humans are happiest when engineers remember that they exist.
Anyway, there will be a bunch of interesting research presented at HRI (the proceedings are already online here), but to kick things off were taking a look at the annual HRI Student Design Competition, which is always creative and fun.
The theme for this years Student Design Competition is Affordable Robots. Student teams are asked to create and describe a scenario with robots/agents that are affordable and have a real-life utility in society. More specifically, we are looking for affordable, impactful, scalable, and reliable use cases with real-world application potential. Since the theme of this years conference is HRI for all, we also recommend that students think about inclusion and diversity in HRI in terms of geographical inclusion (both for the developed and developing world), gender inclusion, ethnic inclusion, disability, equity, etc. related to this theme.
This combination of affordable and real-life utility is especially challenging, since robots are by nature not affordable at all, and utility (in the sense of functionality that justifies their cost) is an elusive goal, which is why this is exactly the kind of problem you want students to tackle. There are 20 entries this year, and we can only share a few of them, but here are five that we thought were particularly interesting.
Aimoji: An affordable interaction kit that upcycles used toys
as companion robots
When a child wants to talk with a toy, usually it is a one-way interaction, with the child imagining the toys responses. Our design enables every toy to have a two-way interaction using our low-cost interaction kit. The reaction of the toy is based on a motion sensor that triggers the toy to respond to t...
03:04
Why Do Some Modern Computers Still Have Serial Ports? SoylentNews
Why Do Some Modern Computers Still Have Serial Ports?:
While the parallel port is now safely buried in the grave of obsolescence, it may seem odd that the humble, slow serial port is still around. But as it turns out, bit-by-bit, this humble communications port has become essential.
[...] Serial ports are slow with the standard speed at the high end of the range coming in at a pedestrian 115.2Kbps. At that speed, it would take you almost a day to transfer 1GB of data! That's under ideal circumstances, and things can be much, much slower than that.
If we have USB, and serial ports are so slow and comparatively bulky, why the heck do some computers still have them? There are a few reasons, but the most important ones include:
- Lots, and lots, of industrial and scientific equipment are still in service and use serial ports to interface.
- It's simple, reliable, well understood, and much cheaper to implement than other more modern port types.
- Hobbyists have uses, such as programming microcontrollers.
Do you still use the serial port, or do you depend on equipment that does? I have noticed that it is still widely used in medical equipment but are there other fields in which the serial port is the standard interface?
Read more of this story at SoylentNews.
03:01
Handle exceptions in Ansible Playbooks with block and rescue Linux.com
Handle errors gracefully in your automation by using Ansible block and rescue keywords.
Read More at Enable Sysadmin
The post Handle exceptions in Ansible Playbooks with block and rescue appeared first on Linux.com.
03:00
Intel's Open-Source Linux Compute Stack Maturing Very Well For Arc Graphics Phoronix
From early December to late February there was an absence of new Compute-Runtime updates for that open-source stack for providing OpenCL and oneAPI Level Zero support for Intel graphics hardware on Linux. It was out of trend as they worked to move from a weekly~biweekly release rhythm to a monthly release cadence while taking extra time for making various other changes too. After that three month lull, they are back to pushing out new compute updates and damn it's looking nice. At least in my testing, the progress they've quietly made over the past few months has been very nice for the compute stack compatibility/support and performance.
02:30
ipmitool Repository Archived, Developer Suspended By GitHub Phoronix
The ipmitool utility on Linux systems is widely-used for controlling IPMI-enabled servers and other systems. This tool for interacting with the Intelligent Platform Management Interface (IPMI) is extremely common with server administrators while now its development is in a temporary state of limbo due to GitHub...
02:00
ChatGPTs Hallucinations Could Keep It From Succeeding IEEE Spectrum
ChatGPT has wowed the world with the depth of its knowledge and the fluency of its responses, but one problem has hobbled its usefulness: It keeps hallucinating.
Yes, large language models (LLMs) hallucinate, a concept popularized by Google AI researchers in 2018. Hallucination in this context refers to mistakes in the generated text that are semantically or syntactically plausible but are in fact incorrect or nonsensical. In short, you cant trust what the machine is telling you.
Thats why, while OpenAIs Codex or Githubs Copilot can write code, an experienced programmer still needs to review the outputapproving, correcting, or rejecting it before allowing it to slip into a code base where it might wreak havoc.
High school teachers are learning the same. A ChatGPT-written book report or historical essay may be a breeze to read but could easily contain erroneous facts that the student was too lazy to root out.
Hallucinations are a serious problem. Bill Gates has mused that ChatGPT or similar large language models could some day provide medical advice to people without access to doctors. But you cant trust advice from a machine prone to hallucinations.
OpenAI Is Working to Fix ChatGPTs Hallucinations
Ilya Sutskever, OpenAIs chief scientist and one of the creators of ChatGPT, says hes confident that the problem will disappear with time as large language models learn to anchor their responses in reality. OpenAI has pioneered a technique to shape its models behaviors using something called reinforcement learning with human feedback (RLHF).
RLHF was developed by OpenAI and Googles DeepMind team in 2017 as a way to improve reinforcement learning when a task involves complex or poorly defined goals, making it difficult to design a suitable reward function. Having a human periodically check on the reinforcement learning systems output and give feedback allows reinforcement-learning systems to learn even when the reward function is hidden.
For ChatGPT, data collected during its interactions are used to train a neural network that acts as a reward predictor, which reviews ChatGPTs outputs and predicts a numerical score that represents how well those actions ali...
01:59
Large-scale Cyber Attack Hijacks East Asian Websites for Adult Content Redirects The Hacker News
A widespread malicious cyber operation has hijacked thousands of websites aimed at East Asian audiences to redirect visitors to adult-themed content since early September 2022. The ongoing campaign entails injecting malicious JavaScript code to the hacked websites, often connecting to the target web server using legitimate FTP credentials the threat actor previously obtained via an unknown
01:30
Dark Pink APT targets Govt entities in South Asia Security Affairs
Researchers reported that Dark Pink APT employed a malware dubbed KamiKakaBot against Southeast Asian targets.
In February 2023, EclecticIQ researchers spotted multiple KamiKakaBot malware samples that were employed by the Dark Pink APT group (aka Saaiwc) in attacks against government entities in Southeast Asia countries.
The activity of the group was first detailed by Group-IB in January 2023, the group used custom malware such as KamiKakaBot and TelePowerBot.
The Dark Pink APT is active in the ASEAN region and has been active since at least mid-2021. The group focuses on military and government organizations to steal sensitive information, including confidential data and intellectual property.
The main difference between the January campaign and the attacks spotted by EclecticIQ is that the threat actors have improved the malwares obfuscation routine to avoid detection.
The researchers noticed overlaps in malware delivery and adversary techniques between Earth Yako and Dark Pink APT groups, including the use of Winword.exe for DLL Hijacking.
The KamiKakaBot malware spreads via phishing emails that contain a malicious ISO file as an attachment. The ISO image file contains a WinWord.exe which is legitimately signed by Microsoft, which is used to launch DLL side-loading attack, a loader (MSVCR100.dll), and a decoy Microsoft Word document. Upon clicking on WinWord.exe, the loader is executed in the memory of WinWord.exe.
The malware gain persistence via a registry key into HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell used to abuse features of Winlogon (Windows component).
The ISO file also contains a decoy Word document that has an XOR-encrypted section. The KamiKakaBot loader uses this section to decrypt the XOR-encrypted content from the decoy file then writes the decrypted XML KamiKakaBot payload into the disk (C:\Windows\temp) and executes it via a living-off-the-land binary called MsBuild.exe. reads the analysis published by EclecticIQ.
The attackers employed different lures in each decoy Word document to trick their victims into opening the attachment.
Before the execution of the decrypted XML payload, KamiKakaBot loader writes a registry key into HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell to abuse features of Winlogon (Windows component) for establishing persistent access.
KamiKakaBot can steal data stored in popular web browsers, including Chrome, MS Edge, and Firefox. Then the stolen data is sent to the attackers Telegram bot channel in a compressed ZIP format.
...01:27
[$] Heuristics for software-interrupt processing LWN.net
The kernel's software-interrupt ("softirq") mechanism was added prior to the 1.0 kernel release, but it implements a design seen in systems that were already old when Linux was born. For much of that time, softirqs have been an impediment to the kernel community's scalability and response-time goals, but they have proved resistant to removal. A recent discussion on a proposed new heuristic to mitigate a softirq-related performance problem may have reinvigorated interest in doing something about this subsystem as a whole rather than just tweaking the parameters of how it operates.
00:53
Links 13/03/2023: GNU Octave 8.1.0 and Scrcpy 2.0 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* an...
00:24
Up to 1,000,000 Times Faster: A Switch Made From a Single Molecule Lifeboat News: The Blog
An international team of researchers, including those from the University of Tokyos Institute for Solid State Physics, has made a groundbreaking discovery. They have successfully demonstrated the use of a single molecule named fullerene as a switch, similar to a transistor. The team achieved this by employing a precisely calibrated laser pulse, which allowed them to control the path of an incoming electron in a predictable manner.
The switching process enabled by fullerene molecules can be significantly faster than the switches used in microchips, with a speed increase of three to six orders of magnitude, depending on the laser pulses utilized. The use of fullerene switches in a network could result in the creation of a computer with capabilities beyond what is currently achievable with electronic transistors. Additionally, they have the potential to revolutionize microscopic imaging devices by providing unprecedented levels of resolution.
Over 70 years ago, physicists discovered that molecules emit electrons in the presence of electric fields, and later on, certain wavelengths of light. The electron emissions created patterns that enticed curiosity but eluded explanation. But this has changed thanks to a new theoretical analysis, the ramification of which could not only lead to new high-tech applications but also improve our ability to scrutinize the physical world itself.
00:24
Reduced Blood Pressure: Was It Caused By Lung Muscle Training? Lifeboat News: The Blog
Join us on Patreon! https://www.patreon.com/MichaelLustgartenPhD
Discount Links:
NAD+ Quantification: https://www.jinfiniti.com/intracellular-nad-test/
Use Code: ConquerAging At Checkout.
Green Tea: https://www.ochaandco.com/?ref=conqueraging.
Oral Microbiome: https://www.bristlehealth.com/?ref=michaellustgarten.
Epigenetic Testing: https://bit.ly/3Rken0n.
Use Code: CONQUERAGING!
At-Home Blood Testing: https://getquantify.io/mlustgarten.
00:22
2302.037101.pdf Lifeboat News: The Blog
Bouncing cosmology from nonlinear dark energy with two cosmological constants.
Dropbox is a free service that lets you bring your photos, docs, and videos anywhere and share them easily. Never email yourself a file again!
00:19
Midazolam Murders When a Common Sedative Becomes an Execution Drug cryptogon.com
Via: Peak Prosperity:
00:19
Denmark is Storing CO2 in Abandoned North Sea Oil Fields SoylentNews
Last week, Denmark has stored the first volumes of carbon dioxide in an old oil and gas field in the Danish North Sea. The carbon dioxide sequestered comes from a chemical production plant (Ineos Oxide) in the Port of Antwerp, Belgium.
Since 2010, Ineos Oxide has captured CO2 as a by-product from its ethylene oxide (plastics) production, cooled it down to a liquid, and resold the product to the food (fizzy drinks, beer) and agricultural (greenhouse cultivation) industry. Now, instead, part of this production was transported to Nini, a previously abandoned oil platform about 200 km in front of the Danish coast, and injected 1,800 meters deep.
The test project, named Greensand, needs to prove that the process is possible, and safe. The modified transport vessel used, Aurora Storm, can only take 800 ton CO2 per traject; it will have to shuttle back and forth between Antwerp and Denmark about 20 times, enough for 15,000 ton, this year alone. The project will be upscaled to 1.5 million ton a year by 2025.
By 2030, 8 million ton a year is planned, or about half the carbon dioxide emitted by Antwerp's chemical cluster, the largest in Europe. This, however, requires investments in new offshore infrastructure, and larger transport ships known as CO2 carriers.
The Greensand project is racing behind another project though. That project is called Northern Lights, and aims to be able to store 1.5 million ton a year, by next year, 2024. Northern Lights is a partnership between Shell, Equinor and Total, and supported by Norway's government Langskip (Longship) CCS project.
The EU has set a target of capturing and storing a minimum 300 million ton CO2 a year by 2050.
Read more of this story at SoylentNews.
00:05
A USB-accessible slab-out-of-bounds read in Linux kernel driver Open Source Security
Posted by Jisoo Jang on Mar 13
=== Description ===A slab-out-of-bounds read bug was found in the Broadcom Full MAC Wi-Fi
driver (e.g., brcmfmac.ko in the linux-modules-extra package in Ubuntu),
The bug occurs in kmemdup() called from brcmf_get_assoc_ies(), when
assoc_info->req_len, data from a URB provided by a USB device, is bigger
than the size of buffer which is defined as WL_EXTRA_BUF_MAX.
The driver duplicates the data of cfg->extra_buf to conn_info->req_ie...
Monday, 13 March
23:36
Intel Meteor Lake Graphics IDs Enabled For Mesa 23.1 Phoronix
The open-source OpenGL and Vulkan support for Intel's next-generation Meteor Lake client processors is taking a step forward with next quarter's Mesa 23.1 release...
23:24
Fake ChatGPT Chrome Extension Hijacking Facebook Accounts for Malicious Advertising The Hacker News
A fake ChatGPT-branded Chrome browser extension has been found to come with capabilities to hijack Facebook accounts and create rogue admin accounts, highlighting one of the different methods cyber criminals are using to distribute malware. "By hijacking high-profile Facebook business accounts, the threat actor creates an elite army of Facebook bots and a malicious paid media apparatus," Guardio
23:23
How to Apply NIST Principles to SaaS in 2023 The Hacker News
The National Institute of Standards and Technology (NIST) is one of the standard-bearers in global cybersecurity. The U.S.-based institutes cybersecurity framework helps organizations of all sizes understand, manage, and reduce their cyber-risk levels and better protect their data. Its importance in the fight against cyberattacks cant be overstated. While NIST hasnt directly developed
22:47
Warning: AI-generated YouTube Video Tutorials Spreading Infostealer Malware The Hacker News
Threat actors have been increasingly observed using AI-generated YouTube Videos to spread a variety of stealer malware such as Raccoon, RedLine, and Vidar. "The videos lure users by pretending to be tutorials on how to download cracked versions of software such as Photoshop, Premiere Pro, Autodesk 3ds Max, AutoCAD, and other products that are licensed products available only to paid users,"
22:27
Michelle Catts SVP, Nuclear Programs, GE-Hitachi Reliable Carbon-Free Power For The World Lifeboat News: The Blog

Reliable carbon-free power for the world michelle catts, senior vice president, nuclear programs, ge-hitachi nuclear energy.
Michelle Catts is the Senior Vice President of Nuclear Programs at GE-Hitachi (GEH https://nuclear.gepower.com/) located in Wilmington, NC.
Ms. Catts has over 18 years of demonstrated managerial and technical expertise in nuclear Regulatory Affairs and currently is responsible for ensuring world-class Quality, Continuous Improvement, Regulatory Affairs, and oversight of Environment, Health & Safety programs. She manages a multimillion-dollar budget and over a 30-member organization. She provides licensing and quality leadership and guidance to support nuclear fuel facility licensing, current nuclear fleet fuel reload/outage licensing activities, new reactor and new fuel opportunities, Technical Regulations and Standards, and GE-Hitachiss Vallecitos and Morris sites.
Prior to joining GE-Hitachi, Ms. Catts worked for the U.S. Nuclear Regulatory Commission (NRC) where she held positions of increasing responsibility including as a nuclear reactor inspector stationed onsite at nuclear power plants up to the Policy Advisor to the Presidential Appointed NRC Chairman.
Ms. Catts holds a B.S. in Nuclear Engineering from North Carolina State University and is currently working on her MBA at UNCW.
Ms. Catts is also on the board of Smart Start of New Hanover County, an organization that seeks to build bridges to develop, sustain and enhance health, family support and early education services for all children, ages birth to five.
22:24
An Introduction to Neuroinformatics Lifeboat News: The Blog

Details
The goal of brain imaging is to provide in-vivo measures of the
human brain to better understand how the brain is structured,
connected and functions.
In this talk, we will discuss how to analyze brain imaging data in
order to make sense of the large amount of data that comes out of
the scanner.
 **About
the speaker**
**About
the speaker**
[Dr. Camille Maumet](https://twitter.com/cmaumet) is a
research scientist in neuroinformatics at Inria, Univ Rennes, CNRS,
Inserm in Rennes, France.
Her research focuses on the variability of analytical pipelines and
its impact on our ability to reuse brain imaging datasets.
She obtained her PhD in computer science at the University of
Rennes on the analyses of clinical neuroimaging datasets in
functional magnetic resonance imaging and.
arterial spin labelling. She was then a postdoctoral research
fellow in the Institute of Digital Healthcare at the University of
Warwick and the University of Oxford.
where she focused on meta-analyses and standards for neuroimaging
data sharing. She is also an open science advocate.
involved in the development of more inclusive research practices
and community-led research and participates in many collaborative
efforts including Brainhack.
the INCF, and the Open Science Special Interest Group of the
Organization for Human Brain Mapping that she chaired in 2020.
[Nipype Tutorial](https://miykael.github.io/nipype_tutorial/)
Annual Brain Imaging Events:
[OHBM Brainhack (Brain Hackathon) June 1618](https://ohbm.github.io/hackathon2022/)[registration via](https://www.humanbrainmapping.org/i4a/ams/meetings/index.cfmageID=4073)
- [OHBM Open Science Room (Discussions around open science practices & brain imaging)](https://ohbm.github.io/osr2022/)
22:00
Breaking Into the Nintendo DSi Through the (Browser) Window Hackaday

The Nintendo DSi was surpassed by newer and better handhelds many years ago, but that doesnt stop people like [Nathan Farlow] from attempting to break into the old abandoned house through a rather unexpected place: the (browser) window.
When the Nintendo DSi was released in 2008, one of its notable [Nathan] reasoned an exploit in this browser would be an ideal entry point, as theres no OS or kernel to get past once you get execution, you control the system. To put this plan into action, he put together two great ideas. First he used the WebKit layout tests to get the browser into weird edge cases, and then tracked down an Windows build of Opera 9.50 that he could run on his system under WINE. This allowed him to identify the use-after-free bugs that he was looking for.
21:40
Linux 6.1.19 LTS & 6.2.6 Released With AMD System Stuttering Workaround Phoronix
Following last night's Linux 6.3-rc2 release that brings a workaround for system stuttering on some AMD Ryzen systems, that workaround was quickly back-ported to the Linux 6.1 LTS and 6.2 stable series and spun into new releases for Monday morning...
21:39
Raising the Bar for Software Security: GitHub 2FA Begins March 13 SoylentNews
On March 13, we will officially begin rolling out our initiative to require all developers who contribute code on GitHub.com to enable one or more forms of two-factor authentication (2FA) by the end of 2023.
GitHub is central to the software supply chain, and securing the software supply chain starts with the developer. Our 2FA initiative is part of a platform-wide effort to secure software development by improving account security. Developers' accounts are frequent targets for social engineering and account takeover (ATO). Protecting developers and consumers of the open source ecosystem from these types of attacks is the first and most critical step toward securing the supply chain.
[...] If your account is selected for enrollment, you will be notified via email and see a banner on GitHub.com, asking you to enroll. You'll have 45 days to configure 2FA on your accountbefore that date nothing will change about using GitHub except for the reminders. We'll let you know when your enablement deadline is getting close, and once it has passed you will be required to enable 2FA the first time you access GitHub.com. You'll have the ability to snooze this notification for up to a week, but after that your ability to access your account will be limited.
So, what if you're not in an early enrollment group but you want to get started? Click here and follow a few easy steps to enroll in 2FA.
[...] You can choose between TOTP, SMS, security keys, or GitHub Mobile as your preferred 2FA method.
Recent GitHub security incidents:
GitHub says hackers cloned code-signing certificates in breached
repository(1/30/2023)
Slack's private GitHub code repositories stolen over
holidays(1/5/2023)
Okta's source code stolen after GitHub repositories
hacked(12/21/2022)
Read more of this story at SoylentNews.
21:26
AMD Working On VirtIO GPU & Passthrough GPU Support For Xen Virtualization Phoronix
AMD is working to enable VirtIO GPU and pass-through GPU support for the Xen virtualization hypervisor with Radeon graphics...
21:21
21:14
Intel Sends Out Sixteenth Round Of Linux LAM Patches Phoronix
Intel's Linux engineers continue working on Linear Address Masking (LAM) for making use of untranslated address bits of 64-bit linear addresses so that it can be used for arbitrary metadata. The hope is that this LAM metadata can lead to more efficient address sanitizers, optimizations for JITs and VMs, and more, but it's been a lengthy journey getting the support upstreamed...
21:00
Empowering Corporate IP Professionals with a Connected Ecosystem IEEE Spectrum

In this age of continuous innovation, intellectual property (IP) is a core business asset. As IP becomes ever more central to businesses ability to innovate, compete and grow, managing these assets is becoming more criticaland more complex.
In this new paper, we review why a new approach to IP management is needed - enabling corporate teams to remove friction from their IP management workflows and unlock the full potential of their IP.
Download this whitepaper to learn:
- The real costs associated with this disconnected approach to managing IP assets
- The economic value of taking steps to optimize IP management
- How a unified full lifecycle approach benefits corporate IP teams
- About our commitment to delivering the industrys most comprehensive, fully integrated solution for corporate IP lifecycle management
20:54
Experimental RADV Vulkan Video Decoding For VP9 Phoronix
David Airlie has managed to get some early code in place for handling VP9 video decoding with Vulkan using the Mesa RADV driver. This early Vulkan Video VP9 support also is accompanied by an FFmpeg branch supporting this experimental Mesa extension...
20:51
The SVB demise is a fraudsters paradise, so take precautions Help Net Security
For those who havent followed the drama, Silicon Valley Bank has been shut down by the California Department of Financial Protection and Innovation, after a bank run that followed an insolvency risk and a stock crash. The Federal Deposit Insurance Corporation has been named the receiver, and has established a deposit insurance national bank, through which SVB customers will be able to access the insured part of their deposits. Understandably, there is a lot of More
The post The SVB demise is a fraudsters paradise, so take precautions appeared first on Help Net Security.
20:25
20:22
Nokia Magic Max, Nokia is About to Reclaim its Crown with this Ultimate Flagship Lifeboat News: The Blog

Reports say that the Nokia Magic Max will come in three different memory configurations. We will have 8GB, 12GB and 16GB of RAM with 256GB and 512GB storage options. It will launch with Android 13 out of the box with Snapdragon 8 Gen 2 SoC under the hood. We may also see a 6.7-inch AMOLED display with 120Hz refresh rate on the device. Corning Gorilla Glass 7 protection could be on the display of the upcoming flagship device from Nokia.
The device will feature a triple camera setup on the back with 144MP main sensor, 64MP ultrawide and 48MP Telephoto lens. Rumors have suggested a massive 7950mAh battery which can also charge from 0 to 100 within a few minutes, thanks to the 180W fast charger.
The memory configurations will determine the price of each variant. Nevertheless, sources have suggested the starting price to be around $550 (INR44,900). There is no firm rumor with respect to the launch date, but we expect to see the launch of the Nokia Magic Max in a matter of few weeks.
19:43
Marvel Wants Reddit to Expose Mods Suspected of Ant-Man 3 Leak TorrentFreak
 As Reddit fights to
protect the identities of users who simply participated in
piracy-related discussions, two new cases filed last Friday may
also prove controversial.
As Reddit fights to
protect the identities of users who simply participated in
piracy-related discussions, two new cases filed last Friday may
also prove controversial.
On February 17, 2023, Marvels Ant-Man and the Wasp: Quantumania officially kicked off Phase 5 of the Marvel Cinematic Universe (MCU). Distributed by Disney to lukewarm reviews, the movie took $105 million at the box office in its first week and then plummeted 70% to $32 million in week two.
Thanks to a leak posted online around a month before the movies theatrical debut, some fans already had an idea of how the movie would play out. Marvels pursuit of the leakers is likely to have a storyline all of its own.
MVL Film Finance LLC Targets Google
When MVL Film Finance LLC (MVL) was incorporated in 2004/5, its purpose was to finance Marvel Studios production of 10 live-action or animated films based on up to 10 of Marvels comic book characters. Several related business entities, including Marvel Studios and parent company Marvel Entertainment, are owned by The Walt Disney Company.
Last Friday at the United States District for the Northern District of California, Marvel Studios submitted a declaration in support of a DMCA subpoena application targeting Google. Matthew Slatoff, Marvels Vice President, Global Security & Content Protection, informed the Court that his responsibilities include monitoring and addressing infringement of MVL Film Finances rights.
According to Slatoffs declaration, on January 21, a Disney anti-piracy analyst submitted a copyright infringement notice to Google after discovering that Ant-Man and the Wasp: Quantumania content had been uploaded to systems operated by Google, without MVLs authorization. The takedown notice, submitted via Googles webform, contained a prompt from Google and a response from the rightsholder.
Identify and describe the copyrighted work: Unreleased leaked script of the new Disney movie Ant-man and the Wasp: Quantumania.
Marvel supplied a docs.google.com/document/ URL as the location for the allegedly infringing content. The content no longer exists at that location.
19:06
Security updates for Monday LWN.net
Security updates have been issued by Debian (imagemagick, libapache2-mod-auth-mellon, mpv, rails, and ruby-sidekiq), Fedora (chromium, dcmtk, and strongswan), Mageia (chromium-browser-stable, dcmtk, kernel, kernel-linus, libreswan, microcode, redis, and tmux), SUSE (postgresql14 and python39), and Ubuntu (linux-kvm, linux-raspi-5.4, and thunderbird).
19:00
AI and Savvy Marketing Create Dubious Moon Photos Hackaday

Taking a high-resolution photo of the moon is a surprisingly difficult task. Not only is a long enough lens required, but the camera typically needs to be mounted on a tracking system of some kind, as the moon moves too fast for the long exposure times needed. Thats why plenty were skeptical of Samsungs claims that their latest smart phone cameras could actually photograph this celestial body with any degree of detail. It turns out that this skepticism might be warranted.
Samsungs marketing department is claiming that this phone is using artificial intelligence to improve photos, which should quickly raise a red flag for anyone technically minded. [ibreakphotos] wanted to put this to the test rather than speculate, so a high-resolution image of the moon was modified in such a way that most of the fine detail of the image was lost. Displaying this image on a monitor, standing across the room, and using the smartphone in question reveals details in the image that cant possibly be there.
The image that accompanies this post shows the two images side-by-side for those skeptical of these claims, but from what we can tell it looks like this is essentially an AI system copy-pasting the moon into images it thinks are of the moon its...
18:52
When Should Data Scientists Try a New Technique? SoylentNews
If a scientist wanted to forecast ocean currents to understand how pollution travels after an oil spill, she could use a common approach that looks at currents traveling between 10 and 200 kilometers. Or, she could choose a newer model that also includes shorter currents. This might be more accurate, but it could also require learning new software or running new computational experiments. How to know if it will be worth the time, cost, and effort to use the new method?
A new approach developed by MIT researchers could help data scientists answer this question, whether they are looking at statistics on ocean currents, violent crime, children's reading ability, or any number of other types of datasets.
The team created a new measure, known as the "c-value," that helps users choose between techniques based on the chance that a new method is more accurate for a specific dataset. This measure answers the question "is it likely that the new method is more accurate for this data than the common approach?"
Traditionally, statisticians compare methods by averaging a method's accuracy across all possible datasets. But just because a new method is better for all datasets on average doesn't mean it will actually provide a better estimate using one particular dataset. Averages are not application-specific.
So, researchers from MIT and elsewhere created the c-value, which is a dataset-specific tool. A high c-value means it is unlikely a new method will be less accurate than the original method on a specific data problem.
Read more of this story at SoylentNews.
18:49
Sirius UK CEO Resigns (or Gets Sacked) and Completely Deletes His Whole Past With Sirius Open Source Techrights
Not a single mention of Sirius, which used to be all over his LinkedIn page only weeks ago
Summary: The above person was with Sirius since 2017 and CEO for about 2 years; hes now hiding any connection to the company (it used to be all over his LinkedIn profile, from top to bottom); any attempts to send him E-mails bounce back from GMail, so he is eager to leave no paths open
18:36
Researchers Uncover Over a Dozen Security Flaws in Akuvox E11 Smart Intercom The Hacker News
More than a dozen security flaws have been disclosed in E11, a smart intercom product made by Chinese company Akuvox. "The vulnerabilities could allow attackers to execute code remotely in order to activate and control the device's camera and microphone, steal video and images, or gain a network foothold," Claroty security researcher Vera Mens said in a technical write-up. Akuvox E11 is
18:23
Uneven Circuit Aging Becoming A Bigger Problem Lifeboat News: The Blog
The industry is gaining ground in understanding how aging affects reliability, but more variables make it harder to fix.
Circuit aging is emerging as a first-order design challenge as engineering teams look for new ways to improve reliability and ensure the functionality of chips throughout their expected lifetimes.
The need for reliability is obvious in data centers and automobiles, where a chip failure could result in downtime or injury. It also is increasingly important in mobile and consumer electronics, which are being used for applications such as in-home health monitoring or for navigation, and where the cost of the devices has been steadily rising. But aging also needs to be assessed in the context of variation models from the foundries, different use cases that may stress various components in different ways, and different power and thermal profiles, all of which makes it harder to accurately predict how a chip will behave over time.
18:23
Designing for Data Flow Lifeboat News: The Blog
Processing more data in more places while minimizing its movement becomes a requirement and a challenge.
Movement and management of data inside and outside of chips is becoming a central theme for a growing number of electronic systems, and a huge challenge for all of them.
Entirely new architectures and techniques are being developed to reduce the movement of data and to accomplish more per compute cycle, and to speed the transfer of data between various components on a chip and between chips in a package. Alongside of that, new materials are being developed to increase electron mobility and to reduce resistance and capacitance.
18:23
Strange Circular Sand Dunes Discovered on Mars Lifeboat News: The Blog
Sand dunes of many shapes and sizes are common on Mars. In this example, the dunes are almost perfectly circular, which is unusual. Credit: NASA/JPL-Caltech/University of Arizona.
Sand dunes of many shapes and sizes are common on Mars.
Mars is the second smallest planet in our solar system and the fourth planet from the sun. It is a dusty, cold, desert world with a very thin atmosphere. Iron oxide is prevalent in Mars surface resulting in its reddish color and its nickname The Red Planet. Mars name comes from the Roman god of war.
18:13
IRC Proceedings: Sunday, March 12, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-120323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-120323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-120323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-120323.gmi
Over HTTP:
|
... |
18:00
How to Make Peace with Canada Geese Terra Forming Terra
...
Sugar-coated antibodies cross blood-brain barrier to fight Alzheimer's Terra Forming Terra

...
Clean energy breakthrough as electricity is produced out of thin air Terra Forming Terra

Do not ovethink this guys. Just make it work handily.
Behold 900+ Magnificent Botanical Collages Created by a 72-Year-Old Widow, Starting in 1772 Terra Forming Terra

17:46
Theo de Raadt to be presenting at CanSecWest. OpenBSD Journal
Dragos Ruiu recently announced that Theo de Raadt will be presenting at this year's CanSecWest, March 22-24 2023 in Vancouver, BC.
17:42
Game of Trees 0.86 released OpenBSD Journal
Version 0.86 of Game of Trees has been released (and the port updated):
17:24
The risk of pasting confidential company data into ChatGPT Security Affairs
Experts warn that employees are providing sensitive corporate data to the popular artificial intelligence chatbot model ChatGPT.
Researchers from Cyberhaven Labs analyzed the use of ChatGPT by 1.6 million workers at companies across industries. They reported that 5.6% of them have used it in the workplace and 4.9% have provided company data to the popular chatbot model since it launched. ChatGPT uses this data to build its knowledge base, but it publicly shares information built on it.
The use of ChatGPT is becoming a serious problem in the workspace, it can potentially cause the leak of sensitive and confidential data. For this reason, companies like JP Morgan and Verizon are blocking access to the chatbot over concerns about confidential data.
The experts reported that less than one percent (0.9%) of employees is responsible for 80% of leaks caused by pasting company data into the chatbot. This percentage could rapidly increase in the next months with the integration of the technology in multiple services, for example through the use of ChatGPT API.
Employees believe that the artificial intelligence chatbot developed by OpenAI can significatively improve their productivity.
The experts also warn that enterprise security software cannot monitor the use of ChatGPT by employees and prevent the leak of sensitive/confidential company data.
Since ChatGPT launched publicly, 5.6% of knowledge workers have tried using it at least once in the workplace. Furthermore, 2.3% of employees have put confidential company data into ChatGPT. reads the report published by Cyberhaven Labs. Despite a growing number of companies outright blocking access to ChatGPT, usage continues to grow exponentially. On March 1, our product detected a record 3,381 attempts to paste corporate data into ChatGPT per 100,000 employees, defined as data egress events in the chart below.
The researchers also monitored workers copying data out of the popular chatbot and pasting it elsewhere, like a company email, Google Doc, or their source code editor. They noticed that employees copy data out of the chatbot more than they paste company data into ChatGPT at a nearly 2-to-1 ratio.
The researchers pointed out that the average company leaks sensitive data to ChatGPT hundreds of times each week. For example, during the week of February 26 March 4, workers at the average company with 100,000 employees provided confidential documents into the AI-based chatbot 199 times, client data 173 times, and source code 159 times.
...17:15
KamiKakaBot Malware Used in Latest Dark Pink APT Attacks on Southeast Asian Targets The Hacker News
The Dark Pink advanced persistent threat (APT) actor has been linked to a fresh set of attacks targeting government and military entities in Southeast Asian countries with a malware called KamiKakaBot. Dark Pink, also called Saaiwc, was extensively profiled by Group-IB earlier this year, describing its use of custom tools such as TelePowerBot and KamiKakaBot to run arbitrary commands and
16:30
TSA issues additional cybersecurity rules for the aviation sector Help Net Security
The Transportation Security Administration (TSA) issued a new cybersecurity amendment to the security programs of certain TSA-regulated (airport and aircraft) operators in the aviation sector, following similar measures announced in October 2022 for passenger and freight railroad carriers. This is part of the Department of Homeland Securitys efforts to increase the cybersecurity resilience of U.S. critical infrastructure and follows extensive collaboration with aviation partners. Protecting our nations transportation system is our highest priority and TSA More
The post TSA issues additional cybersecurity rules for the aviation sector appeared first on Help Net Security.
16:07
ISS Swerves to Avoid Collision With Earth-Imaging Satellite SoylentNews
Earlier this week, the International Space Station was forced to adjust its orbit to avoid an encroaching commercial satellite. The object is likely one of many Earth-observing satellites that are falling into and aligning with the space station's orbital path, according to experts.
On Monday, the Progress 83 resupply ship that's docked to the space station fired its engines for just over six minutes, slightly raising the orbit of the ISS in order to avoid an approaching satellite, NASA wrote in a blog post. The space agency did not identify the object, except to say that it was an "Earth observation satellite."
However, there is speculation that the satellite in question may be Argentina's Nusat-17, one of 10 commercial Earth observation satellites form the Aleph-1 constellation operated by Satellogic. Jonathan McDowell, an astrophysicist at the Harvard-Smithsonian Center for Astrophysics, wrote on Twitter that the orbits of the Satellogic constellation has been gradually decaying and the satellites are now crossing the orbit of the ISS.
The latest ISS maneuver points to a larger issue of the growing number of satellites, both defunct and operational, and debris that pose a threat to orbiting spacecraft. More than 27,000 pieces of orbital debris are currently being tracked by the Department of Defense's global Space Surveillance Network, with lots of smaller pieces also floating around undetected.
Read more of this story at SoylentNews.
16:00
Fighting financial fraud through fusion centers Help Net Security
Keeping up with financial fraud is incredibly difficult because accurate fraud detection requires a deep, real-time analysis of all the events surrounding a transaction. Consider a typical payment transaction: A single transfer of funds to a new payee may not raise suspicion, but when authentication records show a discrepancy between the account owners usual geographic location and that of several device logins from multiple IP addresses in the same time frame, the transfer should be More
The post Fighting financial fraud through fusion centers appeared first on Help Net Security.
16:00
Flipper Zero Mayhem Hat Adds Camera, More Radios Hackaday

For a device advertised as the Multi-tool Device for Hackers, the Flipper Zero already offers a considerable list of onboard capabilities. But some hard decisions had to be made to get the retail price down, so features like WiFi and Bluetooth had to be left off. Luckily, theres an expansion interface along the top of the device which makes it possible to plug in additional hardware.
One of those expansions is the Mayhem Hat from [Erwin Ried]. This board adds many requested features to the Flipper Zero, as well as some that might not seem as obvious. The addition of an ESP32-CAM brings WiFi and Bluetooth to the party, while also unlocking access to the highly-capable ESP32Marauder firmware and the plethora of security research tools therein.
15:30
Understanding password behavior key to developing stronger cybersecurity protocols Help Net Security
Passwords are still the weakest link in an organizations network, as proven by the analysis of over 800 million breached passwords, according to Specops Software. The study found 88% of passwords used in successful attacks consisted of 12 characters or less, with the most common being 8 characters (24%). The most common base terms used in passwords were: password, admin, welcome and p@ssw0rd. Passwords containing only lowercase letters were the most common character combination found, More
The post Understanding password behavior key to developing stronger cybersecurity protocols appeared first on Help Net Security.
15:15
FBI Finally Admits to Buying Location Data on Americans cryptogon.com
As disturbing as this Ars Technica piece is, the actual situation might as well be infinitely worse. In 2013, we learned that law enforcement was laundering data collected through U.S. national security intercept systems for use against Americans, U.S. Communications Intelligence Secretly Shared with Law Enforcement for Use Against Americans in Criminal Investigations: Its just []
15:00
New algorithm may change the future of secure communication Help Net Security
Researchers have made a significant breakthrough in secure communication by developing an algorithm that conceals sensitive information so effectively that it is impossible to detect anything hidden. The team, led by the University of Oxford in close collaboration with Carnegie Mellon University, envisages that this method may soon be used widely in digital human communications, including social media and private messaging. In particular, the ability to send perfectly secure information may empower vulnerable groups, such More
The post New algorithm may change the future of secure communication appeared first on Help Net Security.
15:00
Linux 6.3-rc2 Released With Two AMD Workarounds, Drops The Useless r8188eu Driver Phoronix
The Linux 6.3-rc2 kernel is out today as the second weekly kernel test release since last weekend's closure of the Linux 6.3 merge window...
14:41
Deluxe Home Vintage Computer Den cryptogon.com
Via: Ars Technica: In a world where millions of people carry a 1990s-grade supercomputer in their pockets, its fun to revisit tech from a time when a 1 megahertz machine on a desktop represented a significant leap forward. Recently, a collector named Brian Green showed off his vintage computer collection on Twitter, and we thought []
13:35
Audio: Sirius Never Paid the Pension Provider, Staff Was in Effect Defrauded schestowitz.com
Video download link |
md5sum fadf7fcdfd1c9473e9ab4e8ebfed252e
Sirius Pension Crimes
Creative Commons Attribution-No Derivative Works 4.0
Summary: The company known as Sirius Open Source has stolen money of many workers; today we share audio of management at the pension provider admitting behaviour to that effect
THE news will be full of discussions about banks later today. People cannot access their own accounts, businesses cannot pay their workers, and as just noted two or three banks have already been suspended (some over the weekend). The time seems right to continue with our series about how Sirius plundered not just my pension but also colleagues or, as it seems on the surface, put the pension money in its own pockets (I can think of 3 people who conspired to do this) instead of a pension fund, in effect embezzling workers and falsifying payslips. As readers may recall from December, there were incidents of payslips not being sent out at all (for long periods of time, including for months before I resigned).
Over the next few weeks well share more information about what happened. The lesson for the general public is, check whether what employers say about pensions is true and get in contact with pension providers to verify youre not being lied to (validation of claims is imperative).
Of all the payslips I do have, in about 60 of them I have evidence of pensions being contributed to; but thats false, as the company did not pass the money and former colleagues were similarly embezzled. Played out in the video above (from a 55-minute audio) is 0-1:20, 1:50-, 2:30-5:40, 11:50-20:00, 21:18-22:08, 22:15-, 26:30-36:30, 39:40-, 41:55-51:00, 51:10-. I basically skip the pauses (waiting on the line), some personally-identifying details/codes and towards the end I note that even though the manager said shed contact me today (6 days ago) it never happened. They dont seem to consider embezzlement impacting many employees im...
13:26
The Sirius Pensions Heist Confirmed by the Pension Provider Techrights
Video download link |
md5sum fadf7fcdfd1c9473e9ab4e8ebfed252e
Sirius Pension Crimes
Creative Commons Attribution-No Derivative Works 4.0
Summary: The company known as Sirius Open Source has stolen money of many workers; today we share audio of management at the pension provider admitting behaviour to that effect
THE news will be full of discussions about banks later today. People cannot access their own accounts, businesses cannot pay their workers, and as just noted two or three banks have already been suspended (some over the weekend). The time seems right to continue with our series about how Sirius plundered not just my pension but also colleagues or, as it seems on the surface, put the pension money in its own pockets (I can think of 3 people who conspired to do this) instead of a pension fund, in effect embezzling workers and falsifying payslips. As readers may recall from December, there were incidents of payslips not being sent out at all (for long periods of time, including for months before I resigned).
Over the next few weeks well share more information about what happened. The lesson for the general public is, check whether what employers say about pensions is true and get in contact with pension providers to verify youre not being lied to (validation of claims is imperative).
In some ways it feels like 2008 re-enacted, except now they blame Russia, China, pandemic, crypto etc.Of all the payslips I do have, in about 60 of them I have evidence of pensions being contributed to; but thats false, as the company did not pass the money and former colleagues were similarly embezzled. Played out in the video above (from a 55-minute audio) is 0-1:20, 1:50-, 2:3...
13:18
The Time Russians Really Did Target Americans With Microwaves SoylentNews
The Time Russians Really Did Target Americans With Microwaves
A year before his arrival, State Department officials had told embassy staffers and their families that the Soviet Union had been blasting some kind of microwave beam at the embassy for up to 14 hours per day. But American higher-ups said there was little reason for concern. Issuing a "Fact Sheet," [1976] the State Department said that this microwave beam later dubbed the "Moscow Signal" was "no cause for concern," as "no causal relationship had been established between these microwave transmissions and any health problems."
There was, in other words, nothing to worry about. As a precaution, American officials erected aluminum "screening" around the embassy all the better to "reduce the anxiety of employees." But that was it. And so Schumaker went about his work, day in and day out. For years, he and dozens of others operated out of the American embassy, assured that the microwave radiation was perfectly normal.
It was only years later, when Schumaker received a surprise leukemia diagnosis and after multiple American ambassadors had already died from cancer, with the another diagnosed with a "severe blood disorder" that Schumaker realized that microwave radiation, and the U.S.'s lackadaisical response, was far more disastrous, and even fatal, than he ever thought. And in recent months, that realization only deepened, for a pair of reasons.
First, a tranche of newly declassified documents confirmed that the Soviets saturated American embassy staffers in decades of elevated microwave radiation and American higher-ups spent years trying to sweep the entire affair under the rug. And second, recent revelations about the so-called "Havana Syndrome" have given Schumaker and other diplomats who remember the days of Moscow Signal a sense of, as he sees it, "dj vu all over again."
Read more of this story at SoylentNews.
13:00
Efficient x86_64 Emulation with Box86 Hackaday

Running applications on a different architecture than the one for which they were compiled is a common occurrence, not in the least with Apples architectural migration every decade or so. Its also commonly used with for example ARM, OpenRISC, and RISC-V systems to run applications that are only available for x86 or x86_64. While QEMU and kin are often used here, theyre pretty resource heavy, which is where an option like Box86 and its 64-bit sibling Box64 are attractive options. Unlike QEMU, both offer dynamic recompilation and redirection of dynamic library calls to native libraries, including those for SDL and OpenGL.
Both are available on GitHub under an MIT license, with Box64 probably the most interesting these days as applications and games have moved on to a 64-bit only world. The only hard requirement that Box64 has for a host system is that it is little-endian, which is a pretty easy requirement to meet. The most recent release was on March 10th, with Box86 0.3 and Box64 0.2.2. As essentially a translation layer, it does not offer full compatibility with every bit of software out there, but it...
12:47
Mozilla and Many Other Companies Are in Trouble as Silicon Valley Bubbles Are Bursting Techrights
Video download link |
md5sum 2c5c09befcd83be44bd00fedc02d351c
Mozilla and SVB
Creative Commons Attribution-No Derivative Works 4.0
Summary: Some banks are collapsing, including very major ones; it seems like Mozilla will be among the companies affected
THE US regulators have just shut down another bank the second if not third one in days (during weekend). This is a very serious matter and itll caused a lot of panic later today when European markets open (and then American ones). What companies that we know and care about are impacted by this? Well, Mozilla seems like one of them.
The video above is a bunch of more personal thoughts and my interpretation of the situation. These turbulent times can affect Free software (negatively) and its safe to predict the matter will be in the news for weeks to come.
11:19
Kernel prepatch 6.3-rc2 LWN.net
The 6.3-rc2 kernel prepatch is out.
This one looks fairly normal, although if you look at the diffs, they are dominated by the removal of a staging driver (r8188eu) that has been superceded by a proper driver. That removal itself is 90% of the diffs. But if you filter that out, it all looks normal
11:12
DistroWatch Weekly, Issue 1010 DistroWatch.com: News
This week in DistroWatch Weekly: Review: blendOS 2023.01.26News: Improved network widget comes to elementary OS, Vanilla OS changes its base, Slackware phases out legacy dependenciesQuestions and answers: Keeping track of which files a package installsReleased last week: LibreELEC 11.0.0, Rescuezilla 2.4.2, siduction 22.1.1, helloSystem 0.8.1Torrent corner: SparkyLinuxUpcoming releases:....
11:00
HPR3811: mkfifo and named pipes Hacker Public Radio
A named pipe is like a UNIX pipe, except it takes the form of a file. $ mkfifo mypipe $ echo "Hacker Public Radio" > mypipe & $ cat mypipe Hacker Public Radio
Covert Cloud Communication with Lambdas It Will Never Work in Theory
The biggest change in practical computing in the last decade has been the nearly-universal return to shared hardware. As with the mainframes of my youth, companies rent time on other people's computers rather than buying and managing their own. And as with any form of sharing, that opens up new security holes and new avenues of attack.
This paper looks at something I would once have dismisssed as Hollywood word salad: covert communication between lambdas co-resident on the same physical server. The authors leverage the hardware's memory bus to detect what's running, and show that they can send a couple of hundred bits per second between supposedly-isolated processes. That might not seem like a lot, but it's more than enough to share a password or a private key, and like most of computer security it's both fascinating and frightening.
Anil Yelam, Shibani Subbareddy, Keerthana Ganesan, Stefan Savage, and Ariana Mirian. CoResident evil: covert communication in the cloud with lambdas. In Proceedings of the Web Conference 2021. ACM, Apr 2021. doi:10.1145/3442381.3450100.
"Serverless" cloud services, such as AWS lambdas, are one of the fastest growing segments of the cloud services market. These services are popular in part due to their light-weight nature and flexibility in scheduling and cost, however the security issues associated with serverless computing are not well understood. In this work, we explore the feasibility of constructing a practical covert channel from lambdas. We establish that a fast co-residence detection for lambdas is key to enabling such a covert channel, and proceed to develop a reliable and scalable co-residence detector based on the memory bus hardware. Our technique enables dynamic discovery for co-resident lambdas and is incredibly fast, executing in a matter of seconds. We evaluate our approach for correctness and scalability, and use it to establish covert channels and perform data transfer on AWS lambdas. We show that we can establish hundreds of individual covert channels for every 1000 lambdas deployed, and each of those channels can send data at a rate of ~200 bits per second, thus demonstrating that covert communication via lambdas is entirely feasible.
Linux 6.3-rc2 Introduces Stuttering Workaround For AMD Ryzen PCs Due To fTPM RNG Phoronix
Since the Linux 6.1 kernel various users have reported system stuttering issues when using modern AMD Ryzen systems. This has been similar to an "intermittent system stutter" issue AMD disclosed last year for Windows 10 and Windows 11 while now for today's Linux 6.3-rc2 a workaround is finally being merged that in turn will also be back-ported to the stable kernel series...
10:00
Hackaday Links: March 12, 2023 Hackaday

With a long history of nearly universal hate for their products, youd think printer manufacturers would by now have found ways to back off from the policies that only seem to keep aggravating customers. But rather than make it a financially wiser decision to throw out a printer and buy a new one than to buy new ink cartridges or toners, manufacturers keep coming up with new and devious ways to piss customers off. Case in point: Hewlett-Packard now seems to be bricking printers with third-party ink cartridges. Reports from users say that a new error message has popped up on screens of printers with non-HP cartridges installed warning that further use of the printer has been blocked. Previously, printers just warned about potential quality issues from non-HP consumables, but now theyre essentially bricked until you cough up the money for legit HP cartridges. Users who have contacted HP support say that they were told the change occurred because of a recent firmware update sent to the printer, so thats comforting.
In other news of corporate unpleasantness, if youve bought into t...
08:34
NASA Ready for Artemis II SoylentNews
The Moon or Bust, Says NASA, After Successful Test Flight
Heat shield sustained more damage than expected, but this shouldn't discourage astronauts:
NASA is ready to fly a crew of astronauts to the Moon next year after the success of the first test flight of its Space Launch System (SLS) rocket and Orion capsule.
[...] Orion fulfilled 161 test objectives and was more energy efficient than predicted, generating 20 per cent more power than predicted while consuming about 25 per cent less power than expected. All maneuvers including flying to and from the Moon, returning to Earth, and releasing the parachute for splashdown into the Pacific Ocean were executed without any major problems.
There are, however, a few niggling complications. Orion's latching current limiters which act like circuit breakers to transfer and distribute power from its solar panels switched open randomly during its flight for unknown reasons. Also, the material covering the heat shield used to protect the capsule and prevent it and any occupants from incineration as Orion re-enters Earth's atmosphere deteriorated more than NASA thought it would.
Little things like that.
The mobile launcher part of the SLS also sustained more damage than expected. NASA said its cryogenic fuel lines corroded, while 60 panels and cabinets broke, as did its elevators and blast shields. Officials continue to review hundreds of gigabytes worth of data gathered from the mission.
[...] "We're learning as much as we possibly can from Artemis I to ensure we fully understand every aspect of our systems and feed those lessons learned into how we plan for and fly crewed missions," said Jim Free, NASA associate administrator for the Exploration Systems Development Mission Directorate, in a prepared statement. "Safely flying crew is our top priority for Artemis II."
Engineers will, for example, modify the mobile launcher for the upcoming Artemis mission. They will build an emergency egress system at the launchpad in case the crew needs to make a last-minute exit from the rocket.
Read more of this story at SoylentNews.
07:46
Security Affairs newsletter Round 410 by Pierluigi Paganini Security Affairs
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are free for you in your email box.
If you want to also receive for free the newsletter with the international press subscribe here.
07:00
A Parts Bin Cyberdeck Built for Satellite Hacking Hackaday

While theres little in the way of hard rules dictating what constitutes a cyberdeck, one popular opinion is that it should be a piecemeal affair a custom rig built up of whatever high-tech detritus the intrepid hacker can get their hands on, whether it be through trades or the time-honored tradition of dumpster diving. It should also be functional, and ideally, capable of some feats which would be difficult to accomplish with a garden variety laptop.
If youre looking for an example that embraces these concepts to the fullest, look no further than the Spacedeck built by [saveitforparts]. Combining a touch screen all-in-one computer pulled from a police cruiser in the early 2000s, an RTL-SDR, and the contents of several parts bins, the rig is designed to work in conjunction with his growing collection of motorized satellite dishes to sniff out signals from space.
06:37
Robin Mansukhani, CEO of Deciduous Therapeutics, a venture-backed startup developing novel immunotherapies to treat age-related diseases, joins our Life Extension Board. Lifeboat News
Robin Mansukhani, CEO of Deciduous Therapeutics, a venture-backed startup developing novel immunotherapies to treat age-related diseases, joins our Life Extension Board.
05:45
GNOME 44 Release Candidate Arrives With Many Last Minute Changes Phoronix
The GNOME 44 release candidate was officially declared today as desktop later this month...
04:41
Why Would OpenAI Send ChatGPT Takedown Notices to Google? TorrentFreak
 ChatGPT
has captured the imagination of millions of people, offering a
glimpse of what an AI-assisted future might look like.
ChatGPT
has captured the imagination of millions of people, offering a
glimpse of what an AI-assisted future might look like.
The new technology also brings up novel copyright questions. Several people are worried that their work is being used to train AI without any form of compensation, for example.
Parent company OpenAI may in turn be worried that third parties are exploiting the ChatGPT model without permission. Thats what a recent DMCA takedown notice sent to Google tends to suggest.
OpenAIs Takedown Notice
The takedown request lists OpenAI as the sender and targets several ChatGPT-related links. These include the ChatGod app, which has since been removed from Google Play, as well as the Chat AI Pro app for iOS.
The notice isnt just restricted to apps. It also lists a PC Guide article with information on the chatbot, which appears to be relatively harmless.
This isnt the first time that an OpenAI takedown notice has shown up in Googles transparency report. In December, a similar DMCA request asked for the removal of an AI writing tools GitHub repository.
Legitimate?
These enforcement actions are certainly newsworthy, but we cant independently confirm that OpenAI sent them. In the past, we have seen plenty of imposters claiming to be reputable rightsholders, and it could be the case here as well.
TorrentFreak reached out to OpenAI to confirm or deny the legitimacy of the notices but the organization didnt respond. Googles view on the matter is also unknown. What we do know is that the search engine hasnt removed any of the reported URLs.
Without a co...
04:00
Building the Sanni Cartridge Reader To Back Up and Restore Games and Saves Hackaday

Game cartridges are generally seen as a read-only medium with the contents as immutable as text chiseled into a granite slab, and with accompanying save files on the cartridge surviving for generations. The unfortunate truth is that as with any media storage, cartridges can and do fail, and save files are often just ethereal bits in battery-backed SRAM. This makes being able to copy not only the game data but also the save files off these cartridges essential. Projects like the Open Source Cartridge Reader by [sanni] make this something that everyone can do.
Intended to be a kind of Swiss Army knife of game cartridges, many game systems are supported directly, and many others via (user-created) adapters. A how-to-build tutorial is provided on the project wiki, though anyone inte...
03:50
DuckDuckGo's New Wikipedia Summary Bot: We Fully Expect It to Make Mistakes SoylentNews
Not to be left out of the rush to integrate generative AI into search, on Wednesday DuckDuckGo announced DuckAssist, an AI-powered factual summary service powered by technology from Anthropic and OpenAI. It is available for free today as a wide beta test for users of DuckDuckGo's browser extensions and browsing apps. Being powered by an AI model, the company admits that DuckAssist might make stuff up but hopes it will happen rarely.
Here's how it works: If a DuckDuckGo user searches a question that can be answered by Wikipedia, DuckAssist may appear and use AI natural language technology to generate a brief summary of what it finds in Wikipedia, with source links listed below. The summary appears above DuckDuckGo's regular search results in a special box.
[...] Update (March 9, 2023): We spoke with a representative of DuckDuckGo and they said they're using OpenAI's GPT-3.5 and Anthropic's Claude as LLMs. "We're experimenting with OpenAI's recently announced Turbo model, too," they said.
Related:
Robots
Let ChatGPT Touch the Real World Thanks to Microsoft (Article
has a bunch of other SoylentNews related links as well.)
Read more of this story at SoylentNews.
03:31
Recognizing the worst in government transparency.
The Foilies are co-written by EFF and MuckRock News and published in alternative newspapers around the country through a partnership with the Association of Alternative Newsmedia.
It seems like these days, everyone is finding classified
documents in places they shouldn't be: their homes, their offices,
their storage lockers, their garages, their guitar cases, between
the cracks of their couches, under some withered celery in the
vegetable drawer OK, we're exaggeratingbut it is getting
ridiculous.
While the pundits continue to speculate whether President
Donald Trump, Vice President Mike Pence and President Joe Biden put
national security at risk by hoarding these secrets, that
ultimately might not be the biggest problem.
What we know for sure is that these episodes illustrate
overlapping problems for government transparency. It reveals an
epidemic of over-aggressive classification of documents that could
easily be made public. It means that an untold number of documents
that belong to the public went missingeven though we may not get to
see them for at least 25 years, when the law requires a mandatory
declassification review. And then there's the big, troubling
transparency question: If these officials pocketed national
secrets, what other troves of non-secret but nonetheless important
documents did they hold on to, potentially frustrating the public's
ability to ever see them?
It doesn't do much good to file a Freedom of Information Act request for records that have mysteriously disappeared.
Misbehavior like this is why we created The Foilies, our annual tongue-in-cheek awards for agencies and officials that thwart the public's right to government information or otherwise respond outrageously to requests for documents and records. Each year, the Electronic Frontier Foundation and MuckRock News, in partnership with the Association of Alternative Newsmedia, publish this list of ne'er-do-wells to celebrate Sunshine Week (March 12-18)an annual event to raise the profile of the democratic concept of government transparency.
It may be many years before the public learns what secret and not-so-secret documents weren't turned over by past administrations to the National Archives. But when we do, we'll be sure to nominate them for the top prizes. In the meantime, we have no shortage of redaction rascals and right-to-know knaves, from agencies assessing astronomical fees to obtain documents to officials who overtly obstruct openness to protect corporat...
03:14
Links 12/03/2023: GNOME Extensions Site Adds Download Counts Techrights
![]()
Contents
-
GNU/Linux
-
Instructionals/Technical
-
Citizix How to set up Wireguard on Ubuntu 22.04
WireGuard is a communication protocol and free and open-source software that implements encrypted virtual private networks, and was designed with the goals of ease of use, high speed performance, and low attack surface. It is a lightweight Virtual Private Network (VPN) that supports IPv4 and IPv6 connections.
-
ID Root How To Install Ansible on Fedora 37
In this tutorial, we will show you how to install Ansible on Fedora 37. For those of y...
-
-
03:08
Linux Landing XMM Register Rollback Workaround For AMD Zen 1 / Zen 2 CPUs Phoronix
Sent in this morning via x86/urgent for integration into Linux 6.3 and also for back-porting to stable kernel series is disabling the XSAVES instruction for AMD Zen 1 and Zen 2 processors to workaround an AMD processor erratum made public last year...
01:25
Acronis states that only one customers account has been compromised. Much ado about nothing Security Affairs
Acronis downplays the severity of the recent security breach explaining that only a single customers account was compromised.
The CISO of Acronis downplayed a recent intrusion, revealing that only one customer was impacted.
This week a threat actor, who goes online with the moniker kernelware, claimed the theft of data from technology firm Acronis and started leaking it on the cybercrime forum Breached Forums.
The threat actor is the same who recently offered for sale the data stolen from Taiwanese multinational hardware and electronics corporation Acer.
The Acronis leak contains multiple certificate files, command logs, system configurations, system information logs, filesystem archives, python scripts for the companys maria.db database, backup configuration stuff, screenshots of backup operations,
Based on our investigation so far, the credentials used by a single specific customer to upload diagnostic data to Acronis support have been compromised. We are working with that customer and have suspended account access as we resolve the issue. We also shared IOCs with our industry partners and work with law enforcement. said Acronis CEO Kevin Reed. No other system or credential has been affected. There is no evidence of any other successful attack, nor there is any data in the leak that is not in the folder of that one customer. Our security team is obviously on high alert and the investigation continues.
The company added that its products were not affected by the security breach and that it is not aware of vulnerabilities affecting its s...
01:00
The EV Battery Wish List IEEE Spectrum
Electric cars barely existed in 2010, when the Tesla Model S was still a glint in Elon Musks eye. Now more than 20 million EVs girdle the globe, according to BloombergNEFand that count is expected to nearly quadruple to 77 million by 2025. A battery will be the high-voltage heart of each of those 77 million electric vehicles, and by far their most expensive component, setting off a worldwide race to ethically source their materials and crank up production to meet exploding demand.
EVs may have seized a record 5.8 percent of the United States market in 2022, according to J.D. Power, and could approach 11 percent of the global market this year. But experts still believe that better batteries, and many more of them, are a key to EVs reaching a market tipping point, even as Reuters projects automakers spending a whopping $1.2 trillion to develop and produce EVs through 2030.
IEEE Spectrum asked five industry experts to gaze deeply into their own crystal balls and outline what needs to happen in the EV battery space to wean the world off fossil-fueled transportation and onto the plug. Heres what they said:
Emad Dlala, Lucid Motors, vice-president of powertrain
Upstart Lucid Motors hasnt built many cars, but its built a reputation with the record-setting, 830-kilometer driving range of the Air Grand Touring Performance sedan. That range is a testament to Lucids obsessive pursuit of efficiency: The Air uses the same 2170-format cylindrical cells (supplied by Samsung SDI) as many EVs, but ekes out more miles via superior battery management, compact-yet-muscular power units and slippery aerodynamics.
Sophisticated chassis and battery design gives new life to lesser chemistriesespecially lithium iron phosphate thats the hottest thing in batteries around the worldthat would otherwise be uncompetitive and obsolete.
One might think Lucid would call for every electric model to cover such vast distances. Instead, Lucid leaders see a bright future in cars that aim for maximum efficiency rather than range...










 additions & protect yourself from a malicious
additions & protect yourself from a malicious