| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Thursday, 16 March
01:00
Review: XHDATA D-219 Short Wave Radio Receiver Hackaday

As any radio amateur will tell you, the world of radio abounds with exciting possibilities. Probably the simplest pursuit of them all is that of the SWL, or short wave listener, who scours the airwaves in search of interesting stations. SWLs will often have fully-featured setups with high-end general-coverage communications receivers and tuned antenna arrays, but it can start with the cheapest of radios at its bottom end. Such a radio is the subject of this review, the XHDATA D-219 is a miniature portable receiver that costs under ten dollars, yet is currently the talk of the town in SWL circles. This interest is in no small amount due to its being an especially low-price way to get your hands on a shortwave radio using one of the SIlicon Labs integrated software-defind radio receiver chips. We dont often review a consumer radio here at Hackaday, but with an avid eye for unexpected gems at the cheaper end of the market this ones worth a second look.
What Do You Get For Your Tenner?
00:49
YoroTrooper Stealing Credentials and Information from Government and Energy Organizations The Hacker News
A previously undocumented threat actor dubbed YoroTrooper has been targeting government, energy, and international organizations across Europe as part of a cyber espionage campaign that has been active since at least June 2022. "Information stolen from successful compromises include credentials from multiple applications, browser histories and cookies, system information and screenshots," Cisco
00:23
00:22
Debian project leader elections 2023 LWN.net
The 2023 election for the Debian project leader looks to be a relatively unexciting affair: incumbent leader Jonathan Carter is running unopposed for a fourth term. His platform lays out his hopes and plans for that term.
00:22
A 53-year-old longevity researcher says his biological age is a decade younger thanks to 4 daily habits but the science behind them is mixed Lifeboat News: The Blog
Thats got molecules in it that will prevent cancer, among other things like anti-inflammatory properties, he said. Some older research has shown, for example, that green tea consumption might be linked to a lower risk of stomach cancer.
Sinclair also said he takes supplements (like those sold on the Tally Health website) that contain resveratrol, which his teams research has shown can extend the lifespan of organisms like yeast and worms.
While the compound, famously found in red wine, is known to have anti-inflammatory, anti-cancer, heart health, and brain health benefits, the research is mixed on if or how well such benefits can be achieved in humans through a pill.
00:05
Security updates for Wednesday LWN.net
Security updates have been issued by Debian (node-sqlite3 and qemu), Fedora (libmemcached-awesome, manifest-tool, sudo, and vim), Red Hat (gnutls, kernel, kernel-rt, lua, and openssl), Slackware (mozilla), SUSE (amanda, firefox, go1.19, go1.20, jakarta-commons-fileupload, java-1_8_0-openjdk, nodejs18, peazip, perl-Net-Server, python, python-cryptography, python-Django, python3, rubygem-rack, and xorg-x11-server), and Ubuntu (ipython, linux-ibm, linux-ibm-5.4, and linux-kvm).
Wednesday, 15 March
23:24
Vitamin D Reduced Dementia by 40% cryptogon.com
Never forget how mainstream/corporate controlled medicine refused to acknowledge the Vitamin D Covid relationship. My guess is that you wont hear much about this Vitamin D dementia research from them either. Via: Dr. John Campbell:
23:10
How Mirel Sehic relies on simplicity to focus on product security Help Net Security
If you are developing a modern medical, manufacturing, or logistics facility, theres no doubt that a large portion of your investment was made into the electronic aspects of your device. Sensors, connected devices, and machinery are synchronized to deliver a streamlined experience. For facility operators, this includes elevators, HVAC systems, PLC controls, valves, pumps, and a whole slew of systems that we dont think of as connected. And thats precisely the problem. Many of the More
The post How Mirel Sehic relies on simplicity to focus on product security appeared first on Help Net Security.
23:04
First Demonstration of Universal Control of Encoded Spin Qubits SoylentNews
First demonstration of universal control of encoded spin qubits:
HRL Laboratories, LLC, has published the first demonstration of universal control of encoded spin qubits. This newly emerging approach to quantum computation uses a novel silicon-based qubit device architecture, fabricated in HRL's Malibu cleanroom, to trap single electrons in quantum dots. Spins of three such single electrons host energy-degenerate qubit states, which are controlled by nearest-neighbor contact interactions that partially swap spin states with those of their neighbors.
[...] The encoded silicon/silicon germanium quantum dot qubits use three electron spins and a control scheme whereby voltages applied to metal gates partially swap the directions of those electron-spins without ever aligning them in any particular direction. The demonstration involved applying thousands of these precisely calibrated voltage pulses in strict relation to one another over the course of a few millionths of a second.
The quantum coherence offered by the isotopically enriched silicon used, the all-electrical and low-crosstalk-control of partial swap operations, and the configurable insensitivity of the encoding to certain error sources combine to offer a strong pathway toward scalable fault tolerance and computational advantage, major steps toward a commercial quantum computer.
[...] "It is hard to define what the best qubit technology is, but I think the silicon exchange-only qubit is at least the best-balanced," said Thaddeus Ladd, HRL group leader and co-author.
Journal Reference: Aaron J. Weinstein et al, Universal logic with encoded spin qubits in silicon, Nature (2023). https://dx.doi.org/10.1038/s41586-023-05777-3
Read more of this story at SoylentNews.
22:22
AI Might Be Seemingly Everywhere, but There Are Still Plenty of Things It Cant DoFor Now Lifeboat News: The Blog

These days, we dont have to wait long until the next breakthrough in artificial intelligence impresses everyone with capabilities that previously belonged only in science fiction.
In 2022, AI art generation tools such as Open AIs DALL-E 2, Googles Imagen, and Stable Diffusion took the internet by storm, with users generating high-quality images from text descriptions.
Unlike previous developments, these text-to-image tools quickly found their way from research labs to mainstream culture, leading to viral phenomena such as the Magic Avatar feature in the Lensa AI app, which creates stylized images of its users.
22:10
Data loss prevention company hacked by Tick cyberespionage group Help Net Security
ESET researchers have uncovered a compromise of an East Asian data loss prevention (DLP) company. The attackers utilized at least three malware families during the intrusion, compromising both the internal update servers and third-party tools utilized by the company. This resulted in two of the companys customers being subsequently compromised. Illustration of the chain of compromise ESET attributes the campaign with high confidence to the Tick APT group. Based on Ticks profile, the objective of More
The post Data loss prevention company hacked by Tick cyberespionage group appeared first on Help Net Security.
22:00
The International Space Station Is Always Up There Hackaday
Thanks to its high orbital inclination, the International Space Station (ISS) eventually passes over most inhabited parts of the Earth. Like other artificial satellites, though, its typically only visible overhead during passes at sunrise and sunset. If youd like to have an idea of where it is beyond the times that its directly visible, take a look at this tabletop ISS tracking system created by [dpelgrift].
22:00
Linux 6.4 Looking To Drop The SLOB Memory Allocator Phoronix
A patch series is proposing that the SLOB memory allocator be removed from the Linux 6.4 kernel this summer...
21:44
The Latest from New Horizons Centauri Dreams Imagining and Planning Interstellar Exploration
New Horizons is, like the two Voyagers, a gift that keeps on giving, even as it moves through the Kuiper Belt in year 17 of its mission. Thus the presentations that members of the spacecraft team made on March 14 at the 54th Lunar and Planetary Science Conference. Papers will flow out of these observations, including interpretations of the twelve mounds on the larger lobe of Arrokoth, the contact binary that is being intensely studied through stereo imaging to identify how these features formed around a larger center mound. Alan Stern (SwRI) is principal investigator for the New Horizons mission:
We discovered that the mounds are similar in many respects, including their sizes, reflectivities and colors. We believe the mounds were likely individual components that existed before the assembly of Arrokoth, indicating that like-sized bodies were formed as precursors to Arrokoth itself. This is surprising, and a new piece in the puzzle of how planetesimals building blocks of the planets, like Arrokoth and other Kuiper Belt objects come together.
Science team members also discussed the so-called bladed terrain, evidently the product of methane ice, that seems to stretch across large areas of Plutos far side, as observed during the spacecrafts approach. It was intriguing to learn as well about the spacecrafts observations of Uranus and Neptune, which will complement Voyager imaging at different geometries and longer wavelengths. And Plutos true polar wander (the tilt of a planet with respect to its spin axis came into play (and yes, I do realize Ive just referred to Pluto as a planet). Co-investigator Oliver White:
Were seeing signs of ancient landscapes that formed in places and in ways we cant really explain in Plutos current orientation. We suggest the possibility is that they formed when Pluto was oriented differently in its early history, and were then moved to their current location by true polar wander.

Image: Plutos Sputnik Planitia, the huge impact basin found in Plutos heart region, seems to have much to do with the worlds axial tilt, while the possibility of a deep ocean pushing against the basin from below has to be taken into account. This image is from the presentation by Oliver...
21:41
Security Firm Rubrik breached by Clop gang through GoAnywhere Zero-Day exploitation Security Affairs
Data security firm Rubrik discloses a data breach, attackers exploited recent GoAnywhere zero-day to steal its data.
Cybersecurity firm Rubrik disclosed a data breach, a ransomware group stolen compeny data by exploiting the recently disclosed zero-day vulnerability in the Fortra GoAnywhere secure file transfer platform.
The company was the victim of a large-scale campaign targeting GoAnywhere MFT devices worldwide by exploiting the zero-day vulnerability.
Rubrik immediately launched an investigation into the incident with the help of third-party forensics experts.
In early February, the popular investigator Brian Krebs first revealed details about the zero-day on Mastodon and pointed out that Fortra has yet to share a public advisory.
According to the private advisory published by Fortra, the zero-day is a remote code injection issue that impacts GoAnywhere MFT. The vulnerability can only be exploited by attackers with access to the administrative console of the application.
Installs with administrative consoles and management interfaces that are not exposed on the internet are safe, however, security researcher Kevin Beaumont discovered about 1000 Internet-facing consoles.
Fortra recommends GoAnywhere MFT customers review all administrative users and monitor for unrecognized usernames, especially those created by system.
According to a statement published by Rubrik, the breach was quickly contained and only impacted a non-production IT testing environment.
We detected unauthorized access to a limited amount of information in one of our non-production IT testing environments as a result of the GoAnywhere vulnerability. Importantly, based on our current investigation, being conducted with the assistance of third-party forensics experts, the unauthorized access did NOT include any data we secure on behalf of our customers via any Rubrik products. reads the statement.
The current investigation has determined there was no lateral movement to other environments. Rubrik took the involved non-production environment offline and leveraged our own security systems and solutions to quickly contain the threat and help restore our test environment.
The company states that stolen data include internal sales information, certain customer and partner company information, and a limited number of purchase orders from its distributors. The company pointed out that customer...
21:38
Open3D 0.17 Released For Open-Source 3D Data Processing Phoronix
Open3D as an open-source library for 3D data processing from 3D machine learning tasks to adaptable viewing of 3D data is out with its newest feature release...
21:19
SPECFEM3D 4.0 Released With AMD HIP GPU Support Phoronix
The latest notable high performance computing (HPC) open-source project adding mainline support for AMD HIP with ROCm is SPECFEM3D...
21:11
New Cryptojacking Operation Targeting Kubernetes Clusters for Dero Mining The Hacker News
Cybersecurity researchers have discovered the first-ever illicit cryptocurrency mining campaign used to mint Dero since the start of February 2023. "The novel Dero cryptojacking operation concentrates on locating Kubernetes clusters with anonymous access enabled on a Kubernetes API and listening on non-standard ports accessible from the internet," CrowdStrike said in a new report shared with The
GCC 13 Adds RISC-V T-Head Vendor Extension Collection Phoronix
Being merged today into the GCC 13 compiler is the set of T-Head vendor extensions to the RISC-V ISA. This set of vendor extensions is designed to augment the RISC-V ISA and provide faster and more energy efficient capabilities...
20:51
The Qt Group Launches Qt Insight Phoronix
The Qt Group as the company behind the Qt open-source toolkit has launched Qt Insight as their newest software offering. However, Qt Insight does not appear to be open-source and is marketed as a SaaS product...
20:46
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Jan Engelhardt on Mar 15
But also: "Perfection is achieved, not when there is nothing more toadd, but when there is nothing left to take away", and it would
appear TIOCSTI does not have https://xkcd.com/2347/ -criticality.
20:44
Founder of the Free Software Movement, Richard Stallman, Turns 70 Techrights
Summary: In some parts of the world it is already the 16th of the month; thats the 70th birthday of Richard Stallman
20:43
The Different Methods and Stages of Penetration Testing The Hacker News
The stakes could not be higher for cyber defenders. With the vast amounts of sensitive information, intellectual property, and financial data at risk, the consequences of a data breach can be devastating. According to a report released by Ponemon institute, the cost of data breaches has reached an all-time high, averaging $4.35 million in 2022. Vulnerabilities in web applications are often the
20:42
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Hanno Bck on Mar 15
From a security perspective tossing out functionality is the betteroption compared to restricting access. If there is practically no use
of that functionality and it's mostly a security risk, then removing it
is the right choice.
Reducing complexity is a good principle for IT security.
20:36
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Casper Dik on Mar 15
I think it makes it mostly useless.In Solaris we've changed how TIOCSTI works; when a process reads the
packet with the stuffed input, it then checks the credential of the
sender. So while the stuffed input is still echoed but ignored:
# su nobody -c tiocsti
exit
echo Payload as `whoami`
#
But when having root calling tciosti, you get:
# su root -c tiocsti
exit
echo Payload as `whoami`
# exit
Payload as root
(The exit here is not...
20:23
Elon Musk reacts to ChatGPT successor GPT-4 passing major exams, says what will humans do? Lifeboat News: The Blog
ChatGPTs successor GPT-4 has not just passed various major exams, but has actually aced them. Elon Musk has now reacted to the news and says, What will humans do?
20:23
Tick APT Targeted High-Value Customers of East Asian Data-Loss Prevention Company The Hacker News
A cyberespionage actor known as Tick has been attributed with high confidence to a compromise of an East Asian data-loss prevention (DLP) company that caters to government and military entities. "The attackers compromised the DLP company's internal update servers to deliver malware inside the software developer's network, and trojanized installers of legitimate tools used by the company, which
Scientists Create the Most Complex Map Yet of an Insect Brain's 'Wiring' SoylentNews
It'll allow researchers to develop a 'a mechanistic understanding of how the brain works':
Researchers understand the structure of brains and have mapped them out in some detail, but they still don't know exactly how they process data for that, a detailed "circuit map" of the brain is needed.
Now, scientists have created just such a map for the most advanced creature yet: a fruit fly larva. Called a connectome, it diagrams the insect's 3016 neurons and 548,000 synapses, Neuroscience News has reported. The map will help researchers study better understand how the brains of both insects and animals control behavior, learning, body functions and more. The work may even inspired improved AI networks.
"Up until this point, we've not seen the structure of any brain except of the roundworm C. elegans, the tadpole of a low chordate, and the larva of a marine annelid, all of which have several hundred neurons," said professor Marta Zlatic from the MRC Laboratory of Molecular Biology. "This means neuroscience has been mostly operating without circuit maps. Without knowing the structure of a brain, we're guessing on the way computations are implemented. But now, we can start gaining a mechanistic understanding of how the brain works."
[...] As a next step, the team will investigate the structures used for behavioural functions like learning and decision making, and examine connectome activity while the insect does specific activities. And while a fruit fly larva is a simple insect, the researchers expect to see similar patterns in other animals. "In the same way that genes are conserved across the animal kingdom, I think that the basic circuit motifs that implement these fundamental behaviours will also be conserved," said Zlatic.
Read more of this story at SoylentNews.
20:22
Google AI just announced the PaLM API! Lifeboat News: The Blog
It will be released with a new tool called MakerSuite, which lets you prototype ideas, do prompt engineering, synthetic data generation and custom-model tuning. Waitlist available soon.
20:22
Now Microsoft has a new AI model Lifeboat News: The Blog
Microsofts Kosmos-1 can take image and audio prompts, paving the way for the next stage beyond ChatGPTs text prompts.
Microsoft has unveiled Kosmos-1, which it describes as a multimodal large language model (MLLM) that can not only respond to language prompts but also visual cues, which can be used for an array of tasks, including image captioning, visual question answering, and more.
OpenAIs ChatGPT has helped popularize the concept of LLMs, such as the GPT (Generative Pre-trained Transformer) model, and the possibility of transforming a text prompt or input into an output.
20:22
Links 15/03/2023: DietPi 8.15 and digiKam 7.10.0 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Monopolies
-
GNU/Linux
-
Audiocasts/Shows
-
Late Night Linux Episode 220
Flathubs grand plans spark a debate the merits of modern packaging, we feel old 20 years on from the SCO lawsuit, great news for un-Googled Android users, a lengthy quest to stream DRM-restricted media on Arm Macs, KDE Korner, and more. News Flathub in 2023 The SCO lawsuit, 20 years later NewF-Droid repository format
-
WordPress ...
-
-
20:21
Operation 404: 11 Arrests, Hundreds of Pirate Sites, Apps & Domains Blocked TorrentFreak
 Brazils crackdown against pirate sites, IPTV services,
infringing apps, and other mechanisms delivering illegal content to
the masses, continues to press ahead.
Brazils crackdown against pirate sites, IPTV services,
infringing apps, and other mechanisms delivering illegal content to
the masses, continues to press ahead.
In the wake of similar operations in previous years, including action reported in August 2022, a new phase of Brazils Operation 404 anti-piracy initiative was announced on Tuesday.
Operation 404.5 Phase 5
The launch of the 5th phase of Operation 404 is described by Brazils Ministry of Justice and Public Security (MJSP) as an international mobilization coordinated by the MJSP, through the National Secretariat for Public Security (Senasp), with support from police in eight states.
The objective is the removal of audio and video content, such as games and music, blocking and suspension of illegal streaming websites and applications, de-indexing of content in search engines and removal of profiles and pages on social networks, an MJSP announcement reads.
In this 5th phase, eleven people were arrested: four in So Paulo, two in Paran, one in Bahia and four in Minas Gerais, the government ministry reports.
Search and seizure warrants to locate computer equipment were executed in the states of Pernambuco, So Paulo, Paran, Minas Gerais, Rio Grande do Sul, Bahia, Cear and Rio de Janeiro.
199 illegal streaming and gaming sites and 63 music apps were also removed, in addition to blocking 128 domains, the ministry says.
A total of six messaging app channels with more than 4,000 subscribers were also blocked, reportedly for distributing music that had not been officially released.
International Cooperation
The local operation received significant international support. Authorities say they collaborated with the UKs Police Intellectual Property Crime Unit and the British Embassy, Peruvian intellectual property protection agency INDECOPI, MPA Latin American, anti-piracy group Alianza, and US-based videogame industry group Entertainment Software Alliance (ESA).
TorrentFreak obtained what appears to be a notice directed toward visitors to seized sites and domains. In addition to the groups listed above, it reveals the participation of the UKs Intellectual Property Office, the Alliance for Creativity and Entertainment, Brazil-based music industry group APDIF, and global music industry group IFPI.
20:14
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Dave Horsfall on Mar 15
I hate tossing out functionality; would you not make it a privilegedoperation instead?
-- Dave
20:10
CVE-2023-25695: Information disclosure in Apache Airflow Open Source Security
Posted by Jarek Potiuk on Mar 15
Severity: lowDescription:
Generation of Error Message Containing Sensitive Information vulnerability in Apache Software Foundation Apache
Airflow.This issue affects Apache Airflow: before 2.5.2.
Credit:
kuteminh11 (finder)
References:
https://github.com/apache/airflow/pull/29501
https://airflow.apache.org/
https://www.cve.org/CVERecord?id=CVE-2023-25695
19:46
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Fabian Keil on Mar 15
Shawn Webb <shawn.webb () hardenedbsd org> wrote on 2023-03-14 at 16:57:25:In ElectroBSD I removed TIOCSTI support in 2017 [0] and haven't
noticed any problems.
According to the commit message "TIOCSTI is still used in tcsh,
but as tcsh isn't compiled on ElectroBSD we don't care".
I should probably do the same.
Fabian
[0]:
<...
19:40
Key aerospace player Safran Group leaks sensitive data Security Affairs
Top aviation company Safran Group left itself vulnerable to cyberattacks, likely for well over a year, underlining how vulnerable big aviation firms are to threat actors, according to research by Cybernews.
Original post at https://cybernews.com/security/key-aerospace-player-leaks-sensitive-data/
The Cybernews research team recently discovered that the French-based multinational aviation company, the eighth largest aerospace supplier worldwide, was leaking sensitive data due to a misconfiguration of its systems. The vulnerability left the company at risk from cyberattacks over an extended period of time.
According to its own estimates, Safran Group s revenue for 2022 was above 19 billion. It collaborates with Airbus, the second-largest aerospace company globally after Boeing, to manufacture aerospace equipment.
The Safran Group is also involved in developing cutting-edge technologies beyond aviation, such as modules currently in use in the James Webb Telescope, the worlds largest optical telescope in space. Also, the company manufactures surface-to-air defense systems and missiles.
Cybernews reached out to Safran Group regarding the leak researchers found, and at the time of writing, the misconfiguration has been fixed.
The discovery
Researchers found a publicly available environment file used by the beta deployment of the open-source video-calling app Jitsi Meet. The Cybernews team estimates that the file stayed publicly available for around a year-and-a-half, leaving Safran Group vulnerable to potential attacks throughout that time.
The leaked sensitive information included the Laravel app key, JSON Web Token (JWT) key, MySQL credentials, and Simple Mail Transfer Protocol (SMTP) credentials for the no-reply email.
The Cybernews researchers highlight that the exposure of these keys and credentials could have made it relatively easy for attackers to gain access to the websites backend, employee computers, and other servers.
The Laravel app key is a token that helps to keep user browser cookies safe. If threat actors know this token, they can use it to decrypt cookies, which might contain session IDs. Knowing them, a threat actor could be able to hijack the session and therefore the account.
The leak also included the JWT secret key, another type of token, which is usually used for authentication. These tokens can be both for a user, and for an admin. If attackers had access to this key, they could create an admin account and have privileged access to a website.
The JWT secret key is used to generate and verify...
19:04
Ken Thompson, Who Co-created UNIX, is Now Moving to Debian GNU/Linux (Raspbian) Techrights
New talk: Ken Thompson Closing Keynote SCaLE 20x Invidious
Video download link | md5sum
37094b98ccf1f1e690ddd4f2739085b5
The Person Who Created UNIX Has Abandoned It and Is Now Moving
to Debian GNU/Linux (Raspbian)
Summary: Ken Thompson has shared incredible news; hes moving to GNU/Linux (transcript of the excerpt above can be found below)
[00:00] Audience member: ok, Ken. Whats your operating system of choice, today?
Ken Thompson: I have for most of my life, because I was sort of born into it run Apple. Right now, recently, meaning within the last five years Ive become more and more and more depressed and
[laughter from audience]
what Apple is doing to something which should allow you to work
[00:30] is just atrocious but they are taking space and time to do it so its ok. And I have come within the last month or two to say even though Ive invested a zillion years in Apple, Im throwing it away and Im going to Linux, Raspbian in particular.
[applause and cheers from audience]
Ken Thompson: Anyway, Im half transitioned now.
19:00
A Smart Home That CAN Do It All Hackaday

In an ideal smart home, the explosion of cheap WiFi and Bluetooth chips has allowed hundreds of small wireless devices to control the switches, lights, and everything else required for a smart home at a relatively low price. But what if you dont want hundreds of internet-connected devices in your home polluting the wireless spectrum and allowing potential security holes into your network? If youre like [Lucas Teske], you might reach for something wired and use cheap and (currently) available Raspberry Pi Picos to create PicoHome.
The unique twist of PicoHome is that it uses a CAN bus for communication. One of [Lucas] goals was to make the boards easily swappable when hardware failed. This meant board-to-board communication and protocols like I2C were susceptible to noise (every time a relay triggered, the bus would lock up briefly). The CAN bus is designed to work in an electrically noisy environment.
There are two parts to the system: pico-relay and pico-input. The first connects to a 16 relay board and can control 16 different 24v relays. The second has 16 optoisolators to read from 12v-24v switches and various buttons throughout the house. These can be placed in a giant metal box in a central wiring location and not worry about it.
The...
18:52
IRC Proceedings: Tuesday, March 14, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-140323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-140323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-140323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-140323.gmi
Over HTTP:
|
... |
18:23
Morgan Stanley is testing an OpenAI-powered chatbot for its 16,000 financial advisors Lifeboat News: The Blog
The bank has been testing the artificial intelligence tool with 300 advisors and plans to roll it out widely in the coming months, according to Jeff McMillan, head of analytics, data and innovation at the firms wealth management division.
Morgan Stanleys move is one of the first announcements by a financial incumbent after the success of OpenAIs ChatGPT, which went viral late last year by generating human-sounding responses to questions. The bank is a juggernaut in wealth management with more than $4.2 trillion in client assets. The promise and perils of artificial intelligence have been written about for years, but seemingly only after ChatGPT did mainstream users understand the ramifications of the technology.
The idea behind the tool, which has been in development for the past year, is to help the banks 16,000 or so advisors tap the banks enormous repository of research and data, said McMillan.
18:22
Unlocking the Secrets of Deep Learning with Tensorleaps Explainability Platform Lifeboat News: The Blog
Deep Learning (DL) advances have cleared the way for intriguing new applications and are influencing the future of Artificial Intelligence (AI) technology. However, a typical concern for DL models is their explainability, as experts commonly agree that Neural Networks (NNs) function as black boxes. We do not precisely know what happens inside, but we know that the given input is somehow processed, and as a result, we obtain something as output. For this reason, DL models can often be difficult to understand or interpret. Understanding why a model makes certain predictions or how to improve it can be challenging.
This article will introduce and emphasize the importance of NN explainability, provide insights into how to achieve it, and suggest tools that could improve your DL models performance.
18:00
A return to our hunter-gatherer roots may benefit child development Terra Forming Terra

Oral pill cuts bad cholesterol by 60% in phase 2 clinical trial Terra Forming Terra

This is very promising and leads to direct changes in the cholesterol balance. So yes, i would take it on.
So far there are no surprises as well.
The Greatest Hero and Villain of Our Times Terra Forming Terra

Claims of Practical Room Temperature Superconductor Terra Forming Terra
17:37
Are Embedded Systems Overengineered? SoylentNews
Hackaday has a story about a simple non-scientific calculator that packs an Alwinner A50 tablet SoC and the Android operating system:
As shipped they lack the Android launcher, so they aren't designed to run much more than the calculator app. Of course that won't stop somebody who knows their way around Google's mobile operating system for very long - at the end of the review, there's some shots of the gadget running Minecraft and playing streaming video.
But it does beg the question as to why such a product was put into production when the same task could have been performed using very cheap microcontroller. Further, having done so they make it a non-scientific machine, not even bestowing it with anything that could possibly justify the hardware.
Embedded has more generic related post about overengineering in embedded systems:
Embedded systems have traditionally been resource-constrained devices that have a specific purpose. They are not general computing devices but often some type of controller, sensor node, etc. As a result, embedded systems developers often are forced to balance bill-of-material (BOM) costs with software features and needs, resulting in a system that does a specific purpose efficiently and economically.
Over the last few years, I've noticed many systems being built that seem to ignore this balance. For example, I've seen intelligent thermostats that could be built using an Arm Cortex-M4 with a clock speed of fewer than 100 MHz and several hundred kilobytes of memory. Instead, these systems are designed using multicore Arm Cortex-M7 (or even Cortex-A!) parts running at 600 MHz+ with several megabytes of memory! This leads me to ask, are embedded systems developers today overengineering their systems?
Read more of this story at SoylentNews.
16:42
Distribution Release: Qubes OS 4.1.2 DistroWatch.com: News
Qubes OS 4.1.2, the latest "patch" release of the project's security-oriented operating system for single-user desktop stable release of....
16:30
So, you want to deploy air-gapped Kubernetes, huh? Help Net Security
So, you want to deploy Kubernetes in an air-gapped environment, but after months of grueling work, youre still not up and running. Or maybe youre just embarking on the journey but have heard the horror stories of organizations trying to manage their Kubernetes deployment in air-gapped environments without success. Whether youre working in a mission-critical or life-critical environment, be it a hospital or the military, you likely have critical systems and sensitive data you want More
The post So, you want to deploy air-gapped Kubernetes, huh? appeared first on Help Net Security.
16:26
Microsoft Rolls Out Patches for 80 New Security Flaws Two Under Active Attack The Hacker News
Microsoft's Patch Tuesday update for March 2023 is rolling out with remediations for a set of 80 security flaws, two of which have come under active exploitation in the wild. Eight of the 80 bugs are rated Critical, 71 are rated Important, and one is rated Moderate in severity. The updates are in addition to 29 flaws the tech giant fixed in its Chromium-based Edge browser in recent weeks. The
16:24
Top 7 AI Examples In Healthcare The Medical Futurist Lifeboat News: The Blog

Artificial intelligence is no longer a futuristic idea. Its already here, and it has turned out to be a powerful, disruptive force in healthcare fueling some of the most innovative diagnostic tools of today.
Lets take a look at 7 examples where AI has started to transform healthcare!
16:22
The Secret to Learning Anything: Albert Einsteins Advice to His Son Lifeboat News: The Blog
That is the way to learn the most, that when you are doing something with such enjoyment that you dont notice that the time passes.
16:00
Exfiltration malware takes center stage in cybersecurity concerns Help Net Security
While massive public data breaches rightfully raise alarms, the spike in malware designed to exfiltrate data directly from devices and browsers is a key contributor to continued user exposure, according to SpyCloud. The 2023 report identified over 22 million unique devices infected by malware last year. Of the 721.5 million exposed credentials recovered by SpyCloud, roughly 50% came from botnets, tools commonly used to deploy highly accurate information-stealing malware. These infostealers enable cybercriminals to work More
The post Exfiltration malware takes center stage in cybersecurity concerns appeared first on Help Net Security.
16:00
A Pi Calculating Pi for Pi Day Hackaday

What is it about pi that we humans at least some of us find so endlessly fascinating? Maybe thats just it its endless, an eternal march of digits that tempts us with the thought that if we just calculate one more digit, something interesting will happen. Spoiler alert: it never does.
That doesnt stop people from trying, of course, especially when Pi Day rolls around on March 14 every day with apologies to the DD/MM set, of course. This year, [Cristiano Monteiro] commemorated the day with this Pi-based eternal pi calculator. The heart of the build is a Raspberry Pi Pico board, which does double duty thanks to its two cores. One core is devoted to running the pi calculation routine, while the other takes care of updating the seven-segment LED display with the last eight calculated digits. Since the calculation takes increasingly more time the farther into pi it gets, [Cristiano] thoughtfully included a 1-Hz heartbeat indicator, to assure users that the display isnt frozen; the video below shows how slow the display gets even just a few seconds after starting up, so its a welcome addition.
This is actually [Cristiano]s second go at a Pi Day pi calculator;...
15:31
Suspicions That Microsoft Has Begun Blocking Linux Developers From Russia (Updated) Techrights
Not unprecedented: People From Half a Dozen Countries May be Banned From Participating in the Linux Foundation Because Its Outsourcing Many Projects to Microsoft/GitHub
Summary: Microsofts GitHub, which is constantly shilled by the Linux Foundation, keeps censoring Free software while profiting from GPL violations; RMS turns 70 tomorrow and he would be wise to remind people to delete GitHub ASAP (he gives a talk the following day)
Updated: LWN has more: It would appear that the ipmitool repository has been locked, and its maintainer suspended, by GitHub. This Hacker News conversation delves into the reason; evidently the developer was employed by a sanctioned Russian company. Ipmitool remains available and will, presumably, find a new home eventually (see the comments, too)
15:30
Best practices for securing the software application supply chain Help Net Security
As server-side security advances, more attackers are exploiting vulnerabilities and launching malicious attacks through the less protected and seldom monitored client-side supply chain. Unfortunately, because of these attacks sophisticated and subtle nature, they can be hard to detect until its too late. In this Help Net Security video, Uri Dorot, Sr. Security Solutions Lead at Radware, discusses how without proper client-side protection, organizations are flying blind. Companies are exposing end users along with personally More
The post Best practices for securing the software application supply chain appeared first on Help Net Security.
15:00
Top 50 most impersonated brands by phishing URLs Help Net Security
Today, phishing is the fastest growing Internet crime, and a threat to both consumers and businesses. Finance, technology, and telecom brands were the most commonly impersonated industries, notably for the unprecedented access and financial benefit that bank accounts, email and social media, and phone companies can give attackers, according to Cloudflare. The challenge of phishing URLs By masquerading as a reputable source sometimes with an enticing request, other times with a severe consequence More
The post Top 50 most impersonated brands by phishing URLs appeared first on Help Net Security.
14:52
FISA Oversight Board Member Says Americans Need More Privacy Protections as Congress Debates Section SoylentNews
One of the NSA's most powerful spying tools is up for renewal at the end of the year. The problem with this power isn't necessarily the NSA. I mean, the NSA has its problems, but the issue here is the domestic surveillance performed by the FBI via this executive power something it shouldn't be doing but has almost always done.
The FBI is currently catching a lot of heat for its "backdoor" access to US persons' data and communications, something it has shown little interest in controlling or tracking. Abuse is a regular occurrence and this abuse finally received some high profile attention after Congressional Republicans got bent out of shape because some of their own people ended up under the FBI's backdoor Section 702 microscope.
[...] Section 702 allows the NSA to perform "upstream" collections of data and communications. It's foreign-facing but it also collects any communications between foreign targets and US persons. That's where the FBI steps in. It's only supposed to be able to access minimized data and communications, but these restrictions are often ignored by the agency.
[...] Specifically, the program needs constraints on the FBI's access and use of the data collected by the NSA. For years, the FBI has abused its access to perform backdoor searches of Americans' data. And for years, it has been unable to explain why it can't stop violating minimization procedures and what, if anything, this unexpected, "incidental" treasure trove contributes to its law enforcement work.
Read more of this story at SoylentNews.
14:45
Webinar: Tips from MSSPs to MSSPs starting a vCISO practice Help Net Security
There is a consensus among MSPs and MSSPs that vCISO services pose an excellent opportunity for a new revenue stream, but how do you successfully do that? Watch this panel discussion to hear from MSSP leaders who already sell vCISO services as they discuss why they have expanded into offering vCISO services and share expert tips and recommendations. Watch now to get first-hand tips on: What to consider when starting a vCISO practice Where to More
The post Webinar: Tips from MSSPs to MSSPs starting a vCISO practice appeared first on Help Net Security.
14:25
Concentric AIs DSPM solution detects sensitive or business critical content Help Net Security
Concentric AI announced a DSPM solution with support for optimized large language models delivering improved data security and protection. As a result, Concentric AIs Semantic Intelligence delivers semantic understanding of data and leverages context to offer precise accuracy in discovering sensitive data from intellectual property to financial data to business confidential information to PII/PCI/PHI, and more. According to Gartner, Foundation models (which are mostly large language models) are designed to replace task-specific modelsFoundation models represent More
The post Concentric AIs DSPM solution detects sensitive or business critical content appeared first on Help Net Security.
14:15
Motorola Solutions releases new Avigilon security suite to improve enterprise security Help Net Security
Motorola Solutions announced the new Avigilon physical security suite that provides secure video security and access control to organizations of all sizes around the world. The Avigilon security suite includes the cloud-native Avigilon Alta and on-premise Avigilon Unity solutions, each powered by advanced analytics and designed to provide an effortless user experience. Avigilon has been the capstone of Motorola Solutions Video Security & Access Control business, which has grown through strategic acquisitions over the past More
The post Motorola Solutions releases new Avigilon security suite to improve enterprise security appeared first on Help Net Security.
14:05
Tanium expands XEM platform with enhanced device and policy management Help Net Security
Tanium has released its new certificate manager and enhanced policy management capabilities, offering organizations convenient tool consolidation, cost and time savings, and more accurate reporting via Taniums XEM platform. Organizations today struggle to see and manage digital certificates; the average modern enterprise manages up to hundreds of thousands of certificates, often through manual means. When digital certificates are not managed properly, the resulting downtime can impact business operations and cause financial and reputational damage, with More
The post Tanium expands XEM platform with enhanced device and policy management appeared first on Help Net Security.
13:37
Links 14/03/2023: AMD Defects and GNOME 44 Release Candidate Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Kernel Space
-
Neowin New Linux kernel patches introduce workaround for system stuttering on AMD systems
Linux maintainers have pushed patches to Linux 6.1 and Linux 6...
-
-
13:06
Standard Life Making False Promises About Cracking Down on Pension Fraud and Embezzlement schestowitz.com
Video download link
| md5sum 6e89d71f88131559a0e06773ecfefd81
The Standard Cover-up
Creative Commons Attribution-No Derivative Works 4.0
Summary: Standard Life lied to me about investigating fraud committed in their name; to make matters worse, upon contacting them one week later (after they were supposed to get back to me) theyre still not escalating, not even getting in touch, and victims of embezzlement are running out of patience, having already lose their pensions
THE above video gives some background and plays back a conversation I had today with Standard Life. Its a continuation of the long video (and notes) from 2 days ago. I had the phone with me throughout the above recording and Standard Life simply failed to phone me. They had already failed to contact me a week ago as the manager promised. It certainly starts looking like a pattern.
This time I play the audio without hiding the names of those accountable. Readers/viewers can probably understand why we name them publicly after months of wasted efforts and hours on the phone. The short story is, Standard Life is failing to hold people accountable, knowing embezzlement affected a lot of people. Some time in the next few days we shall explain the significance of this and the ramifications. This passivity isnt acceptable.
13:00

Virtual Reality always seemed like a technology just out of reach, much like nuclear fusion, the flying car, or Linux on the desktop. It seems to be gaining steam in the last five years or so, though, with successful video games from a number of companies as well as plenty of other virtual reality adjacent technology that seems to be picking up steam as well like augmented reality. Another sign that this technology might be here to stay is this virtual reality headset made for mice.
These arent any ordinary pets out to take a pleasant jaunt through VR, though. These are lab mice from Cornell University that are helping to study various various aspects of neuroscience and behavior. The tiny headset is based on a Raspberry Pi and uses two small SPI-based displays with special lenses chosen and mounted specifically for a mouses field-of-view. The mouse will run on a Styrofoam ball that is attached to a separate set of sensors that can measure aspects of its motion.
While the project is still a work in progress, its an interesting solution to what would otherwise be a difficult problem to solve when studying mice in a laboratory setting. The team responsible for this effort has made their project available to the public as well and is...
12:55
How Poorly Standard Life Has Dealt With Pension Fraud Techrights
Video download link
| md5sum 6e89d71f88131559a0e06773ecfefd81
The Standard Cover-up
Creative Commons Attribution-No Derivative Works 4.0
Summary: Standard Life lied to me about investigating fraud committed in their name; to make matters worse, upon contacting them one week later (after they were supposed to get back to me) theyre still not escalating, not even getting in touch, and victims of embezzlement are running out of patience, having already lose their pensions
THE above video gives some background and plays back a conversation I had today with Standard Life. Its a continuation of the long video (and notes) from 2 days ago. I had the phone with me throughout the above recording and Standard Life simply failed to phone me. They had already failed to contact me a week ago as the manager promised. It certainly starts looking like a pattern.
This time I play the audio without hiding the names of those accountable. Readers/viewers can probably understand why we name them publicly after months of wasted efforts and hours on the phone. The short story is, Standard Life is failing to hold people accountable, knowing embezzlement affected a lot of people. Some time in the next few days we shall explain the significance of this and the ramifications. This passivity isnt acceptable.
12:33
The Linux Foundation Announces Conference Schedule for Open Source Summit North America 2023 Linux.com

Read the original post at: Read More
The post The Linux Foundation Announces Conference Schedule for Open Source Summit North America 2023 appeared first on Linux.com.
12:25
Two U.S. Men Charged in 2022 Hacking of DEA Portal Krebs on Security
Two U.S. men have been charged with hacking into a U.S. Drug Enforcement Agency (DEA) online portal that taps into 16 different federal law enforcement databases. Both are alleged to be part of a larger criminal organization that specializes in using fake emergency data requests from compromised police and government email accounts to publicly threaten and extort their victims.

Prosecutors for the Eastern District of New York today unsealed criminal complaints against Sagar Steven Singh a.k.a Weep a 19-year-old from Pawtucket, Rhode Island; and Nicholas Ceraolo, 25, of Queens, NY, who allegedly went by the handles Convict and Ominus.
The Justice Department says Singh and Ceraolo belong to a group of cybercriminals known to its members as ViLE, who specialize in obtaining personal information about third-party victims, which they then use to harass, threaten or extort the victims, a practice known as doxing.
ViLE is collaborative, and the members routinely share tactics and illicitly obtained information with each other, prosecutors charged.
The government alleges the defendants and other members of ViLE use various methods to obtain victims personal information, including:
-tricking customer service employees;
-submitting fraudulent legal process to social media companies to
elicit users registration information;
-co-opting and corrupting corporate insiders;
-searching public and private online databases;
-accessing a nonpublic United States government database without
authorization
-unlawfully using official email accounts belonging to other
countries.
The complaint says once they obtained a victims information, Singh and Ceraolo would post the information in an online forum. The government refers to this community only as Forum-1, saying that it is administered by the leader of ViLE (referenced in the complaint as CC-1).
Victims are extorted into paying CC-1 to have their information removed from Forum-1, prosecutors allege. Singh also uses the threat of revealing personal information to extort victims into giving him access to their social media accounts, which Singh then resells.
Sources tell KrebsOnSecurity in...
12:10
How a Small Business in Arizona is Helping Decarbonize Concrete SoylentNews
Block-Lite is a small concrete manufacturer in an industrial corridor of Flagstaff, Arizona. The third-generation family business makes bricks and other masonry materials for retaining walls, driveways, and landscaping projects. The company was already a local leader in sustainability in 2020, it became the first manufacturer in Flagstaff to power its operations with on-site solar panels. But now it's doing something much more ambitious.
On Tuesday, Block-Lite announced a pioneering collaboration with climate tech startups Aircapture and CarbonBuilt to suck carbon dioxide from the atmosphere and stash it in concrete blocks. The companies estimate the project will reduce the carbon footprint of Block-Lite's products by 70 percent, creating a model they hope could reshape the industry.
[...] CarbonBuilt has developed a solution that addresses the issue in two distinct ways. First, the company found a proprietary way to replace cement with a mix of inexpensive, locally-sourced industrial waste materials. CEO Rahul Shendure told Grist they include common byproducts of coal plants, steelmaking, and chemical production that would, for the most part, otherwise be destined for landfills. The company's second feat is the way its equipment hardens that slurry into concrete blocks by curing it with carbon dioxide. That's where Aircapture comes in. The company will build one of its machines which extract carbon dioxide from the ambient air directly on Block-Lite's site.
[...] Block-Lite did not respond to Grist's inquiry, but in a press release, the company suggested that the new concrete products would be no costlier than its current offerings. "All too often sustainable building materials require a trade off between cost and performance, but what is unique about this project is that there's no 'green premium.'" Block-Lite said. "We're going to be able to produce on-spec, ultra-low carbon blocks at price parity with traditional blocks which should speed adoption and impact."
Read more of this story at SoylentNews.
11:33
Beyond Price Point: Analyzing Differences in Cloud Storage Options HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
Do you really get more value from a paid cloud storage service, or are free clouds enough? Heres
This is a post from HackRead.com Read the original post: Beyond Price Point: Analyzing Differences in Cloud Storage Options
11:22
NEW 'Off The Wall' ONLINE 2600 - 2600: The Hacker Quarterly
NEW 'Off The Wall' ONLINE
Posted 15 Mar, 2023 0:22:51 UTC
The new edition of Off The Wall from 03/14/2023 has been archived and is now available online.
11:00
HPR3813: The postmarketOS Podcast Hacker Public Radio
postmarketOS Podcast Website: https://cast.postmarketos.org/ Feed: https://cast.postmarketos.org/feed.rss Copyright: Creative Commons Attribution-ShareAlike 4.0 International (CC BY-SA 4.0) License https://cast.postmarketos.org/episode/28-FOSDEM-2023-special/ #28 FOSDEM 2023 Special Between the Saturday closing of FOSDEM 2023 and going to a restaurant, we managed to squeeze around a table outside the cafeteria to record the very first ever in-person postmarketOS podcast episode! Fresh in the moment we share our experiences from the FOSS on mobile devroom, meeting great people at the Linux on Mobile stand (and everywhere else at FOSDEM/in Brussels) and random other cool things that were going down. Featuring @spaetz (sampled in the intro), @ollieparanoid, @linmob, @craftyguy, @MartijnBraam, @calebccff, @PureTryOut, @z3ntu (in order of appearance). Photos: @calebccff: "recorded the first in person @postmarketOS podcast episode LIVE from #FOSDEM !" @craftyguy: "#postmarketOS core team... Assemble!" @awai: "The beauty and diversity of the #LinuxOnMobile bazaar!" @z3ntu: "The Linux on Mobile stand at #FOSDEM is pretty packed!" @linmob: "#FOSDEM was really awesome, it only went by too quickly!" @mntmn: "this was ~intense~! thanks to everyone who was interested in MNT Pocket Reform" Video recordings of the talks: Where do we go from here? (Audio fixup) Matrix room: #fossmo-wg:matrix.org FOSS on mobile devices devroom (as of writing, most talks have already been uploaded) PinePhone and Lima / Mesa: We're aware that mesa#8198 is still causing problems for people on the PinePhone. Big thanks to @enues from mesa who was talking to us at the stand and is now looking into it! We also have issue pmaports#805 about screen freezes. If you are affected by this and would like to help out, firing up a profiler and making/contributing to detailed, useful bugreports upstream at mesa is appreciated. @spaetz from Mobian did a great job at moderating the devroom! (Correction: Ollie said from Maemo instead of Mobian in the recording.) Editing by: @ollieparanoid, Music by: The Passion HiFi
Automatically Assessing Method Names It Will Never Work in Theory
Amidst the excitement about using large language models to
generate code, it's easy to lose sight of all the other ways that
the things programmers have built can be used to make programming
better. One example is this work, which looks at whether we can use
natural language processing to assess the quality of method names.
The authors collected ten rules (shown in the table below) and used
them to score names from like setIconItemStatus() from
several software projects. (That name gets a score of 10 out of 10,
by the way.) The authors recognize that the rules are not fully
objectivefor example, they split on whether the first letter after
an acronym should be capitalized or notand automatic tools
sometimes struggle because of grammatical ambiguities (e.g., words
that can be both nouns and verbs), but their work points the way
toward a new generation of code checking tools.
| # | Standard Name | Rules |
|---|---|---|
| 1 | Naming Style | A single standard naming style is used. |
| 2 | Grammatical Structure | If there are multiple words, they form a grammatically correct sentence structure. |
| 3 | Verb Phrase | It is a verb or a verb phrase. |
| 4 | Dictionary Terms | Only natural language dictionary words and/or familiar/domain-relevant terms are used. |
| 5 | Full Words | Full words are used rather than a single letter. |
| 6 | Idioms and Slang | It does not contain personal expressions, idioms, or slang. |
| 7 | Abbreviations | It only contains known or standard abbreviated terms. All abbreviations are well known or part of the problem domain. |
| 8 | Acronyms | It only contains standard acronyms. All acronyms are well known or part of the problem domain. |
| 9 | Prefix/Suffix | It does not contain a prefix/suffix that is a term from the system. This standard does not apply to languages such as C that do not have namespaces. |
| 10 | Length | Maximum number of words is no greater than 7. |
Reem S. Alsuhaibani, Christian D. Newman, Michael J. Decker, Michael L. Collard, and Jonathan I. Maletic. An approach to automatically assess method names. In Proceedings of the 30th IEEE/ACM International Conference on Program Comprehension, May 2022. doi:10.1145/3524610.3527780.
An approach is presented to automatically assess the quality of method names by providing a score and feedback. The approach implements ten method naming standards to evaluate the names. The naming standards are taken from work that validated the standards via a large survey of software professionals. Natural language...
10:33
LockBit Ransomware gang claims to have stolen SpaceX confidential data from Maximum Industries Security Affairs
The LockBit ransomware group claims to have stolen confidential data belonging to SpaceX from the systems of Maximum Industries.
The LockBit ransomware gang claims to have stolen confidential data of SpaceX after they hacked the systems of production company Maximum Industries. Maximum Industries is a full-service, piece-part production, and contract manufacturing facility.
The ransomware gang hacked the systems of the production firm, which also provides its services to SpaceX, and stole its data, including files of the American spacecraft manufacturer and a satellite communications corporation.
The group claims to have stolen roughly 3,000 drawings certified by space-x engineers.
I would say we were lucky if SPACE-X contractors were more talkative. But I think this material will find its buyer as soon as possible. reads the message published by Lockbit operators on their Tor Leak site.
Elon Musk we will help you sell your drawings to other manufacturers build the ship faster and fly away. and now about the numbers: about 3,000 drawings certified by space-x engineers
The gang plans to launch an auction in a week.
SpaceX has yet to comment on Lockbits claims, however, it is important to highlight that SpaceX was not hacked.
The LockBit ransomware gang has been active since 2019 and it is currently one of the most active ransomware operations.
Since the beginning of 2023, LockBit3 added more than 600 victims to its leak site. Below is the list of victims added in the last couple of days:
10:05
LockBit Ransomware Claims Data Breach at SpaceX Contractor HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
The cybercrime group has given a deadline of March 20th, 2023 for their demands, which as expected, is a ransom.
This is a post from HackRead.com Read the original post: LockBit Ransomware Claims Data Breach at SpaceX Contractor
10:00
Solar Powered Split Wireless Mechanically Keyboard Hackaday

When thinking about a perfect keyboard, some of us have a veritable laundry list: split, hot-swapping, wireless, 3d printed, encoders, and a custom layout. The Aloidia keyboard by [Nguyen Vincent] has all that and more.
One of the first things to notice is a row of solar panels on the top, which trickle charge the keyboard. The keyboard uses 65uA when 30uA when in a deep sleep. With the solar panels providing anywhere between 600-1200uAh, the battery should last a year and a half under even harsh conditions. The encoders were specially chosen to reduce pull-up power consumption. Given the focus on power and the lack of wires between the halves, you might wonder how the connection to the computer is handled. Does one-half handle the connection and use more power? The answer is that both talk to a dongle based around an nRF52840. This lets the keyboard halves idle most of the time and enables the dongle to handle the expensive communications to the host PC.
Instead of an e-paper screen in the top left, [Nguyen] placed a Sharp memory display. The 3D-printed case is stunning, with n...
09:43
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Shawn Webb on Mar 14
With commit c7d6d4bb4874720d9dab1625df62c2ea6eeb9df5[0], I've added atoggle in HardenedBSD to disable TIOCSTI. The toggle is set to
prohibit TIOCSTI by default. Now attempts to use TIOCSTI will be met
with EPERM.
I've verified the toggle in a real-world scenario with the doas issue
PoC found at [1].
[0]:
https://git.hardenedbsd.org/hardenedbsd/HardenedBSD/-/commit/c7d6d4bb4874720d9dab1625df62c2ea6eeb9df5
[1]:...
09:20
Russia is Powering Up a Giant Laser to Test its Nukes SoylentNews
To check that atomic weapons work, scientists run simulations of explosions using high-energy lasersand Russia is building the strongest one of all:
In town of Sarov, roughly 350 kilometers east of Moscow, scientists are busy working on a project to help keep Russia's nuclear weapons operational long into the future. Inside a huge facility, 10 storeys high and covering the area of two football fields, they are building what's officially known as UFL-2Mor, as the Russian media has dubbed it, the "Tsar Laser." If completed, it will be the highest-energy laser in the world.
High-energy lasers can concentrate energy on groups of atoms, increasing temperature and pressure to start nuclear reactions. Scientists can use them to simulate what happens when a nuclear warhead detonates. By creating explosions in small samples of materialeither research samples or tiny amounts from existing nuclear weaponsscientists can then calculate how a full-blown bomb is likely to perform. With an old warhead, they can check that it still works as intended. Laser experiments allow testing without letting a nuke off. "It's a substantial investment by the Russians in their nuclear weapons," says Jeffrey Lewis, a nuclear non-proliferation researcher at the Middlebury Institute of International Studies in California.
Until now, Russia has been unique among the best-established nuclear powers in not having a high-energy laser. The United States has its National Ignition Facility (NIF), currently the world's most energetic laser system. Its 192 separate beams combine to deliver 1.8 megajoules of energy. Looked at in one way, a megajoule is not an enormous amountit's equivalent to 240 food calories, similar to a light meal. But concentrating this energy onto a tiny area can create very high temperatures and pressures. France meanwhile has its Laser Mgajoule, with 80 beams currently delivering 350 kilojoules, though it aims to have 176 beams delivering 1.3 megajoules by 2026. The UK's Orion laser produces 5 kilojoules of energy; China's SG-III laser, 180 kilojoules.
If completed the Tsar Laser will surpass them all. Like the NIF, it's due to have 192 beams, but with a higher combined output of 2.8 megajoules. Currently, though, only its first stage has launched. At a Russian Academy of Sciences meeting in December 2022, an official revealed that the laser boasts 64 beams in its current state. Their total output is 128 kilojoules, 6 pe...
08:47
Digital Rights Updates with EFFector 35.3 Deeplinks
New month, new digital rights updates! Version 35, issue 3
of our EFFector newsletter is out now. Catch up on the latest EFF
news by reading our
covers our new Coded Resistance comic as well as our co-sponsorship
of new California legislation to protect communities
from dragnet-style digital surveillance, and much
more.
EFFECTOR 35.3 -
International Women's Day is Every Day
Make sure you never miss an issue by signing up by email to receive EFFector as soon as it's posted! Since 1990 EFF has published EFFector to help keep readers on the bleeding edge of their digital rights. We know that the intersection of technology, civil liberties, human rights, and the law can be complicated, so EFFector is a great way to stay on top of things. The newsletter is chock full of links to updates, announcements, blog posts, and other stories to help keep readersand listenersup to date on the movement to protect online privacy and free expression.
Thank you to the supporters around the world who make our work possible! If you're not a member yet, join EFF today to help us fight for a brighter digital future.
08:46
Microsoft Patch Tuesday fix Outlook zero-day actively exploited Security Affairs
Microsoft Patch Tuesday updates for March 2023 addressed 74 vulnerabilities, including a Windows zero-day exploited in ransomware attacks.
Microsoft Patch Tuesday security updates for March 2023 addressed 74 new vulnerabilities in Microsoft Windows and Windows Components; Office and Office Components; Edge (Chromium-based); Microsoft Dynamics; Visual Studio; and Azure.
Six of the fixed issues are rated Critical and 67 are rated Important, while only one is rated Moderate in severity.
Two of the vulnerabilities addressed by the IT giant, respectively tracked as CVE-2023-23397 and CVE-2023-24880, are actively exploited in the wild.
The CVE-2023-23397 flaw is a Microsoft Outlook spoofing vulnerability that can lead to an authentication bypass.
A remote, unauthenticated attacker can exploit the flaw to access a users Net-NTLMv2 hash by sending a specially crafted e-mail to an affected system.
An attacker who successfully exploited this vulnerability could access a users Net-NTLMv2 hash which could be used as a basis of an NTLM Relay attack against another service to authenticate as the user. reads the advisory published by Microsoft.
The attacker could exploit this vulnerability by sending a specially crafted email which triggers automatically when it is retrieved and processed by the Outlook client. This could lead to exploitation BEFORE the email is viewed in the Preview Pane. External attackers could send specially crafted emails that will cause a connection from the victim to an external UNC location of attackers control. This will leak the Net-NTLMv2 hash of the victim to the attacker who can then relay this to another service and authenticate as the victim.
The vulnerability was reported by the CERT-UA and the Microsoft Incident Response, Microsoft Threat Intelligence (MSTI), suggesting that is has been exploited by a nation-state actor.
The second flaw actively exploited in the wild is a Windows SmartScreen security feature bypass vulnerability tracked as CVE-2023-24880.
An attacker can exploit the vulnerability to bypass Mark of the Web (MOTW) defenses by using specially crafted files. Microsoft Office SmartScreen and Protected View defense features...
07:57
Spinrilla Wants to Ban the Terms Piracy and Theft at RIAA Trial TorrentFreak
 Operating a mixtape site is not without risk. By definition,
mixes include multiple sound recordings that are often protected by
copyright.
Operating a mixtape site is not without risk. By definition,
mixes include multiple sound recordings that are often protected by
copyright.
Popular hip-hop mixtape site and app Spinrilla, which has millions of users, is well aware of these risks. In 2017, the company was sued by several record labels, backed by the RIAA, which accused the company of massive copyright infringement.
Spinrilla specializes in ripping off music creators by offering thousands of unlicensed sound recordings for free, the RIAA commented at the time.
Spinrilla Fought Piracy Accusations
The hip-hop site countered the allegations by pointing out that it had installed an RIAA-approved anti-piracy filter and actively worked with major record labels to promote their tracks. In addition, Spinrilla stressed that the DMCAs safe harbor provision protects the company.
As the case progressed, both parties filed motions for summary judgment. The music companies requested rulings to establish, before trial, that Spinrilla is liable for direct copyright infringement and that the DMCA safe harbor doesnt apply.
Spinrilla countered with cross-motions, filed under seal, in which they argued the opposite. Judge Amy Totenberg eventually sided with the record labels in 2020, concluding that the mixtape site is indeed liable.
Millions in Potential Damages
In her ruling, Judge Totenberg concluded that 4,082 copyrighted sound recordings were streamed, at least once, through Sprinrillas website or app.
The scale of the damages will be decided at trial and after several delays, the jury is currently set to gather in a few weeks. With thousands of copyrights at stake, damages could potentially exceed $600 million if the jury finds that the infringement was willful.
With the stakes this high, both sides will do their best to present their most favorable arguments. That also means efforts to prevent witnesses, evidence, and even specific words being presented to the court.
These requests come in the form of motions in limine where the parties ask the court to keep certain information from the jury. Several of these motions were submitted to court over the past few days.
Piracy and Theft
According to recent filings, Spinrilla is particularly concerned over potentia...
07:50
Intel Adds New Option To Help In Profiling Their Open-Source Vulkan Driver Phoronix
A two year old merge request finally made it to mainline today for Mesa 23.1 to enhance in profiling the open-source Mesa Vulkan drivers...
07:21
Re: Re: sox: patches for old vulnerabilities Open Source Security
Posted by Steffen Nurpmeso on Mar 14
Hello Helmut, list, and special greetings to the happy moderator,Steffen Nurpmeso wrote in
<20230314191132.qDz3u%steffen () sdaoden eu>:
...
|Helmut Grohne wrote in
| <20230314110138.GA1192267 () subdivi de>:
||On Fri, Feb 03, 2023 at 09:44:47PM +0100, Helmut Grohne wrote:
||> * CVE-2021-33844
||
||The original fix for this issue would cause a regression. After applying
||it, sox would be unable to decode WAV GSM files....
07:00
Pocket-Sized Thermal Imager Hackaday

Just as the gold standard for multimeters and other instrumentation likely comes in a yellow package of some sort, there is a similar household name for thermal imaging. But, if theyre known for anything other than the highest quality thermal cameras, its excessively high price. There are other options around but if you want to make sure that the finished product has some sort of quality control you might want to consider building your own thermal imaging device like [Ruslan] has done here.
The pocket-sized thermal camera is built around a MLX90640 sensor from Melexis which can be obtained on its own, but can also be paired with an STM32F446 board with a USB connection in order to easily connect it to a computer. For that, [Ruslan] paired it with an ESP32 board with a companion screen, so that the entire package could be assembled together with a battery and still maintain its sleek shape. The data coming from the thermal imagining sensor does need some post-processing in order to display useful images, but this is well within the capabilities of the STM32 and ESP32.
With an operating time on battery of over eight hours and a weight under 100 grams, this could be just the thing for someone looking for a thermal camera who doesnt...
07:00
Open 3D Engine Sees Momentum Across Robotics Industry Linux.com

Read the original post at: Read More
The post Open 3D Engine Sees Momentum Across Robotics Industry appeared first on Linux.com.
06:46
Remuneration and Pensions at the EPO Reduced (Relative to Inflation), Guaranteeing a Decline in Quality of Work Techrights

Summary: Purchasing power is rapidly decreased and the EPO sitting on a pile of cash illegally obtained refuses to catch up; staff is concerned that life will become a lot harder and, as noted earlier today, this means worse quality of work, not just worse quality of life
Weve only just published the latest letter about the Bringing Teams Together initiative/scheme/scam. Staff of the EPO is under an attack fiercer than ever before (maybe representatives of staff were subjected to a lot more abuse by Benot Battistelli, but thats not all the staff).
Antnio Campinos, who prides himself and brags about his socialist dad, is a crooked corporate shill that is antisocial and to quote himself is just the f*cking president (around a year ago he used the f word repeatedly, acting no better than Vladimir Putin because his relationship with Belarus had been exposed).
Transparency helps because nothing scares vampires more than daylight.This post shares some of the sentiments expressed by EPO insiders. Some days ago there was a call for action, focusing on salary and pension aspects in isolation. To quote:
Safeguard your rights against the adjustment of salaries and pensions in 2023
Dear SUEPO members,
Dear colleagues,The new salary adjustment procedure has caused a noticeable adjustment of salaries and pensions in 2023. However, given the significant cuts and salary freezes in previous years, this should not be overstated. Staff and pensioners will remain at a disadvantage.
It is unclear how the adjustments for 2023 were calculated. It appears that the sustainability clause and the periodical settlement of the new procedure were not applied correctly to the detriment of staff and pensioners. In particular, it is not comprehensible how the balances of the redistribution pool were used and why/how the Office could reach the conclusion that the pool would be implicitly exhausted.
Since the adop...
06:38
Re: Re: sox: patches for old vulnerabilities Open Source Security
Posted by Steffen Nurpmeso on Mar 14
Hello and greetings.Helmut Grohne wrote in
<20230314110138.GA1192267 () subdivi de>:
|On Fri, Feb 03, 2023 at 09:44:47PM +0100, Helmut Grohne wrote:
|> * CVE-2021-33844
|
|The original fix for this issue would cause a regression. After applying
|it, sox would be unable to decode WAV GSM files. This has been reported
...
|I see that most distributions (e.g. RedHat, SUSE, Gentoo, etc.) have not
|picked up the faulty patch....
06:34
Scientists Produce Healthy Mice Using Exclusively Male Cells SoylentNews
Resulting in the birth of several mice that were produced without mothers:
Same-sex reproduction has historically required donor cells, as is the case with egg implantation and some instances of in-vitro fertilization (IVF). Thanks to genetic engineering, however, this might not always be the case. Scientists in Japan have successfully created eggs using male cells, resulting in the birth of several mice that were produced without mothers.
Renowned Kyushu University stem cell researcher Katshuhiko Hayashi presented his team's achievement this week at the Third International Summit on Human Genome Editing in London. Hayashi had led his colleagues through "reprogramming" a male mouse's skin cells into induced pluripotent stem (iPS) cells, or former non-reproductive cells that can be engineered into various cell forms. Because male cells contain the XY chromosome combination, Hayashi had to remove the Y chromosome and replace it with an X chromosome from another cell. (Hayashi's team attempted to devise a way to duplicate the first cell's X chromosome but was unsuccessful, resulting in the need to pull from a donor.)
Hayashi implanted the makeshift eggs inside a mouse ovary organoid, a ball of tissues that function similarly to a natural ovary. After fertilizing the eggs with sperm, his team implanted the resulting 600 embryos into surrogate mice. Seven of these embryos became mouse pups, which grew into adults with normal lifespans and successful mating routines.
Should Hayashi and his colleagues successfully produce eggs in the lab, it could pave the way for novel infertility treatments and for same-sex procreation that incorporates both partners' genes.
Read more of this story at SoylentNews.
06:20
The EPO Treats Its Own Staff Like Trash and Quality/Legitimacy of the EPOs Work is, Expectedly, Reduced to Trash Techrights
Video
download link | md5sum
573d697aa3946018dd94eb0b44d98c01
Cannot Even Get a Seat and Desk at EPO
Creative Commons Attribution-No Derivative Works 4.0
Summary: The Central Staff Committee at Europes second-largest institution (which grants European monopolies to corporations from all around the world) is very upset about a collective assault on the staff, which is already besieged and overworked, urged to grant as many monopolies as possible as quickly as possible, thus defeating the purpose of patent examination (if insufficient time is allocated, the patent application is assumed novel and presumed valid, hence granted)
THE VIDEO above goes through this new letter from the Central Staff Committee (CSC) of the EPO, dealing with the notorious Bringing Teams Together initiative, which will have many casualties and already had some (including very high-profile ones).
The CSCs letter speaks for itself and the video above speaks of related facts, background, and context. Is the EPO certifying monopolies that are unjust if not outright illegal in order to fake 'production'? This whole situation is a stain on Europes reputation. We intend to keep it our top priority for coverage even though we now have other stuff to cover or do, e.g. 1) 2 site migrations; 2) coding; 3) Sirius series and 4) GitHub exclusives. GitHub is already collapsing; not just financially, there are also layoffs, as last noted earlier today. At one point well get around to finishing our long series (ongoing since 2021) about GitHub.
We dont worry about lacking material, we only lack time. The EPO-fr...
06:00
ASUS Unveils The Tinker V As Their First RISC-V Board Phoronix
For over a half-decade ASUS has been selling the Thinker Board devices as their line of Raspberry Pi alternatives. To date the ASUS Tinker Board single board computers have all been Arm-based while now they have launched their first RISC-V board, the Tinker V...
05:51
Adobe fixed ColdFusion flaw listed as under active exploit Security Affairs
Adobe is warning that a critical zero-day flaw in ColdFusion web app development platform was exploited in very limited attacks.
Software giant Adobe released security updates for ColdFusion versions2021 and2018 to resolve a critical flaw, tracked as CVE-2023-26360 (CVSS base score 8.6), that was exploited in very limited attacks.
Adobe is aware that CVE-2023-26360 has been exploited in the wild in very limited attacks targeting Adobe ColdFusion. reads the advisory published by the company.
The vulnerability is an Improper Access Control that can allow a remote attacker to execute arbitrary code. The vulnerability could also lead toarbitrary file system read and memory leak.
The company also fixed a critical deserialization of untrusted data issue in Adobe ColdFusion, tracked as CVE-2023-26359 (CVSS base score 9.8), that can lead to arbitrary code execution.
Adobe also fixed a ColdFusion Improper Limitation of a Pathname to a Restricted Directory (Path Traversal), tracked as CVE-2023-26361 (CVSS base score 4.9) that can lead to memory leak.
In March 2023, the company released eight patches addressing a total of 105 vulnerabilities in Photoshop, Experience Manager, Dimension, Commerce, Substance 3D Stager, Cloud Desktop Application, and Illustrator. ZDI reported that a total of 77 of these bugs were reported through its program. The experts pointed out that this is the largest Adobe update in quite some time.
Only the patch for Cold Fusion is listed as under active exploit.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs hacking, Patch Tuesday)
The post Adobe fixed ColdFusion flaw listed as under active exploit appeared first on Security Affairs.
05:27
The Linux Foundation Announces Conference Schedule for Open Source Summit North America 2023 Linux.com
The foremost conference for the global open source community features 300 sessions across 15 micro conferences, covering the most important and cutting edge topics in open source today. SAN FRANCISCO, March 14, 2023 The Linux Foundation, the nonprofit organization enabling mass innovation through open source, today announced the full schedule for Open Source Summit North America
The post The Linux Foundation Announces Conference Schedule for Open Source Summit North America 2023 appeared first on Linux.com.
05:10
FBI, State Department Miss Deadline to Produce COVID Origin Information to House Panel cryptogon.com
I consider the Wuhan lab leak revelations to be a limited hangout at this point. The goal is to prevent a wide understanding that the whole thing was premeditated. Via: Epoch Times: The FBI and U.S. Department of State didnt provide documents by the deadline in response to a congressional request for information on the []
05:06
From Power Plants to eWallets: The role of ZTNA in the gig economy HackRead | Latest Cybersecurity and Hacking News Site
By Mor Ahuvia - SASE Solution Expert, Check Point Software
The pandemic. A growing gig economy. Rounds of layoffs across industries. Its no wonder the workforce looks nothing
This is a post from HackRead.com Read the original post: From Power Plants to eWallets: The role of ZTNA in the gig economy
05:00
The Maestro Behind Design-Software Behemoth Synopsys IEEE Spectrum

For Synopsys Chief Executive Aart de Geus, running the electronic design automation behemoth is similar to being a bandleader. He brings together the right people, organizes them into a cohesive ensemble, and then leads them in performing their best.
De Geus, who helped found the company in 1986, has some experience with bands. The IEEE Fellow has been playing guitar in blues and jazz bands since he was an engineering student in the late 1970s.
Much like jazz musicians improvising, engineers go with the flow at team meetings, he says: One person comes up with an idea, and another suggests ways to improve it.
There are actually a lot of commonalities between my music hobby and my other big hobby, Synopsys, de Geus says.
Aart de Geus
Employer
Synopsys
Title
CEO
Member grade
Fellow
Alma mater
cole Polytechnique Fdrale de Lausanne, Switzerland
Synopsys is now the largest supplier of software that engineers use to design chips, employing about 20,000 people. The company reported US $1.36 billion in revenue in the first quarter of this year.
De Geus is considered a founding father of electronic design automation (EDA), which automates chip design using synthesis and other tools. It was pioneered by him and his team in the 1980s. Synthesis revolutionized digital design by taking the high-level functional description of a circuit and automatically selecting the logic components (gates) and constructing the connections (netlist) to build the circuit. Virtually all large digital chips manufactured today are largely synthesized, using software that de Geus and his team developed.
Synthesis changed the very nature of how digital chips are designed, moving us from the age of computer-a ided design (CAD) to electronic design automation (EDA), he says.
During the past three and a half decades, logic synthesis has enabled about a 10 millionfold increase in chip complexity, he says. For that reason, Electrical Business magazine named him one of the 10 most influential executives in 2002, as well as its 2004 CEO of the Year.
Creating the first circuit synthesizer
Born in Vlaardingen, Netherlands, de Geus...
05:00
OpenSSL 3.1 Released With Performance Optimizations, More AVX-512 Phoronix
OpenSSL 3.1 is out today as the new stable release for this widely-used cryptographic library. There are a number of performance optimizations to enjoy with OpenSSL 3.1, including some additional AVX-512 tuning...
04:43
Are Bank Failures Tied to COVID Scam, Lockdowns? cryptogon.com
Via: Jon Rappoport: Major media intentionally paid almost no attention to the vastness of the economic destruction caused by the lockdowns. Businesses closing their doors, going into bankruptcy, millions of peoples lives overturned and destroyed, desolate cities MANY of the businesses that failed as a result of the lockdowns had outstanding loans with banks. []
04:31
Russian Fighter Jet Crashes Into U.S. Reaper Drone Over the Black Sea cryptogon.com
Via: Daily Mail: A Russian fighter jet collided with an American Reaper drone over the Black Sea, bringing the unmanned aerial vehicle (UAV) down, the US military confirmed today. The US military said one of two Russian fighters clipped the propeller of the drone, forcing the US to bring it down in the area of []
03:53
Webb Telescope Just Saw More Galaxies in a Snapshot Than Hubble's Deepest Look SoylentNews
And scientists have only seen four percent of the data so far:
A project to map the earliest structures of the universe has found 15,000 more galaxies in its first snapshot than captured in an entire deep field survey conducted 20 years ago.
The James Webb Space Telescope, the new preeminent observatory in the sky, saw about 25,000 galaxies in that single image, dramatically surpassing the nearly 10,000 shown in the Hubble Space Telescope's Ultra Deep Field Survey. Scientists say that little piece of the space pie represents just four percent of the data they'll discover from the new Webb survey by the time it's completed next year.
"When it is finished, this deep field will be astoundingly large and overwhelmingly beautiful," said Caitlin Casey, a University of Texas at Austin astronomer co-leading the investigation, in a statement.
[...] A deep field image is much like drilling deep into Earth to take a core sample: It's a narrow but distant view of the cosmos, revealing layers of history by cutting across billions of light-years. In Hubble's deep field, the oldest visible galaxies dated back to the first 800 million years after the Big Bang. That's an incredibly early period relative to the universe's estimated age of 13.8 billion-with-a-B years.
[...] Four different types of galaxies observed through the COSMOS-Web deep field survey.The COSMOS-Web survey will map 0.6 square degrees of the skyabout the area of three full moons.
The first images from COSMOS-Web, the largest program in Webb's first year, show a rich variety of structures, teeming with spiral galaxies, gravitational lensing, and galaxy mergers. Furthermore, hundreds of galaxies that were previously identified by Hubble are getting reclassified with different characteristics after being shown in more detail with Webb.
Read more of this story at SoylentNews.
03:15
Links 14/03/2023: KDE Plasma 5.27.3 and Fedora Linux 38 Beta Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Digital Restrictions (DRM)
- Monopolies
-
GNU/Linux
-
Instructionals/Technical
-
IT Tavern My Offsite Backup March 2023
Having a disaster recovery strategy for my most important data that is easy to maintain.
The offline backup should be stored offsite in a secure and...
-
-
03:01
How to install Fedora IoT on Raspberry Pi 4 Linux.com
Transform your Raspberry Pi into an edge computing device with Fedora IoT.
Read More at Enable Sysadmin
The post How to install Fedora IoT on Raspberry Pi 4 appeared first on Linux.com.
03:01
ADC's New Argentina Report Flags How ISPs Can Do More for Users Data Privacy Deeplinks
Argentinian telecommunications providers have made strides
in their commitments to protecting users data privacy, but the
gains are uneventhey are doing a better job at informing about data
processing and users' data rights, but still a poor job at
disclosing how they handle government demands for user data,
according to a new
report by digital rights group ADC.
In this third edition of Argentina's report, most of the
improvements relate to the ISPs privacy policies. ADC has increased
the evaluation parameters in this category to follow crucial data
protection principles. Among others, the report checks whether ISPs
commit to only collect data for specific, explicit, and lawful
purposes and stick to those purposes when processing user data;
ensure the data they process is true, adequate, relevant, and not
excessive in regard to the purposes of collection; and adopt
security measures to protect user data. All companies
received credit for their privacy policies, while none of them got
more than a half star.
Once again, Movistar leads the ranking, with three and a half out of five stars. The company has almost doubled its score compared to the 2019 report, and is far ahead of second-place IPLAN, which earned roughly two stars. IPLAN was the only company to engage with ADC researchers in the last edition. Back then, IPLAN, a smaller company in Argentinas market, was taking its first steps to properly adjust its data protection policies and practices. The improvements in IPLANs policy show the companys disposition to receive criticism and recommendations, the ADC report highlights. Arlink, another small local ISP first featured in this new edition, came in last place, while Claro, a much larger provider, was almost as bad.
The new Quin Defiende Tus
Datos? (Who Defends Your Data?) edition evaluated
Movistar (Telefnica), Claro (Amrica Mvil/Carso), DirecTV, Personal
(Telecom Group), Telecentro, IPLAN, and Arlink. While Personal and
DirecTV failed to improve their scores over the last edition, all
others featured in 2019 improved theirs, at least a
little.
ADC assessed each company in five categories: how comprehensive their privacy policies are and whether they commit to notify users of any changes; if they publish transparency reports and what information they cover; whether they commit to notify users about government data requests; if they disclose guidelines authorities must follow to request user data (i.e., law enforcement guidelines) and whether ISPs commit to require a judicial order before handing over such data; and their policy commitments and practices towa...
02:51
The suspension of ipmitool LWN.net
It would appear that the ipmitool repository has been locked, and its maintainer suspended, by GitHub. This Hacker News conversation delves into the reason; evidently the developer was employed by a sanctioned Russian company. Ipmitool remains available and will, presumably, find a new home eventually. (Thanks to Paul Wise).
02:14
DEV-1101 AiTM phishing kit is fueling large-scale phishing campaigns Security Affairs
Microsoft warns of large-scale phishing attacks orchestrated with an open-source adversary-in-the-middle (AiTM) phishing kit available in the cybercrime ecosystem
Adversary-in-the-middle (AiTM) phishing kits are becoming an essential technology in the cybercrime ecosystem that is used by multiple threat actors to launch phishing attacks. AiTM phishing allows threat actors to circumvent multifactor authentication (MFA) through reverse-proxy functionality.
In AiTM phishing, threat actors set up a proxy server between a target user and the website the user wishes to visit, which is the phishing site under the control of the attackers. The proxy server allows attackers to access the traffic and capture the targets password and the session cookie.
Microsoft is currently tracking a threat actor dubbed DEV-1101 who is providing development, support, and advertising of several AiTM phishing kits that are available for sale or rent in the cybercrime underground.
Since May 2022, DEV-1101 is offering an open-source kit that automates setting up and launching sophisticated phishing attacks. The phishing kit was continually enhanced in 2022, threat actors added the capability to manage campaigns from mobile devices and evasion features such as CAPTCHA pages.
The price for the tool was increased multiple times due to the rapid growth of its popularity in the cybercrime ecosystem from July through December 2022. As of this writing, the actor offers the tool for $300, with VIP licenses at $1,000. Legacy users were permitted to continue purchasing licenses at $200 prior to January 1, 2023.
02:12
[$] Zephyr: a modular OS for resource-constrained devices LWN.net
Writing applications for devices with a lot of resource constraints, such as a small amount of RAM or no memory-management unit (MMU), poses some challenges. Running a Linux distribution often isn't an option on these devices, but there are operating systems that try to bridge the gap between running a Linux distribution and using bare-metal development. One of these is Zephyr, a real-time operating system (RTOS) launched by the Linux Foundation in 2016. LWN looked in on Zephyr at its four-year anniversary as well. Seven years after its announcement, Zephyr has made lots of progress and now has an active ecosystem surrounding it.
02:03
ALPHV ransomware gang claims it has hacked Amazons Ring HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
ALPHV ransomware group threatens to leak sensitive data allegedly stolen from amazon's ring security cameras unless demands are met.
This is a post from HackRead.com Read the original post: ALPHV ransomware gang claims it has hacked Amazons Ring
02:00
Development Release: Fedora 38 Beta DistroWatch.com: News
The Fedora project has published a beta snapshot of the distribution's upcoming Fedora 38 release. The new beta features GNOME 44, updtaed development tools, and strict compile flags to protect against common memory attacks. "Fedora 38 Workstation Beta includes GNOME 44. Its currently in beta, with a final....
01:12
SSD Reliability is Only Slightly Better Than HDD, Backblaze Says SoylentNews
SSD Reliability is Only Slightly Better Than HDD, Backblaze Says
A surprising outcome for the first SSD-based AFR report:
Backblaze is a California-based company dealing with cloud storage and data backup services. Every year, the organization provides some interesting reliability data about the large fleet of storage units employed in its five data centers around the world.
For the first time, Backblaze's latest report on storage drive reliability is focusing on Solid State Drives (SSD) rather than HDD units alone. The company started using SSDs in the fourth quarter of 2018, employing the NAND Flash-based units as boot drives rather than data-storing drives. Backblaze uses consumer-grade drives, providing Annualized Failure Rate (AFR) information about 13 different models from five different manufacturers.
The 2022 Drive States review is based on data recorded from 2,906 SSD boot units, Backblaze states, and it is essentially confirming what the company was saying in its 2022 mid-year report. SSDs are more reliable than HDDs, Backblaze says, as they show a lower AFR rate (0.98%) compared to HDDs (1.64%).
The fact that the difference in reliability level isn't exactly staggering (0.66% AFR) is rather surprising, however, as SSDs are essentially just moving electrons through memory chips while hard drives have to deal with a complex (and failure-prone) mechanism employing spinning platters and extremely sensitive read/write magnetic heads.
The reasons behind failing drives aren't known, as only an SSD manufacturer would have the equipment needed to make a reliable diagnose. For 2022, Backblaze says that seven of the 13 drive models had no failure at all. Six of those seven models had a limited number of "drive days" (less than 10,000), the company concedes, meaning that there is not enough data to make a reliable projection about their failure rates.
An interesting tidbit about Backblaze's report is that the company hasn't used a single SSD unit made by Samsung, which is a major player in the SSD consumer market. One possible explanation is that Samsung drives aren't cheap, and Backblaze is essentially using the cheapest drives they can buy in bulk quantities.
Read more of this story at SoylentNews.
01:08
Security updates for Tuesday LWN.net
Security updates have been issued by Debian (redis), Fedora (cairo, freetype, harfbuzz, and qt6-qtwebengine), Red Hat (kpatch-patch), SUSE (chromium, java-1_8_0-openj9, and nodejs18), and Ubuntu (chromium-browser, libxstream-java, php-twig, twig, protobuf, and python-werkzeug).
01:04
Software supply chain attacks are on the rise are you at risk? Graham Cluley
Graham Cluley Security News is sponsored this week by the folks at Sysdig. Thanks to the great team there for their support! Attacks targeting the software supply chain are on the rise and splashed across the news. SolarWinds raised awareness about the risk. More recent events, like the Federal Civilian Executive Branch (FCEB) agency breach, Continue reading "Software supply chain attacks are on the rise are you at risk?"
01:00
PCIe For Hackers: The Diffpair Prelude Hackaday

PCIe, also known as PCI-Express, is a highly powerful interface. So lets see what it takes to hack on something that powerful. PCIe is be a bit intimidating at first, however it is reasonably simple to start building PCIe stuff, and the interface is quite resilient for hobbyist-level technology. There will come a time when we want to use a PCIe chip in our designs, or perhaps, make use of the PCIe connection available on a certain Compute Module, and its good to make sure that were ready for that.
PCIe is everywhere now. Every modern computer has a bunch of PCIe devices performing crucial functions, and even iPhones use PCIe internally to connect the CPU with the flash and WiFi chips. You can get all kinds of PCIe devices: Ethernet controllers, high-throughput WiFi cards, graphics, and all the cheap NVMe drives that gladly provide you with heaps of storage when connected over PCIe. If youre hacking on a laptop or a single-board computer and youd like to add a PCIe device, you can get some PCIe from one of the PCIe-carrying sockets, or just tap into an existing PCIe link if theres no socket to connect to. Its been two decades since weve started getting PCIe devices now, PCIe is on its 5.0 revision, and its clear that its here to stay.
...
01:00
AI Doesnt Have to Be This Way IEEE Spectrum

Not all technological innovation deserves to be called progress.
Thats because some advances, despite their conveniences, may not do
as much societal advancing, on balance, as advertised. One
researcher who stands opposite technologys cheerleaders is MIT economist Daron Acemoglu. (The c in his surname is
pronounced like a soft g.) IEEE Spectrum spoke with
Agemogluwhose fields of research include labor economics, political
economy, and development economicsabout his recent work and his
take on whether technologies such as artificial intelligence will
have a positive or negative net effect on human society.
IEEE Spectrum: In your November 2022 working paper Automation and the Workforce, you and your coauthors say that the record is, at best, mixed when AI encounters the job force. What explains the discrepancy between the greater demand for skilled labor and their staffing levels?
Acemoglu: Firms often lay off less-skilled workers and try to increase the employment of skilled workers.
Generative AI could be used, not for
replacing humans, but to be helpful for humans. ... But thats not
the trajectory its going in right now.
Daron Acemoglu, MIT
In theory, high demand and tight supply are supposed to result in higher pricesin this case, higher salary offers. It stands to reason that, based on this long-accepted principle, firms would think More money, less problems.
Acemoglu: You may be right to an extent, but... when firms are complaining about skill shortages, a part of it is I think theyre complaining about the general lack of skills among the applicants that they see.
In your 2021 paper Harms of AI, you argue if AI remains unregulated, its going to cause substantial harm. Could you provide some examples?
Acemoglu: Well, let me give you two examples from Chat GPT, which is all the rage nowadays. ChatGPT could be used for many different things. But the current trajectory of the large language model, epitomized by Chat GPT, is very much focused on the broad automation agenda. ChatGPT tries to impress the usersWhat its trying to do is trying to be as good as humans in a variety of tasks: answering questions, being conversational, writing sonnets, and writing essays. In fact, in a few things, it can be better than humans because writing coherent te...
00:47
Oceanic Surprise: Pushing Europas Ice Centauri Dreams Imagining and Planning Interstellar Exploration
Getting Europa Clipper to its target to analyze the surface of Jupiters most interesting moon (in terms of possible life, at least) sets up a whole range of comparative studies. We have been mining data for many years from the Galileo mission and will soon be able at last! to compare its results to new images pulled in by Europa Clippers flybys. Out of this comes an interesting question recently addressed by a new paper in JGR Planets: Is Europas ice shell changing in position with time?
An answer here would establish whether we are dealing with a free-floating shell moving at a different rate than the salty ocean beneath. Computer modeling has previously suggested that the oceans effects on the shell may affect its movement, but this is evidently the first study that calculates the amount of drag involved in this scenario. Ocean flow may explain surface features Galileo revealed, with ridges and cracks as evidence of the stretching and straining effects of currents below.
Hamish Hay (University of Oxford) is lead author of the paper on this work, which was performed at the Jet Propulsion Laboratory during his postdoctoral tenure there. The study reveals a net torque on the ice shell from ocean currents moving as alternating east-west jets, sometimes spinning up the shell and at other times spinning it down as convection is altered by the evolution of the moons interior. Says Hay:
Before this, it was known through laboratory experiments and modeling that heating and cooling of Europas ocean may drive currents. Now our results highlight a coupling between the ocean and the rotation of the icy shell that was never previously considered.
Thus we are forced to reconsider some old assumptions, one of them being that the primary force acting on Europas surface is the gravitational pull of Jupiter. The paper calculates that an average jet speed of at least ~1 cm s-1 produces enough ice-ocean torque to be comparable to tidal torque. Calling these results a huge surprise, Europa Clipper project scientist Robert Pappalardo (JPL) notes that thinking about ocean circulation as the driver of surface cracks and ridges takes scientists in a new direction: [G]eologists dont usually think, Maybe its the ocean doing that.

Image: This view of Jupiter&#...
00:29
STALKER 2 hacker demands Ukrainian game developer reinstates Russian language support, or else Graham Cluley
A Ukrainian video game developer has revealed that a hacker has leaked development material stolen from the company's systems, and is threatening to release tens of gigabytes more if their unorthodox ransom demands are not met.
00:24
How Will The World End? Lifeboat News: The Blog
End of World Scenarios what are they? what is likely and what is not?
Posted on Big Think, direct link at.
Posted on Big Think.
00:23
Joel Greshock VP, Oncology, Data Science & Digital Health Janssen Research & Development Lifeboat News: The Blog

Driving Toward the Elimination of Cancer Joel Greshock VP, Oncology, Data Science & Digital Health, Janssen Pharmaceutical Companies of Johnson & Johnson.
Joel Greshock is VP, Oncology, Data Science & Digital Health, Janssen Research & Development (https://www.janssen.com/oncology/leadership-team). In this position, he is responsible for creating unique and actionable medical insights using large and increasingly available datasets. The focus of this research includes discovering novel therapeutic targets, identifying areas of unmet medical need, and enhancing clinical trial recruitment and execution.
Prior to joining Janssen R&D, Joel served as Vice President of Bioinformatics at Neon Therapeutics, Inc., where he built and managed the Data Sciences organization. At Neon, he was responsible for the design and deployment of personalized cancer therapies now under clinical evaluation.
Prior to joining Neon, Joel served as Head of Oncology Translational Informatics for Novartis, where he was responsible for the correlation of patient outcomes with molecular biomarkers, identification of mechanisms of clinical resistance and computational research for assets approaching or being evaluated in early phases of development.
Before joining Novartis, Joel assumed numerous roles for GlaxoSmithKline Oncology, which included Head of Bioinformatics. Earlier in his career, Joel was a Data Analyst at Abramson Family Cancer Research Institute at the University of Pennsylvania, where he built early generation microarray platforms and developed widely used predictive models for cancer predisposition mutations.
Joel holds a Bachelor of Science in Comprehensive Science and a Master of Science in Biology/Biostatistics, both from Villanova University. He also completed studies at the University of Pennsylvania and Temple University in Statistics and Computer Science.
00:22
An AI Learned to Play Atari 6,000 Times Faster Lifeboat News: The Blog

We dont learn by brute force repetition. AI shouldnt either.
Despite impressive progress, todays AI models are very inefficient learners, taking huge amounts of time and data to solve problems humans pick up almost instantaneously. A new approach could drastically speed things up by getting AI to read instruction manuals before attempting a challenge.
One of the most promising approaches to creating AI that can solve a diverse range of problems is reinforcement learning, which involves setting a goal and rewarding the AI for taking actions that work towards that goal. This is the approach behind most of the major breakthroughs in game-playing AI, such as DeepMinds AlphaGo.
As powerful as the technique is, it essentially relies on trial and error to find an effective strategy. This means these algorithms can spend the equivalent of several years blundering through video and board games until they hit on a winning formula.
Tuesday, 14 March
23:56
What You Need to Know to Create a Winning Hybrid Workplace HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
The global epidemic prompted enterprises to operationalize their businesses by switching to remote work. According to numerous surveys,
This is a post from HackRead.com Read the original post: What You Need to Know to Create a Winning Hybrid Workplace
23:55
Fedora 38 Beta Released With Many Exciting Updates Phoronix
The beta of Fedora 38 is out and on-time this morning for those wanting to test this latest major update to Fedora Linux...
23:02
GoBruteforcer: New Golang-Based Malware Breaches Web Servers Via Brute-Force Attacks The Hacker News
A new Golang-based malware dubbed GoBruteforcer has been found targeting web servers running phpMyAdmin, MySQL, FTP, and Postgres to corral the devices into a botnet. "GoBruteforcer chose a Classless Inter-Domain Routing (CIDR) block for scanning the network during the attack, and it targeted all IP addresses within that CIDR range," Palo Alto Networks Unit 42 researchers said. "The threat actor
22:52
The Prolificacy of LockBit Ransomware The Hacker News
Today, the LockBit ransomware is the most active and successful cybercrime organization in the world. Attributed to a Russian Threat Actor, LockBit has stepped out from the shadows of the Conti ransomware group, who were disbanded in early 2022. LockBit ransomware was first discovered in September 2019 and was previously known as ABCD ransomware because of the ".abcd virus" extension first
22:50
Advanced actor targets Fortinet FortiOS in attacks on govt entities Security Affairs
An unknown threat actor is targeting Government entities and large organizations by exploiting a security flaw in Fortinet FortiOS.
Fortinet researchers are warning of an advanced threat actor and is targeting governmental or government-related entities.
The unknown threat actor is exploiting a vulnerability in Fortinet FortiOS software, tracked as CVE-2022-41328, that may allow a privileged attacker to read and write arbitrary files via crafted CLI commands.
The CVE-2022-41328 vulnerability (CVSS score: 6.5) is a path traversal issue in FortiOS can can result in arbitrary code execution.
A improper limitation of a pathname to a restricted directory vulnerability (path traversal) [CWE-22] in FortiOS may allow a privileged attacker to read and write arbitrary files via crafted CLI commands. reads the advisory published by Fortinet.
The vulnerability impacts FortiOS versions 6.0, 6.2, 6.4.0 through 6.4.11, 7.0.0 through 7.0.9, and 7.2.0 through 7.2.3. The company addressed the vulnerability with the release of versions 6.4.12, 7.0.10, and 7.2.4 respectively.
Fortinet launched an investigation into the attacks after the FortiGate devices of one customer suddenly halted and failed to reboot. The devices halted displaying the following error message:
System enters error-mode due to FIPS error: Firmware Integrity self-test failed
The failure of the integrity test blocks the re-boot of the device to protect the integrity of the network.
The researchers discovered that the attackers modified the /sbin/init folder in the firmware image, they noticed the presence of a new file /bin/fgfm. The modification aims at providing a persistent access to the attacker.
The modification to /sbin/init ensures that /bin/fgfm, which may provide an attacker with persistent access and control, runs before proceeding with regular boot-up actions. reads the analysis published by Fortinet.
Upon executing the fgfm malware, it contacts a remote server (C2) and awaits for commands to execute.
The malicious code can perform various actions depending on the commands it receives from the C&C server, including exit program, exfiltrate data, download/write files, establish a remote shell.
The security firm pointed out that the exploit requires a deep understanding of FortiOS and the underlying hardware, a circumstance that suggests t...
22:43
CISA warns CI operators about vulnerabilities on their networks exploited by ransomware gangs Help Net Security
Organizations in critical infrastructure sectors whose information systems contain security vulnerabilities associated with ransomware attacks are being notified by the US Cybersecurity and Infrastructure Security Agency (CISA) and urged to implement a fix. A pilot program to strengthen critical infrastructure against ransomware CISA leverages multiple open-source and internal tools to research and detect vulnerabilities within U.S. critical infrastructure, the agency explained in the formal announcement of its Ransomware Vulnerability Warning Pilot (RVWP). CISA additionally leverages More
The post CISA warns CI operators about vulnerabilities on their networks exploited by ransomware gangs appeared first on Help Net Security.
22:43
Security issue in Hotspot elevate_perf_privileges.sh (CVE-2023-28144) Open Source Security
Posted by Matthias Gerstner on Mar 14
Hello list,this report is about a possible security vulnerability I found in the Hotspot
[1] project.
An openSUSE packager for hotspot requested a review of a Hotspot update to
and Polkit
authentication. During the review I found a vulnerability in the helper script
`elevate_perf_privileges.sh` that is likely not exploitable by default, but
could easily become a local root...
22:38
Re: sox: patches for old vulnerabilities Open Source Security
Posted by Helmut Grohne on Mar 14
The original fix for this issue would cause a regression. After applyingit, sox would be unable to decode WAV GSM files. This has been reported
as https://bugs.debian.org/1032082. I am attaching an updated patch that
fixes this regression. It is meant to replace the previous patch. The
updated patch includes a regression test case to avoid repeating the
mistake.
I see that most distributions (e.g. RedHat, SUSE, Gentoo, etc.) have not
picked up...
22:34
FBI reveals that more money is lost to investment fraud than ransomware and business email compromise combined Graham Cluley
The latest annual FBI report on the state of cybercrime has shown a massive increase in the amount of money stolen through investment scams. Read more in my article on the Hot for Security blog.
22:26
How We Navigate Through Crowds SoylentNews
Whether you are making your way through a crowded pedestrian zone or striving towards the goal in a team game, in both situations it is important to think not only about your own movements but also those of others. These navigation and orientation processes are carried out by brain cells that register our current position, where we are coming from, where we are moving towards and in which direction we are looking. Through their joint activity, they create a "map" of our surroundings. A special type of these cells are the so-called grid cells in the entorhinal cortex, a small brain region in the middle temporal lobe. They function like the brain's own GPS, because they not only represent our position in space, but can also put it in relation to other points in the same space.
[...] They found that the brain activity recorded while watching others was comparable to the activity of grid cells. In addition, the team was able to show that this activity was part of a larger network of brain regions that are associated with navigation processes. Interestingly, however, it turned out that the better a subject was at following the path of others, the less active this network was. "We interpret this as greater efficiency of the grid cells, which might make it less necessary to engage the larger brain network," Wagner explains.
The results of the study thus suggest that grid cells belong to a larger network of brain regions that, among other aspects, coordinates navigation processes. However, this network is particularly affected by ageing processes and especially by dementia. Wagner explains: "The function of grid cells decreases with age and dementia. As a result, people can no longer find their way around and their orientation is impaired." The group's further research is now dedicated to the question of whether grid cells are also involved in recognising other people - an aspect that is often impaired in advanced dementia.
Journal Reference:
Wagner, I.C., Graichen, L.P., Todorova, B. et al.
Entorhinal grid-like codes and time-locked network dynamics
track others navigating through space. Nat Commun
14, 231 (2023). https://doi.org/10.1038/s41467-023-35819-3
Read more of this story at SoylentNews.
22:25
The Future of VPNs Lifeboat News: The Blog
This post is also available in:  (Hebrew)
(Hebrew)
According to a report done by Surfshark VPN, out of the approximately 5 billion of internet users, over 1.6 billion of them (31% of users) use a VPN. Thats close to a fifth of the worlds population.
A VPN, or a Virtual Private Network, is a mechanism for creating a secure connection between a computing device and a computer network, or between two networks, using an insecure communication medium such as the public Internet. A VPN can extend a private network (one that disallows or restricts public access), enabling users to send and receive data across public networks as if their devices were directly connected to the private network.
22:24
6 Theories About What Lies Outside The Observable Universe! Lifeboat News: The Blog

For copyright contact: stienlemane2379(at)gmail.com.
Welcome to Futureunity, where we explore the fascinating world of science, technology, and the universe! From the inner workings of the human body to the outer reaches of space, we delve into the latest and most interesting discoveries that are shaping our world. Whether youre a science buff or just looking for some mind-blowing facts, weve got you covered. Join us as we uncover the mysteries of the world around us and discover new frontiers in the fields of science and technology. Get ready for a journey thats both educational and entertaining!
Disclaimer Fair Use:
1. The videos have no negative impact on the original works.
2. The videos we make are used for educational purposes.
3. The videos are transformative in nature.
4. We use only the audio component and tiny pieces of video
footage, only if its necessary.
Copyright Disclaimer under section 107 of the Copyright Act 1976,
allowance is made for fair use for purposes such as criticism,
comment, news reporting, teaching, scholarship, education, and
research. Fair use is a use permitted by copyright statutes that
might otherwise be infringing.
Disclaimer:
Our channel is based on facts, rumors & fiction.
22:23
A modal defense of strong AI Lifeboat News: The Blog
Dropbox is a free service that lets you bring your photos, docs, and videos anywhere and share them easily. Never email yourself a file again!
22:12
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Peter Bex on Mar 14
Indeed, the GitHub issue makes this clear as well (that's why Ispecifically mentioned opendoas and not doas in general).
It just shows that even for security-minded folks it's a big trap
to fall into.
This is the case *especially* when either
a) the developers are mainly working on OpenBSD
or
b) it's a port from OpenBSD
Because it isn't even an issue there. And you wouldn't expect an
OpenBSD-developer to include a PTY...
22:06
High Court Bans Singer From Hitting YouTube Rival With DMCA Notices TorrentFreak
 Having developed a highly automated system that attempts
to deal with huge and increasing instances of piracy, YouTube has
shown it can handle copyright complaints on an unprecedented
scale.
Having developed a highly automated system that attempts
to deal with huge and increasing instances of piracy, YouTube has
shown it can handle copyright complaints on an unprecedented
scale.
Whether the next stages of development will tackle widespread abuse of the takedown system remains to be seen but the High Court of Justice, via the Business and Property Court in Birmingham, UK, hopes to reduce the volume, if only by a little.
Two Can Play The Takedown Game
Those with both the time and the patience to read the judgment handed down last week in Moviebox Megastores International Ltd & Ors v Rahi & Ors will likely emerge from the other side with a) a headache and b) relief that relatively few copyright takedown abuse cases ever get near a courtroom.
The judgment references a trial related to three sets of proceedings that were consolidated by court order in 2021.
The Courts timeline of the dispute dates back to February 2017 when singer and claimed songwriter Mohammad Rahi emailed Kamraan Ahmed, a director of music publisher Moviebox Megastores International Limited. Rahi warned that if his music albums werent removed from Movieboxs YouTube channel and from iTunes, legal action would follow.
When Ahmed refused to remove the albums, Rahi responded by setting up his own YouTube channel, populated with music he claimed to own. A month after that, in April 2017, Rahi filed copyright claims at iTunes for four of his albums published by Moviebox, and six published on iTunes by the second claimant in the case, Oriental Star Agencies Ltd. All complaints were rejected.
In May 2017, Moviebox used YouTubes Content ID system to take all revenue generated by Rahi in respect of four albums hed uploaded to his newly-created YouTube channel. Two years later in October 2019, Rahi began filing applications at the Intellectual Property Office in Pakistan seeking copyright certificates for a number of songs, and a book in which several songs were written.
Game On: Laying the Foundations
The background to the dispute is an extraordinary maze of claims, counterclaims, and bitterness spread out over several years, during which documents were forensically examined and fingerprints subjected to professional scrutiny.
The Courts judgment, dated March 8, 2023, is concise yet still manages to weigh in at almost 54,000 words; our focus here will be on the YouTube takedown campaign and the subsequent fallout.
Rahis albums were legally obtained by one company and then transferred to another; both companies operated under Moviebox branding. It was alleged that two of Rahis co-defend...
22:03
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Hanno Bck on Mar 14
Though some context is relevant here: doas is a tool from OpenBSD.According to the Linux kernel commit message [1] OpenBSD has fixed this
already 3 years ago by entirely removing TIOCSTI [2][3].
[1]
https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=83efeeeb3d04
[2] https://undeadly.org/cgi?action=article;sid=20170701132619
[3] https://marc.info/?l=openbsd-cvs&m=149870941319610
22:00
Three Way LED Bulb Gives Up Its Secrets Hackaday

Youve probably seen three-way bulbs. You know, the ones that can go dim or bright with each turn of a switch. [Brian Dipert] wondered how
Inside the LED, [Brian] found two rings of LEDs that took the place of the filaments. He was able to identify all the ICs and devices on the board except one, an MT7712S. If you can read Mandarin, we think this is the datasheet for it.
We werent sure what [Brian] would find inside. After all, you could just sense which contacts had voltage and dim the LEDs using PWM. It probably wouldnt take any less circuitry. LED lighting is everywhere these days, and maybe they don̵...
22:00
Vulkanised 2023 Vulkan Conference Slides/Videos Available Phoronix
Taking place last month in the most wonderful city of Munich, The Khronos Group hosted Vulkanised 2023 as their Vulkan Developers' Conference and Meetup. The slides and videos from the event are now available, including talks on Valve's RADV effort and more...
21:48
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Peter Bex on Mar 14
thisexact bug as well: https://github.com/Duncaen/OpenDoas/issues/106
Cheers,
Peter
21:45
AMD Launches The EPYC Embedded 9004 Series Phoronix
AMD is using Embedded World 2023 in Nrnberg to launch the EPYC Embedded 9004 series as their 4th Gen EPYC processors intended for telecommunications, edge computing, automation, and IoT applications...
21:38
Re: TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Jakub Wilk on Mar 14
* Hanno Bck <hanno () hboeck de>, 2023-03-14 09:51:I believe this is the post in question:
https://www.openwall.com/lists/oss-security/2017/06/03/9
Nice, but...
On Linux virtual terminals, it's possible to achieve pretty much the
same effect using TIOCLINUX, the ioctl used by gpm to implement
copy&pasting.
I've attached a minimal PoC. A more elaborate one is here:
https://github.com/jwilk/ttyjack
21:33
21:28
How Cloudflare Updates The BIOS & Firmware Across Thousands Of Servers Phoronix
For those wondering how Cloudflare keeps their thousands of servers around the world up-to-date for the latest BIOS and firmware, Cloudflare's engineering blog has put out an interesting post that outlines their process of handling system BIOS updates as well as various other firmware updates...
21:17
Ubuntu Core now compatible with the Arm SystemReady IR systems specification Help Net Security
Canonical announced its Ubuntu Core OS is now compatible with the Arm SystemReady IR system specification, enabling security best practices across connected devices. In addition, the OS has achieved the PSA Certified Level 1. Ubuntu Core is a minimal devices, IoT devices, and other similar applications. It is a lightweight and secure Linux-based operating system that is optimized for efficiency and performance. Arm SystemReady More
The post Ubuntu Core now compatible with the Arm SystemReady IR systems specification appeared first on Help Net Security.
21:11
Microsoft Warns of Large-Scale Use of Phishing Kits to Send Millions of Emails Daily The Hacker News
An open source adversary-in-the-middle (AiTM) phishing kit has found a number of takers in the cybercrime world for its ability to orchestrate attacks at scale. The Microsoft Threat Intelligence team is tracking the threat actor behind the development of the kit under its emerging moniker DEV-1101. An AiTM phishing attack typically involves a threat actor attempting to steal and intercept a
21:02
KDE KWin's Move Away From GBM Surfaces Phoronix
KDE developer Xaver Hugl has written a blog post how the KWin compositor's DRM back-end has been working to move itself off GBM surfaces (gbm_surfaces) to instead allocate buffers directly and import them into EGL. This ultimately should be a win for the KWin compositor once everything is complete...
19:52
TTY pushback vulnerabilities / TIOCSTI Open Source Security
Posted by Hanno Bck on Mar 14
Hi,This blogpost highlights TTY Pushback vulnerabilities enabled via the
TIOCSTI kernel functionality available in the Linux kernel:
https://www.errno.fr/TTYPushback.html
This has been discussed here previously:
https://www.openwall.com/lists/oss-security/2017/06/03/9
Though I think there are some noteworthy updates. In the 2017 post
solar designer mentioned that the Linux kernel developers have multiple
times rejected changes in the kernel....
19:42
Wildfire Smoke Eroded Ozone Layer by 10 Percent in 2020 SoylentNews
Wildfire Smoke Eroded Ozone Layer By 10 Percent In 2020: Study:
The havoc wreaked by wildfires isn't just on the ground. Researchers at MIT have found that wildfire smoke particles actively erode Earth's protective ozone layer, thus widening the gap we've been spending the last decade trying to close.
When something burns and produces smoke, those smoke particlesotherwise called wildfire aerosolcan drift into the stratosphere, where they hang out for a year or more. According to a study published Wednesday in the journal Nature, chemists and atmospheric scientists have found that suspended wildfire aerosol sparks chemical reactions that ultimately degrade the ozone layer, or the thin atmospheric layer responsible for shielding Earth from the Sun.
The newly-discovered chemical reaction increases hydrochloric acid's solubility. While hydrochloric acid is already present in the atmosphere, MIT found that larger hydrochloric acid quantities activate chlorine in the air and increase ozone loss rates when warmer temperatures strike. This spells danger for the storied hole in the ozone layer, which environmental activists, scientists, and policymakers have been fighting to shrink for several years.
[...] Thankfully, recent attempts to mitigate damage to the ozone layer have been quite successful. International treaties like the Montreal Protocol have helped phase out the use of ozone-depleting pollutants. The world's gradual adoption of electric vehicles might have also helped. The US National Oceanic and Atmospheric Administration even found that the Antarctic ozone hole was slightly smaller in 2022 than in 2021 and far smaller than in 2006 when its size peaked. That said, it's difficult to know right now whether these efforts are enough to compensate for the ozone damage caused by wildfire smoke.
Journal Reference:
Solomon, S., Stone, K., Yu, P. et al. Chlorine
activation and enhanced ozone depletion induced by wildfire
aerosol. Nature 615, 259264 (2023). https://doi.org/10.1038/s41586-022-05683-0
...
19:40
Re: A USB-accessible slab-out-of-bounds read in Linux kernel driver Open Source Security
Posted by Jisoo Jang on Mar 14
This bug was assigned CVE-2023-1380.Best,Jisoo
19:00
Classic Gaming With FPGA and ATX Hackaday

Playing classic games, whether they are games from the golden age of arcades or simply games from consoles that are long out of production, tends to exist on a spectrum. At one end is grabbing a games ROM file, finding an emulator, and kludging together some controls on a keyboard and mouse with your average PC. At the other is meticulously restoring classic hardware for the true feel of what the game would have felt like when it was new. Towards the latter end is emulating the hardware with an FPGA which the open-source MiSTer project attempts to do. This build, though, adds ATX capabilities for the retrocomputing platform.
The ATX standard was developed as a way to standardize motherboard mounting points in PC cases. This one uses the Mini-ITX version, allowing the MiSTer FPGA board to mount to a PCB which fits into a Mini-ITX case. All of the ports on the board appear where the I/O would normally be if this was a standard motherboard, but filling the otherwise empty space with blank PCB is where this project really shines. This allows the...
18:39
Dissecting the malicious arsenal of the Makop ransomware gang Security Affairs
Cyber security researcher Luca Mella analyzed the Makop ransomware employed in a recent intrusion.
Executive summary
- Insights from a recent intrusion authored by Makop ransomware operators show persistence capability through dedicated .NET tools.
- Makop toolkit includes both off-the-shelf tools and custom-developed ones, including tools from the Chinese underground ecosystem.
- Makop gang did not conduct any significative retooling since 2020, which is a clear indicator of their effectiveness even after three years and hundreds of successful compromises.
- The gang leverages exposed remote administration services and internet-facing vulnerabilities to gain and maintain access to victim networks.
Introduction
The Makop ransomware operators started their infamous criminal business in 2020 leveraging a new variant of the notorious Phobos ransomware. During the last years, the gang maintained a solid presence in the criminal underground even if they did not join the double extortion practice.
Their operations are based on the human operator ransomware practice where most of the intrusion is handled by hands-on keyboard criminals, even in the encryption stage.
Makop ransomware gang is classified as a tier-B ransomware actor, but despite this, they keep hitting companies in Europe and Italy. Technical details of the Makop ransomware encryption tool have been greatly deepened by the Lifars security team (link), so, in this article, I am going to focus on other parts of the Makop gang arsenal leveraged to conduct digital extortions.
Technical Details
Makop ransomware operator arsenal is a hybrid one: it contains both cust-developed tools and off-the-shelf software taken from public repositories. In particular, recent investigations were able to identify four of them: the ARestore escalation tool, the backdoor, and other publicly available toolkits such as Advanced_Port_Scanner and a particular popular Chinese hack tool.
Custom tools
After the initial access, Makop criminals are still using an old tool dated back to their first operations in cyberspace. The ARestore tool is .NET executable built in 2020 and partially obfuscated. Also, the compilation time in the PE header looks time stomped, but the metadata from the .NET assembly modules reveal a more plausible date matching the time scale of the Makop operations.
filename: ARestore.exe
md5: 7f86b67ac003eda9d2929c9317025013
18:32
IRC Proceedings: Monday, March 13, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-130323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-130323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-130323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-130323.gmi
Over HTTP:
|
... |
18:28
Immediate complete revascularization found to be as safe, effective as staged procedure in treating multi-vessel disease Lifeboat News: The Blog
In patients with multi-vessel heart disease who have had a heart attack, immediate treatment with stents in all diseased arteries was found to be as safe and effective at one year of follow-up as staged treatment, according to findings from the first large, randomized trial to address this question that is being presented at the American College of Cardiologys Annual Scientific Session Together With the World Congress of Cardiology. In staged treatment, the blocked artery that caused the heart attack is treated with a stent immediately and other partially blocked arteries are treated in a second procedure up to six weeks later. This study was simultaneously published online in The Lancet at the time of presentation.
About half of patients who have a heart attack have multi-vessel heart diseasethis means that in addition to having one completely blocked coronary artery that caused their heart attack, they have additional narrowed coronary arteries that are at risk of becoming blocked or unstable, leading to another heart attack. Clinicians refer to the blocked artery that causes a heart attack as the culprit lesion and to the other at-risk arteries as non-culprit lesions.
The purpose of the international, randomized BIOVASC trial was to compare outcomes for immediate and staged complete revascularization for patients with multi-vessel heart disease who have suffered a heart attack. The goal was not to determine which approach was superior but rather to establish whether immediate complete vascularization was not inferior to the staged approach, which needed to be answered first, said Roberto Diletti, MD, Ph.D., an interventional cardiologist at Erasmus Medical Center in Rotterdam, Netherlands, and lead author of the study.
18:27
Your brain is moving along the surface of the torus Lifeboat News: The Blog
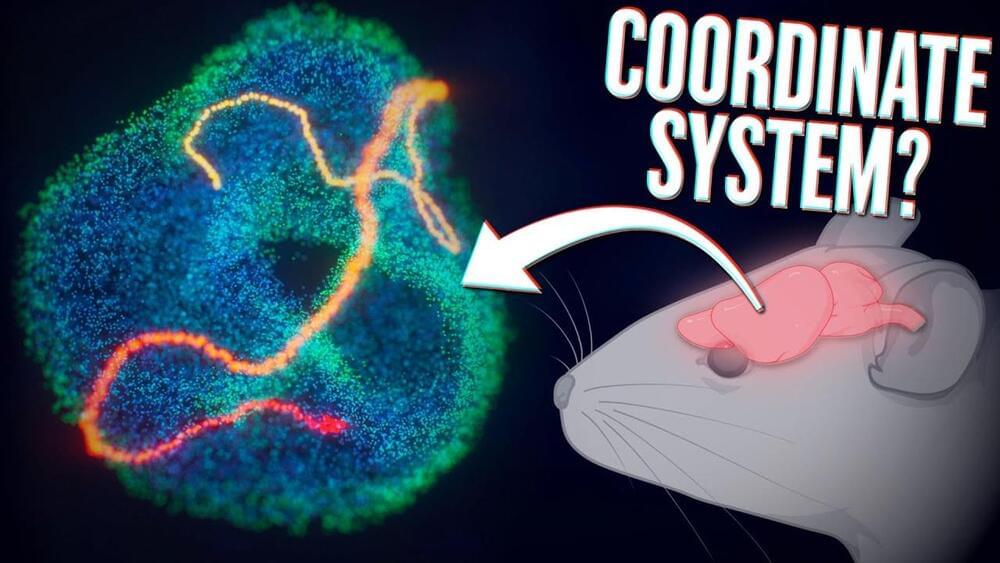
Shortform link:
https://shortform.com/artem.
In this video we will explore a very interesting paper published in Nature in 2022, which describes the hidden torus in the neuronal activity of cells in the entorhinal cortex, known as grid cells.
Place cell video: https://www.youtube.com/watch?v=iV-EMA5g288&t=158s.
Neural manifolds video: https://www.youtube.com/watch?v=QHj9uVmwA_0
My name is Artem, Im a computational neuroscience student and
researcher.
Socials:
Twitter: https://twitter.com/ArtemKRSV
REFERENCES:
1. Gardner, R. J. et al. Toroidal topology of population activity
in grid cells. Nature 602123128 (2022).
2. Pisokas, I., Heinze, S. & Webb, B. The head direction
circuit of two insect species. eLife 9, e53985 (2020).
3. Shilnikov, A. L. & Maurer, A. P. The Art of Grid Fields:
Geometry of Neuronal Time. Front. Neural Circuits 10, (2016).
4. Moser, M.-B., Rowland, D. C. & Moser, E. I. Place Cells,
Grid Cells, and Memory. Cold Spring Harb Perspect Biol 7, a021808
(2015).
5. Lewis, M., Purdy, S., Ahmad, S. & Hawkins, J. Locations in
the Neocortex: A Theory of Sensorimotor Object Recognition Using
Cortical Grid Cells. http://biorxiv.org/lookup/doi/10.1101/436352
(2018) doi:10.1101/436352.
18:26
Logarithmic nature of the brain Lifeboat News: The Blog

Shortform link:
https://shortform.com/artem.
My name is Artem, Im a computational neuroscience student and researcher.
In this video we will talk about the fundamental role of lognormal distribution in neuroscience. First, we will derive it through Central Limit Theorem, and then explore how it support brain operations on many scales from cells to perception.
REFERENCES:
1. Buzski, G. & Mizuseki, K. The log-dynamic brain: how
skewed distributions affect network operations. Nat Rev Neurosci
15264278 (2014).
2. Ikegaya, Y. et al. Interpyramid Spike Transmission Stabilizes
the Sparseness of Recurrent Network Activity. Cerebral Cortex
23293304 (2013).
3. Loewenstein, Y., Kuras, A. & Rumpel, S. Multiplicative
Dynamics Underlie the Emergence of the Log-Normal Distribution of
Spine Sizes in the Neocortex In Vivo. Journal of Neuroscience 31,
94819488 (2011).
4. Morales-Gregorio, A., van Meegen, A. & van Albada, S. J.
Ubiquitous lognormal distribution of neuron densities across
mammalian cerebral cortex. http://biorxiv.org/lookup/doi/10.1101/2022.03.17.480842
(2022) doi:10.1101/2022.03.17.480842.
OUTLINE:
00:00 Introduction.
01:15 What is Normal distribution.
03:03 Central Limit Theorem.
04:23 Normality in biology.
05:46 Derivation of lognormal distribution.
10:20 Division of labour in the brain.
12:20 Generalizer and specialist neurons.
13:37 How lognormality arises.
15:19 Conclusion.
16:00 Shortform: sponsor message.
16:54 Outro.
18:24
1129890b-1.pdf Lifeboat News: The Blog
A hidden pattern a patternist philosophy of mind by Ben Goertzel.
Dropbox is a free service that lets you bring your photos, docs, and videos anywhere and share them easily. Never email yourself a file again!
18:00
Rolex Prices to Drop Further as Supply Surges Terra Forming Terra
:quality(70)/cloudfront-eu-central-1.images.arcpublishing.com/businessoffashion/76BKM47SP5CPPGZILXQUPWHF3E.jpg)
Naomi Wolf - Dear Conservatives, I Apologize Terra Forming Terra
Here we are, a full two years later seeing a key reporter do a full on recantation. I do not think that MSM can do this until their leaders have been formally removed with full disclosure.
Naoni can at least get on with salvaging her reputation somewhat. Who was she listening to?
Ontario MPP Leaves PC Caucus After Report Alleges He Funnelled CCP Money to Candidates Terra Forming Terra
Room-Temperature Superconductor Discovery Meets With Resistance Terra Forming Terra

17:39
10,000 Dutch Farmers Protest Governments Crippling Nitrogen Emissions Target in The Hague cryptogon.com
Famine is a common result of maniac big state policies. Via: ReMix: Thousands of Dutch farmers protested on Saturday against the governments policies to reduce nitrogen emissions, warning they will put farms out of business and affect food production. Hundreds of tractors from across the Netherlands could be seen driving to the event in The []
17:01
Fortinet FortiOS Flaw Exploited in Targeted Cyberattacks on Government Entities The Hacker News
Government entities and large organizations have been targeted by an unknown threat actor by exploiting a security flaw in Fortinet FortiOS software to result in data loss and OS and file corruption. "The complexity of the exploit suggests an advanced actor and that it is highly targeted at governmental or government-related targets," Fortinet researchers Guillaume Lovet and Alex Kong said in an
16:54
Microsoft Has Had THREE Waves of Layoffs in Less Than Three Months (Yes, Its Happening Again) While Media Obsesses Over HEY HI Vapourware Techrights
On February 11th we mentioned the second round of layoffs in 2023. Now this:
Even supposedly strategic areas are culled (including Bing, Azure), but media barely bothers to mention it. Today:
Summary: Third round of job cuts at Microsoft is reported today, but many wont notice because of ChatGPT fluff and lies (targeting shareholders, trying to make it seem like Microsoft is leading in some domain and has a future)
16:54
British Chipmaker Issues Warning About Inventory Glut SoylentNews
IQE says collapse in smartphone sales may wipe one-third off revenue in first half of 2023:
Plunging demand for semiconductors is taking an obvious toll on the chip sector, and Brit compound semiconductor wafer maker IQE is warning of a serious dent in sales.
In a trading update to investors, the London Stock Exchange listed business said it had seen an acceleration of de-stocking trends across the tech industry, "with weaker demand leading to inventory build-up throughout the supply chain."
"This reduction in customer orders and forecasts is expected to result in a decline of approximately 30 million in reported revenues for H1 2023," the Cardiff-based wafer manufacturer said.
It noted the patterns monitored by the Semiconductor Industry Association that reported an 18.5 percent tumble in shipments during calendar Q1.
[...] IQE makes wafers used for radio frequency and photonics applications in several smartphones, and was a major supplier to multiple chip companies who supplied Huawei, before the US government intervened to destroy Huawei's handset business. It is widening the portfolio to also include Power Electronics and Micro-LED tech used in VR headsets.
]...] The smartphone industry has shrunk for the past two years and great things aren't expected this year either. Likewise, the PC industry has also stumbled and isn't expected to bumble along in 2023. As such, the sales bonanza that chipmakers enjoyed in recent years is over for now.
Read more of this story at SoylentNews.
16:30
We cant wait for SBOMs to be demanded by regulation Help Net Security
Old ads can be startlingcigarette ads used to boast their health-giving properties, sugar-laden candy was once advertised as a dietary aid, and soft drinks were advertised as a milk alternative for babies. None of this would fly today, of course, thanks to regulations. Foods must be advertised more responsibly, and they must list their ingredients clearly on the packaging, especially allergens. Software bills of materials (SBOMs) are like ingredient lists for software. No software is More
The post We cant wait for SBOMs to be demanded by regulation appeared first on Help Net Security.
16:00
The Curious Etymology Of The Elements Hackaday

Its not often that the worlds of lexicography and technology collide, but in a video by the etymologist [RobWords] we may have found a rare example. In a fascinating 16-minute video he takes us through the origins of the names youll find in the periodic table. Heres a word video you dont have to be on the staff of a dictionary to appreciate!
Etymology is a fascinating study, in which the scholar must disentangle folk etymologies and mistaken homophones to find the true root of a word. Fortunately in the case of most elements they bear a name bestowed on them by the scientists who discovered them, so their etymologies are rarely in dispute.
The etymologies split neatly into categories, with among them such distinctions as Latin or Greek descriptions, places including the Swedish village of Ytterby which has more elements named after it than anywhere else, elements named for mythological figures, and those named for people.
He artfully skates over the distinction between aluminium and a curiously similar metal the Americans call aluminum, because etymologists are used to deflecting controversy when language differences colour, or even color, peoples emotions. Thank you,...
16:00
Product showcase: Permit.io Application-level permissions with a no-code UI Help Net Security
Managing user access in applications has always been a headache for any developer. Implementing policies and enforcing them can prove to be quite complex, and very time-consuming. Even if a homebrew authorization solution has been developed for an application, sooner or later, problems will arise with scaling the permission system. More roles will need to be created, and further resources and actions will need to be applied and thus, more developer time will be More
The post Product showcase: Permit.io Application-level permissions with a no-code UI appeared first on Help Net Security.
15:30
The rise of AI threats: Is your business prepared to face ChatGPT? Help Net Security
Skyhigh Security has seen firsthand how 33,000 enterprise users have accessed ChatGPT through corporate infrastructures. Almost 7 TB of data has been transacted with ChatGPT through corporate web and cloud assets between Nov 2022 Feb 2023. In this Help Net Security video, Rodman Ramezanian, Global Cloud Threat Lead at Skyhigh Security, discusses how ChatGPT can strengthen business defenses. Still, nasty actors can exploit it to carry out attacks more easily and effectively. Therefore, security More
The post The rise of AI threats: Is your business prepared to face ChatGPT? appeared first on Help Net Security.
15:00
Organizations need to re-examine their approach to BEC protection Help Net Security
BEC attacks are growing year over year and are projected to be twice as high as the threat of phishing in general, according to IRONSCALES and Osterman Research. 93% of organizations experienced one or more of the BEC attack variants in the previous 12 months, with 62% facing three or more attack variants. Moreover, 43.3% of respondents from large enterprises (10,000 employees) expect these BEC attacks to increase over the next 12 months. The report More
The post Organizations need to re-examine their approach to BEC protection appeared first on Help Net Security.
14:45
Security in the cloud with more automation Help Net Security
Hopefully, youve been working with the Center for Internet Security (CIS) on securing your cloud infrastructure for a while now. Initially, you might have used our CIS Benchmarks and other free resources to manually configure your operating systems in the public cloud. Now, you might be using the CIS Hardened Images, virtual machine (VM) images that are pre-hardened to the CIS Benchmarks recommendations. They are both designed to help you avoid misconfigurations and stay secure More
The post Security in the cloud with more automation appeared first on Help Net Security.
14:06
C++ is Still 100 Times Faster Than a Compiled Version of Python SoylentNews
The Register has a story about a Python compiler called Codon that turns Python code into native machine code without a runtime performance hit.:
Python is among the one of the most popular programming languages, yet it's generally not the first choice when speed is required.
"Typical speedups over Python are on the order of 10-100x or more, on a single thread," the Codon repo declares. "Codon's performance is typically on par with (and sometimes better than) that of C/C++."
"Unlike other performance-oriented Python implementations (such as PyPy or Numba), Codon is built from the ground up as a standalone system that compiles ahead-of-time to a static executable and is not tied to an existing Python runtime (e.g., CPython or RPython) for execution," the paper says. "As a result, Codon can achieve better performance and overcome runtime-specific issues such as the global interpreter lock."
C++ Weekly - Ep 366 - C++ vs Compiled Python (Codon) performs a benchmark by running the same algorithm in Python (Codon) 8.4 seconds and C++ which takes 0.09 seconds. The video also points out the following:
We need a python code that works with codon. It takes some porting. We have to give types. It is a lot like C++ in this regard.
Read more of this story at SoylentNews.
13:34
Links 13/03/2023: Firefox 111 and FreeBSD 13.2 RC2 Techrights
![]()
Contents
- GNU/Linux
- Graphics Stack
- Applications
- Instructionals/Technical
- Games
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
13:00
Building A Communications Grid with LoRaType Hackaday

Almost all of modern society is built around various infrastructure, whether thats for electricity, water and sewer, transportation, or even communication. These vast networks arent immune from failure though, and at least as far as communication goes, plenty will reach for a radio of some sort to communicate when Internet or phone services are lacking. It turns out that certain LoRa devices are excellent for local communication as well, and this system known as LoraType looks to create off-grid text-based communications networks wherever they might be needed.
The project is based around the ESP32 platform with an E22 LoRa module built-in to allow it to operate within its UHF bands. It also includes a USB-based battery charger for its small battery, an e-paper display module to display the text messages without consuming too much power, and a keyboard layout for quickly typing messages. The device firmware lets it be largely automated; it will seek out other devices on the local mesh network automatically and the user can immediately begin communicating with other devices on that network as soon as it connects.
There are a few other upsides of using a device like this. Since it doesnt require any existing communications infrastructure to function, it can be used wherever there are...
11:46
Even Rep. LaHood Likely Can't Sue the NSA or FBI to Protect His Rights Deeplinks
In a stunning revelation, a sitting U.S. Congressman has publicly
identified himself as the subject of likely
illegal surveillance by the NSA and FBI. During a hearing on the
question of renewal the controversial mass NSA spying authorities
known as FISA Amendments Act section 702, Rep. Darin LaHood of
Illinois revealed: the member of Congress who was wrongly
queried multiple times solely by his name was in fact me. It seems
Rep. LaHood was one of the Congresspersons identified in a footnote
(footnote 92) in a
recent government report about the mass
spying program which stated that an intelligence analyst improperly
repeatedly searched 702 data using only the name of a
U.S. congressman.
Whats equally stunning is that despite absolutely knowing
that he was spied upon something that is extremely rare given the
level of secrecy around 702 neither Rep. LaHood nor anyone else
illegally spied upon will likely get a chance to seek a remedy in a
court. Thats not just because 702 is poorly drafted and
has been even more poorly executed. Its because of how
governmental secrecy has now metastasized to completely prevent
anyone from stopping illegal NSA spying of them, much less get any
other legal remedy.
Quite simply, governmental secrecy now renders moot many
of the accountability and oversight mechanisms for national
security surveillance that exist on paper in FISA as well as in the
U.S. constitution.
A Little History EFF in the Courts
One of EFFs highest priorities for nearly two decades is
making sure you can have a private conversation online. And
specifically, we want to ensure that individuals can seek judicial
accountability for violations of their constitutional and statutory
rights committed through the governments warrantless foreign
intelligence surveillance inside the United States.
EFFs work on this issue predates the passage of Section 702 itself. Our 2006 lawsuit, Hepting v. AT&T, relied on first-hand evidenc...
11:25
This Texas Bill Would Systematically Silence Anyone Who Dares to Talk About Abortion Pills Deeplinks
Texas State Representative Steve Toth recently introduced a bill that targets the most viable form of safe and effective abortion access todaymedication abortion.
House Bill (HB) 2690 seeks to prevent the sale and distribution of abortion pills like Mifepristone and misoprostol, but it doesnt stop there. By restricting access to certain information online, the bill seeks to prevent people from learning about abortion drugs, or even being aware of their existence. It would also systematically incentivize people and companies to silence anyone who wants to speak about abortion pills.
If passed, HB2690 would make it illegal to provide information on how to obtain an abortion-inducing drug. This includes stopping people from making or maintaining websites or creating and distributing applications on the topic.
On top of going after online speakers who create and post content, the bill also targets internet service providers (ISPs)companies like AT&T and Spectrum that provide access to the internet. HB 2690 would require ISPs to make every reasonable and technologically feasible effort to block Internet access to information or material intended to assist or facilitate efforts to obtain an elective abortion or an abortion-inducing drug.
In other words, Texas legislators not only want to make sure no one can start a discussion on these topics, they also want to make sure no one can find one. That creates glaring free-speech issues with this bill and, if passed, the consequences would be dire.
The bill is carefully designed to scare people into silence. First, HB 2690 encourages individuals to sue people or organizations that violate the proposed law. An interactive computer service can also be sued if it allows residents of [Texas] to access information or material that assists or facilitates efforts to obtain elective abortions or abortion-inducing drugs.
So, similar to Texas Senate Bill 8, the bill encourages anyone to file lawsuits against those who merely speak about or provide access to certain information. This is intended to, and will, chill free speech. The looming threat of litigation can be used to silence those who seek to give women truthful information about their reproductive optionspotentially putting their health or lives in danger.
Second, in a more novel approach, the legislation targets ISPs and incentivizes them to be overbroad in what they restrict. The bill encourages people to notify ISPs of abortion-related content and request th...
11:16
Scientists Call for a Global Treaty to Address Space Junk SoylentNews
What goes up must come down, and that includes all of the satellites, rocket stages, and junk that humans have launched into space. A group of scientists is sounding the alarm about how that growing cloud of debris orbiting Earth may cause us trouble in the future, and are championing a global approach to governing Earth's orbit.
In a letter published in Science today, the team of researchers says that there are 9,000 satellites currently in orbit, but that that number is projected to rise to 60,000 by 2030. All of these satellites are sources of orbital debris, whether the spacecraft themselves become junk when they are decommissioned or whether they become involved in an in-orbit crash resulting in a cascade of debris that will circle the planet.
Regardless, this group of researchers points to this boom in the space economy as a problem for the future of space safety and are calling for a legally-binding treaty to enforce the sustainability of Earth's orbitmuch the way 190 nations just vowed to protect the global oceans."
[...] Until a global initiative to reign in the issue of space debris is achieved, some space agencies are taking steps to tackle the problem. Last year, NASA announced it would be funding three projects from various universities to better understand orbital debris and sustainability in space. Likewise, ESA has approved ClearSpace's giant claw that will grab onto junk in orbit and send it into Earth's atmosphere to burn up to take care of pre-existing space debris. Meanwhile, The Drag Augmentation Deorbiting System, a 38-square-foot (3.5-square-meter) sail to increase a satellite's surface drag, could be a way to retire yet-to-be-launched satellites at the end of their lives.
Read more of this story at SoylentNews.
11:15
Adtran and Satelles offer new levels of security for synchronization network infrastructure Help Net Security
Adtran and Satelles collaboration will enable operators of critical infrastructure to safeguard their timing networks with Satellite Time and Location (STL) technology. By integrating Satelles STL into its Oscilloquartz network synchronization products, Adtran will provide an alternative to GNSS systems or a way to augment them with reliability and security. With the ability to deliver precise PNT service, even in GNSS-denied applications, STL offers a vital resource for mobile operators, power utility companies, government, scientific More
The post Adtran and Satelles offer new levels of security for synchronization network infrastructure appeared first on Help Net Security.
11:00
HPR3812: PeePaw's computer does nothing Hacker Public Radio
peepaws computer does nothing who's peepaw, whats the goal to build and understand the inner workings of an 8 bit computer and maybe one day pass it on to a grand kid this episode -nop test do a nop test, that is get the z80 up and running executing the nop instruction using the facilities of an arduino mega board running flash forth to do that, talk about pictures why? flash forth is interactive, without being such a big application itself. Happily runs on an atmega328 why the mega, oodles and oodles of io, so emulating hardware should be a snap use the microcontroller board to provide 5 volts, clock signal and data to get the z80 up and running use the logic probe to see if there is activity on the address bus wiring up hot glued solderless breadboard on to an arduino mega protoshield, white wire is the logicprobe input power and ground first clock, blue control lines int, nmi, wait busrq and reset orange wires data bus address lines go around the chip clockwise from the clock signal (blue wire) we'll be probing A0, next to the ground line 1.logicprobe.jpg 2.power.jpg 3.clock.jpg 4.control.signals.jpg 5.data.jpg 6.ready.to.probe.jpg z80-pinout.jpg 2560-pinout.jpg Click the thumbnail to see the full-sized image fixing some words, refactoring some words, defining new words fixed the data processing word to us the input on pin e4 (digital 2) not the output on pin h6 (digital 9) changed freq= some value to simply pulse, not interested in the specific frequency split clock and logic probe init words added some words to control the reset line reset and run added a word step that allows for single clock pulses the test, mega board plugged into laptop, seral terminal running spool up the logic probe spool up the microcontroller board setting up a port to provide data on the z80 data bus (rudimentary rom) add 5 volts initialize and start the clock probe the clock line probe a0 line a little more to see what else we can discern single step to reset probe m1 single step to reset add halt instruction probe halt line this is output captured from the tests run on the show. lines that begin with a back slash are comments used as narration ok<#,ram> is the forth interpreter reporting it has successfully processed the proceeding word(s), including comments pulse, high and low are output from the logicprobe, all other words are defined in the source text and the end of the notes E FlashForth 5 ATmega2560 13.06.2022 initialize the logic probe
Test Flakiness Across Programming Languages It Will Never Work in Theory
How are programming languages similar, and how do they differ? Most arguments about this are based on lists of language features, but another way to tackle the question is to ask how different languages behave in practice. This paper does that by looking at how flaky tests in C, Go, Java, JavaScript, and Python are similar and how they differ. The authors find that things like concurrency are hard everywhere, but other things (like resource management) vary from language to language. They also found that less than a dozen strategies for fixing flaky tests accounting for 85% of fixes, which suggests that explicitly teaching people bug-fixing and refactoring patterns for tests would be beneficial. Finally, they found that people either fix flaky tests right away or leave them broken for a long time, suggesting either that some tests are useful and some are not, or that some projects have a culture of clean coding and others don't with little middle ground.
Keila Costa, Ronivaldo Ferreira, Gustavo Pinto, Marcelo d'Amorim, and Breno Miranda. Test flakiness across programming languages. IEEE Transactions on Software Engineering, pages 114, 2022. doi:10.1109/tse.2022.3208864.
Regression Testing (RT) is a quality-assurance practice commonly adopted in the software industry to check if functionality remains intact after code changes. Test flakiness is a serious problem for RT. A test is said to be flaky when it non-deterministically passes or fails on a fixed environment. Prior work studied test flakiness primarily on Java programs. It is unclear, however, how problematic is test flakiness for software written in other programming languages. This paper reports on a study focusing on three central aspects of test flakiness: concentration, similarity, and cost. Considering concentration, our results show that, for any given programming language that we studied (C, Go, Java, JS, and Python), most issues could be explained by a small fraction of root causes (5/13 root causes cover 78.07% of the issues) and could be fixed by a relatively small fraction of fix strategies (10/23 fix strategies cover 85.20% of the issues). Considering similarity, although there were commonalities in root causes and fixes across languages (e.g., concurrency and async wait are common causes of flakiness in most languages), we also found important differences (e.g., flakiness due to improper release of resources are more common in C), suggesting that there is opportunity to fine tuning analysis tools. Consid...
New Research on What Drives Developer Productivity It Will Never Work in Theory
Cat Hicks (who spoke at our first two live events), Carol Lee (who's speaking next month), and their colleague Morgan Ramsey have released a new report: Developer Thriving: The Four Factors that Drive Software Developer Productivity Across Industries. It's important, insightful work, and I hope it will spark useful conversations among your team.
10:42
Why Were Suing to Protect the Right of Incarcerated People to Receive Physical Mail Deeplinks
In 2021, San Mateo County, California, banned people
incarcerated in county jails from receiving physical mail. Instead,
family and friends were required to mail their letters to Smart
Communications, a private for-profit company based in Florida that
would scan and destroy those letters so that incarcerated people
would be required to access them digitally through a limited number
of shared tablets and kiosks in public spaces within the
jails.
This is why the Electronic Frontier Foundation, the Knight
First Amendment Institute at Columbia University, and the Social
Justice Legal Foundation
filed a complaint last week challenging this
unconstitutional policy.
The lawsuit was filed on behalf of five people incarcerated in San Mateo County jails, several of their family members, and A.B.O. Comix, a collective of artists who correspond with people in jail. The complaint argues that the new mail policy violates the expressive, associational, and privacy rights of those in the countys jails, and their family, friends, and supporters who send them letters. This lawsuit is the first major challenge to the digitization of personal mail in U.S. jails.
The current policy invades the privacy of the 850 people incarcerated in the Redwood City jail, as well as that of their families. With only a few tablets to go around, this procedure is also a cruel way of limiting access to communications from family and friends by drastically reducing the ability of a person to spend time reading them. Its also hard to overstate exactly how important written correspondences are to people inside jails and prisons in the U.S. a true lifeline to the world outside.
This lawsuit also marks EFFs commitment to stopping the
current trend that seeks to privatize aspects of the carceral
system for profit as well as strip privacy away from incarcerated
individuals. Another such practice is charging exorbitant fees for
people to make phone calls to family membersa scheme that
Connecticut has just made
illegal.
Nationwide, over 500,000 people are incarcerated in county jails...
10:00
The Nixie Clock from Outer Space Hackaday

Nixie clocks are nothing new. But [CuriousMarc] has one with a unique pedigree: the Apollo Program. While restoring the Apollos Central Timing Equipment box, [Marc] decided to throw together a nixie-based clock. The avionics unit in question sent timing pulses and a mission elapsed time signal to the rest of the spacecraft. Oddly enough, while it had an internal oscillator, it was only used during failures. It normally synched to the guidance computers onboard clock.
There is a detailed explanation of the unit, along with some of the ancillary equipment and panels. Much of what the output from the unit is driving counters to display timers, although some of the clocks drive other pieces of equipment, like the telemetry commutator, which time stamps each telemetry frame.
[Marc] reminds us of an archeologist employing X-rays and other tools to examine the rare hardware. Some of the connectors are very strange these days, too, and require some custom boards. The nixie clock depends on an old HP counter. The counter had an output that sends the BCD digits visible on the display. [Marc] intercepted the connections there and allowed the connector to receive the digits instead of sending them.
The modification involved removing some buffer ICs and replacing them with sockets. If you plug the original ICs in, the counter works as before. If you plug in a special substitute board, you can use the counter as an externally-driven nixie display.
...09:49
Golang-Based Botnet GoBruteforcer targets web servers Security Affairs
A recently discovered Golang-based botnet, dubbed GoBruteforcer, is targeting web servers running FTP, MySQL, phpMyAdmin, and Postgres services
Researchers from Palo Alto Networks Unit 42 recently discovered a Golang-based botnet, tracked as GoBruteforcer, which is targeting web servers running FTP, MySQL, phpMyAdmin, and Postgres services.
In order to compromise a target system, the samples require special conditions on it, such as the use of specific arguments and targeted services already being installed (with weak passwords).
GoBruteforcer targets all IP addresses within a chosen Classless Inter-Domain Routing (CIDR) block, then attempt to compromise the identified servers with brute force attacks. The botnet uses a multiscan module to scan for the hosts inside a CIDR for its attack.
Once the multi-scan module has identified open ports for targeted services, it performs a brute-force attack against the server using a set of credentials.
The botnet targets x86, x64 and ARM processor architectures, experts noticed that it relies on an internet relay chat (IRC) bot on the victim server to communicate with the attackers server.
Once a host is found, GoBruteforcer tries to get access to the server via brute force. After achieving access, GoBruteforcer deploys an IRC bot containing the attackers URL. reads the analysis published by Palo Alto Networks. Later, GoBruteforcer also tries to query the victim system using a PHP web shell.
Unit 42 has yet to determine the initial vector of the GoBruteforcer and the PHP web shell campaign is s...
08:57
Distribution Release: Kali Linux 2023.1 DistroWatch.com: News
Kali Linux is a Debian-based distribution with a collection of security and forensics tools. The project's latest release, Kali Linux 2023.1, introduces a few new features, including defensive (purple) tools and Python virtual environments. "There are times where apt may not work for you, such as if there....
08:36
Nearly Every Person in Iraq is an Illegal Streaming Pirate, Sources Say TorrentFreak
 Piracy is a global phenomenon but the availability of
enforcement options varies from country to country.
Piracy is a global phenomenon but the availability of
enforcement options varies from country to country.
In Iraq, for example, tackling copyright infringement isnt seen as a priority or a new phenomenon.
When U.S. troops were still stationed in Iraq, rightsholders discovered that American soldiers were picking up the local habit. As a result, copyright notices were sent to US bases and United States Central Command was put on high alert.
At the end of 2021, the U.S. combat mission in Iraq officially ended, so thats no longer an issue. Iraq still faces plenty of internal issues, of course, but fighting piracy doesnt appear to be high on the agenda. Thats a concern for copyright holders.
Rightsholders Report Iraq to the USTR
Given Iraqs history, it is no surprise that the country has been repeatedly flagged by the U.S. Trade Representative. The USTR considers rightsholder input and other public signals when compiling its Special 301 Report, an annual list of countries that deserve extra attention due to intellectual property shortcomings that may hurt U.S. businesses.
The report doesnt lead directly to concrete action but is used as a leverage tool at the highest diplomatic levels to demand change. As such, recommendations are taken very seriously.
Ideally, strong statements and claims from rightsholders should be backed up by solid evidence. Thats not always needed for their positions to be cited in the USTR report but, more recently, the USTR has begun asking detailed follow-up questions. That has lead to some insightful results, also regarding Iraq.
90% Are Pirates?
Miramax and beIN, for example, stated in their submission that around 90% of the Iraqi population watches pirated live sports events and other media content. Thats a remarkable figure that we have never seen in any official reports, and it also triggered the USTR to ask how these estimates are formulated.

With roughly half of Iraq lacking a basic broadband connection, describing this section of society as online pirates is problematic. And since mor...
08:35
VW Says Sorry for Child Carjacking Fiasco, Makes Safety Service Free SoylentNews
Last month,
Volkswagen garnered plenty of bad publicity when it emerged
that the company's connected car service refused to help track a
stolen carwith a 2-year-old child still on boarduntil someone paid
to reactivate the service. Now, the automaker says it's very sorry
this happened, and it's making its connected vehicle emergency
service free to most model-year 2020-2023 Volkswagens.
[...]
Most MY2020 or newer VWs are able to use connected services, apart
from MY2020 Passats.
Some additional story details for the click-averse:
As Lake County deputies desperately tried to find a stolen Volkswagen with a toddler still inside, they reached out to Car-Net, a service that lets VW owners track their vehicles.
But the Car-Net trial period had ended, and a representative wanted $150 to restart the service and locate the SUV.
The detective pleaded, explaining the "extremely exigent circumstance," but the representative didn't budge, saying it was company policy, sheriff's office Deputy Chief Christopher Covelli said Friday.
"The detective had to work out getting a credit card number and then call the representative back to pay the $150 and at that time the representative provided the GPS location of the vehicle," Covelli said.
Read more of this story at SoylentNews.
07:43
CISA adds Plex Media Server bug, exploited in LastPass attack, to Known Exploited Vulnerabilities Catalog Security Affairs
US CISA added remote code execution vulnerability in Plex Media Server to its Known Exploited Vulnerabilities Catalog.
U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a remote code execution (RCE) vulnerability in the Plex Media Server, tracked as CVE-2020-5741 (CVSS score: 7.2), to its Known Exploited Vulnerabilities Catalog.
The three-year-old high-severity flaw is a deserialization of untrusted data in Plex Media Server on Windows, a remote, authenticated attacker can trigger it to execute arbitrary Python code.
This issue allowed an attacker with access to the server administrators Plex account to upload a malicious file via the Camera Upload feature and have the media server execute it. This could be done by setting the server data directory to overlap with the content location for a library on which Camera Upload was enabled. reads the advisory published by Plex. This issue could not be exploited without first gaining access to the servers Plex account.
The company addressed the vulnerability with the release of Plex Med...
07:10
CVE-2023-1032 - Linux kernel io_uring IORING_OP_SOCKET double free Open Source Security
Posted by Thadeu Lima de Souza Cascardo on Mar 13
A double-free vulnerability was found in the handling of IORING_OP_SOCKEToperation with io_uring on the Linux kernel.
It was fixed by commit:
649c15c7691e9b13cbe9bf6c65c365350e056067 ("net: avoid double iput when sock_alloc_file fails")
It has been assigned CVE-2023-1032.
It affects kernel versions starting with 5.19-rc1 and should affect any
backports including commits da214a475f8bd1d3e9e7a19ddfeb4d1617551bab ("net: add...
07:00
Low Power Challenge: LCD Solar Creatures Live on Sunlight, Sleep at Night Hackaday

With all those e-paper based projects doing the rounds these days, including in our Low Power Challenge, youd almost forget that monochrome LCDs were the original ultra-low-power display. Without them, we wouldnt have had watches, calculators and handheld games operating off button cell batteries or tiny solar panels back in the 80s and 90s. [Gabor] decided to build a set of gadgets with a 1990s LCD aesthetic, called LCD Solar Creatures. These cute little beasts live on nothing but solar power and provide some amusing animations on a classic seven-segment LCD screen.
The Creatures activity depends entirely on the amount of power thats available to them. If their supercapacitors dip below 3.3 V, their micros enter a deep sleep state and do nothing except briefly flash an LED every now and then as a sign of life. When light hits the solar panel, the supercaps are charged up and the Creatures come to life and display a few basic stats. Once the caps hit 4.1 V...
06:08
Kali Linux 2023.1 released and so is Kali Purple! Help Net Security
OffSec (formerly Offensive Security) has released Kali Linux digital forensics platform, and the release is accompanied by a big surprise: a technical preview of Kali Purple, a one stop shop for blue and purple teams. Kali Purple We are making defensive security accessible to everyone. No expensive licenses required, no need for commercial grade infrastructure, no writing code or compiling from source to make it More
The post Kali Linux 2023.1 released and so is Kali Purple! appeared first on Help Net Security.
06:00
Ubuntu 23.04 Preparing To Land Its Linux 6.2 Based Kernel Phoronix
The Ubuntu 23.04 "Lunar Lobster" development builds recently transitioned from Linux 5.19 as in use by Ubuntu 22.10/22.04.2 to a Linux 6.1 based kernel. This led some -- including myself -- to wonder if Canonical changed course and shifted to Linux 6.1 LTS instead of the Linux 6.2 kernel that has been out as stable since last month. Fortunately, that's not the case and Ubuntu 23.04 is preparing to soon land Linux 6.2 across all kernel flavors...
05:53
The Key to Healthier Employees Could be a Quieter or Louder Office Space SoylentNews
A new study suggests that too much or too little office noise has a negative effect on employee well-being. The sweet spot? About 50 decibels, comparable to moderate rain or birdsong.
Choosing to work in the murmur of a busy coffee shop rather than in an office with library-level silence might be healthier, according to a new study by researchers at the University of Arizona and University of Kansas.
The study finds perhaps unsurprisingly that loud noises at the office have a negative impact on employee well-being. But the study also suggests that complete silence is not conducive to a healthy workplace.
[...] "Everybody knows that loud noise is stressful, and, in fact, extremely loud noise is harmful to your ear," said study co-author Esther Sternberg, director of the UArizona Institute on Place, Wellbeing & Performance. "But what was new about this is that with even low levels of sound less than 50 decibels the stress response is higher."
[...] Humans' tendency to get distracted, Sternberg said, is a result of the brain's stress response to potential threats. Our brains are "difference detectors" that take note of sudden changes in sounds so we can decide to fight or flee, she said.
That may explain why low, steady sounds help mask distractions in the workplace, she added.
"People are always working in coffee shops those are not quiet spaces. But the reason you can concentrate there is because the sounds all merge to become background noise," Sternberg said. "It masks sound that might be distracting. If you hear a pin drop when it's very, very quiet, it will distract you from what you're doing."
Journal Reference:
Karthik Srinivasan, Faiz Currim, Casey M. Lindberg, et
al., Discovery of associative patterns between workplace
sound level and physiological wellbeing using wearable devices and
empirical Bayes modeling [open], npj Digital Medicine
(2023) 6:5 ; https://doi.org/10.1038/s41746-022-00727-1
Read more of this story at SoylentNews.
05:30
Version 2.40.0 of the Git source-code management system is out. Changes include a new --merge-base option for merges, a built-in implementation of bisection, Emacs support for git jump, a fair number of smallish user-interface tweaks, and a lot of bug fixes. See the announcement and this GitHub blog entry for the details.
05:10
Cat Toys, Toaster Bots, and Scolding Lamps IEEE Spectrum

The 2023 ACM/IEEE Human-Robot Interaction Conference (HRI) is taking place this week in Stockholm, with the theme of HRI for all. Its a good theme, promoting diversity and inclusion, but its also a good reminder that all robots have (or should have) some thought put into how they interact with humans. HRI isnt just for social robots. Even the most industrial of industrial robots, the lights-out manufacturing sorts of things that may never see a human while operating unless something is (or is about to be) very very wrong, still have to be set up and programmed by a human. And those humans are happiest when engineers remember that they exist.
Anyway, there will be a bunch of interesting research presented at HRI (the proceedings are already online here), but to kick things off were taking a look at the annual HRI Student Design Competition, which is always creative and fun.
The theme for this years Student Design Competition is Affordable Robots. Student teams are asked to create and describe a scenario with robots/agents that are affordable and have a real-life utility in society. More specifically, we are looking for affordable, impactful, scalable, and reliable use cases with real-world application potential. Since the theme of this years conference is HRI for all, we also recommend that students think about inclusion and diversity in HRI in terms of geographical inclusion (both for the developed and developing world), gender inclusion, ethnic inclusion, disability, equity, etc. related to this theme.
This combination of affordable and real-life utility is especially challenging, since robots are by nature not affordable at all, and utility (in the sense of functionality that justifies their cost) is an elusive goal, which is why this is exactly the kind of problem you want students to tackle. There are 20 entries this year, and we can only share a few of them, but here are five that we thought were particularly interesting.
Aimoji: An affordable interaction kit that upcycles used toys
as companion robots
When a child wants to talk with a toy, usually it is a one-way interaction, with the child imagining the toys responses. Our design enables every toy to have a two-way interaction using our low-cost interaction kit. The reaction of the toy is based on a motion sensor that triggers the toy to respond to t...
03:04
Why Do Some Modern Computers Still Have Serial Ports? SoylentNews
Why Do Some Modern Computers Still Have Serial Ports?:
While the parallel port is now safely buried in the grave of obsolescence, it may seem odd that the humble, slow serial port is still around. But as it turns out, bit-by-bit, this humble communications port has become essential.
[...] Serial ports are slow with the standard speed at the high end of the range coming in at a pedestrian 115.2Kbps. At that speed, it would take you almost a day to transfer 1GB of data! That's under ideal circumstances, and things can be much, much slower than that.
If we have USB, and serial ports are so slow and comparatively bulky, why the heck do some computers still have them? There are a few reasons, but the most important ones include:
- Lots, and lots, of industrial and scientific equipment are still in service and use serial ports to interface.
- It's simple, reliable, well understood, and much cheaper to implement than other more modern port types.
- Hobbyists have uses, such as programming microcontrollers.
Do you still use the serial port, or do you depend on equipment that does? I have noticed that it is still widely used in medical equipment but are there other fields in which the serial port is the standard interface?
Read more of this story at SoylentNews.
03:01
Handle exceptions in Ansible Playbooks with block and rescue Linux.com
Handle errors gracefully in your automation by using Ansible block and rescue keywords.
Read More at Enable Sysadmin
The post Handle exceptions in Ansible Playbooks with block and rescue appeared first on Linux.com.
03:00
Intel's Open-Source Linux Compute Stack Maturing Very Well For Arc Graphics Phoronix
From early December to late February there was an absence of new Compute-Runtime updates for that open-source stack for providing OpenCL and oneAPI Level Zero support for Intel graphics hardware on Linux. It was out of trend as they worked to move from a weekly~biweekly release rhythm to a monthly release cadence while taking extra time for making various other changes too. After that three month lull, they are back to pushing out new compute updates and damn it's looking nice. At least in my testing, the progress they've quietly made over the past few months has been very nice for the compute stack compatibility/support and performance.
02:30
ipmitool Repository Archived, Developer Suspended By GitHub Phoronix
The ipmitool utility on Linux systems is widely-used for controlling IPMI-enabled servers and other systems. This tool for interacting with the Intelligent Platform Management Interface (IPMI) is extremely common with server administrators while now its development is in a temporary state of limbo due to GitHub...
02:00
Hallucinations Could Blunt ChatGPTs Success IEEE Spectrum
ChatGPT has wowed the world with the depth of its knowledge and the fluency of its responses, but one problem has hobbled its usefulness: It keeps hallucinating.
Yes, large language models (LLMs) hallucinate, a concept popularized by Google AI researchers in 2018. Hallucination in this context refers to mistakes in the generated text that are semantically or syntactically plausible but are in fact incorrect or nonsensical. In short, you cant trust what the machine is telling you.
Thats why, while OpenAIs Codex or Githubs Copilot can write code, an experienced programmer still needs to review the outputapproving, correcting, or rejecting it before allowing it to slip into a code base where it might wreak havoc.
High school teachers are learning the same. A ChatGPT-written book report or historical essay may be a breeze to read but could easily contain erroneous facts that the student was too lazy to root out.
Hallucinations are a serious problem. Bill Gates has mused that ChatGPT or similar large language models could some day provide medical advice to people without access to doctors. But you cant trust advice from a machine prone to hallucinations.
OpenAI Is Working to Fix ChatGPTs Hallucinations
Ilya Sutskever, OpenAIs chief scientist and one of the creators of ChatGPT, says hes confident that the problem will disappear with time as large language models learn to anchor their responses in reality. OpenAI has pioneered a technique to shape its models behaviors using something called reinforcement learning with human feedback (RLHF).
RLHF was developed by OpenAI and Googles DeepMind team in 2017 as a way to improve reinforcement learning when a task involves complex or poorly defined goals, making it difficult to design a suitable reward function. Having a human periodically check on the reinforcement learning systems output and give feedback allows reinforcement-learning systems to learn even when the reward function is hidden.
For ChatGPT, data collected during its interactions are used to train a neural network that acts as a reward predictor, which reviews ChatGPTs outputs and predicts a numerical score that represents how well those actions ali...
01:59
Large-scale Cyber Attack Hijacks East Asian Websites for Adult Content Redirects The Hacker News
A widespread malicious cyber operation has hijacked thousands of websites aimed at East Asian audiences to redirect visitors to adult-themed content since early September 2022. The ongoing campaign entails injecting malicious JavaScript code to the hacked websites, often connecting to the target web server using legitimate FTP credentials the threat actor previously obtained via an unknown
01:30
Dark Pink APT targets Govt entities in South Asia Security Affairs
Researchers reported that Dark Pink APT employed a malware dubbed KamiKakaBot against Southeast Asian targets.
In February 2023, EclecticIQ researchers spotted multiple KamiKakaBot malware samples that were employed by the Dark Pink APT group (aka Saaiwc) in attacks against government entities in Southeast Asia countries.
The activity of the group was first detailed by Group-IB in January 2023, the group used custom malware such as KamiKakaBot and TelePowerBot.
The Dark Pink APT is active in the ASEAN region and has been active since at least mid-2021. The group focuses on military and government organizations to steal sensitive information, including confidential data and intellectual property.
The main difference between the January campaign and the attacks spotted by EclecticIQ is that the threat actors have improved the malwares obfuscation routine to avoid detection.
The researchers noticed overlaps in malware delivery and adversary techniques between Earth Yako and Dark Pink APT groups, including the use of Winword.exe for DLL Hijacking.
The KamiKakaBot malware spreads via phishing emails that contain a malicious ISO file as an attachment. The ISO image file contains a WinWord.exe which is legitimately signed by Microsoft, which is used to launch DLL side-loading attack, a loader (MSVCR100.dll), and a decoy Microsoft Word document. Upon clicking on WinWord.exe, the loader is executed in the memory of WinWord.exe.
The malware gain persistence via a registry key into HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell used to abuse features of Winlogon (Windows component).
The ISO file also contains a decoy Word document that has an XOR-encrypted section. The KamiKakaBot loader uses this section to decrypt the XOR-encrypted content from the decoy file then writes the decrypted XML KamiKakaBot payload into the disk (C:\Windows\temp) and executes it via a living-off-the-land binary called MsBuild.exe. reads the analysis published by EclecticIQ.
The attackers employed different lures in each decoy Word document to trick their victims into opening the attachment.
Before the execution of the decrypted XML payload, KamiKakaBot loader writes a registry key into HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell to abuse features of Winlogon (Windows component) for establishing persistent access.
KamiKakaBot can steal data stored in popular web browsers, including Chrome, MS Edge, and Firefox. Then the stolen data is sent to the attackers Telegram bot channel in a compressed ZIP format.
...01:27
[$] Heuristics for software-interrupt processing LWN.net
The kernel's software-interrupt ("softirq") mechanism was added prior to the 1.0 kernel release, but it implements a design seen in systems that were already old when Linux was born. For much of that time, softirqs have been an impediment to the kernel community's scalability and response-time goals, but they have proved resistant to removal. A recent discussion on a proposed new heuristic to mitigate a softirq-related performance problem may have reinvigorated interest in doing something about this subsystem as a whole rather than just tweaking the parameters of how it operates.
00:53
Links 13/03/2023: GNU Octave 8.1.0 and Scrcpy 2.0 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* an...










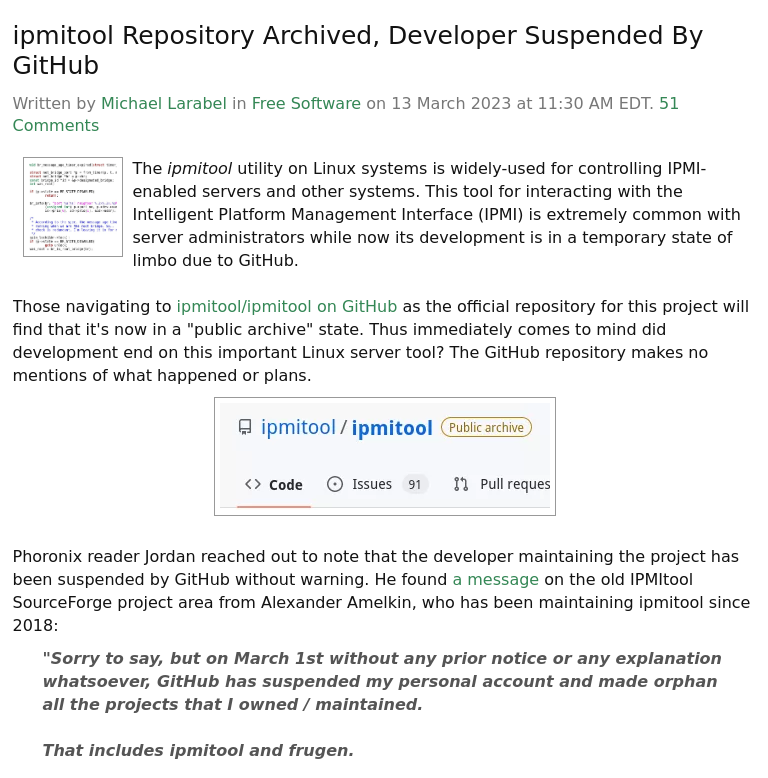









 additions & protect yourself from a malicious
additions & protect yourself from a malicious