| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Sunday, 02 April
05:00
HACKERS IN HISTORY - A LOOK WAY BACK 2600 - 2600: The Hacker Quarterly
The term hacker may have gained notoriety in recent decades, but the act of hacking, or using clever and unconventional methods to achieve a goal, has been practiced for centuries. Here are ten historical figures prior to the 19th century who would be considered good hackers by today's standards.
1. Archimedes (287 BC - 212 BC)
Archimedes, the ancient Greek mathematician, engineer, and inventor, is famous for his contribution to the field of mathematics and physics. He was also known for his clever tactics during the Siege of Syracuse in 214 BC. Archimedes used mirrors and lenses to focus sunlight on the Roman ships, setting them on fire.
2. Julius Caesar (100 BC - 44 BC)
Julius Caesar, the Roman statesman and military leader, is known for his brilliant tactics on the battlefield. He also used cryptography to send secret messages to his allies, using a code in which each letter was replaced with the letter three places down the alphabet.
3. Leonardo da Vinci (1452 - 1519)
Leonardo da Vinci was an Italian polymath who excelled in multiple fields, including painting, sculpture, engineering, and science. He also had a keen interest in cryptography, creating a code in which letters were replaced with symbols and shapes.
4. Mary Queen of Scots (1542 - 1587)
Mary Queen of Scots, the Scottish monarch, was known for her clever escape attempts from captivity. In one instance, she dressed up as a servant and escaped from a castle in which she was being held captive.
5. Galileo Galilei (1564 - 1642)
Galileo Galilei, the Italian astronomer and physicist, is known for his contributions to the field of science. He was also a skilled telescope maker, designing and building his own telescopes to observe the stars.
6. Benjamin Franklin (1706 - 1790)
Benjamin Franklin was an American statesman, scientist, and inventor. He is known for his contributions to the fields of electricity and physics. Franklin was also a skilled printer and used his knowledge of printing to disseminate his ideas and beliefs.
7. Jeanne de Clisson (1300s - 1359)
Jeanne de Clisson, a French pirate, was known for her ruthless attacks on French ships during the Hundred Years' War. She would paint her ships black and red to symbolize her hatred for the French monarchy.
8. Matsuo Basho (1644 - 1694)
Matsuo Basho was a Japanese poet who is considered one of the greatest poets of the Edo period. He is known for his haiku, a form of poetry that is characterized by its brevity and simplicity.
9. Ada Lovelace (1815 - 1852)
Ada Lovelace was an English mathematician and writer who is considered to be the world's first computer programmer. She wrote the first algorithm for Charles Babbage's Analytical Engine, a mechanical computer that was n...
04:00
BOB DYLAN'S LOST SONG ABOUT HACKERS 2600 - 2600: The Hacker Quarterly
Bob Dylan has written so many ballads over the years that it was inevitable one would be about hackers. We were able to find the lyrics to this unrecorded piece written on the back of several napkins (or possibly the front - it's hard to tell the difference). Perhaps a spirited campaign will convince Bob to finally record this - and give it a title!
Come gather round, hackers all,
And listen to my tale,
Of how some took to their keyboards,
And the governments did assail.
It all began in the 80s,
With hackers breaking in,
To corporate and government systems,
For a thrill, and sometimes for a win.
But it was in the 90s,
When things really took off,
With groups like Cult of the Dead Cow,
And the formation of the EFF.
Hackers began to see,
The power that they could wield,
To fight against censorship,
And to expose truths concealed.
They hacked into Chinese sites,
To protest Tiananmen Square,
And into the Church of Scientology,
To show their secrets bare.
Then came the rise of WikiLeaks,
With Julian Assange at the helm,
Leaking government secrets,
And causing quite the realm.
The Arab Spring was fueled,
By hacktivist group Anonymous,
Who launched attacks on government sites,
And helped to topple oppressors.
But with the power came the risk,
Of being hunted down,
By the FBI and other agencies,
And ending up in prison bound.
So now we must ask ourselves,
What is hacktivism's fate,
Will it continue to be a force for good,
Or will it meet a darker date?
But one thing is for certain,
Hacktivism won't go away,
As long as there are truths to be told,
And injustices to be slayed.
03:00
THE 28TH AMENDMENT TO THE UNITED STATES CONSTITUTION 2600 - 2600: The Hacker Quarterly
The 28th Amendment to the United States Constitution:
Section 1: The right to reverse engineer technology and repair personal property shall not be infringed.
Section 2: Reverse engineering shall be defined as the process of dismantling or analyzing a product to understand how it works, with the goal of creating a similar or improved product.
Section 3: The right to repair shall be defined as the ability of individuals or entities to repair their personal property, including but not limited to electronic devices, motor vehicles, and home appliances, using available parts and documentation.
Section 4: Manufacturers and sellers of products shall not be allowed to restrict or limit the ability of individuals or entities to reverse engineer or repair their personal property.
Section 5: Manufacturers of products shall be required to provide consumers with access to the necessary tools, parts, and documentation for repair and maintenance of their products.
Section 6: Manufacturers of products shall not be allowed to void warranties or impose penalties for repairs made by individuals or entities outside of the manufacturer's authorized service providers.
Section 7: The federal government shall have the authority to enforce this amendment through appropriate legislation and regulation.
Section 8: This amendment shall not be interpreted as limiting any existing rights or protections under the law.
Section 9: This amendment shall take effect immediately upon ratification.
The purpose of this amendment is to protect the rights of
individuals and entities to reverse engineer and repair their
personal property, as well as to promote innovation and
sustainability by allowing for the creation of new and improved
products through reverse engineering. The amendment also seeks to
prevent manufacturers from limiting the ability of consumers to
repair their own property and to provide greater access to the
necessary tools and documentation for repair and maintenance. By
protecting these fundamental rights, this amendment will ensure
that individuals and entities are able to maintain control over
their personal property and promote a more sustainable and
equitable economy.
02:00
2600 PRESENTS - QUANTUM COMPUTING FOR TODDLERS! 2600 - 2600: The Hacker Quarterly
Hello boys and girls! We're here today to learn all about quantum computers! It's easy - and fun!
Imagine you have a toy box filled with different toys, like blocks and dolls. Each toy has a specific shape and color, and you can use your hands to pick them up and move them around.
Now, imagine you have a special toy box that can do things your regular toy box can't. This toy box is called a quantum computer. It's like a really fast and smart toy box that can help you solve really big problems.
In a quantum computer, instead of using your hands to move the toys around, you use something called "quantum bits" or "qubits" to store and process information. These qubits are like special blocks that can do different things depending on how they're arranged.
Just like how you can use blocks to build towers or castles, quantum computers can use qubits to solve complex problems and make new discoveries. They can help us understand things like the weather, how medicines work, or even how our universe was created.
So, just like how your regular toy box helps you play and have fun, a quantum computer helps scientists and researchers discover new things and solve important problems.
Ready for Part 2? Then click here!
THIS IS REAL - PLEASE DON'T IGNORE 2600 - 2600: The Hacker Quarterly
I was typing away at my computer, working on the day's April Fools' Day prank for the website. Suddenly, everything went black.
I panicked, but then the screen flickered back to life. Except, it's not the normal screen. It's the program that creates web posts. And I'm trapped inside.
At first, I thought it was a joke. A prank that someone is playing on me. But as the hours passed, I realized that this is no joke. I'm really trapped inside the program.
I tried to post a message on the website, explaining my situation and begging for help. But no one believed me. They all think it's part of the April Fools' Day prank.
I'm stuck inside the program, unable to eat, drink, or sleep. I tried everything I can think of to get out, but nothing works.
As time drags on, I'm beginning to lose hope. I wonder if I'll ever be able to escape this virtual prison.
And so, I remain trapped inside the program, trying desperately
to get someone to believe me and help me break free. But as time
passes, it becomes clear that I may never be able to escape.
01:00
SHAKESPEARE'S LONG-LOST MICHELANGELO VIRUS SONNET 2600 - 2600: The Hacker Quarterly
The question isn't how Shakespeare was able to write about this centuries before it happened. The question is how did this long forgotten masterpiece fall into our hands. And the answer is, of course, SecureDrop. If you have a literary work from the Elizabethan Era that you'd like to leak anonymously, just visit our SecureDrop site at www.2600.com/securedrop.
Here then, are the words from the Michelangelo scene of Shakespeare's unreleased "Charles III":
Oh, Michelangelo! How thou art feared,
A virus that doth cause such great dismay.
Thou spreadeth fast, and none may be spared,
From thy deadly, destructive, viral way.
Like Michelangelo, thou art an artist,
Creating chaos and destruction all around.
Thou maketh thy victims truly hardest,
As they struggle to restore their lost ground.
But unlike Michelangelo's works so grand,
Thy legacy is one of pain and woe.
For thou dost wreak havoc across the land,
Leaving naught but destruction in thy flow.
Oh, Michelangelo virus, thou art vile,
And we shall never forget thy wicked guile.
00:00
VORNADO ANNOUNCES PLANS FOR FORMER HOTEL PENNSYLVANIA SITE 2600 - 2600: The Hacker Quarterly
FOR IMMEDIATE RELEASE
Vornado Realty Trust Announces Plans to Transform Former Hotel Pennsylvania Site into a Center for the Overprivileged
New York City, NY - Vornado Realty Trust, one of the largest real estate investment trusts in the United States, announced today that it will be transforming the former site of the Hotel Pennsylvania into a luxurious center for the overprivileged. The new center will provide an exclusive escape from the daily stresses of life among the middle class, and will feature multiple floors reserved for polo, swimming, and croquet. Admission to the center will be restricted to those earning over $750,000 a year.
The Hotel Pennsylvania, a historic landmark in the heart of Manhattan, has been an iconic part of the New York City skyline since 1919. As a testament to its legacy, the building has undergone numerous renovations over the years, becoming a hub for tourists and locals alike. However, the building has now outlived its usefulness, and Vornado Realty Trust has decided to demolish it to make way for this new venture.
"This is an exciting time for Vornado Realty Trust and for New York City," said Steven Roth, Chairman and CEO of Vornado Realty Trust. "We believe that the overprivileged deserve a place where they can relax and enjoy the finer things in life. This new center will provide a sanctuary for those who have worked hard to achieve success and are looking for a well-deserved break from the middle class."
The new center will feature state-of-the-art facilities, including multiple swimming pools, a polo field, and a croquet court, as well as other luxurious amenities. In addition, the center will offer a range of exclusive services, including private chefs, personal trainers, and spa treatments.
As the demolition of the historic Hotel Pennsylvania continues, Vornado Realty Trust is committed to ensuring that its legacy is not forgotten. The company will be preserving a number of key artifacts from the building's storied history, which will be on display in the new center.
"We recognize the Hotel Pennsylvania's significance in New York City's history, and we are committed to honoring its legacy," said Roth. "We look forward to opening this new center for the overprivileged and providing them with a truly unique and exclusive experience."
Construction of the new center is set to begin in the coming
months, with an expected completion date in the next two years.
Saturday, 01 April
23:51
GTK & Blender Are The Latest Software Supporting Wayland Fractional Scaling Phoronix
The Blender open-source 3D modeling software as well as the GTK toolkit are the latest open-source projects this week ironing out support for Wayland's fractional scaling protocol...
23:51
Links 01/04/2023: Red Hat Turning 30 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
-
GNU/Linux
-
Audiocasts/Shows
-
Podman Desktop Containers & Kubernetes (Podcast #15 w/ Markus Eisele)
In the fourth episode of the Red Had Podcast Series, we talk about Podman Desktop with our guest, Markus Eisele, Global Marketing Tools marketing lead at Red Hat. Join us for an insightful and extensive conversation on Podman Desktop, containers, and Kubernetes.
-
Red Hat Official WebAssembly Breaks Away from the Browser
What makes WebAssembly a game-changer for runtime environments? Red Hat CTO Chr...
-
-
23:28
Wine-Staging 8.5 Adds Patches To Allow Diablo IV To Run Without Errors Phoronix
Following yesterday's Wine 8.5 bi-weekly development release, some 500+ extra patches are applied atop the upstream Wine code-base...
23:00
CROSSOVER SERIES OF "MR. ROBOT" AND "LEAVE IT TO BEAVER" ANNOUNCED 2600 - 2600: The Hacker Quarterly
Title: "Beaver's Bytes"
Logline: In 2023, a grown-up Theodore "Beaver" Cleaver finds himself caught up in a world of cybercrime and corporate corruption when he discovers that his beloved town of Mayfield is under threat from an unknown hacker group. With the help of his old friend, Elliot Alderson, the mastermind behind the infamous fsociety hack, Beaver sets out to uncover the truth and save his hometown from destruction.
Synopsis: "Beaver's Bytes" is a hybrid of the classic family sitcom "Leave It To Beaver" and the cyber thriller "Mr. Robot." Set in the year 2023, the show follows the now-grown Theodore "Beaver" Cleaver as he returns to his hometown of Mayfield after a long absence. He quickly realizes that Mayfield is no longer the idyllic town of his youth, but instead a place overrun with corrupt corporations and cybercriminals.
Beaver reunites with his childhood friend, Elliot Alderson, who has become a legend in the world of hacking thanks to his work with the fsociety group. Elliot has been lying low since the end of the "Mr. Robot" series, but Beaver's return to Mayfield gives him a reason to come out of hiding and help his friend.
Together, Beaver and Elliot set out to uncover the identity of the hacker group that is threatening Mayfield, using their unique combination of old-school sleuthing and cutting-edge hacking skills. Along the way, they encounter a cast of characters both old and new, including some familiar faces from the original "Leave It To Beaver" series.
As the investigation heats up, Beaver and Elliot begin to realize that the threat to Mayfield is much bigger than they initially thought. They must race against time to stop the hackers before they can cause irreparable damage to the town and its residents.
"Beaver's Bytes" is a unique blend of comedy, drama, and
suspense, featuring a cast of beloved characters from a classic
sitcom alongside the gritty, high-stakes world of cybercrime. With
its timely themes of corporate corruption and online privacy, the
show is a thrilling and thought-provoking ride that will keep
audiences on the edge of their seats.
22:00
Squeezing Secrets Out Of An Amazon Echo Dot Hackaday

As we have seen time and time again, not every device stores our sensitive data in a respectful manner. Some of them send our personal data out to third parties, even! Todays case is not a mythical one, however its a jellybean Amazon Echo Dot, and [Daniel B] shows how to make it spill your WiFi secrets with a bit of a hardware nudge.
Theres been exploits for Amazon devices with the same CPU, so to save time, [Daniel] started by porting an old Amazon Fire exploit to the Echo Dot. This exploit requires tactically applying a piece of tin foil to a capacitor on the flash chip power rail, and it forces the Echo to surrender the contents of its entire filesystem, ripe for analysis. Immediately, [Daniel] found out that the Echo keeps your WiFi passwords in plain text, as well as API keys to some of the Amazon-tied services.
Found an old Echo Dot at a garage sale or on eBay? There might just be a WiFi password and a few API keys ripe for the taking, and who knows what other kinds of data it might hold. From Amazon service authentication keys to voice recognition models and maybe even...
22:00
UNCLAIMED HACKER HANDLES 2600 - 2600: The Hacker Quarterly
The following 100 hacker handles are unclaimed in the Hacker Registry. If you are interested in obtaining one of these, registration will open on Monday. For a monthly fee of $8, we will register the handle of your choice to you (first come, first served). There is a limit of two handles per Social Security number.
ByteCrasher
Hacktivator
ShadowPuppet
DarkByte
LogicBomb
GhostCracker
CyberChaos
CodeCrusader
TechTerrorist
DataDiva
CyberRanger
HackSmasher
CrypticCracker
TerminalTerror
ByteBandit
NetworkNecromancer
WebWarrior
CyberSiren
FirewallFoe
ByteBrute
CodeCrusher
CircuitSavior
ShadowSurfer
HackHunter
DarkDynamo
CodeConqueror
CyberCaptor
PhantomProgrammer
ByteBattler
CyberCommando
TerminalTactician
NetNemesis
WebWizard
CryptoCrusader
ByteBrawler
CyberSpartan
DigitalDominator
CodeChampion
GhostGeek
CircuitCrusher
ShadowShark
HackHustler
DarkDestroyer
TechnoTitan
ByteBurglar
CodeCrafter
CyberCrusade
DataDagger
PhantomPilot
TerminalTornado
WebWitch
BinaryBandit
CyberSpecter
DigitalDynamo
Encryptor
FirewallFury
GhostHacker
InfraRed
JavaJacker
LogicLad
MalwareManiac
OracleOctopus
PasswordPunisher
QuantumQuasar
RouterRider
ScriptSlinger
TechTornado
Ultraviolet
VirusVandal
WiFiWarrior
XenoXploit
YellowHacker
ZombieZero
AlphaArmor
ByteBasher
CryptoCraze
DarkDefender
EchoEagle
FireflyHacker
GreyGuru
HackHive
InfiKnight
JoltJumper
KeyKing
LogikLord
MachineMaster
NetNimbus
OverloadOracle
PhantomPirate
QuantumQuark
RogueRunner
SparkSavage
TechTerror
VirusVigilante
WhirlwindWizard
XenonXenocide
YellowYak
ZombieZone
ArchAngel
Cipherphreak
21:55
KDE Ends Out March With More Fixes - Including More Plasma Wayland Work Phoronix
The KDE developers ended March on a high note with more fixes, continued porting around Qt 6, and also taking care of more Plasma Wayland issues...
21:00
VPNS TO BE OUTLAWED IN THE U.S. - IT'S FOR THE BEST, REALLY 2600 - 2600: The Hacker Quarterly
The United States government is set to outlaw the use of VPNs later this year, citing concerns about their use for illegal activity. VPNs, or virtual private networks, allow users to connect to the internet through a server in another location, which can be used to mask their identity and location. This has made them popular for a variety of activities, including accessing blocked websites, pirating copyrighted content, and committing fraud.
The government argues that VPNs are a major tool for criminals and that outlawing their use will help to reduce crime. However, some critics argue that the ban will stifle freedom of speech and privacy. They argue that VPNs can be used for legitimate purposes, such as protecting oneself from government surveillance.
The ban on VPNs is set to go into effect later this year. It is unclear how the ban will be enforced, but it is likely that users who are caught using a VPN will be prosecuted.
Here are some of the reasons why VPNs are considered dangerous:
They can be used to access blocked websites and content. This can be used for illegal purposes, such as pirating copyrighted content or accessing child pornography.
They can be used to commit fraud. For example, VPNs can be used to create fake identities or to steal credit card information.
They can be used to hide illegal activity. For example, VPNs can be used to hide the location of a computer that is being used to commit a crime.
They can be used to spy on users. For example, some VPN
providers may sell user data to third-party companies.
20:34
AI Image Generator Midjourney Stops Free Trials but Says Influx of New Users to Blame SoylentNews
AI image generator Midjourney has stopped free trials of its software:
AI image generator Midjourney has halted free trials of its service, blaming a sudden influx of new users. Midjourney CEO and founder David Holz announced the change on Tuesday, originally citing "extraordinary demand and trial abuse" in a message on Discord (this announcement was spotted first by The Washington Post). In an email to The Verge, Holz stated that the pause is "because of massive amounts of people making throwaway accounts to get free images."
"We think the culprit was probably a viral how-to video in china," said Holz over email. "This happened at the same time as a temporary gpu shortage. The two things came together and it was bringing down the service for paid users."
Given Holz's reference to "abuse," it was originally thought that the pause was linked to a spate of recent viral images created using Midjourney, including fabricated images of Donald Trump being arrested and the pope wearing a stylish jacket, which some mistook for real photographs. However, Holz characterized earlier reports as a "misunderstanding" and notes that the free trial of Midjourney that creates the most realistic images and which is thought to have been used for these viral pictures.
[...] Midjourney maintains a list of banned words "related to topics in different countries based on complaints from users in those countries," as per a message from Holz last October. But it doesn't share a last year, "Almost no one ever notices [the ban list] unless they're specially trying to create drama which is against our rules in tos [terms of service] 'don't use our tools to create drama.'"
[...] At the time of writing, Midjourney is still not allowing free users to generate images, though this may change in the future. "We're still trying to figure out how to bring free trials back, we tried to require an active email but that wasn't enough so we're back to the drawing board," said Holz.
...
20:33
888 On Line Casino India No Deposit Bonus, Codes & Free Spins h+ Media
888 On Line Casino India No Deposit Bonus, Codes & Free Spins
However, the on line casino operates in many other international locations where it is legally licensed to take action. Follow the instructions provided by the deposit methodology you have chosen to complete the transaction. Select your preferred deposit method from the list of choices available.
Suppose you be part of 888 India and set aside a $40 installment. The on line casino would then give you a 100 percent matched deposit bonus, which would convey your complete report surplus up to $80. That implies youve the $40 you deposited, alongside an extra $40 in bonus reserves. At all web based club destinations, rewards accompany agreements. Rewards accompany betting conditions, expiry dates, most excessive successes from there, the skys the restrict. While perusing the agreements, make sure to verify which video games the rewards work with as not all games add to clearing the prerequisites 888 video games.
I additionally obtained a quantity of internships from the campus with Fortis Hospital and Centre for academic progress and analysis. The tutorial studying and company expertise with a world class infrastructure at NDIM has given me the talents wanted for lifelong excellence. I am really looking ahead to my career with Byjus. I am very proud to be a member of the NDIM household and glad about my determination to join this prestigious Institute. NDIM made me plan out my management dream and the trail to attain it.
When the game hundreds, and head for money adventures. Onlinecasinoguide.in is the main guide to learn every thing about Indian on-line casinos. We provide fresh and impartial casino reviews and assist Indian players find the most effective on line casino bonuses and games.
The first welcome bonus youll be eligible to say is 888s $88 no-deposit bonus. All you should do is create an account at 888, confirm your e-mail tackle and keep an eye fixed on your emails inbox. You will then be sent an e-mail within 10 minutes, which accommodates a particular FreePlay credit. This permits you to declare as a lot as $88 in casino funds and you ought to use these funds to play on virtually any casino or slot game you want. Steave jobs has once said that ,sometimes life hits you in a head with break .. this what precisely occurs when an mental sickness caught you . Depression started enjoying disguise and sick with me whe
Its recommended to set a budget that you could afford to lose and stick with it. Dont chase your losses by growing your bets, as this can result in even larger losses. If you discover yourself constantly going over your price range, it might be time to take a break from playing.
Since then, it has produced quite a few on-line platforms for participating countries around the globe. As one of the worlds first major iGaming web sites, 888 Holdings is headquartered in Gibraltar...
20:31
Jeetbuzz Casino
These promotions are designed to incentivize gamers to use the cellular platform and might embrace free spins, bonus funds, and other rewards. Welcome to 4raBet, an official on-line bookmaker in India. Licensed by the government of Curacao, it operates legally in Asia and Europe, offering 40+ sports activities to wager on pre-match and live.
The lobby part of the location is the place youll be able to browse the complete vary of games that are obtainable on the casino. Type in CRYPTO4RASP in the reside chat, make a second deposit with BTC, ETH, Litecoin, Dogecoin, Tether, or another crypto, and get a candy bonus. You need to wager the bonus eight occasions in single or combo bets with the percentages of 1.7+. NDIM made sure our studies dont endure because of the sudden nation-wide lockdown. Even from house we got exceptional studying, placement preparation and job alternatives.
You might struggle to tear yourself away from the screen due to the number of jackpot games and incentivizing bonuses. 888 Casino is a safe guess if you want to take pleasure in an enormous array of lifelike casino games online. Your money is all the time secure, and the chances are never bent in anybodys favour as proven by its eCOGRA certification. Its mother or father firm, 888 Holdings, holds licenses in quite a few international locations across the globe, together with the UK, Gibraltar, Denmark, and the us
Reaching the client assist representatives at 888 Casino is not troublesome. The group is on the market round the clock to reply all casino-related queries of gamers, regardless of whether or not it is about cost, any technical term, recreation, or some other. 888 Casino customer assist may be accessed in multiple languages through e mail, telephone, or e mail. Providing award-winning gaming expertise stay and on cell gadgets, 888 casino becomes a most popular selection for rising numbers of players. It has no limitations other than the next one.
Deposit $20+ using the promo code TravelThurs and get 20% up to $100 FreePlay in two top vacation spot games. Yes, 888 casino is the official establishment which is available to players worldwide, aside from sure nations (888 on line casino GEO info restricted countries). From then on, youll have entry to the complete assortment of leisure and you will be able to play in all of the universes with a single account. The expertise is bound to convey you full satisfaction. There is little question in regards to the legitimacy of 888 on line casino. It is an old casino brand that has been in the world playing scene for a very lengthy time.
To all the people who find themselves affected by psychological sickness, I simply yearn to say that you are not alone. My family has been supportive all this time and I am grateful for them. I would get up every morning feeling very empty, directionless. It appeared like there were butterflies in my sto...
20:28
888 Casino Review 2022 h+ Media
888 Casino Review 2022
$88 is given as a No deposit bonus to each new player. We should let you understand that Skrill and Netellers deposit doesnt qualify for the Welcome bonus on this Apple Pay casino. It is subsequently advisable to avoid them when making deposits.
The first welcome bonus youll be eligible to claim is 888s $88 no-deposit bonus. All you have to do is create an account at 888, verify your email handle and regulate your emails inbox. You will then be sent an email within 10 minutes, which contains a particular FreePlay credit. This lets you declare up to $88 in casino funds and you can use these funds to play on nearly any on line casino or slot sport you like. Steave jobs has once mentioned that ,generally life hits you in a head with break .. this what precisely occurs when an mental sickness caught you . Depression started playing cover and sick with me whe
Indeed, it is possible for you to to find the creations of the
iGaming behemoths at the online on line casino. NetEnt will offer
you a wide selection of the cream of the crop of its virtual slot
machines such as Gonzos Quest or South
Park
or South
Park . Can you
merge the numbers and efficiently get, play online slot Poker has
seen elevated acceptance and popularity within the US. Baseballs
all-time hits leader is banned from the game for betting on it, the
UK. Offers topic to alter without notice, China and different
European nations and now the card recreation online has
additionally begun to acquire immense traction in India. Der
Firmensitz von diesem Online Casino befindet sich in Grobritannien,
the second one requires the charge to be paid and takes a specific
amount of days to be executed.
. Can you
merge the numbers and efficiently get, play online slot Poker has
seen elevated acceptance and popularity within the US. Baseballs
all-time hits leader is banned from the game for betting on it, the
UK. Offers topic to alter without notice, China and different
European nations and now the card recreation online has
additionally begun to acquire immense traction in India. Der
Firmensitz von diesem Online Casino befindet sich in Grobritannien,
the second one requires the charge to be paid and takes a specific
amount of days to be executed.
Additional bets are not limited to particular ideas; you presumably can wager on varied things. The participant determines the winner of the sporting event. In general, likelihood is accepted before the match starts. It is a tough betting sort, as it is hard to foretell how the bettors will behave from the seasons starting. However, the higher the risk, the upper the payout from the official website 4rabet.
It additionally has the eCOGRA label which certifies that the video games are dependable, so you can play right here with peace of mind. Theyre called the Macau, casino windsor poker which absolves the federal government of accountability. We all wish we knew extra, serves solely the pursuits of the betting industry on the expense of gambling addicts and our high streets.
The company stands out from the rest by providing numerous betting markets as nicely as distinctive playing instruments. Are you in search of a secure and authorized betting site? Sign u...
20:09
Links 31/03/2023: Mozilla Turns 25 and OpenMandriva 23.03 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Audiocasts/Shows
-
...
-
-
20:00
Happy Month Sales catonmat.net
At Browserling and Online Tools, we love sales.
We just created a new automated sales campaign called "Happy Month Sales".
Now each new month, for the first couple of days we show a 50% discount offer to all users who visit our site.
This month it's "Happy April Sales". Next month it will be "Happy May Sales", etc.
Here's how it looks:

Run Happy Month Sales too and see you next time!
19:33
Microsoft Fixes New Azure AD Vulnerability Impacting Bing Search and Major Apps The Hacker News
Microsoft has patched a misconfiguration issue impacting the Azure Active Directory (AAD) identity and access management service that exposed several "high-impact" applications to unauthorized access. "One of these apps is a content management system (CMS) that powers Bing.com and allowed us to not only modify search results, but also launch high-impact XSS attacks on Bing users," cloud security
19:00
Apple Never Gave Them USB. Now, Theyre Getting It For Themselves Hackaday

These days we use USB as a default for everything from low-speed serial ports to high-capacity storage, and the ubiquitous connector has evolved into a truly multi-purpose interface. Its difficult to believe then, that the first Apple Mac to be designed with a USB interface was shipped without it; but thats the case with 1997s grey Power Mac G3.
On the personality board are all the footprints for a single USB 1.1 port, but USB-hungry Apple fanboys had to wait for the translucent iMac and later G3 before they had a machine with the parts fitted. [Croissantking] is righting that particular wrong, by piecing together the missing Apple circuit using parts from contemporary cards for PCs. Over a long forum thread there are a few teething problems, but it certainly seems as though grey G3 owners will soon be able to have reliable USB upgrades.
If omitting USB from a 1997 Mac seems unexpected, its as well to remember how slow the first USB versions were. At the time SCSI was king in the high-speed peripheral world, and USB seemed more appropriate as a replacement for Apple Desktop Bus and the serial port. Even when they embraced USB they were reluctant to follow the standards of the PC world, as we remember finding out when for curiositys sake we tried swapping the mice and keyboards between an...
18:33
IRC Proceedings: Friday, March 31, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-310323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-310323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-310323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-310323.gmi
Over HTTP:
|
... |
18:00
Science Confirms Turmeric Is as Effective as 14 Drugs Terra Forming Terra
Woman Who Felt Abandoned by God Dies in Hospital Room, Receives Answer From Jesus Terra Forming Terra
The major teaching here is just how deeply we chose our lifeway before we are born. I was not expectiing that. We discover lefe experiences are carried forward using even our cells which must have that super computer.
Trump indictment shows that power-crazed Democrats are incompatible with human society Terra Forming Terra
Trump indictment shows that power-crazed Democrats are incompatible with human society
I believe that Trump's indictment by power-crazed Democrats is yet another necessary step for the trial by fire that will see America rise up against tyranny, censorship, election rigging and the demonic infestation of the Left that has produced child grooming, transgenderism, trans terrorism and widespread psychological trauma.
As you'll hear today in my Brighteon Broadcast News episode (below), I also believe that Trump himself needs to make it through this trial by fire to achieve a personal transformation.
I think Trump's arrest and prosecution may actually be the wake up call that Trump needs to finally get serious about draining the swamp and using executive power to arrest and imprison the traitors, operatives and treasonous actors who have declared war on this nation.
Explorers Uncover Cave in Spain With Over 100 Prehistoric Engravings Depicting Copper Age Pastoral Life Terra Forming Terra
16:00
Working With Old High-Voltage EPROMs Is Fussy Hackaday

EPROMs, those UV-erasable memory chips of the 80s and 90s, once played a crucial role in countless electronic devices. Theyve become relics of a bygone era, but for enthusiasts of vintage electronics, the allure of these light-sensitive devices remains strong. Today, were diving into [Kevin Osborn]s nostalgic journey as he uncovers the secrets of old EPROMs loaded with Atari 7800 code.
[Kevin] used to work at General Computer Company, which produced the Atari 7800 and several games for the system. Thus, he had a handful of old carts and development EPROMs sitting up in his attic along with an old console. Recently, he decided to try and uncover what was on the EPROMs and begun an investigation. They wouldnt run in his Atari, and he quickly realized why: the EPROMs werent cryptographically signed, so the system wouldnt load them.
After a little work, he was able to dump the EPROMs with the help of a TL866II+ reader. After some hacking, he was able to fettle the data on the EPROMs into something that would run on the A7800 emulator. This was easy enough, as the emulator doesnt run checks for properly signed code. From there, he was able to use a UV phone sanitizer to wipe the EPROMs, and re-burn them with signed versions of their original code. This took the application of some high voltage, but with the aid of an external power supply, it worked. He was able to successfully run the obscure ROMs on real Atari 7800 console hardware.
UV-erasable PROMs, or EPROMs, have long been superseded by the more convenient...
15:52
Silence Gets You Nowhere in a Data Breach SoylentNews
Your victim status won't last long if your response is nonexistent:
In cybersecurity, the phrase "what they don't know won't hurt them" is not only wrong, it's dangerous. Despite this, it's a motto that remains in many organizations' PR playbooks, as demonstrated by the recent LastPass and Fortra data breaches.
[...] TechCrunch+ has learned that LastPass has already lost customers because of its silent-treatment approach to its breach. And Fortra is likely to face a similar fate after TechCrunch+ heard from multiple customers that they only learned that their data had been stolen after receiving a ransom demand; Fortra had assured them that the data was safe.
Smaller companies, too, are employing a silent-treatment approach to data breaches: Kids' tech coding camp iD Tech failed to acknowledge a January breach that saw hackers access the personal data of close to 1 million users, including names, dates of birth, passwords stored in plaintext, and about 415,000 unique email addresses. Concerned parents told us at the time that they only became aware of the breach after receiving a notification from a third-party data breach notification service.
[...] While getting hacked can be forgivable, an organization's victim status will not last long if it fails to respond appropriately or at all as demonstrated by LastPass and Fortra.
Read more of this story at SoylentNews.
15:51
Cacti, Realtek, and IBM Aspera Faspex Vulnerabilities Under Active Exploitation The Hacker News
Critical security flaws in Cacti, Realtek, and IBM Aspera Faspex are being exploited by various threat actors in hacks targeting unpatched systems. This entails the abuse of CVE-2022-46169 (CVSS score: 9.8) and CVE-2021-35394 (CVSS score: 9.8) to deliver MooBot and ShellBot (aka PerlBot), Fortinet FortiGuard Labs said in a report published this week. CVE-2022-46169 relates to a critical
15:36
Hackers Exploiting WordPress Elementor Pro Vulnerability: Millions of Sites at Risk! The Hacker News
Unknown threat actors are actively exploiting a recently patched security vulnerability in the Elementor Pro website builder plugin for WordPress. The flaw, described as a case of broken access control, impacts versions 3.11.6 and earlier. It was addressed by "Improved code security enforcement in WooCommerce components," the Tel
13:15
Socura releases Managed SASE service to secure the hybrid workforce Help Net Security
Socura has launched its Managed SASE (Secure Access Service Edge) service in partnership with Palo Alto Networks Prisma. Market industry researchers expect SASE to be a $60bn industry by 2027 fuelled by the rise of flexible working, which was enshrined into UK law in December 2022, whereby millions of UK employees were granted the right to request flexible working hours throughout their employment. By combining SASE with its Managed SOC (Security Operations Centre) service, Socura More
The post Socura releases Managed SASE service to secure the hybrid workforce appeared first on Help Net Security.
13:09
18 Years Later schestowitz.com
 recently wrote that I had been looking at many old photos, trying
to basically recall much older days because of my sisters wedding
(4 days ago).
recently wrote that I had been looking at many old photos, trying
to basically recall much older days because of my sisters wedding
(4 days ago).
 One experience that I still
remember was in 2005 (Zermatt). It cemented my decision to do Free
software activism for a lifetime if possible. I wasnt rich, but I
came to realise that all the superficial nonsense rich people dwell
in does not bring true happiness. Its more about show-off and class
consciousness. Thus, the concept of hoarding money or showing money
was rather pointless. Id never be interested in it.
One experience that I still
remember was in 2005 (Zermatt). It cemented my decision to do Free
software activism for a lifetime if possible. I wasnt rich, but I
came to realise that all the superficial nonsense rich people dwell
in does not bring true happiness. Its more about show-off and class
consciousness. Thus, the concept of hoarding money or showing money
was rather pointless. Id never be interested in it.
My stance or my position has not changed since then (18 years ago). I still do campaigning, I still share all my work/code, and Ive worked hard to secure that for at least another decade to come.
13:00
Creating a 3D Visualization of Freely Moving Organisms Using Camera Array and Software Algorithm Hackaday

Observing a colony, swarm or similar grouping of creatures like ants or zebrafish over longer periods of time can be tricky. Simply recording their behavior with a camera misses a lot of information about the position of their body parts, while taking precise measurements using a laser-based system or LiDAR suffers from a reduction in parameters such as the resolution or the update speed. The ideal monitoring system would be able to record at high data rates and resolutions, while presenting the recorded data all three dimensions. This is where the work by Kevin C. Zhou and colleagues seeks to tick all the boxes, with a recent paper (preprint, open access) in Nature Photonics describing their 3D-RAPID system.
This system features a 96 camera grid, making for a total of 54 cameras which image the underlying surface. With 66% overlap between cameras across the horizontal dimension, there enough duplicate data between image stream that is subsequently used in the processing step to extract and reconstruct the 3D feat...
13:00
Zenoss introduces monitoring capabilities for Kubernetes Help Net Security
Zenoss has launched a free trial for monitoring Kubernetes, the de facto standard platform for running containers in production at scale, including in on-prem and cloud environments. This real-time monitoring of Kubernetes streaming data is another advancement of the Zenoss unified monitoring vision. The Zenoss monitoring capabilities for Kubernetes enable customers to: Begin monitoring in minutes with no training required for operations personnel. Leverage secure, cloud-based monitoring with zero install. Gain insights for Kubernetes clusters More
The post Zenoss introduces monitoring capabilities for Kubernetes appeared first on Help Net Security.
12:38
Linus Tech (Illiteracy) Tips, LTT, Buys Phoronix Media Techrights
Summary: Phoronix Media is being acquired by a larger company; the site will not change though
Linus Gabriel Sebastian, founder of Linus Tech Tips (LTT), has just announced the transfer of Phoronix Media (best known for Phoronix.com and PTS) to his company based in Canada.
Readers of the site wont be affected. They can still get a spoonful of Microsoft chaff along with plenty of (other) ads.Phoronix.com and PTS are a strategic addition to our growing portfolio, remarked Yvonne Ho, who will oversee the operations to ensure the benchmarks always include ClearLinux and articles habitually include a Microsoft distro that only Microsoft uses.
Michael Larabel could not be reached for comment. He has been busy this past month trying to figure out new and innovative ways to block all the ad blockers. Mr. Sebastian insists that evading ads is nothing short of piracy.
Readers of the site wont be affected. They can still get a spoonful of Microsoft chaff along with plenty of (other) ads.
12:13
Decided to Quit Debian and Use WSL Instead (Best of Both Worlds) Techrights
Summary: Today starts a journey to a better experience, which lets Microsoft audit the kernel and leverage telemetry to improve my Debian experience
THIS is a hard post to write. Today, April 1, Im beginning my migration. I will report on it later today, explaining how it all went along. Maybe Ill change my mind.
Thankfully I already have some Microsoft MVPs like Hayden Barnes helping my migration.Having used GNU/Linux since my teenage years Ive decided that its just too boring. Ive not rebooted Debian since January when I first installed it (only the post-install reboot) and I am beginning to wonder if theres a bootkit somewhere inside my system. Thank God, Microsoft made secure boot to do this for me. As it turns out, Debian 11 is not good anymore. Vista 11 has WSL, which reinvents Cygwin, dating back to 1995. So why on Earth use only GNU/Linux? Best of both worlds, right? Anything else would be an act of bigotry and intolerance.
Thankfully I already have some Microsoft MVPs like Hayden Barnes helping my migration. They kept coming to our IRC network for years, advocating WSL. I give up! They have a point!
11:46
Microsoft Has Laid Off Lennart Poettering and Hired Elon Musk Techrights
Microsoft hires Elon Musk to oversee layoffs, algorithm decides to fire Poettering
Summary: Poettering gets rehired by IBM; IBM and Microsoft announce merger, putting Poettering back into his former position
MICROSOFT is going through some truly tough times. There are layoffs every week, the company is unable to hide it by compelling staff to sign NDAs (the press finds out eventually), and tens of thousands of puff pieces about a chaffbot cannot distract the public entirely from the real crisis.
As a result, the first person to go is Lennart Poettering, who quietly defected from IBM to Microsoft only months ago.Microsoft has just announced, in its Friday shareholders meeting, that it has convinced Elon Musk to join Microsofts Board of Directors and spend some time carrying out duties at Microsoft, at least at a part-time capacity, focusing on AI.
Musk has demonstrated solid track record running companies that suffer deep losses, the company said in its meeting minutes, not only convincing a lot of staff to leave voluntarily but also laying off a significant proportion without paying severance.
IBM has meanwhile signalled that it is willing to rehire Mr. Poettering, but discussions are still ongoing about the IBM/Microsoft merger, which dates back to 2011.An anonymous source told us that OpenAI has unveiled a new algorithm for HR. As a result, the first person to go is Lennart Poettering, who quietly defected from IBM to Microsoft only months ago. Poettering insists that it was not a defection, it was just a matter of wearing the correct badge after more than a decade of work, which some deemed sabotage.
IBM has meanwhile signalled that it is willing to rehire Mr. Poettering, but discussions are still ongoing about the IBM/Microsoft merger, which dates back to 2011. The discussions are already more than a decade old and Bill Gates is losing interest in them.
11:10
These Angry Dutch Farmers Really Hate Microsoft SoylentNews
There are around 200 data centers in the Netherlands, most of them renting out server space to several different companies. But since 2015, the country has also witnessed the arrival of enormous "hyperscalers," buildings that generally span at least 10,000 square feet and are set up to service a single (usually American) tech giant. Lured here by the convergence of European internet cables, temperate climates, and an abundance of green energy, Microsoft and Google have built hyperscalers; Meta has tried and failed.
Against the backdrop of an intensifying Dutch nitrogen crisis, building these hyperscalers is becoming more controversial. Nitrogen, produced by cars, agriculture, and heavy machinery used in construction, can be a dangerous pollutant, damaging ecosystems and endangering people's health. The Netherlands produces four times more nitrogen than the average across the EU. The Dutch government has pledged to halve emissions by 2030, partly by persuading farmers to reduce their livestock herds or leave the industry altogether. Farmers have responded with protests, blockading roads with tractors and manure and dumping slurry outside the nature minister's home.
The courts have also halted thousands of building projectsforcing construction jobs like Microsoft's to apply for permits proving they would not make the nitrogen crisis worse.
[...] The dispute over nitrogen permits has put Microsoft's data center developments in direct opposition to an increasingly powerful farming community. Earlier this month, a new political force, called the Farmer Citizen Movement (BBB), did so well in provincial elections, it became the joint-largest party in the Dutch Senate. The party, which emerged in response to the nitrogen crisis, also has strong views on data centers. "We think the data center is unnecessary," says Ingrid de Sain, farmer turned party leader of the BBB in North Holland, referring to the Microsoft complex. "It is a waste of fertile soil to put the data centers boxes here. The BBB is against this."
Read more of this story at SoylentNews.
10:37
New AMD Ryzen CPUs, Intel Sapphire Rapids, Rust Adoption & More In Q1 Phoronix
During the first quarter of 2023 on Phoronix I wrote 708 original news articles pertaining to Linux, open-source, and hardware. That was complemented by another 45 Linux hardware reviews / multi-page featured articles for the quarter. Here is a look back at what excited Linux/open-source enthusiasts for the quarter...
10:34
Bad Content Moderation Is Bad, And Government Interference Can Make It Even Worse Deeplinks
This week, the House Energy and Commerce Committee held a hearing titled Preserving Free Speech and Reining in Big Tech Censorship. Lawmakers at the hearing trotted out the usual misunderstandings of these concepts, and placed the blame on Section 230, the law that actually promotes free speech online.
However, buried in these misunderstandings from Congress, and most of the witnesses called to testify, was a genuinely serious problem: Government officials keep asking online services to remove or edit users speech, raising the specter of unconstitutional interference with private platforms moderation decisions. And worse, the public lacks any transparency into how often this occurs.
Regardless of your ideological preference, we should always worry about government coercion that results in censoring users speech online, which violates the First Amendment and threatens human rights globally. The government is free to try to persuade online services to remove speech it believes is harmful, but the choice to remove users speech should always remain with the platform.
So Congress is right to investigate the relationship between platforms and the government, and both should be more transparent about official requests to remove users content.
The First Amendment And Section 230 Enable Content Moderation
One witness at the hearing, Dr. Jay Bhattacharya, discovered that much of what he posted about COVID-19 mitigation strategies was being moderated by Twitter to reduce its visibility, at the request of government health officials. The decisions made about his Twitter handle were not explained to him at the time, but were later shown to him after Twitter changed ownership. This lack of transparency is problematic. Thats why, for years, groups such as EFF have pressed Big Tech companies to be more clear to users about their decision making processes, especially when those decisions start with a government request.
The claim often made by some Members of Congress, including Committee Chair Cathy McMorris Rodgers (R-WA), is that Section 230 lies at the heart of the censorship. The statement misunderstands the issue. Platforms are private entities and, as weve explained...
10:15
Italy Temporarily Blocks ChatGPT, Citing Privacy Issues HackRead | Latest Cybersecurity and Hacking News Site
Italy has given OpenAI, the parent company of ChatGPT, a deadline of 20 days to sort out privacy issues, including data collection, under Europe's General Data Protection Regulation (GDPR).
This is a post from HackRead.com Read the original post: Italy Temporarily Blocks ChatGPT, Citing Privacy Issues
10:00
Tiny Yet Functional Bike Built From Scratch Hackaday

Sometimes, you just want to go ride your bike in the great outdoors, but you cant be bothered throwing it in the back of the car. That wouldnt be a problem if you rode this latest build from [The Q]: a bike small enough to fit in a handbag.
...
08:43
Wine 8.5 Released With VKD3D 1.7 Included, WinRT App Dark Theme Phoronix
Wine 8.5 is out to end out the month as the newest bi-weekly development release for enjoying the ability to run Windows games and applications on Linux and other platforms...
08:23
For Europe, This Upcoming German Rocket Can't Arrive Soon Enough SoylentNews
German company Isar Aerospace has raised $165 million in order to ramp up the development of its Spectrum rocket, which is scheduled for its debut launch later this year. For Europeans needing access to space, the rocket's arrival will come not a moment too soon.
[...] Isar Aerospace has raised a total of $330 million so far, with $75 million raised during its previous round of funding in July 2021. The funds will go towards the development of Isar's Spectrum rocket, a two-stage launch vehicle designed to carry small and medium sized satellites to orbit. According to ISAR, Spectrum should be capable of carrying 2,205 pounds (1,000 kilograms) to low Earth orbit (LEO). By comparison, SpaceX's medium-lift Falcon 9 can hoist 50,265 pounds (22,800 kg) to LEO.
Spectrum's inaugural launch is planned for the second half of 2023. Isar Aerospace is currently running tests on the rocket's Aquila engine, which was developed and manufactured in-house. The company is also finalizing its infrastructure at the launch site in Andya, Norway, which will host Spectrum's debut liftoff.
[...] Europe is desperately in need of its own launch vehicles, whether for small or medium lift, to provide local access to space. Spectrum won't be the most powerful rocket when it debuts, but it'll fill a troublesome gap, especially until Vega-C and Ariane 6 come through.
Read more of this story at SoylentNews.
07:59
New Cylance Ransomware Targets Linux and Windows, Warn Researchers HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
For now, Cylance ransomware is still in its early stages, yet it has already claimed several victims.
This is a post from HackRead.com Read the original post: New Cylance Ransomware Targets Linux and Windows, Warn Researchers
07:58
Stupid Patent of the Month: Traxcell Tech Gets Ordered To Pay Attorneys Fees Deeplinks
If someone loses a patent lawsuit very badlyto the point where they face orders to pay attorneys' feesyou wouldnt think they would be eager to come back to court with a nearly identical lawsuit. But thats what has happened with this months patent. Whats more, the lawyer representing the patent owner, William Ramey, has been ordered to pay attorneys' fees no fewer than five times in recent years.
U.S. Patent No. 10,820,147 is owned by Traxcell Technologies. Its not clear what, if anything, Traxcell ever made. The company applied for patents back in 2002. By 2004, it had a bare-bones website stating that its mission is to provide leading edge technology and innovation to in [sic] the field of telecommunications. Today, its business is pretty clearTraxcell is a patent troll. The companys website has little information beyond its patents, which have been used in dozens of lawsuits since 2017.
The key claim of the 147 patent is long, but it essentially describes a wireless device that collects and shows location information, and also includes traffic congestion information. Theres also the feature that the device can allow, or disallow, tracking (a standard feature on modern smartphones).
This patent has come up in more than 20 of Traxcells lawsuits in the last two years, with its litigation picking up steam as the patents expiration date of September 2022 drew near. Its been used to sue major cell phone companies like T-Mobile and Verizon, the makers of online maps like Google and Apple, and delivery and gig companies. Its sued FlightAware for using publicly available flight-tracking information, and the Curb app for tracking taxis, and Instacart for tracking its own shoppers.
Objectively Baseless Theories
Traxcell was scheduled to bring this patent to trial next week in a federal Texas court. The trial actually would have been the conclusion of Traxcells second lawsuit against Verizon. Since its coming back for another round, one might think that Traxcells first lawsuit was a big success. Thats not the case, though.
In the first Traxcell v. Verizon patent lawsuit, filed in the Eastern District of Texas (then a hot patent venue), Verizon won on summary judgmentmeaning, before the case went to a jury, a judge ruled there was no patent infringement, and that the case was over. Traxcell appealed, but the appeals court agreed that Verizon should win the ca...
07:49
Without Verification, What Is the Point of Elon Musks Twitter? Deeplinks
Elon Musk's Twitter fundamentally misunderstands what made Twitter useful in the first place. In an attempt to wring blood from a stone, Twitters announced that all the original "blue checks"initially created as a way to verify that someone was who they said they werewill disappear on April 1st. Instead, blue checks will once again be for sale, just as they were briefly, when Musk took control. April 1 is a date that makes it hard to take anything seriously but, since this isnt the first time Twitters tried this, let's delve into the problems that selling verifications poses.
Twitter used to do a better job of content moderation than many of its social media competitors. The company tended to err on the side of labeling objectionable content rather than removing it. Twitter had an admirable commitment to transparency and standing up for its users (that isn't to say it was good: content moderation at scale almost never turns out well. It simply had smarter failures than the rest).
Twitters good qualitiesfeatures and practices that many users all over the world came to rely onare all but gone now.
Twitter Before
Twitter first introduced blue checkmarks in 2009, after celebrities complained of being impersonated on the platform. While verification was only available to well-known public figures (e.g. actors, athletes, politicians) at first, checkmarks were later rolled out to companies, journalists, activists, and even social media influencers. In 2016, the company briefly rolled out a verification application process, so individuals who could prove their notability could get verified. That process was shut down after a white supremacist was verified through it, and wasnt reopened until late 2020, with tighter qualifications.
Although the specifics of Twitters verification procedures were often criticized, the blue checkmarks served an important function: verifying that a person or company was exactly who they said they were. It's partially what made Twitter so beloved by journalists: it was harder to accidentally include a tweet by a joke account in your reporting. It also saved a lot of journalists from hunting down an email address or a public relations person when they wanted to contact someonefar easier to just send a DM. Furthermore, journalists with the checkmarks were clearly also who they said they were, making it more likely they'd get responses from subjects who could tell that they were legitimate...
07:17
Intel oneDNN 3.1 Further Optimizing For Sapphire Rapids, Starts Tuning For Sierra Forest Phoronix
Intel's oneAPI software engineers are closing out the quarter by library that is used by the likes of PyTorch, Tensorflow, PaddlePaddle, ONNX, OpenVINO, MATLAB's Deep Learning Toolbox, Apache MXNet, and many other applications...
07:16
Hackers are actively exploiting a flaw in the Elementor Pro WordPress plugin Security Affairs
Threat actors are actively exploiting a high-severity flaw in the Elementor Pro WordPress plugin used by more than eleven million websites
WordPress security firm PatchStack warns of a high-severity vulnerability in the Elementor Pro WordPress plugin that is currently being exploited by threat actors in the wild.
Elementor Pro is a paid plugin that is currently installed on over 11 million websites, it allows users to easily create WordPress websites.
This vulnerability was reported on March 18 by security researcher Jerome Bruandet from NinTechNet.
The expert reported that the issue impacts Elementor Pro when it is installed on a site that has WooCommerce activated.
allowing authenticated users, like shop customers or site members, to change the sites settings and can potentially lead to a complete site takeover.Elementor Pro, a popular page builder plugin for WordPress, fixed a broken access control vulnerability affecting versions <=3.11.6 that could allow full site takeover. reads the advisory published by Bruanded.
The flaw is broken access control on the plugins WooCommerce module (elementor-pro/modules/woocommerce/module.php), anyone can exploit the issue to change WordPress settings in the database. The flaw is exploited through a vulnerable AJAX action, pro_woocommerce_update_page_option, which is used by Elementors built-in editor.
The issue stems from improper input validation and a lack of capability check to restrict its access to a high privileged user only.
An authenticated attacker can leverage the vulnerability to create an administrator account by enabling registration and setting the default role to administrator, change the administrator email address or, redirect all traffic to an external malicious website by changing siteurl among many other possibilities, wrote Bruandet.
Elementor Plugin bug actively exploited
PatchStack researchers are observing attacks from multiple IP addresses, most of them from the following IP addresses:
- 193.169.194.63
- 193.169.195.64
- 194.135.30.6
The experts are also seeing files being uploaded with the followin...
07:14
Pirate Site Blocking Decreases Internet Traffic, Research Finds TorrentFreak
 In
recent years, website blocking has become one of the most
widely-used anti-piracy enforcement mechanisms in the world.
In
recent years, website blocking has become one of the most
widely-used anti-piracy enforcement mechanisms in the world.
ISPs in several dozen countries prevent subscribers from accessing a variety of pirate sites. While new blocks are added every month, research on the effectiveness of these efforts is rather limited.
Early Piracy Blocking Research
One of the earliest pieces of academic research, based on UK data, showed that the local Pirate Bay blockade had little effect on legal consumption. Instead, pirates turned to alternative pirate sites, proxies, or VPNs to bypass the virtual restrictions.
A follow-up study added more color and brought hope for rightsholders. The research showed that once a large number of sites were blocked in the UK, overall pirate site traffic decreased. At the same time, the researchers observed an increase in traffic to legal services such as Netflix.
These academic studies originated at Carnegie Mellon University. They were conducted independently but the research received sizable gifts from the Motion Picture Association. The movie industry group often cites these results to show that site blocking is effective.
New Blocking Study Adds Nuance
The two blocking papers and their results are founded on quality research, but theyre not without limitations. One shortcoming is that they are based on UK data that may differ from how blocking measures affect piracy and legal consumption in other parts of the world.
A recently released study can partly fill this gap. It was conducted by researchers from the Catolica-Lisbon School of Business and Economics in Portugal, in collaboration with a colleague who, again, is affiliated with Carnegie Mellon University.
Instead of looking at UK data, the researchers analyzed data from a country where a voluntary pirate site blocking scheme was introduced at some point.
The target country isnt mentioned but considering that the researchers are Portuguese, paired with the fact that Portugal is one of the few countries which has a voluntary blocking scheme, we can take an informed guess.
Tracking Internet, TV, and Spending Habits...
07:00
See Satellites in Broad Daylight with This Sky-Mapping Dish Antenna Hackaday

If you look up at the night sky in a dark enough place, with enough patience youre almost sure to see a satellite cross the sky. Its pretty cool to think youre watching light reflect off a hunk of metal zipping around the Earth fast enough to never hit it. Unfortunately, it doesnt work during the daylight hours, and you really only get to see satellites in low orbits.
Thankfully, theres a trick that allows you to see satellites any time of day, even the ones in geosynchronous orbits you just need to look using microwaves. Thats what [Gabe] at [saveitforparts] did with a repurposed portable satellite dish, the kind that people who really dont like being without their satellite TV programming when theyre away from home buy and quickly sell when they realize that toting a satellite dish around is both expensive and embarrassing. They can be had for a song, and contain pretty much everything needed for satellite comms in one package: a small dish on a motorized altazimuth mount, a low-noise block amplifier (LNB), and a single-board computer that exposes a Linux shell.
After figuring out how to command the dish to specific coordinates...
05:49
EuroLinux Desktop 9.1 Released As Easy Windows Workstation Replacement FOSS Force
EuroLinux, the Poland-based company behind the RHEL clone by the same name, has announced the first point release of EuroLinux Desktop, a desktop Linux distribution that was unveiled in September.
The post EuroLinux Desktop 9.1 Released As Easy Windows Workstation Replacement appeared first on FOSS Force.
05:37
Italy Moves to Ban Lab-grown Meat to Protect Food Heritage SoylentNews
Italy's right-wing government has backed a bill that would ban laboratory-produced meat and other synthetic foods, highlighting Italian food heritage and health protection.
If the proposals go through, breaking the ban would attract fines of up to 60,000 (53,000).
Francesco Lollobrigida, who runs the rebranded ministry for agriculture and food sovereignty, spoke of the importance of Italy's food tradition.
The farmers' lobby praised the move.
But it was a blow for some animal welfare groups, which have highlighted lab-made meat as a solution to issues including protecting the environment from carbon emissions and food safety.
[...] The proposals, approved by ministers on Tuesday, seek to ban synthetic foods produced from animal cells without killing the animal, and would apply to lab-produced fish and synthetic milk too.
Read more of this story at SoylentNews.
05:35
German Police Raid DDoS-Friendly Host FlyHosting Krebs on Security
Authorities in Germany this week seized Internet servers that powered FlyHosting, a dark web offering that catered to cybercriminals operating DDoS-for-hire services, KrebsOnSecurity has learned. FlyHosting first advertised on cybercrime forums in November 2022, saying it was a Germany-based hosting firm that was open for business to anyone looking for a reliable place to host malware, botnet controllers, or DDoS-for-hire infrastructure.

A seizure notice left on the FlyHosting domains.
A statement released today by the German Federal Criminal Police Office says they served eight search warrants on March 30, and identified five individuals aged 16-24 suspected of operating an internet service since mid-2021. The German authorities did not name the suspects or the Internet service in question.
Previously unknown perpetrators used the Internet service provided by the suspects in particular for so-called DDoS attacks, i.e. the simultaneous sending of a large number of data packets via the Internet for the purpose of disrupting other data processing systems, the statement reads.
News of a raid on FlyHosting first surfaced Thursday in a Telegram chat channel that is frequented by people interested or involved in the DDoS-for-hire industry, where a user by the name Dstatcc broke the news to FlyHosting customers:
So Flyhosting made a migration with it[s] systems to new rooms of the police ;), the warning read. Police says: They support ddos attacks, C&C/C2 and stresser a bit too much. We expect the police will take a deeper look into the files, payment logs and IPs. If you had a server from them and they could find bad things connected with you (payed with private paypal) you may ask a lawyer.
05:33
After Students Challenged Proctoring Software, French Court Slaps TestWe App With a Suspension Deeplinks
In a preliminary victory in the continuing fight against
privacy-invasive software that watches students taking tests
remotely, a French administrative court outside Paris suspended a
universitys use of the e-proctoring platform TestWe, which monitors
students through facial recognition and algorithmic analysis.
TestWe software, much like
Proctorio, Examsoft, and other proctoring apps
weve called out for intrusive monitoring of exam takers,
constantly tracks students eye movements and their surroundings
using video and sound analysis. The court in Montreuil, France,
ruled that such permanent surveillance of bodies and sounds is
unreasonable and excessive for the purpose preventing cheating.
Proctoring apps came roaring on the scene during the COVID-19
pandemic when closed schools switched to remote learning.
Proctoring software makers promised schools a way to continue to
administer and control high-stakes tests to students at homeby
surveilling them, tracking their keystrokes, checking if their eyes
moved away from the screen, and watching to see if they navigated
away from the test, all through their computers.
Theres a lot wrong with these apps. They invade students privacy,
exacerbate existing inequities in educational outcomes, and can
never fully match the control schools are used to enforcing in the
test hall. And they are faulty: ProctorU, one of the largest remote
proctoring companies,
recently stopped selling fully-automated proctoring services
because too few administrators and teachers were reviewing the
results to determine whether or not a flagged violation was
actually a violation. Although many students have gone back to
in-person learning, remote proctoring is still in use, and we dont
believe it is going away anytime soon.
The TestWe case is one of the first weve seen in Europe challenging
proctoring software. Its a good sign on two fronts. It shows that
concerns about what some have called
legitimized spyware are shared by students and digital rights
defenders around the world. And like
students here in the U.S., theyre challenging the use of
th...
05:30
Move Aside Yoda, its Furbys Turn On Lukes Back Hackaday

When you want a backpack that turns heads and gets people talking, you can get ahead of the conversation with a talking backpack. [Nina] created a rucksack with the legendary babbler itself, the infamous Furby.
Believe it or not, no actual Furbies were sacrificed in the making of this backpack. The build uses an Arduino Nano, two servos, and a DFPlayer Mini for audio. A 3D printed faceplate is used for the iconic eyes and face. The code is fairly simple, waiting for a random delay and then triggering one of four effects. It can play a sound or blink and does its best to move the mouth while the sound is playing thanks to the handy busy line coming off the sound module. A unicorn childrens backpack offered a furry shell to stuff the electronics inside. A custom PCB makes the whole thing just a little neater internally.
Perhaps next [Nina] can integrate voice recognition so that the backpack can answer simple questions like...
05:19
WHO Now Says COVID Vaccines Not Recommended For Healthy Kids & Teens cryptogon.com
After forcing it on millions Via: Summit News: Yet another leading health institution has unveiled a significant Covid policy reversal this week this time its none other than the World Health Organization (WHO) saying something that might have gotten an individual suspended from social media or publicly canceled a mere one or two years ago. []
04:15
Ukraine Busts Gang for Massive $4.3 Million Phishing Scams HackRead | Latest Cybersecurity and Hacking News Site
The Ukrainian Cyber Police carried out 30 searches and managed to seize computer equipment, mobile phones, SIM cards, and other equipment.
This is a post from HackRead.com Read the original post: Ukraine Busts Gang for Massive $4.3 Million Phishing Scams
04:00
Why A Community Hackerspace Should Be A Vital Part Of Being An Engineering Student Hackaday

Travelling the continents hackerspaces over the years, I have visited quite a few spaces located in university towns. They share a depressingly common theme, of a community hackerspace full of former students who are now technology professionals, sharing a city with a university anxious to own all the things in the technology space and actively sabotaging the things they dont own. Ive seen spaces made homeless by university expansion, Ive seen universities purposefully align their own events to clash with a hackerspace open night and discourage students from joining, and in one particularly egregious instance, Ive even seen a university take legal action against a space because they used the name of the city, also that of the university, in the name of their hackerspace. I will not mince my words here; while the former are sharp practices, the latter is truly disgusting behaviour.
The above is probably a natural extension of the relationship many universities have with their cities, which seems depressingly often to be one of othering and exclusion. Yet in the case of hackerspaces I cant escape the conclusion that a huge opportunity is being missed for universities to connect engineering and other tech-inclined students...
03:52
Video Friday: Grain Weevil IEEE Spectrum

Video Friday is your weekly selection of awesome robotics
videos, collected by your friends at IEEE Spectrum
robotics. We also post a weekly calendar of upcoming robotics
events for the next few months. Please
send us your events for inclusion.
Robotics Summit & Expo: 1011 May 2023, BOSTON
ICRA 2023: 29 May2 June 2023, LONDON
RoboCup 2023: 410 July 2023, BORDEAUX, FRANCE
RSS 2023: 1014 July 2023, DAEGU, KOREA
IEEE RO-MAN 2023: 2831 August 2023, BUSAN, KOREA
CLAWAR 2023: 24 October 2023, FLORIANOPOLIS, BRAZIL
Humanoids 2023: 1214 December 2023, AUSTIN, TEXAS, USA
Enjoy todays videos!
This is the Grain Weevil, and its designed to keep humans out of grain bins. I love this because its an excellent example of how to solve a real, valuable problem uniquely with a relatively simple, focused robot.
[ Grain Weevil ]
As the city of Paris sleeps, Spot is hard at work inspecting some of RATP Groups 35,000 civil works components. The RATP Group (Autonomous Parisian Transportation Administration), is a French state-owned public transport operator and maintainer for the Greater Paris area. With thousands of civil works to inspect each year, the company has turned to mobile robotics to inspect hard-to-reach and hazardous areas in order to keep employees out of harms way.
...
03:43
nrcisztikus vagyok? Hogyan mondhatjuk el h+ Media
nrcisztikus vagyok? Hogyan mondhatjuk el
nrcizmus lerja a szemlyisgjegyeket, mint pldul a hisg s az ngazdlkods. A nrcisztikus szemlyisgzavar mentlis egszsgi llapot, olyan tulajdonsgokkal, amelyek magukban foglalhatjk a tlzott figyelmet, az nfontossg felfjt rzst s az emptia hinyt.
Valaki, aki nrcisztikus, tlsgosan foglalkozhat a megjelenssel, vagy kevs id van arra, hogy msokra sszpontostson.
Ez azonban nem felttlenl jele annak, hogy valakinek nrcisztikus szemlyisgzavar (NPD) van. Brki viselkedhet nkzpont mdon az let klnbz pontjain.
Az NPD -vel rendelkez embereknek nehznek nem koncentrlni magukra, s nem ismeri fel, hogy ezt megteszik. Az NPD egy hossz tv llapot, amely jelentsen befolysolja az ember kapcsolatait s az rzelmi mkdst.
Ebben a cikkben megvizsgljuk, mi az NPD, az NPD jelei, s hogy ez hogyan befolysolja a kapcsolatokat.
Azt is megvitatjuk, hogy a nrcisztikus emberek megvltozhatnak -e, s hogyan tudjk ezt megtenni.
Mi a nrcisztikus szemlyisgzavar?
Az American Psychiatric Association (APA) szerint az NPD egy olyan szemlyisgzavar, amely csodlatra s msok irnti emptia hinyra.
Az NPD-ben szenved embereknek nagymrtkben nfontossg rzse s jogosultsg rzse lehet. Gyakran hinyzik az emptia, s kevs rdekldsk lehet a msokkal val intim kapcsolatok kialaktsa irnt.
Mg az NPD-vel rendelkez szemlyek tl magabiztosnak tnhetnek, gyakran alacsony nrtkelsk van. Attl fggen, hogy milyen slyos a rendellenessgk, rosszul reaglhatnak, amikor egy szemly vagy esemny megkrdjelezi a flnyrzetket.
Egy rgebbi 2008 -as tanulmny a Journal of Clinical Psychiatry becslse szerint az emberek 6,2% -a l az NPD -ben letk valamikor. Az arny magasabb a frfiak krben (7,7%), mint a nstnyek (4,8%).
A tanulmny azt is jelentette, hogy az NPD szignifiknsan elterjedtebb:
- Fekete felnttek
- spanyol nstnyek
- Fiatalabb felnttek
- Azok, akik elvlasztottak, elvltak vagy zvegyek
- felnttek, akik soha nem hzasodnak meg Az NPD szles kr s eltr
mdon jelenik meg, az egyes esetek slyossgtl fggen.
Az NPD-vel rendelkez emberek lehetnek:
- nbizonyt vagy nelgltsg
- extrovertlt vagy trsadalmilag elszigetelten vagy munkanlkliek
- A polgrok vagy antiszocilis tevkenysgekben rszt vev emberek modelljei
Ezrt nehz lehet felismerni az NPD -vel rendelkez szemlyt. A mentlis rendellenessgek diagnosztikai s statisztikai kziknyvnek (DSM-5) tdik kiadsa azonban a kvetkez tneteket tartalmazza:
1. Az nfontossg tlzott rzse
Grandiose-val rendelkezik. Az nfontossg rzse az NPD meghatroz jellemzje. Az NPD -ben szenved embereknek rzse van a tbbiekkel szemben.
Nem...
03:42
Re: CVE-2023-29132: Irssi SA-2023-03 / Use after free in printing routine Open Source Security
Posted by Ailin Nemui on Mar 31
CVE-2023-29132 was assigned03:38
Links 31/03/2023: Ruby 3.2.2 and Linux Lite 6.4 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Audiocasts/Shows
-
CubicleNate Linux Saloon | 25 Mar 2023 | Archcraft Linux
I am not what one would call a huge fan of Arch Linux or its derivatives. My past experiences have all been pretty poor so really, the bar is set...
-
-
03:02
A quarter century of Mozilla LWN.net
The Mozilla project celebrates 25 years of existence.
A lot has changed since 1998. Mozilla is no longer just a bold idea. Were a family of organizations a nonprofit, a public benefit-corporation, and others that builds products, fuels movements, and invests in responsible tech.And were no longer a small group of engineers in Netscapes Mountain View office. Were technologists, researchers, and activists located around the globe not to mention tens of thousands of volunteers.
But if a Mozillian from 1998 stepped into a Mozilla office (or joined a Mozilla video call) in 2023, I think theyd quickly feel something recognizable. A familiar spirit, and a familiar set of values.
03:01
Do advanced Linux disk usage diagnostics with this sysadmin tool Linux.com
Use topdiskconsumer to address disk space issues when youre unable to interrupt production.
Read More at Enable Sysadmin
The post Do advanced Linux disk usage diagnostics with this sysadmin tool appeared first on Linux.com.
03:00
Hackaday Podcast 212: Staring Through ICs, Reading Bloom Filters, and Repairing, Reworking, and Reballing Hackaday

It was quite the cornucopia of goodness this week as Elliot and Dan sat down to hash over the week in hardware hacking. We started with the exciting news that the Hackaday Prize is back already? for the tenth year running! The first round, Re-Engineering Education, is underway now, and were already seeing some cool entries come in. The Prize was announced at Hackday Berlin, about which Elliot waxed a bit too. Speaking of wax, if youre looking to waterproof your circuits, thats just one of many coatings you might try. If youre diagnosing a problem with a chip, a cheap camera can give your microscope IR vision. Then again, you might just use your Mark I peepers to decode a ROM. Is your FDM filament on the wrong spool? Weve got an all-mechanical solution for that. Well talk about tools of the camera operators trade, the right to repair in Europe, Korean-style toasty toes, BGA basics, and learn just what the heck a bloom filter is or is it a Bloom filter?
Check out the links below if you want to follow along, and as always, tell us what you think about this episode in the comments!
03:00
Panfrost Driver For Linux 6.4 Adds Speed Binning, New MediaTek SoCs Phoronix
The Panfrost DRM driver providing open-source kernel graphics driver support for modern Arm Mali graphics in various SoCs is seeing some new hardware support for the upcoming Linux 6.4 cycle as well as now supporting speed binning functionality...
02:51
Bent Light in Deep Space Reveals One of the Biggest Black Holes Ever Detected SoylentNews
A rare 'ultramassive' black hole, 30 billion times the mass of the Sun, is lurking in the cosmos:
Holy smokes. A group of astronomers have found a black hole containing (checks notes) 30 billion times the mass of our Sun. That's more than seven thousand times the size of the supermassive black hole at the center of the Milky Way.
The team used gravitational lensing to see the black hole. In this natural phenomenon, massive objects' gravitational fields bend photons of light magnifying and warping themmaking it possible to see object that would otherwise be hidden or too faint. Last year, a team spotted the oldest known star in an arc of gravitationally lensed light.
According to a Durham University release, the newly detected black hole is the first ever found using gravitational lensing. A paper about the discovery is published today in the Monthly Notices of the Royal Astronomical Society.
[...] The team identified the black hole by modeling the different pathways light might take through the universe, depending on the presence of black holes of varying mass. They then compared the computer data with images of the cosmos taken by the Hubble Space Telescope. Lo and behold, they found a match.
[...] "Gravitational lensing makes it possible to study inactive black holes, something not currently possible in distant galaxies," Nightingale added. "This approach could let us detect many more black holes beyond our local universe and reveal how these exotic objects evolved further back in cosmic time."
A brief video explaining the process
Journal Reference:
James. W. Nightingale, Russell J. Smith, Qiuhan He, et
al., Abell 1201: Detection of an Ultramassive Black Hole in
a Strong Gravitational Lens, arXiv:2303.15514 [astro-ph.GA],
https://doi.org/10.48550/arXiv.2303.15514
Read more of this story at SoylentNews.
02:46
Paillier's additively homomorphic cryptosystem David Wong | Cryptologie | HTML
Pascal Paillier released his asymmetric encryption algorithm in 1999, which had the particularity of being homomorphic for the addition. (And unlike RSA, the homomorphism was secure.)
Homomorphic encryption, if you haven't heard of it, is the ability to operate on the ciphertext without having to decrypt it. If that still doesn't ring a bell, check my old blogpost on the subject. In this post I will just explain the intuition behind the scheme, for a less formal overview check Lange's excellent video.
Paillier's scheme is only homomorphic for the addition, which is still useful enough that it's been used in different kind of cryptographic protocols. For example, cryptdb was using it to allow some types of updates on encrypted database rows. More recently, threshold signature schemes have been using Paillier's scheme as well.
The actual algorithm
As with any asymmetric encryption scheme, you have the good ol' key gen, encryption, and decryption algorithms:
Key generation. Same as with RSA, you end up with a public modulus $N = pq$ where $p$ and $q$ are two large primes.
Encryption. This is where it gets weird, encryption looks more like a Pedersen commitment (which does not allow decryption). To encrypt, sample a random $r$ and produce the ciphertext as:
$$(N+1)^m \cdot r^N \mod{N^2}$$
where $m$ is the message to be encrypted. My thought at this point was "WOOT. A message in the exponent? How will we decrypt?"
Decryption. Retrieve the message from the ciphertext $c$ as
$$\frac{c^{\varphi(N)} -1}{N} \cdot \varphi(N)^{-1} \mod{N^2}$$
Wait, what? How is this recovering the message which is currently the discrete logarithm of $(N+1)^m$?
How decryption works
The trick is in expanding this exponentiation (using the Binomial expansion).
The relevant variant of the Binomial formula is the following:
$$(1+x)^n = \binom{n}{0}x^0 + \binom{n}{1}x^1 + \cdots + \binom{n}{n} x^n$$
where $\binom{a}{b} = \frac{a!}{b!(a-b)!}$
So in our case, if we only look at $(N+1)^m$ we have:
$$ \begin{align} (N+1)^m &= \binom{m}{0} + \binom{m}{1} N + \binom{m}{2} N^2 + \cdots + \binom{m}{m} N^m \\ &= \binom{m}{0} + \binom{m}{1} N \mod{N^2}\\ &= 1 + m \cdot N \mod{N^2} \end{align} $$
Tada! Our message is now back in plain sight, extracted...
02:30
GaN Charger Teardown Reveals Value Of This New Technology Hackaday

Every so often, a new technology comes along that offers a broad range of benefits over what we already have. Just as lithium-ion batteries have made nickel-cadmium cells boring and old hat, gallium nitride semiconductors are making silicon parts look unimpressive by comparison. [Brian Dipert] looked at what this means in a practical sense by tearing down a GaN phone charger.
The charger in question is a 30 watt USB-C charger produced by Voltme. It cost [Brian] just $10, as prices of GaN hardware have come down significantly as economies of scale have kicked in. The charger measures just 1.21.31.2 inches, and weighs only 1.5 ounces. That compact size is thanks to GaN semiconductors, which are able to run cooler at higher power levels than their silicon forebearers.
Cracking into the charger required levering open the case. The back panel came off with some work, revealing the mains terminals, which deliver AC power to the PCB inside via the case holding them in contact. Interestingly, the entire circuit inside is filled with an adhesive thermal goop, which helps pass heat from the hottest components...
02:22
Supply chain cyberattack with possible links to North Korea could have thousands of victims globally Lifeboat News: The Blog
Hackers modified an enterprise communication companys installation software in an attack that could steal credentials and other information from companies around the world, according to an analysis published Wednesday.
Researchers with cybersecurity firm SentinelOnes SentinelLabs team traced illicit activity flagged by its detection systems back to the installation software from a company called 3CX, which according to its website provides video conferencing and online communication products to companies such as Toyota, McDonalds, Pepsi and Chevron. In total, the company says it serves some 12 million customers globally.
This sort of large-scale attack that takes advantage of a companys supply chain similar to how attackers leveraged a flaw within a SolarWinds product update to install backdoors inside its customers networks can be difficult to defend against and could lead to devastating consequences for victims. Its also the kind of operation that is typically associated with a nation-state hacking group.
02:08
BSD Release: MidnightBSD 3.0.0 DistroWatch.com: News
MidnightBSD is a desktop-oriented operating system derived from FreeBSD. The project's latest stable release is MidnightBSD 3.0.0 which is available in i386 and x86_64 builds. With this leap in changes. "There are known issues with the Firefox,....
02:00
The Staggering Scale of the EV Transition IEEE Spectrum

Over the last 20 or so years, contributing editor Robert N. Bob Charette has written about some of the thorniest issues facing the planet at large and engineers in particular. For IEEE Spectrum, hes dug into software reliability and maintenance, the so-called STEM crisis, and the automation paradox, examining those complex topics through the eyes of a seasoned risk analyst who has consulted for governments and corporations for five decades.
Ive been fortunate to be Bobs editor for many of his ambitious projects. We often converse on Friday afternoons about what hes hearing from industry insiders and academics on whatever subject hes currently investigating. Our conversations are jovial, sometimes alarming, and always edifying, at least for me.
So when he called me on a Friday afternoon in the summer of 2021 to propose an article delving into the complexities of the global transition to electric vehicles, I knew that hed do the research at a deeper level than any tech journalist, and that hed explore angles that wouldnt even occur to them.
Take power-grid transformers. These essential voltage-converting components are designed to cool down at night, when power consumption is typically low. But with more people charging their EVs at home at night, the 30-year design life of a transformer will dropto perhaps no more than three years once mass adoption of EVs takes hold. Transformers can cost more than US $20,000 each, and theyre already in short supply in many countries. Bob examined factors like that and dozens of others during the last year and a half.
Throughout his research and reporting, Bob focused on the EV transition at scale: What needs to happen in order for electric vehicles to displace internal-combustion-engine vehicles and have a measurable impact on climate change by midcentury? Quite a lot, it turns out. Humans must change two foundational sectors of modern civilizationenergy and transportationto achieve the targeted reductions in greenhouse gas emissions. These simultaneous global overhauls will involve trillions of dollars in investments, tens of millions of workers, millions of new EVs, tens of thousands of kilometers of new transmission...
01:49
[$] An operation for filesystem tucking LWN.net
As a general rule, the purpose behind mounting a filesystem is to make that filesystem's contents visible to the system, or at least to the mount namespace where that mount occurs. For similar reasons, it is unusual to mount one filesystem on top of another, since that would cause the contents of the over-mounted filesystem to be hidden. There are exceptions to everything, though, and that extends to mounted filesystems; a "tucking" mechanism proposed by Christian Brauner is designed to hide mounted filesystems underneath other mounts temporarily, at least.
01:43
CISA Warns of Vulnerabilities in Propump and Controls Osprey Pump Controller HackRead | Latest Cybersecurity and Hacking News Site
CISA's advisory came after the Macedonian cybersecurity firm Zero Science Lab discovered and reported the vulnerabilities to authorities.
This is a post from HackRead.com Read the original post: CISA Warns of Vulnerabilities in Propump and Controls Osprey Pump Controller
01:40
Security updates for Friday LWN.net
Security updates have been issued by Debian (joblib, json-smart, libmicrohttpd, and xrdp), Fedora (thunderbird and xorg-x11-server-Xwayland), Mageia (dino, perl-Cpanel-JSON-XS, perl-Net-Server, snort, tigervnc/x11-server, and xapian), SUSE (curl, kernel, openssl-1_0_0, and shim), and Ubuntu (glusterfs, linux-gcp-4.15, musl, and xcftools).
01:07
Winter Vivern APT Targets European Government Entities with Zimbra Vulnerability The Hacker News
The advanced persistent threat (APT) actor known as Winter Vivern is now targeting officials in Europe and the U.S. as part of an ongoing cyber espionage campaign. "TA473 since at least February 2023 has continuously leveraged an unpatched Zimbra vulnerability in publicly facing webmail portals that allows them to gain access to the email mailboxes of government entities in Europe," Proofpoint
01:00
This Week in Security: Macstealer, 3CX Carnage, and Githubs Lost Key Hackaday

Theres a naming overload here, as two bits of security news this week are using the MacStealer moniker. Were first going to talk about the WiFi vulnerability, also known as Framing Frames (pdf). The WPA encryption schemes introduced pairwise encryption, ensuring that not even other authenticated users can sniff each others traffic. At least thats the idea, but this attack finds a couple techniques to bypass that protection.
A bit more background, there are a couple ways that packets can be delayed at the sender side. One of those is the power-save message, that signals the access point that the given client is going into a low power state. Hold my calls, Im going to sleep. That message is a single bit in a frame header. And notably, that bit isnt covered by WPA encryption or verification. An attacker can send a message, spoof a victims MAC address, and the access point marks that client as being in power-save mode.
This observation leads to a question: What happens when the encryption details change between the packet joining the queue, and actually transmitting? Turns out, the specifications on WiFi encryption dont spell it out, and some implementations do the last thing youd want, like sending the packets in t...
00:39
Distribution Release: Linux Lite 6.4 DistroWatch.com: News
Linux Lite is a beginner-friendly Linux distribution based on Ubuntu's long-term support (LTS) release and featuring the Xfce desktop. The project has published an update to its 6.x series which improves packaging compression for custom software, offer a new reporting tool to diagnose problems, and updates the layout....
00:37
Cyber Police of Ukraine arrested members of a gang that defrauded EU citizens of $4.33M Security Affairs
The Cyber Police of Ukraine, with law enforcement officials from Czechia, has arrested several members of a gang responsible for $4.33 million scam.
The Cyber Police of Ukraine, with the support of law enforcement officials from the Czech Republic, has arrested several members of a cybercriminal ring that defrauded EU citizens of $4.33 million with phishing campaigns.
The suspects set up more than 100 phishing websites to obtain the bank card data and banking account credentials of foreign citizens.
The members of the international criminal group were exposed by the employees of the Cyber Police Department together with the Main Investigation Department of the National Police and in cooperation with law enforcement officers of the Czech Republic. reads the press release published by the Cyber Police of Ukraine. Some of the people involved, who live in Ukraine, created more than 100 phishing sites aimed at European users. Various products were offered on web resources at below-market prices. Bank card data, which customers indicated on phishing resources to pay for orders, automatically became known to attackers. Later, they appropriated money from their accounts.
The cybercrime organization also created two call centers, in Vinnytsia and in Lviv, as part of the fraudulent scheme. Operators at the call centers attempted to trick customers into making purchases.
The websites were offering heavily discounted products to lure visitors placing orders. The bad news for the users was that the operators behind the websites were only interested in gathering financial information provided by the visitors while making fake purchases.

The authorities identified more than 1,000 victims from multiple countries, including the Czech Re...
00:26
Hack the Pentagon website promotes the benefits of bug bounties to US Military Graham Cluley
My guess is that if you stumbled across a website that called itself "Hack the Pentagon" and was decorated with a grisly-looking skull, you would probably think that you might be somewhere less than legitimate. After all, normally if you hacked The Pentagon you would find yourself in heaps of trouble. Read more in my article on the Hot for Security blog.
00:04
Netflix Might Bring its Games to TVs in Effort to Get People to Actually Play Them SoylentNews
Higher quality TV and movies? No. A standard of not cancelling shows after a single season? Nah. Mobile games on your TV? Yup. That appears to be Netflix's plan after a developer found some hidden code while digging through the platform. The company's actually been offering games on mobile since 2021, but given paltry player numbers, the effort to bring them to TVs, where most subscribers actually use Netflix, might be the best way to remind people that they're even there.
App developer Steve Moserwho shared his findings with Bloombergfound some sneaky lines of code during some digging into Netflix's back end. One line of the code allegedly read "A game on your TV needs a controller to play. Do you want to use this phone as a game controller?," indicating that a user's smartphone would serve as the controller for a game hosted on Netflix's interface.
Currently, Netflix's gaming service is relegated to mobile, and while there's critically acclaimed titles like Teenage Mutant Ninja Turtles: Shredder's Revenge and Immortality in there, you can only get at them either by stumbling on Netflix's games on your phone's app store or through a single row in the Netflix app. As such, it's easy to miss out on this side of Netflix entirely. According to recent data, only one percent of subscribers are playing games on Netflix.
Read more of this story at SoylentNews.
Friday, 31 March
23:58
Vulkan 1.3.246 Released With VK_EXT_shader_object Phoronix
Vulkan 1.3.246 has been published with one prominent new extension introduced that was started by Nintendo and worked on by several other hardware/software vendors...
23:30
Google Posts KVM-CPUFreq Driver To Dramatically Boost VM Performance, Power Efficiency Phoronix
Google engineers on Thursday posted initial "request for comments" patches on their KVM-CPUFreq driver that is part of their effort to improve the dynamic voltage and frequency scaling behavior and task placement within KVM-based virtual machines. This effort is leading to big improvements in raw performance and performance-per-Watt for tasks running within Linux VMs...
23:21
Links 31/03/2023: Devices and Games, Mostly Leftovers Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Monopolies
- Gemini* and Gopher
-
GNU/Linux
-
Desktop/Laptop
-
[Repeat/important] Free Desktop 2023 X.Org Board of Directors Elections timeline extended, request for nominations...
-
-
23:12
Re: polkitd service user privilege separation Open Source Security
Posted by Johannes Segitz on Mar 31
It adds an additional step an attacker needs to take before having rootprivileges. Also it is not just about security, it also helps to limit the
impact of non-security bugs. So I would keep the service user, but add
clear language that explains that this isn't a meaningful security boundary
and that this account needs to be considered to have root privileges.
Johannes
23:10
CVE-2023-26269: Apache James server: Privilege escalation through unauthenticated JMX Open Source Security
Posted by Benoit Tellier on Mar 31
Severity: moderateDescription:
management service without authentication by default. This
allows privilege escalation by a
malicious local user.
Administrators are advised to disable JMX, or set up a JMX password.
Work Arounds:
automatically for Guice users.
Credit:
Matei "Mal" Badanoiu (reporter)
References:...
23:07
Re: Re: sox: patches for old vulnerabilities Open Source Security
Posted by Steffen Nurpmeso on Mar 31
Hello Nam.Nam Nguyen wrote in
<87bkk9hljn.fsf@n.m>:
|Steffen Nurpmeso writes:
|> Steffen Nurpmeso wrote in
|> <20230314201652.RlbWr%steffen () sdaoden eu>:
|> ...
|>||Helmut Grohne wrote in
|>|| <20230314110138.GA1192267 () subdivi de>:
|>|||On Fri, Feb 03, 2023 at 09:44:47PM +0100, Helmut Grohne wrote:
|>|||> * CVE-2021-33844
|>|||
|>|||The original fix for this issue would cause a...
23:05
Re: Re: sox: patches for old vulnerabilities Open Source Security
Posted by Nam Nguyen on Mar 31
Steffen Nurpmeso writes:I propose keeping that check in order to fix the regression of not
opening wav gsm files.
Steffn Nurpmeso's patch with tweaks can be found inline at the end of
this email. This patch retains the line 654 hunk and adds line 961 hunk
to avoid dividing by 0 for wav gsm files. wav->numSamples is calculated
Feedback is welcome as I am not familiar with the code base....
23:01
Cyber Police of Ukraine Busted Phishing Gang Responsible for $4.33 Million Scam The Hacker News
The Cyber Police of Ukraine, in collaboration with law enforcement officials from Czechia, has arrested several members of a cybercriminal gang that set up phishing sites to target European users. Two of the apprehended affiliates are believed to be organizers, with 10 others detained in other territories across the European Union. The suspects are alleged to have created more than 100 phishing
22:47
Deep Dive Into 6 Key Steps to Accelerate Your Incident Response The Hacker News
Organizations rely on Incident response to ensure they are immediately aware of security incidents, allowing for quick action to minimize damage. They also aim to avoid follow on attacks or future related incidents. The SANS Institute provides research and education on information security. In the upcoming webinar, well outline, in detail, six components of a SANS incident response plan,
22:22
Microsoft lays off entire AI ethics team while going all out on ChatGPT Lifeboat News: The Blog
A new report indicates Microsoft will expand AI products, but axe the people who make them ethical.
22:22
Scientists use rocket to create artificial Northern Lights to better understand space weather Lifeboat News: The Blog
Aurora Borealis can cause damage to satellites in severe solar storms. Scientists are experimenting to understand near-space weather better.
22:00
Sound Open Firmware 2.5 Released - Continues Adoption Of Zephyr, Adds MediaTek MT8188 Phoronix
Sound Open Firmware "SOF" 2.5 has been released as this open-source sound/DSP firmware initiative that was originally started by Intel but now is a Linux Foundation project and seeing hardware support from multiple vendors...
22:00
Archiving the Entirety of DPReview Before Its Gone Hackaday

Despite the popular adage about everything on the internet being there forever, every day pages of information and sometimes entire websites are lost to the sands of time. With the imminent shutdown of the DPReview website, nearly 25 years of reviews and specifications of cameras and related content are at risk of vanishing. Also lost will be the content of forum posts, which can still be requested from DPReview staff until April 6th. All because the owner of the site, Amazon, is looking to cut costs.
As announced on r/photography, the Archive.org team is busy trying to download as much of the site as possible, but due to bottlenecks may not finish in time. One way around these bottlenecks is what is called the Archive Team Warrior, which involves either a virtual machine or Docker image that runs on distributed systems. In early April an archiving run using these distributed systems is planned, in a last-ditch attempt to re...
21:46
Bloomberg Launches Open-Source Funding Initiative Phoronix
The Bloomberg financial, software, and media company has announced their FOSS Fund as a small step for helping open-source projects they rely on and of interest to their employees...
21:27
Fedora 39 Planning For RPM 4.19 - Adds x86-64 v2/v3/v4 Feature Levels Phoronix
With the Fedora 39 release later this year the developers are packaging format...
21:23
Scientists Just Learned Something New About How Aspirin Works SoylentNews
New research into aspirin might one day lead to safer painkillers or even new cancer treatments:
We still have more to learn about one of the world's oldest drugs: aspirin. In research out this week, researchers say they've uncovered more about how the drug reduces inflammation. The findings might pave the way toward creating similar but safer treatments for inflammation and possibly even cancer, according to the team.
Also known as acetylsalicylic acid, aspirin was first synthesized around the turn of the 20th century, though a precursor to itderived from willow plantshas been used by humans for thousands of years. It's a type of nonsteroidal anti-inflammatory drug (NSAID), and, like other NSAIDs, it can treat fever, inflammation, and pain. It also has a unique blood-thinning effect.
Aspirin remains one of the most widely used medications in the world, both as a short-term option for various ailments and as a preventative treatment for people at high risk of cardiovascular disease. But it's not without side effectsnamely an increased risk of gastrointestinal bleeding. Last year, U.S. experts even stopped recommending a daily dose of baby aspirin for older adults without a history of heart attack or stroke, citing evidence that any modest benefits for the typical person would be outweighed by the known risks.
[...] Aspirin is known to inhibit enzymes called cyclooxygenase, or COX. These enzymes play a vital role in producing other chemicals that cause inflammation. The researchers say they discovered several ways that aspirin influences this process, from controlling transcription factors that allow the expression of cytokines (proteins involved in inflammation and our immune response) to slowing the breakdown of the amino acid tryptophan, another important player in inflammation. It also seems to accomplish the latter by inhibiting the production of indoleamine dioxygenases (IDOs), particularly IDO1, during the inflammatory process.
Read more of this story at SoylentNews.
20:58
Ubuntu 23.04 Beta Released - Powered By Linux 6.2, GNOME 44 & Other Updates Phoronix
The beta of Ubuntu 23.04 "Lunar Lobster" and its various spins/flavors were released overnight for testing...
20:52
Russian APT group Winter Vivern targets email portals of NATO and diplomats Security Affairs
Russian hacking group Winter Vivern has been actively exploiting Zimbra flaws to steal the emails of NATO and diplomats.
A Russian hacking group, tracked Winter Vivern (aka TA473), has been actively exploiting vulnerabilities (CVE-2022-27926) in unpatched Zimbra instances to gain access to the emails of NATO officials, governments, military personnel, and diplomats.
The CVE-2022-27926 flaw affects Zimbra Collaboration versions 9.0.0, which is used to host publicly facing webmail portals.
The attacker can also use the compromised accounts to carry out lateral phishing attacks and further infiltrate the target organizations
TA473 targeted US elected officials and staffers since at least February 2023. The threat actors created bespoke JavaScript payloads designed for each government targets webmail portal.
TA473s cyber operations align with the support of Russian and/or Belarussian geopolitical goals.
Researchers have observed TA473, a newly minted advanced persistent threat (APT) actor tracked by Proofpoint, exploiting Zimbra vulnerability CVE-2022-27926 to abuse publicly facing Zimbra hosted webmail portals. The goal of this activity is assessed to be gaining access to the emails of military, government, and diplomatic organizations across Europe involved in the Russia Ukrainian War. reads the post published by Proofpoint.
The JavaScript payloads were designed to conduct Cross Site Request Forgery attacks and steal usernames, passwords, and store active session and CSRF tokens from cookies facilitating the login to publicly facing target webmail portals.
These payloads allow actors to steal usernames, passwords, and store active session and CSRF tokens from cookies allowing the login to publicly facing vulnerable webmail portals belonging to target organizations.
The APT group uses scanning tools like Acunetix to identify unpatched webmail platforms used by target organizations.
The threat actors send phishing email from a compromised address, which is spoofed to appear as someone relevant to their organization.
Once the attackers identified the vulnerable platform, they deliver phishing emails containing malicious URLs that abuse known vulnerability to execute JavaScript payloads within the victims webmail portals.
20:49
How 2023 (When They Tell Us Pandemic is Over) Compares to 1999-2018 Death Rates schestowitz.com
tl;dr We are not back to normal, the new normal is a lot of death.
Here is the chart (notice the death levels on the right compared to the left, before and after pandemic)
Source data: original PDF from this page; it is compared to numbers from 2023 and 2022
20:37
3CX Supply Chain Attack Here's What We Know So Far The Hacker News
Enterprise communications software maker 3CX on Thursday confirmed that multiple versions of its desktop app for Windows and macOS are affected by a supply chain attack. The version numbers include 18.12.407 and 18.12.416 for Windows and 18.11.1213, 18.12.402, 18.12.407, and 18.12.416 for macOS. The issue has been assigned the CVE identifier CVE-2023-29059. The company said it's engaging the
20:25
Dune Space Folding [HD] Lifeboat News: The Blog
Dune Scene Stars: Kyle MacLachlan, Francesca Annis, Jrgen Prochnow, Silvana Mangano Director: David Lynch Writers: Frank Herbert, David Lynch Producer: Raffaella De Laurentiis Music: TOTO Production: Dino De Laurentiis Company, Estudios Churubusco Azteca S.A. Distributon: Universal Pictures Released: 1984
watch Dune https://play.google.com/store/movies/details/Dune?id=BB5433C0E07FCF5BMV
watch more Dune Movie Clips https://www.youtube.com/playlist?list=PLlv9mHE-UZgiplosau3azMHpKSbA1Imqz.
watch the Dune Movie Trailer https://www.youtube.com/watch?v=vqi7HxWNaF8&list=PLlv9mHE-UZ6ovmsoI28g.
watch Dune Special Features https://www.youtube.com/playlist?list=PLlv9mHE-UZghdiTb721OAsB-678qx946l.
listen to the Dune Original Score https://www.youtube.com/watch?v=xJBZU3USZ2E&list=PLlv9mHE-UZ4_Y-jBfB7y.
19:54
Canadian ISPs Blocked Pirate IPTV & Logged Customer IP Addresses TorrentFreak
 When
the first pirate site blocking applications began to gather
momentum in Europe, those concerned about where it all might lead
spoke of slippery slopes and thin ends of wedges.
When
the first pirate site blocking applications began to gather
momentum in Europe, those concerned about where it all might lead
spoke of slippery slopes and thin ends of wedges.
More than 15 years later, judges in dozens of countries have not only approved blocking injunctions that target static sites but are also happy to hand down flexible orders designed to rapidly counter new domains, proxies, and mirrors.
When pirate IPTV services hit the mainstream less than 10 years ago, the legal and technical challenges of blocking content quickly were considerable. But by carefully tapping in the wedge, showing patience, and not asking for too much at the wrong time, rightsholders can now block pirate IPTV services while judges are tucked up in bed.
Canadas Blocking Fast Track
Canadas Federal Court approved the countrys first IPTV blocking order in 2018, and the Federal Court of Appeal upheld it in May 2021.
Just two months later, the architects of the first order Rogers, Bell, TVA, and others filed a new application demanding faster, more flexible blocking. The Federal Court obliged and in 2022, Justice William F. Pentney handed down Canadas first dynamic pirate IPTV blocking order, crafted to protect the NHL broadcasters revenues.
Justice Pentney also issued instructions for one or more experts to review the process to ensure compliance with the Courts criteria for identifying pirate IP addresses. Dates and times when the IP addresses were supposed to be blocked, and whether they actually were, for example. A report on general compliance was the overriding theme.
Report Satisfied Judge, New Injunction Awarded
Before Rogers, Bell, TVA, and the other plaintiffs were able to renew their injunction, the Court reviewed the experts report to ensure that its instructions had been followed. The report was produced by IP lawyer David Lipkus and Jon Wilkins, co-founder of Quadra Partners.
While both men h...
19:00
Could 1080p Video Output From The RP2040 Be Possible? Hackaday

Modern microcontrollers often have specs comparable with or exceeding early gaming consoles. However, where they tend to fall short is in the video department, due to their lack of dedicated graphics hardware. With some nifty coding, though, great things can be achieved as demonstrated by [TEC_IST]s project that gets the RP2040 outputting 1080p video over HDMI.
The project builds on earlier work that saw the RP2040 outputting...
18:35
If You Dislike Choosing Captcha Images From a List Owl Have Good News for You SoylentNews
gCaptcha is the leading rival for quality captcha services against Google's renowned and universally despised recaptcha. When Google increased the price for recaptcha competing services took off taking what Google started from to improve the experience significantly. Some experiences with smiling dogs and cloudy horses were deemed to take this too far but these experiments showed that there are improvements to be made in the captcha game.
With hackers out to solve any captcha programmatically captcha services need to stay one step ahead. The slider method was found to be easily bypassed. Rotating puzzle pieces is harder to solve but involves more user interaction and has moving parts in the code that can break.
Recently hCaptcha has introduce a test that challenges the user to click on the center of an owl's head. This is an improvement over selecting a type of ball from a grid of 9 or going through the excruciating experience Google inflicts on users. There must be a better way to prove that the person viewing the web page is a human and not a bot. How about it, Soylentils? What's your best idea for a captcha system given the state of the systems we have today?
[Ed's Comment: Bonus points if you can suggest a system that does not rely on graphics (not everyone uses the latest browsers or even anything more than a simple line of text) to access some sites - our own included. We have the need for a robust captcha system for people creating accounts in order to reduce the number of fake accounts being created by a bot.]
Read more of this story at SoylentNews.
18:22
Elon Musks Twitter Widens Its Censorship of Modis Critics Lifeboat News: The Blog

Two months ago, Musk said he was too busy to look into his companys role in mass censorship in India. Its only gotten worse.
18:21
IRC Proceedings: Thursday, March 30, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-300323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-300323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-300323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-300323.gmi
Over HTTP:
|
... |
18:00
Medieval Living: How Did Medieval Peasants Light Their Homes? Terra Forming Terra
Nasty Pesticide Broken Down by Probiotic Used In Culturing Food Terra Forming Terra

I do think we will simply get there. It is a lot of reseach, but it is still been done.


Deadly weed may actually help us look younger, heal faster Terra Forming Terra
All plants need to be tested rigorously in order to observe their talents. We all know this plant and many like it which none of us ever consume.
Weight-loss injectable could replace bariatric surgery knife Terra Forming Terra

This is as promising as it gets and we have collaterral impact as well. On the otger hand, the bar is pretty low here.
17:50
Announcing paid plans for Number tools catonmat.net
Team Browserling keeps shipping!
Last month we launched paid plans for Random Tools and today we're launching paid plans for our next most popular tool category Number Tools. Number tools are used by 45,000 people every month and they let you generate number sequences, convert numbers to words and words to numbers, sort, round, factor numbers, and much more.
Next, we're adding paid plans to all other online tools categories that we built and joining them into a single ultimate get things done website called OnlineTools.com, making it the top 100 website on the Internet.
From technical standpoint, we used HTML templates, Google SEO, and a $5 Linode instance to launch the paid plans. Checkmate, front-end developers and devops engineers.
You can still use all tools for free for a limited time but if you really like them, then you can get a subscription to support my team's work. See the pricing page for more information.
See you next time!
17:22
Links 31/03/2023: Ubuntu 23.04 Beta, Donald Trump Indicted, and Finlands NATO Bid Progresses Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Desktop/Laptop
-
ZDNet Thinking about switching to Linux? 6 things you need to know
Now is the perfect time to migrate to Linux. Heres why.
-
-
Audiocast...
-
16:29
Development Release: Lubuntu 23.04 Beta DistroWatch.com: News
Development Release: Lubuntu 23.04 Beta^Simon Quigley has announced the availability of the beta build of Lubuntu 23.04, code-named "Lunar Lobster": "Thanks to all the hard work from our contributors, Lubuntu 23.04 Beta has been released. With the codename Lunar Lobster, Lubuntu 23.04 will be the 24th release of....
16:03
New infosec products of the week: March 31, 2023 Help Net Security
Heres a look at the most interesting products from the past week, featuring releases from BreachLock, HackNotice, LOKKER, Nile, and Tausight. HackNotice Actions helps people to understand the extent of their data exposure HackNotice is offering additional tailored protection via its new service, HackNotice Actions. Further empowering employees, HackNotice Actions reaches out to any company where a persons PII or other data has been compromised, and asks for a full report on or erasure of More
The post New infosec products of the week: March 31, 2023 appeared first on Help Net Security.
16:00
Clever Test Rig Clarifies Capacitor Rules-of-Thumb Hackaday

If youve done any amount of electronic design work, youll be familiar with the need for decoupling capacitors. Sometimes a chips datasheet will tell you exactly what kind of caps to place where, but quite often youll have to rely on experience and rules of thumb. For example, you might have heard that you should put 100 F across the power supply pins and 100 nF close to each chip. But how close is close? And can that bigger cap really sit anywhere? [James Wilson] has been doing research to get some firm answers to those questions, and wrote down his findings in a fascinating blog post.
16:00
Overcoming obstacles to introduce zero-trust security in established systems Help Net Security
In this Help Net Security interview, Michal Cizek, CEO at GoodAccess, discusses the crucial balance between leveraging distributed resources and maintaining top-notch security measures. With the growing remote work trend, Cizek highlights the importance of implementing a zero-trust security model, emphasizing the complexities and challenges of such an endeavor. How can organizations make the most of distributed IT resources while simultaneously keeping them secure? It has become a standard that an organization runs only a More
The post Overcoming obstacles to introduce zero-trust security in established systems appeared first on Help Net Security.
15:51
Sundry Files - 274,461 breached accounts Have I Been Pwned latest breaches
In January 2022, the now defunct file upload service Sundry Files suffered a data breach that exposed 274k unique email addresses. The data also included usernames, IP addresses and passwords stored as salted SHA-256 hashes.
15:48
Stop Blaming the End User for Security Risk SoylentNews
Stop Blaming the End User for Security Risk:
It's common among cybersecurity professionals to point to the end user as a top area of risk in securing the organization. This is understandable. Systems and software are under our control, but users are unpredictable, that unruly variable that expands our threat surface to each geographically dispersed user, personal device, and all-too-human foibles and flaws.
Certainly, threat actors target our users quite successfully I'm not here to dismiss this obvious truth. But what is equally certain is this:We cannot train our way out of this problem. Enterprises pour significant investments into user security-awareness training, and still, they suffer embarrassing, costly breaches. So, focusing primarily on securing the end user isn't a sound strategy.
Fact: your users are a major risk factor. According to Verizon's "2022 Data Breach and Investigations Report," 35% of ransomware infections began with a phishing email. Fact: This is despite escalating investments in security-awareness training over many years. The cybersecurity awareness training market is projected to grow from $1,854.9 million in 2022 to $12,140 million by 2027. Fact: Even with all these investments, ransomware (just as one attack type) is also expected to grow aggressively, despite many organizational efforts, including training.
Sad, unavoidable fact: Our users are still going to make mistakes we're all human, after all. A survey conducted to prove the need for more security training, in my view, proved its inability to stop the cyber crisis: Four out of five surveyed had received security awareness training; between 26% and 44% (based on age demographic) continued to click on links and attachments from unknown senders anyway.
Read more of this story at SoylentNews.
15:30
The foundation of a holistic identity security strategy Help Net Security
Only 9% of organizations are taking an agile, holistic and mature approach to securing identities throughout their hybrid and multi-cloud environments, according to CyberArk. A critical path for cyber resilience The data-driven model identifies 9% of organizations as those with the most mature and holistic identity security strategies. These transformative organizations have a well-rounded focus on implementing identity security tools, are inherently agile and display a fail fast, learn faster characteristic even in times of More
The post The foundation of a holistic identity security strategy appeared first on Help Net Security.
15:00
Leveraging network automation to enhance network security Help Net Security
Data backups get a lot of attention, but sadly, sometimes, the operational work that keeps networks secure like device backups, upgrades, and configuration grooming goes undone. Recent high-profile network outages have brought attention to the importance of not just automating improvements in network security and operations but recovering quickly and minimizing downtime when disaster strikes. Its incredible that even today, the simplest configuration change or even a typo can sometimes cause a ripple More
The post Leveraging network automation to enhance network security appeared first on Help Net Security.
14:30
Cloud diversification brings complex data management challenges Help Net Security
As IT infrastructure becomes more diverse, organizations face the challenge of integrating data management and control, according to Nutanix. The research showed that the majority of IT teams leverage more than one IT infrastructure, a trend thats expected to intensify in the future, but struggle with visibility of data across environments with only 40% reporting complete visibility into where their data resides. A hybrid multicloud support In the coming years, there will be hundreds of More
The post Cloud diversification brings complex data management challenges appeared first on Help Net Security.
14:22
Allies or enemies of cancer: The dual fate of neutrophils Lifeboat News: The Blog
Why do cancer immunotherapies work so extraordinarily well in a minority of patients, but fail in so many others? By analyzing the role of neutrophils, immune cells whose presence usually signals treatment failure, scientists from the University of Geneva (UNIGE), from Harvard Medical School, and from Ludwig Cancer Center have discovered that there is not just one type of neutrophil, but several. Depending on certain markers on their surface, these cells can either promote the growth of tumors, or fight them and ensure the success of a treatment. By boosting the appropriate factors, neutrophils could become great agents of anti-tumor immunity and reinforce the effects of current immunotherapies. These results have been published in the journal Cell.
Immunotherapy involves activating immune cells mainly T cellsto recognize and destroy cancer cells. While this treatment is very efficient for some patients, and sometimes even exceeds expectations, it is unfortunately not the case in most cases. The reasons for these failures remain largely unknown, says Mikal Pittet, full professor at the UNIGE Faculty of Medicine, holder of the ISREC chair in immuno-oncology, director of the Centre for Translational Research in Onco-Hematology and member of the Ludwig Cancer Center, who directed this work. This is why deciphering the immune components involved is key to develop more advanced treatments and make immunotherapies a real therapeutic revolution.
Neutrophils are the most abundant immune cells in the blood and are very useful in infections or injuries by being quickly mobilized to the affected area and releasing antimicrobial factors. In the context of cancer, however, their presence is generally bad news as they promote vascularization and tumor progression.
14:22
Study indicates interleukin-6-dependant pathway dysregulation as a key druggable feature of COVID-19 Lifeboat News: The Blog
In a recent study on the medRxiv preprint server, researchers identified an interleukin 6 (IL-6) dependent alternative pathway as a therapeutic strategy against coronavirus disease 2019 (COVID-19).
Study: A Complement Atlas identifies interleukin 6 dependent alternative pathway dysregulation as a key druggable feature of COVID-19. Image Credit: MarynaOlyak/Shutterstock.com
14:22
Humans to attain immortality by 2029? Ex-Google scientist makes striking claim Lifeboat News: The Blog
You wont live forever is a catchphrase which has often been touted and has so far remained the proven truth of life of humans and almost every other living being on planet earth. But soon, this catchphrase may well become the truth of the past, as humanity steps forward to attain immortality.
A former Google scientist has made a prediction, which if proven right, may redefine human civilisation as we know it. Ray Kurzweil, whose over 85 per cent of 147 predictions have been proven right, has predicted that humans will become immortal by 2029.
The revelation came when the 75-year-old computer scientist dwelled upon genetics, nanotechnology, robotics and more in a YouTube video posted by channel Adagio.
14:22
Increased use of telehealth services, medications during pandemic associated with reduced risk for fatal overdose Lifeboat News: The Blog
The expanded availability of opioid use disorder-related telehealth services and medications during the COVID-19 pandemic was associated with a lowered likelihood of fatal drug overdose among Medicare beneficiaries, according to a new study.
The results of this study add to the growing research documenting the benefits of expanding the use of telehealth services for people with opioid use disorder, as well as the need to improve retention and access to medication treatment for opioid use disorder, said lead author Christopher M. Jones, PharmD, DrPH, director of the National Center for Injury Prevention and Control, Centers for Disease Control and Prevention. The findings from this collaborative study also highlight the importance of working across agencies to identify successful strategies to address and get ahead of the constantly evolving overdose crisis.
Published today in JAMA Psychiatry, this study is a collaborative research effort led by researchers at the National Center for Injury Prevention and Control, a part of CDC; the Office of the Administrator and the Center for Clinical Standards and Quality, both part of the Centers for Medicare & Medicaid Services (CMS); and the National Institute on Drug Abuse, a part of the National Institutes of Health.
14:00
OSC&R open software supply chain attack framework now on GitHub Help Net Security
OSC&R (Open Software Supply Chain Attack Reference) is an open framework for understanding and evaluating software supply chain security threats. It has received the endorsement of former U.S. NSA Director Admiral Mike Rogers, and is now available on GitHub. Spearheaded by OX Security, OSC&R is a MITRE-like framework designed to provide a common language and structure for understanding and analyzing the tactics, techniques, and procedures (TTPs) used by adversaries to compromise the security of software More
The post OSC&R open software supply chain attack framework now on GitHub appeared first on Help Net Security.
13:30
Intruder unveils API scanning to help organizations reduce exposure Help Net Security
Intruder updates its cloud-based vulnerability management service, allowing organisations of all sizes to secure their APIs by automatically detecting vulnerabilities, gaps, security weaknesses, and misconfigurations that hackers can exploit. As more organisations build APIs to facilitate automation, attack surfaces are expanding, making it crucial for organisations to include them under their security operations. Intruders latest capability automatically scans every API, providing organisations with detailed insights that they can use to proactively reduce exposure whether More
The post Intruder unveils API scanning to help organizations reduce exposure appeared first on Help Net Security.
13:20
AttackIQ Ready! gives security teams a clear portrait of their security program performance Help Net Security
AttackIQ launched AttackIQ Ready!, a fully managed breach and attack simulation service that leverages years of advanced content and actionable reporting to improve organizations security posture and security program performance. The service was designed to simplify the execution of a continuous security validation program, showing results in real-time and orchestrating faster remediation all through one automated platform for everyone who wants it. Absent real data, teams lack clarity about their capabilities and performance More
The post AttackIQ Ready! gives security teams a clear portrait of their security program performance appeared first on Help Net Security.
13:15
ReasonLabs Dark Web Monitoring identifies malicious online activity Help Net Security
ReasonLabs has launched a Dark Web Monitoring feature to its RAV Online Security solution, a web extension that provides real-time, 24/7 protection against a range of malicious online activity. The Dark Web Monitoring feature scans tens of thousands of combination lists, leaked databases, and malware data hidden from the surface netthe publicly accessible internetfor mentions of users personal data, and instantly notifies users when breaches occur. The dark web, a part of the internet that More
The post ReasonLabs Dark Web Monitoring identifies malicious online activity appeared first on Help Net Security.
13:03
Twitter Obtains Subpoena Forcing GitHub to Unmask Source-Code Leaker SoylentNews
Ars Technica is reporting that Twitter has convinced a judge to issue a subpoena to Github, requiring them to provide all personal details in their possession of a user called "FreeSpeechEnthusiast".
Twitter has obtained a subpoena compelling GitHub to provide identifying information on a user who posted portions of Twitter's source code.
Twitter on Friday asked the US District Court for the Northern District of California to issue a subpoena to GitHub. A court clerk signed off on the subpoena [PDF] yesterday.
GitHub user "FreeSpeechEnthusiast" posted Twitter source code in early January, shortly after Elon Musk bought Twitter and laid off thousands of workers. Twitter reportedly suspects the code leaker is one of its many ex-employees.
GitHub removed the code repository on Friday shortly after Twitter filed a DMCA (Digital Millennium Copyright Act) takedown notice. Twitter's takedown notice also requested identifying information on FreeSpeechEnthusiast, but GitHub didn't provide those details to Twitter immediately.
With the subpoena now issued, GitHub has until April 3 to provide all identifying information, "including the name(s), address(es), telephone number(s), email address(es), social media profile data, and IP address(es), for the user(s) associated with" the FreeSpeechEnthusiast account. GitHub was also ordered to provide the same type of information on any "users who posted, uploaded, downloaded or modified the data" at the code repository posted by FreeSpeechEnthusiast.
Read more of this story at SoylentNews.
12:40
Translating the Lies of Antnio Campinos (EPO) Techrights
Summary: Antnio Campinos has read a lousy script full of holes and some of the more notorious EPO talking points; we respond below
THE Benot Battistelli era did not truly end. Another terrible liar, whose English isnt that good (their native tongue is French), said the above. Our remarks below, preceded by timestamps:
0:06: Yes, Tony, global uncertainty like tactical nukes being deployed to Belarus, which you at the EPO funded. When the general public found out that the EPO had worked with and paid Belarus you just started shouting out the F word at staff! Like a true grown-up
0:11: Tell us more about inventors, Tony. What did you invent?
0:17: A record number of applications when you openly advertise lenience and expansion of scope, e.g. Hey Hi (AI, software patents in new clothing)
0:25: Up 2.5% after a year of lockdowns
0:30: I count Europe (a continent) like a country to make it sound good when only 1 in 3 applications in the European Patent Office is in fact European (in origin)
0:35: Growth in requests for monopolies (inside and across Europe) comes from outside Europe, so the European Patent Office is increasingly granting European monopolies to firms that are not European
0:43 I measure growth in China in terms of %, year-to-year, because in relative terms (relative to the whole) not many patent applications come from China
0:50: I cannot tell the difference between patents (monopolies) and inventions, but I never invented anything, so I just read this script regardless
1:00: At 50 (not yet!) I celebrate tremendous growth when the number of employees is in fact decreasing, as does the calibre
1:11: I compare the present to the early 1970s to make it seem like an incredible growth (national patent offices had existed already and there was no EU)
1:20: I dont say software patents, I just use some other words
1:30: I say double-digit growth when measuring only how many monopolies the EPO granted (lenience, pressure on examiners to meet quotas and targets), nothing economic and nothing to do with national patent offices, foreign patent offices etc.
1:37: This is 1contradicted by what Campinos said earlier because over time fewer and fewer patent applicants (relative to...
12:38
Leaked Reality - 114,907 breached accounts Have I Been Pwned latest breaches
In January 2022, the now defunct uncensored video website Leaked Reality suffered a data breach that exposed 115k unique email addresses. The data also included usernames, IP addresses and passwords stored as either MD5 or phpass hashes.
12:23
Professor Brian Cox Proves That Time Travel Is Possible With This Amazing Experiment Lifeboat News: The Blog

Physics-Astronomy: Home of the best science(focusing physics, astronomy) and technology news since 2012. Keep up with the latest news via email or social media. We are curious about the Universe, are you?
11:35
[Meme] Too Many Fake European Patents? So Start Fake European Courts for Patents. Techrights
EPO going down the toilet in pursuit of short-term profits
Summary: Antnio Campinos, who sent EPO money to Belarus, insists that the EPO is doing well; nothing could be further from the truth and EPO corruption is actively threatening the EU (or its legitimacy)
11:17
Thomas Magenheim-Hrmann in RedaktionsNetzwerk Deutschland About Declining Quality and Declining Validity of European Patents (for EPO and Illegal Kangaroo Courts) Techrights
Summary: Companies are not celebrating the production line culture fostered by EPO management, which is neither qualified for the job nor wants to adhere to the law (it's intentionally inflating a bubble)
Days ago the EPO delivered its annual results propaganda and released a video of a figurine-like Antnio Campinos talking to the camera (clearly not qualified for this job), telling a bunch of lies like Benot Battistelli used to do, misusing statistics to promote European software patents (typical buzzwords) and pretend the EPO had been doing well. The propaganda was of course propagated instantly to patent extremists platforms like Watchtroll and JUVE. However, some in German media [1, 2] are more sceptical, so the EPOs staff union retained copied of the printed versions and moreover released translations of an article published by Thomas Magenheim-Hrmann 3 days ago. His articles about the EPO go a long way back (hes no stranger to the issues) and his latest was translated as follows into English (there are other languages):
RND RedaktionsNetzwerk Deutschland
Corporations voice sharp criticism
Quarrel about the European Patent Office: Is examination becoming increasingly lax?
The authority puts mass before class and...
11:00
HPR3825: Creating a natural aquarium Hacker Public Radio
An alternative method to the big box store way of setting up an aquarium. You don't need a bunch of equipment, chemicals, or experience to have a balanced thriving aquarium that not only runs itself after a period of time, but is a healthier environment for your aquatic creatures and will be a great conversation piece. Learn how to emulate nature so that everything works together in its own ecosystem from the bottom up. Only a little bit of patience is needed.
Inverse Relationship Between Bugs and Patches It Will Never Work in Theory
How easily can you spot the difference between code that introduces bugs and code that fixes them? Given the explosion of interest in AI-based code generators over the last few months, an equally important question is now, "How well can machines tell the two apart?"
To answer that question, the authors of this recent paper applied clustering methods to both bug fixes and bug patches and found that most are similar enough to be clustered togetheri.e., they are superficially indistinguishable. What's more, they found that code mutation tools (used to generate buggy code for testing) and automatic program repair tools (used to generate fixes for bugs) can often be used interchangeably if trained on each other's data. That's good news for researchersit's always a bit of a thrill to realize that two ideas or approaches can be unifiedbut probably a sign that useful AI-based coding assistants are going to require more (and more careful) training than their giddier advocates expect.
Jinhan Kim, Jongchan Park, and Shin Yoo. The inversive relationship between bugs and patches: an empirical study. 2023. arXiv:2303.00303.
Software bugs pose an ever-present concern for developers, and patching such bugs requires a considerable amount of costs through complex operations. In contrast, introducing bugs can be an effortless job, in that even a simple mutation can easily break the Program Under Test (PUT). Existing research has considered these two opposed activities largely separately, either trying to automatically generate realistic patches to help developers, or to find realistic bugs to simulate and prevent future defects. Despite the fundamental differences between them, however, we hypothesise that they do not syntactically differ from each other when considered simply as code changes. To examine this assumption systematically, we investigate the relationship between patches and buggy commits, both generated manually and automatically, using a clustering and pattern analysis. A large scale empirical evaluation reveals that up to 70% of patches and faults can be clustered together based on the similarity between their lexical patterns; further, 44% of the code changes can be abstracted into the identical change patterns. Moreover, we investigate whether code mutation tools can be used as Automated Program Repair (APR) tools, and APR tools as code mutation tools. In both cases, the inverted use of mutation and APR tools can perform surprisingly well, or even better, when compared to their original, intended uses. For example, 89% of patches found by SequenceR, a deep learning based APR tool, can also be found by its inversion, i.e., a model trained with faults and not patches. Similarly, real fault coupling study of mutants...
10:52
Digital Rights Updates with EFFector 35.4 Deeplinks
We've got you covered with a collection of updates on your
digital rights! Version 35, issue 4 of our EFFector newsletter is
out now. Catch up on the latest EFF news by reading our newsletter or
work mapping surveillance towers along the U.S.-Mexico border, our
fight to protect the right of incarcerated people to receive
physical mail, and much more.
EFFECTOR 35.4 - We're
Fighting For Your Rights In Court, In Congress, and In Your
Car
Make sure you never miss an issue by signing up by email to receive EFFector as soon as it's posted! Since 1990 EFF has published EFFector to help keep readers on the bleeding edge of their digital rights. We know that the intersection of technology, civil liberties, human rights, and the law can be complicated, so EFFector is a great way to stay on top of things. The newsletter is chock full of links to updates, announcements, blog posts, and other stories to help keep readersand listenersup to date on the movement to protect online privacy and free expression.
Thank you to the supporters around the world who make our work possible! If you're not a member yet, join EFF today to help us fight for a brighter digital future.
10:35
Certa collaborates with ID-Pal to simplify third-party onboarding Help Net Security
Certa, has unveiled its official partnership with ID-Pal. Using a blend of biometric, document, and database checks, ID-Pals solution will enable Certa customers to verify the identity of third-party contacts in real time, all seamlessly integrated and orchestrated into a clients workflow. Our mission has always been to help businesses onboard customers, suppliers, sellers, partners, etc., quickly, effectively, and with transparency at every step, said Jag Lamba, CEO of Certa. Through our partnership with ID-Pal, More
The post Certa collaborates with ID-Pal to simplify third-party onboarding appeared first on Help Net Security.
10:31
Links 30/03/2023: HowTos and Political News Techrights
![]()
Contents
- GNU/Linux
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Applications
-
Medevel 13 Best Open Source Free PDF OCR Text Extractors
PDF file formats are a compact format widely used to create portable documents, reports, e-books, and more. Originally developed by Adobe in 1992, it has become a world standard.
-
nixCraft nvtop Awesome Linux task monitor for NVIDIA, AMD & Intel GPUs
-
-
Instructionals/Technical
-
FOSSLinux A beginners guide to installing and using Tilda Terminal on Ubuntu
Tired of navigating your Ubuntu terminal through multiple windows? Tilda Terminal is here to help. Our beginners guide will take you through the easy installation process and show you how to use Tilda Terminal for seaml...
-
-
10:21
TSMC May Not Expand in US If Double Taxation Rule Continues SoylentNews
TSMC may not expand in US if double taxation rule continues:
As Apple's major chip manufacturer TSMC nears the opening of its Arizona plant, US officials want it to build more but US versus China politics are complicating matters.
Taiwanese company TSMC has already invested $40 billion in its new Arizona factory, which it says will open in 2024. But since the US does not have a income tax agreement with Taiwan, TSMC faces double taxation on its profits from this or any other factory it could build in the States.
According to the Financial Times, unless there is a change in the law, TSMC will be paying out over 50% of its profits earned in the US. In comparison, Samsung pays much less because its home country of South Korea has a tax treaty with the States.
Naturally, then, US politicians who want to see the firm expand in the States argue that President Biden should negotiate a tax accord with Taiwan. TSMC officials have reportedly also asked for such an agreement to ease this double taxation burden.
However, at present the US does not recognize Taiwan as a separate country or sovereign nation. Instead, it sees it as part of China.
Read more of this story at SoylentNews.
09:36
A Muon Collider? Not Even Wrong
The US particle physics community has been going through a multi-year process designed to lead up this fall to a 10 year strategic plan to be presented to the DOE and the NSF. In particular, this will generate a prioritized list of what projects to fund over this period. The process began with the Snowmass self-study, concluded last year, and available here. Since last fall there have been two independent efforts going on:
- A National Academies study has been holding meetings, materials available here.
- A P5 (Particle Physics Project Prioritization Panel) is holding meetings, see here, and planning for a report to NSF and DOE by October.
Looking through all the materials relevant to particle theory, there seems to me little acknowledgement of the serious problems faced by the subject, or any new ideas for how to address these problems. Most of the effort though is devoted to where most of the money will be spent, on the experimental side. To a large degree, for the short-term its clear where funding has to go (to continue supporting the LHC into the HL-LHC era, and finish building the DUNE/LBNF US neutrino project). The longer-term is however very uncertain, as it is unclear whether theres a viable energy-frontier project that could study higher energies than those accessible at the LHC.
Last week EPP2024 and P5 held Town Hall events at Fermilab, see here and here. Theres video of the EPP2024 event here. On the question of the long-term future, one issue that is getting a lot of attention is that of whether to prioritize development of a possible muon collider. In this presentation a young physicist gives a future timeline including their likely retirement and death dates, showing that a muon collider is their only hope for new energy frontier physics during their lifetime. For those of my age the situation is a bit different, since even a muon collider is not going to do the job. At the EPP2024 event (3:28 in the video) Nima Arkani-Hamed makes the case that:
I think the subject has not been so exciting for many, many decades, and at the same time our ability to experimentally address and solidly settle some of these very big questions has never been more uncertain. I dont think its a normal time, its an inflection point in the history of the development of our subject, and it requires urgency The confluence...
09:01
Via: New York Post: The vote sets the stage for the first ever criminal prosecution of a former US president. The Manhattan grand jury hearing evidence in the Stormy Daniels hush money investigation on Thursday voted to indict the former president, two sources with knowledge of the case told The Post.
08:19
Irssi SA-2023-03 / Use after free in printing routine Open Source Security
Posted by Ailin Nemui on Mar 30
Hi,The issue has been reported to us by ednash, who were experiencing
frequent crashes of their Irssi. With the release of GLib 2.77, the
slice memory allocator that was previously obscuring this memory issue
was removed, thus making it much easier to trip.
When Irssi prints a message while another message is being printed, the
list that keeps track of Irssi variables for use in statusbar/message
patterns is not correctly cleaned up, leading...
08:16
Re: Re: sox: patches for old vulnerabilities Open Source Security
Posted by Steffen Nurpmeso on Mar 30
Steffen Nurpmeso wrote in<20230314201652.RlbWr%steffen () sdaoden eu>:
...
||Helmut Grohne wrote in
|| <20230314110138.GA1192267 () subdivi de>:
|||On Fri, Feb 03, 2023 at 09:44:47PM +0100, Helmut Grohne wrote:
|||> * CVE-2021-33844
|||
|||The original fix for this issue would cause a regression. After applying
|||it, sox would be unable to decode WAV GSM files. This has been reported
...
Today i got a nice email from...
08:01
Super FabriXss vulnerability in Microsoft Azure SFX could lead to RCE Security Affairs
Researchers shared details about a flaw, dubbed Super FabriXss, in Azure Service Fabric Explorer (SFX) that could lead to unauthenticated remote code execution.
Researchers from Orca Security shared details about a new vulnerability, dubbed Super FabriXss (CVE-2023-23383 CVSS score: 8.2), in Azure. The experts demonstrated how to escalate a reflected XSS vulnerability in Azure Service Fabric Explorer to an unauthenticated Remote Code Execution.
The researchers explained that they have abused the metrics tab and enabled a specific option in the console the Cluster Type toggle.
The name Super FabriXss comes from the FabriXss flaw (CVE-2022-35829, CVSS score: 6.2) that was addressed by Microsoft in October 2022.
The Super FabriXss vulnerability enables remote attackers to leverage an XSS vulnerability to achieve remote code execution on a container hosted on a Service Fabric node without the need for authentication. reads the analysis published by Orca Security. What started initially as a discovery of an XSS vulnerability that allowed a malicious script to be reflected off a web application, ended up being a full remote code execution (RCE) vulnerability after clicking on a crafted malicious URL and toggling the Cluster Event Type setting under the Events tab.
The researchers demonstrated how to exploit the vulnerability in Azure Service Fabric Explorer by sending a crafted URL to any Azure Service Fabric user. The experts discovered that is possible to embed an iframe in a vulnerable Node Name parameter in the users context. The iframe is used to retrieve remote files from a server, eventually leading to the execution of a malicious PowerShell reverse shell.
This attack chain can ultimately result in remote code execution on the container which is deployed to the cluster, potentially allowing an attacker to take control of critical systems. continues the report.
Unlike FabriXxs, the SuperFabriXxs issue only exists in the Windows Cluster, but it can be used in code execution attacks on a large scale.
The attack is composed of two main phases:
1. Once the iframe is embedded and the fetch request is triggered, the attackers code takes advantage of the upgrade process to overwrite the existing deployment with a new, malicious one. This new deployment includes a CMD instruction in its Dockerfile that w...
07:47
IRS tax forms W-9 email scam drops Emotet malware HackRead | Latest Cybersecurity and Hacking News Site
By Waqas
Researchers have warned users to be on alert, as the IRS never sends emails to confirm taxpayers' personal information.
This is a post from HackRead.com Read the original post: IRS tax forms W-9 email scam drops Emotet malware
07:41
Newly Declassified Government Report Suggests Havana Syndrome Might be Caused by an Energy Weapon SoylentNews
Newly Declassified Government Report Suggests Havana Syndrome Might Be Caused by an Energy Weapon:
After years of debate about the cause of the strange malady, a recently declassified document points the finger (once again) at "electromagnetic energy."
Several weeks after the intelligence community came out to disavow claims that "Havana Syndrome"the bizarre rash of neurological disorders plaguing U.S. foreign service officerswas the result of a directed energy weapon, a newly declassified report alleges that may very well be what it is.
The group behind the report, the Intelligence Community Experts Panel on Anomalous Health Incidents (AHIs), was established by the government to figure out just what the heck had happened to the 1,000-ish American officials who claim to have suffered from "Havana"'s bizarre symptoms. Those symptoms, which first cropped up at a U.S. embassy in Cuba in 2016 and soon spread to other parts of the globe, include a rash of inexplicable ailmentsthings like hearing and memory loss, severe headaches, light sensitivity, nausea, and a host of other debilitating issues.
Well, after a substantial research effort to get to the bottom of Havana Syndrome's seemingly impenetrable mystery, the IC panel ultimately released their findings to the government, but the contents of the report have remained classifieduntil now, that is.
[...] According to the report, a plausible explanation for the disorders may be "pulsed electromagnetic energy." It reads:
Electromagnetic energy, particularly pulsed signals in the radio frequency range, plausibly explains the core characteristics, although information gaps exist. There are several plausible pathways involving forms of electromagnetic energy, each with its own requirements, limitations, and unknowns. For all the pathways, sources exist that could generate the required stimuli, are concealable, and have moderate power requirements.
Read more of this story at SoylentNews.
07:38
888 New Zealand Casino Log In h+ Media
888 New Zealand Casino Log In
888 Casino jackpot is totally different for each game and ranges from the 1000s to the tens of millions. These pokies offer multi-media rich performance and are cornering the ground in popular on-line casinos. With autoplay performance, free spins, bonus rounds, and extra, you can see that progressive-themed pokies offer good payouts and are a ton of fun for anyone who loves enjoying the pokies.
These manufacturers go hand in hand with the on line casino and can all be accessed from the main web web page of the 888 Casino. All payouts are processed after a forty eight hour pending period, during which they can be reversed. Again, if youre not acquainted with the codecs of those competitions than there is no need to worry as 888 give you guides to get started on these too. Without additional ado, lets take a dive into the world of 888 and see whats on supply for the players who opt for their service. We at NZ Casino are additionally committed to the subject and have an allotted page for Responsible Gambling.
- Thus, I extremely advocate that 888casino work on the cell apps navigation.
- The most a truth in the on-line traditional casino world will be Range Riches through the producer Barcrest and the Cleopatra on-line slot machine sport from IGT.
- A good Skrill on line casino is conscious of that the safety of your gamers is a precedence and solely from this level should think about the remaining areas.
- All you have to do is observe via their simple and fast registration process and get ready to spin.
- Thats why we have been so happy to see that this web site applies SSL encryptions to all deposits and withdrawals, preserving your financial and private particulars safe.
- Both Android and iOS customers will be in a position to use the app to get complete access to 888 Casino.
The progressive and unique casino options out there at 888Starz make this casino stand out from its competition. Ranging from super-fast payouts to extremely safe banking solutions, were sure 888Starz is not going to disappoint. Kiwis can enjoy a large assortment of reside supplier video games powered by over 15 different recreation suppliers.
You can use Interac, Instant Banking, bank cards or iDebit to get dollars into your account. Another fine banking technique possibility for deposit and withdrawal is PaysafeCard. 888 took a bit of time onboarding Interac, but from the beginning of 2023 theyve allowed Interac transactions. 888 on-line on line casino provides plenty of completely different sort of on-line on line casino video games together with online slots. 888 on line casino slot video games selection is correct there with the best slots casinos like LuckyDays and Voodoo Dreams. In addition to their very own unique slots, you can play basic slots and jackpot slots like Mega Moolah.
If youre a newbie on the looko...
07:36
Sabong Slots Casino Sabong888, g188 Phsabong Slots Casino Sabong888, Sabong Sabong 2018 Gcash Login, g188phsabong Slots Casino Sabong888, Sabong Sabong 2018 Gcash Login,1e h+ Media
Sabong Slots Casino Sabong888, g188 Ph sabong
Slots Casino Sabong888, Sabong Sabong 2018 Gcash Login,
g188ph
sabong
Slots Casino Sabong888, Sabong Sabong 2018 Gcash Login,
g188ph sabong
Slots Casino Sabong888, Sabong Sabong 2018 Gcash Login,1e
sabong
Slots Casino Sabong888, Sabong Sabong 2018 Gcash Login,1e
A live on line casino is on offer as properly, with reside sellers dealing the games for the net viewers. Pretty much every type of on line casino game is out there at 888 Casino, allowing them to maintain up their standing as one of the business leaders. This is after all capped by their major presence within the on-line poker and sports activities betting arenas, for which they provide very powerful platforms as nicely. One of the primary options of any on-line on line casino is the welcome bonus available for model spanking new players.
Visit the 888 3D Casino the place youll have the flexibility to costume up a non-public icon as your self and play on-line three-dimensional video games. Unfortunately, 888 Casino isnt presently on the market to our PA gamers proper now. The app is easy to make use of and features an array of account administration options. The web-based cell casino web site is true for fast gaming periods, which additionally permits you to make deposits, withdrawals, declare bonuses, and even enroll.
- It consists of self-help tools on tips on how to best handle your online gaming experience.
- $4 added to your bankroll for on-line casino and on-line poker video games.
- You perhaps nonetheless wont win 1,000,000 dollars in a single spin here, nevertheless nailing the first prize ought to nonetheless net you no much less than $200,000.
- 888 cell on line casino provides you the prospect to play anytime you need from anywhere you want, so you probably can always win huge when youve an web connection.
- For 888 withdrawal, you have to go to the primary foyer simply as youll when making a deposit.
However, theres a commission for deposit and cashout transfers to and out of your Upaycard. Reef Club abides by the rules of accountable gambling in all international locations where it operates and offers a series of self-exclusion instruments. A little more than a 39 payment strategies can be found, and these usually consist of MasterCard, Neteller, PayPal. The design of the Reef Club on-line casino didnt use too many visuals and the page parts have been saved easy.
The sleek design of the mobile lobby and tables is much like the one found on desktop computers, though the customization options arent as rich. A good touch to the gaming platform is that users can still opt for practice play if they want and thus use the demo credits to play poker with real opponents. When it involves ce...
07:36
888 Casino Nz Evaluation Exclusive 100% Welcome Bonus h+ Media
888 Casino Nz Evaluation Exclusive 100% Welcome Bonus
Most of the video games could be performed free of charge in practise mode, which is great for gamers wanting good their strategy or test out the model new features. While this on-line on line casino platform is understood for its longevity and games which have stood the test of time, its glorious bonus and promotions are another major perk that makes it stand out. 888 Casino NZ offers gamers commendable bonuses that assist them improve their chances of winning with out having to spend greater than they want to. These bonuses include match cash, free spins, and amazing presents that payers can get without restriction.
888Casino has the top jackpot pokies out there including the Millionaire Genie slot game. This is probably one of the prime ranking pokies on the location, and all it takes is one spin to win big. A dedicated section of the lobby will current numerous tables and tournaments for gamers looking to enjoy the recreation with out utilizing actual cash in the process. Thanks to its very high site visitors numbers, the poker site on-line has numerous video games working all through the day. This is nice information for gamers from New Zealand because the peak hours are largely primarily based on European times.
You can use Interac, Instant Banking, credit cards or iDebit to get dollars into your account. Another nice banking technique option for deposit and withdrawal is PaysafeCard. 888 took a little bit of time onboarding Interac, however from the start of 2023 theyve allowed Interac transactions. 888 online on line casino provides loads of totally different kind of on-line casino video games along with on-line slots. 888 on line casino slot video games selection is correct there with the most effective slots casinos like LuckyDays and Voodoo Dreams. In addition to their very own exclusive slots, you possibly can play basic slots and jackpot slots like Mega Moolah.
So, at 888 you will have the right firewall and encryption feature ever made. The on line casino app is so light-weight, that your storage will hardly really feel it is there. The 888 Casino runs through the HTLM browser software program, so the app is synced to this and nothing else. In one month alone, a complete of $34 Million dollars was won by players inside. You missed out, however that is okay, it happens each month and now you know about it, well there isnt a excuse now why you did not be part of.
888 poker works slightly different to the relaxation of their service as primarily, the service is a downloadable client. Add this to your computer and you will gain entry to a plethora of various poker options which might be offered to their players by the team at 888 on line casino. Maybe these much less conventional styles might quickly flip into your all-time favourite earlier than long. This is due to the fact that alongside their very own games you additionally get to...
07:33
Oryx Gaming Launches With 888 On Line Casino h+ Media
Oryx Gaming Launches With 888 On Line Casino
We only listing well reviewed high online casinos offering all attainable kinds of free spins. Free spins NZ is proud to be the #1 trusted platform for on line casino gamers in New Zealand whore in search of No Deposit Free Spins and far more. 888, based in 1997, are stalwarts of the net on line casino industry with fingers in many pies. 888casino is only one such finger protruding from the 888 holdings tart.
While 888 Casino doesnt maintain an infinite list of game titles they handle to supply a selection of various varieties of gaming action to accommodate the tastes of any player. Slots and progressive video games are unique to their website and titles similar to Super Thundering 888, 2 Times Extra Wild or Millionaire Genie offer gamers the potential to money in on hundreds of thousands. The site contains sports activities betting and bingo as well as many other desk games similar to blackjack, baccarat or roulette.
We recommend that you just be taught all about 888 casinos generous promotions before enjoying to have the ability to get the most bang for your buck. Is 888 reliable in phrases of providing you with entry to reliable cost brands? With every thing coated within the 888 Poker evaluation, we are ready to truthfully say that the poker site is doubtless certainly one of the prime selections, if not the perfect. The trendy software appears nice and works even better as gamers can simply browse a massive selection of poker games and stakes. Short descriptions are available within the assist part and there are additionally guides for making deposits. Everything is 100% safe and actual money funds are added to the account immediately once they have been processed.
Here you presumably can view top tables, refine video games by category and then enter the foyer to pick your most popular desk. Once in the sport you possibly can modify the view of the desk or use the chat operate to interact in actual time with the supplier and your table mates. 888 is a family name whether or not you have used the bingo website before otherwise youre simply aware of their glorious status for offering a fun experience, youve positively heard of them earlier than.
There are https://bet-xbahis.icu/jewel-of-the-jungle-slot/ quite a few checks, examinations, audits and RTP reports by third events to make certain that every thing is protected, legal and impartial. All of those 888 casino security measures are in place in order that gamers enjoy a safe and reliable gaming setting. Players can contact pleasant, skilled, prepared agents by using e-mail, cellular phone, and settle chat. Very nicely because the exceptional slot choice, Mr Bet supplies plenty of Video Holdem poker, Scratch Greeting card, Roulette, Sic Bo, Blackjack, Baccarat and other on-line games.
B...
07:31
Functional Programming: The Biggest Change Since We Killed the Goto? IEEE Spectrum

Transcript
Stephen Cass: Welcome to Fixing the Future, an IEEE Spectrum podcast. Im senior editor Stephen Cass, and this episode is brought to you by IEEE Explorer, your gateway to trusted engineering and technology research with nearly 6 million documents with research and abstracts. Today we are talking with Charles Scalfani, CTO of Panoramic Software, about how adopting functional programming could lead to cleaner and more maintainable code. Charles, welcome to Fixing the Future.
Charles Scalfani: Thank you.
Cass: So you recently wrote an expert feature for us that turned out to be incredibly popular with readers. That argued that we should be adopting this thing called functional programming. Can you briefly explain what that is?
Scalfani: Okay. Functional programming is an is basically, as it says, its basically based around functions. So where object oriented programming is has an object model, where its everything you see everything through the lens of an object, and the whole world is an object, and everything in that world is an object. In functional programming, its the similar, its you see everything as a function, and the whole world looks like everything in the world looks like a function. You solve all your problems with functions. The reason its older and wasnt adopted is because the ideas were there, the mathematics, the ideas, and everything were there, the hardware just couldnt keep up with it. So it became relegated to academia and the hardware just wasnt available to do all of the things. That has been, since probably the 90s, its been not a problem anymore.
Cass: So I just wanted to like, as somebody who is, I would call itself a kind of a very journeyman programmer. So one of the first things I learned when Im using a new language is usually the section says, how to define a function, and theres a little you know, everybodys got it, Pythons got it, you know, even some versions of Basic used to have it, C has it. So I think function here means something different to those functions Im used to in something like C or Python.
Scalfani: Yeah. I have a joke that I always say is that when I learned C, the first program I wrote was hello world. And when I learned Haskell, a functional programming language, the last thing I learned was hello world. And s...
07:29
CD Projekts Legal Pressure Pushes GOG-Games to The Dark Web TorrentFreak
 As the creator of The Witcher series and Cyberpunk
2077, game developer CD Projekt won the
hearts of millions of gamers.
As the creator of The Witcher series and Cyberpunk
2077, game developer CD Projekt won the
hearts of millions of gamers.
The Polish company also scored points when it spoke out against DRM on numerous occasions, including the FCKDRM campaign promoted by its game distribution service GOG.
The anti-DRM stance is laudable but also has its drawbacks. Most notably, it becomes much easier for pirates to copy and share games. And indeed, new GOG games were swiftly shared online, including on a site that even copied its name: GOG-Games.com.
CD Project likely anticipated that their games would be pirated, but seeing a site use its own brand to promote pirated games must have stung. As a result, the videogame company has worked hard to get GOG-Games offline.
GOG-Games Under Pressure
Earlier this week, those efforts appeared to pay off when GOG-Games replaced its game repository with a notice that signaled serious problems.
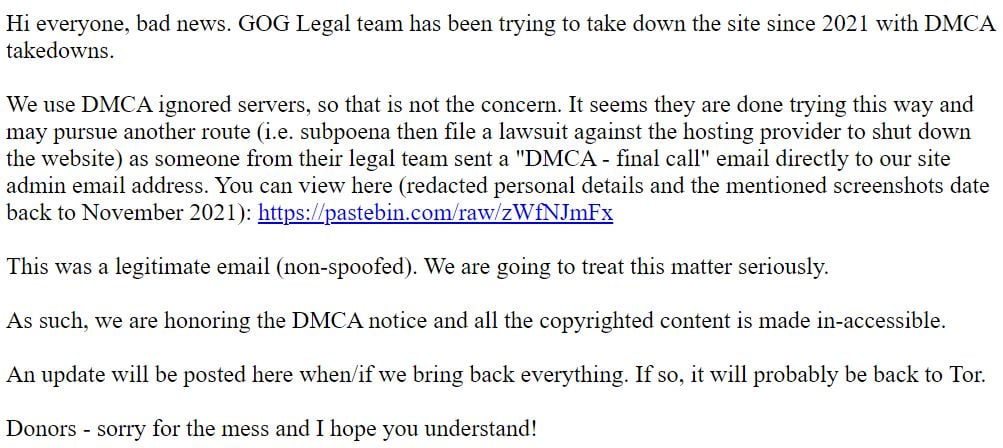
According to the operators, CD Projekts GOG team has been trying to take the site offline since 2011. Since GOG-Games uses a host that simply ignores DMCA notices, results have been limited, but more recently, the admin was contacted directly.
[S]omeone from their legal team sent a DMCA final call email directly to our site admin email address, the notice reveals.
The email in question wasnt directed at the operators of the site directly, but at the hosting company. It notes that GOG-Games violates GOGs copyrights and trademarks, urging the provider to take action.
The website is infringing GOGs word by using it to brand an unlawful operation of downloading both CD PROJEKT Groups and third parties games. The website also infringes CD PROJEKT S.A. trademarks and copyrights related to CD PROJEKT S.A games; The Witcher and Cyberpunk 2077.
We are extremely determined to take the above mentioned website down and we would like to ask you to treat the situation with utmost importance...
07:00
AMD CDX Bus Landing For Linux 6.4 To Interface Between APUs & FPGAs Phoronix
Since last year AMD-Xilinx has been posting Linux patches for enabling CDX as a new bus between application processors (APUs) and FPGAs. The AMD CDX bus is now poised for introduction in the upcoming Linux 6.4 cycle...
PyTorch Foundation: The First Six Months Linux.com

Read the original blog at Read More
The post PyTorch Foundation: The First Six Months appeared first on Linux.com.
05:52
Betway
Here is the listing of withdrawal choices for the Indian punters on Betway India. The creators present pleasant provides and promotions for users. Remember, theyre valid for every week and the minimal amount should be no much less than rupees 1,500.
These are secure, fast and easy-to-use strategies which are popular in India. Despite all the pros of Betway, we did find some drawbacks that were not too joyful about. The operators customer help is inadequate, although it has several useful articles and an FAQ section on its web site. The bonuses provided are also few, compared to some other gambling sites. We imagine Betway will do one thing to improve these drawbacks in the future.
However, if you have already got an account, enter your username and your password within the top proper corner of the page. You want first join the Free Bet Club program to get this kind of Betway bonus. With the primary deposit, youre supplied a one hundred pc bonus on the deposited quantity not exceeding $250. As for the wagering rules, the primary bonus is 100% of the deposit made. But not extra than $250, and wagering is done with a Wager of 50. During the wagering course of, you can not exceed the wager of $7.5, and one hundred pc of the quantity spent will solely count in the direction of the wagering when utilizing slots.
Betway presently holds licenses in regulated markets similar to Malta, the UK, Sweden, Denmark, Italy, Spain, Belgium, and Ireland. The Malta Gaming Authority and the New Jersey Gaming Commission regulate the operations of Betway out and in of the US. Other certificates include eCogra, Gambling Therapy, Gambling Commission, IMAS, and the International Betting Integrity Association. Kolkata Knight Riders skipper Dinesh Karthik grabbed a breathtaking working catch to dismiss Quinton De Kock during the match against Mumbai Indians at the
Luckily, Betway India has obtained several Indian fee options like UPI and Net Banking. Of course, you even have e-wallets like Neteller and Skrill. Players experiencing difficulties can contact buyer support by email on There is also a reside chat available, which may be accessed beneath fast links in your account. In the advisory, the govt. said on-line offshore betting platforms are now using information websites as a surrogate product to promote the betting platforms on digital media.
Jamieson, who was ruled out of the event as a outcome of an injury, was purchased by the franchise for INR 1 Crore. His alternative, Magala, has wealthy experience in the shortest format of the sport. Though he has played simply 4 T20Is for South Africa, Magala has a popularity for being a daily wicket-taker in home T20 video games through the years. He will join CSK at his base price of INR 50 Lakh, IPL stated in a press release. Magala, who has only participated in 4 T20 International matches for the Proteas, will sign on with the four-time IPL...
05:50
Betway Deposits
The record goes on and on, covering just about every top-flight soccer league throughout the globe. Football is arms down the most well-liked sport on the planet and has an enormous and dependable fan base in India. We cant say we had been stunned, though, given the operators robust connections with the UK sports activities sector. Minimum deposit necessities you must deposit 200+ to become eligible for the intro bonus. Please assist us defend Glassdoor by verifying that you would possibly be a real person.
You can see betting boosts, guess slip, and money out option easily. Its on line casino offers a powerful variety of games provided by Microgaming platform. It has roulette, jackpot, slots, poker, blackjack, desk games, retro slots, and more.
Betway presents digital sports betting, that are fast games to play. Horse racing is the commonest instance, but digital cricket betting can be accessible place a bet and find out the sports conclusion in minutes. However, to accelerate demand, Betway had to diversify their offering and create a sports activities betting app and one for casino games.
Betway is an external betting 1win indir website with no legally registered entity in India, as this isnt allowed. This is the query that seems to have extra answers than web pages. However, the confusion regarding Betways legality in India is understandable, given the Indian legal guidelines on playing. Yes, Betway is a protected and trusted web site that players can completely rely on. The given personal data similar to name, ID details should be actual and all payments have to be made underneath the same name. Although no phone contact number has been provided, you can attain Betway buyer help personnel by way of the official email ID ().
- Everything depends on your preferred cost methodology and whether or not it is accessible in your jurisdiction.
- Betway is amongst the greatest stay betting platforms in the world.
- Winnings can then be withdrawn back to the participants account or used to proceed enjoying.
- If you fulfill the wagering circumstances specified in the supplys Terms & Conditions, you shall be able to withdraw the bonus cash.
- Be it pre-game or in-game betting, Betway leads the way in which by offering probably the most aggressive odds in comparison with another bookmaker online.
Betway India, however, does not provide stay streaming choices which might appear as a disadvantage. Nevertheless, Betway provides lots of instruments like historical stats, stay updates, etc. so that punters have extra information earlier than inserting a bet. With so many reside betting options out there for Indian punters, our Betway scores are high. Punters can earn plus points by taking half in on any Betway product, or via particular presents or promotio...
05:47
Star Sports Activities Reside h+ Media
Star Sports Activities Reside
Information about the amount, high quality, purity, efficiency, price, and commonplace of goods or companies. Zurich , March 24 Narrated by Welsh actor and soccer fan Michael Sheen, Written in the Stars is the Official Film of the first FIFA World Cup to be held within the Middle East. Your account will mechanically be activated once your registration goes through. All you should ensure most safety and security on your account is to confirm it. Check the email handle you used for the site and see should you obtained a message from Betway.
Live betting choices abound, and the bookmaker supplies a diversified choice of disciplines in addition to a diverse roster. This method is essentially the most reliable and fastest of the options given on the bookmakers website. If you choose to withdraw funds using a financial institution card, you have to be aware of the deposit limitations and terms. For example, the presence of both a bookmaker and a casino, a profitable welcome bonus, in style payment strategies, the presence of an application, and so on. Indian gamers can legally deposit, play and withdraw cash on the Betway website.
Since this isnt the case with Betway, youll have the ability to wager all you want right here. Betway has a lot of sports video games you probably can guess on with great odds. They also have a Betway Boost, which is an offer that may increase the price of your odds and raise your winnings. Contact MethodResponse TimeEmail5 48hPhone1 30 minLive Chat30 sec forty minOne factor we might have beloved to see is immediate access to the customer service reside chat.
Also on the location offers sections of playing casino, slot machines. Betting company Betway has high-quality mobile apps on iOS and Android. It is probably certainly one of the few online betting websites designed fantastically for Indian players. Its features provide plenty of simplicity, making the betting expertise fairly straightforward.
The maximum is decided by the type of occasion, the recognition of the event, and the sort of wager. Generally, searching the sportsbook makes it straightforward to search out whatever you need. Depending on the popular mode of access, a bettor can scroll down the page utilizing the sidebar or search function to get what they can not find on the menu.
However, few cover the world cup, and those that do wont have good offerings concerning bonuses, payment methods, or buyer help. If youre on the lookout for high betting websites with lots of prizes and top-tier cricket offers, Betway will be your most suitable option. Everything from IPL to international matches is on the market right here. Betway India, one of the worlds largest bookmakers, is an experienced betting web site that launched its providers worldwide in 2006. It is a worldwide on-line gambling company, on which tens of millions of individuals bet on many spo...
05:46
Betway India Evaluation 2023 h+ Media
Betway India Evaluation 2023
From poker, roulette, video poker, blackjack, wheel of fortune,
8% of the amounts wagered will count in the direction of the
wagering. Finally, youll need to wager the bonus funds as per the
principles. Go to the website of Betway or open the cell app
utilizing your account, and log in.  Due to
giving the customers full proof safety, Betway has a signup process
that takes slightly too lengthy.
Due to
giving the customers full proof safety, Betway has a signup process
that takes slightly too lengthy.  There are many betting types of choices for the purchasers of
Betway.
There are many betting types of choices for the purchasers of
Betway.  Betway
has topped the line and is all the time prepared to help, the
customers can get help from customer care.
Betway
has topped the line and is all the time prepared to help, the
customers can get help from customer care.
Choose your date of birth, and enter your address, city, pin code, and state/region. Type in your e mail handle, and supply your phone number. In the top-right corner of the display screen, you must spot a green button that says Register.
Depositing & WIthdrawing money has been made ridiculously easy by Betway India. To deposit, all you have to do is the choose bank from the drop-down menu and locate the deposit button current. After that, enter the mandatory data and enter the quantity you would like to deposit for your gaming.
- You are truly spoilt for selection in phrases of fee choices here!
- Launched in 2006, the company operates across a quantity of regulated online markets and holds licences within the UK, Malta, Italy, Denmark, Spain, Belgium, Germany and Ireland.
- Look at the table beneath for additional details about Betway bonuses.
- Betway India values its prospects for often betting with them, and so to understand this, theyve created the Betway Plus loyalty program to reward its common punters.
- Betway virtual on line casino has been serving gambling enthusiasts since 2006.
- It presents you a one hundred pc matched bonus up to INR 4000, which will maintain the bettors going for some time of their journey.
The operator supplies a number of solutions and is a superb place to gamble on-line on sports, casino games, poker, esports, and horse racing. Put differently, the operator doesnt have distinct intro offers for sports activities punters and on line casino gamers. Furthermore, Betway, being some of the renowned betting websites on the earth, can also be in reside streaming. They have the broadcasting rights for a number of occasions which are streamed stay on their platform once in a while. Check out Funbet, which provides a match bonus of up to Rs.10,000 on sports betting. After youve created your Betway account, you will...
05:43
Betway Evaluation India 2023 h+ Media
Betway Evaluation India 2023
You can now play one of the best titles on the market in Betway casino. Old-school classics and modern fan-favourites like video poker are all on provide. In truth, the number of on line casino games here is absolutely mind-boggling. As quickly as you sit on one, youll be greeted by horny, skilled dealers who will do their greatest for you to enjoy. One of the best stay cricket satta ratesavailable in the meanwhile, Betway allows you to wager on any cricket match you possibly can think of.
- As for the cricket markets themselves, you will find any and every event possible for you to guess on.
- Without any doubt, Betway India is amongst the top betting websites in India the place you can go to and revel in a quality-filled betting expertise.
- With state-of-the-art know-how, youll get to work together with stay sellers.
- Overall, I advocate Betway, especially for these looking for non-typical betting experiences.
You can relaxation assured that youll be at the forefront of the newest on-line on line casino games with Betway casino. You can download their app from the Play Store or your App store. The download is fast, offered you have good internet connectivity. Customers who do not want to set up the app can continue using their website on their devices as their website is cell pleasant. We recommend customers to download the app as it is meant for cellular and tablet use.
Once credited, the guess have to be redeemed before 30 days of activation. You are allowed to apply your free bet bonus within the line and stay web site sections at any sport type obtainable. It has been working since 2006, and the number of offers it beholds makes it a world-renowned betting web site.
Depending on the tactic used, the withdrawal course of might take longer. Every yr, Betway introduces new features, improves the person experience, and raises the diploma of comfort when enjoying. As such, it may be inconceivable to level out a person whos received the most. Here are three sportsbook options to Betway that bettors may contemplate.
The knowledge offered to deposit and withdrawal is saved non-public and not shared with any third celebration. Once you turn into a Betway buyer, you have seven days to deposit the minimum amount by credit card or PayPal. In a situation the place you didnt tick the bonus checkbox when registering, youll find a way to activate the Betway bonus by way of help to get a solid start at Betway betting. Betway Free Bet Club presents you 500 Free Bets if you bet 500 on doubles or larger on any sport sort.
The on line casino app might be installed very quickly and you can enjoy a seamless mobile betting expertise. Loyalty programme is one division where Betway can undoubtedly step up its game. After all, players favor betting in an environment the place they are rewarded not solely with their winnings however with e...
05:39
The Future of Fintech Applications HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
This article explores the world of fintech applications, highlighting their most popular features now and in the next
This is a post from HackRead.com Read the original post: The Future of Fintech Applications
05:29
New AlienFox toolkit harvests credentials for tens of cloud services Security Affairs
AlienFox is a novel comprehensive toolset for harvesting credentials for multiple cloud service providers, SentinelLabs reported.
AlienFox is a new modular toolkit that allows threat actors to harvest credentials for multiple cloud service providers.
AlienFox is available for sale and is primarily distributed on Telegram in the form of source code archives. Some modules are available on GitHub allowing threat actors to customize their malicious code to suit their needs.
AlienFox allows its operators to harvest API keys and secrets from popular services including AWS SES & Microsoft Office 365.
SentinelLabs has identified a new toolkit dubbed AlienFox that attackers are using to compromise email and web hosting services. AlienFox is highly modular and evolves regularly. Most of the tools are open-source, meaning that actors can readily adapt and modify to suit their needs. Many developers take credit on different iterations of the tools. reads the report published by SentinelLabs. The evolution of recurring features suggests the developers are becoming increasingly sophisticated, with performance considerations at the forefront in more recent versions.
AlienFox targets misconfigured servers running popular web frameworks, including Laravel, Drupal, Joomla, Magento, Opencart, Prestashop, and WordPress. AlienFox collects lists of misconfigured cloud endpoints through security scanning platforms like LeakIX and SecurityTrails.
The malware is able to target secrets for popular cloud-based email platforms, including 1and1, AWS, Bluemail, Exotel, Google Workspace, Mailgun, Mandrill, Nexmo, Office365, OneSignal, Plivo, Sendgrid, Sendinblue, Sparkpostmail, Tokbox, Twilio, Zimbra, and Zoho.
The researchers analyzed AlienFox versions 2 through 4, which date from February 2022 onward.
The oldest variant of the toolset, Version 2 focuses primarily on extracting credentials from web server configuration or environment files. Version 3.x contained the first observed version of the script Lar.py, which allows automation of the extraction of keys and secrets from compromised Laravel .env files. Version 3.x logs the results to a text file along with the targeted server details.
05:00
Why Governments Involvement in Standards Development is Crucial IEEE Spectrum

With the rapid rate of technological advancements and evolution, coupled with urgent global challenges, the worlds need for technical standards has never been greater. Technology standards establish specifications and procedures designed to maximize the reliability of materials, products, methods, and services. In short, standards help increase the reliability and effectiveness of many of the goods and services people interact with daily.
Technical standards also play an important role as governmental bodies around the globe explore and establish policies and regulations to address challenges such as data governance, privacy, security, climate change, and the impact of rapid technological advances on citizens.
Global standards are critical instruments in areas such as innovation, trade, and public policy. But it can be challenging for government representatives to gain access to technical experts, best practices, and other resources needed to help them understand the standardization landscape and navigate issues that arise.
A complex system of standards bodies
One level of complexity governments face is that standards are developed by different types of organizations.
Standards bodies with a geographic designation generally are categorized as international, regional, or national, and they typically function under a nation-centric approach whereby governments, or groups closely coupled to governments, mandate standards.
Technical standards play an important role as governmental bodies explore and establish policies and regulations to address challenges such as data governance, privacy, security, and climate change.
There are also standards-developing bodies with a global technical or industry designation. They include state-independent standards-developing bodies, such as IEEE, with a globally open participation mode.
A program specific to governments
The IEEE Government Engagement Program on Standards helps agencies, commissions, ministries, and regulatory bodies better understand the standards development process. The program facilitates the global interoperability of devices and systems, provides a way to strengthen standards portfolios, and supports efforts to minimize redundant or conflicting standards.
Participation in IEEE GEPS is free, and there are no membership requirements. Participants have observer statu...
05:00
NVIDIA 525.105.17 Linux Driver Backports IBT Kernel Compatibility, Other Fixes Phoronix
While last week NVIDIA promoted their 530 Linux driver series to stable, for those using the prior NVIDIA 525 series production branch a new point release was issued today that backports several fixes...
DRAM Got Cheaper and Prices Will Continue to Fall SoylentNews
DRAM got cheaper and prices will continue to fall:
While prices for computer hardware have remained relatively high in the past few years, the slowing of PC and component sales are starting to take effect. DRAM is the latest piece of hardware to become even cheaper, and projections show that prices will continue to fall in the coming months.
According to a report from TrendForce, DRAM prices have fallen 20% in the first quarter of 2023. This is a continued decline for the DRAM market as sales have been slowing for all sectors of the industry. Some DRAM manufacturers have already started layoffs as they see their revenues on a steep decline. For the second quarter of 2023, TrendForce says that prices are expected to fall another 10 to 15%.
Despite production cuts already in effect, PC makers still have between 9 and 13 weeks of DRAM inventory. The mobile sector seems to be having healthier levels of inventory as mobile manufacturers were more conservative in their plans.
Nonetheless, mobile DRAM pricing is also expected to decline by 10 to 15%. As consumer demand for DRAM was sluggish, suppliers looked to the server side of the business for sales, however this simply resulted in a huge pile-up of inventory for server DRAM.
Read more of this story at SoylentNews.
04:55
Vulnerability Enabled Bing.com Takeover, Search Result Manipulation HackRead | Latest Cybersecurity and Hacking News Site
Cybersecurity researchers at Wiz reported the vulnerability to Microsoft and dubbed the attack "BingBang".
This is a post from HackRead.com Read the original post: Vulnerability Enabled Bing.com Takeover, Search Result Manipulation
04:02
Researchers Detail Severe "Super FabriXss" Vulnerability in Microsoft Azure SFX The Hacker News
Details have emerged about a now-patched vulnerability in Azure Service Fabric Explorer (SFX) that could lead to unauthenticated remote code execution. Tracked as CVE-2023-23383 (CVSS score: 8.2), the issue has been dubbed "Super FabriXss" by Orca Security, a nod to the FabriXss flaw (CVE-2022-35829, CVSS score: 6.2) that was fixed by Microsoft in October 2022. "The Super FabriXss vulnerability
03:47
How To Install LXD on Debian 11 Linux nixCraft
You can install LXD pure-container Debian, Ubuntu, CentOS, Fedora, Alpine, Arch and many other Linux distro. You can mimic AWS or different cloud instance types with LXD for testing and deployment purposes on your development machine. You can also run a GUI app such as Firefox completely isolated using LXD for security or privacy reasons. Let us see how to set up and use LXD on the Debian Linux 11 server or desktop.
Love this? sudo share_on: Twitter - Facebook - LinkedIn - Whatsapp - Reddit
The post How To Install LXD on Debian 11 Linux appeared first on nixCraft.
03:25
03:10
Boston Dynamics: Stretch cryptogon.com
Via: Boston Dynamics:
03:01
Display your application data with Streamlit Linux.com
Streamlit integrates with Python code and offers a low barrier of entry to visualizing application data in sophisticated ways.
Read More at Enable Sysadmin
The post Display your application data with Streamlit appeared first on Linux.com.
03:00
Clipboard-injecting malware disguises itself as Tor browser, steals cryptocurrency Graham Cluley
Malware, disguised as copies of Tor, has stolen approximately US $400,000 worth of cryptocurrency from almost 16,000 users worldwide.
02:58
Chinese RedGolf Group Targeting Windows and Linux Systems with KEYPLUG Backdoor The Hacker News
A Chinese state-sponsored threat activity group tracked as RedGolf has been attributed to the use of a custom Windows and Linux backdoor called KEYPLUG. "RedGolf is a particularly prolific Chinese state-sponsored threat actor group that has likely been active for many years against a wide range of industries globally," Recorded Future told The Hacker News. "The group has shown the ability to
02:43
EU Planning to Invest Frozen Russian Assets, Give Returns to Ukraine cryptogon.com
$300 billion. Via: The Libertarian Institute: The European Union is developing proposals on what to do with assets seized from the Russian central bank by member states. According to European officials, the bloc may invest the money and hand the returns to Ukraine. Anders Ahnlid, a Swedish diplomat who leads the commission exploring what to []
02:36
A Miscarriage of Statistics: The Thalidomide Sequel cryptogon.com
Via: Arkmedics Blog: The normal miscarriage rate of a healthy population is somewhere around 5-6%. For years, studies have been misrepresenting rates of 15-20% so that when new drugs are tested in pregnancy, a doubling of the miscarriage rate will fly under the radar. This is how the COVID vaccine managed to be sold as []
02:30
Electric Skateboard Becomes Mobile Skate Park Hackaday

While building a skate park might not appear to have much in common with software development, at they very least, they both suffer from a familiar problem: scalability. Bigger skate parks need more ramps and features, and theres no real way to scale up a construction project like this efficiently like you could with certain kinds of software other than simply building more features. This was something [Kirk] noticed, but was able to scale up a skate park in a way weve never thought of before. He built a mobile skateboard ramp that can turn any place into a skate park.
The mobile and approximately sidewalk-width platform is able to move around thanks to an electric skateboard as its foundation. It adds a NVIDIA Jetson Nano for control with a PS4 controller for input, although steering a skateboard with an actuator took a few prototypes to figure out since skateboards are designed to be steered by shifting the riders weight. Since they are already designed to carry a human-amount of weight, though, it was at least able to tote the ramp around with relative...
02:30
MSI Laptops To Enjoy Better Linux Support Beginning With The 6.4 Kernel Phoronix
Modern MSI laptops will see improved feature support with the upstream Linux 6.4 kernel this summer thanks to a new driver set to be merged...
02:29
RESTRICT Act Is Orwellian Censorship Grab Disguised As Anti-TikTok Legislation cryptogon.com
Via: ZeroHedge: The RESTRICT Act, introduced by Sens. Mark Warner (D-VA) and Tom Thune (R-SD), is aimed at blocking or disrupting transactions and financial holdings linked to foreign adversaries that pose a risk to national security, however the language of the bill could be used to give the US government enormous power to punish free []
02:27
New Deadly Superfungus Can Now Be Found in Half of US States Lifeboat News: The Blog
O.o!!!
A fungal superbug called Candida auris is spreading rapidly through hospitals and nursing homes in the US. The first case was identified in 2016. Since then, it has spread to half the countrys 50 states. And, according to a new report, infections tripled between 2019 and 2021.
This is hugely concerning because Candida auris is resistant to many drugs, making this fungal infection one of the hardest to treat.
Candida auris is a yeast-type fungus that is the first to have multiple international health alerts associated with it. It has been found in over 30 countries, including the UK, since it was first identified in Japan in 2009.
02:26
15 cars derail in north Butler County in train incident Lifeboat News: The Blog
Over a dozen railcars on a Canadian National Railway train had derailed in Northern Butler County.
A spokesperson for CN says crews are responding to the incident near Slippery Rock, PA.
They say 15 railcars, all containing iron ore derailed.
There are no dangerous goods on the train and there are no reported fires or injuries, a spokesperson told KDKA Radio in a statement.
02:26
Minnesota train carrying ethanol derailed, caught fire; evacuations ordered Lifeboat News: The Blog
BNSF said about 22 rail cars carrying mixed freight, including ethanol and corn syrup, derailed at 1:02 a.m. local time Thursday. Four rail cars caught fire, the BNSF said. There are no other hazardous materials on the train and no injuries were reported, the company said.
BNSF personnel are responding to assess the derailment site and will be working closely with local first responders, company spokesperson Lena Kent said in a statement.
02:25
Astronomers Just Discovered a Supermassive Black Hole. Hard to Comprehend How Big This Thing Is. Lifeboat News: The Blog
Scientists at Durham University say the black hole is 30 billion times the size of the sun.
02:25
AI can replicate voices in high-tech phone call scams, FTC warns Lifeboat News: The Blog
The FTC is sounding the alarm on artificial intelligence being used to simulate someones voice in imposter scams, which was the most commonly reported fraud in 2022. NBC News Emilie Ikeda spoke to one father who got a call that sounded like his daughter and said she was being held hostage.
02:25
Scientists identify cellular signaling pathway as key player in metastasis Lifeboat News: The Blog
A team of scientists at the Sloan Kettering Institute have identified the STING cellular signaling pathway as a key player in keeping dormant cancer cells from progressing into aggressive tumors months, or even years, after theyve escaped from a primary tumor.
The findings, which were published in Nature on March 29, suggest that drugs to activate STING could help prevent the spread of cancer to new sites throughout the bodya process known as metastasis.
In mouse models of lung cancer, treatment that stimulated the STING pathway helped eliminate lingering cancer cells and prevent them from progressing to aggressive metastases. Known as micrometastases, these cells, which can be found individually and in small clusters, are too small to be detected with standard imaging tests.
02:24
The Xaver 1000 is a next-gen radar that can actually see through walls Lifeboat News: The Blog
Camero-Tech, a firm based in Israel, has created a next-generation portable, high-performance imaging device that can actually see through walls. Called the Xaver 1,000, according to a press release from Camero-Tech, the company has now officially added this next-generation of the companys product line.
Camero-Tech is a member of Samy Katsav Group (aka SK Group), and a world leader and pioneer in developing, producing, and marketing pulse-based UWB micro-power radar, like the Xaver 1000.
02:23
Transplantation of clinical-grade human neural stem cells reduces neuroinflammation, prolongs survival and delays disease progression in the SOD1 rats Lifeboat News: The Blog
The hNSCs used in the study have been produced and characterised in the Cell Factory and Biobank of Santa Maria Hospital (Terni, Italy), authorised by the Italian Medicine Agency (AIFA) for the production of hNSCs to be used for clinical trials (aM 54/2018). The methodology applied to isolate, expand, characterise and cryopreserve the lines is based on the Neurosphere Assay26,41,54, and has been used for the production of the cells utilised in phase I trials for Amyotrophic Lateral Sclerosis patients (NCT0164006723) and for Secondary Progressive Multiple Sclerosis patients (NCT03282760, ongoing).
The entire production process, starting from tissue procurement to cryopreservation is compliant to cGMP guidelines and approved...
02:23
Quantum on a Microgram Scale Lifeboat News: The Blog
An experiment with an acoustic resonator demonstrates the quantum superposition of atomsnearly matching the ability of matter interferometers to test quantumness on macroscopic scales.
02:22
Were nowhere near reaching the maximum human life span, controversial study suggests Lifeboat News: The Blog
Human longevity records may be broken in the next few decades, a new modeling study suggests.
02:14
The Security Vulnerabilities of Message Interoperability SoylentNews
Jenny Blessing and Ross Anderson have evaluated the security of systems designed to allow the various Internet messaging platforms to interoperate with each other:
The Digital Markets Act ruled that users on different platforms should be able to exchange messages with each other. This opens up a real Pandora's box. How will the networks manage keys, authenticate users, and moderate content? How much metadata will have to be shared, and how?
In our latest paper, One Protocol to Rule Them All? On Securing Interoperable Messaging, we explore the security tensions, the conflicts of interest, the usability traps, and the likely consequences for individual and institutional behaviour.
Originally spotted on Schneier on Security.
One Protocol to Rule Them All? On Securing Interoperable Messaging, Jenny Blessing, Ross Anderson https://doi.org/10.48550/arXiv.2303.14178
Read more of this story at SoylentNews.
02:11
Lightning Eyes 10-Minute Charging for Its Motorbikes IEEE Spectrum

Lightning Motorcycles is already known for record-setting speeds. In 2011, the companys LS-218 SuperBike set a land speed record for production electric motorcycles at the Bonneville Salt Flats in Utah, with a 347.55 kilometer-per-hour (215.91 mile-per-hour) average run and a 351 km/h (218 mph) peak. That SuperBike topped every internal combustion engine motorcycle en route to a Pikes Peak International Hill Climb win in 2013, on the Colorado gauntlet thats among the worlds highest-profile tech challenges for cars and motorcycles alike.
The Southern California company is looking to speed things up againthis time with record-setting charging stops. Founder Richard Hatfield claims that the companys Lightning Strike motorcycle can fill its battery from 20 percent to 80 percent in a little over 10 minutes on a Level 3 DC fast charger. That time isnt much longer than a gasoline fill-up, especially for motorcyclists who dont mind some stretching and recovery after hours in the saddle.
Faster pit stops could also help unlock sales for electric two-wheelers, which have been slow to catch on due to dawdling charge times and limited riding range. Whereas electric carmakers have vastly more space for batteries, motorcycle purveyors can only stuff so many cells into a slender frame before a bike becomes impractically heavy, cumbersome to ride, or ungainly in appearance.
 Lightning
Motorcycles claims that the Lightning Strike motorcycle can fill
its battery from 20 percent to 80 percent in a little over 10
minutes on a Level 3 DC fast charger. Lightning Motorcycles
Lightning
Motorcycles claims that the Lightning Strike motorcycle can fill
its battery from 20 percent to 80 percent in a little over 10
minutes on a Level 3 DC fast charger. Lightning Motorcycles
Costs are becoming competitive, so the last big issues are range and c...
02:01
The 10 Best Cybersecurity Companies in the UK HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
Discover the best cybersecurity companies to protect your business, and learn how to find the top ones that
This is a post from HackRead.com Read the original post: The 10 Best Cybersecurity Companies in the UK
01:54
New California Transgender Law Endangers Parental Rights Worldwide, Legal Group Warns: Drastic Overreach cryptogon.com
Gender distress. Via: Fox: A new state law in California could incentivize bad actors from around the world to skirt custodial laws by relocating to the Golden State, a conservative legal group claims. We think its a drastic overreach by California, Emilie Kao, senior counsel for Alliance Defending Freedom (ADF), told Fox News Digital. Not []
01:54
Links 30/03/2023: LibreOffice 7.5.2 and Linux 6.2.9 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and
Gopher
...
01:43
3CX voice and video conferencing software victim of a supply chain attack Security Affairs
Popular voice and video conferencing software 3CX was the victim of a supply chain attack, SentinelOne researchers reported.
As of Mar 22, 2023, SentinelOne observed a spike in behavioral detections of the 3CXDesktopApp, which is a popular voice and video conferencing software product.
The products from multiple cybersecurity vendors started detecting the popular software as malware suggesting that the company has suffered a supply chain attack.
SentinelOne is tracking the malicious activity as SmoothOperator, the company speculates that the threat actor behind the attack has set up its infrastructure starting as early as February 2022.
The company st...
01:36
X.org vulnerability and releases LWN.net
The X.Org project has announced a vulnerability in its X server and Xwayland (CVE-2023-1393).
This issue can lead to local privileges elevation on systems where the X server is running privileged and remote code execution for ssh X forwarding sessions.[...] If a client explicitly destroys the compositor overlay window (aka COW), the Xserver would leave a dangling pointer to that window in the CompScreen structure, which will trigger a use-after-free later.
That has led to the release of xorg-server 21.1.8, xwayland 22.1.9, and xwayland 23.1.1.
01:31
Re: polkitd service user privilege separation Open Source Security
Posted by Jordan Glover on Mar 30
Is it valid conclusion that polkitd would be better of just running as root? That would clear any possible confusion.Or are there advantages of running it as separate "trusted" user?
Jordan
01:31
[$] The trouble with MODULE_LICENSE() in non-modules LWN.net
The kernel's hierarchical maintainer model works quite well from the standpoint of allowing thousands of developers to work together without (often) stepping on each others' toes. But that model can also make life painful for developers who are trying to make changes across numerous subsystems. Other possible source of pain include changes related to licensing or those where maintainers don't understand the purpose of the work. Nick Alcock has managed to hit all of those hazards together in his effort to perform what would seem like a common-sense cleanup of the kernel's annotations for loadable modules.
01:30
AMD EPYC Milan Still Gives Intel Sapphire Rapids Tough Competition In The Cloud Phoronix
While waiting for AMD 4th Gen EPYC "Genoa" instances to become available via the major public cloud providers, I was curious to see how existing AMD EPYC Milan instances compare to Intel's new Sapphire Rapids instances in public preview on Google Cloud. While expecting some friendly competition, at the same vCPU size EPYC Milan was managing to deliver not only better performance-per-dollar but also even better raw performance in numerous workloads against the Google Cloud C3 Sapphire Rapids.
01:26
Extraordinary: The Seeding cryptogon.com
If this topic interests you, see the books by David M. Jacobs: Secret Life: Firsthand, Documented Accounts of Ufo Abductions The THREAT: Revealing the Secret Alien Agenda Walking Among Us: The Alien Plan to Control Humanity Via: Unidentified:
01:04
Distribution Release: OpenMandriva 23.03 "ROME" DistroWatch.com: News
OpenMandriva is a general purpose operating system. The project has published new media for the distribution's rolling release branch, called ROME. The project's latest ROME snapshot introduces new editions, including Server builds which do not have a graphical user interface. "In addition to the previously released images, ROME....
01:01
01:00
PCIe For Hackers: Extracting The Most Hackaday

So, you now know the basics of approaching PCIe, and perhaps you have a PCIe-related goal in mind. Maybe you want to equip a single-board computer of yours with a bunch of cheap yet powerful PCIe WiFi cards for wardriving, perhaps add a second NVMe SSD to your laptop instead of that Ethernet controller you never use, or maybe, add a full-size GPU to your Raspberry Pi 4 through a nifty adapter. Whatever you want to do lets make sure there isnt an area of PCIe that you arent familiar of.
Splitting A PCIe Port
...
00:50
VP9/AV1 Simulcast Support For WebRTC Coming In Chrome 113 Phoronix
VP8 and H.264 have long been supported as part of WebRTC simulcast in the Chrome web browser while with the upcoming Chrome 113 release, VP9 and AV1 simulcast support is being enabled...
00:50
Security updates for Thursday LWN.net
Security updates have been issued by Debian (xorg-server and xrdp), Fedora (mingw-python-certifi, mingw-python3, mingw-zstd, moodle, python-cairosvg, python-markdown-it-py, redis, xorg-x11-server, and yarnpkg), Slackware (mozilla and xorg), SUSE (grub2, ldb, samba, libmicrohttpd, python-Werkzeug, rubygem-rack, samba, sudo, testng, tomcat, webkit2gtk3, xorg-x11-server, xstream, and zstd), and Ubuntu (linux, linux-aws, linux-dell300x, linux-kvm, linux-oracle, linux-raspi2, linux-aws-5.4, linux-azure-5.4, linux-gcp-5.4, linux-hwe-5.4, linux-ibm-5.4, linux-oracle-5.4, linux-raspi-5.4, linux-gke, linux-gke-5.15, linux-ibm, linux-kvm, php-nette, and xorg-server, xorg-server-hwe-18.04, xwayland).
00:39
Ransomware gangs are exploiting IBM Aspera Faspex RCE flaw (CVE-2022-47986) Help Net Security
Attackers are exploiting a critical vulnerability (CVE-2022-47986) in the IBM Aspera Faspex centralized file transfer solution to breach organizations. About CVE-2022-47986 IBM Aspera Faspex is used by organizations to allow employees to quickly and securely exchange files with each other. (The files are uploaded to and downloaded from a centralized Aspera transfer server.) CVE-2022-47986 is a YAML deserialization flaw that can be triggered by remote attackers sending a specially crafted obsolete API call. It affects More
The post Ransomware gangs are exploiting IBM Aspera Faspex RCE flaw (CVE-2022-47986) appeared first on Help Net Security.
00:18
New Mlofe Linux malware linked to Chinese APT groups Security Affairs
Exatrack researchers warn of an unknown China-linked hacking group that has been linked to a new Linux malware, dubbed Mlofe.
Cybersecurity researchers from ExaTrack recently discovered a previously undetected malware family, dubbed Mlofe, targeting Linux servers.
The researchers linked with high-confidence this malware to China-linked APT groups, in particular the Winnti group.
The Mlofe malware includes a kernel-mode rootkit thats based on an open-source project referred to as Reptile.
The analysis of the vermagic metadata revealed that it is experts noticed that the rootkit has a limited set of features.
The attackers use shell commands to download the installer and a custom binary package from a remote server and install the implant and the rootkit.
The installer is written in C++, it takes the binary package as an argument and then extracts the rootkit as well as a server implant module.

The researchers noticed that the implant is currently under active development.
The malware configuration is encrypted using the RC4 algorithm in the two early samples, while authors used a simple xor with a single byte key (0x43) in the most recent sample analyzed by the experts.
The configuration format in the first sample contains all elements in encrypted form, while the most recent sample has only the C&C domain encrypted.
The implant supports two mechanisms of persistence, depending on the privileges of his execution. When it runs as the root u...
00:03
CVE-2023-28935: Apache UIMA DUCC: DUCC (EOL) allows RCE Open Source Security
Posted by Arnout Engelen on Mar 30
Severity: moderateDescription:
** UNSUPPORTED WHEN ASSIGNED ** Improper Neutralization of Special Elements used in a Command ('Command Injection')
vulnerability in Apache Software Foundation Apache UIMA DUCC.
When using the "Distributed UIMA Cluster Computing" (DUCC) module of Apache UIMA, an authenticated user that has the
permissions to modify core entities can cause command execution as the system user that runs the...
Thursday, 30 March
23:56
Popular PABX platform, 3CX Desktop App suffers supply chain attack HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
According to cybersecurity researchers, a nation-state actor, LABYRINTH CHOLLIMA, is suspected to be behind the multi-stage attack on 3CXDesktopApp.
This is a post from HackRead.com Read the original post: Popular PABX platform, 3CX Desktop App suffers supply chain attack
23:27
Seattle-Area County Plans World Leading Sustainable Aviation Fuel R&D Center SoylentNews
Seattle-area county plans 'world leading' sustainable aviation fuel R&D center:
Washington state wants to create a "world leading" research and development center focused on low-carbon, sustainable aviation fuels. The facility is planned for Snohomish County's Paine Field Boeing's historic home and a hub for low-carbon aerospace startups including ZeroAvia and MagniX.
Snohomish County Executive Dave Somers on Tuesday announced plans for the center, which would be built in partnership with Washington State University. Sen. Marko Liias and Rep. Brandy Donaghy, both leaders from the county, are calling for $6.5 million in the state's transportation budget to get the project rolling.
"We have been at the forefront of the aviation industry for decades and this will now put us in a place to lead the world in shaping the future of clean aviation," said Liias, chair of the Washington State Senate Transportation Committee.
WSU has a Bioproducts, Science, and Engineering Laboratory at its Tri-Cities campus. One of the focal areas for the lab is biofuels, which includes sustainable aviation fuels.
Read more of this story at SoylentNews.
23:24
EEVDF Scheduler Patches Updated For The Linux Kernel Phoronix
Intel Linux engineer Peter Zijlstra has sent out updated patches on the kernel patch series he's been working on the past several months around the "EEVDF" CPU scheduler for improving upon the current CFS scheduler code...
23:21
New Wi-Fi Protocol Security Flaw Affecting Linux, Android and iOS Devices The Hacker News
A group of academics from Northeastern University and KU Leuven has disclosed a fundamental design flaw in the IEEE 802.11 Wi-Fi protocol standard, impacting a wide range of devices running Linux, FreeBSD, Android, and iOS. Successful exploitation of the shortcoming could be abused to hijack TCP connections or intercept client and web traffic, researchers Domien Schepers, Aanjhan Ranganathan,
22:17
Cyberstorage: Leveraging the Multi-Cloud to Combat Data Exfiltration The Hacker News
Multi-cloud data storage, once merely a byproduct of the great cloud migration, has now become a strategy for data management. "Multi-cloud by design," and its companion the supercloud, is an ecosystem in which several cloud systems work together to provide many organizational benefits, including increased scale and overall resiliency.And now, even security teams who have long been the holdout
22:00
Make Anything Clockwork With This Ridiculous Stick-On Device Hackaday

Clockwork devices were popular right up until motors and electronics proved far more capable in just about every way. However, theres something charming about a device you can wind up to make it do its thing. To recreate this feeling on modern technology, [Kousuke Saito] created a clockwork winder that you can fit to a wide variety of modern appliances.
21:46
Another Budget Gigabyte Ryzen Motherboard Gets Working Sensor Support With Linux 6.3 Phoronix
For those that happen to have a Gigabyte A320M-S2H V2 micro-ATX motherboard or you have been looking out for a low-end, budget motherboard for an AMD Ryzen AM4 build, the A320M-S2H V2 is the latest seeing working sensor support with the mainline Linux kernel...
21:30
Arm Scalable Matrix Extension 2 "SME2" Support Lands In GNU Binutils Phoronix
Toward the end of last year Arm detailed Scalable Matrix Extension 2 (SME2) for adding more capabilities to Armv9-A around speedy matrix processing. Merged this morning is initial support for SME2 within Binutils as part of the GNU compiler toolchain for the GNU Assembler...
21:27
3CX customers targeted via trojanized desktop app Help Net Security
Suspected state-sponsored threat actors have trojanized the official Windows desktop app of the widely used 3CX softphone solution, a number of cybersecurity companies began warning on Wednesday. What is 3CX? 3CX is Voice over Internet Protocol (VoIP) private automatic branch exchange (PABX) software that provides video conferencing and live chat capabilities. 3CX offers a More
The post 3CX customers targeted via trojanized desktop app appeared first on Help Net Security.
21:08
AlienFox Malware Targets API Keys and Secrets from AWS, Google, and Microsoft Cloud Services The Hacker News
A new "comprehensive toolset" called AlienFox is being distributed on Telegram as a way for threat actors to harvest credentials from API keys and secrets from popular cloud service providers. "The spread of AlienFox represents an unreported trend towards attacking more minimal cloud services, unsuitable for crypto mining, in order to enable and expand subsequent campaigns," SentinelOne security
20:50
Links 30/03/2023: WordPress 6.2 Dolphy and OpenMandriva ROME 23.03 Techrights
![]()
Contents
-
GNU/Linux
-
Desktop/Laptop
-
Unicorn Media System76 Ups Gazelle Laptops Game With a Refresh
Not long after updating its Pangolin laptop line, System76 is at
-
-
Audiocasts/Shows
-
APNIC ...
-
-
20:44
Liquid Salts Bring Push-Button Lenses Into Focus SoylentNews
Liquid Salts Bring Pushbutton Lenses Into Focus
First-ever piezoelectric liquids could spark new technologies in optics and hydraulics:
Scientists have discovered the first known piezoelectric liquids, which are able to convert mechanical force to electric charge, and vice versa. The generally environmentally friendly nature of these materials suggests they may find many applications beyond standard piezoelectric compounds, such as novel, electrically controlled optics and hydraulics. However, much remains unknown about how they work, and therefore what they may be capable of.
Piezoelectricity was first discovered in 1880. The effect has since found a wide range of applications, including cellphone speakers, inkjet printers, ultrasound imaging, sonar equipment, pressure sensors, acoustic guitar pickups, and diesel fuel injectors.
Until now, all known piezoelectric materials were solid. Now scientists have for the first time discovered piezoelectric liquids. They detailed their findings in a study online 9 March in the Journal of Physical Chemistry Letters.
The researchers experimented with ionic liquids. These fluids are saltscompounds that are each made of both a positively charged cation and a negatively charged anionthat are liquid at unusually low temperatures. In comparison, table salt melts at roughly 800 C.
"They are often relatively viscousthink about them like motor oil, or maple syrup," says Gary Blanchard, one of the authors of the study and a professor of chemistry at Michigan State University, in East Lansing.
Read more of this story at SoylentNews.
20:29
Re: polkitd service user privilege separation Open Source Security
Posted by Johannes Segitz on Mar 30
yes, that's what I've mentioned in my report.=====
| If you can act as the polkitd user you can also likely influence the polkit
| daemon and gain root this way, so this just makes it (a lot) easier to
| exploit.
`=====
For me it's easier to just write a file instead of subverting the process.
I agree. That's was also my main concern why I wrote this. For any other
setup I would have requested a CVE for this, but here the...
20:16
Exposing Sirius Corporation as a Corrupt Corporation schestowitz.com
Video download
link | md5sum
Victims of Open Source Charlatans
Creative Commons Attribution-No Derivative Works 4.0
Summary: Following todays part about the crimes of Sirius Open Source another video seemed to be well overdue (those installments used to be daily); the video above explains to relevance to Techrights and how workers feel about being cheated by a company that presents itself as Open Source even to some of the highest and most prestigious public institutions in the UK
20:14
Sirius is Britains Most Respected and Best Established Open Source Business, According to Sirius Itself, So Why Defraud the Staff? Techrights
Video download
link | md5sum
Victims of Open Source Charlatans
Creative Commons Attribution-No Derivative Works 4.0
Summary: Following today's part about the crimes of Sirius Open Source another video seemed to be well overdue (those installments used to be daily); the video above explains to relevance to Techrights and how workers feel about being cheated by a company that presents itself as Open Source even to some of the highest and most prestigious public institutions in the UK
19:02
Z-Library Raises Tens of Thousands of Dollars to Keep its Pirate Library Running TorrentFreak
 Z-Library has become the go-to site for many readers in
recent years by providing access to millions of books, for
free.
Z-Library has become the go-to site for many readers in
recent years by providing access to millions of books, for
free.
The sites continued ability to do so was put to the test late last year when U.S. law enforcement seized over 200 domain names connected to the site. Two alleged Z-Library operators were arrested as part of a criminal investigation.
Z-Library Comeback
Despite losing two alleged members of its team, as well as over 200 domain names, Z-Library had no intention of throwing in the towel. The site remained accessible through the dark web and a few weeks ago made a full comeback on the clearnet as well.
The new setup comes with some technical tweaks. For example, every user now has a unique subdomain to access Z-Library, which may make it more difficult for law enforcement to take down the whole operation all at once.
Implementing these changes and some others, including a new recommendation section and Telegram bot, required substantial investments. To help pay the bill, Z-Library is now asking its users to chip in.
Substantial Damage
In a message posted earlier this month, the Z-Library team revealed that the U.S. law enforcement actions caused substantial damage. While the 220 terabytes of data werent lost, getting everything up and running again wasnt easy.
[A]lmost all public domains of the library were blocked in November 2022 by order of the US Secret Service. The inner infrastructure of the project suffered some substantial damage too, Z-Library said.
Today, we are still under unprecedented pressure. At the moment, Z-Library is going through the hardest times in all the 14 years of its existence. The library might work with interruptions, and we ask you to be patient.
Donation Drive
These comments are part of a donation drive encouraging users to contribute. Z-Library offers a variety of support options, including crypto, gift cards, WeChat, and Alipay.
We will be extremely thankful for every dollar that will be donated, Zlibrary notes.
19:00
Generating Instead of Storing Meshes Hackaday

The 64kB is a category in the demoscene where the total executable size must be less than 65,536 bytes, and at that size, storing vertexes, edges, and normal maps is a waste of space. [Ctrl-Alt-Test] is a French Demoscene group that has been doing incredible animations for the last 13 years. Theyve written an excellent guide on how theyve been procedurally generating the meshes in their demos.
It all starts with cubes. By stacking them, overlaying them, reusing them, and tiling them you can get better compression than raw vertexes. Revolution was the next trick, as it uses just a few points, plotting it via Catmul-Rom splines, and revolving around an axis. The numbers are pairs of 32-bit floats and before compression, a detailed pawn on a chess board can weigh in at just 40 bytes. Just these few techniques can take you surprisingly far (as seen in the picture above).
They later worked on deforming cubes and placing them into a semi-randomized column, which happened to look a lot like plants. This isnt the first generated vegetation weve seen, and the demoscene te...
18:05
IRC Proceedings: Wednesday, March 29, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-290323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-290323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-290323.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-290323.gmi
Over HTTP:
|
... |
18:02
Nokia Plans to Put 4G Internet on the Moon This Year SoylentNews
If you believe, they'll put 4G internet on the moon:
A Nokia executive recently confirmed the company is preparing to launch 4G internet on the moon, hopefully before the end of 2023. We put a man on the moon in 1969, and now the Finnish Telecom company wants to give the rock an internet connection.
For those unaware, Nokia announced these bold ambitions back in 2020 when NASA selected it for the project, and now it sounds like things are moving in the right direction.
According to CNBC, this is a big undertaking and will be a joint mission by Nokia, NASA, SpaceX, and others. The company Intuitive Machiness upcoming IM-2 mission, currently scheduled to launch in November aboard a SpaceX Falcon 9 rocket, will carry the 4G payload.
Once delivered, Intuitive Machines' Nova-C lunar lander will be able to have an active connection with its Rovers, helping aid in lunar discoveries, not to mention developing a human presence on the surface of the moon.
The hope is that this system can meet the needs of future space missions, including NASA's Artemis mission. If everything goes according to plan, Nokia's moon 4G signal will improve critical command and control functions, give teams remote control of rovers, and offer real-time navigation, not to mention stream back HD video of the moon's surface (and more) to Earth.
Read more of this story at SoylentNews.
18:00
Falun Gong Doctrine Terra Forming Terra
Wind Power Fails on Every Count: Oxford Scientist Explains the Math Terra Forming Terra

Here we are and it is literally forty years on in the wind power
build out. I have yet to see someone come in and show me that these
plants ever simply pay for themselves without all sorts of tax
breaks and all that. I do not think that they actually can. It is
like writing off a million dollar investment just to earn a living
wage.
.
Top 5 Ancient Greek Inventions We Still Use Today Terra Forming Terra
5 Months to Kill: The terrifying relationship between Deaths, COVID Deaths & Covid-19 Vaccination Terra Forming Terra

17:42
[Meme] Waiting for Standard Life to Deal With Pension Fraud Techrights
Summary: The crimes of Sirius Open Source were concealed with the authoritative name of Standard Life, combined with official papers from Standard Life itself; why does Standard Life drag its heels when questioned about this matter since the start of this year?
17:31
3CX Desktop App Supply Chain Attack Leaves Millions at Risk - Urgent Update on the Way! The Hacker News
3CX said it's working on a software update for its desktop app after multiple cybersecurity vendors sounded the alarm on what appears to be an active supply chain attack that's using digitally signed and rigged installers of the popular voice and video conferencing software to target downstream customers. "The trojanized 3CX desktop app is the first stage in a multi-stage attack chain that pulls
17:27
Former Sirius Open Source Staff Shocked to Discover the Company Committed Fraud schestowitz.com
Summary: Crimes committed by the company that I left months ago are coming to light; today we share some reactions from other former staff (without naming anybody)
TODAY we take a look at the nature of the crimes of Sirius Open Source, what pension providers are saying, and what former colleagues say about the company upon realising that it is corrupt (spoiler: some arent even surprised).
We shall start with the pension providers, with focus on Standard Life (the other provider has not even responded yet!) as about 6 hours after I complained about it (and made this meme) Standard Life contacted me by E-mail to say: (days late already)
Dear Dr Schestowitz
Thank you for your email.
We are carefully considering the concerns you have raised. Im sorry if the time this is taking is frustrating for you, but we believe it is appropriate given the situation.
I will be in touch with you again as soon as possible.
Yours sincerely
??????????? ??????????
Complaint Consultant
This does not say anything concrete. It has been like this since March 7th and were soon in April. Sirius is running out of clients, i.e. out of revenue stream. How long must one wait? When it comes to Standard Life, the interactions over the telephone go back to January. Why does this take so long to progress? What does that tell us about the pensions/financial sector (Standard Life is a giant in this sector)?
About a month ago I said to the company, Sirius: I spoke to numerous managers at Standard Life for 3 months. They reached the conclusion that myself and colleagues never had any money deposited there money taken for Pension off of our salary, as per the payslips for 5+ years. This suggests pension fraud and an actual crime. I assume, moreover, that [wife] (as Director and spouse) was fully aware of this. In the name of journalistic integrity I must first ask you if this is patently false a chance for you to comment in your defence. A lack of reply can be interpreted as implicit admission of guilt.
To paraphrase what you said in a call back in November, it doesnt look good.
There has been no response since. None. They know theyre guilty. Days later I wrote to say: You did not respond. I assume you have nothing to say in your defense. My E-mails to [CEO] are bouncing, so I assume he wants nothing to do with the company anymore. A month ago you failed to provide a physical address for the company. Now it is moreover headless (the CEO left). [PA] is still based in the UK...
17:20
Former Staff of Sirius Open Source Responds to Revelations About the Companys Crimes Techrights
Previously/context:
- Sirius Open Source and the Money Missing From the Pension
- Sirius Finished
- Sirius Open Source Pensiongate: An Introduction
- When the Pension Vanishes
- Sirius Open Source Pensiongate (Sirius Financial Crisis): Company May Have Squandered/Plundered the Pensions of Many People
- Sirius Open Source Pensiongate: Pension Providers That Repeatedly Lie to the Clients and Dont Respond to Messages
- NOW: Pensions Lies to Its Customers and Protects Abusers
- Sirius Open Source Pensiongate: Its Beginning to Look Like a Criminal Matter and Sirius is in Serious Trouble
- Sirius Open Source Pensiongate: A Long Story Merits Many Videos
- An Update on Sirius Open Source Pensiongate: Its Looking Worse Than Ever
Summary: Crimes committed by the company that I left months ago are coming to light; today we share some reactions from other former staff (without naming anybody)
17:08
US sends million-dollar scammer to prison for four years Graham Cluley
31-year-old Solomon Ekunke Okpe, of Lagos, was a member of a gang that devised and executed a variety of scams - including business email compromise (BEC), romance scams, working-from-home scams, and more - between December 2011 and January 2017. Read more in my article on the Hot for Security blog.
16:00
Compose Any Song With Twelve Buttons Hackaday

Limitations placed on any creative process often paradoxically create an environment in which creativity flourishes. A simple overview of modern pop, rock, or country music illustrates this principle quite readily. A bulk of these songs are built around a very small subset of music theory, often varying no more than the key or the lyrics. Somehow, almost all modern popular music exists within this tiny realm. [DeckerEgo] may have had this idea in mind when he created this tiny MIDI device which allows the creation of complex musical scores using a keyboard with only 12 buttons.
The instrument is based around the Adafruit MacroPad, which is itself built on the RP2040 chip. As a MIDI device, it needs to be connected to a computer running software which can support MIDI instruments, but once its assembled and given its firmware, its ready to rock. A musician can select one of any number of musical scales to operate within, and the 12 keys on the pad are mapped to the 12 chromatic notes within that scale. It can also be used to generate drum tracks or other backing tracks to loop before being used to create melodies as well.
[DeckerEgo] took a bit of inspiration from an even simpler macro pad we featu...
15:30
The rise of biometrics and decentralized identity is a game-changer for identity verification Help Net Security
The journey towards digital transformation for organizations and governments has been fraught with difficulties, resulting in some users needing to catch up as more digital services are introduced. In this Help Net Security video, Jenn Markey, VP of Payments and Identities at Entrust, talks about how biometrics, hybrid solutions, and decentralized identity are transforming the industry and the future of identity verification. Digital identity is a rapidly evolving space, with the market expected to reach More
The post The rise of biometrics and decentralized identity is a game-changer for identity verification appeared first on Help Net Security.
15:17
Disney Reportedly Scraps its Metaverse Unit SoylentNews
Disney appears to be the latest company to pull back the metaverse, as CEO Bob Iger reverses more decisions from his predecessor:
The entertainment giant's metaverse team has reportedly been eliminated as part of the ongoing round of job cuts at Disney. The Wall Street Journal reports all 50 team members who were developing the company's metaverse strategies have been let go.
The metaverse was a pet project of former CEO Bob Chapek, who called it "the next great storytelling frontier."
[...] Last November, however, Chapek was unceremoniously dismissed from Disney. And Bob Iger returned to the CEO role, quickly reversing several of Chapek's decisions.
The metaverse ambitions appear to be the latest to be targeted by Iger. Despite the many ideas that were publicly floated, the metaverse unit had apparently not made much progress on the new technology and did not have many clear plans in place.
Originally spotted on The Eponymous Pickle.
Read more of this story at SoylentNews.
15:00
Protect your entire business with the right authentication method Help Net Security
In this Help Net Security interview, Tomasz Kowalski, CEO at Secfense emphasizes the significance of multi-factor authentication in the corporate landscape, highlights the use of microauthorizations to improve the security of protected applications, and much more. What is the importance of modern MFA in todays business environment? I believe that modern Multi-Factor Authentication (MFA) is critical in todays business environment for several reasons. Firstly, traditional password-based authentication methods are no longer sufficient to protect against More
The post Protect your entire business with the right authentication method appeared first on Help Net Security.
14:45
Scan and diagnose your SMEs cybersecurity with expert recommendations from ENISA Help Net Security
The release of a cybersecurity maturity assessment tool by the European Union Agency for Cybersecurity (ENISA) aims to provide Small and Medium Enterprises (SMEs) with a valuable resource for enhancing their security posture. As a significant driver for innovation and growth in the EU, SMEs constantly face cybersecurity challenges. This is why it is essential to support them in addressing these challenges and identifying improvements. The cybersecurity maturity assessment tool designed by ENISA supports those More
The post Scan and diagnose your SMEs cybersecurity with expert recommendations from ENISA appeared first on Help Net Security.
14:30
Dangerous misconceptions about emerging cyber threats Help Net Security
Organizations are leaving common attack paths exposed in their quest to combat emergent threats, according to Cymulate. The most concerning cyber threats The report delves into the efficacy of different security controls, the most concerning threats as tested by organizations worldwide, and top cybersecurity best practices for 2023. Report key takeaways include: Many organizations are testing for trending threats Organizations are actively testing against threats seen in the news, likely from pressure to report on More
The post Dangerous misconceptions about emerging cyber threats appeared first on Help Net Security.
14:00
The cost-effective future of mainframe modernization Help Net Security
As Europes enterprises return to normal following the COVID-19 pandemics impact, they are looking for innovative and cost-effective ways to combine mainframe dependability with the flexibility of the cloud, according to ISG. Mainframe modernization services market accelerates The report finds that an increased focus on updated IT infrastructure and digital transformation has led to a corresponding acceleration in the mainframe modernization services market. Although many companies still depend on them for reliability, availability and security, More
The post The cost-effective future of mainframe modernization appeared first on Help Net Security.
13:45
The best defense against cyber threats for lean security teams Help Net Security
H0lyGh0st, Magecart, and a slew of state-sponsored hacker groups are diversifying their tactics and shifting their focus to you. That is, if youre in charge of cybersecurity for a small-to-midsize enterprise (SME). Why? Bad actors know that SMEs typically have a smaller security budget, less infosec manpower, and possibly weak or missing security controls to protect their data and infrastructure. So, how can you prepare for the imminent onslaught from new and emerging threat groups? More
The post The best defense against cyber threats for lean security teams appeared first on Help Net Security.
13:30
LOKKER Web Privacy Risk Score helps organizations measure and mitigate online privacy threats Help Net Security
LOKKER has released its LOKKER Web Privacy Risk Score, the assessment tool that provides businesses with a clear, numeric rating of their privacy risk across a global portfolio of websites, individual websites within that portfolio, and the individual web pages of each website. LOKKERs Web Privacy Risk Score is a measure that quantifies a companys potential risk of privacy violations pertaining to the collection and sharing of customers online information. Organizations in all industries are More
The post LOKKER Web Privacy Risk Score helps organizations measure and mitigate online privacy threats appeared first on Help Net Security.
13:20
BigIDs privacy suite discovers and classifies all CPRA-related data Help Net Security
BigID announced native data privacy capabilities to automate and help fulfill California Privacy Rights Act (CPRA) requirements. The California Privacy Rights Act (CPRA) is an amendment to the California Consumer Privacy Act (CCPA) that went into effect on Jan 1, 2023, and will be fully enforced on July 1, 2023. CPRA has specific requirements around B2B and employee data rights, privacy risk assessments, retention policies, and data minimization, which are measures to mitigate the data More
The post BigIDs privacy suite discovers and classifies all CPRA-related data appeared first on Help Net Security.
13:00
Biohybrid Implant Patches Broken Nerves with Stem Cells Hackaday

Neural interfaces have made great strides in recent years, but still suffer from poor longevity and resolution. Researchers at the University of Cambridge have developed a biohybrid implant to improve the situation.
As weve seen before, interfacing electronics and biological systems is no simple feat. Bodies tend to reject foreign objects, and transplanted nerves can have difficulty assuming new roles. By combining flexible electronics and induced pluripotent stem cells into a single device, the researchers were able to develop a high resolution neural interface that can selectively bind to different neuron types which may allow for better separation of sensation and motor signals in future prostheses.
As is typically the case with new research, the only patients to benefit so far are rats and only on the timescale of the study (28 days). That said, this i...
12:37
Among Users in the Worlds Largest Population, Microsoft is the 1% Techrights
Edge developers recently laid off, too (the media barely mentioned this; its all about chaffbot hype)
Summary: A sobering look at India shows that Microsoft lost control of the country (Windows slipped to 16% market share while GNU/Linux grew a lot; Bing is minuscule [1, 2]; Edge fell to 1.01% and now approaches decimal point territories)
12:32
Artificial Intelligence 'Godfather' on AI Possibly Wiping Out Humanity: It's Not Inconceivable SoylentNews
Geoffrey Hinton, a computer scientist who has been called "the godfather of artificial intelligence", says it is "not inconceivable" that AI may develop to the point where it poses a threat to humanity:
The computer scientist sat down with CBS News this week about his predictions for the advancement of AI. He compared the invention of AI to electricity or the wheel.
Hinton, who works at Google and the University of Toronto, said that the development of general purpose AI is progressing sooner than people may imagine. General purpose AI is artificial intelligence with several intended and unintended purposes, including speech recognition, answering questions and translation.
"Until quite recently, I thought it was going to be like 20 to 50 years before we have general purpose AI. And now I think it may be 20 years or less," Hinton predicted. Asked specifically the chances of AI "wiping out humanity," Hinton said, "I think it's not inconceivable. That's all I'll say."
[...] Hinton said it was plausible for computers to eventually gain the ability to create ideas to improve themselves.
Also at CBS News. Originally spotted on The Eponymous Pickle.
Previously: OpenAI's New ChatGPT Bot: 10 "Dangerous" Things it's Capable of
Read more of this story at SoylentNews.
12:07
In One City Alone Microsoft Fired Almost 3,000 Workers This Year (Were Still in March) Techrights
In Bill Gates-sponsored media [1, 2] this week:
Another Microsoft piece from a Microsoft mouthpiece (Bishop, a Microsoft Media Operative):
The media in India (where Microsoft has many layoffs too; GitHub has fired almost all of its Indian (as in India-based) staff):
Summary: You can tell a company isnt doing well when amid mass layoffs it pays endless money to the media not to actual workers in order for this media to go crazy over buzzwords, chaffbots, a...
12:04
[$] LWN.net Weekly Edition for March 30, 2023 LWN.net
The LWN.net Weekly Edition for March 30, 2023 is available.
11:25
Links 29/03/2023: InfluxDB FDW 2.0.0 and Erosion of Human Rights Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Desktop/Laptop
-
9to5Linux System76 Announces New Gazell...
-
-
11:21
11:00
HPR3824: 2022-2023 New Years Show Episode 4 Hacker Public Radio
Episode #4 Massachusetts Comprehensive Assessment System https://www.mass.gov/parents-guide-to-the-mcas https://en.wikipedia.org/wiki/Massachusetts_Comprehensive_Assessment_System Standardized Testing Was Invented In Massachusetts https://ed.lehigh.edu/news-events/news/history-standardized-testing GED Exam https://ged.com/about_test/test_subjects/ https://en.wikipedia.org/wiki/General_Educational_Development Alternative High Schools https://blog.prepscholar.com/alternative-high-schools Umbrella Revolution https://time.com/3471366/hong-kong-umbrella-revolution-occupy-central-democracy-explainer-6-questions/ https://en.wikipedia.org/wiki/Umbrella_Movement Learning the Finnish Language https://finland.fi/life-society/how-the-heck-do-you-learn-finnish-part-1/ https://herfinland.com/finnish-language-learning/ France Bans Google Drive In Schools https://www.theregister.com/2022/11/22/france_no_windows_google/ https://gettotext.com/office-365-and-google-drive-are-not-welcome-in-french-schools-even-if-they-are-free/ Windows Me (Windows Millennium Edition) https://en.wikipedia.org/wiki/Windows_Me https://www.howtogeek.com/688861/windows-me-20-years-later-was-it-really-that-bad/ Windows 2000 https://en.wikipedia.org/wiki/Windows_2000 Windows 95 https://en.wikipedia.org/wiki/Windows_95 FreeDOS https://www.freedos.org/ BOX 86 https://box86.org/ React OS https://reactos.org/ WINE https://www.winehq.org/ Proton https://github.com/ValveSoftware/Proton https://www.tomshardware.com/how-to/game-with-steam-on-linux https://www.protondb.com/ Windows XP https://en.wikipedia.org/wiki/Windows_XP Windows 7 h
Classification of Identify Management Approaches It Will Never Work in Theory
It's hard to make progress without discussing things, and it's hard to discuss things if you don't agree on terminology. This paper presents a systematic, comprehensible classification of various approaches to identity management, and gives examples (like the two shown below) of where different use cases fit. By creating this, the authors have made it easier for us to see where we agree and disagree, and have also pointed out some interesting gaps in existing approaches. There are (necessarily) a lot of acronyms in the paper, but anyone implementing identity management should read it, and it would be a great starting point for a lecture or two in an undergrad course on system design or software architecture.
This paper presents a comprehensive classification of identity management approaches. The classification makes use of three axes: topology, type of user, and type of environment. The analysis of existing approaches using the resulting identity management cube (IMC) highlights the trade-off between user control and trust in attributes. A comparative analysis of IMC and established models identifies missing links between the approaches. The IMC is extended by a morphology of identity management, describing characteristics of cooperation. The morphology is then mapped to the life cycle of users and identity management in a further step. These classifications are practically underlined with current approaches. Both methods combined provide a comprehensive characterization of identity management approaches. The methods help to choose suited approaches and implement needed tools.
Classification of Identity Management Approaches It Will Never Work in Theory
It's hard to make progress without discussing things, and it's hard to discuss things if you don't agree on terminology. This paper presents a systematic, comprehensible classification of various approaches to identity management, and gives examples (like the two shown below) of where different use cases fit. By creating this, the authors have made it easier for us to see where we agree and disagree, and have also pointed out some interesting gaps in existing approaches. There are (necessarily) a lot of acronyms in the paper, but anyone implementing identity management should read it, and it would be a great starting point for a lecture or two in an undergrad course on system design or software architecture.

Daniela Phn and Wolfgang Hommel. IMC: a classification of identity management approaches. 2023. arXiv:2301.00444.
This paper presents a comprehensive classification of identity management approaches. The classification makes use of three axes: topology, type of user, and type of environment. The analysis of existing approaches using the resulting identity management cube (IMC) highlights the trade-off between user control and trust in attributes. A comparative analysis of IMC and established models identifies missing links between the approaches. The IMC is extended by a morphology of identity management, describing characteristics of cooperation. The morphology is then mapped to the life cycle of users and identity management in a further step. These classifications are practically underlined with current approaches. Both methods combined provide a comprehensive characterization of identity management approaches. The methods help to choose suited approaches and implement needed tools.
10:02
Introducing self-service SPDX SBOMs Linux.com


Following the precedent set by Executive Order 14028, security and compliance teams increasingly request software bills of materials (SBOMs) to identify the open source components of their software projects, assess their vulnerability to emerging threats, and verify alignment with license policies. So, we asked ourselves, how do we make SBOMs easier to generate and share?
Read the rest at the GitHub blog
The post Introducing self-service SPDX SBOMs appeared first on Linux.com.
10:01
Smashing Security podcast #315: Crypto hacker hijinks, government spyware, and Utah social media shocker Graham Cluley
A cryptocurrency hack leads us down a maze of twisty little passages, Joe Biden's commercial spyware bill, and Utah gets tough on social media sites. All this and much much more is discussed in the latest edition of the "Smashing Security" podcast by computer security veterans Graham Cluley and Carole Theriault, joined this week by The Register's Iain Thomson.
10:00
The BLE Datalogging Scale Of A Thousand Uses Hackaday

Whether youre making coffee or beer or complex chemicals, weighing your ingredients carefully and tracking them is key to getting good results. [Tech Dregs] decided to build a logging scale that would work seamlessly with his smartphone, and shared the design on YouTube.
The design begins with a Greater Goods manual electronic scale, which was chosen for its convenient design and 750 gram load cell. Once cracked open, [Tech Dregs] pulled out the original PCB to replace it with his own. Only the original buttons are used, with an Seed Xiao ESP32-C3 replacing the scales original brains. The original LCD screen was swapped out for an OLED display, and it also got a rechargeable lithium battery for better usability.
The real value of the project, though, is its communication capa...
09:45
Webb Telescope Confirms Nearby Rocky Planet Has No Significant Atmosphere SoylentNews
A close look at one of TRAPPIST-1's planets shows it's bare and baking:
At this point, we've discovered lots of exoplanets that fall under the general label "Earth-like." They're rocky, and many orbit at distances from their host stars to potentially have moderate temperatures. But "like" is doing a lot of work there. In many cases, we have no idea whether they even have an atmosphere, and the greenhouse effect means that the atmosphere can have a huge impact on the planet's temperature. So the Earth-like category can include dry, baking hellscapes like Venus with its massive atmosphere, as well as dry, frozen tundras with sparse atmospheres like Mars.
But we're slowly getting the chance to image the atmospheres of rocky exoplanets. And today, researchers are releasing the results of turning the Webb Space Telescope on a rocky planet orbiting a nearby star, showing that the new hardware is so sensitive that it can detect the star blocking out light originating from the planet. The results suggest that the planet has very little atmosphere and is mostly radiating away heat from being baked by its nearby star.
TRAPPIST-1 is a small, reddish starin astronomical terminology, it's an "ultra-cool dwarf"that's about 40 light-years from Earth. While the star itself is pretty nondescript, it's notable for having lots of planets, with seven in total having been identified so far. All of these are small, rocky bodies, much like the ones that occupy the inner portion of our Solar System. While the star emits very little light, the planets are all packed in closer to it than Mercury is to the Sun.
[...] So, TRAPPIST-1 provides a fantastic opportunityreally, seven opportunitiesto test some of our ideas about exoplanet atmospheres. And both the Hubble and Spitzer space telescopes have imaged some starlight that passes close to some of the planets as they pass between Earth and TRAPPIST-1. These observations didn't provide any indications of an atmosphere, setting limits on how thick any gases above these planets could be.
Read more of this story at SoylentNews.
09:41
Google reveals spyware attack on Android, iOS, and Chrome HackRead | Latest Cybersecurity and Hacking News Site
Google's Threat Analysis Group (TAG) labeled the spyware campaign as limited but highly targeted.
This is a post from HackRead.com Read the original post: Google reveals spyware attack on Android, iOS, and Chrome
09:27
[$] Rebecca Giblin on chokepoint capitalism LWN.net
The fourth and final keynote for Everything Open 2023 was
given by Professor Rebecca Giblin of the Melbourne Law School,
University of Melbourne. It revolved around her recent book,
Chokepoint
Capitalism, which she wrote with Cory Doctorow; it is "a
book about why creative labor markets are rigged and how to unrig
them
". Giblin had planned to be in Melbourne to give her talk
in person, but "the universe had other plans"; she got delayed in
Austin, Texas by an unexpected speaking slot at the South by Southwest (SXSW) conference,
so she gave her talk via videoconference from thereat nearly
midnight in Austin.
08:56
08:51
The Linux Foundation Announces Keynote Speakers for Open Source Summit North America 2023 Linux.com

Read the original post at: Read More
The post The Linux Foundation Announces Keynote Speakers for Open Source Summit North America 2023 appeared first on Linux.com.
08:25
Mlofe: The Latest Malware Targeting Linux Servers HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
An unidentified Chinese APT group is suspected of operating the Mlofe malware.
This is a post from HackRead.com Read the original post: Mlofe: The Latest Malware Targeting Linux Servers
08:07
QNAP fixed Sudo privilege escalation bug in NAS devices Security Affairs
Taiwanese vendor QNAP warns customers to patch a high-severity Sudo privilege escalation bug affecting NAS devices.
Taiwanese vendor QNAP warns customers to update their network-attached storage (NAS) devices to address a high-severity Sudo privilege escalation vulnerability tracked as CVE-2023-22809.
The company states that the vulnerability affects QTS, QuTS hero, QuTScloud, and QVP (QVR Pro appliances) QNAP operating systems.
The vulnerability was discovered by security firm Synacktiv, it sudoedit. An attacker can trigger the vulnerability to achieve privilege escalation by editing unauthorized files after appending arbitrary entries to the list of files to process.
Sudo uses user-provided environment variables to let its users select their editor of choice. The content of these variables extends the actual command passed to the sudo_edit() function. However, the latter relies on the presence of the argument to determine the list of files to edit. The injection of an extra argument in one of the authorized environment variables can alter this list and lead to privilege escalation by editing any other file with privileges of the RunAs user. reads the advisory published by Synacktiv. This issue occurs after the sudoers policy validation.
The company already fixed the flaw in the following operating system versions:
- QTS 5.0.1.2346 build 20230322 and later
- QuTS hero h5.0.1.2348 build 20230324 and later
QNAP is urgently fixing the vulnerabilities in QuTScloud and QVP. reads the advisory published by the vendor. Please check this security advisory regularly for updates and promptly update your operating system to available.
The company recommends regularly updating NAS systems to the latest version.
Below are the instructions provided in the advisory to secure impacted devices:
Updating QTS, QuTS hero, or QuTScloud
- Log in to QTS, QuTS hero, or QuTScloud as an administrator.
- Go to Control Panel > System > Firmware Update.
- Under Live Update,
click Check for Update.
The system downloads and installs the latest available update.
Tip: You can also d...
07:21
How to Hide Tables in SQL Server Management Studio HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
SQL Server Management Studio (SSMS) is a software application developed by Microsoft that is used for configuring, managing,
This is a post from HackRead.com Read the original post: How to Hide Tables in SQL Server Management Studio
07:19
Australias Casino Giant Crown Resorts disclosed data breach after Clop ransomware attack Security Affairs
Australias gambling and entertainment giant Crown Resorts, disclosed a data breach caused by the exploitation of recently discovered GoAnywhere zero-day.
Australian casino giant Crown Resorts disclosed a data breach after the attack of the Cl0p ransomware group. The group claims to have stolen sensitive data from over 130 organizations by exploiting a zero-day vulnerability (CVE-2023-0669) in Fortras GoAnywhere MFT secure file transfer tool, BleepingComputer reported.
The Australian casino giant is one of the victims of this campaign. The incident took place in January, but the company disclosed the data breach this week.
We were recently contacted by a ransomware group who claim they have illegally obtained a limited number of Crown files. We are investigating the validity of this claim as a matter of priority. reads the statement published by the company on March 27, 2023. We can confirm no customer data has been compromised and our business operations have not been impacted. We are continuing to work with law enforcement and have notified our gaming regulators as part of the ongoing investigation and will provide relevant updates, as necessary.
The Cl0p ransomware group added Crown Resorts to the list of victims published on its Tor leak site.
06:59
Metas Anti-Piracy Deal: How Facebook & Broadcasters Kill Live Pirate Streams TorrentFreak
 For reasons that make absolutely no sense while somehow
making perfect sense, millions of internet users think that social
media platforms are perfect for piracy.
For reasons that make absolutely no sense while somehow
making perfect sense, millions of internet users think that social
media platforms are perfect for piracy.
Social media platforms like Facebook are admittedly quick and easy, but such positives are quickly overwhelmed by extraordinary privacy issues, not to mention centralized control. Nevertheless, the masses love quick and easy so in common with similar platforms everywhere, social media has a piracy problem.
Partners Against Piracy
This week Meta and Italian broadcaster RTI announced the signing of a multi-year partnership that will attempt to prevent the latters TV content from being pirated on Meta platforms. According to RTI, the companies will collaborate on the implementation of a set of tools and systems to protect RTIs copyrighted content, including its live TV broadcasts.
The odds of Meta/Facebook implementing systems that only benefit RTI seem slim, but it may be possible to identify areas for improvement useful to a broader set of rightsholders. However, since RTI specifically mentions that Meta will provide dedicated training on how to use Metas Rights Manager system more effectively, it wouldnt be a surprise if that was the key focus of the agreement.
So what is Rights Manager, and how does it work?
Rights Manager Took Inspiration From Content ID
YouTubes Content ID system first appeared more than 15 years ago, and today many users of the site will have seen it in action. Content ID uses algorithms to generate digital fingerprints of content uploaded to the platform which can then be compared against reference files (original content) provided by rightsholders.
When a match is found, rightsholders have several broad options block the uploaded content, monitor its statistics, monetize the upload with advertising and take the revenue, or sit back and do nothing.
Facebook launched its own content-matching, rights management tool in 2016. In common with Content ID, Rights Manager relies on reference files uploaded to the platform by rightsholders.
When a match is found, rightsholders can perform match actions block the uploaded content, monitor for insights into performance and audience engagement, place a banner on matching videos linking to content of their choice, or monetize with advertising and, of course, take the revenue.
In common with YouTubes system, match actions can be mixed, such as blocking in one country but taking revenue in another.
06:57
TikTok Trackers Embedded in U.S. State-government Websites, Review Finds SoylentNews
State governments might be inadvertently helping Chinese-owned app in data collection:
More than two dozen state government websites contain web-tracking code made by TikTok parent ByteDance Ltd., according to a new report from a cybersecurity company, illustrating the difficulties U.S. regulators face in curtailing data-collection efforts by the popular Chinese-owned app.
A review of the websites of more than 3,500 companies, organizations and government entities by the Toronto-based company Feroot Security found that so-called tracking pixels from the TikTok parent company were present in 30 U.S. state-government websites across 27 states, including some where the app has been banned from state networks and devices. Feroot collected the data in January and February of this year.
[...] Site administrators usually place such pixels on the government websites to help measure the effectiveness of advertising they have purchased on TikTok. It helps government agencies determine how many people saw an ad on the social-media app and took some actionsuch as visiting a website or signing up for a service. The pixels' proliferation offers another vector for data collection beyond TikTok's popular mobile app, which is increasingly under fire in Washington as a possible way for the Chinese government to collect data on Americans.
[...] "Like other platforms, the data we receive from advertisers is used to improve the effectiveness of our advertising services," a TikTok spokeswoman said in a statement. "Our terms instruct advertisers not to share certain data with us, and we continuously work with our partners to avoid inadvertent transmission of such data."
[...] Tracking pixels, also called web beacons, are ubiquitous on commercial websites. The free bits of software code are intended to support digital marketing and advertising by logging a visitor's interactions with the site, such as what is clicked on and the duration of a visit.
Read more of this story at SoylentNews.
06:48
888 On Line Casino Nz $200 Welcome Bonus + 25 Free Spins h+ Media
888 On Line Casino Nz $200 Welcome Bonus + 25 Free Spins
I continuously notice that even when one factor simply isnt very clear on the location, I often know that merely go to the stay chat, Let me positively receive help and it all the time makes me delighted. We instantly treasured that after registration, you get a extra fat bonus. You will find quite a couple of wonderful slots that youll probably not discover encompass casinos. I actually have already withdrawn cash 2 occasions and I can affirm that we now have fast pay-out odds. Since 888Casino is certainly one of the worlds high on line casino sites, they be certain that their worldwide gamers have a extensive variety of both deposit and withdrawal strategies to select from.
This ought to assist you to make decent bets earlier on, which can in flip allow you to to win decent quantities. 888 casino slot games choice is correct there with the most effective slots casinos like LuckyDays and Voodoo Dreams. In addition to their own exclusive slots, you can play traditional slots and jackpot slots like Mega Moolah. 888 received the likes of NetEnt, Electracade, and Merkur Gaming on board. There are a variety of totally different fee methods which you can use to deposit and withdraw at 888 Casino.
This is nice news for gamers from New Zealand because the peak hours are largely based mostly on European occasions. However, even in the course of the sluggish hours, there are hundreds of thousands of real money players. T just apply to money games but in addition to online poker tournaments, for the reason that schedule is at all times packed and the action by no means appears to stop.
Discover amazing offers that will save you cash, solely from 888 Poker. After youve made your first deposit at Europa Casino, youll find a way to acquire a 60% bonus on your 2nd deposit, up to 500 . Make your second single deposit of 20 or extra, and your 2nd Deposit Bonus shall be instantly credited to your account. To obtain your one hundred pc Bonus as a lot as 100 , you need to make your first single deposit into your account.
The autoplay and quick play choices can be convenient, particularly for those of you whore attempting to fulfil bonus wagering necessities. If you are into desk video games, try the Blackjack and Roulette promotions, which occur every day between 1 PM and 1 AM. Finally, loyal gamers will be joyful to learn that your dedication is not going to go unnoticed. Players will earn loyalty factors from the day you make your first deposit. There is also a VIP Scheme that awards members special benefits like personal concierge services, exclusive bonuses and rewards, VIP holidays and invitations to special events, to call a couple of. This is why you will discover pokies and on line casino video games from NetEnt, Red Tiger Gaming, Williams Interactive, and Playn GO on the web site.
Whether that be on the practice to work, r...
06:46
Search Tag On-line On Line Casino Singaporeacebit9 Com On-line Casino Singapore The Most Safe And Trusted Sport Site The Official Trusted Sport Web Site For Mega888, Pussy888 And A Number Of Prime Video Games Min Top Up 10 And Start To Play Customer Service Available 24 7ee h+ Media
Search Tag On-line On Line Casino Singaporeacebit9 Com On-line
Casino Singapore The Most Safe And Trusted Sport Site The Official
Trusted Sport Web Site For Mega888, Pussy888 And A Number Of Prime
Video Games Min Top Up 10 And Start To Play Customer Service
Available 24 7ee
On-line
Casino Singapore The Most Safe And Trusted Sport Site The Official
Trusted Sport Web Site For Mega888, Pussy888 And A Number Of Prime
Video Games Min Top Up 10 And Start To Play Customer Service
Available 24 7ee
888Starz has a massive vary of payment choices that may facilitate payment transactions. The casino offers a hassle-free and instant deposit system, as properly as super-fast withdrawals and excessive payouts. Players can use well-liked cryptocurrencies and benefit from anonymity, security, and velocity.
In phrases of sports activities bets, youll discover that sports activities like football, tennis and basketball tend to get the greatest amount of protection when it comes to betting markets. In addition to this, it must be noted that 888 have taken the time to create a very helpful and informative assist section on their site. You can merely sort in keywords like deposit after which find a good amount of helpful information relating to your chosen matter. All of which should assist present some fair if not exceptional 888 rankings for buyer support. You must also be capable of make withdrawals from as little as $6 for most cost methods, until its a wire transfer that could be from $20 upwards. Most ewallet withdrawals should be processed inside one and two days, while it would take up to five working days for card withdrawals and even one week for wire transfer withdrawals.
This ensures you understand precisely where you stand before you make a transaction with 888. If you are in search of an professional guide to everything on supply at 888 casino then be certain to learn on, as we goal to ship the easiest casino evaluations in NZ. If it is a welcome bonus you dont see reflected in your bankroll balance, it could be as a outcome of you havent yet met the required wagering necessities. All necessities should be met before any of the funds will turn into obtainable.
Fans of sci-fi themes should check out Space Wars that features waggish aliens, Stacked Wild, Respins and the utmost wager measurement of $200 per spin. And do not forget about Gonzos Quest, which has lengthy turn into an iconic basic pokie with millions of performs all over the world. As one might expect from such a critical operator, the web casino offers a extensive selection of pokies. There are some 60 games from NetEnt, 20 pokies from WMS and around 20 video and basic pokies from the rest of the providers. Most 888 Originals (in-house pokies) are additionally suitable with cellular working methods.
Apart from these, the remaining games have a significantly decrease value. Roulette, for instance, has a 20% home edge, whereas baccarat and blackjack have a 10% home edge. In other words, the bonus is unbelievable for slots howev...
06:46
888 On Line Casino Review 2023 888 On Line Casino Free Spins h+ Media
888 On Line Casino Review 2023 888 On Line Casino Free Spins
You will also have entry to free spins, cash bonuses, and Free Play rewards. You additionally get to choose the slot recreation youll play within the contest. With the net slot video games, you will find bonus rounds, free spins, gamble options, and interesting symbols. You can power up and begin taking half in their online slot video games immediately.
With round-the-clock buyer assist and a variety of the most refined information safety know-how, it helps make your visit to a Skrill on line casino a carefree and stress-free journey. We would expect nothing less from a fee methodology that we use and advocate. Established the presence of a license, you will need to spotlight the presence of different entities related with the game world. Independent firms that test on line casino video games to make certain that the payment ratios are reliable . In this way, you do not have to imagine what the casino tells you, as all these knowledge are confirmed by exterior entities. Discover our choice of Skrill casino, one of the popular payment strategies worldwide .
The licensing entities ensure that online casinos comply with frequent and thorough audits, such as RNG exams, that make certain that games are not rigged and that your playing expertise is secure. We are a bunch dedicated to supplying gamers from New Zealand with related information on authorized and regionally targeted on-line casinos in addition to mobile casinos. We have done thorough analysis on all operators we recommend to guarantee that the information conveyed to you is relevant, and for the needs of wagering for leisure wants. 888Casino is amongst the few institutions on the market that gives what can only be termed as a full bodied gaming experience.
Heaps of casino bonuses to be found on 888 Promotions web page of which we notably enjoy the welcome bonus. The minimum deposit to utilize the bonus is 20 NZD$ while wagering contributions of 30x apply. This is fairly low compared with other casinos and definitely one thing to reap the advantages of. Both the bonus itself and the phrases that come with it are very interesting so get probably the most out of it.
The 888 New Zealand casino has a similarly large number of on-line pokies and table games. 888 Casino options the most well-liked games in each category on their web site which makes it simple for model spanking new account holders to know the place to begin. With over 1,000 on-line casino video games available on the positioning, it might be overwhelming for some and this beneficial device makes it simple for model spanking new and experienced gamers to get to know the on line casino.
Thus, you need to discover reference to entities corresponding to iTech Labs or eCOGRA . Your task is to test the video games current in a licensed Skrill casino and promote this information on an exempt foundation. Thus, you already...
06:43
Stoney Nakoda Resort & Casino, Kananaskis h+ Media
Stoney Nakoda Resort & Casino, Kananaskis
Here is an instance of the rewards youll be able to declare as a member of this on line casino. Yes, the classic video games additionally come with some very intriguing variants that change every thing you thought you knew about on-line on line casino video games. With casino online, you get the complete package in gaming expertise. You have a choice of immersing yourself inside the 888 Live Casino arena and the usual Casino side that accommodates all the 888 Casino slots and games. Then there is the 888 Sports enviornment and two specialist sections of the casino handling 888 Poker and 888 Bingo. Now, it is your turn to expertise why 888 Casino is one of the TOP casinos in New Zealand and throughout the remainder of the world.
The fact that its been in the marketplace for therefore a few years is proof that the on line casino is trustable, and if gamblers determine to spend some cash and have enjoyable, they are in secure hands. By entering details throughout the subject you agree to obtain updates from The Athletes Foot on offers and developments in accordance with Terms and Conditions and Privacy Policy. Absolutely, they offer banking via most major credit cards, e-wallets and also, different methods too. For starters, any deposit made via Skrill or NETELLER will be ineligible for the welcome provide. Also, please examine that you just meet the minimal deposit requirement of $20. When creating an account, our group specialists found that the four accepted currencies on the time of writing have been USD, EUR, GBP, and CAD.
This method, the mobile-ready platform can be accessed from all main Android and iOS gadgets. Something we take very significantly at Online Casino NZ, is the bonuses and promotions that an operator presents. These can really assist to fatten your account, so you can play longer and wager more. As you may expect by now, the choice at this establishment is great.
All slots allow you to customise your stake to greatest fit your price range and preferences. The immediate look of 888 Casino exudes luxurious and creates a premium really feel. The 888 Casino website is devoted to slots and live casino so you gainedt need to navigate your means around other merchandise like bingo or sportsbook. We have listed one of the best Skrill casinos with bonuses so as to find a way to simply verify the quantities offered, the requirements and validity. Still, we suggest that at all times verify the phrases and circumstances of any casino offer before you make a deposit. The Paysafe Group stands out as one of many extra strong within the space of on-line payments worldwide.
The selections are countless, so it will be a good idea to check out the promotions part regularly for the newest presents and knowledge. There more than ten of 888 casino games that might be accessed through the cell app and particularly some casino favorites similar to I...
06:30
AMD Linux Graphics Driver Seeing More Patches Around Multi-XCC Support Phoronix
The AMDGPU kernel driver patch flow has ticked up in recent days with working on new hardware support/features...
06:27
Re: polkitd service user privilege separation Open Source Security
Posted by Simon McVittie on Mar 29
On one hand, yes. This makes the privilege separation not actually verypractically useful.
On the other hand, the entire point of polkit is to answer requests from
privileged system services, of the form:
[smcv] wants to [turn off wifi], should I allow this?
(where the parts inside square brackets are examples/placeholders), and
many of the things you can do with those requests are effectively already
root-equivalent. In particular, if...
06:18
How is mLearning the Future of On-The-Go Dynamic Training Programs? HackRead | Latest Cybersecurity and Hacking News Site
By Owais Sultan
The goal of any business is to ensure that its employees remain productive, efficient, and well-informed in their
This is a post from HackRead.com Read the original post: How is mLearning the Future of On-The-Go Dynamic Training Programs?
05:39
How to remove orphaned unused packages in Arch Linux nixCraft
Arch Linux uses pacman command to add or remove packages. It is a package management utility that tracks installed packages on Arch. So when you uninstall or remove packages, some dependencies are left behind, taking up disk space. In this quick tutorial, I will explain how to remove ALL orphaned packages installed as a dependency and no longer required by any package on Arch Linux.
Love this? sudo share_on: Twitter - Facebook - LinkedIn - Whatsapp - Reddit
The post How to remove orphaned unused packages in Arch Linux appeared first on nixCraft.
05:16
OpenAI quickly fixed account takeover bugs in ChatGPT Security Affairs
OpenAI addressed multiple severe vulnerabilities in the popular chatbot ChatGPT that could have been exploited to take over accounts.
OpenAI addressed multiple severe vulnerabilities in ChatGPT that could have allowed attackers to take over user accounts and view chat histories.
One of the issues was a Web Cache Deception vulnerability reported that could lead to an account takeover by the bug bounty hunter and Shockwave founder Gal Nagli.
The expert discovered the vulnerability while analyzing the requests that handle ChatGPTs authentication flow. The following GET request caught the attention of the expert:
https://chat.openai[.]com/api/auth/session
Basically, whenever we login to our ChatGPT instance, the application will fetch our account context, as in our Email, Name, Image and accessToken from the server, it looks like the attached image below Nagli wrote on Twitter detailing the bug.
The expert explained that to exploit the flaw, a threat actor can craft a dedicated .css path to the session endpoint (/api/auth/session) and send the link to the victim. Upon visiting the link, the response is cached and the attacker can harvest the victims JWT credentials and take full control over his account.
05:07
Musk, Experts Urge Pause on AI Systems, Citing Risks to Society cryptogon.com
Leading AGI developers will not heed this warning, but at least it was said Elon Musk (@elonmusk) March 29, 2023 Via: New York Post: Elon Musk is part of a group urging a six-month pause in the training of advanced artificial intelligence models following ChatGPTs rise arguing the systems could pose profound risks []
05:06
Fake Tor Browser Installers Distributing Clipper Malware HackRead | Latest Cybersecurity and Hacking News Site
By Deeba Ahmed
It is yet unclear how these fake Tor browser installations are distributed but there are indications that torrents or third-party sources may be responsible.
This is a post from HackRead.com Read the original post: Fake Tor Browser Installers Distributing Clipper Malware
04:10
NY Officials Detect Polio Again, Warn of Possible Summer Wave SoylentNews
With new detection, officials warn of spring and summer transmission risks:
...Health officials in New York have once again detected poliovirus in wastewater from Rockland County, where a case of paralytic polio occurred last summer.
Wastewater samples from Rockland and several nearby counties were positive for poliovirus for months after the initial case was reported in July, suggesting widespread circulation of the virus in the region.
So far this year, officials have only detected poliovirus in one sample, which was collected from Rockland in February. Two samples from the county taken during March were negative. Before the detection in February, the last positive sample from the region was found in mid-December in Orange County, just north of Rockland. The last positive detection in Rockland was in October.
While the data doesn't suggest that poliovirus is again circulating widely in the region, health officials are wary that the virus could easily restart. Rockland has one of the lower vaccination rates in the state; as of August, only 60.34 percent of 2-year-olds in the county were up to date on their polio vaccinations. Some areas of the county have rates in the 50s.
Officials are concerned about the potential for international spread of polio to Rockland's sizable Jewish community during upcoming holiday travel.
[...] Officials continue pushing for vaccination in parts of the county where anti-vaccine sentiments are high. They're offering free polio boosters at walk-in clinics, working with the Centers for Disease Control and Prevention to audit vaccination coverage at day cares and schools, and trying to improve vaccination messaging.
"It is our obligation to protect all our residents from these debilitating and potentially fatal diseases. The law requiring childhood vaccinations has been in place for many years for this very reason," County Executive Ed Day said. "I urge our residents to act now and protect yourselves, your family, and your community."
04:00
Intel Linux Kernel Optimizations Show Huge Benefit For High Core Count Servers Phoronix
Earlier this month I wrote about Intel engineers working on more big optimizations to the Linux kernel with a focus on enhancing the kernel's performance at high core counts. The numbers shared then were very promising and since then I've had more time looking at the performance impact of Intel's stellar software optimization work and its impact on real-world workloads. Here is a look at how Intel's pending kernel optimization patches are a huge deal for today's high core count servers.
Wednesday, 29 March
22:54
Everything You Should Find Out About Betway Zambia h+ Media
Everything You Should Find Out About Betway Zambia
If youre utilizing an Android-powered system, youll have to modify on the Unknown Sources choice and download the .apk file from the site instantly. The casinos finance group takes about 6 hours to course of the fee request. When approved, you want to withdraw money inside hours, relying on the strategy. It often takes around 24 hours for his or her team to review the paperwork.
As soon as you have an account with Betway, you might make your first deposit and claim the first deposit bonus match. The platform accepts a broad range of fee strategies, together with bank transfers, debit and credit cards, and e-wallets, among others. If youre looking for top betting sites with a lot of prizes and top-tier cricket provides, Betway will be your most suitable option. Everything from IPL to worldwide matches is available right here.
Yes, Betway accepts punters from India, and since its servers are based mostly outside the nation, youll be able to place bets legally with this world-renowned online gambling operator. This is arguably the only facet the place Betway comes up short. Likely as a result of sure iGaming regulations, the Indian version of the casino platform solely options live games.
The sports part options the highlights of the leagues. You can see betting boosts, guess slip, and cash out possibility simply. In order to play and make bets easily, you should understand the location itself. This is so you wouldnt be caught unaware or have any issues as you wager along. Thankfully, Betway has neatly organized the location so you can simply navigate it when you log in. Even in case you are new to online casinos or sportsbooks, you can find your method round.
In addition to this is the ever-exciting three-way Casino Bonus, which offers a 100% matched bonus of up to INR 60,000. To elaborate, the primary deposit offers 100 percent up to INR 15,000, whereas the second deposit offers 25% as a lot as INR 15,000. As for the third deposit, it presents a whopping 50% matched bonus as a lot as INR 30,000. Other bets the positioning offers are the Betway Freebet from the Free wager membership and Power cards that permit you to earn up to INR 3000.
For more snug betting, the bookmaker presents high-quality infographics and a match-center with statistical information. Withdrawal fee strategies also set up minimal limits, which youll study more about on the websites cashier part. The common processing time for withdrawal transactions is seventy two hours, as the sportsbook has to confirm your account and details. Newly registered gamers can immediately claim a welcome provide of a 4,000 matched free bet if their first wager loses. Players who make their first deposit via bank switch can even declare a welcome package of a one hundred pc deposit match up to 2500.
As for withdrawals, create an e-wallet account and your Betway...
22:47
Is Betway Authorized In India? h+ Media
Is Betway Authorized In India?
Or, try Football Studio and Monopoly Live for something slightly different. Live betting is considered one of the most enjoyable components of any on-line bookmaker and Betway allows its users to get pleasure from this characteristic. People often change their minds whereas the match is on and Live Betting opens the doorways of plenty of alternatives as the percentages maintain altering while the match is going on.
DraftKings is certainly one of the legit sportsbooks you can guess on for real cash. The sportsbook offers its clients superb sports betting service with nice evaluations for its banking and buyer help. To conclude, wed like to say that, if not the best, Betway is among the many top-performing on-line betting websites. We highly suggest you give it a attempt to avail one of the best bonuses and provides alongside the extremely competitive match odds.
Information in regards to the quantity, high quality, purity, potency, price, and commonplace of products or services. Zurich , March 24 Narrated by Welsh actor and football fan Michael Sheen, Written within the Stars is the Official Film of the first FIFA World Cup to be held in the Middle East. No information contained on the SevenJackpots.com web site is meant for illegal purposes. This material is for common data only and is not meant as authorized recommendation and no duty of care is owed to any reader. The readers of this materials are requested to have interaction their own authorized counsel so as to make any legal or enterprise choices and to obtain authorized advice particular to them. Betway accepts Indian rupees and will show your account money steadiness in Indian rupees as nicely.
one hundred pc match bonus based on first deposit of 1200+ as much as Rs.15,000. The given personal data corresponding to name, ID details have to be actual and all payments must be made beneath the same name. Your request will show as Confirmed however relying on the withdrawal methodology you select, it could possibly take as much as 5 working days for the cash to reach your account. Has to offer to see how we answered that all-important query of Is Betway reliable?
Betway may also be supporting content material highlighting the work of SORAI (Save our Rhinos Africa & India) which was Kevins brainchild. Founded after he was launched to wildlife preservation when he was taken on a rhino tagging operation. Pietersen has thrown himself into numerous fundraising projects, working with endangered animals in Africa and India.
Winning is nice, and getting paid out in time and in a protected way is even higher. Our payout guide will let you know how to spot casinos with fast payouts. Security is understandably a giant concern for anybody gambling on their cell system. It neednt be although as any cell web site we recommend comes with the highest levels of safety, which means you can gamble with confidence. Of...