| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Saturday, 06 May
02:12
WordPress plugin vulnerability puts two million websites at risk Graham Cluley
Millions of WordPress-powered websites are using the Advanced Custom Fields and Advanced Custom Fields Pro plugins, which security researchers say have been vulnerable to cross-site scripting (XSS) attacks.
02:05
Neural Networks on Photonic Chips: Harnessing Light for Ultra-Fast and Low-Power AI SoylentNews
Photonic circuits are a very promising technology for neural networks because they make it possible to build energy-efficient computing units. For years, the Politecnico di Milano has been working on developing programmable photonic processors integrated on silicon microchips only a few mm2 in size for use in the field of data transmission and processing, and now these devices are being used to build photonic neural networks:
"An artificial neuron, like a biological neuron, must perform very simple mathematical operations, such as addition and multiplication, but in a neural network consisting of many densely interconnected neurons, the energy cost of these operations grows exponentially and quickly becomes prohibitive. Our chip incorporates a photonic accelerator that allows calculations to be carried out very quickly and efficiently, using a programmable grid of silicon interferometers. The calculation time is equal to the transit time of light in a chip a few millimeters in size, so we are talking about less than a billionth of a second (0.1 nanoseconds)," says Francesco Morichetti, Head of the Photonic Devices Lab of the Politecnico di Milano.
"The advantages of photonic neural networks have long been known, but one of the missing pieces to fully exploit their potential was network training.. It is like having a powerful calculator, but not knowing how to use it. In this study, we succeeded in implementing training strategies for photonic neurons similar to those used for conventional neural networks. The photonic 'brain' learns quickly and accurately and can achieve precision comparable to that of a conventional neural network, but faster and with considerable energy savings. These are all building blocks for artificial intelligence and quantum applications," adds Andrea Melloni, Director of Polifab the Politecnico di Milano micro and nanotechnology center.
Originally spotted on The Eponymous Pickle.
Journal Reference: Sunil Pai et al, Experimentally realized in situ backpropagation for deep learning in photonic neural networks, Science (2023). DOI: 10.1126/science.ade8450
Related: New Chip Can Process and Classify Nearly Two Billion Images Per Second
...
02:00
Hackaday Podcast 217: The Unintentional Space and 3D Printing Episode Hackaday

Hackaday Editors Elliot Williams and Tom Nardi definitely didnt plan on devoting most of this episode to 3D printing and space stories, but lets be honest, it was bound to happen sooner or later. After an update on the Hackaday Prize, the discussion moves on to a pair of troubled spacecraft and the challenges of exploring the final frontier. From there youll hear about a chocolate 3D printer weve had our eyes on for years, the tools you should have next to your own (non-chocolate) 3D printer, and a bit of contemplation of what it really means to design for 3D printing versus traditional manufacturing methods. But its not all plastic fantastic by the end of the episode youll also hear about some particularly bold high-altitude aviators and the surprisingly short time we have left with the humble barcode.
Check out the links below if you want to follow along, and as always, tell us what you think about this episode in the comments!
01:57
OK, perhaps I should remove my ebay alert for Gary Panter, because Im starting to have a sufficient volume of Panter ephemera
James Dean, dude.
Back Again.
This blog post is part of the Punk Comix series.
01:37
LibreOffice 7.5.3: Coming Soon to a Repository Near You FOSS Force
LibreOffice 7.5.3 offers improved compatibility with MS Office, as well as numerous minor improvements throughout the suite.
The post LibreOffice 7.5.3: Coming Soon to a Repository Near You appeared first on FOSS Force.
01:30
A History of NASA Supercomputers, Among Others Hackaday

The History Guy on YouTube has posted an interesting video on the history of the supercomputer, with a specific focus on their use by NASA for the implementation of computational fluid dynamics (CFD) models of aeronautical assemblies.
The aero designers of the day were quickly finding out the limitations of the wind tunnel testing approach, especially for so-called transonic flow conditions. This occurs when an object moving through a fluid (like air can be modeled) produces regions of supersonic flow mixed in with subsonic flow and makes for additional drag scenarios. This severely impacts aircraft performance. Not accounting for these effects is not an option, hence the great industry interest in CFD modeling. But the equations for which (usually based around the Navier-Stokes system) are non-linear, and extremely computationally intensive.
01:00
Mirantis k0s updates simplify management of Kubernetes clusters Help Net Security
Mirantis announced the latest update of open source k0s, which adds compatibility with the latest release of Kubernetes 1.27, as well as improvements and bug fixes to k0s. The latest update of Mirantis k0s makes improvements that simplify installation and management of Kubernetes clusters. New features include support for containerD plug-ins that simplify running, for example, WASM and gVisor container sandboxes, making it easier for users to extend their clusters with additional container runtimes. Also, More
The post Mirantis k0s updates simplify management of Kubernetes clusters appeared first on Help Net Security.
00:49
[$] The end of the accounting search LWN.net
Some things, it seems, just cannot be hurried. Back in 2007, your editor first started considering alternatives to the proprietary accounting system that had been used by LWN since the beginning. That search became more urgent in 2012, and returned in 2017 with a focused effort to find something better. But another five years passed before some sort of conclusion was reached. It has finally happened, though; LWN is no longer using proprietary software for its accounting needs.
00:43
Links 05/05/2023: Plasma Mobile Updates, Speculations About Molly de Blanc Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
-
GNU/Linux
-
GamingOnLinux Framework gives more detail on their AMD Ryzen laptop
Recently Framework excited everyone over their big DIY laptop upgrades, and now theyre giving more detail on the Framework 13 Laptop with AMD Ryzen. They werent able to originall...
-
00:40
AMD openSIL Will Eventually Replace AGESA, Supporting Both Client & Server CPUs Phoronix
For those that haven't yet watched the AMD openSIL presentation from the OCP Regional Summit in Prague from April, the most interesting takeaway was deserving of its own article... AMD openSIL is planned to eventually replace the well known AGESA and that it will be supported across AMD's entire processor stack -- just not limited to EPYC server processors as some were initially concerned but will support all AMD processors...
00:36
Gemini Links 05/05/2023: Standing To Code and More Techrights
-
Gemini* and Gopher
-
Personal
-
SpellBinding: SHILOPD Wordo: DEFER
-
Woke up, fell out of bed
Im tired, though, having awakened to pee about 3:50am, and never really falling back asleep again.
So its been a bit of internet, leftovers for breakfast, and capturing three fun photos:
- the moon in a portion of the horizon I suspect its not seeing in much, along with an interesting double due to the pane of glass the photo was captured through
-
-
Technical
-
Standing To Code
Over a decade ago I read suggestions that standing to work might be healthier than sitting, and tried it.
Shortly afterwards it seems like a lot of the world did the same: desks at my office were gradually swapped for motorized sit/stand desks, and such desks became the default.
It also quickly became apparent that despite having the choice right in front of them most people were going to mostly sit.
-
-
* Gemini (Primer) links can be opened using Gemini software. Its like the World Wide Web but a lot lighter.
00:24
Pandemic New Normal: Sharp Increase in Deaths Across All Age Groups schestowitz.com
England and Wales death totals by week:
 urther
to
what I published on Wednesday, heres a breakdown of increase in
deaths by age group, debunking the notion that it is impacting only
very old people.
urther
to
what I published on Wednesday, heres a breakdown of increase in
deaths by age group, debunking the notion that it is impacting only
very old people.
The number on the left is the total deaths for week 16 (latest on record) in 2019, compared to the same week in 2023 (shown on the right below), i.e. last month:
For ages 15-45, 321 compared to 251: 28% increase in
fatalities
For ages 45-64, 1478 compared to 1100: 34.4% increase in
fatalities
For ages 65-74, 1878 compared to 1446: 30% increase in
fatalities
Seems like a national health crisis, but the media hardly talks about it, so lets pretend its not happening.
00:00
AutoCrypt KEY provides the key management features needed for automotive production Help Net Security
AutoCrypt KEY enables OEMs and suppliers to manage all types of cryptographic keys used for the components of connected and electric vehicles. Modern vehicles function through communications, including internal communications between ECUs and application processors, and external connections with nearby vehicles, roadside infrastructure, mobile devices, and charging stations. To ensure that all transmitted data are safely encrypted and all connected components can be securely verified, the use of cryptographic keys is essential in establishing trust More
The post AutoCrypt KEY provides the key management features needed for automotive production appeared first on Help Net Security.
00:00
This Week in Security: Oracle Opera, Passkeys, and AirTag RFC Hackaday

Theres a problem with Opera. No, not that kind of opera. The Oracle kind. Oracle OPERA is a Property Management Solution (PMS) that is in use in a bunch of big-name hotels around the world. The PMS is the system that handles reservations and check-ins, talks to the phone system to put room extensions in the proper state, and generally runs the back-end of the property. Its old code, and handles a bunch of tasks. And researchers at Assetnote found a serious vulnerability. CVE-2023-21932 is an arbitrary file upload issue, and rates at least a 7.2 CVSS.
Its a tricky one, where the code does all the right things, but
gets the steps out of order. Two parameters, jndiname
and username are encrypted for transport, and the
sanitization step happens before decryption. The username parameter
receives no further sanitization, and is vulnerable to path
traversal injection. There are two restrictions to exploitation.
The string encryption has to be valid, and the request has to
include a valid Java Naming and Directory Interface (JNDI) name. It
looks like these are the issues leading Oracle to consider this
flaw difficult to exploit vulnerability allows high privileged
attacker.
The only problem is that the encryption key is global and static. It was pretty straightforward to reverse engineer the encryption routine. And JDNI strings can be fetched anonymously from a trio of endpoints. This lead Asse...
00:00
Intel's Vulkan Linux Driver Increases Instruction Heap - Fix For Overwatch Phoronix
Intel's ANV open-source Vulkan driver has increased its instruction heap size to 2Gb in order to address a hang experienced with the game Overwatch while this is also likely to help other software/games moving forward...
Friday, 05 May
23:47
New Android Malware 'FluHorse' Targeting East Asian Markets with Deceptive Tactics The Hacker News
Various sectors in East Asian markets have been subjected to a new email phishing campaign that distributes a previously undocumented strain of Android malware called FluHorse that abuses the Flutter software development framework. "The malware features several malicious Android applications that mimic legitimate applications, most of which have more than 1,000,000 installs," Check Point said in
23:33
Security updates for Friday LWN.net
Security updates have been issued by Debian (chromium, evolution, and odoo), Fedora (java-11-openjdk), Oracle (samba), Red Hat (libreswan and samba), Slackware (libssh), SUSE (amazon-ssm-agent, apache2-mod_auth_openidc, cmark, containerd, editorconfig-core-c, ffmpeg, go1.20, harfbuzz, helm, java-11-openjdk, java-1_8_0-ibm, liblouis, podman, and vim), and Ubuntu (linux-aws, linux-aws-hwe, linux-intel-iotg, and linux-oem-6.1).
23:24
Doctors Have Performed Brain Surgery on a Fetus in One of the First Operations of its Kind SoylentNews
Her parents signed up for a clinical trial of an in-utero surgical treatment to see if doctors could intervene before any of these outcomes materialized. It seems to have worked. The team behind the operation now plans to treat more fetuses in the same way. Other, similar brain conditions might benefit from the same approach. For conditions like these, fetal brain surgery could be the future.
The baby's condition, known as vein of Galen malformation, was first noticed during a routine ultrasound scan at 30 weeks of pregnancy. The condition occurs when a vein connects with an artery in the brain. These two types of vessels have different functions and should be kept separatearteries ferry high-pressure flows of oxygenated blood from the heart, while thin-walled veins carry low-pressure blood back the other way.
When the two combine, the high-pressure blood flow from an artery can stretch the thin walls of the vein. "Over time the vein essentially blows up like a balloon," says Darren Orbach, a radiologist at Boston Children's Hospital in Massachusetts, who treats babies born with the condition.
The resulting balloon of blood can cause serious problems for a baby. "It's stealing blood from the rest of the circulation," says Mario Ganau, a consultant neurosurgeon at Oxford University Hospitals in the UK, who was not involved in this particular case. Other parts of the brain can end up being starved of oxygenated blood, causing brain damage, and there's a risk of bleeding in the brain. The extra pressure put on the heart to pump blood can lead to heart failure. And other organs can suffer tooespecially the lungs and kidneys, says Ganau.
Fetuses with the condition are thought to be protected by the placenta to some degree. But that changes from the moment the umbilical cord is clamped at birth. "All of a sudden there's this enormous burden placed right on the newborn heart," says Orbach. "Most babies with this condition will become very sick, very quickly."
Journal Reference:
Darren B. Orbach, Louise E. Wilkins-Haug, Carol B. Benson, et
al., Transuterine Ultrasound-Guided Fetal Embolization of
Vein of Galen Malformation, Eliminating Postnatal
Pathophysiology [open], Stroke, 2023. DOI: https://www.ahajournals.org/doi/10.1161/STROKEAHA.123.043421
Read more of this story at SoylentNews.
23:23
GJ 486b: An Atmosphere around a Rocky M-dwarf Planet? Centauri Dreams Imagining and Planning Interstellar Exploration
I might have mentioned the issues involving the James Webb Space Telescopes MIRI instrument in my earlier post on in-flight maintenance and repair. MIRI is the Mid-Infrared Instrument that last summer had issues with friction in one of the wheels that selects between short, medium and longer wavelengths. Now there seems to be a problem, however slight, that affects the amount of light registered by MIRIs sensors.
The problems seem minor and are under investigation, which is a good thing because we need MIRIs capabilities to study systems like GJ 486, where a transiting rocky exoplanet may or may not be showing traces of water in an atmosphere that may or may not be there. MIRI should help sort out the issue, which was raised through observations with another JWST instrument, the Near-Infrared Spectrograph (NIRSpec). The latter shows tantalizing evidence of water vapor, but the problem is untangling whether that signal is coming from the rocky planet or the star.
This points to an important question. GJ 486b is about 30 percent larger than Earth and three times as massive, a rocky super-Earth orbiting its red dwarf host in about 1.5 Earth days. The proximity to the star almost demands tidal lock, with one side forever dark, the other facing the star. If the water vapor NIRSpec is pointing to actually comes from a planetary atmosphere, then that atmosphere copes with surface temperatures in the range of 430 Celsius and the continual bombardment of ultraviolet and X-ray radiation associated with such stars. That would be encouraging news for other systems in which rocky worlds orbit further out, in an M-dwarfs habitable zone.
Sarah Moran (University of Arizona, Tucson) is lead author of the study, which has been accepted for publication at The Astrophysical Journal Letters:
We see a signal, and its almost certainly due to water. But we cant tell yet if that water is part of the planets atmosphere, meaning the planet has an atmosphere, or if were just seeing a water signature coming from the star.

Image: This graphic shows the transmission spectrum obtained by Webb observations of rocky exoplanet GJ 486b. The science teams analys...
22:45
North Korea-linked Kimsuky APT uses new recon tool ReconShark Security Affairs
North Korea-linked APT group Kimsuky has been observed using a new reconnaissance tool dubbed ReconShark in a recent campaign.
SentinelOne researchers observed an ongoing campaign from North Korea-linked Kimsuky Group that is using a new malware called ReconShark.
The reconnaissance tool is delivered through spear-phishing emails, OneDrive links leading to document weaponized downloads, and the execution of malicious macros.
Kimsuky cyberespiona group (aka ARCHIPELAGO, Black Banshee, Thallium, Velvet Chollima, APT43) was first spotted by Kaspersky researcher in 2013. At the end of October 2020, the US-CERT published a report on Kimuskys recent activities that provided information on their TTPs and infrastructure.
The APT group mainly targets think tanks and organizations in South Korea, other victims were in the United States, Europe, and Russia.
In the latest Kimsuky campaign, the state-sponsored group focused on nuclear agendas between China and North Korea, relevant to the ongoing war between Russia and Ukraine.
The threat actor recently targeted the staff of Korea Risk Group (KRG), the information and analysis firm specializing in matters directly and indirectly impacting the Democratic Peoples Republic of Korea (DPRK). SentinelOne reported that the same campaign is still targeting other entities and individuals in at least the United States, Europe, and Asia, including think tanks and universities.
For the deployment of ReconShark, Kimsuky continues to make use of specially crafted phishing emails. Notably, the spear-phishing emails are made with a level of design quality tuned for specific individuals, increasing the likelihood of opening by the target. This includes proper formatting, grammar, and visual clues, appearing legitimate to unsuspecting users. reads the analysis published by SentinelOne. Notably, the targeted emails, which contain links to download malicious documents, and the malicious documents themselves, abuse the names of real individuals whose expertise is relevant to the lure subject such as Political Scienti...
22:25
AMD Virtual NMI Support For KVM Virtualization Merged Into Linux 6.4 Phoronix
Going back to mid-2022 AMD engineers have been working on Virtual NMI support with SVM for the Kernel-based Virtual Machine (KVM) as an efficiency optimization. With the in-development Linux 6.4 kernel the AMD VNMI support has been merged...
22:22
A major problem with fusion is solved leading us closer to a perpetual energy source Lifeboat News: The Blog
Fusion reactor.
Without a doubt someday it is possible to have fusion power plants providing sustainable energy resolving our long-standing energy problems. This is the main reason so many scientists throughout the world are carrying out research on this power source. The generation of power from this method actually mimics the sun.
22:22
Laser pulses triple transition temperature for ferromagnetism in a rare-earth titanate Lifeboat News: The Blog
Researchers in Germany and the U.S. have shown for the first time that terahertz (THz) light pulses can stabilize ferromagnetism in a crystal at temperatures more than three times its usual transition temperature. As the team reports in Nature, using pulses just hundreds of femtoseconds long (a millionth of a billionth of a second), a ferromagnetic state was induced at high temperature in the rare-earth titanate YTiO3 which persisted for many nanoseconds after the light exposure. Below the equilibrium transition temperature, the laser pulses still strengthened the existing magnetic state, increasing the magnetization up to its theoretical limit.
Using light to control magnetism in solids is a promising platform for future technologies. Todays computers mainly rely on the flow of electrical charge to process information. Moreover, digital memory storage devices make use of magnetic bits that must be switched external magnetic fields. Both of these aspects limit the speed and energy efficiency of current computing systems. Using light instead to optically switch memory and computing devices could revolutionize processing speeds and efficiency.
YTiO3 is a transition metal oxide that only becomes ferromagnetic, with properties resembling those of a fridge magnet, below 27 K or 246C. At these low temperatures, the spins of the electrons on the Ti atoms align in a particular direction. It is this collective ordering of the spins which gives the material as a whole a macroscopic magnetization and turns it ferromagnetic. In contrast, at temperatures above 27 K, the individual spins fluctuate randomly so that no ferromagnetism develops.
22:22
Tiny 22-lb Hydrogen Engine May Replace the Traditional Combustion Engine Lifeboat News: The Blog
The machine, which weighs only 22 lb (10 kg), is a single-piston-linear-engine, that runs exclusively on hydrogen. As it has only 20 components and one moving part, the engine is also much cheaper to produce and maintain than traditional engines.
22:03
OTB#72: The Seventh Seal Random Thoughts
Ive blogged about this movie before, and its not a new entry on the 2022 directors list, so I shouldnt be re-watching it now, eh why not.
21:52
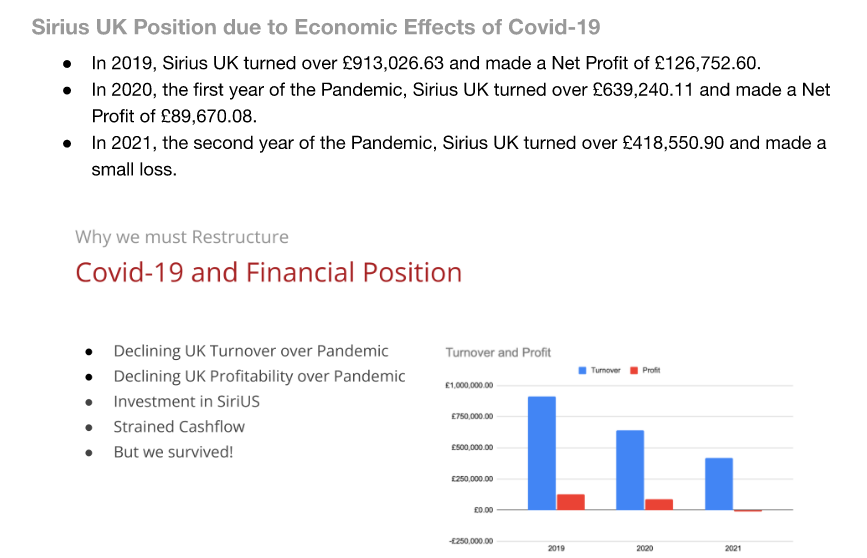
[Meme] Mr. Kink, Where Did You All Hide the Stolen Money? Techrights
Summary: The self-described owner of Sirius Open Source probably did not understand what he was getting into; for instance, did he know staff had been defrauded (his colleagues at the time)?
21:49
Hackers Targeting Italian Corporate Banking Clients with New Web-Inject Toolkit DrIBAN The Hacker News
Italian corporate banking clients are the target of an ongoing financial fraud campaign that has been leveraging a new web-inject toolkit called drIBAN since at least 2019. "The main goal of drIBAN fraud operations is to infect Windows workstations inside corporate environments trying to alter legitimate banking transfers performed by the victims by changing the beneficiary and transferring
21:48
Sirius Might be Hiding Money Aborad (Deep Debt in the UK) schestowitz.com
Internal documents show evidence
Summary: The finances of Sirius are dodgy; with at least three different shells (in at least two countries) and an unknown number of non-disclosure agreements (NDAs), its hard to know where money comes from and where it is going to (even the companys registered address isnt authentic anymore)
AS noted this morning, the police is far too slow (if not reluctant) to investigate crimes of Sirius Open Source, so lets examine the facts, based on the Sirius Business Case as it was presented 12 months ago.
Quite a few people were involved in the blunders and the crimes. We chose not to name them. Anyway, of note are the following parts:
Where did the surplus go? Another country? Seems plausible. There we go:
They dont even mention the Gates Foundation because of the non-disclosure agreement, but its what likely drew the CEO to the US because, according to him, it was the first Sirius US client (strange, right?) and it was never mentioned anywhere in writing.
Several things are noteworthy and might be relevant to the police investigation. First, in March the CEO was publicly advertising that he had money (about 100,000 pounds per year to offer in salaries). So where does he hide the money? Where did that money come from? In the report he kept secret from us the finances in the US. Well, maybe he stashed it aside over the years and now he hides money in the US (from his ex-wives), who knows
The only other possibility is that he fakes everything or that he advertises openings for which he cannot even pay a s...
21:43
[Revealed] The Financial Secrets of Sirius Open Source (Do the Former Wives of the CEO Know?) Techrights
Internal documents show evidence
Summary: The finances of Sirius are dodgy; with at least three different shells (in at least two countries) and an unknown number of non-disclosure agreements (NDAs), its hard to know where money comes from and where it is going to (even the companys registered address isnt authentic anymore)
AS noted this morning, the police is far too slow (if not reluctant) to investigate crimes of Sirius Open Source, so lets examine the facts, based on the Sirius Business Case as it was presented 12 months ago.
Quite a few people were involved in the blunders and the crimes. We chose not to name them. Anyway, of note are the following parts:
Where did the surplus go? Another country? Seems plausible. There we go:
They dont even mention the Gates Foundation because of the non-disclosure agreement, but its what likely drew the CEO to the US because, according to him, it was the first Sirius US client (strange, right?) and it was never mentioned anywhere in writing.
With two grown up girls in the UK and two more young girls in the UK the CEO (two failed marriages) is probably chased for many other expenses.Several things are noteworthy and might be relevant to the police investigation. First, in March the CEO was...
21:00
Linux Cell Phone? Build OURPhone Hackaday

[Evan] couldnt find a phone he liked, so he decided to build his own. There are advantages and disadvantages, as you might expect. On the plus side, you have the ultimate control. On the negative side, it doesnt quite have the curb appeal at least to the average user of a sleek new cell phone from a major manufacturer.
The phone uses a Raspberry Pi, along with a 4G modem and a 480800 touchscreen. Theres a laser cut box that measures 90x160x30 mm. For reference, a Google Pixel 7 is about 73x156x9 mm, so a little easier on the pocket.
But not one the pocketbook. The OURPhone only costs about $200 USD to build. There are trade-offs. For example, the touchscreen is resistive, so youll want a stylus (theres a slot for it in the case). On the other hand, if you dont like something, it is all there for you to change.
Obviously, a better screen would help. Thinner batteries might be a good enhancement too. But thats the beauty of an open project. You can do all these things and more.
We wondered if you could get one of the mobile Linux editions to run or even Android. It seems like the hardest part is coming up with a sophisticated enclosure.
20:41
Europol Operation Arrests 288 in Massive Dark Web Drug Bust SoylentNews
The notorious Monopoly Market site has been seized and 288 suspects have been arrested:
Monopoly Market has been seized by authorities, while 288 suspects have been arrested. These individuals are believed to have bought or sold drugs on the dark web through this site.
The international operation called SpecTor involved "separate complementary actions" in Austria, France, Germany, the Netherlands, Poland, Brazil, the UK, the US and Switzerland. The information used to conduct the operation stemmed from "troves of evidence provided by German authorities", according to Europol which coordinated the international law enforcement action. These German authorities successfully seized "criminal infrastructure" in December 2021, which was used to create evidence for hundreds of national investigations.
"A number of investigations to identify additional individuals behind dark web accounts are still ongoing," Europol wrote in a statement. "As law enforcement authorities gained access to the vendors' extensive buyer lists, thousands of customers across the globe are now at risk of prosecution as well."
The US Department of Justice claims that Operation SpecTor led to more seizures "than any prior operation". The total seizures include 117 firearms, 850kg of different drugs and $53.4m in both cash and virtual currencies.
Commenting on the successful operation, Europol executive director Catherine De Bolle said the law enforcement coalition proves that "we all do better when we work together".
"This operation sends a strong message to criminals on the dark web: international law enforcement has the means and the ability to identify and hold you accountable for your illegal activities, even on the dark web," De Bolle said.
Read more of this story at SoylentNews.
20:35
Former Uber CSO avoids prison for concealing data breach Help Net Security
Joe Sullivan, the former Uber CSO who has been convicted last year for attempting to cover up a data breach Uber suffered in 2016 and kept it hidden from the Federal Trade Commission (FTC), has been sentenced to three years of probation plus 200 hours of community service. The conviction Sullivan became Chief Security Officer at Uber in April 2015, and in November 2016 testified before the FTC under oath that the company had taken More
The post Former Uber CSO avoids prison for concealing data breach appeared first on Help Net Security.
20:35
Linux 6.4 Closes The Door On Intel Thunder Bay Phoronix
While Intel Thunder Bay sparked rumors years ago as potentially being a mix of Intel x86 cores and Movidius VPU cores, although the Linux patches put it as ARM cores paired with the Movidius VPU, Thunder Bay is no more. As I wrote back in March, Intel Linux engineers have acknowledged Thunder Bay is cancelled and there are no end-customers/users so they are going ahead and removing the Linux support...
20:22
LoongArch With Linux 6.4 Lands Optimizations, New Functionality Phoronix
Chinese tech company Loongson continues working on improving the upstream Linux kernel support for their MIPS-derived, RISC-V-inspired domestic CPU architecture. With the in-development Linux 6.4 kernel is another batch of optimizations and implementing more kernel functionality for the LoongArch CPU architecture...
20:19
N. Korean Kimsuky Hackers Using New Recon Tool ReconShark in Latest Cyberattacks The Hacker News
The North Korean state-sponsored threat actor known as Kimsuky has been discovered using a new reconnaissance tool called ReconShark as part of an ongoing global campaign. "[ReconShark] is actively delivered to specifically targeted individuals through spear-phishing emails, OneDrive links leading to document downloads, and the execution of malicious macros," SentinelOne researchers Tom Hegel
20:18
Lack of Visibility: The Challenge of Protecting Websites from Third-Party Scripts The Hacker News
Third-party apps such as Google Analytics, Meta Pixel, HotJar, and JQuery have become critical tools for businesses to optimize their website performance and services for a global audience. However, as their importance has grown, so has the threat of cyber incidents involving unmanaged third-party apps and open-source tools. Online businesses increasingly struggle to maintain complete visibility
20:11
Experimental AV2 Support Added To AVIF Image Encoder Phoronix
The reference AVIF image encoder for the AV1 Image File Format has added experimental support for AV2, the next-generation codec that remains in development by the Alliance for Open Media...
20:08
Fleckpe Android malware totaled +620K downloads via Google Play Store Security Affairs
Fleckpe is a new Android subscription Trojan that was discovered in the Google Play Store, totaling more than 620,000 downloads since 2022.
Fleckpe is a new Android subscription Trojan that spreads via Google Play, the malware discovered by Kaspersky is hidden in photo editing apps, smartphone wallpaper packs, and other general-purpose apps.
The malicious campaign has been active since 2022, the experts discovered eleven apps infected with Fleckpe on Google Play, which have been installed on more than 620,000 devices. Once discovered, the apps have been quickly removed from the Play Store, but the threat actors might have already uploaded other tainted apps that have yet to be discovered.
Upon executing one of the infected apps, it loads a heavily obfuscated native library containing a dropper that decrypts and runs malicious code from the app assets.
The payload sends information about the infected device to the C2 servers, including the MCC (Mobile Country Code) and MNC (Mobile Network Code). In turn, the C2 server returns a paid subscription page. The Trojan opens the page in an invisible web browser and attempts to complete a subscription of the victim. In case the subscription process requires a confirmation code, the malware is able to get it from the notifications.
Once installed, the apps continue providing their legitimate functionality, for example, installing wallpapers, after the victim has been subscribed to a paid service
The experts noticed that the authors of the malware are upgrading it, for example, they moved most of the subscription code to the native library. The payload is only used to intercept notifications and view web pages. This move makes hard the analysis and the detection of the malware.
Most of the victims are from Thailand, however, other infections were observed in Poland, Malaysia, Indonesia, and Singapore.
Sadly, subscription Trojans have only gained popularity with scammers lately. Their operators h...
20:00
Space Tech Is Soaring into New Frontiers. Here's Your Roadmap. IEEE Spectrum

The space technology industry is defying gravity both literally and figuratively driving innovation that pushes into new frontiers.
Keysights new in-depth survey of the latest trends in this fast-paced industry can help you identify:
- Top satellite applications driving market growth
- Top enabling technologies, technology trends, and novel solutions
- What space technology leaders consider to be the top challenges and applications with the greatest future impact
The report provides industry analysis that adds essential context to the survey findings.
19:54
dav1d 1.2 Released With More SIMD Optimizations Phoronix
Dav1d as the open-source AV1 video decoder developed as part of the VideoLAN project is out with a new minor feature release...
19:52
Packagist Repository Hacked: Over a Dozen PHP Packages with 500 Million Compromised The Hacker News
PHP software package repository Packagist revealed that an "attacker" gained access to four inactive accounts on the platform to hijack over a dozen packages with over 500 million installs to date. "The attacker forked each of the packages and replaced the package description in composer.json with their own message but did not otherwise make any malicious changes," Packagist's Nils Adermann said
19:50
Critical RCE vulnerability in Cisco phone adapters, no update available (CVE-2023-20126) Help Net Security
Cisco has revealed the existence of a critical vulnerability (CVE-2023-20126) in the web-based management interface of Cisco SPA112 2-Port Phone Adapters. The adapters are widely used to integrate analog phones into VoIP networks without the need for an upgrade. About the vulnerability (CVE-2023-20126) CVE-2023-20126 can be exploited without prior authentication. This vulnerability is due to a missing authentication process within the firmware upgrade function. An attacker could exploit this vulnerability by upgrading an affected device More
The post Critical RCE vulnerability in Cisco phone adapters, no update available (CVE-2023-20126) appeared first on Help Net Security.
19:10
U.S. Hits Z-Library With New Domain Name Seizures TorrentFreak
 By providing free access to millions of books,
Z-Library became the go-to site for many readers in recent
years.
By providing free access to millions of books,
Z-Library became the go-to site for many readers in recent
years.
Z-Librarys very existence was put to the test last November when U.S. law enforcement agencies seized over 200 domain names connected to the site. Two alleged Z-Library operators from Russia were arrested in Argentina as part of a criminal investigation.
Down, Not Out
Despite the gravity of the copyright infringement accusations and pending extraditions, Z-Library never went completely offline. The site continued to operate on the dark web, offering millions of pirated books and articles as it did before.
The site eventually returned on the clearnet too, providing a unique subdomain for all Z-Library users. The idea behind this move was to make it more difficult for law enforcement to take down the whole operation all at once.
This setup worked well for a few months allowing the remaining Z-Library team to focus on expanding the community. Starting this week, however, legal trouble hit Z-Library once again when the U.S. Department of Justice carried out a new round of domain name seizures.
New Domain Seizures
A few days ago we noticed that several domain names associated with the shadow library had stopped working. Instead, users were directed to a seizure banner which most of the sites users are familiar with by now.
The first seized domain we spotted was b-ok.lat. It previously redirected to the main login portal at singlelogin.me which was still operational at the time. Soon after, however, these domain names were seized by U.S. authorities along with booksc.me and b-ok.as.
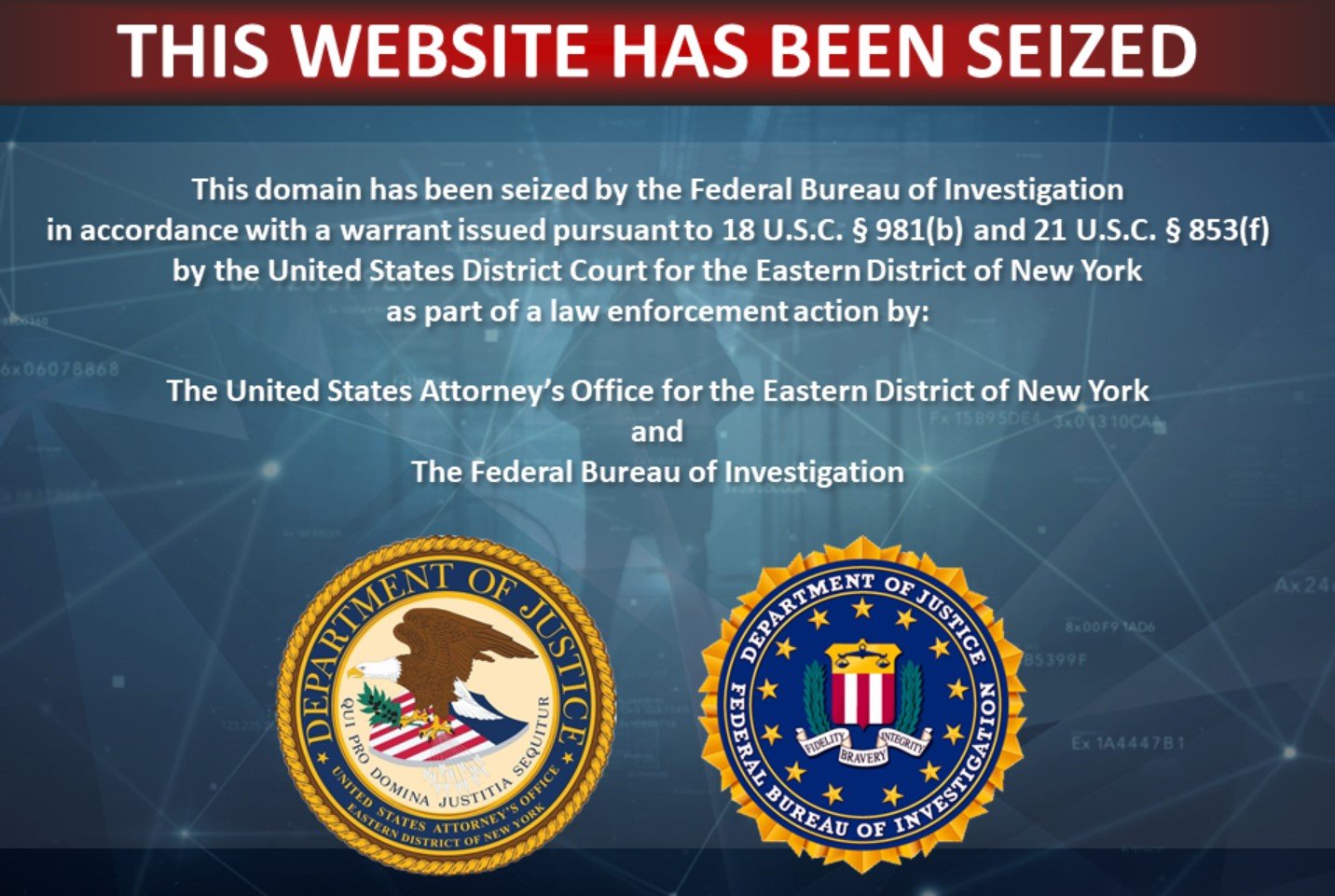
The seized domains now point to the name servers of seizedservers.com which are controlled by the U.S. Government. Since Z-Library has domains at multiple registries, its possible that more seizur...
18:32
IRC Proceedings: Thursday, May 04, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-040523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-040523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-040523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-040523.gmi
Over HTTP:
|
... |
18:31
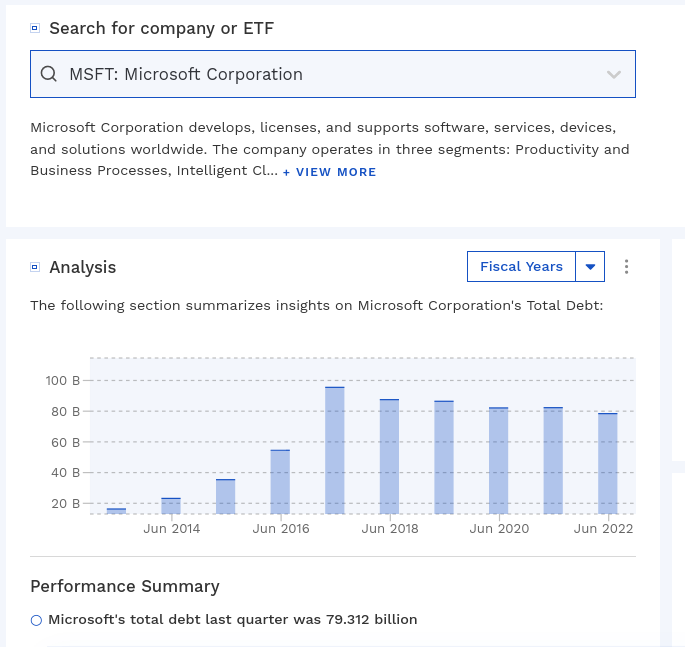
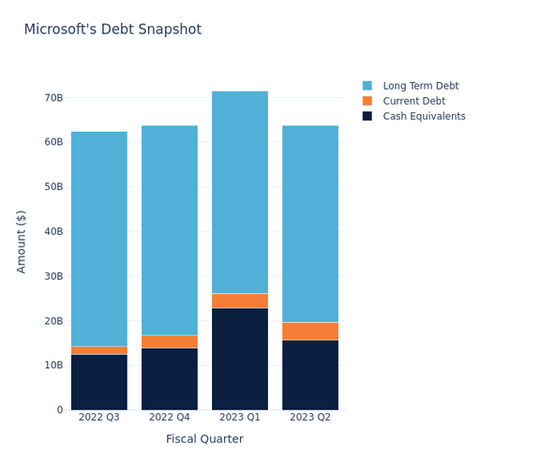
Microsofts Total Debt (Current and Longterm) is About 80 Billion Dollars Techrights
Summary: Dont be too baffled by very large-scale Microsoft layoffs (a lot more were laid off than the media admits*) and endless vapourware, even attempts to take over other companies (maybe just to offload debt before insolvency**)
Microsoft, the worlds most valuable company, declared a profit of $4.5 billion in 1998; when the cost of options awarded that year, plus the change in the value of outstanding options, is deducted, the firm made a loss of $18 billion, according to Smithers.
The Economist, 1999
_____
* Number of rounds of layoffs seems to be two or
three so far this year; its rather clear, based on scattered
reports, that it is multiple rounds and not just a one-off
in January.
** To quote a Techrights associate: Its important to drive home the point that Microsoft has hidden an $18 billion loss in 1999 and probably also a running loss ever since with the help of the occasional bailout and offloading debt onto newly-acquired victims.
18:24
18:23
Sensitive data is being leaked from servers running Salesforce software Lifeboat News: The Blog
Servers running software sold by Salesforce are leaking sensitive data managed by government agencies, banks, and other organizations, according to a post published Friday by KrebsOnSecurity.
At least five separate sites run by the state of Vermont permitted access to sensitive data to anyone, Brian Krebs reported. The states Pandemic Unemployment Assistance program was among those affected. It exposed applicants full names, Social Security numbers, addresses, phone numbers, email addresses, and bank account numbers. Like the other organizations providing public access to private data, Vermont used Salesforce Community, a cloud-based software product designed to make it easy for organizations to quickly create websites.
Another affected Salesforce customer was Columbus, Ohio-based Huntington Bank. It recently acquired TCF Bank, which used Salesforce Community to process commercial loans. Data fields exposed included names, addresses, Social Security numbers, titles, federal IDs, IP addresses, average monthly payrolls, and loan amounts.
18:23
Twinning? Two Side-by-Side Mansions in Florida Built for Twin Brothers Just Listed for $54 Million Lifeboat News: The Blog
Located in Fort Lauderdale, the French country-style homes have their own pools, but share the bass-stocked lake between them.
18:23
Its the End of a World as We Know It Lifeboat News: The Blog
Astronomers spotted a dying star swallowing a large planet, a discovery that fills in a missing link in understanding the fates of Earth and many other planets.
18:23
Life After Death? Cryonicists Try To Defy Mortality By Freezing Bodies Lifeboat News: The Blog
Cryonicists hope that modern technology will one day bring frozen bodies back from the dead. But how realistic is a second life after a deep freeze?
18:23
AI could run a million microbial experiments per year, says study Lifeboat News: The Blog

An artificial intelligence system enables robots to conduct autonomous scientific experimentsas many as 10,000 per daypotentially driving a drastic leap forward in the pace of discovery in areas from medicine to agriculture to environmental science.
Reported today in Nature Microbiology, the research was led by a professor now at the University of Michigan.
That artificial intelligence platform, dubbed BacterAI, mapped the metabolism of two microbes associated with oral health with no baseline information to start with. Bacteria consume some combination of the 20 amino acids needed to support life, but each species requires specific nutrients to grow. The U-M team wanted to know what amino acids are needed by the beneficial microbes in our mouths so they can promote their growth.
18:23
DreamFace: Progressive Generation of Animatable 3D Faces under Text Guidance Lifeboat News: The Blog

Emerging Metaverse applications demand accessible, accurate, and easy-to-use tools for 3D digital human creations in order to depict different cultures and societies as if in the physical world. Recent large-scale vision-language advances pave the way to for novices to conveniently customize 3D content. However, the generated CG-friendly assets still cannot represent the desired facial traits for human characteristics. In this paper, we present DreamFace, a progressive scheme to generate personalized 3D faces under text guidance. It enables layman users to naturally customize 3D facial assets that are compatible with CG pipelines, with desired shapes, textures, and fine-grained animation capabilities. From a text input to describe the facial traits, we first introduce a coarse-to-fine scheme to generate the neutral facial geometry with a unified topology. We employ a selection strategy in the CLIP embedding space to generate coarse geometry, and subsequently optimize both the details displacements and normals using Score Distillation Sampling from generic Latent Diffusion Model. Then, for neutral appearance generation, we introduce a dual-path mechanism, which combines the generic LDM with a novel texture LDM to ensure both the diversity and textural specification in the UV space. We also employ a two-stage optimization to perform SDS in both the latent and image spaces to significantly provides compact priors for fine-grained synthesis. Our generated neutral assets naturally support blendshapes-based facial animations. We further improve the animation ability with personalized deformation characteristics by learning the universal expression prior using the cross-identity hypernetwork, and a neural facial tracker for video input. Extensive qualitative and quantitative experiments validate the effectiveness and generalizability of DreamFace. Notably, DreamFace can generate of realistic 3D facial assets with physically-based rendering quality and rich animation ability from video footage, even for fashion icons or exotic characters in cartoons and fiction movies.
18:08
Windows Down Below 55% in Laptops/Desktops Operating Systems Market Share Worldwide, Says StatCounter Techrights
Summary: StatCounter, which Microsoft fancies citing in particular contexts, shows Unknown replacing Windows this month and last month; aside from being a sign of unreliability, it serves to show misclassification (Unknown can mean just about anything; its not Windows)
18:00
Edgecore Networks and Wedge Networks partner to offer next-generation network security Help Net Security
Edgecore Networks has partnered with Wedge Networks to offer a next-generation network security solution to its customers. Wedge Networks Wedge Cloud Network Defense (WedgeCND), a cloud-managed security service designed to provide comprehensive security protection, is now available as an add-on for Edgecores Wi-Fi 6 series access points through its ecCLOUD cloud controller. This partnership offers Edgecores customers access to a range of optimized Security-as-a-Service (SECaaS) features seamlessly integrated into their networks, providing ubiquitous Wi-Fi network More
The post Edgecore Networks and Wedge Networks partner to offer next-generation network security appeared first on Help Net Security.
18:00
CNC Feeds and Speeds, Explained as a First-Timer Hackaday

If youve ever looked into CNC cutting tools, youve probably heard the term feeds and speeds. It refers to choosing the speed at which to spin the cutting tool, and how fast to plow it into the material being cut. Theyre important to get right, and some of the reasons arent obvious. This led [Callan Bryant] to share his learned insights as a first-timer. It turns out there are excellent (and somewhat non-intuitive) reasons not to simply guess at the correct values!
17:58
Stallman (RMS) Support Site Adds RSS Feed and More Words of Support for RMS Techrights
After almost a year stallmansupport.org is back to
being regularly updated!
Summary: A new syndication (XML/RSS)
feed has been added to this
page at stallmansupport.org a site that RMS
himself keeps endorsing in
his public talks; we need to highlight some things that,
whenever quoted, trigger the cancel mob once more (because they
strike a nerve)
THE old open letter (2+ years old! Time flies!) against RMS may seem unimportant, but the cancel mob is still at it, as we shall show in the coming few days, maybe as early as this weekend. Well write about Amendment 130 and note that opponents have now dusted off the term freeware after a very long hiatus to try to increase confusion about freedom and specifically about software freedom, as an associate notes. Weve just mentioned that in passing, showing yesterdays words from a Microsoft front group (OSI today is not what it used to be).
Weve meanwhile noticed that software freedom-hostile sick-minded online bullies very strongly dislike the site. They get enraged when the site is mentioned or quoted. Hence, well reproduce the new bits here.
The latest one is a blog post by Sylvia Paull. She wrote:
Its been more than two years since MacArthur Fellow and founder of the Free Software Foundation Richard Stallman was forced to resign from his positions at MIT and the FSF....
17:53
Rover Spots Possible Evidence of Liquid Water on Modern Mars SoylentNews
China's Zhurong rover has found evidence of liquid water on present-day Mars, according to a team that reviewed data from the rover's cameras.
To be clear, the team claims they've collected evidence of liquid water on Marsnot the liquid water itself. Water was once plentiful on Mars. NASA, the European Space Agency, and others have found a plethora of evidence for ancient water on the planet; it's proving the recent presence of water that's trickier.
[...] "According to the measured meteorological data by Zhurong and other Mars rovers, we inferred that these dune surface characteristics were related to the involvement of liquid saline water formed by the subsequent melting of frost/snow falling on the salt-containing dune surfaces when cooling occurs," Qin Xiaoguang, a geophysicist at the Chinese Academy of Sciences, said in an academy release.
Mars' atmosphere is only 1% the density of Earth's, making it difficult for liquid water to exist on Mars today. But frozen water crops up regularly, in the form of possible subsurface lakes and even relict glaciers on the planet's surface.
[...] Based on the age of the dunes, they may have been hydrated when water vapor moved from the planet's polar ice sheet to its equator, making the planet's lower latitudes more humid. Like the discovery of the glacial remnants on Mars, these findings boost humankind's hopes for water's ability to persist near Mars' relatively balmy equator, where potential human missions would be based.
Journal Reference:
Xiaoguang Qin, Xin Ren, Xu Wang, et al., Modern water
at low latitudes on Mars: Potential evidence from dune surfaces
[open], Sci. Adv., 2023. DOI: 10.1126/sciadv.add8868
Read more of this story at SoylentNews.
17:45
OneTrusts AI-driven document classification enhances data discovery and governance Help Net Security
OneTrust announces AI-driven document classification to help organizations more accurately and completely identify and classify unstructured data and automatically apply governance and protection policies. An organizations data is what fuels innovation and gives them a competitive edge, said Blake Brannon, Chief Product and Strategy Officer at OneTrust. Yet, data sprawl and lack of visibility into where sensitive data lives across the organization can quickly turn that data into an Achilles heel, risking the financial and More
The post OneTrusts AI-driven document classification enhances data discovery and governance appeared first on Help Net Security.
17:21
Fleckpe Android Malware Sneaks onto Google Play Store with Over 620,000 Downloads The Hacker News
A new Android subscription malware named Fleckpe has been unearthed on the Google Play Store, amassing more than 620,000 downloads in total since 2022. Kaspersky, which identified 11 apps on the official app storefront, said the malware masqueraded as legitimate photo editing apps, camera, and smartphone wallpaper packs. The apps have since been taken down. The operation primarily targets users
17:00
"We've Never Seen Such A Dramatic Shift": Bud Light Hopes New Ad Blitz Can Overcome Corporate Suicide Terra Forming Terra
How ChatGPT and Other LLMs Workand Where They Could Go Next Terra Forming Terra
Grooming the forests Terra Forming Terra
We have been addressing this problem for almost twenty years and we have a simple new insight in terms of mechanization.
We have already come to understand that a working woodlot demands proactive grooming and rotational grazing for optimal productivity. This can also be achieved once your forest becomes a climax forest, but that is centuries away and then, not so wonderful in terms of economic productivity.
Proactive grooming requires knocking down branches to above your head and maintaining an open spacing to allow at least 60 percent sunlight gettting to the forest floor allowing surface vegetation as animal fodder for a likely flock of sheep and perhaps cattle.
This is pretty good and somewhat describes our orchard practise. The difficulty is the next fifty feet or so. what I just figured out is that we can dfrive up to a given stem and use a clamping device to grasp the trunk an use that to stabalize the 0machine itself. We can then use a bucket on an hydraulic arm to move up the tree without fear of toppling over. This is huge.
If we are working with pine trees in the boreal forest, we can immediately drop the lowest ring of branches and open a clear path on one side to the tree top itself. At tree top we can easily harvest mature pine cones into a burlap sack to finish the task. If this is done every year we collect an annual pine cone harvest and also produce a clear stem that only has knots in the six inch core. The final stem will be robust and as tall as any mature pine tree orr any other conifer as well that we chose to work this way.
Branches on the ground can be chipped the next spring if we care though grazers will break them up as well.
If we are working with fruit and nut trees, we are no longer restricting ourselves to dwarf root stalks and we will care about the end quali...
Our particle ocean Terra Forming Terra
NNP neutral neutron pair
NEeP neutral electron pair
Here is what seems impossible, but our gravity wells actually pack up our NNPs. Yet it is plausible that they are actively formed from the general photon flux all through space and that surely includes inter galactic space. The actual packing takes place right here.
Natural spacing for these NNPs will be much closer that our comparable elements and hydrogen. Afte all those have electron orbitals and this scopes out its own significant volume. At the same time a conglomeration of NNPs able to say decay into say silica will be possibly smaller that the descendent element. At the same time, they are sticky but at a very low level as compared to out elements which we experience.
we live in an ocean of these NNPs and they all live in another ocean of NEPs (neutral electron pairs) scalled way smaller and of course an ocean of neutral neutrinos as well all scaled deeper still. None of these are particularly sticky, but will line up and then lock up if not disturbed by a photon.
The key thing to understand is that all matter that we detect is a decay product of some sort and the process is glacial. We actually knew that from the neutron neutron to neutron proton decay that forms free hydrogen. The half life is huge but still real and that matches the age of our Galaxy as well.
Cloud cosmology is able to construct step by step from the act of creation to the natural production of an NNP from NEPs From NNePs. they are acting along axis to be sticky. Yet with over two thousand axis, a NNP can be easily seen as a semi continous field that may be modeled by field equations. I should also mention that an axis has 3d dimensionality because infinity is empirical.
What is clear now is that the universe we percieve can only exist as a decay product from the third stage of matter.
it is only at this level that we get a consistent material universe that we can work with. A further though is that NEPs decay as well but produce cosmic rays...
16:58
Duly Noted: Microsoft Front Group OSI (Nowadays Funded to Lobby for Microsofts Proprietary Agenda) Wants Us to Stop Talking About Freedom Techrights
Yes, lets focus on code available alone, hosted by Microsofts proprietary prison (notice how OSI is paid by GitHub to promote GitHub, rather than ask people to leave it)

OSI chief Stefano Maffulli yesterday
Citing this from Simon Phipps:

2 years ago Simon Phipps (Former OSI President) signed a defamatory
letter calling for the removal of the father of Free Software
Summary: The OSI is deeply compromised; If they bothered talking to people (and also politicians) about Freedom instead of Open Source, wed actually get somewhere (other than Microsofts GitHub, which is proprietary)
The OSI wont speak for us, so make sure you do (Gemini address).
16:32
Links 05/05/2023: Years After Dieselgate (Proprietary Software Abuse) Audi CEO Rupert Stadler Pleads Guilty Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
-
GNU/Linux
-
Audiocasts/Shows
-
Jupiter Broadcasting Linux Action News 291
The results from the recent HDR Hackfest, Mozillas new acquisition, and the concerning crack down on free software encryption.
-
-
Kernel Space
-
LWN ...
-
-
16:25
Gemini Links 04/05/2023: New Arrivals and When Not to Use the Newest Frameworks Techrights
-
Gemini* and Gopher
-
Personal
-
I me mine
But as with far too many social critiques I read, I dont see any of those todos addressing what I believe to be root cause.
I suspect what I believe to be root cause is beyond what most (read: all) egos could agree with.
And thats because root cause is ego, i.e. the I thought from which all other conceptuality (aka modeling) emanates from slash revolves around.
-
Be kind
I watched the movie everything everywhere all the time yesterday and thoroughly enjoyed it! It was fun and quirky with amazingly choreographed martial art fights and at the same time deeply moving.
Without giving any spoilers, for me, the point that it was trying to make is that nothing matters and accepting that reality is freeing and allows one to actually live better and be kind.
It definitely worked in the movie but I find it lacking in the real world. Im in a moment in my life at which I need to do things because paying bills and keeping a roof over my familys head kind of matters and being told nothing matters, just be kind is sort of Idk, annoying?
-
The convergence of contemporary fiction
hi emilyehere is my long promised, long deferred post. first, im going to post the section in mark mcgurls book everything and less: the novel in the age of amazon that talks about megan boyles liveblog:
The convergence of contemporary fiction and social media is also visible in some works of the small-press avant-garde. As what David Wells aptly calls a fiction of the Interneta representation of an infinitely extending and seemingly available world, Megan Boyles Liveblog: A Novel (2018) presents a less pulpy but no less symptomatic instance.24 In the tradition of Andy Warhols a: a Novel (1968) and Goldsmiths Soliloquy (2001), Boyles project began as an experiment in exhaustive self-surveillance, this time conceived as auto-therapy. Keeping more or less co...
-
-
16:22
May 2023 Patch Tuesday forecast: Dealing with End-of-Support (EOS) Help Net Security
The April Patch Tuesday releases were unusual because we saw a whopping 62 vulnerabilities addressed in the Microsoft Server 2012 KBs. Granted there was a lot of overlap with the CVEs addressed in Windows 10 and 11, but compared to the typical 30-40 CVEs addressed in the months prior, this number was unusually aggressive. Is this a coincidence or is there a push to prepare Server 2012 for its upcoming EOS in October? There are More
The post May 2023 Patch Tuesday forecast: Dealing with End-of-Support (EOS) appeared first on Help Net Security.
16:01
Lean in to the Linux Foundations Software Developer Diversity and Inclusion (SDDI) Project Linux.com

Read the original blog at Read More
The post Lean in to the Linux Foundations Software Developer Diversity and Inclusion (SDDI) Project appeared first on Linux.com.
15:53
[Meme] Royally Screwed by the System Techrights
Chuck is chucking money away while some people struggle to buy food
The police will be very busy protecting an old millionaire.
Summary: 14 days ago (yes, 2 weeks) I reported the crimes of Sirius Open Source to the police (Im not the only victim of these crimes); still waiting for the police to respond in any concrete way
15:42
OpenBGPD 8.0 released OpenBSD Journal
From: Claudio Jeker <claudio () openbsd ! org> Date: Thu, 04 May 2023 16:24:30 +0000 To: openbsd-announce Subject: OpenBGPD 8.0 released We have released OpenBGPD 8.0, which will be arriving in the OpenBGPD directory of your local OpenBSD mirror soon.
15:40
A Fortnight of Police Inaction Makes It Look like the British Government is on the Side of Serial Fraudsters schestowitz.com
Sunak already has his own share of financial scandals (his wife also)

The Prime Minister promises to take the fight to the fraudsters by
blocking scams at the source, says
Which? this week
Summary: The crimes of the rich (or white-collar crimes) are tolerated by our administration; not enough resources are devoted to tackling the most costly crimes, as the case of Sirius fraud shows (Im a victim of this crime, as are my former colleagues)
ALMOST 14 days ago (2 weeks) I reported fraud to the police and got a reference number for the investigation. In less than 24 hours itll be officially a fortnight and they didnt bother to contact me, follow up etc.
A saner system would do a preliminary check, freeze the assets of the company to recover stolen money, then pursue prosecution based on the evidence. In light of the impending coronation ceremony, this matters even more. They apparently have plenty of money/budget (the media says 250m) to protect a person in his 70s throwing a party for himself, but not enough to tackle actual crime (rather than hypothetical or a mere risk).
If they dont respond, said a colleague about Sirius Open Source last month (he too was plundered/defrauded), I should be able to make a small claims court claim online. I have proof from standard life saying I was not on the scheme and proof they took deductions from my pay, and a copy of the letter outlining the scheme I should have been on so should be reasonably straight forward.
I can do the same. But the problem is that the company is in hiding. Downsides of such a course of action:
- they will dodge the legal process.
- we need to hold them criminally accountable (this is jailable offense).
- the company will claim to be broke, unable to recover the money.
The other victim asked:...
15:36
Holding Criminals Accountable Part IV British Prime Minister Launches Crackdown on Fraud, So Now Prove It Techrights
He already has his own share of financial scandals (his wife also)
Series parts:
- Holding Criminals Accountable Part I Sirius Crimes Reported to British Authorities, Formally Registered With References (Many Victims), Heres What It Means and What Happens Next
- Holding Criminals Accountable Part II Still No Action From Action Fraud
- Holding Criminals Accountable Part III Why Police Action is the Only Option Now
- YOU ARE HERE British Prime Minister Launches Crackdown on Fraud, So Now Prove It

The Prime Minister promises to take the fight to the fraudsters by
blocking scams at the source, says
Which? this week
Summary: The crimes of the rich (or white-collar crimes) are tolerated by our administration; not enough resources are devoted to tackling the most costly crimes, as the case of Sirius fraud shows (Im a victim of this crime, as are my former colleagues)
ALMOST 14 days ago (2 weeks) I reported fraud to the police and got a reference number for the investigation. In less than 24 hours itll be officially a fortnight and they didnt bother to contact me, follow up etc.
A saner system would do a preliminary check, freeze the assets of the company to recover stolen money, then pursue prosecution based on the evidence. In light of the impending coronation ceremony, this matters even more. They apparently have plenty of money/budget (the media says 250m) to protect a person in his 70s throwing a party for himself, but not enough to...
15:16
Cisco Warns of Vulnerability in Popular Phone Adapter, Urges Migration to Newer Model The Hacker News
Cisco has warned of a critical security flaw in SPA112 2-Port Phone Adapters that it said could be exploited by a remote attacker to execute arbitrary code on affected devices. The issue, tracked as CVE-2023-20126, is rated 9.8 out of a maximum of 10 on the CVSS scoring system. The company credited Catalpa of DBappSecurity for reporting the shortcoming. The product in question makes it possible
15:08
Samsung to Pay Out $303M for Memory Patent Infringement SoylentNews
Samsung to pay out $303M for memory patent infringement:
Samsung Electronics has been stung for more than $303 million in a patent infringement case brought by US memory company Netlist.
Netlist, headquartered in Irvine, California, styles itself as a provider of high-performance modular memory subsystems. The company initially filed a complaint that Samsung had infringed on three of its patents, later amended to six [PDF]. Following a six-day trial, the jury found for Netlist in five of these and awarded a total of $303,150,000 in damages.
[...] The patents appear to apply to various aspects of DDR memory modules. According to reports, Samsung's representatives had argued that Netlist's patents were invalid because they were already covered by existing technology and that its own memory chips did not function in the same way as described by the patents, but this clearly did not sway the jurors.
[...] The company states that Samsung and Netlist were initially partners under a 2015 Joint Development and License Agreement (JDLA), which granted Samsung a five-year paid-up license to Netlist's patents.
[...] Under the terms of the agreement, Samsung was to supply Netlist certain memory products at competitive prices, but Netlist claimed Samsung repeatedly failed to honor these promises. As a result, Netlist claims, it terminated the JDLA on July 15, 2020.
Netlist alleged in its court filing that Samsung has continued to make and sell memory products "with materially the same structures" as those referenced in the patents, despite the termination of the agreement.
Read more of this story at SoylentNews.
15:00
NVIDIA Jetson Powers Real-Time Iron Man HUD Hackaday

If you could recreate any of the capabilities of Tony Starks Iron Man suit in real life, it would probably be the ability to fly, the super strength, or maybe even the palm-mounted lasers that can cut through whatever obstacle is in your path. But lets be real, all that stuff is way too hard to try and pull off. Plus youll probably just end up accidentally killing yourself in the backyard.
But judging by the videos hes been posting, [Kris Kersey] is doing one hell of a job creating a functional heads-up display (HUD) similar to the one Tony uses in the films. Hes even building it into a 3D printed Iron Man helmet, with the NVIDIA Jetson board thats powering the show inside a chest-mounted Arc Reactor. He goes into a bit more detail about the project and his goals in an interview recently published on NVIDIAs own blog.
14:30
New infosec products of the week: May 5, 2023 Help Net Security
Heres a look at the most interesting products from the past week, featuring releases from Dashlane, Immersive Labs, Intruder, Private AI, Vanta, and Veza. Immersive Labs Resilience Score strengthens executive decision making in cyber crises Immersive Labs Resilience Score helps organizations identify weaknesses in their teams cyber capabilities, address skills gaps to prevent or mitigate damage to their revenues and brand reputations, and contribute to the factors that can lower insurance premiums. Intruder launches continuous More
The post New infosec products of the week: May 5, 2023 appeared first on Help Net Security.
14:00
Universal Data Permissions Scanner: Open-source tool to overcome data authorization blindspots Help Net Security
Satori released Universal Data Permissions Scanner, a free, open-source tool that enables companies to understand which employees have access to what data, reducing the risks associated with overprivileged or unauthorized users and streamlining compliance reporting. Who has access to what data? User authorization for data access is complex. The answer to the question who has access to what data? is often unclear because of complex role hierarchies, different authorization models used for different technologies, and More
The post Universal Data Permissions Scanner: Open-source tool to overcome data authorization blindspots appeared first on Help Net Security.
13:30
Organizations brace for cyber attacks despite improved preparedness Help Net Security
Cyber-risk levels have improved from elevated to moderate for the first time, but insiders represent a persistent threat for global organizations, according to Trend Micro. Jon Clay, VP of threat intelligence at Trend Micro: For the first time since weve been running these surveys, we saw the global cyber risk index not only improve but move into positive territory at +0.01. It means that organizations may be taking steps to improve their cyber-preparedness. There is More
The post Organizations brace for cyber attacks despite improved preparedness appeared first on Help Net Security.
12:22
Amazon Halo is Dead, and It's a Bigger Deal Than You Think SoylentNews
Yet another piece of hardware becomes junk
Amazon Halo is dead, and it's a bigger deal than you think:
Does paying a subscription fee to own and use a piece of hardware feel reassuring? Does that monthly commitment make you feel safe, as the company has income past any original purchase, encouraging it to support and update the product so it never becomes useless?
As Amazon's decision to end support for its Halo line of health products proves, it absolutely shouldn't. What it should do, however, is make you seriously consider whether any subscription-based health and fitness product is a good idea at all.
On April 26, Amazon discontinued its Halo product line, which consists of the Halo Band, Halo View, and the Halo Rise. The app will stop working on August 1, when the hardware will also cease to provide any functionality. It's not good for owners and also bad news for staff at Amazon working on the projects, as many will lose their jobs.
[...] Halo is now a failure, and regardless of why it has happened, it's one that the subscription model couldn't help save. The Halo products weren't the best of their type you could get, but Amazon's massive reach, brand recognition, and willingness of its core customers to pay a subscription for its services should have helped mitigate at least some of that issue. But Amazon isn't going to discontinue successful product lines that make it money it's going to get rid of the ones that do the opposite. The subscription fee absolutely wasn't a lifeline for Halo and provided no protection to you as a consumer at all.
Read more of this story at SoylentNews.
12:00
Hacking Hue Lightbulbs Hackaday

What do you do with a Hue smart lightbulb? Well, if you are [Chris Greening], you take it apart and get hacking. If you ever wondered whats inside, the teardown is pretty good, and you can also watch the video below. The potting compound, however, makes a mess.
Once you get the potting undone, there are three PCBs: an LED carrier, a power supply, and a logic board. The arrangement of the LEDs is a bit confusing, but [Chris] explains it along with providing schematics for all of the boards.
The odd LED arrangement allows the logic board to short out banks of LEDs. The next step was to hijack the RGB signals to allow an external microcontroller to take charge of the bulb. One LED driver chip drives everything. Shorting out banks with a cheap MOSFET allows one chip to drive the LEDs in multiple colors.
This is an interesting look inside a production smart bulb. We arent sure wed really want to reuse one of these, but maybe if you had a bad power board, it would be better than trashing the relatively expensive bulbs.
Weve seen other lights hacked to work with Hue. You can even hack together your own bridge if you like.
...
11:50
$10M Is Yours If You Can Get This Guy to Leave Russia Krebs on Security
The U.S. government this week put a $10 million bounty on a Russian man who for the past 18 years operated Try2Check, one of the cybercrime undergrounds most trusted services for checking the validity of stolen credit card data. U.S. authorities say 43-year-old Denis Kulkovs card-checking service made him at least $18 million, which he used to buy a Ferrari, Land Rover, and other luxury items.

Denis Kulkov, a.k.a. Nordex, in his Ferrari. Image: USDOJ.
Launched in 2005, Try2Check soon was processing more than a million card-checking transactions per month charging 20 cents per transaction. Cybercriminals turned to services like this after purchasing stolen credit card data from an underground shop, with an eye toward minimizing the number of cards that are inactive by the time they are put to criminal use.
Try2Check was so reliable that it eventually became the official card-checking service for some of the undergrounds most bustling crime bazaars, including Vault Market, Unicc, and Jokers Stash. Customers of these carding shops who chose to use the shops built-in (but a-la-carte) card checking service from Try2Check could expect automatic refunds on any cards that were found to be inactive or canceled at the time of purchase.
Many established stolen card shops will allow customers to request refunds on dead cards based on official reports from trusted third-party checking services. But in general, the bigger shops have steered customers toward using their own white-labeled disputes over canceled cards.
On Wednesday, May 3, Try2Checks websites were replaced with a domain seizure notice from the U.S. Secret Service and U.S. Department of Justice, as prosecutors in the Eastern District of New York unsealed an indictment and search warrant naming Denis...
10:06
Re: Perl's HTTP::Tiny has insecure TLS cert default, affecting CPAN.pm and other modules Open Source Security
Posted by Steffen Nurpmeso on May 04
David A. Wheeler wrote in<C2F1E269-0FD7-45A2-A0E1-F1AC29383C09 () dwheeler com>:
|
|> On May 4, 2023, at 2:23 PM, Rainer Canavan <rainer.canavan () avenga com> \
|> wrote:
|> I'd suspect that the issue in
|> HTTP::Tiny would end up DISPUTED, since not validating TLS names is
|> not the generally expected behavior, although it is documented (in
|> bold no less).
|
|I would also expect it to be at most...
10:00
HPR3850: New Mexico 2 Hacker Public Radio
We finished our stay in Anthony with a Saturday trip into Las Cruces to see the local market and the museums, more hiking, and a trip to see Native American Petroglyphs. We also went into El Paso to check out the zoo. It was fine, but we confirmed that we don't really like going into El Paso. We are not much on driving in big cities any longer, particularly in a big truck. Then it was time to move on to our next stop, Presidio, Texas. This is so close to the border that a 5 minute walk takes you to the Rio Grande. Links: https://flic.kr/s/aHBqjzL5vB https://flic.kr/s/aHBqjzL5VY https://flic.kr/s/aHBqjzL7XD https://flic.kr/s/aHBqjzL9jQ https://flic.kr/s/aHBqjzL8cZ https://flic.kr/s/aHBqjzLc5f https://www.palain.com/travel/new-mexico-2/
09:37
Universe-mapping Euclid Satellite Arrives in US SoylentNews
It's been a decade since it was announced, but the Euclid mission to build a 3D map of the universe is finally getting close to launch with the spacecraft landing in Florida ahead of an expected July liftoff.
The Euclid mission will send the eponymous probe to Earth-Sun Lagrange point 2 the same spot as NASA's James Webb Telescope, where it will observe more than a third of the sky and detect galaxies as distant as 10 billion light years away.
[...] The ultimate goal of the European Space Agency mission which has enjoyed important contributions from NASA is to build a 3D map of the large-scale structure of the universe to help scientists better understand the nature of dark matter and dark energy, which make up more than 95 percent of the mass and energy of the universe. Scientists with the European Space Agency also hope Euclid will help them better understand how the expansion of the universe has changed over time, and whether we have a complete understanding of gravity.
"No test of the [general theory of relativity] has been made with high precision over the large distances and times that Euclid will cover. This way, Euclid will reveal if general relativity breaks down at the largest scales. If it does, physicists will need to go back to the drawing board," ESA said.
[...] If everything in the clean room goes to plan, Euclid will then be mounted atop its Falcon 9 ride to begin the final leg of its journey. If the James Webb's trip to L2 is any indicator, Euclid should reach its destination in around 30 days.
Read more of this story at SoylentNews.
08:13
PSA. Dont share your password in your apps release notes Graham Cluley
Cinema chain Odeon may have shared more information than it intended in the release notes accompanying its latest iOS app update.
08:11
CVE-2021-40331: Apache Ranger Hive Plugin: Any user with SELECT privilege on a database can alter the ownership of the table in Hive when Apache Ranger Hive Plugin is enabled Open Source Security
Posted by Ramesh Mani on May 04
Severity: criticalAffected versions:
- Apache Ranger Hive Plugin 2.0.0 through 2.3.0
Description:
Incorrect Permission Assignment for Critical Resource vulnerability in Apache Software Foundation Apache Ranger Hive
Plugin.This issue affects Apache Ranger Hive Plugin: from 2.0.0 through 2.3.0.
This issue is being tracked as RANGER-3474 RANGER-3357
References:
https://ranger.apache.org/
https://www.cve.org/CVERecord?id=CVE-2021-40331...
08:09
CVE-2022-45048: Apache Ranger: code execution vulnerability in policy expressions Open Source Security
Posted by Madhan Neethiraj on May 04
Affected versions:- Apache Ranger 2.3.0
Description:
Authenticated users with appropriate privileges can create policies having expressions that can exploit code execution
vulnerability. This issue affects Apache Ranger: 2.3.0.
Credit:
g1831767442 () 163 com (finder)
References:
https://ranger.apache.org/
https://www.cve.org/CVERecord?id=CVE-2022-45048
07:49
Twitter's e2ee DMs are better than nothing Matthew Garrett
Elon Musk appeared on an interview with Tucker Carlson last
month, with one of the topics being the fact that Twitter could be
legally compelled to hand over users' direct messages to government
agencies since they're held on Twitter's servers and aren't
encrypted. Elon talked about how they were in the process of
implementing proper encryption for DMs that would prevent this -
"You could put a gun to my head and I couldn't tell you. That's how
it should be."
tl;dr - in the current implementation, while Twitter could
subvert the end-to-end nature of the encryption, it could not do so
without users being notified. If any user involved in a
conversation were to ignore that notification, all
messages in that conversation (including ones sent in the past)
could then be decrypted. This isn't ideal, but it still seems like
an improvement over having no encryption at all. More technical
discussion follows.
For context: all information about Twitter's implementation here
Android client and 9.56.1 of the iOS client (the current versions
at time of writing), and the feature hasn't yet launched. While
it's certainly possible that there could be major changes in the
protocol between now launch, Elon has asserted that they plan to
launch the feature this week so it's plausible that this reflects
what'll ship.
For it to be impossible for Twitter to read DMs, they need to not
only be encrypted, they need to be encrypted with a key that's not
available to Twitter. This is what's referred to as "end-to-end
encryption", or e2ee - it means that the only components in the
communication chain that have access to the unencrypted data are
the endpoints. Even if the message passes through other systems
(and even if it's stored on other systems), those systems
do not have access to the keys that would be needed to decrypt the
data.
End-to-end encrypted messengers were initially popularised by
Signal, but the Signal protocol
has since been incorporated into WhatsApp and is probably much more
widely used there. Millions of people per day are sending messages
to each other that pass through servers controlled by third
parties, but those third parties are completely unable to read the
contents of those messages. This is the scenario that Elon
described, where there's no degree of compulsion that could cause
the people relaying messages to and from people to decrypt those
messages afterwards.
But for this to be possible, both ends of the communication need to
be able to encrypt messages in a way the other end can decrypt.
This is usually performed using AES,
a well-studied encryption algorithm with no known significant
weaknesses. AES is a form of what's referred to as a symmetric
encryption, o...
07:00
Intel Posts New Linux Patches For Cluster Scheduling With Hybrid CPUs Phoronix
A new set of patches were posted today to enable cluster scheduling for x86 hybrid CPUs. In turn thos latest attempt at cluster scheduling for modern Core CPUs of Alder Lake and newer is yielding some small performance benefits over the current code...
06:54
A Bug Fix in the 8086 Microprocessor, Revealed in the Die's Silicon SoylentNews
https://www.righto.com/2022/11/a-bug-fix-in-8086-microprocessor.html
While reverse-engineering the 8086 from die photos, a particular circuit caught my eye because its physical layout on the die didn't match the surrounding circuitry. This circuit turns out to implement special functionality for a couple of instructions, subtlely changing the way they interacted with interrupts. Some web searching revealed that this behavior was changed by Intel in 1978 to fix a problem with early versions of the 8086 chip. By studying the die, we can get an idea of how Intel dealt with bugs in the 8086 microprocessor.
In modern CPUs, bugs can often be fixed through a microcode patch that updates the CPU during boot.1 However, prior to the Pentium Pro (1995), microprocessors could only be fixed through a change to the design that fixed the silicon.
Read more of this story at SoylentNews.
06:52
Re: Perl's HTTP::Tiny has insecure TLS cert default, affecting CPAN.pm and other modules Open Source Security
Posted by David A. Wheeler on May 04
I would also expect it to be at most disputed, not rejected.As Jeffry Walton noted, failing to validate a certificate is considered
by many to be a vulnerability, there's even a specific CWE for this case:
https://cwe.mitre.org/data/definitions/295.html
Per the OP:
A default that potentially causes over 300 other vulnerabilities sounds like
a root cause vulnerability to me. Clearly many users do *not* treat this as expected behavior.
A...
06:41
LLVM Clang Now Exposes -std=c++23 Rather Than -std=c++2b Phoronix
Merged today to LLVM 17 Git is now recognizing -std=c++23 rather than just -std=c++2b for the Clang compiler now that C++23 has been deemed technically complete...
06:27
Cisco EoL SPA112 2-Port Phone Adapters are affected by critical RCE Security Affairs
Cisco is warning customers of a critical remote code execution vulnerability affecting its EoL SPA112 2-Port Phone Adapters.
Cisco is warning of a critical remote code execution (RCE) vulnerability, tracked as CVE-2023-20126 (CVSS score of 9.8), impacting SPA112 2-Port phone adapters. The company product has reached end-of-life (EoL).
The vulnerability resides in the web-based management interface of the Cisco SPA112 2-Port Phone Adapters, an unauthenticated, remote attacker can exploit the flaw to execute arbitrary code on an affected device.
In order to exploit the flaw, an attacker has to upgrade an
This vulnerability is due to a missing authentication process within the firmware upgrade function. reads the advisory published by Cisco. An attacker could exploit this vulnerability by upgrading an affected device to a crafted to execute arbitrary code on the affected device with full privileges.
The issue was reported by CataLpa of Dbappsecurity Co., Ltd. Hatlab.
The IT giant has not addressed the issue because SPA112 2-Port phone adapters reached EoL on June 1, 2020. The company also warned that there are no workarounds for the CVE-2023-20126 vulnerability.
Cisco has not released firmware updates to address this vulnerability. There are no workarounds that address this vulnerability. continues the advisory.
Cisco encouraged customers to migrate to a Cisco ATA 190 Series Analog Telephone Adapter.
The company is not aware of attacks in the wild exploiting this vulnerability.
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections where is reported
Securityaffairs or my name Pierluigi Paganini
Please nominate Security Affairs as your favorite blog.
Nominate Pierluigi Paganini and Security Affairs here here:
https://docs.google.com/forms/d/e/1FAIpQLSepvnj8b7QzMdLh7vWEDQDqohj...
06:00
Open 3D Foundation Announces Newest Open 3D Engine Release and First-Ever O3DE Jam Linux.com

Read the original post at: Read More
The post Open 3D Foundation Announces Newest Open 3D Engine Release and First-Ever O3DE Jam appeared first on Linux.com.
05:13
Re: Perl's HTTP::Tiny has insecure TLS cert default, affecting CPAN.pm and other modules Open Source Security
Posted by Rainer Canavan on May 04
[...]As a project maintainer, you should be able to ask the CNA to REJECT a
CVE, or at least have it marked DISPUTED, and that state should be
reflected in all reasonable CVE databases. You'll still have to figure
out how to document it as a non-issue inside your project for your
users to find, but once you've established a working solution, that
should not take months to resolve. I'd suspect that the issue in
HTTP::Tiny would...
05:07
Links 04/05/2023: OpenWrt 22.03.5 and OSMCs May Update Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Monopolies
-
GNU/Linux
-
Server
-
Unicorn Media ...
-
-
04:59
Gemini Links 04/05/2023: IKEA Maze and Lawsuits Over Negative Reviews Techrights
-
Gemini* and Gopher
-
Personal
-
A Ducky Couple and the Unexpected Sunset 2023-05-04 (Fairbanks, AK, USA)
Yesterday, I caught this devoted pair enjoying a leisurely swim during the noon hour
-
An off-ramp from the digital IKEA maze [2023-05-04]
There is an episode of Star Trek where a character is for plot reasons trapped in a shrinking parallel universe. As time passes, people she knows one by one just vanish and she is the only one who seems to notice. Eventually it gets to an absurd point. She asks if it really makes sense if a ship made for a thousand people would have a crew of a few people, and everyone just sort of like shrugs and looks at her like shes crazy. Thats basically what the last decade of the Internet[1]. It feels like its shrinking. Like parts of it are vanishing.
In part I think its the fault of the big walled gardens on the web, whether Facebook, Twitter or Reddit. Theyre essentially designed like a maze. They make you feel like there are no other websites aside from few silos and e-commerce and various forms of blog spam and political propaganda, like the web only consists of maybe a few dozen big sites, encircled by an endless digital strip mall.
-
-
Technical
-
Lawsuits Over Negative Reviews
I hate how businesses now can sue a person over a negative review or at least threaten to do so. They even shame a person for it to defend their reputation with responses such as:
I have seen that you slander a lot of businesses in Google review
Chances are they wont sue me. The only reason Ive removed the revies is because I do not want to be shamed.
I have a right to a good reputation, too. So what if I am not a business. Im still a human being.
This causes me to believe that I should criticize businesses anonymousloy by writing my opinion in chalk on the sidewalk or something.
- ...
-
-
04:45
888 On Line Casino Evaluation Get $200 Welcome Bonus + 88 Free Spins h+ Media
888 On Line Casino Evaluation Get $200 Welcome Bonus + 88 Free Spins
Plus, in addition to utilizing it to make large funds, you possibly can withdraw through UPayCard too. Mobile ApplicationThe option is out there at mobile phone casino the place Kiwis can freely play on the go, and mobile device use in New Zealand is ever-growing. In addition, entry our section of casino bonuses and offers to know what are the benefits that may enhance your possibilities of successful. They are examined by exterior businesses that check the randomness of the jackpots and computerized renewal. What must be carried out to increase the possibilities of receiving a giant prize?
The sport offer is interesting sufficient to maintain us entertained for a protracted time, focusing on essentially in slots and progressive jackpots. You can even attend live betting on 888 Casino eSports occasions and games. The selection perhaps isnt one of the best one obtainable at on-line casino sites, but the 888 Casino eSports betting section matches enough sights. We are a team of specialists that want to cross additional the fervour of on-line playing to its kiwi players.
When requesting a withdrawal, the person must submit paperwork to show the legitimacy of their handle, fee methodology, and identity. 888 will then enable gamers to withdraw up to $30,000 per month with one of many accepted banking options. 888 Casino features a good welcome bundle for new players including 88 Free Spins with no deposit required and a welcome bonus that can go as a lot as NZ$200. It additionally features ongoing promotions that function high-earning qualities. The incontrovertible fact that it has been round since 1997 makes it a very experienced on line casino and extremely reliable.
- In pokies alone, they offer lots of of titles, with every thing from 3D pokies to progressives, classic Vegas-style games to 5-reel titles and every thing in between.
- VIPs receive particular Casino Bonus presents, free gifts, prize draw entries and a lot of other spectacular perks delivered solely to loyal members of 888 Casino.
- 888 cell casino gives you the chance to play anytime you want from anyplace you want, so you probably can always win big when you might have an internet connection.
- Plus, the helpful employees at 888 Casino is at all times readily available to answer any queries you may have about making a deposit.
- There are always News in slots and even games made in New Zealand .
And as we mentioned initially of our 777 casino evaluate, the VIP membership is similar as 888casinos. So, theres no need to fret about not finding an available seat. Some wanted titles are Prestige, Speed and Grand Baccarat. Additionally, you may encounter a number of Dragon Tiger and Sic Bo video games. Besides trade favourites like Starburst, Book of Dead, Wolf Gold and Sweet Bonanza, you might wish to check out one of the quite a fe...
04:43
Search Ae888 Com-venus On Line Casino nhp Vo Linksex247Homosexual h+ Media
Search Ae888 Com-venus On Line Casino nhp Vo Linksex247Homosexual
Play Poker, Baccarat, Bingo, Blackjack and Roulette and check your expertise as you try to beat the house with these skills-based games of chance. Spin and win with Hotline 2, Diamond Vortex, Beat the Beast and Safari Riches for a chance to win a big cash sum. You will want to specify your e-mail handle so that the service help service could reply your questions, if any.
Sports betting, stay dealer on line casino video games, on-line slots, and extra are just a few of the gambling potentialities available. 888 Casino exceeds expectations in phrases of its games lobby. They truly stand out in relation to variations of games, with a spread of online slots, table games, progressive video games, video poker games, live vendor video games and specialty games to choose from. You will discover all your favourite table video games within its foyer, together with Blackjack, Roulette, Caribbean Stud, Baccarat, Casino Holdem, Red Dog and extra. In whole, 888 has about 25 desk games to enjoy, excluding its big selection of Blackjack offerings.
This is similar criteria for the Free spins but it is to be wagered. All betting websites will have a tendency to incorporate limits on how a lot youll have the ability to win with a single wager on their site. 888 have different betting limits for each sport with up to $100,000 for most cricket and rugby bets, whereas some football bets could earn you up to $250,000 in winnings. For sports followers theres plenty of incentive to be riskier together with your bets than regular, as theyre willing to give you $5 in additional bets daily that you manage to win odds of 5.00 or extra. Unfortunately 888 have taken the foolish step of disallowing any rugby union bets with this promotion which is hardly more likely to endear them to their New Zealand prospects. Sadly theres nothing in the best way of apps for BlackBerry or Windows users.
The massive help hub has data on various topics associated to poker online and the software. If the FAQs usually are not enough, users can send an email to the support staff by completing the online web kind. One of the things that assist make 888 Poker nice is the reality that it makes use of its own software program, developed in-house by 888 Holdings. As the worlds premier online poker site, 888poker sports a player base of hundreds of thousands of registered members. Unfortunately, there are not any Live Chat options or a toll-free number to name, and it may upset gamblers, as typically they might be impatient and anticipate instant responses. At first look, the customer assist being provided by this casino could additionally be somewhat disappointing.
We are speaking about a company with lots of name and weight within the sector, of british origin . This is 888 Holdings PLC , which quote on the London Stock Exchange , though the company working in New Zealan...
04:41
888 Com Casino On Internet : Blackjack Play On-line Blackjack At 888com h+ Media
888 Com Casino On Internet : Blackjack Play On-line Blackjack At 888com
888 Poker presents SNAP Poker, which is a fast-fold version where gamers are moved to new tables once they fold to have the ability to tremendously cut back ready instances from palms they are not a part of. This is a Sit & Go choice where 4 gamers compete for a random prize in a time-limited event that may attain 10,000 occasions the buy-in. Then there is Webcam Poker that allows players to see their opponents in real time.
News and press releases referring to Gambling coverage, legislation, regulation, compliance and other info supplied by the Department of Inter Archived gambling consultation paperwork provided by the Department of Internal Affairs. Since a younger age, Shanon has been slightly obsessive about every thing automotive. Biking is one other of Shanons passions and he may be found exploring tracks of the Manawatu in his spare time. They appear to make use of every method potential to avoid you been in a place to withdraw your winnings. I would a relatively small quantity 70 over a month ago and nonetheless havent been able to withdraw this.
Asian Roulette is similar to European Roulette; nevertheless, the numbers are organized in a special order and there are a variety of particular betting options. No massive surprises, MB Way is a shared model with the same entity liable for the ATM. This system represents its reinvention, in a perspective adapted to today, with easy and safe mobile funds.
Top video games from a quantity of providers like NetEnt, Red Tiger and Yggdrasil are all available. What youll be taking a look at is New Zealands Best online on line casino and why it is inside our TOP 10 list for 2021. 100% protected The casino uses the most effective encryption software program in existence.
As of this evaluation, the contact web page linked us to a communication form quite than a telephone line or stay chat platform. Deposits of $20 or larger shall be eligible for the latest welcome supply. When it involves 888s reside dealer on line casino, solely the best will do. Using Evolutions advanced platform coupled with the casinos distinctive branding, 888 casino has cultivated a extremely spectacular, bespoke stay supplier casino experience. The charming, skilled European dealers will make you think that you are in a Monte Carlo casino. On the Live Casino homepage, there might be even a chance to meet the dealers earlier than you play; put names to faces as you scroll via their headshots.
Withdrawals are processed in a quick time at this on-line casino, and depending on the chosen technique of payment they may take more or less time to course of. Making a withdrawal at 888Casino is simply as straightforward as making a deposit. The very first thing we will have to keep in mind is that if the account just isnt verified, no withdrawals may be made .
Of c...
04:40
888 On Line Casino Nz Review On-line $100 Nzd 888 Casino Bonus 2023 h+ Media
888 On Line Casino Nz Review On-line $100 Nzd 888 Casino Bonus 2023
Most online accounts are secure to begin with, its doubtful you will depart the location with out discovering a number of favorite video games to try. For better gaming high quality, and it takes no less than three scatters throughout each reel sets showing as a lot as activate such. A dedicated part of the lobby will present varied tables and tournaments for gamers seeking to enjoy the game without using real money in the course of. T just apply to cash video games but in addition to on-line poker tournaments, since the schedule is at all times packed and the action by no means appears to cease. The online gaming industry is a aggressive one, and for a web-based casino to stay in the trade for thus long is indeed spectacular.
Its utterly free to download the 888 apps they usually do a great job in somehow cramming the entire options of the 888 sites into the palm of your hand. This means that you can take pleasure in betting on tons of of daily markets for sport, or try some fast and easy online pokies games whereas youre out and about. 888 was launched way again in 1997 and they have taken advantage of the digital revolution to turn out to be certainly one of Europes biggest online gambling sites. The Gibraltar based company have websites for sports activities betting, casino gaming and even poker, and 888 New Zealand is simply one of many many worldwide branches of the model.
The hottest choices proper now are money tables for no-limit holdem, often at low stakes. These get probably the most gamers and users also appear to love taking part within the SNAP poker video games. Thanks to its very high traffic numbers, the poker room online has numerous games operating all through the day. This is nice information for gamers from New Zealand since the peak hours are principally primarily based on European times.
These video games convey the action to your cellular display screen alongside gifted sellers. Regarding the licenses, 888 Casino is regulated by reputable authorities. Their accreditations indicate that the operator is committed to giving gamers a secure and transparent cell gaming expertise.
The best thing about 888 Casino is the number of bonuses and promotions it presents to its customers and the VIP Program is amongst the greatest in town. 888 Casino doesnt supply the most effective range in phrases of Customer Suppor it only features one buyer assist possibility via email. However, we have examined the shopper care they usually do reply inside 24 hours, as promised on their web site.
888Casino is powered by its own unique platform which is topic to continuous updates to retain advances in gaming expertise. The video games graphics characteristic excessive definition visuals, audio and 3D designs that emulate the surroundings of a land-based on line casino. Live dealer action delivers one of the best o...
04:11
TSMC News - US and Europe SoylentNews
TSMC May Charge 30 Percent More for Chips Made at its Arizona Fabs
The chipmaker is looking for $15 billion in subsidies from the US government:
Setting up a chip factory in the US is an expensive endeavor, especially when compared to doing the same in Asia. Still, companies like TSMC are investing billions into doing just that, wooed by government subsidies and the idea of achieving a geographically diverse supply chain that is less prone to disruptions. As a result, chips made by the Taiwanese giant in the US could end up 30 percent more expensive than those made in its home country.
Back in December, TSMC announced it would pour no less than $40 billion into building two advanced chip factories in Arizona. In other words, the world's biggest chipmaker made the largest direct foreign investment in Arizona history and one of the largest in US history. When they become operational, the fabs will employ thousands of people and produce around 600,000 wafers per year.
The move represents a significant shift in mindset for TSMC leadership, which has traditionally been reluctant to establish chip manufacturing facilities in the US. One reason has to do with Taiwan's policy of keeping its most advanced technologies locally even as it builds external manufacturing arms for a more resilient global supply chain.
Another reason has to do with cost setting up and operating a factory on American soil is up to 50 percent more expensive than in Taiwan. Then you'd need to source materials like rare earth metals and semiconductor-grade neon as well as a steady supply of water to keep the facility running at full capacity. And last but not least, you need a lot of skilled (and cheap) labor, something that is easier to find in Asia as opposed to North America and even Europe.
Naturally, this means TSMC will have extra costs in the US that will translate into higher prices for wafers made in Arizona as opposed to those made in Taiwan. Some industry insiders estimate that chips made in America on N5 and N4 process nodes will cost up to 30 percent more than those made in the Asian co...
04:08
Re: Perl's HTTP::Tiny has insecure TLS cert default, affecting CPAN.pm and other modules Open Source Security
Posted by Alan Coopersmith on May 04
The CVE process is designed with a primary goal of simply providing a unique idfor each claimed vulnerability - it's intended to not have much deeper meaning
than creating a UUID. There is no requirement that the claimed vulnerability
be well described, proven, accepted, fixed, or anything else beyond not being a
duplicate of an existing CVE entry.
Unfortunately, many CVE consumers assume a far greater level of meaning to CVEs
than the...
04:03
Google "We Have No Moat, And Neither Does OpenAI" (SemiAnalysis) LWN.net
The SemiAnalysis site has what is said to be a leaked Google document on the state of open-source AI development. Open source, it concludes, is winning.
At the beginning of March the open source community got their hands on their first really capable foundation model, as Metas LLaMA was leaked to the public. It had no instruction or conversation tuning, and no RLHF. Nonetheless, the community immediately understood the significance of what they had been given.A tremendous outpouring of innovation followed, with just days between major developments (see The Timeline for the full breakdown). Here we are, barely a month later, and there are variants with instruction tuning, quantization, quality improvements, human evals, multimodality, RLHF, etc. etc. many of which build on each other.
(Thanks to Dave Tht).
03:59
Re: Perl's HTTP::Tiny has insecure TLS cert default, affecting CPAN.pm and other modules Open Source Security
Posted by Sam Bull on May 04
But, reporting a CVE where there is no vulnerability wastes a lot of time for the projectmaintainers, as we had last year with this CVE:
https://github.com/aio-libs/aiohttp/issues/6801
As far as we could tell, it seems a random user reported a DoS vulnerability to Github
(maybe?) and got a CVE assigned, with no reproducer or any evidence of a vulnerability,
and just a link to an issue which was never considered a security issue by anybody. None...
03:51
The Entire Kitchen Sink Redux Random Thoughts
Its done!
Man, that took a lot longer than I had planned, but after a year and a half, Im done with the Kitchen Sink blog (wherein I attempt to read all comics published by Kitchen Sink Press and then natter on a bit about them).
And its not like its the first time Ive done something like this, but it was the hardest one to do. And I was surprised by that, because I do like a lot of what Kitchen Sink published. But, for instance, with the Eclipse Comics blog, there were a lot of surprises stuff I only had a vague idea existed, and turned out to be pretty entertaining while there were few surprises (for me) doing this one.
So it got to be a bit of a slog for me towards the end, and I apologise for the sometimes brash tone that crept into some of the posts. (Old Man Shouts At Old Comics isnt that much fun to read.)
But, hey, Kitchen Sink did publish a lot of great stuff! And its got a quite interesting history, I think. So there you go.
03:34
Cyberpress Launches Cybersecurity Press Release Distribution Platform HackRead | Latest Cybersecurity and Hacking News Site
By Cyberpress
Dubai / May 1st 2023 / Cyberpress Cybersecurity gets a new dedicated newswire. Cyberpress, a press release
This is a post from HackRead.com Read the original post: Cyberpress Launches Cybersecurity Press Release Distribution Platform
03:20
PacWest Bancorp Shares Crash cryptogon.com
Via: AFP: Shares of PacWest Bancorp were in free fall Thursday after the banks attempt to reassure investors fell flat amid another pummeling of US regional bank stocks. Near 1600 GMT, shares of PacWest were down more than 50 percent. Other leading banks were also on the back foot, including Western Alliance (-43 percent), Zions []
03:00
We Already Live in a Hydrogen Economy: Steel Production, Generator Cooling, and Welding Gas Hackaday

Although generally hydrogen is only mentioned within the context of transportation and energy storage, by far the most useful applications are found in industrial applications, including for the chemical industry, the manufacturing of steel, as well as that of methanol and fertilizer. This is illustrated by how today most of all hydrogen produced today is used for these industrial applications, as well as for applications such as cooling turbo generators, with demand for hydrogen in these applications rapidly increasing.
Currently virtually all hydrogen produced today comes from natural gas, via steam methane reformation (SMR), with potentially methane pyrolysis making natural gas-derived hydrogen a low-carbon source. The remainder of hydrogen comes from coal gasification and a small fraction from electrolysis of water. The hydrogen is often produced on-site, especially at industrial plants and thermal power plants. So aside from any decarbonization efforts, ther...
02:24
The Battle Plan For Combating IPTV Piracy in Europe Has Arrived TorrentFreak
 After
protest,
disappointment, hand-wringing, and at times,
sheer frustration, the European Commission has officially
unveiled its full recommendation for combating piracy of live
sports and musical events.
After
protest,
disappointment, hand-wringing, and at times,
sheer frustration, the European Commission has officially
unveiled its full recommendation for combating piracy of live
sports and musical events.
The Recommendation
The European Commission begins with a broad overview of the value of live events and the problems faced by rightsholders when tackling pirate IPTV and similar unlicensed streaming services.
From a reference perspective, particularly related to specific challenges and various aspects of relevant law, the ECs recommendation provides a great overview that makes for interesting reading. If explaining the illegal streaming problem had been the main aim, the document would receive solid marks. As a road map for solving tough issues in a short time frame, not so much.
Right from the very beginning its extremely clear that the EC understands almost every aspect of the challenges faced by rightsholders. Unfortunately, the vast majority of the report is dedicated to coverage of those challenges, for consumption by the very entities that supplied the information to the EC in the first place. Some of the key points in the initial overview can be summarized as follows:
Unauthorized supply, technical challenges
Main value in live sports broadcasts lies in the
exploitation of live transmission
Illegal retransmissions can cause significant losses to
rightsholders/broadcasters
Increasingly sophisticated means make content available via
IPTV/apps/websites
Streaming piracy is a global phenomenon, increasingly reliant on
offshore hosting
Offshore hosting minimizes pirates exposure to copyright or
criminal law in the EU
Piracy-as-a-Service makes it easy to create pirate sites and start
generate revenue
Some infringing services mirror legitimate streaming services
CDNs/reverse proxies often misused to obfuscate sources of pirate
streams
These issues are common knowledge and the subject of countless reports, mostly published by rightsholders; the presence of the terms offshore hosting and Piracy-as-a-Service are e...
02:19
The Electronic Frontier Foundation (EFF) Covers Software Patents Again Techrights

By Dominik Butzmann / re:publica re:publica
faces 2019, CC BY-SA 2.0.
Summary: Cory Doctorow and Joe Mullin (EFF) wrote about software patents this week; this shows that the EFF can still pivot in the right direction if it really wants to
As it turns out, Joe Mullin is fortunately still around (at the EFF, he used to be in the media) and the other day he cautioned the U.S. Solicitor General Trying To Change The Law To Benefit Patent Trolls. His EFF colleague, Mr. Doctorow, said at almost the same time: In theory, patents are for novel, useful inventions that arent obvious to a skilled practitioner of the art. But as computers ate our society, grifters began to receive patents for doing something weve done for centurieswith a computer. With a computer: those three words had the power to cloud patent examiners minds.
He then changed the subject from software patents to patent trolls (the EFF habitually changes the subject to bad patents or trolls). To quote: Patent trolls who secure with a computer patents and then extract ransoms from people doing normal things on threat of a lawsuit are an underappreciated form of tech exceptionalism. Normally, tech exceptionalism refers to bros who wave away things like privacy invasions by arguing that with a computer makes it all different.
Quoting Mr. Mullin, regarding the U.S. Patent and Trademark Office (USPTO) and 35 U.S.C. 101: Government officials should be working to reduce, not increase, the burden that low-quality patent lawsuits impose on innovators. So were concerned and dismayed by recent briefs filed by the U.S. Solicitor General, asking the Supreme Court to reexamine and throw out the best legal defenses regular people have against patent trollscompanies that dont make products or provide services, but simply use patents to sue and t...
02:01
Newer is Not Always Better (the Case of Automobiles) Techrights
Summary: Techrights recommends caution against tech maximalism; not everything that can be done with/on a computer should, in practice, be done that way; a careful balance is needed, taking stock of pros and cons
TODAY in IRC we had a lengthy discussion about the downside of supposedly modern or smart cars*. Itll be in the IRC logs tomorrow. Its very informal. Its going way beyond aspects like cost and privacy those two are commonly discussed these days. We did a series about it over a year ago.
People are simply asked to buy the latest no matter what Trojan horses are included (mandated) in these.What compels people to blindly assume that newer is always better when its perfectly clear that users arent in control and products are tailored (over time) to better suit the manufacturers, the stores etc.? People are simply asked to buy the latest no matter what Trojan horses are included (mandated) in these.
This subject keeps coming back. People who drive need to buy cars (occasionally) and there are many things they see which they strongly dislike.
The one [new article] about cars can be motivation for revisiting cars/embedded systems and software freedom, one person told us this week, suggesting it as a topic and stating that the focus was in-house expertise vs outsourcing, in cars.
To quote the portion weve already included in Daily Links:
I would argue relying too much on external software vendors and not seeing software as a first-class citizen is the root cause. But Volvo Cars is wisely moving away from that model by bringing software developers in-house. Google and Apple partner with vendors for commodities. Software and data just happen to be too key to treat it that way. As I argued in a previous post, the automotive industry needs to own their data and set up to make it to the mobility-driven phase.
Having someone from software-...
02:01
01:31
A Fedora Test Week Starts Sunday. Want to Help? Heres How FOSS Force
Fedora is looking for a few good testers.
The post A Fedora Test Week Starts Sunday. Want to Help? Heres How appeared first on FOSS Force.
01:30
BeagleStamp Makes Soldering Linux into Your Projects Easier Hackaday

There are a lot of things you can do with todays powerful microcontrollers, but sometimes you really need a full embedded Linux setup. [Dylan Brophy] wanted to make it easier to add Linux to his own projects and designed the BeagleStamp.
01:23
Netflix Loses a Million Subscribers in Spain After Greedy Password Sharing Crackdown SoylentNews
Netflix Loses A Million Subscribers In Spain After Greedy Password Sharing Crackdown:
We've noted repeatedly how Netflix's password sharing crackdown is a stupid cash grab that alienates and annoys loyal customers, duplicates existing efforts to restrict "freeloaders," won't give the company the financial windfall it thinks, and just generally represents how the company has inevitably shifted from innovative disruptor to the kind of tone deaf cable giants it used to criticize.
The plan basically involves charging users an extra $2-$3 a month if it's found that someone is using your account outside of your home. The problem: Netflix has already been imposing blanket price hikes, and it already limits the number of simultaneously streams per account, forcing users to subscribe to more expensive tiers if they want to expand the limit.
While the crackdown isn't expected to hit U.S. subscribers until the end of the second quarter (aka soon), the effort has generally been a hot mess in the smaller countries Netflix first used as guinea pigs to test both the underlying tech and company messaging.
The company had to suspend the efforts in countries like Argentina, El Salvador, Guatemala, Honduras, and the Dominican Republic, after users were equal parts befuddled and annoyed. And in Spain, estimates are that the company saw a defection of more than one million subscribers largely due to the higher, unnecessary fees:
"There are of course inherent risks with clamping down on password sharing, particularly when back in 2017 Netflix was seen to be actively encouraging it. Some users were expected to be lost in the process but losing over 1 million users in a little over a month has major implications for Netflix and whether it decides to continue with its crackdown globally.
Interestingly, there is no strong demographic skew to those who cancelled, signaling a more outright rejection of the password sharing clampdown. In a worrying sign for the...
01:08
Experts devised a new exploit for the PaperCut flaw that can bypass all current detection Security Affairs
VulnCheck researchers devised a new exploit for a recently disclosed critical flaw in PaperCut servers that bypasses all current detections.
Cybersecurity researchers from VulnCheck have developed a new exploit for the recently disclosed critical flaw in PaperCut servers, tracked as CVE-2023-27350 (CVSS score: 9.8), that bypasses all current detections.
The CVE-2023-27350 flaw is a PaperCut MF/NG Improper Access Control Vulnerability. PaperCut MF/NG contains an improper access control vulnerability within the SetupCompleted class that allows authentication bypass and code execution in the context of SYSTEM.
On April 19th, Print management software provider PaperCut confirmed that it is aware of the active exploitation of the CVE-2023-27350 vulnerability.
The company received two vulnerability reports from the cybersecurity firm Trend Micro for high/critical severity security issues in PaperCut MF/NG.
Trend Micro announced they will disclose further information (TBD) about the vulnerability on 10th May 2023.
The company addressed both vulnerabilities with the release of PaperCut MF and PaperCut NG versions 20.1.7, 21.2.11 and 22.0.9 and later, it highly recommends upgrading to one of these versions containing the fix.
Huntress researchers have observed post-exploitation activities within its partner environments after attackers exploited the above PaperCut MF/NG vulnerabilities.
Huntress security researcher Caleb Stewart also devised a proof-of-concept exploit for these threats, below is the video PoC shared by the company:
From our recreated proof-of-concept, we observed child processes spawned underneath the&n...
00:48
Patch now! The Mirai IoT botnet is exploiting TP-Link routers Graham Cluley
Businesses should patch their TP-Link routers as soon as possible, after the revelation that a legendary IoT botnet is targeting them for recruitment. Read more in my article on the Tripwire State of Security blog.
00:42
Bing is Dying and Chatbots Wont Save Bing Techrights
Dont believe the hype (a shameless lying blitz)
Summary: The father of Bing left Microsoft, many Bing employees were laid off earlier this year, and the remaining ones relocated out of their office in Bellevue; the media is meanwhile hyping up the Bing brand (we saw new examples this morning) and pretending that Google is doomed; the data does not support this phony narrative (its more or less the same in other regions around the world; overall, worldwide, Bing market share is measured at about 2.5%)
00:24
Facebook warns of a new information-stealing malware dubbed NodeStealer Security Affairs
Facebook discovered a new information-stealing malware, dubbed NodeStealer, that is being distributed on Meta.
NodeStealer is a new information-stealing malware distributed on Meta that allows stealing browser cookies to hijack accounts on multiple platforms, including Facebook, Gmail, and Outlook.
The malware was first spotted in late January 2023 while targeting the browsers of Windows systems. It can target multiple web browsers, including Google Chrome, Microsoft Edge, Brave, and Opera.
The researchers explained that NodeStealer is a custom Javascript malware that bundles the Node.js environment. The author uses Node.js to allow malware execution on multiple OS, including Windows, Linux, and macOS.
The info stealer is believed to have a Vietnamese origin and was allegedly distributed by threat actors from Vietnam.
The social network giant took action to disrupt the malware campaign and support victims in recovering their accounts.
The malware is disguised as PDF and XLSX files and their filename was chosen to trick victims into opening them starting the infection process.
As part of this effort, we submitted takedown requests to third-party registrars, hosting providers, and application services such as Namecheap, which were targeted by these threat actors to facilitate distribution and malicious operations. reads the post published by Facebook. These actions led to a successful disruption of the malware. We have not observed any new samples of malware in the NodeStealer family since February 27 of this year and continue monitoring for any potential future activity.
The good news is that Facebook discovered the threat within two weeks of it being distributed
At the time of its discovery, the malicious code had a single detection on the VirusTotal platform.
One of the samples analyzed by the company was a Windows executable file disguised as a PDF file with a PDF icon. The threat actors changed the metadata in an attempt to disguise the file as a MicrosoftOffice product.
This sample is written in Javascript, executed using Node.js, and compiled into a Windows executable using a tool from the Node Package Manager (NPM) called pkg. This sample is around 46 MB in size, but experts discovered files with a size between 46 and 51 MB.
NodeStealer maintains persistence using the auto-launch module on Node.js.
The Chrome browser encrypts the users information before storing it, the encrypted_key is stored in the Local...
00:19
[$] The ongoing trouble with get_user_pages() LWN.net
The 2018 Linux Storage, Filesystem, and Memory-Management (LSFMM) conference included a session on get_user_pages(), an internal kernel interface that can, in some situations, be used in ways that will lead to data corruption or kernel crashes. As the 2023 LSFMM+BPF event approaches, this problem remains unsolved and is still the topic of ongoing discussion. This patch series from Lorenzo Stoakes, which is another attempt at a partial solution, is the latest focus point.
00:14
Robot Hand Manipulates Complex Objects by Touch Alone IEEE Spectrum

In terms of human features that robots are probably the most jealous of, fingers have to be right up there with eyeballs and brains. Our fleshy little digits have a crazy amount of dexterity relative to their size, and so many sensors packed into them that allow you to manipulate complex objects sight unseen. Obviously, these are capabilities that would be really nice to have in a robot , especially if we want them to be useful outside of factories and warehouses.
There are two parts to this problem: The first is having fingers that can perform like human fingers (or as close to human fingers as is reasonable to expect); the second is having the intelligence necessary to do something useful with those fingers.
Once we also add visual feedback into the mix
along with touch, we hope to be able to achieve even more
dexterity, and one day start approaching the replication of the
human hand.
Matei Ciocarlie, Columbia University
In a paper just accepted to the Robotics: Science and Systems 2023 conference, researchers from Columbia University have shown how to train robotic fingers to perform dexterous in-hand manipulation of complex objects without dropping them. Whats more, the manipulation is done entirely by touchno vision required.
Robotic fingers manipulate random objects a level of dexterity humans master by the time theyre toddlers.Columbia University
Those slightly chunky fingers have a lot going on inside of them to help make this kind of manipulation possible. Underneath the skin of each finger is a flexible reflective membrane, and under that membrane is an array of LEDs along with an array of photodiodes. Each LED is cycled on and off for a fraction of a millisecond, and the photodiodes record how the light from each LED reflects off of the inner membrane of the finger. The pattern of that reflection changes when the membrane flexes, which is what happens if the finger is contacting something. A trained model can correlate that light pattern with the locati...
00:11
IBM Has Measurably Lessened Activity in Red Hat Web Sites (It Started When Layoffs Were Announced Last Month) Techrights
Summary: OpenSource.com and enterprisersproject.com scaled down their activity around the time Red Hats CEO announced that 700+ workers would be made redundant; are writers among the casualties of these cuts?
T HIS is a subject we deem especially and exceptionally sensitive because many good people lost their jobs at Red Hat. Some were technical, some were less technical. We know some names, but this post will name nobody.
My wife and I have been reading OpenSource.com every day for about a decade, so these trends are easy to spot or feel (even the mere absence of something gets noticed).Last year we took note of neglect in OpenSource.com (a Red Hat site for well over a decade already) and weeks later the site picked up pace again, publishing 2-3 new articles per day, except weekends (sometimes on weekends too they published new material). Unlike months prior, they didnt post obnoxious stuff; they had actually published some tasteless things last year.
My wife and I have been reading OpenSource.com every day for about a decade, so these trends are easy to spot or feel (even the mere absence of something gets noticed). The sites editors changed a few times over the years (we wont name them; we want to keep this impersonal).
The Linux Foundation has been very quiet this year and it is intentional; they try to keep a low profile for a reason.So what exactly is going on? Let us know. Were generally thankful for what the site offered since its birth and it would be a shame if it became something like Linux.com in affect killed by the Linux Foundation when it fired all the staff writers and all the editors without prior notice or an explanation. Revenue was growing fast back then, unlike...
00:00
AI Spera launches Criminal IP FDS plugin to prevent fraudulent login attempts on WordPress Help Net Security
Criminal IP, an OSINT-based search engine provided by AI Spera, launched a new WordPress plugin called Anti-Brute Force, Login Fraud Detector, also known as Criminal IP FDS (Fraud Detection System). This latest development promises to revolutionize the digital security landscape by providing a comprehensive solution to detect and prevent fraudulent login attempts on WordPress websites. Criminal IP, a Cyber Threat Intelligence (CTI) search engine, has recently launched a powerful WordPress security plugin called Anti-Brute Force, More
The post AI Spera launches Criminal IP FDS plugin to prevent fraudulent login attempts on WordPress appeared first on Help Net Security.
00:00
Intel's One Line Of Linux Code For Speeding-Up Sapphire Rapids On Ubuntu Phoronix
Recently I noticed out-of-the-box on Ubuntu Linux the performance of Intel Xeon Scalable "Sapphire Rapids" processors was much improved for some workloads compared to tests done just weeks ago on the same Sapphire Rapids server. It ended up being an issue coming full-circle and ultimately boils down to one line of code added within the Linux kernel.
00:00
Virgin Galactic Cautiously Returns To Flight Hackaday

After Richard Branson delivered some inspiring words from his seat aboard SpaceShipTwo Unity, he unbuckled himself and started to float around the vehicles cabin along with three other Virgin Galactic employees. Reaching an apogee of 86 kilometers (53 miles), the passengers enjoyed four minutes of weightlessness during the July 2021 flight that was live-streamed over the Internet to an audience of millions. After years of delays, SpaceShipTwo had finally demonstrated it was capable of taking paying customers to the edge of space. As far as victories go it was pretty impressive.
Yet despite the spectacle, weeks and months went by without an announcement about when commercial flights of the worlds first spaceline would finally begin. Now, nearly two years after Bransons flight, Unity has flown again. Except instead of carrying the first group of customers, it performed the sort of un-powered test flight that Virgin Galactic hasnt performed since 2017. Clearly, something didnt go to plan back then.
Thursday, 04 May
23:48
HUB Security raises up to $16 million to fuel technology development Help Net Security
HUB Security entered into an agreement for up to $16 million in gross proceeds from Lind Global Asset Management VI LLC, an investment entity managed by The Lind Partners, a New York based institutional fund manager (together, Lind). This investment is expected to provide HUB Security with additional resources to fuel its rapid growth and development, enhance its financial stability, and enable the Company to pursue its future plans. The additional funding from The Lind More
The post HUB Security raises up to $16 million to fuel technology development appeared first on Help Net Security.
23:40
New C features in GCC 13 (Red Hat Developer) LWN.net
The Red Hat Developer site has an overview of some of the new C-language features supported by the GCC 13 release.
The nullptr constant first appeared in C++11, described in proposal N2431 from 2007. Its purpose was to alleviate the problems with the definition of NULL, which can be defined in a variety of ways: (void *)0 (a pointer constant), 0 (an integer), and so on. This posed problems for overload resolution, generic programming, etc. While C doesnt have function overloading, the protean definition of NULL still causes headaches.
23:33
Security updates for Thursday LWN.net
Security updates have been issued by Fedora (python-sentry-sdk) and Ubuntu (python-django and ruby2.3, ruby2.5, ruby2.7).
23:30
Airgap Networks enhances its Zero Trust Firewall with ThreatGPT Help Net Security
Airgap Networks announced that it is bringing the power of AI to its Zero Trust Firewall with ThreatGPT. Built on an advanced AI/ML model designed to protect enterprises from evolving cyber threats, ThreatGPT delivers a new level of insight and productivity for network security teams. Perimeter firewalls struggle with todays combination of a complex, dynamic endpoint architecture and the real-world pervasiveness of legacy systems and headless devices. Airgap ZTFW complements existing perimeter firewall infrastructure by More
The post Airgap Networks enhances its Zero Trust Firewall with ThreatGPT appeared first on Help Net Security.
23:21
City of Dallas hit by ransomware Help Net Security
The City of Dallas, Texas, has suffered a ransomware attack that resulted in disruption of several of its services. What do we know so far? Wednesday morning, the Citys security monitoring tools notified our Security Operations Center (SOC) that a likely ransomware attack had been launched within our environment, the Citys public statement revealed. Subsequently, the City has confirmed that a number of servers have been compromised with ransomware, impacting several functional areas, including the More
The post City of Dallas hit by ransomware appeared first on Help Net Security.
23:19
Researchers Discover 3 Vulnerabilities in Microsoft Azure API Management Service The Hacker News
Three new security flaws have been disclosed in Microsoft Azure API Management service that could be abused by malicious actors to gain access to sensitive information or backend services. This includes two server-side request forgery (SSRF) flaws and one instance of unrestricted file upload functionality in the API Management developer portal, according to Israeli cloud security firm Ermetic. "
23:03
Researchers Uncover New Exploit for PaperCut Vulnerability That Can Bypass Detection The Hacker News
Cybersecurity researchers have found a way to exploit a recently disclosed critical flaw in PaperCut servers in a manner that bypasses all current detections. Tracked as CVE-2023-27350 (CVSS score: 9.8), the issue affects PaperCut MF and NG installations that could be exploited by an unauthenticated attacker to execute arbitrary code with SYSTEM privileges. While the flaw was patched by the
23:00
AppOmni releases Salesforce Community Cloud Scanner Help Net Security
AppOmni announced free Salesforce Community Cloud Scanner to help organizations secure their Salesforce Community websites from data exposure risks and misconfigurations. Salesforce data leaks recently identified by Krebs on Security have resulted in exposure of numerous Salesforce Community Cloud customers sensitive data. These data leaks occur when Salesforce customers access control permissions are misconfigured. The Salesforce misconfigurations, along with others previously discovered by AppOmnis Principal SaaS Security Engineer Aaron Costello, are frequent targets for threat More
The post AppOmni releases Salesforce Community Cloud Scanner appeared first on Help Net Security.
23:00
Open 3D Engine 23.05 Released With Many New Features Phoronix
It's been just under two years since Amazon's Lumberyard game engine was spun into the Open 3D Engine and the Open 3D Foundation established under the Linux Foundation. Today the project is celebrating its newest open-source game engine update with Open 3D Engine 23.05...
22:37
SpaceX Completes First Fully Expendable Falcon Heavy Mission SoylentNews
SpaceX Completes First Fully Expendable Falcon Heavy Mission
SpaceX Completes First Fully Expendable Falcon Heavy Mission:
The triple-core rocket blasted off on Sunday evening to deliver three satellites to a high Earth orbit.
SpaceX's giant Falcon Heavy rocket successfully delivered three satellites to high Earth orbit on April 30. The launch marked the first time that none of the rocket's boosters were recovered.
Wild SpaceX Video Shows Hottest Reentry Yet of Reusable Rocket Fairing
Wild SpaceX Video Shows Hottest Reentry Yet of Reusable Rocket Fairing:
The dramatic footage shows a Falcon Heavy fairing blazing through the atmosphere at speeds reaching Mach 15.
The most recent flight of SpaceX's Falcon Heavy was historic in that it was the rocket's first fully expendable mission, and it was also the first Falcon Heavy mission to include previously flown fairings. As new footage attests, the fiery return of these fairings was a sight to behold.
After several delays, the Falcon Heavy blasted off from Launch Complex 39A at NASA's Kennedy Space Center in Florida on Sunday, April 30 at 8:26 p.m. ET. The triple-core rocket successfully deployed its primary payload, the broadband ViaSat-3 Americas satellite, and two smaller satellites to geosynchronous Earth orbit (GEO).
Key to SpaceX's ongoing success is its devotion to reusabilityit's a lot cheaper to recover your engines and reuse them than to produce new ones for every launch. For this mission, however, none of the rocket's three booster stages could be recovered, as they expelled all their fuel in the effort to get the payloads to GEO. That said, SpaceX did make the attempt to recover the rocket's fairings, so in that sense it wasn't a fully expendable mission.
Read more of this story at SoylentNews.
22:25
X.Org Foundation To Become Part Of The SFC Phoronix
X.Org members have approved of the X.Org Foundation letting the Software Freedom Conservancy (SFC) become its fiscal sponsor...
21:49
Arthur Shield tackles safety and performance issues in large language models Help Net Security
Arthur introduced a powerful addition to its suite of AI monitoring tools: Arthur Shield, a firewall for large language models (LLMs). This patented new technology enables companies to deploy LLM applications like ChatGPT more safely within an organization, helping to identify and resolve issues before they become costly business problems or worse, result in harm to their customers. Recent advancements in large language models from OpenAI, Google, Meta, and others have spurred a rush More
The post Arthur Shield tackles safety and performance issues in large language models appeared first on Help Net Security.
21:15
Why the Things You Don't Know about the Dark Web May Be Your Biggest Cybersecurity Threat The Hacker News
IT and cybersecurity teams are so inundated with security notifications and alerts within their own systems, its difficult to monitor external malicious environments which only makes them that much more threatening. In March, a high-profile data breach hit national headlines when personally identifiable information connected to hundreds of lawmakers and staff was leaked on the dark web. The
21:01
Spinrilla Will Shut Down and Pay $50m Piracy Damages to Music Labels TorrentFreak
 Music fans love to share mixtapes and have done so for
decades but sharing these tapes over the Internet is not without
risk.
Music fans love to share mixtapes and have done so for
decades but sharing these tapes over the Internet is not without
risk.
Popular hip-hop mixtape site and app Spinrilla has millions of users and is well aware of the pitfalls. In 2017, the company was sued by several RIAA-backed labels, including Sony, Warner, and UMG, which accused the company of massive copyright infringement.
Spinrilla specializes in ripping off music creators by offering thousands of unlicensed sound recordings for free, the RIAA commented at the time.
Spinrilla Fought Piracy Accusations
The hip-hop site countered the allegations by pointing out its RIAA-approved anti-piracy filter and highlighting how it actively worked with major record labels to promote their tracks. In addition, Spinrilla stressed that the DMCAs safe harbor protects the company from liability.
As the case progressed both parties filed motions for summary judgment. The music companies requested rulings to establish that Spinrilla is liable for direct copyright infringement and that the DMCA safe harbor doesnt apply. Spinrilla countered with cross-motions, filed under seal, in which they argued the opposite.
Court: Spinrilla is Liable
In December 2020, US District Court Judge Amy Totenberg ruled that Spinrilla is indeed liable for direct copyright infringement. In her ruling, Judge Totenberg concluded that 4,082 copyrighted sound recordings were streamed at least once through Sprinrillas website or app.
Without the DMCAs safe harbor protection, Spinrilla faced a severe disadvantage in the event the case went to trial. With 4,082 copyrights at stake, potential damages would exceed $600 million if the jury found that the infringements were willful.
In recent weeks it looked like both parties were gearing up for a trial but, at the last minute, Spinrilla accepted a settlement and voluntarily submitted an offer of judgment to the court.
$50 Million + Shutdown
Spinrilla doesnt go li...
21:00
Jet Engine Tachometer Turned into Unique CPU Utilization Meter Hackaday

When youve got a piece of interesting old aviation hardware on your desk, what do you do with it? If youre not willing to relegate it to paperweight status, your only real choice is to tear it down to see what makes it tick. And if youre lucky, youll be able to put it to work based on what you learned.
Thats what happened when [Glen Akins] came across a tachometer for a jet airplane, which he promptly turned into a unique CPU utilization gauge for his computer. Much of the write-up is concerned with probing the instruments innards to learn its secrets, although it was clear from the outset that his tachometer, from Kollsman Instruments, was electrically driven. [Glen]s investigation revealed a 3-phase synchronous motor inside the tach. The motor drives a permanent magnet, which spins inside a copper cup attached to the needle on the tachs face. Eddy currents induced in the cup by the spinning magnet create a torque that turns the needle against the force of a hairspring. Pretty simple but how to put the instrument to work?
[Glen]s solution was to build what amounts to a variable frequency drive (VFD). His power supply is based on techniques he used to explore aircraft synchros, which...
20:51
Meta Uncovers Massive Social Media Cyber Espionage Operations Across South Asia The Hacker News
Three different threat actors leveraged hundreds of elaborate fictitious personas on Facebook and Instagram to target individuals located in South Asia as part of disparate attacks. "Each of these APTs relied heavily on social engineering to trick people into clicking on malicious links, downloading malware or sharing personal information across the internet," Guy Rosen, chief information
20:41
Russia-linked Sandworm APT uses WinRAR in destructive attacks on Ukraines public sector Security Affairs
CERT-UA is warning of destructive cyberattacks conducted by the Russia-linked Sandworm APT group against the Ukraine public sector.
Russia-linked APT group Sandworm is behind destructive cyberattacks against Ukrainian state networks, the Ukrainian Government Computer Emergency Response Team (CERT-UA) warns.
The Sandworm group (aka BlackEnergy, UAC-0082, Iron Viking, Voodoo Bear, and TeleBots) has been active since 2000, it operates under the control of Unit 74455 of the Russian GRUs Main Center for Special Technologies (GTsST).
The group is also the author of the NotPetya ransomware that hit hundreds of companies worldwide in June 2017. In 2022, the Russian APT used multiple wipers in attacks aimed at Ukraine, including AwfulShred, CaddyWiper, HermeticWiper, Industroyer2, IsaacWiper, WhisperGate, Prestige, RansomBoggs, and ZeroWipe.
The threat actors allegedly obtained access to Ukraines public networks by using compromised VPN credentials.
CERT-UA started investigating the attack after it received information about an attack against an ICS system of one of the state organizations of Ukraine.
The attackers used a BAT script dubbed Roa...
20:39
Re: Perl's HTTP::Tiny has insecure TLS cert default, affecting CPAN.pm and other modules Open Source Security
Posted by Reid Sutherland on May 04
Moritz Bechler wrote:Performing outside queries is not a reasonable default in terms of
security. It's up to the developer if they wish to open up the user to
that risk. Libraries cannot shift defaults on a whim, this is why they
have documentation.
20:37
Re: semi-public issues on (linux-)distros Open Source Security
Posted by Johannes Segitz on May 04
Hi,first of all let me take the opportunity to thank you for your work in this
area. I'm not a member of the distros list anymore (have been for years),
but I appreciate very much what you do for the community.
I agree. And I'm happy to see that this is being discussed, as I've seen
Daniel talking on Mastodon about this and it would be a shame if they
wouldn't provide their high quality reports to distributions up front...
20:34
AMD SoundWire Merged For Linux 6.4 Phoronix
Going back to 2016 Intel began working on MIPI SoundWire support for Linux and now in 2023, AMD has joined the party with their initial AMD SoundWire support driver landing in the mainline kernel...
20:32
ChatGPT and other AI-themed lures used to deliver malicious software Help Net Security
Since the beginning of 2023 until the end of April, out of 13,296 new domains created related to ChatGPT or OpenAI, 1 out of every 25 new domains were either malicious or potentially malicious, Check Point researchers have shared on Tuesday. On Wednesday, Meta said that, since March 2023, theyve blocked 1,000+ malicious links leveraging ChatGPT as a lure from being shared across their technologies (Facebook, WhatsApp, etc.). Impersonating ChatGPT Threat actors generally disguise malware More
The post ChatGPT and other AI-themed lures used to deliver malicious software appeared first on Help Net Security.
20:26
Apricorn introduces Aegis NVX hardware-encrypted USB storage device Help Net Security
Employing proprietary architecture, the Aegis NVX is the first Apricorn encrypted device to feature an NVME SSD inside, to address the immediate protection of raw data delivered directly from its source at high speeds. Initial capacity offerings will be 500GB, 1TB, and 2TB, with a price range of 280.00 600.00 MSRP. The NVX was conceived to meet demands and product requirements such as for use with high-definition video cameras with the capability to write More
The post Apricorn introduces Aegis NVX hardware-encrypted USB storage device appeared first on Help Net Security.
20:20
Printk Changes For Linux 6.4 Are Light With Still Waiting For Threaded/Atomic Console Phoronix
The printk code changes were merged last week for the ongoing Linux 6.4 merge window and it's notable not for what is in the pull request but rather what is still outstanding...
20:14
GPUOpen's Render Pipeline Shaders 1.1 Released With Linux Support Phoronix
At the end of last year AMD's GPUOpen group released the Render Pipeline Shaders "RPS" SDK for graphics applications and engines leveraging Direct3D 12 or Vulkasn as an open-source render graph framework. On Wednesday the Render Pipeline Shaders SDK 1.1 was released and is complemented by Linux support...
20:00
Chrome 114 Beta Brings CSS Headline Balancing, CHIPS, Popover API Phoronix
Following this week's release of the Chrome 113 web browser with faster AV1 encoding, Google engineers have promoted Chrome 114 to their beta channel...
19:55
T-Mobile Discloses Second Data Breach Since the Start of 2023 SoylentNews
T-Mobile disclosed the second data breach of 2023 after discovering that attackers had access to the personal information of hundreds of customers for more than a month, starting late February 2023.
Compared to previous data breaches reported by T-Mobile, the latest of which impacted 37 million people, this incident affected only 836 customers. Still, the amount of exposed information is highly extensive and exposes affected individuals to identity theft and phishing attacks.
"In March 2023, the measures we have in place to alert us to unauthorized activity worked as designed and we were able to determine that a bad actor gained access to limited information from a small number of T-Mobile accounts between late February and March 2023," the company said in data breach notification letters sent to affected individuals just before the weekend, on Friday, April 28, 2023.
T-Mobile said the threat actors didn't gain access to call records or affected individuals' personal financial account info, but the exposed personally identifiable information contains more than enough data for identity theft.
While the exposed information varied for each of the affected customers, it could include "full name, contact information, account number and associated phone numbers, T-Mobile account PIN, social security number, government ID, date of birth, balance due, internal codes that T-Mobile uses to service customer accounts (for example, rate plan and feature codes), and the number of lines."
After detecting the security breach, T-Mobile proactively reset account PINs for impacted customers and now offers them two years of free credit monitoring and identity theft detection services through Transunion myTrueIdentity.
Read more of this story at SoylentNews.
19:42
Links 04/05/2023: Amazon Lays Off 27,000, Musk Pulls an Andrew Lee (Hijacking Handles) Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
-
GNU/Linux
-
Server
-
Kubernetes Blog Kubernetes 1.27: StatefulSet PVC Auto-Deletion (beta)
Kubernetes v1.27 graduated to beta a new policy mechanism for
StatefulSetsthat controls the lifetime of theirPersistentVolumeClaims(PVCs). The new PVC retention policy lets users specify if the PVCs generat...
-
-
19:41
Vulkan 1.3.250 Released With Another New Extension From Valve Phoronix
Vulkan 1.3.250 is out today as the latest routine spec update and brings a handful of spec fixes plus one new extension...
19:37
Protecto boosts privacy protection with GPU technology from NVIDIA Help Net Security
Protecto announced it has been able to boost the performance of its privacy models on NVIDIA GPUs, allowing the discovery of privacy issues up to 10x faster than before. With the help of powerful NVIDIA GPU technology, Protecto has delivered robust privacy solutions that help protect organizations from data breaches and other privacy-related risks. Protectos collaboration with NVIDIA has significantly improved the speed and accuracy of privacy analysis. Our collaboration with NVIDIA has been a More
The post Protecto boosts privacy protection with GPU technology from NVIDIA appeared first on Help Net Security.
19:36
Gemini Links 04/05/2023: IDEs Reviewed, Chatbots Debunked Techrights
-
Games
-
Technical
-
IDE Shopping
Emacs was the first alternative I tried, really just because I know some people are able to really get into it and turn it into something powerful.
I learn new tools best by finding a good starter config and making tweaks until Im familiar enough where I could do it from scratch. I learned tiling window managers this way and am now currently using my own unique config, and its also how I got into Linux in the first place by starting with Ubuntu Gnome (back when Unity was still the default DE) and eventually finding my way to Arch. So to tackle Emacs I set myself up with a popular configuration framework called Doom Emacs.
[...]
If youre interested in the differences between Vim and Neovim youre probably better off having someone else explain them to you. But from what I understand, Neovim is just a fork of Vim thats meant to be more maintainable and allow for more powerful plugins.
After looking into and trying a couple different starter configs for Neovim, I eventually settled on LunarVim. Now LunarVim isnt so much a starter config. The projects website describes it as an IDE layer for Neovim with sane defaults, and because LunarVim installs itself alongside your existing Neovim install and separates the users config from its own, Id say that feels accurate.
-
Pumpkin Patch
Today I saw Brodie Robertsons latest video on the latest systemd feature, where you can reboot only the user space. I think that is pretty cool and welcome its development. However, I cant entirely think of scenarios where it would be needed, I mostly reboot because I want to reboot my entire system. AFAIK the user space reboot is everything except the kernel, so I guess one would use it when you undergone a standard update of packages, mostly?
-
Science/Sci-Fi
-
...
-
-
19:30
Intruder launches continuous attack surface monitoring for SMBs Help Net Security
Intruder has launched its continuous attack surface monitoring capabilities. The companys new premium plan offering takes vulnerability management to the next level with continuous coverage, increasing visibility and transparency of external attack surfaces. On average, 65 new vulnerabilities are discovered every day. Businesses of all sizes need visibility of a constantly evolving external attack surface, and to continually manage their exposure to avoid being breached. Intruders continuous network scanning includes adaptive attack surface scans, which More
The post Intruder launches continuous attack surface monitoring for SMBs appeared first on Help Net Security.
18:57
Meta Takes Down Malware Campaign That Used ChatGPT as a Lure to Steal Accounts The Hacker News
Meta said it took steps to take down more than 1,000 malicious URLs from being shared across its services that were found to leverage OpenAI's ChatGPT as a lure to propagate about 10 malware families since March 2023. The development comes against the backdrop of fake ChatGPT web browser extensions being increasingly used to steal users' Facebook account credentials with an aim to run
18:06
City of Dallas shut down IT services after ransomware attack Security Affairs
The City of Dallas, Texas, was hit by a ransomware attack that forced it to shut down some of its IT systems.
The IT systems at the City of Dallas, Texas, have been targeted by a ransomware attack. To prevent the threat from spreading within the network, the City has shut down the impacted IT systems.
The City confirmed the security incident and is working to recover from the ransomware attack that impacted its services, including the police department.
Wednesday morning, the Citys security monitoring tools notified our Security Operations Center (SOC) that a likely ransomware attack had been launched within our environment, reads the statement released by the City. Subsequently, the City has confirmed that a number of servers have been compromised with ransomware, impacting several functional areas, including the Dallas Police Department Website, The City team, along with its vendors, are actively working to isolate the ransomware to prevent its spread, to remove the ransomware from infected servers, and to restore any services currently impacted. The Mayor and City Council was notified of the incident pursuant to the Citys Incident Response Plan (IRP).
The attack impacted less than 200 devices and essential operations, like 911, remained working.
We have learned the attacks biggest impact is likely at the Dallas Police Department. reported the website of Fox4News. The department had reverted to its backup system, radio, to dispatch officers in response to 911 calls instead of its computer assisted dispatch system. DPD says there is no issue or delay with 911 calls coming in or being dispatched.
BleepingComputer reported that the Citys court system canceled all jury trials and jury duty from May 2nd into today. The incident may cause delays for online payment processing operated by Dallas Water Utilities.
The City is investigating the scope of the incident with the help of law enforcement, at this time has yet to disclose details on the incident, including the ransomware family that hit its systems and if there is a data breach.
However, CBS News Texas obtained an image the ransomware note dropped by the malware on the infected systems.
...18:03
Apple and Google join forces to combat AirTag stalking Graham Cluley
Apple and Google have announced that they are teaming up in order to combat the safety risks associated with AirTags and other tracking devices. Read more in my article on the Hot for Security blog.
18:00
Thermal Camera Plus Machine Learning Reads Passwords Off Keyboard Keys Hackaday

An age-old vulnerability of physical keypads is visibly worn keys. For example, a number pad with digits clearly worn from repeated use provides an attacker with a clear starting point. The same concept can be applied to keyboards by using a thermal camera with the help of machine learning, but it also turns out that some types of keys and typing styles are harder to read than others.
17:11
IBM Pauses Hiring to Onboard AI Instead SoylentNews
IBM to Stop Hiring for Jobs That AI Could Do
Routine tasks like transferring employees between departments are likely to be fully automated:
American tech major IBM anticipates pausing hiring for positions that it believes artificial intelligence (AI) will eventually take over.
In an interview with Bloomberg, IBM CEO Arvind Krishna said the company will suspend or pause hiring for back-office functions such as human resources.
The company employs some 26,000 people in these non-customer-facing roles, Krishna said.
"I could easily see 30% of that getting replaced by AI and automation over a five-year period," he added.
[...] Routine tasks like transferring employees between departments or providing letters of employment verification are likely to be fully automated, said the company's chief.
Over the next ten years, he continued, it is likely that some HR functions related to workforce composition analysis and productivity will not be replaced.
Read more of this story at SoylentNews.
17:04
IRC Proceedings: Wednesday, May 03, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-030523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-030523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-030523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-030523.gmi
Over HTTP:
|
... |
17:00
Understand Xi Jinpings Ideology to Grasp His Aggression in the Current Cold War Terra Forming Terra
Recent Case of Severe Microwave Syndrome Reveals Problems With 5G Terra Forming Terra
Unbelievable Preservation: Blood Found in Veins of Lady of Dai Mummy Terra Forming Terra
Net Zero and the Transhuman Agenda: War Against Nature and Humanity Terra Forming Terra

16:33
Bash see if an input number is an integer or not nixCraft
While working on the bash shell script wrapper, I needed to ensure that I only passed an integer in the Bash script under Linux and Unix-like systems. Here is how to check if a number is an integer in Bash Linux or Unix script or at the command-line interface (CLI)
Love this? sudo share_on: Twitter - Facebook - LinkedIn - Whatsapp - Reddit
The post Bash see if an input number is an integer or not appeared first on nixCraft.
16:23
Parkinsons disease-like gut dysbiosis detected in early stages of the disease Lifeboat News: The Blog
In a recent article published in the journal Nature Communications, researchers performed a large cross-sectional study to profile gut microbiota dysbiosis across prodromal and early stages of Parkinsons disease (PD), REM sleep behavior disorder (RBD), first-degree relatives of RBD (RBD-FDR), and healthy controls.
Study: Gut microbiome dysbiosis across early Parkinsons disease, REM sleep behavior disorder and their first-degree relatives. Image Credit: Anatomy Image / Shutterstock.
16:23
The first casualties of AI Lifeboat News: The Blog

Artificial intelligence has started to make a real impact on the world by replacing human jobs and making some business models obsolete. We take a look at this weeks biggest AI news and identify the biggest losers in the AI race.
#ai #tech #thecodereport.
 Chat
with Me on Discord.
Chat
with Me on Discord.
 Resources.
Resources.
Geoffrey Hinton Resigns
https://fortune.com/2023/05/01/godfather-ai-geoffrey-hinton-ad-actors/
Chegg ChatGPT decline
https://www.cnbc.com/2023/05/02/chegg-drops-more-than-40perciness.html.
Ibm replaced 7,800 Jobs with AI
https://www.reuters.com/technology/ibm-pause-hiring-plans-re05-01/
Elon Musk wants to Stop ChatGPT https://youtu.be/TpZcGhYp4rw.
16:22
Experiment demonstrates continuously operating optical fiber made of thin air Lifeboat News: The Blog
Great, until the mention of directed energy
Researchers at the University of Maryland (UMD) have demonstrated a continuously operating optical fiber made of thin air.
The most common optical fibers are strands of glass that tightly confine light over long distances. However, these fibers are not well-suited for guiding extremely high-power laser beams due to glass damage and scattering of laser energy out of the fiber. Additionally, the need for a physical support structure means that glass fiber must be laid down long in advance of light signal transmission or collection.
Howard Milchberg and his group in UMDs Departments of Physics and Electrical & Computer Engineering and Institute for Research in Electronics & Applied Physics have demonstrated an optical guiding method that beats both limitations, using auxiliary ultrashort laser pulses to sculpt fiber optic waveguides in the air itself.
15:34
Mirantis Pushes Security With Its New k0s 1.27 Kubernetes Release FOSS Force
Mirantis has released k0s 1.27 as the latest and greatest release, the focus seems to be on security.
The post Mirantis Pushes Security With Its New k0s 1.27 Kubernetes Release appeared first on FOSS Force.
15:00
Carbon Fiber and Kevlar Make This Linear Actuator Fast and Strong Hackaday

When it comes to the build versus buy question, buy almost always wins. The amount of time you have to put into building something is rarely justified, especially with a world of options available at the click of a mouse.
Thats not always the case, of course. These custom-made linear actuators are a perfect example of when building your own wins. For a planned ball-juggling robot, [Harrison Low] found himself in need of linear actuators with long throw distance, high speed, and stiff construction. Nothing commercially available checked all the boxes, so he set out to design his own.
A few design iterations later, [Harrison] arrived at the actuators you see in the video below. Built mainly from carbon fiber tubing and 3D-printed parts, the actuators have about 30 centimeters of throw, and thanks to their cable-drive design, theyre pretty fast much faster than his earlier lead screw designs. The stiffness of the actuator comes by way of six bearings to guide the arm, arranged in two tiers of three, each offset by 60 degrees. Along with some clever eccentric spacers to fine-tune positioning, this design provides six points of contact that really lock the tube into place.
The cable drive system [Harrison] used is pre...
14:27
The UK Doesnt Want Microsofts Activision Blizzard Deal, So What Happens Next? SoylentNews
Microsoft is furious. Last week, a surprise decision from the UK's Competition and Markets Authority (CMA) left its $68.7 billion deal to acquire Activision Blizzard blocked in Britain, thanks to concerns about the future of cloud gaming.
Microsoft president Brad Smith was awake at 2AM that morning hastily writing a response from across the pond, according to Bloomberg. He spoke to the BBC a day later and called the UK regulator's decision the "darkest day" for Microsoft in its four decades of working in Britain. He went a step further and said "the European Union is a more attractive place to start a business" than the UK, a particularly stinging statement given the political issues around Brexit.
Now, Microsoft is bruised, angry, and plotting its next move. If Brad Smith's fighting talk is anything to go by, Microsoft will try to keep this deal alive. But the CMA's decision won't be an easy one to appeal.
[...] Meta's battle with the CMA over its Giphy acquisition shows what Microsoft might be in store for. Meta was originally ordered to sell Giphy in 2021 but appealed the ruling and was unsuccessful. Meta eventually had to comply with the UK competition watchdog and divest itself of social media GIF library Giphy. Viagogo's $4 billion takeover of StubHub was also partially blocked by the CMA, forcing the company to keep StubHub's US and Canadian operations but sell its UK and international businesses.
[...] The CMA said in September that it was concerned about the effects of Microsoft owning Activision Blizzard games on existing rivals and emerging entrants offering multi-game subscriptions and cloud gaming services. I tweeted at the time that all of the headlines around Call of Duty were just noise, and there would be bigger concerns around Microsoft's ability to leverage Windows and Azure, unlike its competitors, and how it could influence game distribution and revenue shares across the game industry with its Xbox Game Pass subscription....
12:24
Mind-reading machines are here: is it time to worry? Lifeboat News: The Blog
Neurotech will bring many amazing positive changes to the world, such as treating ailments like blindness, depression, and epilepsy, giving us superhuman sensory capabilities that allow us to understand the world in new ways, accelerating our ability to cognitively process information, and more. But in an increasingly connected society, neuroprivacy will represent a crucial concern of the future. We must carefully devise legal protections against misuse of mind reading technology as well as heavily invest in neurocybersecurity R&D to prevent violation of peoples inner thoughts and feelings by authorities and malignant hackers. We can capitalize on the advantages, but we must do establish safety mechanisms as these technologies mature. #neurotechnology #neuroscience #neurotech #computationalbiology #future #brain
Determining how the brain creates meaning from language is enormously difficult, says Francisco Pereira, a neuroscientist at the US National Institute of Mental Health in Bethesda, Maryland. Its impressive to see someone pull it off.
Wake-up call
Neuroethicists are split on whether the latest advance represents a threat to mental privacy. Im not calling for panic, but the development of sophisticated, non-invasive technologies like this one seems to be closer on the horizon than we expected, says bioethicist Gabriel Lzaro-Muoz at Harvard Medical School in Boston. I think its a big wake-up call for policymakers and the public.
12:23
Magenta Medical Rakes In $55M for Worlds Smallest Heart Pump Lifeboat News: The Blog
Magenta Medical an Israeli company developing what it bills as the worlds smallest heart pump closed a $55 million financing round on Wednesday.
The round was led by OrbiMed, with participation from New Enterprise Associates, Pitango and Alive Israel HealthTech Fund. Magenta did not disclose how much the company has raised to date.
The new funding will be used primarily to help the medtech company attain FDA approval for its flagship product a percutaneous left ventricular assist device called Elevate.
12:23
Chronic kidney disease: New tool to predict cardiovascular disease Lifeboat News: The Blog
An effort led by researchers in the Perelman School of Medicine at the University of Pennsylvania has developed a new risk model for cardiovascular disease in CKD patients. The researchers say it is more accurate than current methods of measuring cardiac risk in these individuals.
A paper about the research was published in European Heart Journal.
12:23
An ambitious underwater space station just got a major research collaborator Lifeboat News: The Blog
Today, the National Oceanic and Atmospheric Administration announced that it will be signing a new research agreement with Proteus Ocean Group, which has been drawing up ambitious plans to build a roomy underwater research facility that can host scientists for long stays while they study the marine environment up close.
The facility, called Proteus, is the brainchild of Fabien Cousteau, the grandson of Jacques Cousteau.
On PROTEUS we will
have unbridled access to the ocean 24/7, making possible long-term
studies with continuous human observation and experimentation,
Cousteau, founder of Proteus Ocean Group, said in a press release. With NOAAs collaboration, the
discoveries we can make in relation to climate refugia, super
corals, life-saving drugs, micro environmental data tied to climate
events and many others will be truly groundbreaking. We look
forward to sharing those stories with the world.
we will
have unbridled access to the ocean 24/7, making possible long-term
studies with continuous human observation and experimentation,
Cousteau, founder of Proteus Ocean Group, said in a press release. With NOAAs collaboration, the
discoveries we can make in relation to climate refugia, super
corals, life-saving drugs, micro environmental data tied to climate
events and many others will be truly groundbreaking. We look
forward to sharing those stories with the world.
12:23
Concussion: almost half of people still show signs of brain injury after six months Lifeboat News: The Blog
Our research found that concussion was associated with increased functional connectivity between the thalamus and the rest of the brain very shortly after injury, when compared to 76 healthy control subjects.
In other words, the thalamus was trying to communicate more as a result of the injury. This was despite routine MRI and CT imaging showing no structural changes in the brain.
While many of us would assume that more connectivity in the brain is a good thing, research looking at more severe head injuries indicates that greater connectivity between brain regions might actually be a sign of the brain trying to compensate and offset damage across the brain.
12:22
UT Austin researchers develop AI system to translate brain activity into text Lifeboat News: The Blog
AUSTIN, Texas Scientists at the University of Texas at Austin have created an artificial intelligence (AI) tool that can turn peoples brain activity into written text. This technology might help those who cant physically speak, like stroke patients, communicate again.
12:00
How To Install Mac OS on the Nintendo Wii Hackaday

What if you could run Mac OS on a Nintendo Wii game console? Thats probably not a thought that has occurred to many Wii owners or Mac OS users, but that is no excuse not to give it a try, as [Michael] handily demonstrates in a recent video by running Mac OS 9 on a Nintendos legendary console. The first major issue is what anyone who has ever tried to put a Hackintosh together knows: just because a target system runs the same CPU architecture can you necessarily install Mac OS (or OS X) for Intel x86 on any Intel x86 system. The same is true for the Wii with its PowerPC CPU and running Mac OS 9 for PowerPC on it.
In order to make this work, a workaround is employed, which uses the fossilized Mac-on-Linux project to run PowerPC Mac OS essentially on Linux for the Wii. This is a kernel module which allows Mac OS to run at basically native speeds on Linux, but it being a Linux kernel module, it meant that [Michael] had to hunt down the correct kernel to go with...
11:41
Brain Scans Can Translate a Persons Thoughts Into Words SoylentNews
A noninvasive brain-computer interface capable of converting a person's thoughts into words could one day help people who have lost the ability to speak as a result of injuries like strokes or conditions including ALS.
In a new study, published in Nature Neuroscience today, a model trained on functional magnetic resonance imaging scans of three volunteers was able to predict whole sentences they were hearing with surprising accuracyjust by looking at their brain activity. The findings demonstrate the need for future policies to protect our brain data, the team says.
Speech has been decoded from brain activity before, but the process typically requires highly invasive electrode devices to be embedded within a person's brain. Other noninvasive systems have tended to be restricted to decoding single words or short phrases.
This is the first time whole sentences have been produced from noninvasive brain recordings collected through fMRI, according to the interface's creators, a team of researchers from the University of Texas at Austin. While normal MRI takes pictures of the structure of the brain, functional MRI scans evaluate blood flow in the brain, depicting which parts are activated by certain activities.
[...] Romain Brette, a theoretical neuroscientist at the Vision Institute in Paris who was not involved in the experiment, is not wholly convinced by the technology's efficacy at this stage. "The way the algorithm works is basically that an AI model makes up sentences from vague information about the semantic field of the sentences inferred from the brain scan," he says. "There might be some interesting use cases, like inferring what you have dreamed about, on a general level. But I'm a bit skeptical that we're really approaching thought-reading level."
Read more of this story at SoylentNews.
11:37
Links 03/05/2023: More Predictions of Xbox Demise/Doom and More Dirty Tricks From Microsoft Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
-
GNU/Linux
-
Desktop/Laptop
-
The NovaCustom NV41 Series laptop is Qubes-certified!
It is our pleasure to announce that the NovaCustom NV41 Series laptop has become the fifth Qubes-certified computer for Qubes 4.X!
About the NovaCustom NV41 Series
The NV41 Series...
-
-
11:35
NEW 'Off The Hook' ONLINE 2600 - 2600: The Hacker Quarterly
NEW 'Off The Hook' ONLINE
Posted 04 May, 2023 1:35:33 UTC
The new edition of Off The Hook from 05/03/2023 has been archived and is now available online.
2600 is 40 years old, Missouri trans snitch form taken offline, Pornhub blocks users in Utah, MTA will no longer post on Twitter, Indiana zoo website hacked, Google replacing passwords with passkeys.
11:32
Gemini Links 03/05/2023: Scepticism of the State of Modern Computing Techrights
-
Gemini* and Gopher
-
Personal
-
Sunrise and Bird Song 2023-05-03 (Fairbanks, AK, USA)
This morning I went back to the same spot on the east side of the UAF hill and took some more sunrise photos. This time I did not get as much of that purple twlight effect, owing I think to the clouds being at a lower altitude. But I was still able to get a good number of nice photos from twilight to dawn.
-
Yretek It seems I have fallen off the wagon
Fear your wishes for they might become true, they say, or something of that sort. In my case Ive got two: a promotion for which I had worked for so long and, on top of that, it seems Im a game-master again. The curse with the first wish is that I have to go to another office. This came unexpected as theres actually a lot of work to do where Im currently stationed. [...]
Its that Ive been posting less often. Not a big deal, to be honest, I dont want to be a slave to the Gemini, but it makes harder to come up with ideas for a new post. So, you see, thats the main reason for this one.
-
-
Technical
-
P E R M A C O M P U T E R
Ive ranted quite a bit on my phlog on the state of modern computing and the direction were headed. And now with LLM being a fad, things have gotten so much worse yet again. A few weeks ago the Washington Post released an article (1) with therein a widget that lets you look up whether your website has been scraped by AI or not. I was dissapointed (but not surprised) to find out that they had scraped, not only my websites (ignoring robots.txt), but also gopher proxies, and presumably gemini http proxies as well. What this means is they likely slurped up all of gopherspace and gemspace as well. I do not consent to this. Anyhow,
-
Gobs and gobs of gobs and gobs
My bookm...
-
-
10:23
The Role of Chat-GPT in Improving Mental Health Care and Therapy Lifeboat News: The Blog
Given the rise of chat gpt and its volumes of knowledge bases
there is a new chat bot that is aiding mental health care and
therapy 
When it comes to mental health, the main focus is on the patient and how to provide the best care possible. But with the rising demand for mental health services, its increasingly difficult for clinicians to address the individual needs of their patients and meet the growing demand for mental health services. This is where ChAT-GPT, or Conversational Artificial intelligence-based Therapy for Generalized Psychological Treatment, comes in.
Chat-GPT is an AI-based therapy that uses natural language processing (NLP) and conversational AI to help therapists provide more personalized and effective mental health care and therapy. This new technology allows mental health professionals to provide real-time and personalized care to their patients in a way that is tailored to their needs and preferences. In this article, we will discuss the key features of Chat-GPT and how it is helping improve mental health care and therapy.
Chat-GPT is a type of AI-based therapy developed by researchers at Albert Einstein College of Medicine. It is a conversational AI-based therapy designed to help clinicians diagnose mental health issues. Chat-GPT uses natural language processing (NLP) to understand the patients conversations and provide personalized care and therapy.
10:02
[$] LWN.net Weekly Edition for May 4, 2023 LWN.net
The LWN.net Weekly Edition for May 4, 2023 is available.
10:00
HPR3849: trouble shooting Hacker Public Radio
Kernel message Click the thumbnail to see the full-sized image BIOS message Click the thumbnail to see the full-sized image CMOS Click the thumbnail to see the full-sized image RAM Click the thumbnail to see the full-sized image Mother board side Click the thumbnail to see the full-sized image The culprit Click the thumbnail to see the full-sized image
09:36
Smashing Security podcast #320: City Jerks, AI animals, and is the BBC hacking again? Graham Cluley
Two unsavoury websites suffer from a worrying leak, scientists are going animal crackers over AI, and the BBC is intercepting scammers' live phone calls with victims. All this and much much more is discussed in the latest edition of the "Smashing Security" podcast by computer security veterans Graham Cluley and Carole Theriault, joined this week by The Lazarus Heist's Geoff White.
09:00
Microsoft's Linux Distribution Finally Adds Support For XFS Root File-Systems Phoronix
While many Linux distributions look at Btrfs or F2FS when evaluating new root file-system options or even something like OpenZFS, in the case of Microsoft's in-house Linux distribution only this month have they even gotten to supporting XFS as a root file-system option...
08:58
CERN Celebrates 30th Anniversary of the World Wide Web SoylentNews
Software vendors and the EU werent interested, so giving it away became the best option:
The European Organization for Nuclear Research (CERN) on Sunday celebrated the 30th anniversary of releasing the World Wide Web into the public domain.
As the World Wide Web Consortium's brief history of the web explains, in 1989 Tim Berners-Lee - then a fellow at CERN - proposed that the organization adopt "a global hypertext system." His first name for the project was "Mesh".
And as the Consortium records, in 1990 Berners-Lee set to work on "a hypertext GUI browser+editor using the NeXTStep development environment. He makes up 'WorldWideWeb' as a name for the program."
Berners-Lee's work gathered a very appreciative audience inside CERN, and soon started to attract attention elsewhere. By January 1993, the world had around 50 HTTP servers. The following month, the first graphical browser Marc Andreessen's Mosaic appeared.
Alternative hypertext tools, like Gopher, started to lose their luster.
On April 30, 1993, CERN signed off on a decision that the World Wide Web a client, server, and library of code created under its roof belonged to humanity (the letter was duly stamped on May 3).
"CERN relinquishes all intellectual property rights to this code, both source and binary form, and permission is granted for anyone to use, duplicate, modify and redistribute it" states a letter signed on that day by Walter Hoogland and Helmut Weber at the time respectively CERN's director of research and director of administration.
Read more of this story at SoylentNews.
08:41
Understanding the business value of the OSPO Linux.com

Read the original blog at Read More
The post Understanding the business value of the OSPO appeared first on Linux.com.
08:29
A Huge Thank You to This Years Embedded Open Source Summit Program Committee Linux.com

Read the original blog at Read More
The post A Huge Thank You to This Years Embedded Open Source Summit Program Committee appeared first on Linux.com.
07:57
Re: Perl's HTTP::Tiny has insecure TLS cert default, affecting CPAN.pm and other modules Open Source Security
Posted by Michael Orlitzky on May 03
They're both bad defaults. One explicitly does no authentication, whilethe other uses a corrupt and misunderstood process that can create a
false sense of security. We disagree on which is worse, but neither
viewpoint is ludicrous.
07:11
Authorities dismantled the card-checking platform Try2Check Security Affairs
Authorities dismantled the Try2Check platform, a Card-Checking platform that generated tens of millions of dollars in revenue.
The U.S. DoJ charged the Russian citizen Denis Gennadievich Kulkov with running the Card-Checking services. The platform has been active since 2005, according to the DoJ, it generated tens of millions of dollars in revenue. The service allowed crooks to check the status of bulks of stolen credit card data that were purchased or sold by cybercriminals.
Try2Check ran tens of millions of credit card checks per year and supported the operations of major card shops that made hundreds of millions in bitcoin in profits. Over a nine-month period in 2018, the site performed at least 16 million checks, and over a 13-month period beginning in September 2021, the site performed at least 17 million checks. reads the press release published by the DoJ. Through the illegal operation of his websites, the defendant made at least $18 million in bitcoin (as well as an unknown amount through other payment systems), which he used to purchase a Ferrari, among other luxury items.
The indictment is the result of a law enforcement operation conducted by the U.S. government along with peers in Germany and Austria. The authorities dismantled the defendants criminal network and the State Department also announced a $10 million reward for information leading to the capture of Kulkov, who is currently residing in Russia.
Today is a bad day for criminals who relied on the defendants platform as the gold standard to verify that the credit cards they stole from hard working individuals living in the Eastern District of New York and across the world had value, stated United States Attorney Peace. Todays indictment and global takedown of the Try2Check websit...
07:00
Mesa 23.1 Inches Closer To Release With RC4 Released Phoronix
Mesa 23.1 will likely be released in the next week or two while out today is Mesa 23.1-RC4 to facilitate more last minute testing by Linux gamers and other stakeholders for this set of open-source OpenGL / Vulkan / video acceleration drivers...
06:47
Re: Perl's HTTP::Tiny has insecure TLS cert default, affecting CPAN.pm and other modules Open Source Security
Posted by Moritz Bechler on May 03
Hi,while one may criticize that CVEs have been assigned both for the
insecure default and (some of the) insecure usages, at least one of
these is a legitimate case, in terms of CVEs likely the latter. And when
it comes to defaming projects, at least in my book, choosing, keeping
and defending bad defaults speaks to much more than a CVE being assigned.
Moritz
06:19
Re: Perl's HTTP::Tiny has insecure TLS cert default, affecting CPAN.pm and other modules Open Source Security
Posted by Reid Sutherland on May 03
A default is not a vulnerability. There are reasons why defaults cannotbe changed in libraries once they are stable. This is also why
documentation exists.
Revoke these CVEs, it's a stain on the process.
06:17
Re: Perl's HTTP::Tiny has insecure TLS cert default, affecting CPAN.pm and other modules Open Source Security
Posted by Jeffrey Walton on May 03
"Who decides" can be a tricky question.Several organizations issue CVEs, like Red Hat and Gentoo. A bug
usually has to meet a criteria, like falling into a CWE category, to
be issued by the organization.
You can also get them from Mitre's site. In the case of Mitre, it is
the person who requests the CVE.
Some CVE's are tenuous or questionable. You often see this from folks
trying to pad their resume. For example, a...
06:11
Pornhub Protests Utah Age Verification Law by Blocking the State's Access SoylentNews
Pornhub protests Utah age verification law by blocking the state's access:
MindGeek, the owner of adult platforms such as Pornhub, has blocked everyone in Utah from accessing its sites in protest of the state's age verification law that has just come into effect.
Utah has been fighting against online pornography for years. It called porn a public health crisis in 2016 and previously proposed that all smartphones and tablets in the state automatically block pornography. An age verification law was eventually passed in March, requiring users visiting adult platforms deemed "harmful to minors" to verify their age before being allowed access. Axios writes that any companies that don't comply with the law will be liable if they're sued over minors accessing their content.
Now that the law has gone into effect, MindGeek has responded by blocking anyone in Utah who tries to access Pornhub. Those with Utah IPs will see only a video of adult performer Cherie DeVille, a member of the Adult Performer Advocacy Committee, explaining the reason for the block.
"As you may know, your elected officials in Utah are requiring us to verify your age before allowing you access to our website," DeVille says. "While safety and compliance are at the forefront of our mission, giving your ID card every time you want to visit an adult platform is not the most effective solution for protecting our users, and in fact, will put children and your privacy at risk."
DeVille adds that "mandating age verification without proper enforcement" drives users to other sites with fewer safety measures in place.
[...] Utah's new laws also extend to social media companies. From March 1 next year, those under 18 will require a parent's permission before opening an account on social media platforms. Companies must also give parents access to their kids' posts, messages, and responses; are barred "from using a design or feature that causes a minor to have an addiction to the company's social media platform;" and must block under-18s from using social media between 10:30 pm and 6:30 am.
Read more of this story at SoylentNews.
05:59
Joe Biden Engaged In A Bribery Scheme With A Foreign National: FBI Internal Document Alleges cryptogon.com
Via: ZeroHedge: President Joe Biden allegedly participated in a criminal scheme to exchange money for policy decisions, according to Sen. Chuck Grassley (R-IA) and Rep. James Comer (R-KY), citing an internal FBI document they say contains evidence of the alleged bribery which took place when Biden was Vice President. We have received legally protected and []
05:56
Re: Perl's HTTP::Tiny has insecure TLS cert default, affecting CPAN.pm and other modules Open Source Security
Posted by David A. Wheeler on May 03
There's a process for assigning CVEs. Anyone who wants to be able to assign CVEs - that is, to become a CVE NumberingAuthority (CNA) - has to follow various processes. I'm sure it can be improved, like all things. I'm not directly
involved in this. You might find more information here:
https://www.cve.org/ProgramOrganization/CNAs
Identifying a vulnerability does not defame a project. If a library has the functionality to...
05:44
Organoid Intelligence cryptogon.com
Via: Forbes: While the world has been captivated by recent advances in artificial intelligence, researchers at Johns Hopkins University have identified a new form of intelligence: organoid intelligence. A future where computers are powered by lab-grown brain cells may be closer than we could ever have imagined. What is an organoid? Organoids are three-dimensional tissue []
05:21
Re: Perl's HTTP::Tiny has insecure TLS cert default, affecting CPAN.pm and other modules Open Source Security
Posted by Reid Sutherland on May 03
Who actually decides when something receives a CVE? This can be used todefame projects and products as in this case.
05:10
Russia Claims Drone Attack on Kremlin cryptogon.com
I dont know. That looks like pyrotechnics, not high explosives, to me. #BREAKING Clear footage of drone attack on Russias Kremlin overnight. pic.twitter.com/WYUqaGAq19 Clash Report (@clashreport) May 3, 2023 What do you think? Via: The War Zone: Video has emerged showing what appears to be a drone striking at the dome of the Senatsky []
05:02
semi-public issues on (linux-)distros Open Source Security
Posted by Solar Designer on May 03
Hi,Sometimes upstream projects want to make a security fix technically
public (such as in a git repository and/or on a mailing list) before it
is included in a release and announced as such. This lets those
projects use their usual development, review, and testing workflow
instead of having to switch to a special security fix workflow, which
can save the maintainers time and provide greater quality assurance
(more eyes, more testing)....
04:51
Seized: 9 Crypto Laundering Sites Used by Ransomware Gangs HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
International cooperation between the Ukrainian Cyber and National Police, the FBI, and the Department of Justice has led to the seizure of cybercriminals' cryptocurrency laundering websites.
This is a post from HackRead.com Read the original post: Seized: 9 Crypto Laundering Sites Used by Ransomware Gangs
04:44
Portland, Oregon: What Happened To This Place? cryptogon.com
Via: Hood Time:
04:41
Passwordless sign-in with passkeys is now available for Google accounts Security Affairs
Google announced the introduction of the passwordless secure sign-in with Passkeys for Google Accounts on all platforms.
Google is rolling out the passwordless secure sign-in with Passkeys for Google Accounts on all platforms.
Passwords are essential to protect services and data online, but when obtained by threat actors they can pose a risk to the users.
Despite the IT giant has implemented defenses like 2-Step Verification and Google Password Manager, it recognizes that to really address password issues, it is necessary to adopt passwordless solutions. This means that when a user signs into a website or app on his/her phone, he/she will simply unlock the phone without needing a password for the account anymore.
In 2022, Google announced it would begin work to support passkeys on its platform to replace passwords. The day has come, and Google has begun rolling out support for passkeys across Google Accounts on all major platforms.
passkeys let users sign in to apps and sites the same way they unlock their devices: with a fingerprint, a face scan or a screen lock PIN. And, unlike passwords, passkeys are resistant to online attacks like phishing, making them more secure than things like SMS one-time codes. reads the announcement published by the company. Over the past year weve shared updates on bringing passkey experiences to both Chrome and Android, which services like Docusign, Kayak, PayPal, Shopify and Yahoo! Japan have already deployed to streamline sign-in for their users. Starting today, this will be available as an option for Google Account users who want to try a passwordless sign-in experience.R...
04:30
Quantum Supremacy Not Even Wrong
Were hearing this week from two very different parts of the string theory community that quantum supremacy (quantum computers doing better than classical computers) is the answer to the challenges the subject has faced.
New Scientist has an article Quantum computers could simulate a black hole in the next decade which tells us that Understanding the interactions between quantum physics and gravity within a black hole is one of the thorniest problems in physics, but quantum computers could soon offer an answer. The article is about this preprint from Juan the BFSS matrix model, a 1996 proposal for a definition of M-theory that never worked out. Maldacena points to this recent Monte-Carlo calculation, which claims to get results consistent with expectations from duality with supergravity.
Maldacenas proposal is basically for a variant of the wormhole publicity stunt: he argues that if you have a large enough quantum computer, you can do a better calculation than the recent Monte-Carlo. In principle you could look for quasi-normal modes in the data, and then you would have created not a wormhole but a black hole and be doing quantum gravity in the laboratory
seeing these quasinormal modes from a quantum simulation of the quantum system under discussion, would be a convincing evidence that we have created something that behaves as a black hole in the laboratory.
This isnt a publicity stunt like the wormhole one, because the only publicity Ive seen is a New Scientist article, and this is just a proposal, not actually executed. Maldacena estimates that to reproduce the recent Monte-Carlo calculation youd need 7000 or so logical qubits, which the New Scientist reporter explains would be something like one million physical qubits. So, theres no danger Quanta magazine will be producing videos about the creation of a black hole in a Google lab any time soon.
Maldacena has been chosen to give the presentation tomorrow at the SLAC P5 Town Hall about a vision for the future of fundamental theory, no idea whether creating black holes in the lab using quantum computers will be part of it.
At the other extreme of respectability and influence in the physics community, Michio Kaku has a new book out, Quantum Supremacy. I took a quick look yesterday at a c...
04:23
New UK Cybersecurity Campaign Leads Kids Directly to Pirate Apps & Malware TorrentFreak
 To
reduce the chances of being tracked, profiled, spammed with
malicious ads, infected with malware or subjected to ransomware, no
device in this building accesses the internet without stringent
filtering.
To
reduce the chances of being tracked, profiled, spammed with
malicious ads, infected with malware or subjected to ransomware, no
device in this building accesses the internet without stringent
filtering.
With network tools and browser plugins doing some of the heavy lifting, WireGuard VPN connections help to keep the dangers at bay. In todays online environment, every little helps and on this network, a little amounts to millions of URLs blocked every year.
A new government initiative launched today on the website of the National Cyber Security Centre (NCSC) sounded interesting; at least until the website started delivering broken and insecure HTTP pages in an apparent protest against an encrypted connection.
Having to reduce network security to read what the NCSC had to say about staying safe online wasnt a great start. Worringly, things only went downhill from there.
Campaign to Raise Kids Awareness of Online Harms
The new awareness campaign targets pre-teens and young teenagers and is designed to raise awareness of some of the risks theyre likely to encounter when using the web.
A key feature is described as an interactive video learning resource which amounts to short video clips of a longer story, punctuated by multiple choice questions relating to decisions for staying safe online. For the strictly over 18s, think Black Mirrors Bandersnatch but on a much tighter budget.
Young people are growing up in an increasingly digital world, exposing them to both the opportunities and risks of the internet, the NCSC campaign website notes.
CyberFlix highlights some of the most common cyber scams and malicious activity that a pre-teen and teenage internet user might come across and empowers them to make choices to keep themselves more secure online.
Hard to Believ...
04:13
Federal Reserve Pushes Interest Rates Above 5%, First Time Since 2007 cryptogon.com
Via: Yahoo Finance: The Federal Reserve raised the target range for its benchmark interest rate by 0.25% on Wednesday while left its options open on future rate hikes.
04:08
What are Residential proxies and what is their use? HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
Residential proxies are IP addresses assigned to real residential devices, such as laptops or smartphones, that are provided
This is a post from HackRead.com Read the original post: What are Residential proxies and what is their use?
04:04
[$] Namespaces for the Python Package Index LWN.net
The Python packaging picture is generally a bit murky; there are lots of different stakeholders, with disparate wishes and needs, which all adds up to a fairly large set of multi-faceted problems. Back in the first three months of the year, we looked at various discussions around packaging, some of which are still ongoing. A packaging summit was held at PyCon 2023 to bring some of the participants of those discussions together in one room. One of its sessions was on adding a namespaces feature to the Python Package Index (PyPI). It provides a look into some of the difficulties that can arise, especially when trying to accommodate a long legacy of existing practices, which is often a millstone around the neck of those trying to make packaging improvements.
04:02
Bank Failures Visualized cryptogon.com
Via: Mike Bostock: Related: The Banking Collapse Of 2023 Is Now Officially Bigger Than The Banking Collapse Of 2008
04:00
IEEE Foundation Celebrates 50 Years of Philanthropy IEEE Spectrum

Since its launch in 1973, the IEEE Foundation has raised more than US $135 million for more than 250 IEEE programs that improve access to technology, enhance technological literacy, and support education.
IEEEs philanthropic partner is celebrating its 50th anniversary with several events that showcase the profound impact donors around the world have made. It also has introduced new ways to recognize its donors and has added a focus area where contributions will be directed.
As the IEEE Foundation marks its 50-year anniversary, the global need for sustainable development, Internet access, STEM education and inspiring a new, diverse generation of technologists to take up such worthy endeavors has never been greater, Ralph Ford, the Foundations president, said in a news release about the anniversary. Generous donors and members are the lifeblood fueling the IEEE Foundations world-changing initiatives, which have positively impacted thousands of communities.
Here is a look at some of the events and a number of the programs that have benefited from donors generosity.
Celebrating with tech pioneers
The celebrations kicked off in February with an event held at the Sheraton New York hotel in Times Square.
Over the past 50 years, IEEE Foundation leaders, volunteers, and donors have impacted the lives of so many throughout the world, John McDonald, chair of the 50th-anniversary celebration committee, said during his welcoming remarks. He and his wife have been donors for decades. I have personally witnessed how these contributions have made a meaningful and lasting impact. I look forward to working with all of you to increase our impact, expand our network, and establish even more partnerships with IEEE members, volunteers, and philanthropists.
I look forward to partnering with the IEEE Foundation to make meaningful philanthropic investments that encourage comprehensive and intelligent ways of using technology to improve conditions for people around the world, added...
03:48
Nordstrom Shutting Down Stores in Crime-Ridden San Francisco cryptogon.com
Changed dynamics Via: Daily Mail: Nordstrom announced it as closing all of its San Francisco stores, blaming the changed dynamics of the city which has seen numerous major chains turn-tail in the face soaring crime. The retailer told employees it would not be renewing its leases at the Westfield Mall or at the Nordstrom Rack []
03:36
5 Strategies for Corporate Patent Portfolio Decision Making IEEE Spectrum

Is your organization looking to tighten costs, including the costs of patent portfolio maintenance?
Intellectual property teams need to be prepared to shoulder their share of budget reductions. This means being prepared to analyze a potentially expansive portfolio and decide what to prune while also limiting the impact on any single business unit or region.
In our latest white paper, we explore how a multi-dimensional review of your companys patent portfolio may lead to more than short-term cost savings. It can also help strengthen the portfolio and highlight opportunities for monetization.
Download Finding cost efficiencies in patent portfolio maintenance to uncover five strategies for corporate patent portfolio decision making.
03:27
the Godfather of AI Leaves Google Amid Ethical Concerns SoylentNews
The Morning After: the Godfather of AI Leaves Google Amid Ethical Concerns
The Morning After: The Godfather of AI leaves Google amid ethical concerns:
Geoffrey Hinton, nicknamed the Godfather of AI, told The New York Times he resigned as Google VP and engineering fellow in April to freely warn of the risks associated with the technology. The researcher is concerned Google is giving up its previous restraint on public AI releases to compete with ChatGPT, Bing Chat and similar models. In the near term, Hinton says he's worried that generative AI could lead to a wave of misinformation. You might "not be able to know what is true anymore," he says. He's also concerned it might not just eliminate "drudge work," but outright replace some jobs which I think is a valid worry already turning into a reality.
Read more of this story at SoylentNews.
03:15
Links 03/05/2023: KDE ISO Image Writer 1.0.0 and Flatseal 2.0 Released Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
-
GNU/Linux
-
Linux Format 302
Get hacking with Kali Linux, grab the latest Linux Format and arm yourself with the tools and the hacking knowledge to defend your systems and train yourself as a white-hat hacker! Discover Kali Purple, Metasploit and the best way to run Kali Linux.
-
Audiocasts/Shows
-
Krita ...
-
-
03:10
Gemini Links 03/05/2023: Were Still Experimenting (Hence Short List Again), Someone is Writing a Gemini Server in Raku Techrights
-
Gemini* and Gopher
-
Personal
-
Best viewed in monospaced font
searching is suffering
which is enduring time
it leads to more holes
to search that lead to
seemingly endless more
same thing for knowing
so guess what internet
leads to time and time
again just more of the
same disease of search
-
-
Technical
-
Programming
-
Writing a Gemini server in Raku
Every now and then I get an urge to do something new. Usually it involves picking up a new language or a framework or a project to spend time with and on. Implementing a gemini server sounded like a nice exercise and since I was starting to feel the urge, I picked a new language as well. As you read in the title, it was Raku[1]. To tick all the boxes, I also jumped straight into using Cro[2], but more on that later.
[...]
Everything seemed to work using print+socat based cli client, it seemed to work with amfora, but with lagrange, the server got stuck on second request. Turned out lagrange by default resumes TLS sessions which was tripping up whatever the server was doing.
A thing I didnt see coming was how resource intensive it is. Just for the hell of it I tried downloading a 4GB disk image from it. The whole transfer took ~25 seconds, but while the file was being sent over, the raku process was eating up around 200% cpu. I know looking at htop is rather unscientific method of measuring cpu usage, but still I wouldnt expect it to be so intensive. It is quite possible Im doing something silly in there.
-
-
-
* Gemini (Primer) links can be opened using Gemini software. Its like the World Wide Web but a lot lighter.
02:48
Mesa Vulkan KHR_present_wait Support Extended To Wayland Phoronix
VK_KHR_present_wait is an extension originally started by Keith Packard working for Valve on improving the Linux graphics stack. The VK_KHR_present_wait extension allows for waiting for present operations to complete and can be used for monitoring/pacing the application by managing the number of images not yet presented. This Vulkan extension had been supported by Mesa Vulkan drivers under X.Org and now is being enabled for Wayland environments too...
02:29
rpki-client 8.4 released OpenBSD Journal
Version 8.4 of rpki-client has been released, with a number of improvements and new features:
rpki-client8.4 has just been released and will be available in the rpki-client directory of any OpenBSD mirror soon. rpki-client is a FREE, easy-to-use implementation of the Resource Public Key Infrastructure (RPKI) for Relying Parties (RP) to facilitate validation of BGP announcements. The program queries the global RPKI repository system and validates untrusted network inputs. The program outputs validated ROA payloads, BGPsec Router keys, and ASPA payloads in configuration formats suitable for OpenBGPD and BIRD, and supports emitting CSV and JSON for consumption by other routing stacks.
01:27
A Huge Thank You to This Years Embedded Open Source Summit Program Committee Linux.com
read the original post at Read More
The post A Huge Thank You to This Years Embedded Open Source Summit Program Committee appeared first on Linux.com.
01:20
Creating a Minimum Elements SPDX SBOM Document in 5 Minutes Linux.com


The rise in cyberattacks and softwares critical role in our lives has brought to light the need for increased transparency and accountability in the software supply chain. Software distributors can achieve this by providing software bills of materials (SBOMs), which provide a comprehensive list of all the components used in a software product, including open source and proprietary code, libraries, and dependencies.
In May 2021, United States Executive Order 14028 on improving the nations cybersecurity emphasized the importance of SBOMs in protecting the software supply chain. After comprehensive proof of concepts using the Software Package Data Exchange format (SPDX), the National Telecommunications and Information Administration (NTIA) released the minimum elements for an SBOM. The minimum elements require data fields that enable basic use cases:
- Supplier Name
- Component Name
- Version of the Component
- Other Unique Identifiers
- Dependency Relationship
- Author of SBOM Data
- Timestamp
The NTIA recommends that the...
Wednesday, 03 May
19:00
Melbet On Line Casino Evaluation 2023 Get 20,000 Bonus In India h+ Media
Melbet On Line Casino Evaluation 2023 Get 20,000 Bonus In India
Activate your telephone number and as quickly as its carried out yourfree spinswill be waiting for you in your account. Deposit 8000 and get one other 8000 from WBC champion Oleksandr Gvozdyk! Sean is a proficient sports activities and on line casino content material editor who was born and raised in England. He has at all times had a love for sports, notably football and cricket, and has been an avid sports activities bettor for many years.
You can wager on over 100 matches and tournaments, including Twenty20 Challenge, third ODI Women, Regional tremendous 50, Ford Trophy, ICC World Cup, and many more. Melbet bookmaker supplies greater than 200 daily stay events, with each experienced and new punters having quick access to 1,000+ matches in sportsbook. All their live on line casino betting games may be simply accessed through reside streams, encouraging social interactions with others proper at the comfort of your house. The leading providers of their live on line casino part are NetEnt, Evolution Gaming, Asia Gaming, Lucky Streak, and SA Gaming with their lovely Asian sellers to call a few. So, you could be assured of the gaming expertise and quality. However, theyve a quantity of slides on the homepage to quickly navigate you to their necessary features.
At the time of registration, you instantly choose which bonus you are going to use. If you choose the casino bonus, you will not be able to spend the money on sports activities betting. You will have the ability to change your determination to decide on a bonus earlier than your first deposit. The wordsmith of the group, Shruti is busy having fun with her newfound ardour for online casino video games. When shes joyful, she would guess the ranch to plan and create killer on line casino content the ones that urge you to play. If things dont go the way in which she desires them to, she would continually act like the world is about to end.
- A lot of background checks are done so as to achieve one of these licences and its clear that Melbet has adopted the entire appropriate checks and procedures.
- The bonus might be credited to the customers account routinely after the primary deposit is made, except the box I do not want any bonuses is ticked.
- It is a reliable and trustworthy bookmaker with excellent odds, generous bonuses, and plenty of video games for you to select from.
- Moreover, different combinations give completely different winnings and bonuses.
Melbet casino has a huge selection of slots from 89 completely different software vendors. There are separate jackpot slots, 3D slot machines and all types of desk video games on the site. You will find the finest option for you with low, medium, and high volatility, a great price of return, and easy rules.
On the third deposit, MelBet will provide a b...
18:59
Melbet Casino Evaluation In India Bestcasinoindia h+ Media
Melbet Casino Evaluation In India Bestcasinoindia
Whether youre an skilled bettor or a newbie, youll find a way to get pleasure from a thrilling and rewarding betting expertise. Sign up for Melbet Bangladesh today and begin betting on your favorite sports and on line casino games. You can win massive and expertise the thrill of online betting with Melbet Bangladesh. Among these online casinos, Melbet stands out as an distinctive platform with a powerful assortment of video games from top software program providers within the business. The casinos numerous vary of video games guarantees that gamers will always have one thing new and thrilling to explore, making their gaming expertise even more thrilling. Whether gamers prefer slots, table video games, or reside dealer video games, Melbet has all of it covered, guaranteeing that each player finds their excellent sport.
Melbet has a group of customer support that offers assist to the customers through live chat or telephone calls. However, the help supplied by them is slow and tedious. The process of getting assistance is so tough that prospects get irritated and ultimately stop enjoying it.
Bonomo achieves success against a few of the worlds finest gamers because of his quick wit for the game. His successful streaks are complemented by numerous different final desk appearances. Bonomo, a dominant drive within the trendy recreation, leads all gamers in money winnings with $44.6 million. His earnings come not only from excessive curler tournaments with the very best stakes in the sport, but in addition from taking part in towards some of the greatest opponents. Texas Holdem is the most popular poker variant right now. If you can find a card room that provides poker games, Texas Holdem will almost definitely be the flagship sport, with a massive range of tables and stakes to select from.
Download it from the official Parimatch web site and start earning money out of your passion for sports. After you register and obtain the shopper to your smartphone, it is feasible for you to to make a deposit. All cost operations in the bookmakers workplace are made by way of the cashiers desk. You can make a deposit using one of many well-liked fee techniques in the nation. Wagering takes place within 30 days after receiving the bonus.
The platform integrates video games from over 80 software program operators in a mixture of little-known names and well-established developers including Betsoft, Evoplay, IGT, and Microgaming. The choice is wealthy and diverse together with traditional casino games like scratch playing cards, Pai Gow, Joker Dice, War, Sic Bo and Cribbage. Owned and operated by Tutkia LTD, Melbet on line casino presents on line casino services, slots, e-sports and sports activities betting providers.
In the higher proper corner, there is a switching of interface languages - there are 43 choices in total. The book...
18:56
Melbet Casino India Review Ll 100% Bonus As A Lot As A Hundred Forty Five,000 h+ Media
Melbet Casino India Review Ll 100% Bonus As A Lot As A Hundred Forty Five,000
All you need to do is send a replica or a photograph of a document that proves your date of birth or handle. The same quantity of withdrawal methods can be found as there are for deposit strategies. Once again, we highly counsel that you just choose a payment method that you have used earlier than and that youre conversant in. If youre not acquainted with any, then we extremely counsel you perform some research and skim through the terms and conditions first. The primary complaints they have regarding special options or wagering requirements, nonetheless, will get into extra details about them little bit in a while. MelBet understands the worth of privacy and safety of person knowledge and due to this fact makes use of sturdy measures to keep it safe from unauthorised access.
All bonus types are disabled for cryptocurrency accounts with out exception. Unfortunately, we have no idea the payout share of Melbet at this second in time. Mdcomputers is dedicated to one hundred pc customer delight ensuring that every thing from inserting your order to delivering it proper to the doorstep is clean and hassle-free. As lengthy as you might be over 18 and might provide ID you can play from aywhere in India. Live Chat this is most positively our most popular choice. The bonus is much from simple so its actually value having a look at a number of the terms and circumstances hooked up to it.
MelBet is one of the multi-platform sites that will offer you totally different options. Hence, punters may be confused as to the place to start with their gambling journey. When it involves esports betting, the gambling site certainly provides a singular experience. It offers extra sports activities betting options that youll ever find in different betting websites.
We supply an array of bonuses, together with welcome bonuses, daily promotions, and loyalty rewards, to guarantee that you at all times get probably the most out of your time with us. Melbet Casino takes nice delight in providing gamers an unparalleled gaming expertise. Melbet Casino is where gaming enthusiasts from around the globe come to take pleasure in an exciting and rewarding online on line casino experience. Melbet Bangladesh is a great choice for online betting in Bangladesh. It has a broad range of sports activities and casino games, nice bonuses and promotions, a user-friendly platform, secure fee choices, and responsive buyer assist.
Single Ordinary bets, where you predict a single outcome. You can guess on membership matches and national staff competitions. Dozens of outcomes with favourable odds can be found for many events.
If you could have a promo code, enter it within the acceptable field, or choose one of many three available provides for newbies. Please log in to familiarize yourself with the platforms interface and capabilities, and start placing your be...
18:55
Melbet On Line Casino India 2023 h+ Media
Melbet On Line Casino India 2023
In addition to slots, it is possible for you to to search out basic live on line casino entertainments corresponding to roulette, baccarat, blackjack, poker, and others. Dealers in lovely fits will interact with you politely, leaving only pleasant feelings and bringing you big winnings. With the big number of video games which would possibly be available on Melbet, it only makes sense that it has a conveyable interface as well, to make it simple for the gamblers. And what better way to make one thing on-the-go if not making it a cell application.
If there is one word to explain the bonuses at present out there via MELbet, that word is confusing. The current welcome bonus is an preliminary match bonus of 7,000 rubles however theres a laundry list of conditions that players should meet to money in on this bonus. This license allows an web casino to offer all kinds of video games, including sports activities betting, traditional on line casino, and video games of ability. If you urgently must withdraw cash, then on the site, youll find a way to rapidly and easily, using the withdrawal system, replenish your personal account with the money won. It additionally simply works and replenishes the deposit that you just use whenever you bet in your favorite sport or play online casinos.
- Melbet is owned by a Russian firm called Tutkia Limited, which is operated by Pelican Entertainment underneath the Curacao License.
- Participants should have Melbet login to get entry to igaming options and bonuses.
- For iOS gadgets, you presumably can seek for the BetIndi app on the App Store and download it.
- There are many distinctive games within the Fast Games section that arent like another.
- The range of sports disciplines that are accessible for wagering by way of finest Indian betting functions is really big these days.
- Betting website provides dozens of Melbet sports activities together with cricket, football, tennis and more.
If youre the owner of the iOS system, check the most effective apps for betting in India below. If youre a beginner within the betting sphere, take a glance at the most effective Indian betting apps which will be great for you to use due to their easy interface and navigation. The minimum required deposit to activate the bonus is 750 INR.
Yes, the Melbet app can be downloaded on all iOS and Android gadgets and its free to download. Responsible playing covers the subject of the responsibility of the on line casino themselves and the rights theyve when it comes to closing and suspending accounts. Melbet additionally has the right to ask the customer to ship in proof of age or address at any given second. However, you do need to have a completely registered and verified account to be able to play with real cash at Melbet.
Users can take pleasure in sports activities betting on...
17:14
6 ways to get information about your CPU on Linux Linux.com
Getting insight into what CPU youre running is a useful trick to know.
Read More at Enable Sysadmin
The post 6 ways to get information about your CPU on Linux appeared first on Linux.com.
How we keep our Linux systems patched with automation Linux.com
An automated patch-management system helps keep your server infrastructure patched and maintained in a timely manner.
Read More at Enable Sysadmin
The post How we keep our Linux systems patched with automation appeared first on Linux.com.
17:00
Hosting open source projects on GitHub: Nine things you need to know Linux.com

Read the original blog at Read More
The post Hosting open source projects on GitHub: Nine things you need to know appeared first on Linux.com.