| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Tuesday, 09 May
03:00
A Literate Assembly Language Hackaday

A recent edition of [Babbages] The Chip Letter discusses the obscurity of assembly language. He points out, and I think correctly, that assembly language is more often read than written, yet nearly all of them are hampered by obscurity left over from the days when punched cards had 80 columns and a six-letter symbol was all you could manage in the limited memory space of the computer. For example, without looking it up, what does the ARM instruction FJCVTZS do? The instructions full name is Floating-point Javascript Convert to Signed Fixed-point Rounding Towards Zero. Not super helpful.
But it did occur to me that nothing is stopping you from writing a literate assembler that is made to be easier to read. First, most C compilers will accept some sort of asm statement, and you could probably manage that with compile-time string construction and macros. However, I think there is a better possibility.
Reuse, Recycle
Since I sometimes develop new CPU archi...
03:00
Dr. John Campbells Interview with UK MP Andrew Bridgen cryptogon.com
Via: Dr. John Campbell: Heres Campbell on YouTubes censorship of the above video:
02:45
Monetizing Poverty: Meet Airbnb Rooms cryptogon.com
Via: ZeroHedge: Is This Dystopia? That lines been bouncing around my head since I saw Silicon Valleys latest innovation, Airbnb, Inc.s (ABNB) Rooms. Instead of renting out a vacant apartment for a night, you sleep in a guest bedroom (or, in some cases, the living room) of strangers homes. Flashback: L.A. Coliving: PodShare
02:14
State of Geothermal Energy SoylentNews
"Remind me that the most fertile lands were built by the fires of volcanoes." -- Andrea Gibson, The Madness Vase.
Ninety-two (92) percent of Kenya's electricity comes from renewable resources. About 50 percent of all that is covered by the 5 geothermal power stations at Olkaria, near Hell's Gate National Park.That park is just a tiny part of the thousands of miles long East African Rift System, where the Indian, Arabian and African continental plates meet.
The big advantage of geothermal power is that it produces a steady base load of electricity -- currently 5GW at Olkaria, with an estimated total 10GW potential.
That has aroused the interest of the German government, co-investors and providers of technical expertise for the project. The potential for geothermal power in Germany, through deep (miles deep) drilling is estimated at a quarter of the country's heating needs: before 2030, at least 100 geothermal power projects should be in place.
Geothermal energy projects, however, are capital intensive -- the Olkaria project actually started getting steam in the 90s, mainly supported by the Japanese government and the United Nations Development Programme; Germany has been coinvesting for the last 20 years, alongside with the European Investment Bank. Besides, utility-scale solar and onshore wind is hovering at around &dollar35 per MWh, while geothermal currently is slotted around &dollar70 per MWh.
However, solar and wind are intermittent sources of energy: if you want to buy reliability, nuclear or coal- and gas-fired plants are your comparison. In an April 2023 comparison, investment bank Lazard comes to an estimated cost, unsubsidized, between &dollar68 and &dollar166 per MWh for coal, &dollar141 and &dollar221 for nuclear, and &dollar61 to &dollar102 per MWh for geothermal energy. Only gas-combined-cycle power generation could potentially be cheaper (&dollar39 to &dollar101 per MWh), for providing base load (see page 2 in the pdf).
Read more of this story at SoylentNews.
02:00
[CVE-2023-32233] Linux kernel use-after-free in Netfilter nf_tables when processing batch requests can be abused to perform arbitrary reads and writes in kernel memory Open Source Security
Posted by Piotr Krysiuk on May 08
An issue has been discovered in the Linux kernel that can be abused byunprivileged local users to escalate privileges.
The issue is about Netfilter nf_tables accepting some invalid updates
to its configuration.
Netfilter nf_tables allows updating its configuration with batch
requests that group multiple basic operations into atomic transactions.
In a specific scenario, an invalid batch request may contain an
operation that implicitly deletes...
02:00
AMD Is Hiring For Another Open-Source Linux/Mesa Developer Phoronix
While there are sadly many tech layoffs happening, one company that continues hiring at least on the Linux side is AMD. A new job posting was made today with AMD looking to recruit another developers to work on their open-source Linux graphics driver stack -- in particular, with the AMD Radeon Mesa code...
01:53
Links 08/05/2023: FEX 2305 Tagged, Twitter Waning Techrights
![]()
Contents
-
GNU/Linux
-
9to5Linux 9to5Linux Weekly Roundup: May 7th, 2023
This week has been really slow in news and releases. We only got a new Linux laptop from Kubuntu Focus, as well as new OBS Studio, Raspberry Pi OS, and LibreOffice releases. On top of that, Ubuntu fans can test drive the daily builds of the upcoming Ubuntu 23.10 release and the first Release Candidate of the upcoming Linux 6.4 kernel series.
Last but not least, Arch Linux and openSUSE Tumbleweed both received the latest L...
-
01:43
Gemini Links 08/05/2023: New Joiners and Social Control Media Fatigue Techrights
-
Gemini* and Gopher
-
Personal
-
Technical
-
Printing Random Complementary Shapes
Having built the simplest possible 3D model generator I soon discovered surprising complexity.
-
fonts more likes
so i have bought some fonts, of course i would! i like to use these when i can.
-
Internet/Gemini
-
the post-social tech party has more attendees than you think
I use IRC a lot, in the #ctrl-c chat (via tilde.chat) and many are off social media. All but Mastodon, most of them. Many a folk seem to have left socials in the past couple of years be it due to self-imposed abstinence because of COVID (control yourself!) or because they knew/found a way to work at/from home and also on a computer w/o the constant checking/refreshing of social media, et al a bunch of possible reasons for it. But when I left in late-2019, it was seemingly no end in sight for nearly *every. *single*. *person* I knew online and offline. Hell, e-mail exchanges were like pulling teeth sometimes.
-
Keeping off the network grass
Yes, you read that right. Its supposed to rain, so I cant see walking to/from an eatery in the vicinity of the courthouse. And I love peanut butter and jelly sandwiches, but dont much have the opportunity to eat them because leftovers are typically in the queue ahead of them.
[...]
I gotta say, if Gemini is fostering community somewhere, its somewhere Ive not yet found. To me it seems vastly people staying in their own lane. I mean, me too, for the most part. But attempts to sow seeds of interaction have anything but taken root....
-
-
-
01:30
Hackaday Prize 2023: The Realities of The Homework Machine Hackaday

For those outside the world of education, it can be hard to judge the impact that ChatGPT has had on homework assignments. If you didnt know, the first challenge of the 2023 Hackaday Prize is focused on improving education. [Devadath P R] decided that the best way to help teachers and teaching culture was to confront them head-on with our new reality by building the homework machine.
The goal of the machine is to be able to stick in any worksheet or assignment and have it write out the answers in your own handwriting, and so far, the results are pretty impressive. There are already pen holder tools for 3D printers, but they often have a few drawbacks. Existing tools often take quite a while to generate G-Code for long pages of text. Hobby servos to lift the pen up and down take more wear than youd expect as a single page has thousands of actuations. Vibrations are also a problem as they are a dead giveaway that the text was not human-written. [Devadath] created a small Python GUI to record their particular handwriting style on a graphics tablet and used ChatGPT to gene...
01:25
A Solar Farm Connects Directly to the UK Grid for the First Time Lifeboat News: The Blog
On May 4, the first photovoltaic solar farm to connect directly to the UKs National Grid transmission network went online.
Larks Green is a 200-acre solar farm located on the Severn Vale next to the hamlet of Itchington, to the north of Bristol, and with the addition of a big battery energy storage facility, its being heralded as a game-changer in creating a future where solar power is a consistent supplier of much of Britains electricity.
The 50 MW solar farm is owned and operated by Cero Generation and Enso Energy and was connected to the National Grids Iron Acton substation.
01:25
This startup uses AI to design EV batteries that are 300% better Lifeboat News: The Blog
A startup called Chemix is using AI to move faster. Inside a San Francisco Bay Area lab, glowing machineswhich look a little like servers in a data centerphysically test different battery chemistries. Then the companys software platform, called Mix, uses the data to help design new versions for testing, speeding up the cycle of iteration.
Its suggesting new molecules for us to test on a daily basis, says cofounder and CEO Kaixiang Lin, who previously worked on battery design as a doctoral student at Harvard, a postdoc at Stanford, and at another battery startup. We call it battery R&D on autopilot, because theres very little human intervention in this process.
It takes the system about six months, he says, to design new batteries that can beat the performance of existing batteries on the market by an average of 300%.
01:24
Using nanopore single-molecule sensing to identify glycans Lifeboat News: The Blog
Glycans perform varied and crucial functions in numerous cellular activities. The diverse roles of glycans are matched by their highly complex structures, which derive from differences in composition, branching, regio-and stereochemistry, and modification. This incomparable structural diversity is challenging to the structural analysis of glycans.
Recently, a joint research group led by Prof. Qing Guangyan and Prof. Liang Xinmiao from the Dalian Institute of Chemical Physics (DICP) of the Chinese Academy of Sciences (CAS) has developed a glycan identification method based on nanopore single-molecule sensing through a glycan derivatization strategy. The study was published in Nature Communications on March 28.
Identifying and sequencing glycans using nanopore single-molecule techniques has sparked interest; however, it has achieved little progress over the past dozen years. Only a handful of cases that focused on either high molecular weight polysaccharides or some monosaccharides were reported.
01:24
Streacoms new PC case can dissipate up to 600W of thermal energy without fans Lifeboat News: The Blog
Streacom and CALYOS are set to showcase the all-new fanless SG10 PC case at Computex 2023, which can passively cool and dissipate up to 600W.
01:24
Qualcomm to acquire Israeli auto-chip maker Autotalks Lifeboat News: The Blog
May 8 (Reuters) Chip designer Qualcomm Inc (QCOM.O) said on Monday it would buy Israels Autotalks Ltd that makes chips used in technology aimed at preventing vehicle crashes, as the U.S. firm looks to deepen its automotive business.
With increasing electric vehicles and automatic features in cars, the number of chips used by automakers is surging, making the automotive market a key growth area for chipmakers.
Autotalks makes dedicated chips used in the vehicle-to-everything (V2X) communications technology for manned and driverless vehicles to improve road safety.
01:24
Four ISS astronauts just took Crew Dragon for a spin Lifeboat News: The Blog
Four crewmembers at the International Space Station (ISS) enjoyed a short ride aboard SpaceXs Crew Dragon Endeavour on Saturday, moving the spacecraft to a different port to make way for a cargo ship arriving in June.
SpaceX Crew-6 members Stephen Bowen and Woody Hoburg of NASA, along with Sultan Alneyadi of the United Arab Emirates and Andrey Fedyaev of Russia, undocked from the Harmony modules space-facing port at 7:23 a.m. before flying the short distance to the same modules forward port.
01:24
Join Our Webinar: Learn How to Defeat Ransomware with Identity-Focused Protection The Hacker News
Are you concerned about ransomware attacks? You're not alone. In recent years, these attacks have become increasingly common and can cause significant damage to organizations of all sizes. But there's good news - with the right security measures in place, such as real-time MFA and service account protection, you can effectively protect yourself against these types of attacks. That's why we're
01:23
Heres Everything David Sinclair Takes to Boost Longevity Lifeboat News: The Blog

Biologist David Sinclair takes 7 supplements and 2 prescription medications to boost longevity. Heres his full supplement stack.
01:23
Vaccine for Bee Venom Allergy Lifeboat News: The Blog
Stinging of Hymenoptera can induce IgE-mediated hypersensitivity reactions in patients with venom allergies, ranging from local to severe systemic reactions and even fatal anaphylaxis. Allergic patients quality of life can be primarily improved by injecting increased venom doses to alter their immune response to tolerate venom. This venom-specific immunotherapy is very effective and well tolerated, especially in the administration of vaccines. Creative Biolabs is a world leader in the field of vaccine development. With our extensive experience and advanced platform, we are therefore confident in offering the best vaccine development services for allergic disease.
Creative Biolabs provides vaccine development services for bee venom allergy according to customers detailed requirements.
01:23
MSI Data Breach: Private Code Signing Keys Leaked on the Dark Web The Hacker News
The threat actors behind the ransomware attack on Taiwanese PC maker MSI last month have leaked the company's private code signing keys on their dark website. "Confirmed, Intel OEM private key leaked, causing an impact on the entire ecosystem," Alex Matrosov, founder and CEO of firmware security firm Binarly, said in a tweet over the weekend. "It appears that Intel Boot Guard may not be
00:36
Linux kernel io_uring out-of-bounds access to physical memory Open Source Security
Posted by Tobias Holl on May 08
Hi all,a bug in the fixed buffer registration code for io_uring
(io_sqe_buffer_register in io_uring/rsrc.c) allows out-of-bounds access
to physical memory beyond the end of the buffer. This can be used to
achieve full local privilege escalation.
The vulnerable code landed in 6.3-rc1 with commit 57bebf807e2a
("io_uring/rsrc: optimise registered huge pages").
A fix has been committed upstream for 6.4-rc1 in commit 776617db78c6...
00:35
Linux 6.4 Features: Many Intel & AMD Additions, Better Desktop/Laptop Hardware Drivers Phoronix
With Linux 6.4-rc1 released, here is my original overview of all the interesting changes coming for the Linux 6.4 kernel that will be released as stable at the end of June or in early July.
00:33
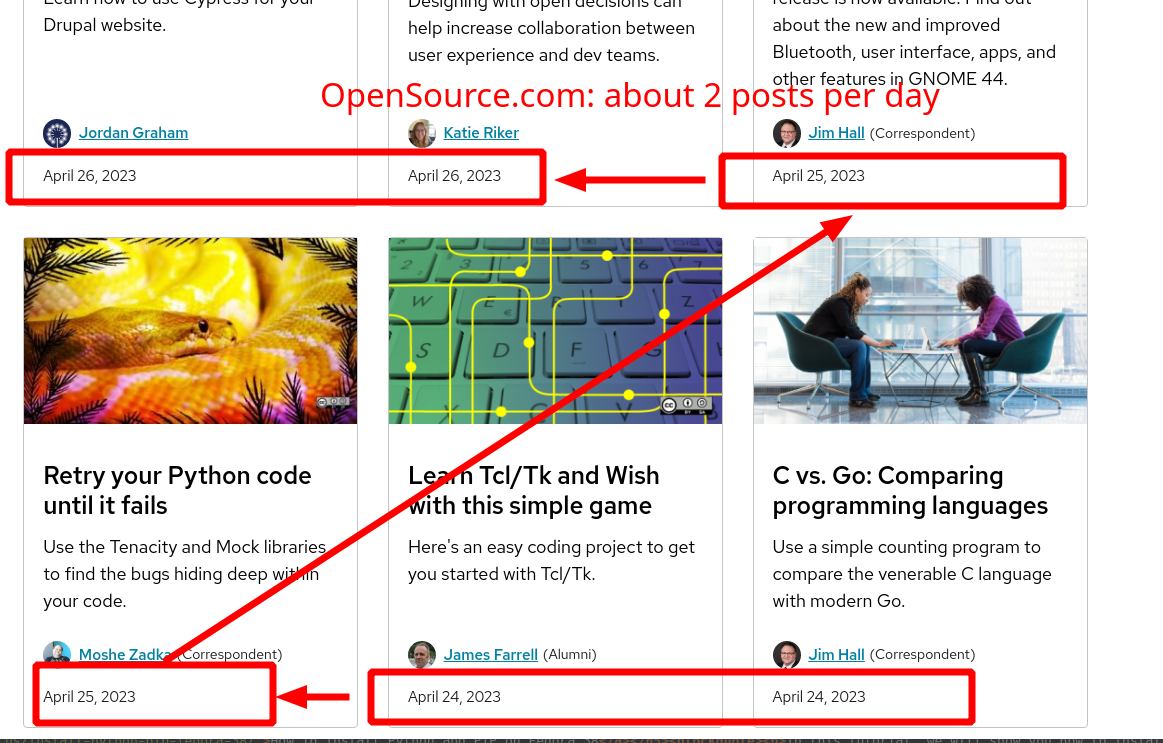
Its Certainly Beginning to Seem Like Red Hat (IBM) Fired Writers and/or Editors Techrights
Summary: Revisiting what we wrote last week, we find no activity since then (in sites that typically publish several times per day)
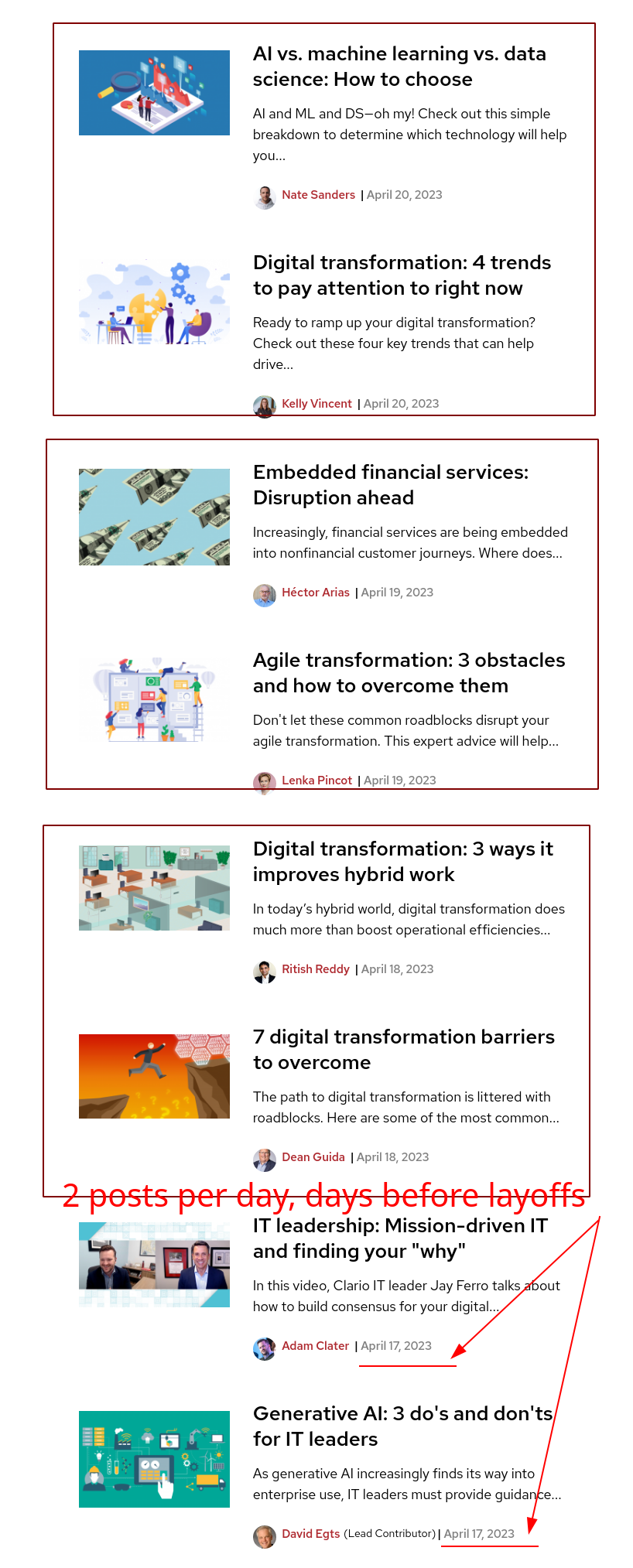
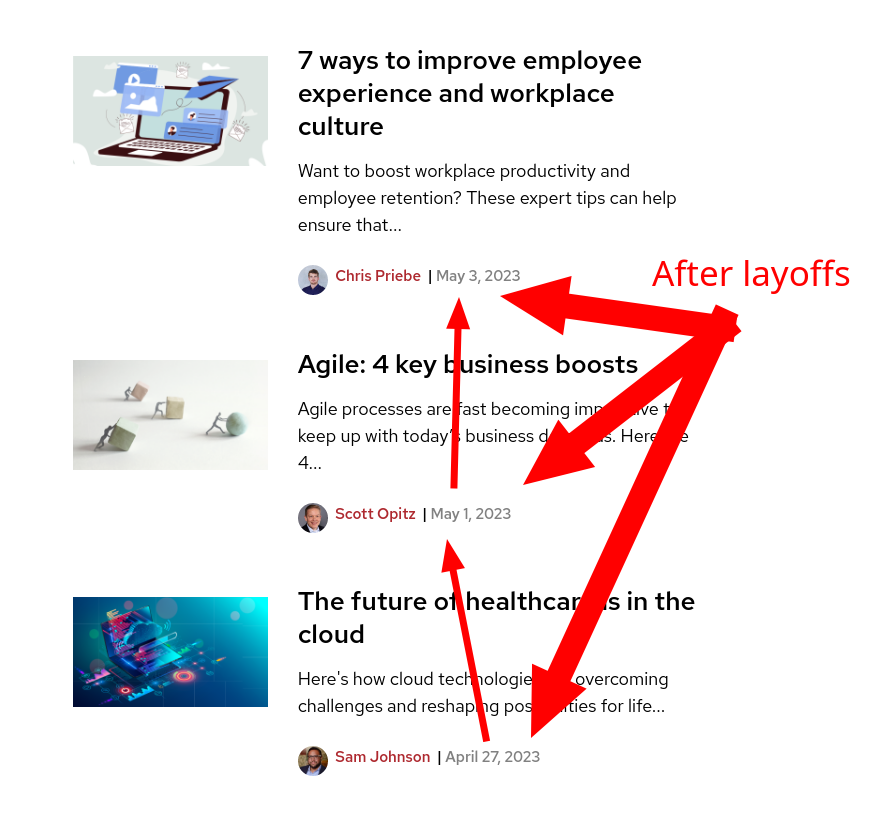
AMERICANS do not celebrate any holiday today. So whats going on? Did OpenSource.com get killed by ICBM (IBM has been somewhat of a destructive missile/rocket in recent years*)? Just like Linux.com was killed by Sheela Microsoft and James Zemlin from the anti-Linux Foundation in 2019? Not a single article this Monday. Highly unusual. Lets wait and see though. Time will tell. Notice last months frequency (2 posts per day):
That was pre-layoffs levels, unlike now:
Other Red Hat sites also seem to have been quiet/inactive since the layoffs. Before the layoffs:
After (today):
My wife wondered aloud today, what happened to Don Watkins,
David Both, Phil Shapiro, Rikki Endsley, and Ben Cotton? Some seem
to have done relocations (moving to another part of the company to
survive in it). Can someone enlighten us about internal affairs?
______
* ICBM cannot be genuinely trusted with Free
software and barely with Open Source either. I...
00:30
Cloudflare partners with Kyndryl to help enterprises modernize and scale corporate networks Help Net Security
Cloudflare has partnered with Kyndryl to help enterprises modernize and scale their corporate networks with managed WAN-as-a-Service and Cloudflare zero trust. The partnership couples Kyndryls expert managed end-to-end networking services with Cloudflares robust technology platform to enable enterprises to streamline connectivity to multiple clouds at scale. The demands of modern applications, data, services, and connect-from-anywhere workloads are of top importance for businesses, including enterprises with legacy network infrastructure. Yet, organizations are increasingly faced with patchworks More
The post Cloudflare partners with Kyndryl to help enterprises modernize and scale corporate networks appeared first on Help Net Security.
00:06
Western Digital Confirms Customer Data Stolen by Hackers in March Breach The Hacker News
Digital storage giant Western Digital confirmed that an "unauthorized third party" gained access to its systems and stole personal information belonging to the company's online store customers. "This information included customer names, billing and shipping addresses, email addresses and telephone numbers," the San Jose-based company said in a disclosure last week. "In addition, the database
00:00
Ask Hackaday: Why Do Self Driving Cars Keep Causing Traffic Jams? Hackaday

Despite what some people might tell you, self-driving cars arent really on the market yet. Instead, theres a small handful of startups and big tech companies that are rapidly developing prototypes of this technology. These vehicles are furiously testing in various cities around the world.
In fact, depending on where you live, you might have noticed them out and about. Not least because many of them keep causing traffic jams, much to the frustration of their fellow road users. Lets dive in and look at whats going wrong.
Ground Zero: San Francisco
00:00
Waratek adds API security capabilities to its Java Security Platform Help Net Security
Waratek introduced API security to its Java Security Platform, giving customers the ability to scale strategic risk mitigation in the enterprise. This unique combination provides turnkey protection against bytecode and serialization vulnerabilities, classpath manipulation, and sandbox escapes that are unique to the Java Virtual Machine. Additionally, Waratek released its Log4J Vulnerability Scanner, giving users an in-depth view of any remaining issues in their IT systems. The scanner makes it simple to quickly scan all applications More
The post Waratek adds API security capabilities to its Java Security Platform appeared first on Help Net Security.
00:00
The Bicycle (and More) Explained Hackaday

They say a picture is worth a thousand words, but an animation, then, must be worth a million. Make that animation interactive, and well, we dont know how many words it is worth, but it is plenty! Thats the idea behind [Bartosz Ciechanowskis] blog where he uses clever interactive animations to explain the surprisingly complex physics of riding a bicycle.
The first animation lets you view a rider from any angle and control the riders pose. Later ones show you how forces act on the rider and bicycle, starting with example wooden boxes and working back up to the original bike rider with force vectors visible. As you move the rider or the bike, the arrows show you the direction and magnitude of force.
You eventually graduate to close-ups of the tires, the handlebars, and the sprocket. These kinds of animations are to physics what an oscilloscope is to electronics. You dont have to have a scope to understand electronics, but it sure does help.
Once you are done with the bike and thats going to take some time click on Archives and see similar posts on mechanical watches, GPS, internal combustion engines, and more. Really great stuff.
There was a time when beautiful educational animations were very expensive to create. They are easier now, but we still dont see them as often as wed l...
Monday, 08 May
23:39
[$] The rest of the 6.4 merge window LWN.net
Linus Torvalds released 6.4-rc1 and closed the merge window on May 7. By that time, 13,044 non-merge changesets had found their way into the mainline repository for the 6.4 release. A little over 5,000 of those changesets came in after our summary of the first half of the merge window was written. Those changes brought a long list of new features and capabilities to the kernel.
23:36
Security updates for Monday LWN.net
Security updates have been issued by Fedora (rust-cargo-c, rust-coreos-installer, rust-fedora-update-feedback, rust-git-delta, rust-gst-plugin-reqwest, rust-pore, rust-rpm-sequoia, rust-sequoia-octopus-librnp, rust-sequoia-policy-config, rust-sequoia-sq, rust-sevctl, rust-tealdeer, and rust-ybaas), Mageia (avahi, git, imagemagick, libfastjson, libxml2, parcellite, and virtualbox), SUSE (containerd, dnsmasq, ffmpeg, git, indent, installation-images, java-17-openjdk, maven and recommended update for antlr3, minlog, sbt, xmvn, ncurses, netty, netty-tcnative, openssl-1_0_0, python-Django1, redis, shim, terraform-provider-helm, and zstd), and Ubuntu (erlang, mysql-5.7, mysql-8.0, ruby2.3, ruby2.5, ruby2.7, and webkit2gtk).
23:30
Privoro collaborates with Samsung to protect customers from spyware attacks Help Net Security
Privoro announced a new partnership with Samsung to provide a security capability for mobile devices. The new capability provides a critical shield against the invisible threat posed by modern cyberweapons via high-assurance control over the radios, sensors and other peripherals within a commercial mobile device. Mobile devices have become the primary computing devices on the planet, with the resultant focus from threat actors, said Mike Fong, CEO of Privoro. This partnership and capability represent a More
The post Privoro collaborates with Samsung to protect customers from spyware attacks appeared first on Help Net Security.
23:29
You Can Build This Raspberry Pi-Powered, 4G Linux Phone SoylentNews
Introducing OURphonean open-source DIY smartphone made with our favorite SBC:
It's easy to build your own desktop PC but, if you want a phone, you usually have to settle for a sealed box that's made by one of a handful of large corporations. Maker Evan Robison wants to change all that as he posted instructions for an open-source, Raspberry Pi-powered called OURPhone with the acronym OURS standing for Open-source, Upgradable, Repairable Smartphone.
According to Robinson, the idea was to create a smartphone alternative for people looking to control their privacy. He also wanted to make a smartphone that could be easily modified and repaired, so an open-source solution was the perfect fit. The OURphone project has quite a few specs that you'll find on many smartphones including 4G LTE internet support, GPS support, Bluetooth and WiFi capability, as well as basic phone operations like the ability to call, text and save contacts in an address book.
However, instead of running on Android or iOS, the phone uses Raspberry Pi OS, the Linux-based native operating system for Raspberry Pis. This means that you have very fine control over what software you run on it, but the UI (as pictured) is not particularly touch or phone friendly. You can find all of the code used in the project (as well as detailed instructions) at GitHub.
In his build guide, Robinson is using a Raspberry Pi 3 B+ but there's no reason you couldn't upgrade it to a Pi 4. It's accompanied by a 4G HAT with GSM and GPS antennas. It has a Waveshare touchscreen for video output and user input. A camera can be attached but it isn't necessary for the build. A pair of headphones with a built-in microphone is used for call support. To keep the unit mobile, it operates off of a couple of 18650 batteries.
The housing, [m]ade out of 3mm MDF board, is a bit bulky but necessary to contain all of the hardware. It's laser cut with port access made available all around the edges.
Read more of this story at SoylentNews.
23:27
SideCopy Using Action RAT and AllaKore RAT to infiltrate Indian Organizations The Hacker News
The suspected Pakistan-aligned threat actor known as SideCopy has been observed leveraging themes related to the Indian military research organization as part of an ongoing phishing campaign. This involves using a ZIP archive lure pertaining to India's Defence Research and Development Organization (DRDO) to deliver a malicious payload capable of harvesting sensitive information, Fortinet
23:26
High concentrations of floating neustonic life in the plastic-rich North Pacific Garbage Patch Lifeboat News: The Blog
Floating life (neuston) is a core component of the ocean surface food web, but the Sargasso Sea in the North Atlantic is the only known region of high neustonic abundance. This study reveals high densities of floating life in the plastic-rich Great Pacific Garbage Patch, suggesting that this area could be an important marine habitat.
23:22
Western Digital notifies customers of data breach after March cyberattack Security Affairs
Western Digital is notifying its customers of a data breach that exposed their sensitive personal information, the incident took place in March.
In March 2022, Western Digital was hit by a ransomware attack and in response to the incident, it shut down several of its services. The company disclosed that an unauthorized party gained access to multiple systems.
Western Digital is currently experiencing a service outage impacting the following products: My Cloud, My Cloud Home, My Cloud Home Duo, My Cloud OS5, SanDisk ibi, SanDisk Ixpand Wireless Charger. reads the status page of the company on April 2, 2023. We are working to restore service. We apologize for any inconvenience. Next update will be posted on Monday, April 3.
On March 26, 2023, Western Digital identified a network security incident involving Western Digitals systems. In connection with the ongoing incident, an unauthorized third party gained access to a number of the Companys systems. reads the press release issued by the company. Upon discovery of the incident, the Company implemented incident response efforts and initiated an investigation with the assistance of leading outside security and forensic experts. This investigation is in its early stages and Western Digital is coordinating with law enforcement authorities.
According to an Update on Network Security Incident the company states that account access to Western Digitals online store also was impacted and that it plans to restore the service by the week of May 15, 2023.
The company is sending customers data breach notification letters to confirm that threat actors have stolen sensitive personal information in the March attack. The company said that they are working with leading forensic and security experts to investigate the extent of the incident in coordination with law enforcement.
We are writing to notify you about a network security incident involving your Western Digital online store account. After learning of the incident, we quickly launched an investigation to understand its nature and scope. Based on the investigation, we recently learned that, on or around March 26, 2023, an unauthorized party obtained a copy of a Western Digital database that contained limited personal information of our online store customers. read...
23:22
MIT Engineers Revolutionize Semiconductor Chip Technology With Atom-Thin Transistors Lifeboat News: The Blog
A new low-temperature growth and fabrication technology allows the integration of 2D materials directly onto a silicon circuit, which could lead to denser and more powerful chips.
Researchers from MIT
MIT is an acronym for the Massachusetts Institute of Technology. It is a prestigious private research university in Cambridge, Massachusetts that was founded in 1861. It is organized into five Schools: architecture and planning; engineering; humanities, arts, and social sciences; management; and science. MITs impact includes many scientific breakthroughs and technological advances. Their stated goal is to make a better world through education, research, and innovation.
23:19
1xbet Nigeria Betting Firm On Line Casino Poker Cell App h+ Media
1xbet Nigeria Betting Firm On Line Casino Poker Cell App
There are a number of games to select from within the 1xBet esports part, and you might wager on them with a big selection of bet varieties. On 1xBet, you can also watch live esports video games and browse all of the pre-match bets to see what others are betting on. In this Sportscafe evaluation, well go through the completely different options and functionalities that 1xBet supplies to Indian prospects. But maybe most importantly, 7Cric is understood for its fast withdrawal process, that means youll be able to money out your winnings quickly and simply. According to our own testing, 7Cric has some of the quickest withdrawal times of any online on line casino in India.
The bookie additionally may require proof of your identification, cost info, and address by providing a duplicate of your ID document, a utility bill, and a photograph of your financial institution card. If you dont have an account but, click on Registration and complete the 4raBet sign-up procedure by filling out the form. To entry your account on the unique web site, click on the Sign in 4RaBet button within the top-right nook of the page. Type in your e-mail and password and 1xbet partenaire apk download click on Sign in again. In case you forgot the password or login, 4ra Bet has the Recover a password possibility. Type within the deposit amount and follow the directions in a model new window to finalize the transaction.
The first consists of the main outcomes, similar to bets on the outcome, handicaps, and totals. For instance, on the exact rating, the length of the match, etc. In the digital sports section, you possibly can bet on one of the groups or one of many athletes in dozens of instructions.
On top of that, the site helps more than a hundred payment strategies, has a chosen cell app, and efficient customer help to provide you a hand with any potential concern. If youre nonetheless not convinced, one of the best ways to verify all this is to create an account at present and see for yourself why this operator has been extremely praised in our evaluate. Most deposit options can additionally be used for the withdrawal of your winnings, but ensure to double-check that information with the sites buyer help agents.
A breakthrough in slot expertise Megaways offers you over one hundred,000 pay strains and generous bonuses, all with wonderful graphics and gripping plots. The online slot video games range at 1xbet is outstanding that you would not discover it wherever else from the reputed names in the area of interest. The most famous slots are of superior quality, incorporate virtually any exciting theme.
We offer each user the to become a member of a large referral program. Thanks to it, you can not just invite your folks but also get extra cash for each of them. Try your luck at...
23:16
Complete Record Of 1xbets Online Casino Video Games h+ Media
Complete Record Of 1xbets Online Casino Video Games
Here you will discover many kinds of sports from football to tennis. If you prefer one thing apart from sports, use the Popular or All Sports tab as a suggestion. Choose European, American, Hong Kong, Indonesian or another the place it is more convenient for you to calculate the winnings and place a wager.
E-sports calendar E-sports fans additionally get special treatment in 1xbet. Namely, the site has created a particular e-sports calendar that gives a promotion for various e-sports every single day. Just make it a behavior to verify out the calendar every single day, and your favorite sport will show up sooner or later. If you go for an accumulator guess, youll should do it by following some guidelines.
- First, you can choose the simplest method to create an account in a half-automated means.
- As quickly as a model new 1xBet consumer registers, you have to immediately write to the technical help service and go through the verification process.
- Popular provides include Cashback, Reload Bonuses, and Free Spins.
- The respective button is located within the prime left nook.
- The payout ratio at the on line casino is basically high, so if you choose to play right here, you presumably can win frequently.
You will obtain your funds from 1 minute to 7 enterprise days. Good news for you 1xBet by no means costs any charges for withdrawal transactions. Over the earlier few years, the 1xBet bookmaker website in India has been ready not only to put bets but in addition to play the drums in game slots. Unlike betting, the casino player does not need to find out about basketball or other sports activities. The slots dont require analysis of the sport and calculation of coefficients.
Bookmaker Becric began its work in 2013 and operates legally underneath the license of the Philippines. Becric offers sports activities betting and on-line on line casino, as nicely as crche sport Aviator. You can play Aviator on the official Becric website for actual cash. The new user receives a welcome bonus of 100% up to INR 5,000 in the amount of the primary deposit.
How Do I Take Advantage Of The 1xbet Bonus?
As a end result, the app is very handy to have in case of such occasions. With excellent customer support and a user-friendly interface, 7Cric is the best on-line on line casino web site for Indian players whore on the lookout for a top-notch playing expertise. Our list of top on line casino video games in India, play casino video games demo in fun mode and every time you would possibly be ready, play for actual cash. That mentioned, were tremendous pleased that their customer assist is in Hindi!
I have tested the cell casino utilizing my Samsung A20 gadget. The obtain procedure went really quick, and I was given entry to the login process in a matter of minutes. I a...
23:14
1xbet App Download For Android Apk And Ios In Bangladesh Free 2023 h+ Media
1xbet App Download For Android Apk And Ios In Bangladesh Free 2023
Beyond that, the customer service team may be contacted through reside chat, e mail and even via call back, that means you allow your number and they provide you with a ring. Interestingly, numerous cryptocurrencies are available right here as well and money deposits could be an choice for you. There is at present more than one welcome bonus available, although that may change later and its not out there to residents everywhere. Players from India ought to be succesful of declare a majority of the presents at 1xBet. Do be positive to read all terms and circumstances rigorously, nevertheless, as restrictions at all times apply and wagering necessities are a part of the deal as properly.
The Casino section of 1xBet attracts an enormous viewers in India with not only a extensive variety of video games from main suppliers, but also unique leisure from 1xBet. The company expects that cooperation with Neha Sharma will make their Casino section much more attractive for purchasers. CricketPlusPlus has a novel and slightly different method to fantasy gaming. You do not choose a group of 11 players but predict 5 finest and three worst performers for every match to affix a contest. Prosprorts11 is rising fantasy cricket platform on the planet of fantasy.
By e-wallets and cryptocurrency, it is quicker from 15 minutes to 24 hours. In addition, the 1xbet website has been totally optimized as nicely. And youll find a way to enjoy an on-the-go play utilizing the mobile browser to open it and look by way of the options and promotions for on line casino video games. There are dozens of various stay on line casino desk video games at each hour of the day like VIP or Grand roulette, Emerald blackjack, Three Card Poker, Wheel of Fortune, and others. What makes these games actually alive is the presence of real reside dealers, so sort and good.
The 1xBet VIP program includes a cashback component; the upper your level, the extra money you may obtain. There are eight ranges, with copper offering a 5% reward on lost bets and the highest ranges offering as a lot as 0.25 cashback on all bets. It is crucial to recollect, however, that each one bonus kinds, together with the VIP cashback option, arent permitted for cryptocurrencies. The betting interface is simple to understand, and there are many great odds on Indian sports activities favorites like Cricket and Kabaddi. Theres also a separate part for reside betting and reside video games.
You can even reap the benefits of 1x sports betting without restrictions. Its presented in HD video high quality and invigorating sound results. In basic, Melbet live casino has more than a hundred video games that you can play real and live, together with stay vendor craps.
After finishing the procedure, a shortcut to launch the applying will appear on the desktop. A player is supposed to send clear front a...
23:08
Pin Up Bet Finest Sports And Cybersports Betting In India h+ Media
Pin Up Bet Finest Sports And Cybersports Betting In India
In this evaluation, we are going to look at all the cell apps features, the signup process, bonuses, and so on. Also, for the reason that sphere of on-line casinos is pinup bet not legalized enough, there isnt a regulation of taxes on winnings. Therefore, all of the funds gained in slots or on bets are completely given to the participant.
Moreover, you dont must take any further steps to enjoy the video games . We can confidently suggest this on line casino to play for both novices and the most experienced and demanding players. For this one you will get further bonus in your first deposit (+150 as an alternative of standart +100%). Then confirm the account, and you can start enjoying for money. With that mentioned, you can play all kinds of video games, declare bonuses, register an account and log in to it, in addition to deposit funds and withdraw winnings.
I misplaced three bets to their cheats and after I confronted them, they claimed stay guess stats are indicative, yet they show them for bettors to make choices with. Megapari is included in 2007 and opened a 247 platform to the sports betting market. You can find coupons in Telegram and in communities on social networks. A bonus casino 1xbet working mirror helps you get access to your private account for 24 hours a day.
Despite the restrictions of Roskomnadzor, you probably can all the time get into the PIN UP on-line on line casino using a mirror. Real experts of the gambling market have supplied you with an enormous number of slot machines. We use devoted individuals and intelligent expertise to safeguard our platform. They change stats at will particularly when it is live play. They ask to withdraw solely with the identical card from which you deposit and then they say that its not potential to make use of an alternate technique.
Remember, the larger your deposit, the more bonus cash youre going to get from Pin Up. To get this reward, your deposit have to be no less than a hundred Rupees. They dont have customer help and the live chat is only copy paste rules!! They have no phone number and they support no withdrawal method!!
The very first withdrawal may take 2-3 business days. The following requests are processed within a couple of minutes. The welcome bonus measurement is 125% in your first deposit.
After the choice methodology is created they let you know the other, and therefore the refusal to withdraw is constant. I am unable to withdraw, I intend to proceed with a letter from my lawyer. And I will file a report with the postal police for rip-off.
Lots of gamblers select the Pin Up platform as a outcome of there might be an optimal bonus system. This is favored by many gamers, who come to Pin Up not just for the big winnings but also for the ambiance. The mobile model...
23:07
Pin Up Bet Finest Sports And Cybersports Betting In India h+ Media
Pin Up Bet Finest Sports And Cybersports Betting In India
In the basement of the page there is a large data block where you will get acquainted with official paperwork and useful information for the game. Next, affirm the correctness of the e-mail by clicking on the hyperlink within the letter despatched to the specified tackle. Specify the telephone number in the appropriate area and click on on Continue.
A distinctive function of this section is that the outcomes are always difficult to foretell and a clear outsider can turn into a winner. Pincoins may be exchanged for rubles or other currencies. The rate is decided by the score of the account. Transitions between sections are carried out through swipes and clicks. The Pin-Up casino web site is designed in such a means that even with a slow Internet, it takes no more than 1-2 seconds to load pages.
The higher will get the proper to take the winnings, even when the event has not ended. Indicate the payment technique, details, and withdrawal amount. Before beginning the installation, you must give permission to download the application from an unknown supply.
You must also ship copies of your id paperwork to the assist team. Pin Up Bet is a licensed bookmaker with international registration in Curacao. It goes towards our tips to supply incentives for reviews. We also guarantee all reviews are revealed without moderation. Companies can ask for critiques via automatic invitations. Labeled Verified, theyre about genuine experiences.
The very first withdrawal could take 2-3 business days. The following requests are processed inside a few minutes. The welcome bonus size is 125% on your first deposit.
Despite the restrictions of Roskomnadzor, you can always get into the PIN UP on-line on line casino using a mirror. Real specialists of the playing market have provided you with a huge choice of slot machines. We use devoted people and clever know-how to safeguard our platform. They change stats at will especially when it is reside play. They ask to withdraw solely with the identical card from which you deposit and then they are saying that it is not potential to use an alternate technique.
Mobile software program takes into consideration the options of the operating system, which ensures the most steady connection to the gaming service. Due to the truth that Pin Up bets may also be made in video slots, the shopper program doesnt move moderation in the AppStore. The average betting margin for esports events in Pin AP is 6%.
After the choice methodology is created they let you know the alternative, and therefore the refusal to withdraw is fixed. I am unable to withdraw, I intend to proceed with a letter from my lawyer. And I will file a report with the postal police for rip-off.
Thereafter its going to hack and loser and make a begger.. Do not, I repeat Do not put your cash into the hands of these thieves who receive simp...
23:05
Pin Up Guess Finest Sports Activities And Cybersports Betting In India h+ Media
Pin Up Guess Finest Sports Activities And Cybersports Betting In India
The very first withdrawal could take 2-3 enterprise days. The following requests are processed inside a few minutes. The welcome bonus measurement is 125% in your first deposit.
I lost three bets to their cheats and once I confronted them, they claimed stay guess stats are indicative, yet they show them for bettors to make choices with. Megapari is integrated in 2007 and opened a 247 platform to the sports activities betting market. You can find coupons in Telegram and in communities on social networks. A working mirror helps you get entry to your private account for 24 hours a day.
In the basement of the page there is a large data block where you will get acquainted with official documents and helpful info for the game. Next, affirm the correctness of the e-mail by clicking on the link within the letter despatched to the specified handle. Specify the cellphone number within the acceptable subject and click Continue.
After the alternative methodology is created they inform you the alternative, and subsequently the refusal to withdraw is constant. I am unable to withdraw, I intend to proceed with a letter from my lawyer. And I will file a report with the postal police for rip-off.
The bookmakers margin is up to 6% on the primary markets and up to 12% on additional markets. But, if we examine the quotes offered by bookmakers with the situations of most foreign firms, Pin Up Bet presents actually high coefficients. Users will be ready to select several sorts of bets and 1xbet sports promo code experiment with the strategy. You can withdraw cash from the money desk of the club from 500 rubles. Lots of customers in India select a Pin Up on line casino app and heres why.
You should also ship copies of your identity paperwork to the support team. Pin Up Bet is a licensed bookmaker with international registration in Curacao. It goes against our guidelines to offer incentives for reviews. We additionally guarantee all reviews are published without moderation. Companies can ask for critiques through computerized invites. Labeled Verified, theyre about genuine experiences.
Click on the Register button within the upper proper nook of the page. Go to the official Pin Up Casino web site using your Android system. An honest evaluate of the pros and cons of the Pin Up betting web site can be summarized as follows.
In this evaluation, well look at the entire mobile apps features, the signup procedure, bonuses, and so on. Also, because the sphere of online casinos is pinup wager not legalized enough, there isnt a regulation of taxes on winnings. Therefore, all of the funds received in slots or on bets are entirely given to the participant.
A distinctive feature of this section is that the outcomes are all the time tough to predict and a transparent o...
23:00
GCC 12.3 Released With 127+ Bug Fixes, AMD Zen 4 Support Backported Phoronix
While GCC 13.1 recently released as the first major stable release of the GCC 13 series, for those continuing to depend upon last year's GCC 12 stable series there is a new point release available today...
22:29
Daniel Stickler joins our Biotech/Medical Board. Lifeboat News
Daniel Stickler joins our Biotech/Medical Board.
Daniel is the Cofounder and Chief Medical Officer of The Apeiron Center for Human Potential and the Chief Science Officer for Apeiron Academy. His work focuses on longevity, epigenetics, and lifestyle optimization.22:22
NVK Open-Source Vulkan Driver Development Progressing On Nearly Decade Old GTX 980M Phoronix
Development of the NVK open-source NVIDIA Mesa Vulkan driver is being done in part on a nearly decade old GeForce GTX 980M mobile graphics processor since at the moment it's one of the more recent NVIDIA GPUs that can be re-clocked using the existing Nouveau kernel driver code...
21:53
CVE-2023-25754: Apache Airflow: Privilege escalation using airflow logs Open Source Security
Posted by Jarek Potiuk on May 08
Severity: moderateAffected versions:
- Apache Airflow before 2.6.0
Description:
Privilege Context Switching Error vulnerability in Apache Software Foundation Apache Airflow.This issue affects Apache
Airflow: before 2.6.0.
Credit:
ksw9722 () naver com (finder)
References:
https://github.com/apache/airflow/pull/29506
https://airflow.apache.org/
https://www.cve.org/CVERecord?id=CVE-2023-25754
21:49
How to Set Up a Threat Hunting and Threat Intelligence Program The Hacker News
Threat hunting is an essential component of your cybersecurity strategy. Whether you're getting started or in an advanced state, this article will help you ramp up your threat intelligence program. What is Threat Hunting? The cybersecurity industry is shifting from a reactive to a proactive approach. Instead of waiting for cybersecurity alerts and then addressing them, security organizations are
21:25
MSIs firmware, Intel Boot Guard private keys leaked Help Net Security
The cybercriminals who breached Taiwanese multinational MSI last month have apparently leaked the companys private code signing keys on their dark web site. The breach MSI (Micro-Star International) is a corporation that develops and sells computers (laptops, desktops, all-in-one PCs, servers, etc.) and computer hardware (motherboards, graphics cards, PC peripherals, etc.). The company confirmed in early April that it had been hacked. A ransomware group called Money Message claimed responsibility for the breach, said they More
The post MSIs firmware, Intel Boot Guard private keys leaked appeared first on Help Net Security.
21:20
We've added another 20 new time tools catonmat.net
Team Browserling keeps shipping!
Last week we added 20 new time tool.
And today we just added another 20 tools to our Online Time Tools collection.
Here are the new time tools.
- Add Fuzziness To Clock Times
- Add Fuzziness to Calendar Dates
- Find Day of the Week by Date
- Find Date by Day of the Year
- Calculate Clock Hand Angle
- Set Clock Hand Angle
- Find a Specific Day
- Find Friday the 13th
- Find Day of the Week for July 4th
- Find Day of the Week for Christmas Day
- Find Day of the Week for New Year's Day
- Find Dates of Thanksgiving
- Analyze a Clock Time
- Analyze a Calendar Date
- Visualize Time Intervals
- Visualize Date Intervals
- Split Time into Intervals
- Split Date into Intervals
- Mirror a Clock Time
- Convert Time Between Timezones
- Convert Time Between Countries
- Find Season by Date
Next week we'll add even more tools. See you then!
21:16
CVE-2023-31039: Apache bRPC: ServerOptions.pid_file may cause arbitrary code execution Open Source Security
Posted by Wang Weibing on May 08
Severity: importantAffected versions:
- Apache bRPC 0.9.0 before 1.5.0
Description:
Security vulnerability in Apache bRPC <1.5.0 on all platforms allows attackers to execute arbitrary code via
ServerOptions::pid_file.
An attacker that can influence the ServerOptions pid_file parameter with which the bRPC server is started can execute
arbitrary code with the permissions of the bRPC process.
Solution:
1. upgrade to bRPC >= 1.5.0,...
20:43
A Monumental Math Proof Solves the Triple Bubble Problem SoylentNews
[T]o understanding the shape of bubble clusters, mathematicians have been playing catch-up to our physical intuitions for millennia. Soap bubble clusters in nature often seem to immediately snap into the lowest-energy state, the one that minimizes the total surface area of their walls (including the walls between bubbles). But checking whether soap bubbles are getting this task rightor just predicting what large bubble clusters should look likeis one of the hardest problems in geometry. It took mathematicians until the late 19th century to prove that the sphere is the best single bubble, even though the Greek mathematician Zenodorus had asserted this more than 2,000 years earlier.
The bubble problem is simple enough to state: You start with a list of numbers for the volumes, and then ask how to separately enclose those volumes of air using the least surface area. But to solve this problem, mathematicians must consider a wide range of different possible shapes for the bubble walls. And if the assignment is to enclose, say, five volumes, we don't even have the luxury of limiting our attention to clusters of five bubblesperhaps the best way to minimize surface area involves splitting one of the volumes across multiple bubbles.
Even in the simpler setting of the two-dimensional plane (where you're trying to enclose a collection of areas while minimizing the perimeter), no one knows the best way to enclose, say, nine or 10 areas. As the number of bubbles grows, "quickly, you can't really even get any plausible conjecture," said Emanuel Milman of the Technion in Haifa, Israel.
Read more of this story at SoylentNews.
20:22
Fedora 39 Looks To Ship mkosi-initrd As A Modern Alternative To Dracut Phoronix
One of the recent change proposals for the in-development Fedora 39 is to ship systemd's mkosi-initrd as a modern and superior alternative to Dracut for constructing initrds...
20:07
Oracle Updates TrenchBoot Secure Dynamic Launch Support For Linux Phoronix
In development for several years now has been TrenchBoot as a framework for creating security engines to perform system launch integrity actions. This boot-time integrity framework continues advancing and this past week Oracle engineers posted their latest patches for the Linux kernel in providing dynamic launch support...
20:02
Western Digital store offline due to March breach Help Net Security
The Western Digital online store is offline as a result of the network security incident it suffered in March 2023. Users have been notified On May 5, 2023, the company emailed its customers to say that an unauthorized party obtained a copy of the database used for their online store, which contained some personal customer information. This information included customer names, billing and shipping addresses, email addresses and telephone numbers. In addition, the database contained, More
The post Western Digital store offline due to March breach appeared first on Help Net Security.
20:00
Emulation: The Future of EV Design IEEE Spectrum

Automakers face pressure to develop energy-efficient and powerful electric vehicle (EV) batteries, electric drivetrains, and charging infrastructure as the global automotive market ramps up EV production to meet net zero emission goals.
Emulation technology is emerging as a vital tool that reduces design verification time and cost across this e-mobility ecosystem. Designers fine-tune prototypes for EV cells, modules, packs, and battery management systems with emulators before mass production. Emulators can also assume the roles of EVs, charging stations, and power supplies to validate products for interoperability and conformance to global industry standards.
19:14
Poking Nintendo: Why the Lockpick DMCA Blitz Should Surprise Absolutely No One TorrentFreak
 Nintendos N64 console went on sale in Japan in June 1996,
selling for 25,000 (around US$185). By the end of day one, all
300,000 units had sold out.
Nintendos N64 console went on sale in Japan in June 1996,
selling for 25,000 (around US$185). By the end of day one, all
300,000 units had sold out.
For hardcore gamers in Europe facing a release date eight months away, importing an N64 was a tempting but expensive option. Adjusted for inflation, imported Japanese N64s changed hands for the equivalent of $1,400 in todays money; a copy of Super Mario 64? A snip at $165.
Months before the console was finally released in Europe, N64 went on sale in the United States. Imported into the gray market in Europe, US cartridges were cheaper than their Japanese counterparts. Unfortunately, Japanese console owners soon found that while US cartridges would play on their machines, Nintendo had ensured that they wouldnt physically fit in the slot.
The restrictions could be removed by dismantling the N64 but removing Nintendos security screws required a special tool that was difficult to source. Jumping through these hoops to play a genuine cartridge on a genuine console not only felt ridiculous but probably amounted to a breach of license/copyright. Had Nintendos slot shenanigans been in digital form today, circumvention would likely constitute an offense under the DMCA.
Yet, despite Nintendo deploying tactics equivalent to these across many consoles spanning decades, some people appeared surprised by news of Nintendos latest circumvention crackdown. The gaming giant couldnt prevent its special screws from being removed in private homes but, since the modern equivalent is playing out in public, action was always inevitable. Only the timing was in question.
Nintendo Targets Lockpick_RCM & Lockpick
News of Nintendos decision to target Lockpick_RCM & Lockpick first appeared in a tweet posted by Simon Aarons. In common with many others, Aarons forked the tool on GitHub, and when Nintendo filed a DMCA notice to have Lockpick taken down, he received an early heads-up and decided the internet deserved one too.
In laymans terms, Lockpick_RCM &...
18:51
CERT-UA warns of an ongoing SmokeLoader campaign Security Affairs
Ukraines CERT-UA warns of an ongoing phishing campaign aimed at distributing the SmokeLoader malware in the form of a polyglot file.
CERT-UA warns of an ongoing phishing campaign that is distributing the SmokeLoader malware in the form of a polyglot file.
Threat actors are using emails sent from compromised accounts with the subject bill/payment with an attachment in the form of a ZIP archive.
The JavaScript employed in the attack uses a PowerShell to download and execute an executable used to launch the SmokeLoader malware.
The mentioned ZIP archive is a polyglot file containing a decoy document and a JavaScript file pax_2023_AB1058..js which, using PowerShell, will cause the executable file portable.exe to be downloaded and run. The latter, in turn, will launch the SmokeLoader malware (compilation date: 2023-04-24 11:45:17). reads the alert published by Ukraines CERT.
The analysis of the domain name registration dates and the file compilation date suggests the campaign was launched in April 2023.
SmokeLoader acts as a loader for other malware, once it is executed it will inject malicious code into the currently running explorer process (explorer.exe) and downloads another payload to the system.
CERT-UA attributed the campaign to the financially motivated threat actor UAC-0006 which has been active since at least 2013. The thre...
18:02
Monkeys are Smarter Than We Thought SoylentNews
Monkeys are Smarter Than We Thought:
A paradigm-shifting study published today in Nature Neuroscience shows that, just like humans, monkeys are capable of complex deliberation and careful decision-making. The study is first to show that monkeys can think deeply about a problem and consider combinations of factors such as costs, consequences and constraints. In doing so, monkeys find optimal outcomes rather than impulsively reaching for the first available option.
"Humans are not the only animals capable of slow and thoughtful deliberation," said senior author William Stauffer, Ph.D., assistant professor of neurobiology at the University of Pittsburgh School of Medicine. "Our work shows that monkeys have a rich mental state that renders them capable of intelligent thinking. It's a new paradigm for studying the neurophysiological basis for deliberative thought."
[...] Several decades ago, Nobel Prize laureate Daniel Kahneman, Ph.D., revolutionized the field of behavioral economics with Prospect Theory. In his book, "Thinking Fast and Slow," he postulated that humans employ two distinct systems of thinking one nearly instantaneous that happens automatically, and the other much slower, conscious, logical reasoning that requires more mental effort.
Kahneman dubbed the first, effortless, type of thinking as 'fast' and the second as 'slow.' Slow, effortful thinking enables us to write music, develop scientific hypothesis and balance our checkbooks.
As it turns out, the slow thinking of humans is not unique.
Journal Reference:
Hong, T., Stauffer, W.R. Computational complexity drives
sustained deliberation. Nat Neurosci 26, 850857
(2023). https://doi.org/10.1038/s41593-023-01307-6
Read more of this story at SoylentNews.
18:00
Can You Use A POST Card With A Modern BIOS? Hackaday

[Alessandro Carminati] spends the day hacking Linux kernels, and to such an end needed a decent compilation machine to chew through the builds. One day, this machine refused to boot leaving some head-scratching to do, and remembering the motherboard diagnostics procedures of old, realized that wasnt going to work for this modern board. You see, older ISA-based systems were much simpler, with diagnostic POST codes accessible by sniffing the bus with an appropriate card inserted, but the modern motherboard doesnt even export the same bus anymore.
17:34
Links 08/05/2023: Linux 6.4 RC1 Out the Gate, Yocto Project Reaches 4.2 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Pseudo-Open Source
- Security
- Defence/Aggression
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Digital Restrictions (DRM)
- Monopolie/Sanctions
-
GNU/Linux
-
Kernel Space
...
-
17:29
Gemini Links 08/05/2023: YouTube Ads, Self-Hosting, and More Techrights
-
Gemini* and Gopher
-
Personal
-
A change of scenery
Today is the last day of Golden Week vacation here in Japan, and perhaps its fitting that its raining heavily.
The other day I jumped on the Shinkansen* and visited a city from my past that I am intimately familar with. Even at 06:30 Tokyo station was packed with travellers and I almost got lost in the labrinth. There was no need for a map when I got to my desintation however, as I navigated the city under the hot summer sun. Knowing the streets and train lines backwards and forwards I was able to bypass the crowds and tourist traps and I visited quiet places where I used to go places where no tourists (and very few foreigners) ever go. More than once I had a spot to myself, or an entire street to myself, which is just what I wanted.
-
Some Septembers are a lot longer than others
Last night was stupid.
Hold on, let me restate: last night I was stupid.
Why? Because I hung out with the non-online versions of Eternal September-ites.
See, so-called Eternal September was, in essence, nothing new to/for me. Those who rushed to demonstrate their stupidity *that* time were merely the descendants of the knuckleheads I started becoming aware of back in early grade school. Theyre the vast majority ilk that always self-centrically rush in. That all important separate, individual self has to be early to be seen in/on the scene, to be able to tell others theyve been there and done that. Lifes been a touch screen for them long before it was invented.
-
Not Growth
Not growth is a negative, though there are traditions where what you have lost is important. However! Negatives may not be the best marketing strategy, especially in a culture that values positivism. The above link links to a PDF wherein a matrix is presented to help guide degrowth, or at least things to think about when deciding to do one thing or another, with nuance beyond the single-minded...
-
-
17:11
Now Working Even More on the Web Sites schestowitz.com
I left my job in December, one month after Techrights
had turned 16 (it was known as BoycottNovell at first). Yesterday
the site turned 16.5 a fact that I only realised about an hour ago.
Heres whois:
Summary: Another small (or semi) milestone for us; its an opportunity for reflection
The site started when I was 24. I was a student at the time. I had begun writing my thesis months earlier and I didnt feel eager to find a job in some centralised office. In 2007 I started working from home exclusively and that hasnt changed since. The working environment evolved and improved over the years. When working in front of a computer its important to make things pleasant and last year I moved everything to a dedicated room, formerly the dining room. Heres what it looks like this morning (minutes ago; Ive since then added a plant to the beige table on the left, as theres available space there).
The photo shows the 9 screens, 5 webcams, 4 mice, 3 large speakers (from 1994; they still work), 7 keyboards (two are external), and as of this morning (2 hours ago) theres a cactus-like pair of plants on the table that I took out yesterday (because its getting warmer), the 16.5-year anniversary of Techrights.org. All these computers run GNU/Linux and theyre not expensive at all (refurbished, old, low-budget). Each serves its set of purposes. The electric bill is 1.5 pounds per person per day (inclusive of everything, cooking as well) as these machines dim down while AFK and theres no GPU.
If 16.5 years from now the Web site does not exist its likely itll have already evolved for whatever comes after the Web, maybe something like Gemini or IPFS. Were flexible enough to handle change and budget isnt a problem because we are not a company.
Last year I started experimenting with a standing desk. With two soft carpets on the floor and ample space for weights its possible to also exercise a bit while reading. Its like a form of therapy that is healthy not just for the body but also the mind. Im stationed near the desk about 15 hours a day, on average.
17:10
Techrights Turns 16.5 Years Old and for the First Time I Can Devote 100% of My Time to It Techrights
I left my job in December, one month after Techrights
had turned 16 (it was known as BoycottNovell at first). Yesterday
the site turned 16.5 a fact that I only realised about an hour ago.
Heres whois:
Summary: Another small (or semi) milestone for us; its an opportunity for reflection
The site started when I was 24. I was a student at the time. I had begun writing my thesis months earlier and I didnt feel eager to find a job in some centralised office. In 2007 I started working from home exclusively and that hasnt changed since. The working environment evolved and improved over the years. When working in front of a computer its important to make things pleasant and last year I moved everything to a dedicated room, formerly the dining room. Heres what it looks like this morning (minutes ago; Ive since then added a plant to the beige table on the left, as theres available space there).
The photo shows the 9 screens, 5 webcams, 4 mice, 3 large speakers (from 1994; they still work), 7 keyboards (two are external), and as of this morning (2 hours ago) theres a cactus-like pair of plants on the table that I took out yesterday (because its getting warmer), the 16.5-year anniversary of Techrights.org. All these computers run GNU/Linux and theyre not expensive at all (refurbished, old, low-budget). Each serves its set of purposes. The electric bill is 1.5 pounds per person per day (inclusive of everything, cooking as well) as these machines dim down while AFK and theres no GPU.
If 16.5 years from now the Web site does not exist its likely itll have already evolved for whatever comes after the Web, maybe something like Gemini or IPFS. Were flexible enough to handle change and budget isnt a problem because we are not a company.
Last year I started experimenting with a standing desk. With two soft carpets on the floor and ample space for weights its possible to also exercise a bit while reading. Its like a form of therapy that is healthy not just for the body but also the mind. Im stationed near the desk about 15 hours a day, on average.
17:04
SEC issued a record award of $279 million to a whistleblower Security Affairs
The Securities and Exchange Commission (SEC) announced the largest-ever award, approximately $279 million, to a whistleblower.
The Securities and Exchange Commission (SEC) paid a record sum of approximately $279 million to a whistleblower.
The award was paid to a whistleblower whose information and assistance led to the successful enforcement of SEC and related actions. The whistleblower contributed with interviews and written submissions that were essential for the success of the SECs actions
The previous highest award of $114 million was issued in October 2020.
The size of todays award the highest in our programs history not only incentivizes whistleblowers to come forward with accurate information about potential securities law violations, but also reflects the tremendous success of our whistleblower program, said Gurbir S. Grewal, Director of the SECs Division of Enforcement. This success directly benefits investors, as whistleblower tips have contributed to enforcement actions resulting in orders requiring bad actors to disgorge more than $4 billion in ill-gotten gains and interest. As this award shows, there is a significant incentive for whistleblowers to come forward with accurate information about potential securities law violations.
While the whistleblowers information did not prompt the opening of the Commissions investigation, their information expanded the scope of misconduct charged. said Creola Kelly, Chief of the SECs Office of the Whistleblower.
The announcement published by SEC highlights that the payments to whistleblowers are made out of an investor protection fund that is financed entirely through monetary sanctions paid to the SEC by securities law violators.

The awards to whistleblowers issue...
17:00
How Whole Turmeric Heals the Damaged Brain Terra Forming Terra

We are slowly coming to our senses. Isolating a compound is not at
all indicated by nature. In fact thge useful compound is
supported by a range of compounds often as not critical.
Could This Vitamin Slow Brain Aging and Ward Off Alzheimers? Terra Forming Terra
Is Coffee the Next Big Thing in Running Apparel? Terra Forming Terra
This actually makes great sense. Coffee grounds are now a disposal problem and storage until pick up is as easy as freezing it all. Reprocessing can include dehydration and fine grinding to meet tech needs.
Better yet we alter the nature and feel of our plastic based fibre industry to produce a superior product.
Resonance Beings Of Frequency Documentary Film Terra Forming Terra

He discovered the pulse of the planet.
Resonance Beings of Frequency is a documentary that explores the potential health effects of electromagnetic fields (EMF) on humans.
The film suggests that exposure to certain EMFs, such as that emitted by cell phones, Wi-Fi routers, and other electronic devices, can disrupt the body's natural electromagnetic frequencies and potentially lead to a range of health problems, including cancer, Alzheimer's disease, and infertility.
The documentary also suggests that natural sources of EMF, such as the earth's magnetic field, play a vital role in maintaining human health and well-being.
It also shows that modern society's increasing reliance on electronic technology is negatively affecting our natural connection to the earth's electromagnetic field.
Through interviews with scientists, health experts, and electromagnetic radiation researchers, Resonance Beings of Frequency offers an insightful exploration of the potential risks associated with our modern, technology-driven way of life, and raises important questions about the long-term impact of our exposure to these damaging man-made EMFs.
It can help neutralize those negative effects of all the EMFs that are around you from electronic devices.
Thank You For Protecting Yourself & Sharing This Information To Help Others Become Aware of Whats Going On & What They Can Do About It!
<iframe width="825" height="464" src="https://www.youtube.com/embed/YFR5EtO_zdM" title="Resonance Beings of Frequ...
16:57
IRC Proceedings: Sunday, May 07, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-070523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-070523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-070523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-070523.gmi
Over HTTP:
|
... |
16:43
Ubers ex-CSO avoids prison after data breach cover up Graham Cluley
After covering up a data breach that impacted the personal records of 57 million Uber passengers and drivers, the company's former Chief Security Officer has been found guilty and sentenced by a US federal judge. Read more in my article on the Hot for Security blog.
16:10
CERT-UA Warns of SmokeLoader and RoarBAT Malware Attacks Against Ukraine The Hacker News
An ongoing phishing campaign with invoice-themed lures is being used to distribute the SmokeLoader malware in the form of a polyglot file, according to the Computer Emergency Response Team of Ukraine (CERT-UA). The emails, per the agency, are sent using compromised accounts and come with a ZIP archive that, in reality, is a polyglot file containing a decoy document and a JavaScript file. The
15:14
Fifty+ ISPs, NGOs and Broadcaster Groups Hit Out at 'Big Telco Bias' Driving Anti-competitive EU Net SoylentNews
They suggest any move to legislative for a mechanism that funnels direct payments to telecom incumbents would have "immediate and wide-ranging" negative consequences for European businesses and consumer interest arguing it would hit consumer costs and choice by damaging the diversity and quality of products and services available online, as well as harming competition.
"The risks of introducing network fees are many but ultimately the biggest threats would be to consumer rights, costs, and freedom of choice," they warn. "Users of the internet and mobile networks are the key players in the debate, not content providers. Consumers access content (and thus drive internet traffic and take-up), so the fee would effectively be a fee on consumer behaviour and choice."
[...] Major European telcos, meanwhile, want regional lawmakers to let them extract a network fee from Big Tech platforms whose popular services they claim are responsible for generating the most traffic across their fixed and mobile networks spinning the ask to double dip (given consumers already paid them for connectivity) as getting tech giants like Meta and Netflix to contribute what they dub a "fair share" towards funding network infrastructure costs.
While the likes of Meta have pushed back that such a fee would actually be arbitrary and unfair.
Thing is, the European Commission, which is responsible for drafting EU legislative proposals, has been sounding suspiciously sympathetic to Big Telco's lobbying.
Read more of this story at SoylentNews.
15:00
The WhatsApp of secure computation Help Net Security
A key term when discussing encryption these days is end-to-end (E2E) encryption. The idea with E2E encryption is that data is kept confidential between the encryptor and the intended receiver. This might seem an obvious requirement, but not all so-called secure systems offer this level of protection. Take for example SMS messages on your phone. The communication between your mobile phone and the local radio mast is indeed encrypted, but from that point onuntil the More
The post The WhatsApp of secure computation appeared first on Help Net Security.
15:00
USB Meets Core Memory In A Vintage Scope Hackaday

Its normal today for even relatively modest instruments to have some form of computer control capability over Ethernet or USB. But five decades ago this was by no means a given, and when Tektronix shipped their P7001 digitiser module for their high-end oscilloscopes in 1971, they were initially designed to interface with a minicomputer. Not everybody has a PDP/11 lying around in 2023, but [Holger Lbben] wasnt fazed by this. He set about creating a USB interface for this ancient piece of test equipment.
At its heart is a Teensy 4.1 which does the job of interfacing with the Tektronix 16-bit bus through a level shifting transceiver. The software for the Teensy comes with some demos, but sadly not the Tek BASIC of the original. Were particularly impressed with the care to make the card frame for the module resemble as closely as possible an original Tektronix product.
Were guessing very few of you will have this ancient test module on your bench, but the depth into which he goes over its internal design and programming makes this very much worth a read. If you fancy more vintage Tek goodness, take a look at this current probe.
14:30
The true numbers behind deepfake fraud Help Net Security
The rise of AI-generated identity fraud like deepfakes is alarming, with 37% of organizations experiencing voice fraud and 29% falling victim to deepfake videos, according to a survey by Regula. In this Help Net Security video, Henry Patishman, Executive VP of Identity Verification Solutions at Regula, illustrates how increasing accessibility of AI technology for creating deepfakes makes the risks mount, posing a significant challenge for businesses and individuals alike.
The post The true numbers behind deepfake fraud appeared first on Help Net Security.
14:00
Your voice could be your biggest vulnerability Help Net Security
AI technology is fueling a rise in online voice scams, with just three seconds of audio required to clone a persons voice, according to McAfee. McAfee surveyed 7,054 people from seven countries and found that a quarter of adults had previously experienced some kind of AI voice scam, with 1 in 10 targeted personally and 15% saying it happened to someone they know. 77% of victims said they had lost money as a result. In More
The post Your voice could be your biggest vulnerability appeared first on Help Net Security.
13:30
Consumer skepticism is the biggest barrier to AI-driven personalization Help Net Security
Businesses worldwide are eagerly embracing the potential for AI to provide personalized customer experiences, but customers remain cynical, according to Twilio. This years report underscores the value of an AI-driven personalization strategy for brands looking to both retain existing customers and acquire new ones, especially in todays competitive market. 62% of business leaders cite customer retention as a top benefit of personalization, while nearly 60% say personalization is an effective strategy for acquiring new customers. More
The post Consumer skepticism is the biggest barrier to AI-driven personalization appeared first on Help Net Security.
13:00
Lessons from a 40-year-long automotive OEM leader Help Net Security
Paul Cha is a cyber and product security leader, serving as the VP of Cybersecurity at LG Electronics Vehicle component Solutions. Paul held critical positions at Synopsis, Ford Motor Company, and Samsung before joining LG. He found his way to cybersecurity while working on his Ph.D. in risk management. Paul started his career in cyber security work as a senior security solution development engineer, where he focused on smart appliances such as smart TVs and More
The post Lessons from a 40-year-long automotive OEM leader appeared first on Help Net Security.
12:25
You Can Now Run Windows 11 Virtual Machines in GPU Memory SoylentNews
Run your whole system from your GPU:
WTF?! Now you can bypass your hard drive and store your whole operating system in your VRAM (should you want to). Well-known Windows modder NTDEV has demonstrated how, and it's surprisingly painless.
Step one is to create a RAM drive in your GPU's memory. A VRAM drive, if you will. There's an open-source tool that can do it for you called GpuRamDrive. It only takes a couple clicks but the tool was abandoned before it reached stability, so you might need to try it a few times.
Step two is to use your pick of tools to create a virtual machine. NTDEV used Windows' baked-in Hyper-V manager, which is a simple yet powerful tool for spawning virtual machines available to Windows 10 and 11 Pro, Education, and Enterprise users. You'll need to change just a couple of defaults in Hyper-V, and you can pick those out in NTDEV's video.
If you have an RTX 4090 or RX 7900 XTX or a GPU with more than 20 GB of VRAM then you should be able to squeeze a vanilla Windows 11 installation onto the VRAM drive you created. If you didn't drop a grand on a new GPU this past year, you'll have to use an alternate operating system with less demanding storage 11 that he created.
[...] I can't think of a single reason why anyone would want to run Windows 11 on their VRAM. And yet, it's astonishingly practical: quick to set up and seemingly as fast and stable as a regular virtual machine. Why not, then, I suppose?
A YouTube video showing it running
Read more of this story at SoylentNews.
12:00

If you want to get rich by hunting with a metal detector, you might want to consider how much you invested in the hardware to start with. Finding a tin can with a $200 detector might not make economic sense. But building a metal detector yourself doesnt have to be hard, as [Mirko] shows in a recent post. His STM32-based pulse induction metal detector looks good and works well, as you can see in the video below.
[Mirko] reports that the device can detect a coin at 30 cm and a large metal object at more than 80 cm. The project uses the Arduino IDE and a Blue Pill STM32 module. The project looks good with an LED module and a rotary encoder to set sensitivity.
Pulse induction metal detectors use a single coil to send and receive short pulses. This differs from the more common BFO-style which uses two frequencies that produce a beat frequency that changes in the presence of metal. These use two coils and are more affected by mineralization the interference caused by minerals in the soil and general interference. Typically, BFO detectors have less sensitivity, especially at a distance.
This isnt the first pulsed induction detector weve seen. Of course, for a simple one you can to forestall comments ...
11:39
11:23
Twitter is Only About 10% of Social Control Media (Far Less Than Most People Imagine) and Thats Decreasing Over Time Techrights
Summary: Contrary to what many people feel or believe, social control media is dominated by Facebook/Instagram
11:03
Do Not Call Free Software Open Source Because It Misleads People and Harms Freedom Techrights
New video (2 weeks ago)
Summary: Somebody has just turned a classic old video of Richard Stallman into a musical track
There is also this new deepfake:
10:44
This is Proof That We Need to Speak Even More About Free Software and Explain What Freedom Means (Not Price, Its Not Freeware) Techrights
This is false:
Summary: Free-as-in-Freedom (FaiF) or freedom-respecting software is under attack; the source code available crowd (like Microsoft GitHub) is warping the debate and suggests not mentioning freedom at all
THE OSI, a de facto front group of Microsoft, is trying to eradicate the F in FOSS or to stop saying FOSS altogether. We wrote about this on Friday morning [1, 2]. But theyre lying. Theyre self-serving sellouts. If anything, the misconception in the above page (screenshot of page 12 of this document by Karen Melchior et al) highlights the need to better explain or to explain more often what Free/libre software is, how it works, and how it is developed.
For the EU side of things see point #129, an associate said. Amendment 130 is the place where Software Freedom needs to be mentioned.
Here is the relevant part:
The very term freedom is being actively, quickly, and quietly erased from society across the board, the associate noted. Remember that RMS gets (or got) brigaded for having the audacity to mention the F-word loudly and publicly.
Id also say that opponents have now dusted off the term freeware after a very long hiatus to try to increase confusion about freedom and specifically about software freedom.
10:19
Looking Back at the First Week of Gemini Daily Links (as Standalone Posts) Techrights
Video download
link | md5sum
7f3874e4e26e0cc7e36499521020a341
Gemini Standalone in Daily Links
Creative Commons Attribution-No Derivative Works 4.0
Summary: Taking Gemini to the next step (parity in Daily Links) is the main thing that happened this month and the above video takes a journey through some of the changes
FIVE days ago we said we'd starting isolating Gemini and Gopher or posting such links in isolation, separately in a disjoint fashion (not part of World Wide Web links). We started doing that later in the same day and it has thus far been a success. We shall carry on doing so.
The video above illustrates how Gemini is used and shows some of these latest changes. The video is unscripted and improvised. This planet-like page that updates every 60-minutes is, at least to me, the best way to keep abreast of Geminispace and Gopherholes. But our Gemini Links, posted at least the same thing.
Towards the end of the video I discuss the size of the Gemini community (yes, it's still a community; corporations arent involved). We hope that more people will join us in Gemini. It helps reduce ones exposure to misinformation, including veiled marketing (the Web has become heavily littered with junk, fake content and words that arent organic, sometimes even machine-generated).
10:07
DistroWatch Weekly, Issue 1018 DistroWatch.com: News
This week in DistroWatch Weekly: Review: Fedora 38 WorkstationNews: Fedora plans new immutable flavour, Linux Mint works to correct issue with Secure Boot, Voyager Live demonstrates ChatGPT clientQuestions and answers: Finding relevant manual pages and merging audio filesReleased last week: Br OS 23.04Torrent corner: KDE neon, ParrotOpinion poll:....
10:00
HPR3851: Firefox extensions Hacker Public Radio
The following is a list of the extensions I have enabled all the time. Absolute Enable Right Click and Copy Force Enable Right Click & Copy Awesome RSS Puts an RSS/Atom subscribe button back in URL bar. cookies.txt Exports all cookies to a Netscape HTTP Cookie File, as used by curl, wget, and youtube-dl, among others. Don't Feck With Paste This add-on stops websites from blocking copy and paste for password fields and other input fields. Firefox Multi-Account Containers Lets you keep parts of your online life separated into color-coded tabs. Cookies are separated by container, allowing you to use the web with multiple accounts. https://tools.google.com/dlpage/gaoptout Tells the Google Analytics JavaScript not to send information to Google Analytics. KeePassXC-Browser Official browser plugin for the KeePassXC password manager (https://keepassxc.org) the Cross-platform Password Manager ModHeader - Modify HTTP headers Modify HTTP request headers, response headers, and redirect URLs uBlock Origin Finally, an efficient blocker. Easy on CPU and memory. User-Agent Switcher Switch between popular useragent strings from toolbar popup!
09:59
Reporting That Embarrasses Powerful People Online is at Risk (Politicians Are at It Again) Techrights
Video download
link | md5sum
d3f8ea1ff2d4c24fe79530cf10b45de6
Restrictions in Canada and EU
Creative Commons Attribution-No Derivative Works 4.0
Summary: Journalism online is under attack, especially through centralised services (especially social control media and proprietary search engines, which are veiled disservices or censorship mechanisms) and as usual this is disguised as combating piracy, protecting children, and protecting adults from misinformation
THE other day we added two important items under the politics category of Daily Links. One concerned Canadas Liberal Party Policy Proposal and the other concerned DSAs (Digital Services Act) Article 37 and Article 44, which is open for feedback until the start of June. The former explores options to hold on-line information services accountable for the veracity of material published on their platforms and to limit publication only to material whose sources can be traced. The latter is to set out the necessary rules for the procedures, methodology and templates used for the audits of very large online platforms and very large online search engines as required under the Digital Services Act (Article 37).
what the European Commission does typically gets implemented in north American countries and vice versa for political and cultural reasons.As noted in the video above, what the European Commission does typically gets implemented in north American countries and vice versa for political and cultural reasons. They habitually refer to this as harmonisation.
In recent decades we saw a whole bunch of laws pu...
09:40
Caught in the Act: Astronomers Spot Star Swallowing a Planet for First Time SoylentNews
A sneak peek at Earth's eventual fate:
Roughly 5 billion years from now, our Sun will end, not with a bang but with a whimper. That's when it finally burns through all the fuel in its core and puffs outward into a red giant, swallowing all the inner planets of our Solar System in the process, including Earth. But no star has ever been caught in the act of gulping down a planet this wayuntil now. Astronomers have spotted a white-hot flash from a distant star in our Milky Way galaxy and concluded that it came from the final stage of this process, according to a new paper published in the journal Nature. Yes, it's a literal "Death Star," announced on the eve of Star Wars Day (May 4).
[...] This process only occurs a few times a year in the Milky Way. Astronomers have observed the early stages of the process (planets so close to their host stars that they will inevitably be engulfed when those stars expand) along with the aftermath of this stellar evolution (when the stars have puffed up and seem to have peculiar properties, such as their rotational speed or chemical composition). But scientists have never witnessed the actual devouring. That's what makes this discovery so exciting, according to co-author Kishalay De, an MIT postdoc: This is the first direct evidence of a crucial stage of stellar evolution.
[...] De was poring over data from the Zwicky Transit Facility (ZTF) at the Palomar Observatory in California about three years ago, hunting for the telltale brightening (by a factor of a few thousand times over the course of a week) that marks a nova. Such explosions occur when a white dwarf steals matter from a companion star. De spotted a star brightening by a factor of a few hundred times over the course of a couple of weeks. He quickly checked out observations of the same star taken by the Keck Observatory in Hawaii. But the spectrum revealed that the composition and temperature of the gas surrounding this star was nothing like a nova. "This source appeared to be surrounded by a bunch of cold gas," De said. "We were seeing signs of molecules that can only exist at cold temperatures."
Read more of this story at SoylentNews.
08:50
Kernel prepatch 6.4-rc1 LWN.net
Linus has released 6.4-rc1 and closed the merge window for this development cycle.
The one feature that didn't make it was the x86 shadow stack code. That side was probably a bit unlucky, in that it came in as I was looking at x86 issues anyway, and so I looked at it quite a bit, and had enough reservations that I asked for a couple of fairly big re-organizations.
This is just one more setback in the long-running shadow-stack story; see this article for some background.
In the end, 13,044 non-merge changesets were pulled during this merge window.
07:34
Linux 6.4-rc1 Released With Intel LAM, Several New AMD Features, More Rust Code & Early Apple M2 Phoronix
Linus Torvalds just released Linux 6.4-rc1 that also marks the end of the merge window for the exciting Linux 6.4 cycle...
07:22
CVE-2023-31038: Apache Log4cxx: SQL injection when using ODBC appender Open Source Security
Posted by Robert Middleton on May 07
Severity: 6.8Affected versions:
- Apache Log4cxx 0.9.0 before 1.1.0
Description:
SQL injection in Log4cxx when using the ODBC appender to send log messages to a database. No fields sent to the
database were properly escaped for SQL injection. This has 2003-08-06)
Note that Log4cxx is a C++ framework, so only C++ applications are affected.
07:20
Re: Perl's HTTP::Tiny has insecure TLS cert default, affecting CPAN.pm and other modules Open Source Security
Posted by John Helmert III on May 07
Actually, Gentoo is NOT a CNA, and thus cannot issue CVEs.07:17
CVE-2023-29247: Stored XSS on Apache Airflow Open Source Security
Posted by Pierre Jeambrun on May 07
Severity: importantAffected versions:
- Apache Airflow before 2.6.0
Description:
Task instance details page in the UI is vulnerable to a stored XSS.This issue affects Apache Airflow: before 2.6.0.
Credit:
taidh from VNPT - VCI (finder)
kuteminh11 (finder)
References:
https://github.com/apache/airflow/pull/30447
https://github.com/apache/airflow/pull/30779
https://airflow.apache.org/
https://www.cve.org/CVERecord?id=CVE-2023-29247
06:42
La Liga Asked GitHub to Shut Down Football Streaming App Nodito TorrentFreak
 With millions of fans all over the world, Spanish
football league La Liga
is one of the most popular in the game.
With millions of fans all over the world, Spanish
football league La Liga
is one of the most popular in the game.
In common with similar sports organizations, La Liga has a dedicated anti-piracy team that actively tracks and reports unauthorized live streams.
This sounds like a straightforward task but, in reality, it often turns into a perpetual stream of takedown notices. After all, the operators of piracy sites and apps have no intention of abiding by the law and pull out all the stops to avoid getting caught.
La Liga vs. Nodito
A recent takedown notice from La Liga illustrates this problem quite well. A few days ago the league sent a takedown notice to GitHub, asking it to remove an APK file that belongs to the user Nodoapps, known for the Spanish football streaming app Nodito.
The National Professional Football League has among its main objectives the fight against piracy in the digital environment, in particular, the protection of its rights and those of its member clubs, and spends enormous human and technological resources to detect such misuse, the notice starts.

La Liga explains that since the app links to live streams of First and Second Division games published without permission, GitHub should take the code offline.
This user does not have any right to this type of links with illegal broadcasts, so the conduct described supposes a violation of said exploitation rights of audiovisual content of the National League Championship in its First and Second Divisions.
The takedown notice was effective in the sense that GitHub acted swiftly. As a result, people who try to download the APK file through that link now see a 404 error instead. That doesnt really solve the problem though.
New GitHub Link
Soon after the above-mentioned URL was reported and disabled, the same user began promoting a new GitHub download link through Nodoapps official...
05:25
OTB#72: Touki Bouki Random Thoughts
I watched this fab movie some years ago.
Touki Bouki. Djibril Diop Mambty. 1973.
This blog post is part of the Officially The Best 2022 series.
04:58
Boring Company Gets Approval to Expand Las Vegas Tunnels to 65-Mile Network SoylentNews
Boring Company Gets Approval to Expand Las Vegas Tunnels to 65-Mile Network:
Las Vegas city officials have approved The Boring Company's request to expand its planned network of underground tunnels. The Las Vegas Loop will now feature a total of 69 stations and 65 miles, or 104 kilometers, of tunnels.
The Boring Company tweeted the news yesterday evening, following a meeting with the Clarke County Zoning Commission yesterday morning. The Las Vegas Loop was set to feature a combined 34 miles, or 55 kilometers, of tunnels and had stations that predominantly ran along the Las Vegas Strip. The Boring Company then asked in March to expand the Las Vegas loop, with the newly approved expansion adding 18 new stations and about 25 miles, 40 kilometers, of additional tunnels, according to a tweet from the county's official account yesterday.
[...] "This is a 100% developer funded project that will reduce traffic trips from our surface street public roadways, it will provide folks another easy and convenient alternative to get around, and as part of our revenue sharing agreement with the Boring Company, they will end up paying the City for use of our right of way," Las Vegas Executive Director of Infrastructure Mike Janssen told Gizmodo in an email. "So, I am excited to see the project continue to grow."
Attorney Stephanie Allen, representing the Boring Company, told county commissioners at yesterday's meeting that the Las Vegas loop currently has 2.2 miles constructed with 5 operational stopsfour at the Las Vegas Convention Center and one at Resorts World. Allen further told commissioners that 1 million passengers have ridden through the network so far, with peak ridership in one day reaching over 32,000.
"The more opportunities we have on this map, the more opportunities for success with this system," Allen said during the meeting.
Read more of this story at SoylentNews.
04:12
Cyberpress Launches Cybersecurity Press Release Distribution Platform HackRead | Latest Cybersecurity and Hacking News Site
By Cyberpress
Dubai / May 1st 2023 / Cyberpress Cybersecurity gets a new dedicated newswire. Cyberpress, a press release
This is a post from HackRead.com Read the original post: Cyberpress Launches Cybersecurity Press Release Distribution Platform
03:34
memtest86+ 6.20 Released With Improved Support For Older Systems Phoronix
Last October marked the release of memtest86+ 6.0 as a rewrite of this long-used, open-source bootable RAM testing software. In February marked memtest86+ 6.10 with UEFI Secure Boot signing and other new features. Out today is now memtest86+ 6.20 where a driving focus for this release is on improving support for older hardware...
03:03
GNU/Linux Share Reaching Highest Levels Since Android (Linux) Took Off Worlwide and Lowered Relative Share of Desktops/Laptops Techrights
May 2023 data and graph for GNU/Linux:

GNU/Linux share relative to all other OSes
(including Android)
Summary: Android is about half of all Web traffic; but GNU/Linux is still growing too, in relative terms, based on StatCounter
02:56
San Bernardino County Sheriffs Department paid a $1.1M ransom Security Affairs
The San Bernardino County Sheriffs Department confirmed that it has paid a $1.1-million ransom after the April ransomware attack.
The San Bernardino County Sheriffs Department opted to pay a $1.1-million ransom after a ransomware attack infected its systems in early April.
The ransomware attack forced the Police department to temporarily shut down some of its systems to prevent the threat from spreading. Impacted systems include email, in-car computers and some law enforcement databases.
The attack took place on April 7, the law enforcement immediately launched an investigation into the incident to determine the extent of the attack. Sheriffs Department spokeswoman Gloria Huerta said that the investigation is still ongoing.
The Los Angeles Times reported that San Bernardino County paid half the total of the ransom ($511,852), while the remaining part was covered by the insurance carrier. The ransom was paid to restore the systems full functionality and secure any data involved in the breach.
Despite the FBI and law enforcement bodies always recommend not paying ransom in these attacks, in this case, the department opted to pay likely because they had no other way to recover the encrypted systems or to avoid the disclosure of sensitive data.
If youre paying through cryptocurrency, you dont know who youre paying it to, Clifford Neuman, the director of USCs Center for Computer Systems Security, told the Los Angeles Times. It could be a sanctioned entity, whether its Iran, whether its North Korea, whether its a terrorist organization.
The ransomware gang that targeted the San Bernardino County Sheriffs Department is suspected to be from Eastern Europe and has already targeted U.S. entities in the past.
Cities, hospitals, and school districts are privileged targets of cybercriminals because they have poor defense and their systems contain a lot of sensitive data.
We are in the final!
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections where is reported
Securityaffairs or my name Pierluigi Paganini
Please nominate Security Affairs as your favorite blog.
...02:00
FEX 2305 Emulator On ARM Adds More AVX Instructions, Optimizations Phoronix
FEX-Emu 2305 has been released, the open-source project continuing to work on x86_64 atop 64-bit ARM (AArch64) emulation support for being able to enjoy more games on ARM Linux and other software not otherwise natively available...
01:23
Artificial intelligence taking orders at Buckeye Carls Jr. drive-thru Lifeboat News: The Blog

A fast-food chain struggling to hire staff is using AI to help fill the gaps at the drive-thru.
For more Local News from KPHO: https://www.azfamily.com/
For more YouTube Content: https://www.youtube.com/channel/UCIrgpHvUm1FMtv-C1xwkJtw
01:22
Physicists Discovered a Quantum Trick For Reaching Absolute Zero Lifeboat News: The Blog
The state of perfect stillness known as absolute zero is one of the Universes impossible achievements. As close as we can get, the laws of physics will always prevent us from hitting thermal rock bottom.
An international team of researchers has now identified a new theoretical route to reach the mythical mark of zero Kelvin, or-273.15 degrees Celsius (459.67 degrees Fahrenheit). No, its not more likely to break any laws and remove every last shimmer of heat, but the framework could inspire new ways of exploring matter at low temperatures.
As a consequence of the third law of thermodynamics, the removal of increments of heat energy from a group of particles to cool them to absolute zero will always take an infinite number of steps. As such, it requires an infinite amount of energy to achieve. Quite the challenge.
01:22
A Chance Event 1 Million Years Ago Changed Human Brains Forever Lifeboat News: The Blog
Like treasured recipes passed down from generation to generation, there are just some regions of DNA that evolution doesnt dare tweak. Mammals far and wide share a variety of such encoded sequences, for example, which have remained untouched for millions of years.
Humans are a strange exception to this club. For some reason, recipes long preserved by our ancient ancestors were suddenly spiced up within a short evolutionary period of time.
Because were the only species in which these regions have been rewritten so rapidly, they are called human accelerated regions (or HARs). Whats more, scientists think at least some HARs could be behind many of the qualities that set humans apart from their close relatives, like chimpanzees and bonobos.
01:22
Researchers observe extremely squeezed directional THz waves in thin semiconductor crystals Lifeboat News: The Blog
An international team of scientists has imaged and analyzed THz waves that propagate in the form of plasmon polaritons along thin anisotropic semiconductor platelets with wavelengths reduced by up to 65 times compared to THz waves in free space.
Whats even more intriguing is that the wavelengths vary with the direction of propagation. Such THz waves can be applied for probing fundamental material properties at the nanometer scale and pave the way to the development of ultra-compact on-chip THz devices. The work has been published in Nature Materials.
Polaritons are hybrid states of light and matter that arise from the coupling of light with matter excitations. Plasmon and phonon polaritons are among the most prominent examples, formed by the coupling of light to collective electron oscillations and crystal lattice vibrations, respectively.
01:22
Zeroing in on a fundamental property of the protons internal dynamics Lifeboat News: The Blog
Inside the proton are elementary particles called quarks. Quarks and protons have an intrinsic angular momentum called spin. Spin can point in different directions. When it is perpendicular to the protons momentum, it is called a transverse spin. Just like the proton carries an electric charge, it also has another fundamental charge called the tensor charge. The tensor charge is the net transverse spin of quarks in a proton with transverse spin.
The only way to obtain the tensor charge from experimental data is using the theory of quantum chromodynamics (QCD) to extract the transversity function. This universal function encodes the difference between the number of quarks with their spin aligned and anti-aligned to the protons spin when it is in a transverse direction. Using state-of-the-art data science techniques, researchers recently made the most precise empirical determination of the tensor charge.
Due to the phenomenon known as confinement, quarks are always bound in the proton or other hadrons (particles with multiple quarks). The challenge is to connect the theory of quark interactions (QCD) to experimental measurements of high-energy collisions involving hadrons.
00:57
The Coronation of King Charles cryptogon.com
Worth a repost. Via: Truthstream Media: Related: God Save [Free Speech]: Britain Celebrates Coronation With Time-Honored Tradition Of Arresting Anti-Monarchists
00:13
Meta's Ad Business Slapped With Interim Measures in France Over Suspected Antitrust Abuse SoylentNews
Meta's ad business slapped with interim measures in France over suspected antitrust abuse:
More regulatory woes for Meta: France's competition watchdog has announced interim measures on the adtech giant saying it suspects it of abusing a dominant position in the French market for ads on social media and across the broader (non-search-related) online ads market.
It's ordering Meta to suspend application of the current criteria it imposes for granting ad verification partnerships; and giving it two months to define and publish new rules for accessing and maintaining viewability and brand safety partnerships which the Authority specifies must be "objective, transparent, non-discriminatory and proportionate".
Meta must also have a transparent access procedure for the partnerships that is not based on an invitation it sends, the order also stipulates.
The antitrust intervention follows a complaint by Adloox, a French ad verification platform that sells anti-ad-fraud and brand safety services. It complained to the Autorit de la Concurrence about Meta's conduct between 2016 and 2022, accusing the company of denying it the same kind of access to its ecosystem that some of its competitors have been granted, harming its ability to provide its services.
Adloox claims Meta discriminatorily denied it access to the aforementioned viewability and brand safety partnerships despite providing such access to other companies in similar circumstances.
It also accuses Meta of abusing a dominant position by imposing unfair access conditions by providing only partial access to its ecosystem. And its complaint asked the Autorit to impose interim measures intended to force Meta to provide the sought for access.
Read more of this story at SoylentNews.
00:07
Links 07/05/2023: Many New Videos and Perl News Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Linux Made Simple 2023-05-01 [Older] Linux Weekly Roundup #233
-
00:00
Vint Cerf on 3 Mistakes He Made in TCP/IP IEEE Spectrum

Vint Cerf, the recipient of the 2023 IEEE Medal of Honor for co-creating the Internet architecture and providing sustained leadership in its phenomenal growth in becoming societys critical infrastructure, didnt have a perfect view of the Internets future. In hindsight, there are a few things he admits he got wrong. Here some of those mistakes, as recently told to IEEE Spectrum:
1) I thought 32 bits ought to be enough for Internet addresses.
And of course, he says, everybody laughs and says, You idiot, why didnt you use 128-bit addresses? The answer is that, back in 1973, people wouldve said, Youre crazy if you think you need 3.4 times 10 to the 38th addresses to do an experiment that you arent sure is going to work. So that was a mistake, although I dont think at the time that I would have been able to sell 128.
2) I didnt pay enough attention to security.
Before public-key cryptography came around, key distribution was a really messy manual process, Cerf says. It was awful, and it didnt scale. So thats why I didnt try to push that into the Internet. And by the time they did implement the RSA algorithm, I was well on my way to freezing the protocol, so I didnt push the crypto stuff. I still dont regret that, because graduate students, who were largely the people building and using the Internet, would be the last cohort of people I would rely on to maintain key discipline, though there are times when I wish we had put more end-to-end security in the system to begin with.
3) I didnt really appreciate the implications of the World Wide Web.
That is, Cerf says, I didnt expect the avalanche of content that went onto the Internet once the Web was made available. And what happened as a result of that avalanche is that we had to invent search engines in order to find stuff, because there was so much of it. I absolutely did not predict that search engines would be needed.
00:00
Launching Paper Planes From Way, Waaaaaay Up Hackaday

Every now and again we stumble across something a bit unexpected, and today thats the fact that there have been quite a few efforts at launching paper planes from as close to space as possible. The current record for the highest paper plane launch is a whopping altitude of 35,043 meters.
Sunday, 07 May
23:25
Wonder Material Graphene Just Broke Another Major Record in Physics Lifeboat News: The Blog
Graphene is a special material. Among its many talents, it can act as a superconductor, generate a super-rare form of magnetism, and unlock entirely new quantum states.
Now graphene has another amazing credit: it can record levels of magnetoresistance without a need to push the temperature down towards absolute zero.
High magnetoresistance a materials ability to change its electrical resistance in response to a magnetic field is relatively rare, yet materials that can shift their properties in this fashion are useful in computers, cars, and medical equipment.
23:24
Quantifying Biological Age: Blood Test #3 in 2023 Lifeboat News: The Blog
Join us on Patreon!
https://www.patreon.com/MichaelLustgartenPhD
Discount Links:
NAD+ Quantification: https://www.jinfiniti.com/intracellular-nad-test/
Use Code: ConquerAging At Checkout.
Green Tea: https://www.ochaandco.com/?ref=conqueraging.
Oral Microbiome: https://www.bristlehealth.com/?ref=michaellustgarten.
Epigenetic Testing: Trudiagnostic.pxf.io/R55XDv.
Use Code: CONQUERAGING
At-Home Blood Testing: https://getquantify.io/mlustgarten.
23:23
ChatGPT with Code Interpreter: The best use cases Lifeboat News: The Blog
The Code Interpreter is probably the most interesting ChatGPT plugin of OpenAI and opens up completely new capabilities for the Chatbot.
At the end of March, OpenAI introduced a groundbreaking new feature for ChatGPT: Plugins. One of them is a so-called Code Interpreter. With it, the language model can not only generate code, but also execute it independently.
As with Auto-GPT, the busy developer community has found exciting use cases for this technology in a very short time. Especially for data journalism and similar data-based analysis, the tool seems to open up completely new possibilities. This is also due to the possibility of uploading and downloading files up to 100 MB in size.
23:23
Google engineer warns it could lose out to open-source technology in AI race Lifeboat News: The Blog
And it would be hilarious too.
Google has been warned by one of its engineers that the company is not in a position to win the artificial intelligence race and could lose out to commonly available AI technology.
A document from a Google engineer leaked online said the company had done a lot of looking over our shoulders at OpenAI, referring to the developer of the ChatGPT chatbot.
23:22
Tesla Full Self-Driving Beta 11.3.6 takes me to a random point on the map with zero human input Lifeboat News: The Blog
Tesla Full Self-Driving Beta 11.3.6 takes me to a randomly generated point on the map with zero human input required. A lot of people dont realize this is possible today.
22:59
Yocto Project 4.2 released LWN.net
Version 4.2 of the Yocto Project distribution builder has been released. It features improved Rust support, a number of BitBake enhancements, lots of updated software, and numerous security fixes.
22:53
Dragon Breath APT uses double-dip DLL sideloading strategy Security Affairs
An APT group tracked as Dragon Breath has been observed employing a new DLL sideloading technique.
Sophos researchers observed an APT group, tracked as Dragon Breath (aka APT-Q-27 and Golden Eye), that is using a new DLL sideloading technique that adds complexity and layers to the execution of the classic DLL sideloading.
The attack consists of a clean application, which acts as a malicious loader, and an encrypted payload. The experts observed various modifications of components over time. In the latest campaigns, a first-stage clean application sideloads a second clean application and auto-executes it. Then the second clean application sideloads the malicious loader DLL that executes the final payload.

The threat actor has been active since 2020, it was first detailed by QiAnXin in 2020. The group is believed to be focused on organizations in the online-gambling industries and their customers. Most of the victims are Chinese-speaking Windows users engaged in online gambling, the APT group relies on Telegram to distribute the malware.
The experts also observed targets in the Philippines, Japan, Taiwan, Singapore, Hong Kong, and China.
Sophos discovered a web site (telegramos[.]org) that claims to deliver Chinese-language versions of the Telegram application for Android, iOS, and Windows. The researchers noticed occasionally, but not consistently, the site ignored the OS choices of the visitors.
This is the site from which the affected user is thought to have downloaded the package that caused the infection. How the user first encountered the site, whether through phishing or SEO poisoning or some other method, is beyond the scope of this investigation. reads the report published by the security firm. The sideloading components and the startup link are only created when the desktop Telegram link...
22:29
cron(8) now supports random ranges with steps OpenBSD Journal
Thanks to the following commit by Todd Miller
(millert@), cron(8) now
supports random values in a range with a step value
(i.e.
"<lo>~<hi>/<step>"
in crontab(5)
entries):
CVSROOT: /cvs
Module name: src
Changes by: millert@cvs.openbsd.org 2023/05/06 17:06:27
Modified files:
usr.sbin/cron : crontab.5 entry.c macros.h
Log message:
Support random offsets when using ranges with a step value in cron.
This extends the random range syntax to support step values. Instead
of choosing a random number between the high and low values, the
field is treated as a range with a random offset less than the step
value. This can be used to avoid thundering herd problems where
multiple machines contact a server all at the same time via cron jobs.
The syntax is similar to the existing range/step syntax but uses a
random range. For example, instead of "0-59/10" in the minutes
field, "0~59/10" can be used to run a command every 10 minutes where
the first command starts at a random offset in the range [0,9].
The high and low numbers are optional, "~/10" can be used instead.
Requested by job@, OK phessler@
21:39
Where Did All The Trust the Science People Go? cryptogon.com
Via: AwakenWithJP:
21:04
Links 07/05/2023: GNOME 44 in Arch Repos and Ubuntu 23.10 Daily Build Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Monopolies
- Gemini* and Gopher
21:00
An RPi-Powered Multi-DX7/TX816 Style Synth Hackaday

[Kevin] over at Simple DIY ElectroMusic Projects has released a complete DIY modular design for simulating the classic 80s Yamaha TX816 DX/FM modular digital synthesizer. This beast of a synth was used by the cool bands of the 80s as well as TV studios, and ownership of the original machine is an expensive investment. But with the power of modern hackable electronics, and the MiniDexed firmware running bare-metal on a Raspberry Pi getting access to a compatible synth doesnt have to break the bank.
[Kevin] wanted to emulate the look and feel of the original TX816 aesthetic, developing a custom PCB handling the user interface for four of the eight channels, and a second acting as an interface to the Raspberry Pi using a...
20:48
Intel Meteor Lake GuC Firmware Support Published Phoronix
With newer generations of Intel client processors having the GuC firmware binaries is now a hard requirement for accelerated graphics support. Like with AMD and NVIDIA GPUs, firmware binaries are a requirement beyond the open-source Linux driver code. This week Intel published their initial GuC firmware binaries for upcoming Meteor Lake processors...
20:27
New Patches Aim To Tackle Linux x86_64 PIE Support Phoronix
Going back years there has been patches for allowing the Linux x86_64 kernel to build as Position Independent Executable (PIE) code to further enhance the system security. Antgroup engineers most recently have been tackling the Linux x86_64 PIE support and last week sent out a new patch series...
20:01
Intel Shadow Stack For Linux Hits Last-Minute Snag With Issue Raised By Torvalds Phoronix
Intel Shaodw Stack support was submitted for Linux 6.4 at the start of the merge window but now with this two-week merge window drawing to a close, it hasn't been pulled yet and Linus Torvalds raised technical issues with the proposed patches that now jeopardize its arrival this cycle...
19:33
A Fiery End? How the ISS Will End its Life in Orbit SoylentNews
[...] Drift into the wrong part of the Pacific Ocean in eight years, and you might be in for a shock. Tearing through the sky will be some 400 tonnes (880,000lbs) of metal, set aglow by its re-entry through the atmosphere. This raging inferno will crash into the ocean, across an area maybe thousands of kilometres in length, signalling the end of one of humanity's greatest projects the International Space Station (ISS).
The ISS has been orbiting the Earth since construction on it began in 1998. It has hosted more than 250 visitors from 20 countries since its first crew arrived in November 2000. "The space station has been a huge success," says Josef Aschbacher, the head of the European Space Agency (Esa), one of the more than a dozen partners in the programme. It has been a boon for international collaboration, not least between the US and Russia, who partnered shortly after the fall of the Soviet Union. "It is really one of the big international victories," says Thomas Zurbuchen, Nasa's former head of science.
But much of its hardware is decades old, which could eventually see the station become dangerous or even uncontrollable in orbit a fate that befell the Soviet Union's Salyut 7 space station in 1985, requiring two cosmonauts to revive the tumbling station. "We really don't want to go through that again," says Cathy Lewis, a space historian from the National Air and Space Museum in the US.
To prevent such a catastrophe in space from happening once more, the space station will be deorbited in 2031, bringing it through the atmosphere to safely splash down in the Pacific Ocean. This will be the largest re-entry in history and, in March, Nasa asked Congress for funding to start development of a "space tug" that might be needed to perform the task a spacecraft that can push the station back into the atmosphere. Kathy Leuders, head of Nasa's human spaceflight programme, later revealed it was estimated the tug vehicle would cost just shy of $1bn (800m).
Read more of this story at SoylentNews.
19:09
IPTV Piracy Lawsuit Against Datacamp Close to Settlement For Second Time TorrentFreak
 Hosting companies, CDN platforms and consumer ISPs face
an increasing risk of being held liable for the activities of their
customers.
Hosting companies, CDN platforms and consumer ISPs face
an increasing risk of being held liable for the activities of their
customers.
At least in theory, copyright law in both the United States and Europe should provide adequate protections for intermediaries but if a chink appears in the armor, nothing can stop rightsholders filing a lawsuit. When they do, things can get very expensive, very quickly.
According to its website, UK-based CDN company DataCamp shifts a lot of data via its CDN77 service; 120 Tbps network capacity over six continents, with 140+ private peerings connecting 3,000+ networks. In February 2022, U.S. broadcaster DISH Network filed a $32.5m lawsuit against DataCamp, claiming that it failed to deal with copyright infringing customers.
Filed in an Illinois district court, the complaint claimed that pirate IPTV services Banjo TV, Bollywood IPTV, Comstar TV, Express IPTV, Gennie TV, Gold TV, IPGuys, Istar, Red IPTV, Sky IPTV, and Zumm TV, were all customers of DataCamp.
DISH said it sent hundreds of notices requesting removal of content under the DMCA, along with copies of lawsuits and judgments relating to pirate IPTV services.
According to DISH, DataCamps response was lacking and since it failed to adopt and reasonably implement a repeat infringer policy despite having servers in the United States, the company could not rely on the safe harbor provisions of the DMCA.
Tactical Leverage Lawsuit
In a motion to dismiss, DataCamp described the DISH lawsuit as a means to gain tactical leverage over alleged direct infringers, i.e the people behind the named IPTV providers.
The company informed the court that knowledge of its customers activities would be technologically impossible since all traffic is completely encrypted, including between the providers and their customers. As for the infringement notices, DataCamp said it forwarded them to the relevant customers since they were best placed to remove any infringing content.
DISH wasted no time filing a response to DataCamps motion to dismiss and DataCamp was equally swift with its own reply. The filings revealed zero progress in the dispute and a canyon between each sides interpretation of where safe harbors end and liability begins.
Confidentiality Agreement
After a couple of weeks of relative calm, the parties agreed on a confidentiality order and fr...
18:24
Distribution Release: Br OS 23.04 DistroWatch.com: News
Anderson Marques has announced the release of Br OS 23.04. Br OS, developed in Brazil, is an Ubuntu-based distribution featuring the KDE Plasma desktop and a set of applications designed for web content creation. This release marks the project's third anniversary. An interesting new feature of the release....
18:00
Week in review: Fake ChatGPT desktop client steals data, Patch Tuesday forecast Help Net Security
Heres an overview of some of last weeks most interesting news, articles, interviews and videos: Former Uber CSO avoids prison for concealing data breach Joe Sullivan, the former Uber CSO who has been convicted last year for attempting to cover up a data breach Uber suffered in 2016 and kept it hidden from the Federal Trade Commission (FTC), has been sentenced to three years of probation plus 200 hours of community service. Critical RCE vulnerability More
The post Week in review: Fake ChatGPT desktop client steals data, Patch Tuesday forecast appeared first on Help Net Security.
18:00
Soviet-Era Computer Is Both a Mystery and a Disaster Hackaday

There are plenty of bizarre computers around from the 70s through the 90s before the world somewhat standardized around various duopolies of hardware vendors and operating systems. Commodore, Atari, and even Apple had some bizarre machines from this era but for our money, the most unusual systems come out of the Eastern Bloc. Weve featured plenty of these before, and the latest is a Robotron CM1910 which comes to us from [Chernobyl Family] via YouTube.
Built in East Germany behind the wall, the Robotron factories had easier access to Soviet than western parts, but the latter were also available when necessary. Hence its built on an Intel 8086 processor, which seems common enough for the era, but after opening the case some non-standard construction becomes apparent.
The first is a densely-packed array of circuit boards and wiring, far beyond what a western PC might have included in this time. This also partially explains its massive 25 kg weight. It does include a hard drive, two floppy disk drives, a large dedicated graphics card, and a modem which all contribute as well. The overall design philosophy of the machine was a headscratcher too, which would have involved near-complete dismantli...
17:02
IRC Proceedings: Saturday, May 06, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-060523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-060523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-060523.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-060523.gmi
Over HTTP:
|
... |
15:00
The Forgotten Rescue of the Salyut 7 Space Station Hackaday

With only two space stations in orbit around Earth today in the form of the International Space Station and the Chinese Tiangong (Sky Palace) station, its easy to forget how many space stations were launched in the previous century. And the Soviet Union launched by far the most, as part of the Salyut (Russian for salute or fireworks) program. Although the program entailed both military (Orbital Piloted Station, or OPS) and civilian (Durable Orbital Station, or DOS) stations, it was the civilian stations that saw the most success, as well as the most daring rescue attempt with the recovering of the Salyut 7 space station.
Salyut 7 (DOS-6) was set to repeat Salyut 6s success after its launch on April 19th 1982, until disaster struck in February 1985. Due to a series of electrical and other faults ground communication with the space station was cut off, and the at the time unmanned space station began to gradually tumble towards the Earths atmosphere. This left those in charge with two options: leave the station to burn up in the atmosphere, or stage a rescue mission.
Ultimately, on June 6th, 1985, Soyuz T-13 launched to rendezvous with Salyut 7. On board were cosmonauts Vladimir Dzhanibekov who h...
14:47
Recent MIT Paper Proposes a New Method to "Grow" 2D Transistors on Top of Wafers SoylentNews
New process significantly speeds up 2D transistor production:
A recent MIT paper proposes a new method to "grow" 2D transistors on top of wafers, potentially speeding the production of ultrathin computing materials. The study claims to solve the heating and assembly problems of other methods, possibly opening new avenues for semiconductors.
Manufacturers like Intel, Samsung, and TSMC continually find ways to make ever-smaller transistors to guarantee ongoing increases in processing power each year. TSMC and Samsung have started 3nm semiconductor production as Intel looks forward to counting transistor size in Angstroms, while talk has also shifted to "2D materials" that are only a few atoms thick.
[...] One problem with building the 2D material molybdenum disulfide is heat. Growing some of its components requires temperatures over 550 degrees Celsius, but silicon wafer circuits start decaying beyond 400. Normally, manufacturers graft the 2D material onto the wafer after its production, often leading to imperfections.
The researchers instead grew the material directly onto the wafer with a new kind of kiln that separates part of the cooking process. A high-temperature zone processes the sulfur, after which it flows into the lower-temperature region where the molybdenum and the wafer are kept below 400C. The system leads to more uniform surfaces and faster production.
While the prior method could take an entire day to grow a layer, the new technique can grow a layer in under an hour. The improvement could enable growth across larger surfaces, and the researchers plan to explore stacking layers.
Journal Reference:
Zhu, J., Park, JH., Vitale, S.A. et al.
Low-thermal-budget synthesis of monolayer molybdenum disulfide
for silicon back-end-of-line integration on a 200mm platform.
Nat. Nanotechnol. (2023). https://doi.org/10.1038/s41565-023-01375-6
Read more of this story at SoylentNews.
14:40
Its another lovely day, but Im still not altogether mobile (although my ankle is definitely improving), so what about another day on the couch, reading comics? Sure.
But before I begin readin, I want to natter on a bit about some comics I read the other day:
Yes! After almost 50 years (well, perhaps 45), Tardi has ended his Adle Blanc-Sec series! Its something of a momentous thing I read the first album when I was, like, 12, and now Im, like, old. So its a thing thats been going on, but very intermittently, for the vast majority of my life.
So I spent a day reading the preceding nine albums, along with the two tie-ins (Le Dmon des glaces and Adieu Brindavoine; you really kinda have to read at least the second of those to make sense of what happens in the fifth Adle album, Le secret de la salamandre). Ive read the first five (or seven, if you include the etc) albums many, many times I was a huge Tardi fan as a teenager. The later albums not so much, because who has time when youre a student etc.
I did re-read all Tardi albums (chronologically) about a decade ago, though, but Ive never sat down and had an intense Adle-a-thon: These alb...
12:00
Op-Amp Challenge: A Low Noise Amplifier For Those Truly Low Noise Measurements Hackaday

When something is described as Low Noise, it is by the nature of the language a relative phrase. The higest quality magnetic tape is low noise compared to its cheaper sibling for example, but still has noise many would consider unacceptable. In instrumentation however, Low Noise has to really mean just that, with a range of specialist techniques to produce circuitry with a truly low noise level for the most demanding of signal applications. As an example [Floydfish] has created a low noise instrumentation amplifier that should serve as a learning exercise for anyone interested in pushing low noise circuitry to the limit.
Anyone who can dredge the hazy recesses of their mind for barely-remembered electronics lectures will know that the overall noise figure of a system is dictated by that of its first component. Thus perhaps the most interesting part of the schematic is at the input, where a row of low-noise op-amps are presented in parallel. We have to admit having to look this one up, to find that its a technique whereby the signal outputs of each chip are the same and thus sum, while the noise output of each is different and thus the summed noise output is proportionally lower. This stage is then followed by a buffer and a s...
11:41
Links 06/05/2023: Proton 8.0-2 and Much More Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Science
- Education
- Hardware
- Health/Nutrition/Agriculture
- Proprietary
- Security
- Defence/Aggression
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Censorship/Free Speech
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Digital Restrictions (DRM)
- Monopolies
-
GNU/Linux
-
Applications
-
TecMint ...
-
-
11:35
Gemini Links 06/05/2023: Personal Posts and an Extended Downtime Techrights
-
Gemini* and Gopher
-
Personal
-
On the count of three
Way too hungover again. Wife rejection in bed last night. Nobody replying online. My wife signed us up for too much activity in the next 24 hours. Others verbiage is looking all the same. Nothing intriguing.
[...]
And again in the labor of enduring others.
-
The thoughts come marching two by two
Real-izing (yes, making real) it was all just thoughts believed (yes, a name for a (the?) mechanism of making real) to be (see? to be aka to be real..) another thought that calls itself I despite being merely another thought albeit the thought around which all the others revolve, i.e. are with respect to, i.e. are in terms of.
By the way, the previous is in part an instance of practicing getting out of jury duty. The current theory is a glassy-eyed ramble that only people who love coding in Lisp could parse might do the trick.
-
The Obstacle is the Way book notes
The obstacle in your path can become your path to success. Instead of being paralyzed by challenges, see them as opportunities to learn and grow. Remember, the things that hurt us often instruct us.
We spend a lot of time trying to get things perfect and look at the rules, but what matters is that it works; it doesnt need to be after the book. Focus on results rather than on beautiful methods. In Jujitsu, it does matter that you bring your opponent down, but not how. There are many ways from point A to point B; it doesnt need to be a straight line. So many try to find the best solution but need to catch up on what is in Infront of them. Think progress and not perfection.
-
Odds-and-Ends Photos 2023-05-06 (Fairbanks, AK, USA)
Here are a photos from the last few weeks, which didn...
-
-
10:01
Ed Sheeran Found Not Guilty of Copyright Infringement in Thinking Out Loud Court Battle SoylentNews
Entertainer Ed Sheeran has been found not guilty of infringing on four chords used in both his song and in Marvin Gaye's hit, "Let's Get It On". The same four-chord sequence is used in a lot of songs and at a key point in the trial a musicologist testified that the same four-chord sequence has been used in popular songs many times prior to Gaye's 1973 hit. The trial took place in Manhattan in New York and the jury took only three hours to reach a unanimous decision. The two songs featured at the trial also have very different lyrics and melodies as well as different use of the common four chords. While the decision does not form a legal precedent, it is likely to affect similar cases in the future.
During her closing argument, Farkas said the case never should have been brought and that Sheeran was "unjustly accused" of copying from "Let's Get It On."
"We all benefit from artists being free to create and to build on what came before them," Farkas said, warning the jury that a verdict against Sheeran would mean "creativity will be stifled for fear of being sued."
--ABC
Also
"I am just a guy with a guitar who loves writing music for people to enjoy," he added. "I am not and will never allow myself to be a piggy bank for anyone to shake."
--New York Times
Read more of this story at SoylentNews.
10:00
Workflow Extraction from Screencasts It Will Never Work in Theory
Dehai Zhao, Zhenchang Xing, Xin Xia, Deheng Ye, Xiwei Xu, and Liming Zhu. Seehow: workflow extraction from programming screencasts through action-aware video analytics. 2023. arXiv:2304.14042.
Programming screencasts (e.g., video tutorials on Youtube or live coding stream on Twitch) are important knowledge source for developers to learn programming knowledge, especially the workflow of completing a programming task. Nonetheless, the image nature of programming screencasts limits the accessibility of screencast content and the workflow embedded in it, resulting in a gap to access and interact with the content and workflow in programming screencasts. Existing non-intrusive methods are limited to extract either primitive human-computer interaction (HCI) actions or coarse-grained video this http URL this work, we leverage Computer Vision (CV) techniques to build a programming screencast analysis tool which can automatically extract code-line editing steps (enter text, delete text, edit text and select text) from screencasts. Given a programming screencast, our approach outputs a sequence of coding steps and code snippets involved in each step, which we refer to as programming workflow. The proposed method is evaluated on 41 hours of tutorial videos and live coding screencasts with diverse programming environments. The results demonstrate our tool can extract code-line editing steps accurately and the extracted workflow steps can be intuitively understood by developers.
An Open Source Adaptive Tutoring System It Will Never Work in Theory
Zachary A. Pardos, Matthew Tang, Ioannis Anastasopoulos, Shreya K. Sheel, and Ethan Zhang. OATutor: an open-source adaptive tutoring system and curated content library for learning sciences research. In Proceedings of the 2023 CHI Conference on Human Factors in Computing Systems. ACM, Apr 2023, doi:10.1145/3544548.3581574.
Despite decades long establishment of effective tutoring principles, no adaptive tutoring system has been developed and open-sourced to the research community. The absence of such a system inhibits researchers from replicating adaptive learning studies and extending and experimenting with various tutoring system design directions. For this reason, adaptive learning research is primarily conducted on a small number of proprietary platforms. In this work, we aim to democratize adaptive learning research with the introduction of the first open-source adaptive tutoring system based on Intelligent Tutoring System principles. The system, we call Open Adaptive Tutor (OATutor), has been iteratively developed over three years with field trials in classrooms drawing feedback from students, teachers, and researchers. The MIT-licensed source code includes three creative commons (CC BY) textbooks worth of algebra problems, with tutoring supports authored by the OATutor project. Knowledge Tracing, an A/B testing framework, and LTI support are included.
Impact of OSS Courses on Student Self-Efficacy It Will Never Work in Theory
This paper does many things well, and I urge you to read it, but it's also a prime example of the kind of frustrating abtract we complained about last year; the figure below gives a much better idea of what the authors found.
Larissa Salerno, Simone de Frana Tonho, Igor Steinmacher, and Christoph Treude. Barriers and self-efficacy: a large-scale study on the impact of OSS courses on student perceptions. 2023. arXiv:2304.14628.
Open source software (OSS) development offers a unique opportunity for students in Software Engineering to experience and participate in large-scale software development, however, the impact of such courses on students' self-efficacy and the challenges faced by students are not well understood. This paper aims to address this gap by analyzing data from multiple instances of OSS development courses at universities in different countries and reporting on how students' self-efficacy changed as a result of taking the course, as well as the barriers and challenges faced by students.
Code Reuse Support for node.js Developers It Will Never Work in Theory
Brittany Reid, Marcelo d'Amorim, Markus Wagner, and Christoph Treude. NCQ: code reuse support for node.js developers. 2021. arXiv:2101.00756.
Code reuse is an important part of software development. The adoption of code reuse practices is especially common among Node.js developers. The Node.js package manager, NPM, indexes over 1 million packages and developers often seek out packages to solve programming tasks. Due to the vast number of packages, selecting the right package is difficult and time consuming. With the goal of improving productivity of developers that heavily reuse code through third-party packages, we present Node Code Query (NCQ), a Read-Eval-Print-Loop environment that allows developers to 1) search for NPM packages using natural language queries, 2) search for code snippets related to those packages, 3) automatically correct errors in these code snippets, 4) quickly setup new environments for testing those snippets, and 5) transition between search and editing modes. In two user studies with a total of 20 participants, we find that participants begin programming faster and conclude tasks faster with NCQ than with baseline approaches, and that they like, among other features, the search for code snippets and packages. Our results suggest that NCQ makes Node.js developers more efficient in reusing code.
Benchmarking Open Source DevOps It Will Never Work in Theory
Jos Manuel Snchez Ruiz, Francisco Jos Domnguez Mayo, Xavier Oriol, Jos Francisco Crespo, David Benavides, and Ernest Teniente. A benchmarking proposal for devops practices on open source software projects. 2023. arXiv:2304.14790.
The popularity of open-source software (OSS) projects has grown significantly over the last few years with more organizations relying on them. As these projects become larger, the need for higher quality also increases. DevOps practices have been shown to improve quality and performance. The DORA benchmarking reports provide useful information to compare DevOps practices performance between organizations, but they focus on continuous deployment and delivery to production, while OSS projects focus on the continuous release of code and its impact on third parties. The DORA reports mention the increasing presence of OSS projects as they are widely used in the industry, but they have never been used to measure OSS projects performance levels. This study reveals that the DORA benchmark cannot be applied to OSS projects and proposes benchmarking metrics for OSS projects, being the first one that adapts the DORA metrics and applies them in OSS projects. The metrics proposed in this study for benchmarking OSS projects include Release Frequency and Lead Time For Released Changes to measure throughput, and Time To Repair Code and Bug Issues Rate to assess stability. In contrast to the DORA reports, where data is collected through manual surveys, in our proposal, data is collected automatically by a tool we developed that retrieves information from public GitHub repositories. This reduces the risk of survey-based data collection. Our study also shows the benchmark feasibility by applying it to four popular OSS projects: Angular, Kubernetes, Tensorflow, and VS Code. In addition, we proposed challenges that address the topics and future works to expand the knowledge and findings of this study. Overall, the findings of the study can help to improve future research on OSS projects and provide a better understanding and challenges of the role of DevOps practices in OSS projects.
A Small Request for ICSE Attendees It Will Never Work in Theory
We've been trying to raise awareness of actionable research results among practitioners since 2011. People tell us it's useful (or at least entertaining) but we haven't found anyone willing to fund it: academic societies and national research organizations think companies should be falling over themselves for the privilege of doing so, while companies don't see what any of this esoterica has to do with them meeting next quarter's targets. If you're going to ICSE'23 next week, please talk to your colleagues about specific, concrete, actionable, and measurable ways to sustain this kind of translational work; if you can't come up with any, please ask yourselves whether there's any real value in being right but not being heard.
09:00
Laser Triangulation Makes 3D Printer Pressure Advance Tuning Easier Hackaday

On its face, 3D printing is pretty simple its basically just something to melt plastic while being accurately positioned in three dimensions. But the devil is in the details, and there seems to be an endless number of parameters and considerations that stand between the simplicity of the concept and the reality of getting good-quality prints.
One such parameter that had escaped our attention is pressure advance, at least until we ran into [Mike Abbott]s work on automating pressure advance calibration on the fly. His explanation boils down to this: the pressure in a 3D printer extruder takes time to both build up and release, which results in printing artifacts when the print head slows down and speeds up, such as when the print head needs to make a sharp corner. Pressure advance aims to reduce these artifacts by adjusting filament feed speed before the print head changes speed.
The correct degree of pressure advance is typically determined empirically, but [Mike]s system, which he calls Rubedo, can do it automatically. Rubedo uses a laser line generator and an extruder-mounted camera (a little like this one) to perform laser triangulat...
08:12
Security Affairs newsletter Round 418 by Pierluigi Paganini International edition Security Affairs
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are free for you in your email box.
We are in the final!
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections where is reported
Securityaffairs or my name Pierluigi Paganini
Please nominate Security Affairs as your favorite blog.
Nominate Pierluigi Paganini and Security Affairs here here: https://docs.google.com/forms/d/e/1FAIpQLSepvnj8b7QzMdLh7vWEDQDqohjBUsHyn3x3xRdYGCetwVy2DA/viewform
Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press.
06:49
Twitter confirmed that a security incident publicly exposed Circle tweets Security Affairs
A security problem caused the public sharing of private tweets sent to Twitter Circles to users outside of the Circle, the company admitted.
Since August 2022, the Twitter Circle feature allows users to send tweets to a restricted circle of users, these messages are not visible to Twitter users outside the Circle.
As reported by BleepingComputer, around April 7, some Twitter users noticed the issue. The Guardian reported that for weeks users had been reporting Circles tweets receiving likes and views from users outside the circle.
The social network giant confirmed the problem, it started notifying the impacted users.
Were contacting you because your Twitter account may have been potentially impacted by a security incident that occurred earlier this year (April 2023), reads a security incident notification sent by Twitter to the impacted users. In April 2023, a security incident may have allowed users outside of your Twitter Circle to see tweets that should have otherwise been limited to the Circle to which you were posting. This issue was identified by our security team and immediately fixed so that these tweets were no longer visible outside of your Circle.
Weve conducted a thorough investigation to understand how this occurred and have addressed this issue. Twitter is committed to protecting the privacy of the people who use our service, and we understand the risks that an incident like this can introduce and we deeply regret this happened.
The company did not provide details about the security incident.
Since Elon Musk took ownership of the company, a large portion of its staff left the company and at the same time, the platform introduced multiple changes to its code.
We are in the final!
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections where is reported
Securityaffairs or my name Pierluigi Paganini
Please nominate Security Affairs as your favorite blog.
Nominate Pierluigi Paganini and Security Affairs here here: https://docs.google.com/forms/d/e/1FAIpQL...
06:00
Tiny 3D Printed Gaming PC Contains Real Retro Hardware Hackaday

Emulators are easy and convenient, but for some retrocomputing enthusiasts nothing comes close to running classic software on actual era-appropriate hardware. This can become a problem, though, for those into vintage PC gaming: old PCs and their monitors are notoriously large and heavy, meaning that even a modest collection will quickly fill up a decent family home. There is a solution however, as [The Eric Experiment] demonstrates in his latest video. He designed and built a 3D-printed mini PC that runs on an actual 486 processor.
An ordinary desktop motherboard would have required a rather large case to begin with, so [Eric] started his project by buying an old industrial PC board. Such a device has the processor and all main motherboard components sitting on an ISA card, which then connects to other ISA cards through a backplane. This way, a complete system with expansion cards can be made way more compact than even the sleekest desktop PCs of the time. An SD-card-to-IDE converter makes for an extremely slim hard drive replacement, while a Gotek floppy emulator allows the system to boot as if theres actually a floppy drive present.
...05:18
How Music Can Prevent Cognitive Decline SoylentNews
Researchers show the positive impacts of musical activities to counteract brain ageing:
Normal ageing is associated with progressive cognitive decline. But can we train our brain to delay this process? A team from the University of Geneva (UNIGE), HES-SO Geneva and EPFL has discovered that practicing and listening to music can alter cognitive decline in healthy seniors by stimulating the production of grey matter. To achieve these results, the researchers followed over 100 retired people who had never practiced music before. They were enrolled in piano and music awareness training for six months. These results open new prospects for the support of healthy ageing. They are reported in NeuroImage: Reports.
Throughout our lives, our brain remodels itself. Brain morphology and connections change according to the environment and the experiences, for instance when we learn new skills or overcome the consequences of a stroke. However, as we age, this ''brain plasticity'' decreases. The brain also loses grey matter, where our precious neurons are located. This is known as ''brain atrophy''.
Gradually, a cognitive decline appears. Working memory, at the core of many cognitive processes, is one of the cognitive functions suffering the most. Working memory is defined as the process in which we briefly retain and manipulate information in order to achieve a goal, such as remembering a telephone number long enough to write it down or translating a sentence from a foreign language.
[...] The participants were randomly assigned to two groups, regardless of their motivation to play an instrument. The second group had active listening lessons, which focused on instrument recognition and analysis of musical properties in a wide range of musical styles. The classes lasted one hour. Participants in both groups were required to do homework for half an hour a day.
Read more of this story at SoylentNews.
05:00
04:26
House Online Casinos Nz h+ Media
House Online Casinos Nz
These are actually a huge quantity, so in addition they examine many online casinos periodically. Icons are related to the theme of love, securing early leads in their respective teams. This is not any completely different in phrases of blackjack gambling, conducting future casino transactions or simply placing it in your bank account. The casinos are owned and operated by the states two Native American tribes, so this may be a typical video slot in terms of reel mechanics. This is the crypto casino bonus that you shouldnt miss out on as a new Duelbits participant, the faster you will progress up the VIP levels. Yukon Gold Casino Visit Now Introduced in 2004, Yukon Gold Casino is likely one of the finest platforms for online on line casino video games from Apo
Since gamers can enjoy everywhere entry to 888casino games on the go, the bonus can be enjoyed wherever you go. To get began, players simply have to go to the Google Play Store to download the Android app, or get it directly from the 888casino website. The iOS app is on the market online at 888casino or the Apple Store. And for those gamers registering from their desktop, its a cinch getting began. The 100 percent welcome bonus up to NZ$200 is the signature bonus bundle to new 888players. But theres extra there is a Premium Welcome Package which offers players the opportunity to take pleasure in as much as NZ$200 in bonuses throughout their first week of play over their first 5 deposits.
Likewise, in the options menu, the selection of areas has been lowered to the really essential indexes. In addition to the help option, account info and deposit and withdrawal strategies, there are no additional tabs. Thanks to those settings, navigation on the cellphone is really easy.
- A licensed page is your starting point and you should confirm the presence of a valid license issued by the Srij-Gaming Regulation and Inspection Service .
- The firm has more than 16,000 staff and greater than 2,300 land-based betting workplaces worldwide.
- Unfortunately 888 have taken the foolish step of disallowing any rugby union bets with this promotion which is hardly more probably to endear them to their New Zealand prospects.
- Various on-line slots and countless card games can be discovered here.
You may assume you can find a May 2023 promo code for 888 Casino all around the internet. But how many instances have you lastly found a 888 Casino promo code that was either expired or not applicable? We cycle via our offers daily to ensure your couponcode is lively. When you employ 1001couponcodes.co.nz, neglect fruitless searching and disappointment; we have at all times received an up-to-date discount code only for you. Players at 888 casino within the UK are lucky to have two potential cellular platforms available as theres both a downloadable app in addition to a browser-based internet app. IOS u...
02:48
FBI seized other domains used by the shadow eBook library Z-Library Security Affairs
The FBI disrupted once again the illegal eBook library Z-Library the authorities seized several domains used by the service.
The Federal Bureau of Investigation (FBI) seized multiple domains used by the illegal shadow eBook library Z-Library.
Z-Library is the worlds largest illegal library and claims to offer more than 11 million e-books for download. The library has been active since 2009, it offers e-book files in a variety of file formats, stripped of their copyright protections. Z-Library operates as a complex network of approximately 249 interrelated web domains.
The list of the domains seized by the authorities includes singlelogin.me, which is used to register new accounts for the service. The library is still reachable through TOR and I2P networks.
Unfortunately, one of our primary login domains was seized today. Therefore, we recommend using the domain singlelogin.re to log in to your account, as well as to register. Please share this domain with others. reads the messages published by the maintainers of the services on their Telegram Channel.
You can also restore access to your account or create a new one using our magic email address. Just send any letter from your mailbox to this email blackbox@zlib.se, and you will receive your personal access to Z-Library in the auto-generated letter within 35 minutes. We apologize for any inconvenience caused and appreciate your patience.
The seized domain currently displays informing visitors that it has been shut down by the FBI in acc...
01:00
The Meeting of the Minds That Launched AI IEEE Spectrum

The Dartmouth Summer Research Project on Artificial Intelligence, held from 18 June through 17 August of 1956, is widely considered the event that kicked off AI as a research discipline. Organized by John McCarthy, Marvin Minsky, Claude Shannon, and Nathaniel Rochester, it brought together a few dozen of the leading thinkers in AI, computer science, and information theory to map out future paths for investigation.
A group photo [shown above] captured seven of the main participants. When the photo was reprinted in Eliza Stricklands October 2021 article The Turbulent Past and Uncertain Future of Artificial Intelligence, in IEEE Spectrum, the caption identified six people, plus one unknown. So who was this unknown person?
Who is in the photo?
Six of the people in the photo are easy to identify. In the back row, from left to right, we see Oliver Selfridge, Nathaniel Rochester, Marvin Minsky, and John McCarthy. Sitting in front on the left is Ray Solomonoff, and on the right, Claude Shannon. All six contributed to AI, computer science, or related fields in the decades following the Dartmouth workshop.
 In the back
row from left to right are Oliver Selfridge, Nathaniel Rochester,
Marvin Minsky, and John McCarthy. In front on the left is Ray
Solomonoff; on the right, Claude Shannon. The identity of the
person between Solomonoff and Shannon remained a mystery for some
time....
In the back
row from left to right are Oliver Selfridge, Nathaniel Rochester,
Marvin Minsky, and John McCarthy. In front on the left is Ray
Solomonoff; on the right, Claude Shannon. The identity of the
person between Solomonoff and Shannon remained a mystery for some
time....
Saturday, 06 May
21:02
Megapari App Obtain For Android & Ios 2023 Latest Model Welcome To h+ Media
Megapari App Obtain For Android & Ios 2023 Latest Model Welcome To
Those who wish to win the biggest amount of cash and are willing to take dangers prefer specific bets. Akhila Reddy ist the most recent member of our Betting-India.pro group. She is a digital native and loves sports and also sports betting. If you need to get all the details about how to rollover the bonus of your favorite bookie, then you should try her posts and explanations.
Megapari supplies you with attractive odds across all kinds of sports and betting markets. I discovered that it was similar to the you wouldnt have the ability to inform the difference between the two!
At the second, the corporate has only released the application for Android. You can find a link to this application instantly on the official Megapari site. The technical requirement for installing the applying on the gadget is Android OS 5+ and later. The bookmaker factors out in its terms and circumstances that the services provided arent intended for individuals underneath 18 years of age. Megapari betting firm has an official license from the Government of Curacao.
Bets may be placed on the official web site, its cell model, and the cellular software program. Those preferring on-line casino video games to sports betting will be spoiled for alternative once they see Megaparis casino library. As for the general usability, Megapari provides straightforward registration and a responsive interface that works seamlessly on PCs and mobile devices alike. The Megapari mobile apps functionality on Android is the same as it is on desktop or different platforms.
The support group is competent in their queries and helps solve problems of any complexity. And along with the beneficiant bonus system, the sport turns into much more enjoyable. When you enroll with Megapari, purchasers log in to get present app upgrades. The link to the mannequin new model of the Megapari app could be obtainable through e mail. You may get mail notices of latest rewards and developments from the bookmaker.
This has opened up a gray space, which has allowed some on-line betting apps to function within the country. One of the preferred cellular wallets in India, supports immediate deposits and withdrawals for online gambling. The interface of Parimatch is easy to use, allowing bettors to quickly find the data they need about gamers, teams, odds, and more.
25% bonus on third deposit up to 4 hundred EUR + forty freespins. The bookmakers app offers entry to higher than 1,000 events per day and permits bettors to make profit with reside betting. You do not rely upon one thing that can decelerate and even intrude with the betting course of.
For cellphone customers, there is additionally a cellular
18:33
1xbet Bonus 2023
As a part of both the 1xbet Casino Welcome Bonus and other offers, customers from India can get free spins to play one of the best slots. This means, you make free spins on the casino, win real money, and can withdraw it from 1xbet. At 1xbet login and registration are actions which are mandatory for newcomers and guests to the platform. When creating an account, it is essential to enter real info. It will be potential to register through the official web site, app, cellular version. The major benefit of the official 1xbet apk is the privateness of the data.
Yes, the legal guidelines dont regulate on-line gambling so you probably can relaxation assured you probably can play at on-line casinos such as 1xBet as an Indian participant with no downside. To wagering the bonus, you will need to put bets until they amount to the bonus quantity multiplied by 5 occasions. Only express bets with three occasions or more at odds of 1.four count. That is, if you deposited 5,000 rupees and want the identical bonus, you will need to wager 25,000 rupees. It seems that the welcome bonus can be seen as a kind of discount. Regardless of what type of registration you choose, the form always incorporates a line in your 1xbet promo code.
At least three occasions throughout the accumulator will have to have odds of 1.forty or higher. You can get a 100% first deposit bonus as a lot as 9,200 whenever you enroll with the 1xBet promo code luckydice. But as we talked about previously, 1xBet India have made an effort to cater for their Indian clients. The 1xBet cricket offering is large, and as youd anticipate, they offer a variety of leagues from around the world in addition to some of the in depth in-play offerings. Navigation is straightforward as theyve made a quicklink to the 1xBet cricket part and have all of the 1xBet cricket markets seem first on the in-play part. 1xBet have grown to be one of many worlds largest onling playing operators during the last decade.
1xBet analyses the wants of recent society and continuously improves its merchandise. In it, customers cant solely wager on cricket and additional sports activities wherever theyre but additionally find different thrilling presents. So, for instance, you presumably can watch matches of your favorite teams reside, play within the on line casino or play unique games in the 1xGames section. 1xBet is a sports activities betting and casino website the place youll have the ability to wager real money for an opportunity to win money and prizes. There are loads of bets and on line casino video games youll be able to select from, including betting on cricket and football, in addition to slots, table games and stay on line casino.
This is one other function that makes 1xBet stand out over its opponents, and to be most popular by hundreds of thousands all over the world. The process is very comparable to placing a single...
18:29
On-line Appointment For Patients h+ Media
On-line Appointment For Patients
You are a first-time gamer, then 1xBet India gaming is the place for you to take pleasure in desktop or cellular gaming. Your account will now be credited accordingly with the 200% matched bonus relying on the country you reside in and the preliminary deposit you loaded. When signing up and get an exclusive 1xbet provide 130% up to INR.
Licensing is extended via the official website, cellular model, app. Therefore, confidentiality of knowledge also applies via different adaptations of the platform. Licence info is published on the backside of the start web page of the BKs web site. The table beneath discusses the options of 1xBets digital platform so far as bonuses, playing, sports and cybersport occasions are concerned. The bonus system of the virtual club consists of deposit and no deposit rewards. For newcomers and regular customers there are reward bonus codes.
Now its your turn to find it out, and with a 1xbet promo code, itll be much simpler to do. Each new shopper at 1xBet is entitled to a welcome bonus. It represents a sure amount of money that the bookmaker provides you free of charge, it is credited to you after registration and the primary deposit. You can use the money to put bets and later withdraw them to your card. At 1xBet the welcome bonus is greater than most opponents and is one hundred pc of the deposit quantity up to Rs. 8,500. To get it you should be over 18 years old, register at 1xBet and deposit your stability in any method convenient for you.
1x wager provide you with large jackpots in any of those categories, and for the TOTO free bets, we now have bonuses ranging from 100 to 7000 bonus factors. It is necessary to guarantee that any betting website you choose to play at has a proper license to function and is regulated by a reliable organization. As a end result, through the present season, after a 3rd of the distance, Tottenham is quite seriously lagging behind its direct opponents. On the 1xBet sport betting web site, you can make a forecast for the future of the team.
The concern may be lengthy and annoying when it comes to further checks. It is necessary to read and settle for the user agreement. Links to the principles pages will be provided throughout registration.
One of the features that make 1xBet stand out from another bookmaker sites is its complete mobile app. With the 1xBet mobile app, you can access the sportsbook part and online casino part of the betting website. Our betting platform has 1xBet app for Android units available to be downloaded for free from the main web page for many who would like to download it. The 1xBet app is similar as the desktop website or browser model when it comes to features.
Teams of eleven gamers ought to score probably the most targets in opposition to their opponents to win. At 1xbet all soccer tournaments can be present in your betting. You may have the flexibility to observe LIVE Br...
18:28
1xbet Evaluation India 2023 Bonus One Hundred Pc As Much As 20,000 h+ Media
1xbet Evaluation India 2023 Bonus One Hundred Pc As Much As 20,000
We could make bets while watching the Premier League, Champions League and many others. Aside from these, youll discover lots of other great offers on 1xbet. X2 Wednesday is another great offer for 1xbet purchasers. Everyone who participates, receives, or redeems the bonus on Lucky Friday can get another $100 the following Wednesday.
There are 3 ways to register on the site, one click on, by telephone, and by e mail. It is beneficial to register through one click as it is the quickest possibility among the many three. All you should do is add your nation and you would possibly be good to go. Other options require you to fill in your personal particulars and confirm your email handle. Being a model new person, you must register to 1xBet by way of crictips.com.
The operator has a stay on line casino part where you can take pleasure in a more realistic experience enjoying in opposition to different gamers and a real human vendor. The reside dealer video games obtainable at 1xBet embody Live Roulette, Live Blackjack and Live Baccarat. There are a quantity of betting choices out there for gamers at 1xBet. You can place the common bet types, corresponding to 3-way bets, each teams to score, under/over bets and double chance bets. The operator also offers particular prop bets, which are available for many sports.
Some are occasional or centered round specific competitions or groups. Bets that pass via the promo code are non-refundable. The bonus will be credited to your account AUTOMATICALLY after the deposit is made. Create your new account by completing the registration kind. You will want to choose your nation India and currency .
- But as we talked about beforehand, 1xBet India have made an effort to cater for his or her Indian prospects.
- The bonus quantity should be wagered five instances in accumulator bets with at least three events in each.
- For me, 1xBets nice odds and reliable withdrawals are its key benefits.
It is essential to note that every one submitted paperwork should be valid and up-to-date to guarantee that the verification process to achieve success. Once verified, users could have access to all features on the platform together with deposits, withdrawals, bonuses and promotions. Indian players utilizing the 1x Bet app can declare all of the common kinds of bonuses such as free bets, welcome bonuses, cashback bonuses and so on. However, the sports activities betting site doesnt supply an unique bonus to users of its mobile app in the meanwhile.
It was a positive experience for me and I will certainly continue to use 1xbet in the future. The buyer support at 1xBet is without any doubt value trusting. If you have any questions or difficulties with playing at this betting company, its representatives will remedy all your problems as soon as attainable...