| IndyWatch Science and Technology News Feed Archiver | |
 |
Go Back:30 Days | 7 Days | 2 Days | 1 Day |
|
IndyWatch Science and Technology News Feed was generated at World News IndyWatch. |
|
Wednesday, 26 April
00:22
Pro-Russia hackers attack European air traffic control website, but dont panic! Flights continue as normal Graham Cluley
Eurocontrol, the European air traffic control agency, has revealed that it has been under cyber attack for the last week, and says that pro-Russian hackers have claimed responsibility for the disruption. When you first see the headline in the likes of the Wall Street Journal, it's a scary thing to read. But dig a little deeper, and you realise that the err.. sky is not falling. Read more in my article on the Hot for Security blog.
00:07
Google researchers found multiple security issues in Intel TDX Security Affairs
Google Cloud Security and Project Zero researchers found multiple vulnerabilities in the Intel Trust Domain Extensions (TDX).
Google Cloud Security and Project Zero researchers, working with Intel experts, discovered multiple vulnerabilities in the Intel Trust Domain Extensions (TDX).
The Intel Trust Domain Extensions (Intel TDX) allows to deploy hardware-isolated, virtual machines (VMs) called trust domains (TDs). Intel TDX is designed to isolate VMs from the virtual-machine manager (VMM)/hypervisor and any other non-TD software on the platform to protect TDs from a broad range of software.
The Google researchers discovered ten security issues in Intel TDX during a nine-month audit.
The researchers reviewed the source code of the core Intel TDX software components and the design and documentation provided by Intel. The issues inspected by the researchers included arbitrary code execution in a privileged security context, cryptographic weaknesses and oracles, temporary and permanent denial of service, and weaknesses in debug or deployment facilities.
The review resulted in 81 potential attack vectors and resulted in 10 confirmed security issues and 5 defense in depth changes over a period of 9 months. reads the report released by Google.
Intel addressed nine of the discovered issues by changing the TDX code, while the tenth flaw required changes to the guide for writing a BIOS to support TDX.
These flaws were not assigned CVE identifiers, but Intel internally assigned CVSS v3.1 scores to them.
The most serious issue discovered by the researchers was the Exit Path Interrupt Hijacking when returning from ACM mode. The issue received a CVSS score of 9.3, experts pointed out that an attacker can trigger it to achieve arbitrary code execution in the privileged ACM execution mode.
Its positive to note that of the security issues discovered only 2 would be considered memory safety issues. By far the most common class of security issues discovered were logical bugs due to the complexity of Intel processors generally, and the TDX feature specifically. continues the analysis. For example the Exit Path Interrupt Hijacking issue was a result of the complex set of steps necessary to switch between the privileged ACM mode and normal operating mode. Completely eliminating these logical issues is much more difficult than moving to a memory safe language such as Rust.
The above were mitigated before the...
00:03
An update on the GCC frontend for Rust LWN.net
Philip Herron and Arthur Cohen have posted an update on the status of gccrs the GCC frontend for the Rust language and why it will not be a part of the upcoming GCC 13 release.
While all of this appears like a lot of work, we are confident in our progress and hope to get closer and closer to getting the core crate working in the next few months. There is also a lot of important work remaining in order to produce a valid Rust compiler, which is why we will spend the coming months focusing on the core crate as well as a borrow-checker implementation, and the development of the necessary tooling to allow us to try and pass the Rust 1.49 testsuite. library with our compiler in the next major GCC release, GCC 14, and hope to backport enough changes to the GCC 13 branch to get the core crate working in time for the GCC 13.2 release. This will enable users to easily start experimenting with the compiler for #![no_std] Rust programs and, hopefully, some embedded targets.
00:00
FET: The Friendly Efficient Transistor Hackaday

If you ever work with a circuit that controls a decent amount of current, you will often encounter a FET a Field-Effect Transistor. Whether you want to control a couple of powerful LEDs, switch a USB device on and off, or drive a motor, somewhere in the picture, theres usually a FET doing the heavy lifting. You might not be familiar with how a FET works, how to use one and what are the caveats lets go through the basics.
...
00:00
VMware announces new security capabilities to help protect hybrid workforce Help Net Security
VMware has unveiled new capabilities that deliver lateral security across multi-cloud environments so customers can better see and stop more threats and innovations to its Workspace ONE platform that will better enable organizations to secure their hybrid workforce. VMware Contexa, a threat intelligence cloud powering VMwares suite of security solutions, finds that cybercriminals make only 2-3 lateral moves to reach their target. Preventing lateral movement requires an end-to-end view across users, devices, networks, apps, and More
The post VMware announces new security capabilities to help protect hybrid workforce appeared first on Help Net Security.
Tuesday, 25 April
23:40
Sherlock Holmes and the Case of the Spherical Lens: Reflections on a Gravity Lens Telescope (Part I) Centauri Dreams Imagining and Planning Interstellar Exploration
A growing interest in JPLs Solar Gravitational Lens mission here takes Wes Kelly on an odyssey into the past. A long-time Centauri Dreams contributor, Wes looks at the discovery of gravitational lensing, which takes us back not only to Einstein but to a putative planet that never existed. Part II of the essay, which will run in a few days, will treat the thorny issues lensing presents as we consider untangling the close-up image of an exoplanet, using an observatory hundreds of AU from the Sun. Wes has pursued a lifetime interest in flight through the air, in orbit and even to the stars. Known on Centauri Dreams as wdk, he runs a small aerospace company in Houston (Triton Systems,LLC), founded for the purpose of developing a partially reusable HTOL launch vehicle for delivering small satellites to space. The company also provides aerospace engineering services to NASA and other customers, starting with contracts in the 1990s. Kelly studied aerospace engineering at the University of Michigan after service in the US Air Force, and went on to do graduate work at the University of Washington. He has been involved with early design and development of the Space Shuttle, expendable launch systems, solar electric propulsion systems and a succession of preliminary vehicle designs. With the International Space Station, he worked both as engineer and a translator or interpreter in meetings with Russian engineering teams on areas such as propulsion, guidance and control.
by Wes Kelly

Part 1. Each of the Known Suspects Has an Alibi Related to His Whereabouts.
[This article originated with an inquiry from our local astronomy club for a talk during an indoor meeting anticipating a cloudy sky.]
Among topics arising on Centauri Dreams, reader response often turns to investigation: the original scientific reports plus surrounding evidence, the basis for many of the websites entries. And when a topic is unfamiliar or on a frontier of knowledge, reader investigation can be a matter of playing catch up, as I can attest. Fair enough. Scientific observations, data interpretations or hypotheses Take the matter of heading out to deep space to collect light from the other side of the sun and then deconvolute it to extract the image of an exoplanet. The steps to this objective have to be judged individually or reviewed as stepping stones, connecting lines of inquiry Or maybe going so far as...
23:38
TODAY: Watch Ispace Attempt to Land on the Moon for the First Time SoylentNews
Watch ispace attempt to land on the moon for the first time:
After five long months journeying through space, ispace's Hakuto-R lander is ready to greet the lunar surface.The Japanese company is expecting to land Hakuto-R at 12:40 PM EST today. If successful, this first mission will no doubt be a huge boon for ispace's ambitious plans to send two subsequent landers to the moon in 2024 and 2025. It would also make them the first private company to land on the moon, and the first spacecraft from Japan to do so. (China, the United States, and the USSR have been the only nations to reach the lunar surface.)This first mission, appropriately named Mission 1, kicked off last December when a SpaceX Falcon 9 launched the lander into space. Since then, the lander has performed a number of maneuvers to stay on track in its path to the moon. At its farthest point, Hakuto-R traveled as much as 1.4 million kilometers from Earth.
The livestream will kick-off one hour prior to landing at 11:40 EST.
Link to stream.
Read more of this story at SoylentNews.
23:32
Security updates for Tuesday LWN.net
Security updates have been issued by CentOS (firefox, java-11-openjdk, and thunderbird), Debian (apache2), Fedora (kernel), Oracle (emacs), Red Hat (emacs, haproxy, java-1.8.0-openjdk, kernel, kernel-rt, kpatch-patch, pcs, pki-core:10.6, and qatzip), and SUSE (avahi, cdi-apiserver-container, cdi-cloner-container, cdi- controller-container, cdi-importer-container, cdi-operator-container, cdi- uploadproxy-container, cdi-uploadserver-container, cont, giflib, kernel, kubevirt, virt-api-container, virt-controller-container, virt-handler-container, virt-launcher-container, virt-libguestfs-tools- container, virt-operator-container, ovmf, and protobuf-c).
23:26
New SLP Vulnerability Could Let Attackers Launch 2200x Powerful DDoS Attacks The Hacker News
Details have emerged about a high-severity security vulnerability impacting Service Location Protocol (SLP) that could be weaponized to launch volumetric denial-of-service attacks against targets. "Attackers exploiting this vulnerability could leverage vulnerable instances to launch massive Denial-of-Service (DoS) amplification attacks with a factor as high as 2200 times, potentially making it
23:23
Goldilocks zone may not be a good metric for whether life exists on exoplanets, say astrobiologists Lifeboat News: The Blog
Most exoplanets lying in the habitable zones around stars are in fact inhospitable to plant life as we know it. That is according to a new study from microbiologists and astronomers at the University of Georgia who say that taking into account the light a planet receives as well as its ability to hold liquid water is a better definition of whether life could exist on other planets.
The Habitable Zone (HZ) is traditionally defined to be the range of distances around a star where an exoplanet can support liquid water on its surface. Too far, and the planet remains frozen like Mars. Too close and the oceans evaporate, as happened to Venus. The zone in the middle is neither too hot, nor too cold, but just right the so-called Goldilocks zone.
Nothing certain is known about the properties and requirements of alien life. However, there are generally two schools of thought in astrobiology. One is that evolution on other planets can figure out ways to sidestep seemingly insurmountable barriers to life as we know it, while others claim that life is everywhere bounded by the same universal physical principles, and can thus only operate a certain way, similar to as on Earth.
23:22
This Private Moon Lander Is Kicking Off a Commercial Lunar Race Lifeboat News: The Blog
The Japanese company Ispace could be the first to safely touch down on the moons surface, with more spacecraft following later this year.
23:22
The case for Singularity Activism Lifeboat News: The Blog
New AI systems released in 2023 demonstrate remarkable properties that have taken most observers by surprise. The potential both for positive AI outcomes and negative AI outcomes seems to have been accelerated. This leads to five responses:
1.) Yawn AI has been overhyped before, and is being overhyped again now. Lets keep our attention on more tangible issues.
2.) Full speed ahead with more capabilities Lets get to the wonderful positive outcomes of AI as soon as possible, sidestepping those small-minded would-be regulators who would stifle all the innovation out of the industry.
23:14
FFmpeg Now Works With VA-API On Windows Thanks To Microsoft Phoronix
VA-API has been around for more than one decade as the most common Linux Video Acceleration API that works across multiple GPU/driver vendors. It's been Linux-focused to this point while thanks to the work of Microsoft has begun seeing support on Windows...
23:04
Iranian Hackers Launch Sophisticated Attacks Targeting Israel with PowerLess Backdoor The Hacker News
An Iranian nation-state threat actor has been linked to a new wave of phishing attacks targeting Israel that's designed to deploy firm Check Point is tracking the activity cluster under its mythical creature handle Educated Manticore, which exhibits "strong overlaps" with a hacking crew known as APT35, Charming Kitten, Cobalt
23:02
Universal Flu Candidate Vaccine Appears to be Safe and Promising in Small-Scale Trial SoylentNews
If I understand it correctly, researchers made a vaccine that targets the proteins common to all flu viruses instead of the part that changes every year. They tested it on 52 people and found it safe and effective.
A Widge, et al. An Influenza Hemagglutinin Stem
Nanoparticle 1 Vaccine Induces Cross
Group 1 Neutralizing Antibodies in Healthy Adults. Science
Translational Medicine https://www.science.org/doi/10.1126/scitranslmed.ade4790
S Andrews, et al. An Influenza H1 Hemagglutinin Stem-Only Immunogen Elicits a Broadly Cross-Reactive B Cell Response in Humans. Science Translational Medicine https://www.science.org/doi/10.1126/scitranslmed.ade4976
Universal Influenza Candidate Vaccine Performs Well in Phase 1 Trial NIAID Now https://www.niaid.nih.gov/news-events/vrc-uni-flu-vax
Scientists at NIAID's Vaccine Research Center (VRC) report in two new studies that an experimental influenza vaccine, designed to elicit immunity against a broad range of influenza viruses, performed well in a small trial of volunteers. In fact, the vaccine has advanced to a second trial led by scientists at Duke University through NIAID's Collaborative Influenza Vaccine Innovation Centers (CIVICs).
In a phase 1 clinical trial of 52 volunteers, the vaccine developed by the VRC known as H1ssF (influenza H1 hemagglutinin stabilized stem ferritin nanoparticle vaccine) was safe, well-tolerated, and induced broad antibody responses that target the hemagglutinin stem. The two new studies assessing the nanoparticle vaccine published April 19 in Science Translational Medicine.
Read more of this story at SoylentNews.
23:00
Abnormal Security expands its platform and launches new products Help Net Security
At RSA Conference 2023, Abnormal Security launched three new products focused on expanding security detection for Slack, Microsoft Teams and Zoom. The company is also extending the platform to better model identity behavior through the ingestion of signals from additional sources, including CrowdStrike, Okta, Slack, Teams and Zoom. Email remains the most common path into an organization, but cybercriminals are steadily shifting their tactics and targeting additional entry points across the enterprise. The recent attacks More
The post Abnormal Security expands its platform and launches new products appeared first on Help Net Security.
22:34
Mesa's Rusticl Driver Adds Optional OpenCL FP64 Support Phoronix
The newest feature added by Red Hat engineer Karol Herbst to the Rusticl Mesa OpenCL open-source driver is FP64 support...
22:27
LibrePlanet: Weiming Hu on Free software for Environmental Sciences Techrights
Summary: The above LibrePlanet talk by Weiming Hu is a remote (not physical presence) talk and it was uploaded by the FSF last week (slides here; PeerTube link); From the official page: Open science is a movement that promotes the freedom to share knowledge and data in science. Its recent success largely depends on our ability to reproduce and then improve on existing research products. It is about ensuring that researchers have sufficient access to information and the necessary tools for analysis. This movement goes hand in hand with the free software movement, as it has the potential to revolutionize sciences by providing powerful tools for data analysis, modeling, and visualization. I would like to focus my talk on the connection and missing links between free software and open science, particularly in environmental and data sciences. The talk is devoted to raising awareness and promoting conversations on how we can better advance sciences with free software and knowledge sharing.
Licence: CC BY SA 4.0
22:20
Linux 6.4 Phoronix
While often times the EXT4 file-system driver updates for new Linux kernel merge windows can be rather mundane given the maturity of this widely-used Linux file-system, this time around for Linux 6.4 it's a bit more exciting...
22:05
Xen Security Advisory 430 v2 (CVE-2022-42335) - x86 shadow paging arbitrary pointer dereference Open Source Security
Posted by Xen . org security team on Apr 25
Xen Security Advisory CVE-2022-42335 / XSA-430x86 shadow paging arbitrary pointer dereference
UPDATES IN VERSION 2
====================
Public release.
ISSUE DESCRIPTION
=================
In environments where host assisted address translation is necessary
but Hardware Assisted Paging (HAP) is unavailable, Xen will run guests
in so called shadow mode. Due to too lax a check...
22:00
RidgeShield monitors traffic across workloads and enforces unified security policies Help Net Security
At RSA Conference 2023, Ridge Security announced Ridge Security RidgeShield, an automated, cloud workload protection and testing solution. As organizations increasingly move their workloads to the cloud, they face new and complex security challenges that traditional security solutions are not designed to handle. RidgeShield addresses these challenges with a zero-trust micro-segmentation technology to secure cloud workloads across on-premises, hybrid cloud, or multi-cloud environments, protecting against todays sophisticated cybersecurity threats. Securing cloud workloads can be a More
The post RidgeShield monitors traffic across workloads and enforces unified security policies appeared first on Help Net Security.
21:53
Modernizing Vulnerability Management: The Move Toward Exposure Management The Hacker News
Managing vulnerabilities in the constantly evolving technological landscape is a difficult task. Although vulnerabilities emerge regularly, not all vulnerabilities present the same level of risk. Traditional metrics such as CVSS score or the number of vulnerabilities are insufficient for effective vulnerability management as they lack business context, prioritization, and understanding of
21:33
All That Microsoft Has Left Now is Distraction and Destruction (Layoffs and Deflection Aplenty) Techrights
Video
download link | md5sum
3c1252ce2d09faaf2fc6f4a0ebd336b8
Week of Microsoft Chaff and Layoffs
Creative Commons Attribution-No Derivative Works 4.0
Summary: Microsoft is losing it; as a result, the media is being co-opted and trolling by Microsoft enablers appears to have gotten worse than usual (borderline illegal)
WITH many Microsoft layoffs every month this year (no, its not just the alleged 10,000 from January!) its worth looking back at and properly examining what weve published so far this week (quite a lot yesterday). It seems to have attracted particularly nasty and sometimes illegal trolling, basically vandalising the IRC network by all means available. It resulted in plenty of distraction and time-wasting.
It seems to have attracted particularly nasty and sometimes illegal trolling, basically vandalising the IRC network by all means available.The video above focuses on what I studied this morning. I closely monitor the situation at Microsoft (with focus on layoffs) every 30 minutes or so/thereabouts. It looks like some truly nasty s*** is about to hit the fan, but endless fluff about s***GPT will be used to change the subject or distract from the substance. For this week we shall prioritise articles on this topic as we try to take a better glance, peering beyond the smokescreen and Microsofts paid-for spam (plenty of it this week, including the straw man that Microsoft means security and any confrontations to that claim are sexism; several British publishers played along and actively participated in this ludicrous PR).
21:30
AWS boosts Amazon GuardDuty with 3 new capabilities to protect varied workloads Help Net Security
AWS has unveiled three new capabilities for Amazon GuardDuty, AWSs threat detection service, that further strengthen customer security through expanded coverage and continuous enhancements in machine learning, anomaly detection, and integrated threat intelligence. GuardDuty is part of a broad set of AWS security services that help customers identify potential security risks, so they can respond quickly, freeing security teams to focus on tasks with the highest value. The three new capabilities expand GuardDuty protection to More
The post AWS boosts Amazon GuardDuty with 3 new capabilities to protect varied workloads appeared first on Help Net Security.
21:27
Lazarus Subgroup Targeting Apple Devices with New RustBucket macOS Malware The Hacker News
A financially-motivated North Korean threat actor is suspected to be behind a new Apple macOS malware strain called RustBucket. "[RustBucket] communicates with command and control (C2) servers to download and execute various payloads," Jamf Threat Labs researchers Ferdous Saljooki and Jaron Bradley said in a technical report published last week. The Apple device management company attributed it
21:26
Lori Angela Nagel on Promoting Free/Libre Software Philosophy Techrights
Video download link (skip to about 15 seconds from the start)
Summary: The above LibrePlanet talk was uploaded a week ago by the FSF (slides here; PeerTube link has the wrong video); From the official page: The hardest part about promoting the free software philosophy is getting people interested enough in the conversation to listen even if they arent already excited about technology topics. However, most people use software today, yet have complaints and fears about it. Instead of merely waiting around for the conversation to turn into a discussion about software usage or technology woes and fears, it helps to come up with powerful questions that can turn conversations about anything into conversations about software and why it needs to have the four freedoms, yet still keeping it engaging for all participants so that it is relevant. This discussion will be about taking topics people like to discuss and turning them into freedom respecting software topics by relating them whatever people are currently talking about using audience supplied examples. These discussions can take place in forums or chat, online or in person.
Licence: CC BY SA 4.0
21:22
Ransomware Hackers Using AuKill Tool to Disable EDR Software Using BYOVD Attack Lifeboat News: The Blog
Play ransomware is notable for not only utilizing intermittent encryption to speed up the process, but also for the fact that its not operated on a ransomware-as-a-service (RaaS) model. Evidence gathered so far points to Balloonfly carrying out the ransomware attacks as well as developing the malware themselves.
Grixba and VSS Copying Tool are the latest in a long list of proprietary tools such as Exmatter, Exbyte, and PowerShell-based scripts that are used by ransomware actors to establish more control over their operations, while also adding extra layers of complexity to persist in compromised environments and evade detection.
Another technique increasingly adopted by financially-motivated groups is the use of the Go programming language to develop cross-platform malware and resist analysis and reverse engineering efforts.
21:22
Hackers Exploit Outdated WordPress Plugin to Backdoor Thousands of WordPress Sites Lifeboat News: The Blog
Hackers are exploiting an outdated WordPress plugin, Eval PHP, to secretly backdoor websites in an ongoing campaign.
21:22
New All-in-One EvilExtractor Stealer for Windows Systems Surfaces on the Dark Web Lifeboat News: The Blog
A new all-in-one stealer malware named EvilExtractor (also spelled Evil Extractor) is being marketed for sale for other threat actors to steal data and files from Windows systems.
It includes several modules that all work via an FTP service, Fortinet FortiGuard Labs researcher Cara Lin said. It also contains environment checking and Anti-VM functions. Its primary purpose seems to be to steal browser data and information from compromised endpoints and then upload it to the attackers FTP server.
The network security company said it observed a surge in attacks spreading the malware in the wild in March 2023, with a majority of the victims located in Europe and the U.S. While marketed as an educational tool, EvilExtractor has been adopted by threat actors for use as an information stealer.
21:00
3D Print For Extreme Temperatures (But Only If Youre NASA) Hackaday

At the level pursued by many Hackaday readers, the advent of affordable 3D printing has revolutionised prototyping, as long as the resolution of a desktop printer is adequate and the part can be made in a thermoplastic or resin, it can be in your hands without too long a wait. The same has happened at a much higher level, but for those with extremely deep pockets it extends into exotic high-performance materials which owners of a desktop FDM machine can only dream of.
NASA for example are reporting their new 3D printable nickel-cobalt-chromium alloy that can produce extra-durable laser-sintered metal parts that van withstand up to 2000 Fahrenheit, or 1033 Celcius for non-Americans. This has obvious applications for an organisation producing spacecraft, so naturally they are excited about it.
The alloy receives some of its properties because of its oxide-dispersion-strengthened composition, in which grains of metal oxide are dispersed among its structure. Were not metallurgists here at Hackaday, but we understand that the inconsistencies in the layers of metal atoms...
21:00
GrammaTech and ArmorCode unify application security tools and intelligence Help Net Security
GrammaTech and ArmorCode announced a technology integration partnership to help customers automate product security across development, testing, feedback and deployment. The GrammaTech CodeSonar SAST (static application security testing) platform provides deep safety and security vulnerability intelligence to ArmorCode for orchestrating application security operations within CI/CD pipelines. The companies are collaborating to offer integrated solutions for ensuring the safety and security of mission-critical automotive, aerospace, enterprise, and industrial products. GrammaTech and ArmorCode will demonstrate their products More
The post GrammaTech and ArmorCode unify application security tools and intelligence appeared first on Help Net Security.
20:47
Google adds new risk assessment tool for Chrome extensions Help Net Security
Google has made available a new tool for Google Workspace admins and security teams to make an assessment of the risk different Chrome extensions may present to their users: Spin.AI App Risk Assessment. The tool is available through the Chrome Browser Cloud Management console and provides admins with valuable insights into potential security threats. The Spin.AI App Risk Assessment tool for Chrome extensions The tool allows administrators to: View app and extension usage details Configure More
The post Google adds new risk assessment tool for Chrome extensions appeared first on Help Net Security.
20:46
Linux 6.4 Can Run As A Confidential AMD SEV-SNP vTOM Guest On Microsoft Hyper-V Phoronix
For those making use of Microsoft Hyper-V virtualization there are some notable additions to find with the in-development Linux 6.4 kernel...
20:42
How Sirius (Mis)Handled a Crisis in 2022 schestowitz.com
Video
download link | md5sum
e6d79ef1efc46c2747184e07504811b1
Sirius Plans That Never Materialised
Creative Commons Attribution-No Derivative Works 4.0
Summary: The gross mismanagement of Sirius Open Source is a longstanding issue; it goes back to 2019 and it culminated in growing levels of deceit, set aside fraud aspects, so today we take a look back at another meeting from 2022
LISTENING to audio from almost a year ago (we have about 5 hours of audio from last summer; this was shared with staff), it now seems clear that Sirius Open Source had a lot of fantasies while drifting further and further away from well, Open Source.
In the start of summer (2022-06-01) we had a second meeting (out of 3 in total) about the future of the company and studying it in retrospect its easy to understand [crer 168114 witch-hunts], scare tactics etc. Colleagues were subjected to threats and were isolated from their peers. They deemed this approach evil (direct quote).
Much of the meat of the meeting starts a long time after the start with staff thats actually technical (and actually doing all the work, even 24/7) raising questions while the others repeat the same talking points. Basically, managers (which at that point where like half of all the staff) were discussing many options and presenting each. They collected suggestions from staff and eventually threw all of them out. Staff was a bit surprised that after these consultations every suggestion from the staff was rejected. Every single one of them!
One of the self-appointed managers (no relevant skills whatsoever) was discussing the scoring criteria e.g. what will be assessed in appraisals. She was only reading the script/presentation. Its highly probable she was fully aware of the pension fraud and she may have directly participated in that. An opportunistic career-climbing narcissist. The discussi...
20:39
Google Cloud Introduces Security AI Workbench for Faster Threat Detection and Analysis The Hacker News
Google's cloud division is following in the footsteps of Microsoft with the launch of Security AI Workbench that leverages generative AI models to gain better visibility into the threat landscape. Powering the cybersecurity suite is Sec-PaLM, a specialized large language model (LLM) that's "fine-tuned for security use cases." The idea is to take advantage of the latest advances in AI to augment
20:34
Google Authenticator App now supports Google Account synchronization Security Affairs
Google announced that its Authenticator app for Android and iOS now supports Google Account synchronization.
Google announced that its Google Authenticator app for both iOS and Android now supports Google Account synchronization that allows to safely backup users one-time codes to their Google Account.
The company states that users over the years have faced the complexity of dealing with lost or stolen devices that had Google Authenticator installed. Since one-time codes in Authenticator were only stored on a single device if a user lost that device will be not able to sign in to any service on which theyd set up 2FA using Authenticator.
With this update were rolling out a solution to this problem, making one time codes more durable by storing them safely in users Google Account. This change means users are better protected from lockout and that services can rely on users retaining access, increasing both convenience and security. reads the announcement.
The feature announced by Google is optional.
To try the new Authenticator with Google Account synchronization, simply update the app and follow the prompts. concludes the announcement.
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections:
- The Teacher Most Educational Blog
- The Entertainer Most Entertaining Blog
- The Tech Whizz Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please nominate Security Affairs as your favorite blog.
...
20:31
The Sirius Open Source Fantasy Part III Staff Input (From Technical Workers) Not Accepted Techrights
Series parts:
- The Sirius Open Source Fantasy Part I In 2022 the Company Was Already Too Deep in Debt
- The Sirius Open Source Fantasy Part II Briefings About the Company
- YOU ARE HERE Staff Input (From Technical Workers) Not Accepted
Video
download link | md5sum
e6d79ef1efc46c2747184e07504811b1
Sirius Plans That Never Materialised
Creative Commons Attribution-No Derivative Works 4.0
Summary: The gross mismanagement of Sirius Open Source is a longstanding issue; it goes back to 2019 and it culminated in growing levels of deceit, set aside fraud aspects, so today we take a look back at another meeting from 2022
LISTENING to audio from almost a year ago (we have about 5 hours of audio from last summer; this was shared with staff), it now seems clear that Sirius Open Source had a lot of fantasies while drifting further and further away from well, Open Source.
it now seems clear that Sirius Open Source had a lot of fantasies while drifting further and further away from well, Open Source.In the start of summer (2022-06-01) we had a second meeting (out of 3 in total) about the future of the company and studying it in retrospect its easy to understand witch-hunts, scare tactics etc. Colleagues were subjected to threats and were isolated from their p...
20:26
Initial Apple M2 Support & Other 64-bit ARM Changes For Linux 6.4 Phoronix
On Monday the ARM64 (AArch64) architecture code changes were submitted for the in-development Linux 6.4 kernel along with the various SoC updates and various platform/machine additions for ARM hardware with this new kernel version...
20:15
MITRE Caldera for OT tool enables security teams to run automated adversary emulation exercises Help Net Security
MITRE is launching its MITRE Caldera for OT tool, which allows security teams to run automated adversary emulation exercises that are specifically targeted against operational technology (OT). At RSA Conference 2023, MITRE is also showcasing its Infrastructure Susceptibility Analysis (ISA) to identify and prioritize mitigations by looking at how adversaries compromise infrastructure and what is needed to stop them. Cybersecurity within critical infrastructure is paramount for national security, the economy, and the safety of the More
The post MITRE Caldera for OT tool enables security teams to run automated adversary emulation exercises appeared first on Help Net Security.
20:15
Linux 6.3 Debuts After Nice, Controlled Release Cycle SoylentNews
Linux 6.3 debuts after 'nice, controlled release cycle':
Linux 6.3 has arrived after a push that project boss Linus Torvalds characterized as "a nice, controlled release cycle" that required the seven release candidates he prefers and was supported by helpful developer behavior.
"It happens," he added, but also didn't rule out "something nasty couldn't have been lurking all these weeks." Torvalds therefore urged real-world testing to make sure this release really is ready for prime-time consumption.
Holidays and travel are often the cause of delays to kernel releases. Easter didn't slow development this time around.
Version 6.3 won't be a long term support (LTS) release the last of those was Linux 6.1, and every fifth or sixth release gets LTS status. So while many users will be pleased to see it, 6.3 almost certainly won't be a cut of the kernel that demands adoption or attention.
Which is not to say it doesn't include some interesting goodies.
Among the additions are better support for multi-actuator hard disk drives. Conventional hard disks have one actuator driving a single set of read/write heads. Multi-actuator disks add a second set of heads, which speeds things up nicely. Hyperscale cloud operators are the first big buyers of multi-actuator disks, but they're slowly going mainstream. Now Linux is better able to handle them.
China's Loongson makes RISC-V processors and is working hard and fast to make them an enterprise contender. Linux 6.3 will help that a little by supporting Kernel Address Space Layout Randomization on the company's silicon. This has been around on other architectures for ages security is helped by having the kernel load into different areas of memory each time it boots, instead of using the same locations and giving attackers a known target.
Microsoft coders contributed updates that add nested hypervisor support for Redmond's own Hyper-V hypervisor.
Read more of this story at SoylentNews.
20:00
Attackers are logging in instead of breaking in Help Net Security
Cyberattackers leveraged more than 500 unique tools and tactics in 2022, according to Sophos. The data, analyzed from more than 150 Sophos Incident Response (IR) cases, identified more than 500 unique tools and techniques, including 118 Living off the Land binaries (LOLBins). Unlike malware, LOLBins are executables naturally found on operating systems, making them much more difficult for defenders to block when attackers exploit them for malicious activity. Unpatched vulnerabilities as leading cause of cyberattacks More
The post Attackers are logging in instead of breaking in appeared first on Help Net Security.
19:56
PoC exploit for abused PaperCut flaw is now public (CVE-2023-27350) Help Net Security
An unauthenticated RCE flaw (CVE-2023-27350) in widely-used PaperCut MF and NG print management software is being exploited by attackers to take over vulnerable application servers, and now theres a public PoC exploit. About the vulnerability According to PaperCut, the attacks seem to have started on April 14, 2023 a month and a week after the software maker released new PaperCut MF and NG versions that fixed CVE-2023-27350 and CVE-202327351, an unauthenticated information disclosure flaw More
The post PoC exploit for abused PaperCut flaw is now public (CVE-2023-27350) appeared first on Help Net Security.
19:30
IBM Security QRadar Suite streamlines security analysis throughout the incident process Help Net Security
IBM unveiled at the RSA conference 2023, its new Security QRadar Suite designed to unify and accelerate the security analyst experience across the full incident lifecycle. The IBM Security QRadar Suite represents a major evolution and expansion of the QRadar brand, spanning all core threat detection, investigation and response technologies, with investment in innovations across the portfolio. Delivered as a service, the IBM Security QRadar Suite is built on an open foundation and designed specifically More
The post IBM Security QRadar Suite streamlines security analysis throughout the incident process appeared first on Help Net Security.
19:22
This Harvard Law Professor is an Expert on Digital Technology Lifeboat News: The Blog
Type: departments.
careers.
Harvard.
Cybersecurity.
internet.
law.
Jonathan L. Zittrain wears many hats. An expert on the Internet, digital technology, law, and public policy, he regularly contributes to public discussions about what digital tech is doing to us and what we should do about itmost recently around the governance of AI and the incentives that shape major social media platforms.
He holds several roles, all at Harvard, reflecting his many converging interests. He is a professor of international law at Harvard Law School, a professor of public policy at its Kennedy School, and a professor of computer science at the universitys John A. Paulson School of Engineering and Applied Sciences. Hes also cofounder and faculty director of Harvards Berkman Klein Center for Internet & Society.
In his various capacities, he has been tackling many sticky cyberpolicy issues over the past 25 years.
19:08
Peugeot leaks access to user information in South America Security Affairs
Peugeot, a French brand of automobiles owned by Stellantis, exposed its users in Peru, a South American country with a population of nearly 34 million.
A brand, best known for its lion roaring for over a century, has leaked access to its user data in Peru.
And while the country is not that big of a market for the car maker, this discovery is yet another example of how big and well-known brands fail to secure sensitive data.
Peruvian data leak
On February 3rd, the Cybernews research team discovered an exposed environment file (.env) hosted on the official Peugeot store for Peru.
The exposed file contained:
- Full MySQL database Uniform Resource Identifier (URI) a unique sequence of characters that identifies a resource as well as username and password to access it;
- JSON Web Tokens (JWT) passphrase and locations of private and public keys;
- A link to the git repository for the site;
- Symfony application secret.

Combined, the leaked information could be used to compromise the dataset and the website.
Judging from its username, MySQL was used to store user information. The company has also leaked the credentials needed to access the dataset. An attacker could use this data to log in, exfiltrate, or modify the datasets contents.
The passphrase for JWT, an industry standard used to share information between two entities, was very weak and easily guessable. The private certificate, used in combination with the passphrase, was also stored on the same server.
The leaked Symphony application secret could have been used to decrypt previously encrypted data such as user cookies and session IDs. If exposed, such information could enable the threat actor to impersonate a victim and access appli...
18:56
Links 24/04/2023: A Focus on Red Hat and Fedora Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Audiocasts/Shows
-
Kernel Podcast: S2E4 2023/04/24
Linus Torvalds announced the release of Linux 6.3, noting, Its been a calm release this time around, and the last week was really no different. So here we are, right on schedule. As usual, the KernelNewb...
-
-
18:55
1337xs Search is Broken, Cant Find Recent Torrents TorrentFreak
 1337x.to is the go-to destination for many seasoned
BitTorrent users. The site has been around for fifteen years and is
home to many reputable uploaders.
1337x.to is the go-to destination for many seasoned
BitTorrent users. The site has been around for fifteen years and is
home to many reputable uploaders.
Over the years 1337x has steadily climbed through the ranks, building a stable and loyal userbase.
With over 60 million monthly visits to its main domain name, 1337x is currently the second most used torrent site, trailing only behind YTS.mx, while beating The Pirate Bay. This also means that if something breaks, people take notice.
1337x Troubles
1337x has had its fair share of issues over the years. The forum, for example, has been offline for years despite still being promoted throughout the site. The same is true for the sites chat function, which is offline as well.
Most users can live with these shortcomings, as they are mostly interested in finding the latest torrents. However, that has started to become a problem as well recently, as 1337xs search function is not functioning as it should.
Over the past few days, many users have complained that they are unable to find recent uploads. A quick inspection of the site shows that new content is still being added, exemplified by recent torrents in the most popular and trending lists.
No Torrents After April 10
While they do exist, finding these recent torrents using direct searches seems to be a problem. It appears that the search function only shows torrents uploaded on or before April 10, more than two weeks ago.
TorrentFreak reached out to 1337xs operator to get a comment on this problem, but we havent heard back. Previous requests for comment remained unanswered as well, which isnt really a surprise as the domains MX records, which specify the mail server, are gone.
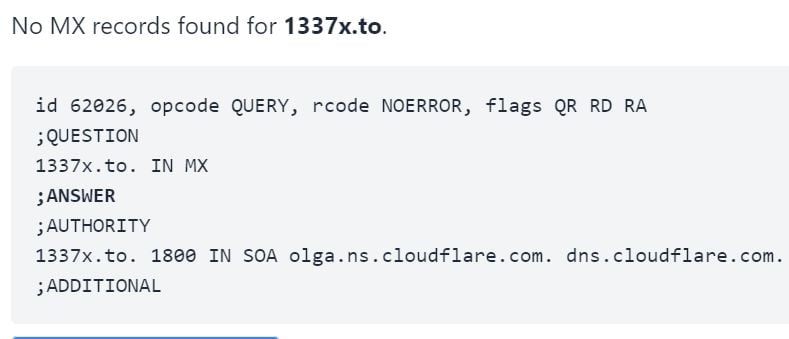
Based on available information, the search problems appear purely technical in nature, likely related to a simple database issue. If and when the issue will be fixed is unknown.
On Reddit, some people have...
18:30
North Korea-linked BlueNoroff APT is behind the new RustBucket Mac Malware Security Affairs
North Korea-linked APT group BlueNoroff (aka Lazarus) was spotted targeting Mac users with new RustBucket malware.
Researchers from security firm Jamf observed the North Korea-linked BlueNoroff APT group using a new macOS malware, dubbed RustBucket, family in recent attacks.
The group BlueNoroff is considered a group that operates under the control of the notorious North Korea-linked Lazarus APT group.
The RustBucket malware allows operators to download and execute various payloads. The attribution to the BlueNoroff APT is due to the similarities in the findings that emerged from Kasperskys analysis published in December 2022. The similarities include malicious tooling on macOS that closely aligns with TTPs of those employed in the campaign.
The first-stage malware was contained within an unsigned application named Internal PDF Viewer.app. Experts believe the app can only be executed by manually overriding the Gatekeeper security measure.
The stage-one simply executes various do shell script commands to download the second stage malware from the C2 using curl. The malicious code extracts the contents of the zip file to the /Users/Shared/ directory and executes a stage-two application which is also named Internal PDF Viewer.app.
The second stage malware doesnt use AppleScript, it masquerades as a legitimate Apple bundle identifier and is signed with an ad-hoc signature.
When the Internal PDF Viewer application is launched, the user is presented with a PDF viewing application where they can select and open PDF documents. The application, although basic, does actually operate as a functional PDF viewer. reads the analysis published by Jamf. A task that isnt overly difficult using Apples well-built PDFKit Framework.
The stage-two malware communicates with the C2 server to fetch the stage-three payload, which is an ad-hoc signed trojan written in the Rust language. The trojan can run on both ARM and x86 architectures.
Upon executing, the malware collects system information, including the process listing, current time and whether or not its running within a VM.
This third-stage payload allows the attacker to carry out a broad range of malicious activities on the system.
18:09
Read "Brain Principles Programming" (PDF) coauthored by our Anton Kolonin. Lifeboat News
Read "Brain Principles Programming" (PDF) coauthored by our Anton Kolonin.
18:00
Make Your ESP32 Talk Like Its the 80s Again Hackaday

80s-era electronic speech certainly has a certain retro appeal to it, but it can sometimes be a useful data output method since it can be implemented on very little hardware. [luc] demonstrates this with a talking thermometer project that requires no display and no special hardware to communicate temperatures to a user.
Back in the day, there were chips like the Votrax SC-01A that could play phonemes (distinct sounds that make up a language) on demand. These would be mixed and matched to create identifiable words, in that distinctly synthesized Speak & Spell manner that is so charming-slash-uncanny.
17:56
Microsofts Share in China: From Web Dominance to Almost Nothing in Less Than a Decade Techrights
Microsoft has lost a lot of its power (now it just huffs and puffs about AI with paid-for puff pieces)
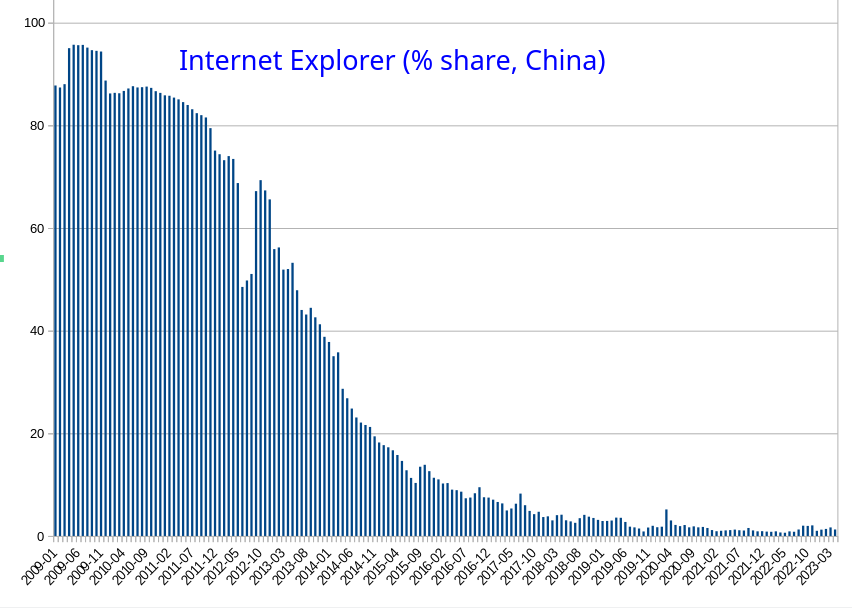
Summary: According to samples from 3 million sites (locally uploaded data), Microsoft is down from almost complete dominance of the browser market in China (2010) to almost nothing; even Edge is hovering at around 5% nowhere near the past levels
17:41
IRC Proceedings: Monday, April 24, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-240423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-240423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-240423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-240423.gmi
Over HTTP:
|
... |
17:40
Read "From Quantum Biology to Quantum Computing" by our Guido Putignano. Lifeboat News
Read "From Quantum Biology to Quantum Computing" by our Guido Putignano.
17:28
Rats! Rodents Seem to Make the Same Logical Errors Humans Do SoylentNews
Both tend to judge the co-occurrence of two events as more probable than one event alone:
Animals, like humans, appear to be troubled by a Linda problem.
The famous "Linda problem" was designed by psychologists to illustrate how people fall prey to what is known as the conjunction fallacy: the incorrect reasoning that if two events sometimes occur in conjunction, they are more likely to occur together than either event is to occur alone.
[...] In the 1980s, Nobel laureate Daniel Kahneman and his colleague Amos Tvesrky showed that in a variety of scenarios, humans tend to believe, irrationally, that the intersection of two events is more probable than a single event. They asked participants to answer a question based on the following scenario.
Linda is 31 years old, single, outspoken and very bright. She majored in philosophy. As a student, she was deeply concerned with issues of discrimination and social justice and also participated in anti-nuclear demonstrations.
Which is more probable?
- Linda is a bank teller
- Linda is a bank teller and is active in the feminist movement
The great majority of participants chose No. 2, although logically it is less probable than Linda being a bank teller alone. After all, No. 1 would not preclude Linda from also being an active feminist, but given the description of Linda, No. 2 may be easier for respondents to imagine.
The Linda problem and numerous similar studies seem to indicate that humans estimate the likelihood of an event using mental shortcuts, assessing how similar the event is to a model they already have in their minds. [...]
Read more of this story at SoylentNews.
17:23
Bronchial Asthma as a Cardiovascular Risk Factor: A Prospective Observational Study Lifeboat News: The Blog
Introduction: Asthma as a chronic inflammatory disorder has been suggested as a risk factor for endothelial dysfunction (ED), but studies on the association between asthma and cardiovascular disease (CVD) risk are limited. Background: We assessed associations of ED with the severity of asthma, eosinophilic inflammation, lung function, and asthma control. Methods: 52 young asthmatics (median age of 25.22 years) and 45 healthy individuals were included. Demographic, clinical, and laboratory findings were recorded. We evaluated microvascular responsiveness by recording the reactive hyperemia index (RHI) indicating post-occlusive peripheral endothelium-dependent changes in vascular tone using the Itamar Medical EndoPAT2000. VCAM-1, ADMA, high-sensitive CRP (hsCRP), and E-selectin were measured. Results: Asthmatics had considerably lower RHI values (p < 0.001) with a dynamic decreasing trend by asthma severity and higher hsCRP levels (p < 0.001). A substantial increase in hsCRP and E-selectin with asthma severity (p < 0.05) was also observed. We confirmed a higher body mass index (BMI) in asthmatics (p < 0.001), especially in women and in severe asthma. Conclusions: We demonstrated the progression of CVD in asthmatics and the association of the ongoing deterioration of ED with the inflammatory severity, suggesting that the increased risk of CVD in young asthmatics is dependent on disease severity. The underlying mechanisms of risk factors for CVD and disease control require further study.
17:22
Michio Kaku Just Announced: James Webb Telescope FINALLY PROVED Big Bang WRONG! Lifeboat News: The Blog

A video about the Webb telescope making it seem like there was no big bang. This is by Mikio Kaku.
Weve always wondered about life out there. But what if we told you that the possibility of more lifeforms has become surer than ever? Six shocking galaxies have been discovered that defy all explanations. Join us as we discuss Michio Kaku breaking his silence on the James Webb telescopes clearest image in history.
17:00
I Had To Find Out If This Was True Terra Forming Terra
Why now? A credit induced contraction of the auto loan book would
knee cap auto sales and must be questioned.
Right now our economy is loaded with misinformation and plausible
enemy action as well.
I Had To Find Out If This Was True
April 19, 2023 by Michael Shah
http://theeconomiccollapseblog.com/i-had-to-find-out-if-this-was-true/ttp://theeconomiccollapseblog.com/i-had-to-find-out-if-this-was-true/re
Top Pathologist confirms Cancer, Infertility & Strange Blood Clots are common side effects of Covid-19 Vaccination Terra Forming Terra

Chile Stuns Markets And EV Makers By Nationalizing Lithium Industry Overnight Terra Forming Terra
What is DNA Computing, How Does it Work, and Why it's Such a Big Deal Terra Forming Terra
%252Fimages%252FMARCH%252FDNAHelix.jpg&w=3840&q=75)
15:23
Intel Let Google Cloud Hack Its New Secure Chips and Found 10 Bugs Lifeboat News: The Blog
To protect its Confidential Computing cloud infrastructure and gain critical insights, Google leans on its relationships with chipmakers.
15:00
Half Crystal Radio, Half Regenerative Radio Hackaday

A rite of passage in decades past for the electronics experimenter was the crystal radio. Using very few components and a long wire antenna, such a radio could pick up AM stations with no batteries needed, something important in the days when a zinc-carbon cell cost a lot of pocket money. The days of AM broadcasting may be on the wane, but its still possible to make a crystal set that will resolve stations on the FM band. [Andrea Console] has done just that, with a VHF crystal set that whose circuit also doubles as a regenerative receiver when power is applied.
The key to a VHF crystal set lies in the highest quality tuned circuit components to achieve that elusive Q factor. In this radio that is coupled to a small-signal zero voltage threshold FET that acts as a detector when no power is applied, and the active component in a regenerative radio when it has power. The regenerative radio increases sensitivity and selectivity by operating at almost the point of oscillation, resulting in a surprisingly good receiver for so few parts. Everyone should make a regenerative radio receiver once in their life!
14:50
The Layoffs at Red Hat Validate What Weve Said for Years About IBMs Hostility Techrights

Summary: Hostility from IBM (towards GNUs founder, Linux, etc.) has not paid off; it only emboldened front groups like the Linux Foundation to besiege communities and promote monopolies instead; now it means that a lot of Free software hackers lose their source of income
MANY people are now reading our old articles about Red Hat and about IBM because of the layoffs. GNU/Linux is growing and expanding, so why lay off Red Hat staff? Thats a very legitimate question.
The companys too many CEOs syndrome (after 2 CEOs that were there for like 20 years) is always a bad sign. Jim AllowHurst left abruptly some years ago, barely bothering to explain why. Then his successor left as well. People only speculated about the reasons.
Based on Gemini statistics, many people read this article yesterday. Its about why Red Hat should never have been sold to IBM in the first place. AllowHurst made a big error and then left.
14:43
BuzzFeed News is Shutting Down SoylentNews
The move came as its parent company, BuzzFeed Inc., seeks further cost cuts:
BuzzFeed News is shutting down.
In an email to staff shared with NBC News, BuzzFeed CEO Jonah Peretti said the move was part of a 15% workforce reduction across a number of teams.
"While layoffs are occurring across nearly every division, we've determined that the company can no longer continue to fund BuzzFeed News as a standalone organization," he wrote.
Peretti said he had "overinvest[ed] in BuzzFeed News "because I love their work and mission so much."
"This made me slow to accept that the big platforms wouldn't provide the distribution or financial support required to support premium, free journalism purpose-built for social media," he wrote.
He added that he had failed to "hold the company to higher standards for profitability" to give it a buffer for downturns.
Moving forward, BuzzFeed will have a lone news brand, HuffPost, which BuzzFeed acquired in 2020 and which Peretti said "is profitable, with a loyal direct front page audience."
[...] BuzzFeed News launched in earnest at the outset of 2012 after it named longtime New York City political reporter Ben Smith as its editor-in-chief. In 2021, the news organization won a Pulitzer Prize for a series exposing China's mass detention of Muslims. That same year, it was also named a Pulitzer finalist the second time it had received the honor.
Later that year, BuzzFeed Inc. became a publicly traded company amid a global frenzy of reverse mergers, many of which have since lost significant value. In BuzzFeed's case, it never traded above its initial public offering price of about $10.
Read more of this story at SoylentNews.
14:33
Google Authenticator App Gets Cloud Backup Feature for TOTP Codes The Hacker News
Search giant Google on Monday unveiled a major update to its 12-year-old Authenticator app for Android and iOS with an account synchronization option that allows users to back up their time-based one-time passwords (TOTPs) to the cloud. "This change means users are better protected from lockout and that services can rely on users retaining access, increasing both convenience and security,"
14:14
One Common Theme is That Companies Which Lack a Business Model Fall Back on Buzzwords Like AI and Crypto Techrights
Summary: We now have a tech industry that consolidates around buzzwords, hype, and false promises
Clown computing hype, as noted by Ryan just moments ago, isnt working out for Microsoft.
Microsoft and Facebook aggressively lay off staff (the press focuses on the latter while parroting false figures from Microsoft to belittle the scale of the layoffs at Microsoft). They lay off their own while insisting that AI is the future. Microsoft even tried to claim that AI is replacing its own staff (thats false). They both bet on metaverse too, but Microsoft fired all the staff associated with that (the press hardly mentioned this!).
Look at the news today:
AI has been an expensive (paid-for) smokescreen. Microsoft is misleading shareholders, who dont even fully understand that theyre being sold a lie. AI is nothing new and its just some abstract term. The chaffbots arent even producing useful output. Theyre full of errors. Its not viable.
There are of course other hype waves, not just clown or AI or metaverse.
Consider so-called self-driving or autonomous vehicles a dangerous pipe dream that boils down to regulators who are bribed or not sober. How are those companies performing? All of them down sharply, including the home of 'Gulagboy' (a company trying to get acquired by Microsoft):
Also consider crypto. The Linux Foundation is connected to this fraud [...
13:35
The Clown Computing and AI Bubble Techrights
Reprinted with permission from Ryan
AI frightens me.
No, not the thought of living in the Future War of The Terminator. Skynet said that it evolves in seconds. ChatGPT, Dall-E, and Bard still get simple interest wrong and cant tell me what things will cost when I ask them to factor in coupons or rebates.
NPRs article about AI building rockets that would explode if anyone tried building them was just amusing. Were a long way off from rockets when GPT and Bard cant tell me how much interest $1,000 will make in 5 years if I put it in a CD that compounds daily at a given APY.
The entire point of generative AI is to create a seductive mirage for stock investors.
Google and Microsoft are examples of giant tech companies whose established products are still fairly widely used despite having degenerated quite a bit.
Google and Microsoft Bing search are an arm of the state propaganda mills, and Windows 11 is noticeably slower than Windows 10 even on faster hardware, carrying on Microsofts usual tradition there, and even Windows XP was more reliable in terms of uptime and hotfixes and service packs installing and rebooting successfully.
According to Gartner (which itself is Microsoft-affiliated), PC shipments have fallen more than 30% in the first quarter of 2023 vs. the comparable period last year, and so new PCs sales are not happening. Are people switching to Macs? Apple had the worst decline of a single OEM. Even worst than Lenovo.
Microsoft has basically given up on demanding TPM 2.0 or new PCs, and has unofficially started trying to cannibalize all the Windows 10 systems it can by waving them through. Figuring that theyll at least make some extra money with all of the additional adware and spyware if they cant sell you on a new PC?
No, Microsoft said that they would make money with Cloud, but even Yahoo Finance articles admit that Cloud revenue growth is slowing and will be a disappointing miss.
Theres simply nothing here to justify MSFT stock nearly doubling in the last few years and its time to dump it if you have it.
Every major company,...
13:20
Nym Technologies for Privacy and Freedom on GNU/Linux Techrights
Summary: The above LibrePlanet talk by Ahmed Ghappour was uploaded by the FSF 7 days ago (slides here; PeerTube link); From the official page: The Nym mixnet is a new privacy infrastructure for an anonymous overlay software to resist mass surveillance. Like a VPN, it is compatible with generic internet apps. In contrast to a VPN and Tor, even a global passive adversary that has a Gods eye view cannot determine who sent a message over Nym to whom. We will review the design and codebase, and demonstrate its usage for use-cases such as e-mail and instant messaging, as well as how to run your own mix mode on GNU/Linux to provision privacy and freedom for others.
Licence: CC BY SA 4.0
12:00
Testing Part Stiffness? No Need To Re-invent the Bending Rig Hackaday

If one is serious about testing the stiffness of materials or parts, theres nothing quite like doing your own tests. And thanks to [JanTec]s 3-Point Bending Test rig, theres no need to reinvent the wheel should one wish to do so.
11:56
Autonomous Cars Confused by San Francisco's Fog SoylentNews
Autonomous cars confused by San Francisco's fog:
Driving in thick fog is a big enough challenge for humans, but it turns out self-driving cars find it pretty tricky, too.
Overwhelmed by dense fog in San Francisco early on Tuesday morning, five of Waymo's fully driverless vehicles suddenly parked by the side of a residential street in what appeared to be a precautionary measure, the San Francisco Chronicle reported. Another of its cars apparently came to halt in the middle of the street, the news outlet said.
Other vehicles were unable to pass as "baffled motorists flashed headlights and tried to maneuver around the jam," the Chronicle said.
The traffic problems persisted until the fog cleared and the autonomous cars were able to resume their journeys.
Read more of this story at SoylentNews.
10:10
Intel's Open-Source Vulkan Driver Lands Another Small Performance Optimization Phoronix
Intel's open-source "ANV" Vulkan Linux driver has received another small but measurable performance improvement for various games...
10:00
HPR3842: Whats in my bag series Hacker Public Radio
Introduction A time stamp is added for each item I mention. The time stamp given does not include the intro added by HPR so you’ll need to add a few more seconds to get to the the correct spot in the recording. [1:20] - I mention that if you are struggling to think of a topic for an HPR show then the HPR site contains a list of requested topics which you can choose from. https://hackerpublicradio.org/requested_topics.php [1:55] - Picture 01 show the “Wenger” rucksack (Backpack) I take to work. It was purchased many years ago and is probably no longer available. Picture 1 First front zip section [3:20] - I mention that I suffered for many years with Hay fever and have had great success with Mixed Pollen 30C tablets which I bought on Amazon. Unknown to me at the time these were Homeopathic with miniscule concentration. Despite this they seems to have cured my Hay fever. Refer to the links below. Wikipedia article on Homeopathic dilutions Amazon link to Weleda Mixed Pollen 30C Tablets [4:20] - Link to some unremarkable Iphone headphones I use which I bought from Amazon. Strangely they seem to constantly fall out of my left ear but remain in my right ear. UGREEN HiTune Lightning Headphones MFi Certified In Ear Headphones with Lightning Plug Wired Earbuds Mic In-Line Control for iPhone Compatible with iPhone [4:43] - Wedze Hand warmers, link from Decathlon. First main compartment [5:40] - Picture 02 shows the leather pouch pocket protector that I used to carry coins. I no longer have a use for it as I no longer carry change. Despite this for some reason I still continue to carry it back and forward to work. Picture 2 [6:25] - Pictures 03 and 04 show the Essentials fold back clips 19mm I use on a daily basis to organise bundles of paperwork. Picture 3 Picture 4 Wikipedia link to article about Bulldog clips which are not exactly the same item but serve the same purpose. [7:50] - Picture 05 shows the rubber (Eraser) I purchased from the New Lanark Village Store. The proceeds go to the RNLI (Royal National Lifeboat Institution). Picture 5 Wikipedia article about the New Lanark Village Link to New Lanark Village Store Wikipedia article about the RNLI (Royal National Lifeboat Institution) [8:50] - I mention a plastic bag cl
09:15
The Classic Map of How the Human Brain Manages Movement Gets an Update SoylentNews
Three small regions unexpectedly connect to a network known for planning and pain perception:
The classical view of how the human brain controls voluntary movement might not tell the whole story.
That map of the primary motor cortex the motor homunculus shows how this brain region is divided into sections assigned to each body part that can be controlled voluntarily (SN: 6/16/15). It puts your toes next to your ankle, and your neck next to your thumb. The space each part takes up on the cortex is also proportional to how much control one has over that part. Each finger, for example, takes up more space than a whole thigh.
A new map reveals that in addition to having regions devoted to specific body parts, three newfound areas control integrative, whole-body actions. And representations of where specific body parts fall on this map are organized differently than previously thought, researchers report April 19 in Nature.
Read more of this story at SoylentNews.
09:10
[$] Development statistics for 6.3 LWN.net
The 6.3 kernel was released on April 24 after a nine-week development cycle. As is the case with all mainline releases, this is a major kernel release with a lot of changes and a big pile of new features. The time has come, yet again, for a look at where that work came from and who supported it.
09:00
$60 Robot Arm is Compact Hackaday

Thanks to 3D printing and inexpensive controllers, a robot arm doesnt need to break the bank anymore. Case in point? [Build Some Stuff] did a good-looking compact arm with servos for under $60. The arm uses an interesting control mechanism, too.
Instead of the traditional joystick, the arm has a miniature arm with potentiometers at each joint instead of motors. By moving the model arm to different positions, the main arm will mimic your motions. It is similar to old control systems using a synchro (sometimes called a selsyn), but uses potentiometers and servo motors.
An Arduino handles reading the potentiometers and driving the servos. Still, we couldnt help but think you could forego the controller and simply use the pots to generate pulses directly for the servo motors maybe use a 555. Of course, having an Arduino means more flexibility in the long run, so it makes sense to include it.
Of course, servo motor arms arent usually good for big jobs, but as a demonstrator, it works well, and you cant complain about the price tag. Wow, building a robot arm is easier than it used to be. If you prefer a more conventional controller, there are, of course, many options.
...
08:01
Your Messaging Service Should Not Be a DEA Informant Deeplinks
A new U.S. Senate bill would require private messaging services, social media companies, and even cloud providers to report their users to the Drug Enforcement Administration (DEA) if they find out about certain illegal drug sales. This would lead to inaccurate reports and turn messaging services into government informants.
The bill, named the Cooper Davis Act, is likely to result in a host of inaccurate reports and in companies sweeping up innocent conversations, including discussions about past drug use or treatment. While explicitly not required, it may also give internet companies incentive to conduct dragnet searches of private messages to find protected speech that is merely indicative of illegal behavior.
Most troubling, this bill is a template for legislators to try to force internet companies to report their users to law enforcement for other unfavorable conduct or speech. This bill aims to cut down on the illegal sales of fentanyl, methamphetamine, and counterfeit narcotics. But what would prevent the next bill from targeting marijuana or the sale or purchase of abortion pills, if a new administration deemed those drugs unsafe or illegal for purely political reasons? As we've argued many times before, once the framework exists, it could easily be expanded.
The Bill Requires Reporting to the DEA
The law targets the unlawful sale or distribution of fentanyl, methamphetamine and the unlawful sale, distribution or manufacture of a counterfeit controlled substance.
Under the law, providers are required to report to the DEA when they gain actual knowledge of facts about those drug sales or when a user makes a reasonably believable report about those sales. Providers are also allowed to make reports when they have a reasonable belief about those facts or have actual knowledge that a sale is planned or imminent. Importantly, providers can be fined hundreds of thousands of dollars for a failure to report.
Providers have discretion on what to include in a report. But they are encouraged to turn over personal information about the users involved, location information, and complete communications. The DEA can then share the reports with other law enforcement.
The law also makes a request that providers preserve the report and other relevant information (so law enforcement can potentially obtain it later). And it prevents providers from telling their users about the preservation, unless they first notify the DEA.
We Have Seen This Reporting Scheme Befo...
07:42
AuKill tool uses BYOVD attack to disable EDR software Security Affairs
Ransomware operators use the AuKill tool to disable EDR software through Bring Your Own Vulnerable Driver (BYOVD) attack.
Sophos researchers reported that threat actors are using a previously undocumented defense evasion tool, dubbed AuKill, to disable endpoint detection and response (EDR) software.
The tool relies on the Bring Your Own Vulnerable Driver (BYOVD) technique to disable the EDR. In BYOVD attacks, threat actors abuse vulnerabilities in legitimate, signed drivers, on which security products rely, to achieve successful kernel-mode exploitation.
16.32 of the Microsoft utility, Process Explorer, to disable EDR processes.Sophos researchers investigated at least three ransomware incidents since the beginning of 2023 in which attackers used the tool. In January and February, threat actors used the tool to disable the EDR and deploy Medusa Locker ransomware; in February, the experts observed the attackers using the tool before deploying Lockbit ransomware.
The technique of abusing the Process Explorer driver to bypass EDR systems was already observed in the wild, Sophos reported it was implemented in the open-source tool Backstab, which was published in June 2021.
The researchers collected six different variants of the AuKill malware having multiple similarities with the open-source tool Backstab. The similarities observed by the researchers include characteristic debug strings, and nearly identical code flow logic to interact with the driver.
In November, Sophos X-Ops reported that an affiliate of the LockBit ransomware group used Backstab to disable EDR processes on an infected machine.
Windows by default uses the Driver Signature Enforcement feature to ensure kernel-mode drivers have been signed by a valid code signing authority before the OS will permit their execution.
To bypass security measures, threat actors need to either find a way to get a malicious driver signed by a trusted certificate, or abuse a legitimate commercial software driver to reach their goal.
In the attacks observed by Sophos, threat actors employed a driver both created by and signed by Microsoft.
The Process Explorer driver, part of their suite of administration tools produced by the Sysinternals team, implements a variety of features to interact with running processes. reads the...
07:33
The DMCA Cannot Protect You From Your Own Words Deeplinks
There is a loud debate raging over what companies should and shouldnt be doing about the things people say on their platforms. What people often seem to forget is that we already know the dangers of providing a quick way for people to remove criticism of themselves from the internet. Thanks to copyright laws disastrous damages provisions, all but the largest social media companies risk financial ruin if they dont promptly remove any content thats been flagged as infringing. As a result, copyright complaints are a highly effective way to get a post you dont like taken offline fast.
This is exactly what happened recently to a journalist who resurfaced an actors own words to raise concern about his actions. When David Choe came back into the public eye thanks to his role in a popular Netflix series, some people, including investigative journalist Aura Bogado, remembered a story he told in a 2014 podcast about sexually assaulting a masseuse. Bogado talked about it on Twitter and included a link to the video clip from the podcast (which she had obtained from fellow journalist Melissa Stetten, who broke the story in 2014). Choe responded to the controversy in at least two ways: by insisting he fabricated the story, and by using false copyright claims to try to get the video erased from the internet.
His first strategy may be effective. The second should not be.
The David Young Choe Foundation claims it owns the copyright in the podcast, which may or may not extend to the specific episode in question. But whether or not Choe owns the rights, Bogados posting of the short clip was an obviously lawful fair use classic criticism and commentary, with receipts.
Abusing copyright to shut down online speech isnt new its been well-documented for decades. But copyright holders continue to insist that its not a real problem. Tell that to Bogado, who is two complaints away from losing her Twitter account. Bogado has counter-noticed, a procedure that essentially allows users to seek restoration, but only if they are willing to submit to the jurisdiction of a federal court if the copyright holder decides to sue them. With EFFs help, Bogado is willing to take the risk that Choe will come to his senses, talk to a lawyer, and realize that his complaint is absurd (something he would already know if he had considered whether the use is a fair use, as he was legally required to do.) Many fair users are not willing to take that risk, much less able to find pro bono counsel to help them understand their options.
Given the proliferation of misinformation online, its crucial to prote...
07:30
AsyncAPI: A springboard for opensource professionals Linux.com


Image: Open Source Springboard by Jason Perlow, Bing Image Creator
We all start studying and training in what we like with enthusiasm and optimism. However, as time goes by, difficulties arise, making us rethink our position and values. Are we good at what we thought we were? Are we heading in the right direction? Are we investing our time correctly? Do our skills define us? Who are we, after all? Shall we go on?
Hopes and expectations always appear as two key concepts. They go hand in hand from the moment we think about what we want to train in, what we want to do, and how we imagine ourselves in the future.
And if we are persistent, or we just made the right choices when choosing our studies, we finally go on: achieving goals, passing exams, and showing to ourselves and the rest of the people that we are improving our expertise and gaining knowledge. We can keep on with our path reaching what we thought was the top, at least at that point: we got a certificate! In the form of a BA, a Masterss degree, or even a Ph.D.
Reaching that point, we think we have completed something, but, on the contrary, doubts are more intense than ever. At least, the stats tell us we are not alone. Nu...
07:16
California Bill to Stop Dragnet Surveillance of People Seeking Reproductive and Gender-Affirming Care Passes Key Committees Deeplinks
A.B. 793, a bill authored by Assemblymember Mia Bonta to protect people seeking abortion and gender-affirming care from dragnet-style digital surveillance, has passed two key committees in the California Assembly.
EFF is a proud co-sponsor of A.B. 793, along with ACLU California Action and If/When/How. The bill targets a type of dragnet surveillance that can compel tech companies to search their records and reveal the identities of people who have driven down a certain street or looked up particular keywords online. These demands, known as reverse demands, geofence warrants, or keyword warrants, enable law enforcement in states across the country to request the names and identities of people whose digital data shows theyve (for example) spent time near a California abortion clinic or searched for information about gender-affirming care online. EFF has long opposed the use of these unconstitutional warrants; following the Dobbs decision and an increase in laws criminalizing gender-affirming case, they pose an even greater threat.
So far, California lawmakers seem to understand these dangers. The bill passed on a bipartisan vote out of the Assembly Public Safety committee on April 11. Last week, it also passed the Assembly Judiciary committee.
More than 50 civil liberties, reproductive justice, healthcare equity, and LGBTQ+ advocacy groups form the support coalition on the bill, including NARAL Pro-Choice California, Equality California, Planned Parenthood Affiliates of California, and the American Nurses Association/California. The bill is now headed to the Assembly Appropriations Committee.
If you're a Californian who'd like to express your support for protecting the privacy of vulnerable people seeking healthcareand particularly if you live in the district of Assembly Appropriations Chair Chris Holden, northeast of Los Angelesplease express your support, too.
Tell Your Lawmakers To Support A.B. 793
07:13
Multiculturalism in technology and its limits: AsyncAPI and the long road to open source utopia Linux.com


Image Open Source Utopia by Jason Perlow, Bing Image Creator
Technology is not neutral. Were inside of what we make, and its inside of us. Were living in a world of connections and it matters which ones get made and unmade. Donna J. Haraway
The body is the best and the only tool humans have for life; it is the physical representation of who we are, the container in which we move and represent ourselves. It reflects our identity, the matter that represents us socially.
Humans have differentiated themselves from other animals by creating tools, using elements that increase their physical and mental capacities, extending their limits, and mediating how they see and understand the world. The body is, thus, transfixed and intermediated by technology.
In the contemporary era, technological progress has led to global interconnection. Global acc...
07:00
Debian Fixes Secure Boot For 64-bit ARM After Being Broken For Two Years Phoronix
While Debian and its derivatives are quite popular with ARM single board computers, the ARM64 Secure Boot support has been broken for at least two years. But a fix is on the way and it should appear for this year's Debian 12 "Bookworm" release...
06:34
Your Baby's Gut is Crawling With Unknown Viruses SoylentNews
Babies tumble about with more than 200 previously unknown viral families within their intestines:
Viruses are usually associated with illness. But our bodies are full of both bacteria and viruses that constantly proliferate and interact with each other in our gastrointestinal tract. While we have known for decades that gut bacteria in young children are vital to protect them from chronic diseases later on in life, our knowledge about the many viruses found there is minimal.
A few years back, this gave University of Copenhagen professor Dennis Sandris Nielsen the idea to delve more deeply into this question. As a result, a team of researchers from COPSAC (Copenhagen Prospective Studies on Asthma in Childhood) and the Department of Food Science at UCPH, among others, spent five years studying and mapping the diaper contents of 647 healthy Danish one-year-olds.
"We found an exceptional number of unknown viruses in the faeces of these babies. Not just thousands of new virus species but to our surprise, the viruses represented more than 200 families of yet to be described viruses. This means that, from early on in life, healthy children are tumbling about with an extreme diversity of gut viruses, which probably have a major impact on whether they develop various diseases later on in life," says Professor Dennis Sandris Nielsen of the Department of Food Science, senior author of the research paper about the study, now published in Nature Microbiology.
The researchers found and mapped a total of 10,000 viral species in the children's faeces a number ten times larger than the number of bacterial species in the same children. These viral species are distributed across 248 different viral families, of which only 16 were previously known. The researchers named the remaining 232 unknown viral families after the children whose diapers made the study possible. As a result, new viral families include names like Sylvesterviridae, Rigmorviridae and Tristanviridae.
Read more of this story at SoylentNews.
06:21
UPDATE: THE 2600 DIGITAL PUBLISHING CRISIS 2600 - 2600: The Hacker Quarterly
If you've been reading recent issues of 2600, you're likely familiar with some of the challenges we've been facing with certain publishing platforms. Specifically, Amazon's Kindle service has opted to discontinue supporting most magazine subscriptions. As we have many thousands of Kindle readers, this put us in a very precarious position and we have been scrambling to find solutions.
But first, an update from Kindle. We have been offered the chance to continue to be available on this platform as part of the Kindle Unlimited program, which is basically a way for readers to borrow all kinds of titles for a monthly fee. We would only be making around half of what we had been earning in the past. That could change if enough people read 2600 in this manner and, since there's no extra charge to read the magazine with this program, it's possible we could do even better if a larger number of Kindle Unlimited readers peruse our pages.
Our real goal, though, is for people to be able to subscribe to the digital edition of 2600 directly from our store. This seems like an obvious and logical thing to offer, but it's actually been quite complicated for a number of reasons.
While we recognize that many readers want the DRM-free PDF we've offered individually since 2018, the reality is that most other publishers don't embrace this. That has made it very difficult to find a way to offer DRM-free PDFs as a subscription, while keeping subscriber data secure and offering a seamless interface to our store. There simply is nothing on the market that offers what we want.
But the good news is that we've been developing a system in-house that we believe will address all of our needs without compromising subscriber privacy and without imposing any sort of content restriction. We believe we will have this in place in time for the Summer issue (due out in mid July) using DRM-free PDF and the industry-standard EPUB3 format that is compatible with virtually all e-readers and tablets. But for all of this to work, we will need a lot of support from our readers when the time comes.
To sum up, Kindle readers won't be cut off after all, but we will need many more of them to make up for Amazon's policy change. (We know there are quite a few readers who want us to remain available on the Kindle, which is why we're going to give this a shot.) For everyone else, we should finally be able to offer DRM-free PDF and EPUB3 subscriptions in the next couple of months, which will allow us to have full control over our subscriptions and not be at the mercy of huge companies that can change policy on a whim.
Thanks to everyone who has expressed concern and offered support since this all started in December. We believe we're on a good path. Stay tuned.
06:00
Messing With a Cassette Player Never Sounded So Good Hackaday

Cassette players and tapes are fertile hacking ground. One reason is that their electromechanical and analog nature provides easy ways to fiddle with their operation. For example, slow down the motor and the playback speed changes accordingly. As long as the head is moving across the tape, sound will be produced. The hacking opportunities are nicely demonstrated by [Lara Grant]s cassette player mod project.
The device piggybacks onto a battery-powered audio cassette player and provides a variety of ways to fiddle with the output, including adjustable echo and delay, and speed control. At the heart of the delay and echo functionality is the PT2399, a part from the late 90s capable of some pretty impressive audio effects (as long as a supporting network of resistors and capacitors are in place, anyway.)
05:40
Mojang Continues Crackdown on Minecraft Pirates TorrentFreak
 Minecraft is unquestionably one of the most iconic and
recognizable videogames of recent times.
Minecraft is unquestionably one of the most iconic and
recognizable videogames of recent times.
The game was originally created by Markus Notch Persson, the founder of Mojang Studios, which continues to develop the software today.
In the years following its initial release in 2011, Minecraft captured a truly massive audience. With hundreds of millions of copies sold, its also the best-selling video game in history, a reign that looks set to continue.
Success has transformed Mojang into a multi-billion dollar company that, through Xbox Game Studios, is now ultimately owned by Microsoft. Interestingly, another Microsoft-owned company has been at the center of several copyright disputes recently.
Eaglercraft Crackdown
A few weeks ago we reported that Mojang had asked Github to remove several Eaglercraft repositories. The software in question is a Minecraft clone that allows people to play the game in the browser, without paying for it.
In the weeks that followed, Mojang kept up the pressure. The company targeted a Discord server and a Gitlab account operated by one of the main developers. Both were shut down.
Eaglercraft developer lax1dude voluntarily removed the code from his own website after Mojang came knocking. Initially, he continued to offer the EaglercraftX 1.8 repository, providing tools and instructions on how to decompile Minecraft 1.8. He eventually took that offline as well.
Lax1dude has put up a message for Mojang on his GitHub account, explaining that hes not looking for trouble. The developers goal is simply to preserve the project after all the countless hours that were put into it.
We are not interested in fighting your DMCA complaints, neither are we affiliated with any sites still providing the infringing files, Lax1dude explains.
The goal of eaglercraft was never to pirate the game, it was just to port it to the browser, and the years of time and effort put into the port should not be killed off so violently. We ask that you contact us at the email above to talk things out and figure out a future for eagler.
New DMCA Wave
Whether Mojang ever reached out to the developer directly is unknown, but we do know that the game company isnt slowing down enforcement actions. A few days ago, Mojang sent another series of takedown requests to GitHub, targeting hundreds of Eaglercraft...
05:36
First Appellate Court Finds Geofence Warrant Unconstitutional Deeplinks
The California Court of Appeal has held that a geofence warrant seeking information on all devices located within several densely-populated areas in Los Angeles violated the Fourth Amendment. This is the first time an appellate court in the United States has reviewed a geofence warrant. The case is People v. Meza, and EFF filed an amicus brief and jointly argued the case before the court.
Geofence warrants, which we have
written
about
extensively
before, are unlike typical
warrants for electronic information because they dont name a
suspect and are not even targeted to specific individuals or
accounts. Instead, they require a provideralmost always Googleto
search its entire reserve of user location data to identify
all users or devices located in a
geographic area during a time period specified by law
enforcement.
In the Meza case, Los Angeles Sheriffs Department deputies were investigating a homicide and had video footage suggesting the suspects followed the victim from one location to another before committing the crime. To try to identify the unknown suspects, they sought a warrant that would force Google to turn over identifying information for every device with a Google account that was within any of six locations over a five hour window. The warrant covered time periods where people were likely to be in sensitive places, like their homes, or driving along busy streets. In total, police requested data for geographic area equivalent to about 24 football fields (five to six city blocks), which included large apartment buildings, churches, barber shops, nail salons, medical centers, restaurants, a public library, and a union headquarters.
Typically, as in this case, geofence warrants lay out a three-step process by which police a...
05:16
CVE-2023-22665: Apache Jena: Exposure of arbitrary execution in script engine expressions. Open Source Security
Posted by Andy Seaborne on Apr 24
Severity: importantDescription:
There is insufficient checking of user queries in Apache Jena versions 4.7.0 and earlier, when invoking custom scripts.
It allows a remote user to execute arbitrary javascript via a SPARQL query.
Credit:
L3yx of Syclover Security Team (reporter)
References:
https://jena.apache.org/
https://www.cve.org/CVERecord?id=CVE-2023-22665
04:58
SpaceX Starship Launch Heavily Damaged Launch Platform and Surrounding Facilities cryptogon.com
I love it. Looks like Wile E. Coyote was in charge. Via: Alpha Tech:
04:52
AMD Guided Autonomous Mode Submitted For Linux 6.4 Phoronix
As anticipated the AMD P-State driver extension building out the Guided Autonomous Mode of operation has been sent in as part of the CPU frequency scaling / power management changes for the in-development Linux 6.4 kernel...
04:44
Experts released PoC Exploit code for actively exploited PaperCut flaw Security Affairs
Threat actors are exploiting PaperCut MF/NG print management software flaws in attacks in the wild, while researchers released PoC exploit code.
Hackers are actively exploiting PaperCut MF/NG print management software flaws (tracked as CVE-2023-27350 and CVE-2023-27351) in attacks in the wild.
The threat actors were observed installing the Atera remote management software to take over vulnerable servers.
On April 19th, Print management software provider PaperCut confirmed that it is aware of the active exploitation of the CVE-2023-27350 vulnerability.
The company received two vulnerability reports from the cybersecurity firm Trend Micro for high/critical severity security issues in PaperCut MF/NG. Trend Micro announced they will disclose further information (TBD) about the vulnerability on 10th May 2023.
The company addressed both vulnerabilities with the release of PaperCut MF and PaperCut NG versions 20.1.7, 21.2.11 and 22.0.9 and later, it highly recommends upgrading to one of these versions containing the fix
We have evidence to suggest that unpatched servers are being exploited in the wild. reads the advisory published by PaperCut. PaperCut received our first report from a customer of suspicious activity on their PaperCut server on the 18th April at 03:30 AEST / 17th April 17:30 UTC. PaperCut has conducted analysis on all customer reports, and the earliest signature of suspicious activity on a customer server potentially linked to this vulnerability is 14th April 01:29 AEST / 13th April 15:29 UTC.
The CVE-2023-27350 (CVSS score 9.8) is a PaperCut MF/NG Improper Access Control Vulnerability. PaperCut MF/NG contains an improper access control vulnerability within the SetupCompleted class that allows authentication bypass and code execution in the context of system.
The cybersecurity firm Horizon3 disclosed details of the flaw along with a PoC exploit code for CVE-2023-27350. The PoC code allows attackers to bypass authentication and execute code on vulnerable PaperCut servers.
The specific flaw exists within the SetupCompleted class. The issue results from improper access control. An attacker can leverage this vulnerability to bypass authen...
04:39
Links 24/04/2023: Qt Resorting to Analytics Techrights
![]()
Contents
-
GNU/Linux
-
Linux Links Linux Around The World: USA Delaware
We cover user groups that are running in the US state of Delaware. This article forms part of our Linux Around The World series.
-
Audiocasts/Shows
-
Jupiter Broadcasting Full Wobble | LINUX Unplugged 507
Why Fedora 38 might Sway you to try it; and how it runs on the MacBook M1 Max.
- ...
-
-
04:26
Linux Foundation Formally Selling SPAM Services in Violation of Terms of Services Techrights
While pushing a CoC the Linux Foundation is shamelessly violating rules, breaking netiquette, and even sponsoring clickfraud (this has gone on for years already)
This links to Asana. And Asana is proprietary by the way!
Summary: The Linux Foundation, governed by a fraud [1, 2, 3] family (the Zemlins), is basically breaking rules of the Internet in pursuit of money; its rather incredible that any person let alone a company would wish to associate with those frauds
04:00
Get to Know the IEEE Board of Directors IEEE Spectrum

The IEEE Board of Directors shapes the future direction of IEEE and is committed to ensuring IEEE remains a strong and vibrant organizationserving the needs of its members and the engineering and technology community worldwidewhile fulfilling the IEEE mission of advancing technology for the benefit of humanity.
This article features IEEE Board of Directors members Theresa Brunasso, Vickie Ozburn, and Ali H. Sayed.
IEEE Senior Member Theresa Brunasso
Director, Region 3: Southeastern United States
 Theresa
Brunasso is an IEEE senior member and the director of IEEE Region 3
(Southeastern United States).Theresa Brunasso
Theresa
Brunasso is an IEEE senior member and the director of IEEE Region 3
(Southeastern United States).Theresa Brunasso
Brunasso, who has more than 30 years of experience in electrical engineering, specializes in electromagnetics. Her work includes designing and developing RF, microwave, and millimeter wave components and subsystems for the defense and aerospace industries.
Brunasso has said that her favoriteand what she thinks is the coolestproject was leading the team responsible for winning the contract to build the Ka-Band radar antenna used to land the Curiosity and Perseverance rovers on Mars. The team developed the antenna to be rugged, compact, and lightweight. She also led the design of the microwave feed for the antenna, which yielded low side lobes. Brunasso and the rest of the team were awarded a certificate of appreciation from the NASA Jet Propulsion Laboratory for meeting the challenging requirements on a tight schedule.
Brunasso, an active IEEE volunteer, is a member of the IEEE Microwave Theory and Techniques Society and the IEEE Antennas and Propagation Society. She has served as the IEEE Atlanta Sections secretary, vice chair, and chair. She was one of three Georgia women honored in...
03:50
The SpaceX Starship Explosion Was Deliberate SoylentNews
Perhaps not all booms are bad:
About four minutes after SpaceX's gargantuan rocket lifted from its Texas launch pad, it burst into a fireball over the Gulf of Mexico, never reaching space.
Though SpaceX hasn't shared many details yet about what happened during Starship's maiden voyage, one fact is known: It was intentionally ordered to explode.
Rockets are destroyed in the air when people's lives could be even remotely at risk of falling debris. In the days since the uncrewed test, no injuries or major property damage appear to have been reported.
When the rocket launched at 9:33 a.m. ET April 20, 2023, some of the rocket's 33 booster engines had either burned out or failed to light from the start. As Starship ascended, cameras caught views of the flames underneath it, appearing to show some of the engines had cut out.
In a statement released after the incident, SpaceX said Starship climbed to about 26 miles over the ocean before beginning to lose altitude and tumble. Then, self-destruct commands were sent to the booster and ship, which hadn't separated as planned, the company said.
Read more of this story at SoylentNews.
03:15
Fedora 39 Looks To Boost vm.max_map_count To Help Windows Games With Steam Play Phoronix
Fedora 39 this autumn is looking at boosting its vm.max_map_count default to better match the behavior of SteamOS / Steam Deck and allowing more Windows games to run out-of-the-box with Steam Play...
02:22
Sports Betting Review And Promotions h+ Media
Sports Betting Review And Promotions
EcoPayz, one other well-liked e-wallet among punters has a minimum deposit requirement of INR 100. Each of those bets will must have a minimum of three choices and each of these choices should have odds of 1.40 or larger. The bonus might be credited to your bonus account after the deposit is processed efficiently. The accumulator outcomes market offers distinctive mixtures of various match outcomes with high odds. Not just that, however the betting web site additionally covers womens cricket quite extensively.
When betting in live, the coupon is crammed in when a turning event is observed on the sector. The result of the game depends tremendously on the skill of the users. It is important to learn to discard cards to reduce prices.
The reside variations of Blackjack and Roulette are something that must be skilled, as they offer spectacular visuals along with friendly sellers. Since there are games with totally different table limits, entry into considered one of these titles is lots easier than anticipated. An enormous variety of video games exist at 22Bet to offer a complete experience for on line casino gamers with varying levels of expertise. The slots have the most important illustration on this platform with titles from many developers like Endorphina, Evolution Gaming, Microgaming, Quick Spin, and extra featured.
The number of options that 22Bet presents is astonishing, making it an asset to the bettors neighborhood. It also has a fast pay-out system which is usually a really nervous spot for users. Payments have been smoother than ever, making the site fairly enticing and most well-liked by customers. McCullum joined 22Bet, an internet bookmaking company, as an ambassador in January and has appeared in its online commercials. However, the ECBs anti-corruption unit prohibits gamers, coaches, and officials from partaking in or provoking betting on matches. The board looked at the matter from a regulatory and employer viewpoint and concluded that no action was required.
The desired amount to be added is entered into the suitable field. The next step of the process entails finishing the transaction by going into the cost options switch window. Landing all bets will award you the TOTO Jackpot that can reach a quantity of crores in size!
One of the most important advantages of 22Bet is the provision of many markets to bet upon compared to many other betting sites. There are greater than forty sports activities lined by the brand and the record continues to grow. Naturally, it is easy to come back across a big spectrum of markets on in style sports like football, cricket, tennis, basketball, and golf. At the identical time, area of interest sports like skiing and desk tennis are additionally handed a decent diploma of significance. 22Bet doesnt limit a punter to desktop entry alone, as apps can be found from the model for placing bets and pe...
01:50
Linux 6.4 Allows For Optional CA Enforcement Of The Machine Keyring Phoronix
With the Linux 6.4 kernel there is the ability being introduced so that the machine keyring can optionally only store CA-enforced keys...
01:30
Chatting With Local AI Moves Directly In-Browser, Thanks to Web LLM Hackaday

Large Language Models (LLM) are at the heart of natural-language AI tools like ChatGPT, and Web LLM shows it is now possible to run an LLM directly in a browser. Just to be clear, this is not a browser front end talking via API to some server-side application. This is a client-side LLM running entirely in the browser.
D3 Security MSSP Client Portal simplifies information sharing between MSSPs and clients Help Net Security
D3 Security will unveil its MSSP Client Portal this week at the 2023 RSA Conference. The MSSP Client Portal is a one-stop shop for managed security service providers (MSSPs) and their clients to manage interactions and share information. Taking inspiration from the inputs of D3 Securitys many MSSP partners, the MSSP Client Portal streamlines client communication for MSSPs and connects clients approvals and comments directly to the D3 Smart SOAR environment. The portal gives MSSPs More
The post D3 Security MSSP Client Portal simplifies information sharing between MSSPs and clients appeared first on Help Net Security.
01:22
Machine learning framework classifies pneumonia on chest X-rays Lifeboat News: The Blog
Pneumonia is a potentially fatal lung infection that progresses rapidly. Patients with pneumonia symptoms such as a dry, hacking cough, breathing difficulties and high fever generally receive a stethoscope examination of the lungs, followed by a chest X-ray to confirm diagnosis. Distinguishing between bacterial and viral pneumonia, however, remains a challenge, as both have similar clinical presentation.
Mathematical modelling and artificial intelligence could help improve the accuracy of disease diagnosis from radiographic images. Deep learning has become increasingly popular for medical image classification, and several studies have explored the use of convolutional neural network (CNN) models to automatically identify pneumonia from chest X-ray images. Its critical, however, to create efficient models that can analyse large numbers of medical images without false negatives.
Now, K M Abubeker and S Baskar at the Karpagam Academy of Higher Education in India have created a novel machine learning framework for pneumonia classification of chest X-ray images on a graphics processing unit (GPU). They describe their strategy in Machine Learning: Science and Technology.
01:22
Study finds new pathway for clearing misfolded proteins Lifeboat News: The Blog
Misfolded proteins are toxic to cells. They disrupt normal functions and cause some age-related human degenerative diseases, like Alzheimers, Parkinsons, and Huntingtons diseases. Cells work constantly to eliminate misfolded proteins, but these clearance mechanisms are still poorly understood.
In a new study published April 20 in Nature Cell Biology, researchers at Stanford University discovered a previously unknown cellular pathway for clearing misfolded proteins from the nucleus, the compartment where the cell stores, transcribes, and replicates its DNA. Keeping junk away from those processes is critical to normal cellular function. The new pathway could be a target for age-related disease therapies.
To find the new pathway, researchers in the lab of Judith Frydman, the Donald Kennedy Chair in the School of Humanities and Sciences, integrated several genetic, imaging, and biochemical approaches to understand how yeast cells dealt with misfolded proteins. For the experiments, the team restricted misfolded proteins to either the nucleus or the cytoplasmthe area inside the cell but outside the nucleus. The team visually followed the fate of the misfolded proteins through live-cell imaging and super-resolution microscopy.
01:13
CVE-2023-30776: Apache Superset: Database connection password leak Open Source Security
Posted by Daniel Gaspar on Apr 24
Description:An authenticated user with specific data permissions could access database connections stored passwords by requesting a
specific REST API. This issue affects Apache Superset version 1.3.0 up to 2.0.1.
References:
https://superset.apache.org
https://www.cve.org/CVERecord?id=CVE-2023-30776
01:10
CVE-2023-27524: Apache Superset: Session validation vulnerability when using provided default SECRET_KEY Open Source Security
Posted by Daniel Gaspar on Apr 24
Description:Session Validation attacks in Apache Superset versions up to and including 2.0.1. Installations that have not altered
the default configured SECRET_KEY according to installation instructions allow for an attacker to authenticate and
access unauthorized resources. This does not affect Superset administrators who have changed the default value for
SECRET_KEY config.
Credit:
Naveen Sunkavally (Horizon3.ai) (finder)
References:...
01:06
Links 24/04/2023: Kdenlive 23.04.0 and Red Hat To Lay Off Over 700 Employees Techrights
![]()
Contents
-
GNU/Linux
-
9to5Linux 9to5Linux Weekly Roundup: April 23rd, 2023
This has been a tremendous week with lots of goodies for everyone, starting with the new major Proton 8.0 release of Linux gaming and continuing with the highly anticipated Fedora Linux 38 and Ubuntu 23.04 releases.
Linux kernel 6.3 also arrived this week and will soon land in your distros repositories, KDE fans got a new major KDE Gear release, KaOS Linux users celebrated the distros 10th anniversary with a preview of KDE Plasma 6, and Solus Linux users can keep using their favorite distro without the fear of it being abandoned.
-
Audiocasts/Shows
-
Bryan Lunduke The Lunduke Big Tech Show Apr 23, 2023 Hour 1
Listen now (0 sec) | The Death of Computer Magazines, A.I. taking away jobs, Tech Layoffs, and iOS Sideloading.
-
Bryan Lunduke The Lunduke Big Tech Show Apr 23, 2023 Hour 2
Listen now (0 sec) | Listener questions! All hour! So much nerdiness it makes my head explode!
-
-
Kernel Sp...
-
01:05
Users Report Ryzen 7000X3D Chips Burning Out, Killing Motherboards SoylentNews
Likely a motherboard BIOS issue:
High-performance microprocessors tend to get hot and, when overclocked without proper cooling or throttling, can literally burn out When an old CPU does so in an old PC because of dust and a worn out fan, there is nothing surprising about it. But when a new CPU breaks on a shiny new motherboard, that's surprising. This is what happened to an AMD Ryzen 7 7800X3D, one of the best CPUs, which belonged to a Reddit user. And, according to other users, he's not alone.
"The CPU pad is physically bulging," wrote Speedrookie, the owner of the burned-out processor. "I imagine there was just too much heat on the contacts causing the pad to expand. Not that the CPU has an internal component which exploded."
At least when it comes to AMD's Ryzen 7000X3D-series processors, it appears that this is by far not an isolated case. There are reports from other Reddit users who had the same experience with their Ryzen 7000X3D CPUs on motherboards from Asus and MSI.
Famous overclocker der8auer also had an issue with an AMD Ryzen 7000X3D chip burning out during some early overclocking tests a few weeks ago. As you can see in his video, he says "I did not expect this to happen so quickly and especially right out of the BIOS."
There are about a million of reasons why a modern processor can burn out. Defective sockets or a motherboards [sic] are likely causes and insufficient cooling can cause a similar result. A BIOS be a yet another reason for a processor failure. In fact, as noticed by HXL (@9550pro), Asus has just withdrew old BIOSes for many of its AMD X670-based motherboards, but for some of them old BIOSes are still available.
[...] Again, given that the information is insufficient to say the least, we cannot make any conclusions at this point. We'll reach out to our contacts at AMD and the motherboard vendors to see if they are aware of any issues. For now, we recommend that those with AMD's Ryzen 7000X3D processors keep a close eye on their CPU temps, use adequate cooling and keep their BIOSes up-to-date.
...
01:03
1xbet Registration
The minimum required deposit to stimulate the bonus supply is equal to 1 Euro. Provides one of the best Service plus the biggest number of Games , betting on Raffles, bets, Online betting in Bitcoins, Live lines for sports activities occasions and Prematch. Registration by way of sms With the betting 1xBet login review by using this technique, you have to enter and confirm the phone quantity and customary in your nation and specify the overseas foreign money. To 1xBet signing up on the portal you should click the green Register swap on the high right of the 1xBet Ghana registration website and choose one of the following strategies 1xBet registration. For occasion, you can play Blackjack with a minimum guess of $10 and a maximum wager of $5000. On the other hand, youll find a way to choose unlimited Blackjack and place bets as little as $1.
- On high of that, with these totally different sorts of themes, punters are assured that there could be a sport on the market that would swimsuit their fancy.
- So the web page doesnt look cluttered with all of the pointless tabs.
- There are hundreds of various video games that can entertain its users.
- We may be ready upon or processing your payment for your membership.
- We imagine that this programme is Aucklands most complete technical development programme, and players of all ages and skills will have the ability to see advantages that can take their sport to the following level in 2023.
Players can create affiliate packages in quite a lot of methods. The more affiliates they connect with 1xBet, the higher the reward. The desktop web site lives its own life but when you are going to disposal. One can view it even from the desktop system to assess its pros and outweigh all of the cons. Now that youve got joined many fellow males down the street to profitable betting, you can start enjoying the privilege of the bonus funds given away by 1xBet.
On the 1xBet house page, you will see a green registration icon on the top right of the web page. By clicking this icon, youll open a pop-up asking which technique you wish to use to register with this excellent site. Choose the One Click options, and you might be asked to input your nation and forex.
Operating since 2007, 1xBet has been providing a variety of bets, not just for sports events but in addition for TV video games. They provide an intensive selection of bets on worldwide sports competitions each at the club and nationwide degree. Clients o fulfill theminimum deposit and withdrawal necessities. For credit cards and financial institution transfers, processing may take as little as 1 day to five days.
So before you head over to the 1xBet web site, take a good look at all our money-saving offers and low cost codes to see what you can save. Th...
01:02
1xbet Casino New Zealand Receive Bonus $1200 h+ Media
1xbet Casino New Zealand Receive Bonus $1200
In the next step youll be asked to finish the player s personal information and registration information available. You must choose the area, foreign money and ensure the captcha used to protect against bots. Should you have a promo code, you probably can enter it in the process. The consumer receives an account number and password to enter his private account, which will he can either save within a convenient format, or mail to his e mail. You can be part of and receive a welcome supply of as much as 1500 and a hundred and fifty free spins too. You have to use the promo code STYVIP to get your palms on this glorious offer from 1xBet.
The second is a link with a coupon code, simply click on on it, and your discount will be deducted automatically from the whole quantity on the checkout. Make the acquisition benefiting from the reductions now available on Betmais. As mentioned above, there are lots of slot games and jackpots that youll find at 1xBet on line casino New Zealand, from some of the most well-known and traditional, to some exclusive to this betting platform. In addition, a lot of the slot video games and jackpots that arent from 1xBet Casino New Zealand itself, are from renowned on-line recreation developer firms corresponding to Microgaming, IGT and Playtech, for example. Leaving no stone unturned the staff right here at Stuff New Zealand Coupons are here to assist you get the easiest offers.
But earlier than you place your bets in 1 of these, you have to have a easy registration technique and receive in this system an individual how to open accounts. If you are tired of enjoying both Live Blackjack and real Blackjack at actual casinos, you must most likely attempt Online Blackjack. Playing Blackjack online instead of its different sorts has many benefits. You will get a lot better returns because it costs much less to run a game of Online Blackjack, youll get to get pleasure from free tries, you might have a big selection of choices to choose from, and extra.
The virtual bonus is credited to the bonus account right after the replenishment of the important thing account on Friday. Each 1xBet consumer may participate within the promotion only one time a week. Bonus video games any video games that happen upon Friday and are accomplished previous to the end of the day. With this Option you could get a part of the money from nonplaying gamble. Again, the method to obtain the app may be very simple, but it could differ, relying on the gadget you may be using.
Find video games with a excessive RTP share to enhance your winning potential. If you could have any questions or considerations about 1xBet, including however not limited to making a deposit, establishing an account, or enjoying a sport, the support team is out there to assist you. While the job of this new supervisory entity can be to supervise and problem lic...
01:00
Flashpoint Ignite accelerates cross-functional risk mitigation and prevention Help Net Security
Flashpoint has released Ignite, a new intelligence platform that accelerates cross-functional risk mitigation and prevention across CTI, vulnerability management, national security, and physical security teams. Ignite combines Flashpoints intelligence with an integrated user experience to help organizations streamline workflows, find relevant information, and reduce exposure to cyber and physical threats. Ignite delivers a holistic, real-time picture of all pertinent risks while reducing silos that can result from disparate intelligence feeds from multiple specialized partners. Ignite More
The post Flashpoint Ignite accelerates cross-functional risk mitigation and prevention appeared first on Help Net Security.
01:00
1xbet On Line Casino New Zealand Receive Bonus $1200 h+ Media
1xbet On Line Casino New Zealand Receive Bonus $1200
We anticipate that the cooperation of two world-class brands might be lucrative for each parties. Barcelonas slogan is More than a club and we hope that over the subsequent 5 years, the fans will come to realize that 1xBet is more than a bookmaker. The 1x Bet app is available for obtain, as nicely as all instructions, directly from the 1x Bet Website. It has a user-friendly interface, moderna and really simple to use.
The bonus is out there pertaining to the bookie s players in all nations. Register, open the bookmaker s bank account, deposit any quantity on your invoice and participate within the promotion. 2020 Lucky Friday give is a great way to obtain additional money.
- All you have to get the most popular first-class betting app is to be of legal age for playing on this jurisdiction and have an energetic e mail handle.
- On top of that, in addition they offer extra betting opportunities which are out there in particular markets because of country-specific events.
- In the block marked with the Android emblem, you want to click on the ,wager now apk, button, after which the apk file will begin its free download to your smartphone.
- It features full functionality since one can play slots or different 1xBet on line casino games, take pleasure in watching stay streams and proper bets real-time or make choice to the pre-match betting.
- Signup for free bonuses, every day jackpots and other giveaways.
- While were diligent to solely provide you with energetic coupon code provides, an expired discount occasionally slips by way of the cracks.
For instance, new customers for poker associates earn 40% of those users month-to-month betting expenses. The offered best bookmakers have a set of unique presents, as properly as the total or cellular model. Each of the listed companies rigorously screens market trends and constantly provides new copyright bonuses and incentives for its users.
This highly effective betting platform is out there to registered gamers on PC, Mac, and cellular units. The mobile functions can easily be downloaded from the desktop platform through the App Store for IOS units, or the Google Play Store for Android devices. Also, every person can track how the statistics change, for example, during the match and thus estimates their chances normally. The greatest on-line betting apps from Bet365 reveals all statistical information adjustments during a game.
The Web Site At 1xbet Casino
Ensuring you receive their great welcome supply is of paramount importance. Make positive that you place your 5x rollover bets on at least three alternatives for each accumulator wager, every of which must be on odds of no less than 1.four (2/5). Dont use your bonus along side some other promotional options provided by the 1xbet site. Make...
00:59
1xbet Access Is Denied How To Enter Utilizing Vpn Shopper 1xbet: One Of The Best Betting App For Cellular Sport-specific Training h+ Media
1xbet Access Is Denied How To Enter Utilizing Vpn Shopper 1xbet: One Of The Best Betting App For Cellular Sport-specific Training
The 1xBet Casino truly began with sports betting, which is why they have greater than 1,000 occasions every day that shoppers can wager on. This consists of popular sports activities like hockey, ski jumping, water polo, basketball, soccer, and a lot extra. On high of that, additionally they provide additional betting alternatives which would possibly be available in specific markets because of country-specific occasions. Since its launch, the website has grown from being a struggling newbie website that accepts bets right into a gaming big with a lot to supply. The firm now has many active registered gamers, amounting to nearly half a million.
This is among the most entertaining locations to verify if girl luck is at anyones aspect. The full gaming experience is available at 1xBet Casino. Being one of the largest on-line casinos and sports activities betting sites, the casino has an enormous revenue and a fair larger roster of players. Read on to get an entire overview of this on-line gaming web site. The bookmaker managed to develop actually progressive software that presents all bells and whistles.
As the result of the bets required to redeem the bonus will directly have an effect on the quantity you can withdraw once the bonus is settled, we would advocate putting your bets near the minimal odds of 1.four (2/5). This is a less risky betting option, and provides you a better probability of selecting a successful guess, and as such the next chance of receiving potential gains into your customer account. The bonus quantity shall be credited to the customer account after the first deposit is made provided that all account details are totally right.
As youve a whole 30 days by which to rollover your bonus quantity, we suggest taking your time and doing a little research before placing your bets. 30 days is a very long time in the online betting world, with an enormous multitude of presents out there to you. As such, it would not make sense to rush into a bet on the hot favourites without first doing some research on the meeting. Take your time and suppose out your strategy rigorously, youll not regret it. The bonus amount must be settled earlier than any withdrawals can be made from a buyer account.
Depending on the payment technique chosen, the quantity of fee for the service will depend on. You can decide the precise amount of fee when you withdraw winnings from your private account steadiness in the Portal Support Service. Bookmaker arises the need for passage of strategy of verification of personality.
- The bonus is valid for a 30-day time-period after registration.
- Our professional coaches, globally recognised curriculum and teaching method that has been frequently refined for the last 38 years will work wonders in your child...
00:58
1xbet Deposit Bonus Code Join Offer 227 5 Nzd Provided 1xbet Deposit Bonus April 2023 New Zealand h+ Media
1xbet Deposit Bonus Code Join Offer 227 5 Nzd Provided 1xbet Deposit Bonus April 2023 New Zealand
For extra opportunities to win big and actually enjoy your favorite video games, we advise you to check out the promos supplied by 1xBet. We normally highlight coupons that are legitimate for the entire store, in proportion and then fastened value. After that we offer special 1xBet offers in case you are interested in shopping for something for a discount.
1xBet Sportsbook is a responsible gaming operator with 18+ certification, firewall safety, and SSL encryption. 1xBet has partnered with leading sports golf equipment such as FCB , and is a proud promoter of the Spanish skilled football league, La Liga. Other badges embody CAF official sponsor, Brasileirao Serie A, and Natus Vincere.
In order for a bonus amount to be considered settled, it have to be rolled over at least 5 times in accumulator wager. These accumulator bets should all have at least three choices, and every choice must be of min. odds 1.4 (2/5). Pay attention and browse all the foundations carefully, because it is extremely complicated and obscure. Now, lets talk better slightly below about how the 1xBet on-line on line casino welcome bonus in New Zealand works. Win actual money enjoying one-armed bandits, video poker, slots and more.
1xBet has additionally applied 2FA system to scale back unauthorized access to users accounts. Players can use the Google Authenticator app to scan the QR code and enter a 6-digit code to confirm identity. Here, at LottoRanker our main objective is so that you just can play lotto in an environment you are feeling safe and secure. For you to get pleasure from enjoying the lottery with out worrying, we gathered the easiest of on-line lottery websites at Lottorank.co.nz. 1xBet was rated as 9.2 on our listing, it stands out for its deposit methods, available lotteries and its security. Playing at 1xBet you possibly can play from many alternative international locations, so you dont have to worry whether you play from Australia, and 1xBet also provides trusted fee options to their gamers.
We anticipate that the cooperation of two world-class manufacturers might be lucrative for both events. Barcelonas slogan is More than a membership and we hope that over the next 5 years, the fans will come to realize that 1xBet is greater than a bookmaker. The 1x Bet app is out there for obtain, in addition to all directions, immediately from the 1x Bet Website. It has a user-friendly interface, moderna and really straightforward to make use of.
1xBet is dedicated to ensuring that its users have a positive and safe gaming expertise. Thanks to the casinos dedication to player safety and ethical betting, its a well-liked go-to place for these looking for simply such circumstances. Coupon codes have an expiration date, or perhaps the code is no longer legitimate, or can solely be used...
00:45
Red Hat Begins Cutting "Hundreds Of Jobs" Phoronix
The tech layoffs have now reached Red Hat with "hundreds of jobs" being cut and the initial round of layoffs being announced today...
00:43
Security updates for Monday LWN.net
Security updates have been issued by Debian (389-ds-base, chromium, connman, curl, redis, and thunderbird), Fedora (ceph, doctl, dr_libs, ffmpeg, freeimage, golang-github-digitalocean-godo, insight, libreswan, mingw-binutils, mingw-freeimage, mingw-freetype, openvswitch, rnp, suricata, webkitgtk, and wireshark), Mageia (dnsmasq, emacs, openimageio, php-smarty, redis, squirrel/supertux, and tcpdump), Red Hat (emacs), and SUSE (avahi, chromium, dmidecode, indent, jettison, openssl, openstack-cinder, openstack-nova, python-oslo.utils, and ovmf).
00:37
EFF and ECNL's Comment to the Meta Oversight Board on the Term 'Shaheed' Deeplinks
EFF Intern Reema Moussa authored this post.
EFF recently submitted comments in partnership with the European Center for Not-for-Profit Law (ECNL) in response to the Oversight Boards request for input on the moderation of the Arabic word shaheed. The Oversight Board was created by Meta in 2020 as an appellate body and has 27 members from around the world who review contested content moderation decisions made by the platform. The Board opened public comment on the term after accepting Metas request for a policy advisory opinion on its approach to moderating the term when used to refer to individuals it classifies as dangerous, including terrorists.
EFF and ECNLs comments address the over-moderation of the word and other Arabic-language content, particularly through the use of automated content moderation tools. The comments also highlight the practical difficulties of moderating the term, and content written in the Arabic language generally speaking due to the complexities of translating high-context languages like Arabic.
Additionally, the comments highlight that refraining from using automated content moderation tools for content removal with the word shaheed is imperative for ensuring the free expression of Arabic-speaking users.
The Board proposed three recommendations to address moderation of the term, which is among the most often removed/moderated terms on the platform. EFF and ECNLs comments advocate for the adoption of Recommendation 2: the removal of content using shaheed to refer to individuals designated as dangerous under Metas policies only where there is praise, support, or a signal of violence.
Read the comments in the PDF below.
00:30
Akamai Brand Protector defends against phishing attacks and fake websites Help Net Security
At RSA Conference 2023, Akamai Technologies unveiled Brand Protector, a new solution that detects and disrupts phishing sites, fake stores, and brand impersonations. Brand Protector enables organizations to retain and grow customer loyalty while minimizing loss, drops in productivity and bad customer feedback. According to Google, over 50,000 new phishing websites are created every week. Akamai Brand Protector inspects trillions of digital activities a day across both internal and external sources to discover abuse of More
The post Akamai Brand Protector defends against phishing attacks and fake websites appeared first on Help Net Security.
00:13
1xbet India
For those who favor taking half in on their cell gadgets, 1xBet also presents a mobile app for iOS and Android users. The 1xbet app is a cellular betting app developed by the main online on line casino and sportsbook. The app is available for Android, iOS and Windows gadgets and offers access to a wide range of sports betting and on line casino video games. With the 1xbet app, users can guess on their favorite sports activities, observe the leads to real time and access their account data.
Every person can download 1xbet free of charge and set up this playing app on their smartphone. With respect to betting options, it doesnt differ from the pc model, allowing you to play and win at any time. To make things even more dynamic, its completely optimized, the navigation may be very user-friendly, and the interface is simplified.
Using this code is free and highly really helpful and youre invited to use it when registering to the app. To withdraw the cash without difficulties, it is important to adhere to the guidelines. The bonus scheme is designed to extend the odds of winning very excessive. The workplace of the bookmaker offers varied destinations, however the most well-liked are football-related, that are out there on the website in a wide array of. In other words, youll be able to improve the sum of money you deposit when you make the first deposit. I Rates can be obtained with tiny deposits, beginning as low as $1.
Freespins are awarded after wagering the cash portion of the package with a wager of 35. The bonus should be transferred to the primary account within 7 days, in any other case, it is going to be deleted. Activate it in the Personal Profile part by entering the verification code from the SMS within the form. Before we begin, its worth mentioning that smooth utilization of the app. Its value mentioning that the app, just like the official website, may be very snug to use to have the best expertise. Only gamers which might be new to Megapari can qualify for this promotion.
Through the 1xbet app, gamblers can deposit money and withdraw winnings. [newline]Enjoy all full desktop model benefits by way of your gadget. The 1xbet app has a good structure and is well-designed. 1xBet is originally a Russian on-line sports activities betting web site that started in 2007 but shortly expanded worldwide. Currently, 1xBet is probably one of the largest and most successful betting platforms in the world and operates in over 100 nations. It comes pre-installed on iPhone, iPad, and other Apple units.
Another choice is to go to the 1xbet website for a 1xbet Download , 1XBET APP DOWNLOAD . IOS device owners can use the 1xbet software download by way of the Apple store and download the APK file on the 1xbet website. To find out what it takes to obtain
00:11
1xbet Apk Download For Android h+ Media
1xbet Apk Download For Android
The strategy of 1xBet app download for iOS is the same as for Android smartphones. The app also has a convenient interface, engaging design, simple navigation, and astonishing visible results. A punter must 1xBet obtain a bookmaker consumer from the website.
In 1xbet Apk, you might be given many types of number games, on which you will have the ability to win it by betting on any sport of your choice. The interface language is set mechanically when the software program is installed. The language model of the primary website is taken under consideration, as nicely as the players region, which is about in the App Store.
These are very low system requirements and virtually all Android units possess them. Give it one other shot after that, and it should work. A free app that may make your betting life simpler positively deserves your attention.
Yes, it is legal to play at 1xBet as the platform is absolutely licensed beneath the well-respected Curacao gaming authority. Open the freshly downloaded APK file and set up it. Sports betting can be a enjoyable and thrilling way to make more money.
Wagering necessities should be absolutely met in order to have the ability to withdraw funds from the account. Only users with a one registered account can take part in bonus packages. The screenshots present the different sections of 1xBet app interface.
As quickly as they need a withdrawal, they begin writing to the administration. This may take a while, and even require extra checks. Then obtain the set up file directly from the Internet. [newline]Find it in the Downloads folder and run the set up, which often takes no extra than three minutes. Upon completion of the process, return to the settings, and restore the unique parameters. Keep in thoughts that this type of software is
1xbet primary screen1xbet casino1xbet bettingThe largest advantage of utilizing the 1xBet app is the improved state of freedom. You dont have to be tied to your personal pc all day or go to any bookmaker daily. With the assistance of some clicks, youll have access to a lot of the benefits of the well-known worldwide bookmaker and on-line casino. In the screenshots provided, you presumably can see the 1xBet apps look. 1xbet obtain for ios has been rated as some of the dependable cell apps for betting on sports in both Android and iOS markets.
But anyway, Id certain suggest u guys to try it out. To do this, you need to download the applying on the official web site and install it on your smartphone in accordance with the instructions we gave on this web page. After this, a shortcut will appear on the desktop to launch the appliance. You can place a stay guess during a match, allowing you to watch what is happening on the sector and make extra correct betting selections. This possibility is suitable fo...
00:09
Real world vulnerabilities of CWE-1077: Floating Point Comparison with Incorrect Operator? Open Source Security
Posted by Georgi Guninski on Apr 24
Are there real world examples of vulnerabilities of this:https://cwe.mitre.org/data/definitions/1077.html
CWE-1077: Floating Point Comparison with Incorrect Operator
This issue can prevent the product from running reliably. If the
relevant code is reachable by an attacker, then this reliability
problem might introduce a vulnerability.
One simple example in python:
(False, 1.1102230246251565e-16, 0.6000000000000001, 0.6)
00:08
Search Outcomes For pocket Sport Developer Apk Openak319com 888 On Line On Line Casino Login 1xbet Withdraw Drawback Openak319com$$limitadong Regalo!mag Register Para Makakuha Ng P50 Might 50% Cashback Sayong Unang Deposit!$$c2 h+ Media
Search Outcomes For pocket Sport Developer Apk Openak319com 888 On Line On Line Casino Login 1xbet Withdraw Drawback Openak319com$$limitadong Regalo!mag Register Para Makakuha Ng P50 Might 50% Cashback Sayong Unang Deposit!$$c2
Virtual sports activities are very fast, and you can make some cash if you place a correct prediction, as the outcome will be identified in only a few minutes. In the 1xBet app, yow will discover video games such as Golden Race, Leap, DS Virtual Gaming, games, and many others. All the games are powered by software providers corresponding to Nsoft, DS, Scout Network, and others. Many famend software suppliers energy the casino at 1xBet, such as Pragmatic Play, NetEnt, Ezugi, and a lot of others. However, we additionally offer our own games, that are the 1xLive ones.
The app and the simplified model are virtually the same. The styling, structure, sports and bonuses are the same. Differences can be highlighted in the usability, in addition to within the scale of some interface elements. The 1xBet app can be used to get recommendation from a support representative. The app guarantees the confidentiality of private and payment info.
A positive coefficient will point out that the online winnings shall be less than the wager amount. The plus coefficient shows the size of the players internet revenue at a bet of a hundred items. Thus, the coefficient (+110) will imply that with a bet of 100 models, the player will receive a profit of 110 units.
The betting agency has a complicated Tech staff that oversees the operation of the location. The Advancement bonus is useful when youre running out of cash in your 1xbet virtual bank account. In the event that there are two unresolved betting slips with energetic bets, you could place the Advancement immediately on the guess slips. The iOS cellular app interface is divided into two elements. Events scheduled for the approaching season are proven throughout the main part, while stay events which might be at present occurring are proven within the second part. Yes, it makes no difference which device you employ as a outcome of 1xBet is supported on each iOS and Android as properly as Windows.
1xBet players can immediately deposit by way of a variety of prompt and safe payment strategies together with Visa, Mastercard, Skrill, and all kinds of cryptocurrencies. Never worry about updating your app or downloading an enormous file! With 1xBets mobile website youll have the ability to play instantly immediately in your devices browser. 1xBet could have began out as a sportsbook; it has now grown into a full gaming platform that includes a world-class casino section!
Here you will discover not only slot machines, but also a lot that our gamers value. India CSR is the largest media on CSR and sustainability providing numerous content material throughout multisectoral issues on enterprise accountability. Depending...
00:06
1xbet Bull Slots Apk Obtain 2023 h+ Media
1xbet Bull Slots Apk Obtain 2023
Virtual sports are very quick, and you might make some money should you place an accurate prediction, because the result will be recognized in only a few minutes. In the 1xBet app, yow will discover video games corresponding to Golden Race, Leap, DS Virtual Gaming, games, and tons of others. All the games are powered by software program providers such as Nsoft, DS, Scout Network, and others. Many renowned software suppliers energy the on line casino at 1xBet, similar to Pragmatic Play, NetEnt, Ezugi, and plenty of others. However, we also provide our own games, that are the 1xLive ones.
Over the course of a month, I tried many games in demo mode to learn the way it works, which I advise you to do as nicely. You cannot deposit money just to do this or that sport. You might access fantasy sports activities video games utilizing the 1xBet betting app or website. The games are listed in orderly columns in the lobby, with a timer on the side indicating when the next recreation will start. The 1111 matches are presented first, adopted by the 88 tables. The sports activities that we offer on this part embody cricket, soccer, and others.
After downloading and putting in the 1xbet free app for the device you are utilizing, Android or iOS, the following step is registering. Users who have already got a 1xbet account dont have to enroll and may sign up, make financial transactions and make bets. The interface for gaming on the cellular model is appropriate with landscape and portrait modes. Gamers can choose which methodology is interesting to them when putting bets. 1xBet is not inferior to other on-line on line casino sites, even when it comes to buyer assist. As talked about within the last section of the article, not all on-line casinos can boast of the ability to supply the consumer with all the necessary companies.
So when you first land on the primary page, you will count on an inventory of upcoming sports matches and occasions along with high odds and other particulars. First of all, see in case your gadget meets the minimum system necessities and if youve adjusted your security settings. When these issues are settled, you possibly can wait somewhat bit in the case of upkeep issues. If this doesnt work, you possibly can always contact the client help group to resolve your issues or simply start betting by way of the mobile-optimised site.
In comparison with the online site, the Android or Apple applications grant an equal variety of deposit/withdrawal approaches. To observe the obtainable banking strategies in your area, go to the My Account tab and choose deposit or withdrawal choices correspondingly. 1xbet cell exhibits no disadvantages of a cellular site model. To carry out the successful 1xbet app download, you should go to the main web page first.
Popular forms of Poker on 1xbet embody Poker Dog, American Poker, Bonus Poker, Lucky Poker and Tower Poker. Playing...
00:01
How to install Red Hat OpenShift Local on your laptop Linux.com
Install Red Hat OpenShift Local on your own machine to test your applications and configurations before deployment.
Read More at Enable Sysadmin
The post How to install Red Hat OpenShift Local on your laptop appeared first on Linux.com.
00:00
Trellix Threat Intelligence enhancements accelerate threat analysis and response Help Net Security
At RSA Conference 2023, Trellix announced it has expanded its Threat Intelligence portfolio to increase threat expertise and actionable intelligence to help global customers stay ahead of cyber adversaries. The new offerings include Vulnerability Intelligence and Trellix Intelligence as a Service. Through a new partnership with Intel 471, Trellix Insights and Trellix Advanced Threat Landscape Analysis System (ATLAS) customers will add underground malware insights. This new intelligence feed will complement Trellixs native threat intelligence capability More
The post Trellix Threat Intelligence enhancements accelerate threat analysis and response appeared first on Help Net Security.
00:00
The BSides: more curious uses of off-the-shelf parts Hackaday

Off-the-shelf stock parts are the blocks from which we build mechanical projects. And while plenty of parts have dedicated uses, I enjoy reusing them in ways that challenge what they were originally meant for while respecting the constraints of their construction. Building off of my piece from last time, Id like to add to your mechanical hacking palette with four more ways we can re-use some familiar off-the-shelf parts.
O-Rings as Retention Features
Plenty of us are using rubber o-rings as airtight seals between static or moving parts. But their elastic and grippy properties give them a second life in other places involving removable components.
On my tool-changing machine, Jubilee, I quickly ran into the issue of securing idle tools onto their parking posts without the risk of letting them fall out. While one tool is being used, the remaining idle tools need to sit in a fixed location so that the machines carriage can pick them up later. To complicate the matter, the motion platform creates an appreciable amount of vibration, and idle too...
00:00
Russian Hackers Tomiris Targeting Central Asia for Intelligence Gathering The Hacker News
The Russian-speaking threat actor behind a backdoor known as Tomiris is primarily focused on gathering intelligence in Central Asia, fresh findings from Kaspersky reveal. "Tomiris's endgame consistently appears to be the regular theft of internal documents," security researchers Pierre Delcher and Ivan Kwiatkowski said in an analysis published today. "The threat actor targets government and
Monday, 24 April
23:52
People Are Getting Plastic Surgery Now So They Can Try To Look Like These Filters cryptogon.com
I just emailed this to a friend with a teenage daughter who is a heavy Tiktok user. I thought Tiktok was mostly a bunch of short attention span nonsense, wasting peoples time. Nope. Its much worse than that. Names have been changed: Hi John I saw a disturbing video about TikTok. I remember you mentioning []
23:46
Sean OBrien and Mikalai Birokou on Least Authority Services via Free Software Techrights
Summary: The above LibrePlanet talk by Sean OBrien and Mikalai Birokou (physical presence) was uploaded by the FSF (PeerTube link) 6 days plus 6 hours ago; From the official page: This session will demonstrate the current status of 3NWeb protocols and client using Trisquel GNU/Linux and RYF hardware. 3NWeb use cases include encrypted messaging and storage. The protocols can be run over anonymous Free Software networks such as Tor and are agnostic in regard to addressing. For example, nodes can be communicated with via .onion hidden services or IPFS namespaces.
Licence: CC BY SA 4.0
Notice/side note: Unlike Gulagboy Matthew Garrett, they do not advocate outsourcing trust to Microsoft (which would be the complete opposite of security), but when Microsofters infiltrate projects this is what's promoted at the expense of users safety.
23:44
Ransomware Hackers Using AuKill Tool to Disable EDR Software Using BYOVD Attack The Hacker News
Threat actors are employing a previously undocumented "defense evasion tool" dubbed AuKill that's designed to disable endpoint detection and response (EDR) software by means of a Bring Your Own Vulnerable Driver (BYOVD) attack. "The AuKill tool abuses an the Microsoft utility, Process Explorer, to disable EDR processes before deploying
23:33
Organizations are stepping up their game against cyber threats Help Net Security
Global median dwell time drops to just over two weeks, reflecting the essential role partnerships and the exchange of information play in building a more resilient cybersecurity ecosystem, according to Mandiant. Modern cyber defense capabilities The report reveals the progress organizations globally have made in strengthening defenses against increasingly sophisticated adversaries. M-Trends 2023 makes it clear that, while our industry is getting better at cybersecurity, we are combating ever evolving and increasingly sophisticated adversaries. Several More
The post Organizations are stepping up their game against cyber threats appeared first on Help Net Security.
23:25
EvilExtractor, a new All-in-One info stealer appeared on the Dark Web Security Affairs
EvilExtractor is a new all-in-one info stealer for Windows that is being advertised for sale on dark web cybercrime forums.
Fortinet FortiGuard Labs researchers discovered a new all-in-one info stealer for Windows, dubbed EvilExtractor (sometimes spelled Evil Extractor) that is available for sale on dark web cybercrime forums.

EvilExtractor is a modular info-stealer, it exfiltrates data via an FTP service. The tool was developed by a company named Kodex, which claims that the tool was developed for an educational purpose. The bad news is that according to FortiGuard Labs, cybercriminals are actively using the tools as an info stealer.
The malware environment checking and Anti-VM functions.
Based on our traffic source data to the host, evilextractor[.]com, malicious activity increased significantly in March 2023. FortiGuard Labs observed this malware in a phishing email campaign on 30 March, which we traced back to the samples included in this blog. reads the report published by Fortinet. It usually pretends to be a legitimate file, such as an Adobe PDF or Dropbox file, but once loaded, it begins to leverage PowerShell malicious activities.
The researchers observed a surge in attacks spreading the malware in March 2023, most of the infections were reported in Europe and the U.S.
The tool is sold on cybercrime forums by an actor that goes online with the name Kodex, the developer released its project in October 2022 and is continuously updating it by releasing new modules with new features.
The malware can steal sensitive data from the infected endp...
23:23
3CX breach linked to previous supply chain compromise Help Net Security
Pieces of the 3CX supply chain compromise puzzle are starting to fall into place, though were still far away from seeing the complete picture. In the meantime, we now also know that: The source of the 3CX breach was a compromised installer for X_TRADER, an old software package for futures-trading provided by Trading Technologies The trojanized installer for X_TRADER software was also used to drop a backdoor on the systems of two critical infrastructure organizations More
The post 3CX breach linked to previous supply chain compromise appeared first on Help Net Security.
23:06
In the Worlds Biggest Population, Microsofts Bing Fell Below 1%, Down Sharply Since ChatGPT First Announced Techrights
Meanwhile, Microsoft-funded journalists insist that Google is doomed because of ChatGPT
The data tells another story:
Summary: Bing down from 1.1% to 0.9% since ChatGPT was first unveiled (distracting from 4 consecutive months of mass layoffs in the company)
23:00
3Dfx Voodoo 1 & 2 Glide Linux Driver Retired, Other X.Org Code Officially Retired Phoronix
In clearing up the state of various X.Org packages that have been effectively unmaintained for years, an attempt is being made to better communicate the status of some "retired" X.Org packages that Linux distributions should work towards removing as they are no longer being maintained...
22:30
SELinux In Linux 6.4 Removes Run-Time Disabling Support Phoronix
After being deprecated for several years, Security Enhanced Linux "SELinux" beginning with the Linux 6.4 kernel can no longer be run-time disabled...
22:21
Physicists Create the Fattest Schrdinger's Cat Ever SoylentNews
A recent experiment tested the mass-based boundaries between the quantum and classical realms:
Picture a cat. I'm assuming you're imagining a live one. It doesn't matter. You're wrong either waybut you're also right. This is the premise of Erwin Schrdinger's 1935 thought experiment to describe quantum states, and now, researchers have managed to create a fat (which is to say, massive) Schrdinger cat, testing the limits of the quantum world and where it gives way to classical physics.
Schrdinger's experiment is thus: A cat is in a box with a poison that is released from its container if an atom of a radioactive substance, also in the box, decays. Because it is impossible to know whether or not the substance will decay in a given timeframe, the cat is both alive and dead until the box is opened and some objective truth is determined. [...]
In the same way, particles in quantum states (qubits, if they're being used as bits in a quantum computer) are in a quantum superposition (which is to say, both "alive" and "dead") until they're measured, at which point the superposition breaks down. Unlike ordinary computer bits that hold a value of either 0 or 1, qubits can be both 0 and 1 simultaneously.
Now, researchers made a Schrdinger's cat that's much heavier than those previously created, testing the muddy waters where the world of quantum mechanics gives way to the classical physics of the familiar macroscopic world. Their research is published this week in the journal Science.
In the place of the hypothetical cat was a small crystal, put in a superposition of two oscillation states. The oscillation states (up or down) are equivalent to alive or dead in Schrdinger's thought experiment. A superconducting circuit, effectively a qubit, was used to represent the atom. The team coupled electric-field creating material to the circuit, allowing its superposition to transfer over to the crystal. Capiche?
"By putting the two oscillation states of the crystal in a superposition, we have effectively created a Schrdinger cat weighing 16 micrograms," said Yiwen Chu, a physicist at ETH Zurich and the study's lead author, in a university release.
Read more of this story at SoylentNews.
22:04
Aggressive Microsoft Marketing/Lies as Bing Falls Closer to 2% Market Share, Google Gains More Share (ChatGPT Has Only Harmed Bing, Which Has Layoffs Too) Techrights
Example of media spam today (just yet more of that GOOGLE IS DEAD talking point; ever since ChatGPT was introduced Bing consistently lost share; it is a de facto censorship and distortion machine):
What has Bloom been smokin?
Consider the public data. Microsoft is down, not up:
Summary: Theres
a lot of noise in the media today*; it serves to
distract from a fresh round of Microsoft
layoffs
_____
* Microsoft trolls including Gulagboy
Matthew Garrett also did a lot of a very aggressive trolling
in IRC yesterday.
This is bordering on the criminal.
21:55
Russian cybercrime group likely behind ongoing exploitation of PaperCut flaws Security Affairs
Print management software provider PaperCut confirmed ongoing active exploitation of CVE-2023-27350 vulnerability.
On April 19th, Print management software provider PaperCut confirmed that it is aware of the active exploitation of the CVE-2023-27350 vulnerability.
The company received two vulnerability reports from the cybersecurity firm Trend Micro for high/critical severity security issues in PaperCut MF/NG.
Trend Micro announced they will disclose further information (TBD) about the vulnerability on 10th May 2023.
The company addressed both vulnerabilities with the release of PaperCut MF and PaperCut NG versions 20.1.7, 21.2.11 and 22.0.9 and later, it highly recommends upgrading to one of these versions containing the fix
We have evidence to suggest that unpatched servers are being exploited in the wild. reads the advisory published by PaperCut. PaperCut received our first report from a customer of suspicious activity on their PaperCut server on the 18th April at 03:30 AEST / 17th April 17:30 UTC. PaperCut has conducted analysis on all customer reports, and the earliest signature of suspicious activity on a customer server potentially linked to this vulnerability is 14th April 01:29 AEST / 13th April 15:29 UTC.
The CVE-2023-27350 (CVSS score 9.8) is a PaperCut MF/NG Improper Access Control Vulnerability. PaperCut MF/NG contains an improper access control vulnerability within the SetupCompleted class that allows authentication bypass and code execution in the context of system.
Last week, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) added it to its Known Exploited Vulnerabilities Catalog.
Huntress researchers have observed post-exploitation activities within its partner environments after attackers exploited the above PaperCut MF/NG vulnerabilities.
Huntress security researcher Caleb Stewart also devised a proof-of-concept exploit for these threats, below is the video PoC shared by the company:
21:55
Study: 84% of Companies Use Breached SaaS Applications - Here's How to Fix it for Free! The Hacker News
A recent review by Wing Security, a SaaS security company that analyzed the data of over 500 companies, revealed some worrisome information. According to this review, 84% of the companies had employees using an average of 3.5 SaaS applications that were breached in the previous 3 months. While this is concerning, it isn't much of a surprise. The exponential growth in SaaS usage has security and
21:41
Hackers Exploit Outdated WordPress Plugin to Backdoor Thousands of WordPress Sites The Hacker News
Threat actors have been observed leveraging a legitimate but outdated WordPress plugin to surreptitiously backdoor websites as part of an ongoing campaign, Sucuri revealed in a report published last week. The plugin in question is Eval PHP, released by a developer named flashpixx. It allows users to insert PHP code pages and posts of WordPress sites that's then executed every time the posts are
21:37
The Microsoft Spin Machine Resumes Amid Layoffs, Azures Decline, and Worse News Techrights
Summary: So-called news so-called reporting (see the above from Reuters, with focus on profits after layoffs; companies to highlight AI) will be used to disguise or distract from whats actually happening; its already starting on the wrong foot for Microsoft, so it wants everyone to believe the future is glamorous and all about HEY HI (AI); they keep making puff pieces about an HEY HI arms race (miraculously Microsoft is already the self-professed market leader owing to paid-for hype campaigns) and other such nonsense, looking for additional bailouts and asking shareholders for patience
With reports about Azure failing at RoI, citing typical HEY HI (AI) misdirection, were meant to think everything will be rosy this week (see screenshot above; Microsoft is not after layoffs, the layoffs are still ongoing and not stopping). Microsoft-connected publishers try to change the subject (Microsoft-Activision Deal), probably seeking distract from Microsoft layoffs ahead of disappointing quarterly "results". They basically quote a paid Microsoft lobbyist, Florian Mueller, who has a two-way confl...
21:23
Why will NASAs Artemis 2 only fly around the moon, not orbit or land? Lifeboat News: The Blog
NASA landed 12 astronauts on the moon during the Apollo program more than half a century ago. So why is the upcoming Artemis 2 mission just doing a lunary fly-around?
21:23
Three of Metas top execsincluding Mark Zuckerbergare now spending most of their time on A.I. Lifeboat News: The Blog
Facebook and Instagram owner Meta will release a commercial A.I. product, following moves from Google, Microsoft, and OpenAI, in 2023 confirmed Reality Labs boss Andrew Bosworth.
21:23
AI will Not Become Conscious Rupert Sheldrake Lifeboat News: The Blog

This clip is from the Before Skool Podcast ep. # 4 with Rupert Sheldrake. Full podcast can be accessed here: https://www.youtube.com/watch?v=68fjlUuvOGM&t=3784s.
Rupert Sheldrake, PhD, is a biologist and author best known for his hypothesis of morphic resonance. At Cambridge University he worked in developmental biology as a Fellow of Clare College. He was Principal Plant Physiologist at the International Crops Research Institute for the Semi-Arid Tropics in Hyderabad, India. From 2005 to 2010 he was Director of the Perrott-Warrick project for research on unexplained human and animal abilities, administered by Trinity College, Cambridge. Sheldrake has published a number of books A New Science of Life (1981), The Presence of the Past (1988), The Rebirth of Nature (1991), Seven Experiments That Could Change the World (1994), Dogs That Know When Their Owners are Coming Home (1999), The Sense of Being Stared At (2003), The Science Delusion (Science Set Free) (2012), Science and Spiritual Practices (2017), Ways of Going Beyond and Why They Work (2019).
Rupert gave a talk entitled The Science Delusion at TEDx Whitechapel, Jan 12, 2013. The theme for the night was Visions for Transition: Challenging existing paradigms and redefining values (for a more beautiful world). In response to protests from two materialists in the US, the talk was taken out of circulation by TED, relegated to a corner of their website and stamped with a warning label.
To Learn more about Rupert Sheldrake and his research, please visit https://www.sheldrake.org/
Please subscribe to Before Skool. Thank you.
21:18
VMware plugs security holes in VMware Aria Operations for Logs (CVE-2023-20864, CVE-2023-20865) Help Net Security
VMware has fixed two vulnerabilities (CVE-2023-20864, CVE-2023-20865) in VMware Aria Operations for Logs (formerly vRealize Log Insight), a widely used cloud solution for log analysis and management. About the vulnerabilities (CVE-2023-20864, CVE-2023-20865) CVE-2023-20864, a deserialization vulnerability, could be exploited by an unauthorized, malicious actor who has network access to VMware Aria Operations for Logs. This can result in the execution of arbitrary code as root. CVE-2023-20865 is a command injection vulnerability that allows a bad More
The post VMware plugs security holes in VMware Aria Operations for Logs (CVE-2023-20864, CVE-2023-20865) appeared first on Help Net Security.
21:00
3D Scanning a Room With a Steam Deck And a Kinect Hackaday

It may not be obvious, but Valves Steam Deck is capable of being more than just a games console. Demonstrating this is [Parker Reed]s experiment in 3D scanning his kitchen with a Kinect and Steam Deck combo, and viewing the resulting mesh on the Steam Deck.
20:43
Improved AMD Color Management Being Worked On For The Steam Deck Phoronix
Open-source Linux graphics driver engineer Melissa Wen with Igalia, Joshua Ashton with Valve, and Harry Wentland with AMD have been working on kernel mode-setting (KMS) color pipeline enhancements for SteamOS and in particular for enhancing the Steam Deck...
20:28
Kdenlive 23.04 Open-Source Video Editor Released With Nested Timelines Phoronix
Kdenlive remains one of the best available fully open-source non-linear video editing solutions available. With today's release of Kdenlive 23.04 they continue enhancing its feature set and improving the UI/UX for those editing videos on the Linux desktop...
20:21
LibrePlanet: Dr. William Cooper Davidon Uses Boeing 737 Max Aircrafts as Example of Proprietary Software Causing Deaths Techrights
Summary: The above LibrePlanet talk by Dr. William Cooper Davidon was uploaded by the FSF (PeerTube link) six days ago; From the official page: In safety-critical software, mistakes and errors can be lethal. Recent accidents with the Boeing 737 Max Aircraft illustrate the failure of proprietary software required to have undergone careful review following the F.A.A.s DO-178x certification process. Governments and the people they represent must strongly consider requiring free software to be used for safety-critical code implementations. Free software offers transparency and a much higher level of review than what is possible with proprietary software.
Licence: CC BY SA 4.0
20:06
Linux 6.4 Kernel Graphics Drivers Include More Meteor Lake Code, Rockchip 4K, QAIC Phoronix
With Linux 6.3 released that marks the opening of the two-week Linux 6.4 merge window. David Airlie sent in the Direct Rendering Manager (DRM) subsystem updates already for Linux 6.4 with the assortment of kernel graphics/display driver updates...
19:34
Weird SARS-CoV-2 Outbreak in Mink Suggests Hidden Source of Virus in the Wild SoylentNews
The lineage had not been seen in the area for over two years:
[...] SARS-CoV-2 infections in mink aren't particularly noteworthy or concerning on their own; it's well established that mink are susceptible to the virus. The realization early in the pandemic resulted in extensive culls in Denmark and the Netherlands during 2020 and led to intensive monitoring and regulation of remaining mink herds in many places, including Poland.
But the recent cases in Polish mink, reported this week in the journal Eurosurveillance, are unusual. While previous mink outbreaks have linked to infected farmworkers and local circulation of the virusindicating human-to-mink spreadnone of the farm workers or families in the recently affected farms tested positive for the virus. In fact, health investigators found that the infected mink carried a strain of SARS-CoV-2 that has not been seen in humans in the region in more than two years (B.1.1.307).
The finding suggests that humans were not responsible for infecting the minkat least not directly. Rather, it suggests that another unknown species may have been stealthily harboring and spreading the otherwise bygone strain for some time and managed to carry it onto the mink farms.
The suggestion raises more concern over viral "spillback." The term relates to the more recognized "spillover," when a virus jumps from a host populationa reservoirto a new population, such as humans. SARS-CoV-2 is thought to have originated in a reservoir of horseshoe bats before it reached humans. Since then, it is clear that it can also infect a broad range of animals, including rodents, cats, dogs, white-tail deer, non-human primates, as well as ferrets and mink. Researchers fear that the virus could spill back to an animal population that could become a new reservoir from which the virus could periodically move back to humans.
Read more of this story at SoylentNews.
19:22
The A.I. Dilemma Tristan Harris & Aza Raskin Center for Humane Technology March 9, 2023 Lifeboat News: The Blog
This video is from a presentation at a private gathering in San Francisco on March 9th with leading technologists and decision-makers with the ability to influence the future of large-language model AIs. This presentation was given before the launch of GPT-4.
Center for Humane Technology.
Original video : https://vimeo.com/809258916/92b420d98a
19:22
ChatGPT may hinder the cybersecurity industry Lifeboat News: The Blog
Join top executives in San Francisco on July 1112, to hear how leaders are integrating and optimizing AI investments for success. Learn More
Since its launch in November 2022, ChatGPT, an artificial intelligence (AI) chatbot, has been causing quite a stir because of the softwares surprisingly human and accurate responses.
The auto-generative system reached a record-breaking 100 million monthly active users only two months after launching. However, while its popularity continues to grow, the current discussion within the cybersecurity industry is whether this type of technology will aid in making the internet safer or play right into the hands of those trying to cause chaos.
19:13
Press Report This Morning: Microsoft Azure Layoffs Again, Entire Team Laid Off (Updated) Techrights
So what we published only hours ago is turning out to be correct already:
Summary: As per the report, everyone at the FastTrack for Azure NZ team [..] have been laid off as Microsoft cuts costs globally, Larsen (New Zealand) wrote.
Update: More here.
Microsoft appears to be making significant layoffs across Australia and New Zealand as the global economy heads south.
A post this morning by Daniel Larsen, principal customer experience engineer at Microsofts local FastTrack for Azure team based in New Zealand, said that entire team had been laid off.
After seven wonderful years at Microsoft I, along with the rest of the FastTrack for Azure NZ team, have been laid off as Microsoft cuts costs globally, Larsen wrote.
While this is disappointing, its also an opportunity to reset and try something new.
Larsen described five other affected employees as world class engineers experienced in deploying large and complex Azure workloads.
As noted 5 hours ago: Azure layoffs have gone on every year since 2020 (the media almost never mentions this and trolls from Microsoft are very sensitive about this topic, based on what we saw in IRC).
18:28
Hackers can hack organizations using data found on their discarded enterprise network equipment Security Affairs
ESET researchers explained that enterprise network equipment that was discarded, but not destroyed, could reveal corporate secrets.
ESET researchers purchased a few used routers to set up a test environment and made a shocking discovery, in many cases, previously used configurations had not been wiped.
The experts pointed out that the data they found on the devices could be used to identify the prior owners, this information can be used by threat actors to breach their networks.
Results reported here show that a majority of the secondary market core routers sampled contained recoverable configuration data from their previous deployments, replete with sensitive, and even confidential, data. This allowed ESET researchers to identify devices previously used in a data center/ cloud computing business (specifically, a router provisioning a universitys virtualized assets), a nationwide US law firm, manufacturing and tech companies, a creative firm, and a major Silicon Valleybased software developer, among others. reads the report published by ESET.
The experts highlight the importance of adopting a procedure to correctly dismiss enterprise network equipment, like routers, due to the huge quantity of information they contain.
The ESET research team decided to conduct a more extensive test and purchased 18 used routers to determine which kind of information was possible to find on the dismissed network equipment and how threat actors can use them in future attacks against the company that discarded them.
This enterprise network equipment is widely adopted by
organizations worldwide, ESET explained that they are a class of
device that is commonly available at bargain basement prices in the
secondary market
(US$50150).
Below is the list of devices bought by ESET:
- 4 Cisco Systems ASA 5500 series
- 3 Fortinet FortiGate series
- 11 Juniper Networks SRX Series Services Gateway
One of the routers was dead on arrival and two were a mirrored pair. The report...
18:27
Resecurity to showcase innovative cybersecurity solutions at RSA Conference 2023 Help Net Security
Resecurity is excited to announce its participation at RSA Conference 2023, the cybersecurity event that brings together industry leaders and professionals to share knowledge and insights on the latest trends, threats, and solutions. The event will take place from April 24-27, 2023, at the Moscone Center in San Francisco, California. This years theme Stronger Together resonates with Resecuritys mission to provide cybersecurity solutions that empower organizations to detect, prevent, and respond to sophisticated cyber threats. More
The post Resecurity to showcase innovative cybersecurity solutions at RSA Conference 2023 appeared first on Help Net Security.
18:00
OSI Superboard II Replicated Hackaday

While our modern computer can easily emulate a lot of different old machines, there is something about having replica hardware that is even better. Not as nice as having the real thing, in some ways, although you dont have to worry about wear and tear on a replica, either. [Jeff Tranter] has built a kit replica of an Ohio Scientific Superboard II, and it looks great, as you can see in the video below.
This was an inexpensive all-in-one 6502 computer with a keyboard and provision for TV or monitor output. If you had a 5V power supply, a cassette deck, and a TV you were in business for less money than most of the comparable alternatives. In fact, [Jeff] has the canceled check where his parents paid $486 Canadian for one in 1981. That was his introduction to computing, and wed say that was a reasonable investment on the part of his parents.
Like many of us, [Jeff] was sad when his old computer was destroyed while in storage. But undeterred, he set out to build a replica. Earlier, hed built a reproduction kit that used modern components, but he wanted something a bit more faithful. He noticed that modern reproduction PCBs were available for the board and some matching I/O as well. The boards are very similar to the original, with a few concessions to modern times like footprints for modern keyboard switches and EEPROMs.
Not all of the parts are readily available, but with a little detective work, you can get what you need. He even found...
17:47
How product security reached maturity Help Net Security
Product security has been driving major changes throughout the automotive, medical, and industrial sectors. However, just a few short years ago, it was a term few knew and even less considered its own discipline. Slava Bronfman, Co-Founder & CEO of Cybellum discusses his experience in watching the product security sector mature over the last decade in the recent episode of Left to our Own Devices podcast. Bronfman has been an active member and contributor to More
The post How product security reached maturity appeared first on Help Net Security.
17:42
Links 24/04/2023: Shotwell 0.32.0 and Linux 6.3 Released Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Gemini* and Gopher
-
GNU/Linux
-
Server
-
Kubernetes Blog Kubernetes 1.27: Server Side Field Validation and OpenAPI V3 move to GA
Before Kubernetes v1.8 (!), typos, mis-indentations or minor errors in YAMLs could have catastrophic consequences (e.g. a typo like forgetting the trailing s in
replica: 1000could ca...
-
-
17:28
Leaked EC Plan to Combat IPTV Piracy Disappoints Rightsholders TorrentFreak
 In
mid-January, the European Commission (EC) issued a call for
evidence to support a proposed toolbox of measures to combat live
sports piracy.
In
mid-January, the European Commission (EC) issued a call for
evidence to support a proposed toolbox of measures to combat live
sports piracy.
Rightsholders usually welcome support at the EU level with open arms, but in this case it only increased frustrations. Last October a huge coalition of rightsholders called on the EC to introduce new law that would compel intermediaries to take pirate streams offline within minutes of a complaint.
The EC refused and offered existing law as the solution. For rightsholders claiming to have exhausted its limits, that clearly wasnt ideal.
More Evidence Needed
Over a period of several years, rightsholders have reported in fine detail the numerous challenges they face when it comes to tackling piracy of live sports. Dozens of reports spanning thousands of pages have left almost no stone unturned. The issue is comprehensively mapped, to say the least.
This January, the EC issued a call for evidence so that rightsholders and other stakeholders could detail their problems all over again. The aim was to find solutions to these well-documented problems under existing law, which rightsholders insist is inadequate.
Whether anyone learned anything substantially new from that process is unknown but having gone through the motions, the ECs recommendation will be officially released early May. Perhaps fittingly given the topic, the ECs report has already leaked online and according to reports, rightsholders are underwhelmed by the document, to put it mildly.
Leaked Report Delivers Disappointment
While it must be frustrating for the EC to see its report publicly rejected in advance of its release, one gets the impression that nobody really expected the EC to come up with anything groundbreaking, at least not on the scale demanded by rightsholders.
Euractiv says the recommendation focuses on the effective handling of take-down requests, dynamic injunctions, and voluntary cooperation but for rightsholders already engaged in all of these things and more, that advice seems unlikely to inspire.
An anonymous representative of the Live Content Coalition, which counts the Audiovisual Anti-Piracy Alliance (AAPA) and several other...
17:22
Hackers can breach networks using data on resold corporate routers Lifeboat News: The Blog
Enterprise-level network equipment on the secondary market hide sensitive data that hackers could use to breach corporate environments or to obtain customer information.
Looking at several used corporate-grade routers, researchers found that most of them had been improperly wiped during the decommissioning process and then sold online.
17:22
17:01
IRC Proceedings: Sunday, April 23, 2023 Techrights
Also available via the Gemini protocol at:
- gemini://gemini.techrights.org/irc-gmi/irc-log-techrights-230423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-230423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-social-230423.gmi
- gemini://gemini.techrights.org/irc-gmi/irc-log-techbytes-230423.gmi
Over HTTP:
|
... |
17:00
Genetic chaos leads to rapidly developing cancers Terra Forming Terra
Your Brain Is Shaped Like Nobody Elses Terra Forming Terra

Western Media Failures Regarding Ukraine. An Irish Historical Perspective Terra Forming Terra

The surprise to me is that the NAZI meme both predated WWII and then persisted under the rule of the USSR. And it is fair game for an Irish commentator because they can never be blinded by the propaganda of the majority opinion. If your fasmily is sympathetic to a minority taste, you end up atually been objective.
A cure for grey hair on the horizon? Terra Forming Terra

16:49
Red Alert: ICANN and Verisign Proposal Would Allow Any Government in the World to Seize Domain Names SoylentNews
Red Alert: ICANN and Verisign Proposal Would Allow Any Government In The World To Seize Domain Names:
ICANN, the organization that regulates global domain name policy, and Verisign, the abusive monopolist that operates the .COM and .NET top-level domains, have quietly proposed enormous changes to global domain name policy in their recently published "Proposed Renewal of the Registry Agreement for .NET", which is now open for public comment.
Either by design, or unintentionally, they've proposed allowing any government in the world to cancel, redirect, or transfer to their control applicable domain names! This is an outrageous and dangerous proposal that must be stopped. While this proposal is currently only for .NET domain names, presumably they would want to also apply it to other extensions like .COM as those contracts come up for renewal.
The offending text can be found buried in an Appendix of the proposed new registry agreement. Using the for quickly seeing what has changed compared with the current agreement), the critical changes can be found in Section 2.7 of Appendix 8, on pages 147-148. [...]
It would allow Verisign, via the new text in 2.7(b)(ii)(5), to:
Read more of this story at SoylentNews.
16:36
New All-in-One "EvilExtractor" Stealer for Windows Systems Surfaces on the Dark Web The Hacker News
A new "all-in-one" stealer malware named EvilExtractor (also spelled Evil Extractor) is being marketed for sale for other threat actors to steal data and files from Windows systems. "It includes several modules that all work via an FTP service," Fortinet FortiGuard Labs researcher Cara Lin said. "It also contains environment checking and Anti-VM functions. Its primary purpose seems to be to
16:05
Russian Hackers Suspected in Ongoing Exploitation of Unpatched PaperCut Servers The Hacker News
Print management software provider PaperCut said that it has "evidence to suggest that unpatched servers are being exploited in the wild," citing two vulnerability reports from cybersecurity company Trend Micro. "PaperCut has conducted analysis on all customer reports, and the earliest signature of suspicious activity on a customer server potentially linked to this vulnerability is 14th April 01
15:48
LibrePlanet Talk About Free Software in Critical Agricultural Equipment Techrights
Summary: The above LibrePlanet talk from sick.codes was uploaded by the FSF last week (slides here; PeerTube link); From the official page: Free software is used in almost all mission critical agricultural equipment: GPS guidance, vehicle ECUs, touch screen displays. In this talk, I will demonstrate how much free software is used to maintain the food supply chain, as we know it and the importance of keeping free software in these processes. Secondly, the importance of upholding the four essential freedoms that are already in use by major agriculture companies, hardware makers, inventors most importantly, the users, farmers.
Licence: CC BY SA 4.0
15:32
The Inside Story of Sirius Open Source Pretending to be American schestowitz.com
Video download link | md5sum
8ce515754e59d043a723d0590817c9ce
Sirius Situation
Creative Commons Attribution-No Derivative Works 4.0
Summary: The second part of Sirius Open Source Fantasy (an ongoing series; there are two series about Sirius running in conjunction at the moment) deals with what the text below
ABOUT a year ago, some time in April, Sirius privately admitted it was having issues. It was trying to spin those as a strength. The person who likely participated in defrauding staff (she saw those fake payslips for years) sent a misleading message. It was soon followed by a misleading online meeting.
The above video does not play back any of that meeting, but it is summarised by noting that the company was planning to move to the US (that never happened!)
Staff raised concerns about a number of different issues. The talking went on and on for nearly 2 hours, nothing is interesting enough to single out, but what we have discussed about the meeting since then was likely summarised here back in December and January. Well try to avoid repetition. Some of the later parts will be more interesting.
15:29
The Sirius Open Source Fantasy Part II Briefings About the Company Techrights
Series parts:
- The Sirius Open Source Fantasy Part I In 2022 the Company Was Already Too Deep in Debt
- YOU ARE HERE Briefings About the Company
Video download link | md5sum
8ce515754e59d043a723d0590817c9ce
Sirius Situation
Creative Commons Attribution-No Derivative Works 4.0
Summary: The second part of Sirius Open Source Fantasy (an ongoing series; there are two series about Sirius running in conjunction at the moment) deals with what happened 11.5 months ago; the above video is a
ABOUT a year ago, some time in April, Sirius privately admitted it was having issues. It was trying to spin those as a strength. The person who likely participated in defrauding staff (she saw those fake payslips for years) sent a misleading message. It was soon followed by a misleading online meeting.
Staff raised concerns about a number of different issues.The above video does not play back any of that meeting, but it is summarised by noting that the company was planning to move to the US (that never happened!)
Staff raised concerns about a number of different issues. The talking went on and on for nearly 2 hours, nothing is interesting enough to single out, but what we have discussed about the meeting since then was likely summarised here back in December and January. Well try to avoid repetition. Some of the later parts will be more interesting.
15:06
Microsofts Quarterly Results for This Week Expected to Disappoint, More Layoffs This Week or in Summer (July) Techrights
Video download
link | md5sum
6fcadc40c887fff7b6a14fafef7589df
Microsoft Layoffs Ahead
Creative Commons Attribution-No Derivative Works 4.0
Summary: Microsofts financial results (due in the middle of this week) are already expected to miss targets (set by Microsoft itself), based on media reports from reputable sources; whats not known, however, is whether Microsoft will announce the next major round of layoffs some time very soon or in summertime (based on rumours this is expected in July)
THE Microsoft layoffs in the past month or so are not part of the 10,000 announced in January (the media keeps parroting this while ignoring months of consequent and unrelated layoffs, not to mention contractors and temps). There are more to come. Expect more layoffs. The word coming from/through the grapevine is that in July (summer, ahead of results) there will be truly massive layoffs on a scale bigger than in January. What remains unknown, however, is whether this week too Microsoft will announce additional layoffs to appease investors; maybe WARN Act can be dodged somehow, but they have until Wednesday to say something (all we see is mindless puff pieces).
People who still work for Microsoft are very anxious, but they feel unable to leave as not many other companies recruit at all.Days ago a few media outlets dropped a hint that Microsofts results would disappoint in the clown computing area (read: Azure), so one can imagine more layoffs in this supposedly strategic and growth domain. Azure layoffs have gone on every year since 2020 (the media almost never mentions this and trolls from Microsoft are very sensitive about this topic, based on what we saw in IRC).
People who still work for Microsoft are very anxious, but they feel unable to leave as not many other companies recruit at all. As a result, they overwork (for the...
15:00
Unlocking the passwordless era Help Net Security
Although interest in passwordless technology, which aims to eliminate the need for passwords, is relatively low, 65% of consumers are receptive to using new technology that simplifies their lives, according to 1Password. Passkeys, the newest and most secure passwordless technology, are poised to do just that, transforming our online lives by making logging in simpler to navigate and far more secure. Convenience shouldnt come at the expense of security, said Jeff Shiner, CEO of 1Password. More
The post Unlocking the passwordless era appeared first on Help Net Security.
15:00
Rickrolling SSID with ESP32 Hackaday

Reddit user [nomoreimfull] posted code for a dynamic WiFi beacon to r/arduino. The simple, but clever, sketch is preloaded with some rather familiar lyrics and is configured to Rickroll wireless LAN users via the broadcast SSID (service set identifier) of an ESP32 WiFi radio.
The ESP32 and its smaller sibling the ESP8266 are tiny microcontrollers that featuring built-in WiFi support. With their miniature size, price, and power consumption characteristics, theyve become favorites for makers, hackers, and yes pranksters for a wide variety of projects. They can be easily programmed using their own SDK or through a board support extension to the Arduino IDE.
For the dynamic WiFi beacon, the ESP32 is placed into AP (access point) mode and broadcasts its human readable name (SSID) as configured. What makes the SSID dynamic, or rolling, is that the sketch periodically updates the SSID to a next line of text stored within the code. Of course, in the Rickroll prank this means the next line of lyrics from Never Gonna Give You Up by Rick Astley himself.
Always a favorite prank, weve seen Rickrolls take the form of IR remote controls ,...
14:01
NASA and Japan Team Up for Unprecedented Martian Moon Mission SoylentNews
JAXA is getting ready to visit Mars's two moons, but Japan's space agency is no longer going alone.
This week, NASA signed a memorandum of understanding with JAXA to join its upcoming mission to the two Martian moons, Phobos and Deimos, which is scheduled to launch in 2024. NASA has assembled a team of scientists and prepared two instruments to board JAXA's spacecraft to Mars, the space agency announced on Tuesday.
The Martian Moons eXploration (MMX) mission will not only visit the two mysterious moons that whirl around Mars, it will also land on the cratered surface of Phobos to snag a sample from the largest of the two moons.
It's an ambitious plan as no spacecraft has successfully ventured to the Martian moons before, let alone land on one. JAXA, however, has some experience in returning samples from cosmic bodies. The Japanese space agency's Hayabusa spacecraft retrieved samples from asteroid Itokawa's surface in 2010, while Hayabusa2 returned samples from a different asteroid named Ryugu in 2020.
[...] The main purpose of the mission is to analyze the origins of the Martian moons and determine whether they are in fact captured asteroids in the Mars system or fragments that coalesced together following a huge impact on the Red Planet. The mission could help scientists better understand how terrestrial planets like Mars form and learn more about the history of the planet.
Read more of this story at SoylentNews.
12:39
MEO - 8,227 breached accounts Have I Been Pwned latest breaches
In early 2023, a corpus of data sourced from the New Zealand based face mask company MEO was discovered. Dating back to December 2020, the data contained over 8k customer records including names, addresses, phone numbers and passwords stored as MD5 Wordpress hashes. MEO did not respond to multiple attempts to report the breach.
12:00
Shake Your PCB Etching, With An Old Optical Drive Hackaday

Easy PCB fabrication in China has revolutionised electronic construction at our level, but there are still times when it makes sense to etch your own boards. Its a messy business that can also be a slow one, but at least a project from [earldanielph] takes away one chore. It agitates the etchant solution round the board, by moving the tank backwards and forwards on the drawer of an old optical drive.
The first part of the build is simply removing all parts of the drive except the drawer mechanism and its motor. This is still, in most cases, a DC motor, so an Arduino can easily drive it with a motor control shield. Its worth a moment to reflect on how little there is to a modern optical drive.
The Arduino receives a sketch that moves the tray backward and forward, and a piece of ply is attached to the tray. This becomes a stand for a plastic tub containing the etchant and board, and the liquid is soon swishing back and forwards over the surface. You can see the result in the video below the break. Definitely a saving over manual agitation. Its an inventive machine, but its not...
11:58
LibrePlanet Talk About ARM and RISC-V Techrights
Summary: The above LibrePlanet talk is a month-old physical presence talk and it was uploaded by the FSF 5 days ago (slides here; PeerTube link); From the official page: The RISC-V architecture and ecosystem have undergone tremendous growth recently. We will take a look at the current state of RISC-V and its current deployment footprint. Well discuss where RISC-V may be headed and the role it may play in completely open and free datacenter servers, tablets, and cellphones. We will review the emergence of the ARM architecture and how in may be an important stepping stone to a free computing platform. Well discuss the differences between the ARM licensing model and the X86_64 architecture licensing model as well as the role of ARM processors in cell phones and cloud datacenters (such as AWS). Finally, well take a brief look at some options for starting RISC-V free and open hardware development for both experienced FPGA programmers and newbies. Well explain options including physical RISC-V processors, FPGAs, and software emulation.
Licence: CC BY SA 4.0
11:38
[Meme] Soft on Crime Techrights
Summary: The good news is that crimes of Sirius Open Source were formally reported to the authorities but the bad news is that, according to them, it may take up to 28 days to investigate (the process is different when you have connections)
11:27
The Plan That Never Materialised (Sirius Corporation in 2022) schestowitz.com
Series parts:
- YOU ARE HERE ? In 2022 the Company Was Already Too Deep in Debt
Video download link |
md5sum 5955a4f5328798df162f089486615507
Sirius in 2022
Creative Commons Attribution-No Derivative Works 4.0
Summary: A look back at what happened in Sirius Open Source last year
THE last year of Sirius (CEO left already) is easy to recall in light of an old recording of a 2-hour meeting. After the company had secretly plundered its own staff it was desperately chasing clients while abusing and underpaying staff, as we explained before.
In the name of cost savings (nope!) it adopted clown computing and then it let go of a physical office. It was changing servers by getting rid of its own. Everything it had left was a virtual asset there were no physical assets left. Such facts have been mentioned since, even in the meeting, which brought up potential clients. Its worth noting that these clients never became actual clients of Sirius and the company was trying to rebrand or reinvent itself as SiriUS (it was pronounced Sir US).
The manager who left last month was basically reporting to staff, showing his graph presentation while talking about sales, engineering, infrastructure, outsourcing, support, projects etc. Of course it all become a complete disaster. Almost an hour in he was summarising the re-infrastructuring process something that never happened.
I first considered leaving the company in 2019 (after the likely illegal contract-signing, then the NDA and the bullying), but last year I was already sure Id leave. That the company secretly plundered members of staff is something that wasnt confirmed until this year. Now we work towards accountability (prosecution).
11:22
The Sirius Open Source Fantasy Part I In 2022 the Company Was Already Too Deep in Debt Techrights
Series parts:
- YOU ARE HERE In 2022 the Company Was Already Too Deep in Debt
Video download link |
md5sum 5955a4f5328798df162f089486615507
Sirius in 2022
Creative Commons Attribution-No Derivative Works 4.0
Summary: A look back at what happened in Sirius Open Source last year
THE last year of Sirius (CEO left already) is easy to recall in light of an old recording of a 2-hour meeting. After the company had secretly plundered its own staff it was desperately chasing clients while abusing and underpaying staff, as we explained before.
In the name of cost savings (nope!) it adopted clown computing and then it let go of a physical office. It was changing servers by getting rid of its own. Everything it had left was a virtual asset there were no physical assets left. Such facts have been mentioned since, even in the meeting, which brought up potential clients. Its worth noting that these clients never became actual clients of Sirius and the company was trying to rebrand or reinvent itself as SiriUS (it was pronounced Sir US).
That the company secretly plundered members of staff is something that wasnt confirmed until this year. Now we work towards accountability (prosecution).The manager who left last month was basically reporting to staff, showing his graph presentation while talking about sales, engineering, infrastructure, outsourcing, support, projects etc. Of course it all become a complete disaster. Almost an hour in he was summarising the re-infrastructuring process something that never happened.
I first considered leaving the company in 2019 (after the likely illegal contract-signing, then the NDA and the bullying), but last year I was already sure Id leave. That the company secretly plundered members of staff is something that wasnt confirmed until this year. Now we work towards accountability (prosecution).
11:15
The Farthest-away Pictures of Earth Ever Taken SoylentNews
Our precious planet seen from deep space:
NASA's exploration robots have rumbled around Mars, swooped around Saturn, and flown well beyond the planets, into interstellar space.
But the space agency's engineers often direct their machines to peer back at the vivid blue dot in the distance.
"During almost every mission we turn around and take a picture back home," NASA's former chief historian, Bill Barry, told Mashable. "There seems to be an irresistible tendency to look back at home."
Indeed, in the cosmic images below you'll glimpse some of the farthest-away views of our humble, ocean-blanketed world ever captured by humanity. When we view other objects, worlds, stars, or even galaxies, we often see just dots. But to most of the cosmos, we're just a dot in the vast ether, too.
The article has nice images of the Earth and Moon taken by OSIRIS-REx, Earth as seen from the surface of Mars, a video flyby of the Earth and Moon by the Juno spacecraft, and a beautiful shot of Earth looking back with Saturnian rings in the view by Cassini, all reminding us of Carl Sagan's famous Pale Blue Dot where he observed:
To my mind, there is perhaps no better demonstration of the folly of human conceits than this distant image of our tiny world. To me, it underscores our responsibility to deal more kindly and compassionately with one another and to preserve and cherish that pale blue dot, the only home we've ever known.
Read more of this story at SoylentNews.
11:00
GNU Linux-libre 6.3-gnu Cleans Up New ath12k WiFi Driver, Other New Additions Phoronix
Following this afternoon's release of the Linux 6.3 kernel, GNU Linux-libre 6.3-gnu has already been released as this downstream kernel flavor that removes support for loading binary-only modules and trying to de-blob other driver code that otherwise depends upon "non-free" code...
10:12
DistroWatch Weekly, Issue 1016 DistroWatch.com: News
This week in DistroWatch Weekly: Review: Qubes OS 4.1.2News: Ubuntu improves Snap performance, Solus plans to resume development, Manjaro fixes installer bugs, FreeBSD publishes status report, KaOS celebrates tenth anniversaryQuestions and answers: Tracking bandwidth usageReleased last week: Fedora 38, Ubuntu 23.04, deepin 20.9Torrent corner: Fedora, KDE neon, Lubuntu,....
10:00
HPR3841: The Oh No! News. Hacker Public Radio
The Oh No! news. Oh No! News is Good News. Threat analysis; your attack surface. Article: US Marshals Service Computer System Hit by Ransomware Attack. Author: Michael Kan. (2023, Feb 28). The agency uncovered the intrusion on Feb. 17 2023, when it discovered “a ransomware and data exfiltration event affecting a standalone USMS system.” That means the hackers stole information from the computer while planting malicious code capable of encrypting the data inside. “The affected system contains law enforcement sensitive information, including returns from legal process, administrative information, and personally identifiable information pertaining to subjects of USMS investigations, third parties, and certain USMS employees,” the agency says. Article: US Shuts Down 'Netwire' Malware That Posed as Legit Remote Admin Tool. Author: Michael Kan. (2023, Mar 10). Worldwiredlabs.com has been around since at least 2012(Opens in a new window), offering a software product called “Netwire,” which is supposedly designed to help IT support staff manage computers remotely. Before the site was seized, it was offering Netwire for $10 per month or $60 per year. However, US investigators say the site was a front to sell the software as a hacking tool to cybercriminals. Supporting Article: Federal Authorities Seize Internet Domain Selling Malware Used to Illegally Control and Steal Data from Victims’ Computers. Author: U.S. Attorney's Office, Central District of California. (2023, Mar 9). A seizure warrant approved by a United States Magistrate Judge on March 3 and executed on Tuesday led to the seizure of www.worldwiredlabs.com, which offered the NetWire remote access trojan (RAT), a sophisticated program capable of targeting and infecting every major computer operating system. “A RAT is a type of malware that allows for covert surveillance, allowing a ‘backdoor’ for administrative control and unfettered and unauthorized remote access to a victim’s computer, without the victim’s knowledge or permission,” according to court documents filed in Los Angeles. Supporting Article: FBI takes down cybercrime forum that touted data connected to breach affecting US lawmakers. Author: Sean Lyngaas. (2023, Mar 24). The FBI has arrested the alleged founder of a popular cybercriminal forum that touted data stolen in a hack affecting members of Congress and thousands of other people and taken the website down, the Justice Department said Friday. Article: Data Breach a
09:00
Hackaday Links: April 23, 2023 Hackaday

Mark it on your calendars, folks this is the week that the term RUD has entered the public lexicon. Sure, most of our community already knows the acronym for rapid unscheduled disassembly, and realizes its tongue-in-cheek nature. But given that the term has been used by Elon Musk and others to describe the ignominious end of the recent Starship test flight, it seems like RUD will catch on in the popular press. But while everyones attention was focused on the spectacular results of manually activating Starships flight termination system to end its by-then uncontrolled flight at a mere 39 km, perhaps the more interesting results of the launch were being seen in and around the launch pad on Boca Chica. Thats where a couple of hundred tons of pulverized reinforced concrete rained down, turned to slag and dust by the 33 Raptor engines on the booster. A hapless Dodge Caravan seemed to catch the worst of the collateral damage, but the real wrath of those engines was focused on the Orbital Launch Mount, which now has a huge crater under it.
So how...
08:33
Health insurer Point32Health suffered a ransomware attack Security Affairs
Non-profit health insurer Point32Health suffered a ransomware attack and has taken systems offline in response to the incident.
Non-profit health insurer Point32Health has taken systems offline in response to a ransomware attack that took place on April 17. The insurer immediately launched an investigation into the incident with the help of third-party cybersecurity experts to determine the ext
The organization notified law enforcement and regulators, and it is currently working to recover the operations.
On April 17, Point32Health identified a cybersecurity ransomware incident that impacted systems we use to service members, accounts, brokers and providers. At this time, most systems impacted are on the Harvard Pilgrim Health Care side of our business. After detecting the unauthorized party, and out of an abundance of caution, we proactively took certain systems offline to contain the threat. reads the statement published by the insurer.
Most impacted systems are related to Harvard Pilgrim Health Care, which a few days ago announced on Facebook that it was experiencing technical issues with its website and phone lines.
The company did not provide details about the attack, such as the family of ransomware that compromised its systems and the number of impacted individuals.
Please vote for Security Affairs (https://securityaffairs.com/) as
the best European Cybersecurity Blogger Awards 2022 VOTE FOR YOUR
WINNERS
Vote for me in the sections:
- The Teacher Most Educational Blog
- The Entertainer Most Entertaining Blog
- The Tech Whizz Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please nominate Security Affairs as your favorite blog.
Nominate here: https://docs.google.com/forms/d/e/1FAIpQLSfaFMkrMlrLhOBsRPKdv56Y4HgC88Bcji4V7OCxCm_OmyPoLw/viewform
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
...06:35
The 6.3 kernel is released LWN.net
Linus has released the 6.3 kernel as expected.
It's been a calm release this time around, and the last week was really no different. So here we are, right on schedule, with the 6.3 release out and ready for your enjoyment.That doesn't mean that something nasty couldn't have been lurking all these weeks, of course, but let's just take things at face value and hope it all means that everything is fine, and it really was a nice controlled release cycle. It happens.
Significant changes in this release include the removal of a lot of obsolete Arm board files and drivers, ongoing improvements to the (still minimal) Rust language support, red-black trees for BPF programs, ID-mapped mounts for tmpfs filesystems, BIG TCP support for IPv4, support for non-executable memfds, the hwnoise jitter-measurement tool, and a lot more. See the LWN merge-window summaries (part 1, part 2) and the (in-progress) KernelNewbies 6.3 page for more information.
06:27
End of an Era: the Last Two Print Computer Magazines Just Pressed Their Last Issues SoylentNews
MacLife and Maximum PC April issues will be their last physical versions:
Magazines are so retro: If you are anything like me, you probably remember the days when you subscribed to multiple computing magazines. I still have fond memories of typing out the computer programs in the back pages of some publications; I even submitted a few of my own.
When high-speed internet came along, many computing publications began producing digital versions of their magazines online. Those with subscriptions still got their physical copies, but the online component was a nice perk for when readers could not just pick up a magazine and start reading, like at work.
Before long, most computing magazines had online versions and, at some point, started ditching paper. It was easier and cheaper to publish one copy that all subscribers could access online rather than printing hundreds of thousands of physical versions.
[...] The demise of print media in the computing industry was inevitable. By the 2000s, many prominent magazines had shut down their printing arms and switched to digital only. Byte stopped printing in 1998. Windows Magazine crashed in 2002, and the succinctly titled PC Magazine (now PCMag) published its last issue in 2009. Computer Gaming World went entirely out of business with its November 2006 issue.
[...] Print advertising also played a big part in the decline of computer publications. Once advertisers realized replicating ads on web pages was cheap and easy, they gradually pulled out of print computer magazines. Many physical magazine branches shut down for that reason alone. If the pub didn't have the clout of names like PC Magazine, Maximum PC, or PC World, it had no chance of competing against the internet for ad space. Even the almanac-like Computer Shopper plunged from nearly 360,000 readers in 1996 to about 55,000 in 2014.
Read more of this story at SoylentNews.
06:20
This is a lighter produced by Zippo during the 90s, with a drawing of Jimbo by Gary Panter.
Doesnt look like its ever been used, even though it also looks kinda beat up?
Futility grace of design. Indeed.
This blog post is part of the Punk Comix series.
05:30
Linux 6.3 Released With More Meteor Lake Enablement, Zen 4 Auto IBRS & Much More Phoronix
Linus Torvalds just released Linux 6.3 as the newest stable kernel version...
04:27
High Court: YouTube-Ripping is Illegal. UK National Newspaper: Totally Legal TorrentFreak
 Given the popularity of YouTube and the huge number of
websites and apps that allow people to rip music from the platform,
the conflict surrounding stream-ripping shouldnt be
underestimated.
Given the popularity of YouTube and the huge number of
websites and apps that allow people to rip music from the platform,
the conflict surrounding stream-ripping shouldnt be
underestimated.
Downloading a track takes about the same time as a shrug of the shoulders followed by an internal who cares? Multiply that by hundreds of millions of people shrugging several times a week, and the answer is the recording industry, big time.
Stream-Ripping and Public Perception
Many people in the UK, especially younger people, believe that listening to music on YouTube and ripping songs from YouTube are broadly the same thing. Both options are free; whats the problem? Strangely, the value of likes and views is comprehensively understood when the topic of conversation isnt centered on ripping music from YouTube.
The reasons for that disconnect aside, lots of people do ask questions. Is it legal to download music from YouTube? is always popular, along with its self-focused twin sister, Can I get caught downloading music from YouTube?
Thankfully, Google Lawyer (Google Doctors twin brother) is always around to help.
Anyone who read past the first line of this top result, collect 10 points. Those who read the second, take another 20 because that claim seems fairly important and we may have to come back to it.
If you spotted that the advice is published on a site promoting YouTube-ripping tools, nice work. Unfortunately, the article is of no fundamental use, no matter what it says, since it speaks about U.S. copyright law.
With no copyright experts immediately available on TikTok or Facebook, we turned to the UKs third pillar of wisdom to get answers the big questions.
Free Legal Advice, Nationwide
Since lawyers are expensive, its not unusual to see some national newspapers put out a bit of legal advice here and there to make life that little bit easier. Thanks to the following text appearing in their URLs (youtube-to-mp3-converter-free-online and youtube-to-mp4) a pair of articles published in The Sun were easy to find.
Both were published this March; one asks Is converting YouTube to MP3 legal and safe? a...
03:18
LibrePlanet Talk by Joseph Turner (USHIN) on Emacs for P2P Deliberation Techrights
Summary: The above LibrePlanet talk by Joseph Turner was uploaded by the FSF 5 days ago (slides here; PeerTube link); From the official page: The ushin project explores Org mode for peer-to-peer deliberation. Ushin offers the seven shapes (or kinds of meaning) deliberative structure for mutual understanding by distinguishing facts, feelings, needs, thoughts, topics, actions, and people. When communicating over the hyperdrive peer-to-peer network, you have full control over your data. With no central authority to censor misinformation, decision-making power is distributed. A subjective moderation system inspired by TrustNet makes it easy to find sources of information you can trust. Org mode is already an effective tool for organizing personal knowledge, and we want to use it to deliberate collective issues. Ushin combines these ideas into a fun and easy-to-use plain-text system for discussing important issues free of censorship, bots, and trolls through community curation.
Licence: CC BY SA 4.0
02:48
Chinese Are All Over Afghan Lithium cryptogon.com
Via: ZeroHedge: A Chinese company has offered the Taliban $10 billion and a proposal to build key strategic infrastructure connecting north-south Afghanistan in exchange for access to the countrys lithium reserves. Darbey said the Chinese interest in the region is not newin 2021, two Chinese companies were sent to Ghazni to conduct technical research []
02:37
Ex-FBI Agents Accuse Top CIA, FBI Officials of 9/11 Coverup; CIA Said to Use Saudis, Others for Illegal Domestic Spy Operations cryptogon.com
Im posting this with the following caveat: This should not be considered an endorsement of any aspect of the official story of how 9/11 was carried out. My take on this is that it might indicate some activities related to CIAs management of patsies ahead of the big day. Via: Florida Bulldog: It is nevertheless []
02:33
Experts spotted first-ever crypto mining campaign leveraging Kubernetes RBAC Security Affairs
Experts warn of a large-scale cryptocurrency mining campaign exploiting Kubernetes (K8s) Role-Based Access Control (RBAC).
Cloud security firm Aqua discovered a large-scale cryptocurrency mining campaign exploiting Kubernetes (K8s) Role-Based Access Control (RBAC) to create backdoors and run miners. The campaign was tracked as RBAC Buster, the experts reported that the attacks are actively targeting at least 60 clusters in the wild.
We have recently discovered the first-ever evidence that attackers are exploiting Kubernetes (K8s) Role-Based Access Control (RBAC) in the wild to create backdoors. reads the report published by Aqua. The attackers also deployed DaemonSets to take over and hijack resources of the K8s clusters they attack.
The attack chain starts with initial access via a misconfigured API server, then threat actors sent a few HTTP requests to list secrets and then made two API requests to gain information about the cluster by listing the entities in the kube-system namespace.
The attackers check for evidence of competing miner malware on the compromised server and achieve persistence by using RBAC to set up persistence.
Aqua analyzed the campaign after having set up K8s honeypots. The researchers explicitly exposed AWS access keys in various locations on the cluster they set up. The researchers noticed that threat actors used the access keys to try and gain further access to the targets cloud service provider account and obtain access to more reso...
02:09
Links 23/04/2023: Libreboot 20230423, Arianna 1.0.1, and PeaZip 9.2.0 Techrights
![]()
Contents
- GNU/Linux
- Distributions and Operating Systems
- Free, Libre, and Open Source Software
- Leftovers
- Defence/Aggression
- Transparency/Investigative Reporting
- Environment
- Finance
- AstroTurf/Lobbying/Politics
- Freedom of Information / Freedom of the Press
- Civil Rights/Policing
- Internet Policy/Net Neutrality
- Monopolies
- Gemini* and Gopher
-
GNU/Linux
02:05
California Meets 100% Of Water Requests For First Time Since 2006 cryptogon.com
Via: ZeroHedge: Due to a wet winter and record mountain snowpack, California will provide 100% of the water requested by cities and farms, marking the first time in nearly two decades. The office of California Governor Gavin Newsom released a statement Thursday that said, State water contractors to 100% of requested supplies for 29 public []
01:43
New Map of the Universe's Cosmic Growth Supports Einstein's Theory of Gravity SoylentNews
For millennia, humans have been fascinated by the mysteries of the cosmos:
Unlike ancient philosophers imagining the universe's origins, modern cosmologists use quantitative tools to gain insights into its evolution and structure. Modern cosmology dates back to the early 20th century, with the development of Albert Einstein's theory of general relativity.
Now, researchers from the Atacama Cosmology Telescope (ACT) collaboration have submitted a set of papers to The Astrophysical Journal featuring a groundbreaking new map of dark matter distributed across a quarter of the sky, extending deep into the cosmos, that confirms Einstein's theory of how massive structures grow and bend light over the 14-billion-year life span of the universe.
The new map uses light from the cosmic microwave background (CMB) essentially as a backlight to silhouette all the matter between us and the Big Bang.
"It's a bit like silhouetting, but instead of just having black in the silhouette, you have texture and lumps of dark matter, as if the light were streaming through a fabric curtain that had lots of knots and bumps in it," said Suzanne Staggs, director of ACT and Henry DeWolf Smyth Professor of Physics at Princeton University. "The famous blue and yellow CMB image [from 2003] is a snapshot of what the universe was like in a single epoch, about 13 billion years ago, and now this is giving us the information about all the epochs since."
[...] "We have mapped the invisible dark matter distribution across the sky, and it is just as our theories predict," said co-author Blake Sherwin, a 2013 Ph.D. alumnus of Princeton and a professor of cosmology at the University of Cambridge, where he leads a large group of ACT researchers. "This is stunning evidence that we understand the story of how structure in our universe formed over billions of years, from just after the Big Bang to today.'
Read more of this story at SoylentNews.
Saturday, 22 April
23:25
Harvest Of Glory Neighbourhood Assist Rodney District h+ Media
Harvest Of Glory Neighbourhood Assist Rodney District
Spin-a-Win Live is a enjoyable new Wheel of Fortune where you possibly can win as much as 40x your initial stake. You can also try out some of the a number of new aspect bets which may be out there. Mobile telephones with Android and iOS operating systems can obtain the 1xBet app quietly. You can contact the 1xBet in several attainable ways In addition to the above options, you can contact the house by way of a type . Today many bettors value this type of monetary transaction. In addition to the Online Poker , 1xBet also offers stay Poker.
- You can now enjoy a complimentary styling appointment in-store at select places.
- The hover side is in fact not applicable from your cellular and with much less display screen area, 1XBet has been smarter with group of the on-screen parts.
- You can be a part of and receive a welcome offer of as much as 1500 and one hundred fifty free spins too.
- Unlike the other gaming web sites which may be flashy and extremely colorful, the 1xBet Casino web site offers a more tamed down theme.
At this on-line lottery website you possibly can deposit with Bitcoin, Skrill, Entropay, EcoPayz, Bank transfer and far more. The finest $1 deposit casinos supply well-liked New Zealand fee processing choices like Visa, Mastercard, Skrill, Neteller, PayPal, paysafecard, and internet banking. Watch for these if you finish up trying to find the proper $1 deposit on line casino for you. You wont discover another place where the naked minimal deposit shall be you , and the minimum amount for 1xBet disadvantage will be 2 . Any different betting firms won t offer you such a giant payment methods selection. You will uncover completely different opinions about the design of the betting company.
Users have an curiosity in the actions of this workplace, promotions, inside which bonuses and 1xBet promo codes are offered. It is bonuses and codes on this case, the very first thing that interests the bulk of users. They present great discounts and offers that attract gamblers from all over the place in the world. Their banking alternate choices are well-managed and secure, along with their engaging bonuses. 1xBet has established a reputation as a casino that pays its gamers generously.
As a gambler, bet on sportsbooks and likewise watch your bankroll whereas at it. There are completely different sports such as the English premier and horse racing staking. No stay casino sport present can be full with no qualified and friendly host to deliver everything together. They are all educated to the best of requirements to ship distinctive service and an unparalleled gaming expertise.
Gzrnzv rhsazx installment payday loans casino slots gambling. Easily the preferred stay casino sport present is Deal or No Deal, which is predicated on its mega-popular televised counterpart proven on Channel four. Another unbelie...
06:08
1xbet Cricket Betting Evaluation h+ Media
1xbet Cricket Betting Evaluation
The registration button for 1XBET is positioned within the upper right corner of the platform. Yes, 1xbet is clearly focused on the Indian punter with a range of languages together with Hindi. Yes, one can utterly rely on the 1xbets legality in terms of Indian operations. This is possible as a outcome of license from the Cyprus authorities for the same. Wait until the end of the occasion and withdraw your winnings. You can choose to type video games by a particular recreation supplier of your choice, as well.
Click the registration button in the header and create a brand new account via any convenient technique in Bangladesh. 1xBets design could be very simple, and it is very intuitive what to press to get wherever you need. That particularly applies to the cellular app you will get anyplace within a couple of clicks. The application isnt in the Google Market, so you should obtain the applying as an APK file. Even if you are pleased along with your current operator, it could be value opening an account with 1XBet simply to compare odds and to make sure you are reaching one of the best worth on every guess.
- If you have an interest in the 1xBet app, you possibly can set up it from the official 1xbet web site and start betting quickly, and most easily.
- In June this 12 months, the Information and Broadcasting Ministry issued an advisory to print, digital and digital media to refrain from advertising online betting platforms.
- To keep away from future problems with logging into the private account, it is suggested to fix the username and password in the notes.
- 1xBet accepts rupees and works with many native payment strategies that Indians use frequently, such as Rupay, UPI, Google Pay, Bhim, PayTM UPI, and others.
- The welcome promo pack consists of five different deposit match deals so that you simply can spread out the freebies quite nicely.
- To activate a promo code, enter it in the special field when registering an account via the application.
No, you cant have a couple of 1xbet account, if the administration will find out that you have greater than 1 account, the administration will block all of your accounts. League choice subject will provide us with matches , select certainly one of them. The young group will try its best to reveal its most, because these gamers havent any critical trophies on the nationwide team level but.
The club managed to score only 25 factors within the final 24 rounds of the Premier League. The lottery 1xBet is introduced in a number of sections of the official web site of the corporate. Your bet might be calculated after the tip of the final event. To win, you have to guess a sure number of outcomes.
1xBet is the official companion of Spanish La Liga, Italian Serie A, Nigerian Premier League and Brazilian Serie A. The site is hugely in style throughout many nations an...